Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
56results about How to "Maintain security and stability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Transmission line mountain fire spread warning method with combination of public network weather
ActiveCN105279884AMaintain security and stabilityStrong targetingFire alarmsInformation supportPower grid
The invention provides a transmission line mountain fire spread warning method with the combination of public network weather. The method comprises a step of obtaining a fire point coordinate, a step of calculating the spread speed of a fire point spread direction based on the fire point coordinate, a step of calculating the linear position of the fire point in the spread direction after a spread time according to the spread speed, and obtaining a spread coordinate, a step of calculating the spread area of the fire point according to the spread coordinate, a step of carrying out warning level definition on the transmission line in the spread area according to the spread time and issuing warning. According to the method, an effective information support is provided for the judgment of a grid mountain fire disaster by a power department, the mountain fire spread speed from the fire point to the transmission line can be calculated, the warning level of the transmission line is judged through time according to the mountain fire spread speed, and the method has high accuracy and practicability and plays an important role in maintaining security and stability of a grid and reducing a disaster loss.
Owner:STATE GRID CORP OF CHINA +1
Spurious response system and method based on dynamic variation and network security system and method
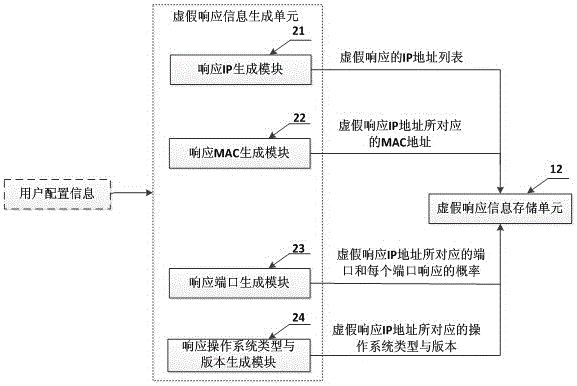
ActiveCN105721442ADefense against penetration attacksMaintain security and stabilityTransmissionData packIp address
The invention provides a spurious response system and method based on dynamic variation and a network security system and method.The spurious response system comprises a spurious response information configuration unit and a spurious response unit, the spurious response information configuration unit configures spurious response information which can be varied dynamically and comprises a spurious IP address and a spurious MAC address at a minimum according to user configuration information, and the spurious response unit constructs a spurious response data packet and conducts spurious response on suspected scanning detection data packets according to the spurious response information.According to the spurious response system and method, spurious response is conducted on scanning detection behaviors of attackers, spurious response can be varied dynamically according to configuration, thereby the attackers cannot obtain the topological structure of a network and cannot accurately obtain real information of hosts in the network, in this way, network penetration attacking behaviors are effectively defended, and safety and stability of the network are maintained.
Owner:北京卫达信息技术有限公司
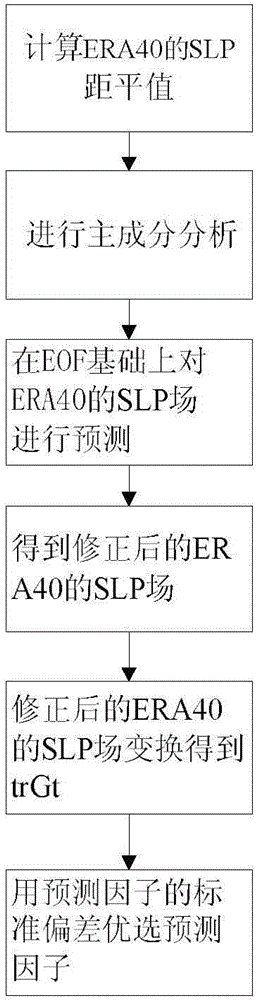
Sea wave significant wave height long-term trend prediction method based on reanalysis data
InactiveCN104050514AAddress reliabilityMaintain security and stabilityForecastingAnalysis dataData set
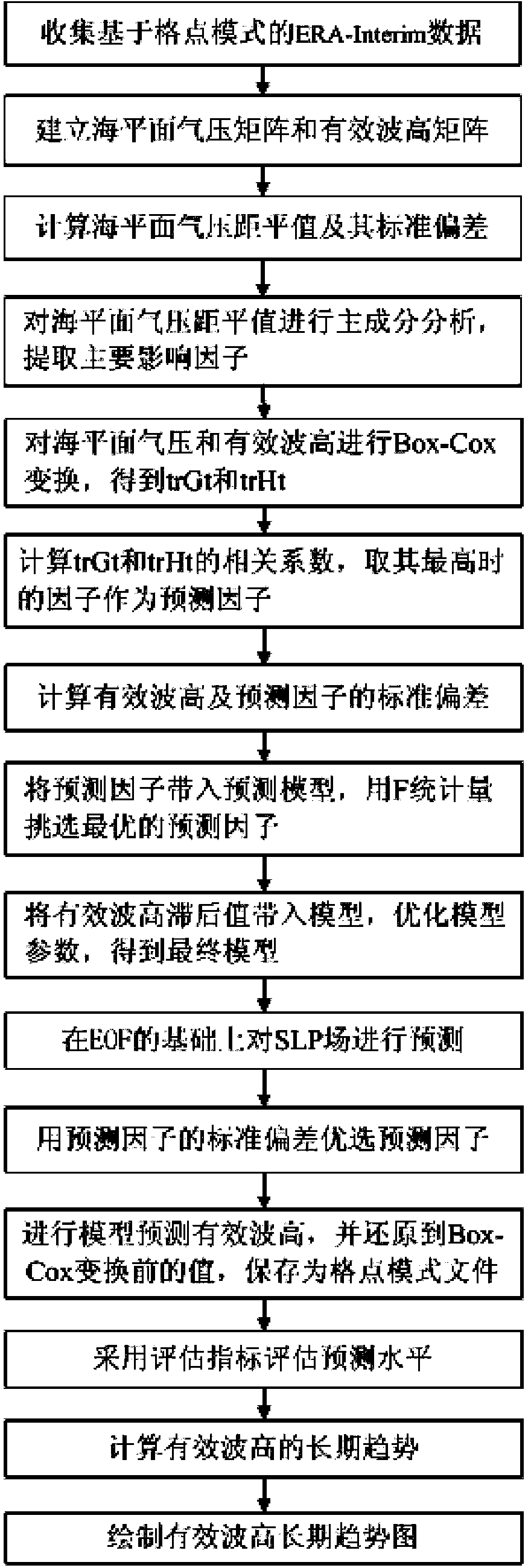
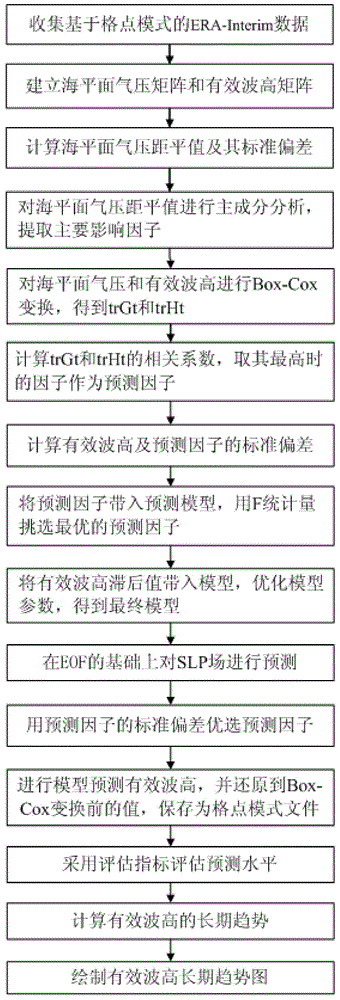
The invention relates to a sea wave significant wave height long-term trend prediction method based on reanalysis data. The sea wave significant wave height long-term trend prediction method is characterized by comprising the steps that (1) weather forecast data of an ERA-Interim reanalysis data set at each time frequency are collected, (2) coordinates of all lattice points are obtained, (3) SLP anomaly and standard deviation are calculated, (4) principal component analysis of the SLP anomaly is conducted, (5) Box-Cox transformation is conducted on sea area data, (6) a predictive factor of sea wave significant wave height is calculated, (7) the standard deviation of the significant wave height and the predictive factor is calculated, (8) the predictive factor is applied into a prediction model, (9) a significant wave height lagged value is applied into the model, (10) SLP field prediction on the basis of EOF is carried out, (11) predictive factor optimization selection is conducted, (12) the sea wave significant wave height is predicted through the model, (13) the prediction level is evaluated, (14) the sea wave significant wave height long-term trend is calculated, and (15) a significant wave height long-term trend chart is drawn. According to the sea wave significant wave height long-term trend prediction method based on the reanalysis data, the significant wave height long-term trend of multiple time frequencies can be predicted, and accuracy is high.
Owner:HOHAI UNIV
Electric transmission line forest fire forecasting method
The invention provides an electric transmission line forest fire forecasting method, which includes the following steps: (1), collecting meteorological data; (2.1), analyzing fire using conditions in industry and agriculture; (2.2), analyzing precipitation conditions; (2.3) analyzing rainless days conditions; (2.4), analyzing temperature conditions; (2.5), analyzing humidity conditions; (3), drawing forecasting conclusion; (4), issuing forecasting conclusion. The electric transmission line forest fire forecasting method has the following advantages that:(1),the method can perform electric transmission line forest fire forecasting for power grid forest fire area of next two days; (2), the electric transmission line forest fire forecasting method is high in practical application and convenient to operate; (3), the accuracy rate of forecasting electric transmission line forest fire is high; (4), the method has a guiding significance for electric transmission line operating staffs to draw up a forest fire prevention and control measurement, and has an important effect on maintaining the safety and stability of the power grid and reducing disaster loss.
Owner:STATE GRID HUNAN ELECTRIC POWER +3
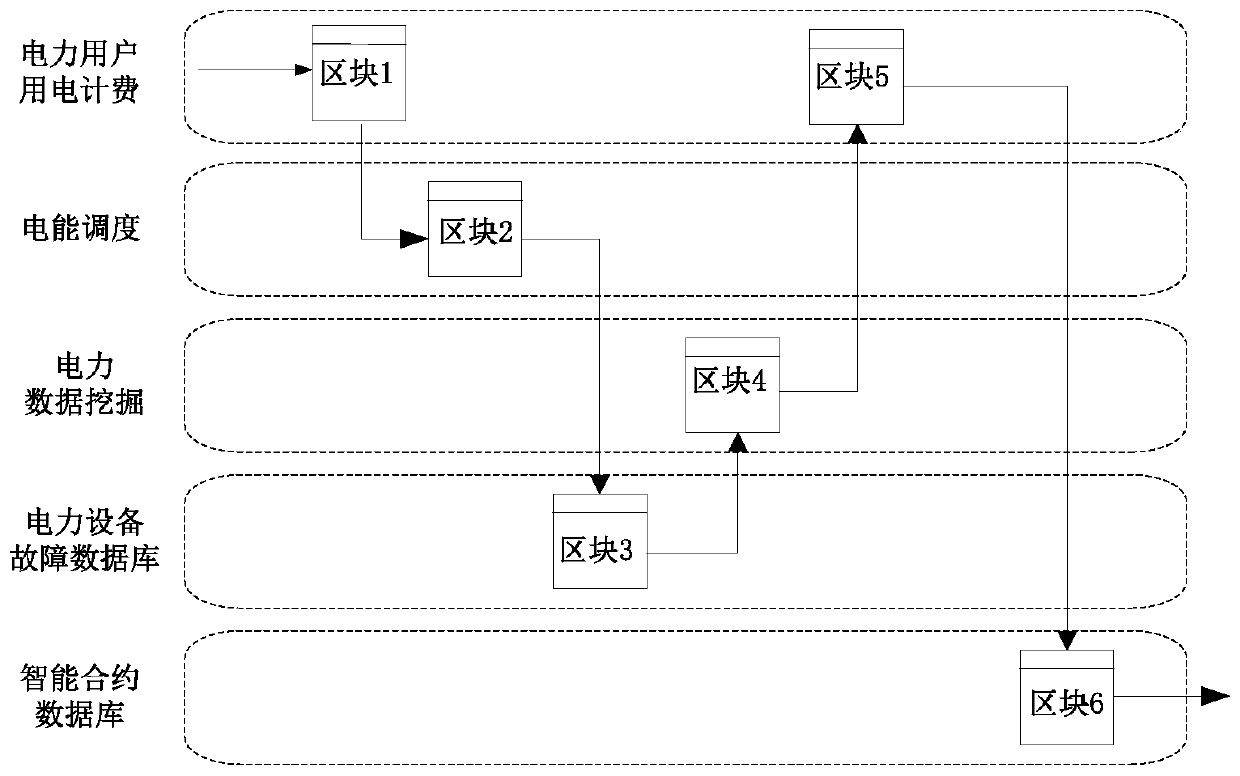
Intelligent power grid data management system and method based on main right block chain technology
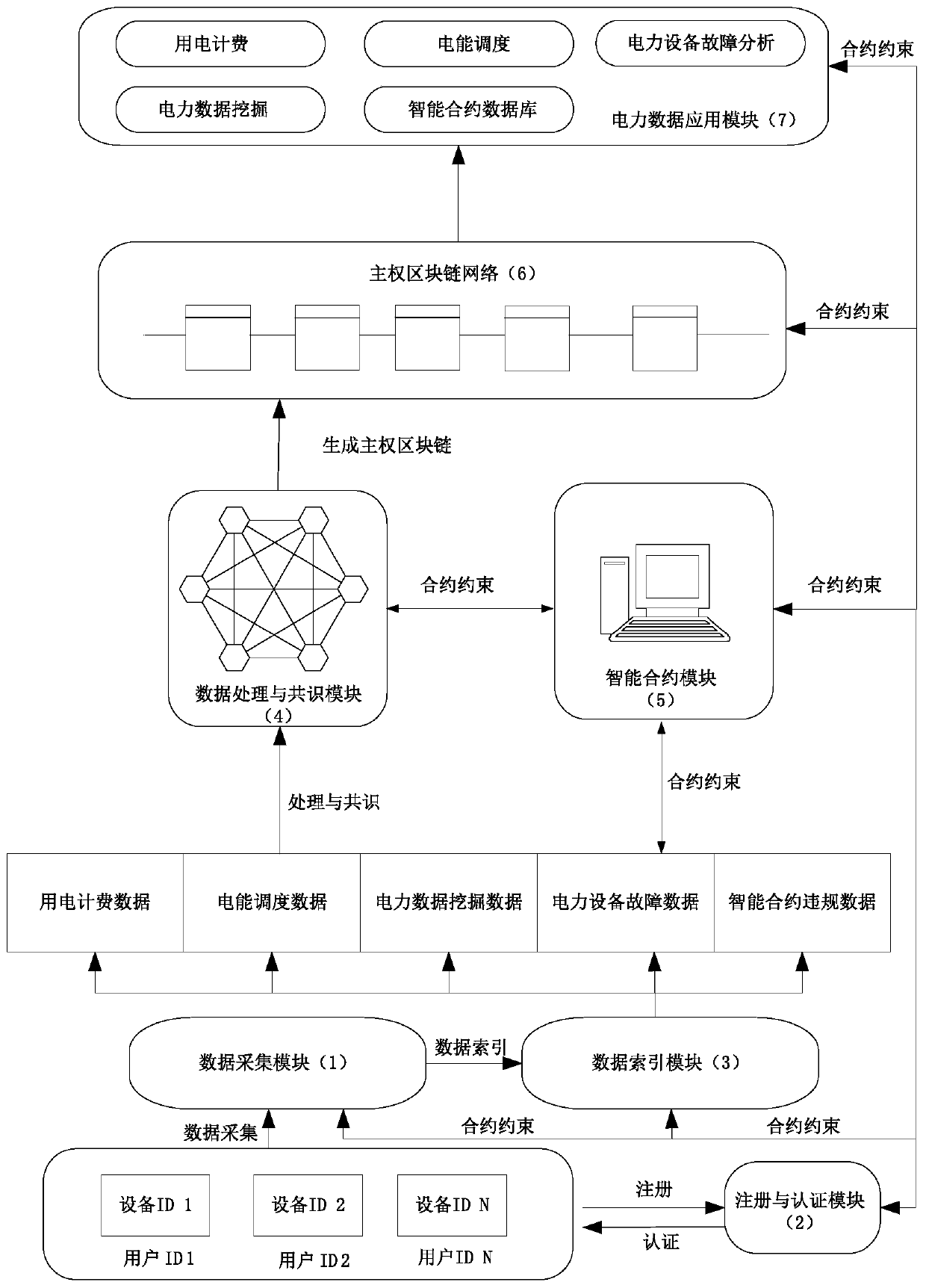
ActiveCN110287186AImprove credit scoreMaintain security and stabilityData processing applicationsDatabase distribution/replicationSmart gridControllability
The invention relates to an intelligent power grid technology, in particular to an intelligent power grid data management system and method based on a main right block chain technology. The system comprises a data collection module, a registration and authentication center, a data index module, a data processing and consensus module, an intelligent contract module, a main right block chain network, and a power data application module. According to the present invention, not only the problem of electric power data leakage risk caused by a large amount of data in the smart power grid is solved, but also the mining value of the electric power data is improved, and the electric power data mining process is standardized. By writing the national law regulations into a block chain intelligent contract, and placing the diverse and complex application and management block chains of the power data under supervision of the law regulations, the advantages of power user identity information controllability, intelligent contract legality supervision, power information targeted opening and the like in the block chain are realized, and the storage and utilization efficiency of the electric power data is improved through the block chain structure of the electric power data application service type identifier.
Owner:WUHAN UNIV
Power grid icing growth trend forecasting method based on digital elevation model
InactiveCN103473610APredictable Icing AreasPredictable icing conditionsForecastingSystems intergating technologiesIcing conditionsPower grid
The invention provides a power grid icing growth trend forecasting method based on a digital elevation model. The method includes the following steps of firstly, setting up a power grid comprehensive geographic information platform; secondly, collecting data of the weather forecast at each time level; thirdly, obtaining a coordinate of each grid point; fourthly, correcting temperature data; fifthly, calculating the icing increment; sixthly, saving the icing increment into a file in the grid point mode; seventhly, repeating the fourth step, the fifth step and the sixth step; eighthly, drawing an icing growth distribution diagram at each time level; ninthly, marking icing growth data of an electric transmission line. The method has the advantages that the power grid icing conditions at multiple time levels can be forecasted, the operability is strong, the accuracy of forecasting of the power grid icing trend is high, the deicing work of the electric transmission line can be powerfully guided, and the method plays an extremely important and absolutely necessary role in keeping a power grid to be safe and stable and reducing ice damage losses.
Owner:STATE GRID CORP OF CHINA +2
ERA (ECMWF (European Centre for Medium-range Weather Forecasts) Reanalysis)-Interim and ERA40-based method for predicting significant wave height of sea waves
InactiveCN104021308AAddress reliabilityMaintain security and stabilitySpecial data processing applicationsAnalysis dataSea waves
The invention discloses an ERA (ECMWF (European Centre for Medium-range Weather Forecasts) Reanalysis)-Interim and ERA40-based method for predicting a significant wave height of sea waves. The ERA-Interim and ERA40-based method comprises the following steps: acquiring original data, performing data preprocessing; selecting a proper sea-level pressure field; correcting a model by using data of ERA-Interim; evaluating the corrected model by using data of ERA40; and predicting the significant wave height of the sea waves. According to the ERA-Interim and ERA40-based method, information of predicting the significant wave height of the sea waves is extracted from a long-term stable ERA-Interim reanalysis data source of the ECMWF; further, under the assistance of a method of analyzing a main component, and by using the ERA40 reanalysis data source, the evaluation is performed, thus the significant wave height of the sea waves of multiple hour-times can be predicted; and the ERA-Interim and ERA40-based method is strong in maneuverability and high in prediction accuracy rate.
Owner:HOHAI UNIV
WEB dynamic adaptive defense system and defense method based on false response
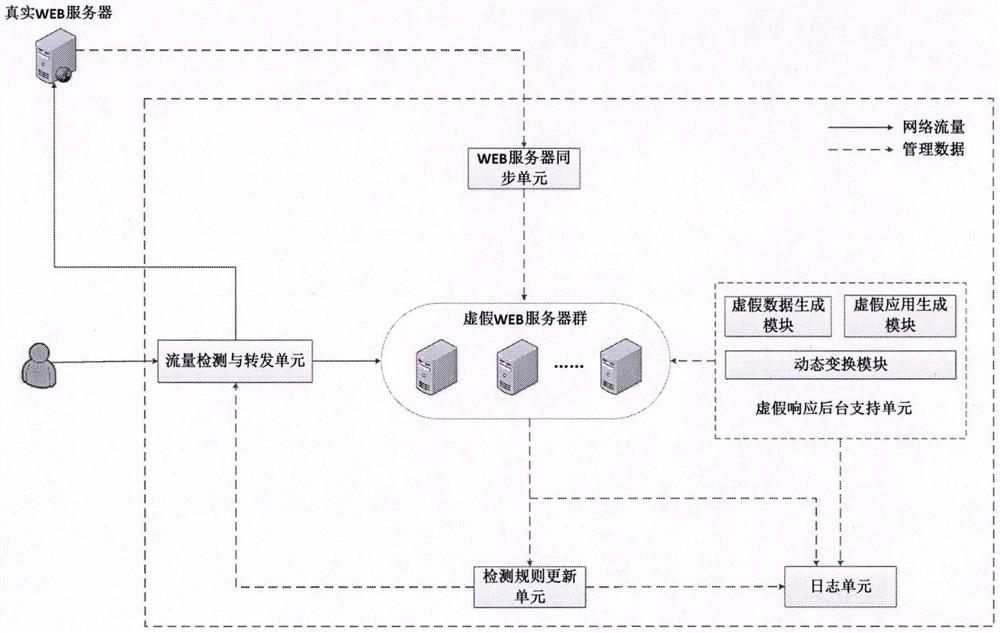
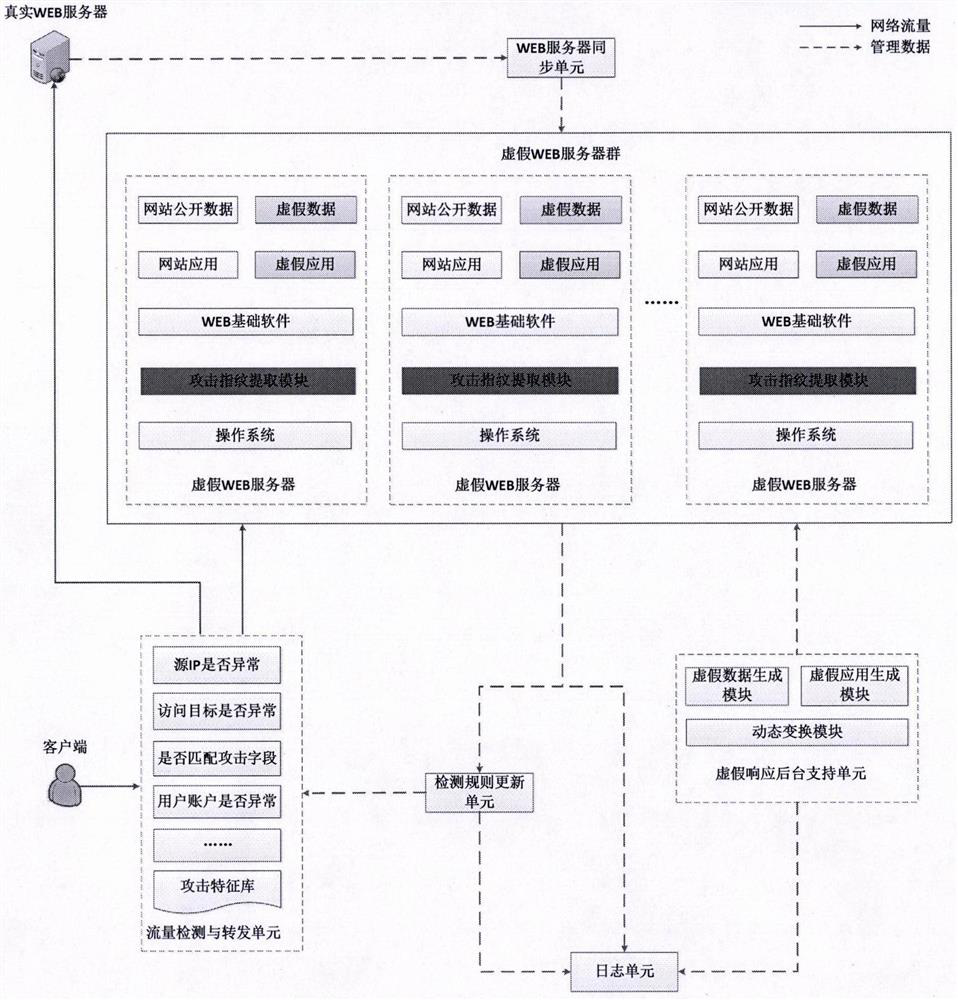
The invention provides a WEB dynamic adaptive defense system and defense method based on false response. Based on the concept of moving target defense, a plurality of false WEB servers capable of being dynamically transformed is constructed around a protected WEB server, false sensitive data, false applications, false vulnerabilities and the like are constructed on the false WEB servers, and cheating hackers attack the false WEB servers. When a known attack or a suspicious behavior is identified, the known attack or the suspicious behavior is introduced into the false WEB server, and an attacker enters the false environment and then executes a subsequent attack action in the false environment until the attack is finished, so that multiple attempt attacks of the attacker are effectively defended, and meanwhile, the method has a relatively good defending capability on an unknown WEB attack. Besides, by continuously observing attack behaviors in a false environment, WEB attack features can be automatically extracted, attack detection rules are dynamically and adaptively adjusted, and the dynamic adaptive capacity of a defense system is improved.
Owner:张长河
Network social contact system based on geographic positions and communication method
InactiveCN104410696AFacilitate communicationPsychological feeling warmTransmissionGeographic siteGeolocation
The invention provides a system which is based on geographic positions, and can ensure that a user performs social contact with other users within any ranges on a map through a terminal and a network of the user, without register and login, and a communication method. The method mainly comprises the following steps: a, the terminal obtains an unique identity in the system; b, the geographic position of the terminal is positioned and sent to a virtual practical map module; c, the position of the terminal or the terminal user doppelgangers in a virtual practical map and the forwarding range of the position are marked; d, terminal user behavior information is forwarded to other terminals within a user behavior range on the virtual practical map and virtual doppelgangers of other terminal users, and fed back user behavior information of other terminals within the range and the virtual doppelgangers of other terminal users are received.
Owner:吴金河
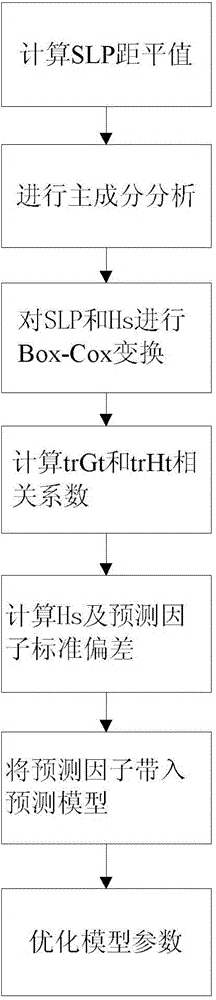
Short time trend predicating method for sea wave significant wave height based on reanalysis data
ActiveCN104036123AAddress reliabilityMaintain security and stabilitySpecial data processing applicationsSignificant wave heightComposition analysis
The invention relates to a short time trend predicating method for a sea wave significant wave height based on reanalysis data. The method is characterized by comprising the following specific steps that firstly, data of the sea wave significant wave height based on the reanalysis data and data of sea level pressure are collected; secondly, a sea level pressure matrix and a significant wave height matrix are built; thirdly, the anomaly of the SLP and the standard deviation of the anomaly are calculated; fourthly, main composition analysis is conducted on the anomaly of the SLP; fifthly, Box-Cox conversion is conducted on the data of the sea level pressure and the data of the sea wave significant wave height; sixthly, predicating factors of the sea wave significant wave height are obtained through calculation; seventhly, the predicating factors are substituted into a predicating model, and the optimal predicating factor is selected for predicating with F-statistics; eighthly, the short time trend of the sea wave significant wave height is calculated; ninthly, the value of the sea wave significant wave height is restored and stored into a lattice point mode file; tenthly, a short time trend chart of the sea wave significant wave height is drawn. According to the short time trend predicating method, the multi-time short time trend of the sea wave significant wave height can be forecasted, and the accuracy of forecasting the short time trend of the significant wave height is high.
Owner:HOHAI UNIV
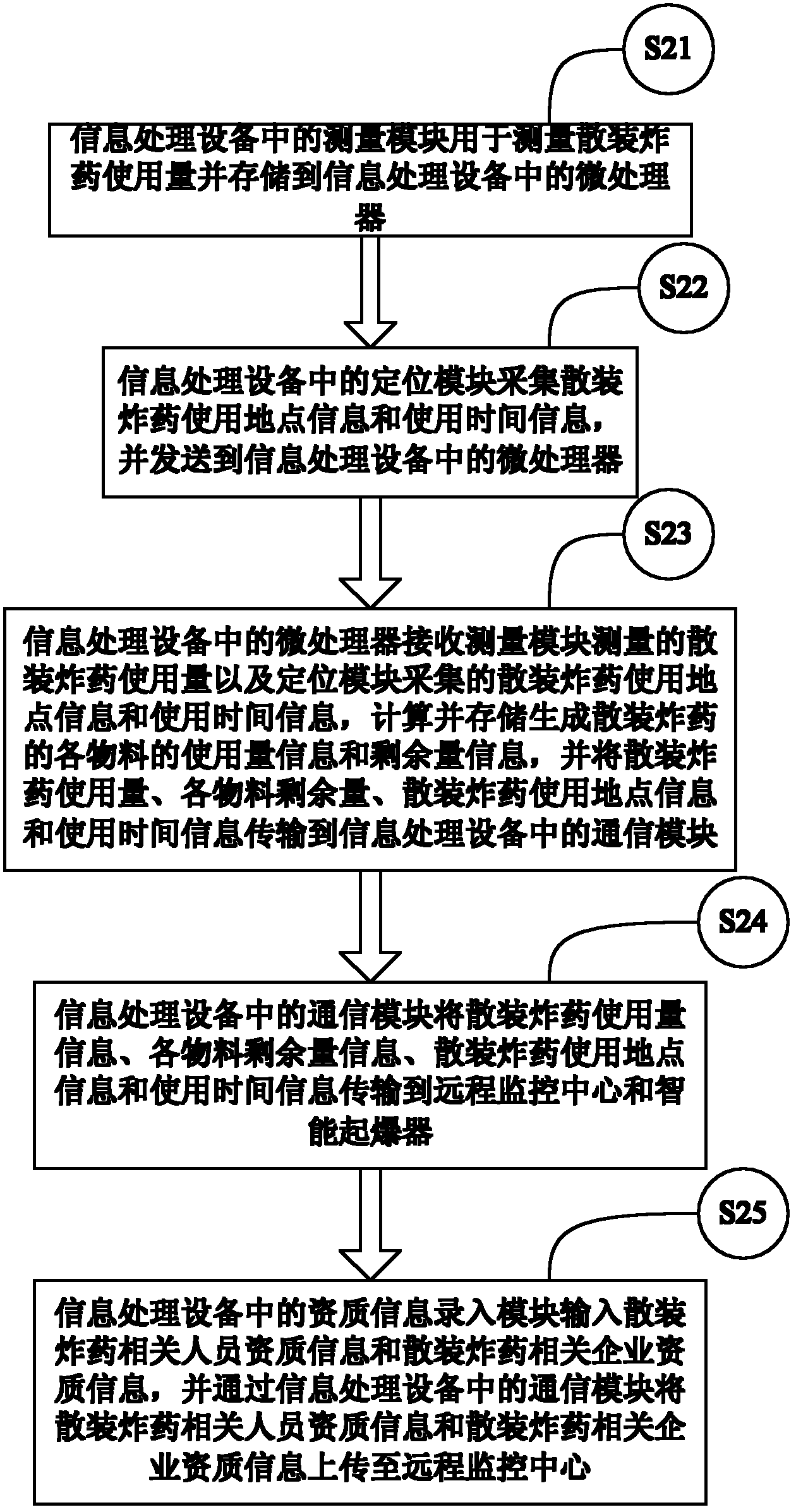
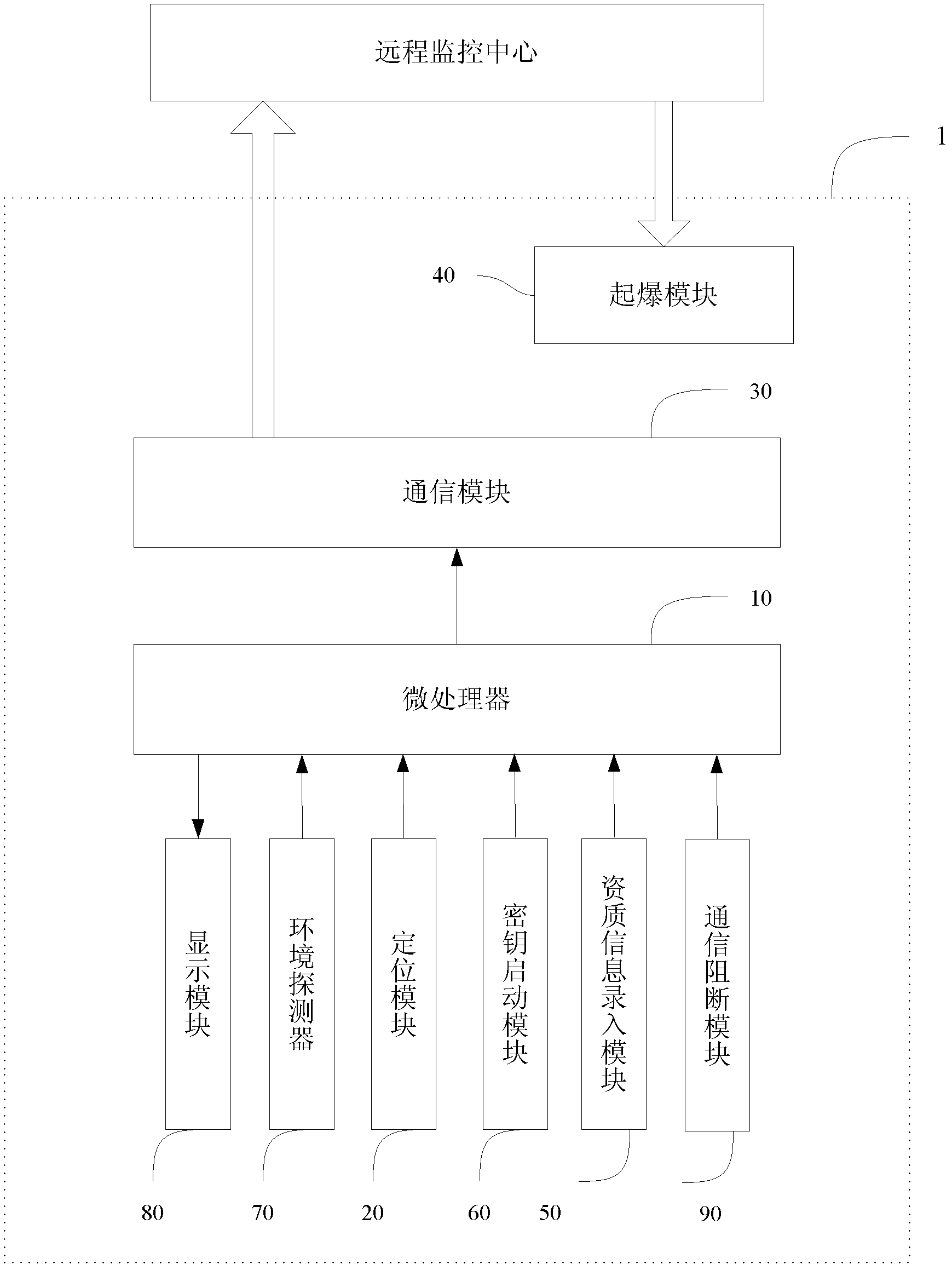
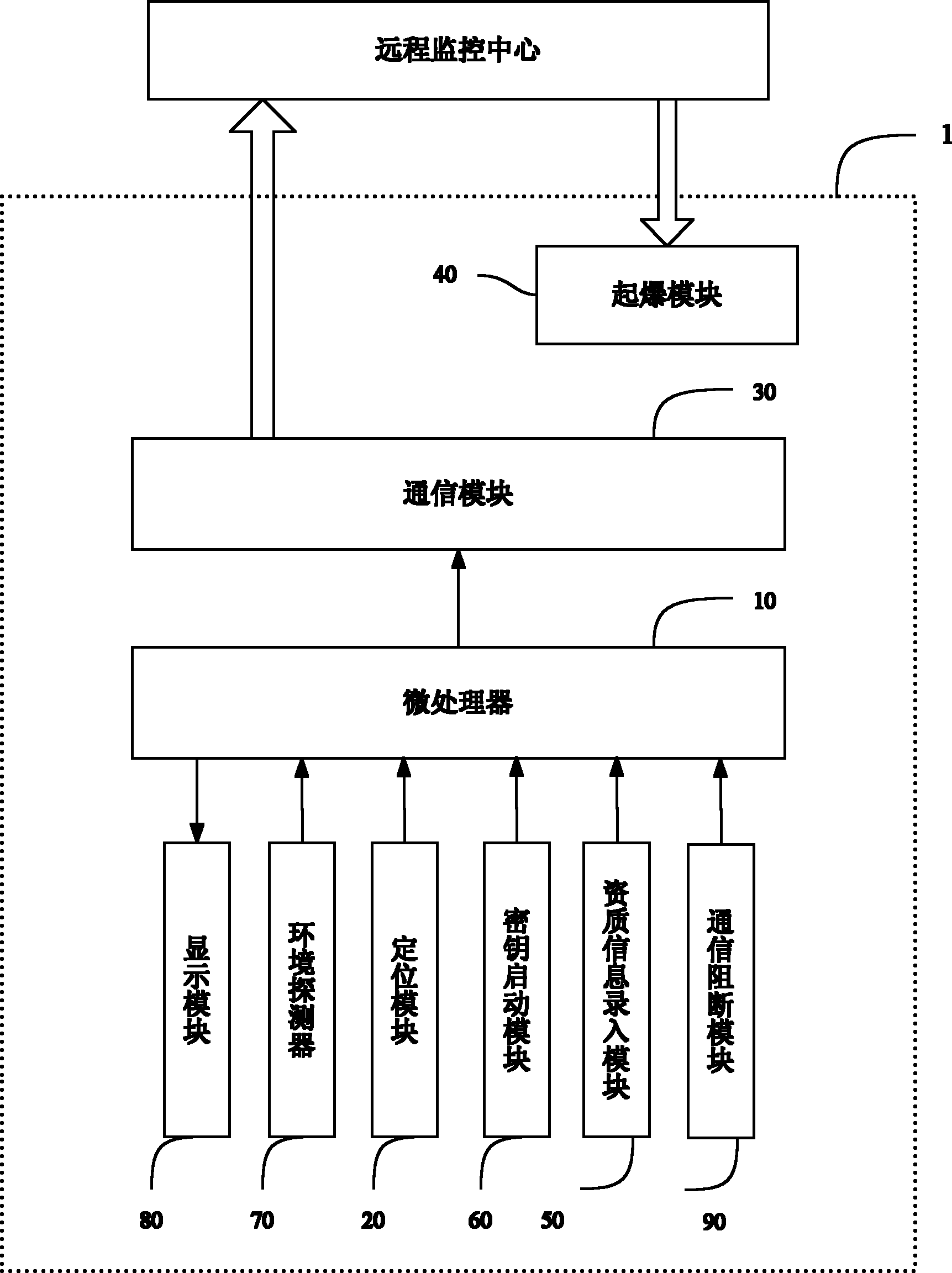
Explosive monitoring system and method
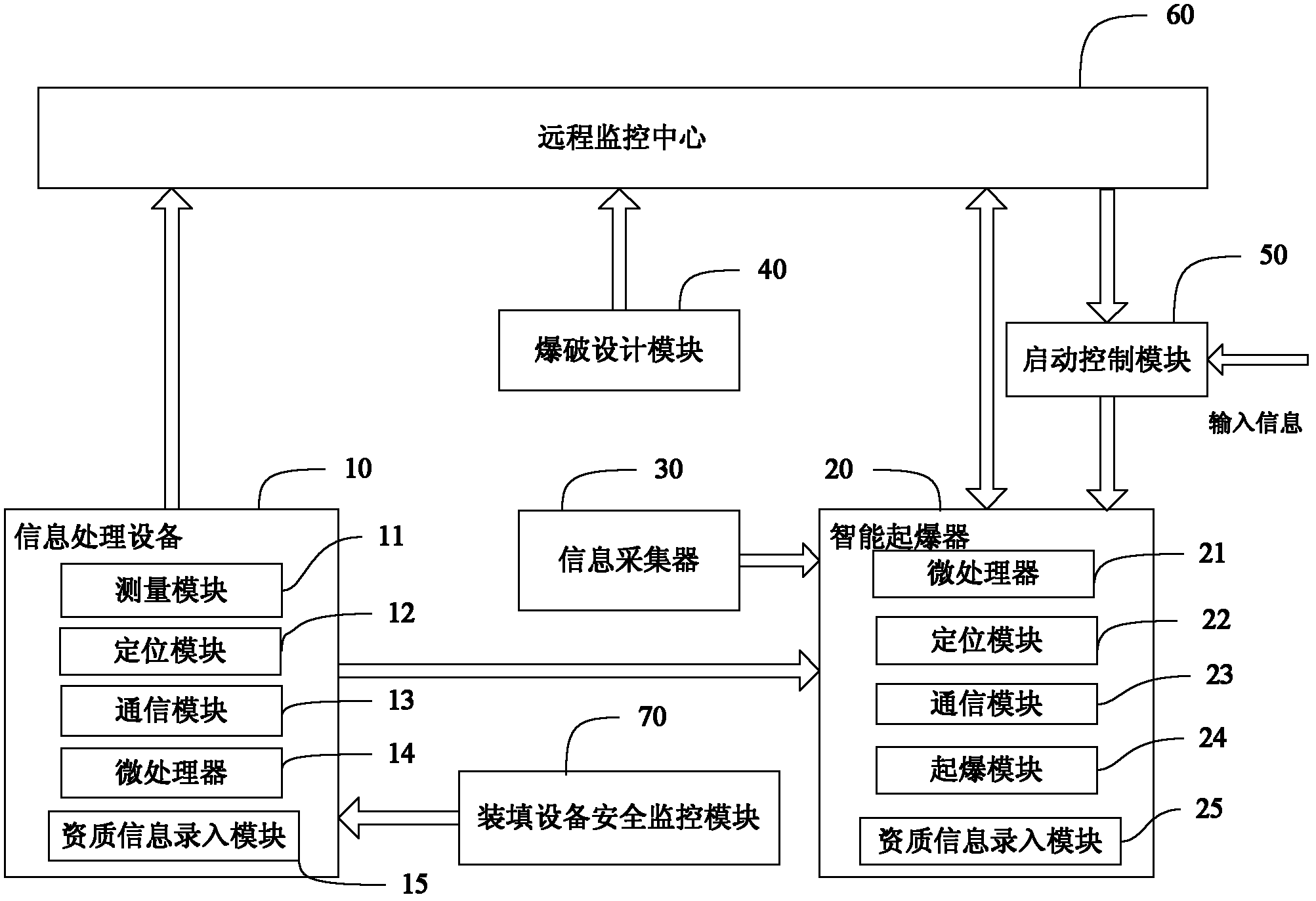
ActiveCN102608959AAvoid lossPrevent theftTotal factory controlProgramme total factory controlTime informationDetonator
The invention relates to an explosive monitoring system and method. The system comprises a blasting design module, signal processing equipment, an information collector, an intelligent detonator and a remote monitoring center. The usage amount, filling place and filling time information of the bulk explosives and the identify information of the packed explosives and the detonating device are collected and whether the detonation conditions are satisfied is judged, and if the detonation conditions are satisfied, the remote monitoring center issues the detonation permission information. By adopting the system and the method, generation and field use of the bulk explosives, legality of the packed explosives and the detonating device and reasonableness and legality of blasting can be monitored in real time and life cycle supervision of the explosives can be achieved.
Owner:ZHUOLIWEI BEIJING TECH
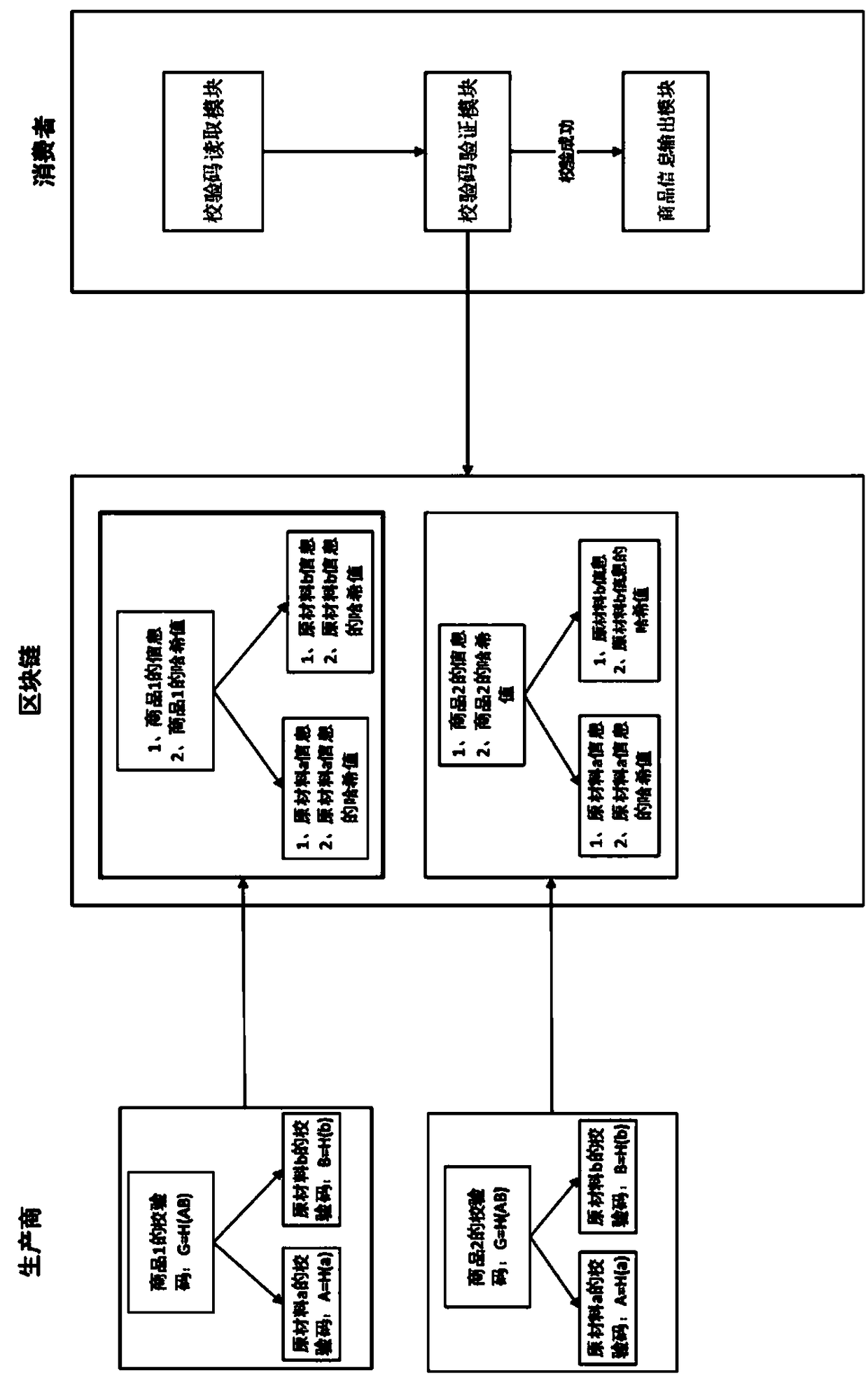
Commodity anti-counterfeiting method and system based on block chain
InactiveCN109146528AOpenWith transparencyCo-operative working arrangementsCommerceComputer scienceData preservation
The invention provides a commodity anti-counterfeiting method and a commodity anti-counterfeiting system based on a block chain, including a commodity information generation module, a commodity information storage module, a check code reading module, a verification code verification module and a commodity information output module, wherein a unified commodity anti-counterfeit system is built by using safe and reliable block chain technology, the establishment of the system will not overthrow the traditional anti-counterfeiting design, nor need to change the habits of consumers, but renovate the original bottom anti-counterfeiting framework into a system based on the block chain design, and store the data in the block chain, so that the information of the uplink can not be tampered with andcounterfeited, according to the characteristic, the reliability of the commodity information is ensured.
Owner:郑州信大壹密科技有限公司
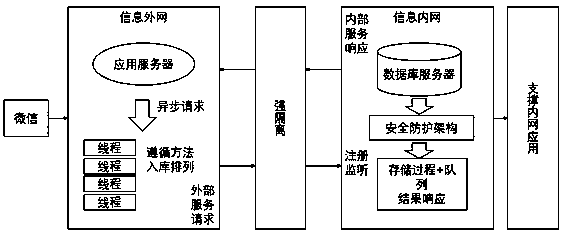
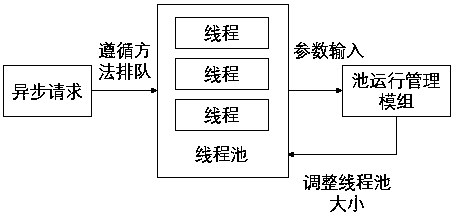
Internal and external network isolation penetration design method
InactiveCN110401635AReduce occupancyEasy to handleProgram initiation/switchingData switching networksDynamical optimizationThread pool
The invention discloses an internal and external network isolation penetration design method. The method comprises the following steps: S1, queuing a large number of load requests by utilizing an M / M / 1 / K / infinity / FCFS queuing idea; S2, introducing an extended thread pool on the basis of the basic thread pool, transmitting configuration parameters and control messages through a pool management module to obtain system performance indexes, and creating a new thread and a blocked extended thread according to a dynamic optimization strategy; S3, queuing a system; S4, performing a thread pool dynamic management mechanism; S5, giving a thread scheduling algorithm based on the M / M / 1 / K / infinity / FCFS queuing model and the two dynamic adjustment processes; and S6, designing a boundary security protection architecture for internal and external network information interaction. According to the method, by effectively adjusting the scale of the thread pool, the performance guarantee capability of theserver applying the method is improved, data in the penetration process are monitored and protected, and the safety and stability of the internal and external network environment are maintained.
Owner:ELECTRIC POWER RES INST OF STATE GRID ANHUI ELECTRIC POWER +1
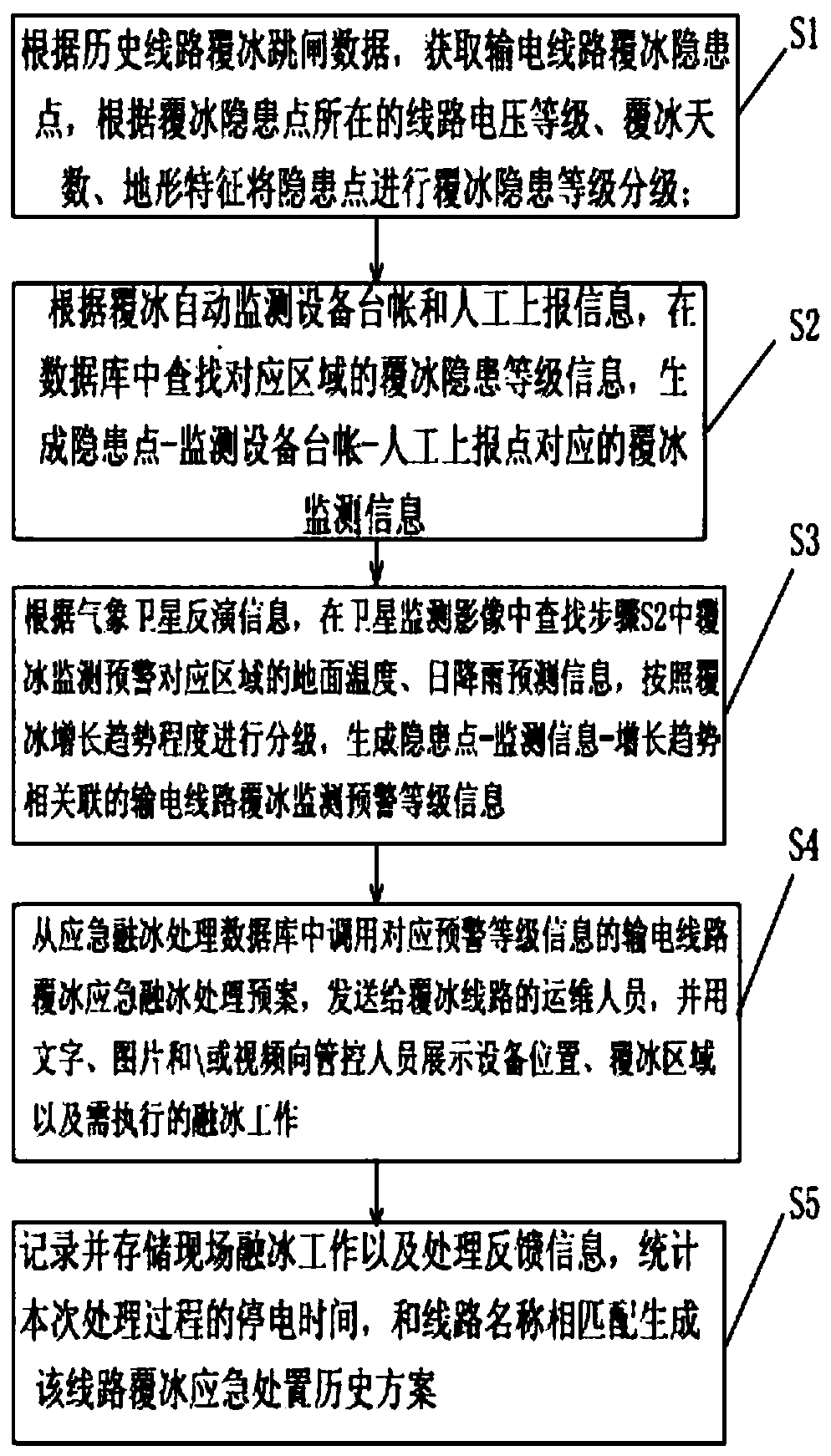
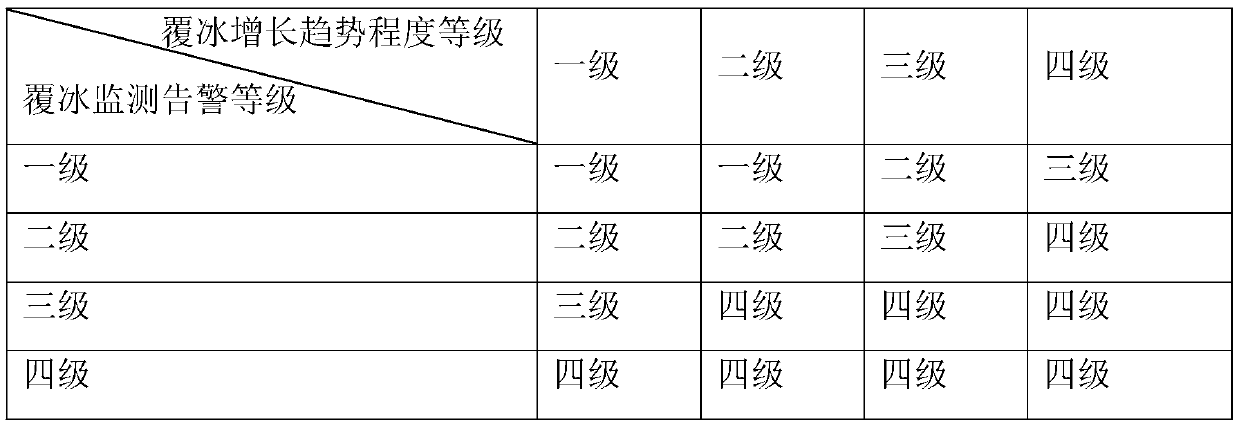
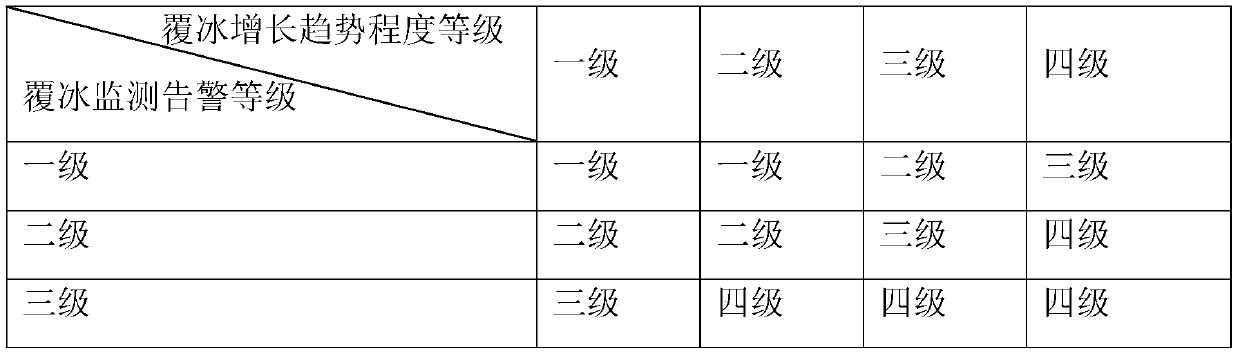
Power transmission line icing multi-source monitoring and early warning method and system
PendingCN111047177AConducive to preventionPracticalGeographical information databasesResourcesMeteorologyMonitoring data
The invention discloses a power transmission line icing multi-source monitoring and early warning method and system. According to the method, by combining various data sources from power grid icing automatic monitoring, manual reporting and meteorological satellite inversion and the like, coupling correlation analysis of power grid icing multi-source monitoring data is carried out, a power grid icing multi-source monitoring and early warning model integrating icing hidden danger, icing real-time monitoring, icing growth trend and emergency ice melting is established, comprehensive sensing andearly warning of power grid large-range regional icing are achieved, and power grid icing disaster prevention and control are facilitated. The method is high in practicability and convenient to operate, has guiding significance for power transmission line operation personnel in making icing emergency decisions, and plays an important role in maintaining safety and stability of a power grid and reducing disaster losses.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
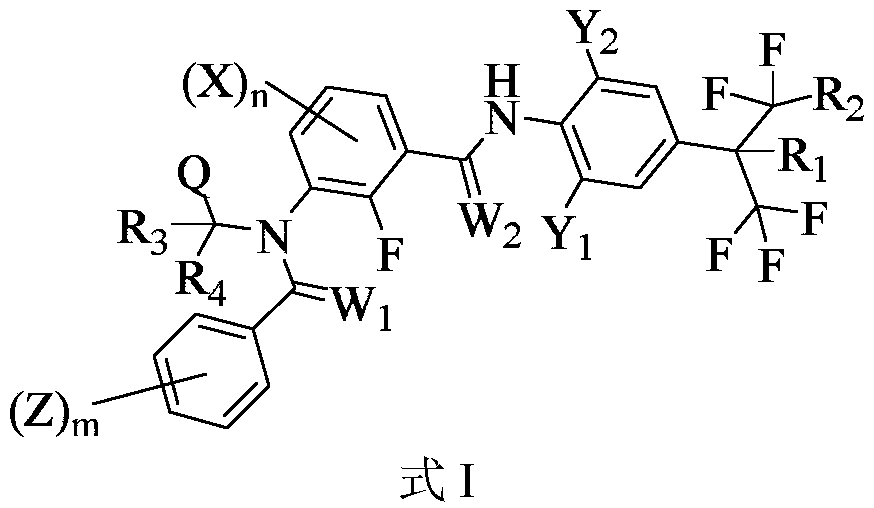
Medicine composition containing m-diamide compound and application of medicine composition
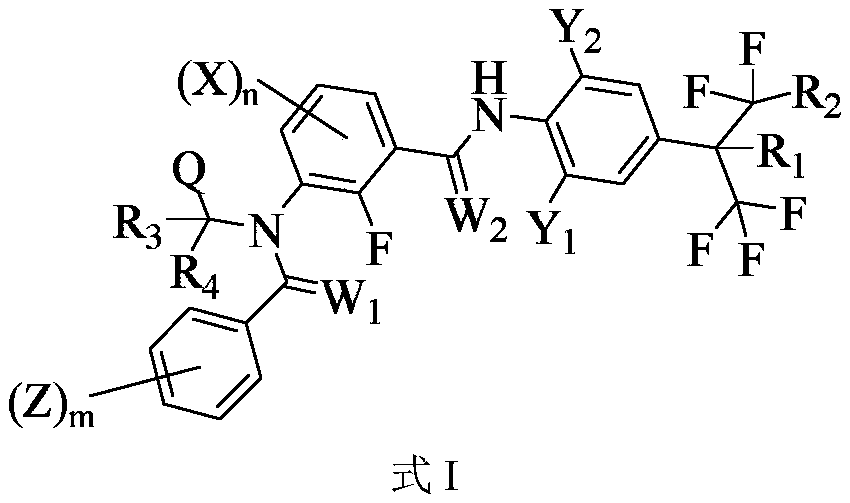
ActiveCN110810409AResidue reductionImprove residual problemsBiocideFungicidesFruit treeChemical compound
The invention provides a medicine composition containing an m-diamide compound and application of the medicine composition. The medicine composition comprises an effective component A and an effectivecomponent B, wherein the effective component A is an m-diamide compound of a structure of a formula I shown in the description; and the effective component B comprises any one or a combination of twoof other insecticides. The composition with the effective component A and the effective component B, which is provided by the invention, has unique functions of synergism, resistant insect control, activity spectrum expansion, virus transmission insect control, and the like, and is capable of effectively preventing and treating a diversity of diseases and insects of crops such as rice, corn, wheat, vegetables, fruit trees, flowers, oil plants and sugar plants, and gardening and forestry as well.
Owner:CAC NANTONG CHEM
Reservation access method, system, computer device and storage medium
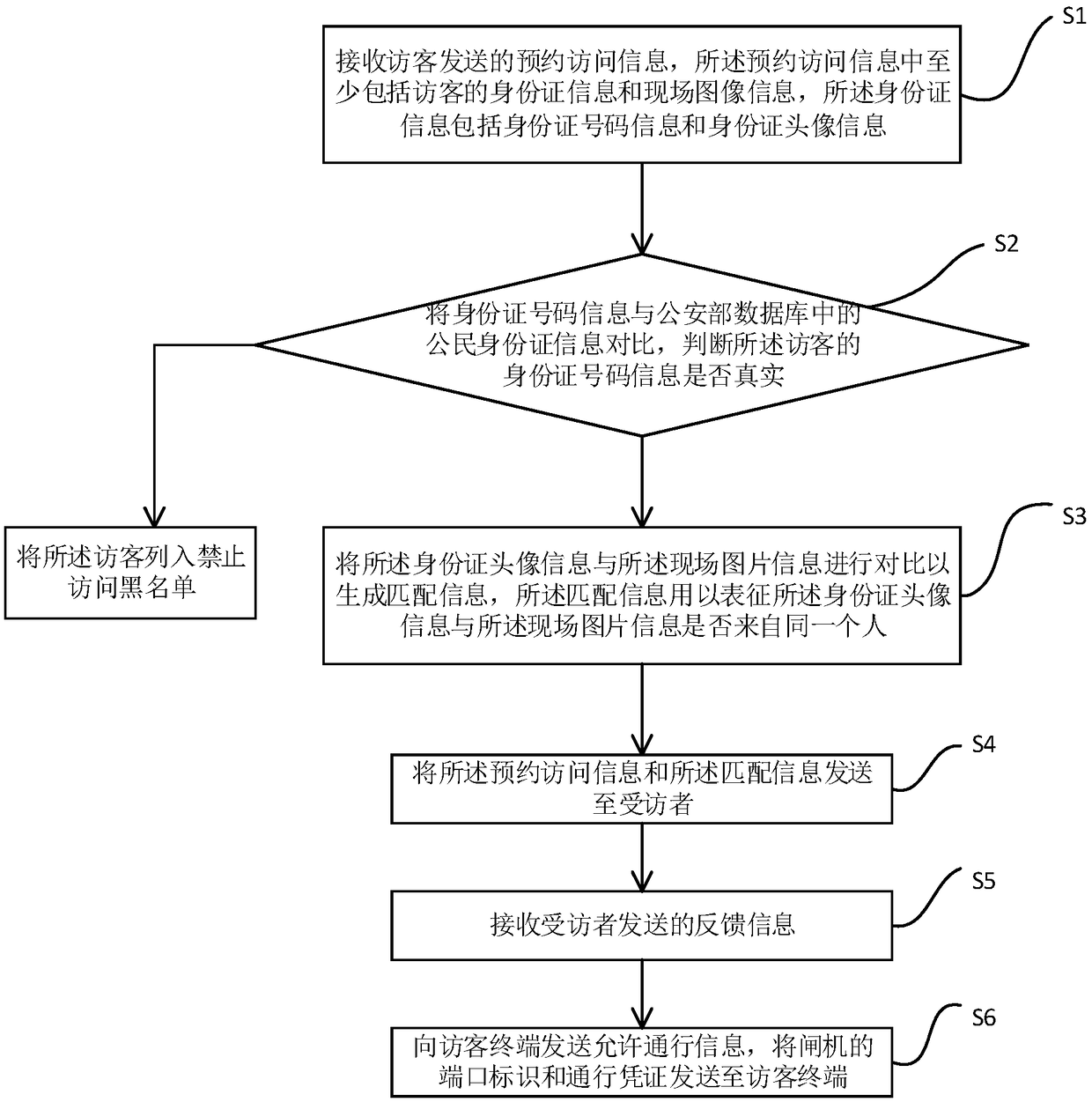
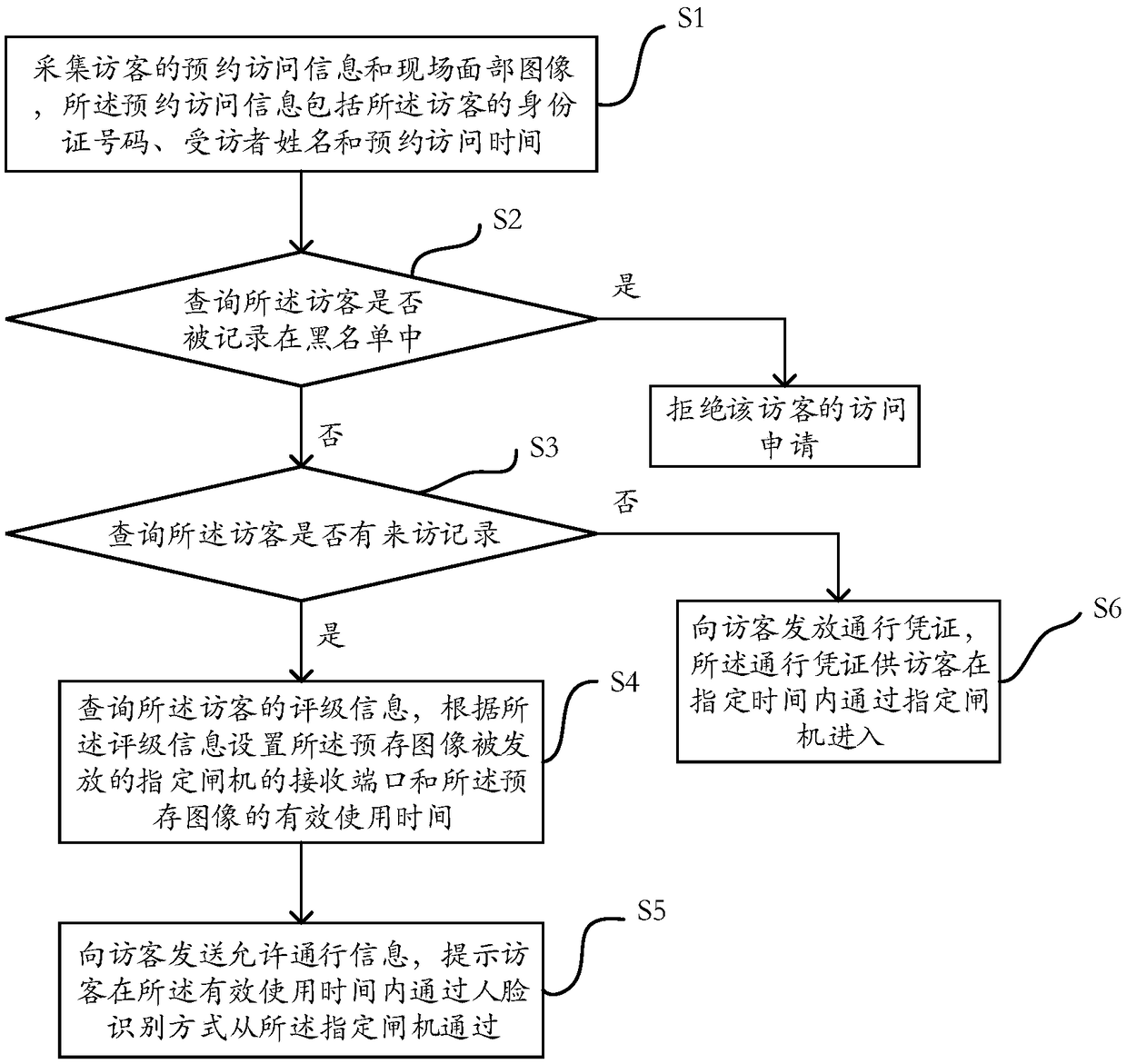
InactiveCN109409552AAvoid entering the office area of the workplaceRealize self-service appointment visitReservationsIndividual entry/exit registersAccess methodData bank
The invention provides a reservation access method with self-checking identity function. The method comprises the following steps: S1, receiving reservation access information sent by a visitor, wherein the reservation access information comprises at least ID card information and scene image information of the visitor, and the ID card information comprises ID card number information and ID card head image information; S2, comparing the ID card number information with the citizen ID card information in the database of the Ministry of Public Security, and judging whether the ID card number information of the visitor is true or not; S3, compare that head image information of the ID card with the scene picture information to generate matching information, wherein the match information is usedfor characterizing whether the head image information of the ID card and the scene picture information come from the same person or not; S4: sending the reservation access information and the matchinginformation to the interviewee; S5: receiving feedback information sent by the interviewee; S6: Sending the passage information to the visitor according to the feedback information.
Owner:PING AN TECH (SHENZHEN) CO LTD
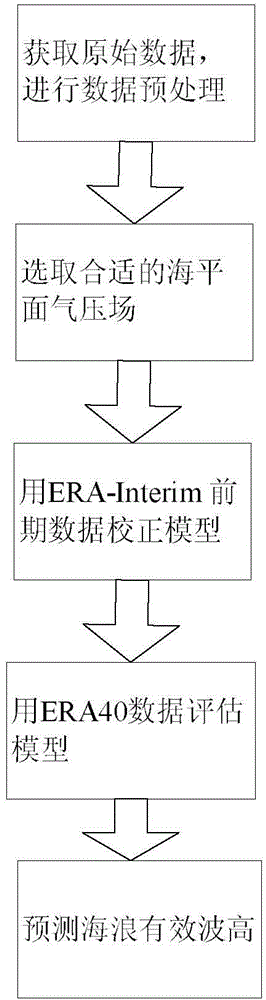
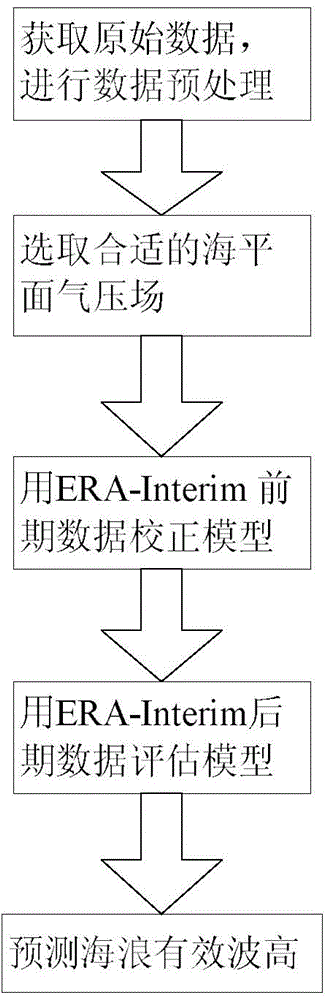
Method for forecasting sea wave significant wave height based on ERA-Interim
InactiveCN104021434AAddress reliabilityMaintain security and stabilityForecastingSignificant wave heightAnalysis data
The invention discloses a method for forecasting sea wave significant wave height based on ERA-Interim. The method includes the following steps that original data are acquired, and data preprocessing is conducted; an appropriate sea level pressure field is selected; a data correction forecast model in a first time period in the ERA-Interim is adopted; the prediction model is evaluated through data of a second time period which is posterior to the first time period in the ERA-Interim; the sea wave significant wave height is predicted through the forecast model. A data source is reanalyzed through the long-term stable ERA-Interim in the European centre for medium-range weather forecasts, data for forecasting the sea wave significant wave height are extracted from the data source, the sea wave significant wave height in multiple time levels can be forecasted in assistance with a principal component analysis method, operability is high, and forecast accuracy is high.
Owner:HOHAI UNIV
Drivage peripheral hole homoenergetic blasting method
The invention discloses a drivage peripheral hole homoenergetic blasting method. Peripheral holes (6) are dug on a roadway contour line of a surrounding rock (1) at the end part of a roadway; explosives (4) and cushioning materials (3) are alternatively arranged in each peripheral hole (6) from inside to outside; the explosives (4) in the adjacent peripheral holes (6) are distributed in a shape of a Chinese character pin; detonators (5) are arranged in sections along the explosives (4); nonel tubes (9) of the detonators (5) are led out of the holes along the hole walls of the peripheral holes (6); hole orifices of the peripheral holes (6) are plugged by stemming (2); then detonation is carried out according to a designed detonation network connecting line. According to the method disclosed by the invention, the explosives (4) and the cushioning materials (3) are distributed symmetrically, so that energy is more uniformly distributed, an energy utilization rate of the explosives is improved, a contour of a roadway section is well controlled, the back break phenomenon is avoided, and roadway supporting cost is reduced; meanwhile, the uniformly distributed explosive energy can enable a fragment size for blasting to be uniform, obviously improve a blasting effect and improve shovel-loading efficiency after blasting.
Owner:SINOSTEEL MAANSHAN INST OF MINING RES +1
Dustproof and explosion-proof pelleting and drying equipment for oily sludge
PendingCN108558164ANo mechanical actionReduce productionSludge treatment by de-watering/drying/thickeningGranulation in rotating drumsSludgeCombustible gas
The invention discloses dustproof and explosion-proof pelleting and drying equipment for oily sludge. The equipment comprises a pelleting cabin and a drying cabin, multiple roller cylinders are horizontally installed in the pelleting cabin, and a motor A is installed at the exterior of the pelleting cabin; a feeding port is formed in the upper portion of the pelleting cabin, and a thermometer A and a pressure gauge A are installed at the feeding port; a rotation shaft is vertically installed in the drying cabin, a motor B is connected to the bottom of the rotation shaft, and a small heating disc and a large heating disc are alternatively installed on the rotation shaft; multiple rake arms are distributed on the small heating disc and the large heating disc from the center to the exterior,multiple rake blades are vertically installed on the rake arms, and a discharging port is formed in the lower end of the drying cabin; a thermometer B, a pressure gauge B and a combustible gas concentration detection meter are installed on the side wall of the drying cabin; communicated steam pipes are arranged in the pelleting cabin and the drying cabin. The dustproof and explosion-proof pelleting and drying equipment has the advantages that the safety is high, the running maintenance cost is low, the low-quality heat source can be used, the products are good in quality, and the water treatment amount in the later period and the water demand amount are small.
Owner:JIANGSU LV CHUAN ENVIRONMENTAL PROTECTION TECH
A power grid mountain fire potential fire point identification method based on a two-dimensional OTSU
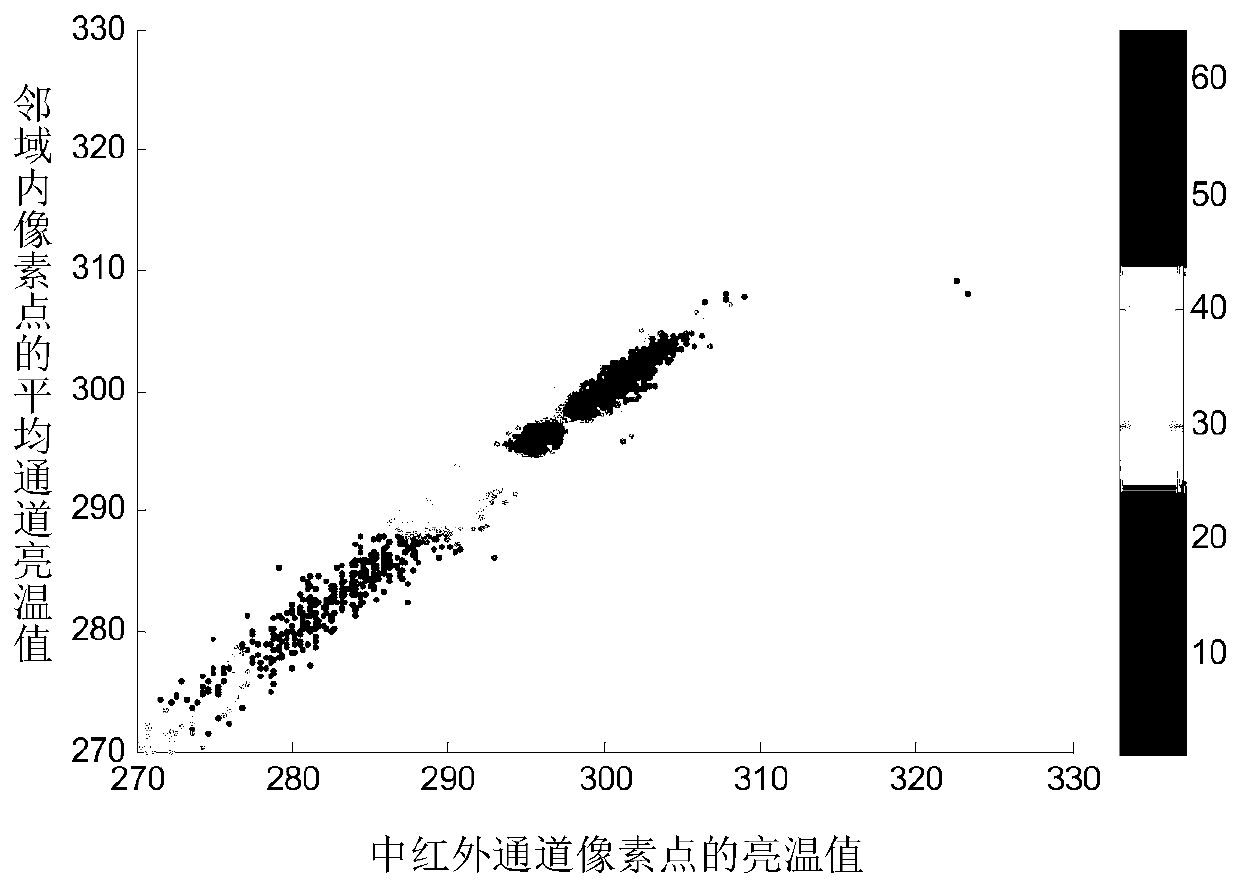
PendingCN109902666AMaintain security and stabilityImproving the efficiency of wildfire monitoring and identificationImage analysisCharacter and pattern recognitionBrightness temperaturePower grid
The invention discloses a power grid mountain fire potential fire point identification method based on a two-dimensional OTSU. The method comprises the following steps: firstly, dividing a satellite image data plane into a plurality of rectangular sub-regions according to latitude and longitude; Selecting a sub-region as a to-be-identified region, calculating an average channel brightness temperature characteristic value of pixel points in a neighborhood of each pixel point in the to-be-identified region, and calculating two-dimensional probability distribution of the pixel brightness temperature characteristic values in the to-be-identified region; And obtaining a fire point determination optimization threshold based on a two-dimensional OTSU method, and determining whether each pixel point in the to-be-identified area is a potential fire point according to the optimization threshold. According to the method, the judgment threshold of the potential fire point is calculated only according to the current image; According to the method, the characteristic value distribution information of the whole pixels in the region is fully utilized, the adaptive adjustment of the mountain fire judgment threshold can be carried out according to different time and different regions without the help of historical threshold values, the alarm accuracy is high, the calculation efficiency is high,the practicability is high, and the method plays an important role in maintaining the safety and stability of a power grid and preventing and reducing disasters.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
Power transmission line forest fire monitoring and early warning method and system based on multi-source data
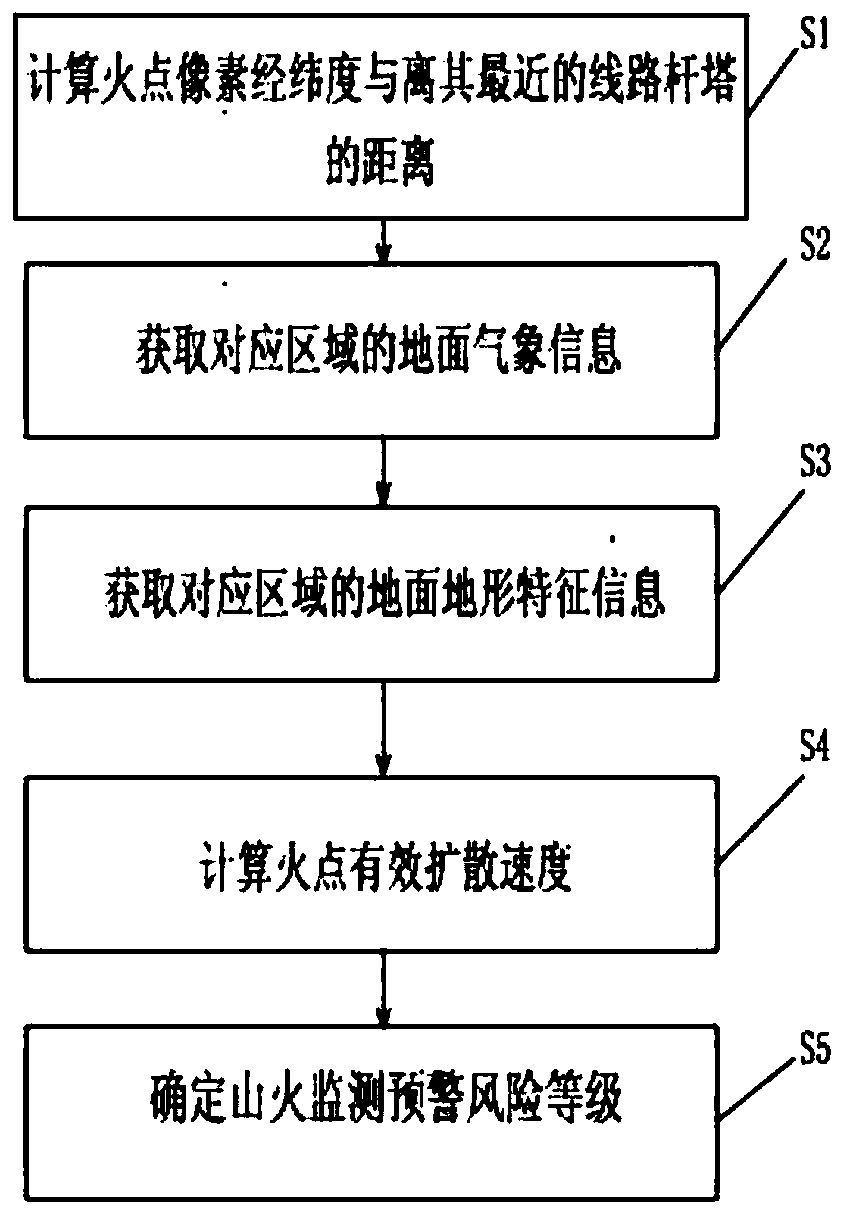
PendingCN110955744ASecurityPracticalGeographical information databasesResourcesMeteorologyMonitoring data
The invention discloses a power transmission line forest fire monitoring and early warning method and system based on multi-source data. The power transmission line forest fire monitoring and early warning method comprises the following steps: (1) calculating the distance between forest fire point pixels and a tower; (2) extracting ground meteorological information; (3) extracting ground topographic features; (4) calculating the effective diffusion speed of the fire point; and (5) releasing mountain fire monitoring early warning. By combining various data sources such as power grid mountain fire satellite monitoring alarm information, ground online monitoring device meteorological monitoring information, topographic features, underlying surface features and the like, the power transmissionline forest fire monitoring and early warning method evaluates the effective diffusion speed of the mountain fire of the power transmission line corridor at different moments, carries out comprehensive alarm analysis of power grid mountain fire multi-source monitoring data, monitors and alarms mountain fire alarm position-mountain fire diffusion trend near the power transmission channel corridorintegrally, and guarantees the operation safety of the power transmission line. The power transmission line forest fire monitoring and early warning method is clear in thought, convenient to operate and high in calculation speed and can be widely applied to the field of power grid forest fire satellite monitoring and early warning.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
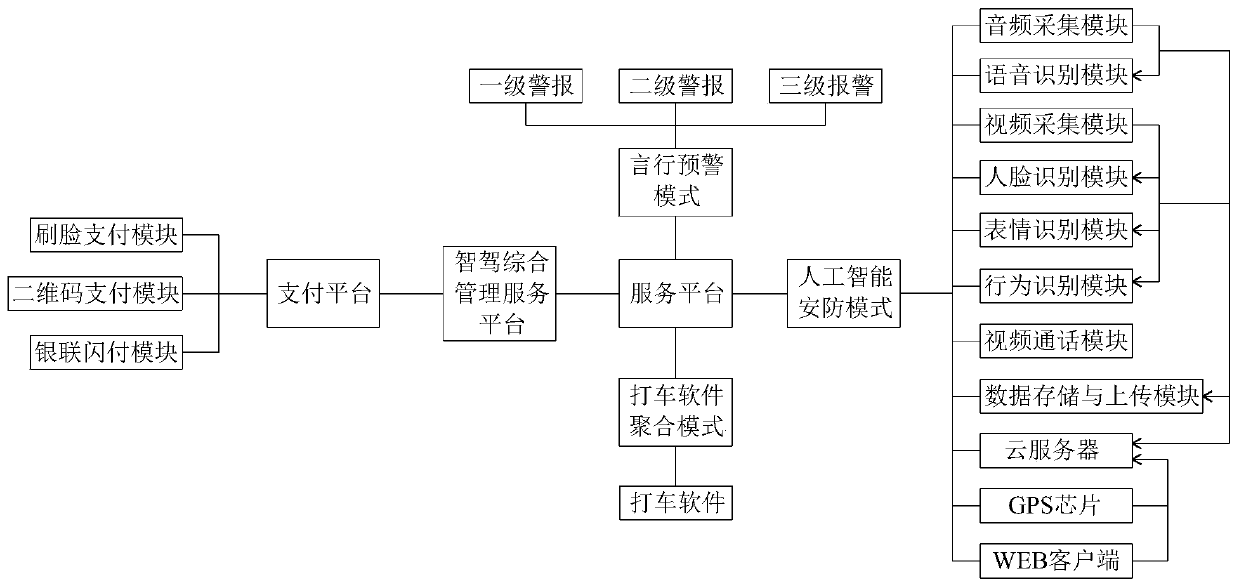
5G communication open type taxi or online taxi-hailing intelligent driving comprehensive management service platform
PendingCN111488784AGuarantee personal safetyMaintain security and stabilitySpeech recognitionTransmissionEngineeringClient-side
The invention discloses a 5G communication open type taxi or online taxi-hailing intelligent driving comprehensive management service platform. The 5G communication open type taxi or online taxi-hailing intelligent driving comprehensive management service platform comprises a payment platform and a service platform. The service platform comprises an artificial intelligence security mode, a taxi taking software aggregation mode and a speech early warning mode. The artificial intelligence security mode comprises an audio acquisition module, a video acquisition module, a face recognition module,an expression recognition module, a behavior recognition module, a voice recognition module, a video call module, a data storage and uploading module, a cloud server, a GPS chip and a WEB client. According to the platform, the condition that passengers use taxis or online taxi hailing during travel can be supervised; the service platform can timely give an alarm to stop or give an alarm for bad behaviors of passengers or vehicle owners, can record and automatically judge speech of the passengers and the vehicle owners, and can timely and accurately give an alarm and give an alarm, so that thepassengers and the vehicle owners are monitored by a public security system, personal safety of the passengers and the vehicle owners is guaranteed, illegal criminal behaviors are effectively restrained, and social safety and stability are maintained.
Owner:四川鼎鸿物联网科技有限公司
Intelligent detonator and intelligent detonating method for explosives
The application relates to an intelligent detonator and an intelligent detonating method for explosives. The intelligent detonator for the explosives comprises a microprocessor, a positioning module, a communication module and a detonating module. The intelligent detonator for the explosives can collect information about usage amount of the bulk explosives, loading location and loading time of the bulk explosives, and identity information of packaged explosives and detonating devices, and upload the information to a remote monitoring center. If detonating conditions are matched, the remote monitoring center sends a detonation permission message to permit the intelligent detonator for the explosives to work, so as to detonate the detonating devices and then detonate the explosives. By using the intelligent detonator and the intelligent detonating method for the explosives, unreasonable and illegal explosion can be effectively avoided.
Owner:ZHUOLIWEI BEIJING TECH
Reservation access method and system, computer device and storage medium
PendingCN109447297AAdd contrast functionMaintain security and stabilityReservationsIndividual entry/exit registersAccess methodBlacklisting
The invention provides a reservation access method and system, a computer device and a storage medium. The method comprises the following steps of S1 collecting reservation access information of a visitor and a scene face image; S2 querying whether the visitor is recorded in the blacklist, and if so, rejecting the visitor's access application; if not, proceeding to the next step; S3 querying whether the visitor has a visiting record, if so, calling out a pre-stored image of the visitor for the visitor to enter the gate through comparison, and executing the step S4; if not, proceeding to step S6; S4 querying the rating information of the visitor, and according to the rating information, setting the effective use time of the receiving port of the designated gate to which the pre-stored imageis issued and the pre-stored image; 5 sendig the permission information to that visitor, prompting the visitor to pass through the designated gate through the face recognition mode within the effective use time; S6 issuing the passport to the visitor for the visitor to enter through the designated gateway within a specified time.
Owner:PING AN TECH (SHENZHEN) CO LTD
A long-term trend prediction method for significant wave height of ocean waves based on reanalysis data
InactiveCN104050514BAddress reliabilityMaintain security and stabilityForecastingSpecial data processing applicationsAnalysis dataData set
The invention relates to a sea wave significant wave height long-term trend prediction method based on reanalysis data. The sea wave significant wave height long-term trend prediction method is characterized by comprising the steps that (1) weather forecast data of an ERA-Interim reanalysis data set at each time frequency are collected, (2) coordinates of all lattice points are obtained, (3) SLP anomaly and standard deviation are calculated, (4) principal component analysis of the SLP anomaly is conducted, (5) Box-Cox transformation is conducted on sea area data, (6) a predictive factor of sea wave significant wave height is calculated, (7) the standard deviation of the significant wave height and the predictive factor is calculated, (8) the predictive factor is applied into a prediction model, (9) a significant wave height lagged value is applied into the model, (10) SLP field prediction on the basis of EOF is carried out, (11) predictive factor optimization selection is conducted, (12) the sea wave significant wave height is predicted through the model, (13) the prediction level is evaluated, (14) the sea wave significant wave height long-term trend is calculated, and (15) a significant wave height long-term trend chart is drawn. According to the sea wave significant wave height long-term trend prediction method based on the reanalysis data, the significant wave height long-term trend of multiple time frequencies can be predicted, and accuracy is high.
Owner:HOHAI UNIV
External breaking controlling method and system for human defense, physical defense and technical defense of power transmission line
The invention discloses an external breaking controlling method and system for human defense, physical defense and technical defense of a power transmission line. The method comprises the steps of: obtaining hidden danger points of external breaking of the power transmission line according to historical external breaking data and classifying the hidden danger points according to areas where the hidden danger points are located, statistical information of construction sites and on-site vegetation information; searching equipment accounts and control personnel information of corresponding areasin a database according to the areas where the hidden danger points are located; establishing corresponding hidden danger point information of the hidden danger points-the classes-the equipment accounts-the control personnel; and respectively monitoring the hidden danger points according to the classes of the hidden danger points, when real-time data of a hidden danger point exceed a monitoring threshold of the corresponding class, generating corresponding class of the power transmission line external breaking warning information, calling a processing plan of the corresponding class of the power transmission line external breaking warning from the database, sending to the control personnel of the hidden danger point and displaying the equipment position, the hidden danger point area and the processing work needing to be carried out to the control personnel. The method disclosed by the invention has the beneficial effects that the prevention and the treatment of the external breaking ofa power grid are benefited; and the method is strong in practicability and convenient to operate.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
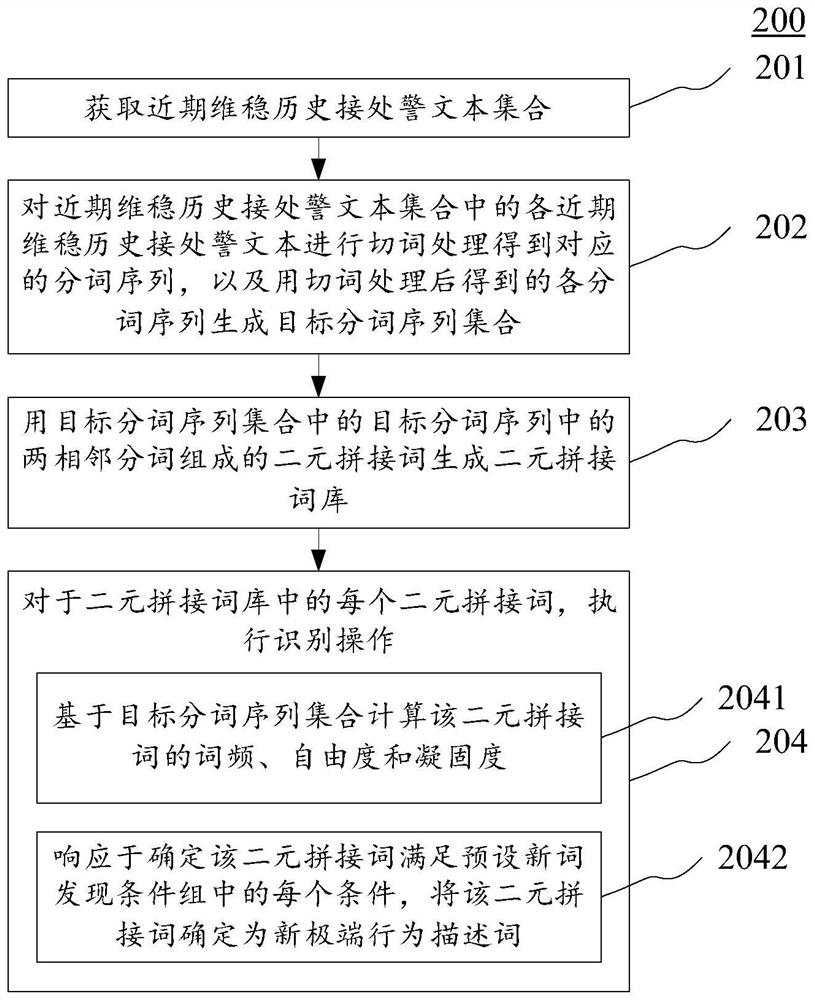
New illegal behavior descriptor recognition method and device, electronic equipment and storage medium
PendingCN111626054AReduce labor costsAvoid time costData processing applicationsNatural language data processingPattern recognitionEngineering
The invention provides a new illegal behavior descriptor recognition method and device, electronic equipment and a storage medium. A specific embodiment of the method comprises the steps of obtaininga recent historical alarm receiving and processing text set; performing word segmentation processing on each recent historical alarm receiving and processing text in the recent historical alarm receiving and processing text set to obtain a corresponding word segmentation sequence, and generating a target word segmentation sequence set by using each word segmentation sequence obtained after word segmentation processing; generating a binary spliced word bank by using binary spliced words formed by two adjacent segmented words in a target segmented word sequence in the target segmented word sequence set; and for each binary spliced word in the binary spliced word bank, executing an identification operation to determine whether the binary spliced word is a new illegal behavior description word. According to the embodiment, the new illegal behavior description words in the recent historical alarm receiving and processing text set are automatically extracted.
Owner:北京明亿科技有限公司
Electric transmission line forest fire forecasting method
The invention provides an electric transmission line forest fire forecasting method, which includes the following steps: (1), collecting meteorological data; (2.1), analyzing fire using conditions in industry and agriculture; (2.2), analyzing precipitation conditions; (2.3) analyzing rainless days conditions; (2.4), analyzing temperature conditions; (2.5), analyzing humidity conditions; (3), drawing forecasting conclusion; (4), issuing forecasting conclusion. The electric transmission line forest fire forecasting method has the following advantages that:(1),the method can perform electric transmission line forest fire forecasting for power grid forest fire area of next two days; (2), the electric transmission line forest fire forecasting method is high in practical application and convenient to operate; (3), the accuracy rate of forecasting electric transmission line forest fire is high; (4), the method has a guiding significance for electric transmission line operating staffs to draw up a forest fire prevention and control measurement, and has an important effect on maintaining the safety and stability of the power grid and reducing disaster loss.
Owner:STATE GRID HUNAN ELECTRIC POWER +3
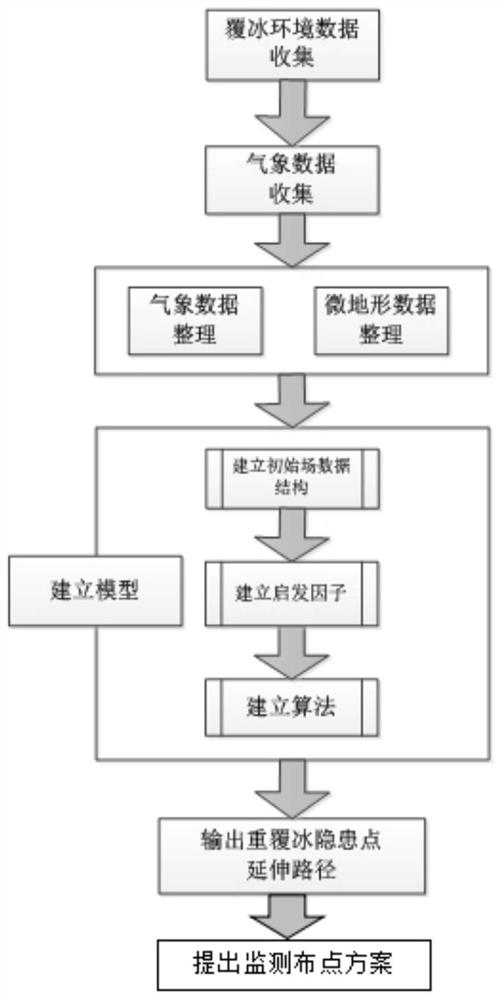
Monitoring point distribution method and system based on power grid microtopography icing threat path extension analysis
ActiveCN112630836AAchieve improvementImprove targetingSeismic signal processingPower gridAtmospheric sciences
The invention discloses a monitoring point distribution method and system based on power grid microtopography icing threat path extension analysis, and the method comprises the steps: selecting a to-be-analyzed region easy to ice, and collecting topographic data and meteorological prediction data of the region before the region is frozen by rain and snow in winter; implementing gridding; utilizing numerical elevation topographic data to establish icing micro-topographic grid data, and establishing icing micro-topographic heuristic factors; forming an icing environment multi-dimensional array; establishing a heuristic factor corresponding to the type of the meteorological prediction data; outputting an extension path of the microtopography icing threat by optimizing the ant colony algorithm according to a microtopography heuristic factor, the heuristic factor corresponding to the type of the meteorological prediction data and a distance heuristic factor and a pheromone factor of the ant colony algorithm; and monitoring and distributing key microtopography point locations and important power transmission lines on an extension path threatened by microtopography icing. According to the invention, the occurrence position and development condition of the icing threat can be directly obtained.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
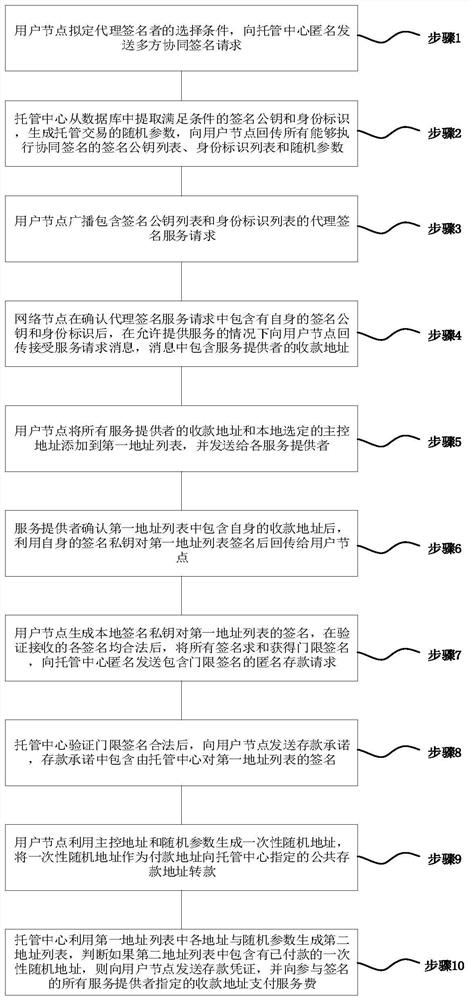
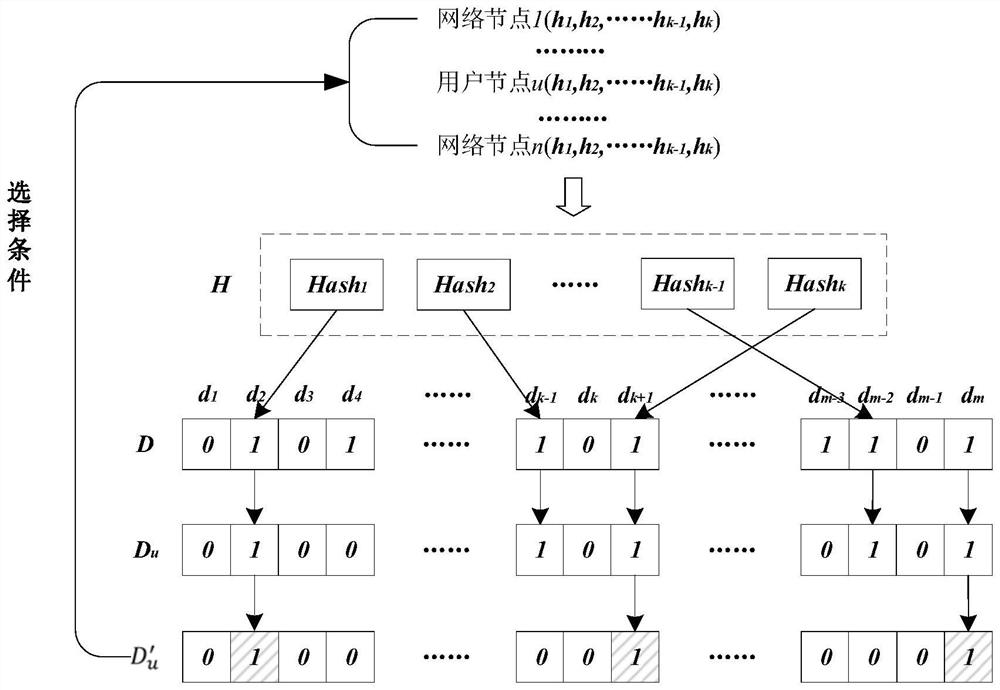
Block chain hosting transaction method and system for multi-party collaborative privacy protection
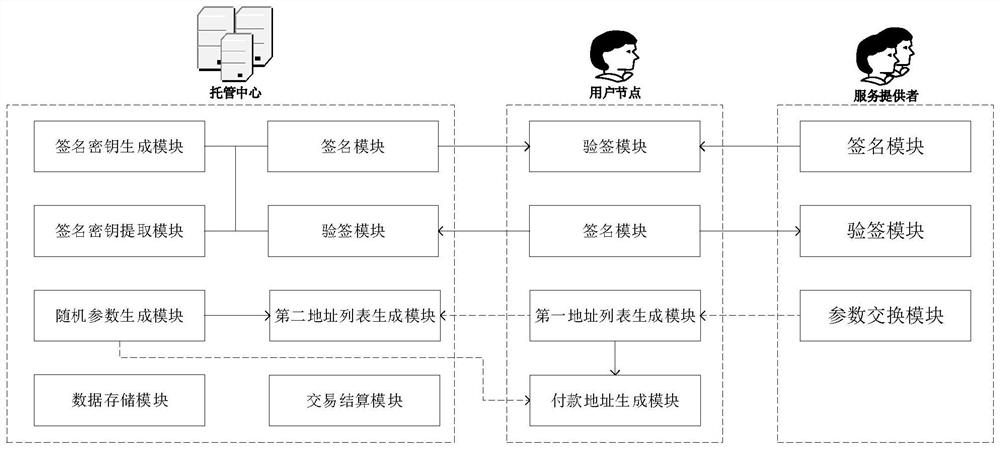
PendingCN114565386AEnhanced anonymityAvoid exposureDigital data protectionPayment protocolsDigital currencyComputer network
The invention relates to a block chain trusteeship transaction method and system for multi-party collaborative privacy protection, and the method comprises the steps: initiating a deposit request to a trusteeship center through a user node, and enabling the trusteeship center to distribute a signature public key and identity information of a legally registered proxy signature service provider for the user node; then providing self-signature components for the user node by a service provider through negotiation, and aggregating the signature components which contain the self-signature of the user and are not less than a threshold number so as to obtain a threshold signature with a collaborative protection characteristic, so that the independent signature of the user node is completely hidden in the threshold signature; a personal signature of a user node is prevented from being directly exposed to a hosting center under the condition that a signature validity verification function is ensured, so that a digital currency input address and a signer identity cannot be associated; in addition, the trusteeship center isolates the user deposit transaction from the payment service fee transaction, and the deposit address of the user node is transparent to the service provider, so that the user anonymization is completely realized.
Owner:潘林浪
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com