Kernel hook based process behavior monitoring method
A process and behavior technology, applied in the field of process behavior monitoring based on kernel hooks, can solve problems such as infringement, ordinary user layer protection is difficult to achieve file security protection, and file security protection cannot achieve satisfactory results, so as to improve security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
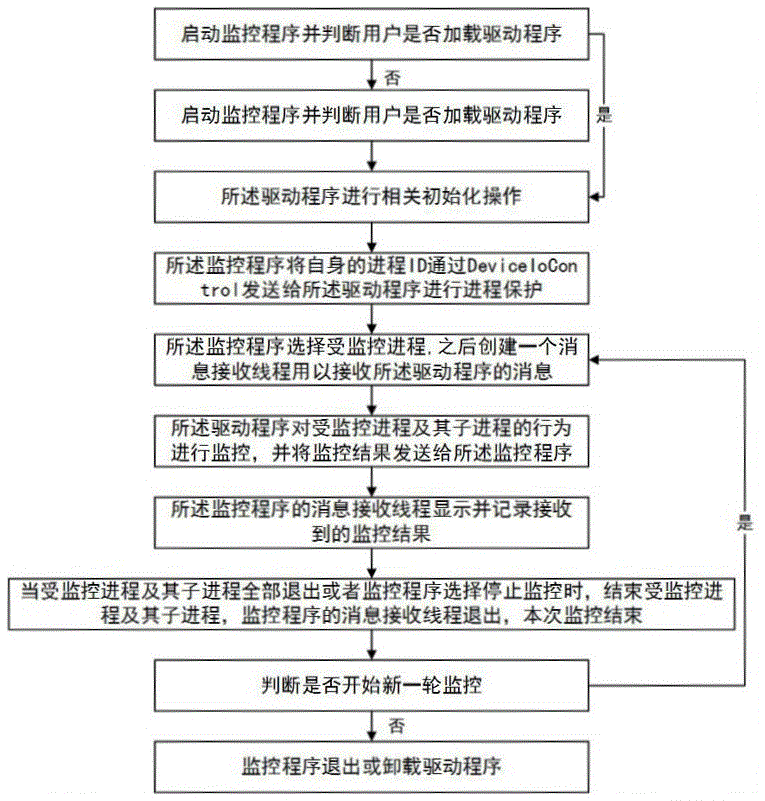
[0031] Such as figure 1 As shown, the present embodiment provides a process behavior monitoring method based on kernel hook, which specifically includes the following steps:
[0032] Step S1: Start the monitoring program and determine whether the user has loaded the driver program. If not, prompt the user to load the driver program and proceed to step S2; if it has been loaded, proceed to step S3;
[0033] Step S2: perform an initialization operation, and load the driver;
[0034] Step S3: The driver performs related initialization operations;
[0035] Step S4: The monitoring program sends its own process ID through DeviceIoControl to the driver for process protection to prevent malicious programs from forcibly stopping the monitoring program;
[0036] Step S5: the monitoring program selects a monitored process, the monitored process is an executable...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com