Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
217results about How to "Free from attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
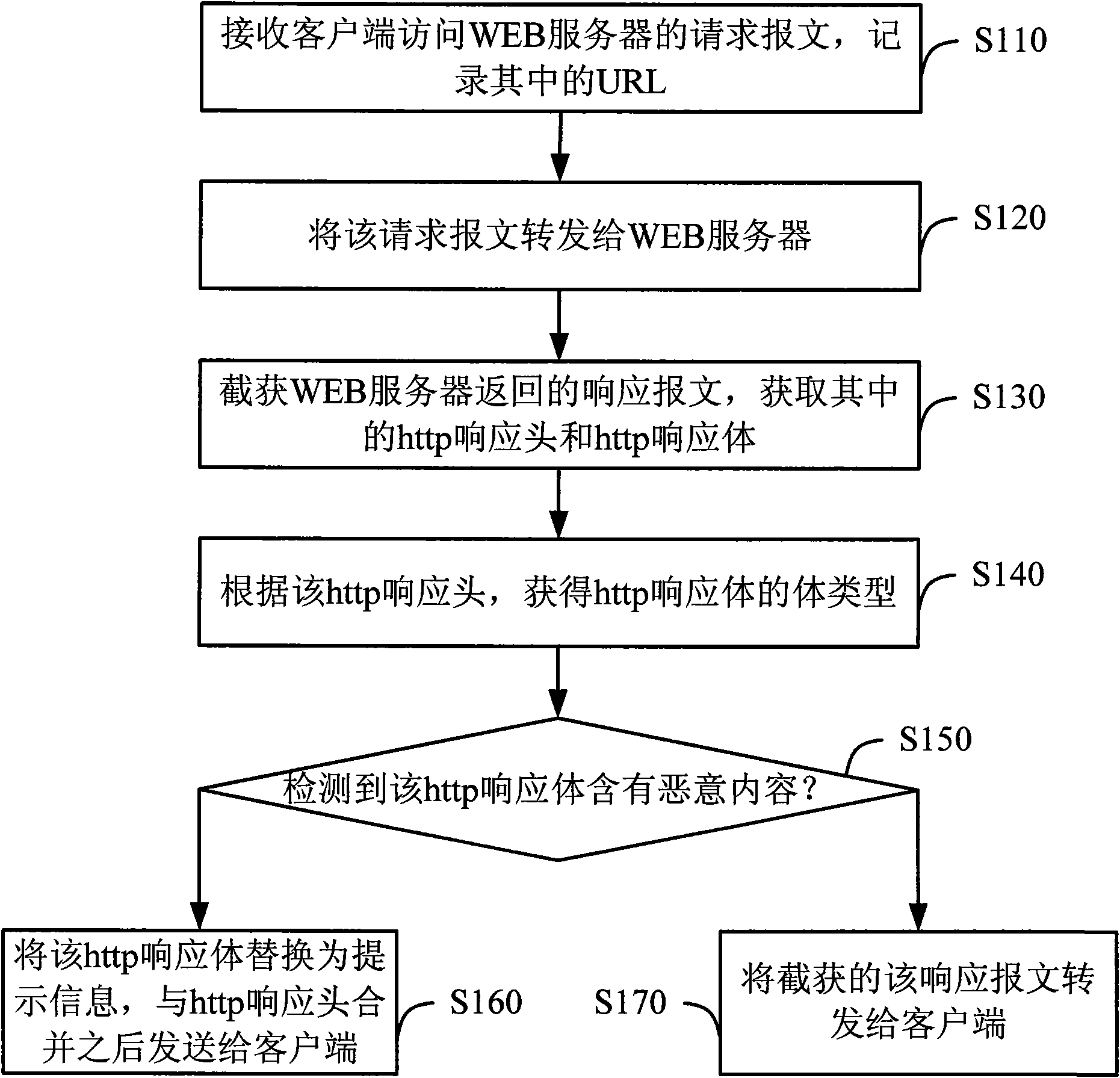
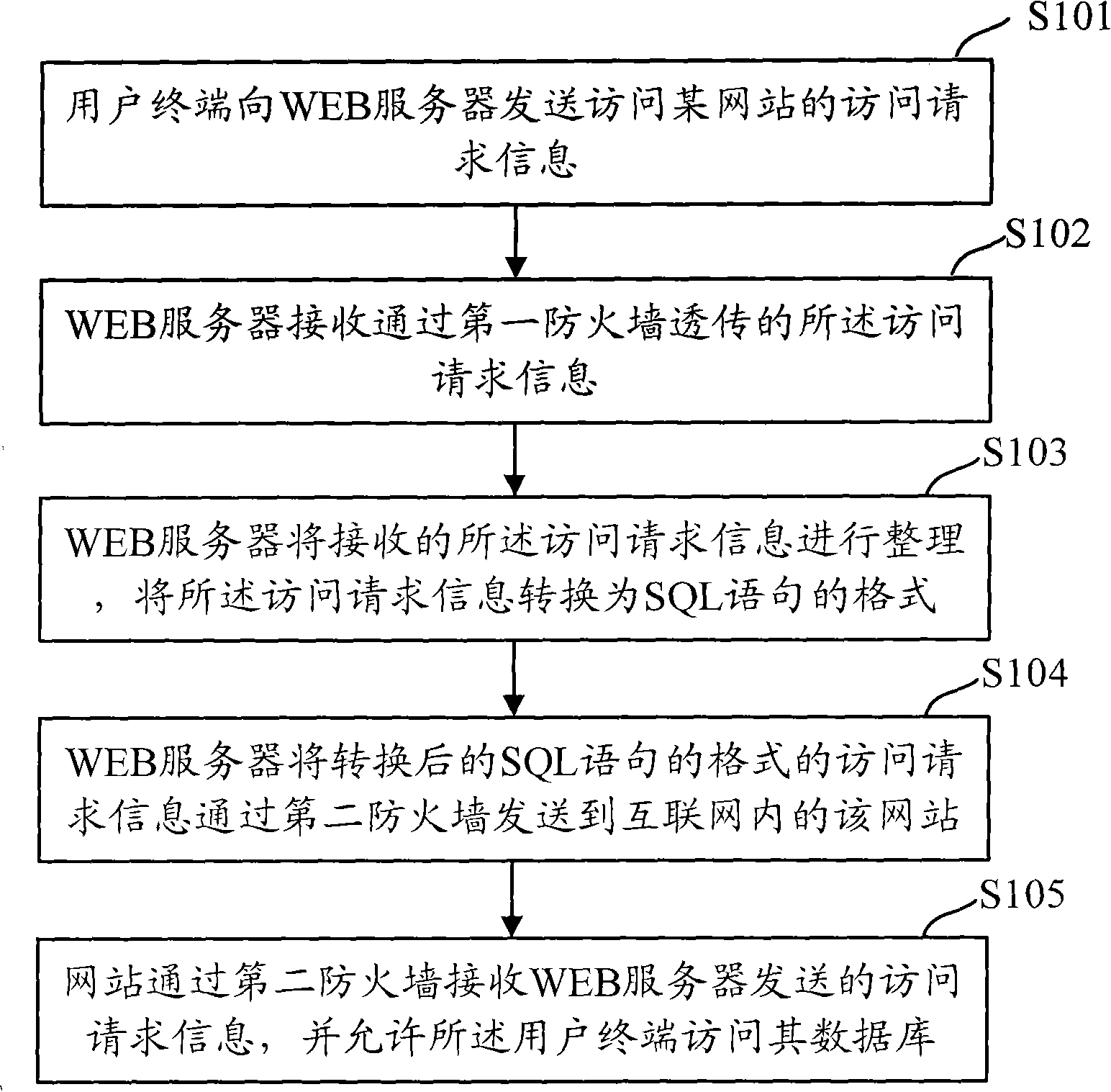
Attack detection and response method and device of WEB page
InactiveCN101888312AFree from attackAvoid manslaughterPlatform integrity maintainanceData switching networksWeb serviceResponse method
The invention discloses an attack detection and response method and a device of a WEB page, aiming at filtering the web page and protecting a client-side from the attack of malicious contents. The method comprises the following steps: intercepting the response message returned to the client-side by a WEB server, acquiring the response header and the response body in the response message, carrying out scanning detection on the response body, replacing the response body with prompt messages when the response body is detected to contain malicious contents, combining the prompt information with the response header and sending to the client-side. Compared with the prior art, the invention realizes the aim of precisely filtering the WEB page containing malicious contents such as Trojan horses and viruses and the like, protects the client-side from the attack of malicious contents and avoids interception of normal web page contents.
Owner:BEIJING VENUS INFORMATION TECH +1
Transmission control protocol (TCP) connection processing method and system and synchronization (SYN) agent equipment
The invention provides transmission control protocol (TCP) connection processing method and system and synchronization (SYN) agency equipment. The TCP connection processing method comprises the following steps of: receiving a first synchronization message sent by a client and used for requesting to establish first TCP connection with a server, and establishing second TCP connection with the client; and after the second TCP connection is established, if an access request message is sent by the client, controlling the establishment of the first TCP connection, and transmitting the access request message to the server. The invention improves SYN agency and starts to establish the connection with the sever only after the access request message sent by the client is received again when the SYN agency and the client complete three times of TCP hand shaking connection, thereby ensuring that the attack of TCP full-connection can not reach the server; and in addition, the invention enables that the server not only well defenses the attack of SYN FLOOD, but also avoids the attack of the TCP full-connection, thereby enhancing the safety of the WEB server.
Owner:RUIJIE NETWORKS CO LTD
Collaborative filtering recommendation method based on emotions and trust
ActiveCN107330461AIncrease credibilityImprove accuracyData processing applicationsCharacter and pattern recognitionDirected graphSupervised learning
The invention relates to the field of a recommendation system and discloses a collaborative filtering recommendation method based on emotions and trust. The collaborative filtering recommendation method comprises a step 1 of obtaining an explicit degree of satisfaction by normalizing an item scored matrix of users; calculating the similarity between scored items and items that are not scored according to a vector cosine method, obtaining an implicit degree of satisfaction by using the explicit degree of satisfaction and the similarity, and constituting an extended satisfaction matrix by the explicit degree of satisfaction and the implicit degree of satisfaction; a step 2 of calculating the score similarity and the preference similarity according to the extended satisfaction matrix, and obtaining an objective degree of trust generated by the users on the opinion similarity of the items by using the score similarity, the preference similarity and weights set by a supervised learning algorithm; and a step 3 of abstracting a user social network according to the user satisfaction interaction frequency, establishing a weighted directed graph based on the six-degree partition theory, and calculating a subjective degree of trust generated by familiarity among the users. The method of the invention realizes the collaborative filtering.
Owner:ANHUI NORMAL UNIV
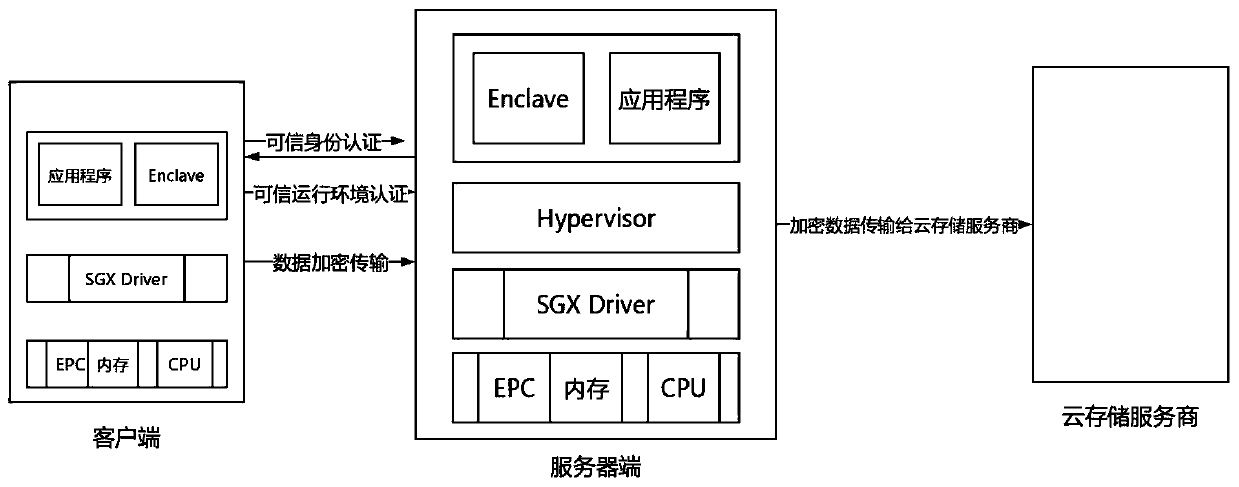
Secure cloud storage method based on SGX
The invention belongs to the technical field of trusted cloud computing, and particularly relates to a secure cloud storage method based on SGX. The method is suitable for a client / server architecturesystem based on SGX, and comprises the following steps: a trusted identity authentication step: a client performs bidirectional authentication of a trusted identity with a server through a trusted identity authentication module of the server, and establishes a session with the server after the trusted identity authentication is completed; a credible operation environment authentication step: after the client passes the credible identity authentication, the client verifies the legality of the operation environment of the server to the server through a credible operation environment authentication module of the server; a credible execution step: the client transmits the data to an endclave of the server through a credible channel, and the endclave encrypts the data; and a cloud storage step: the server side sends the encrypted data to a cloud storage service provider. According to the method, the problems of trusted authentication and key packaging of the client and the server are solved.
Owner:NORTHEASTERN UNIV
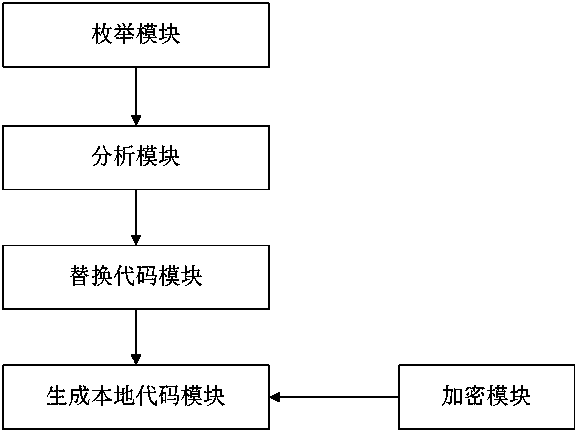
Method and equipment for protecting JAVA executable program
ActiveCN103413073AProtection logicProtection processProgram/content distribution protectionSoftware engineeringSoftware
The invention discloses a method and equipment for protecting a JAVA executable program. The method comprises the steps of creating a local dynamic chained library file, enumerating .class files in protected JAVA software, analyzing JVM codes in the .class files, drawing fragments of the codes at random, replacing the original position of the drawn fragments of the codes with call of a native method, and generating a derivative function in the local dynamic chained library file to achieve the function of drawing the fragments of the codes. By means of the method, the codes and logic of the JAVA software are effectively prevented from being reversed and broken, and the safety strength of the software is improved.
Owner:BEIJING SENSESHIELD TECH
Method for distinguishing baleful program behavior
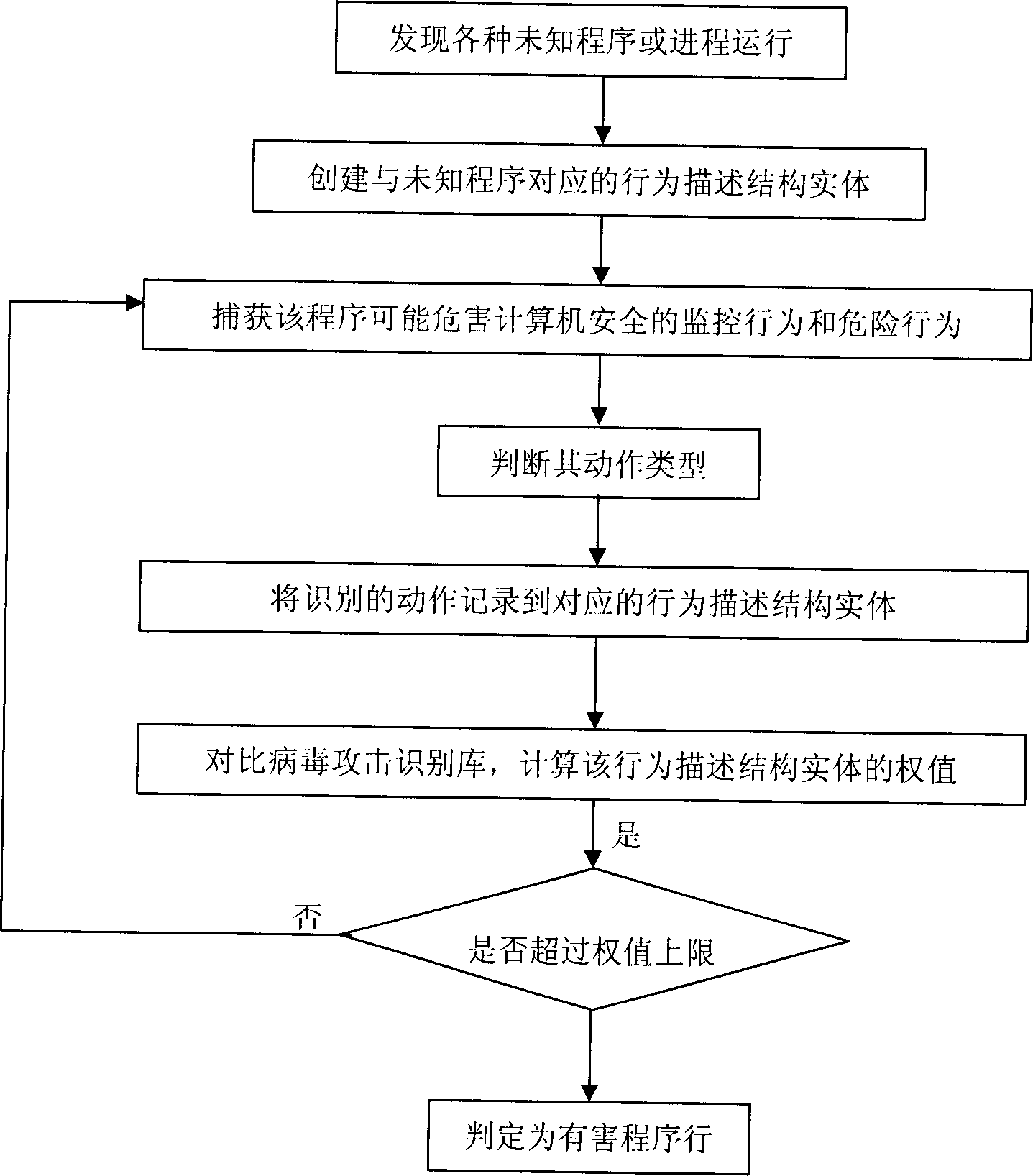
InactiveCN1801030AAccurate checkFree from attackDigital data processing detailsUnknown procedureProgram behavior
The invention discloses a specification method of harmful program based on the virus attack identification base of state movement set, which comprises the following steps: 1.1) monitoring and recording the movement behavior of unknown program; 1.2) integrating the recorded program to compare with the virus identification regular base; 1.3) judging the compared result whether the result is harmful program behavior; alarming or stopping the operation of program if yes; continuing operating and returning to the step 1.1) if not. The invention analyses the unknown program behavior without depending virus code, which improves the efficiency and precision.
Owner:MICROPOINT WISDOM (BEIJING) INFORMATION SECURITY TECH CO LTD
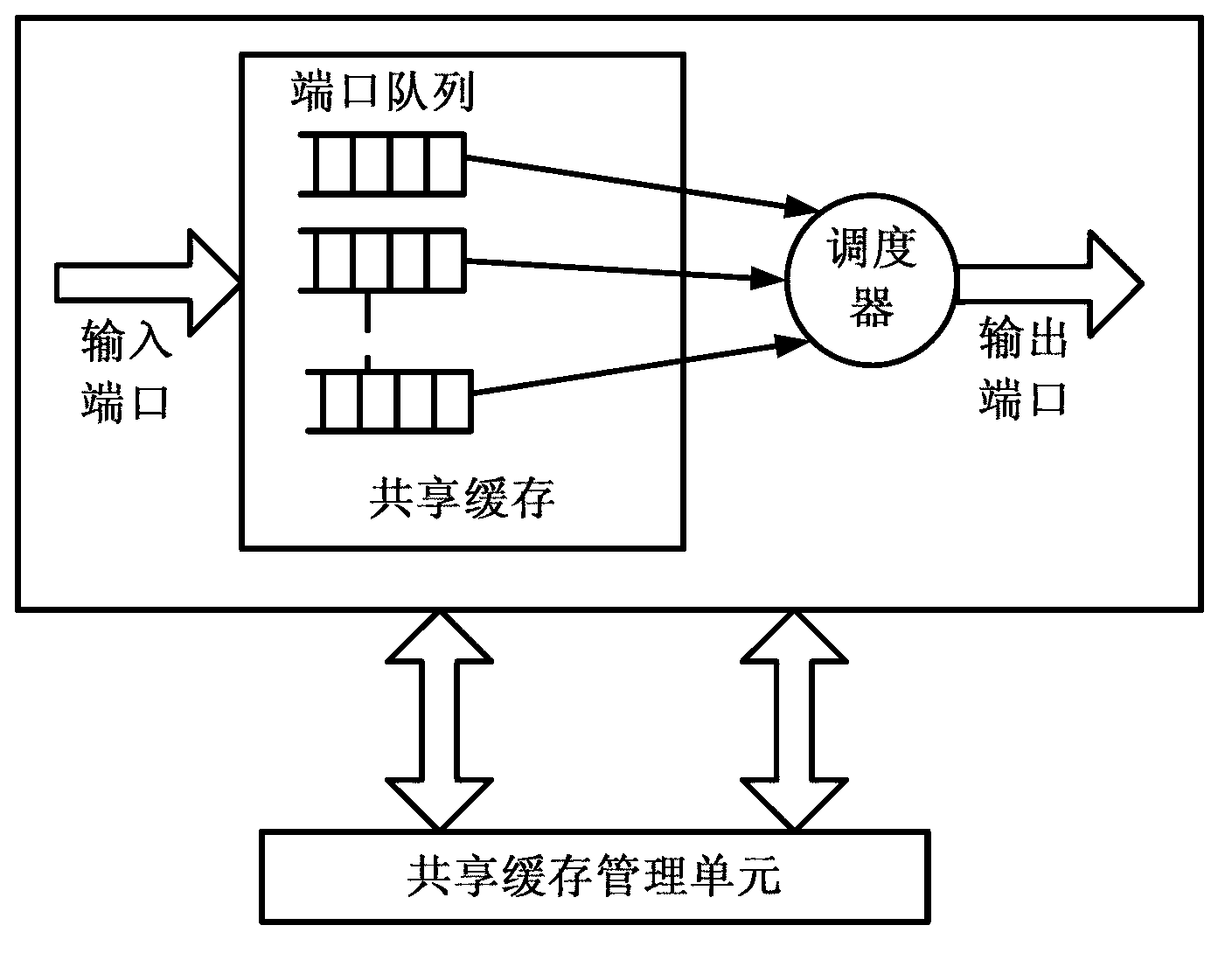
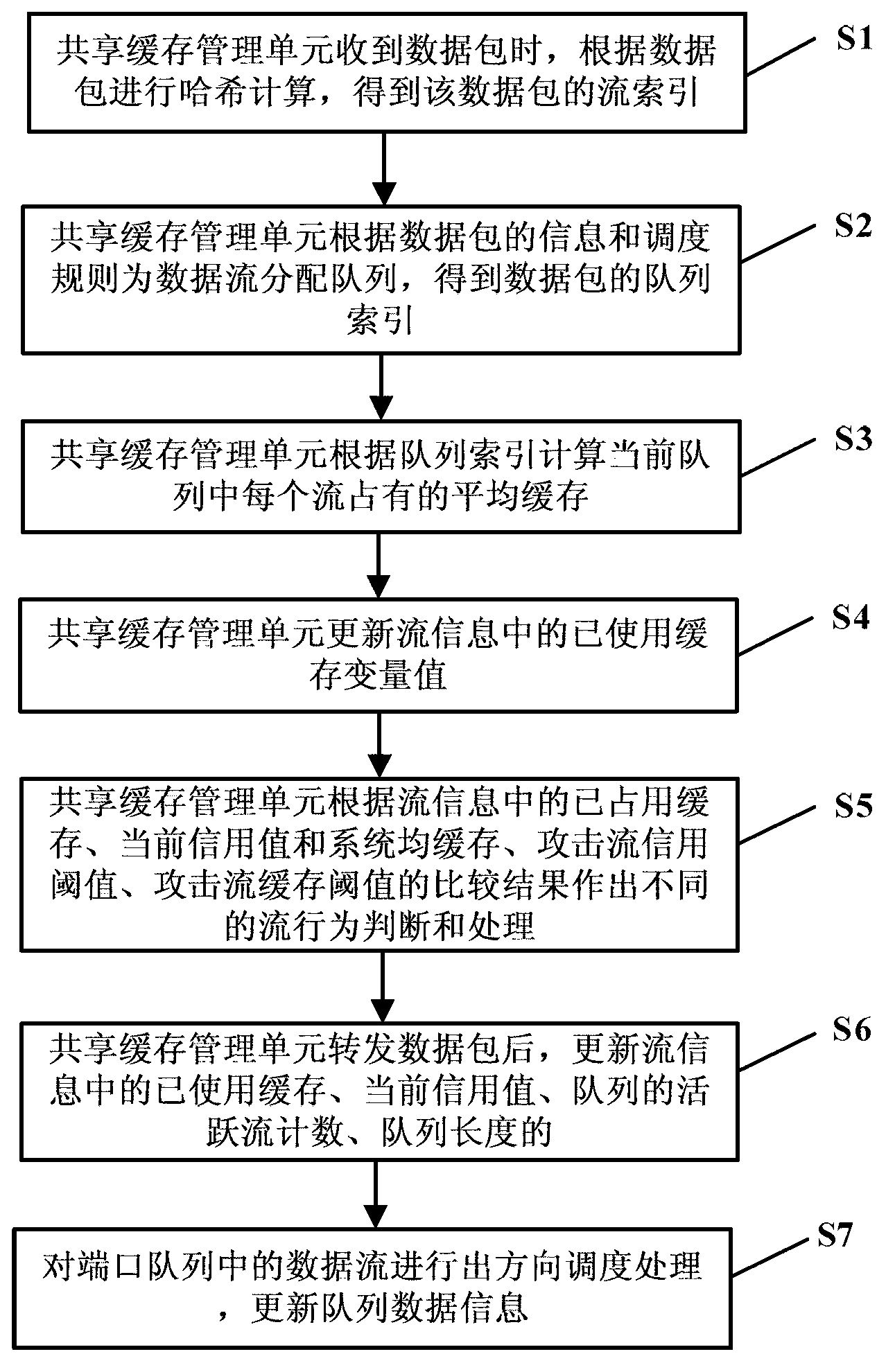
Control method and control device of cache resource of shared cache type Ethernet switch
ActiveCN103023806AEfficient schedulingControl congestionData switching networksArray data structureNetwork packet
The invention discloses a control method and a control device of a cache resource of a shared cache type Ethernet switch, and relates to the communication field. The method includes following steps: receiving a data package and simultaneously performing hash calculation, then obtaining a flow index of the data package, and retrieving a data flow array according to the flow index to obtain flow information; retrieving a queue array according to a queue index to obtain the length of a current queue and a flow number of the queue; updating a used cache variable value of the flow information according to the length of the data package; carrying out different judging treatments of different flow behaviors according to a comparative result of an occupied cache value and a current credit value of the flow information with an average cache value, an attack flow credit threshold value, an attack flow cache value of a system; and updating the used cache value, the current credit value, an active flow count of the queue, the length of the queue in the flow information after forwarding the data package. The control method and the control device of the cache resource of the shared cache type Ethernet switch can respond timely according to a current use condition of the cache, discover an attack behavior rapidly, prevent the attack behavior from consuming the cache resources, and control network congestion effectively.
Owner:FENGHUO COMM SCI & TECH CO LTD
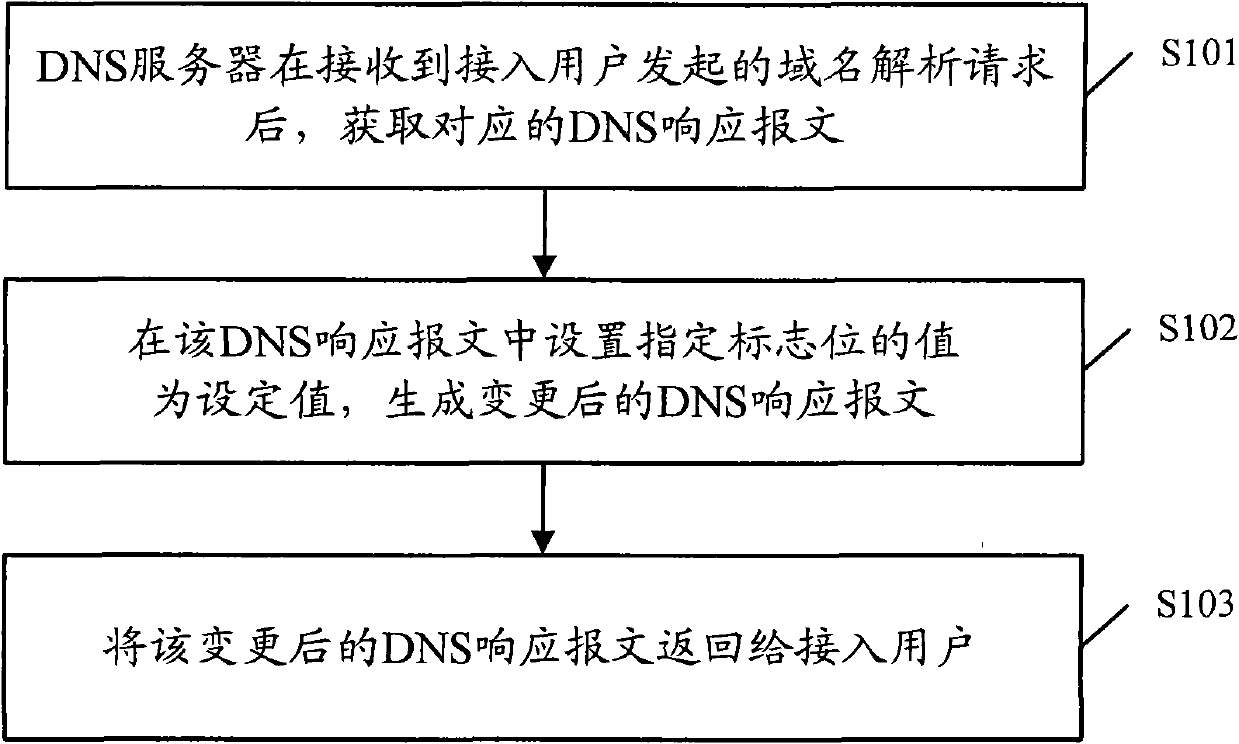
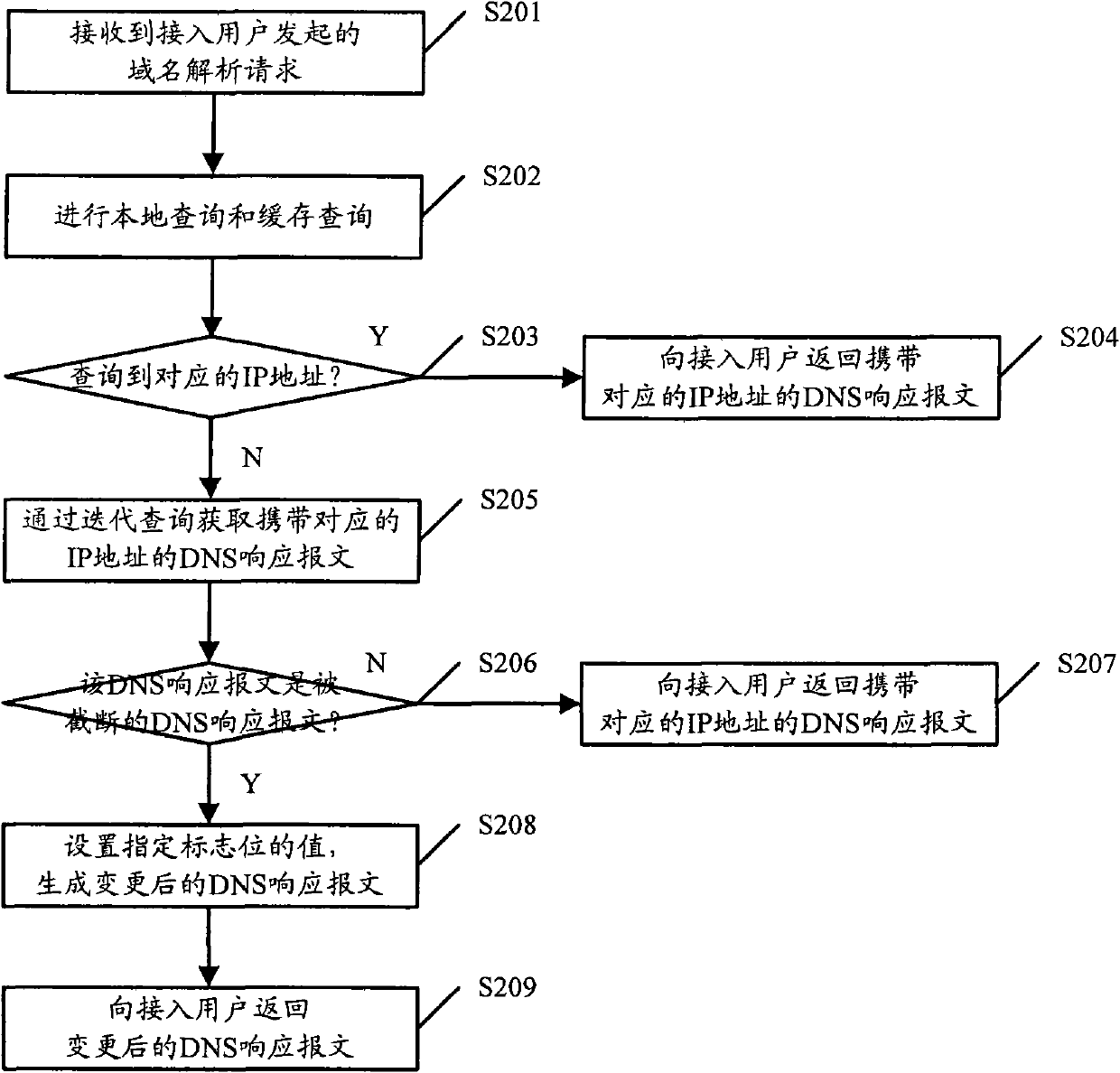
Domain name resolution method, DNS (Domain Name Server) server and system
ActiveCN102025794ACircumvent parsing queriesShorten analysis timeTransmissionUser Datagram ProtocolName resolution
The invention discloses a domain name resolution method, a DNS (Domain Name Server) server and a system. The method comprises the following steps of: after the DNS server receives a domain name resolution request initiated by an accessed user, a corresponding DNS response message is obtained; when the obtained DNS response message is a disconnected DNS response message based on a UDP (User Datagram Protocol), a value of a specified zone bit is set in the DNS response message to generate a DNS response message after change; after the value of the specified zone bit is set to indicate that the accessed user receives the DNS response message after change, the domain name resolution request initiated in a TCP (Terminal Control Protocol) mode is cancelled and the DNS response message after change is returned to the accessed user. By adopting the scheme, the domain name resolution search based on the TCP mode is avoided, therefore, the system can not be attacked by the TCP mode, the DDOS (Distributed Denial of Service) attack resisting capability of the system is effectively increased, and the domain name resolution efficiency of the system is improved.
Owner:CHINA MOBILE GRP BEIJING
Anti-flavivirus envelope E protein monoclonal antibody and application thereof
ActiveCN101891806AGood broad-spectrum anti-flavivirus effectInfection fromFungiBacteriaCell strainProtein.monoclonal
The invention discloses an anti-flavivirus envelope E protein monoclonal antibody and application thereof. The anti-flavivirus envelope E protein monoclonal antibody of the invention is secreted by a mouse source hybrid tumour cell strain D2-2A10G6 with the preservation number of CGMCC No. 3292. The anti-flavivirus monoclonal antibody of the invention can be specifically combined with the function epitope of flavivirus envelope E protein. The amino acid sequence of the functional epitope of envelope E protein is SEQ ID NO: 17. The monoclonal antibody of the invention is subject to screening by indirect immunofluorescent method, and indirect enzyme-linked immunization is used for evaluating the specificity and affinity when being combined with antigen. By adopting the monoclonal antibody or immunoconjugate of the invention, flavivirus infection cell can be blocked and suckling mouse can be protected from virus attack, thus achieving the effect of inhibiting virus infection. The monoclonal antibody or immunoconjugate of the invention also can be used for flavivirus envelope E protein detection.
Owner:MICROBE EPIDEMIC DISEASE INST OF PLA MILITARY MEDICAL ACAD OF SCI
Release layer paste and method of production of a multilayer type electronic device
InactiveUS20070190251A1Enable formationPrintabilityOther chemical processesFixed capacitor electrodesAdditive ingredientSolvent
A release layer paste used for producing a multilayer type electronic device and forming a release layer of a thickness of 0.05 to 0.1 μm, used in combination with an electrode layer paste including one or more solvents selected from limonene, dihydroterpinyl methyl ether, α-terpinyl acetate, terpinyl methyl ether, isobornyl acetate, caryophyllene, 1-dihydrocarvyl acetate, menthone, menthyl acetate, perillyl acetate, carvyl acetate, d-dihydrocarvyl acetate, and butyl carbitol acetate and a binder comprised of ethyl cellulose, including a ceramic powder, organic vehicle, plasticizer, and dispersion agent, the organic vehicle containing a binder having polyvinyl acetal as its main ingredient, a ratio (P / B) of the ceramic powder with respect to the binder and plasticizer being controlled to 1.33 to 5.56 (however, excluding 5.56).
Owner:TDK CORPARATION
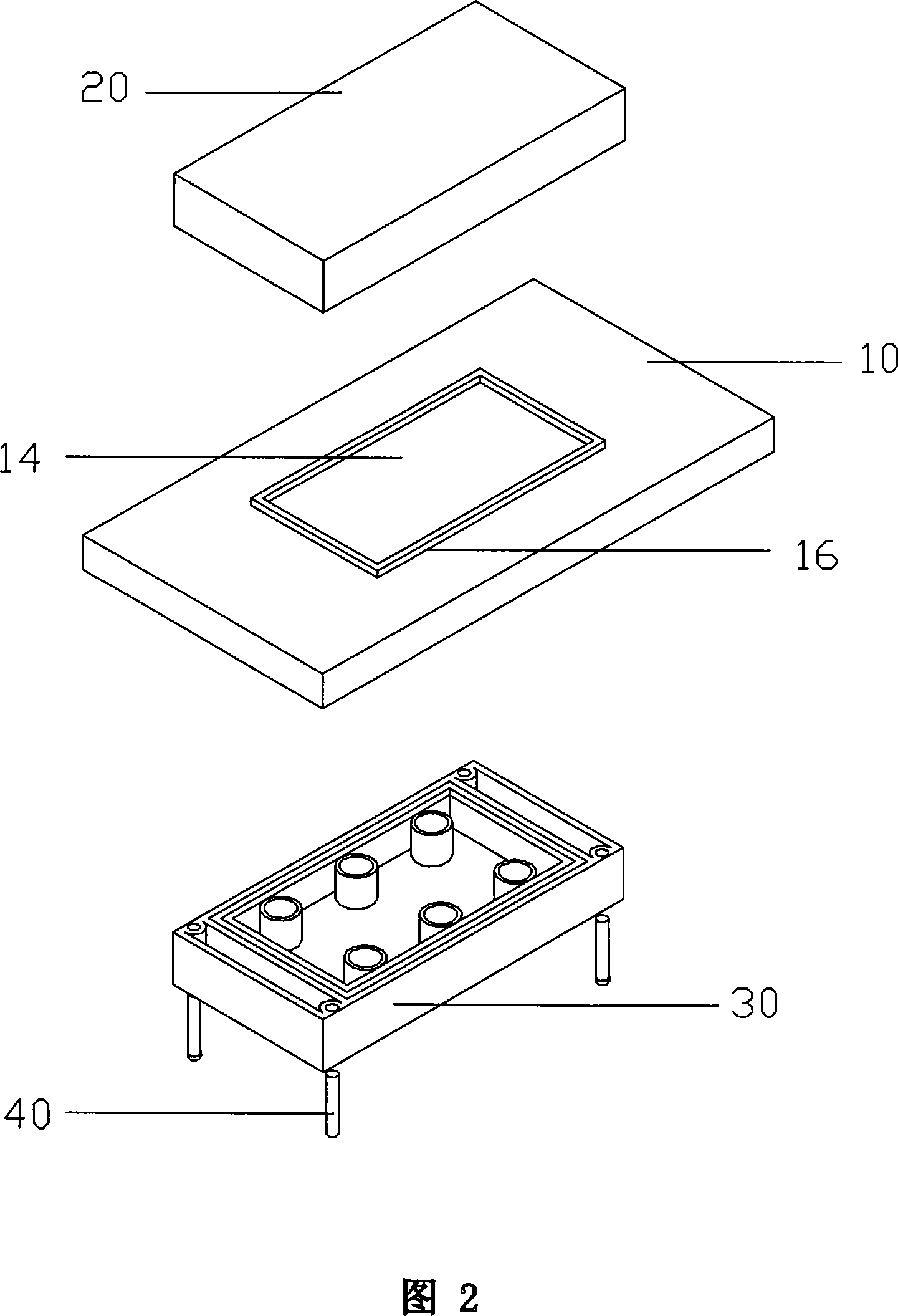
Secure protection cover
ActiveCN101128093AFree from attackCircuit security detailsCasings/cabinets/drawers detailsFlexible circuitsEngineering
The utility model provides a safety cover, belonging to the field of electronic circuit protection , used for covering a protected area of a protected circuit board and providing protection for the elements in the protected area. The safety cover comprises a flexible circuit board which can be folded up to form a holding space with an opening on a side of the holding space and the flexible circuit board covers the protected area of the protected circuit board, covering the elements of the protected area; wherein, the flexible circuit board can trigger a circuit to erase or damage the message on the elements of the protected area when the flexible circuit board is under physical attack. The utility model has the advantages that protecting the important elements from suffering attack by covering the important elements of the circuit board via the flexible circuit board with a holding space.
Owner:PAX COMP TECH SHENZHEN
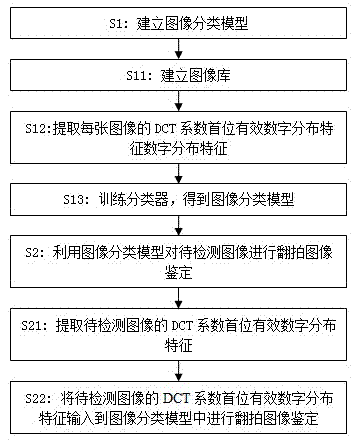
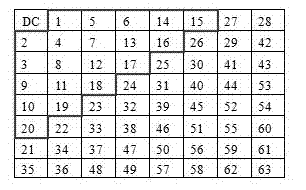
Identification method of coping digital image
InactiveCN102521614AValid identificationFree from attackCharacter and pattern recognitionGraphicsPattern recognition
The invention belongs to the multimedia information safety field and particularly relates to an identification method of a coping digital image. The method comprises the following steps that: (1), an image classification model is established; more particularly, an image library is established and a copying image and a natural image are stored in the image library; discrete cosine transform (DCT) coefficient matrixes of all images in the image library are extracted and DCT coefficient first effective digit distribution characteristics of all the images are extracted; and a classifier is trained to obtain an image classification model; and (2), the image classification model is utilized to treat a detected image to carry out coping image identification. According to the invention, on the basis of a DCT coefficient first effective digit distribution change during a secondary image obtaining process, statistics of the DCT coefficient first effective digit distribution characteristics is carried out and the characteristics are input into the classifier to carry out study, so that the image classification model is obtained; and the classification model is utilized to analyze a digital image, so that it can be effectively identified whether the digital image is a copying image or not.
Owner:SUN YAT SEN UNIV
High-temperature-resistant environment-friendly composite pigment and production method thereof
InactiveCN104861742AImprove light fastness and weather resistanceBright colorPigment physical treatmentPigment treatment with non-polymer organic compoundsWeather resistanceNickel oxides
The invention relates to the technical field of chemical pigment fabrication and discloses a high-temperature-resistant environment-friendly composite pigment and a production method thereof. Inorganic titanium yellow pigment carriers are enveloped with organic yellow pigments to form the composite pigment. The preparation method comprises processing titanium dioxide and nickel oxide into mixed-phase inorganic titanium yellow pigment carriers to be mixed with organic yellow pigments with negative charges, and performing enveloping treatment through positive and negative charge particle attraction action to achieve composition of organic and inorganic pigments. By nanometer fine processing, surface charges are increased, the envelop is dense, the structure force is large, the composition process is environmentally friendly, the composite pigment is non-toxic, the composite titanium yellow carriers can protect the sensitive organic pigments from ultraviolet attack like ultraviolet absorbers, and accordingly, the weather resistance and the light resistance of the pigment are improved greatly, and the pigment has the advantages of being environmentally friendly, weather resistant, light resistant, heat resistant, anti-ageing, bright in organic pigment color and high in tinting strength.
Owner:HUNAN JUFA TECH
Method for Anti-debugging
InactiveCN105793860AGuaranteed uptimeFree from attackSoftware engineeringHardware monitoringSoftware engineeringEmbedded system
The present invention relates to an anti-debugging method employed by an anti-debugging device. The anti-debugging method includes: a child process generation step; a parent process monitoring step in which a parent process is monitored by a child process; and a child process monitoring step in which the parent process monitors the child process.
Owner:INKA ENTWORKS INC
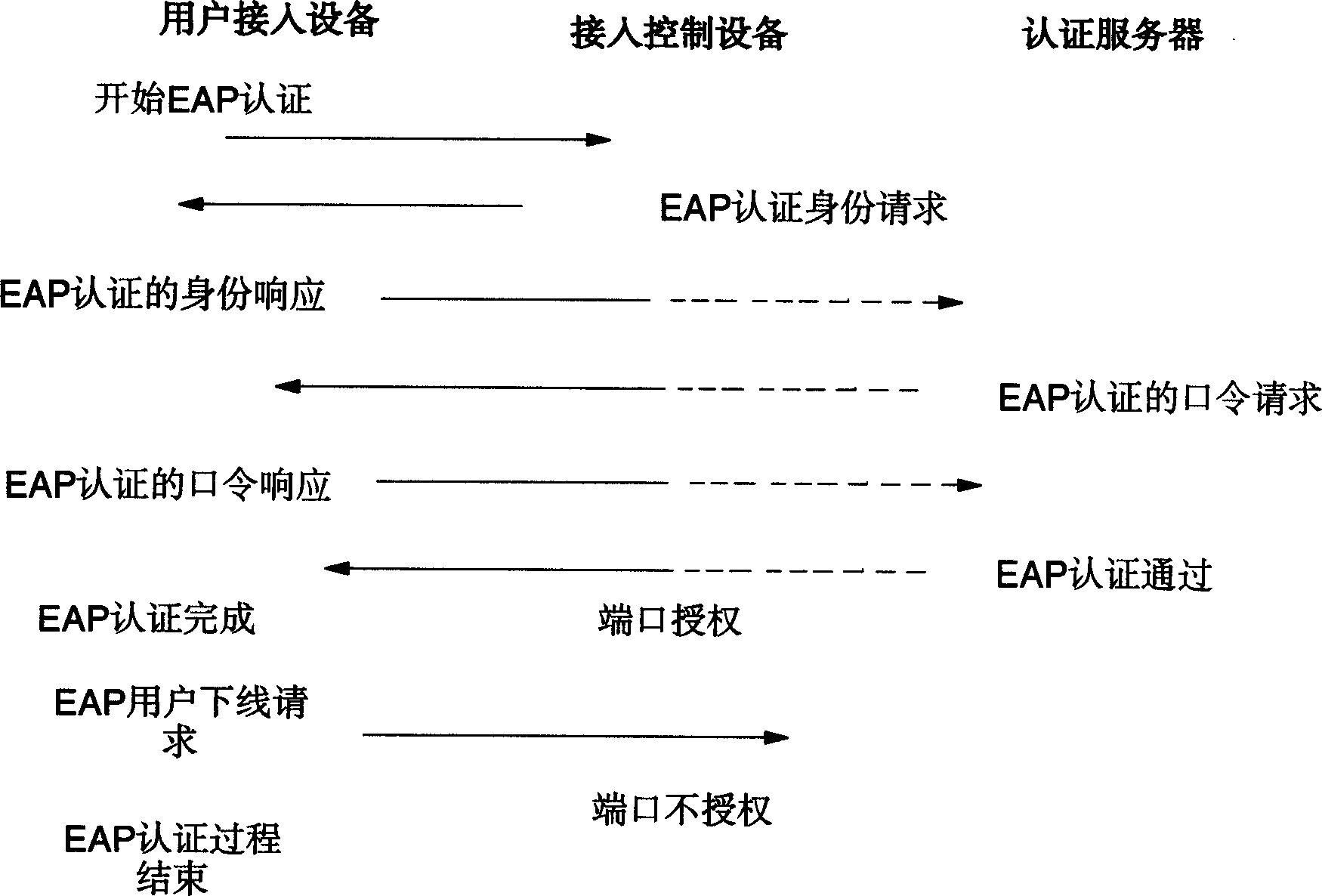
Method and apparatus for VLAN based network access control
InactiveCN1486032AEasy to manageFree from attackUser identity/authority verificationData switching by path configurationVirtual LANIp address
The invention refers to net access control method based on virtual LAN. The method is: configures the access authority of ports on LAN user access appliances, when a user access in LAN, user access appliance examines the authority state of application port; carries on the user LAN access control according to the authority state. The device includes: user access appliance, access control applianceand access identification server, the user accesses the net through user access appliance, and carries net access authentication through access control appliance and access authentication server.
Owner:HUAWEI TECH CO LTD
Pathogen vaccines and methods of producing and using the same
ActiveCN108697778AFree from attackAntibacterial agentsCosmetic preparationsResistant bacteriaVaccination
The present invention provides vaccine compositions and methods of producing such compositions. Other embodiments of the invention include methods of treating a pathogen infection, methods of vaccinating a subject against a pathogen infection, and methods for treating an antibiotic-resistance bacterial infection in a subject in need thereof. In further embodiments, the invention includes methods of decreasing the level of a pathogen in a subject having a pathogen infection, methods of increasing the surviving rate of a subject having a pathogen infection, methods of reducing the level of painassociated with a pathogen infection, and methods of reducing the level of distress associated with a pathogen infection in a subject in need thereof. Novel scaffold compositions and opsonin-bound orlectin-bound pathogen compositions, and uses thereof, are also provided herein.
Owner:PRESIDENT & FELLOWS OF HARVARD COLLEGE
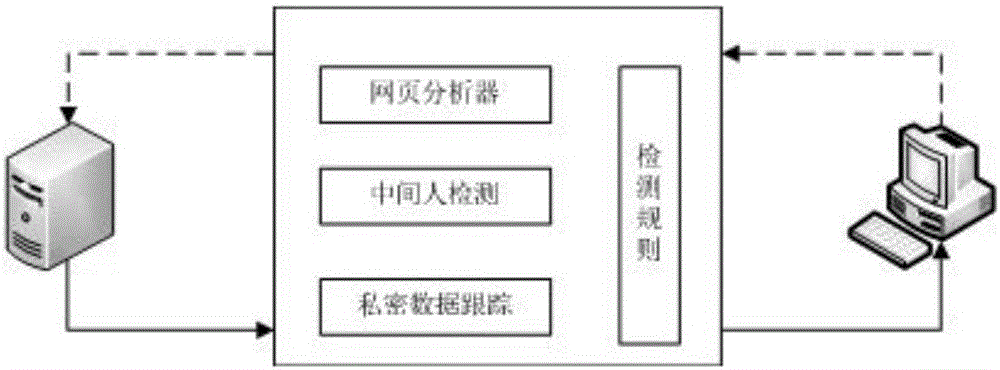
SSL strip defense method based on historical information
The invention discloses a defense method aiming at SSL strip attack and based on historical information. The defense method includes: establishing detection rules, and creating configuration files of all safe sites browsed by a user through the detection rules, wherein each configuration file contains accurate using status of the corresponding site; defaulting that an attacker successfully realizes MITM (man in the middle), establishing a MITM detector, and using the configuration file and the detection rules, wherein once a page is tampered maliciously by the MITM, a system can recognize and inform the user of a network attack while stopping connection of the attacker; establishing a private data tracking module, inserting JavaScript code into a login page, and detecting whether a login request contains plaintext private information or not to completely eradicate leakage of private information. By detecting client requests and server response content, the user can be protected from the SSL strip attack, and certificate of the user can be protected from being stolen by illegal means, so that safety and reliability when the user accesses websites are improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
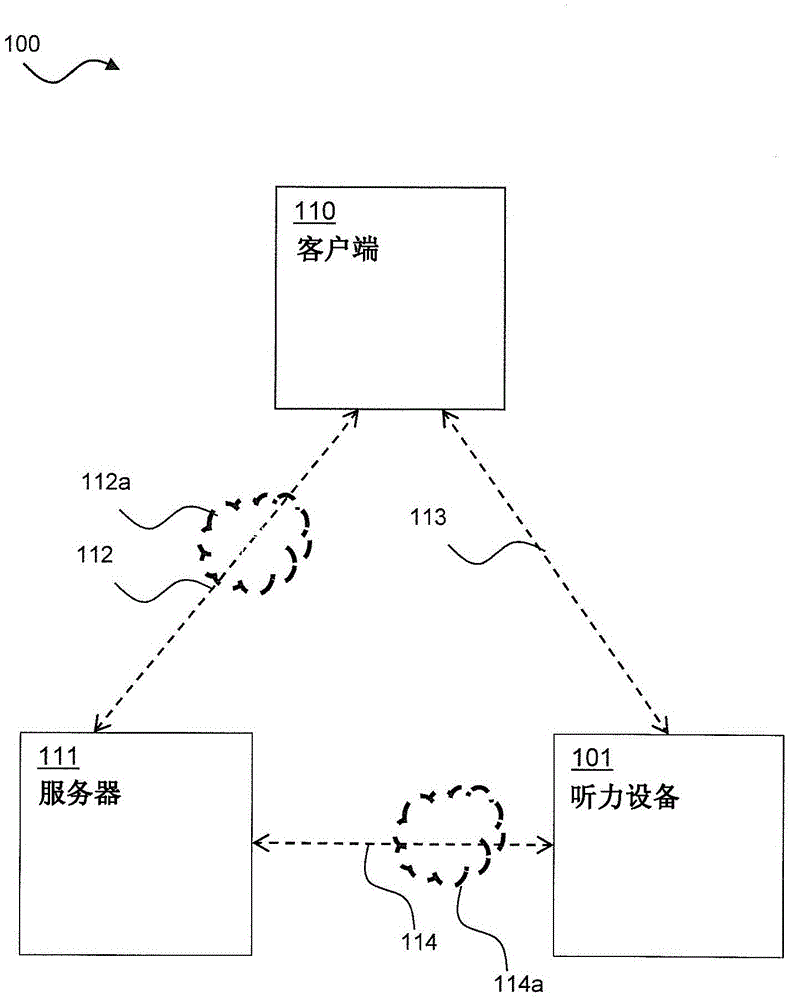
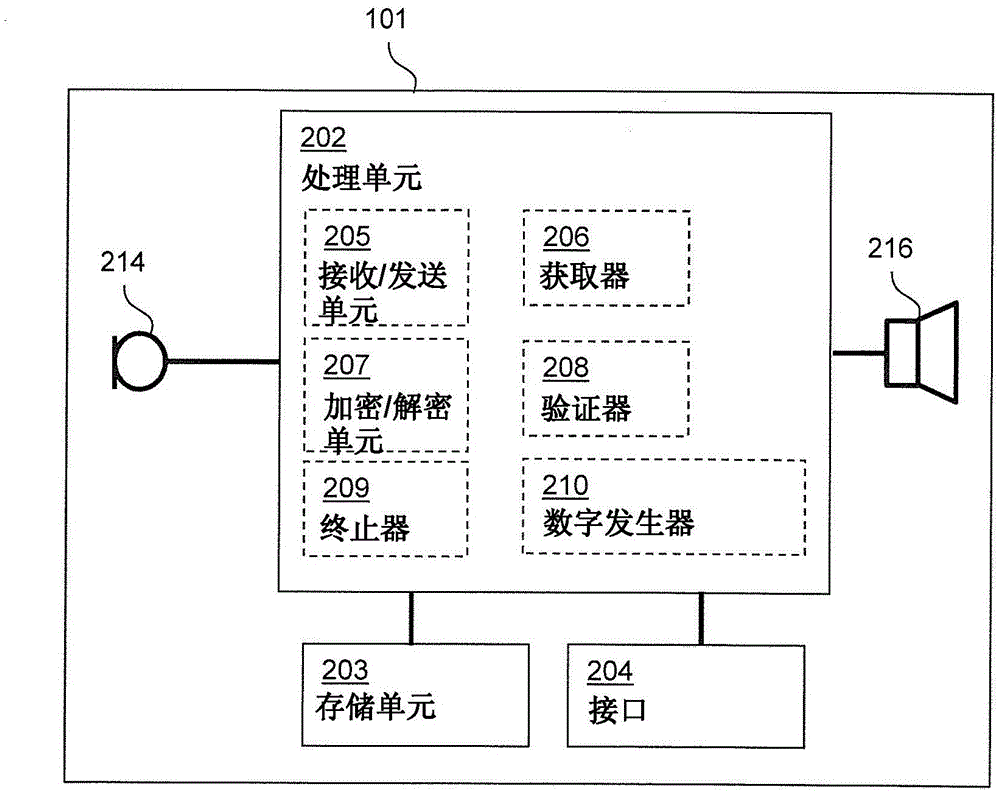
Hearing device with communication protection and related method
InactiveCN105704113AFree from attackUser identity/authority verificationDigital data protectionComputer securityCorrelation method
A hearing device includes: a processing unit configured to compensate for hearing loss of a user of the hearing device; and an interface; wherein the processing unit is configured to: receive a session request for a session via the interface, obtain and store a session key, encrypt the session key based on a hearing device key, send a session response comprising the encrypted session key, and receive session data in the session via the interface.
Owner:GN HEARING AS
Transdermal immune influenza multivalent vaccine and preparation method thereof
InactiveCN101450209AEnhanced antigen presentation functionFacilitated DiffusionPowder deliveryAntiviralsBALB/cAdjuvant
The invention provides a transdermal immunity flu polyvalent vaccine and a preparing method. The transdermal immunity flu polyvalent vaccine comprises transdermal immunity adjuvant, flu polyvalent vaccine antigen, permeation agent and medical dressing. The flu polyvalent inactivation or attenuated live vaccine is differ from prior vaccine immunity approach and adjuvant. A result through permeation purpose immunity to Balb / c mouse, ferret, monkey and human body improves that the transdermal immunity flu polyvalent vaccine can generate IgA and IgG antibody with high valency, namely, can induce immune system and mucosal immune simultaneously, also can be used for immunoprophylaxis to popular flu and highly pathogenic avian influenza.
Owner:MICROBE EPIDEMIC DISEASE INST OF PLA MILITARY MEDICAL ACAD OF SCI
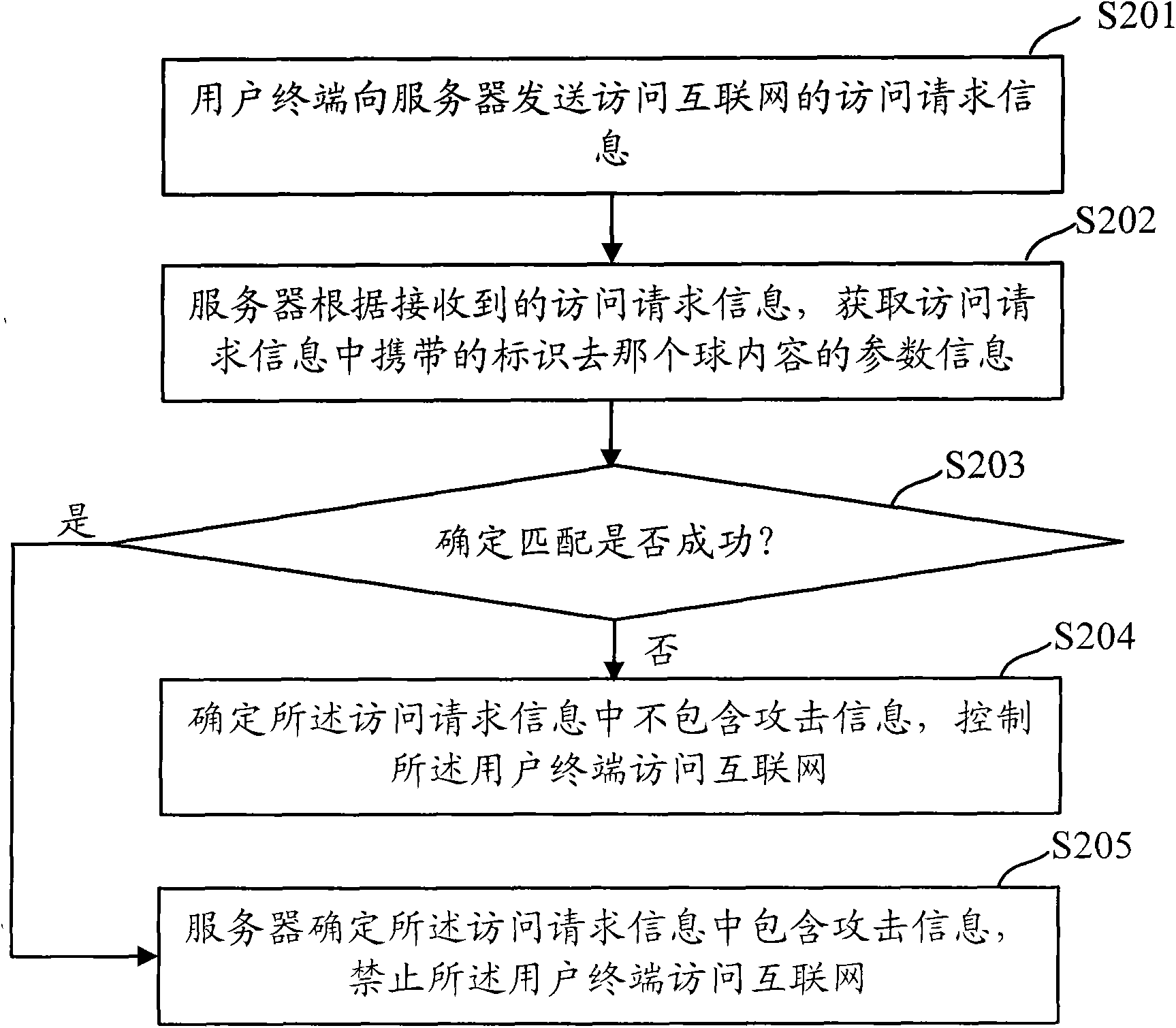
Method, system and device for user terminal to access internet
ActiveCN102082810AAccess forbiddenFree from attackTransmissionSpecial data processing applicationsThe Internet
The invention discloses a method, system and device for a user terminal to access internet and solves the problem in the prior art that the user terminal cannot safely access the internet, so that websites in the internet are attacked. The method comprises the following steps of: acquiring parameter information carried by access request information, transmitted by the user terminal and matching the acquired parameter information with keywords saved in a keyword database by a server; and when the matching is successful, prohibiting the user terminal from accessing the internet. In the embodiment of the invention, the acquired parameter information of the access request information is matched with the keywords saved in the keyword database by the server, thereby determining whether the access request information carries the attack information or not; and when the access request information carries the attack information, the user terminal is prohibited from accessing the internet, thereby ensuring the safety of the user terminal to access the internet and ensuring that the internet is prevented from being attacked.
Owner:中国移动通信集团广西有限公司
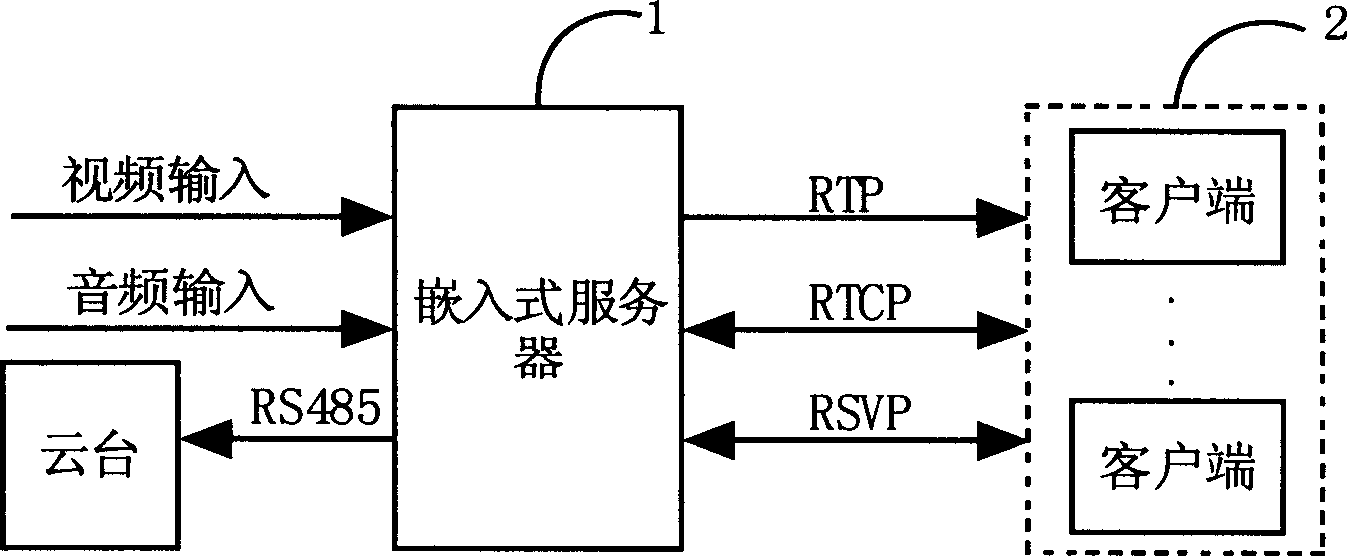
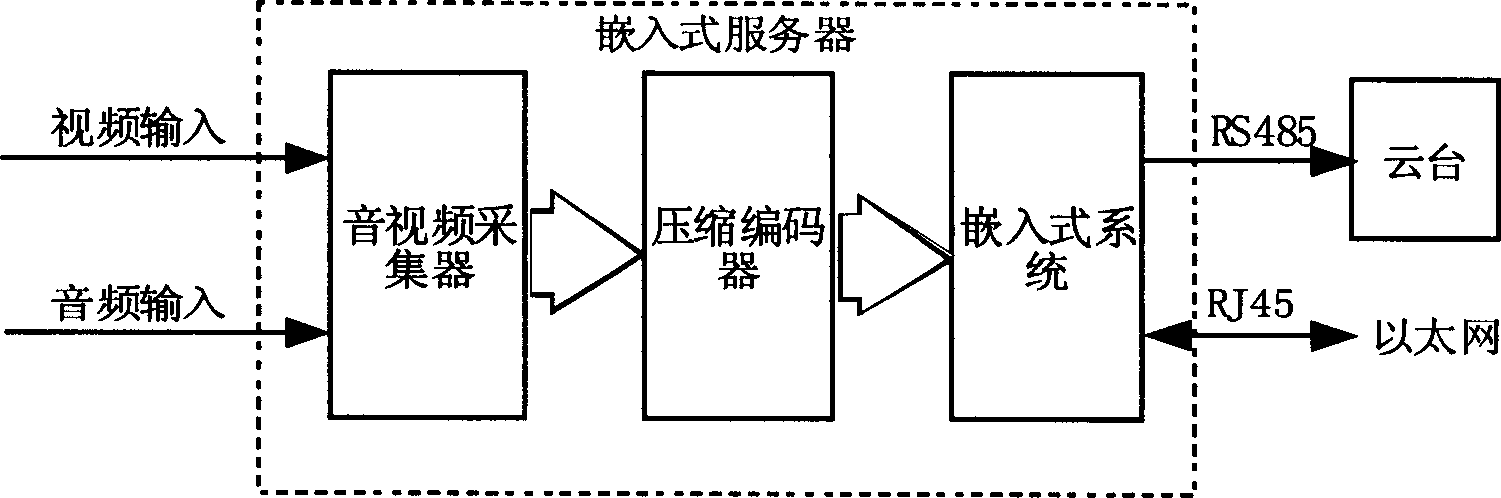
Embedded Linux multimedia signal acquisition and processing apparatus and its transmission method
InactiveCN1805356AReduce occupancyFree from attackData switching by path configurationSecuring communicationVideo monitoringRemote area
The invention relates to an embedded Linux multimedia information collection processing device and relative transmission method. Said device comprises: an embedded server, several client terminals and a cloud platform, wherein, said embedded server and cloud platform are connected via the RS485 bus; the embedded server and the client terminal process interactive control and data transmission via the RTP / RTCP to use the RSVP to realize QoS resource preparation. The invention uses safety strategy to prevent the impact on the server to confirm the safety of server authorization and safety of flow media in the network transmission. The network self-adaptive strategy of user terminal can make said device realize the balance between the band width process and the replay possibility when transmitting data in limit network. The invention can apply the remote control area, especially the unattended remote area to apply stable real-time interactive acoustic-virtual detection.
Owner:SOUTH CHINA UNIV OF TECH
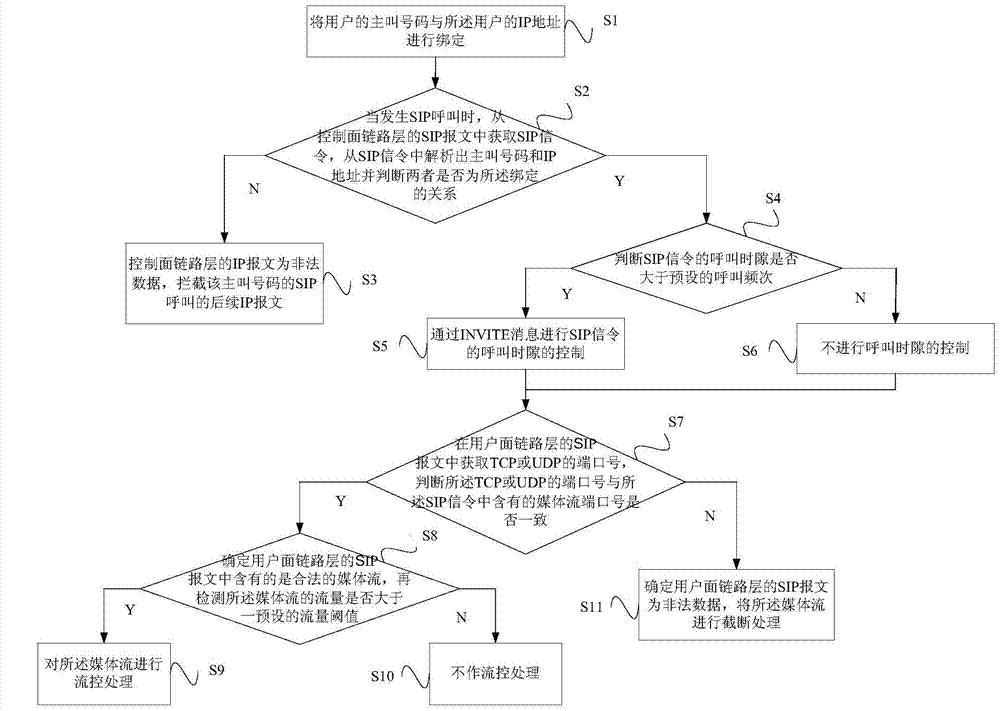
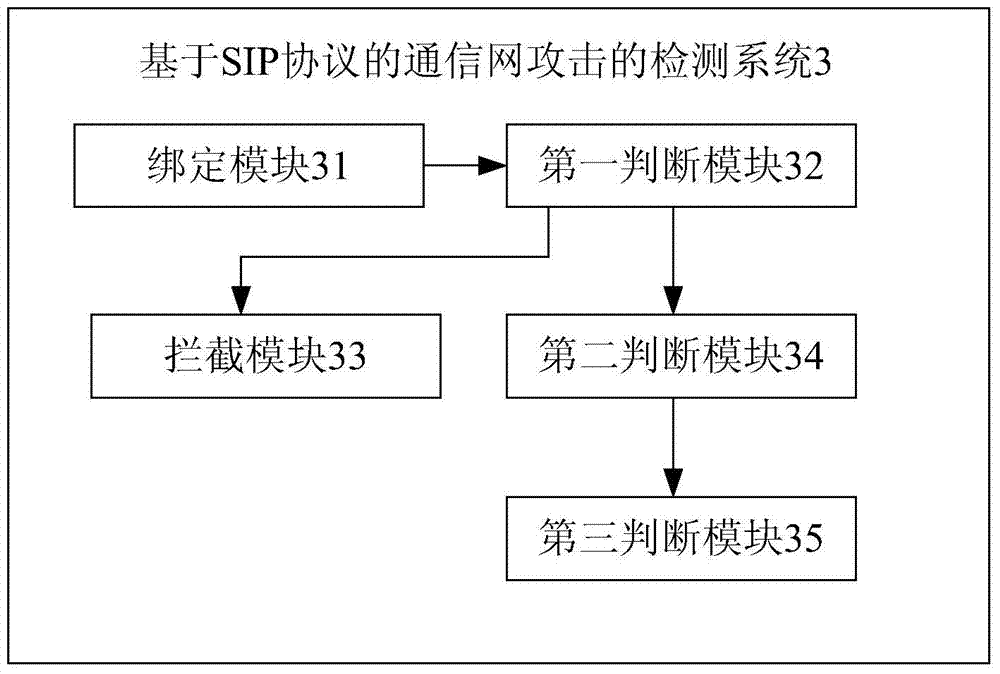
SIP-protocol-based method and system for detecting communication network attack
The invention provides an SIP-protocol-based method and system for detecting communication network attack. The method comprises the following steps of binding a calling number of a user with an IP (Internet Protocol) address of the user; when an SIP call is initiated, obtaining SIP signaling from an SIP message of a control plane link layer, obtaining a calling number and an IP address from the signaling through analysis, and judging whether the calling number and the IP address have binding relationship; intercepting follow-up messages of the SIP call of the calling number if that the calling number and the IP address have binding relationship is determined and IP messages from the control plane link layer are invalid data; judging whether call time slot of the SIP signaling is greater than a predetermined call frequency if that the calling number and the IP address do not have binding relationship is determined; and controlling the call time slot of the SIP signaling through INVITE information if the call time slot of the SIP signaling is greater than the predetermined call frequency. According to the invention, without changing prior signaling and network equipment, analysis and detection are carried out on the SIP signaling and the media streams which flow through the network so as to judge whether the messages are an attack messages and whether corresponding safeguard measures need to be taken, so that the security of a core network is protected, and the attack to a network layer and an application layer is prevented.
Owner:上海信擎信息技术有限公司
Dietary supplement and preparation method thereof
The invention discloses a dietary supplement and a preparation method thereof. The dietary supplement comprises two varieties of plant extractives, nine varieties of vitamins and two varieties of minerals. Active components comprise by weight 12-18 parts of rhodioloside, 100-114 parts of proanthocyanidins, 0.7-0.9 part of vitamin A, 1-3 parts of vitamin B1, 1-3 parts of vitamin B2, 3-5 parts of vitamin 6, 0.004-0.006 part of vitamin B12, 80-150 parts of vitamin C, 40-60 parts of vitamin E, 0.3-0.5 part of folic acid, 12-18 parts of nicotinamide, 5-15 parts of zinc and 0.02-0.06 part of selenium. The dietary supplement of the invention has comprehensive nutrition, can enhance antioxidation capability and reduce electromagnetic radiation damage, and is suitable for daily dietary supplement of radar troops as well as population living and working for long time in environment of high electromagnetic radiation, low illumination and continuous noise.
Owner:AVIATION MEDICINE INST AIR FORCE PLA
Scene self-adaptive smart window based on multiple sensors
InactiveCN107687306AAvoid poisoningAvoid fireProgramme controlComputer controlMicrocontrollerMicrocomputer
The invention discloses a scene self-adaptive smart window based on multiple sensors. The smart window is composed of a single-chip microcomputer, a stepping motor module, multiple sensor modules including a raindrop sensor, a temperature and humidity sensor, a smog sensor, an air quality sensor and a human body pyroelectric infrared sensor, a human-computer interaction module, an alarm module, apower supply module, a window cleaning module, an infrared transmission module, a clock module and an air humidifier. According to the scene self-adaptive smart window, the rich functions of automatically opening and closing the window when it rains, discharging out indoor harmful gas in time, avoiding outside air pollution, achieving invasion short-message warning, achieving manual and automaticmode switching, displaying time, air quality and temperature information in real time, controlling startup and shutdown of an air conditioner and the air humidifier to adjust the indoor environment, collecting rainwater to clean the window and the like can be achieved; and a solar panel is matched with a mobile power source for supplying power to a whole system, energy is saved, meanwhile, the trouble of grooving wiring is omitted, and convenience of mounting of the smart window is increased.
Owner:SHANGHAI MARITIME UNIVERSITY
Gene synthesis of wild boar alpha-interferon, vector construction and method for producing outcome
InactiveCN101392256AOptimize free energySimple structurePeptide/protein ingredientsAntiviralsEscherichia coliInclusion bodies
The invention discloses a gene synthesis of Alpha-interferon of wild boars and vector construction thereof as well as a production method of a product. A number of problems of low expression capacity, products expressed in a fusion state, products with purification tags or no fermentation technology with high density exist in the domestic recombinant strains. The invention includes a method that a codon and codon pairs, preferred by Escherichia coli, are used for synthesizing an Alpha-interferon gene of the wild boar, establishing a high-efficiency expression vector and transforming a high-efficiency expression strain as well as methods of high-density fermentation of engineering bacteria, separation and purification of inclusion bodies, the modification, the renaturation and the purification of target protein and the determination of biological activity of the expressed product. The gene synthesis, the vector construction and the production method pertain to the technical field of the production of polypeptide drugs by genetic engineering in biopharmaceuticals.
Owner:黑龙江省农业科学院畜牧研究中心 +1
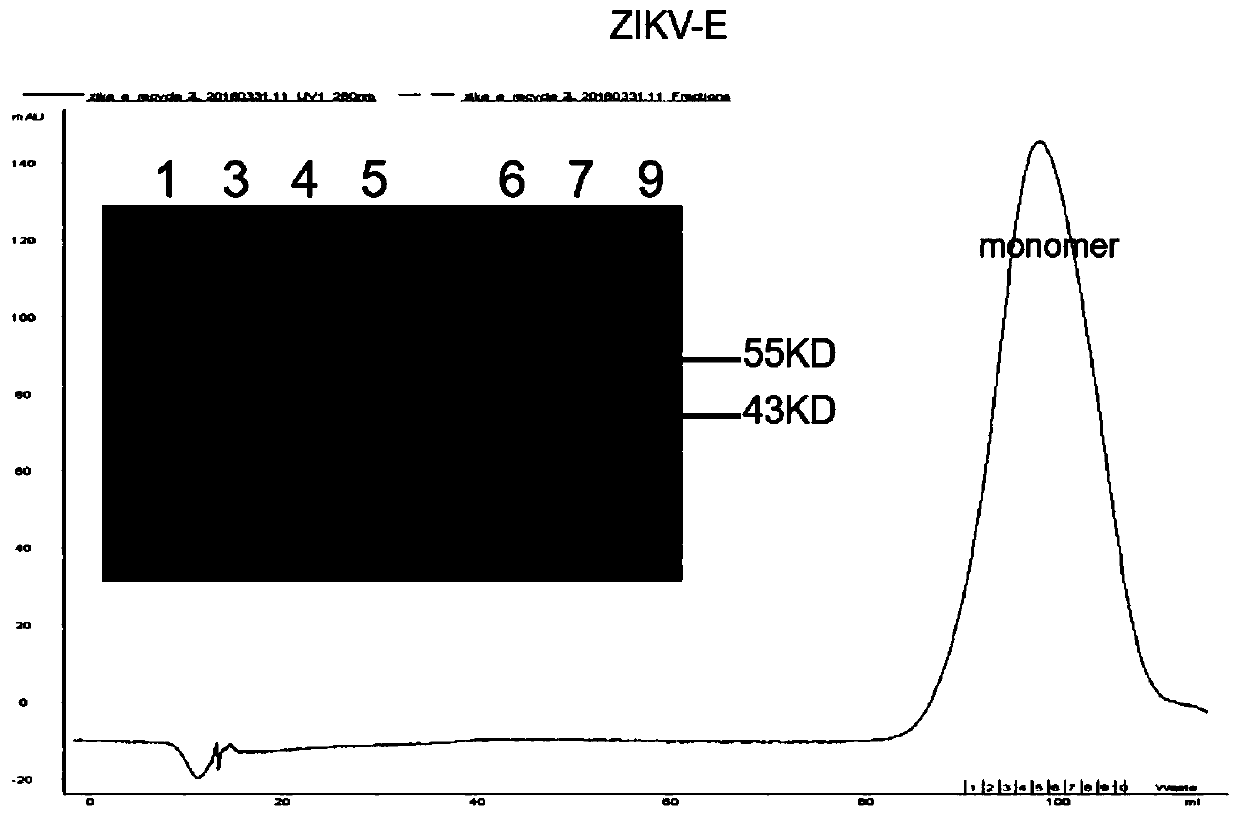
Human monocolonal antibody with high neutralization activity for Zika virus and application thereof
ActiveCN110172095AFree from attackStrong neutralizing activityImmunoglobulins against virusesAntiviralsAntigenEscherichia coli
Owner:INST OF MICROBIOLOGY - CHINESE ACAD OF SCI
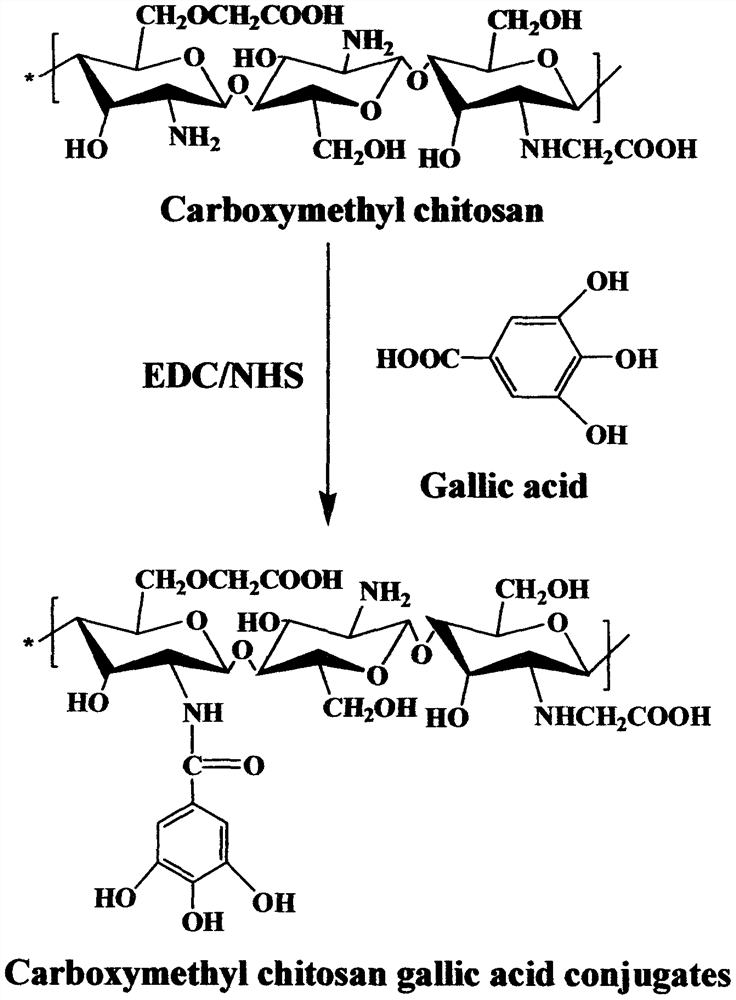
Self-repairing antibacterial chitosan hydrogel and preparation method thereof
The invention relates to a self-repairing antibacterial chitosan hydrogel and a preparation method thereof, the self-repairing antibacterial chitosan hydrogel is characterized in that the hydrogel is a self-repairing antibacterial hydrogel, the preparation method of the self-repairing antibacterial hydrogel comprises the following steps of: (1) reacting carboxymethyl chitosan with gallic acid to obtain a soluble carboxymethyl chitosan gallic acid derivative, wherein the molar ratio of gallic acid to carboxyl on carboxymethyl chitosan is 1:1-10:1; and (2) mixing an aqueous solution of the carboxymethyl chitosan gallic acid derivative with a FeCl3 solution according to a concentration ratio of 5:1-20:1 to obtain the self-repairing chitosan hydrogel, wherein the pH value of the mixed solution is 5-10. According to the invention, the intelligent hydrogel with self-repairing performance is synthesized in a short time through the interaction of dynamic metal ligands. In addition, the hydrogel also shows excellent antibacterial performance, and the antibacterial rate is increased along with the increase of the content of the carboxymethyl chitosan gallic acid derivative.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
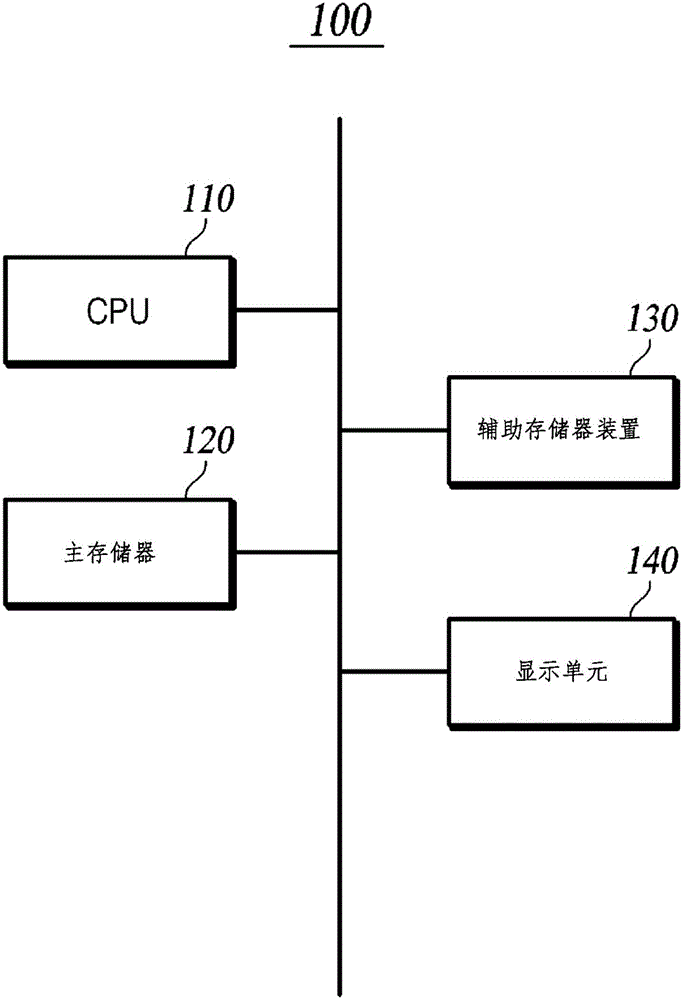
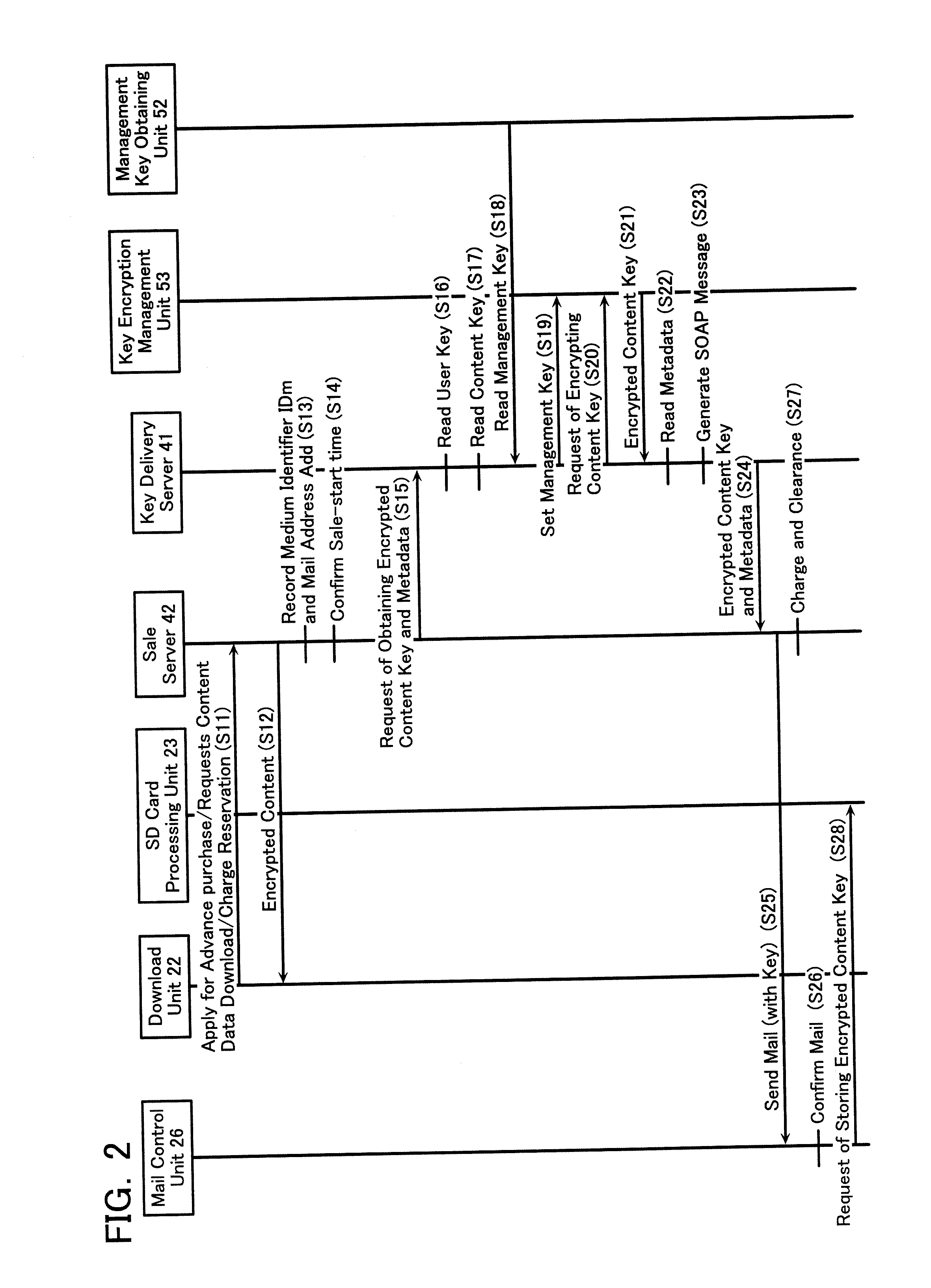
Storage Medium Processing Method, Storage Medium Processing Device, and Program
InactiveUS20080310638A1Shorten access timeReduce download timeKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer networkStart time
A situation where accesses concentrate on a release day is eased. A user terminal 20 requests a license center unit 40 to deliver content data submitting medium identifier data IDm. The license center unit 40 confirms a sale-start time of the content data concerning the delivery request in the sale-start time database 47, and delivers the content data or the like to the user terminal when the sale-start time has elapsed.
Owner:KK TOSHIBA
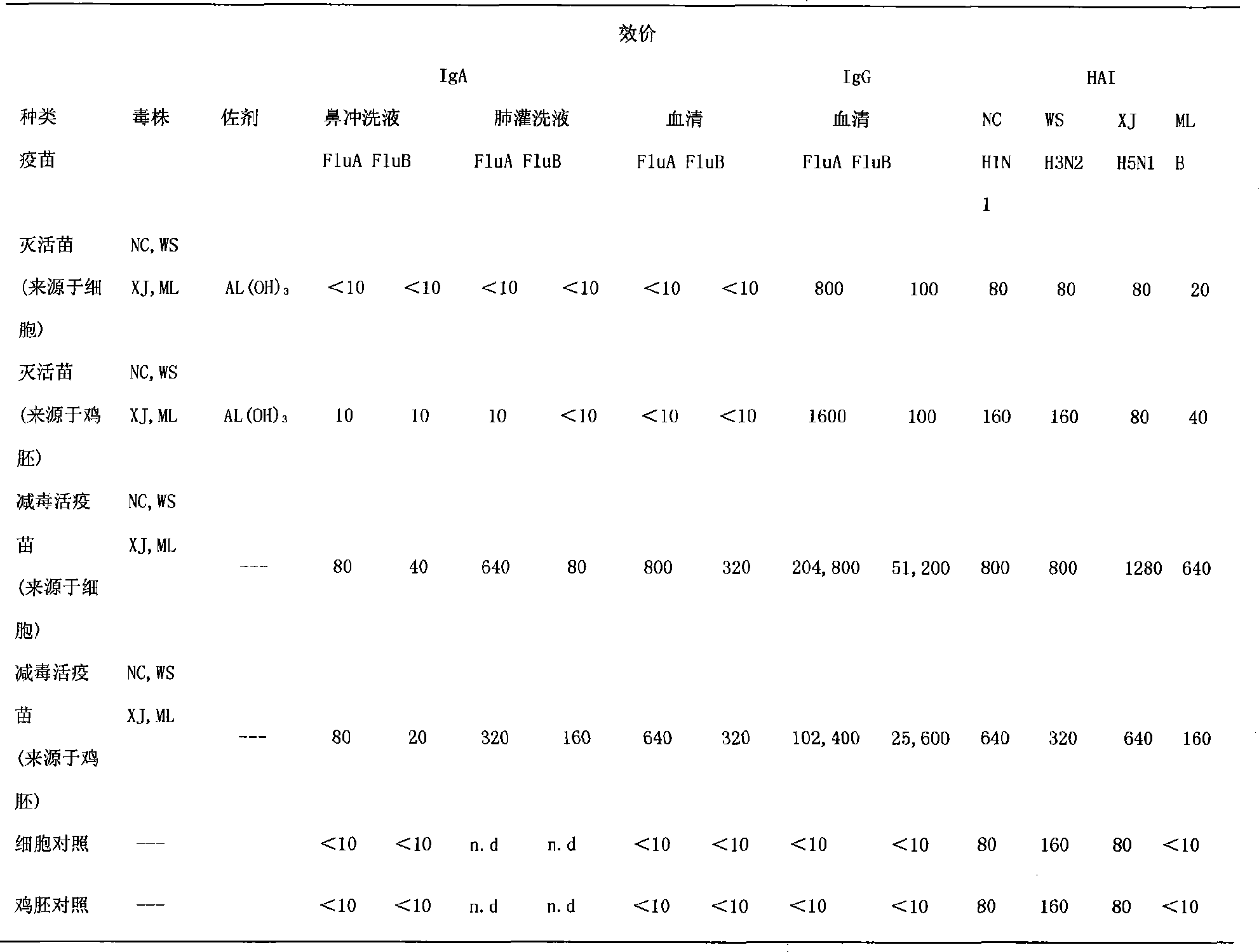
Nasal-spraying immune influenza multivalent vaccine and preparation method thereof
InactiveCN101450208AEasy to useLess antigenPowder deliveryAerosol deliveryHighly Pathogenic Avian Influenza VirusInfluenza a
The invention discloses a nasal spray immunity flu polyvalent vaccine and a preparing method. Flu quadrivalence (H1N1, H3N2, H5N1, B type) or polyvalent attenuated live vaccine is used for immunoprophylaxis through nose spraying, popular flu and highly pathogenic avian influenza can be prevented safely and efficiently.
Owner:MICROBE EPIDEMIC DISEASE INST OF PLA MILITARY MEDICAL ACAD OF SCI
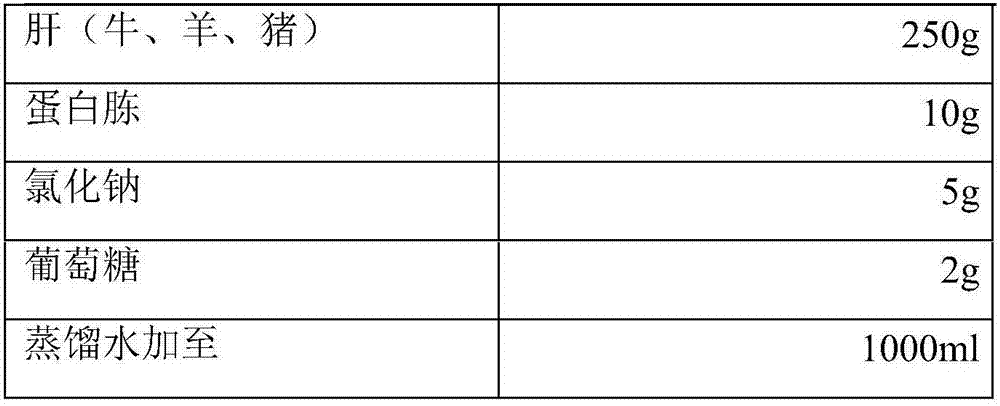
Veterinary D-type clostridium perfringen toxin, and preparation method and special culture medium of D-type clostridium perfringen toxin
ActiveCN107299070AStrong toxin production abilityToxic performance is stableAntibacterial agentsBacterial antigen ingredientsSerum neutralizationBiologic Products
The invention discloses a preparation method and a special culture medium of veterinary D-type clostridium perfringen toxin. The culture medium per 100ml comprises the following components: 1-1.5g soy peptone, 1-1.5g casein peptone, 0.5-0.75g yeast extract, 0.5-0.75g Na2HPO4.12H2O, 1-1.5g dextrin and the balance of water, wherein a pH (potential of hydrogen) value of the culture medium is 8.0-8.5. The preparation method of the D-type clostridium perfringen toxin comprises the steps of inoculating a D-type clostridium perfringen production strain into the culture medium, collecting a culture material, performing centrifugation, and then filtering a supernate. With the adoption of the method, the maximum toxicity can be improved to be 45 times a seedling standard in Regulations on National Veterinary Biological Products, and an output-input ratio can be increased to be 30-225 times that of the original traditional technology. In addition, corresponding serum neutralization titer of a toxoid vaccine prepared by the D-type clostridium perfringen toxin on a rabbit and a sheep is also improved to be 8.3 and 13.3 times a regulation standard respectively.
Owner:CHINA INST OF VETERINARY DRUG CONTROL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com