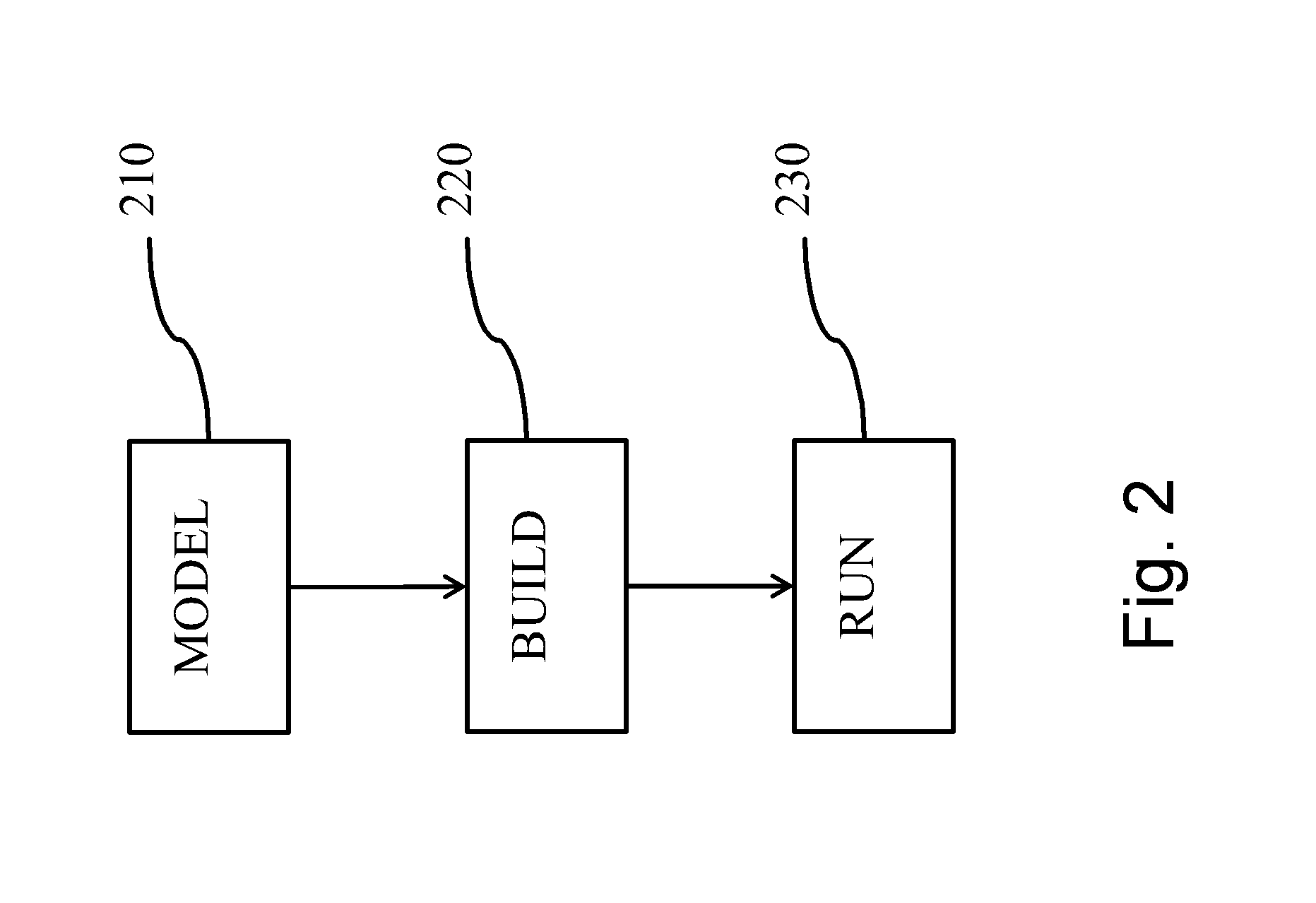
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
89 results about "Object graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
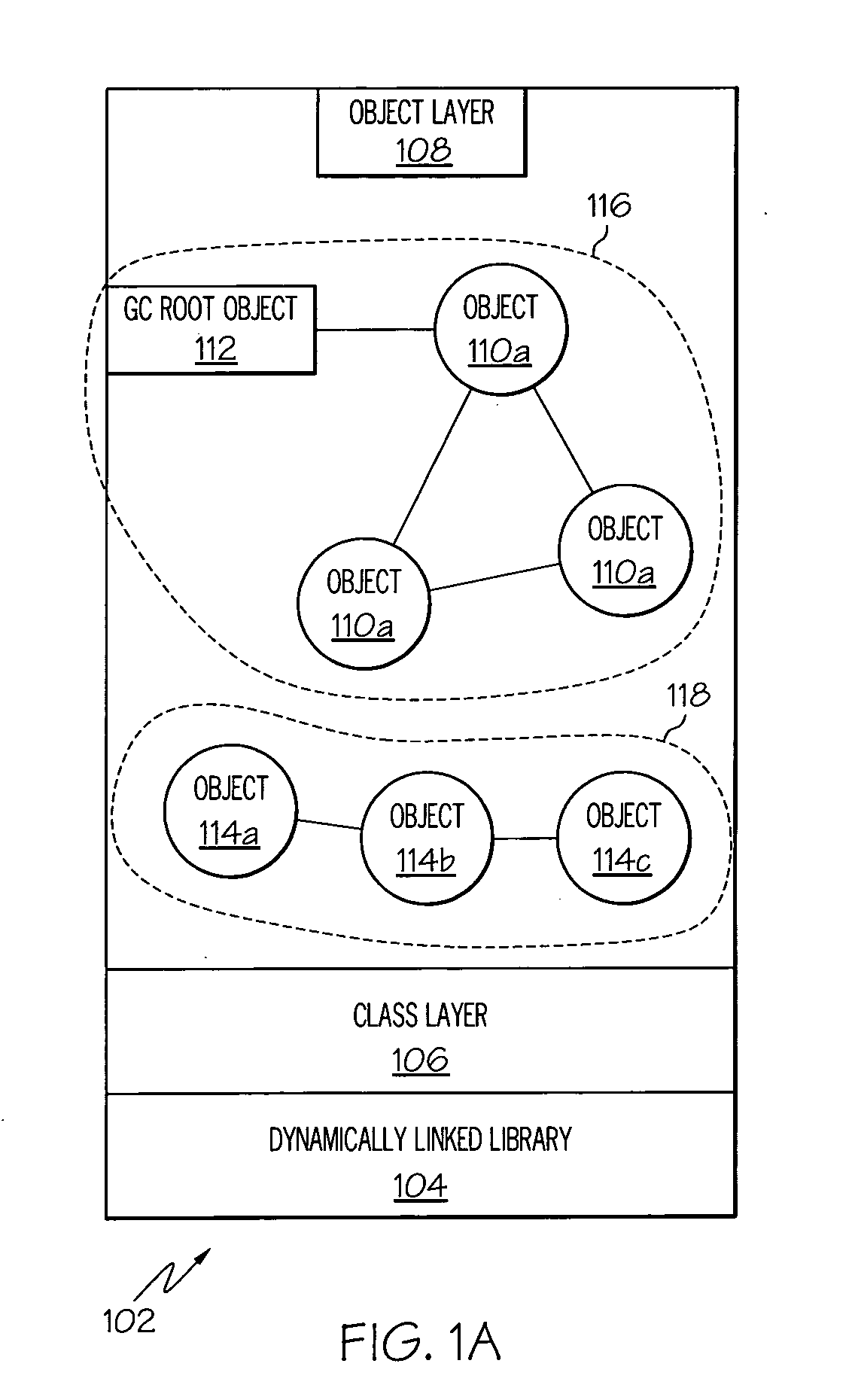
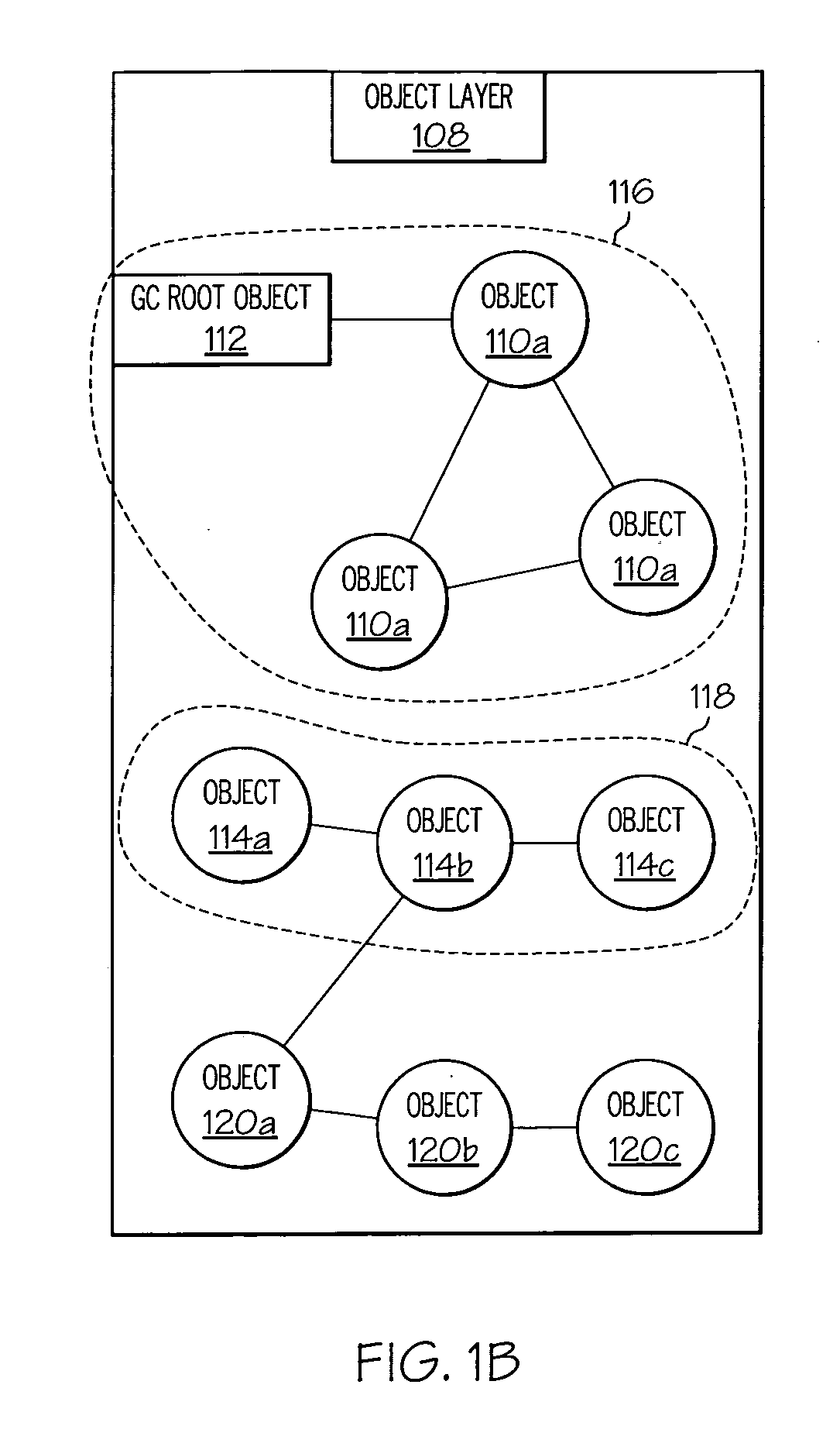
In computer science, in an object-oriented program, groups of objects form a network through their relationships with each other—either through a direct reference to another object or through a chain of intermediate references. These groups of objects are referred to as object graphs.
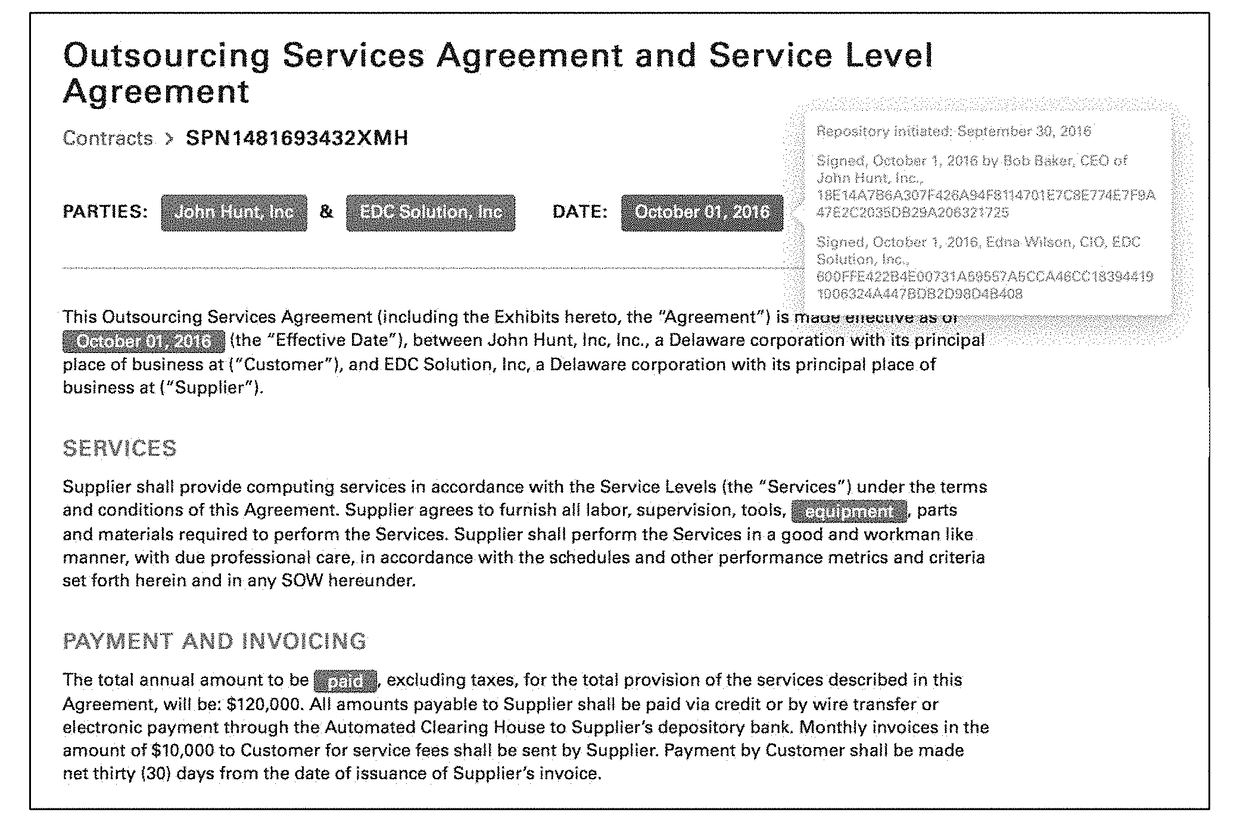
System and method for forming, storing, managing, and executing contracts
ActiveUS20180005186A1Efficiently and verifiably moveReduce dataDrawing from basic elementsCryptography processingDocumentationObject graph
A system and method for computable contracts that includes a contract management system accessible by involved parties, managing a formation stage of a contract document by obtaining object components, assembling a contract object graph from the object components, and committing the contract object graph to post formation execution; and in an execution environment during a post-formation stage, executing the contract object graph where instances of execution include receiving a contract state update, and appending at least one update object component to the contract object graph in accordance with the contract state update. Variations of the system and method may apply peer-to-peer negotiation and execution, use a cryptographic directed acyclic contract object graph, and / or interface with distributed ledgers.
Owner:DOCUSIGN
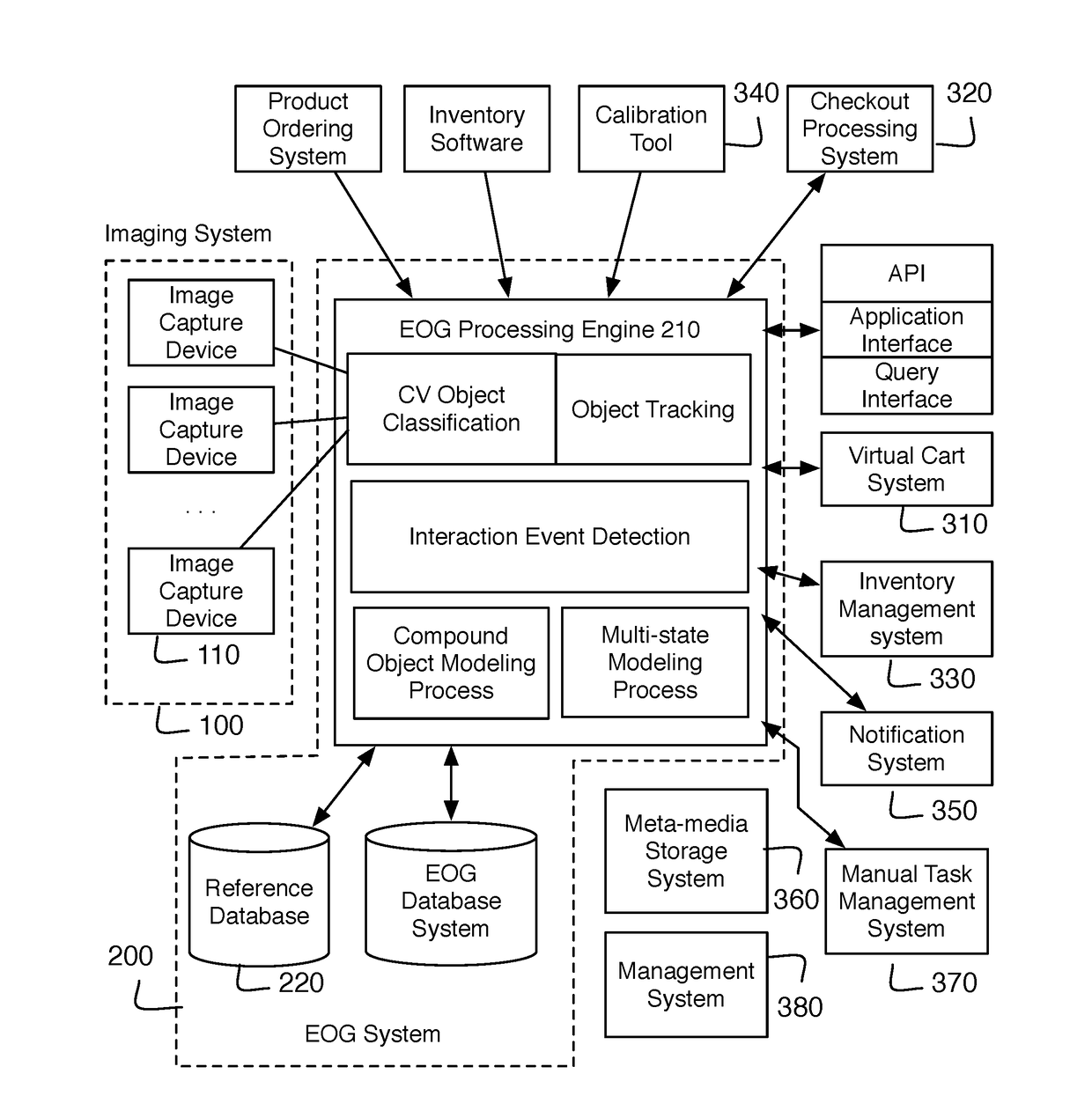
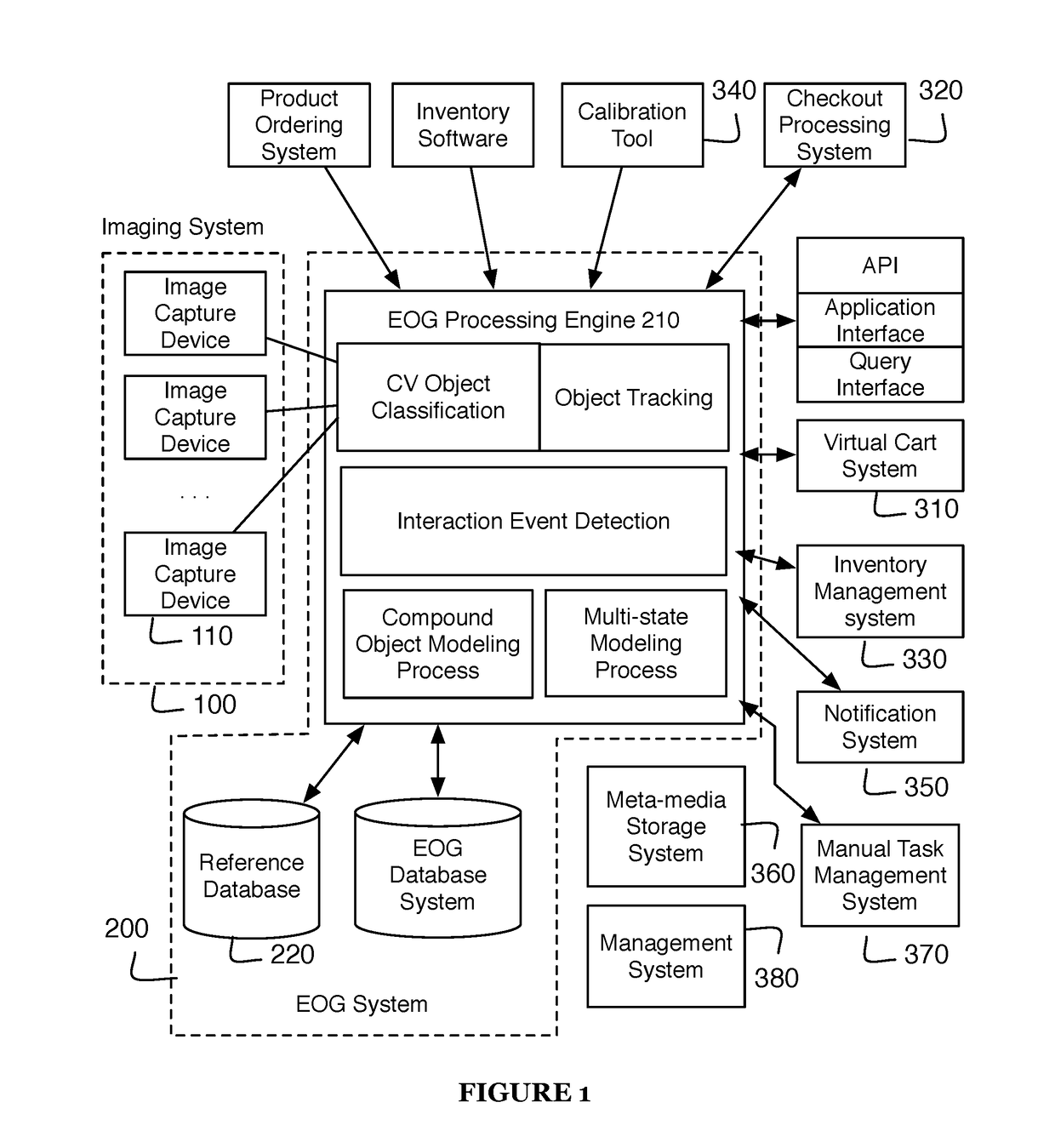
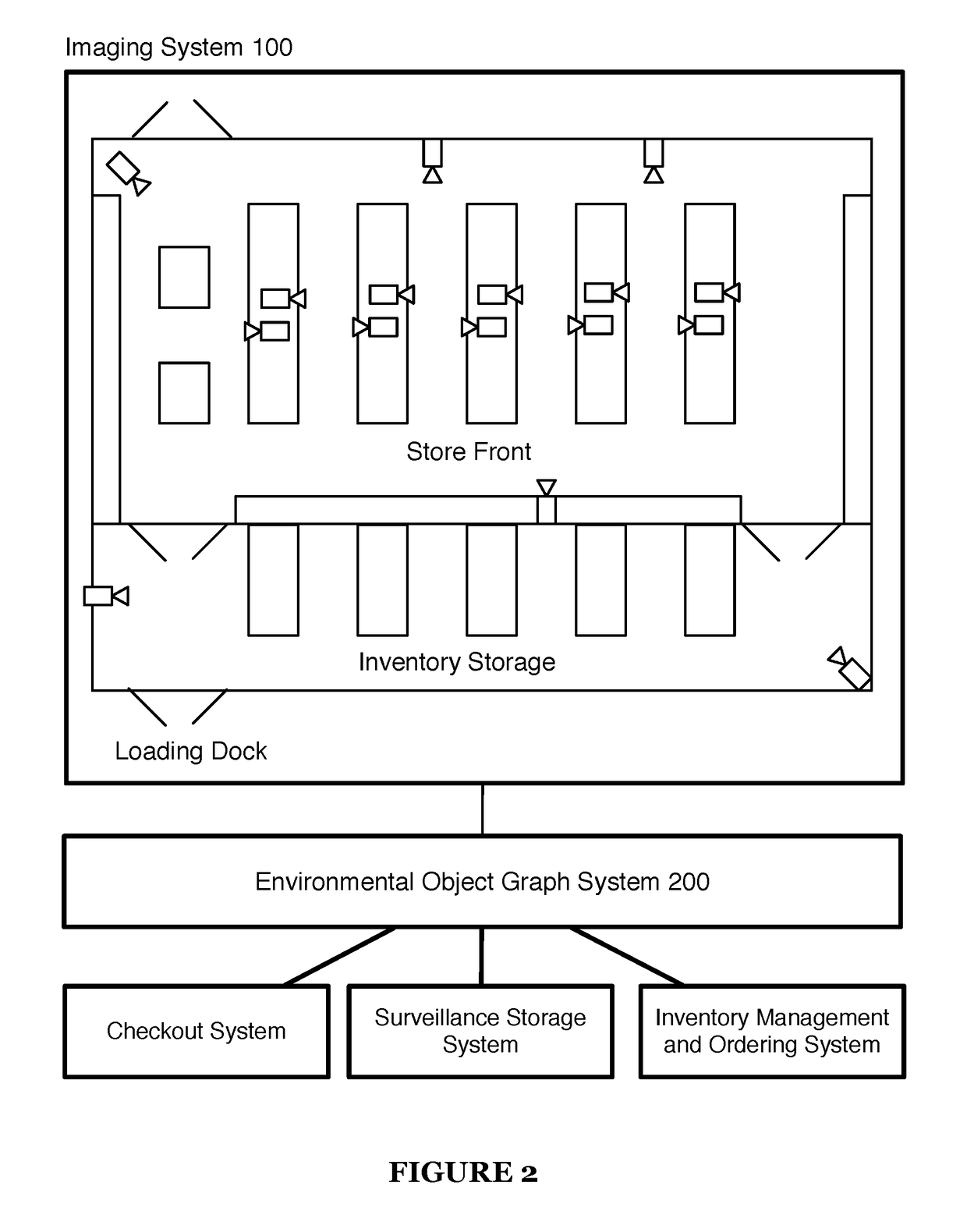
System and method for computer vision driven applications within an environment
ActiveUS20170323376A1Easy maintenanceConfidenceCharacter and pattern recognitionClosed circuit television systemsSystem integrationState dependent
A system and method for computer vision driven applications in an environment that can include collecting image data across an environment; maintaining an environmental object graph from the image data whereby maintaining the environmental object graph is an iterative process that includes: classifying objects, tracking object locations, detecting interaction events, instantiating object associations in the environmental object graph, and updating the environmental object graph by propagating change in at least one object instance across object associations; and inspecting object state for at least one object instance in the environmental object graph and executing an action associated with the object state. The system and method can be applied to automatic checkout, inventory management, and / or other system integrations.
Owner:GRABANGO CO
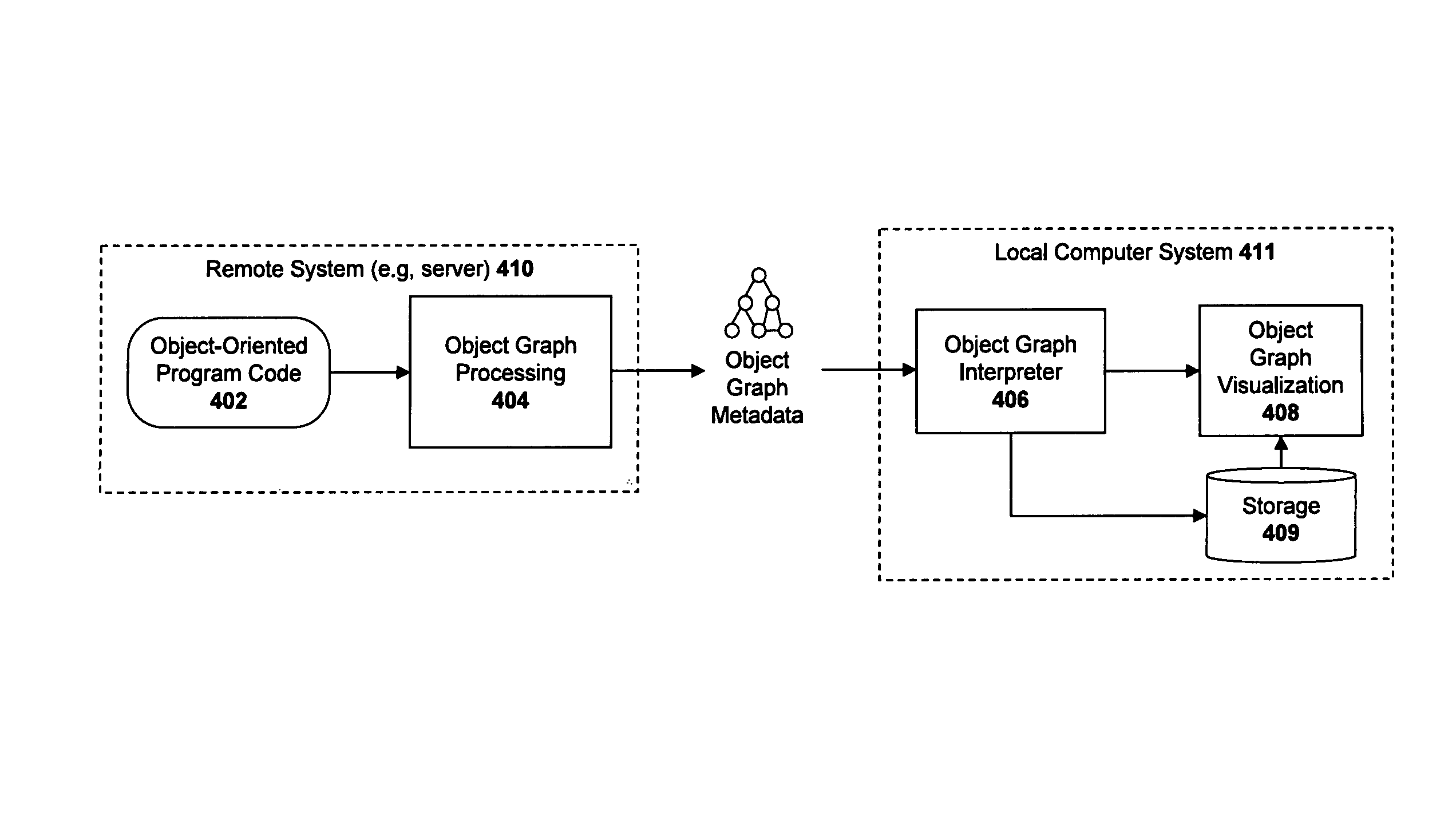
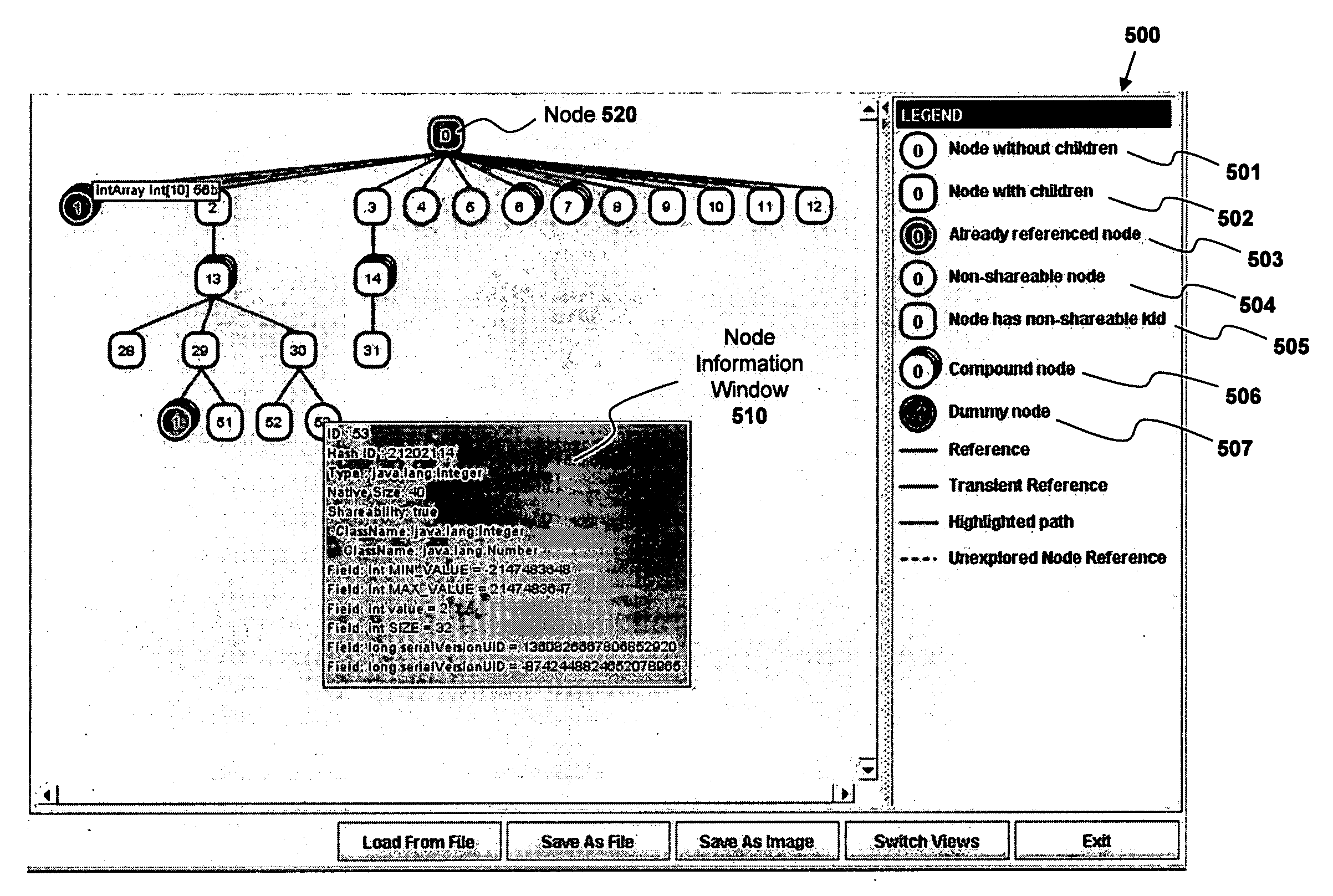
Graphical user interface system and method for presenting objects
ActiveUS8640086B2Error detection/correctionExecution for user interfacesGraphicsGraphical user interface
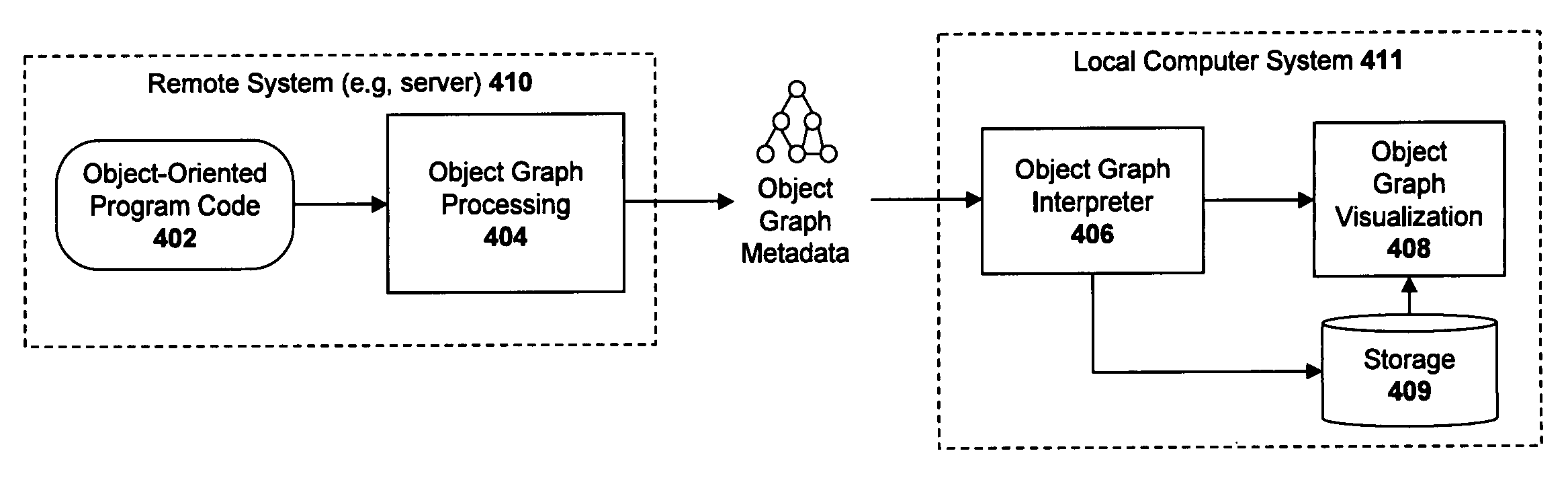
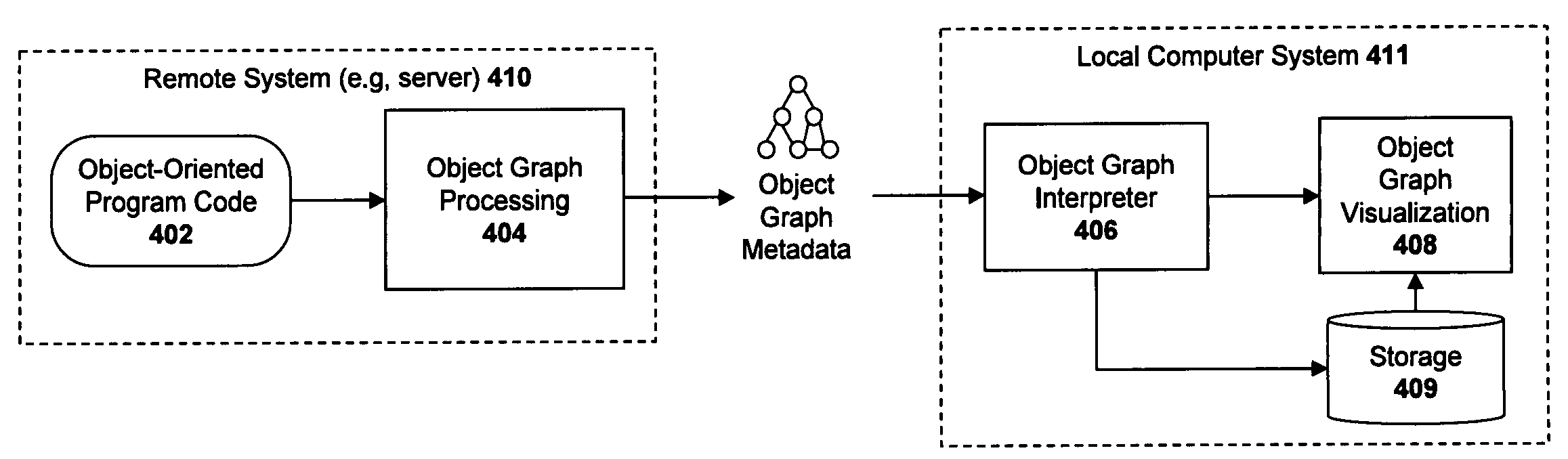
A system and method for visualizing objects within an object network. For example, a computer-implemented method according to one embodiment comprises: receiving object graph data from a remote computing system, the object graph data representing characteristics of objects and relationships between objects in object-oriented program code executed on the remote computer system; interpreting the object graph data to determine one or more characteristics of each of the objects; and generating a graphical user interface (“GUI”) comprised of a plurality of graphical nodes arranged in a graph structure, each of the nodes representing one of the objects and the graph structure representing the relationships between the objects, wherein the graphical nodes are rendered with graphical characteristics representing characteristics of the objects which they represent, the graphical characteristics including at least a color and a shape.
Owner:SAP AG
System, method and software for creating or maintaining distributed transparent persistence of complex data objects and their data relationships
InactiveUS20030046266A1Digital data processing detailsObject oriented databasesApplication softwareByte
The invention provides systems, methods and software for creating or maintaining distributed transparent persistence of complex data objects and associated data stores. In one aspect, the invention also relates to an application programming object capable of creating or maintaining distributed transparent persistence of data objects or data object graphs without the necessity of inserting any byte codes or modification of the object graph. Virtually any java object or object praph can be transparently persisted. Further, copies of a data graph or of a portion of the data graph can be automatically reconciled and changes persisted without any persistence coding in the object model.creating.
Owner:MULLINS WARD +1
Graphical user interface system and method for presenting objects
ActiveUS20080163124A1Error detection/correctionExecution for user interfacesGraphicsGraphical user interface
A system and method for visualizing objects within an object network. For example, a computer-implemented method according to one embodiment comprises: receiving object graph data from a remote computing system, the object graph data representing characteristics of objects and relationships between objects in object-oriented program code executed on the remote computer system; interpreting the object graph data to determine one or more characteristics of each of the objects; and generating a graphical user interface (“GUI”) comprised of a plurality of graphical nodes arranged in a graph structure, each of the nodes representing one of the objects and the graph structure representing the relationships between the objects, wherein the graphical nodes are rendered with graphical characteristics representing characteristics of the objects which they represent, the graphical characteristics including at least a color and a shape.
Owner:SAP AG
Displayable presentation page and SQL searchable relational data source implementation of a system, method and software for creating or maintaining distributed transparent persistence of complex data objects and their data relationships
The invention provides systems, methods and software for creating or maintaining distributed transparent persistence of complex data objects and associated data stores. In one aspect, the invention also relates to an application programming object capable of creating or maintaining distributed transparent persistence of data objects or data object graphs without the necessity of inserting any byte codes or modification of the object graph. Virtually any java object or object praph can be transparently persisted. Further, copies of a data graph or of a portion of the data graph can be automatically reconciled and changes persisted without any persistence coding in the object model.
Owner:THOUGHT
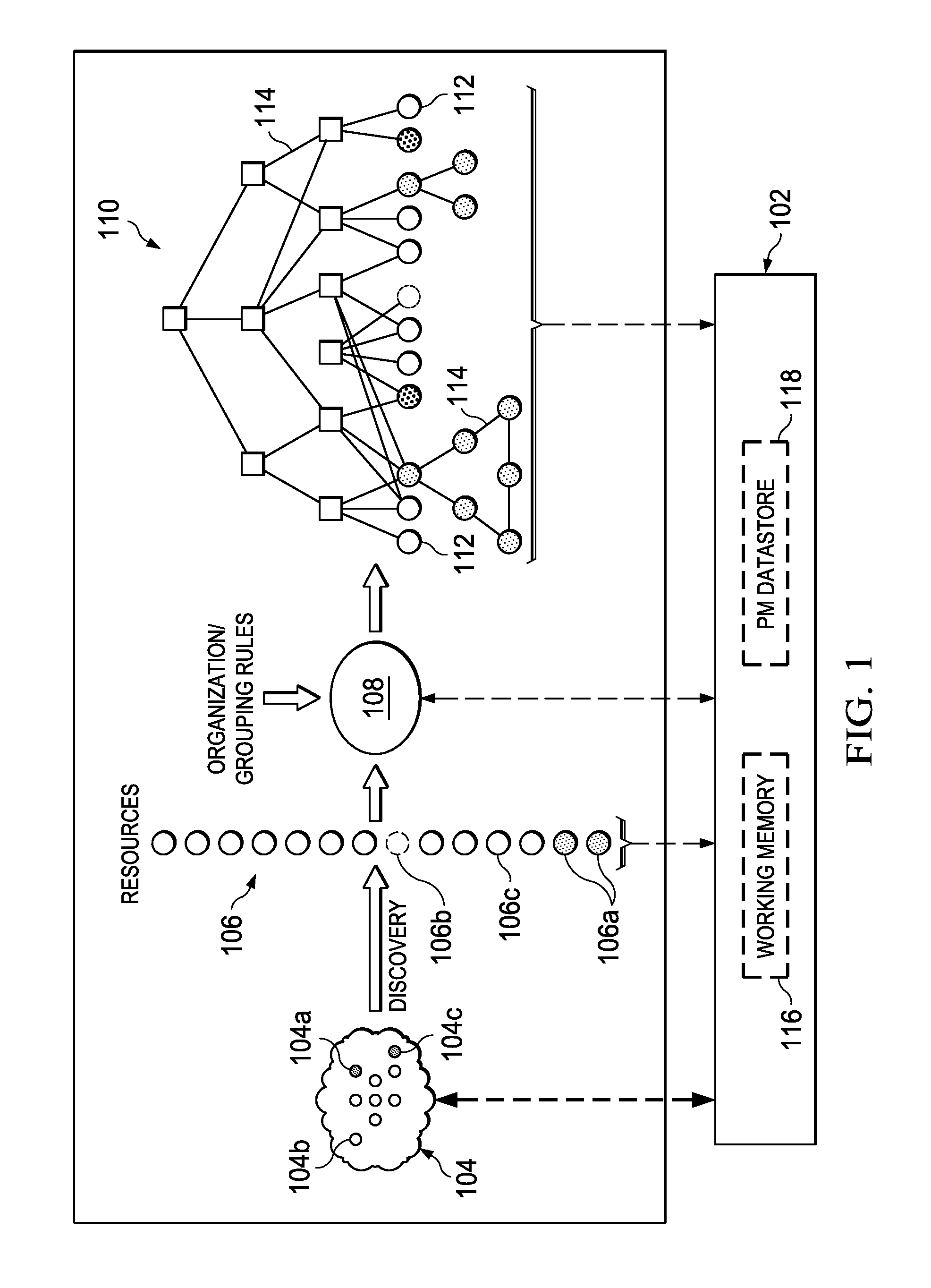
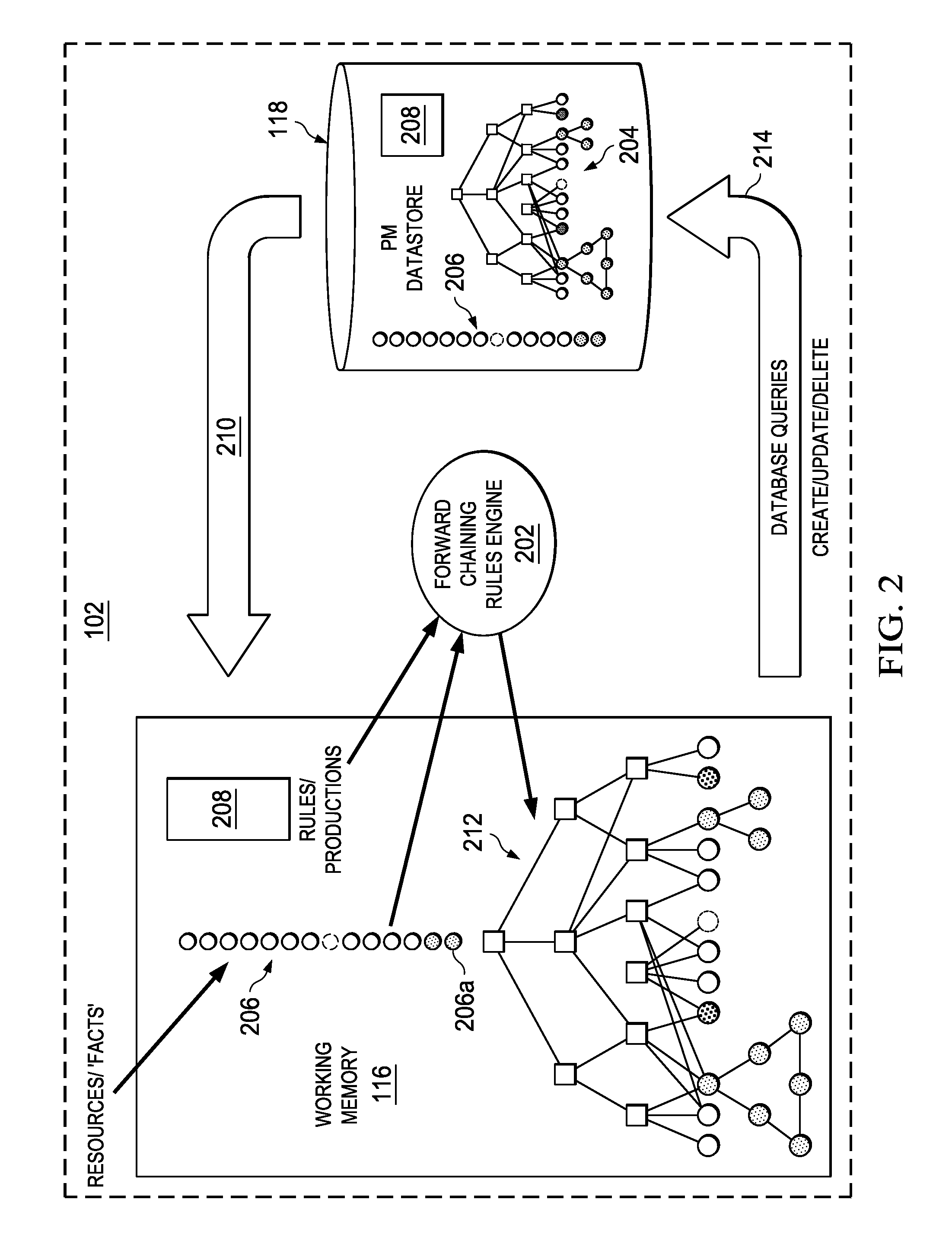
Creation and Revision of Network Object Graph Topology for a Network Performance Management System
InactiveUS20110320394A1Digital data information retrievalDigital data processing detailsManagement systemObject graph
An embodiment of the invention comprises, providing an initial object graph to a database, the initial object graph being generated by applying a set of rules to resources included in a resource set at a specified time, or by revising a previous object graph at the previous time, the resource set at the specified time comprising an initial resource set. The method includes providing the initial object graph to a working memory, maintained in separation from the database; discovering a changed fact associated with one of the resources of the initial resource set; and upon discovering the changed fact, determining modifications required by the changed fact to the initial object graph. If modifications are required, the initial object graph is revised in the working memory to include such modifications. The same revisions are then made to the initial object graph in the system database.
Owner:IBM CORP
Session bean implementation of a system, method and software for creating or maintaining distributed transparent persistence of complex data objects and their data relationships
InactiveUS7167862B2Data processing applicationsSpecial data processing applicationsData graphTheoretical computer science
The invention provides systems, methods and software for creating or maintaining distributed transparent persistence of complex data objects and associated data stores. In one aspect, the invention also relates to an application programming object capable of creating or maintaining distributed transparent persistence of data objects or data object graphs without the necessity of inserting any byte codes or modification of the object graph. Virtually any java object or object graph can be transparently persisted. Further, copies of a data graph or of a portion of the data graph can be automatically reconciled and changes persisted without any persistence coding in the object model.
Owner:THOUGHT
Displayable presentation page and SQL searchable relational data source implementation of a system, method and software for creating or maintaining distributed transparent persistence of complex data objects and their data relationships
InactiveUS20040177093A1Provides reusabilityData processing applicationsObject oriented databasesData sourceApplication software
The invention provides systems, methods and software for creating or maintaining distributed transparent persistence of complex data objects and associated data stores. In one aspect, the invention also relates to an application programming object capable of creating or maintaining distributed transparent persistence of data objects or data object graphs without the necessity of inserting any byte codes or modification of the object graph. Virtually any java object or object praph can be transparently persisted. Further, copies of a data graph or of a portion of the data graph can be automatically reconciled and changes persisted without any persistence coding in the object model.
Owner:THOUGHT
Transformer excitation inrush current and fault differential current recognition method based on Hausdorff distance algorithm
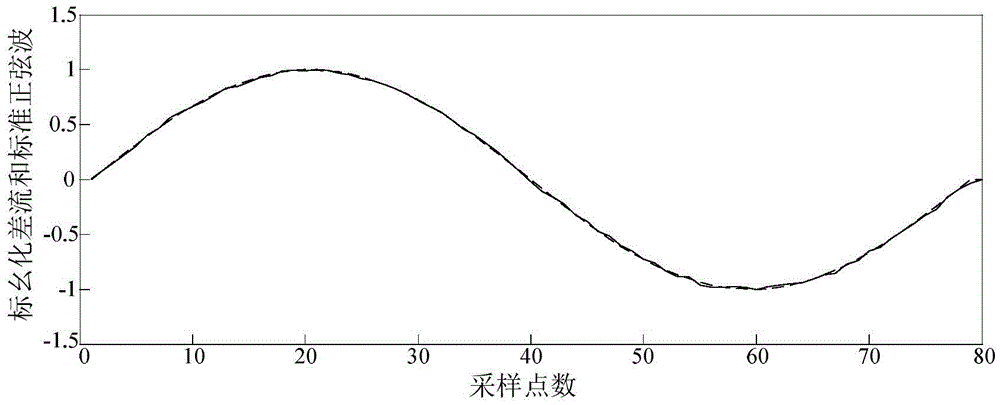
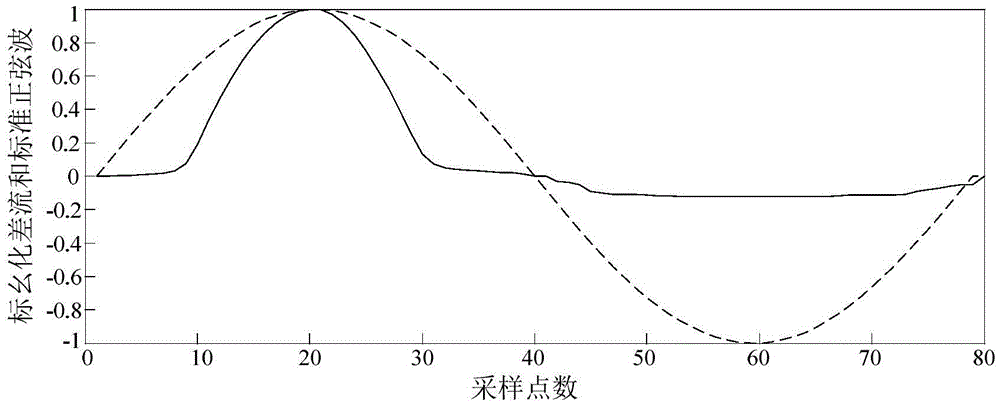
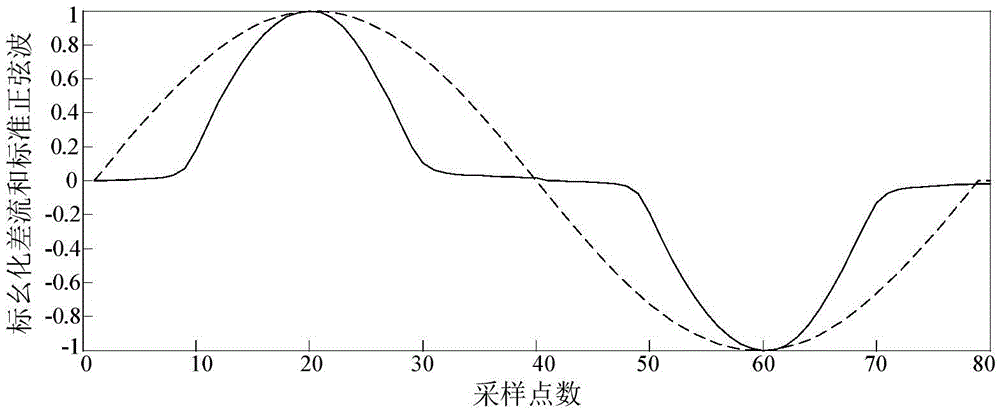
ActiveCN105529688AFlexible settingsIncrease speedEmergency protective circuit arrangementsElectrical testingObject graphElectrical current
The invention provides a transformer excitation inrush current and fault differential current recognition method based on a Hausdorff distance algorithm. The transformer excitation inrush current and fault differential current recognition method comprises the steps of: acquiring secondary currents of current transformers at two differential protection sides of a transformer on each cyclic wave N point, and form a differential current signal sequence I; judging whether a value of the differential current signal sequence I exceeds a setting valve of a differential protection starting component, and starting a criterion disclosed by the invention for distinguishing a fault differential current and an excitation inrush current if the value exceeds the setting value differential protection starting component; judging and acquiring an extreme value of the differential current signal sequence I by adopting a 1 / 4 cyclic wave data window, regarding a differential sequence A after per-unit treatment as an edge feature point of a Hausdorff distance algorithm object graph, regarding a standard sine sequence B with amplitude being 1 as an edge feature point of a Hausdorff distance algorithm template graph, comparing an Hi value with a set Hausdorff distance threshold value Hset, and conducting protection action if the Hi value is less than the threshold value; and blocking protection if the Hi value is greater than the threshold value. The transformer excitation inrush current and fault differential current recognition method is used for directly judging difference of waveform pattern overall features of inrush currents including symmetric inrush currents, and ensures correct action of transformer differential protection.
Owner:CHINA THREE GORGES UNIV
System and method for measuring memory consumption differences between objects within an object-oriented programming environment
A computer-implemented system and method are described for measuring the memory consumption difference between two objects in an object-oriented programming environment. For example, one embodiment of a method comprises: analyzing relationships between objects within a network of objects to determine an object network structure; generating object graph data representing the object network structure, the object graph data including nodes representing objects and arcs representing relationships between objects; removing all incoming arcs to each of two nodes; building resulting sub-graphs for each of the two nodes; summing the memory consumed by each of the sub-graphs of the two nodes; and subtracting the memory amounts consumed by each of the sub-graphs to determine the memory consumption different between the two nodes.
Owner:SAP AG
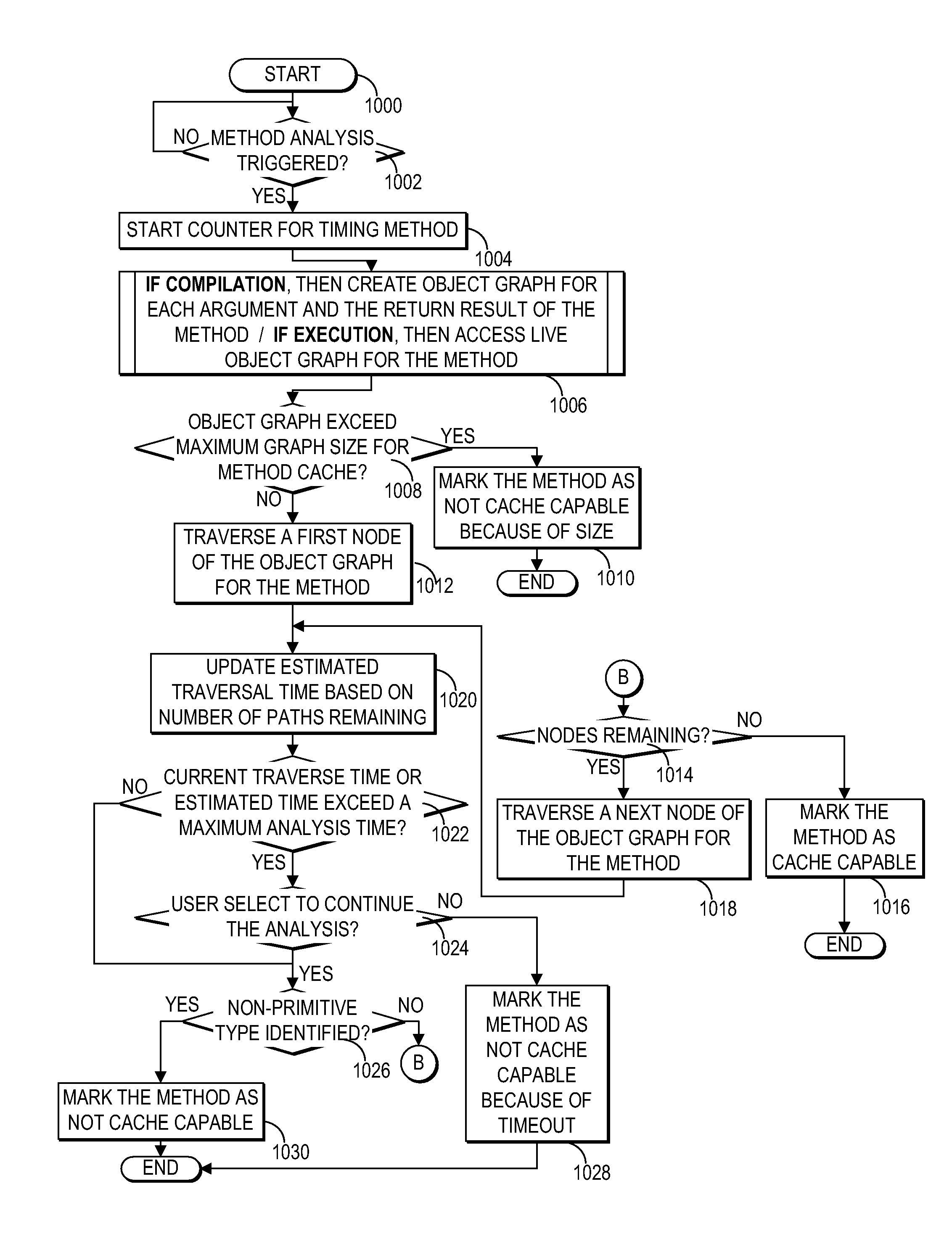
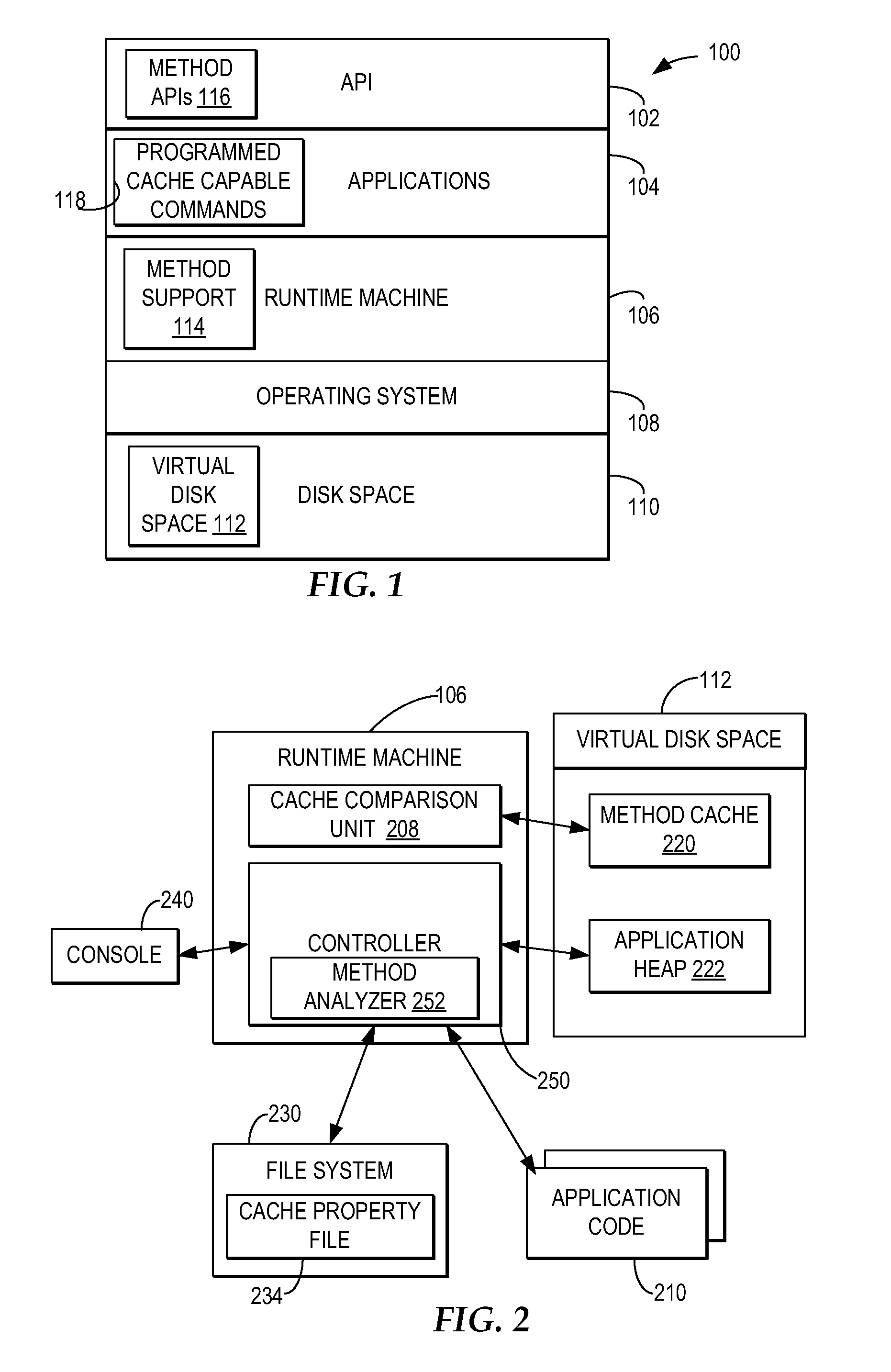
Runtime machine analysis of applications to select methods suitable for method level caching
A runtime machine manages a selected disk space allocated to the runtime machine by the operating system and manages a separate method cache within the selected virtual disk space. The runtime machine controls caching within the method cache of a separate result of at least one method of the application marked as cache capable. For a next instance of the method detected by the runtime machine, the runtime machine accesses the cached separate result of the method in lieu of executing the method again. The runtime machine marks a method as cache capable by analyzing the types of objects within the argument object graph and result object graph of a method. If the runtime machine detects only primitive type objects, then the runtime machine marks the method so that the result of the method will be stored in the method cache.
Owner:INT BUSINESS MASCH CORP
Image segmentation method and device, computer equipment and storage medium
ActiveCN109492608AAchieve segmentationQuick fixImage enhancementImage analysisReference imageImage segmentation
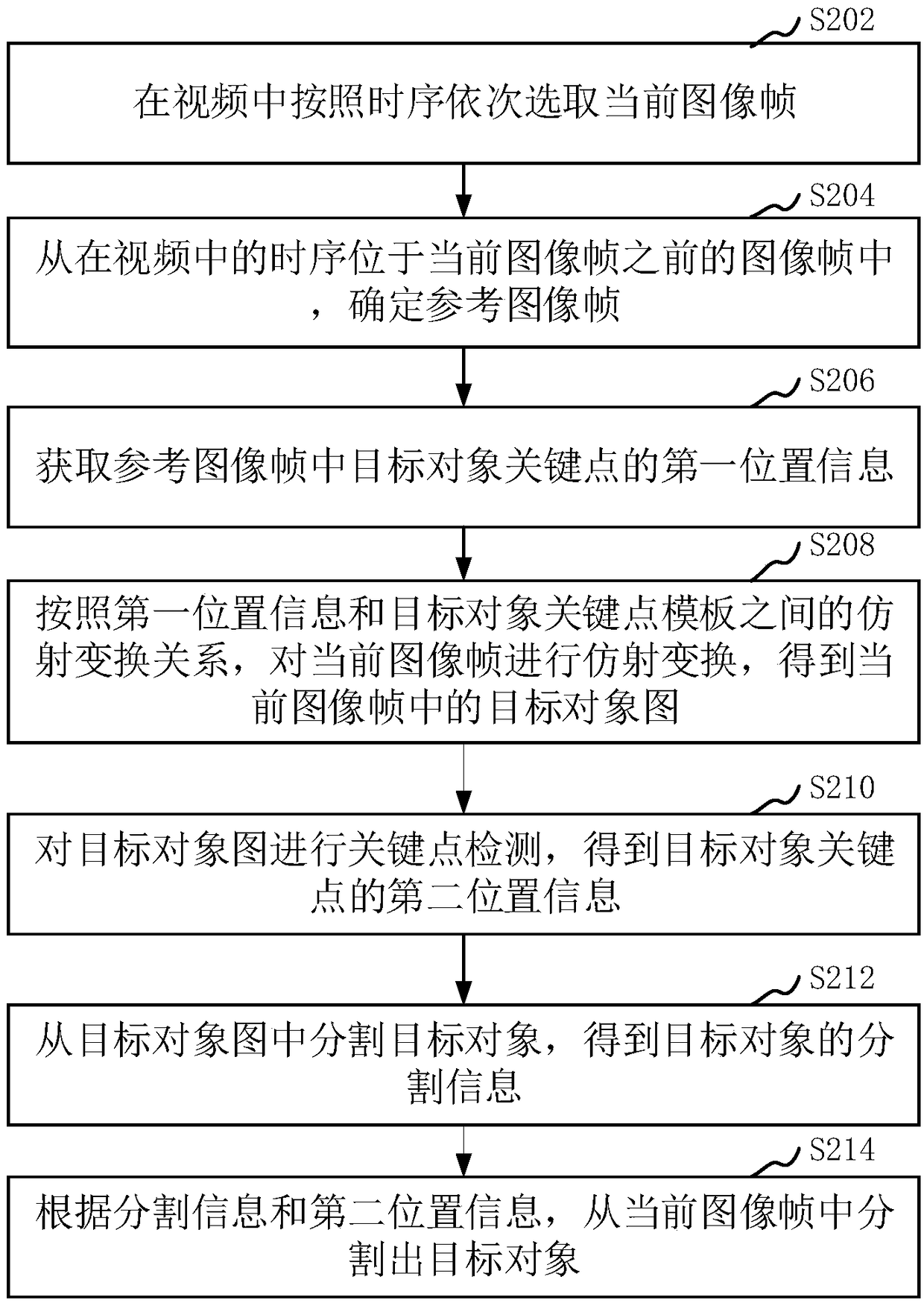
The invention relates to an image segmentation method and device, computer equipment and a storage medium. The method comprises the steps of sequentially selecting current image frames in a video according to a time sequence; determining a reference image frame from an image frame in which a timing sequence in the video is located in front of a current image frame; obtaining first position information of a target object key point in the reference image frame; affine transformation is carried out on the current image frame by referring to an affine transformation relation between the first position information and a target object key point template to obtain a target object graph of the current image frame; performing key point detection on the target object graph to obtain second positioninformation of a key point of the target object; segmenting a target object from the target object graph to obtain segmentation information of the target object; and segmenting the target object fromthe current image frame according to the segmentation information and the second position information. According to the scheme, the calculated amount is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Container-based architecture for simulation of entities in a time domain
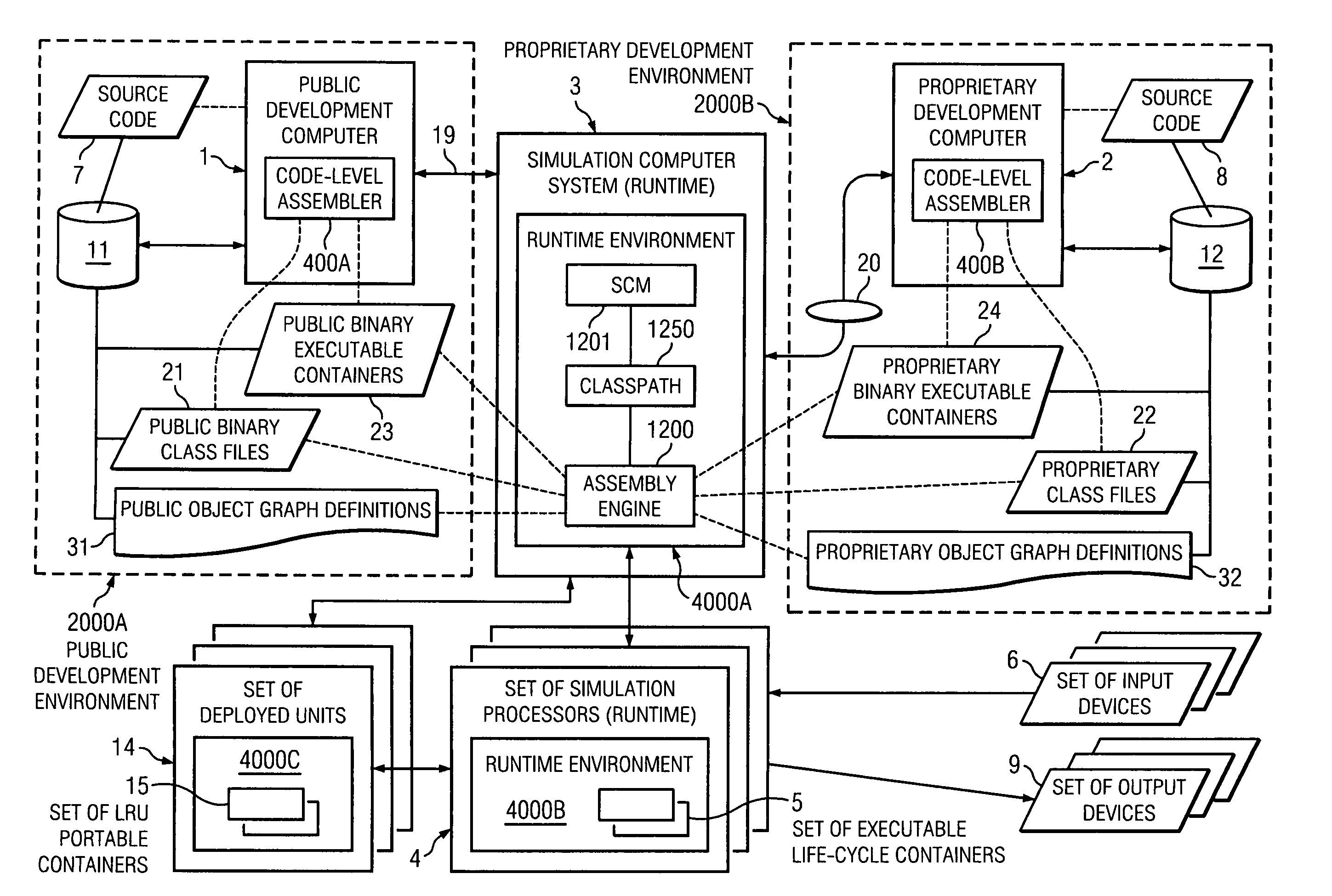
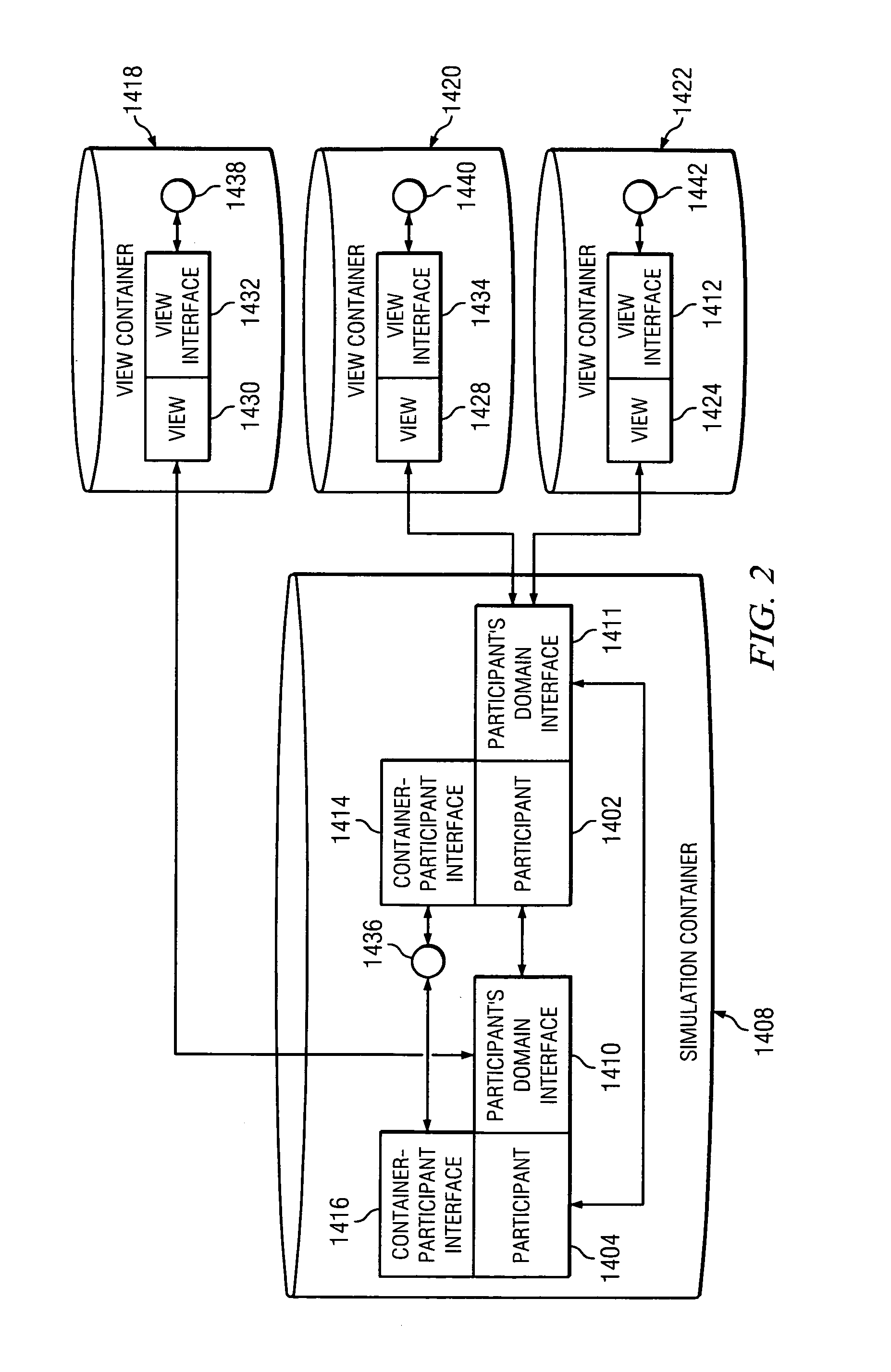
ActiveUS20120117533A1Design optimisation/simulationSpecial data processing applicationsExtensibilityCOLA (software architecture)
The present invention relates generally to a software architecture for simulation of physical entities. The invention provides an object-oriented container-based framework architecture for simulator implementations, methods, and objects in a time domain on a distributed computer network and in field deployed units. The invention further provides an interface system and a plug-in definition which allows compartmentalization of participants in the container and easy extensibility of the system. A hierarchy of life-cycle containers having contained objects is disclosed. An object graph description is used by an assembly engine to construct an executable object graph including the hierarchy of life-cycle containers. Life-cycle containers can be implemented as LRU portable containers for field deployed units.
Owner:ZEDASOFT
Synchronization of cms data to mobile device storage
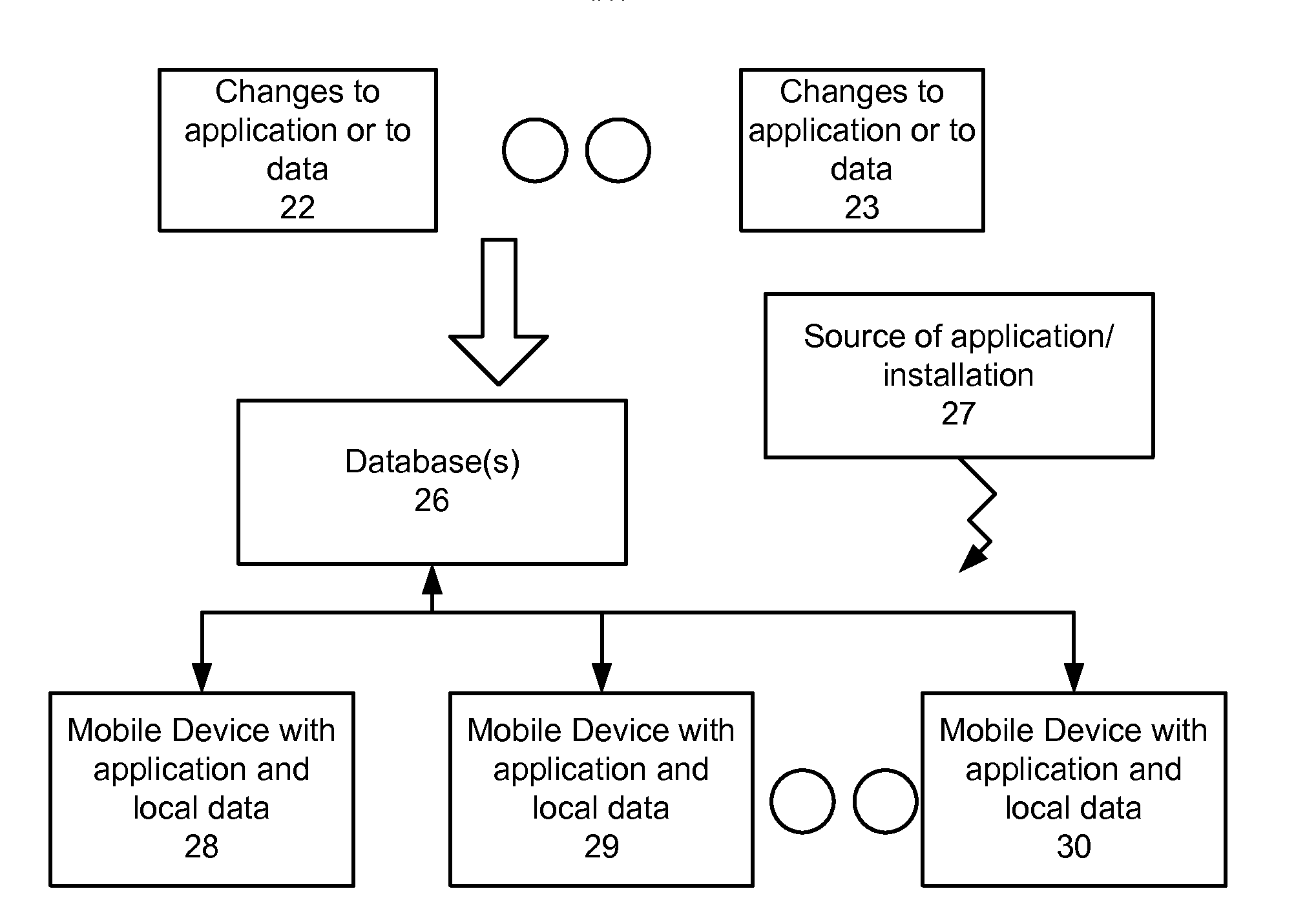
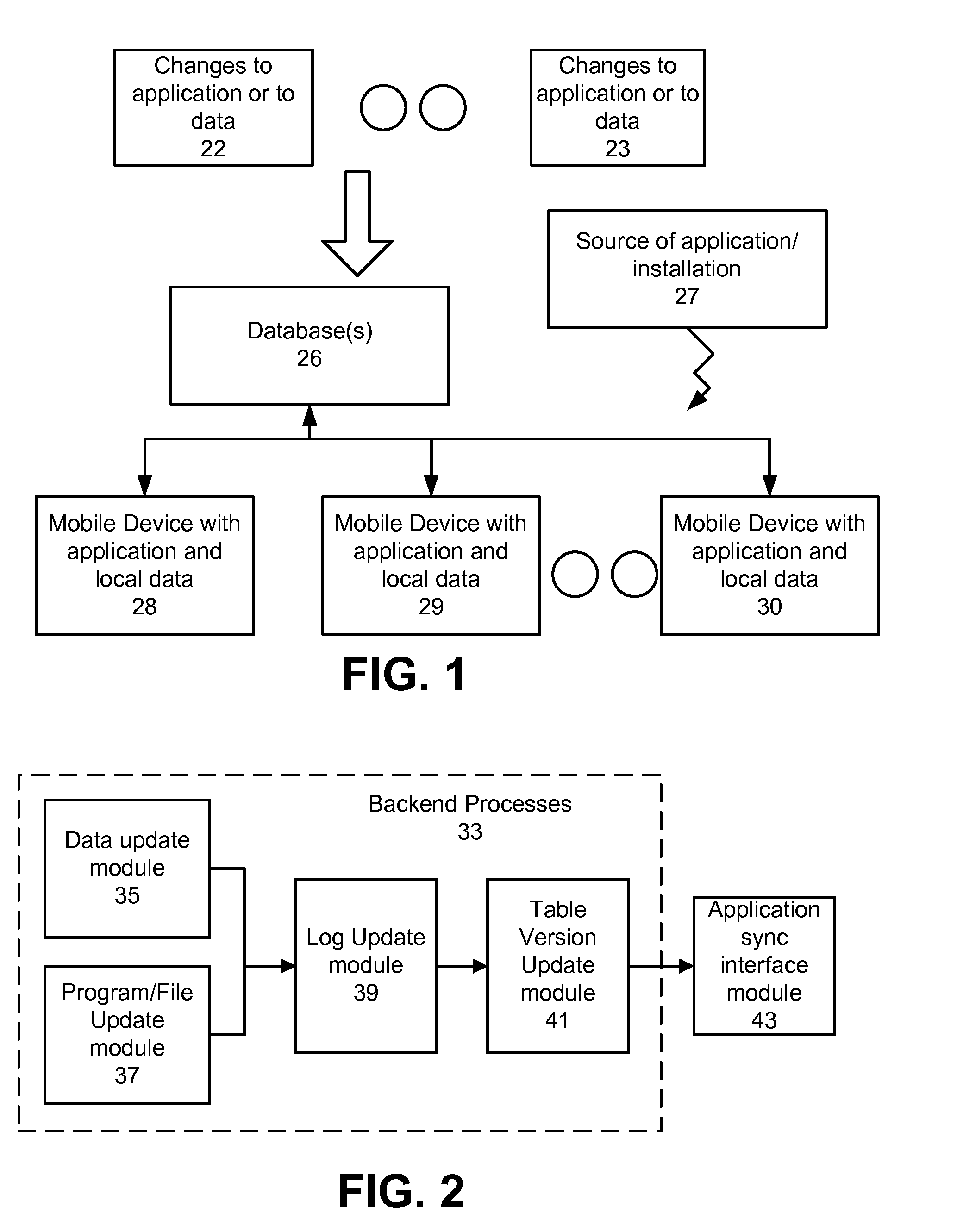
InactiveUS20140258234A1Improve trustIncrease the difficultyDigital data processing detailsDatabase distribution/replicationData setRelational database
Aspects include systems and methods for synchronizing a remote datastore that includes files and data for use by an application on a remote device, which can be represented on the device in a device-specific format, while the remote data store can have a different data representation, such as a relational database or object graph data model. A server can maintain a unique row identifier for each row in all synchronized tables and an update log table that has rows with the unique row identifiers for changed rows (inserted, updated or deleted), for each insert, update, or delete operation and a current update version that reflects the last change to that row. An update request from a device can comprise identifiers for a (sub)set of the data. The update log table can be used to prepare an update package containing this data.
Owner:PRIOR ARC INC
Attributing memory usage by individual software components
InactiveUS20070261043A1Data processing applicationsError detection/correctionPattern matchingTheoretical computer science
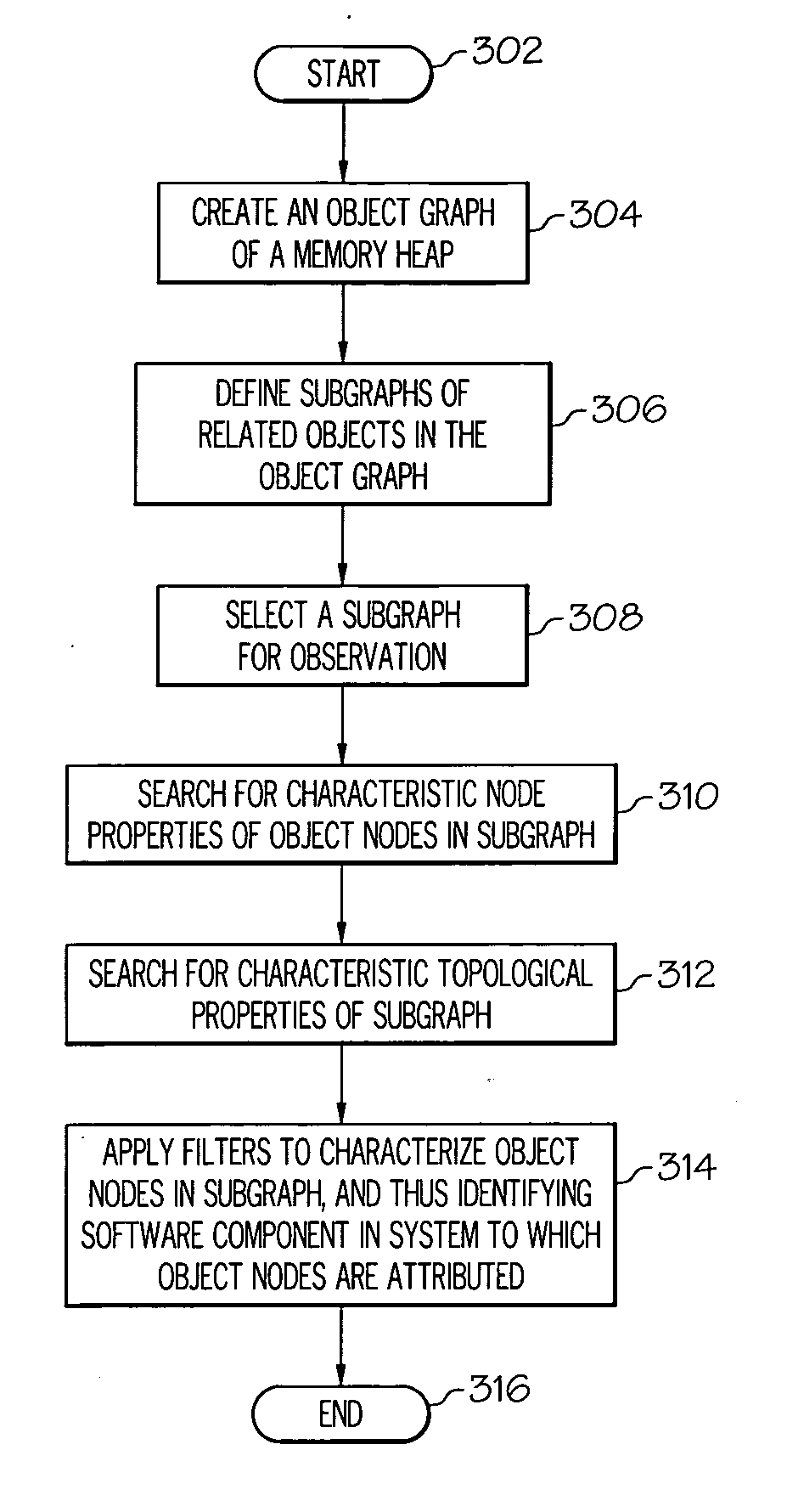
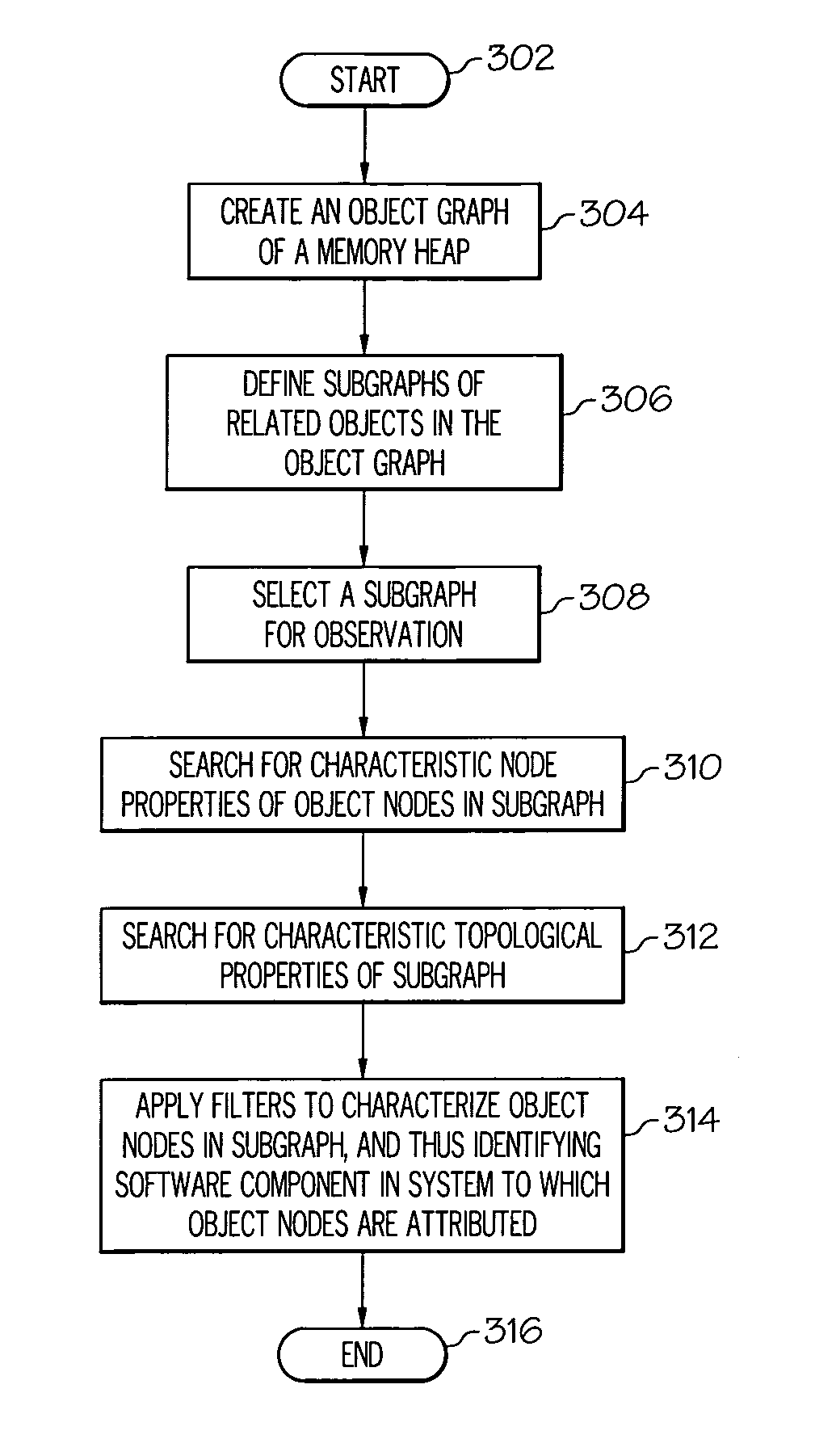
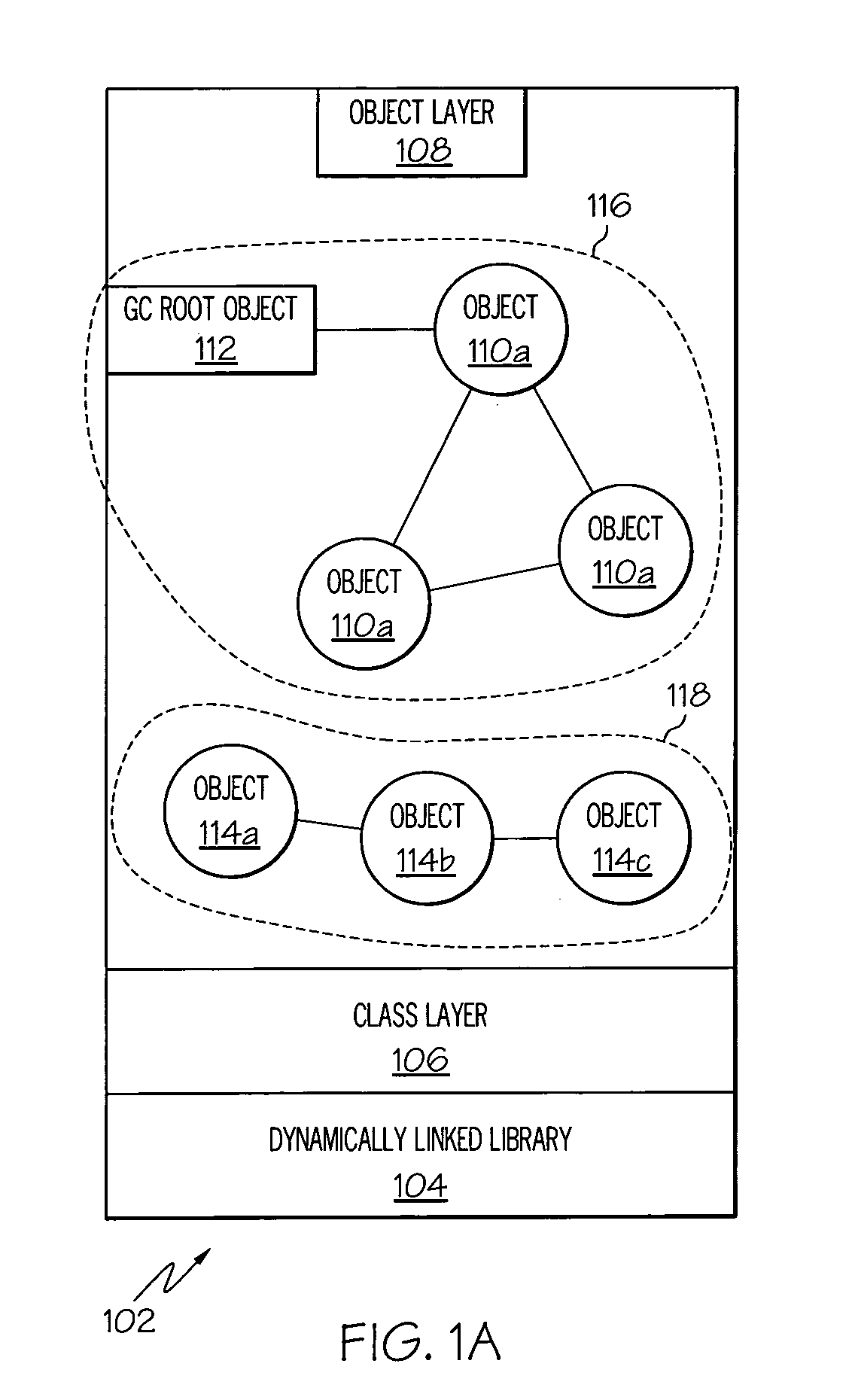
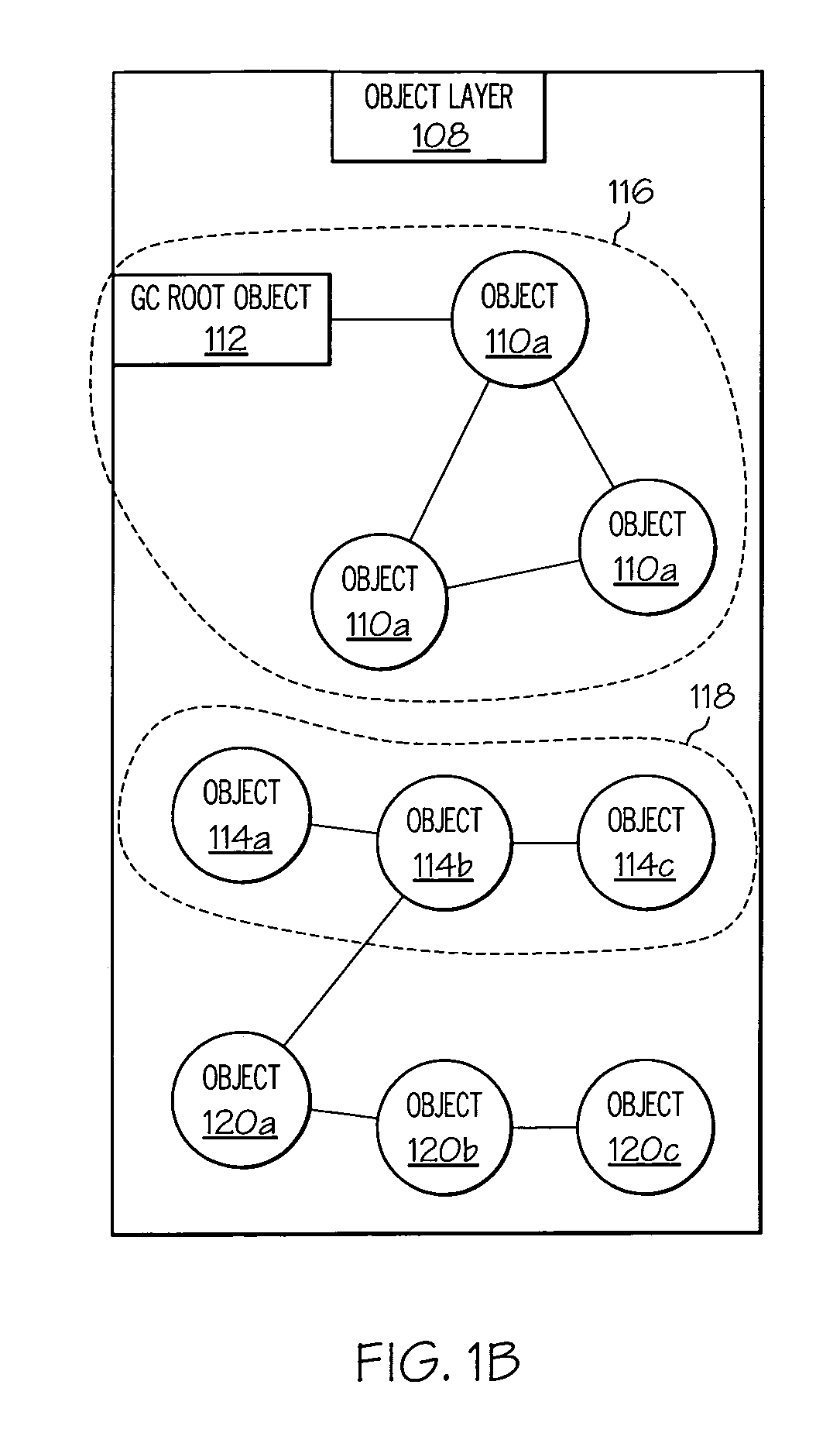
A method, system and computer-usable medium for attributing memory usage are presented. The method includes the steps of creating an object graph of a portion of a memory heap, wherein the object graph includes nodes that represent objects and associated properties of the objects, and wherein the object graph includes connectors that represent relationships between the objects in the memory heap; observing nodes in one or more subgraphs of the object graph, wherein the nodes represent objects that are selected for observation by a pre-determined criteria; searching for characteristic node properties of nodes that are sampled, from the subgraph, for observation; searching for characteristic topological properties of the subgraph that sampled nodes participate in; and applying a set of pre-determined domain-specific pattern matching filters to the node characteristic properties and the topological characteristic properties to attribute memory usage to a proper software component in a system.
Owner:IBM CORP
Customized recommendation method based on graphs
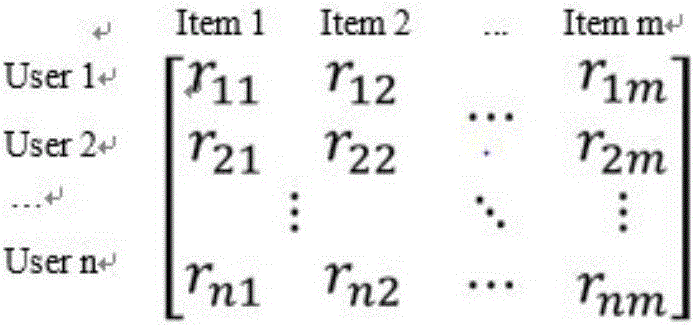
The invention provides a customized recommendation method based on graphs and can effectively reduce influence of sparsity on the recommendation effect. According to the method, a first step, a hidden meaning model is utilized to calculate historical scoring records of users to acquire hidden relationships among users and among objects; a second step, similarity among the users is calculated by utilizing the hidden relationships acquired in the first step, similarity among the objects is calculated, and a user graph and an object graph are constructed for the similar users and the similar objects; a third step, a user-object graph model is constructed by utilizing a user graph model and an object graph model acquired in the second step and a bipartite graph of the users and the objects acquired through utilizing the historical scoring records of the users; and a fourth step, the access probability of objects without scoring record of each user is ordered in a descending mode by utilizing a random walk personalrank algorithm, and front N objects are acquired to form a recommendation list for recommendation to the users.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Business management system
InactiveUS20130238384A1Reduce delaysReduce errorsVisual/graphical programmingModel driven codeModel managementEvent trigger
A method, system and computer program product of managing an executable process application based on a BPMN process model, including: Receiving a BPMN process model; Parsing the process model to an process model object graph; Validating the process model dependent on a predetermined set of validation rules; Identifying start events in the process model; Providing an event handler for each start event based on a start event trigger comprised in the process model; Generating an executable process application based on the process model object graph.
Owner:BARIUM
Method and system for syncing data structures
ActiveUS20160055226A1Powerful and versatile and flexible representation of dataLoss of resourceDigital data information retrievalDigital data processing detailsOperational transformationObject graph
The consistency of a data structure is maintained where changes in the form of atomic operations are requested by more than one user to an object graph containing a plurality of objects. Operational transformations specifying how one atomic operation is transformed against another one are accessed and the object graph is modified with the first and second set of changes by employing the operational transformations on the atomic operations and applying the resulting transformed operations to the object graph. The transformed operations are recorded in a history log. The atomic operations are object operations that create or delete an object of the object graph and / or property operations changing a property of an object. Each operation retains the identifier of the object it acts on and information on each change of the object resulting from the operation. Multi-operation conflicts are resolved by defined conflict resolution events.
Owner:PROJECTWIZARDS
System and method for measuring memory consumption differences between objects within an object-oriented programming environment
A computer-implemented system and method are described for measuring the memory consumption difference between two objects in an object-oriented programming environment. For example, one embodiment of a method comprises: analyzing relationships between objects within a network of objects to determine an object network structure; generating object graph data representing the object network structure, the object graph data including nodes representing objects and arcs representing relationships between objects; removing all incoming arcs to each of two nodes; building resulting sub-graphs for each of the two nodes; summing the memory consumed by each of the sub-graphs of the two nodes; and subtracting the memory amounts consumed by each of the sub-graphs to determine the memory consumption different between the two nodes.
Owner:SAP AG
Image cooperative segmentation method based on salient image fusion
ActiveCN109448015AOvercome the disadvantage of not being able to reflect the semantic features of the regionReduce deletionImage enhancementImage analysisPattern recognitionImaging processing
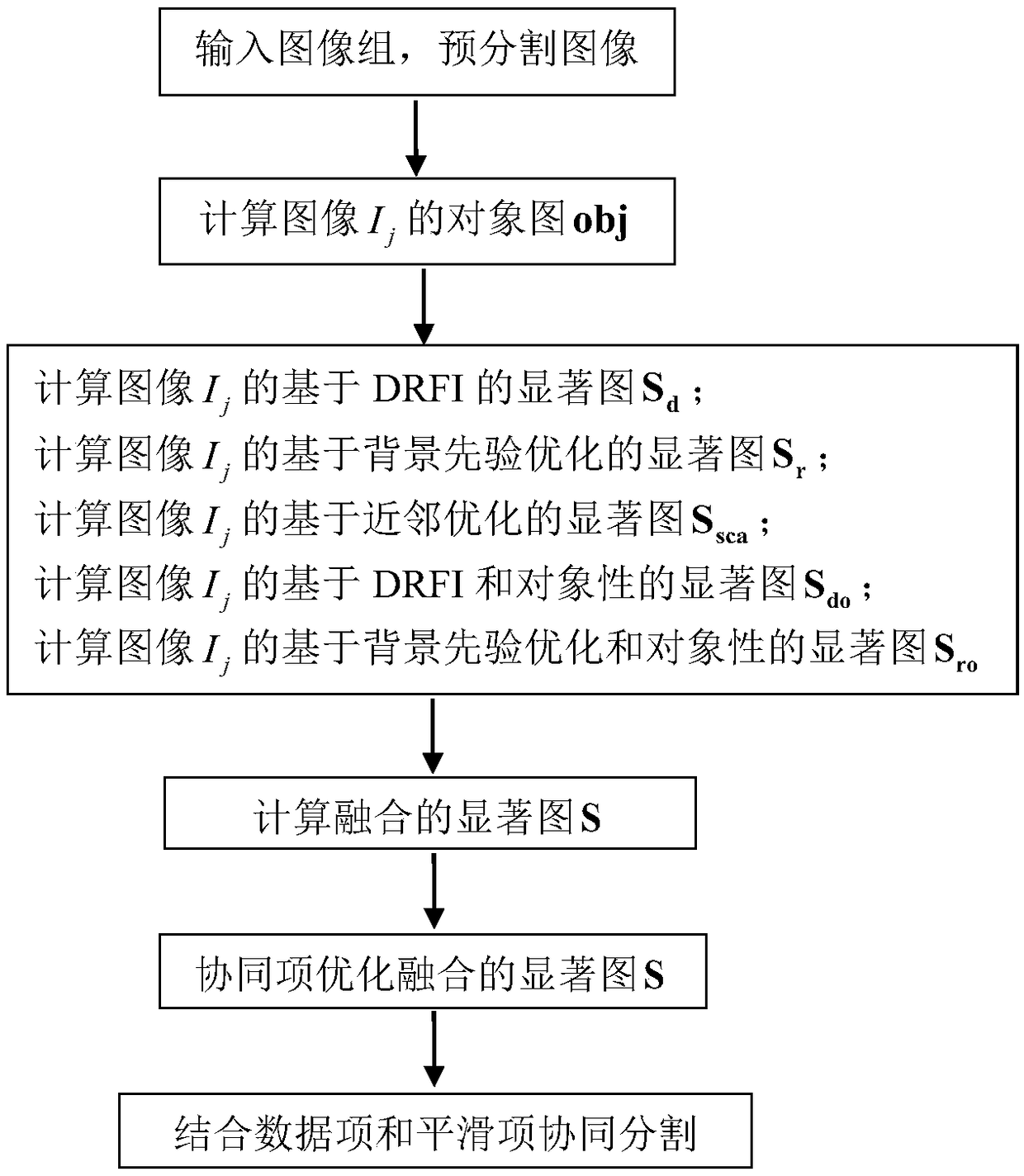
The invention relates to the technical field of image processing, and relates to an image cooperative segmentation method based on salient image fusion, comprising the steps of inputting an image group, pre-segmenting an image; calculating an object graph obj of the image Ij; calculating a DRFI-based saliency map Sd of the image Ij, calculating a saliency map Sr based on background prior optimization of the image Ij, calculating a saliency map Ssca based on nearest neighbor optimization of the image Ij, calculating a saliency map Sdo based on DRFI and objectivity of the image Ij, and calculating a saliency map Sro based on background prior optimization and objectivity of the image Ij; calculating a significance graph S of the cooperative computational fusion. By combining with the cooperative segmentation of the data item and the smooth item, the invention overcomes the problems that the foreground object is missing in the segmentation result of the prior art, and the foreground objectcan not be accurately segmented at the boundary.
Owner:HEBEI UNIV OF TECH
Camera parameter obtaining method and device of a vehicle-mounted multi-camera surround view system
ActiveCN109615659AHigh degree of automationImage analysisInternal combustion piston enginesMulti cameraMulti camera calibration
The invention discloses a camera parameter obtaining method of a vehicle-mounted multi-camera surround view system, which comprises the following steps: obtaining a calibration object image collectedby a target camera, the target camera being any one of a plurality of cameras, a preset number of calibration objects being displayed in the calibration object image, and the calibration objects beingchessboards; extracting feature points in the calibration object graph, wherein the feature points are chessboard corner points in the chessboard; obtaining a first coordinate of the feature point onthe calibration object image and a second coordinate of a checkerboard corner point corresponding to the feature point on a checkerboard coordinate system; and inputting the first coordinates and thesecond coordinates into a preset machine model to obtain internal parameters and external parameters of the target camera. The technical problems of low efficiency and low automation degree of a multi-camera calibration process of a vehicle-mounted all-round view system in the prior art are solved. Meanwhile, the invention further discloses a camera parameter obtaining device of the vehicle-mounted multi-camera surround view system.
Owner:CHENGDU CK TECH
Deterministic immutable access elimination for efficient distributed state saves
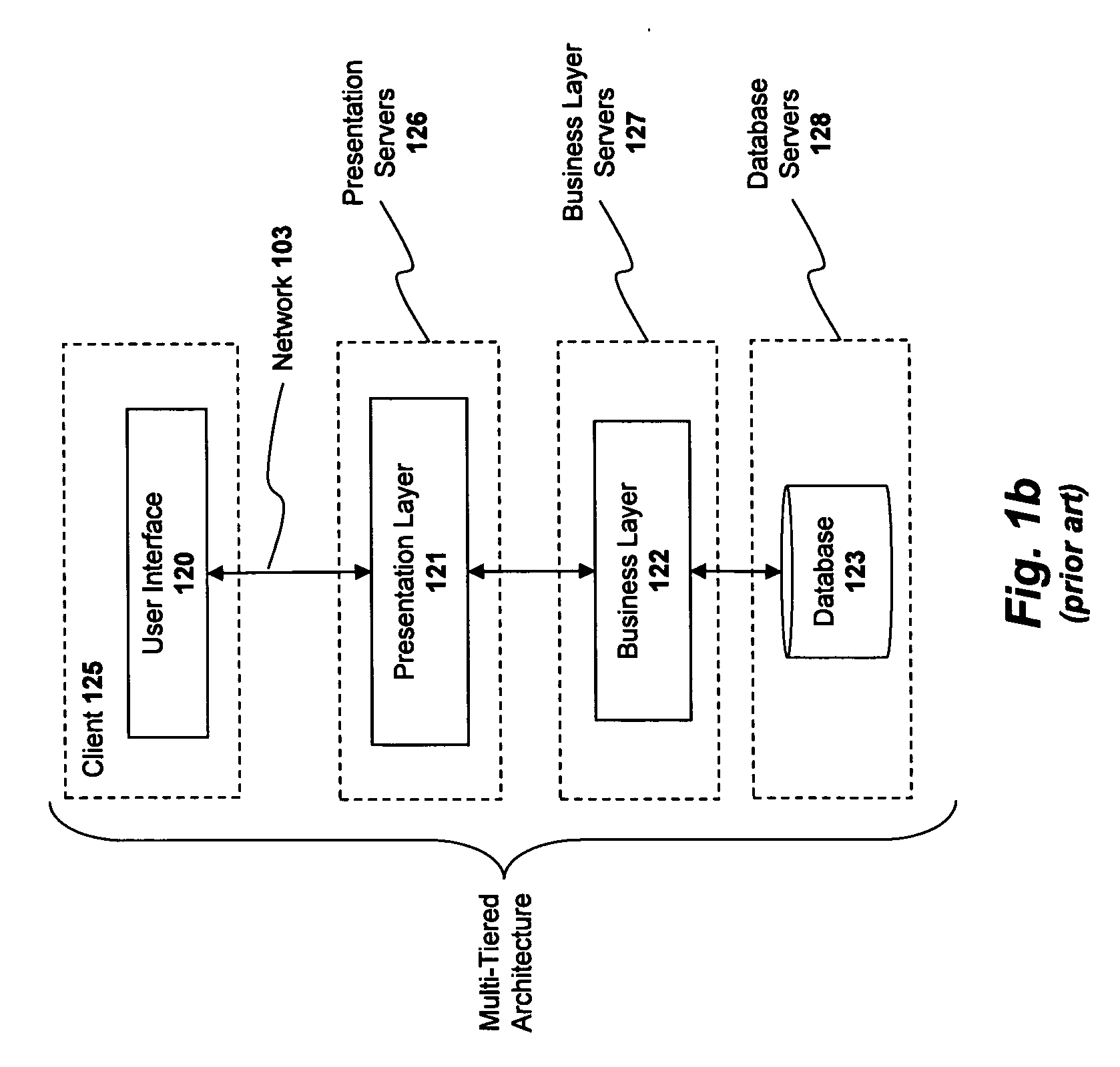
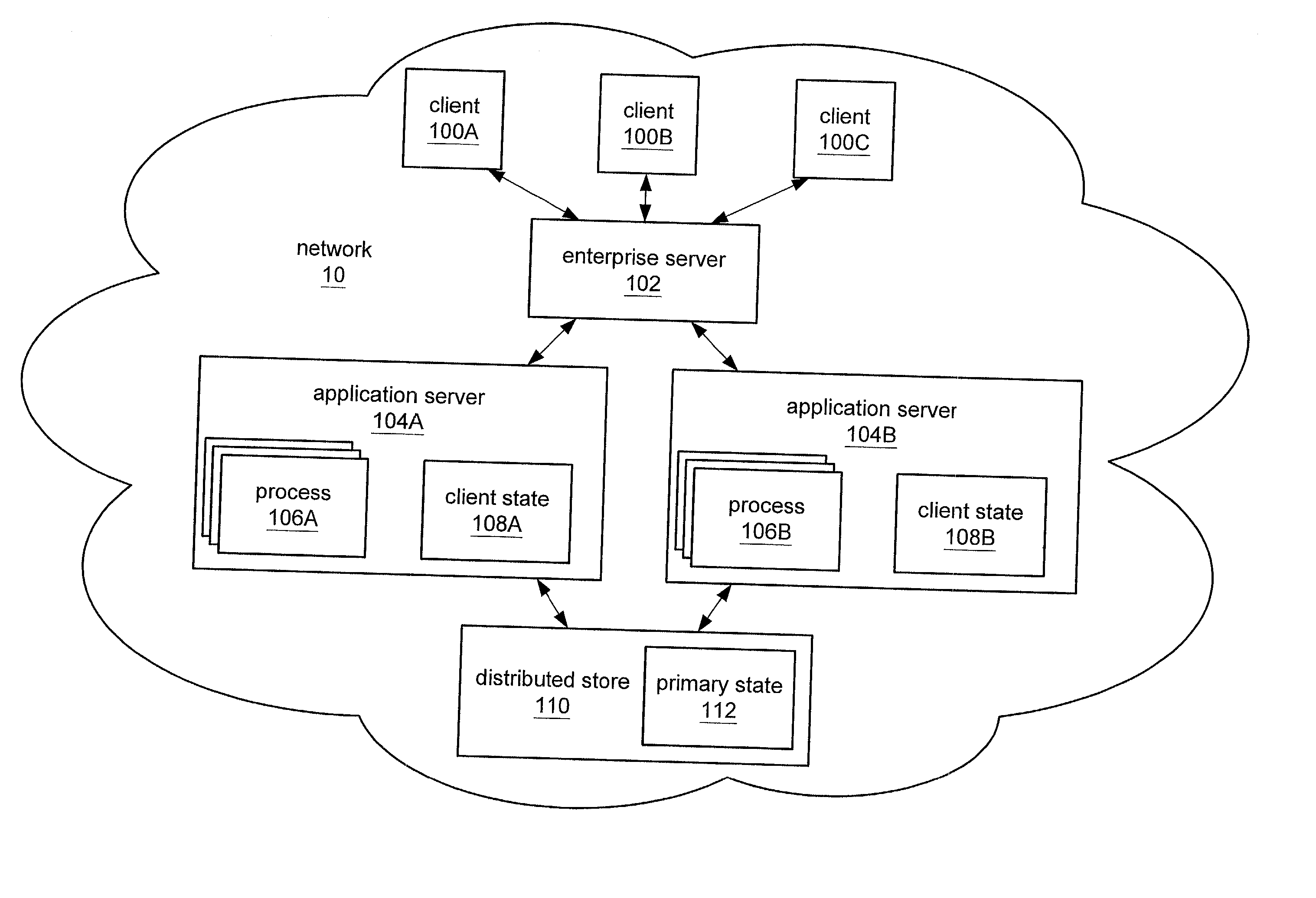
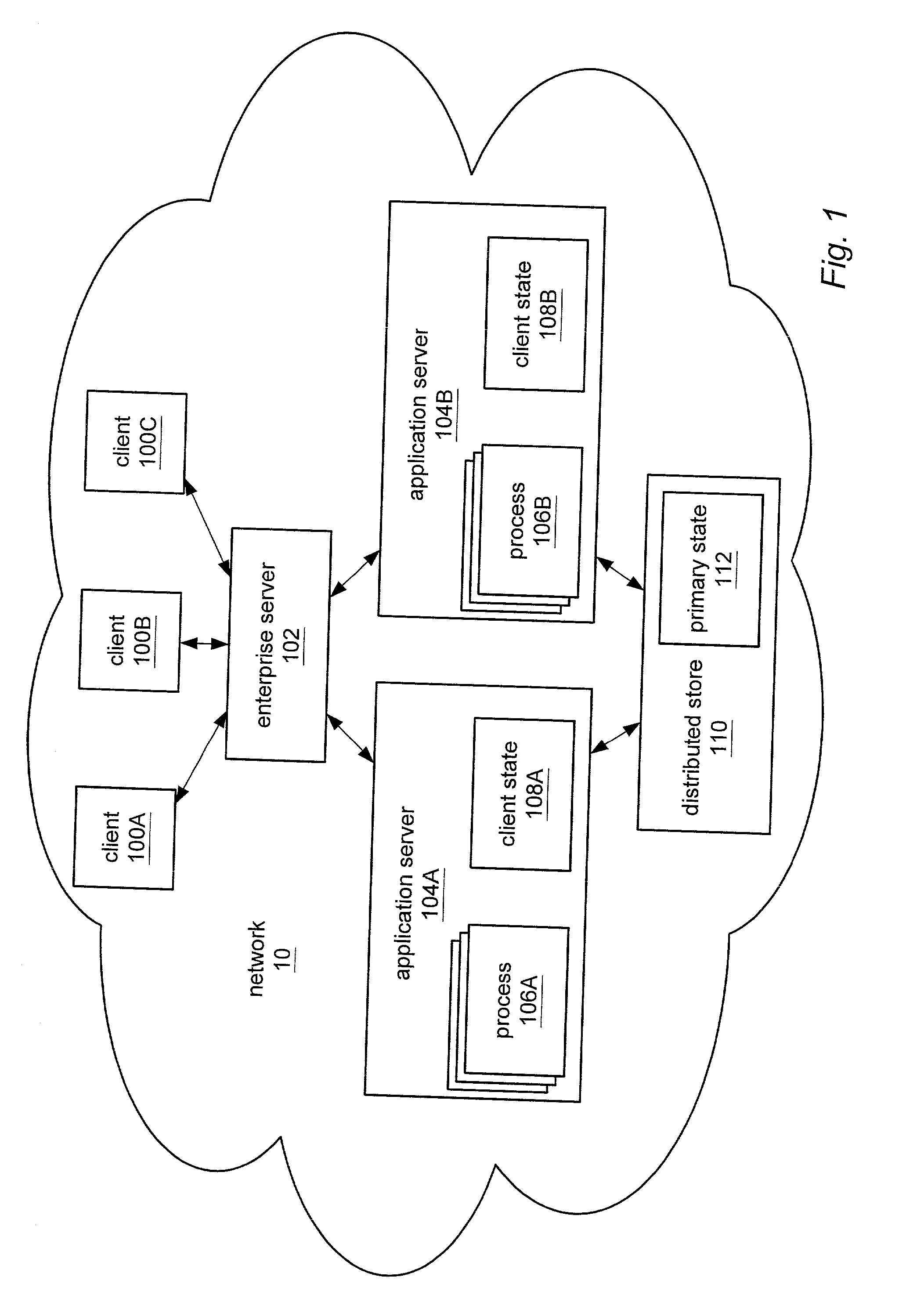
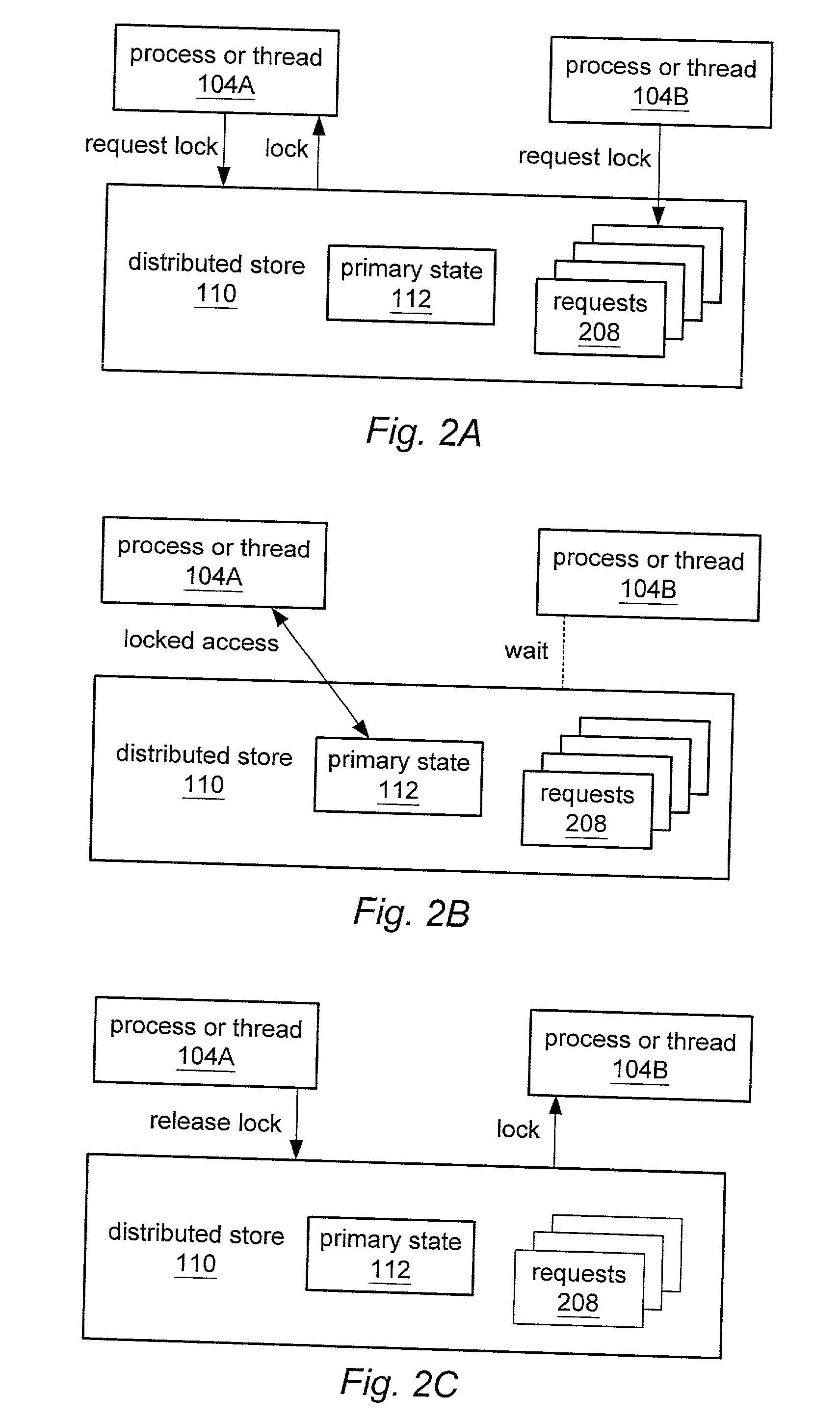
ActiveUS20030167297A1Multiple digital computer combinationsTransmissionApplication serverClient server systems
A client-server system may include a primary state of session data. Application servers may include client states of the session data and may access the primary state. The session data may include attributes. An application server may generate a set of attributes of the session data for synchronizing the primary state with the client state. The set may exclude immutable attributes. In some embodiment the set may further exclude attributes only immutably accessed and / or further exclude attributes that were not accessed. In some embodiments, the application server may use a binary comparison or an object graph comparison of the set of attributes to a benchmark of the client state to determine a subset of the generated set of attributes that are modified. The distributed store may synchronize the primary state with the client state using the generated set of attributes or, in some embodiments, using only the modified attributes.
Owner:ORACLE INT CORP
Attributing memory usage by individual software components
InactiveUS7472132B2Data processing applicationsError detection/correctionPattern matchingTheoretical computer science
A method, system and computer-usable medium for attributing memory usage are presented. The method includes the steps of creating an object graph of a portion of a memory heap, wherein the object graph includes nodes that represent objects and associated properties of the objects, and wherein the object graph includes connectors that represent relationships between the objects in the memory heap; observing nodes in one or more subgraphs of the object graph, wherein the nodes represent objects that are selected for observation by a pre-determined criteria; searching for characteristic node properties of nodes that are sampled, from the subgraph, for observation; searching for characteristic topological properties of the subgraph that sampled nodes participate in; and applying a set of pre-determined domain-specific pattern matching filters to the node characteristic properties and the topological characteristic properties to attribute memory usage to a proper software component in a system.
Owner:INT BUSINESS MASCH CORP
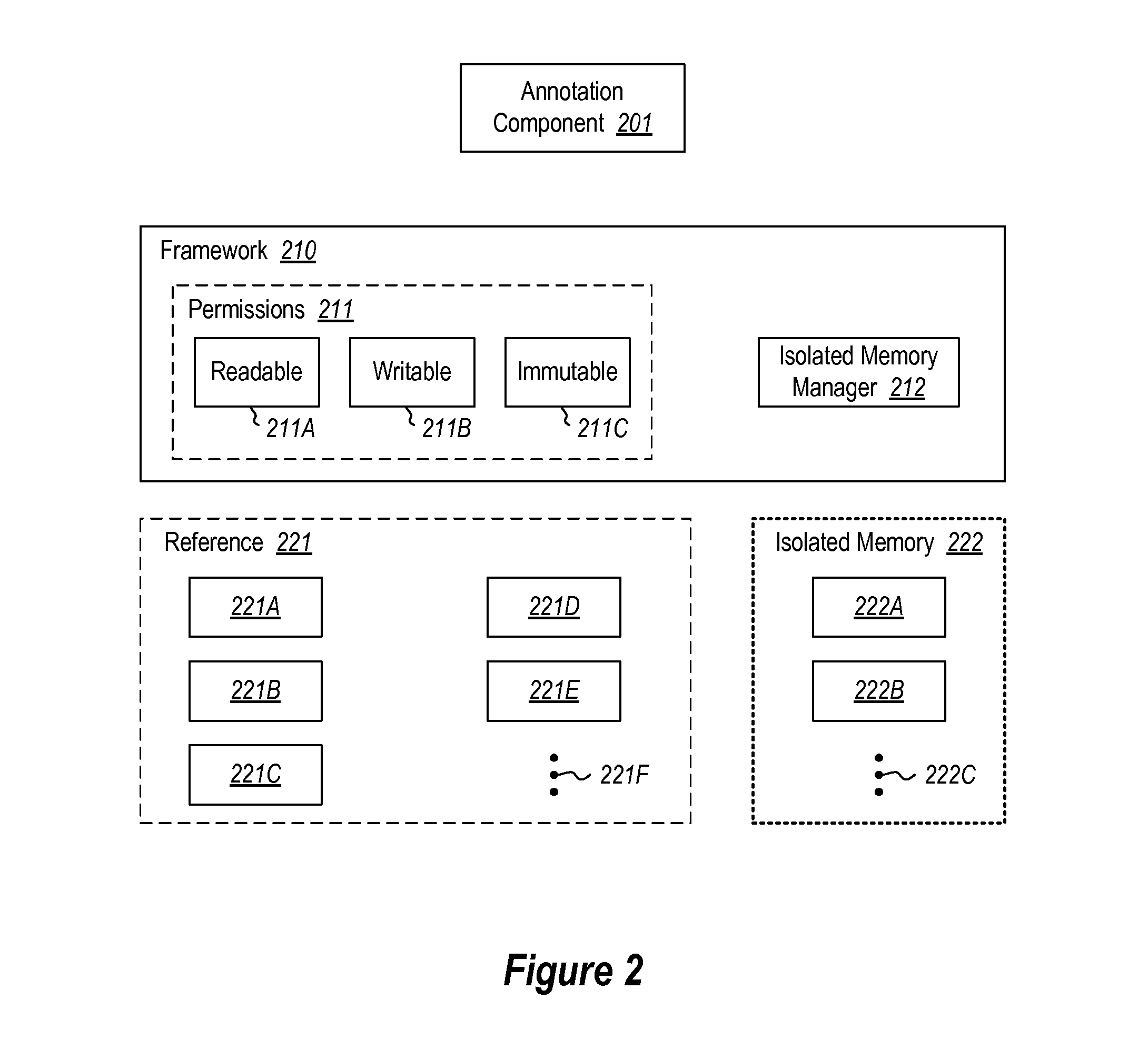
Reference attribute annotation signifying no external reference
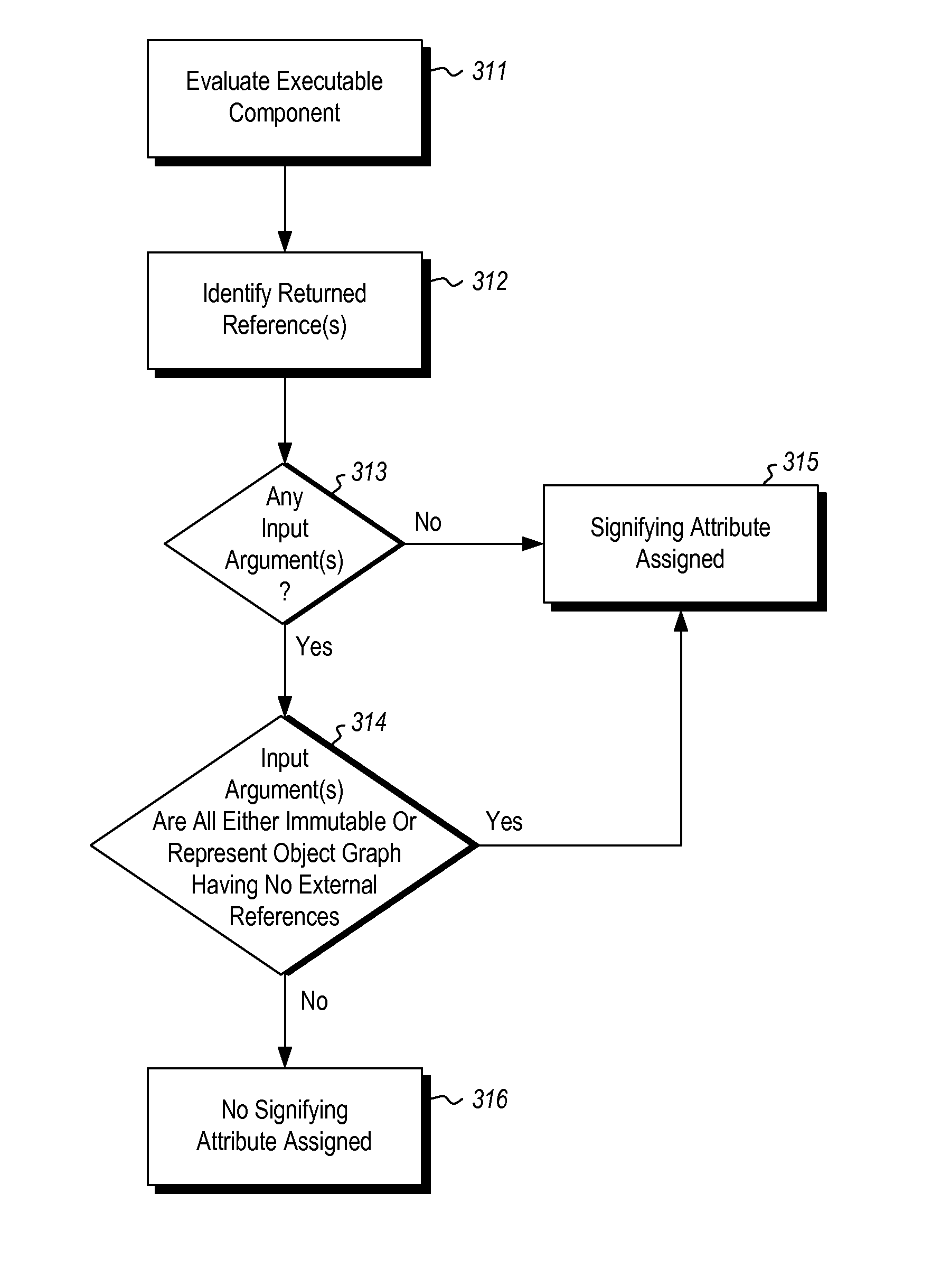
ActiveUS20140108438A1Specific access rightsProgram synchronisationProgramming languageExternal reference
The annotation of a returned reference from an executable component to signify that there are no external references to the particular object graph referenced by the returned reference. If either 1) there are no input arguments to the executable component or 2) each input argument is either immutable or represents an object graph that has no external mutable references pointing into the object graph, and no internal mutable references that reference external objects, the particular attribute is assigned to the returned reference. Accordingly, if the returned reference is writable (as determined by evaluating the declaration code or the call code for the executable component), the returned reference is free to have whatever access permissions assigned to it, and may also be assigned to an isolated memory location, though such assignments will cause the returned reference to lose the particular attribute.
Owner:MICROSOFT TECH LICENSING LLC
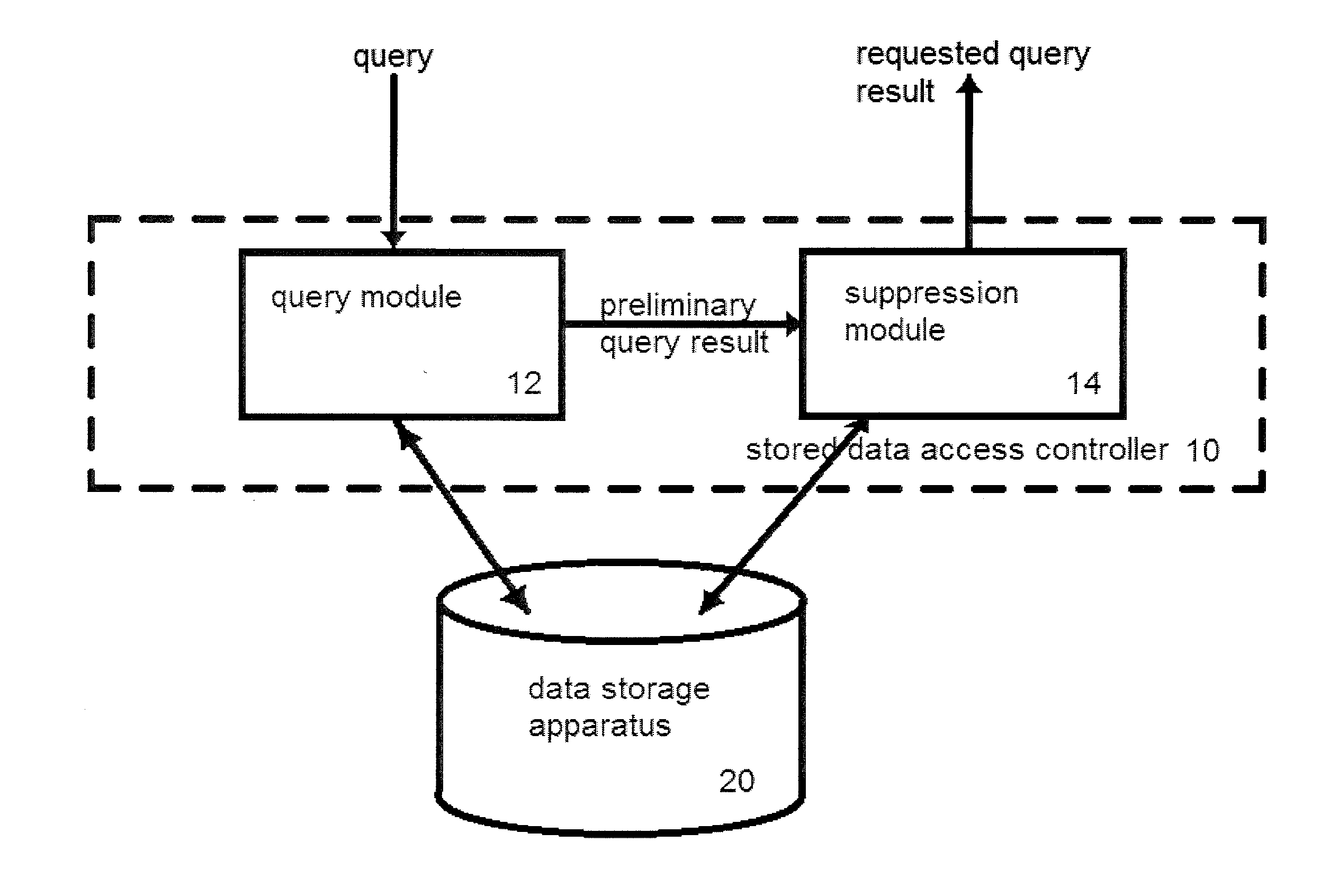
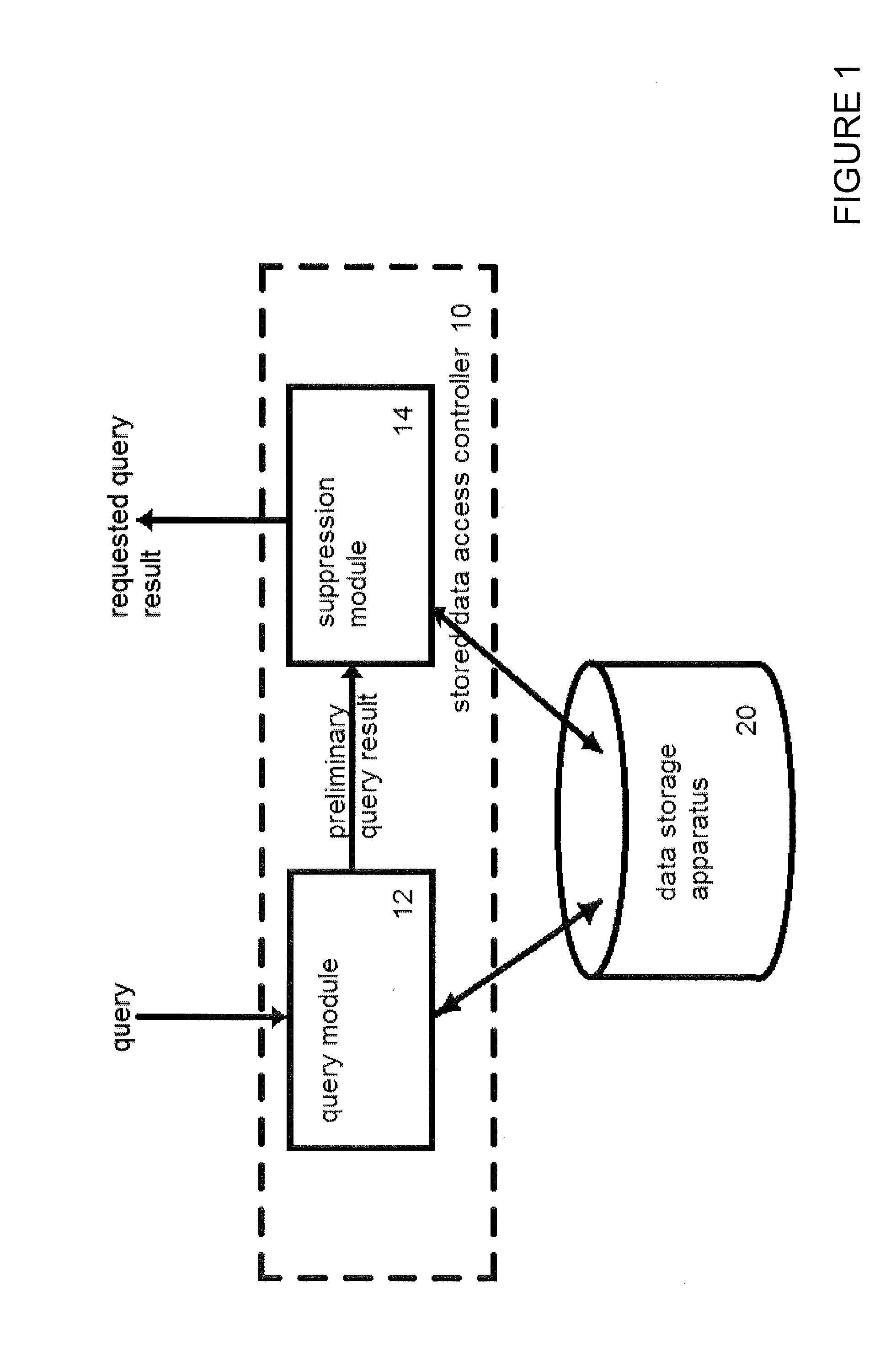
Stored data access controller
ActiveUS20150193636A1Easy to processDifficult to implementDigital data information retrievalDigital data processing detailsData access controlTheoretical computer science
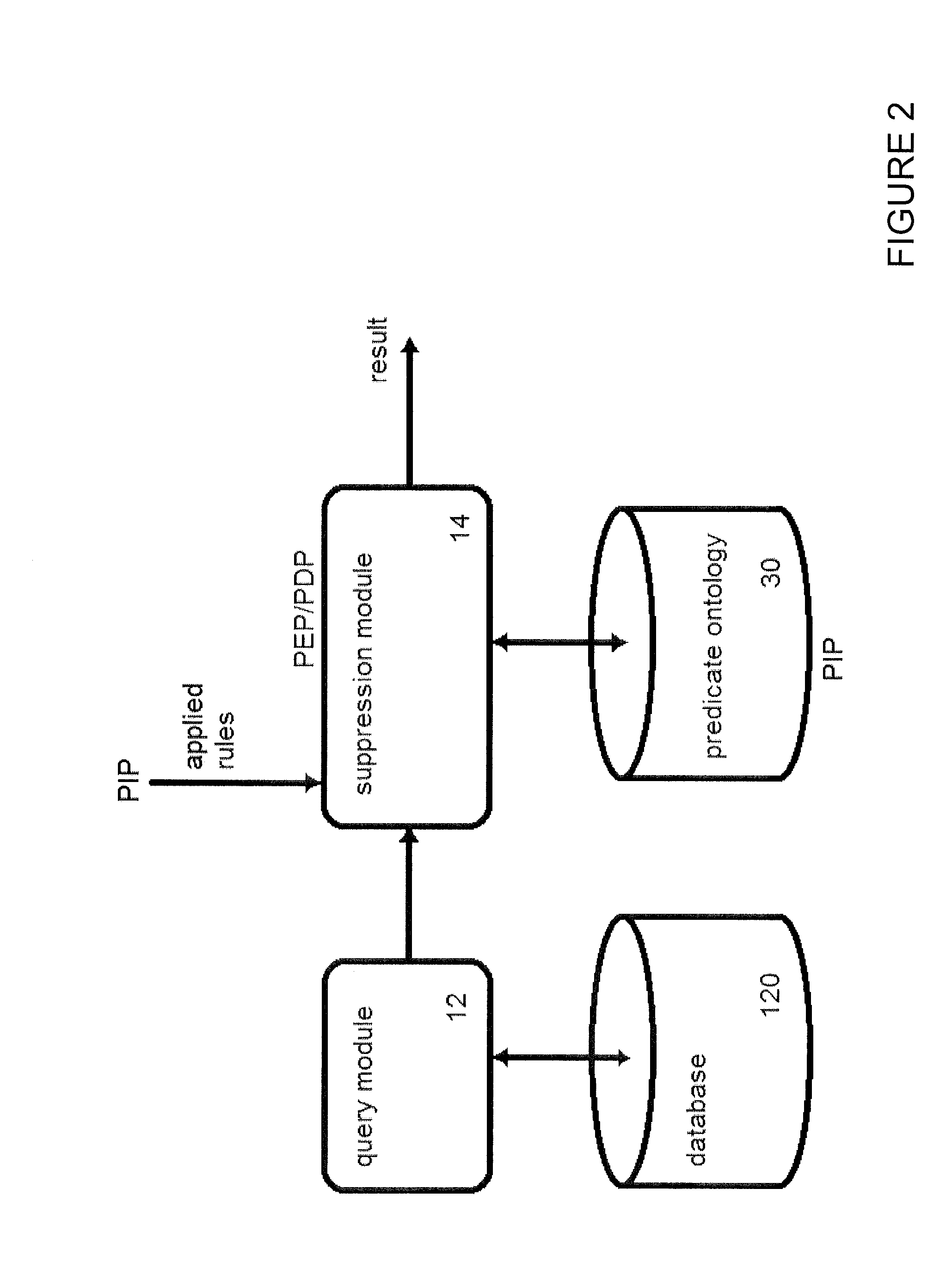
A stored data access controller, configured to control access to data items, stored in a data storage apparatus, composed of data values encoding a labelled link between a subject graph node and an object graph node. The stored data access controller comprising: a query module, configured to receive a query requesting a specified subset of the data items and further configured to obtain the specified subset of the data items as a preliminary query result. The stored data access controller further comprising: a suppression module, configured to obtain the preliminary query result from the query module, and to generate a revised version of the preliminary query result by selectively suppressing the data value of one or more graph nodes in accordance with access control information attributed to the label of a labelled link between the subject graph node and the object graph node.
Owner:FUJITSU LTD
Data access reporting platform for secure active monitoring
ActiveUS8584254B2Digital data processing detailsUser identity/authority verificationOperational systemActive monitoring
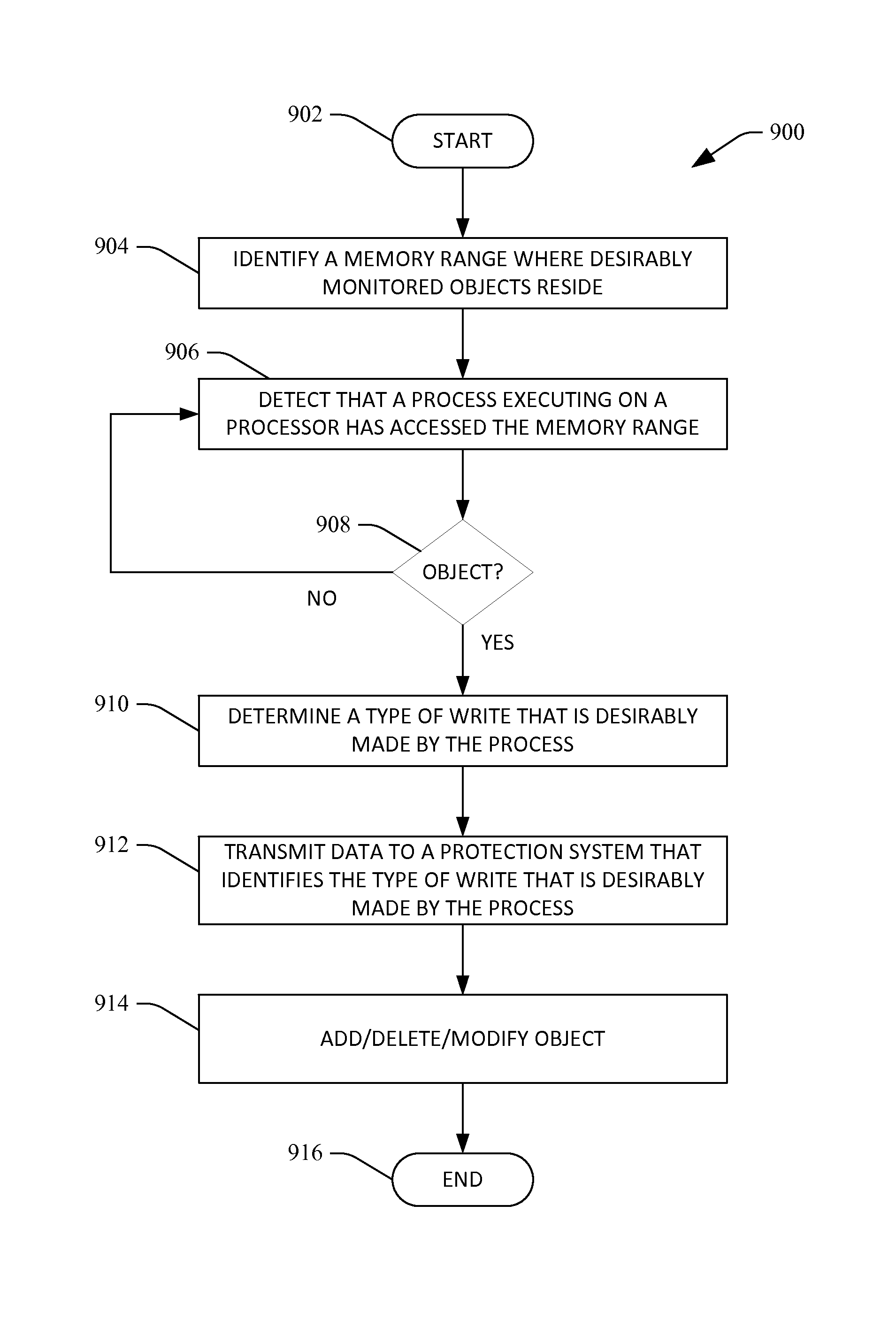
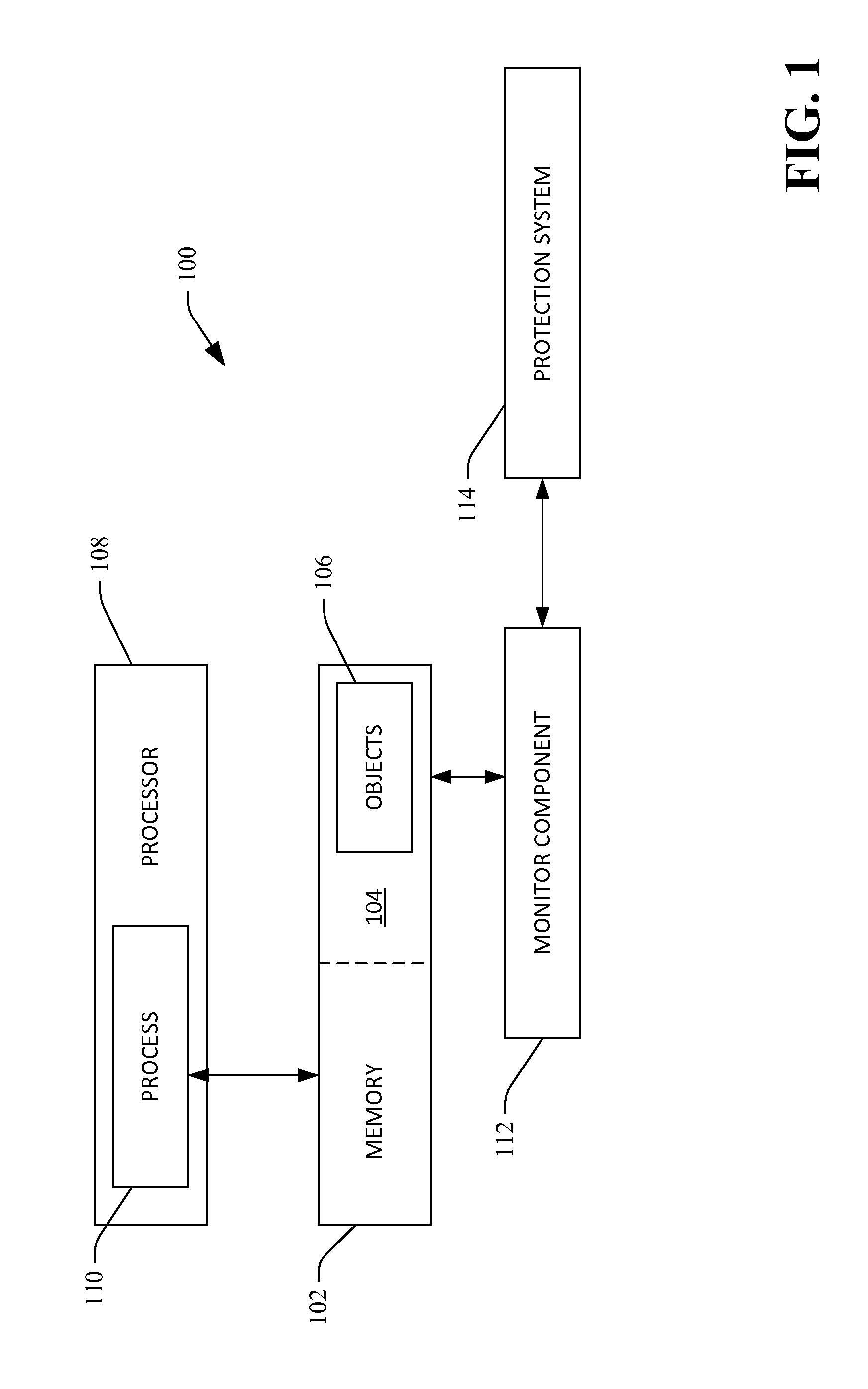
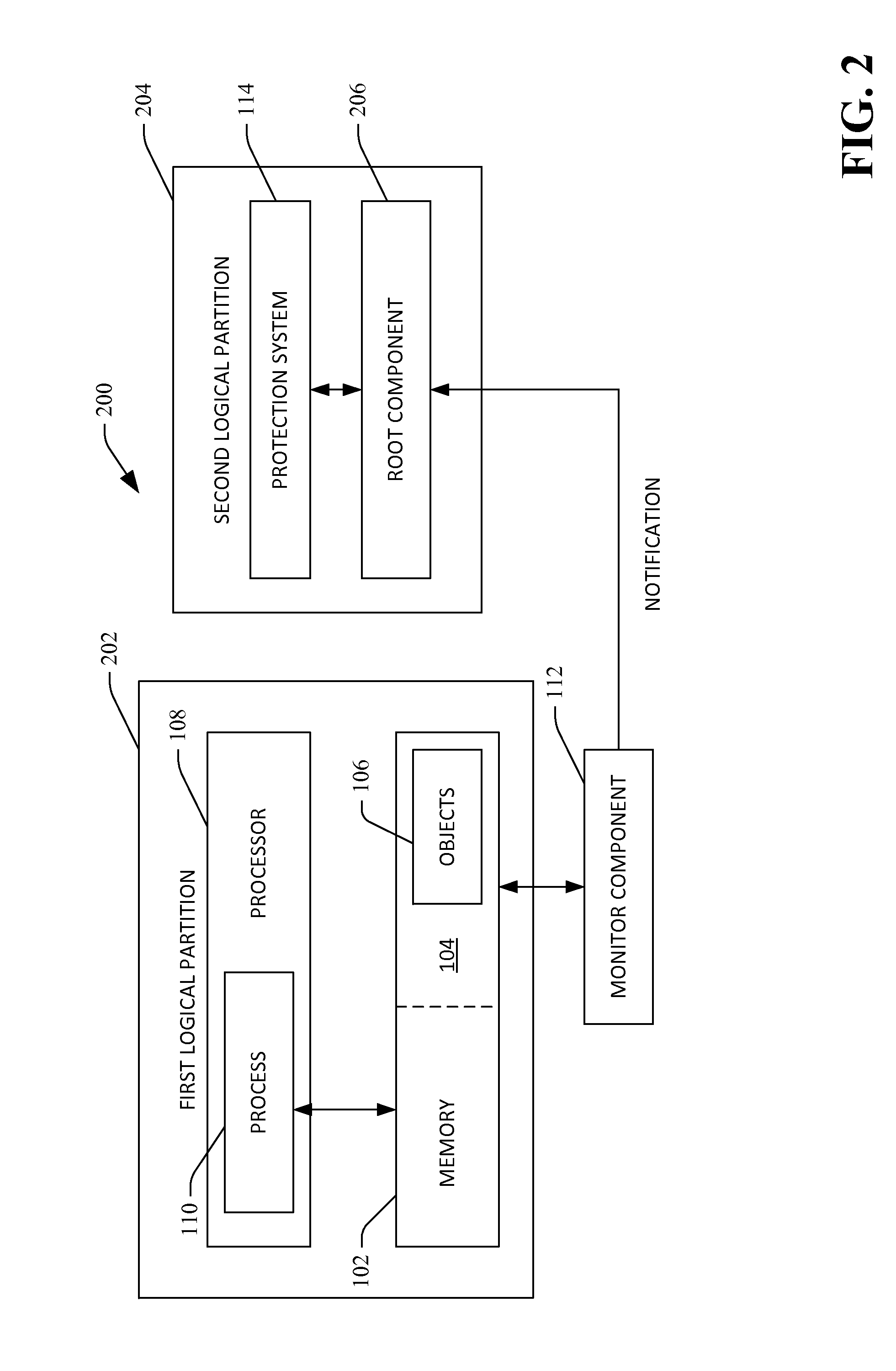
Technologies pertaining to detecting accesses to monitored regions of memory and transmitting data to a protection system responsive to the detecting are described herein. A region of memory that includes objects in an object graph utilized by an operating system to determine which processes to execute and an order to execute such processes is monitored. If a process executing on a processor attempts to write to an object in the object graph, a field that is being written to is identified, and a determination is made regarding whether the field includes a pointer. Based upon whether the field includes a pointer, a type of write desirably undertaken by the object is ascertained, and an object event is transmitted to the protection system that informs the protection system of the type of write.
Owner:MICROSOFT TECH LICENSING LLC
Text visual question-answering system and method based on concept interaction and associated semantics
ActiveCN111858882AIncrease diversityDiverse visual featuresDigital data information retrievalNeural architecturesAlgorithmTheoretical computer science
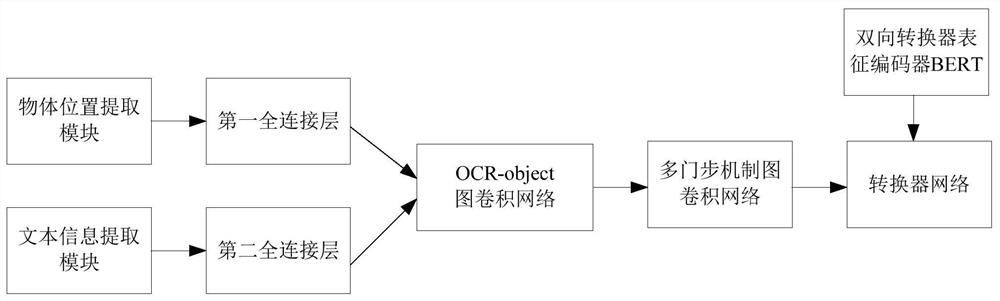
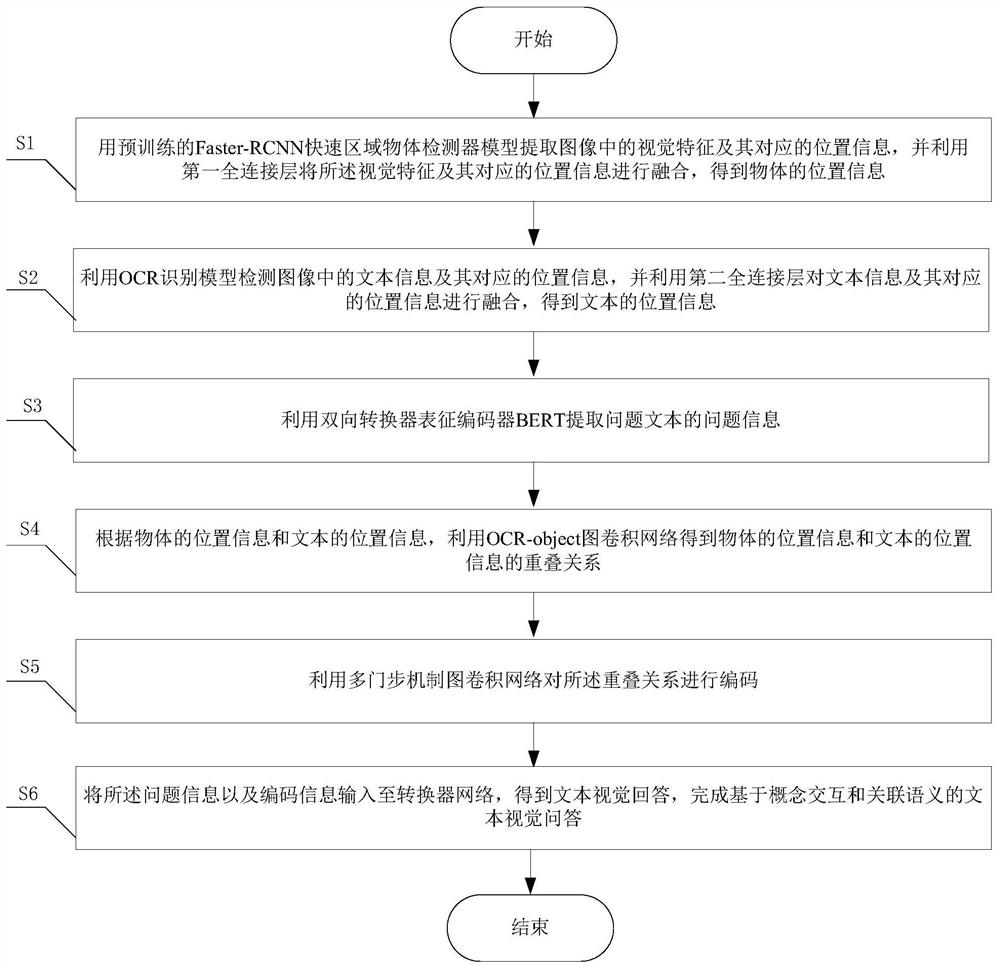
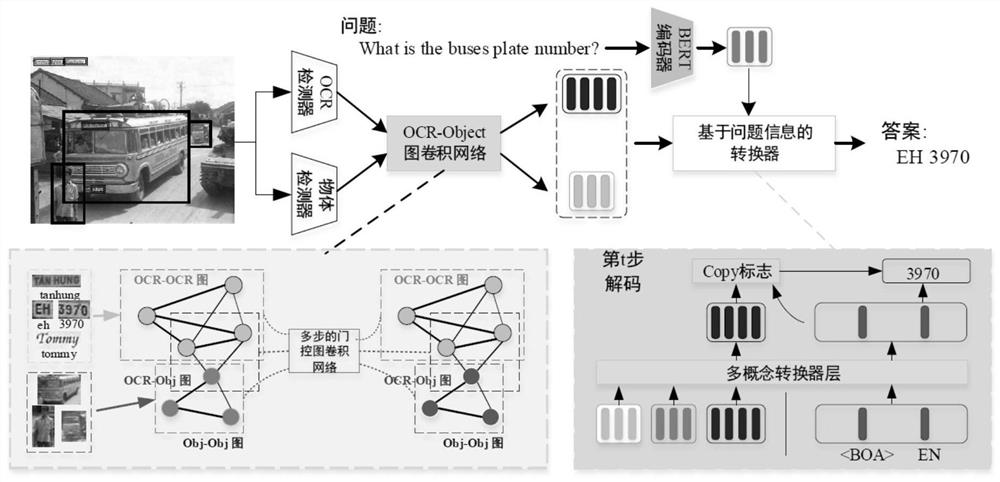
The invention provides a text visual question-answering system and method based on concept interaction and associated semantics. The system comprises an object position extraction module, a first fullconnection layer, a text information extraction module, a second full connection layer, an OCR-object graph convolutional network, a multi-gate-step mechanism graph convolutional network, a converternetwork and a bidirectional converter representation encoder BERT. According to the invention, modeling is carried out by using a position relationship between an object and text information in an image, then modeling is performed on text information and object information through the OCR-object graph convolutional network, thus learning abundant and directional features for relationship coding through a gate mechanism, and finally, precisely paying attention to objects and texts in an image through a converter network, thereby obtaining a more accurate answer.
Owner:GUIZHOU UNIV +1
Propagating ordered object changes
PendingUS20200159560A1Version controlInterprogram communicationTheoretical computer scienceEngineering
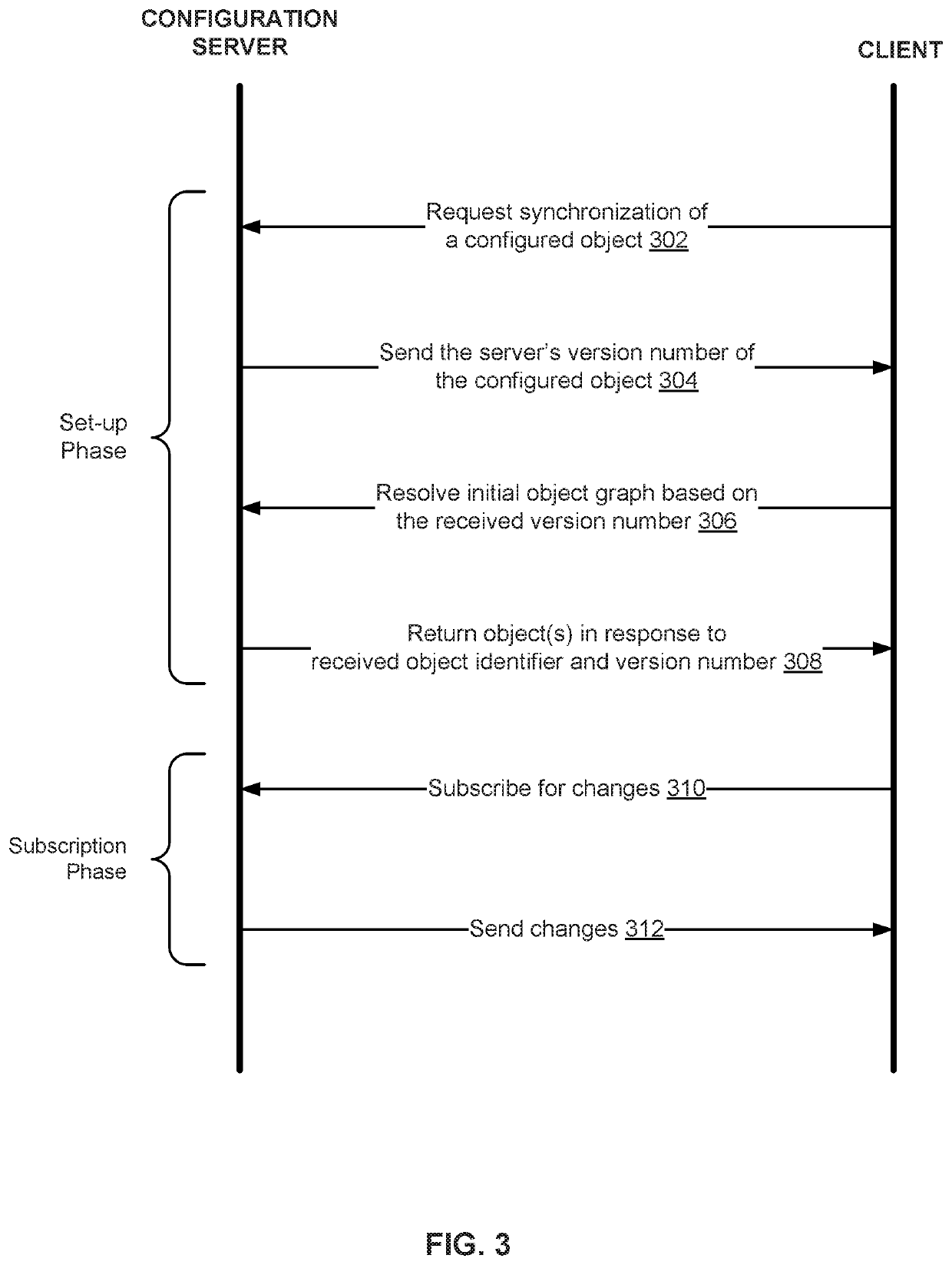
In an embodiment, a method for propagating ordered object changes includes synchronizing a client's version of configured objects with a configuration server's version of configured objects, including obtaining a list of object identifiers and a first version identifier of an object from the server. The method includes recursively getting objects at a version identified by the first version identifier from the server to construct an object graph on the client. The method includes subscribing to a configuration stream associated with the server (including sending the first version identifier) and obtaining responses from the configuration server where a response includes a second version identifier and a corresponding object identifier for an object that has been reconfigured between the first version and the second version. The method includes getting an updated version of the objects identified in the stream by the second version identifier to update the object graph.
Owner:VMWARE INC
Apparatuses and methods for producing runtime architectures of computer program modules
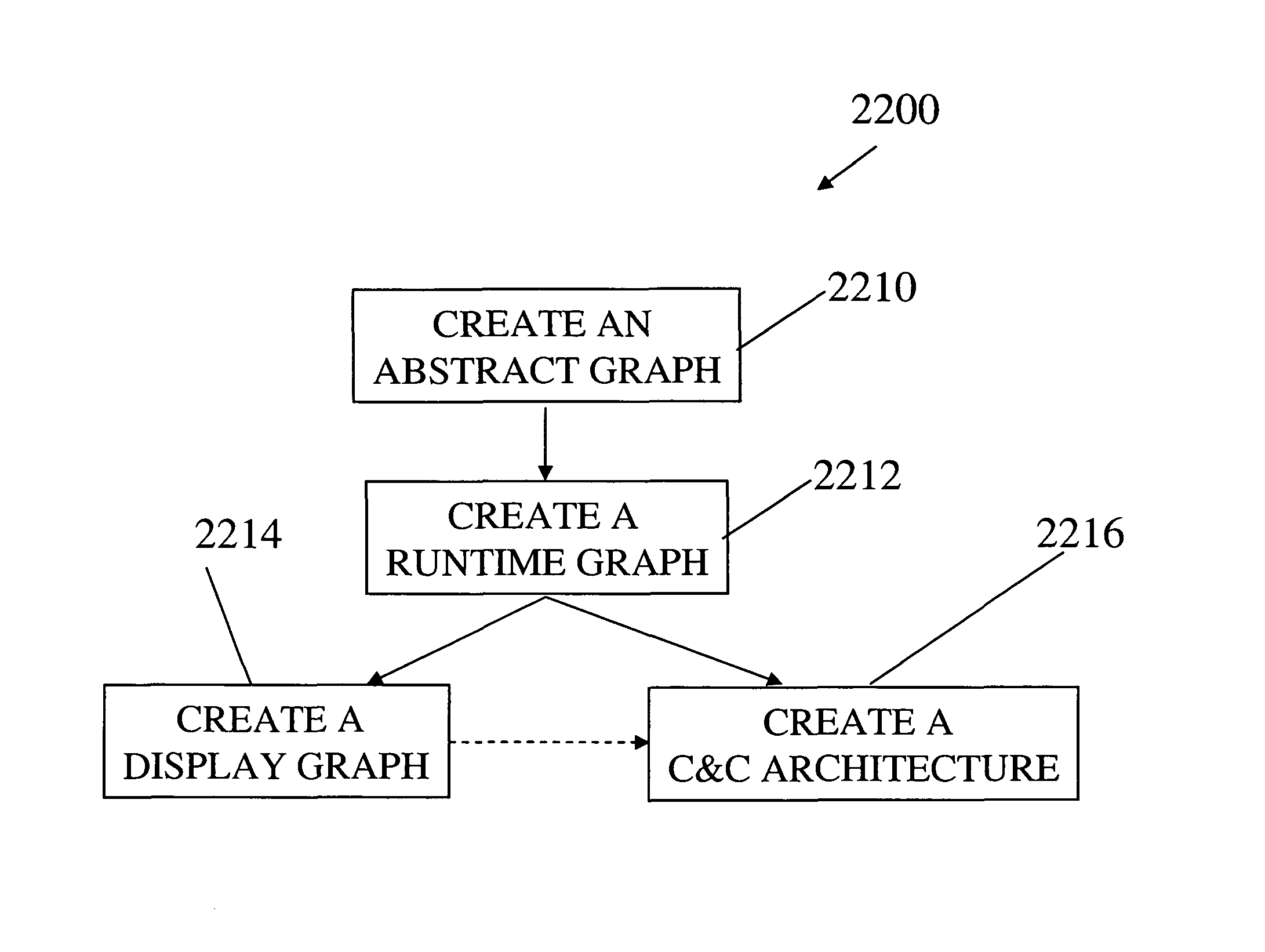
Apparatuses and methods for producing run-time architectures of computer program modules. One embodiment includes creating an abstract graph from the computer program module and from containment information corresponding to the computer program module, wherein the abstract graph has nodes including types and objects, and wherein the abstract graph relates an object to a type, and wherein for a specific object the abstract graph relates the specific object to a type containing the specific object; and creating a runtime graph from the abstract graph, wherein the runtime graph is a representation of the true runtime object graph, wherein the runtime graph represents containment information such that, for a specific object, the runtime graph relates the specific object to another object that contains the specific object.
Owner:CARNEGIE MELLON UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com