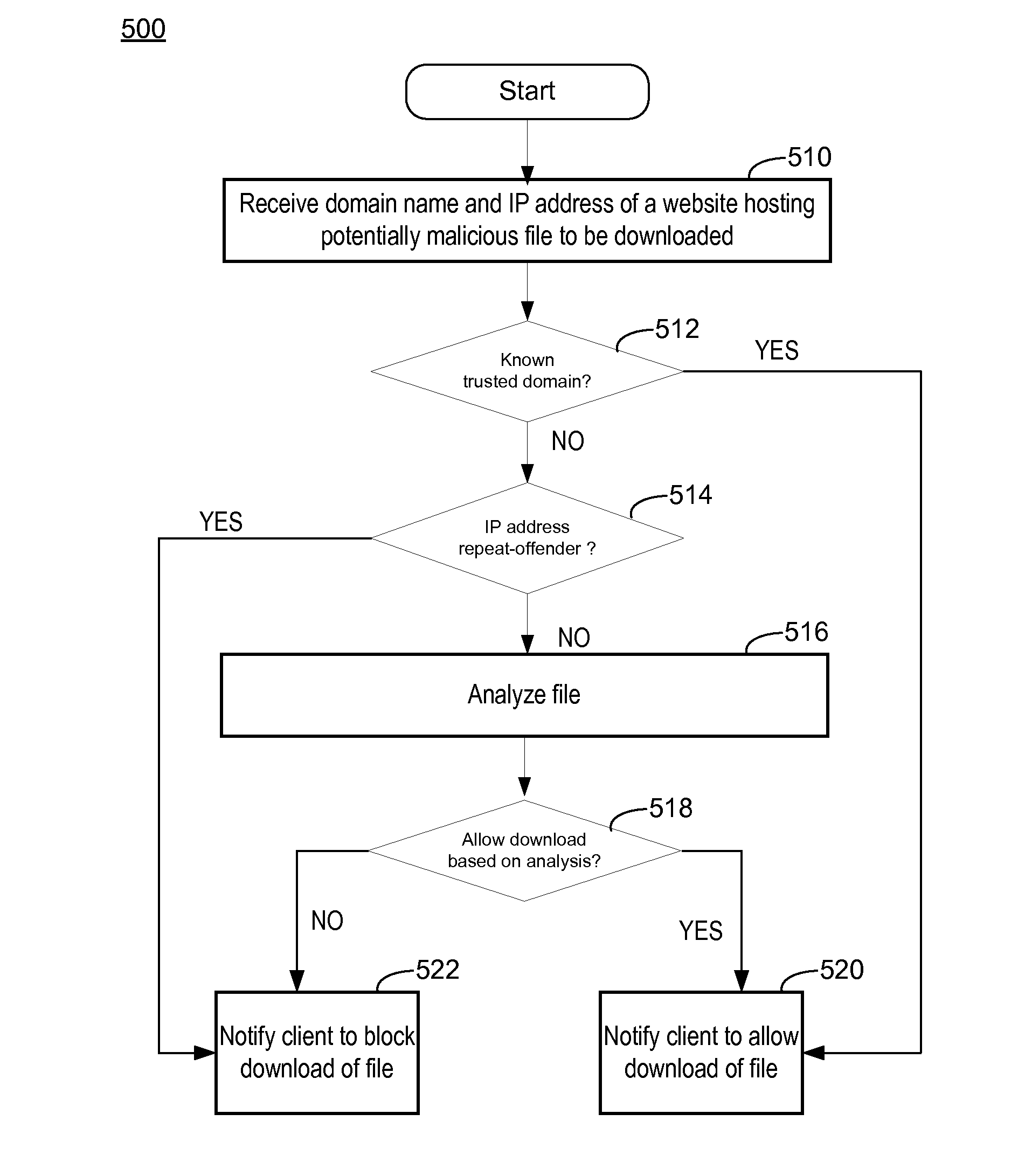
Ip-based blocking of malware
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
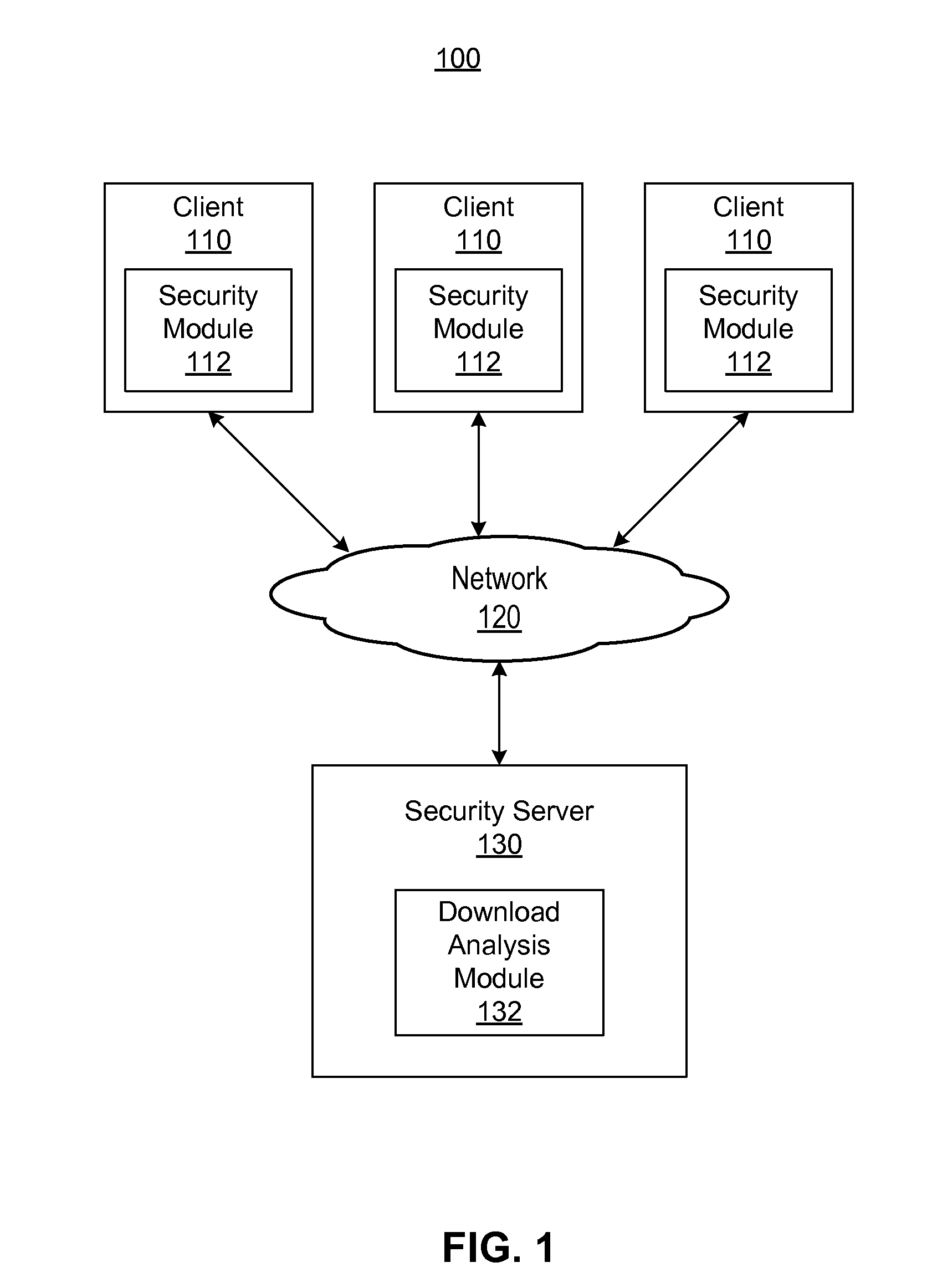
[0018]FIG. 1 is a high-level block diagram of a computing environment 100 for detecting and blocking malicious software (malware) downloads according to one embodiment. FIG. 1 illustrates a security server 130 and three clients 110 connected by a network 120. The illustrated environment 100 represents a typical computing environment where multiple clients 110 interact with the security server 130 to identify and remediate malware at the clients 110. Only three clients 110 are shown in FIG. 1 in order to simplify and clarify the description. Embodiments of the computing environment 100 can have many clients 110 and security servers 130 connected to the network 120.
[0019]The client 110 is used by a user to interact with the security server 130 and / or other entities on the network 120. In one embodiment, the client 110 is a personal computer (PC) such as a desktop or notebook computer. In other embodiments, the client 110 is a mobile telephone, personal digital assistant, or other elec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com