Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
176results about How to "Avoid downloading" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
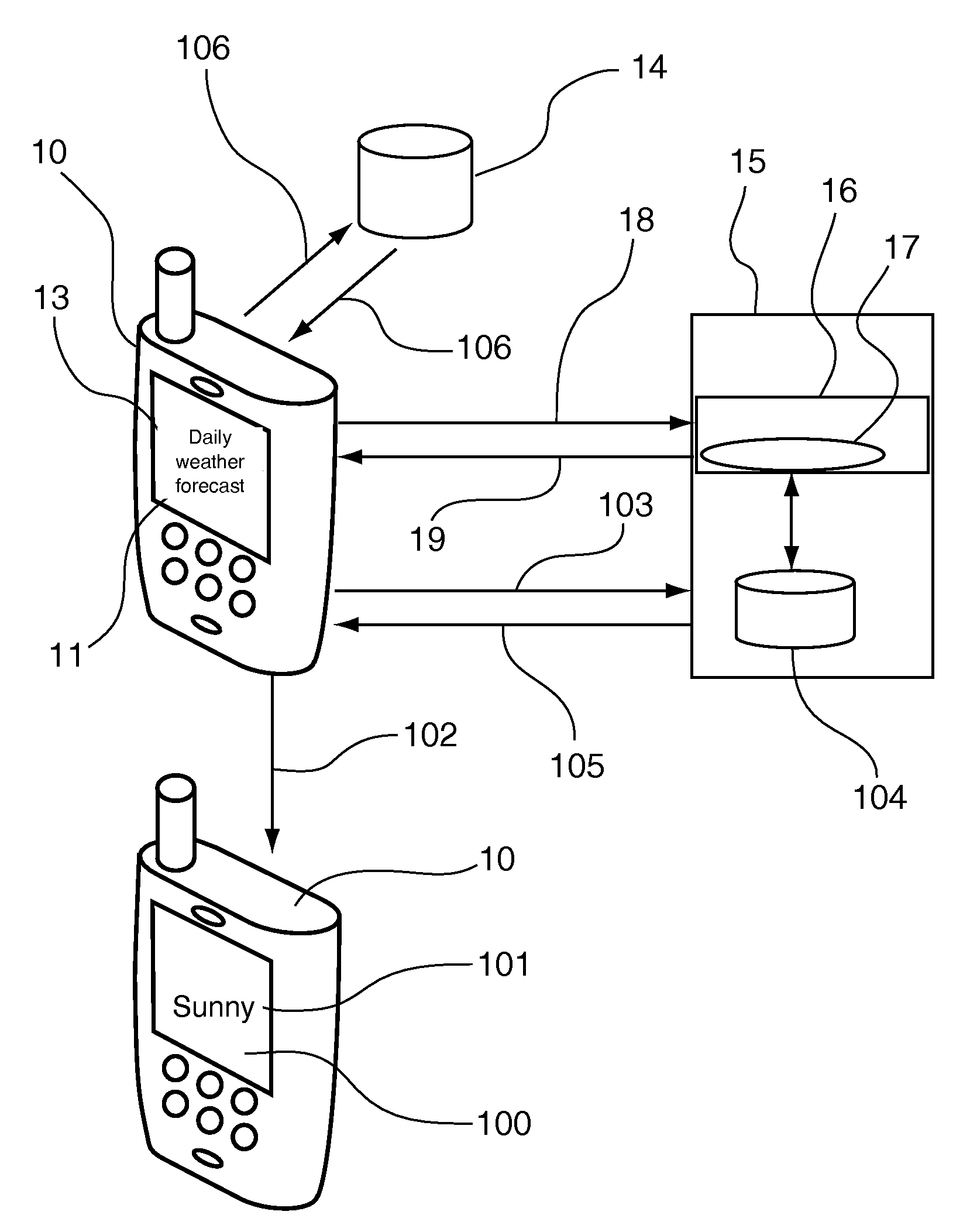
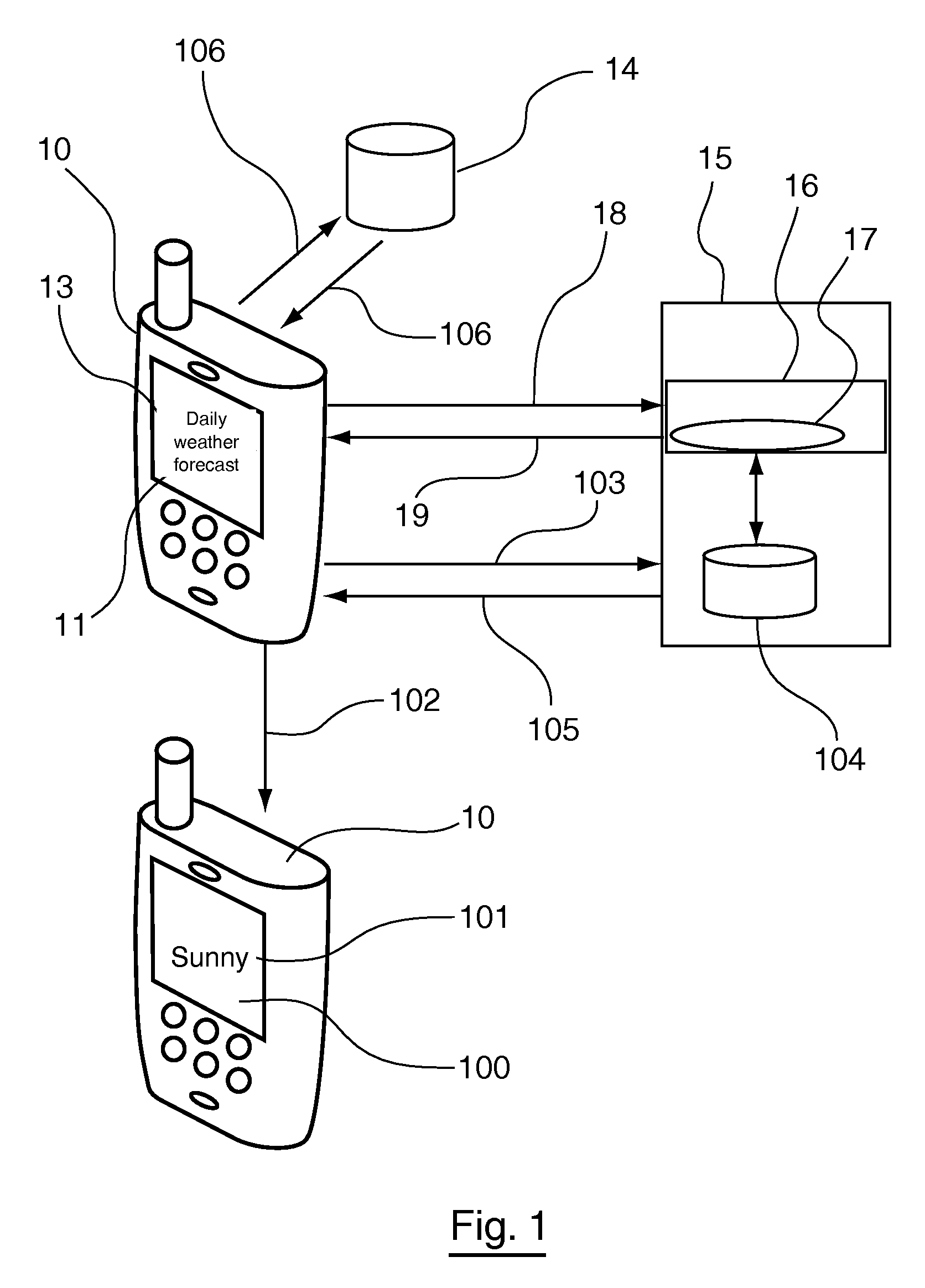
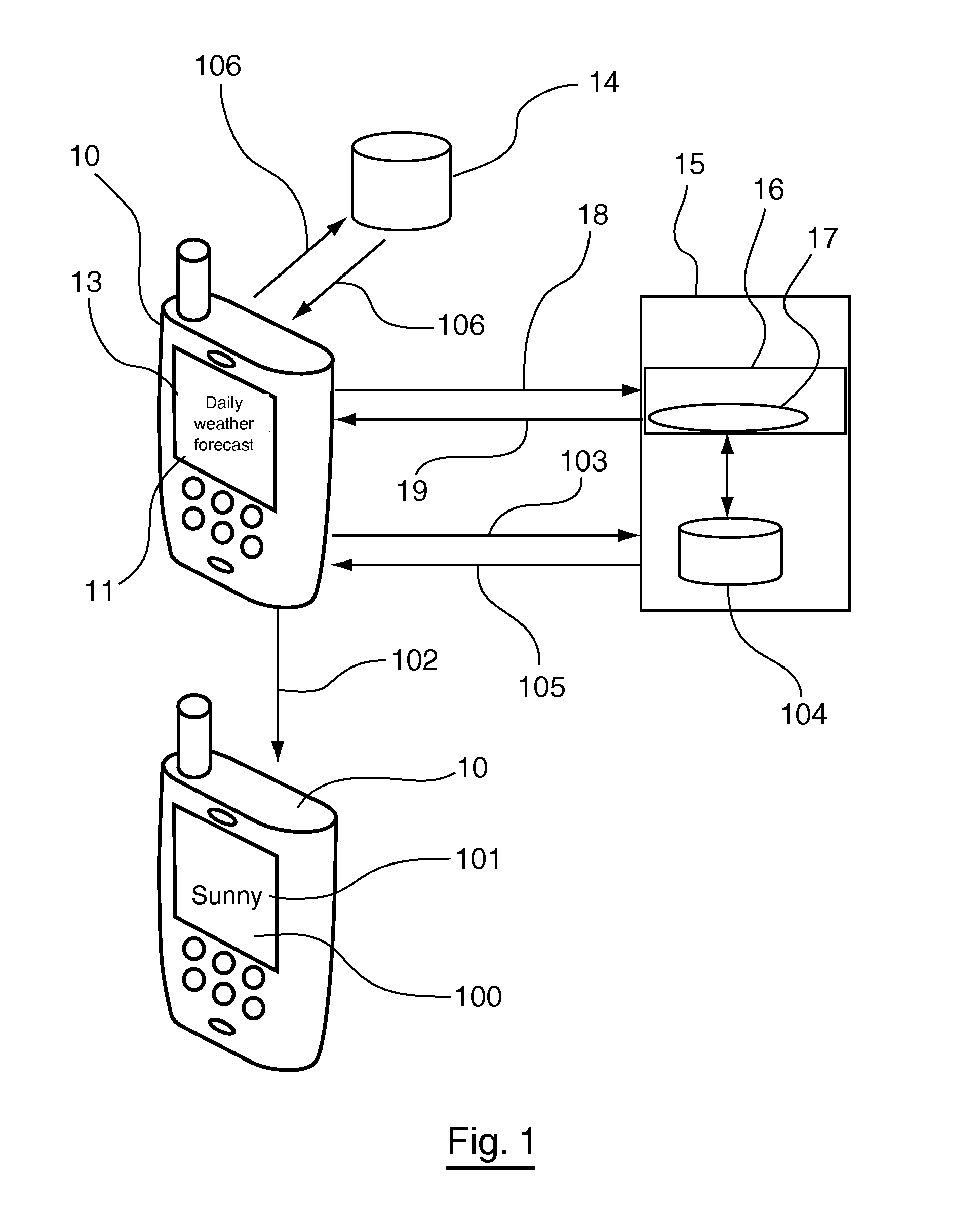
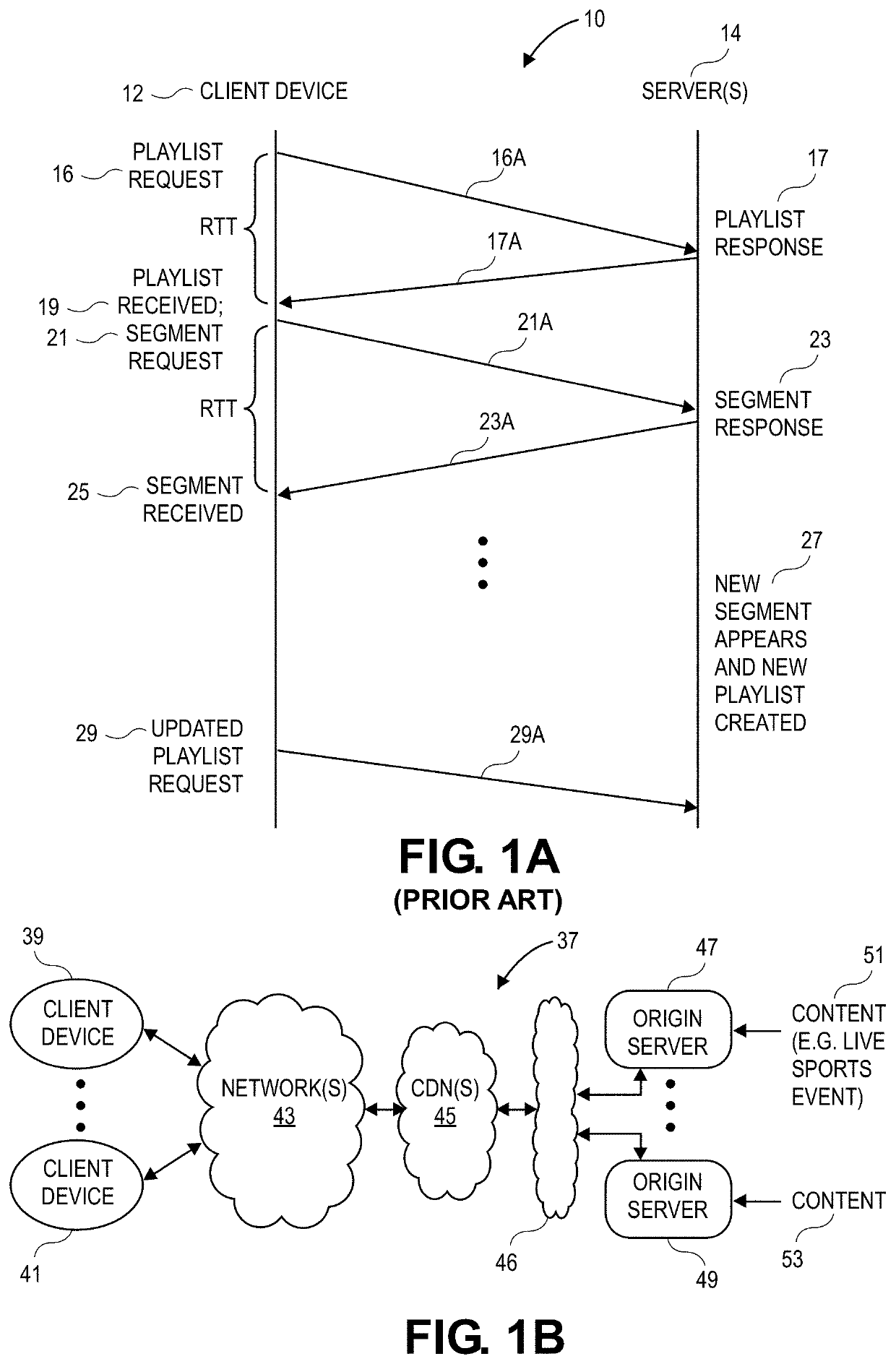
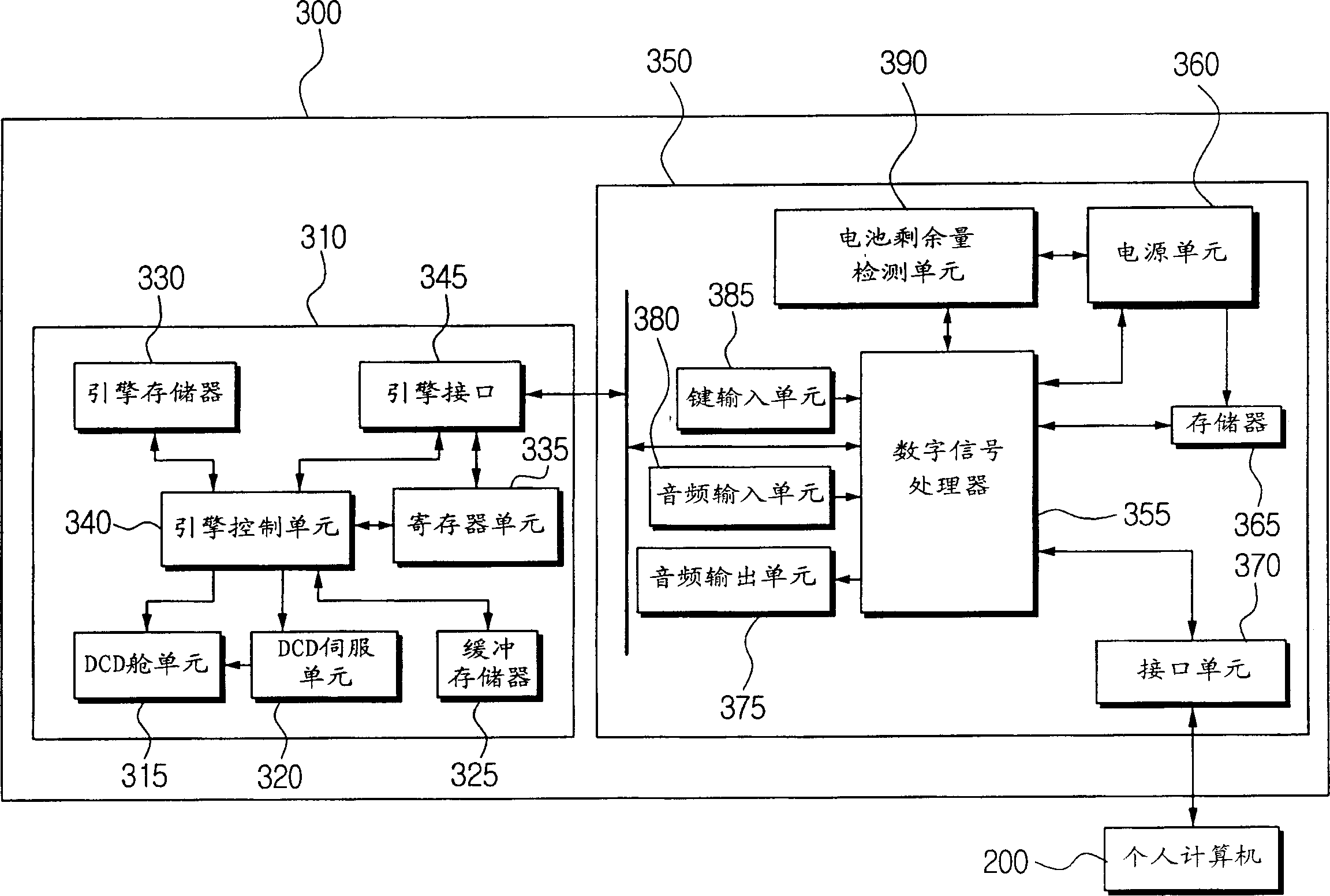
Method of managing character fonts within multimedia scenes, and the corresponding computer program and terminal
InactiveUS20090031220A1Avoid downloadingEfficient managementCathode-ray tube indicatorsComputer security arrangementsComputer graphics (images)Computer program
A method is provided for managing fonts in a radio communication terminal, which can receive fonts in order to render contents on a screen. One such method involves the use of the following elements in the terminal, namely: a font database that lists all of the fonts or font portions stored by the terminal and matches at least one management parameter with each of the fonts; and set of font management commands including at least one command, which is applied to a font portion and which belongs to the group containing at least a command for transmitting a font portion for storage in the terminal, a command for updating a font portion stored in the terminal and a command for deleting a font portion stored in the terminal.
Owner:STREAMEZZO
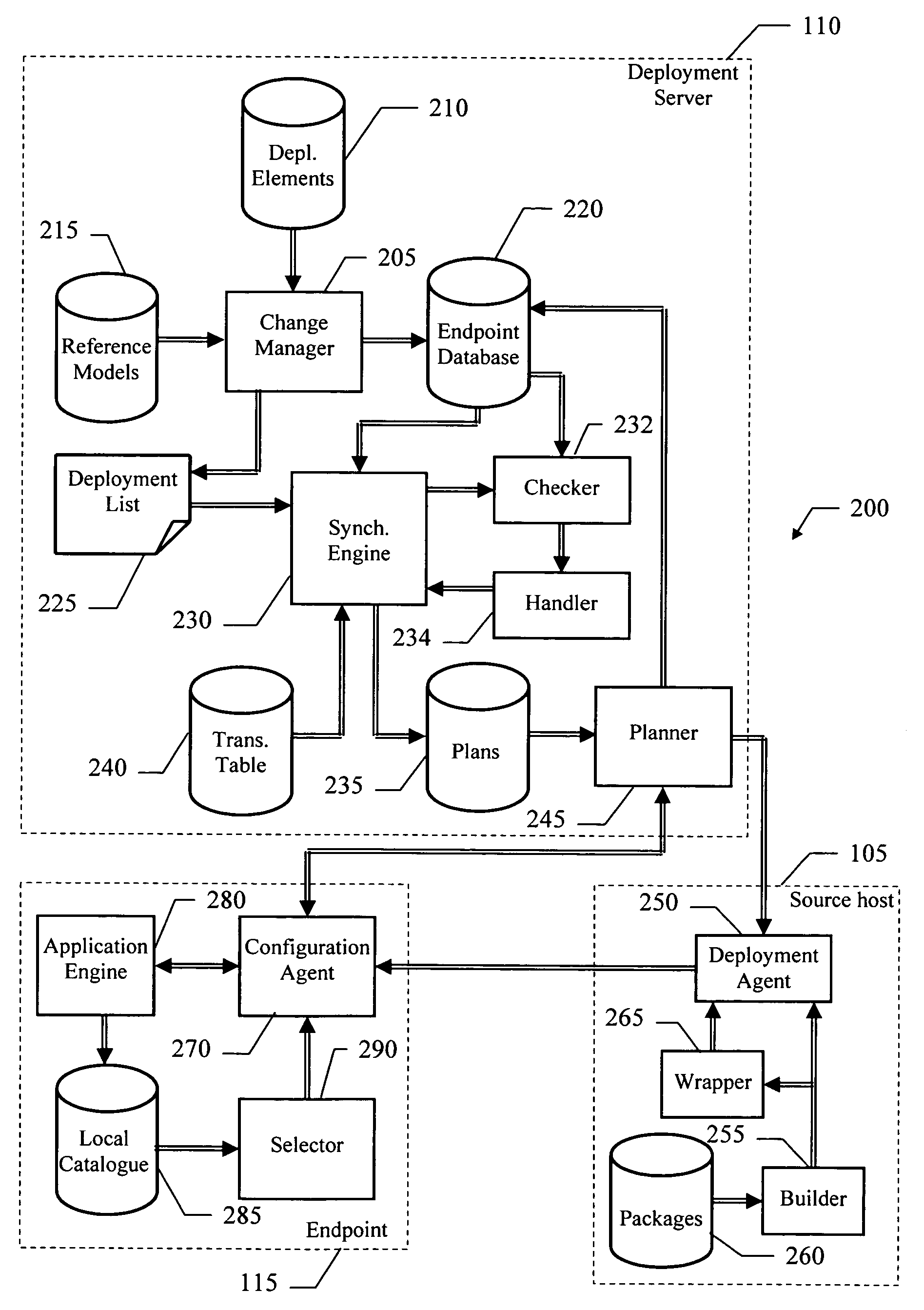
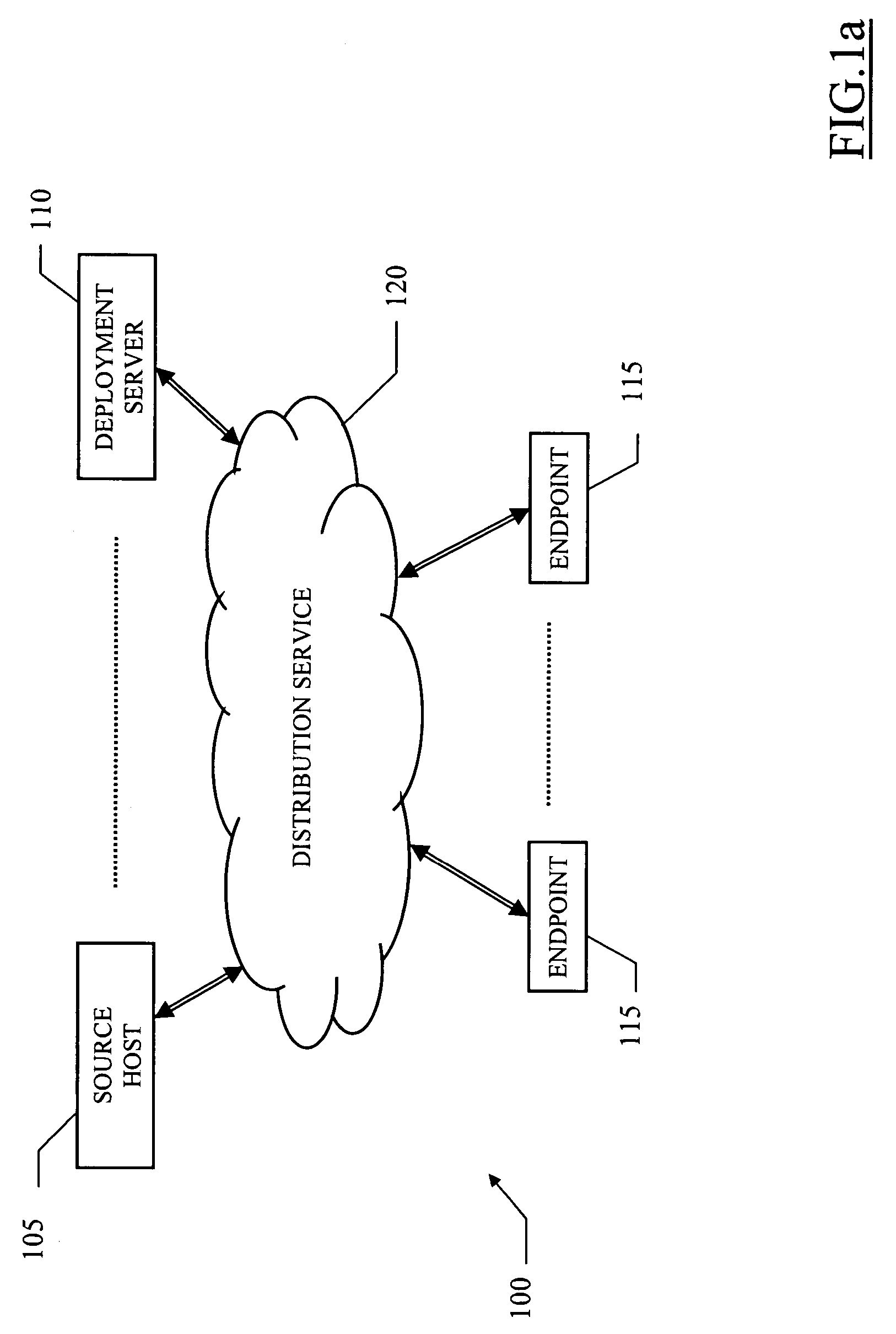
Software distribution method and system with automatic prerequisite installation
InactiveUS20060048145A1Reduce needIncrease reliability and performanceProgram loading/initiatingMemory systemsPreconditionSoftware
A software distribution method (300) is proposed. The solution of the invention relates to the deployment (from a source host to selected endpoints) of main packages that require one or more prerequisite packages. In this case, the source host builds (304-326) and transmits (330-332) a multi-segment distribution structure that embeds the main package and any prerequisite package that is not available on at least one of the endpoints. Each endpoint receiving the distribution structure only installs (336-360) the prerequisite packages that are not available on the endpoint. The main package can then be installed (362-366) correctly (with the required configuration of the endpoint)
Owner:IBM CORP +1
Method and system for updating client software
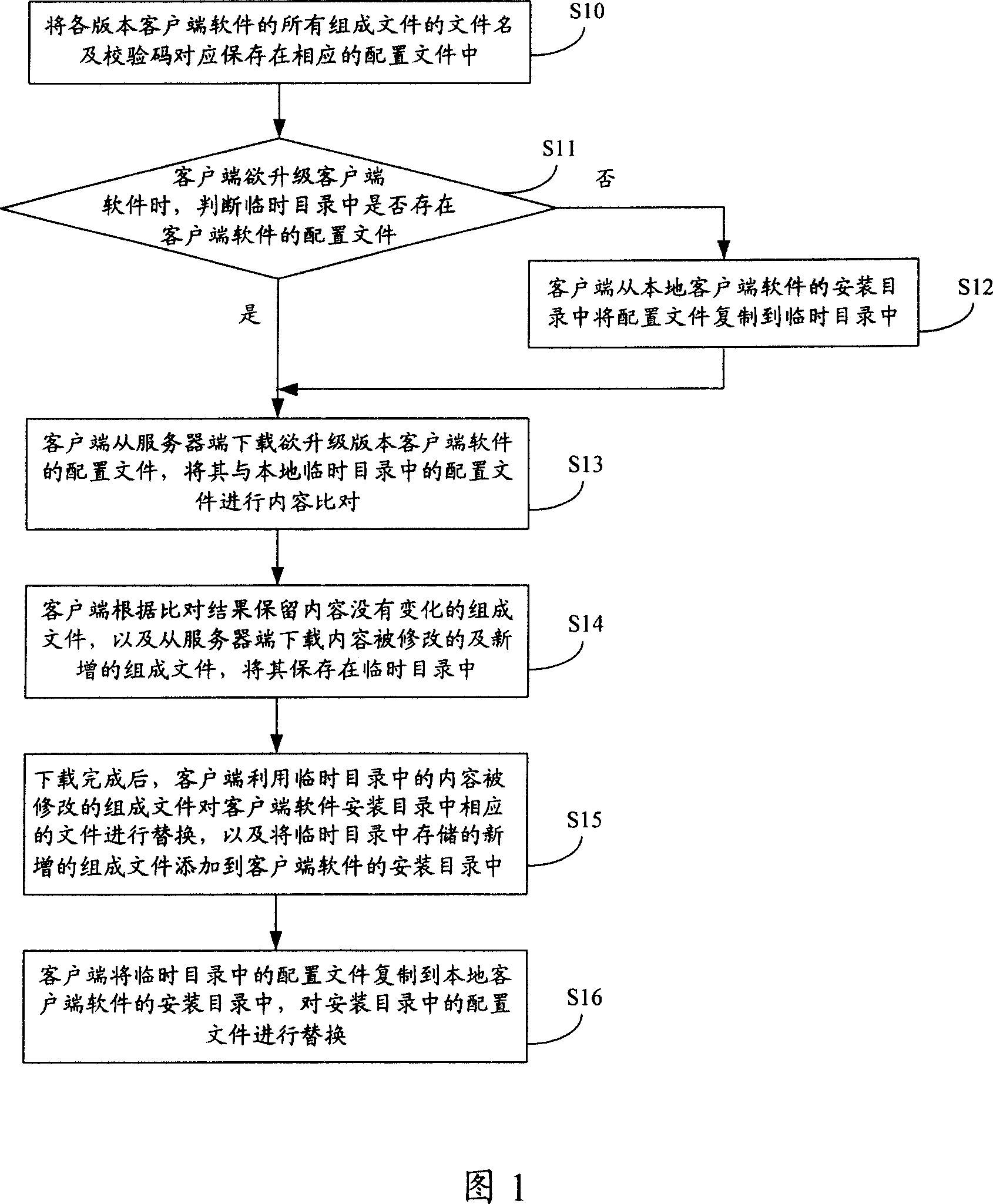
ActiveCN101110788AAvoid downloadingLower requirementProgram loading/initiatingData switching networksClient-sideFile comparison
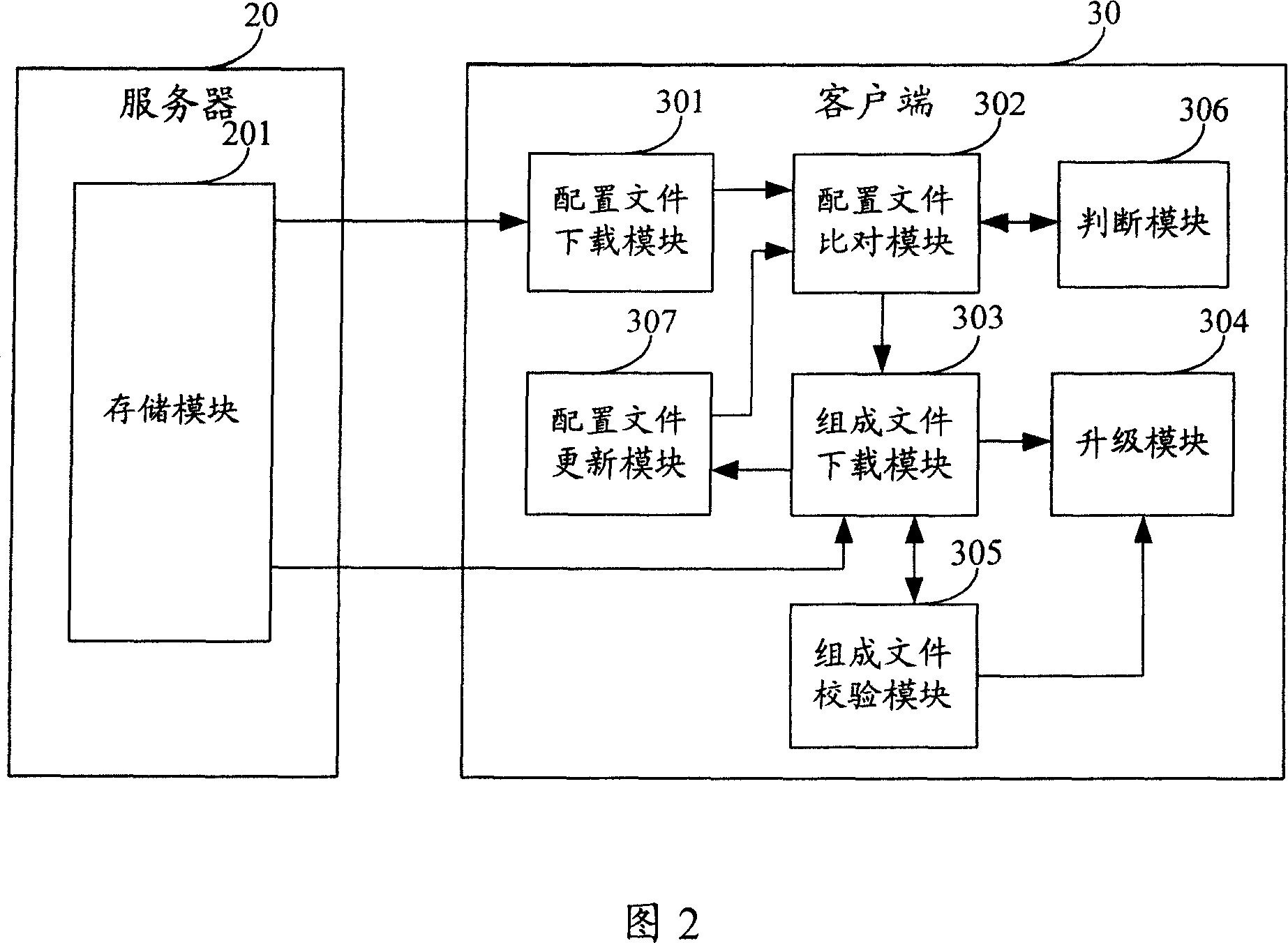
The present invention discloses a method and a system for updating a client side software, which is used to solve the problem existing in the prior art that all bundle files contained in the new edition client side software need to be downloaded when the client side software is updated. The method comprises that the file names of the bundle files of the client side software of each edition and verification codes stored by a server side are correspondingly saved in the configuration files; when the client side software of local installation is updated by the client side, the configuration files of the specified edition client side software are downloaded from a server side, and are compared with the local corresponding configuration files in the content aspect, and according to the comparison results, the bundle files with unchanged contents and the bundle files revised and newly added in contents which are downloaded from a server side are retained locally. The system comprises a server and a client side, wherein the server comprises memory modules, and the client side comprises configuration file index modules, configuration file comparison modules, bundle file downloading modules and updating modules.
Owner:ALIBABA GRP HLDG LTD
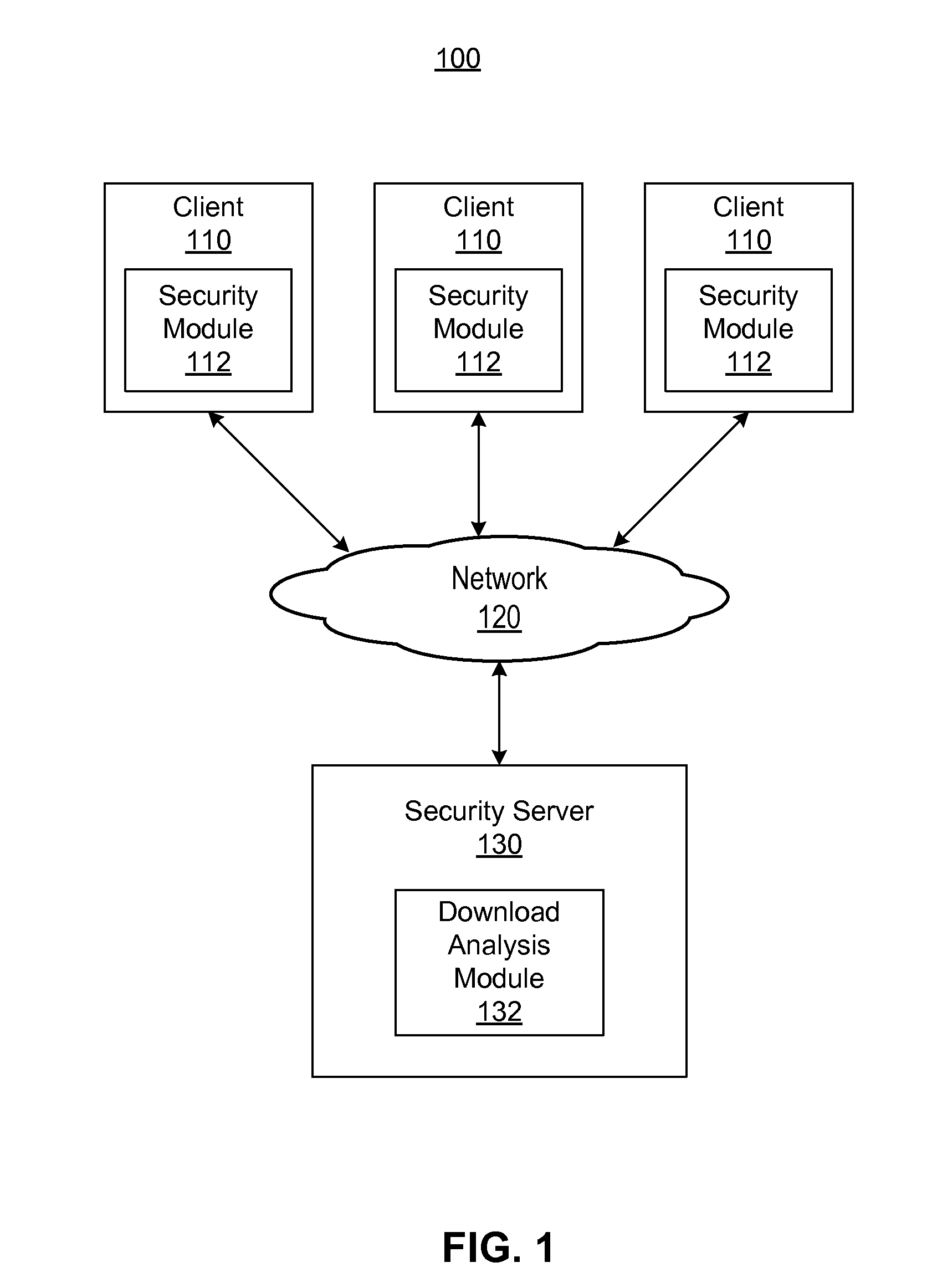
Ip-based blocking of malware
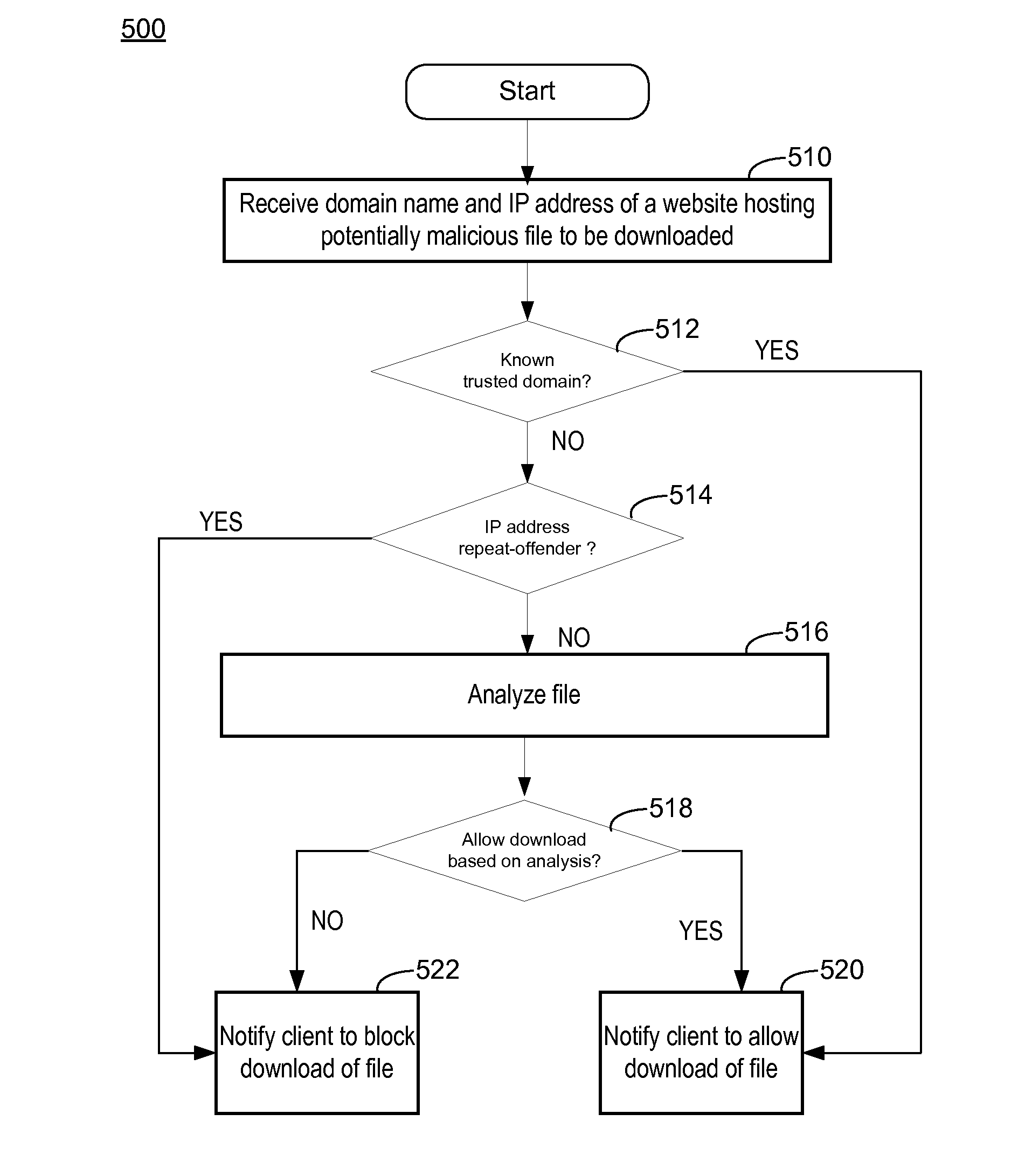
ActiveUS20120117650A1Avoid downloadingMemory loss protectionError detection/correctionClient-sideIp address
A security module on a client monitors file download activities at the client and reports hosting website data to a security server. A download analysis module at the security server receives a hosting website data report from the client, where the hosting website data report describes a domain name and an IP address of a website hosting a file the client is attempting to download. The download analysis module analyzes the domain name and IP address of the website to generate file download control data indicating whether to allow downloading of the file to the client. The download analysis module reports the file download control data to the security module of the client. The security module uses the file download control data to selectively block downloading of the file.
Owner:CA TECH INC
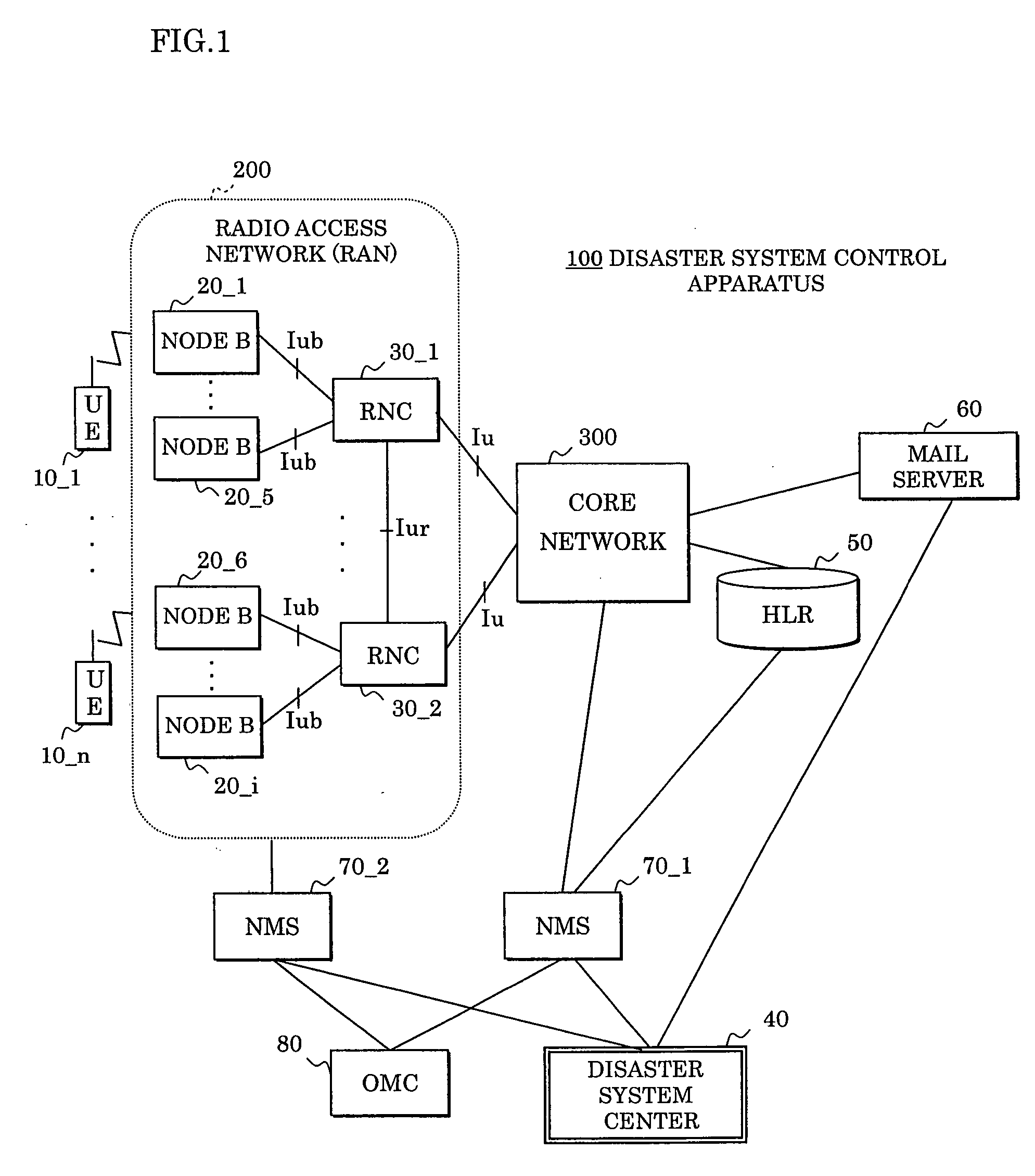
Disaster system control method and disaster system control apparatus
InactiveUS20060079200A1Call congestion state upon disaster can be reducedAvoid downloadingEmergency connection handlingNetwork traffic/resource managementDisaster monitoringMobile communication network
In a disaster system control method and apparatus transmitting disaster status information through a mobile communication network or a fixed communication network, in order to promptly transmit / receive disaster status information at a time of a disaster occurrence between a disaster monitoring person and afflicted people within a disaster occurrence area, a bandwidth control apparatus assigns a bandwidth for a packet call in preference to other calls, a mobile terminal installs an application for disaster thereon for transmitting / receiving disaster status information between a disaster system center and the mobile terminal itself, and the disaster system center provides the mobile terminal within a disaster occurrence area with an application for disaster startup mail to start up the application for disaster.
Owner:FUJITSU LTD
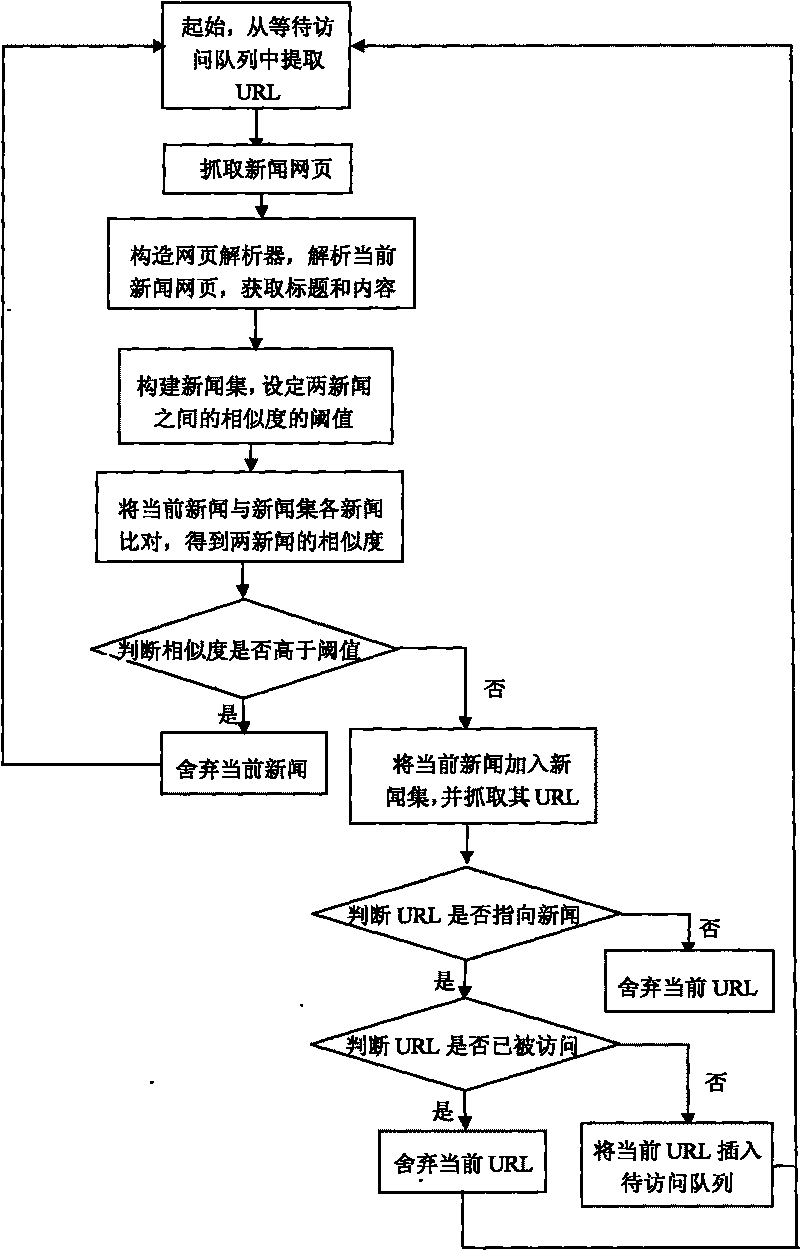
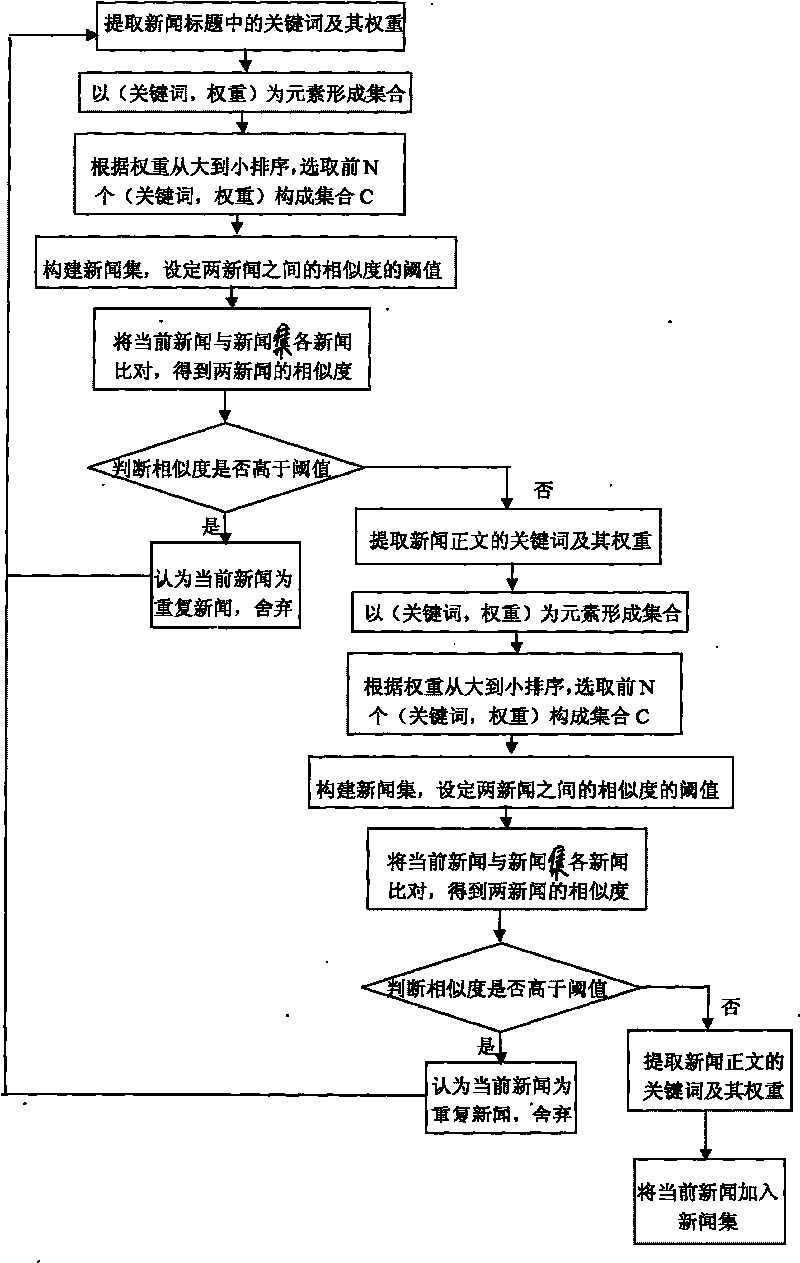
Method for constructing webpage crawler based on repeated removal of news
ActiveCN101694658AAvoid downloadingReduce consumptionSpecial data processing applicationsUniform resource locatorWeb page
The invention relates to a method for constructing a webpage crawler based on the repeated removal of news, which comprises the following steps: constructing an analyzer for analyzing news webpages; constructing a news set; setting a threshold value of the similarity among the webpages; comparing the currently grabbed news webpage with the news set and judging whether the similarity is higher than the threshold value or not; if the similarity is lower than the threshold value, adding the current webpage into the news set; if the similarity is higher than the threshold value, discarding the news and grabbing the next webpage; grabbing a URL of the current webpage and judging whether the URL points at the news webpage or not, if so, judging whether the URL is accessed or not; otherwise, discarding; if the URL is accessed, discarding the URL; if the URL is not accessed, storing the URL into a queue to be accessed; sequentially extracting the URL from the queue to be accessed to access; and repeatedly executing the steps. The invention has the advantages of high algorithm efficiency, less resource waste and convenient data maintenance and prevents from grabbing the webpage with repeated content.
Owner:ZHEJIANG UNIV
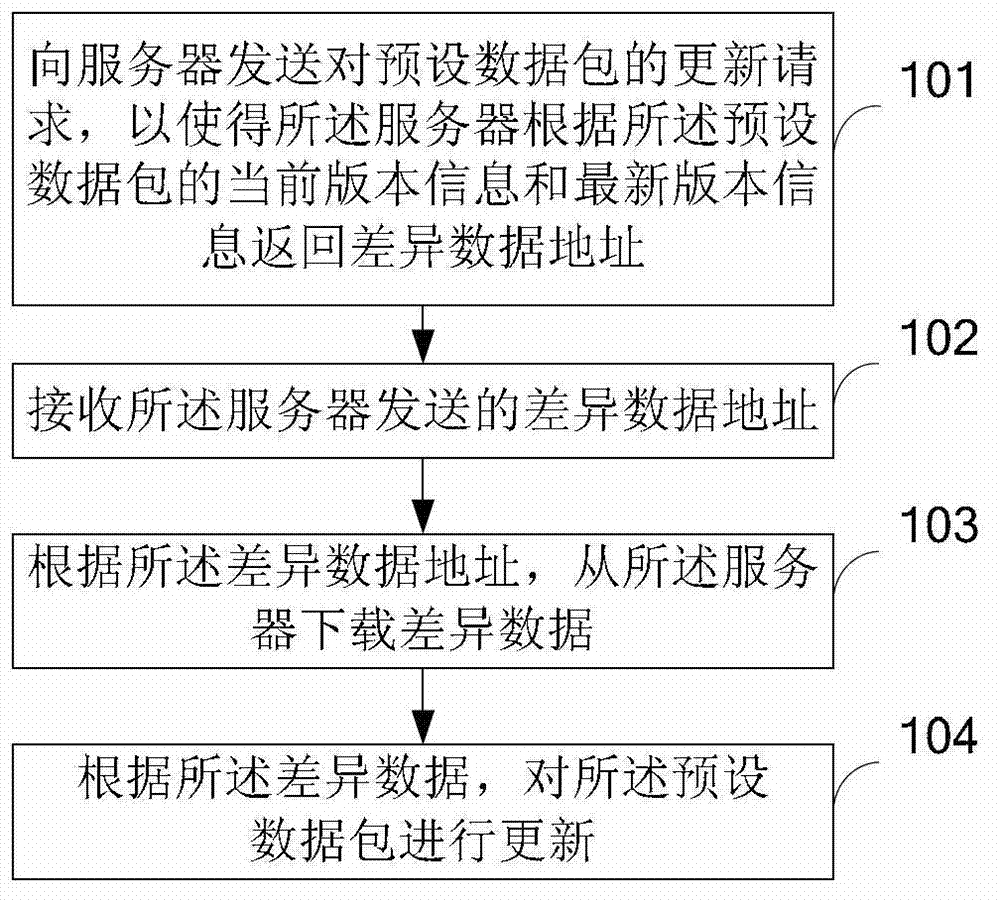
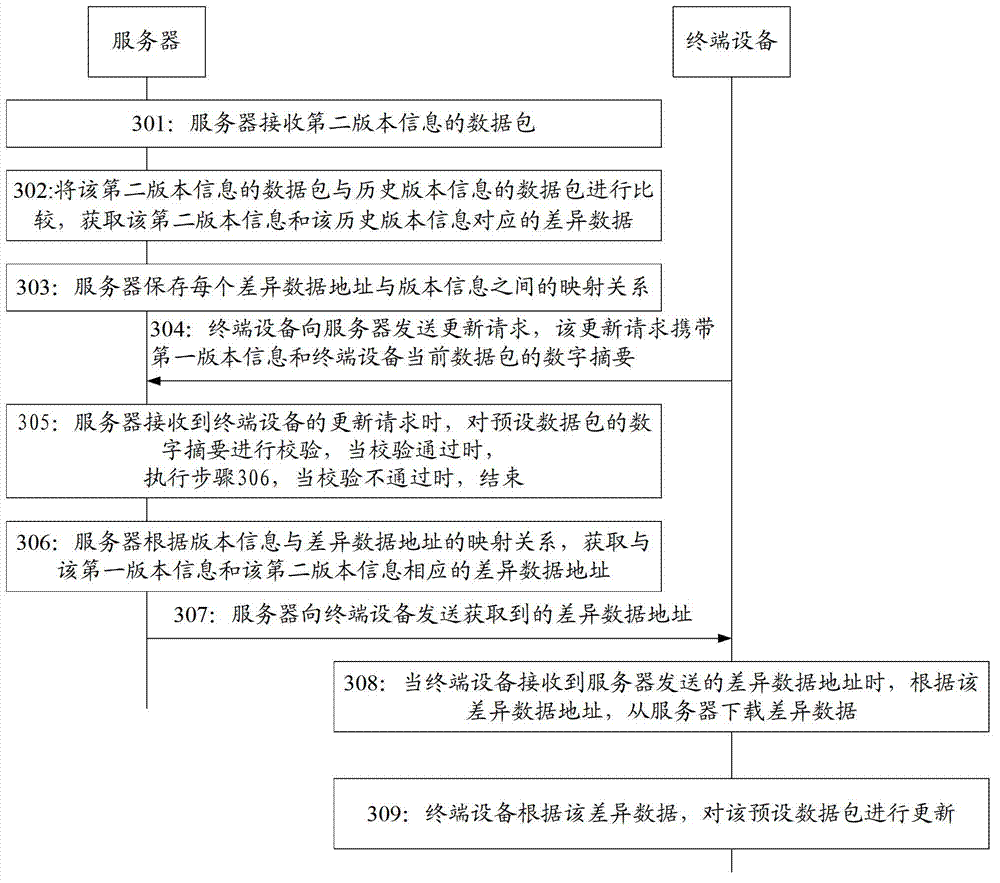
Data package updating method, device, terminal equipment and server
The invention discloses a data package updating method, a data package updating device, a terminal equipment and a server, and belongs to the technical field of communication. The method includes sending an update request of a preset data package to the server so that the server sends back a differential data address according to current version information and latest version information of the preset data package, receiving the differential data address sent by the server, downloading differential data from the server according to the differential data address, and updating the preset data package according to the differential data. Due to the fact that the update request of the preset data package is sent to the server, the differential data address sent by the server is received, the differential data is downloaded, and therefore users can avoid downloading of the whole data package when the data package is updated, downloading amount of the users is effectively reduced, network flow of the users is saved, and the downloading speed is increased.
Owner:XIAOMI INC
Method of managing character fonts within multimedia scenes, and the corresponding computer program and terminal
InactiveUS20090307585A1Avoid downloadingEfficient managementCathode-ray tube indicatorsComputer security arrangementsComputer graphics (images)Multimedia data streams
A method is provided for managing fonts in a radio communication terminal, which can receive fonts in order to render contents on a screen. One such method involves the use of the following elements in the terminal, namely: a font database that lists all of the fonts or font portions stored by the terminal and matches at least one management parameter with each of the fonts; and a set of font management commands, which is transmitted in a multimedia data flow.
Owner:STREAMEZZO
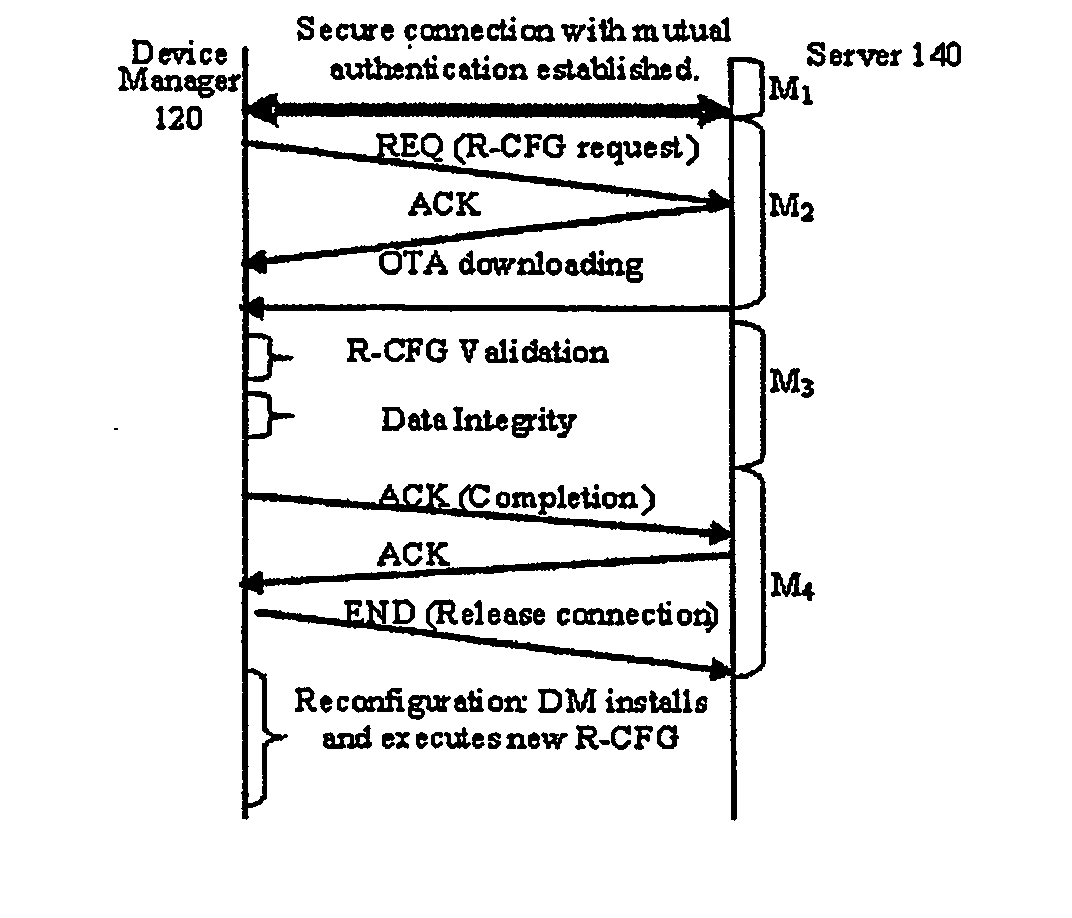
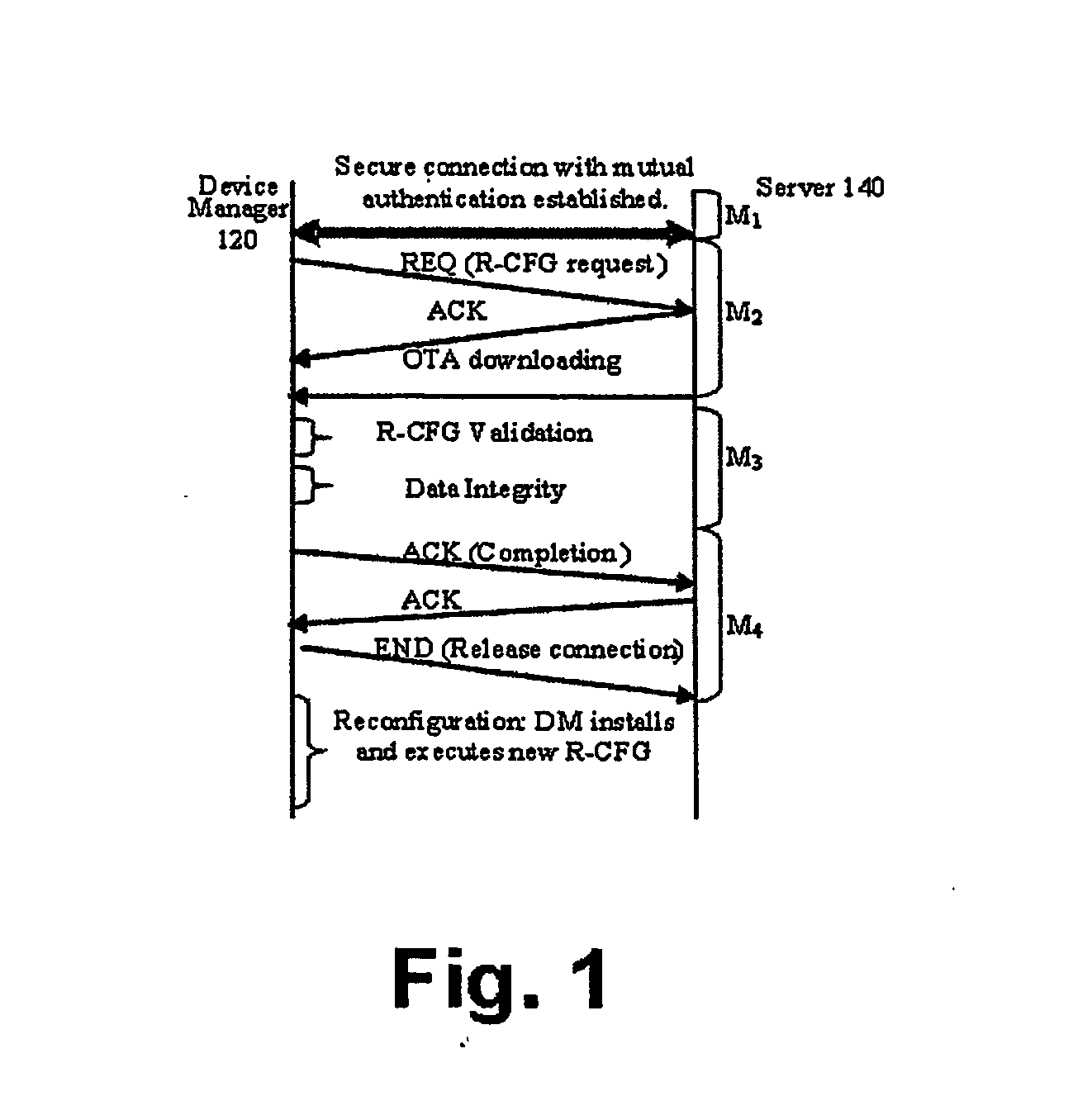
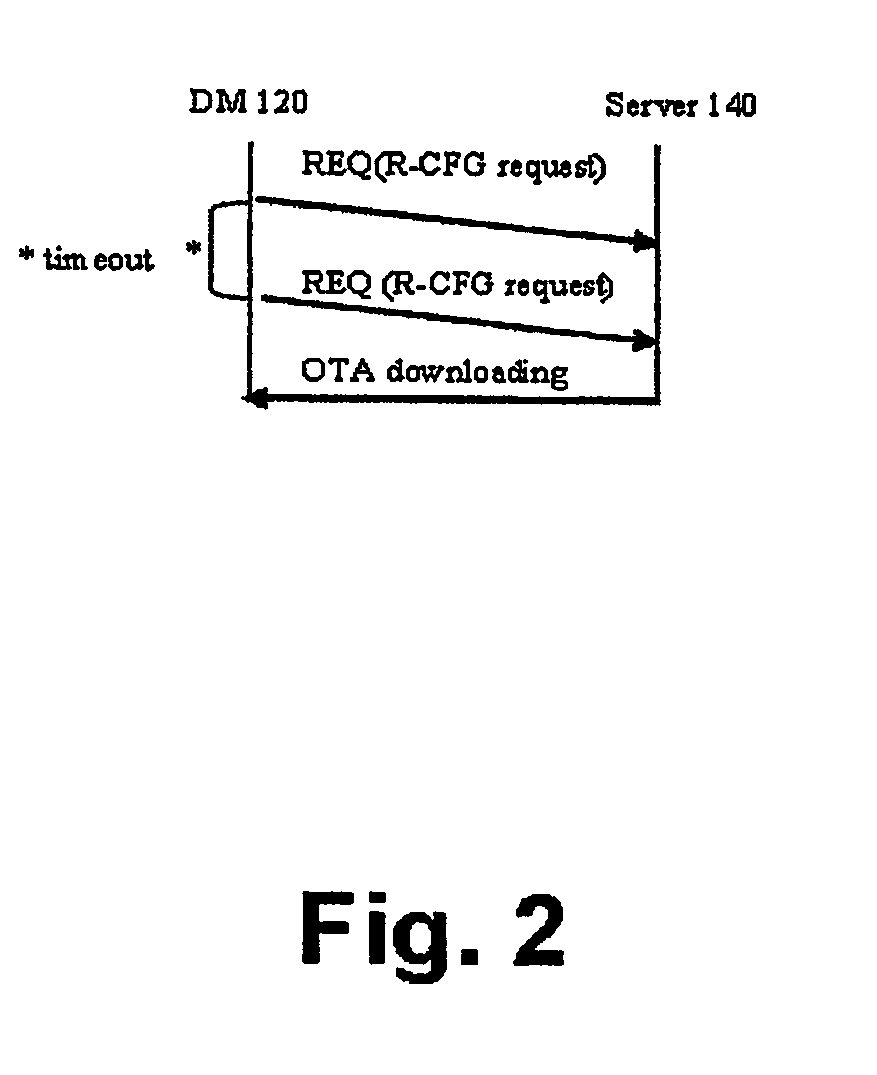
Software defined radio download
InactiveUS20060282497A1Avoid downloadingOvercome disadvantagesNetwork traffic/resource managementMultiple digital computer combinationsComputer hardwareSoftware define radio
A method for securely connecting a software defined radio (SDR) (110) to a server (140) through a network is presented. A request to download a radio configuration (R-CFG) file is sent from the SDR device to the server. A determination is made that the R-CFG file is configured to control a plurality of radio frequency parameters for the SDR device solely within levels permitted by a regulatory agency. The R-CFG is then downloaded to the SDR device.
Owner:SOVEREIGN PEAK VENTURES LLC
Method for sharing applications between terminals and terminal
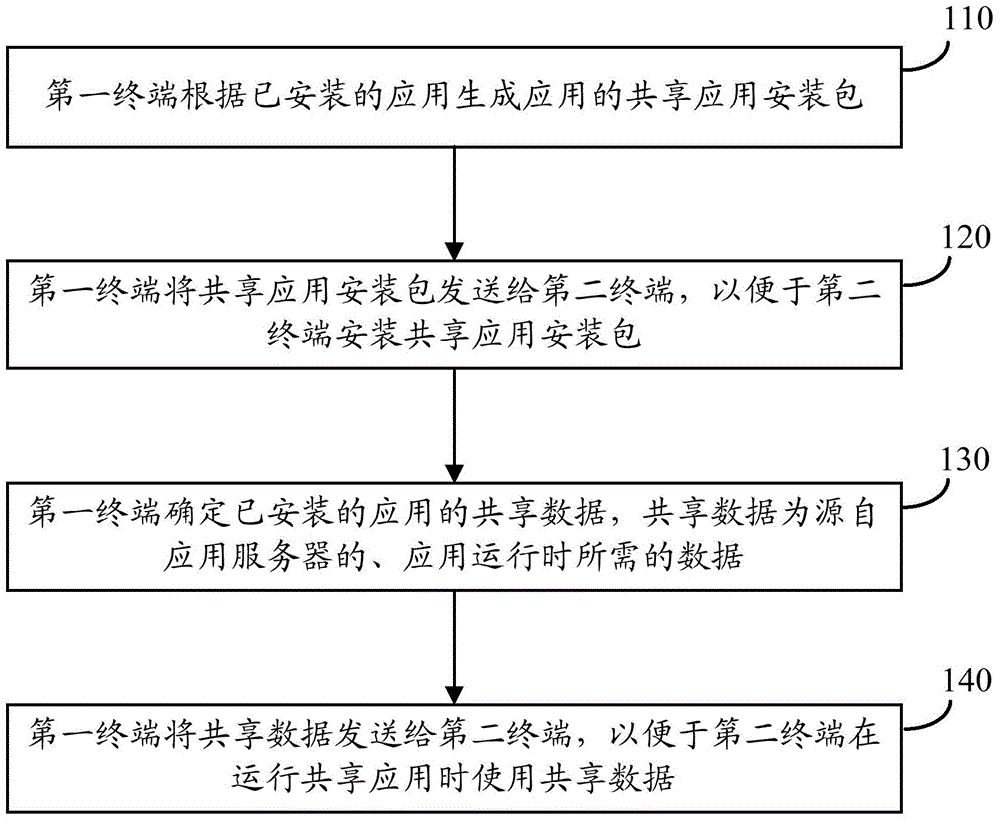
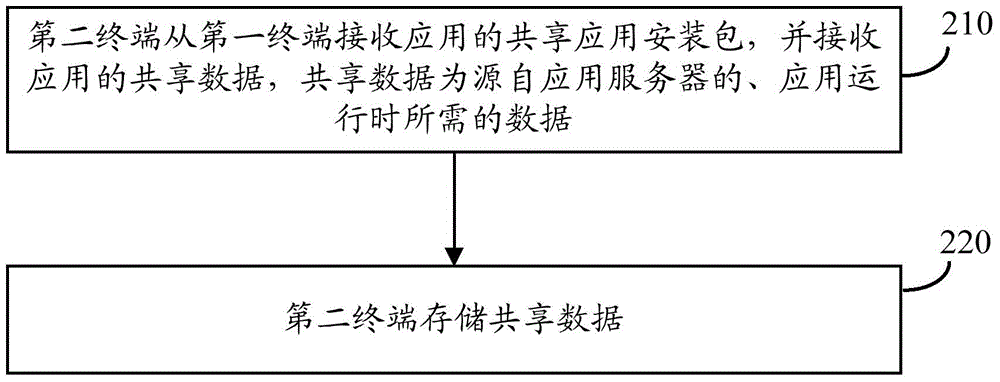
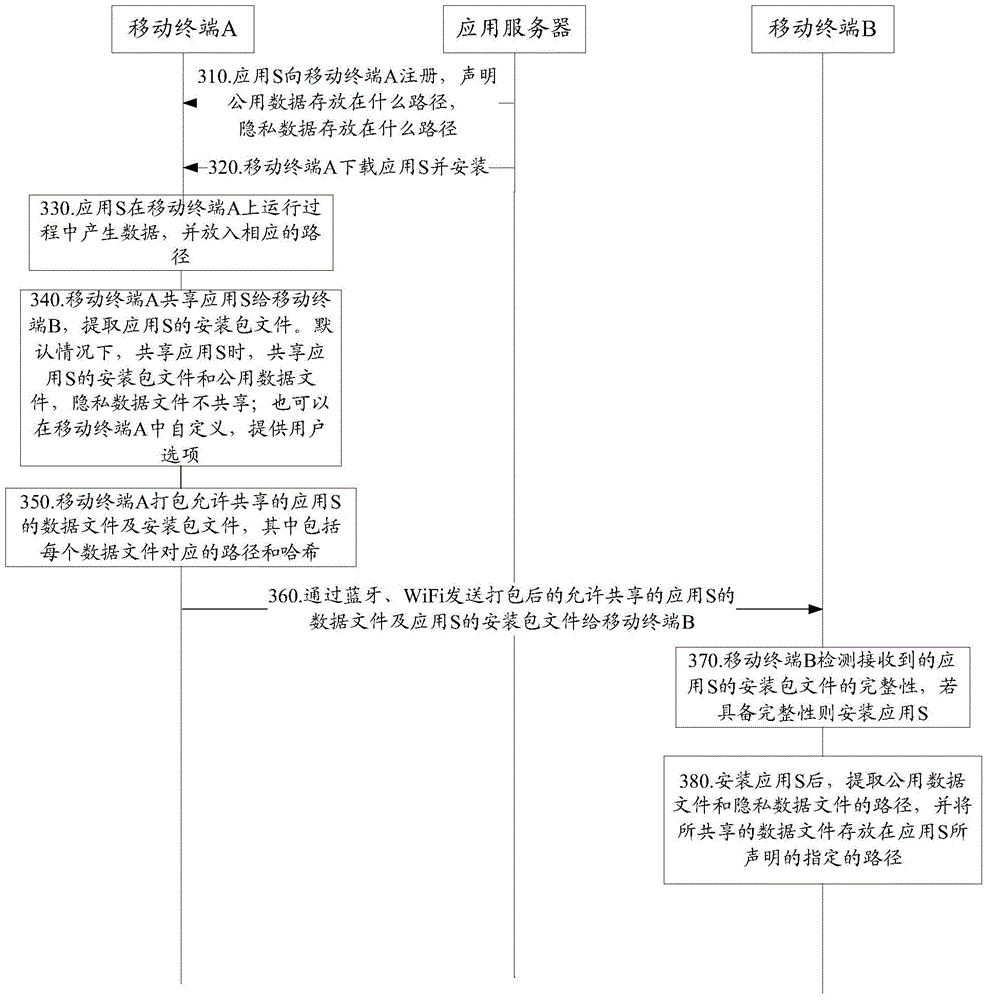
ActiveCN104683409AAvoid downloadingEasy to operateService provisioningTransmissionApplication serverComputer terminal
Embodiments of the present invention provide a method for sharing an application between terminals and the terminals, so as to facilitate operations of a reception end terminal user. The method comprises: a first terminal generating, according to an installed package, a shared application installation package of the application; the first terminal sending the shared application installation package to a second user, so that the second user installs the shared application installation package; the first terminal determining shared data of the installed application, the shared data being data coming from an application server and required during the operation of the application; and the first terminal sending the shard data to the second terminal, so that the second terminal uses the shared data when the second terminal operates the shared application. In the embodiments of the present invention, when two terminals share an application, the terminals share an installation package of the application and also share shared data of the application, thereby avoiding that a reception end downloads the shared data from an application server, facilitating operations of a reception end user, and improving the user experience.
Owner:HUAWEI DEVICE CO LTD
Resource file updating method, device and system and server
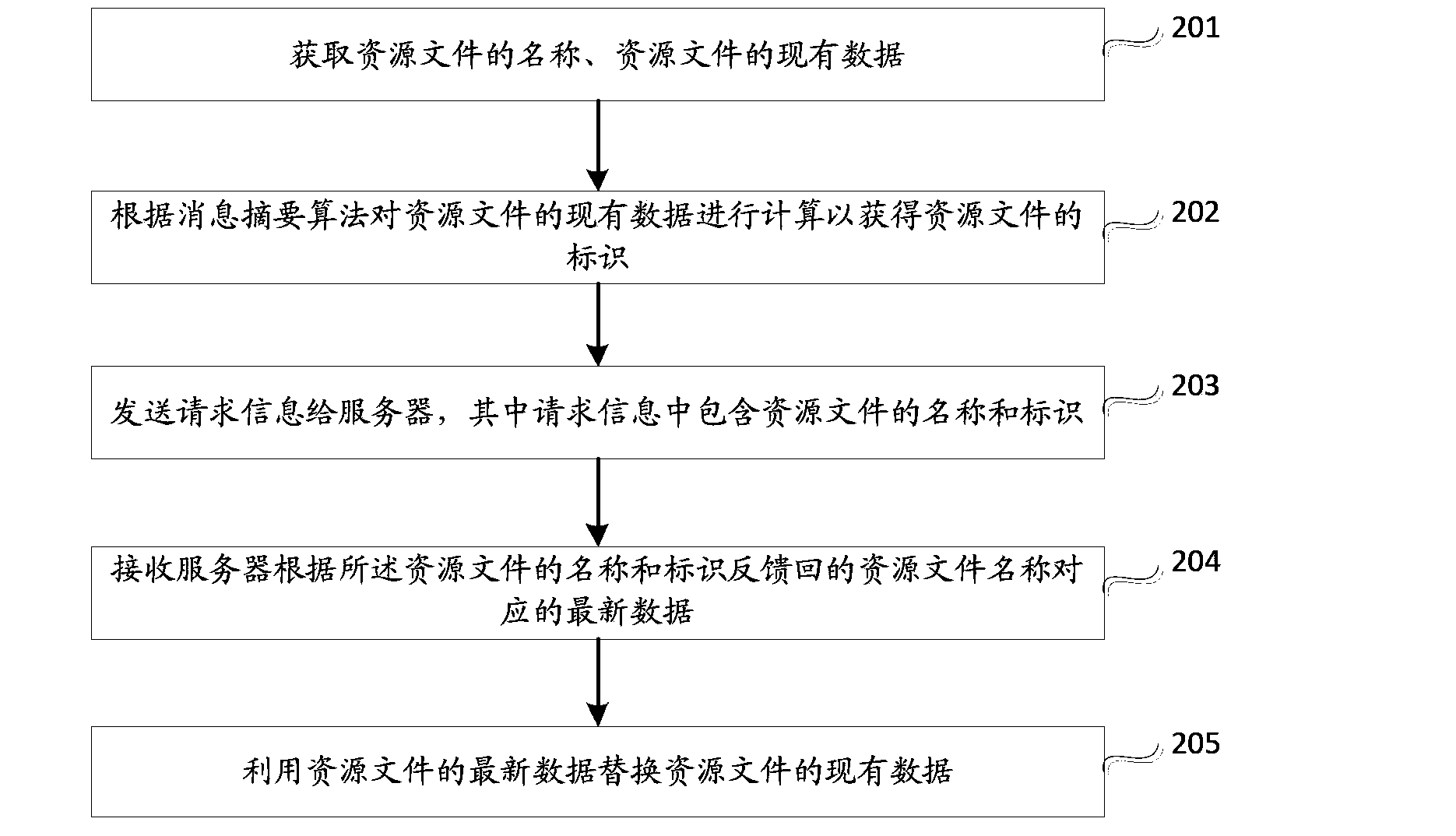
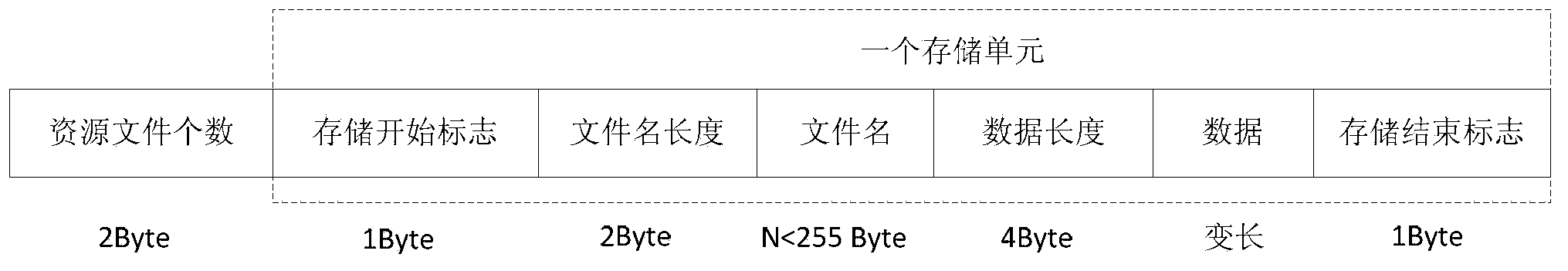
ActiveCN103678319ASave download timeReduce download burdenSpecial data processing applicationsSoftware deploymentResource fileComputer terminal
The invention discloses a resource file updating method, device and system and a server, and belongs to the technical field of computers. The method comprises the steps of sending a request message to the server, wherein the request message comprises the name and the identification of a resource file, and the identification is acquired according to the name of the resource file and available data of the resource file; receiving latest data which correspond to the name of the resource file and are fed back according to the name and the identification of the resource file by the server, and replacing the available data of the resource file through the latest data of the resource file. According to the resource file updating method, device and system and the server, whether the resource file is updated or not is judged by comparing data corresponding to the resource file on a mobile terminal and the server, if updating exists, the latest data of the resource file are acquired, so that automatic updating of the resource file is achieved, the fact that an entire installing package is downloaded again under the condition that certain resource files are updated is avoided, and the downloading burden of the mobile terminal is lowered.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Programming system and programming method thereof
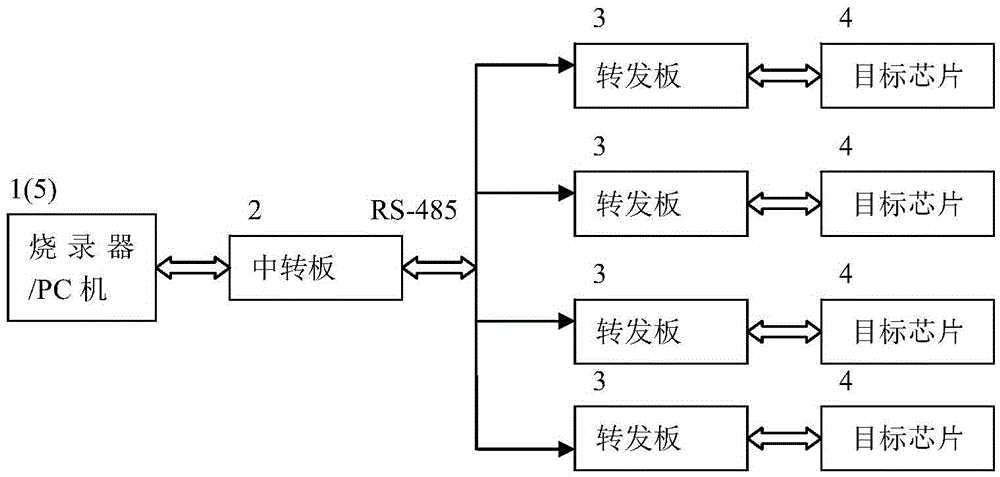
ActiveCN105607939ARealize offline programmingImprove programming efficiencyProgram loading/initiatingSoftware deploymentControl signalProgramming method
The invention discloses a programming system and a programming method thereof. The system comprises a programmer / PC, a transfer plate and at least one transmit plate, wherein level conversion circuits are arranged on the transfer plate and the transmit plate; the programmer is connected with the transfer plate; the transfer plate and the transmit plate are in communication connection through an RS-485 bus; the transmit plate is connected with a target chip in a one-to-one corresponding way; the transfer plate, the RS-485 bus and the transmit plate form a communication path. The method comprises the following steps: converting a target program into a binary BIN file; converting the binary BIN file into data meeting an IPS protocol; sending control signals through the communication path and controlling the target chip into an IPS download mode; sending a synchronization frame to the target chip through the programmer from the communication path to perform synchronization; reading the model and sector of the target chip through the programmer / PC after synchronization, and writing the model and sector into a program. The system has the advantages that off-line programming can be realized, one-to-multiple parallel programming can be realized, the programming efficiency is improved, and the system cost is low.
Owner:ZHANGZHOU CANNET ELECTRICAL APPLIANCE
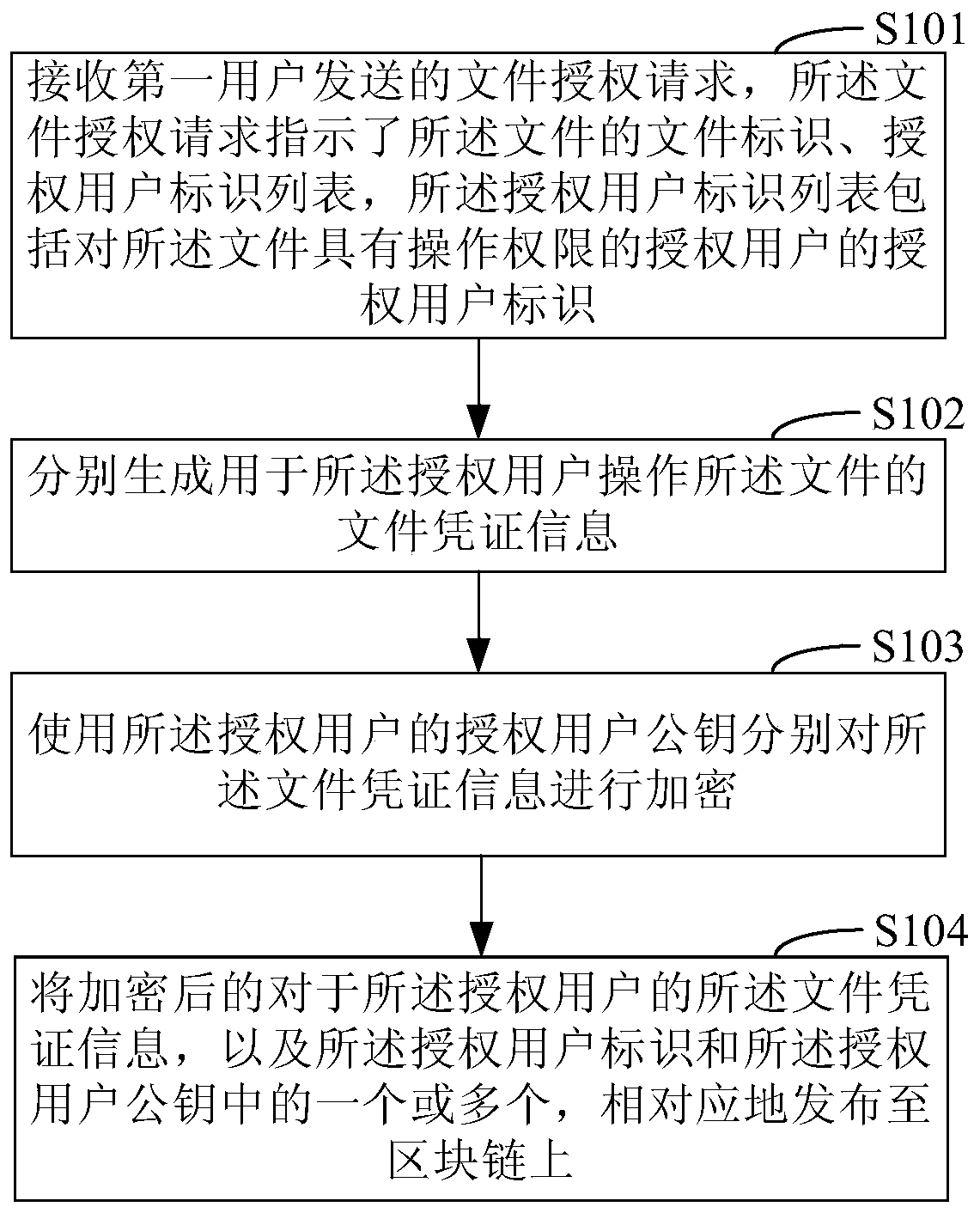
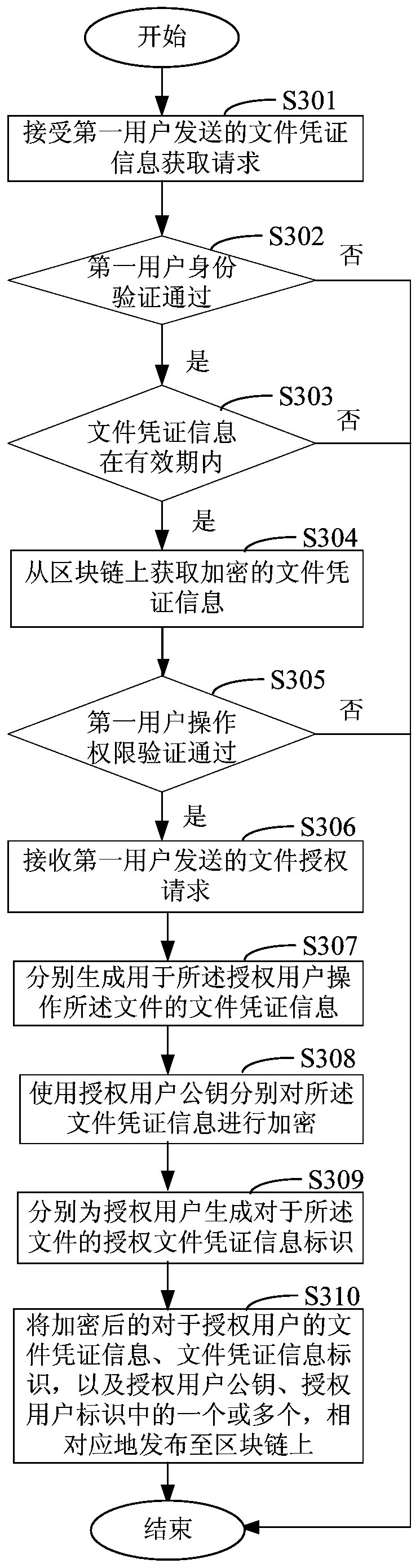
File authorization access method, device and system based on block chain
InactiveCN110636043AAvoid uploads and downloadsImprove securityUser identity/authority verificationBlockchainUser identifier
The invention discloses a file authorization access method, device and system based on a block chain, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: receiving a file authorization request sent by a first user, wherein the file authorization request indicates an authorized user identifier list and a file identifier of the file,and the authorized user identifier list comprises an authorized user identifier of an authorized user having an operation authority for the file; respectively generating file certificate information for the authorized user to operate the file; respectively encrypting the file certificate information by using an authorized user public key of the authorized user; and correspondingly publishing the encrypted file certificate information for the authorized user and one or more of the authorized user identifier and the authorized user public key to a block chain. According to the embodiment, file uploading or downloading in the file authorization process is avoided, the file security is improved, and network resources are saved.
Owner:THE PEOPLES BANK OF CHINA DIGITAL CURRENCY INST
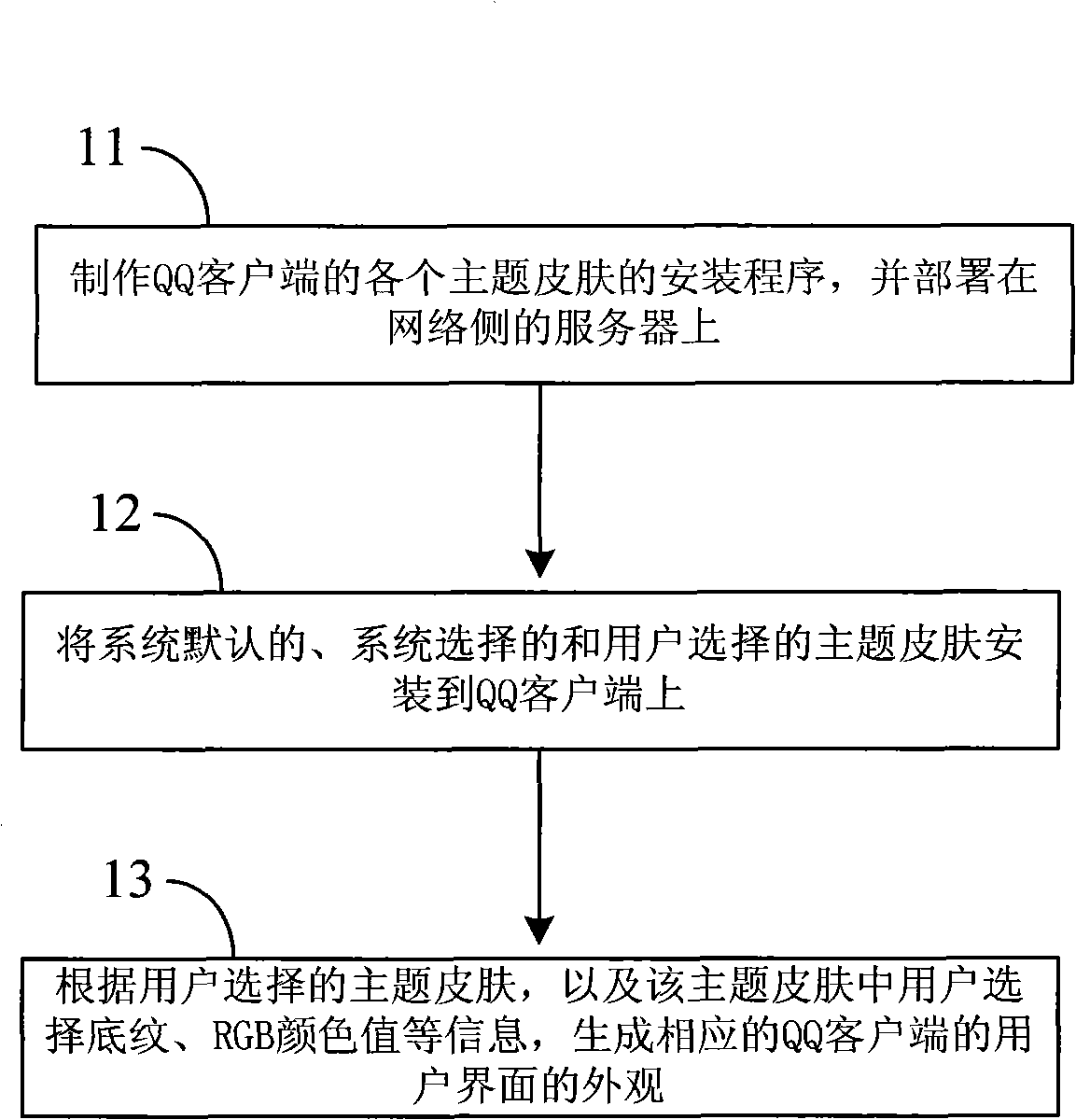
Method and device for outputting user interface of client
InactiveCN101561747AMeet the needs of personalized experienceChange appearance flexiblyProgram loading/initiatingInput/output processes for data processingPersonalizationClient-side
The invention provides a method and a device for outputting a user interface of a client. The method mainly comprises the following steps: providing a plurality of theme skins to the client, wherein each theme skin comprises a plurality of shading patterns and red-green-blue (RGB) color values; and outputting the user interface of the client according to the theme skin selected by a user, and information on shadings and the RGB color values selected by the user in the theme skins. By using the method and the device, the user can select the information of the shadings, the RGB color values and the like under the theme skins at will according to personal wishes, and can define the RGB color values under the theme skins by self. Thus, the user can flexibly change the appearance of the user interface of the client, and the personalized experience requirements of the user are better satisfied.
Owner:TENCENT TECH (SHENZHEN) CO LTD
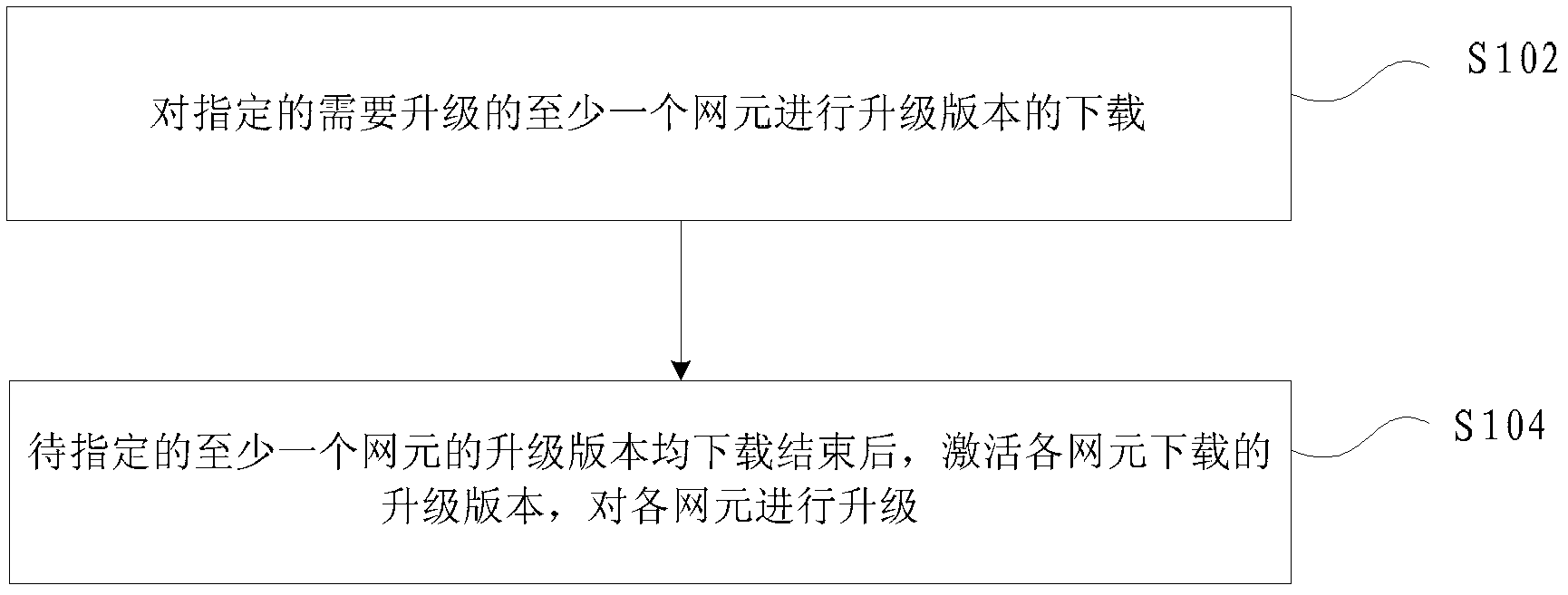
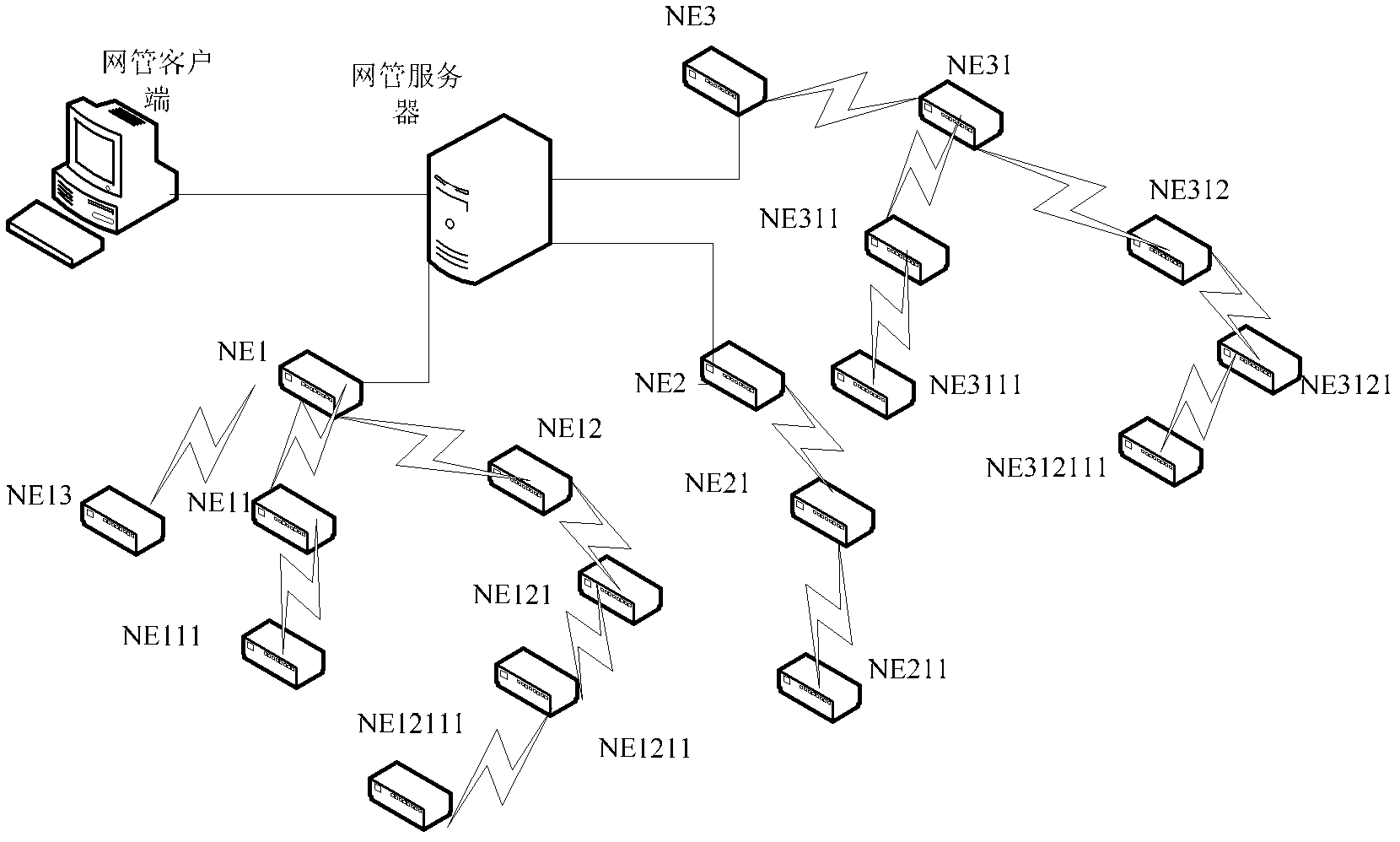
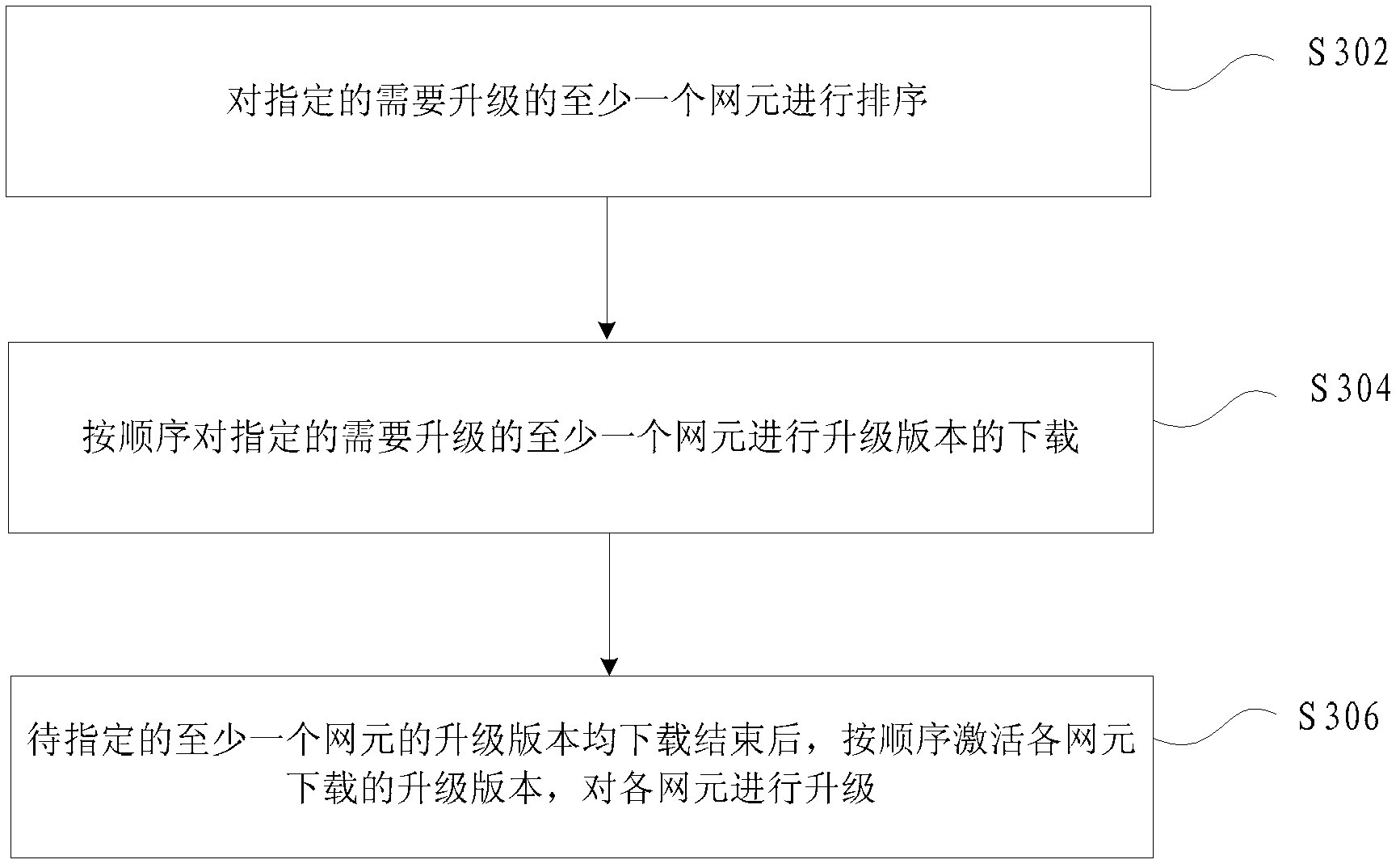
Method and device for updating network elements
InactiveCN103139245AAvoid downloading and business interruptionImprove download speed and service qualityProgram loading/initiatingData switching networksNetwork elementDistributed computing
The invention discloses a method and a device for updating network elements. The method comprises performing upgrade version downloading on at least one designated network element needing updating; and activating the upgrade versions downloaded by the network elements after upgrade versions of the at least one network element are downloaded, and updating the network elements. By means of the method and the device for updating network elements, the problem of service interruption of far-end network elements with near-end networks as starting points caused by reboot operation in near-end network element updating in correlation techniques can be solved, and the network bandwidth is fully used.
Owner:ZTE CORP
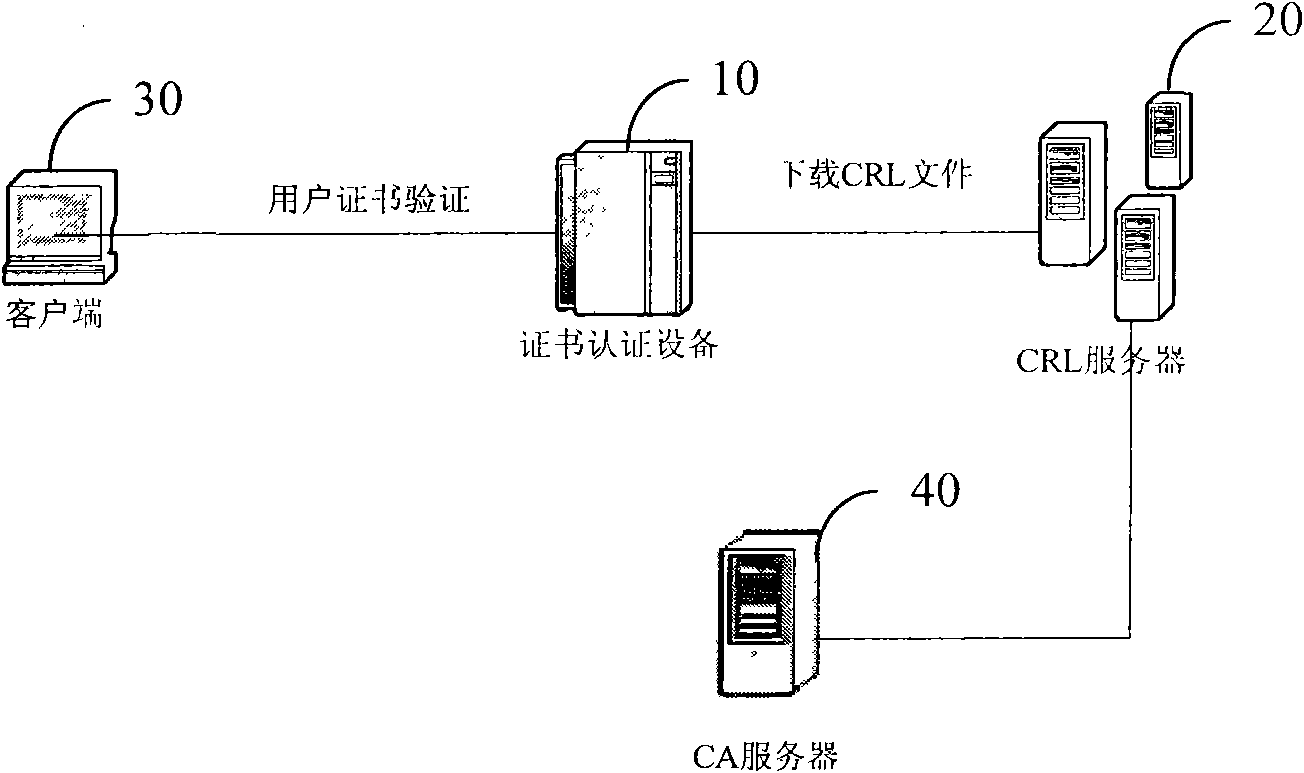
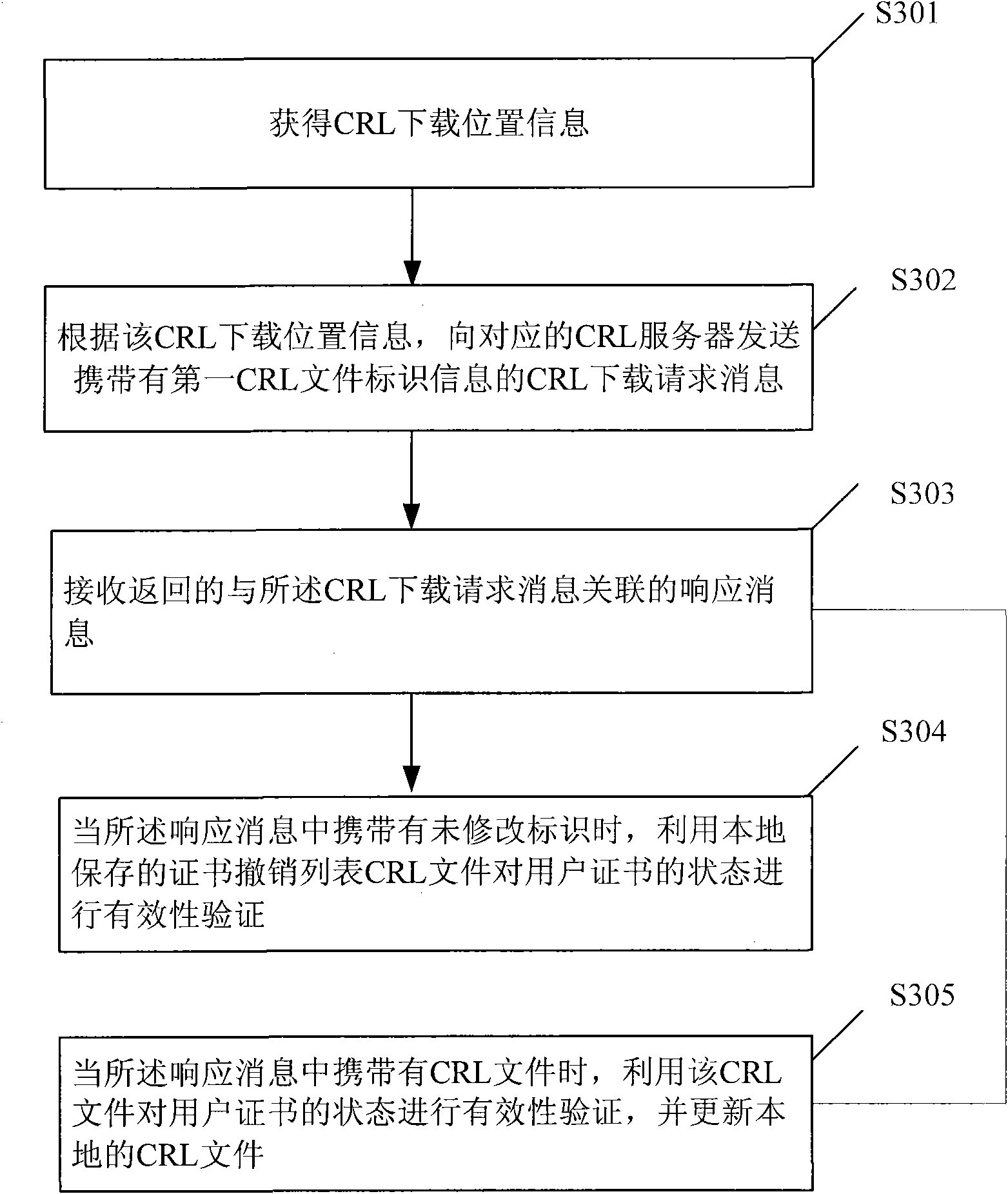
Method, apparatus and system for validating certificate state
InactiveCN101572707AAvoid downloadingAvoid duplicate downloadsPublic key for secure communicationUser identity/authority verificationValidation methodsOperating system
An embodiment of the invention provides a validation method of certificate state, a certificate authenticating apparatus, a certificate revocation list (CRL) server and a CRL system; wherein the CRL system comprises the certificate authenticating apparatus and the CRL server; the certificate authenticating apparatus is used for transmitting a CRL downloading request message carrying a first CRL file identification information to the corresponding CRL server according to the obtained CRL downloading position information and validating the validity of the state of a user certificate by using a locally stored certificate revocation list (CRL) file when a received response message associated with the CRL downloading request message carries unmodified identification; and the CRL server is used for comparing the first CRL file identification information in the received CRL downloading request message with the second CRL file identification information of the corresponding CRL file on the CRL server and returning the response message carrying the unmodified identification when the comparison result is that the first CRL file identification information is the same as the second CRL file identification information. Such a technical proposal prevents from downloading the CRL repeatedly so as to ease network load.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Low latency streaming media
ActiveUS20200267437A1Reduce latencyImproving delivery and processingTransmissionSelective content distributionMediaFLOTransmission system
Content streaming systems, such as systems that use HTTP compliant requests to obtain media segments for presentation of the content on a device. These content streaming systems can be optimized to reduce latency to a low level so that live events can be streamed to receiving devices in such a manner so that the time between an action in the live event and the presentation of the action on a receiving device that receives the streamed content is less than about 10 seconds. A client device can use rendition reports to tune-in to a new rendition (at a first bit rate) after presenting a prior rendition (of a second bit rate) when switching between the different bit rates; also, for example, a client device can use playlist annotations that indicate independent frames to avoid downloading depending frame media segments when switching between different renditions.
Owner:APPLE INC
Content download system and its method
InactiveCN1397896AAvoid downloadingDigital data processing detailsMultiple digital computer combinationsWeb browserTerminal equipment
Owner:SAMSUNG ELECTRONICS CO LTD
Method and system for installing application programs into mobile terminals
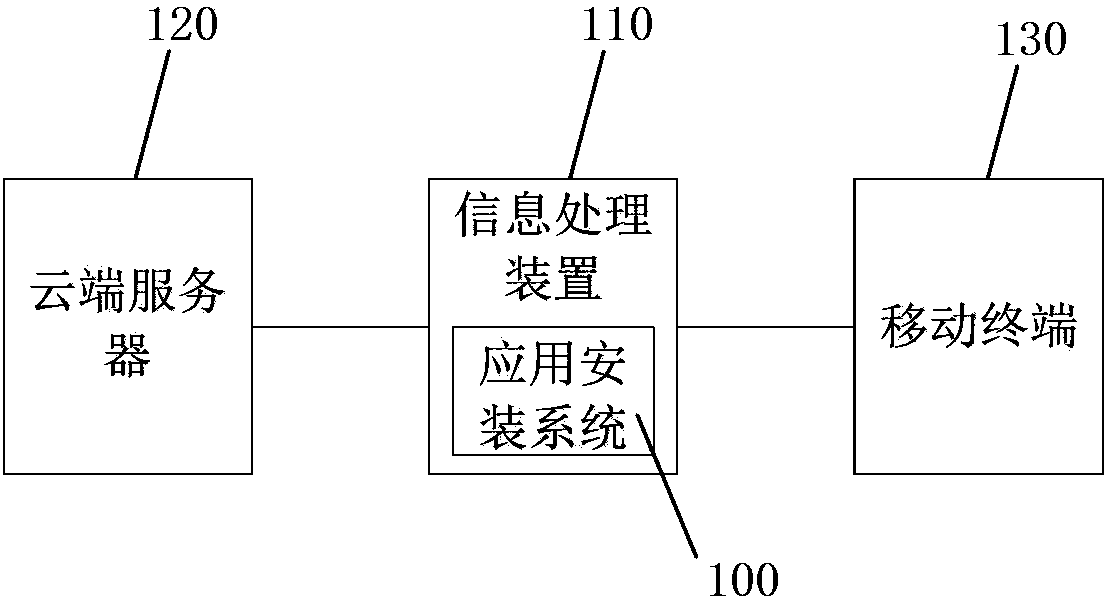
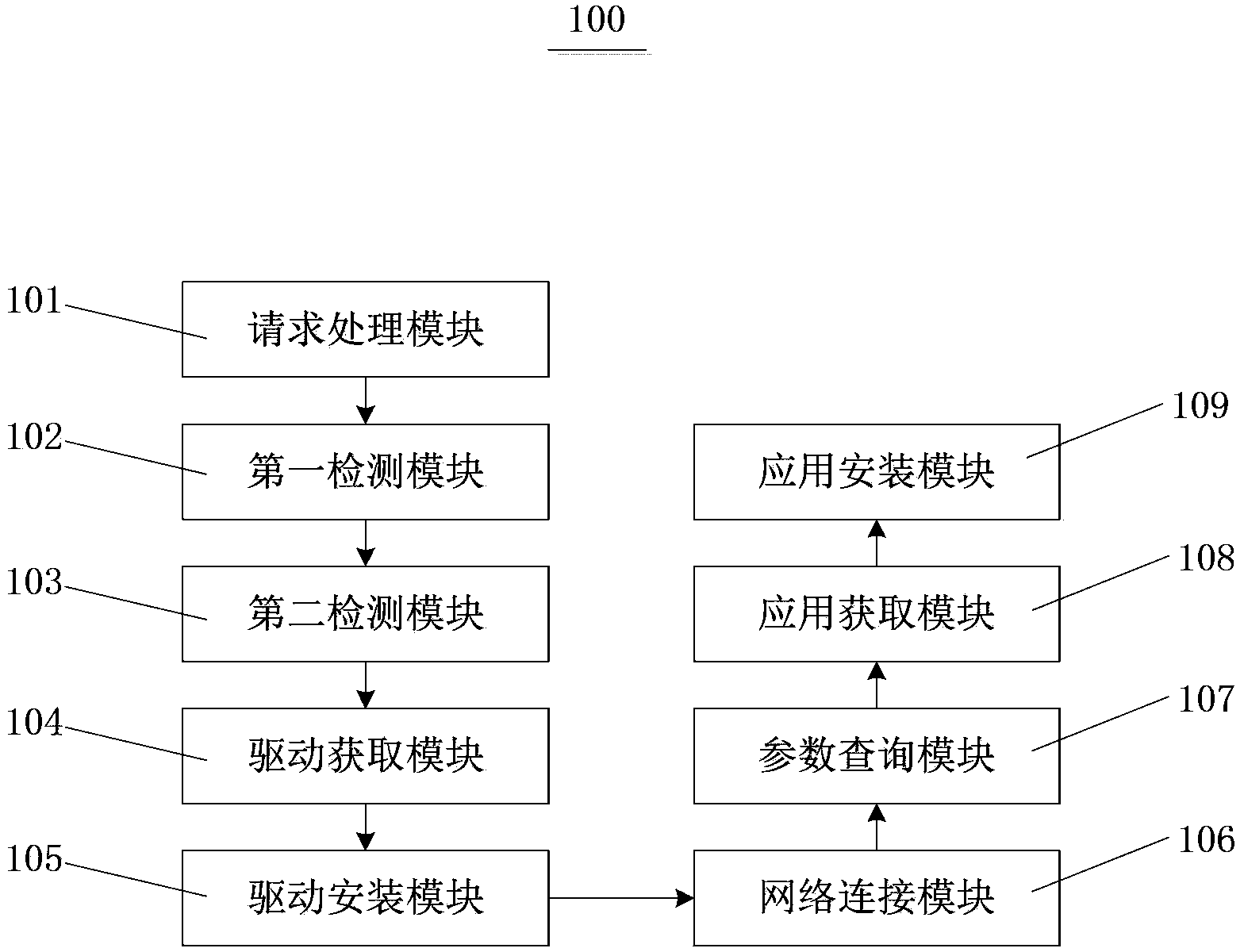
InactiveCN104111844AShorten the timeAvoid downloadingProgram loading/initiatingInformation processingNetwork connection
Systems and methods are provided for installing an application on a mobile terminal. For example, one or more first drivers are obtained based on at least information associated with identification of a first mobile terminal; the first drivers are installed on an information-processing device; a network connection between the information-processing device and the first mobile terminal is established based on at least information associated with the first drivers; one or more local parameters of the first mobile terminal are queried through the network connection; an application-installation package is obtained based on at least information associated with the local parameters; and an application is installed on the first mobile terminal using the network connection based on at least information associated with the application-installation package.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for issuing relative information of key characters of internet
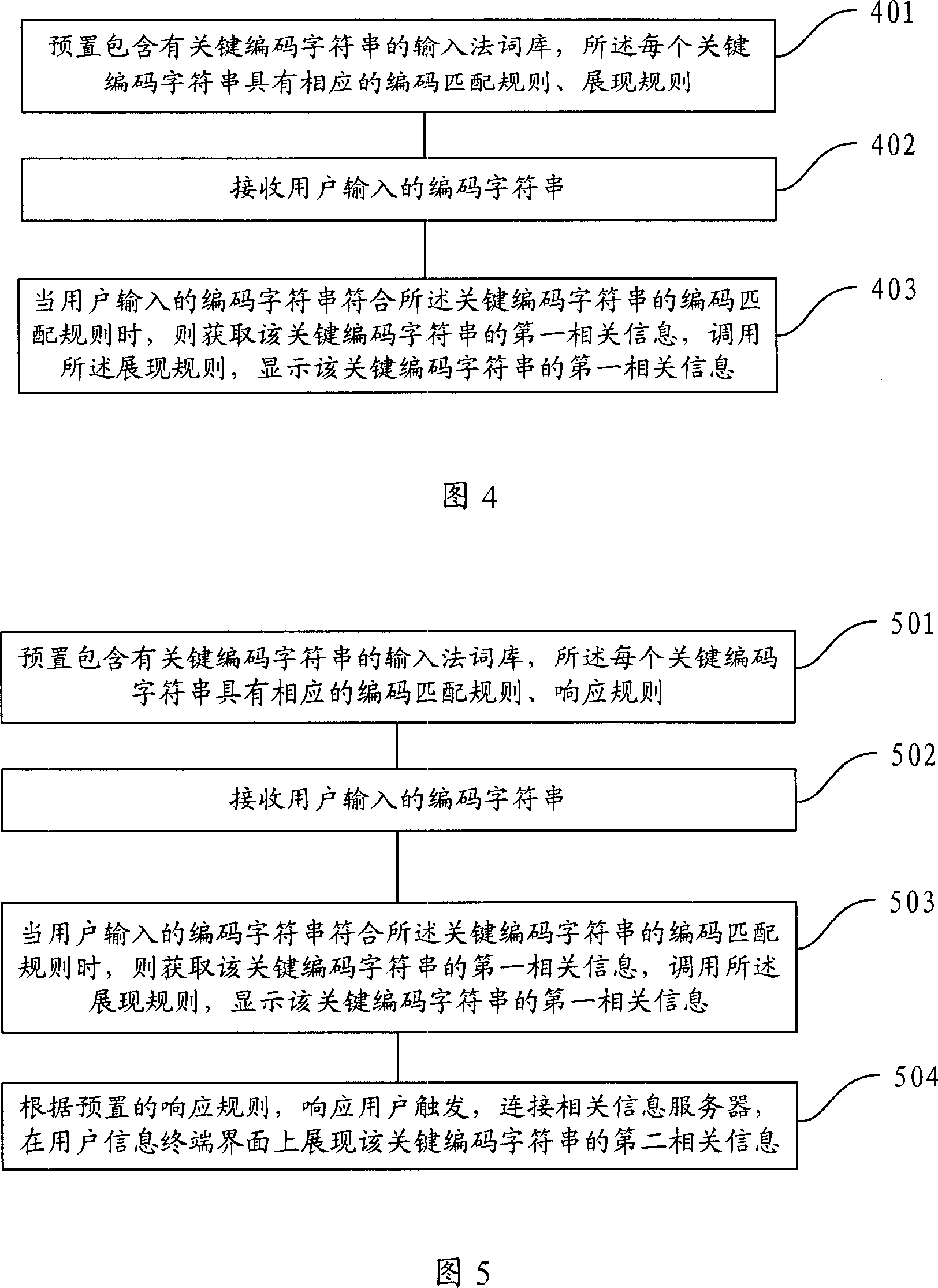
InactiveCN1971568ABroaden the way to connectMeet needsDigital data information retrievalSpecial data processing applicationsInternet communicationRelevant information
The invention discloses an issuing method of the relative information of internet keywords that includes following steps: presetting the word stocks of input method with keywords, said keywords have relative code match rule and display rule; receiving the code character string input by the users, and match with the word stocks of input method to obtain the candidate words; when the candidate words contain said keywords, the display rule is called, and the conformed display information is displayed by the means of determined rule. Said method can be used to issue the relative information of the key code character string. The invention opens up a new issuing method and system for the relative information of internet keywords, and widens the connecting path between the relative information of keywords between the users. The invention can reduce the application experience at minimum limit, and it can avoid downloading the unnecessary, invalid or useless keywords to the local, and improve the availability ratio of internet communication source.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Application program processing method and device and computer equipment
ActiveCN110166543AImprove download speedReduce bandwidth costsTransmissionApplication softwareComputer engineering
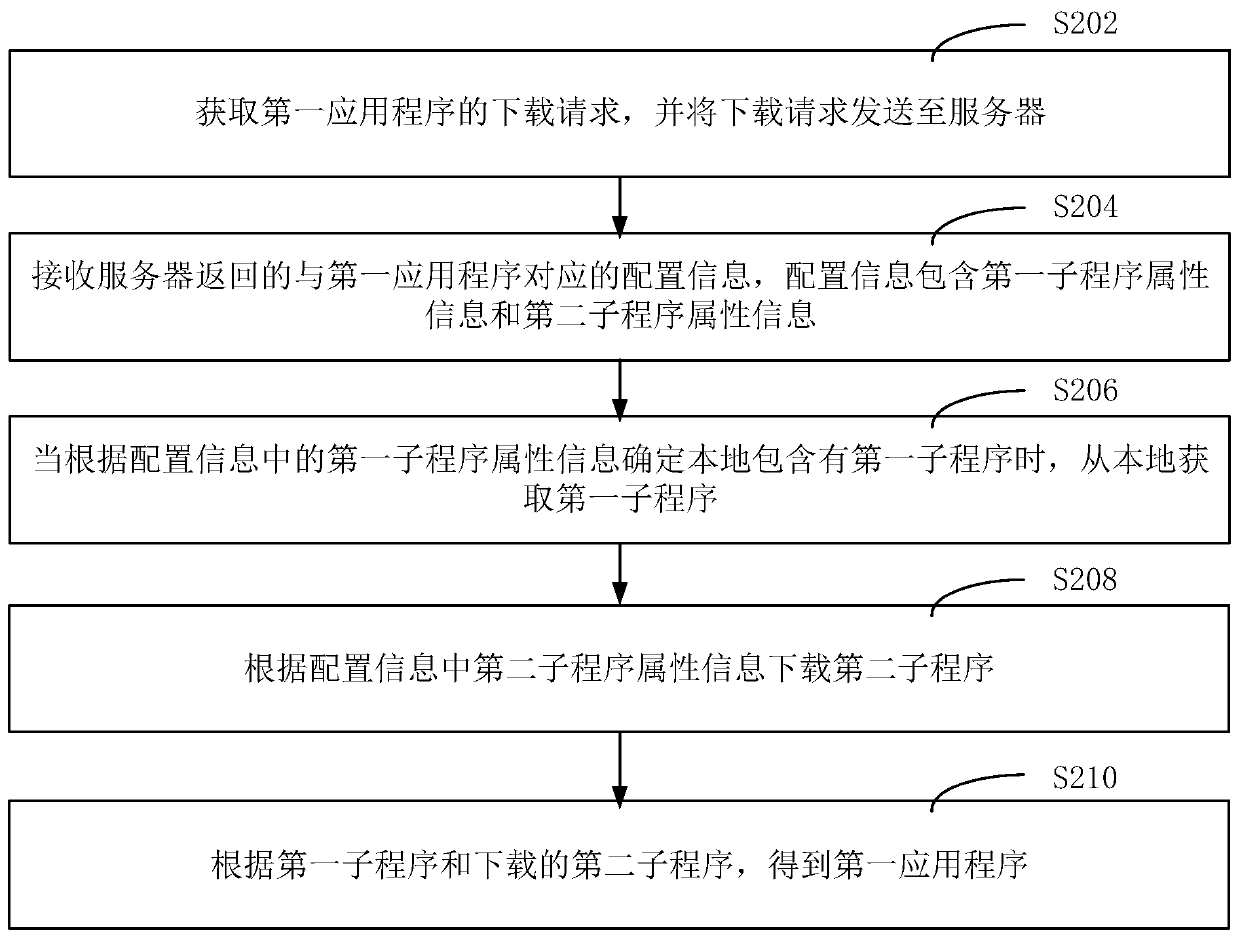
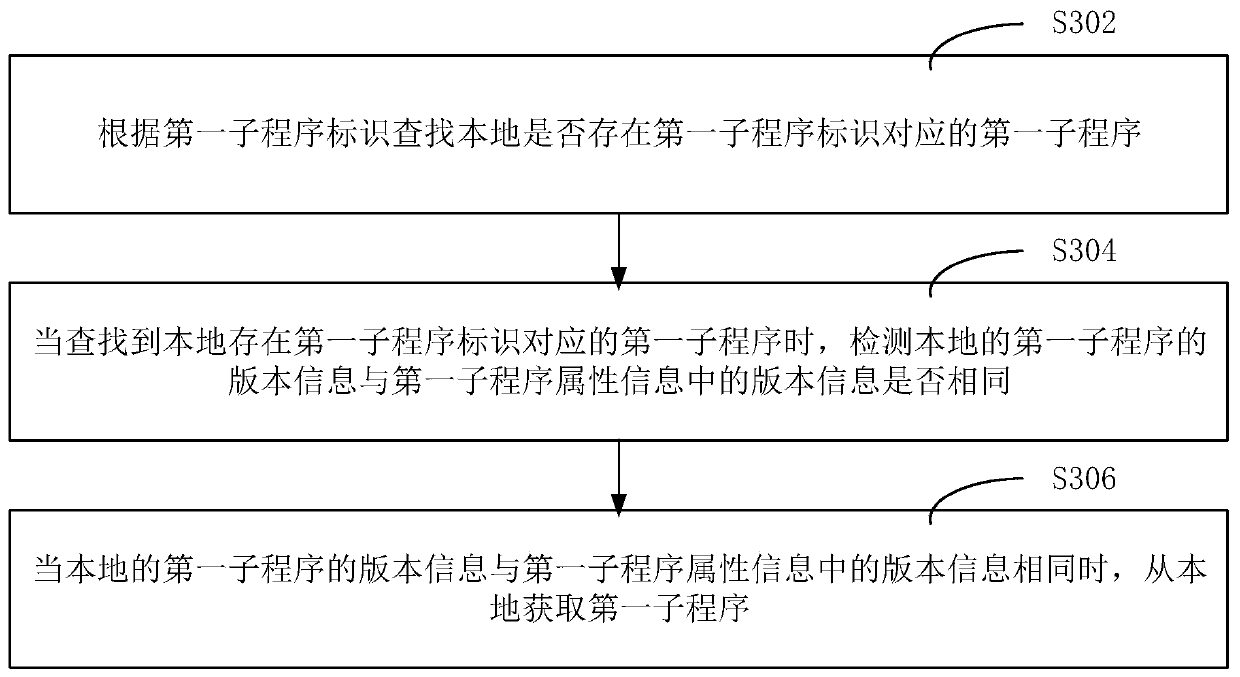
The invention relates to an application program processing method and device, a computer readable storage medium and computer equipment, and the method comprises the steps: obtaining a downloading request of a first application program, and sending the downloading request to a server; receiving configuration information which is returned by the server and corresponds to the first application program, wherein the configuration information comprises first sub-program attribute information and second sub-program attribute information; when it is determined that the first sub-program is containedlocally according to the first sub-program attribute information in the configuration information, obtaining the first sub-program locally; downloading a second sub-program according to the attributeinformation of the second sub-program in the configuration information; and obtaining the first application program according to the first subprogram and the downloaded second subprogram. According tothe scheme provided by the invention, the downloading speed of the application program can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
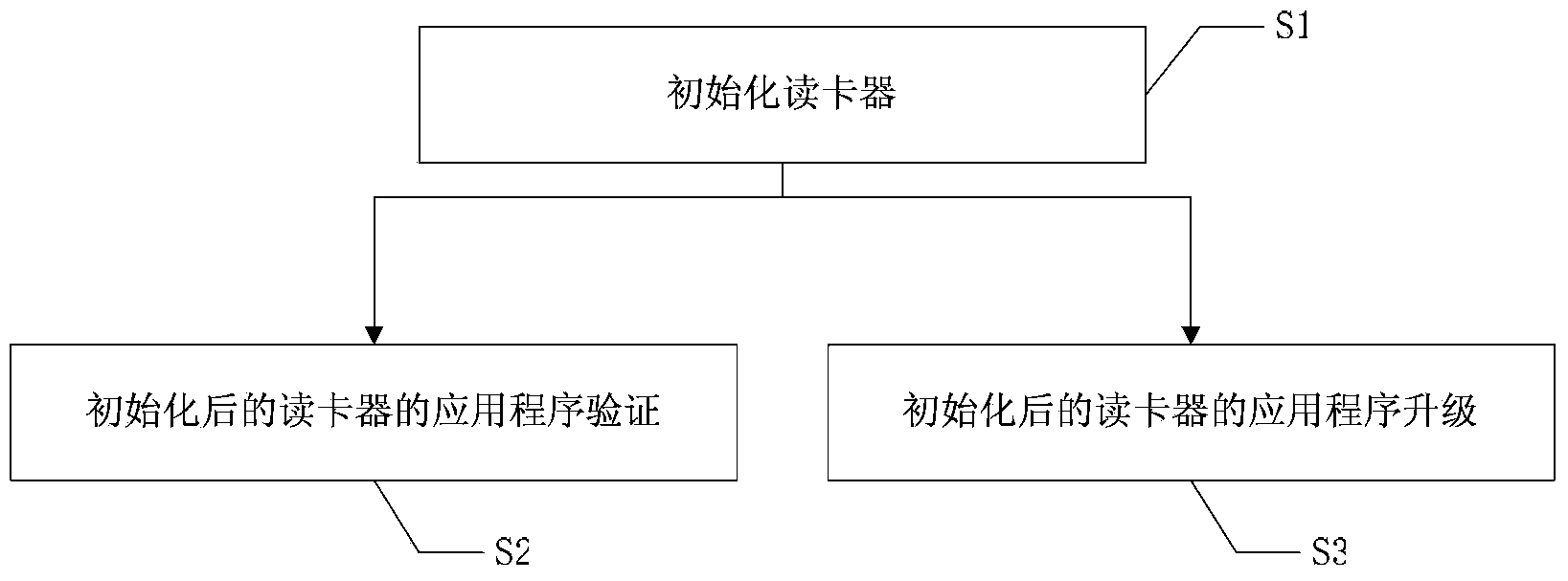
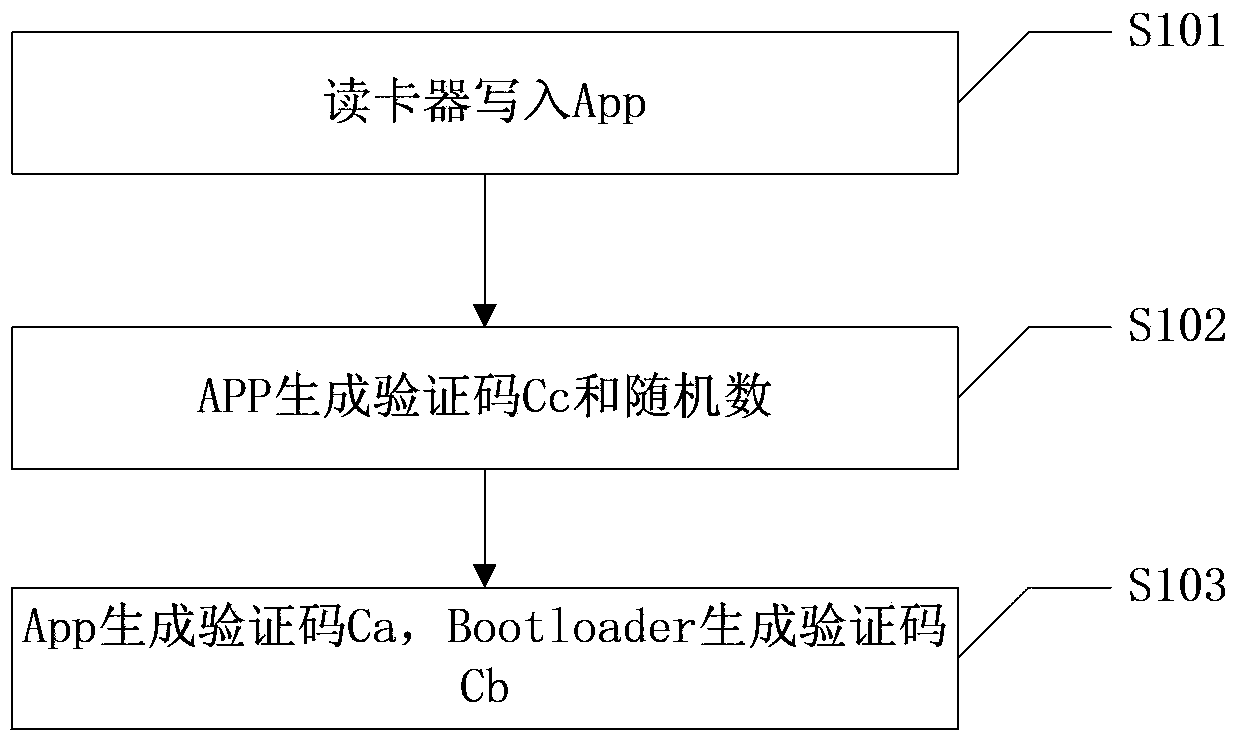
Application encipherment protection method of card reader
ActiveCN103366103AAvoid downloadingAvoid upgradeSensing record carriersProgram/content distribution protectionMicrocontrollerCard reader
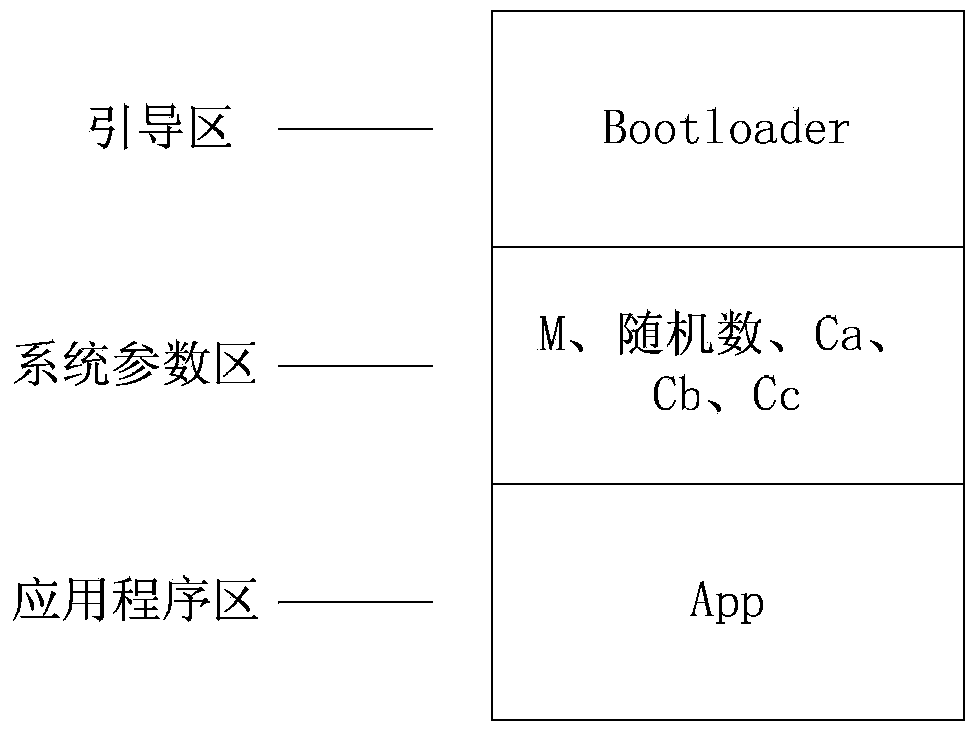
The invention relates to an application encipherment protection method of a card reader. The method adopts a three verification techniques: (1) the verification of an App (Application) to Bootloader is used for verifying the validity of the bootloader; the App is executed if the verification passes, or else, the App performs self-destruction; and the situation that the App is acquired illegally and used for other illegal test or production is avoided; (2) the verification of the App to unique CID (Chip Identification) of a singlechip is used for binding the App with a corresponding chip; and even if chip contents are illegally copied to another chip, the App cannot run normally; and (3) the verification of the Bootloader to the App is used for verifying the validity of the App; and an illegal App is prevented from being downloaded and upgraded.
Owner:广东岭南通股份有限公司
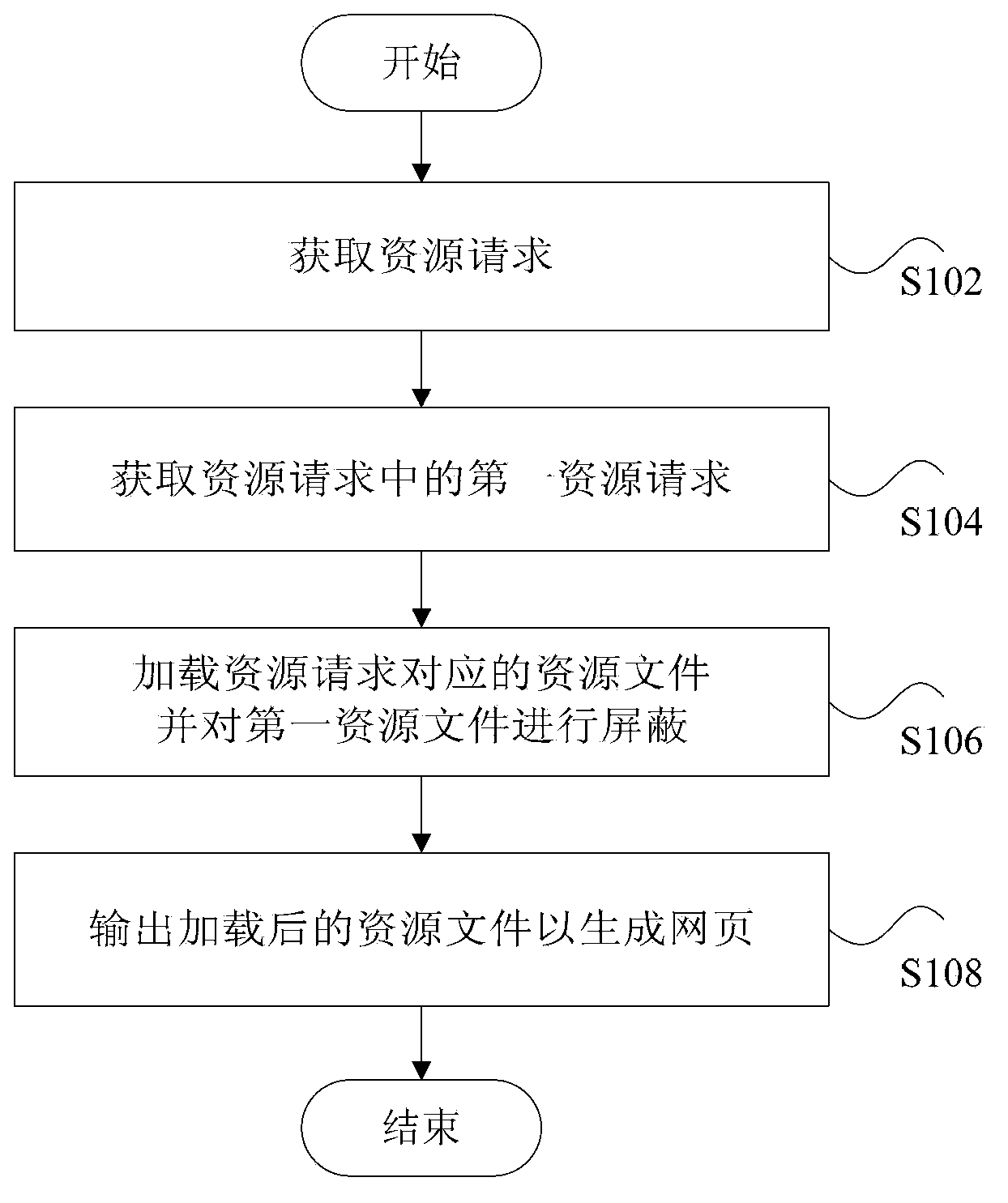
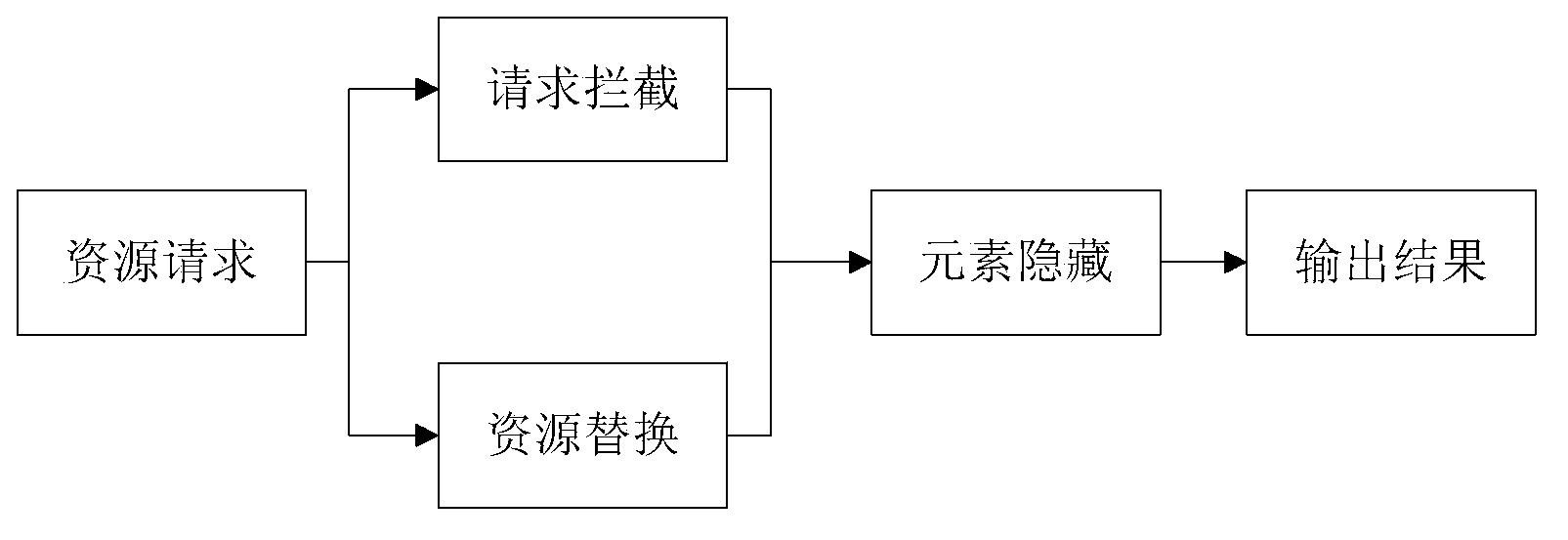
Webpage element shielding method and device
InactiveCN103810193AImprove loading speedAvoid downloadingSpecial data processing applicationsWeb pageOperating system
The invention discloses a webpage element shielding method and device, wherein the webpage element shielding method comprises the steps of acquiring a resource request; acquiring a first resource request in the resource request, wherein a resource file corresponding to the first resource is a shielding resource; loading the resource file corresponding to the resource request and shielding the first resource file, wherein the first resource file is the resource file corresponding to the first resource request; outputting the loaded resource file to generate a webpage. By the webpage element shielding method and device, the problem of the reduced webpage loading speed easily caused by the webpage element shielding method in the prior art is solved, and the effect of improving the webpage loading effect is achieved.
Owner:KINGSOFT +3
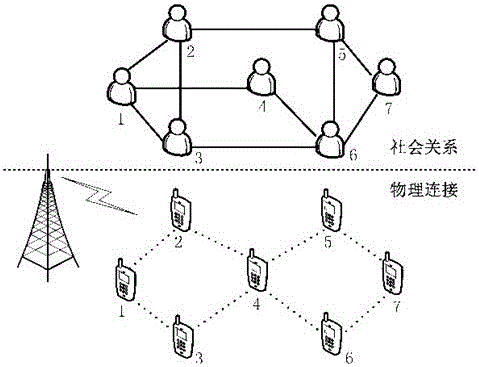
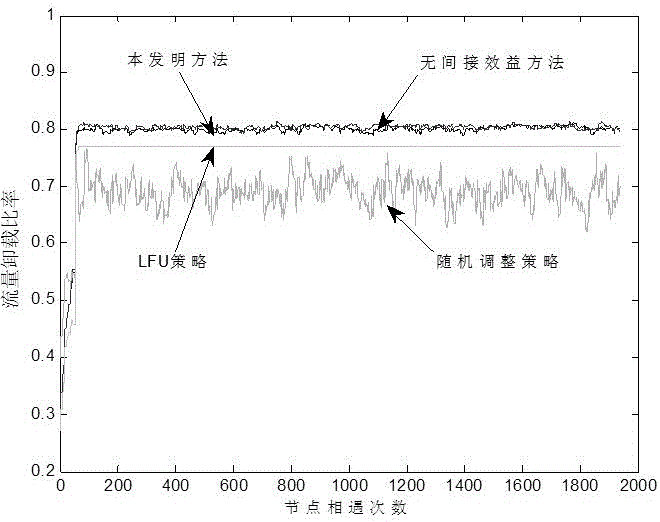
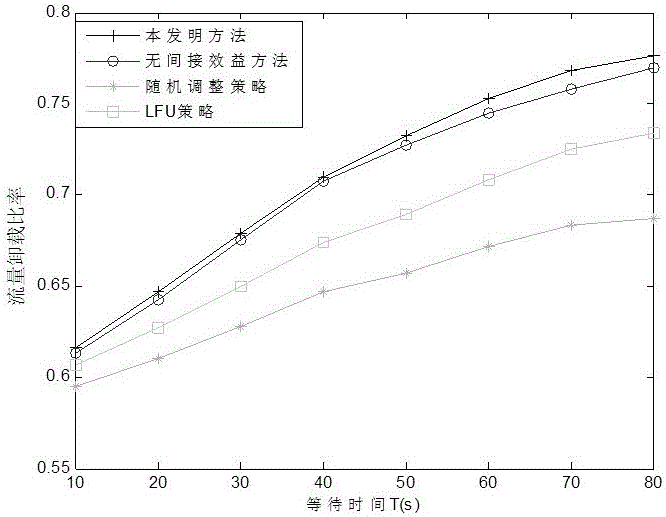
Distributed mobile node file caching method based on social relation in cellular network
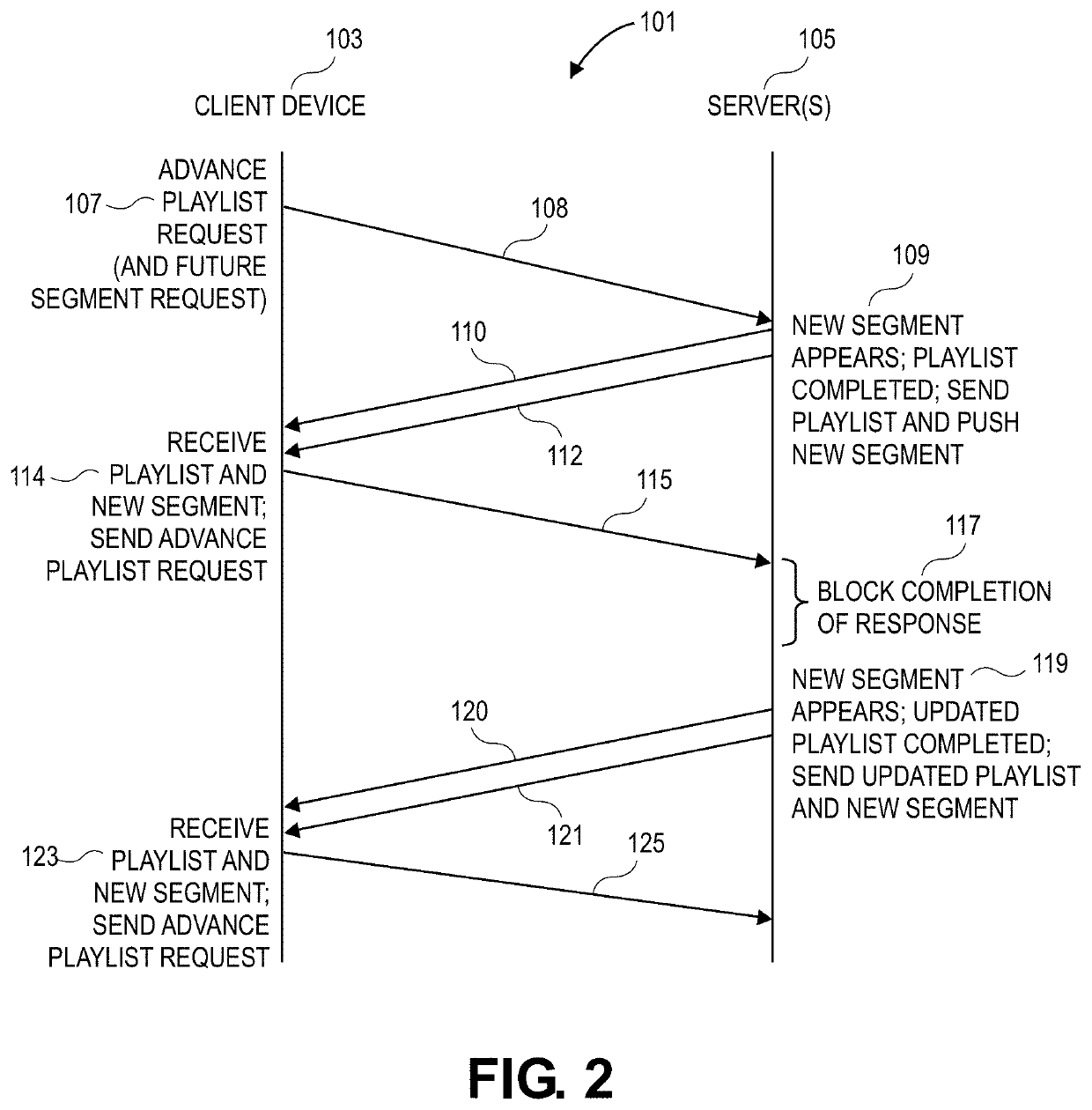
ActiveCN106851741AAvoid downloadingOptimize cache stateNetwork traffic/resource managementDirect communicationFile caching
The invention discloses a distributed mobile node file caching method based on a social relation in a cellular network, and belongs to the field of wireless communication. After a mobile node meets a friend node (a one-hop social neighbor node) based on the social relation, the mobile node and the friend node transmit necessary files to each other, direct benefits and indirect benefits obtained by caching these files are calculated according to all files cached in the both parties to reallocate the caching schemes of the two nodes, wherein the direct benefits are system benefits of the two nodes by satisfying the demands of the respective friend nodes, and the indirect benefits are used for bringing larger opportunity for multi-hop social neighbor nodes to obtain the necessary files by direct communication through terminals so as to increase the direct benefits of other nodes. According to the distributed mobile node file caching method disclosed by the invention, the demands of the multi-hop social neighbor nodes are considered, so that the system obtains the maximum overall direct benefit. The distributed mobile node file caching method disclosed by the invention can be applied to node file caching methods in mobile cellular systems having caching functions and having the social relation.
Owner:ZHEJIANG UNIV
Television program list service system and technical method relying on movable electronic equipments
InactiveCN101257614AAvoid downloadingSolve the problem of not being able to see the TV program list convenientlyTelephonic communicationAnalogue secracy/subscription systemsMobile electronicsData bank
A mobile electronic device based TV program list service system and technical method, characterized in that: the TV program list service system comprises the following parts: user requirement steps, identification confirming steps, service processing steps, classification displaying steps, function support server steps, database steps. The invention changes the function of the traditional mobile electronic devices and provides TV program list service system and technical method, which can be applied in the mobile electronic devices.
Owner:沈阳康耐克软件有限公司
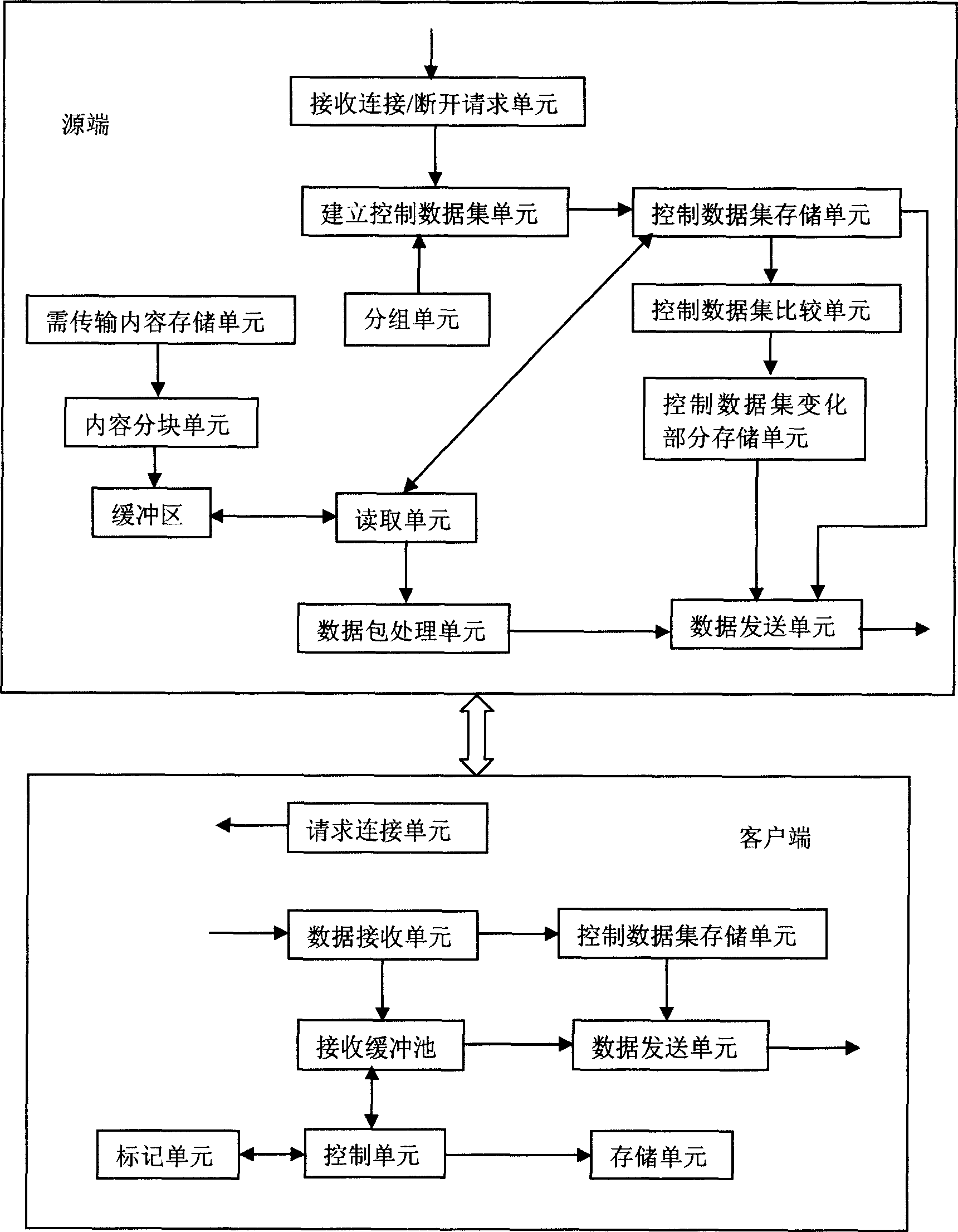
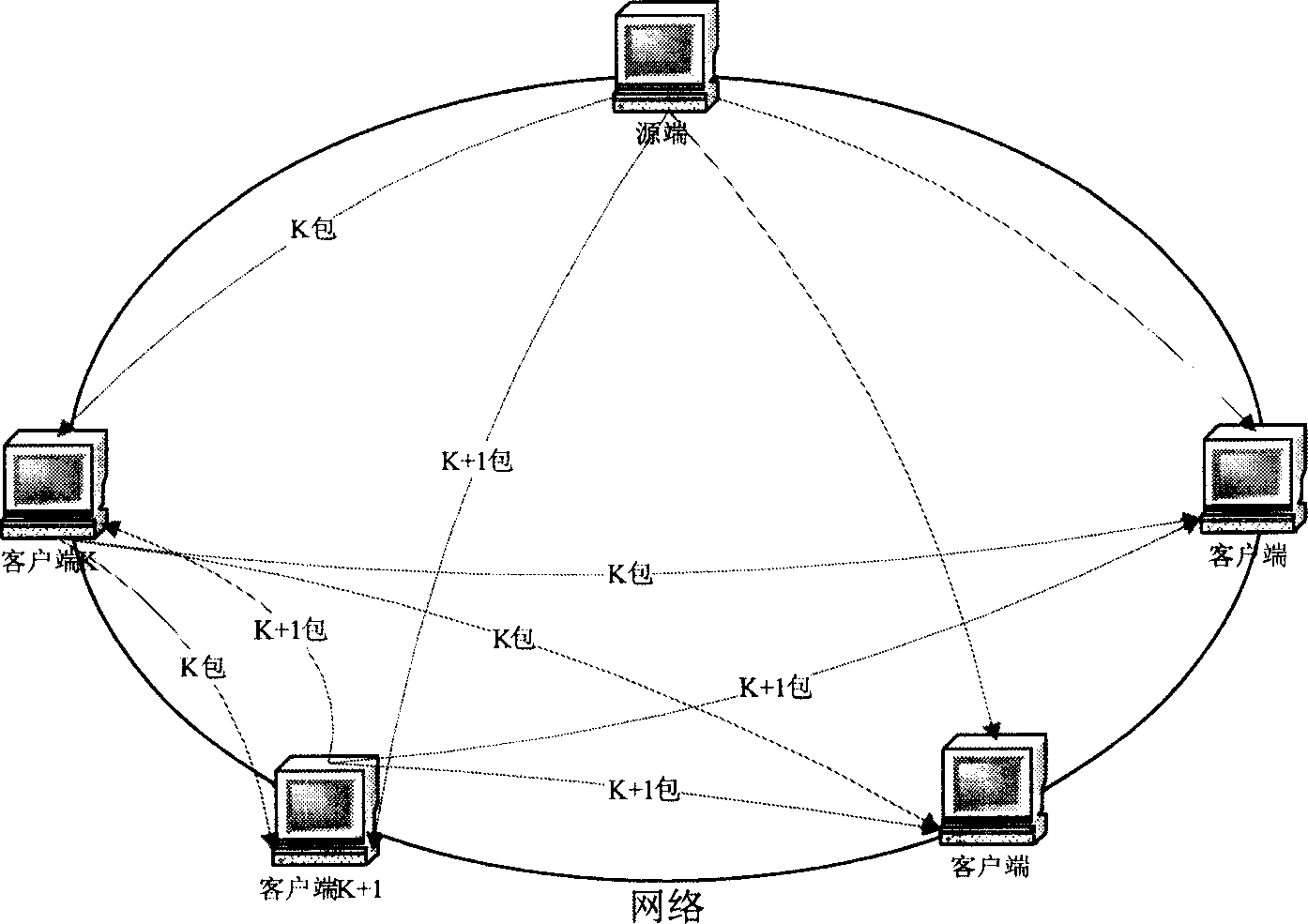
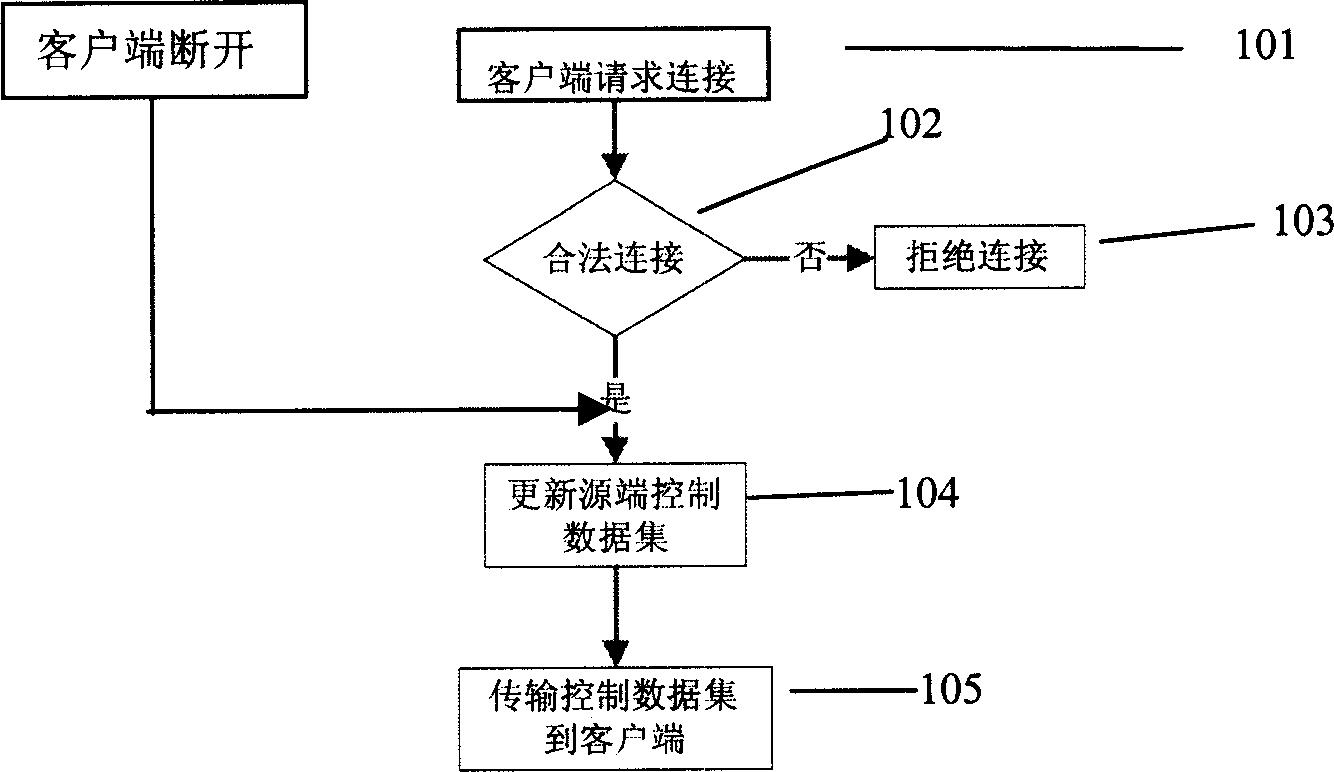
Data block transmission method
This invention puts forward a method for transmitting data in blocks including: a source for transmitting data monitors the connection requirement and cuts the connection of customer ends that will receive data and sets up a control data set for customer ends transmitting a same content including communication data and labels showing changes of the control data set, the source divides the customer ends joining into the set into M groups, each of them includes at least one and numbers of ends in the set should be almost equal, and M is 1 or a natural number greater than 1, the source transmits the set to the customer ends and divides the content asked by the customer ends into data blocks and thransmits them to the customer ends of M groups, which exchange data blocks based on the control data set to compose a complete content.
Owner:张永敏
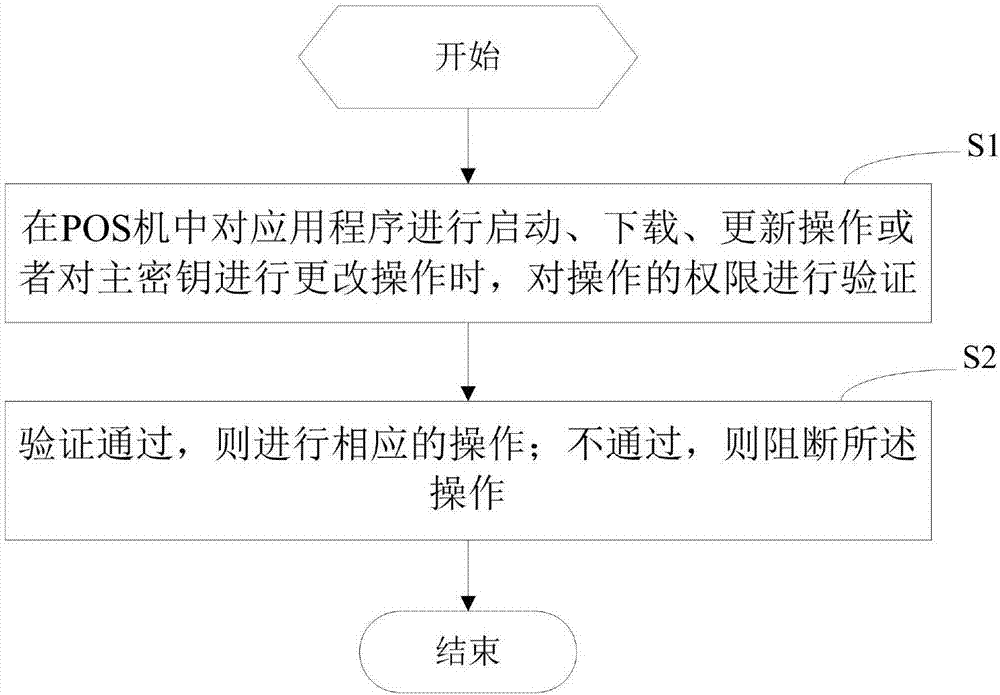
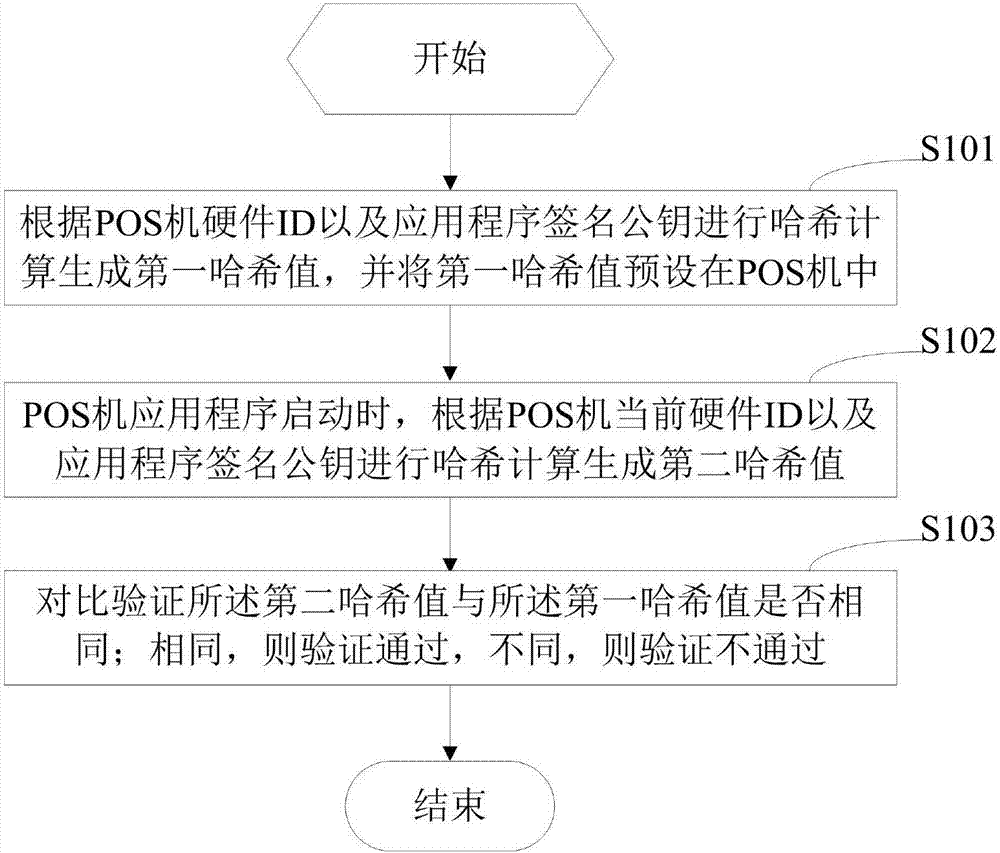
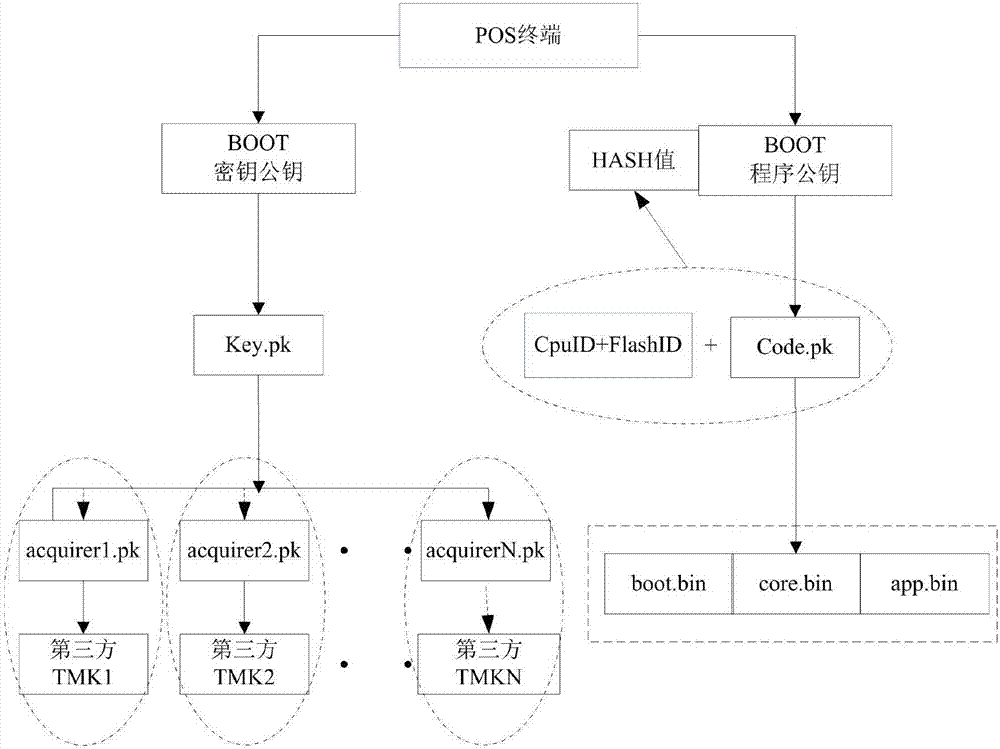
POS machine safety verification method and device
ActiveCN107466455AEnsure safetyAvoid downloadingUser identity/authority verificationCash registersMaster keyComputer engineering
The invention provides a POS machine safety verification method and device. An application program is started, downloaded and updated in a POS machine, the master key is changed, the permission of the operation is verified; the verification is passed, and then the corresponding operation is carried out; the verification is not passed, the operation is blocked. The safety of the master key and the application program in the POS machine is guaranteed, so that the master key and the application program in the POS machine are prevented from being illegally tampered and downloaded; and the POS machine is prevented from being switched by the whole machine.
Owner:SHENZHEN TRENDIT CO LTD
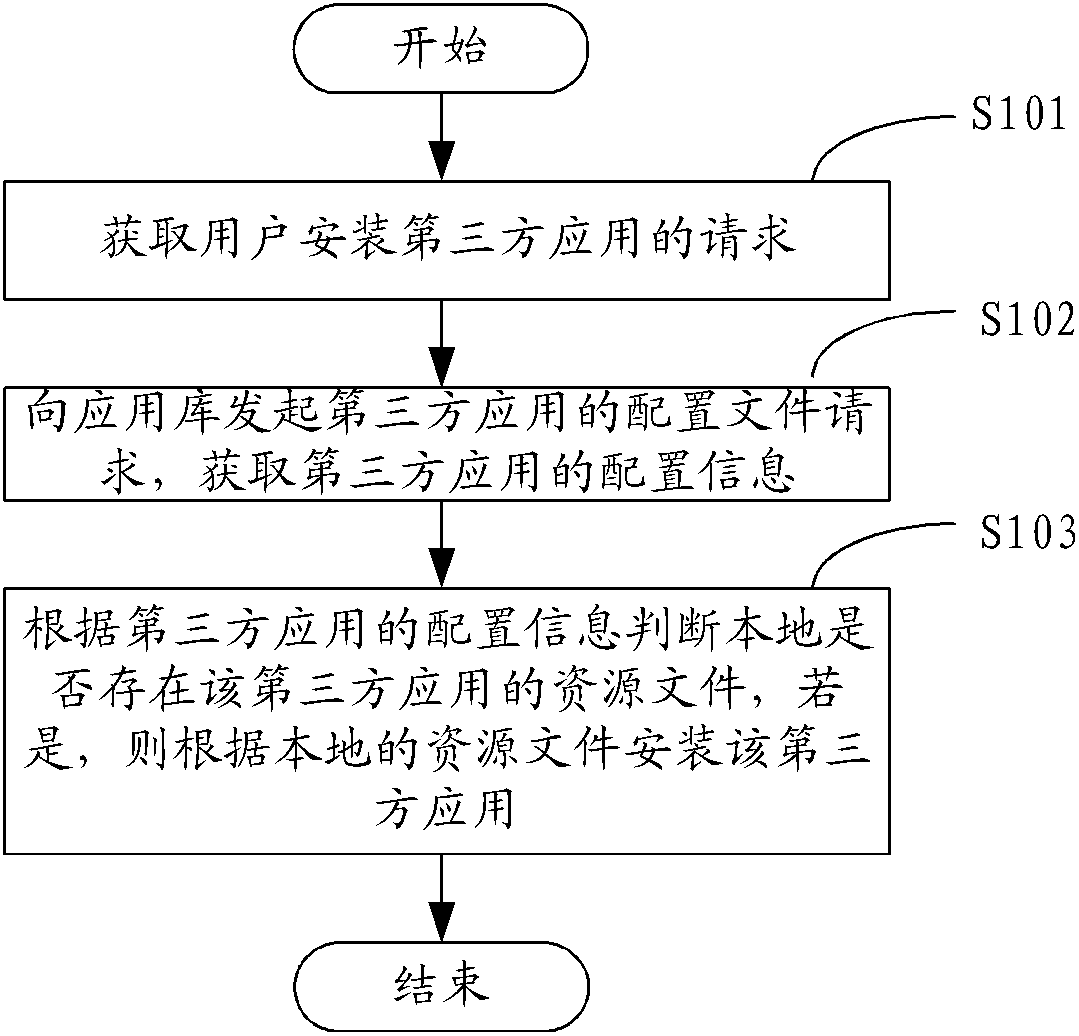
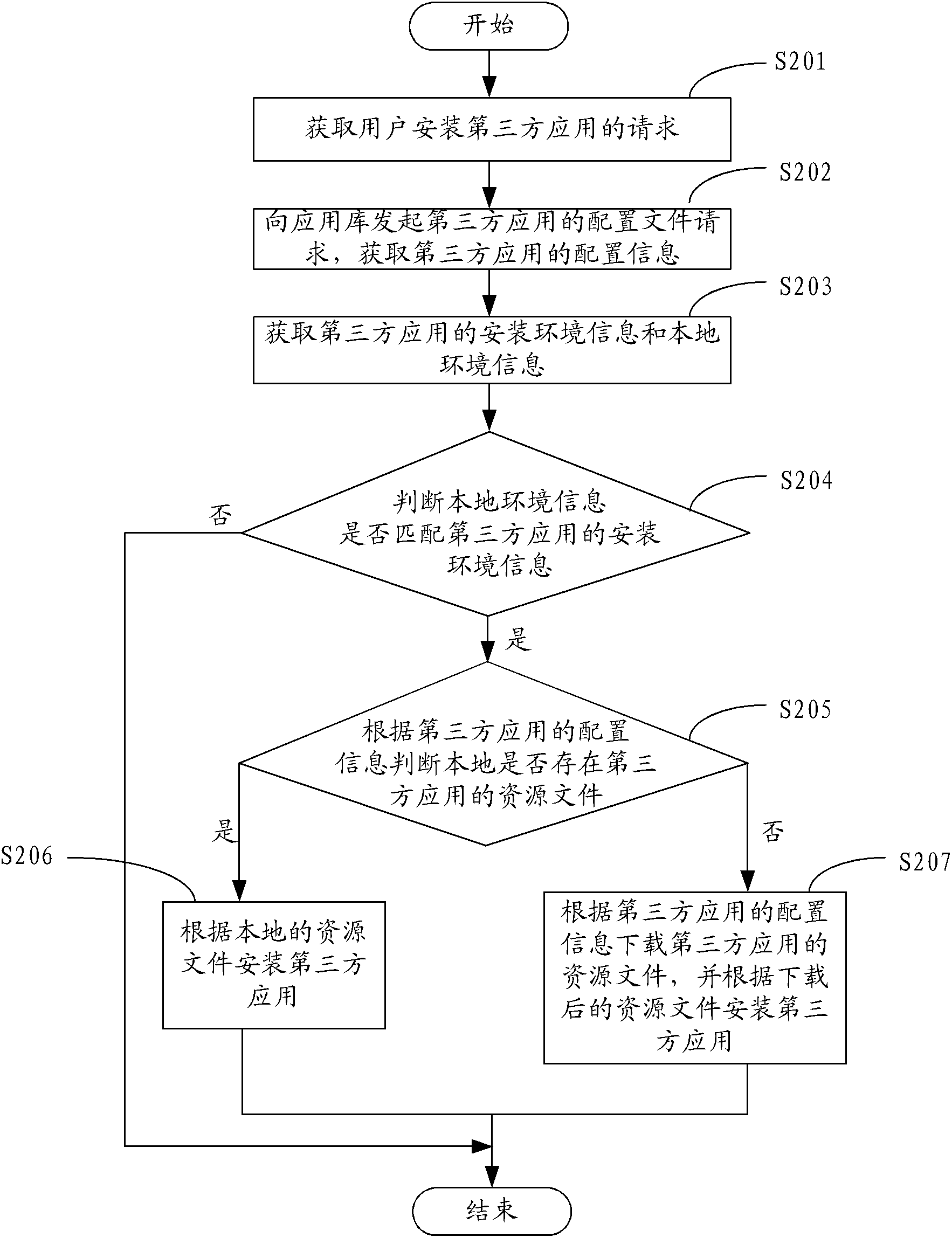
Third party application installation method and third party application installation system
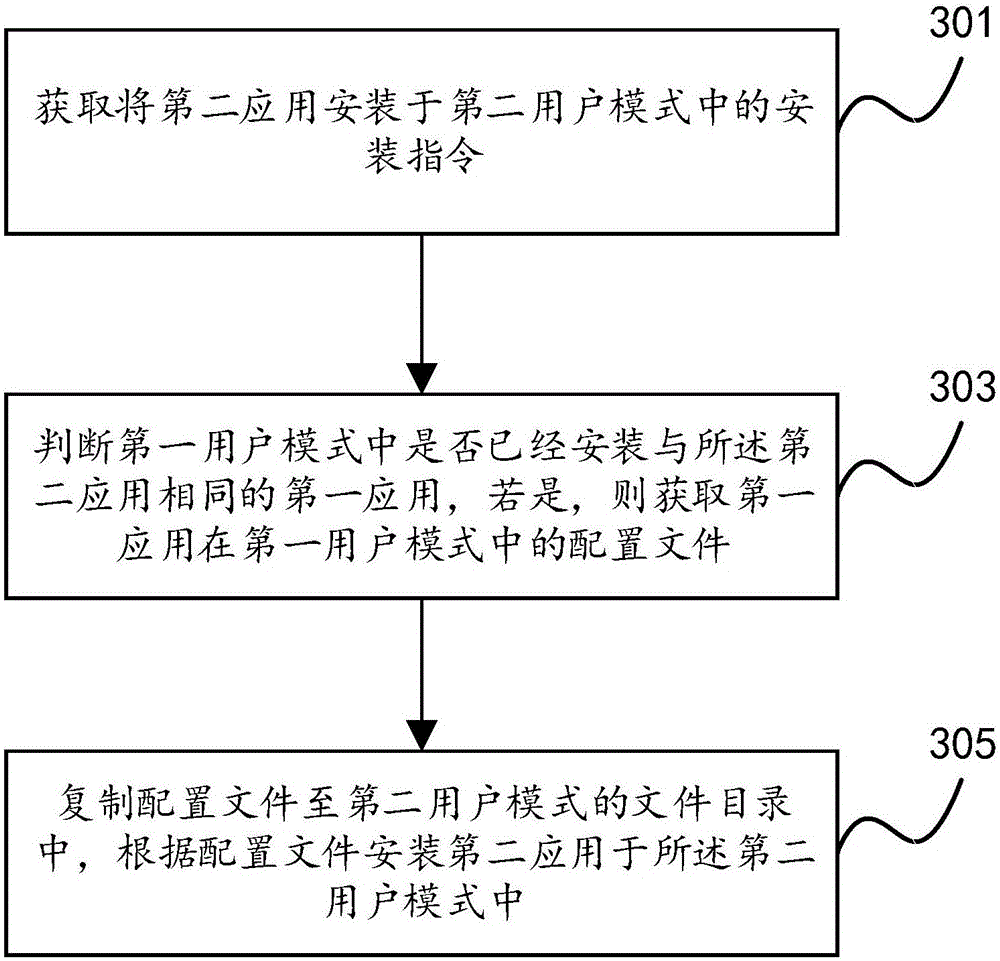
ActiveCN103176811AShorten the timeImprove operational convenienceProgram loading/initiatingThird partyComputer science
The invention provides a third party application installation method which includes the following steps: obtaining a request of a user for installing a third party application; initiating a configuration file request of the third party application to an application repository, obtaining the configuration information of the third party application; judging whether the resource files of the third party application exist in local or not according to the configuration information, if the resource files exist in the local, installing the third party application according to the local resource files. According to the third party application method, the configuration information of the third party application which is installed specified according to the user is obtained from the application repository, whether the resource files of the third party application exist in the local or not is judged according to the configuration information, if the resource files of the third party application exist in the local, the third party application is installed according to the local resource files, unnecessary downloading is avoided, and the time of the user is saved. In addition, the user does not need to participate in the installation process, and thus convenience of the operation of the user is improved. Besides, the invention further provides a third party application installation system.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multi-account login method and device and mobile terminal
ActiveCN106843868AImprove experienceOvercome the defect that the login method only supports one accountSpecific program execution arrangementsComputer terminalComputer science
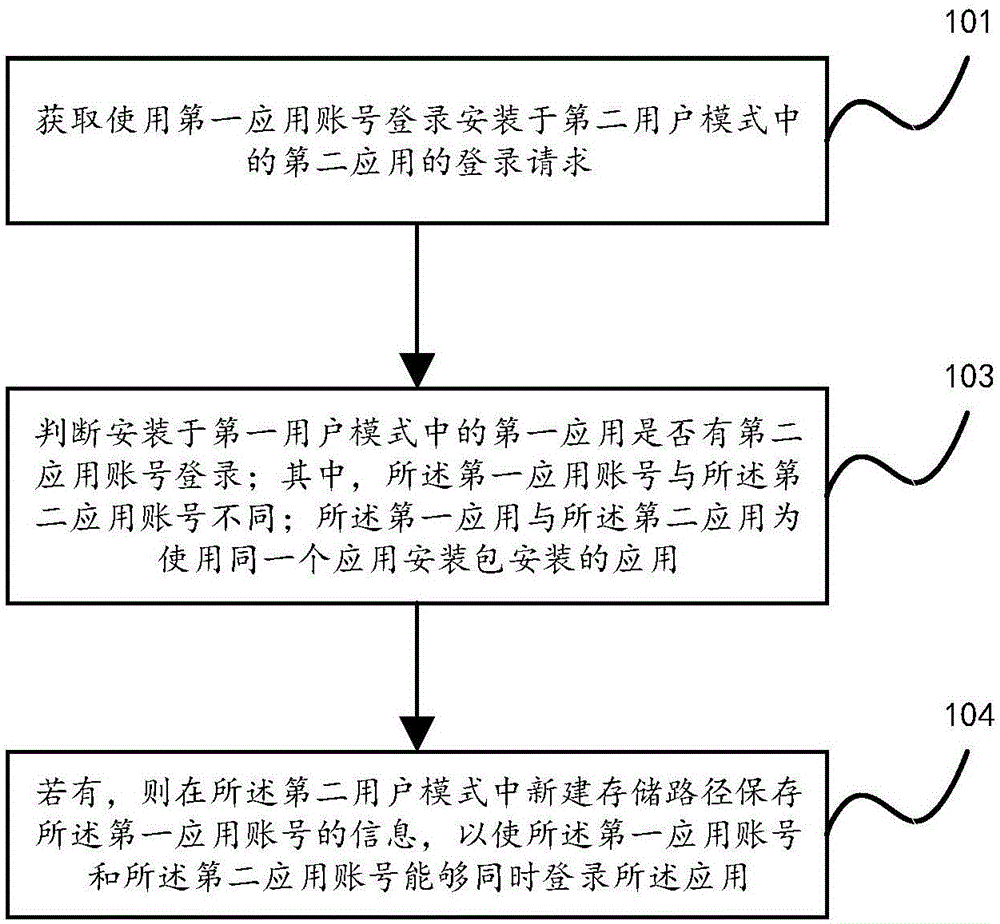
The invention discloses a multi-account login method and device and a mobile terminal; the multi-account login method comprises: acquiring a login request to use a first application account to log in to a second application installed in a second user mode; judging whether a first application installed in a first user mode experiences login of a second application account or not; if yes, establishing a storage path in the second user mode to save information of the first application account so that the first application account and the second application account can log in to the application at the same time. The function of the second application logging in under the second user mode is achieved by setting the storage path in the second user mode, the defect that login modes of most existing applications support only one account is partly overcome, the application need of a user for multi-account login is met, and good user experience is provided.
Owner:BEIJING ANYUNSHIJI TECH CO LTD
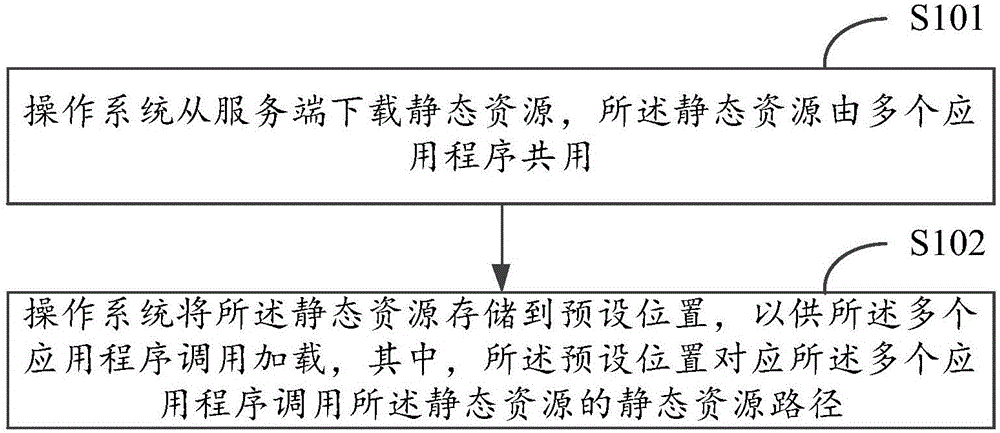
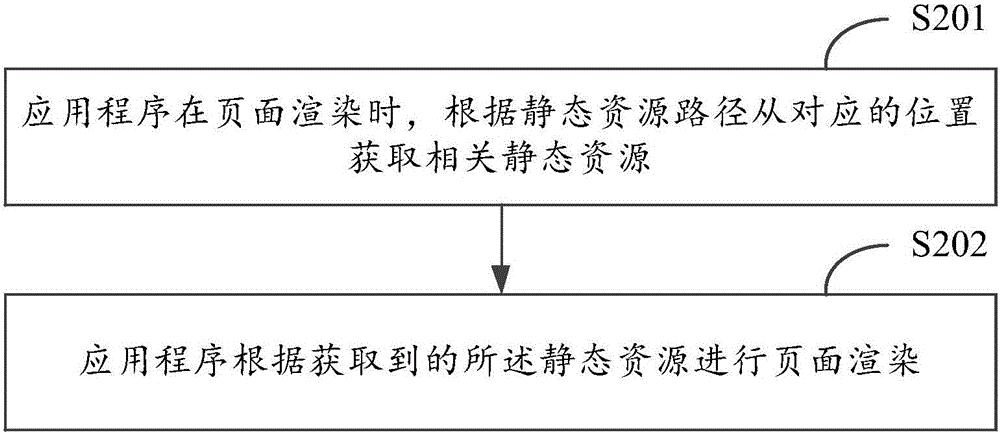
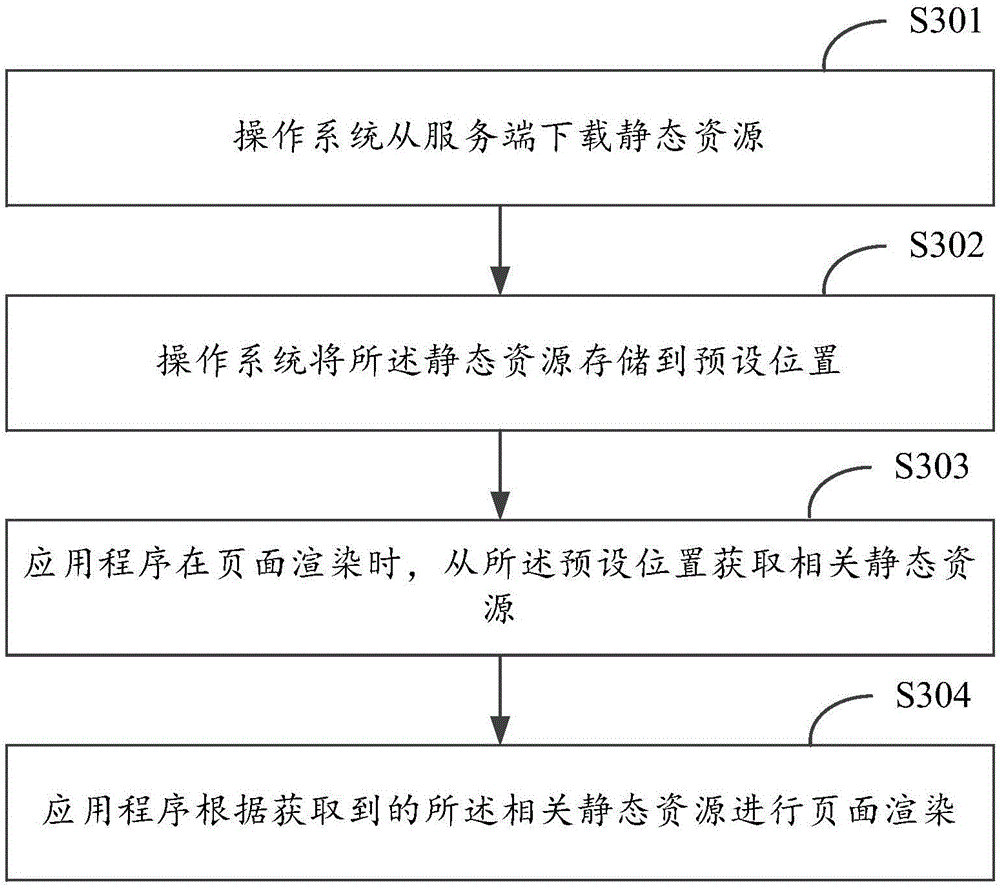
Static resource loading method and device
ActiveCN105808305AImprove maintenance efficiencySave storage resourcesProgram loading/initiatingSoftware deploymentMultiple applicationsServer-side
The invention discloses a static resource loading method and device. The method comprises the steps that an operation system downloads a static resource from a server side, wherein the static resource is shared by multiple applications; the static resource is stored at a predetermined position by the operation system to be called and loaded by the applications, wherein the predetermined position corresponds to a static resource path for the applications to call the static resource. The operation system can download the static resource shared by multiple applications from the server side, and the static resource is stored at a predetermined position by the operation system to be called and loaded by the applications; for the same static resource, downloading and storage are conducted by the operation system in a centralized mode rather than by the applications respectively, and therefore storage resources of equipment are saved. Meanwhile, for the same static resource, a developer only needs to conduct updating once to take effect on all the applications, and therefore application maintenance efficiency is improved.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com