SQL injection attack detection system suitable for high speed LAN environment
An injection attack and detection system technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve the problems of high false positive rate, high false negative rate, SQL injection attack signature easily deceived, etc. Dealing with stress and reducing false positives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
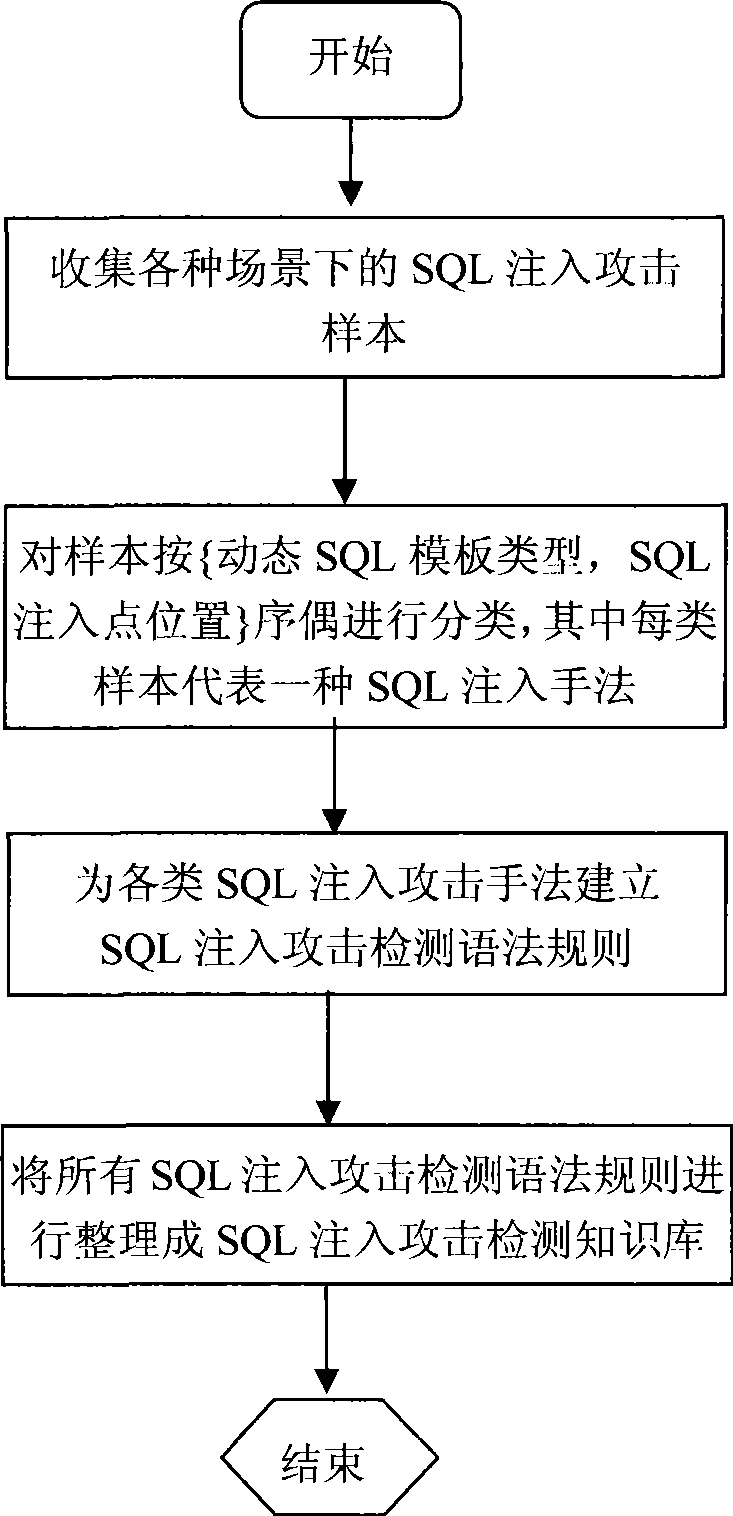
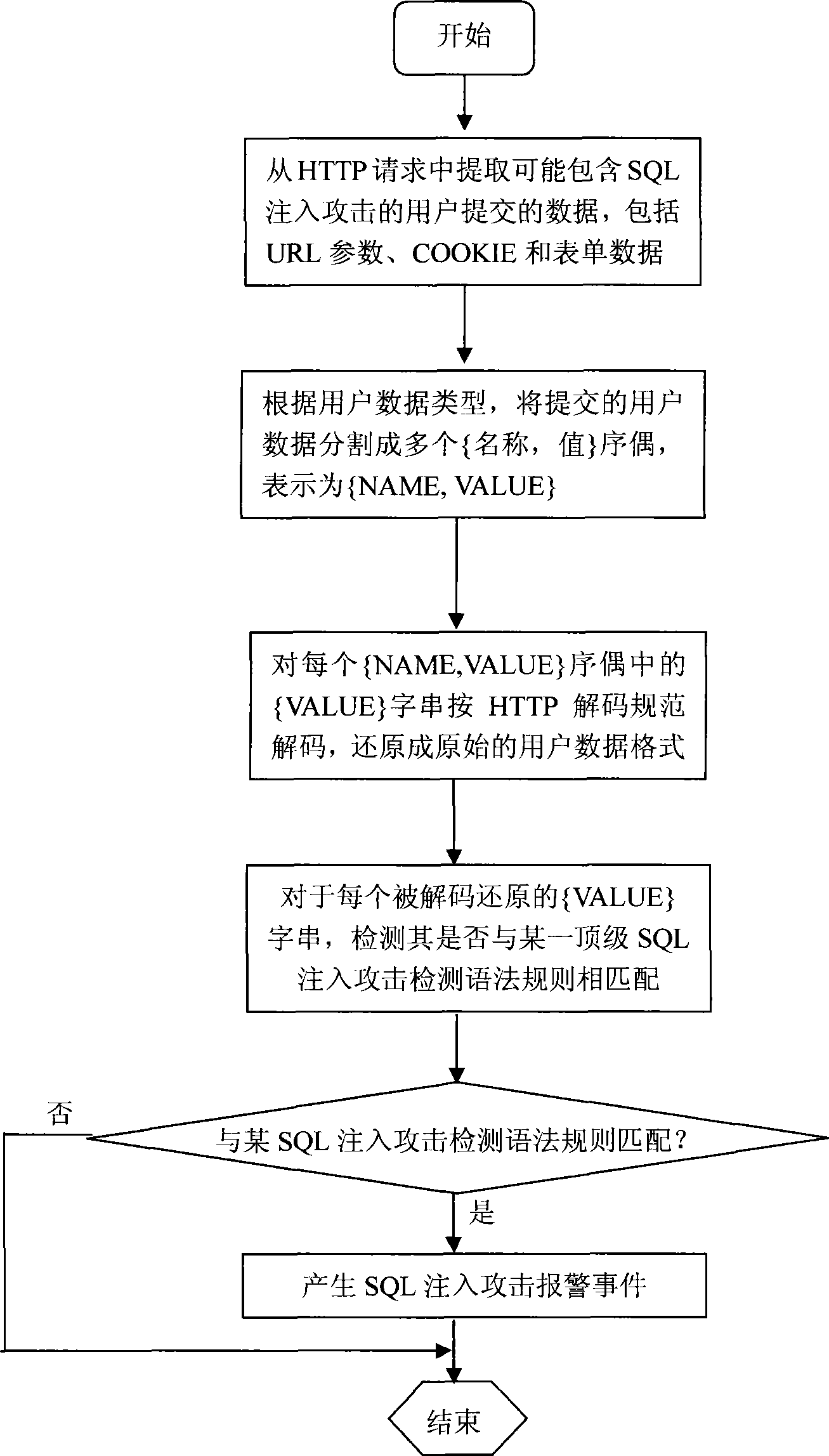
[0023]The SQL injection attack detection system suitable for high-speed local area network environment according to the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
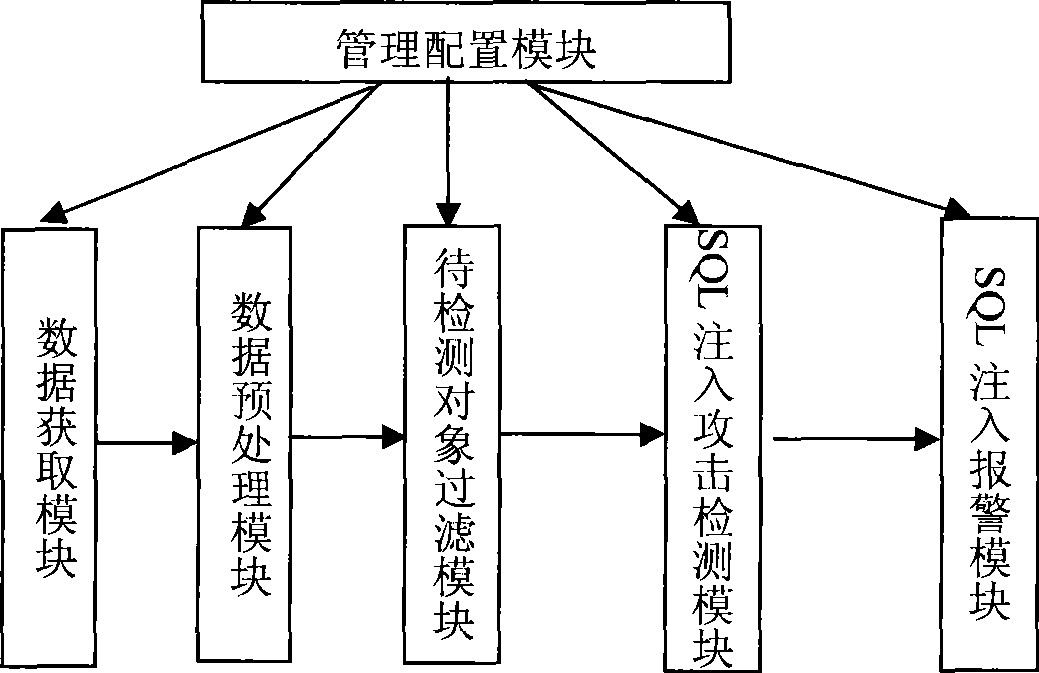
[0024] The architecture of the SQL injection attack detection system of the present invention is as attached image 3 As shown, it includes the following modules:
[0025] Data acquisition module: used to capture a large number of network data packets generated during the communication between the Web client and the Web application server; the network data packets can be captured in a bypass mode or a routing mode. In the bypass working mode, all network data packets in the monitored network can be captured through the mirror port of the hub, switch or router, and then the packets are filtered according to the HTTP service port (such as port 80) to obtain the network that needs further preprocessing data pack.
[0026] Data preprocessing module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com