Aware-data-based wireless sensor network abnormity type discriminating method
A wireless sensor and data sensing technology, applied in network topology, wireless communication, advanced technology, etc., can solve the problems of not giving energy consumption relationship, increasing node energy consumption, high energy consumption, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
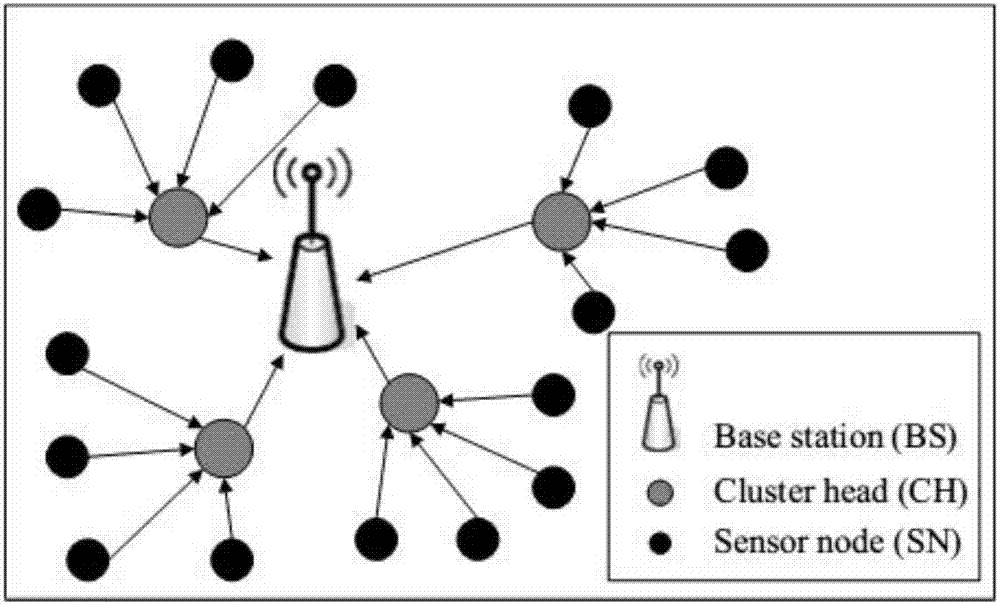
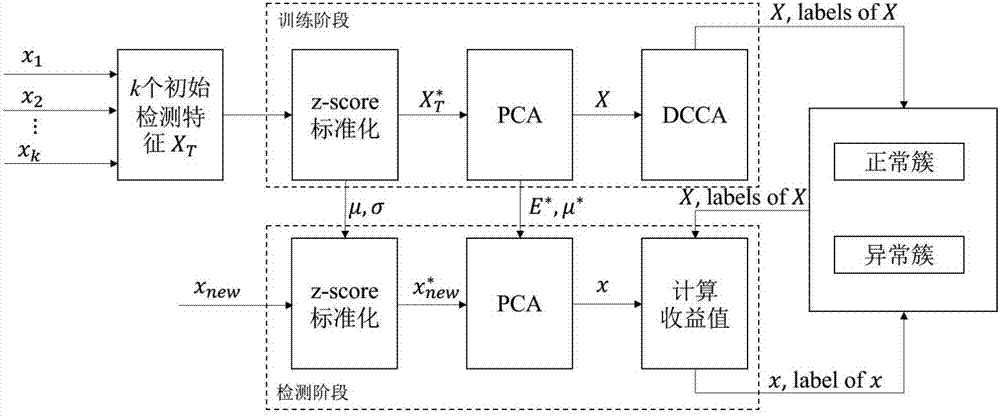
[0048] figure 1 It is a structural diagram of a wireless sensor network for implementing the present invention. The network node sends sensing data to the base station every time interval Δt, and the base station generates the detection feature based on the received sensing data. The detection feature set generated during the normal time period (without the occurrence of aggressive behavior) is used as the training set. The method is deployed in the base station, and the flow chart of the method is as follows figure 2 shown. The steps are as follows:
[0049] Step 1: Wireless sensor network node S={S j :j=1,2,...,m} Every fixed time interval Δt, each node collects a set of sensing data (such as temperature, humidity and brightness, etc.) and sends it to the base station. Node S j A set of recorded sensory data is a p-dimensional vec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com