Method for controlling software behavior based on least privilege principle
A control method and minimization technology, applied in the field of information security, can solve problems such as frequent access to the registry, suspicious system file writing operations, etc., and achieve the effects of convenient communication, avoiding cross-border behavior, and high stability
Inactive Publication Date: 2011-10-05
江苏云木养老科技有限公司
View PDF4 Cites 14 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In addition, from the perspective of the user's usage logic, the behavior of the software should conform to the conventional operation logic: for example, when using a browser, known applications such as download tools and readers may be launched when the browser is running. If there are some unknown processes, the behavior is suspicious; the browser will access a large numb
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
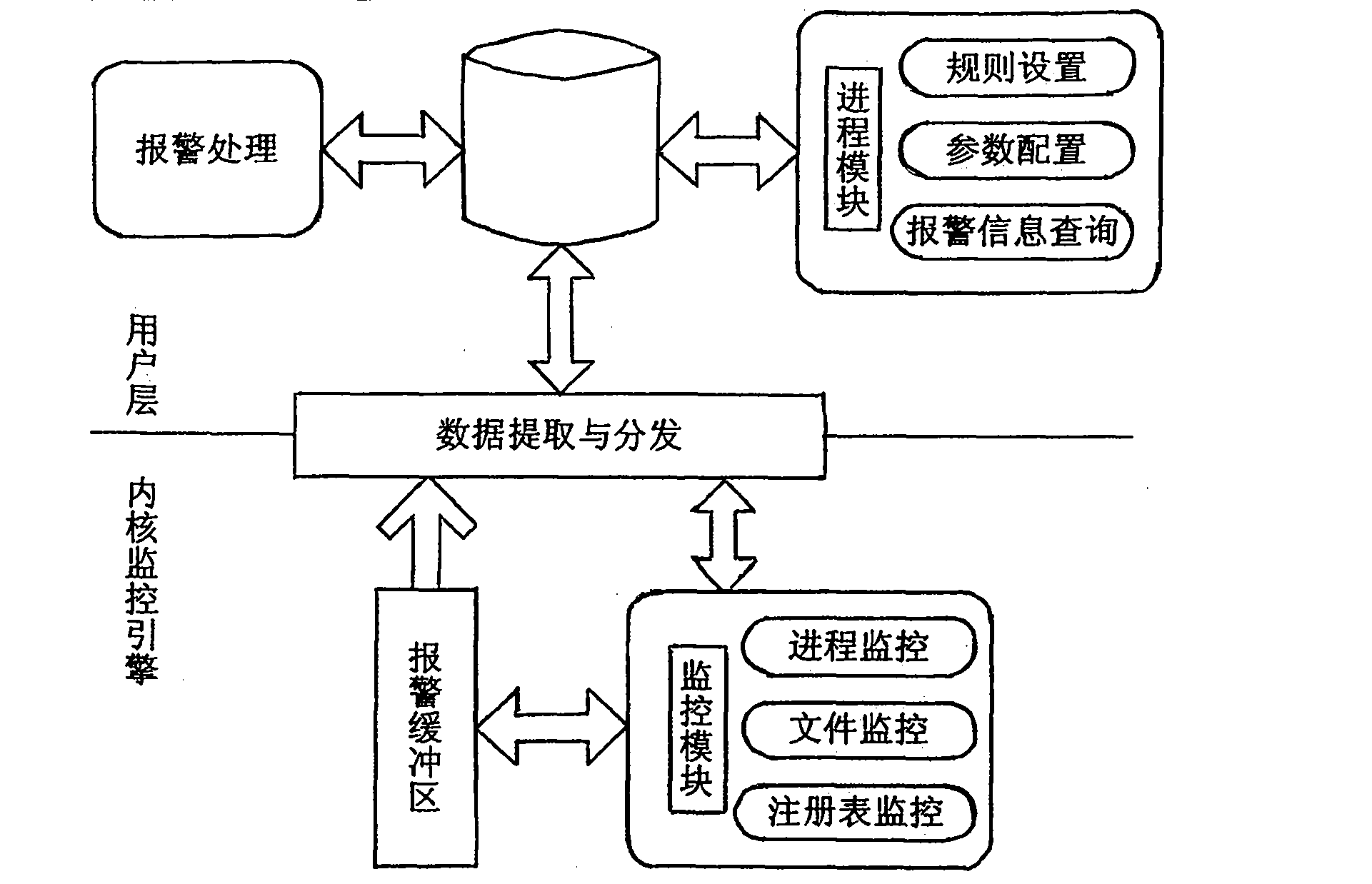
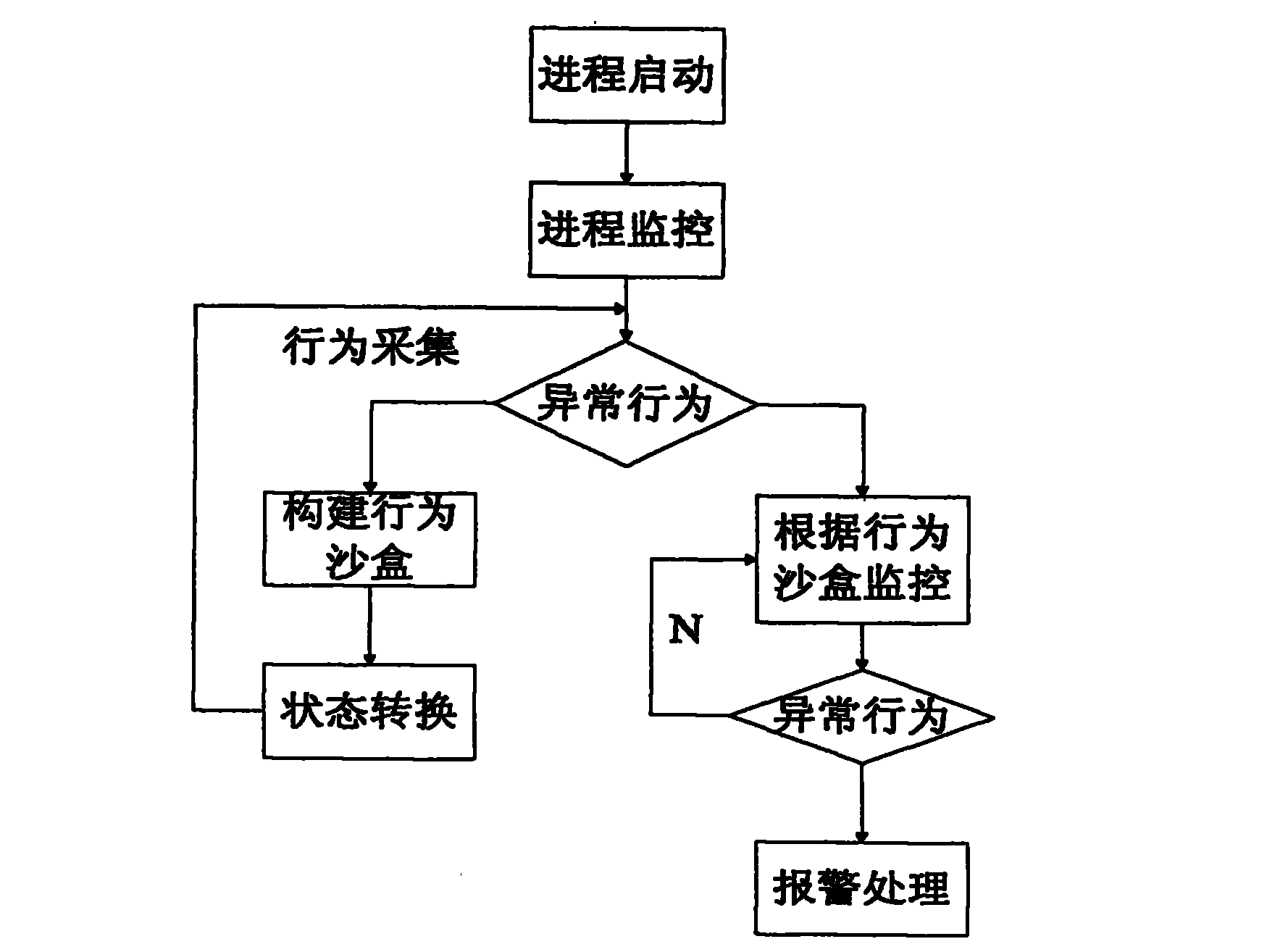
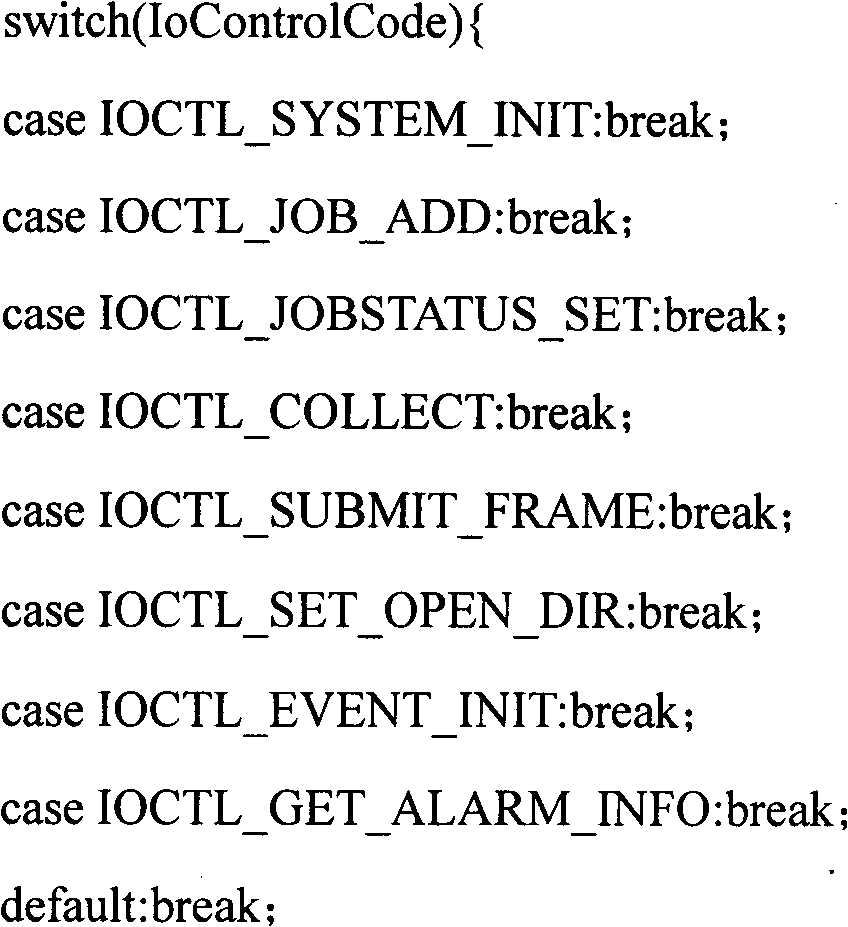
The invention relates to a method for controlling software behavior based on a least privilege principle, used for protecting a computer operating system from being damaged by malicious behaviors. The method comprises the following specific steps: setting parameters of a monitoring module according to the least privilege principle, storing the parameters in a registration list, and reading and storing through a control module interface; creating a process behavior sandbox, a file behavior sandbox and a registration list behavior sandbox, and monitoring the clue of process tree by the behaviorsand boxes; for interaction with users or file operation, filtering IRP (input/ output request package) process, and determining different operations according to different function request control codes; for process or registration list monitoring, not carrying out IRP filtration process; turning to step 5) and keeping monitoring if no abnormal situation is monitored; actively transmitting alarming information in real time to a control module positioned at an user layer; and carrying out system alarming.
Description
technical field [0001] The invention proposes a software behavior control scheme based on the principle of least privilege, which can be used to protect computer operating systems from malicious acts, and belongs to the field of information security. Background technique [0002] The demand for information in modern warfare is becoming more and more intense. Information equipment with computers as the core is widely used in the military field, which has become an important symbol of military modernization and advanced weapons. The nerve center, its performance and condition will directly affect the combat effectiveness of the army and its performance. Information confrontation with the goal of competing for the right to control information, that is, "information warfare", has become the key to determining the outcome of a war. Malicious code technologies represented by computer viruses and network worms have been confirmed to destroy data, interrupt operations, affect and d...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): G06F21/22G06F21/50
Inventor 张登银赵晓强王汝传李鹏张伟肖甫
Owner 江苏云木养老科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com