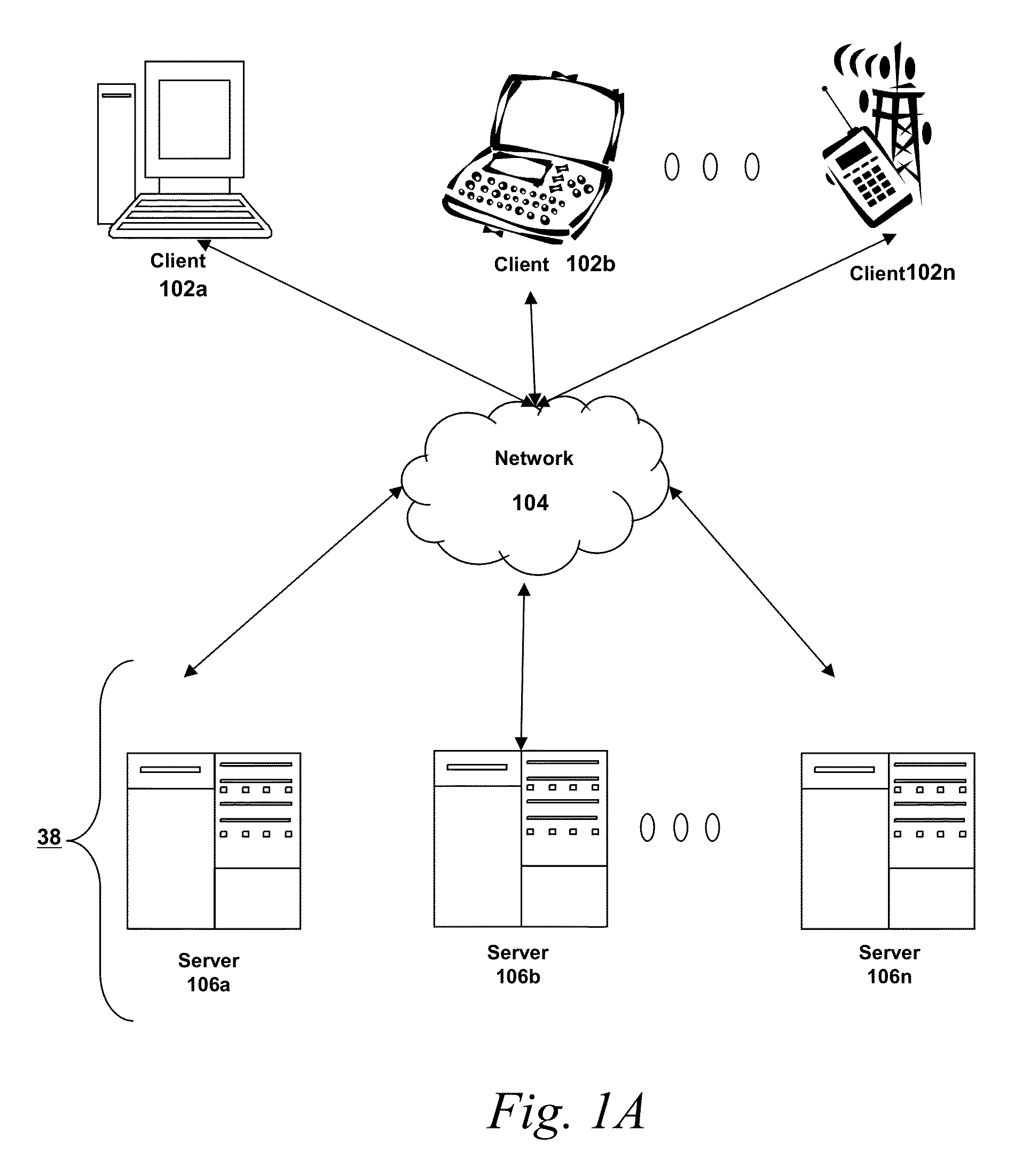
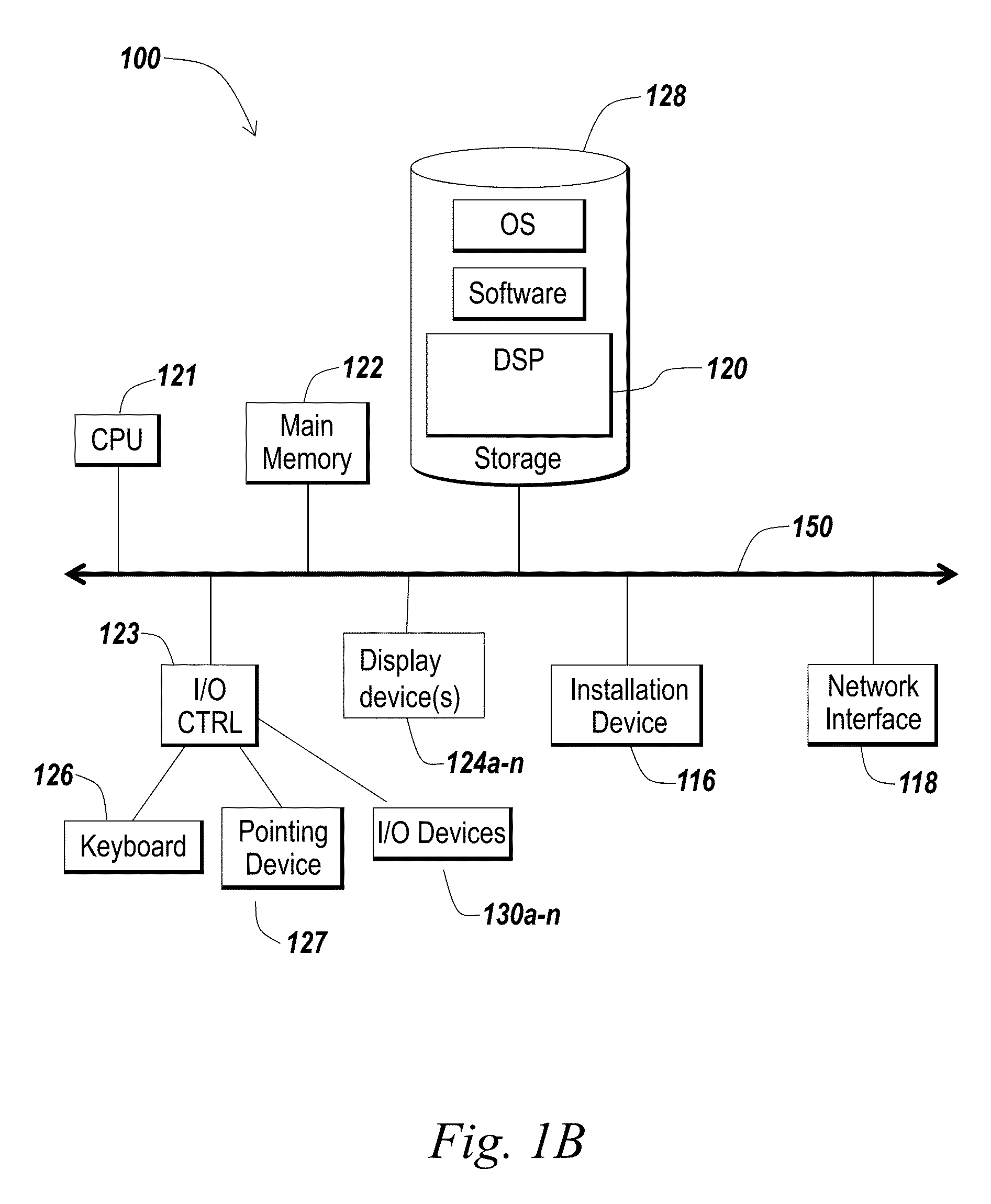
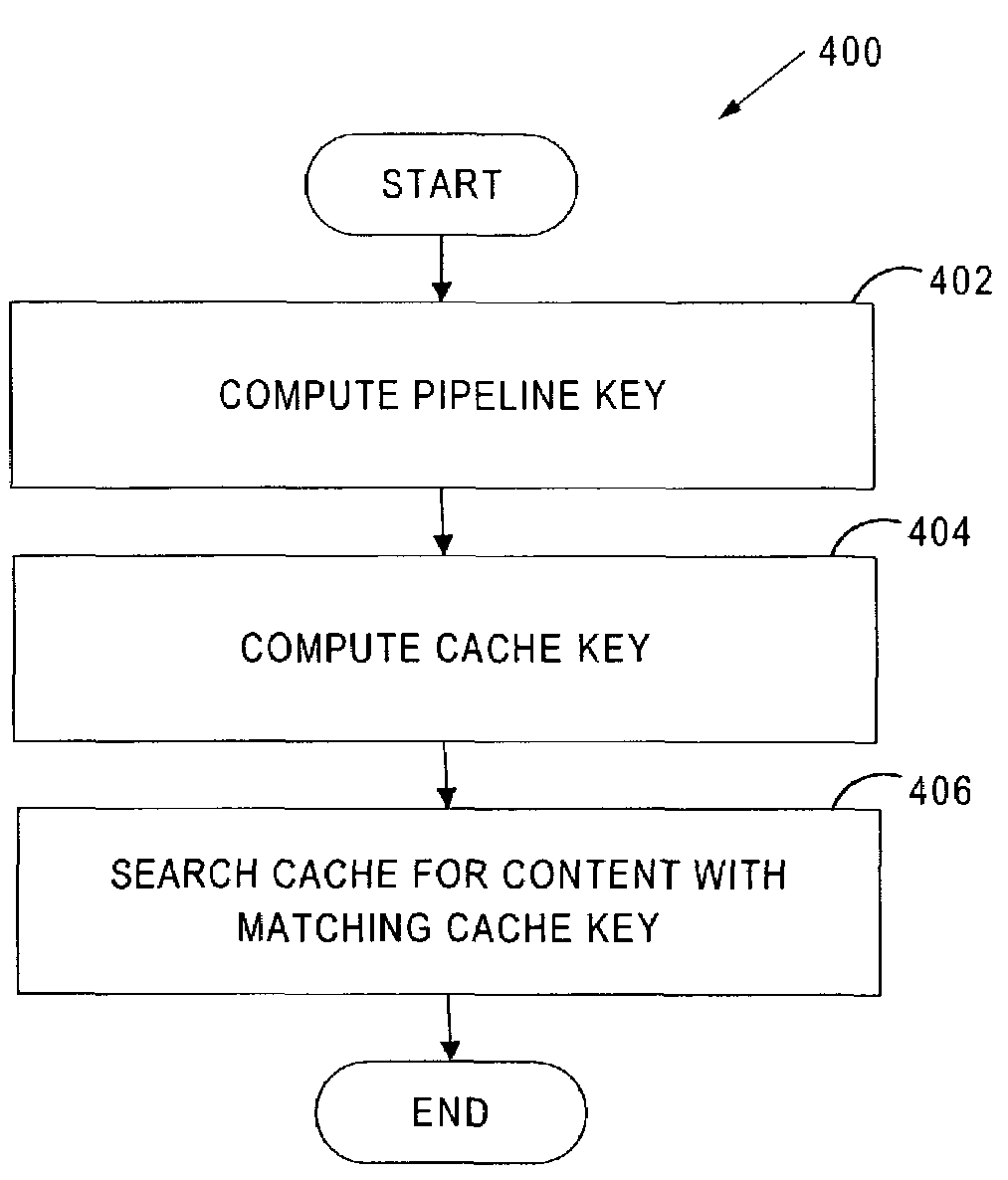
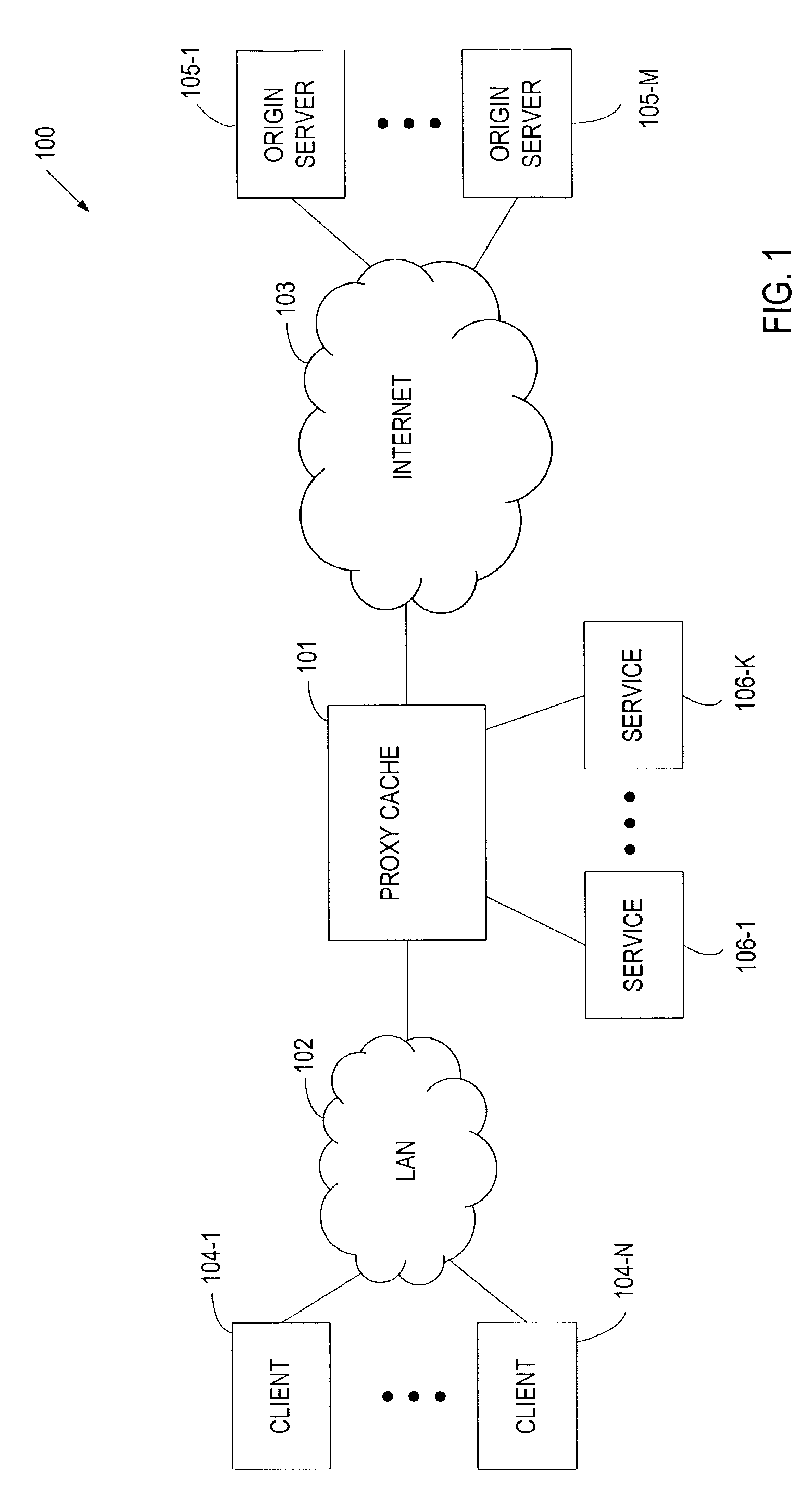
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
122 results about "Web object" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
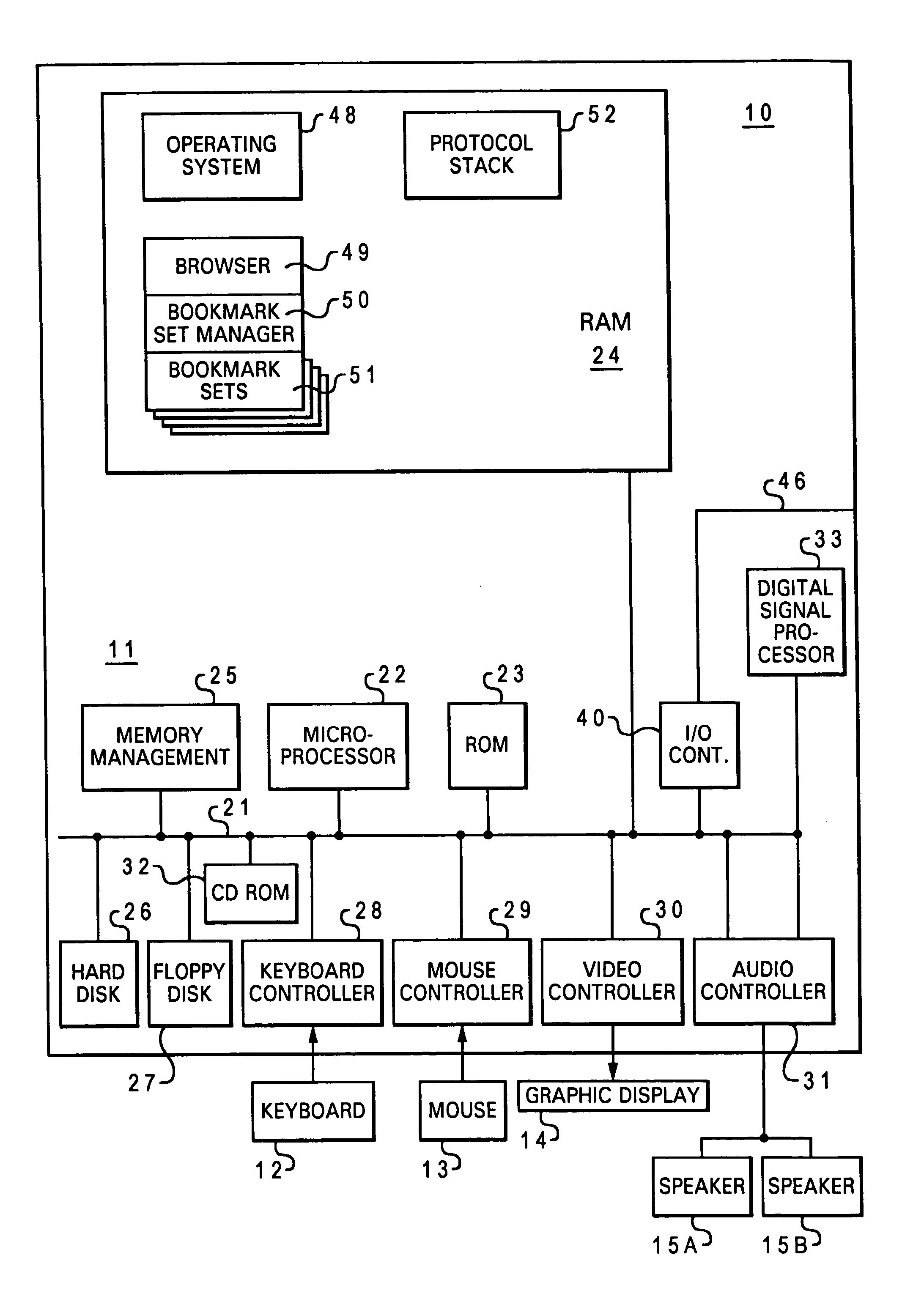
A Web Object, simply put, is any content that can be contained in a Web page. Web Objects can be used for inserting existing Web pages into your presentation, thereby allowing you to leverage previously created content.
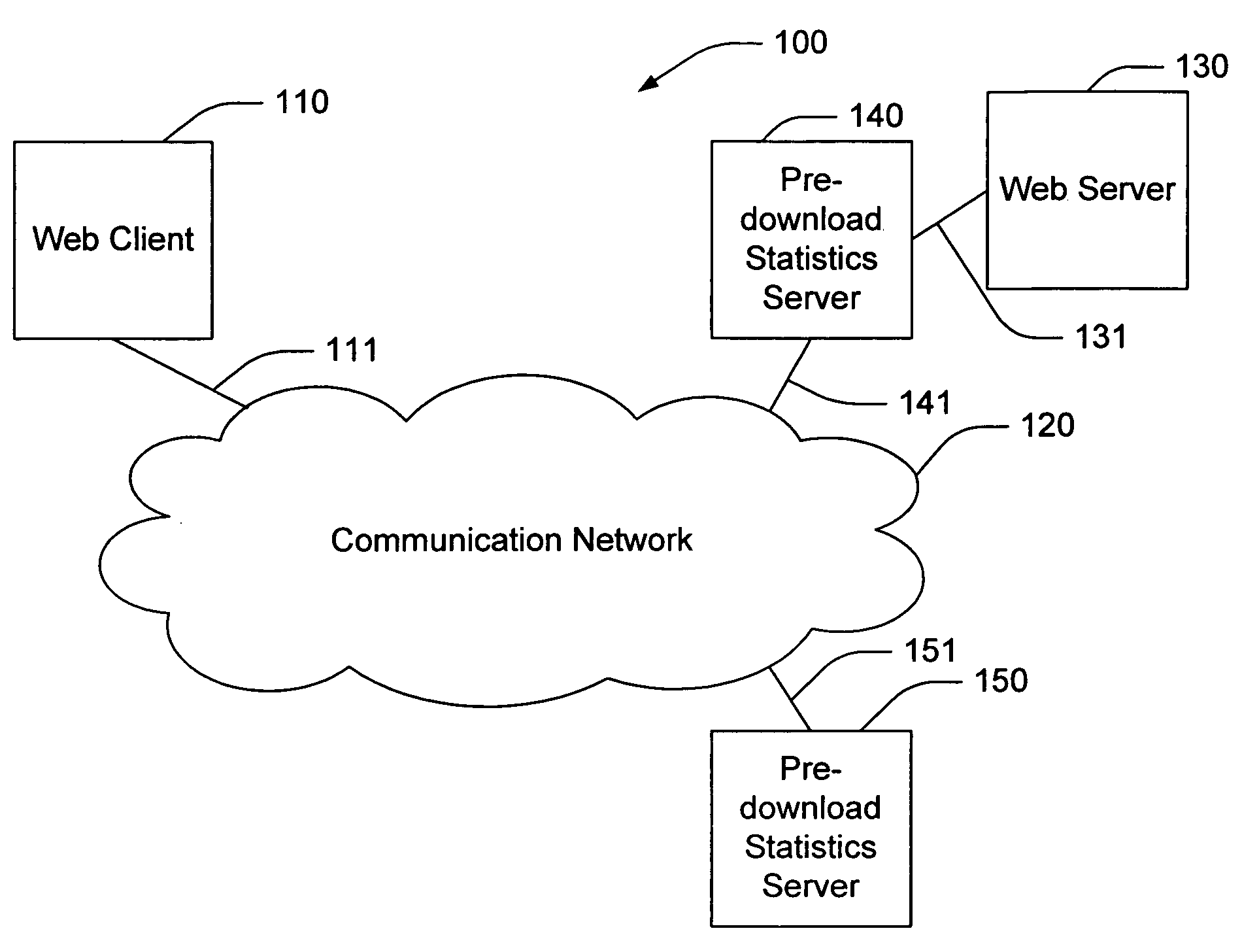
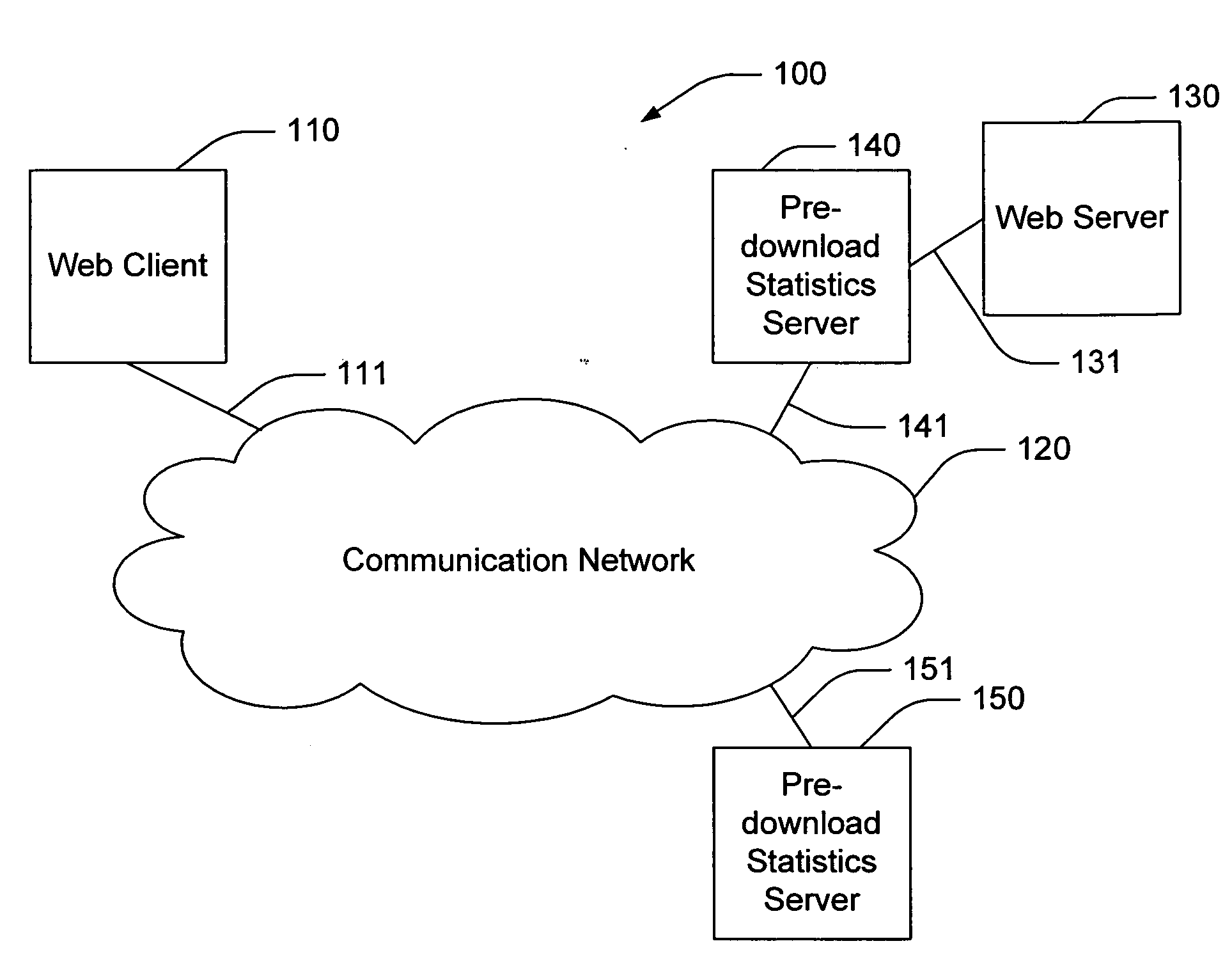
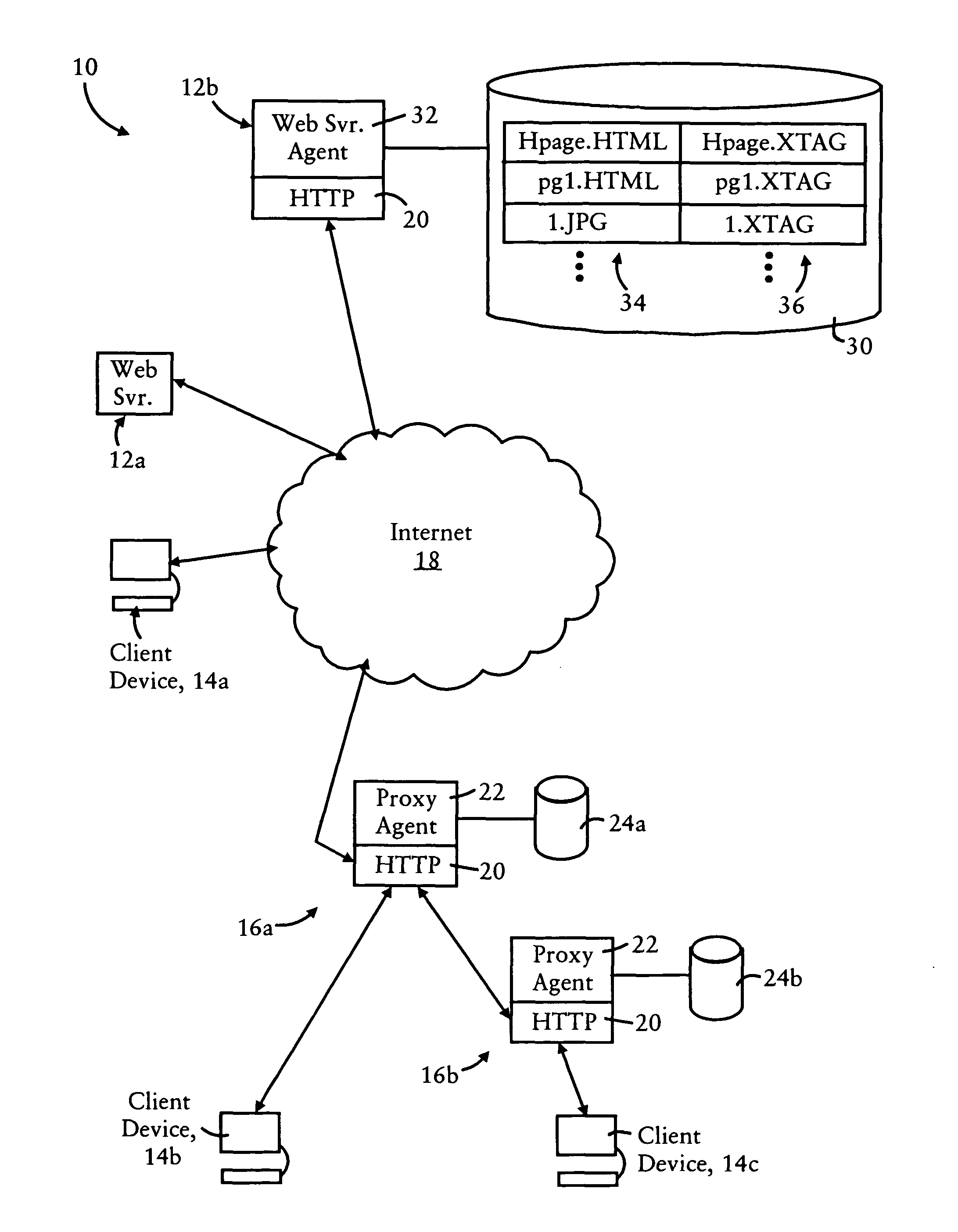
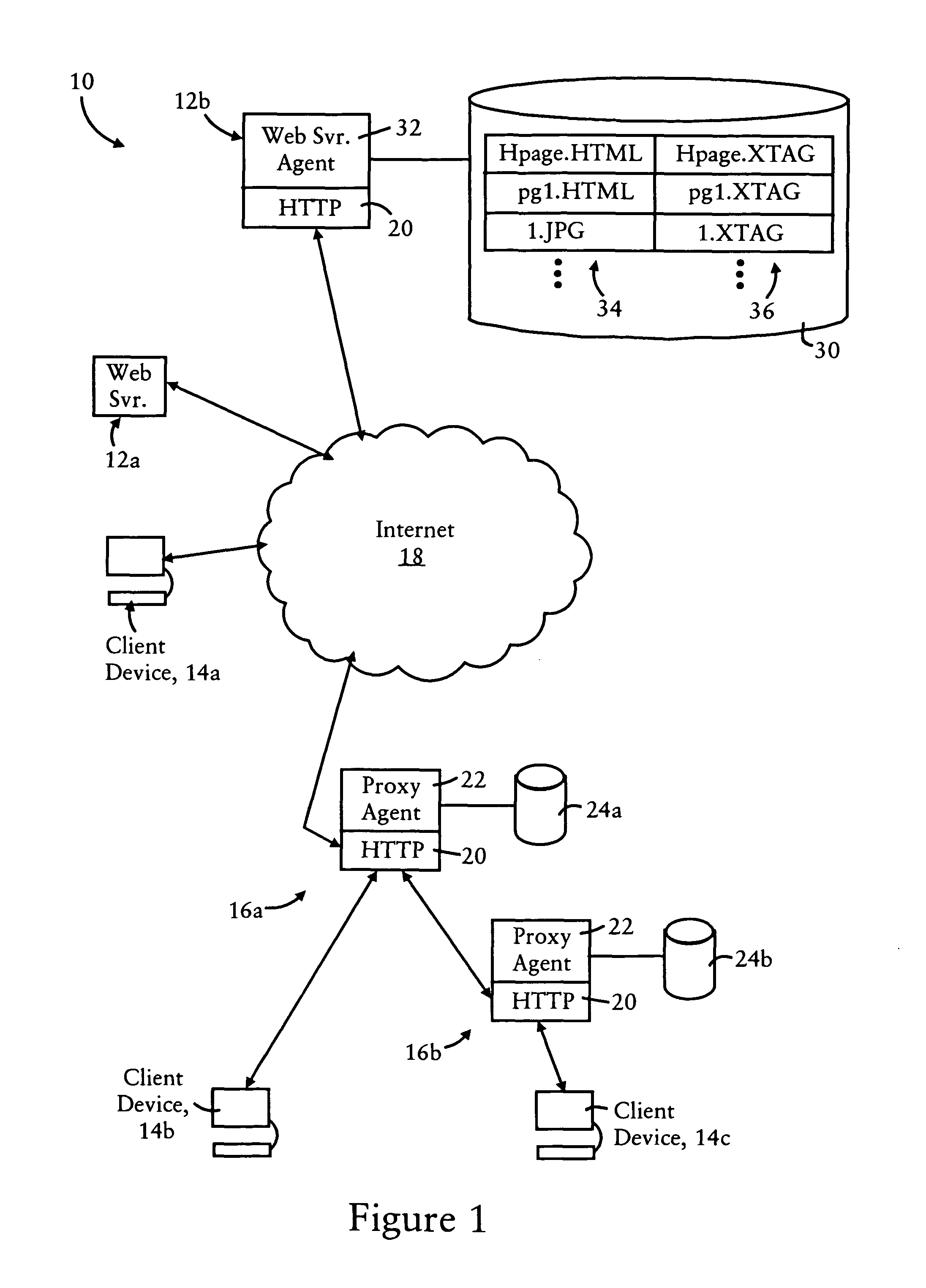
Predictive pre-download using normalized network object identifiers
InactiveUS6981017B1Shorten the timeBetter able to predictDigital data information retrievalMultiple digital computer combinationsInformation repositoryWeb service
The invention provides a method for predicting which network objects are likely to be requested by a web user from a web server, such as that used in conjunction with an internetworking environment. A request made by a web user for a web object is parsed and dynamic values contained therein normalized. A prediction is made based on the normalized request, statistical measures, and other factors about what other web objects the web user is likely to request. The predictive information is then made available to the web server and the predicted net objects are pre-downloaded to the Web client. A pre-download statistics server may be used to record and provide statistics to assist in the prediction process. Examples described herein relate to web pages, but the invention is broadly applicable to many different types of requests for information (such as, for example, database queries and other libraries of information.)
Owner:DIGITAL RIVER INC
Method and system for communication in the usenet
InactiveUS20010054084A1Shorten the timeAvoid downloadingMultiple digital computer combinationsSpecial data processing applicationsSystems designInternet information services
The present invention relates to Internet information services. In particular, the present invention relates to improvements related to and / or use of the Usenet. The present invention also has application to email systems, as well as other electronic distribution media. In one aspect, the present invention relates to the distribution, access and / or download speed of Web objects, and involves a new system design and method of use, providing a Usenet based alternative to the current Web caching and mirroring solutions. A second aspect of the present invention relates to a method that enables relatively transparent encoding within Web objects' URLs information necessary to locate the object in a Usenet server and retrieve it. The method also allows transparent retrieving of news cached objects from their original servers.
Owner:CSIRO DIV OF MATHEMATICAL & INFORMATION SCI +1
Apparatus and methods for concept-centric information extraction
InactiveUS20100241639A1Digital data information retrievalDigital data processing detailsTheoretical computer scienceA domain
Disclosed are methods and apparatus for extracting (or annotating) structured information from web content. Web content of interest from a particular domain is represented as one or more tree instances having a plurality of branching nodes that each correspond to a web object such that the tree instances correspond to one or more structured data instances. The particular domain is associated with domain knowledge that includes one or more presentation rulesets that each specifies a particular structure for a set of data instances, a domain-specific concept labeler, one or more specified properties of the web objects in the tree instances, and a concept schema that specifies a representation of the data to be extracted from the web content. A structured data instance that conforms to the concept schema is extracted from the one or more tree instances based on the domain knowledge for the particular domain. Extraction of the structured data instances is accomplished by (i) using the domain-specific concept labeler to annotate a subset of nodes of the tree instances; and (ii) using a locally adaptive concept annotator to extract the structured data instances based on the annotated segments and the local properties associated with such annotated segments. The extracted structured data instance is stored as structured output records in a database.
Owner:OATH INC
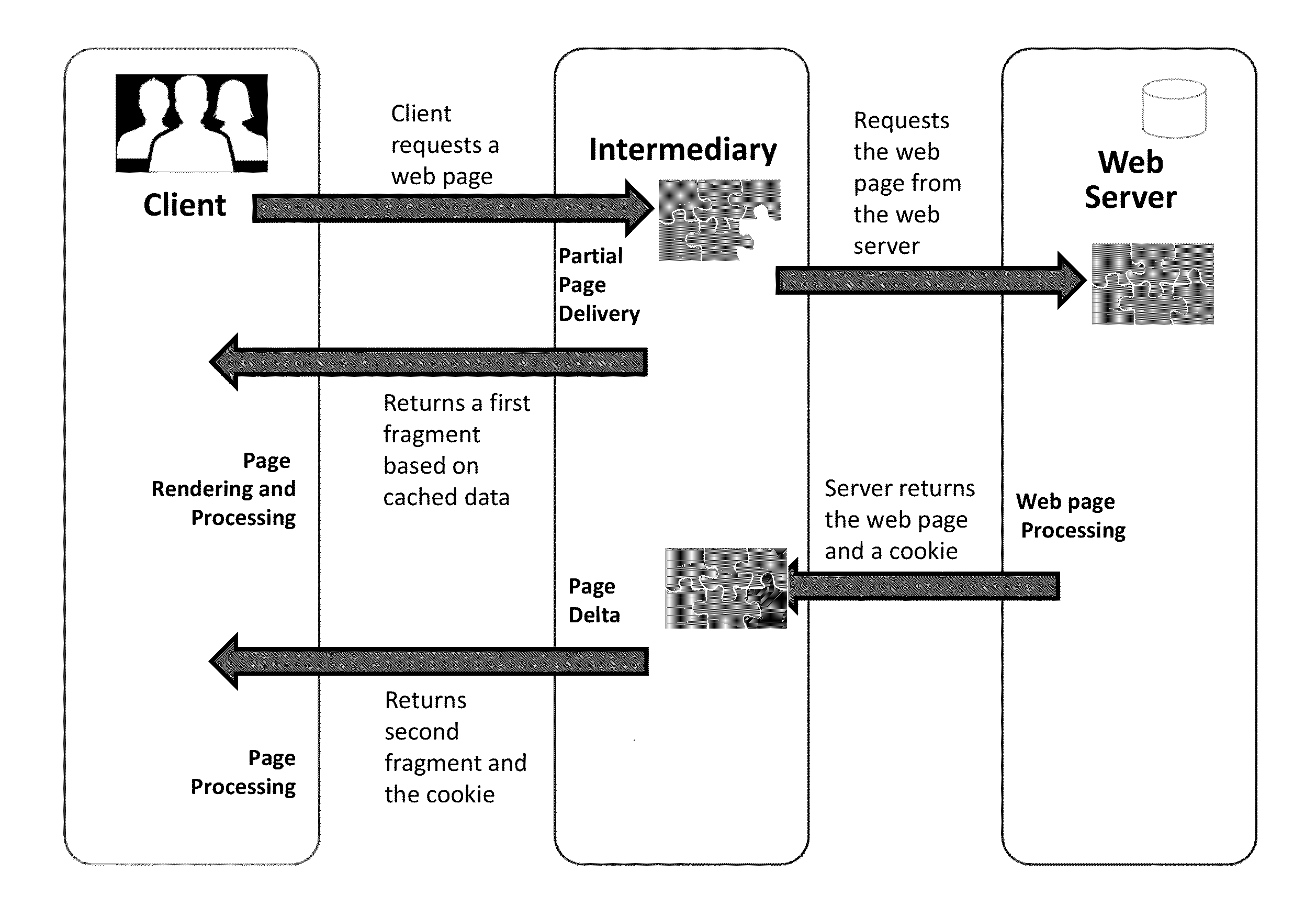
Systems and methods for managing loading priority or sequencing of fragmants of a web object
ActiveUS20150088968A1Improve page loading performanceImprove user experienceInterprogram communicationNatural language data processingClient-sideWeb object
This disclosure is directed to methods and systems for delivering an item of web content requested by a client. An intermediary between a client and a server may intercept a request from the client to the server for an item of web content. The intermediary may split the item of web content into a plurality of fragments. The intermediary may identify, responsive to the request, a first fragment of the plurality of fragments to transmit to the client. The intermediary may inject executable code into the first fragment of the plurality of fragments. The executable code may be configured to conditionally incorporate additional fragments from the plurality of fragments into the first fragment at the client.
Owner:YOTTAA
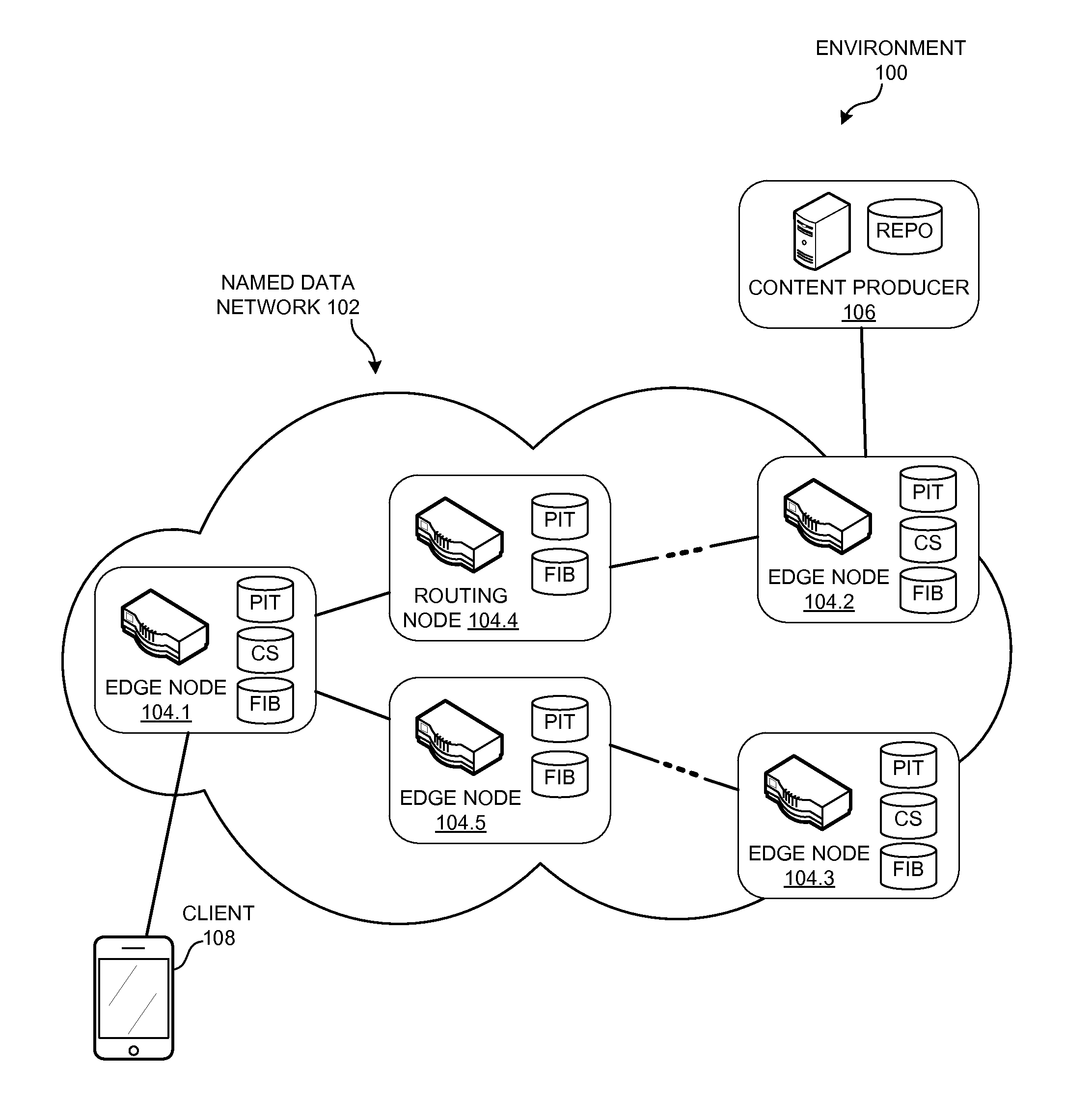
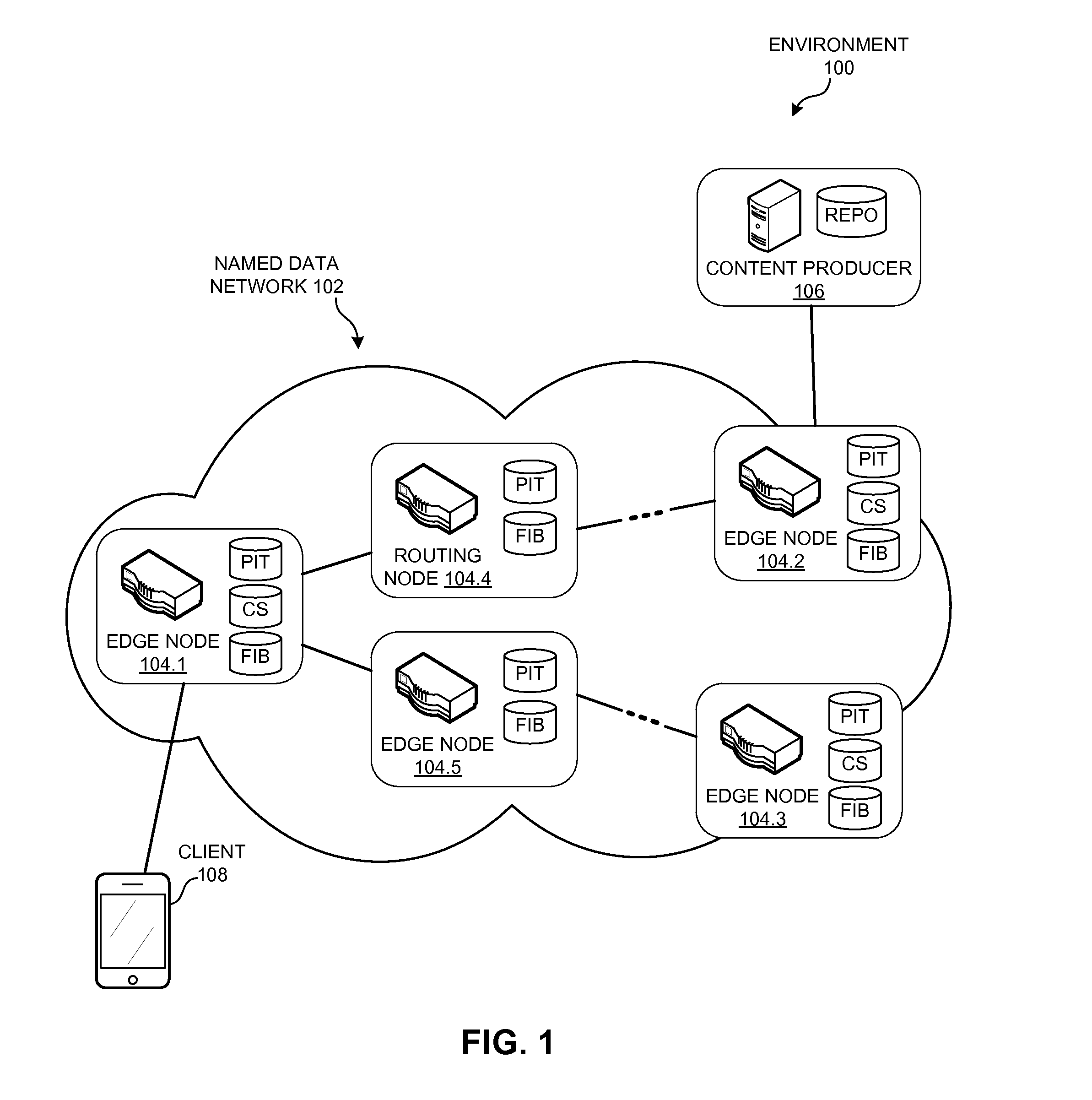
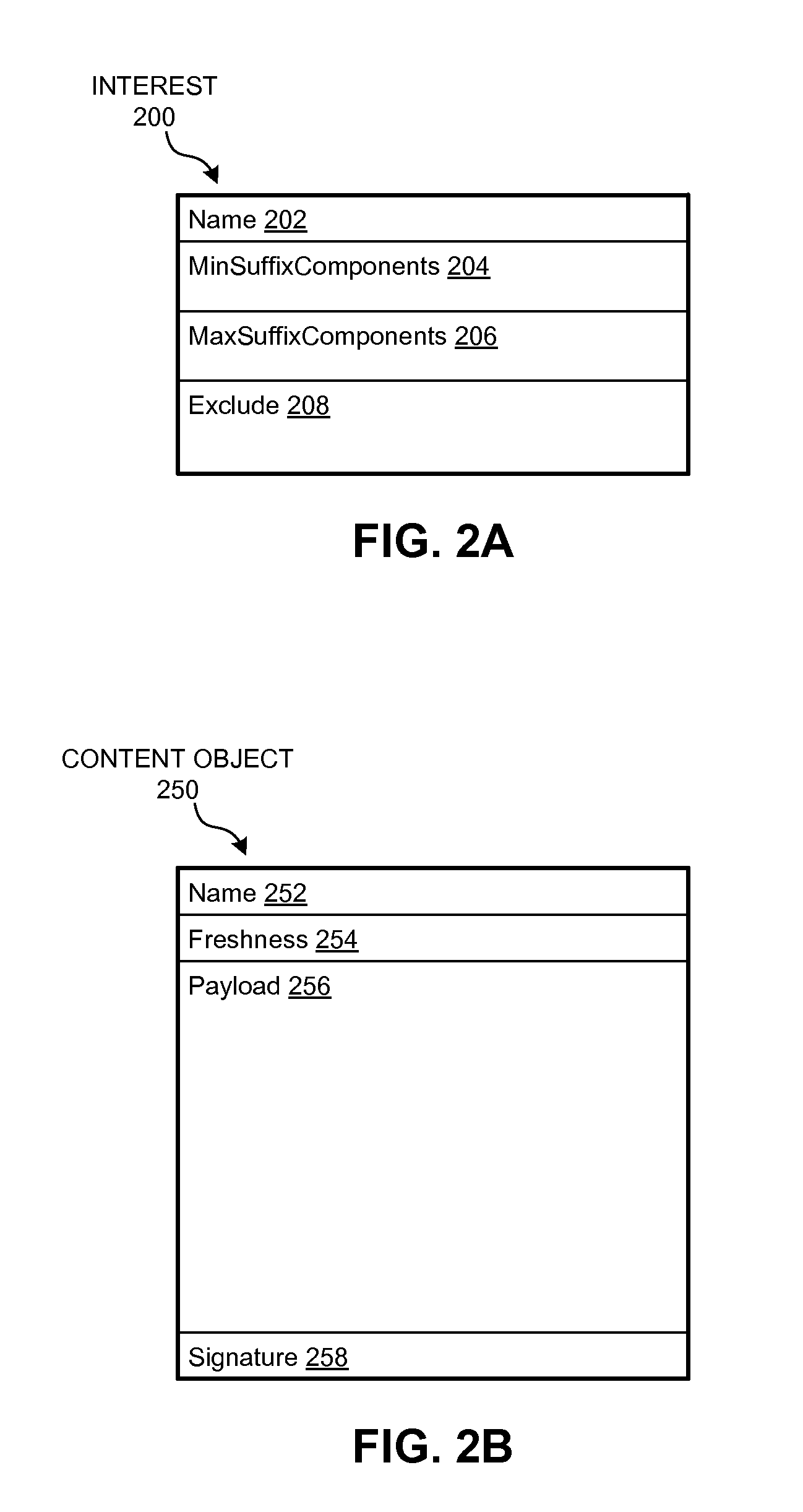
System and method for ranking named-data networking objects in a cache
A router can select a cached Content Object to rank, and analyzes historical usage information for the Content Object to determine a set of exclusions received for the Content Object. The router then computes a rank value for the Content Object, based on the set of exclusions for the Content Object and one or more predetermined exclusion patterns, and stores the rank value in association with the Content Object. When the router receives an Interest whose name is associated with multiple cached Content Objects, the router selects, from the multiple cached Content Objects, a cached Content Object with a highest rank value. The router can return the selected cached Content Object to satisfy the Interest.
Owner:CISCO TECH INC
Memory admission control based on object size or request frequency
InactiveUS7051161B2Improved memory operationImprove operationDigital data information retrievalSpecial data processing applicationsObject basedParallel computing
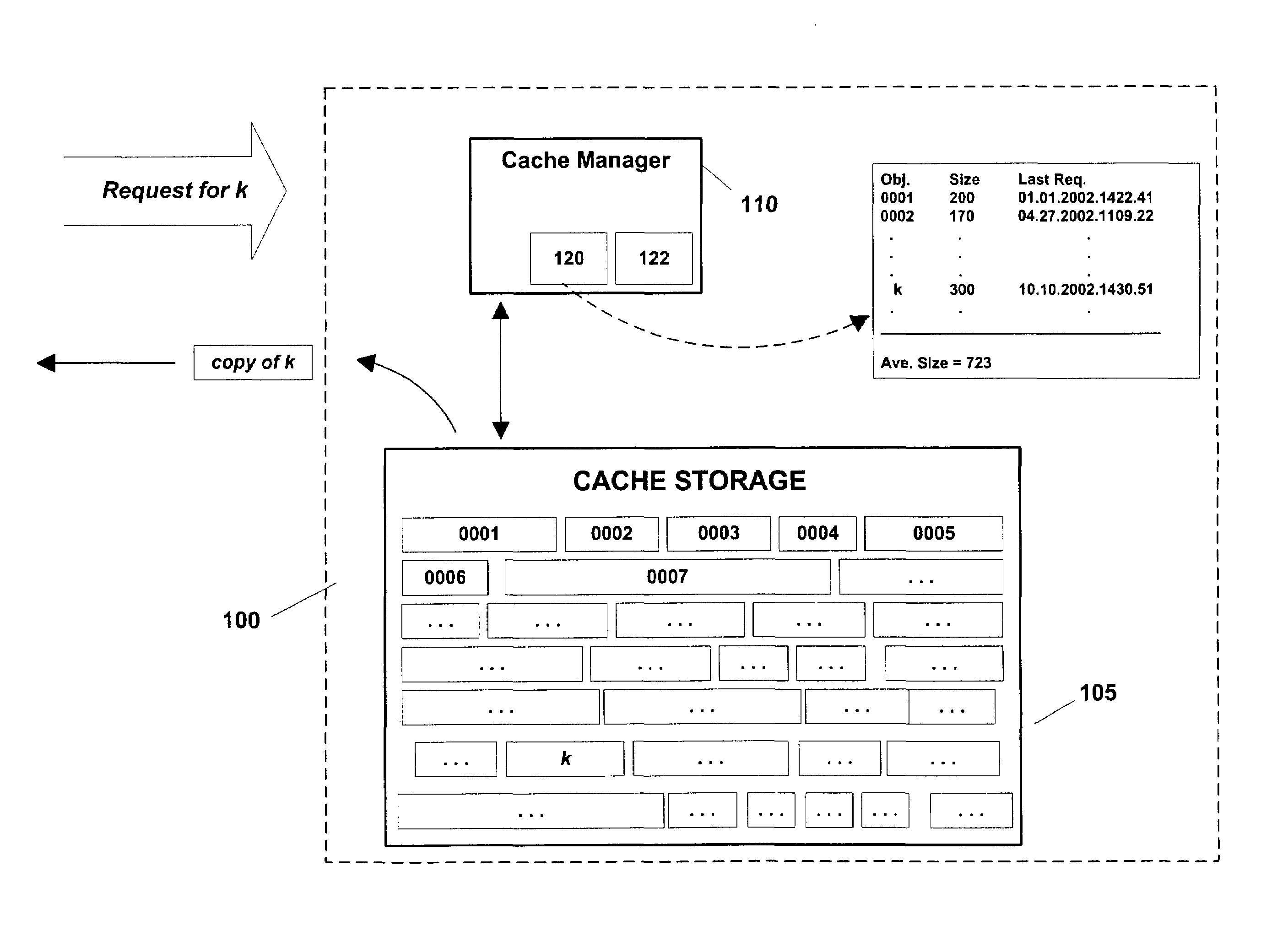
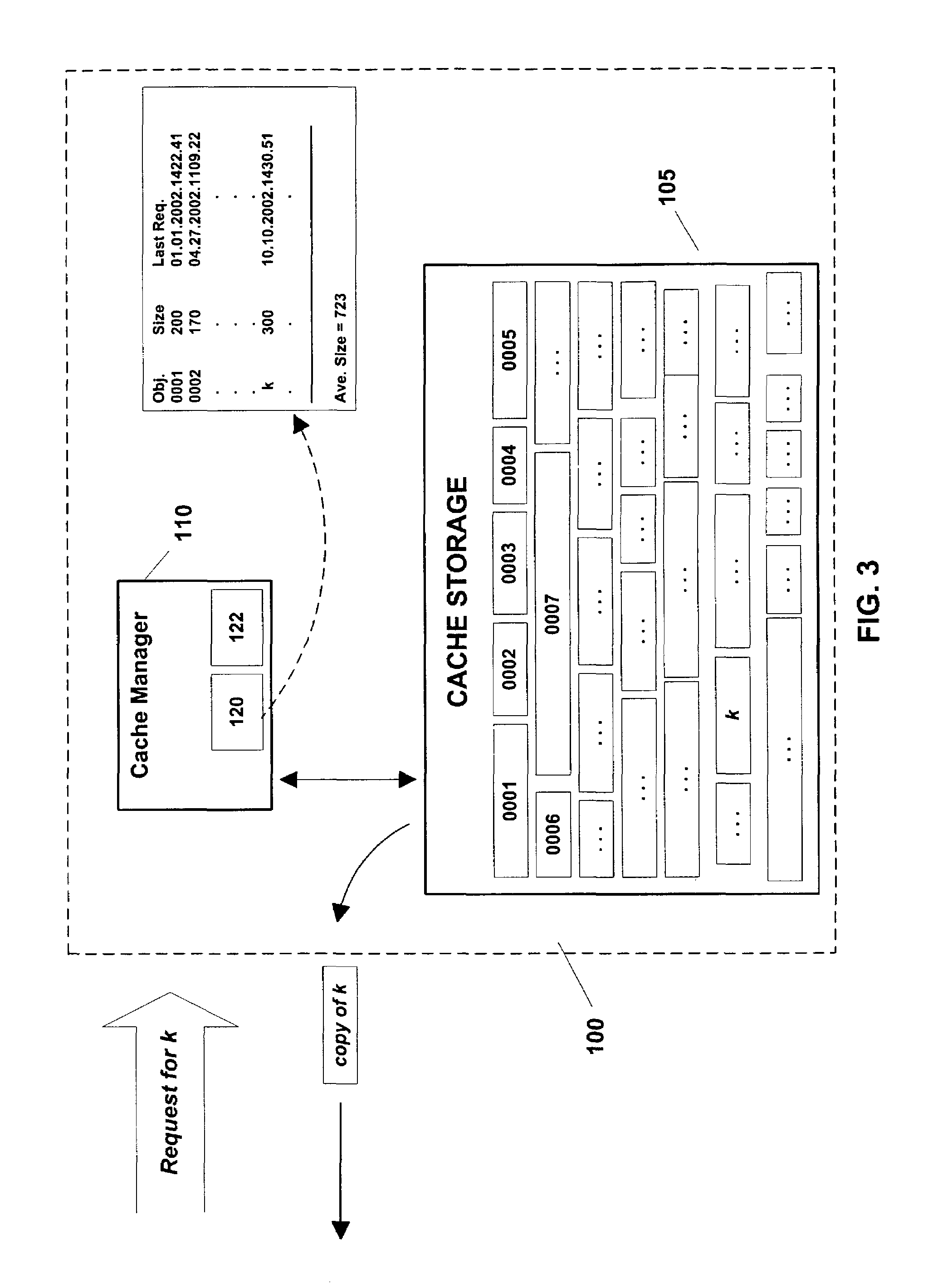
Admission of new objects into a memory such as a web cache is selectively controlled. If an object is not in the cache, but has been requested a specified number of prior occasions (e.g., if the object has been requested at least once before), it is admitted into the cache regardless of size. If the object has not previously been requested the specified number of times, the object is admitted into the cache if the object satisfies a specified size criterion (e.g., if it is smaller than the average size of objects currently stored in the cache). To make room for new objects, other objects are evicted from the cache on, e.g., a Least Recently Used (LRU) basis. The invention could be implemented on existing web caches, on distributed web caches, in client-side web caching, and in contexts unrelated to web object caching.
Owner:III HLDG 3
Mechanisms for web-object event/state-driven communication between networked devices
InactiveUS6829630B1Efficient assemblySimplify creationMultiple digital computer combinationsData switching networksProcedural programmingApplication software
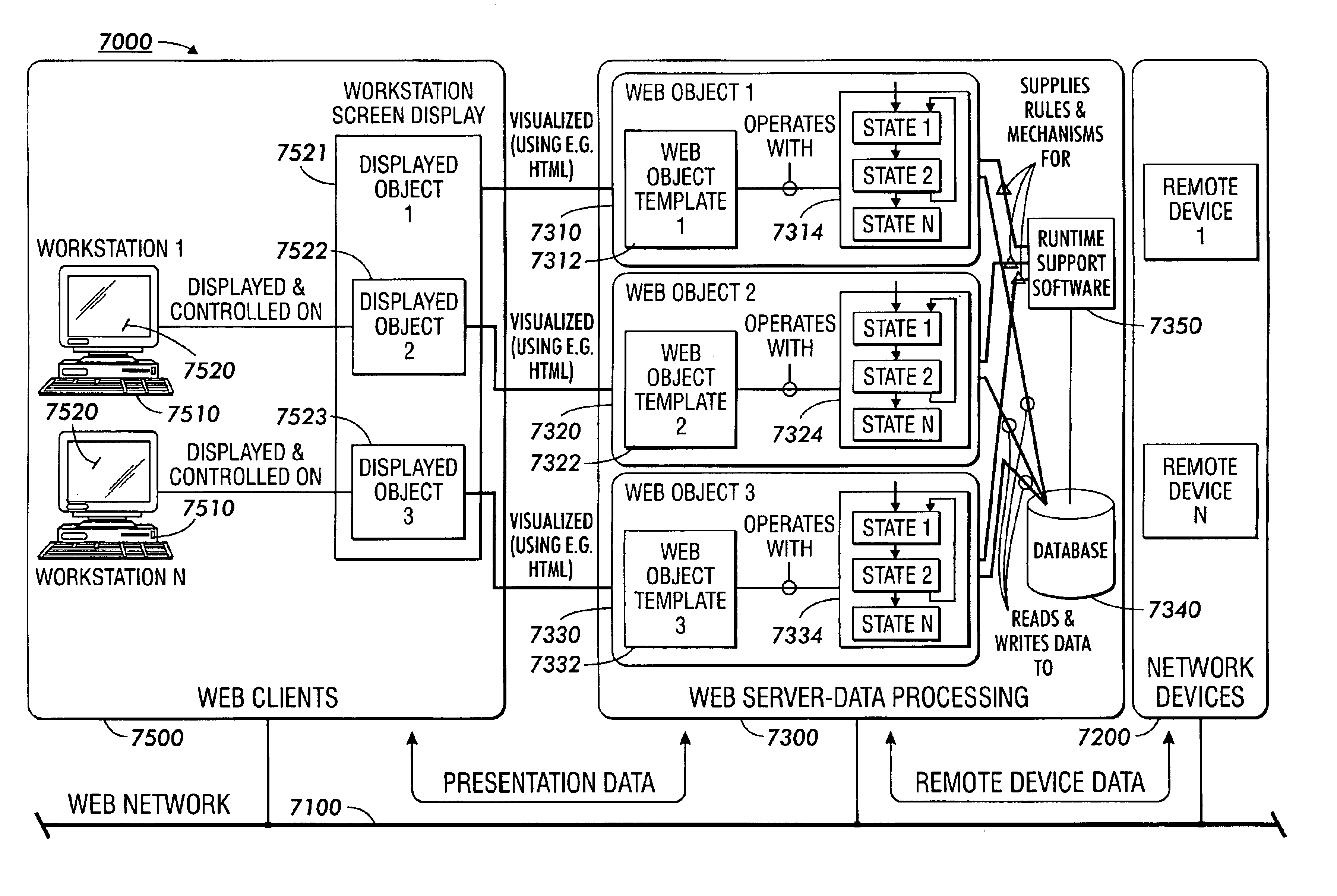
Web-based event / state-driven mechanisms and methods for simplifying communication between networked multifunction devices, such as copiers, printers, facsimile machines and multifunction devices using a networked database for the creation and presentation of device metrics and status data. Web-based multifunction performance metrics and calculations themselves are created within concurrent (multiple instances) of Web objects, wherein a Web object is a self-contained entity with data and a state machine lifecycle. State changes inside and outside the Web object are made by sending events to event queues and routing them to other state machines within other Web objects or instances of the same Web object. Data and events between Web objects are formed into a regular event syntax providing a simpler method of communication than those of procedural programming approaches. The arguments of the events are processed by specific instances of state machines that compose each Web object to perform an appropriate action. The metrics displays and corresponding calculations within the Web object's state machine are highly self-contained and concurrent, hiding networked database contention and database locking, and enforcing atomicity with it's runtime software. Calculations are performed and displayed from within a very small context within each Web object's state minimizing external communications and further simplifying software application development efforts.
Owner:MAJANDRO LLC
Creation and Revision of Network Object Graph Topology for a Network Performance Management System
InactiveUS20110320394A1Digital data information retrievalDigital data processing detailsManagement systemObject graph
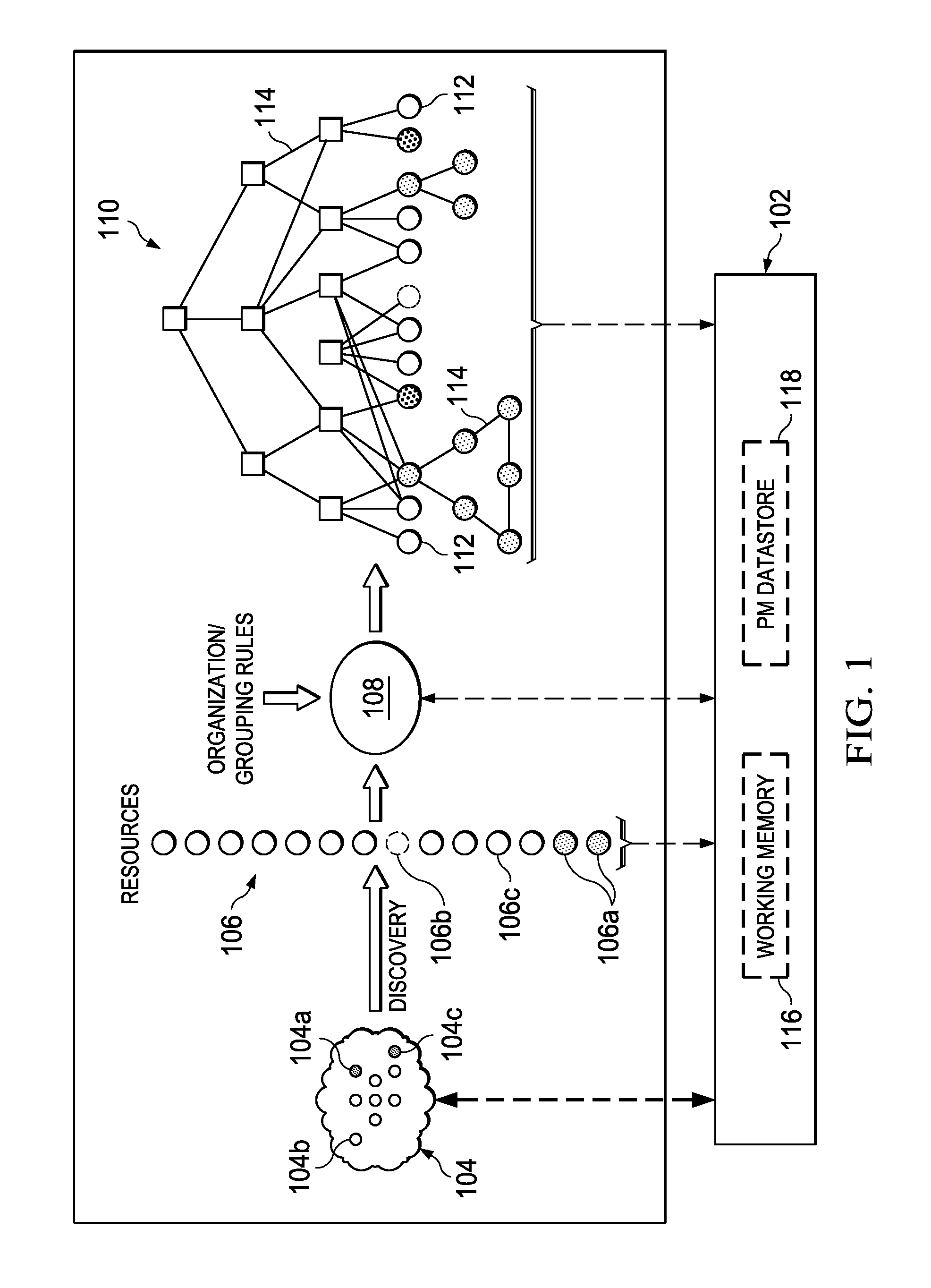
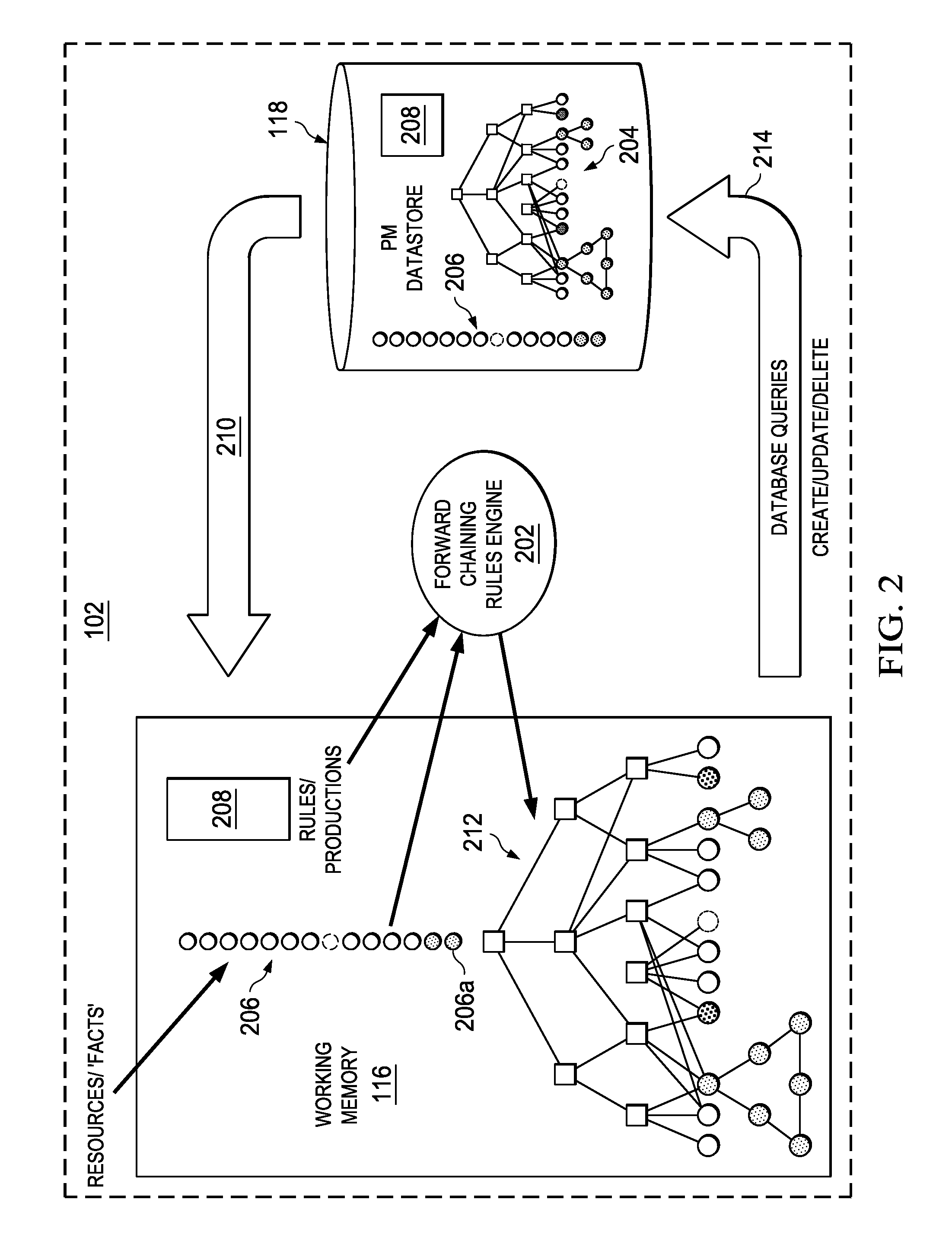
An embodiment of the invention comprises, providing an initial object graph to a database, the initial object graph being generated by applying a set of rules to resources included in a resource set at a specified time, or by revising a previous object graph at the previous time, the resource set at the specified time comprising an initial resource set. The method includes providing the initial object graph to a working memory, maintained in separation from the database; discovering a changed fact associated with one of the resources of the initial resource set; and upon discovering the changed fact, determining modifications required by the changed fact to the initial object graph. If modifications are required, the initial object graph is revised in the working memory to include such modifications. The same revisions are then made to the initial object graph in the system database.
Owner:IBM CORP
DNS prefetch
InactiveUS20100146415A1Reducing round tripTransparent to userDigital data information retrievalMultiple digital computer combinationsIp addressNetwork packet
The disclosure relates to systems, apparatus, and methods of reducing round trips associated with DNS lookups in ways that are substantially transparent to the user. Embodiments implement prefetching of DNS entries, sometimes piggybacking on the prefetching of associated web objects. In one embodiment, prefetching of an object continues according to other prefetching techniques, until the point where the HTML response may be parsed. When an embedded object request is identified, a DNS lookup is performed, and the resulting IP address is pushed to the client as part of a prefetch data package. In some embodiments, the client strips off the relevant portion of the prefetch data package to create a local DNS entry. The DNS entry may be used to locally handle DNS requests by the client, thereby potentially avoiding a round trip to a remote DNS.
Owner:VIASAT INC
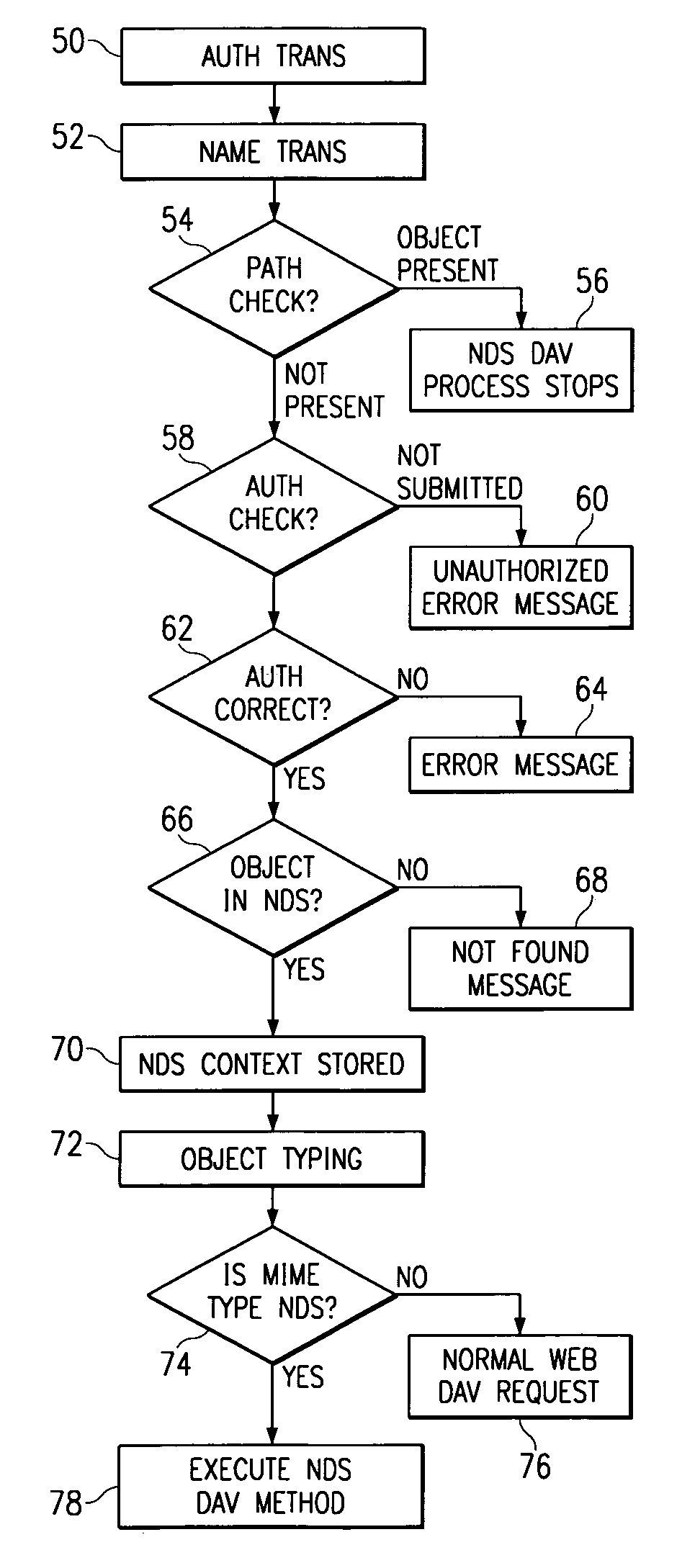
Method and apparatus for exposing network administration stored in a directory using HTTP/WebDAV protocol
InactiveUS6947991B1Efficient administrationReduce workloadData processing applicationsMultiple digital computer combinationsDrag and dropPassword
A method and system to manipulate network objects by using Internet authoring, collaboration and versioning tools is described. The method includes: receiving a request for a manipulation of a first network object from a requesting user; verifying a first set of authorization information; translating a logical address of the first network object to a physical file system path; checking a local file system for validity and authorization for the requesting user including determining whether the first network object is a first network object; verifying a username and a password for the requesting user; returning a first error message if requesting user is unauthorized to access the first network object; determining an object type for the first network object; and sending a response to the requesting user. The method can also include verifying that the first network object is found and returning a second error message if the first network object is not found. The first network object can be user object and the request can be to assign new rights to the user object. The new rights for the user can also be for another network object. The new rights can be assigned by dragging and dropping the user object on another network object by the use of interactive computer screen.
Owner:APPLE INC
Pre-fetch communication systems and methods
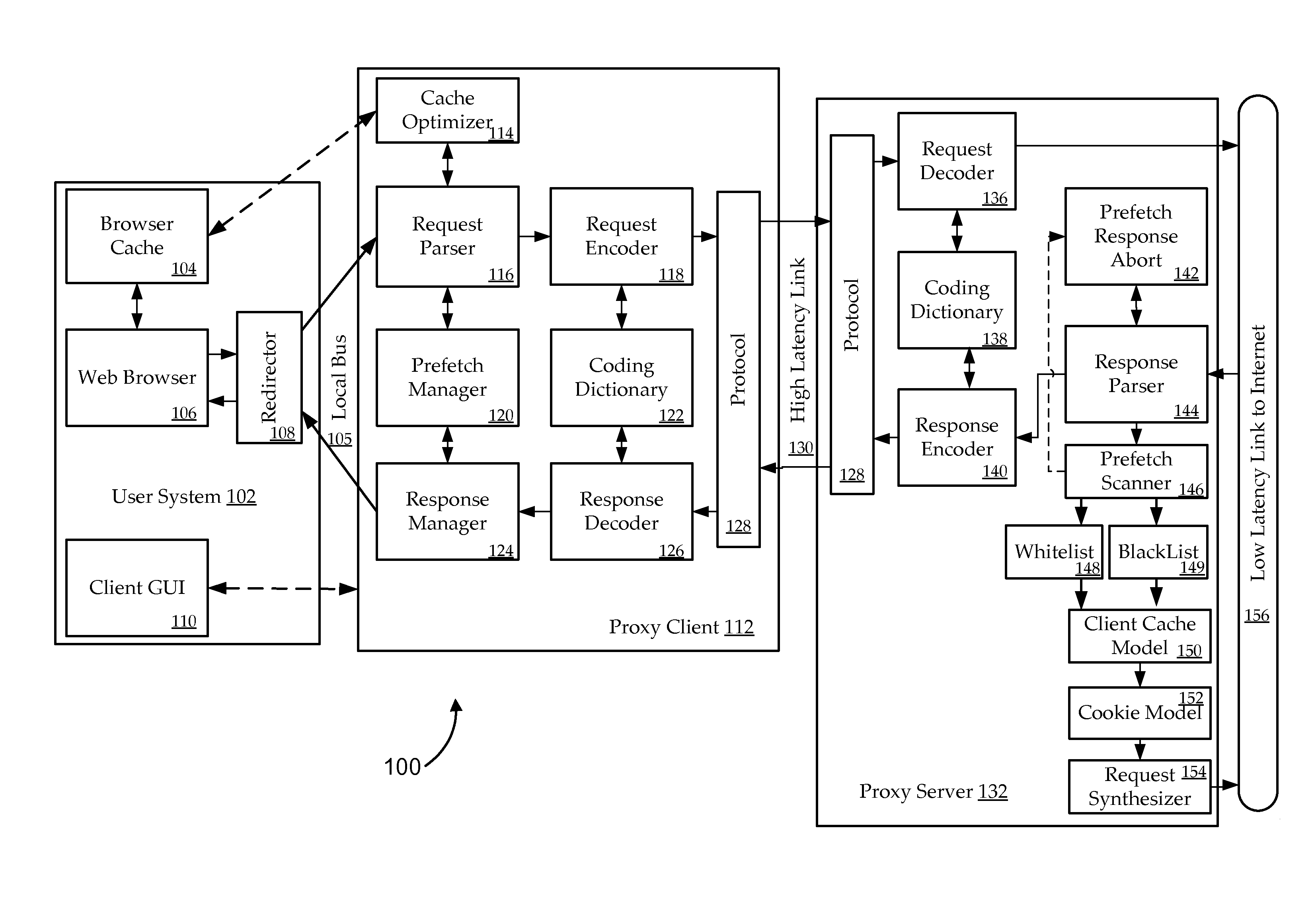
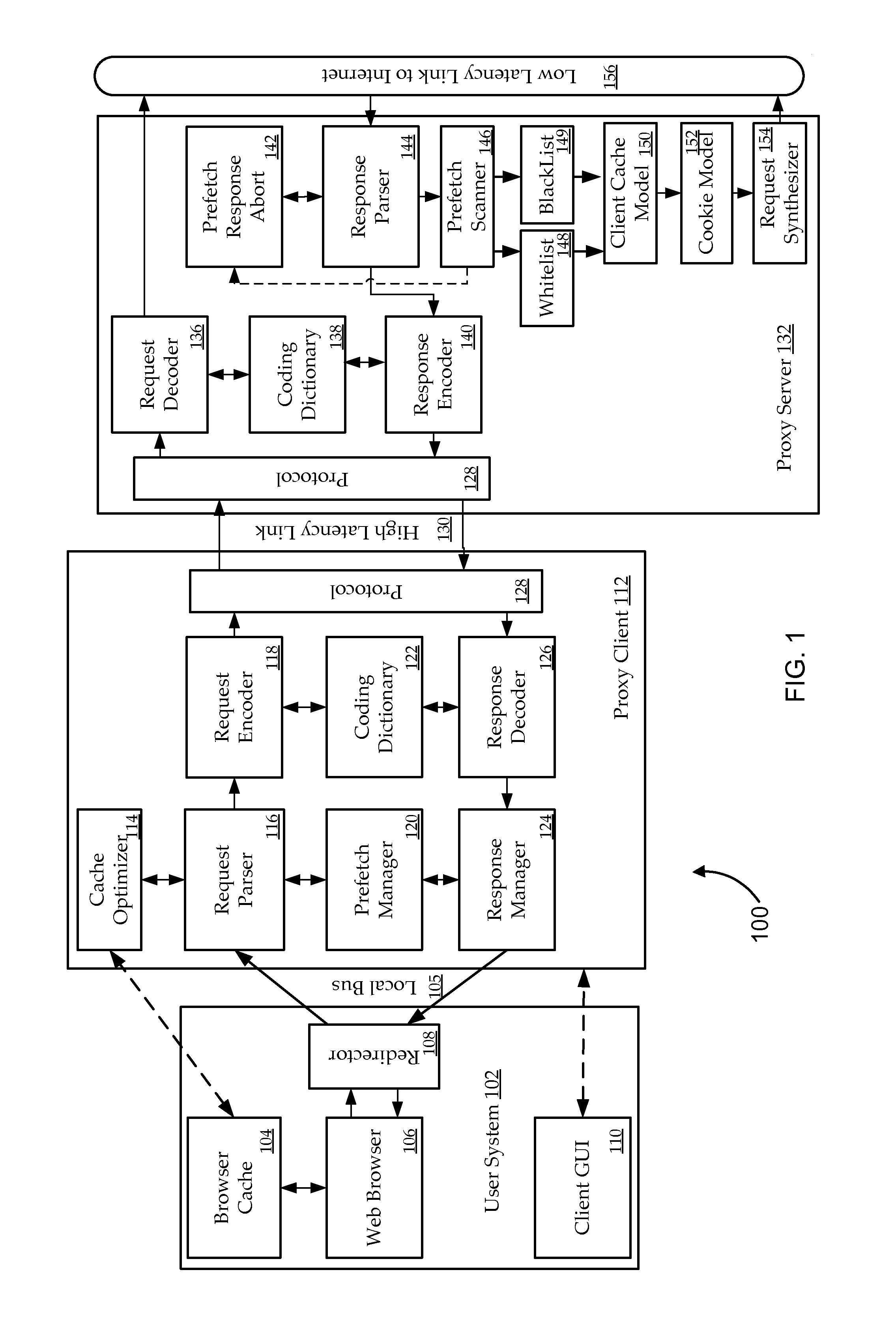
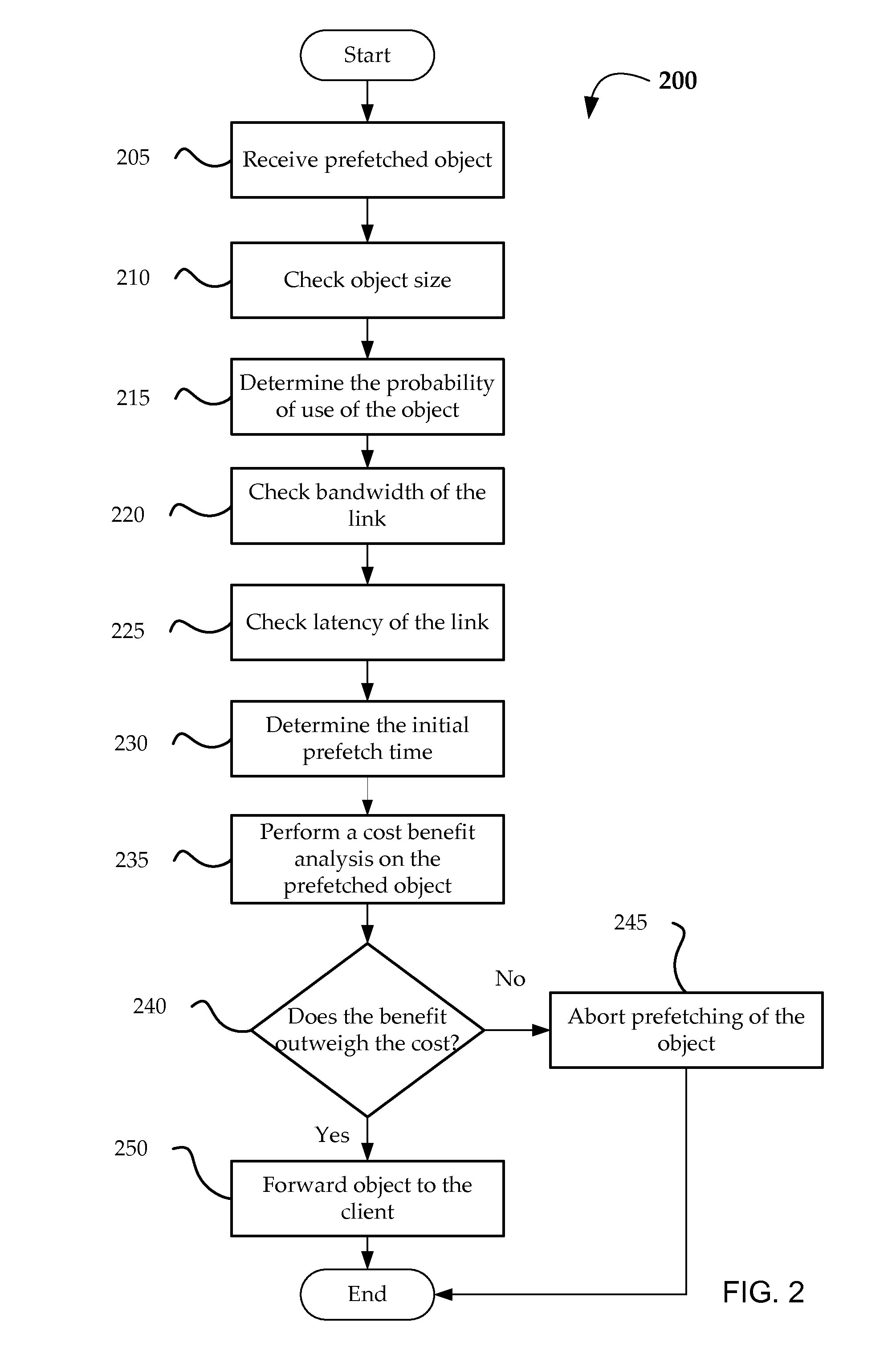
ActiveUS7359395B2Increase speedImprove efficiencyData switching by path configurationMultiple digital computer combinationsLong latencyCommunications system
The present invention relates to telecommunications devices, systems and methods for providing improved performance over long latency communications links. Some embodiments selectively pre-fetch and transmit information over the link using improved protocol and pre-fetch mechanisms. One system includes a first gateway (430) adapted to communicate with a client (410), the first gateway including a processor coupled to a storage medium. The storage medium includes code for receiving a request for retrieving a web object, code for forwarding the request to a second gateway (440) over the long latency link, and code for receiving a pre-fetch announcement and response data for the web object from the second gateway. The pre-fetch announcement is received prior to receiving the response data.
Owner:CA TECH INC
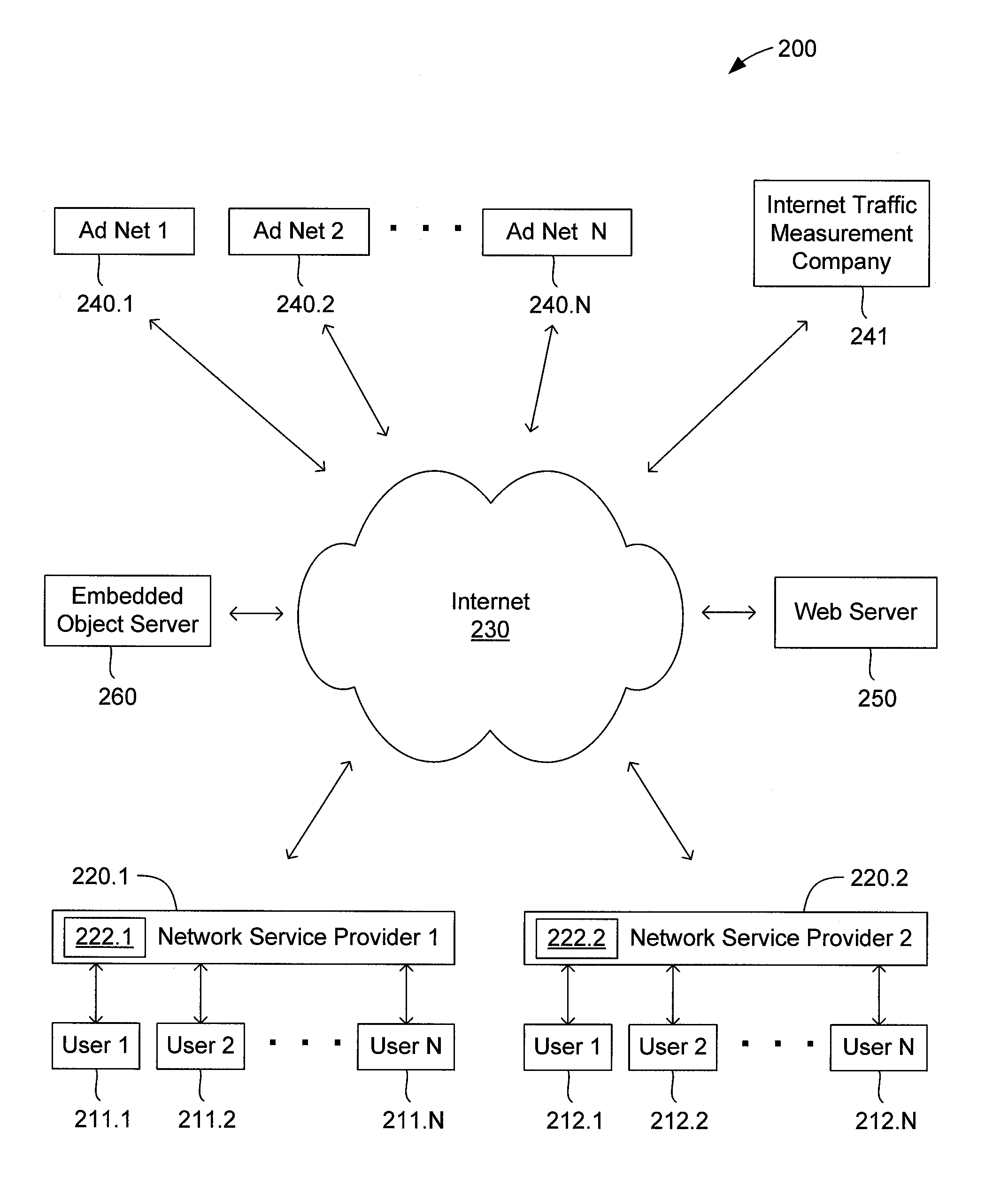
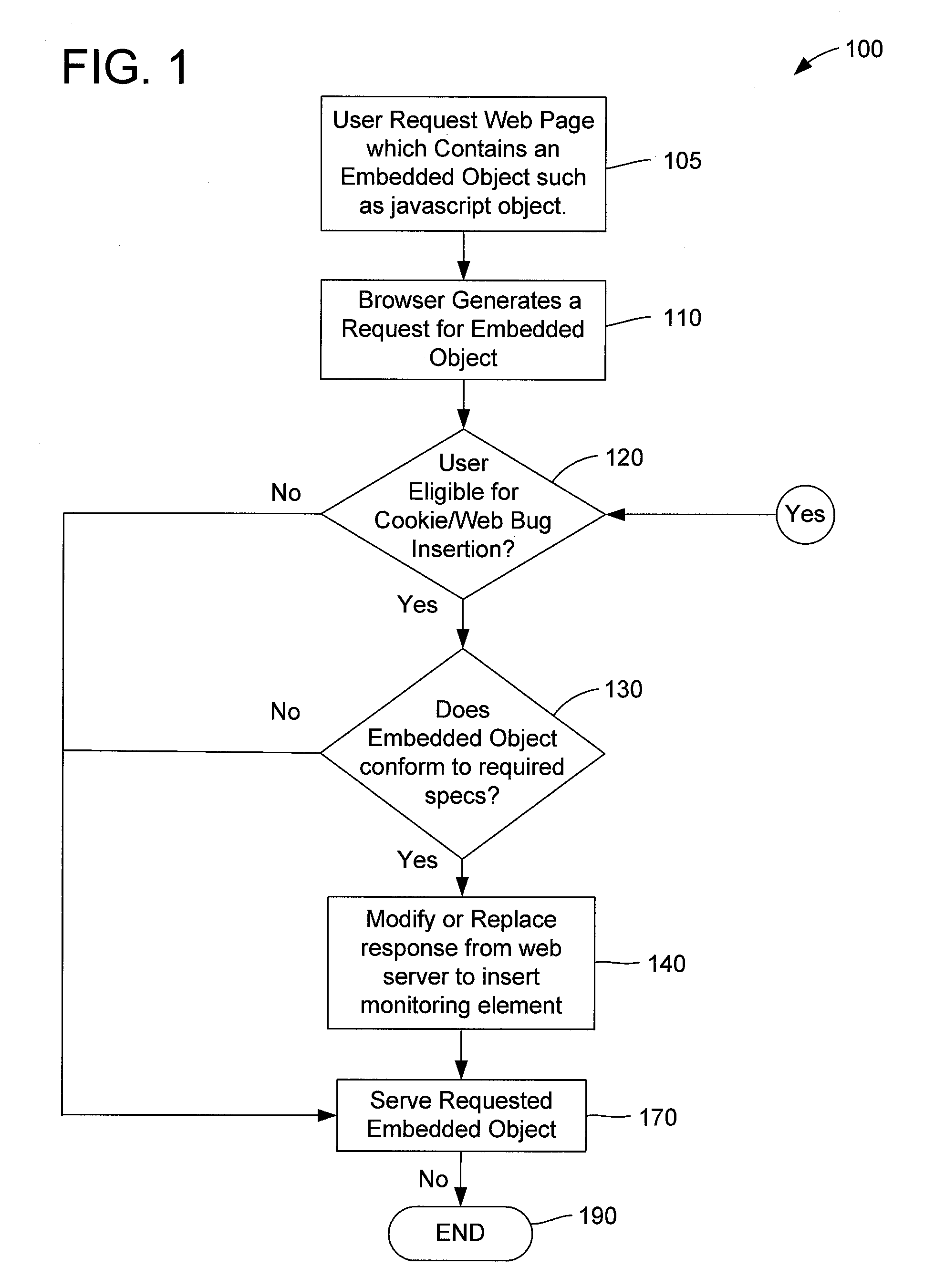
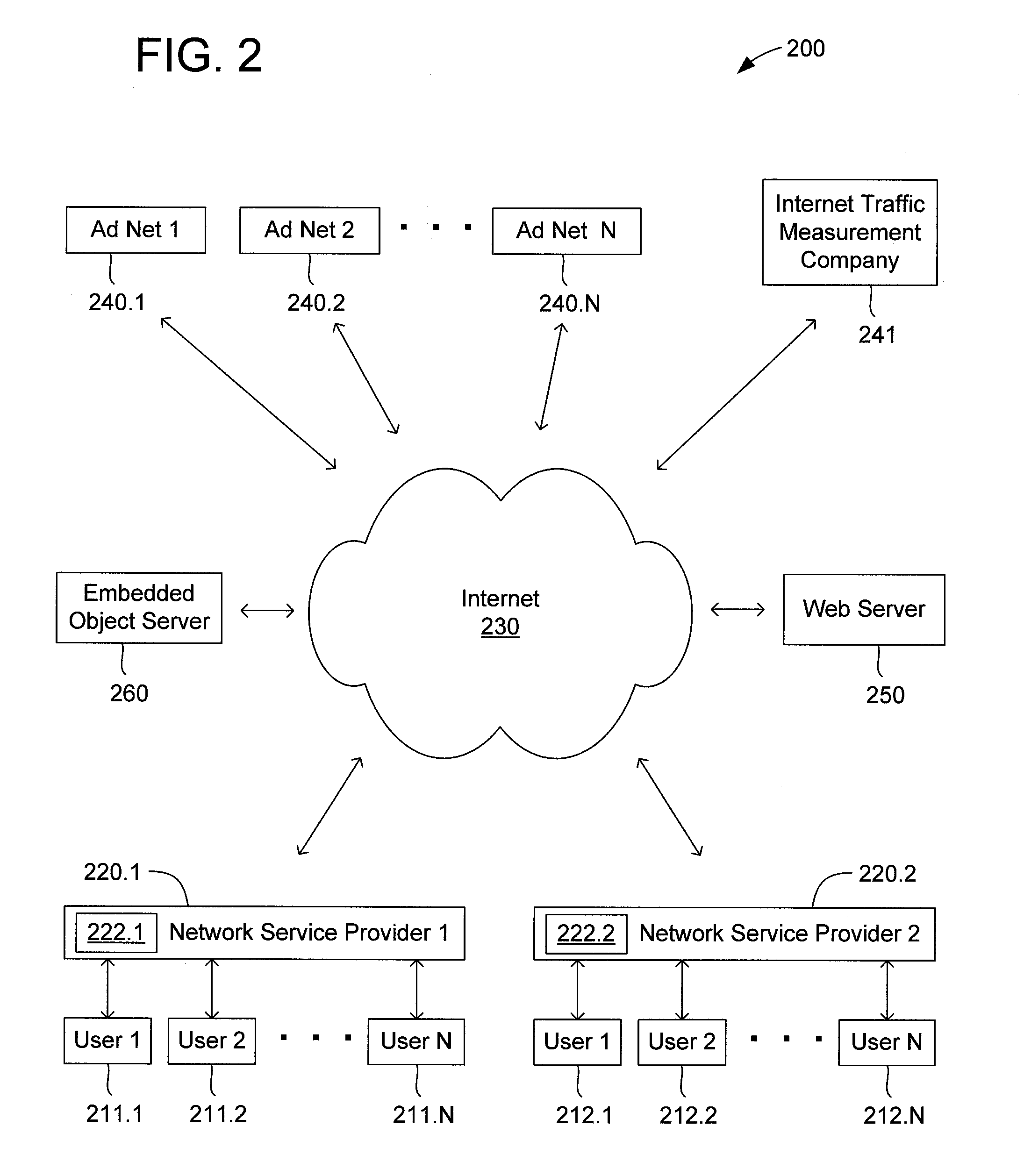
Method and apparatus for internet traffic monitoring by third parties using monitoring implements transmitted via piggybacking HTTP transactions
Disclosed is an internet traffic monitoring method that includes a network service provider analyzing an HTTP transaction involving an internet user client. The network service provider responds to the HTTP transaction by forwarding, to the internet user client, a modified web object including a monitoring implement. After forwarding the modified web object to the internet user client, the network service provider forwards a web object, originally associated with the HTTP transaction, to the internet user client.
Owner:FRONT PORCH
Systems and methods for managing loading priority or sequencing of fragments of a web object
InactiveUS20150088970A1Improve page loading performanceImprove user experienceInterprogram communicationNatural language data processingUnique identifierClient-side
This disclosure is directed to methods and systems for managing delivery and rendering of an item of web content. An intermediary between a client and a server may intercept a request from the client to the server for an item of web content. The intermediary may split the item of web content into a first fragment and a plurality of fragments. The intermediary may inject, into the first fragment for delivery to the client, executable code and a plurality of unique identifiers corresponding to the plurality of fragments. The intermediary may send the first fragment to the client. The injected executable code may generate a request at the client to the server for a second fragment from the plurality of fragments responsive to detecting an event. The intermediary may intercept the request for the second fragment, and may send the second fragment to the client responsive to the request.
Owner:YOTTAA
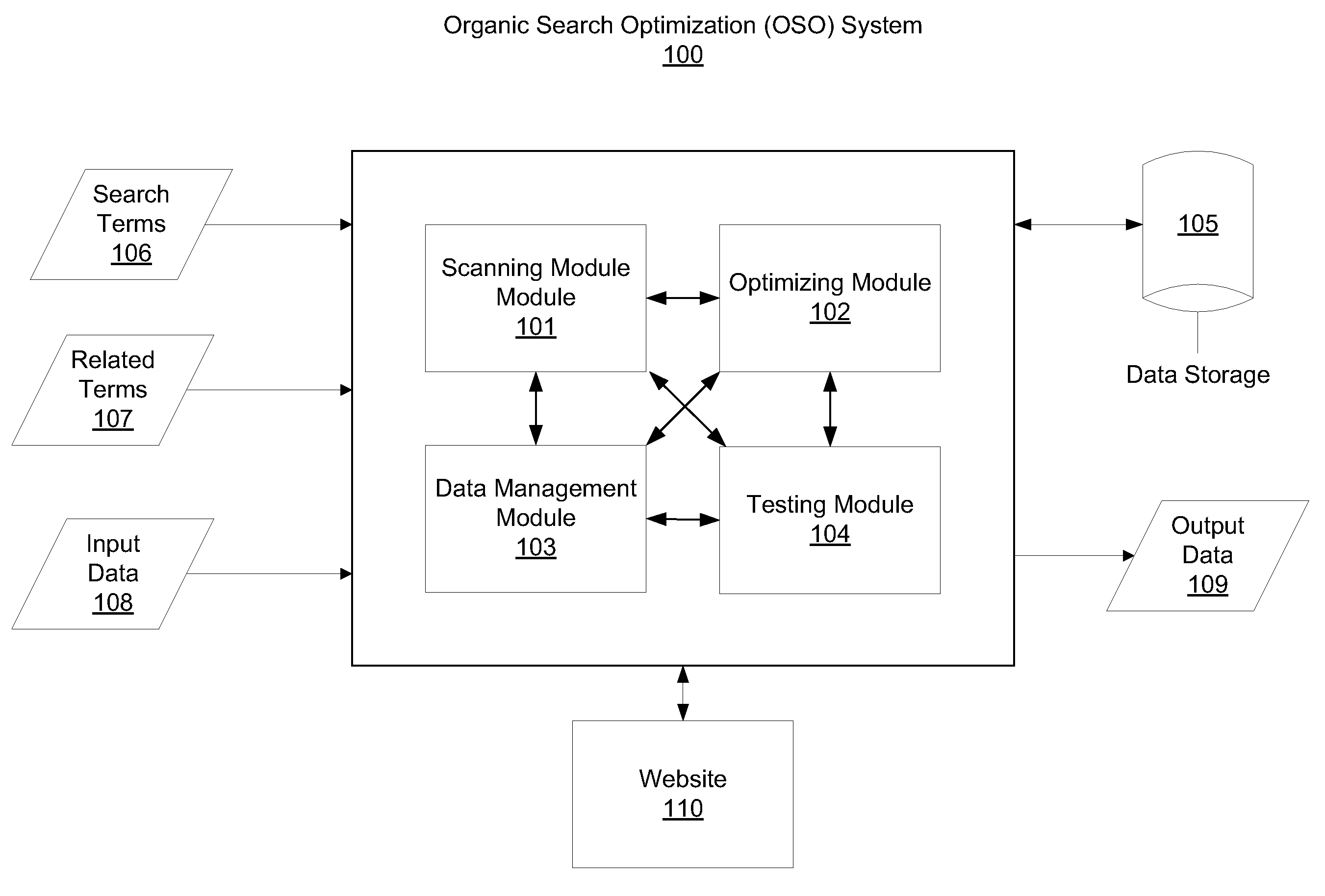
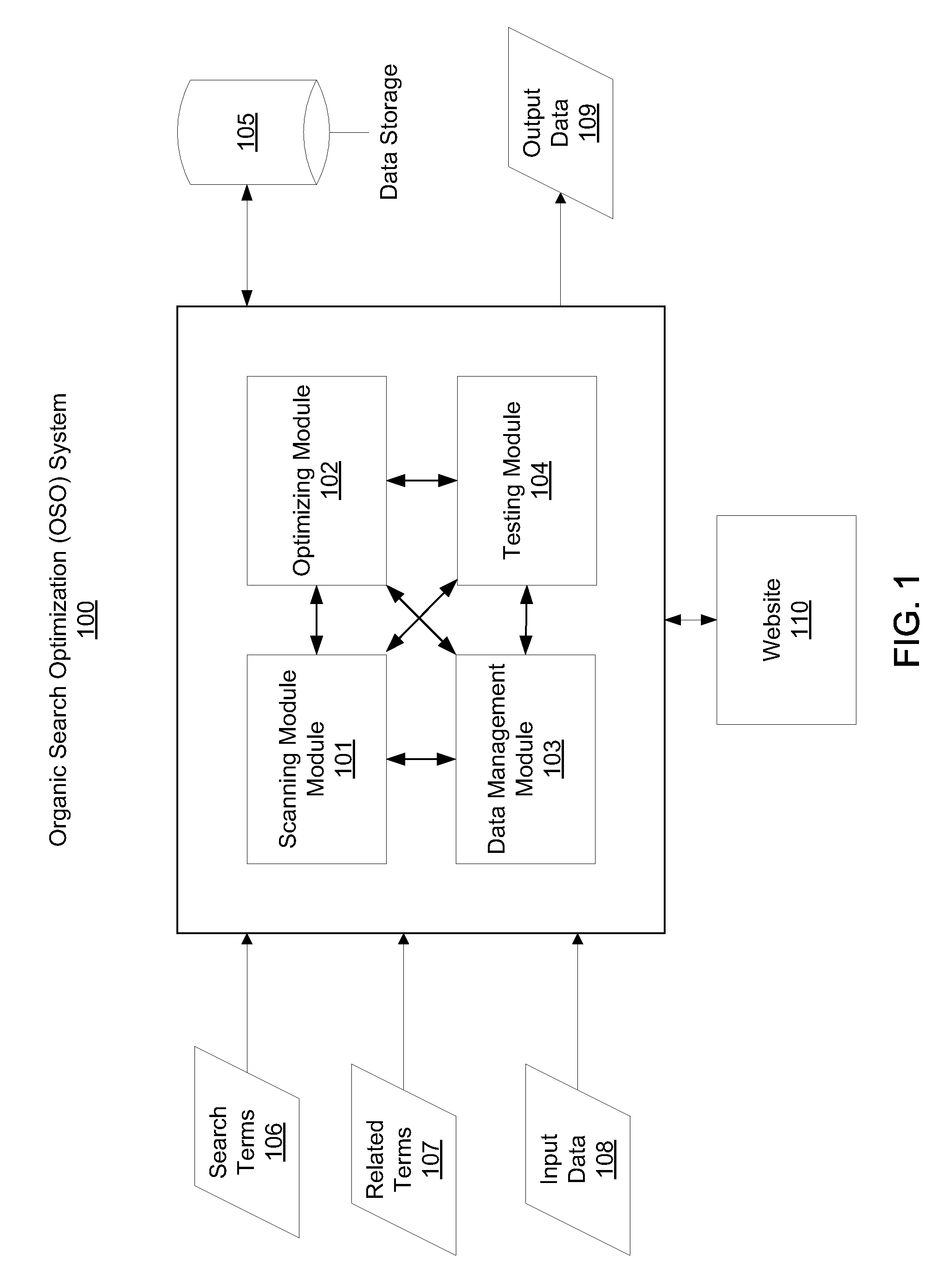
System to modify websites for organic search optimization
A system is configured to modify a website to optimize the website for an organic search of a topic. The system includes a data management module configured to receive search terms for the topic, receive related terms to the search terms for the topic, and receive website input data. The system also includes a scanning module configured to scan and index web pages and web objects in the website and identify a subset of web pages and web objects associated with the search terms and the related terms. The system also includes an optimizing module configured to process the subset of web pages and web objects from the website by prioritizing the subset of web pages and web objects or measuring a metric with respect to the subset of web pages and web objects. The search terms and related terms are deployed into the subset of web pages and web objects on the website based on the processing.
Owner:ACCENTURE GLOBAL SERVICES LTD
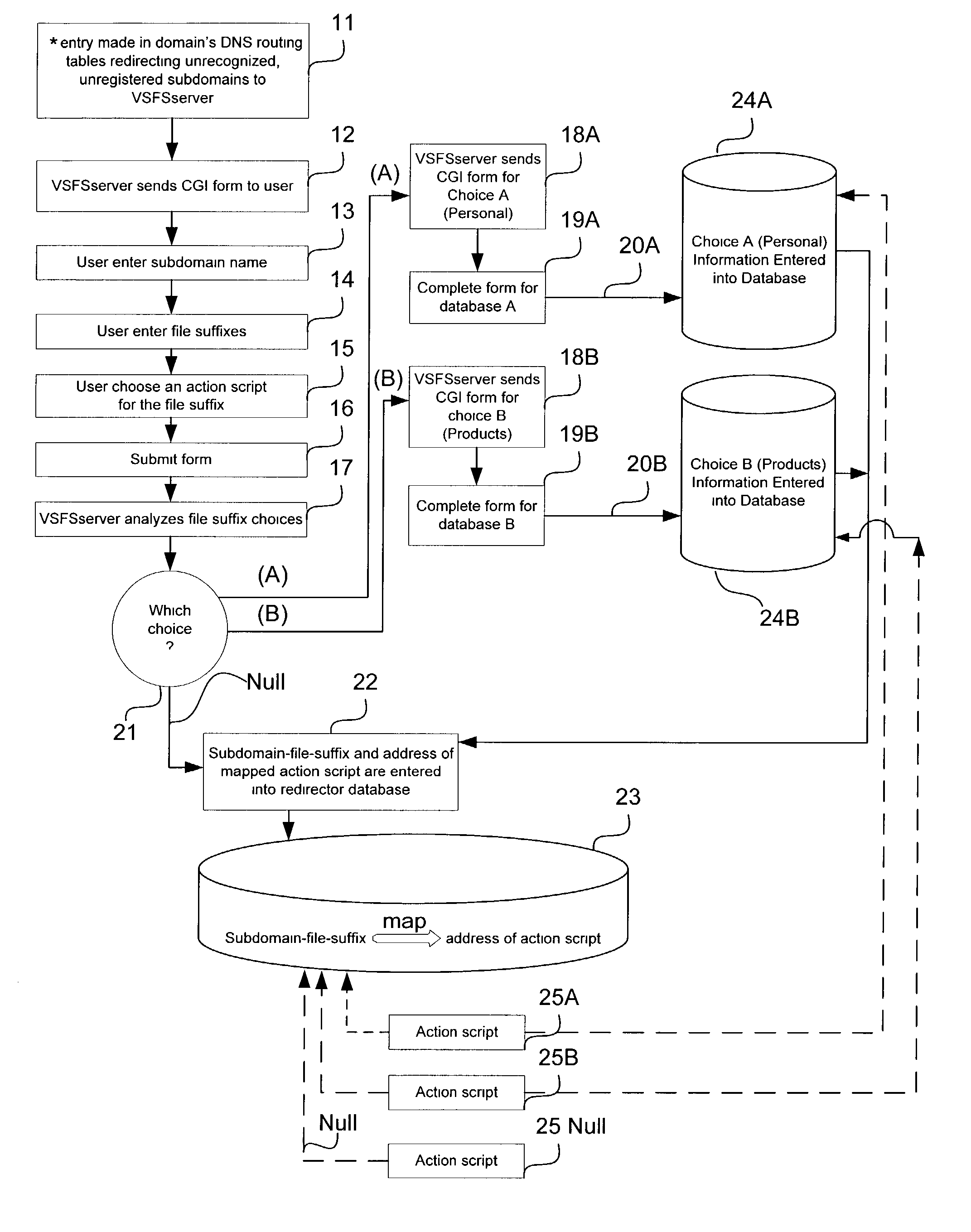
Virtual subdomain address file suffix
Prior to this invention, a virtual subdomain address could not have a file suffix because the virtual subdomain name in a URL did not refer to a standard host that the file suffix could be applied to. With the invention, the file suffix can be added to virtual subdomains through remapping the virtual-subdomain-domain-file-suffix combination or the virtual subdomain-file suffix combination to a new address where an action script then occurs. In creating this file suffix and remapping, the user enters a file suffix name and chooses an action script to associate with this file suffix name. When a browser requests a virtual-subdomain-domain-file-suffix combination through entering it through the browser's URL box, this URL request is redirected to an address with the mapped action script. The action script then typically causes the sending of response web objects containing information previously entered or programmed for that virtual subdomain-domain-file-suffix combination. The response information typically is a database driven webpage. This invention changes the way virtual subdomain URLs can be represented and makes it indistinguishable in appearance from a standard URL. Two applications are organizing web content of a virtual subdomain address and to provide a level of privacy, security, and communications paths to virtual subdomain addresses.
Owner:WEB & NET COMPUTING
Traffic visualization across web maps
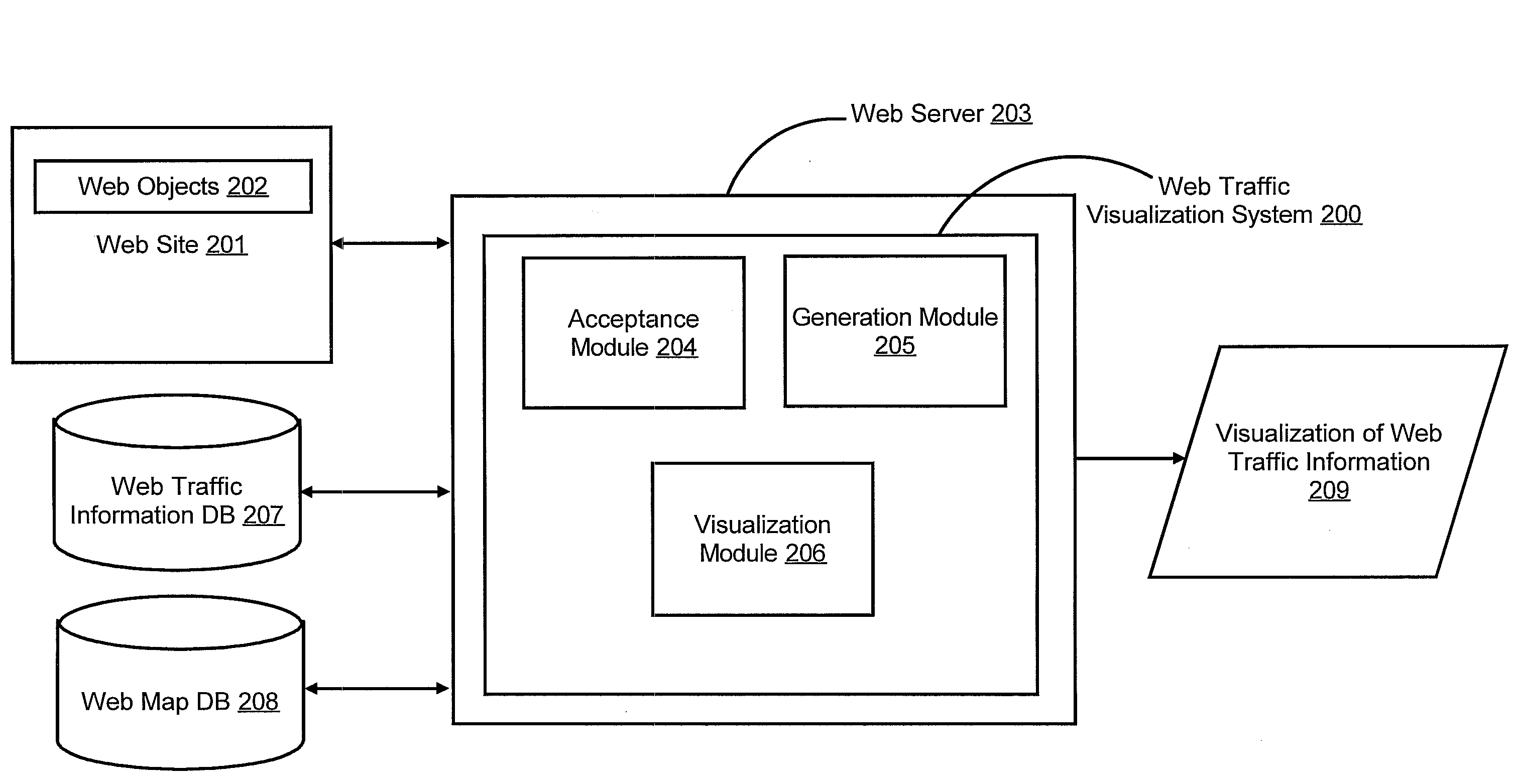
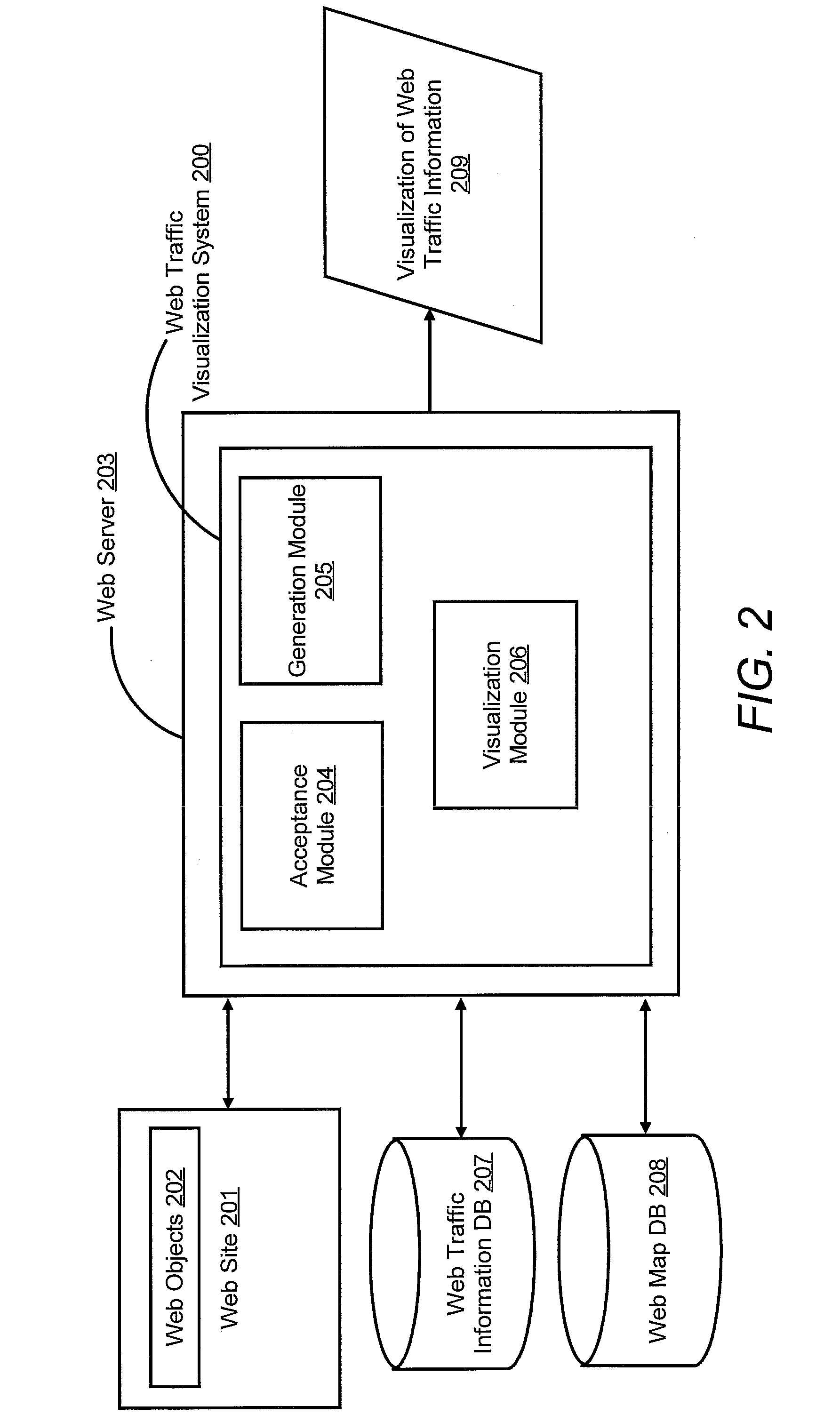
ActiveUS20110055710A1Input/output for user-computer interactionDigital computer detailsWeb siteInternet traffic
A web traffic visualization system includes a generation module configured to generate a web map. The web map includes web objects and links connecting the web objects, where the web objects are for a web site. The web traffic visualization system also includes an acceptance module configured to assign a unique ID to a visitor of the web site and receive a visitor action performed by the visitor on a web object in the web site tagged with the unique ID. The web traffic visualization system is further configured to include a visualization module configured to generate and display the visitor action on the web map in response to receiving the visitor action tagged with the unique ID.
Owner:ACCENTURE GLOBAL SERVICES LTD
Method, system and program product for automatically modifying a display view during presentation of a web page
A system and method of using a browser for displaying a web page on a computer screen wherein the browser executes a web page animated construction and / or provides zoom in and out viewing of the web page as the web page is constructed. The animated construction involves the browser associating each web object with an animated mover character. The web object and animated mover character are moved from outside a boundary area of the web page to its programmed location within the web page wherein the movement simulates that the animated mover character is building the web page. The zoom in and out viewing of a web page involves execution of a web page construction algorithm, such as the web page animated construction algorithm, for display of the web objects on the web page. The browser determines whether web object display has exceeded a current zoomed view of the web page and zooms out the current zoomed view to accommodate additional web objects if display has exceeded the current zoomed view. The browser processes all of the web objects to display the entire web page with all of the web objects. The browser then zooms back into the current view of the web page to only an initial portion of the web page. A scroll indicator with the current view of the web page for indicating to a user scrollability and accessibility to more and other portions of the web page.
Owner:INT BUSINESS MASCH CORP
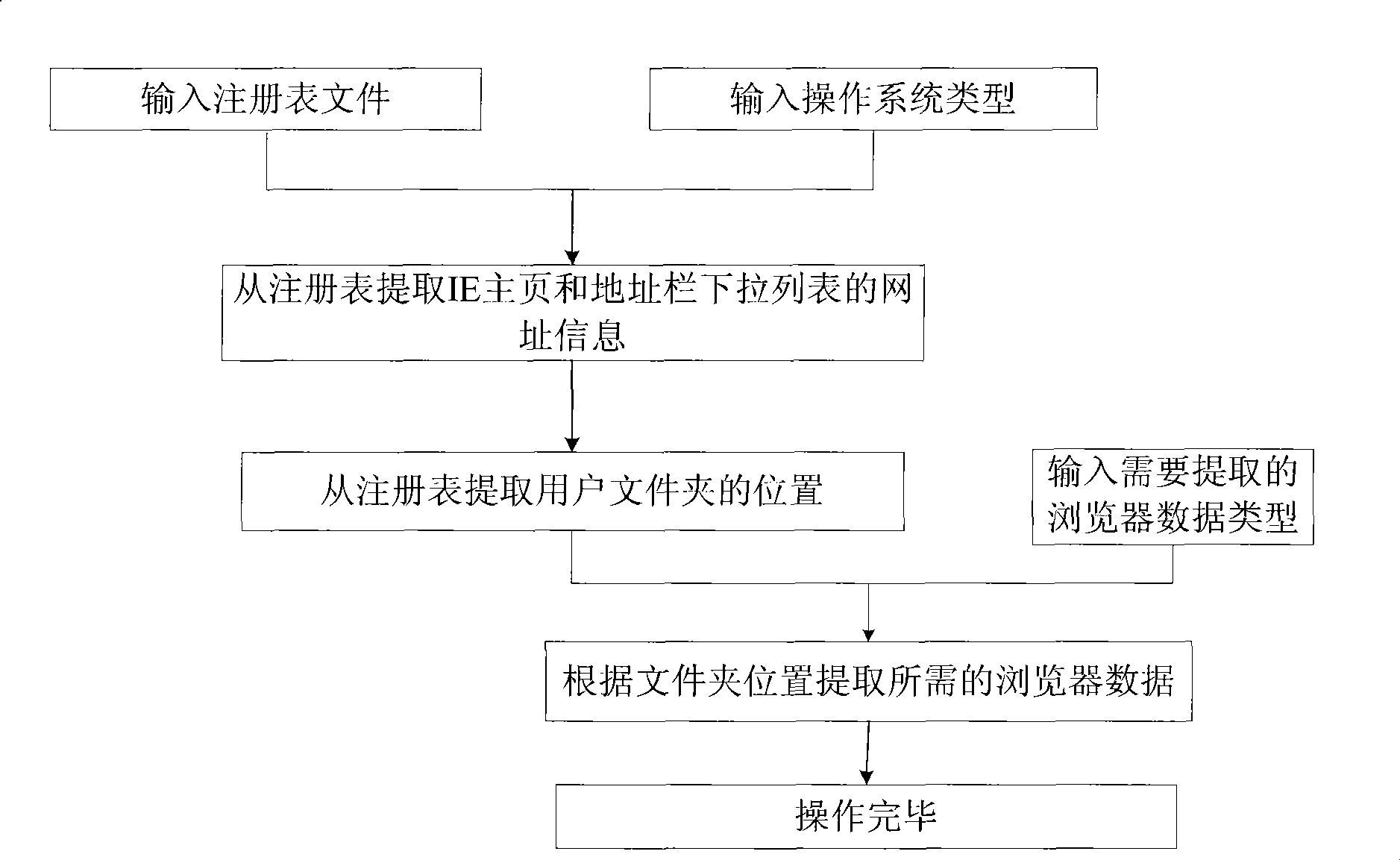
Evidence obtaining method for Web browser caching data
InactiveCN101369276AEasy to viewRefining the browsing pathSpecial data processing applicationsVisit timeWeb browser
The invention relates to an evidence-taking method of Web browser buffer memory data. In the method of the prior art, it is difficult to acquire click operation of the web and information which is acquired by users. The method comprises: inputting a Web browser data file and searched sensitive key words; resolving and pretreating an evidentiary document; conforming each record and other associated Web evidence into a Web object using Web browse record as a main line; selecting special Web object as a root node, constructing a Web tree according to link reference and web visit time between webs, construct a web evidence forest; performing intelligent search on the forest though input key words, obtaining relative web object; performing content analysis on relative Web object and Web tree; generating a Web evidence-taking report for the user to browse. The method of the invention is high in efficiency, strong in intelligibility and low in requirement on proficiency of investigators.
Owner:HANGZHOU DIANZI UNIV
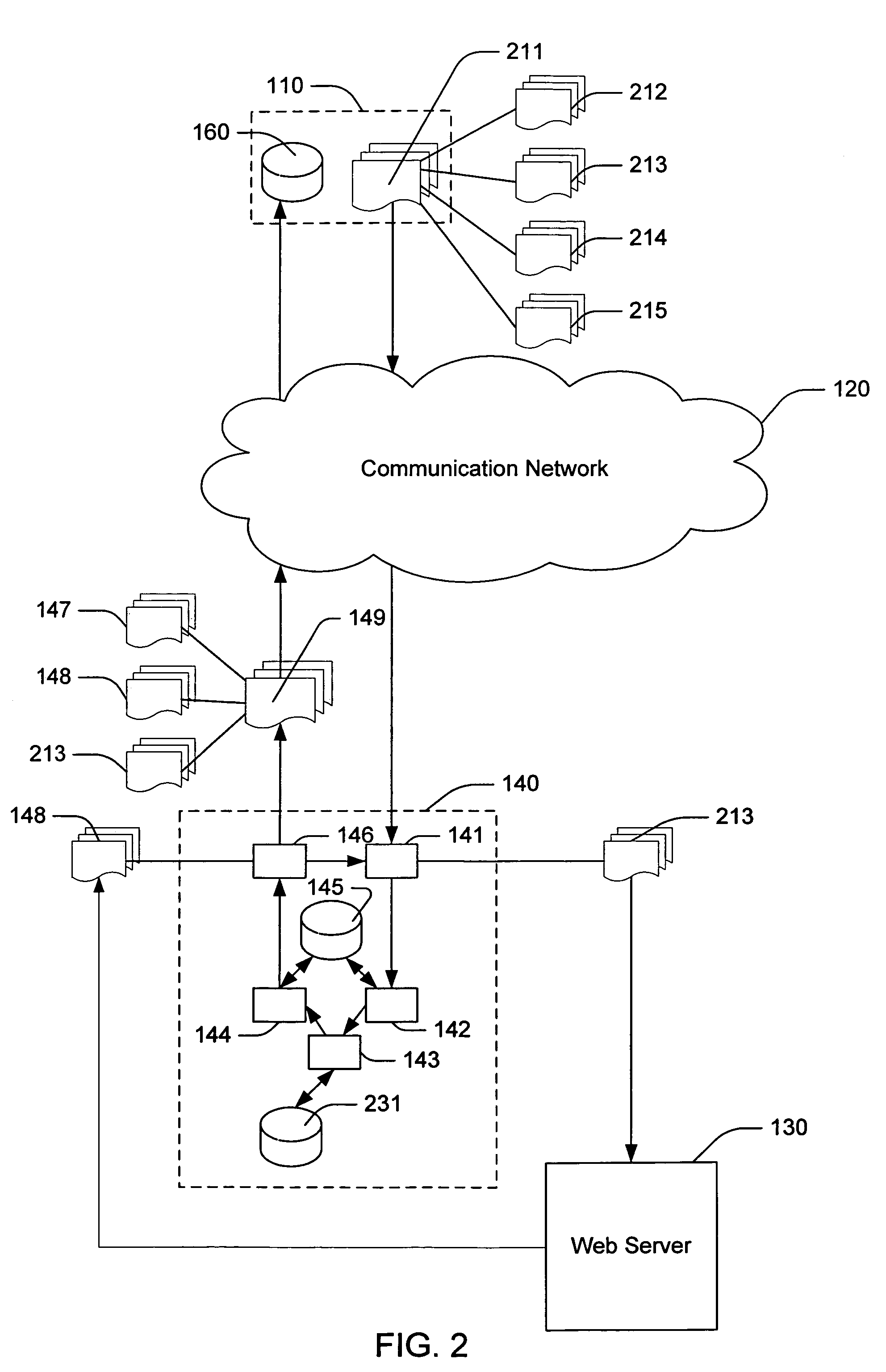
Predictive pre-download of a network object
InactiveUS20060075068A1Shorten the timeBetter able to predictDigital data information retrievalMultiple digital computer combinationsClient-sideWeb object
A method for fetching network objects from a web server is described. The method includes intercepting at a device a request from a web client to a web server for a first network object. The same device intercepts a response to the request from the web server. The device determines at least one second network object most probable to be requested in the future from the web server. Subsequently, a message is sent from the device to the web client the first message informing the web client of the at least one second network object to be cached by the web client.
Owner:DIGITAL RIVER INC
Tangible icon representing network objects
InactiveUS20050193339A1Cathode-ray tube indicatorsSpecial data processing applicationsEngineeringWorld Wide Web
Owner:MEYERS STEPHAN
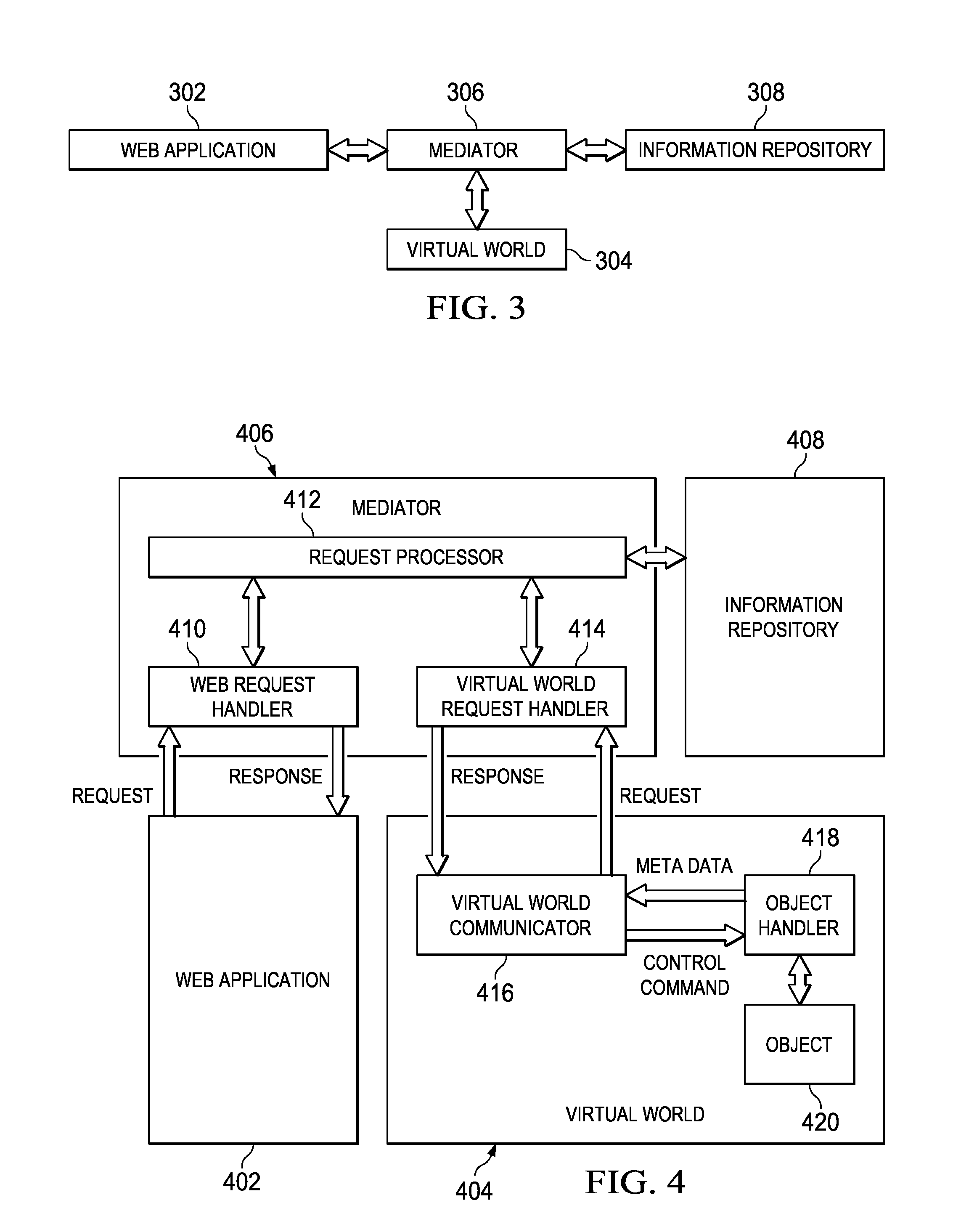
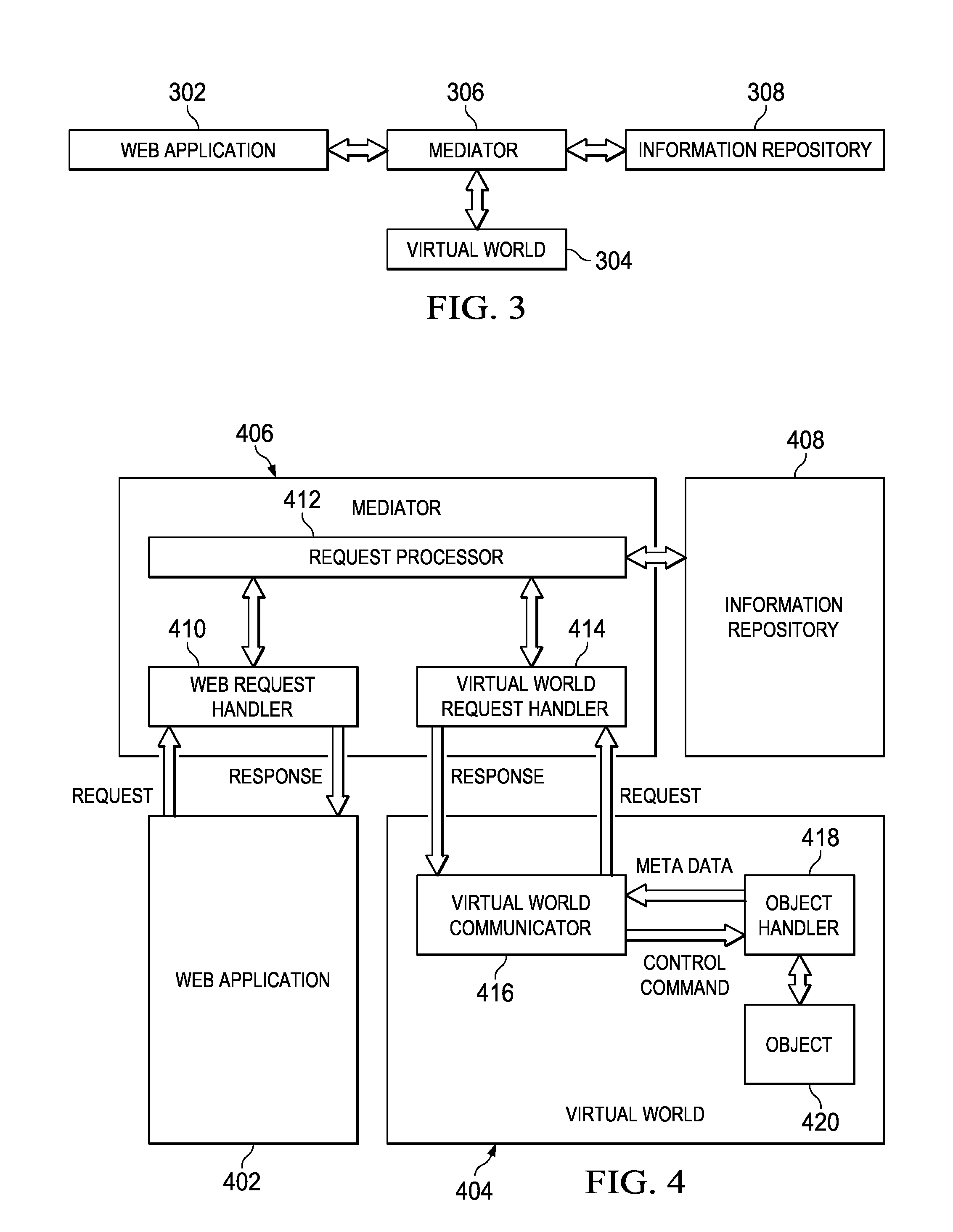
Method and apparatus for bridging real-world web applications and 3D virtual worlds
ActiveUS20090100352A1Digital data processing detailsWebsite content managementData processing systemInformation sharing
A computer implemented method, data processing system, and computer program product for automating information sharing and propagation of control commands and events between software objects created in Web applications and 3D virtual world objects created in virtual world applications. A relationship is created to link a Web object with one or more virtual world objects, or to link a virtual world object with one or more Web objects. A Web application may retrieve the meta-data of one or more virtual world objects or send commands or events to manipulate one or more virtual world objects to which a Web object within the Web application is linked. A virtual world system may retrieve the meta-data of one or more Web objects or send commands or events to manipulate one or more Web objects to which a virtual world object within the virtual world system is linked.
Owner:ROBLOX CORP
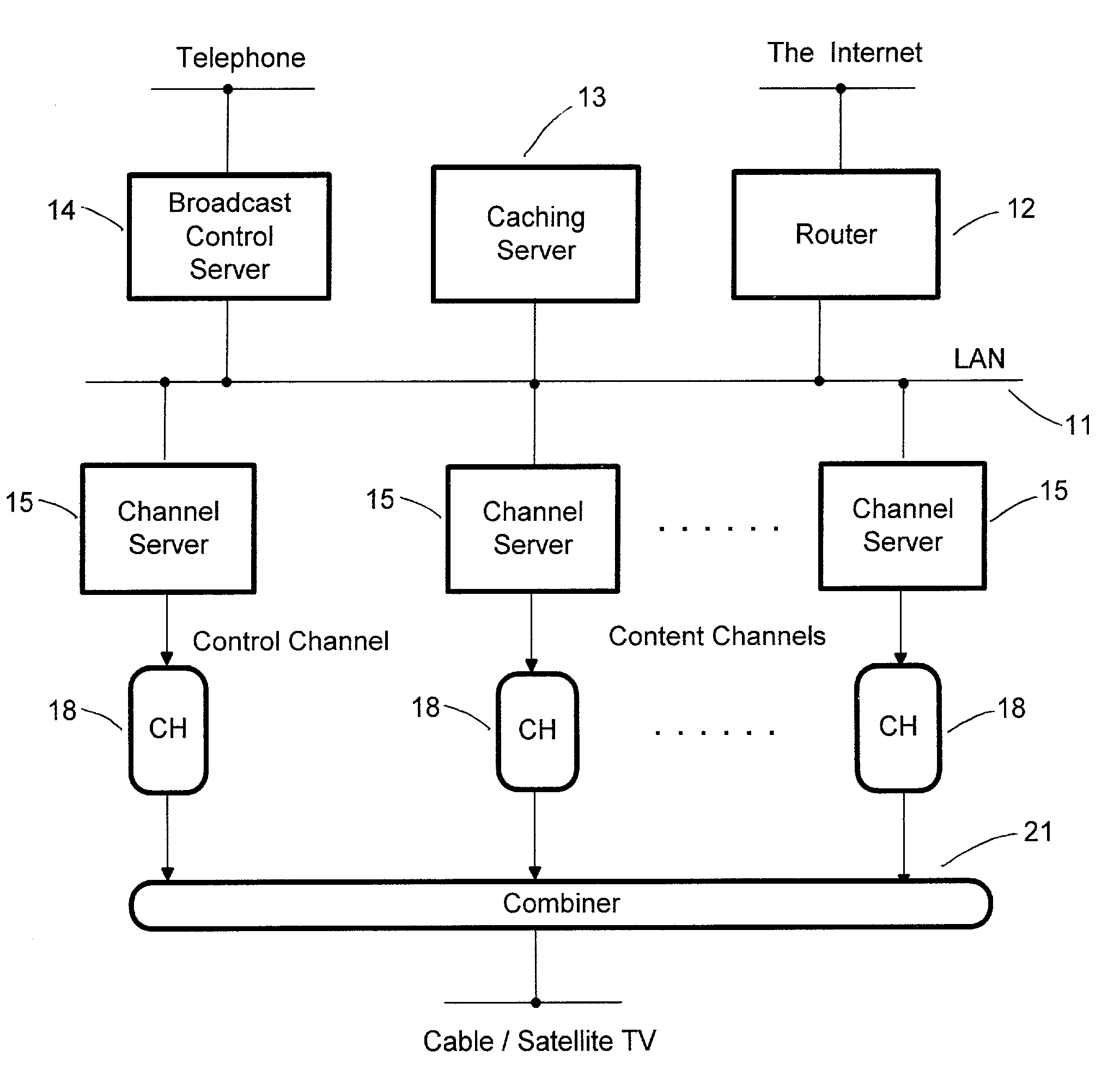
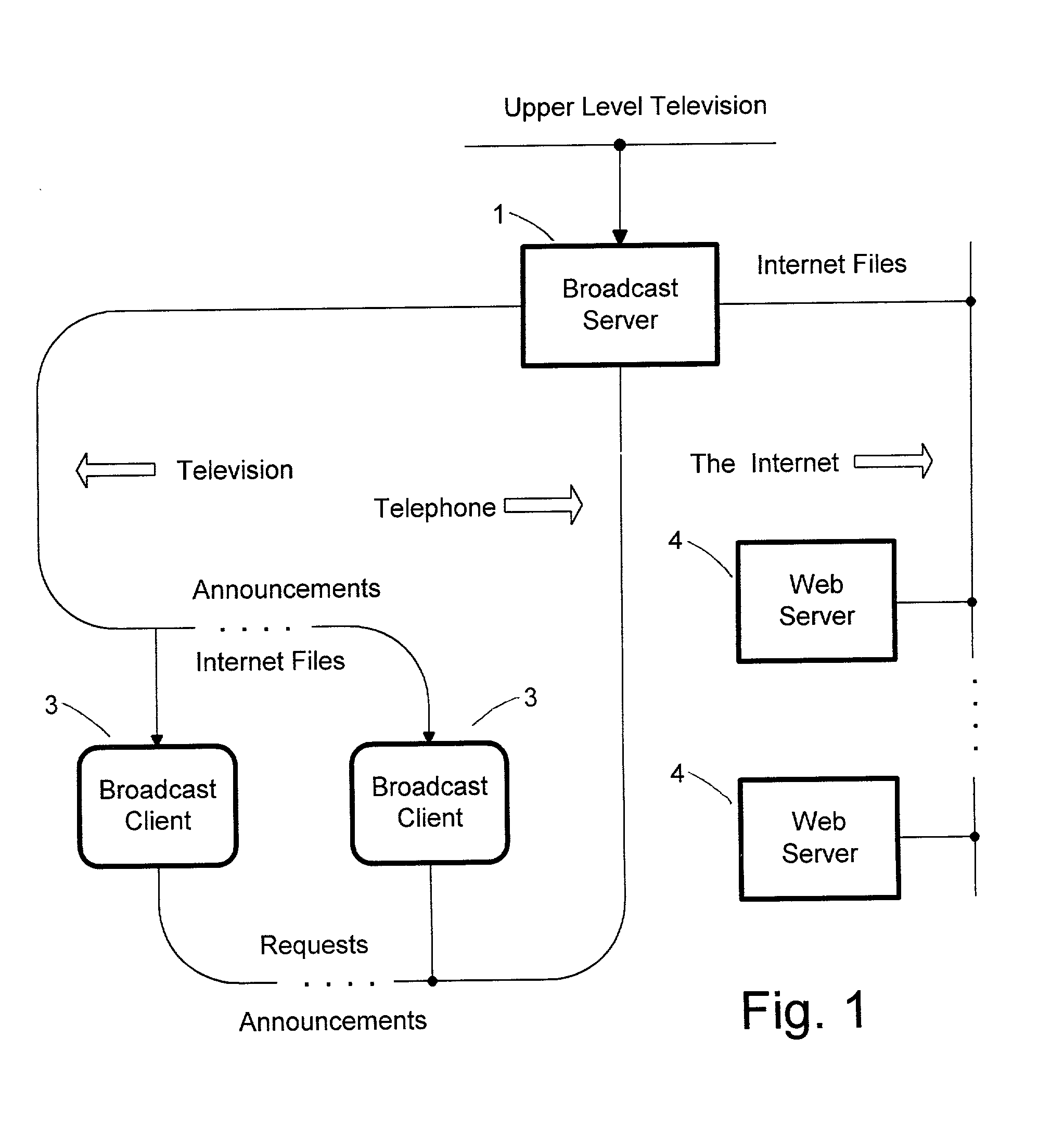
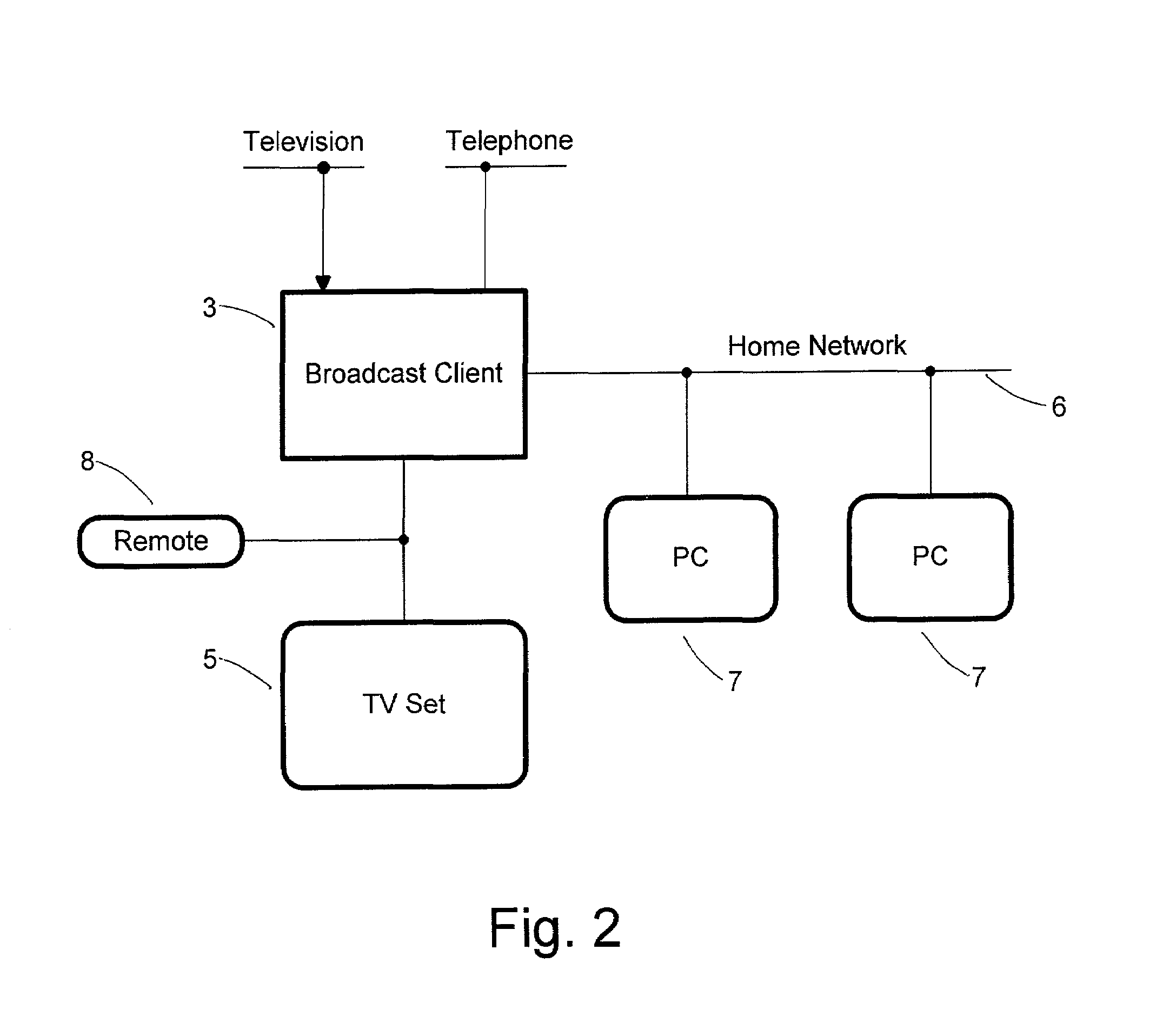
Data broadcast network for congestion-free internet access
InactiveUS7092999B2Avoid receivingSpecial service provision for substationPulse modulation television signal transmissionBroadcast channelsCable Internet access
The invention is an Internet access system that puts together interactivity of the Internet and congestion-free content delivery inherent in broadcast media in order to reduce delays in content presentation. The system delivers any web object (web page, music file, video etc.) in two steps. First, a single copy of object is downloaded according to a standard Internet protocol into a server provided at a broadcast center no matter how many client computers have requested the object; then the copy is transmitted over a broadcast channel according to a data broadcast protocol so that all clients could download it simultaneously. A web object is transmitted as a flow of packets and the transmission is preceded with an announcement specifying a broadcast channel and a flow number. The packet header contains a flow number and a destination address that could be a client address or a broadcast address, thereby enabling an efficient handling of both one-to-one and one-to-many transmissions. The system provides, when necessary, a protection of transmitted content against unauthorized reception by biding packets identity and transmitting packets of the same content over different, pseudorandomly changing channels.
Owner:LEVITAN GUTMAN
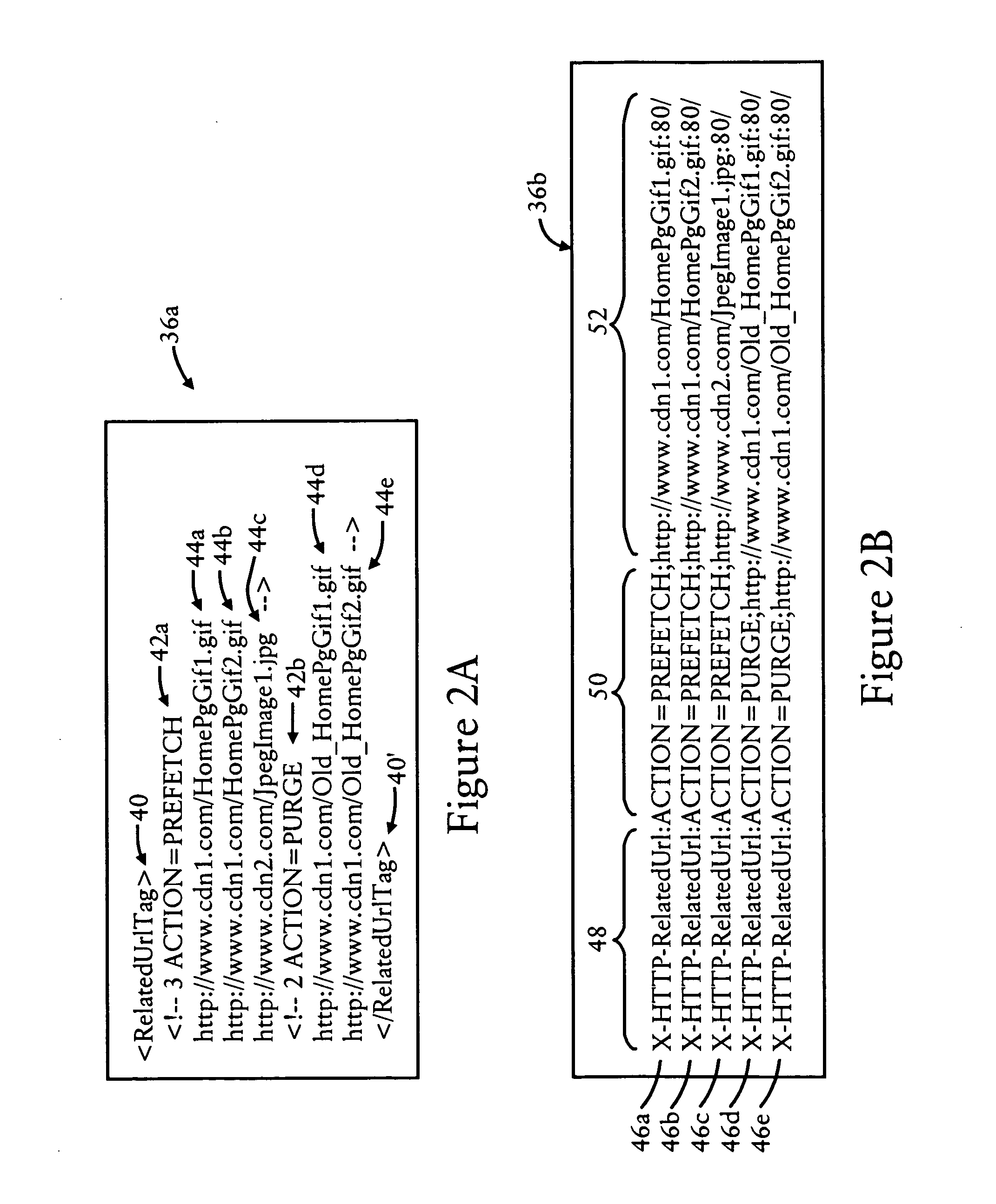
Arrangement for providing content operation identifiers with a specified HTTP object for acceleration of relevant content operations
ActiveUS7797376B1Delay minimizationEfficiently perform content operationMultiple digital computer combinationsTransmissionWeb serviceClient-side
Web content provided by a server includes associated content operation identifiers that identify related content objects. The web server, in response to receiving an HTTP Get request for the web object, retrieves the web object, and concurrently retrieves the content operation identifiers associated with the web object. The server sends the content operation identifiers with the requested web object as part of an HTTP response. The content operation identifiers may be inserted with an HTTP header, or may be added to the web content, for example by prepending HTML tags specifying the content operation identifiers to an HTML page that includes the requested web object. A proxy device receiving the HTTP response can forward the response to the requesting client device, and execute the content operations specified by the content operation identifiers within the HTTP response. Hence, content operations can be performed for relevant content objects based on content operation identifiers within the HTTP response, eliminating the necessity of client side executable resources that may otherwise affect the device performance.
Owner:CISCO TECH INC
Systems and methods for managing loading priority or sequencing of fragments of a web object
ActiveUS9282145B2Improve experienceImprove performanceDigital data information retrievalInterprogram communicationCode injectionDatabase
This disclosure is directed to methods and systems for managing rendering of a web page in a browser. A client operated by a user may execute code within a first fragment of a web page as the first fragment is presented to the user. The code may be injected into the first fragment by an intermediary between the client and a server of the web page. The intermediary may have split the web page into the first fragment and a plurality of fragments, and may have modified a default rendering characteristic for each of the plurality of fragments. Each of the modified rendering characteristic may include a trigger and action for rendering of a corresponding fragment. The executing code may dynamically detect a trigger for rendering of a second fragment from the plurality of fragments. The executing code may initiate a corresponding action for rendering of the second fragment.
Owner:YOTTAA
Caching web objects transformed by a pipeline of adaptation services
ActiveUS7565399B1Digital data information retrievalMultiple digital computer combinationsApplication softwareClient-side
In one embodiment, a method for processing a client request for content comprises receiving, at an intermediary network node, a client request for content on a network. The client request is associated with a set of attributes indicating a requirement to process the requested content by multiple designated applications prior to transferring the requested content to a client. The method further comprises searching, at the intermediary network node, a content cache for matching content conforming to the processing requirement, and determining, at the intermediary network node, whether the matching content is currently valid. If this determination is positive, the matching content is transferred to the client.
Owner:NETWORK APPLIANCE INC
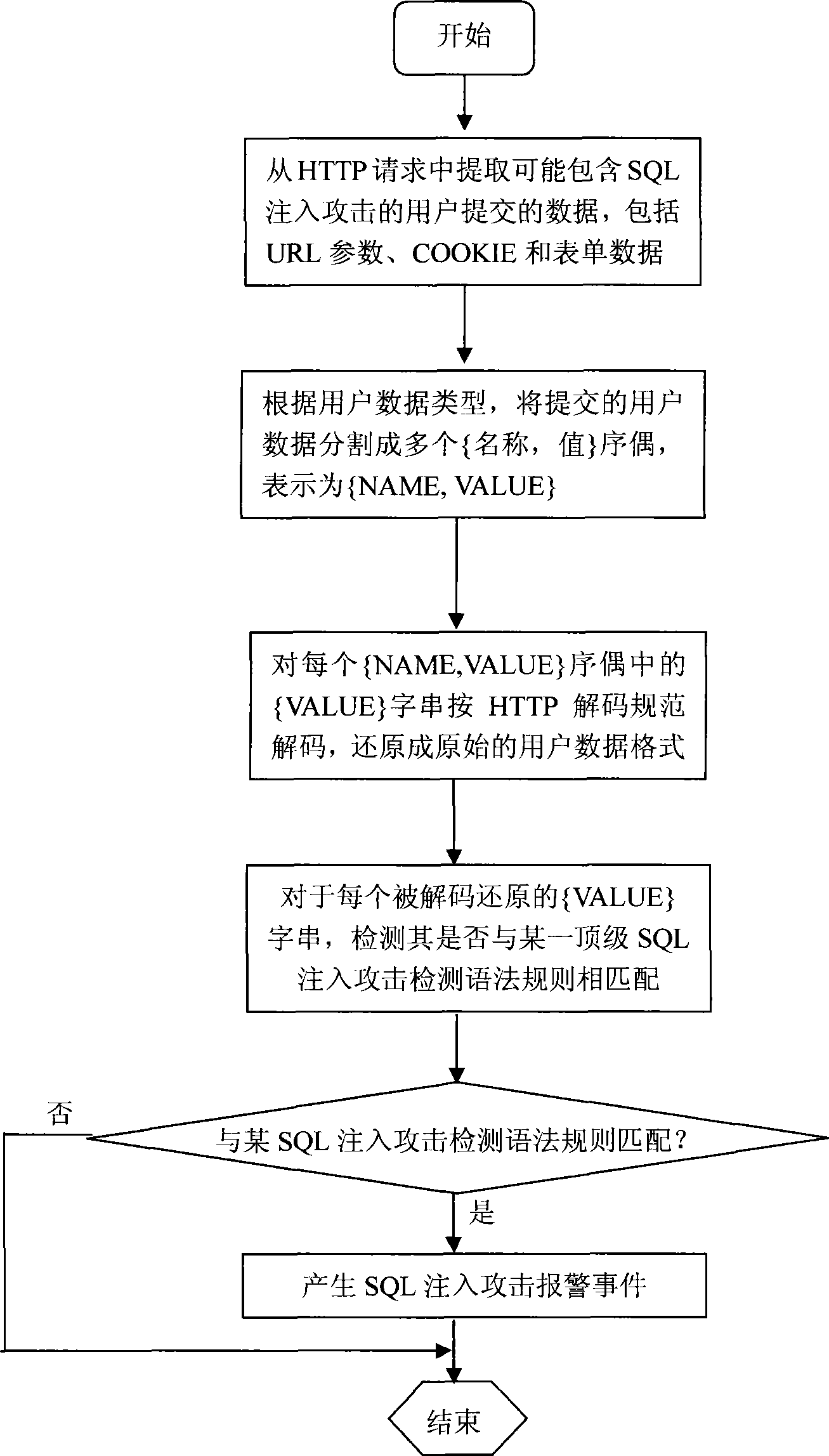
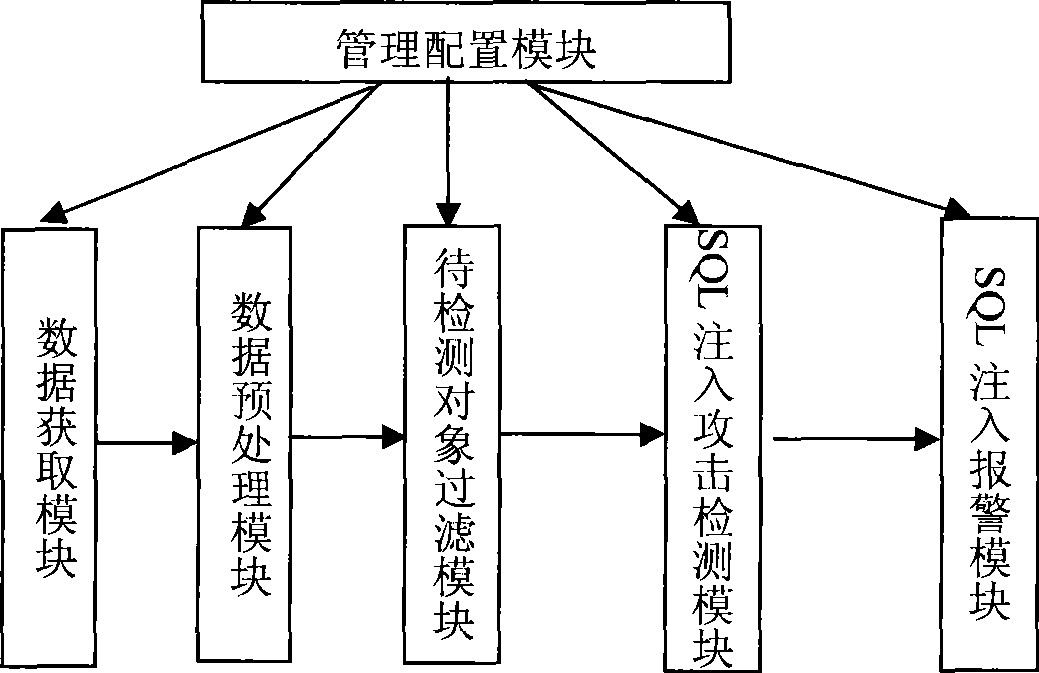
SQL injection attack detection system suitable for high speed LAN environment
InactiveCN101425937AReduce false alarm rateRelieve stressData switching by path configurationNetwork packetSQL injection
SQL injection attack detection system adapting to high speed LAN environment comprises data acquisition module, data pretreatment module, filter module for object to be detected, SQL injection attack detection module and SQL injection alarming module. The data acquisition module acquires network data pack related with HTTP service from protected network; data pretreatment module resolves operation and establishes object to be detected and transmits to the filter module for object to be detected based on TCP stream reassembly and HTTp protocol; the filter module for object to be detected matches URL of every object to be detected according to filtering rule sequence established, and performs designated processing action of matched filtering rule. The Web object type of HTTP request is divided into static Web type and dynamic Web type; static Web type HTTP requests during real time SQL injection attack detection is filtered out, which largely relieves processing pressure for SQL injection attack detection module, reduces rate of false alarm.
Owner:BEIJING VENUS INFORMATION TECH
Bridging real-world web applications and 3D virtual worlds
ActiveUS8370370B2Digital data processing detailsWebsite content managementData processing systemInformation sharing
A computer implemented method, data processing system, and computer program product for automating information sharing and propagation of control commands and events between software objects created in Web applications and 3D virtual world objects created in virtual world applications. A relationship is created to link a Web object with one or more virtual world objects, or to link a virtual world object with one or more Web objects. A Web application may retrieve the meta-data of one or more virtual world objects or send commands or events to manipulate one or more virtual world objects to which a Web object within the Web application is linked. A virtual world system may retrieve the meta-data of one or more Web objects or send commands or events to manipulate one or more Web objects to which a virtual world object within the virtual world system is linked.
Owner:ROBLOX CORP
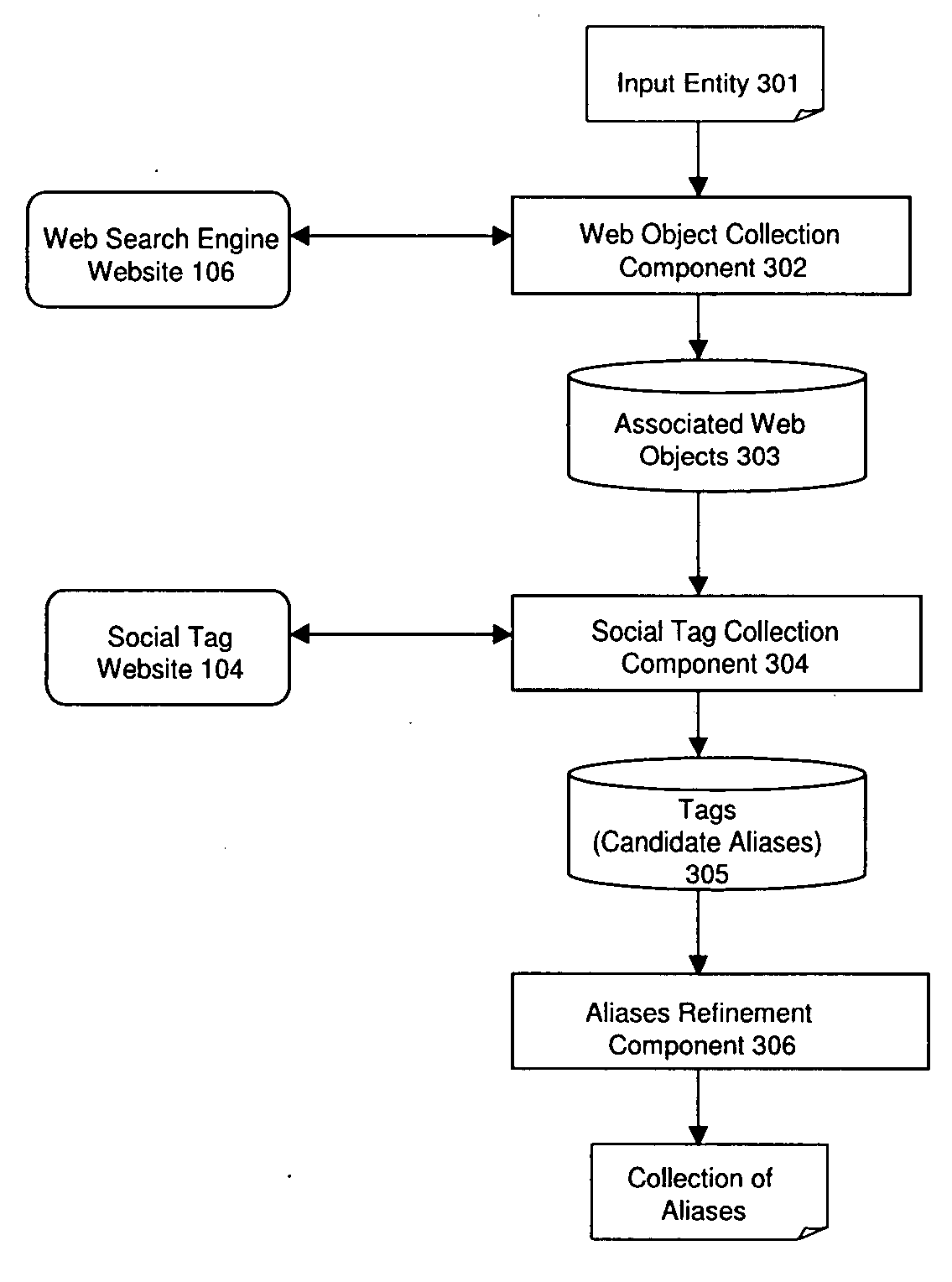
Method and apparatus for collecting entity aliases
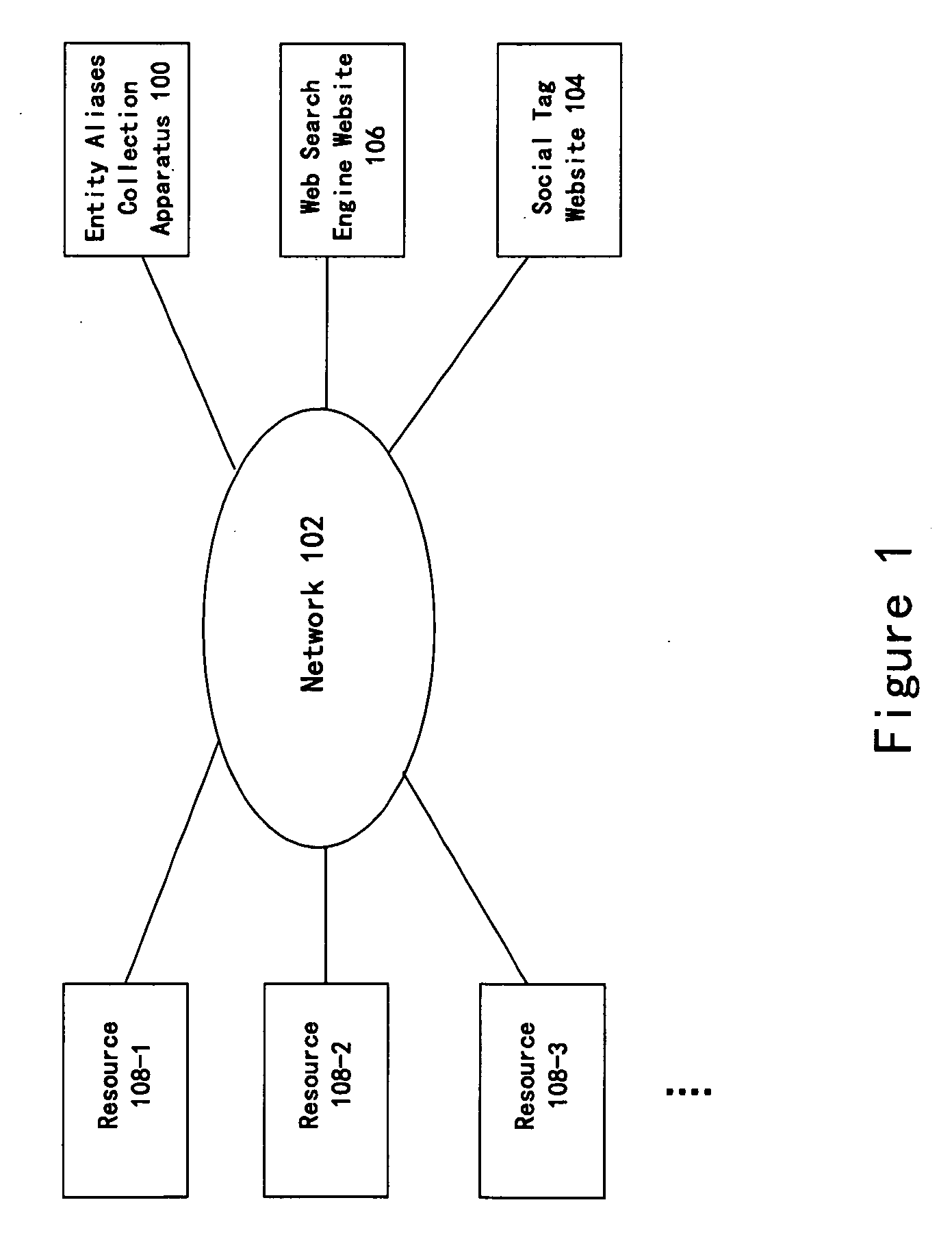
ActiveUS20090192996A1More time-effectiveDigital data processing detailsSpecial data processing applicationsWeb siteWeb search engine
A system and method for collecting entity aliases include a web object collection component that obtains, from a web search engine, at least one Web object associated with a user' input entity. The system and method also include a social tag collection component that obtains a respective set of social tags for each of the Web objects from a social tag website and defines candidate aliases for the user's input entity based upon the respective set of social tags. An aliases refinement component refines the candidate aliases to obtain a collection of aliases of the user's input entity.
Owner:RAKUTEN GRP INC
Optimization framework for tuning ranking engine
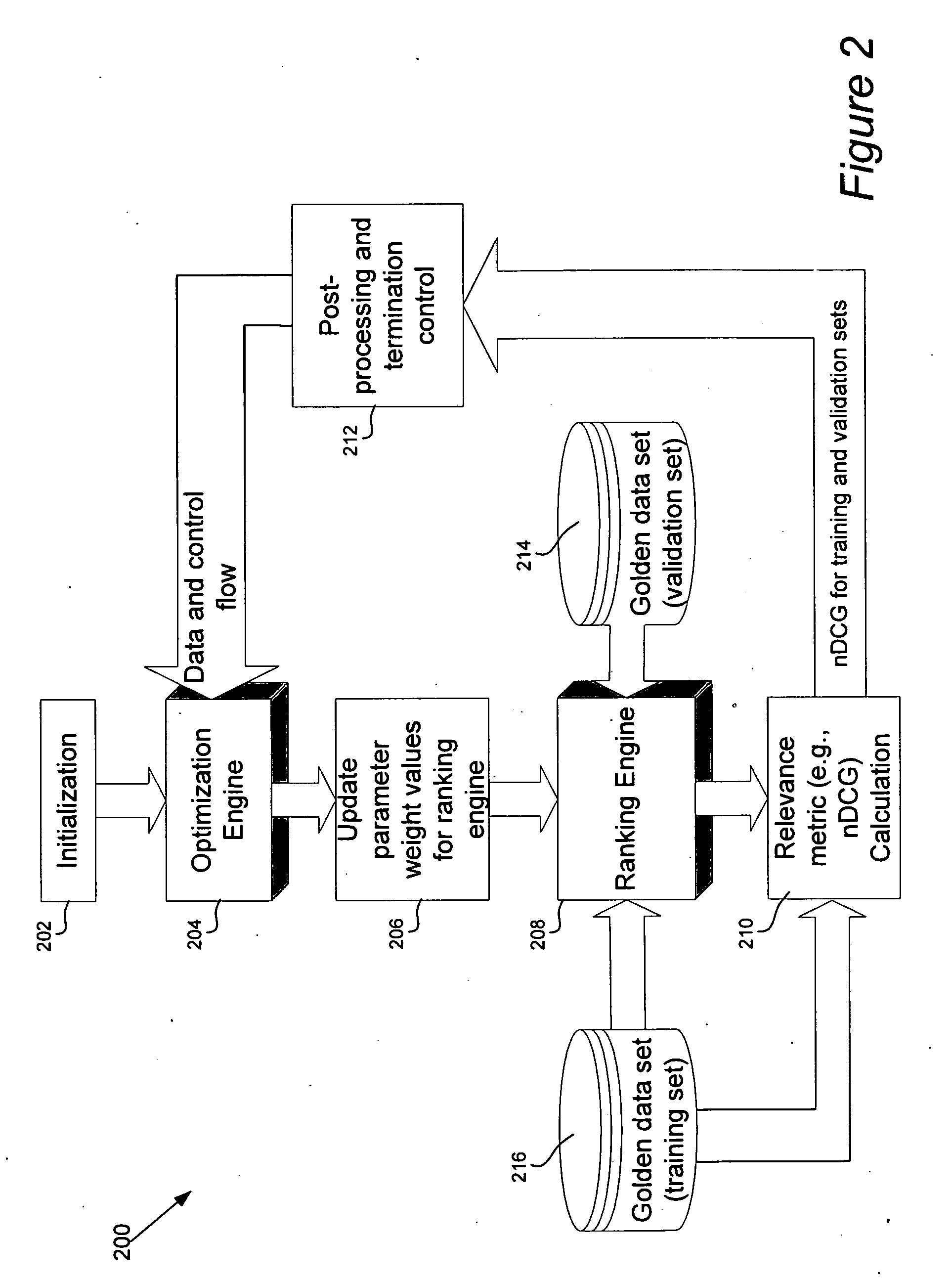
ActiveUS20100070498A1Improve rankingLower overall renovationWeb data indexingDigital data processing detailsLocal optimumRanking
Disclosed are apparatus and methods for facilitating the ranking of web objects. The method includes automatically adjusting a plurality of weight values for a plurality of parameters for inputting into a ranking engine that is adapted to rank a plurality of web objects based on such weight values and their corresponding parameters. The adjusted weight values are provided to the ranking engine so as to generate a ranked set of web objects based on such adjusted weight values and their corresponding parameters, as well as a particular query. A relevance metric (e.g., that quantifies or qualifies how relevant the generated ranked set of web objects are for the particular query) is determined. The method includes automatically repeating the operations of adjusting the weight values, providing the adjusted weight values to the ranking engine, and determining a relevance metric until the relevance metric reaches an optimized level, which corresponds to an optimized set of weight values. The repeated operations utilize one or more sets of weight values including at least one set that results in a worst relevance metric value, as compared to a previous set of weight values, according to a certain probability in order to escape local optimal solution to reach the global optimal solution.
Owner:YAHOO AD TECH LLC
Architecture and methodology of redirection for dynamic new URL links
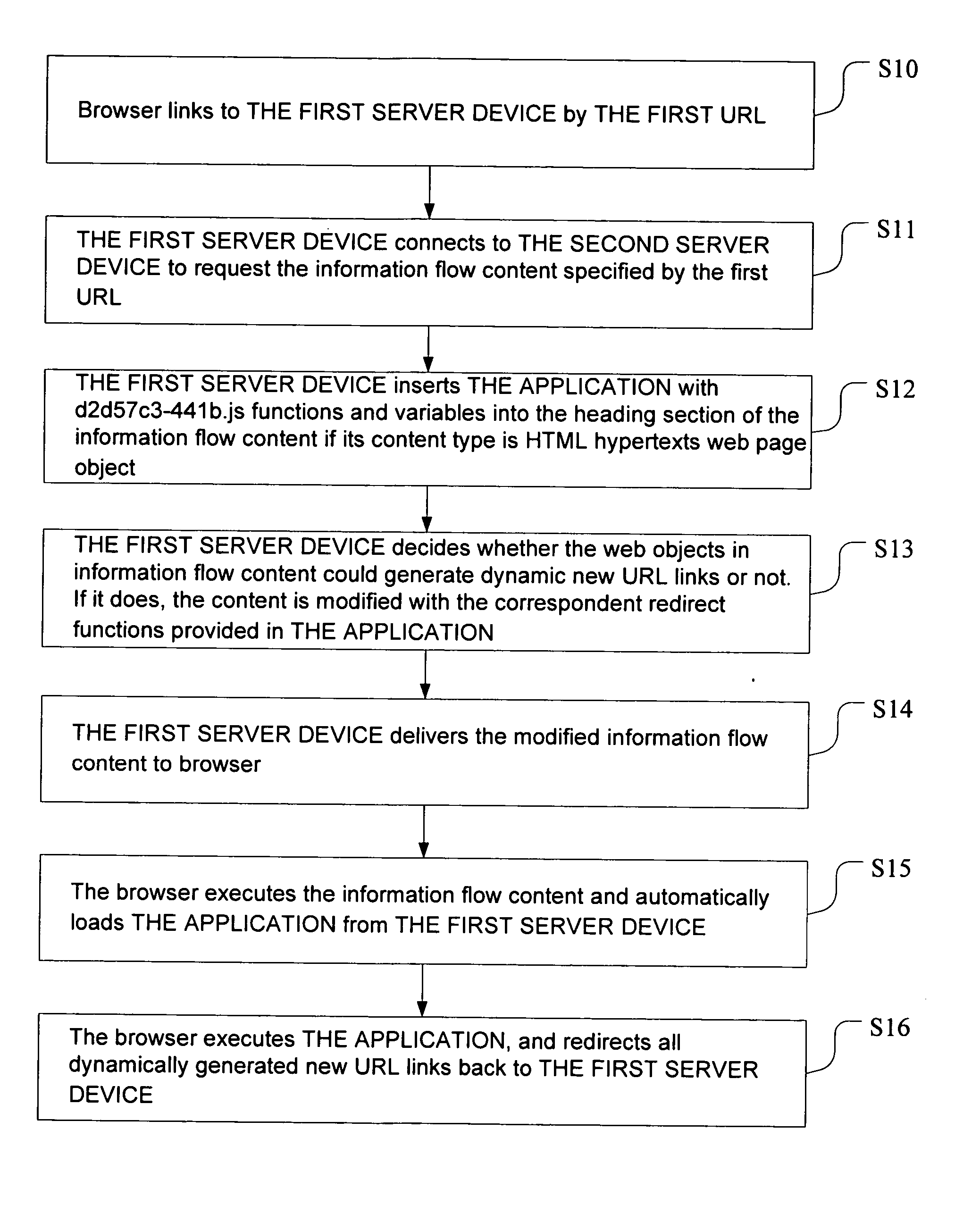
InactiveUS20060059416A1Remove obstaclesReduce loadNatural language translationDigital data information retrievalUniform resource locatorServer appliance
An architecture and methodology of redirection for dynamic new URL Links uses a first server device to get information flow content from a second server device. By inserting an application into the information flow content retrieved from the second server device, the first server device replaces the web objects, which may generate dynamic new URL links, with the redirect functions in the code and sends the content to the browser. The browser will execute the code automatically. Whenever the browser generates new dynamic new URL links, it would call the provided redirect functions, and thus redirect them and retrace back to the first server device.
Owner:LIN JIMMY JONG YUAN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com