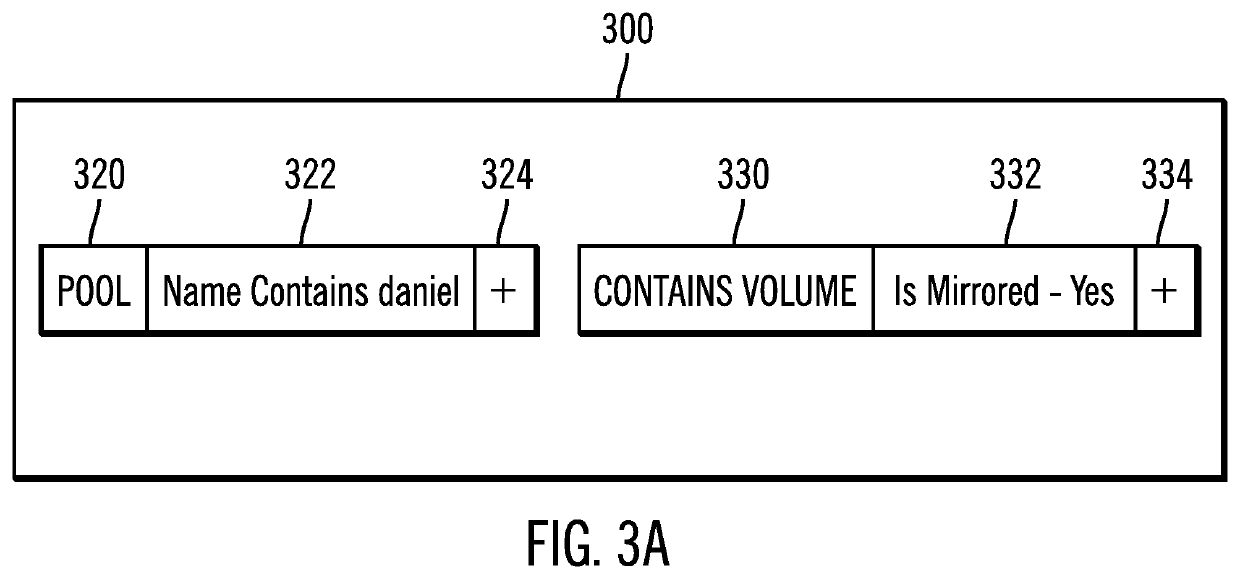
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
86 results about "Object type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, an object type (a.k.a. wrapping object) is a datatype that is used in object-oriented programming to wrap a non-object type to make it look like a dynamic object. Some object-oriented programming languages make a distinction between reference and value types, often referred to as objects and non-objects on platforms where complex value types don't exist, for reasons such as runtime efficiency and syntax or semantic issues. For example, Java has primitive wrapper classes corresponding to each primitive type: Integer and int, Character and char, Float and float, etc. Languages like C++ have little or no notion of reference type; thus, the use of object type is of little interest.
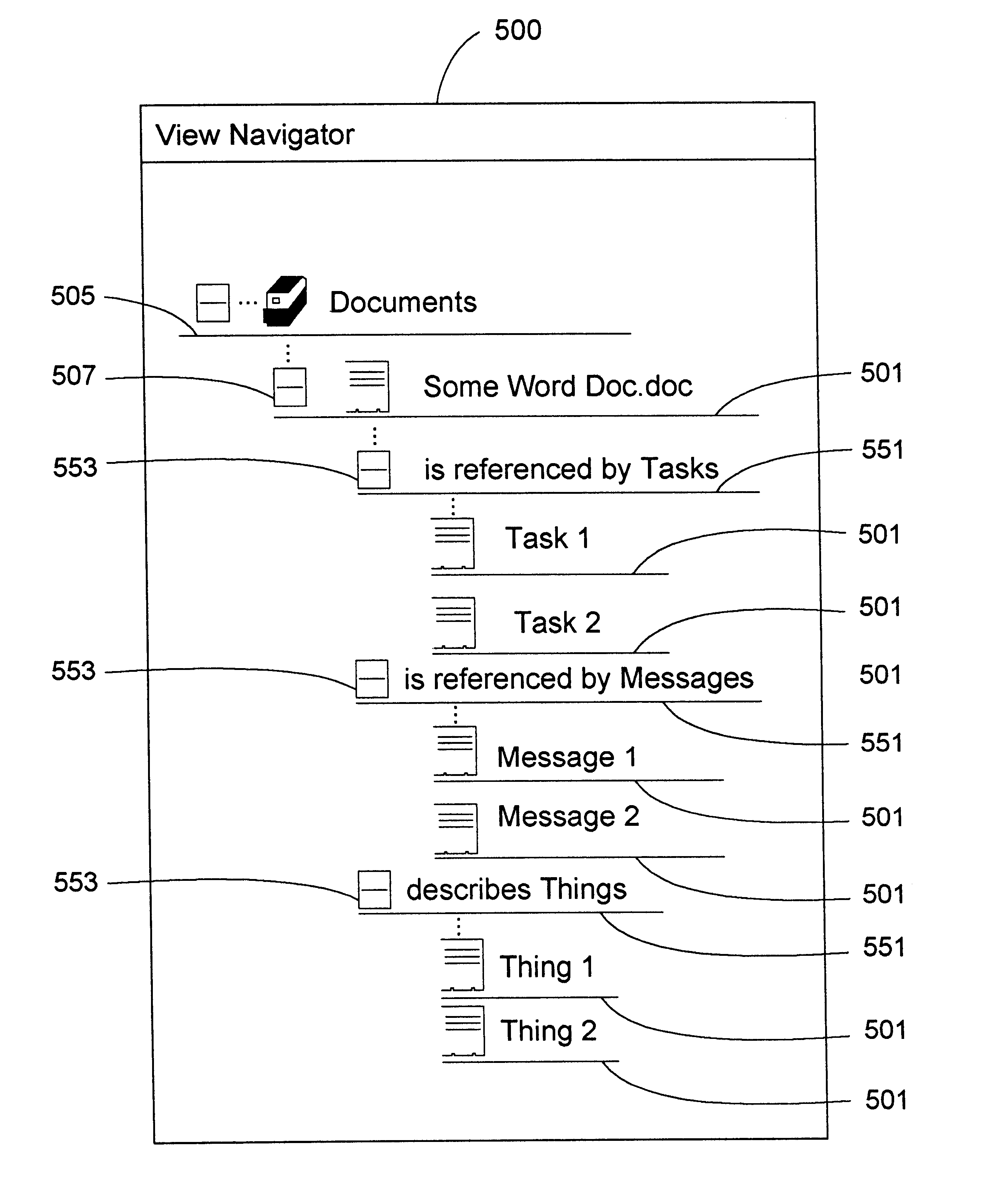
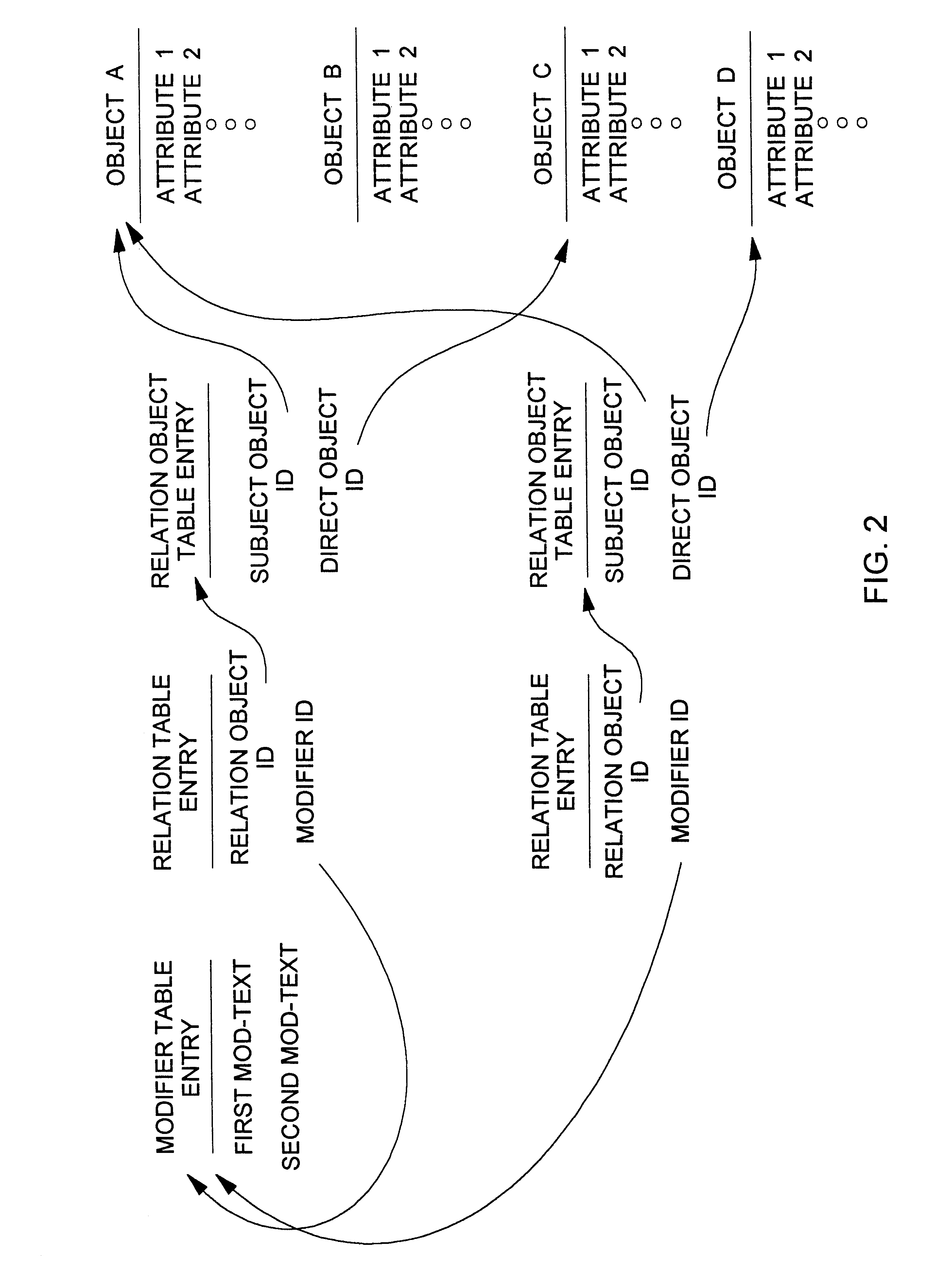
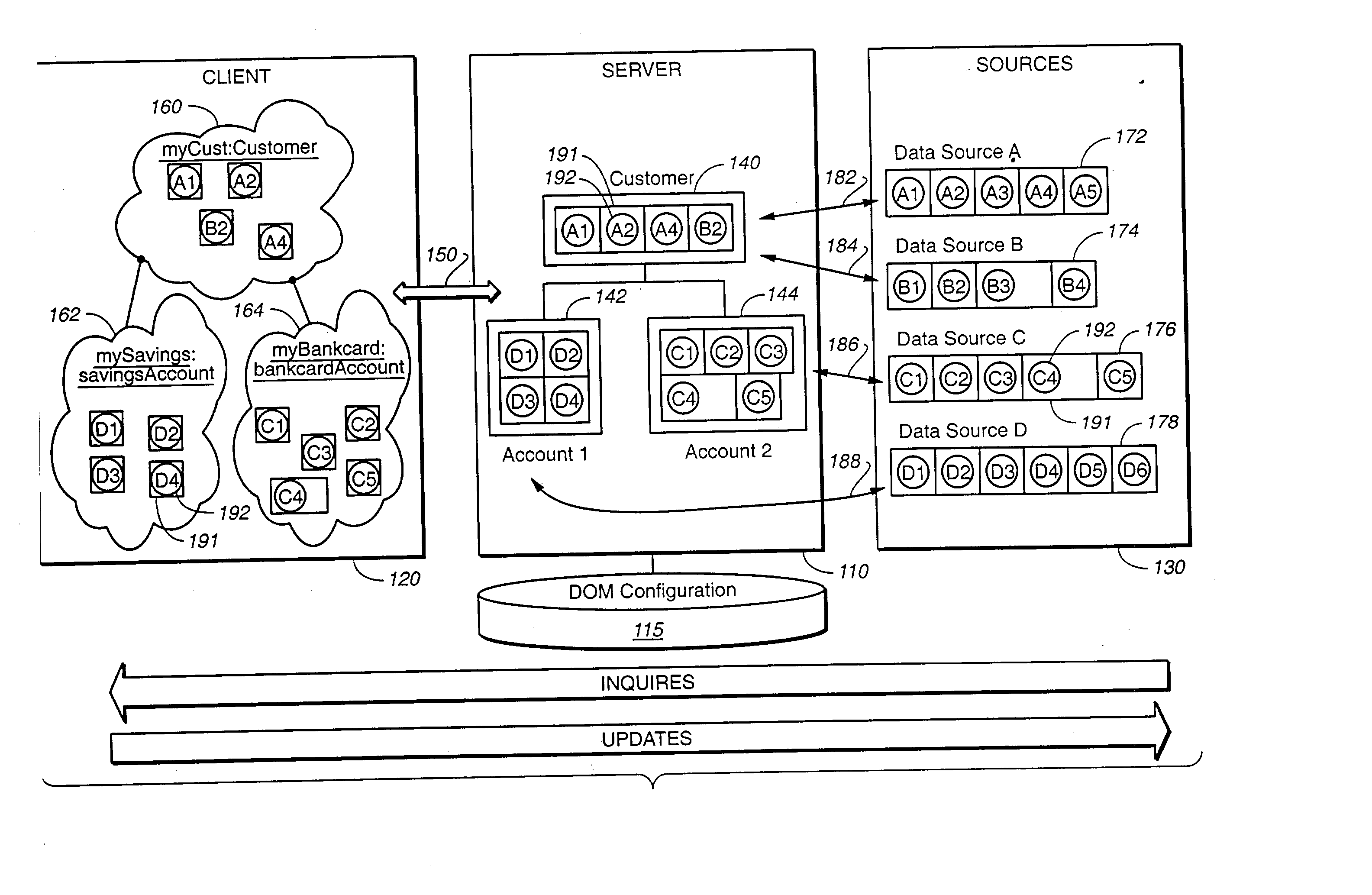
Database query handler supporting querying of textual annotations of relations between data objects
InactiveUS6618732B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsDatabase queryCustomer relationship management
An improved command handler (and database system utilizing the improved command handler) interfaces to a datastore storing item data for a plurality of items and bi-directional modifier data, corresponding to a relation between at least one first item and at least one second item, that represents first text characterizing semantics of a relationship of the at least one first item to the at least one second item, and represents second text characterizing semantics of a relationship of the at least one second item to the at least one first item. The command handler operates, in response to receiving a first-type query command that specifies at least one given item, to access the datastore to identify i) at least one related item that is related to the given item, and identify ii) either the first text or the second text characterizing semantics of the relation between the given item and the at least one related item. The command hander returns i) data corresponding to the at least one related item; and ii) data corresponding to the identified first text and or second text characterizing semantics of the relation between the given item and the at least one related item. Preferably, the data returned in response to the first-type query command identifies the at least one related item. and identifies the first text or second text characterizing semantics of the relation between the given item and the at least one related item. In addition, the command handler preferably supports additional commands that retrieve from the datastore information related to specified objects, object types, and relations.The command handler (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the command handler (and database system) provides an efficient mechanism to query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that efficient and readily adaptable to client-server database systems or other distributed database systems.
Owner:REVELINK
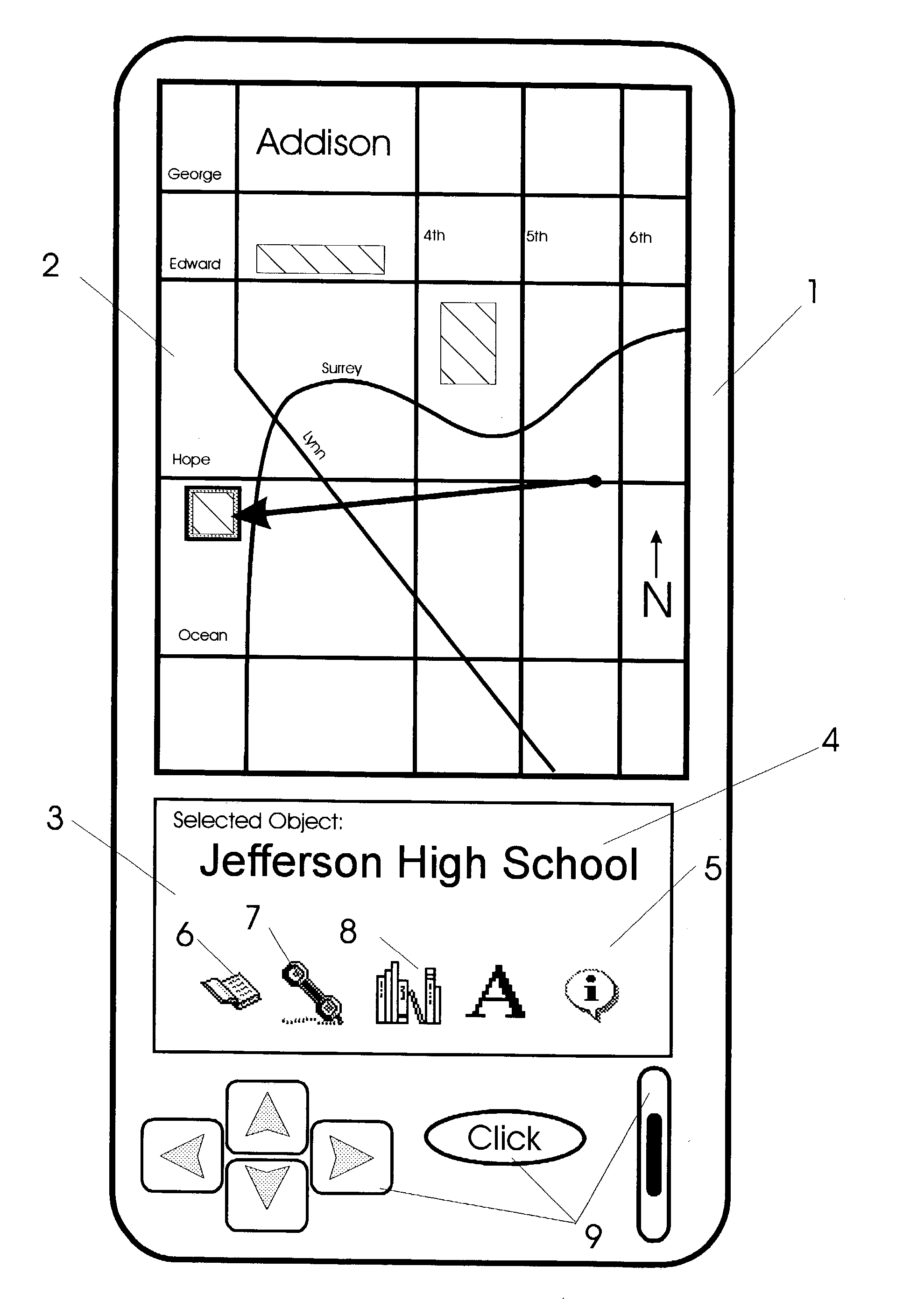
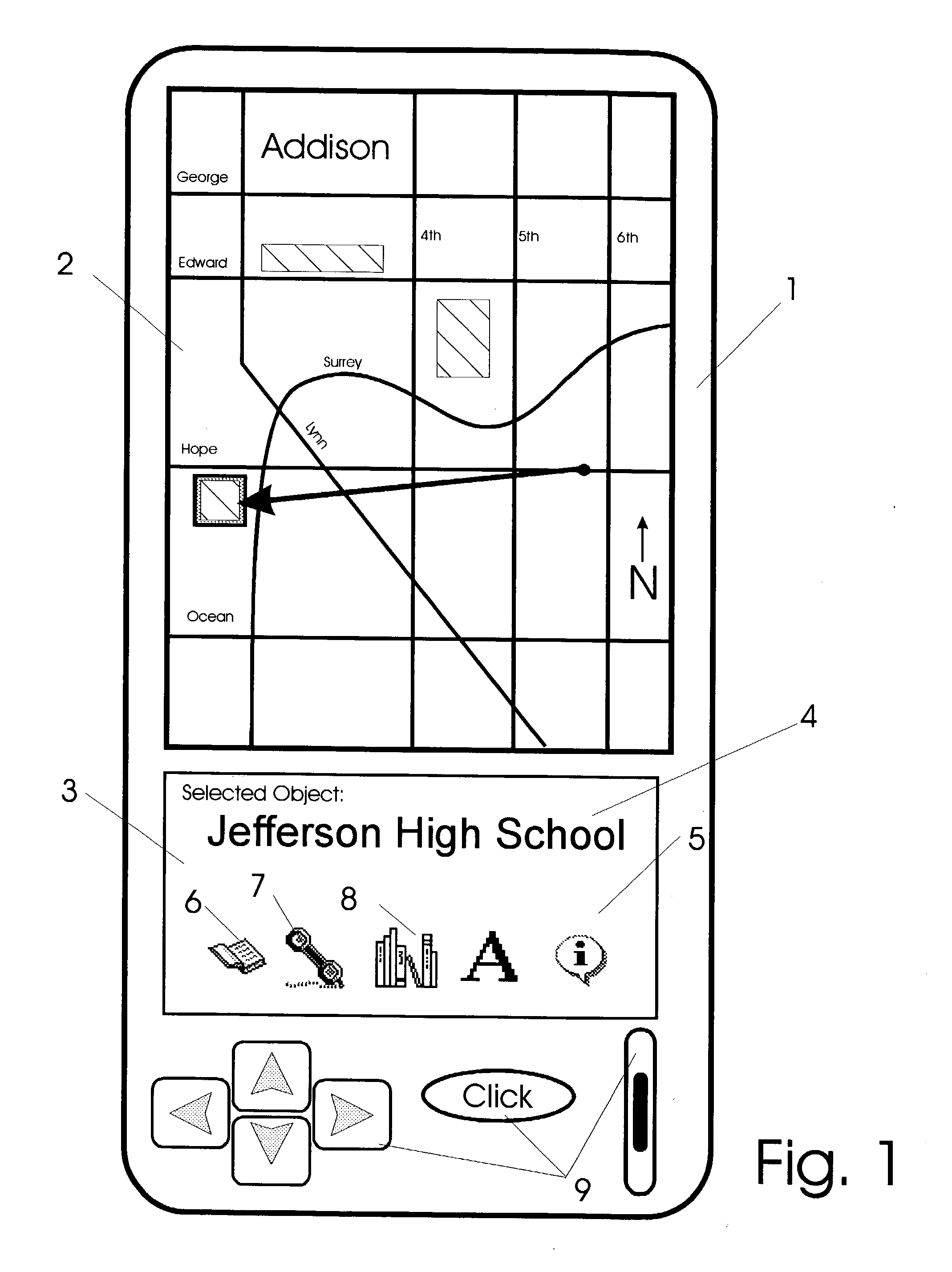
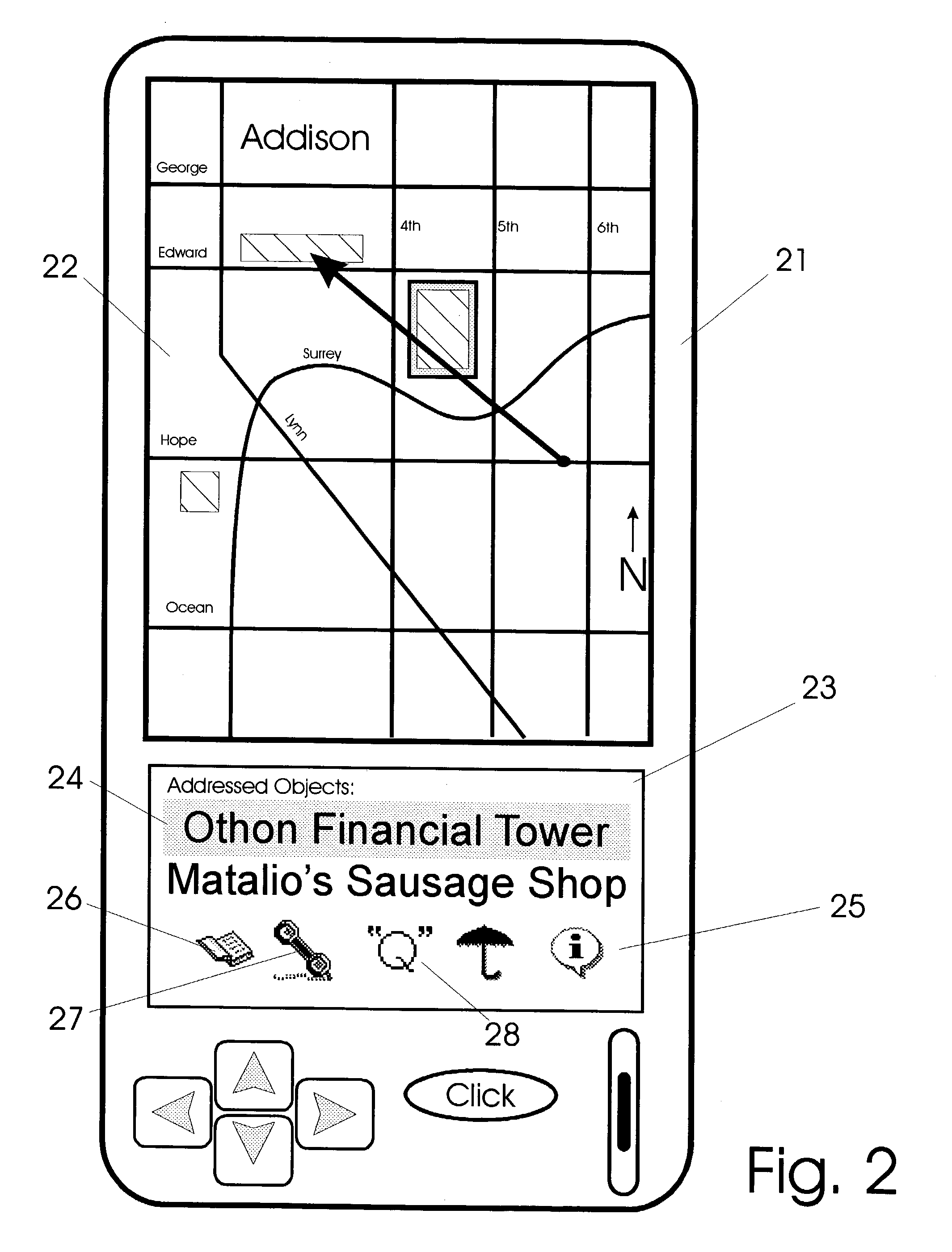
Apparatus and methods for interfacing with remote addressing systems
InactiveUS20030184594A1Navigational calculation instrumentsCathode-ray tube indicatorsForm and functionComputer device
Devices for remotely addressing objects via pointing action are provided with graphical user interfaces. In response to an object being addressed, a computer device and software provide graphical user interfaces which relates to objects being addressed. As different types of objects are addressed, user interfaces provided change in form and function to agree with the type of category of object being addressed at that instant. Devices have position and attitude determining facility in communication with a computer having prerecorded data. The data includes information relating to object types and corresponding graphical user interfaces.
Owner:ELLENBY JOHN +3
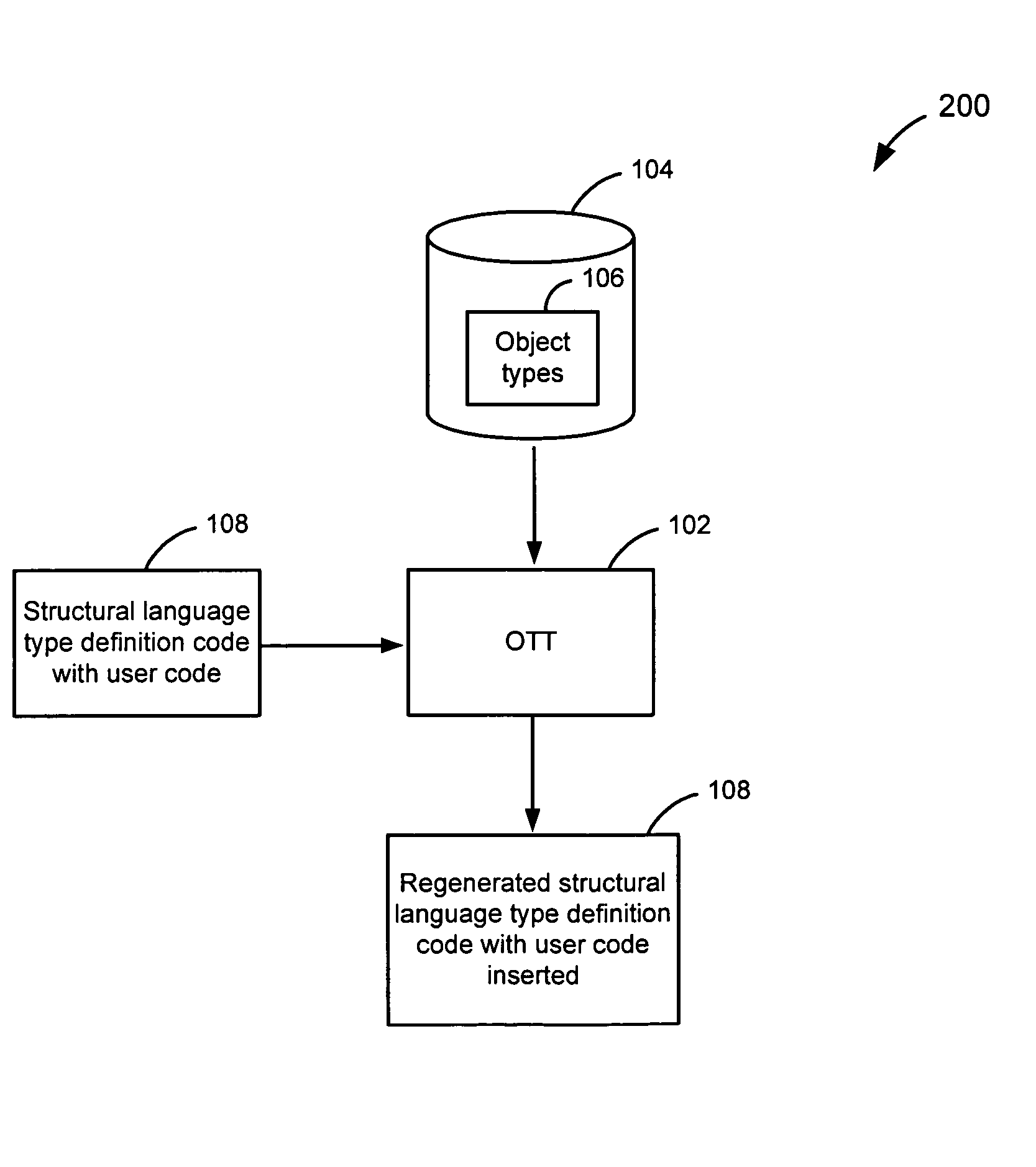
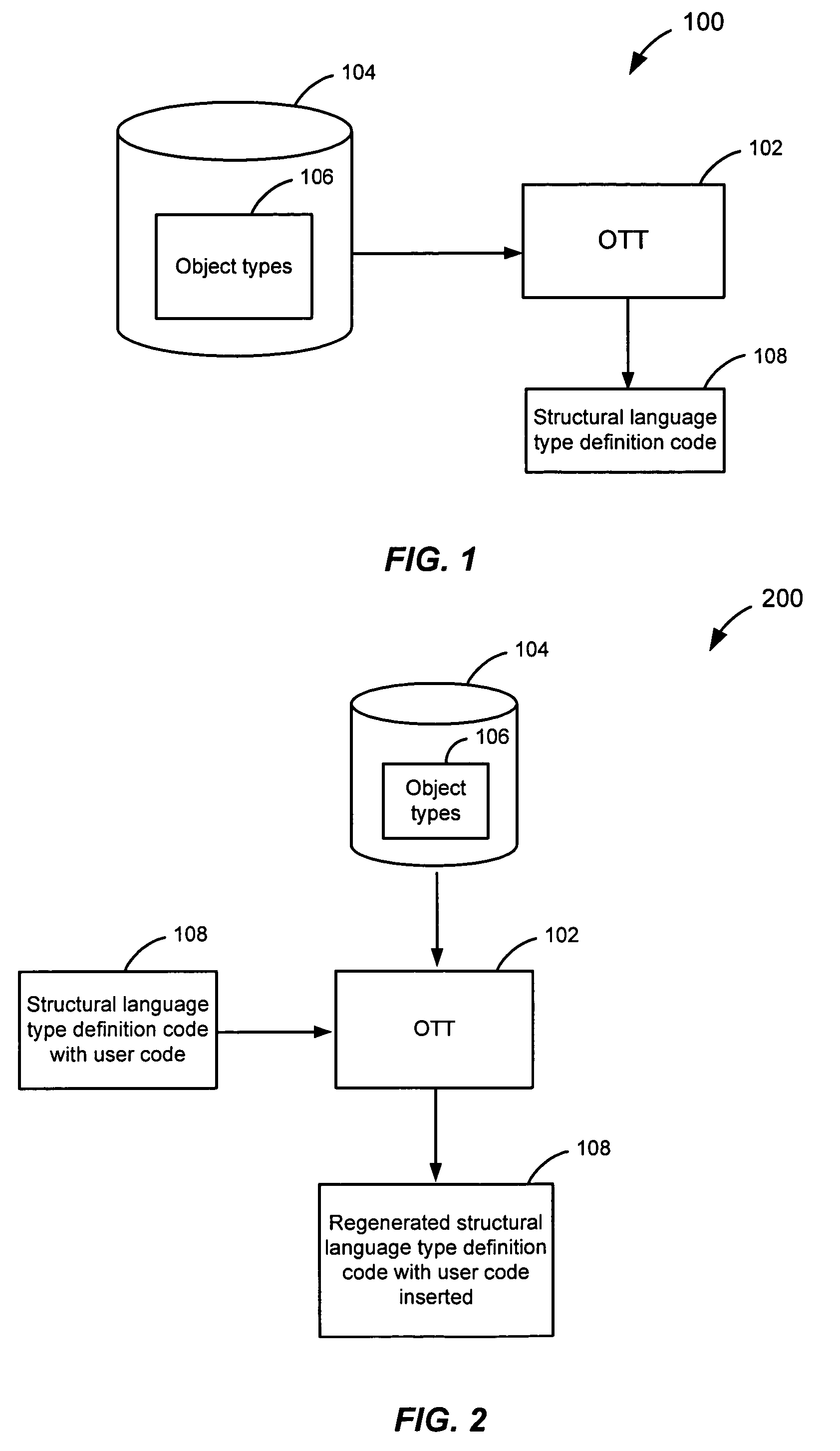
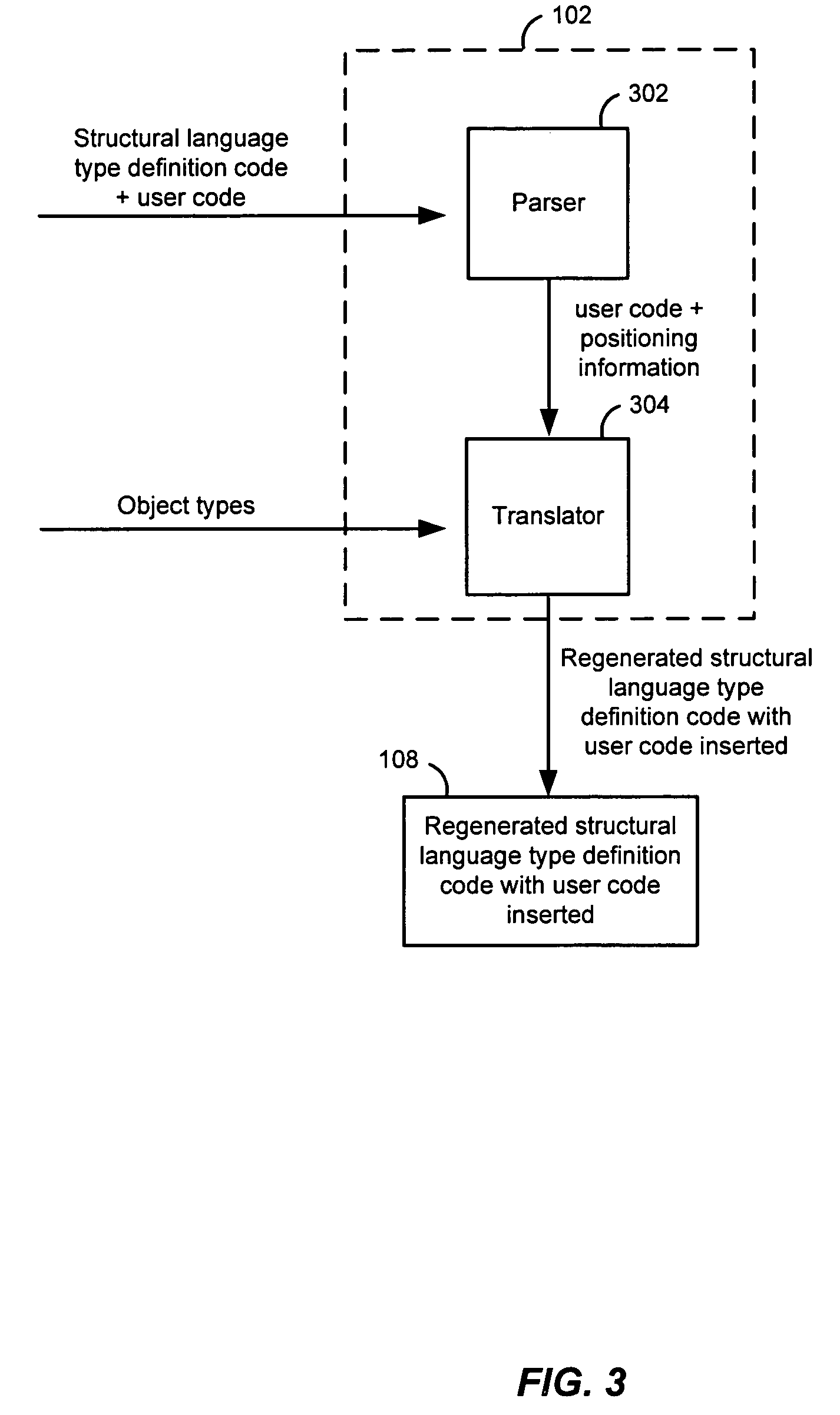
Preserving user code in OTT-generated classes
ActiveUS7401088B2Data processing applicationsDigital data information retrievalCode generationObject type
An object type translator (OTT) determines one or more database object types. The one or more database object types are mapped to a first structural language type definition code. After being generated, the user may add user code to the first structural language type definition code. During regeneration of these files, the first structural language type definition code is then parsed to determine the user code that has been added, based on the start and end markers that the user code segments have been marked with. OTT maps these user-code segments to the corresponding database types and keeps track of the mapping and the user code. When the OTT starts generating the second structural language code, the OTT determines a position where the user code should be inserted into the second structural language type definition code using that mapping. The user code is then inserted in the second structural language code in the position determined. Accordingly, the user code that was added is not lost when the structural language type definition code is regenerated from the one or more database object types.
Owner:ORACLE INT CORP
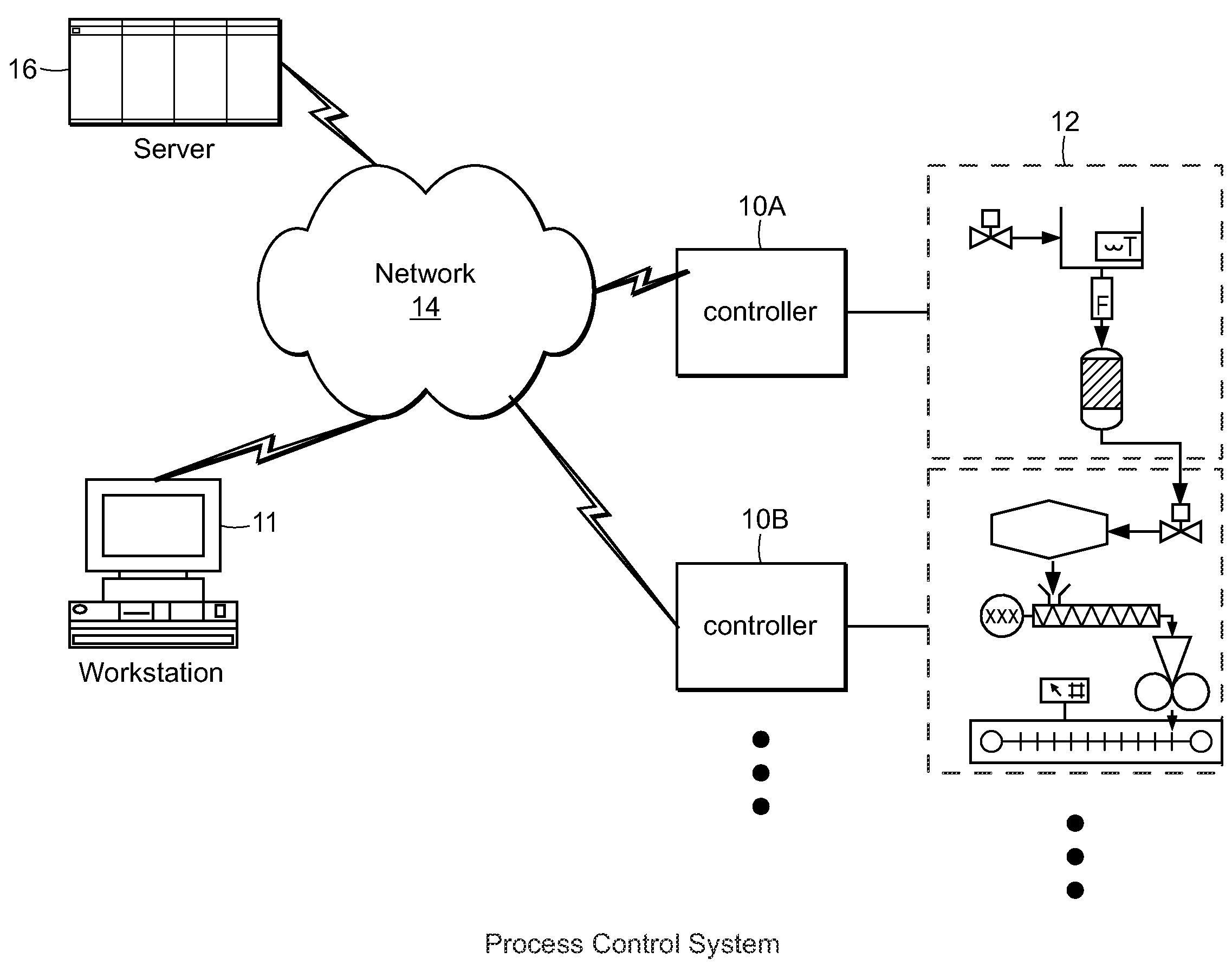
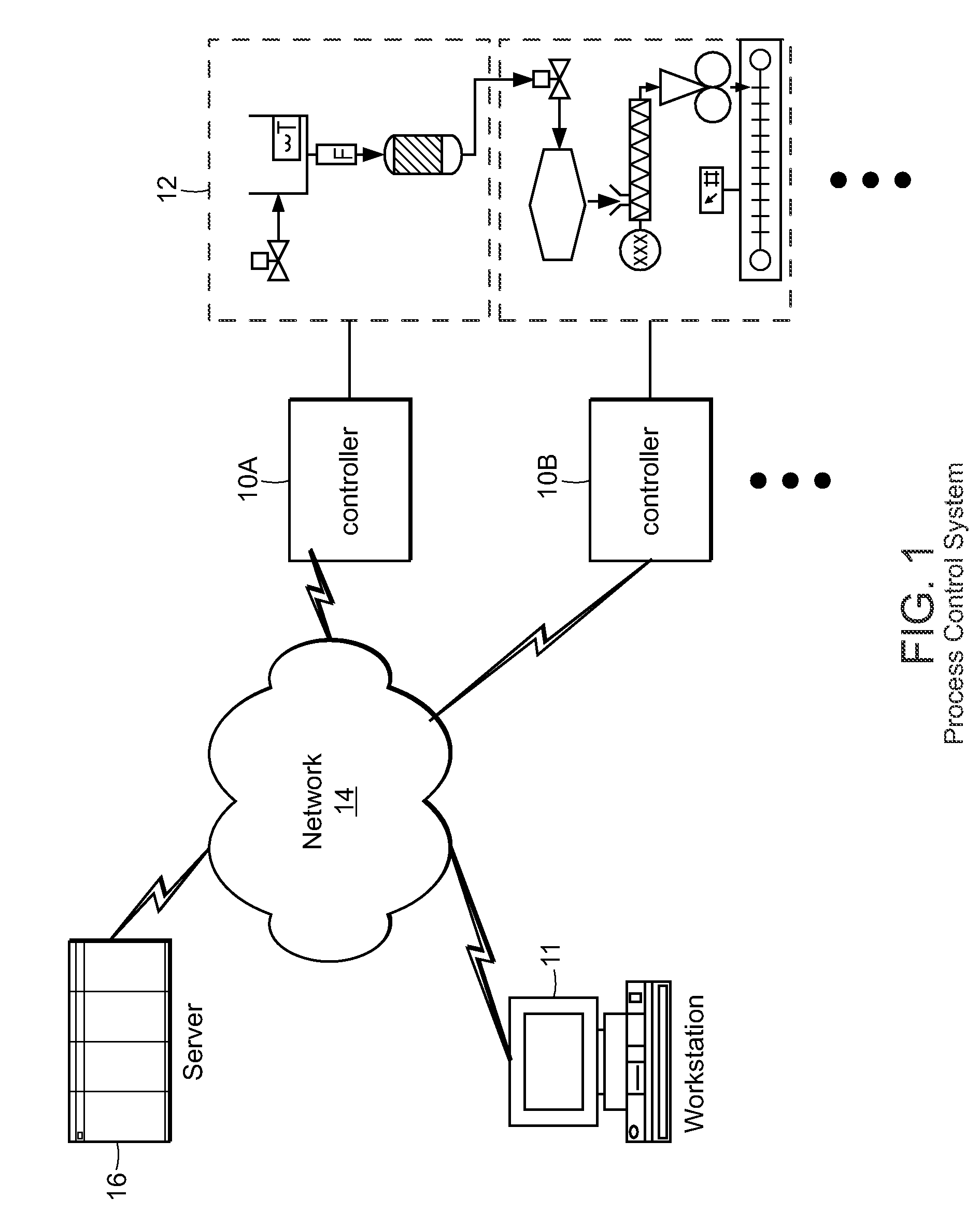
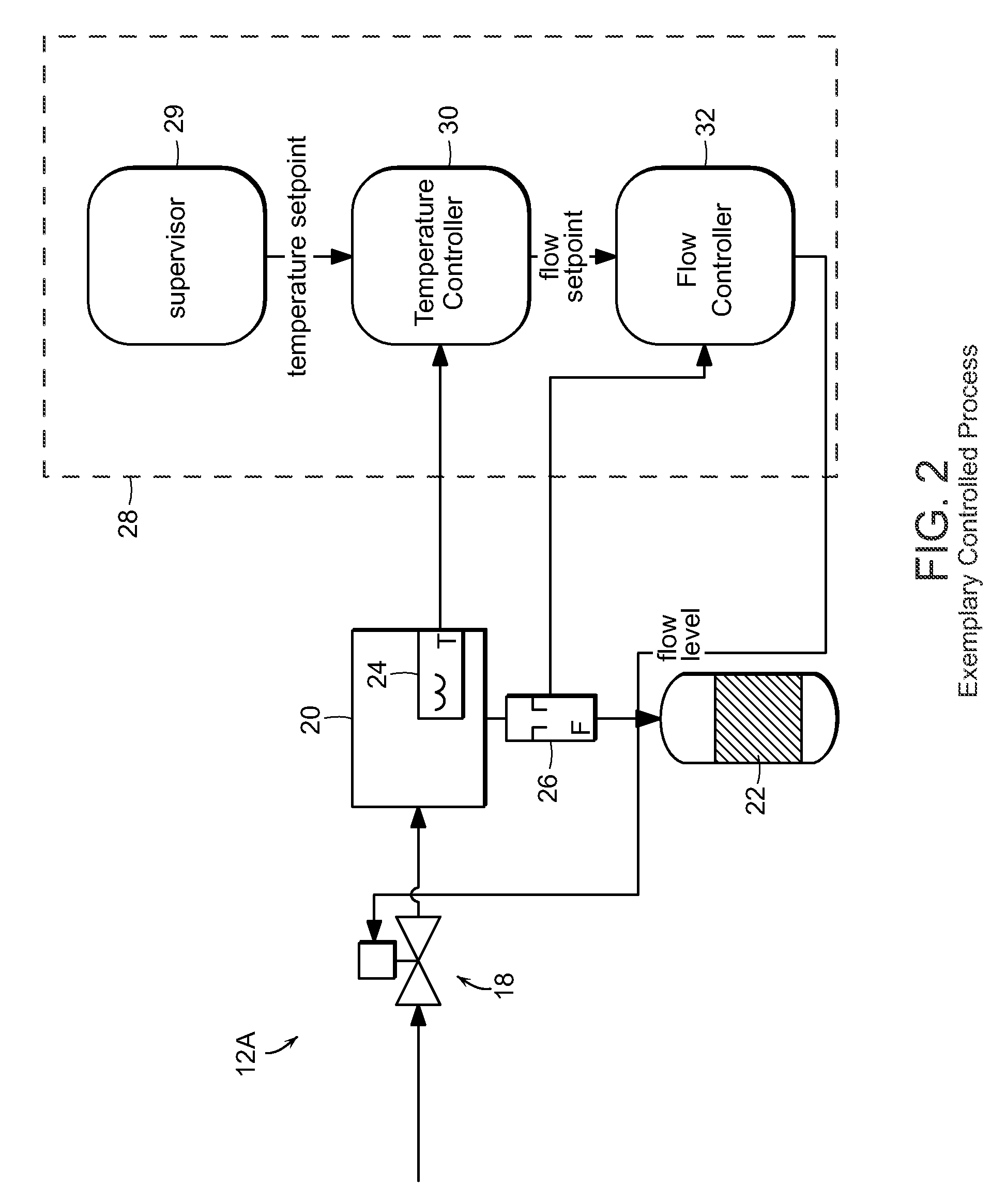
Control system configuration and methods with object characteristic swapping
InactiveUS20090118845A1OptimizationOptimize system configurationVersion controlElectric testing/monitoringGraphicsComposite object
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
Control systems and methods with smart blocks
InactiveUS20090118846A1OptimizationOptimize system configurationData processing applicationsComputer controlGraphicsGraphical user interface
Methods and apparatus for configuring process, environmental, industrial and other control systems generate and / or utilize models representing configurations of control systems and / or the systems controlled by them. Records of changes to the models or the configurations represented by them are maintained, thereby, for example, providing bases for determining current states, prior states and histories of changes. Objects in the model have characteristics, such as an object type characteristic and an area characteristic. Users can have corresponding permissions. A security mechanism apparatus controls access by users to the objects. Composite objects are defined by definition objects and are displayed in encapsulated or expanded formats. Objects can include an edit control type identifier that determines how they are presented for editing. Functionality responds to user commands by transferring characteristics of a first object depicted by the graphical user interface to a second object. Configuration-time formulas contained objects are evaluated to constants prior to downloading to the control system.
Owner:SCHNEIDER ELECTRIC SYST USA INC
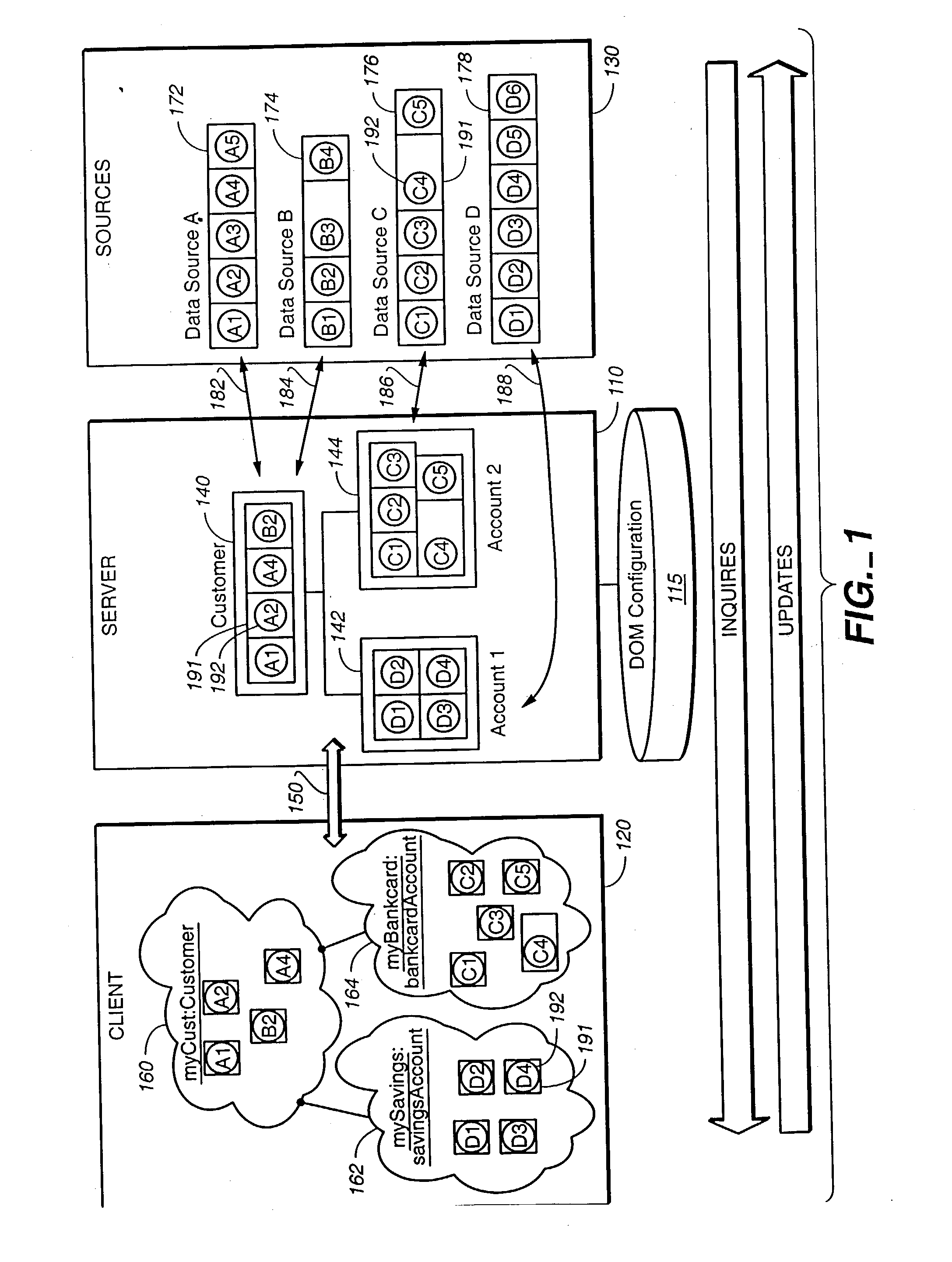
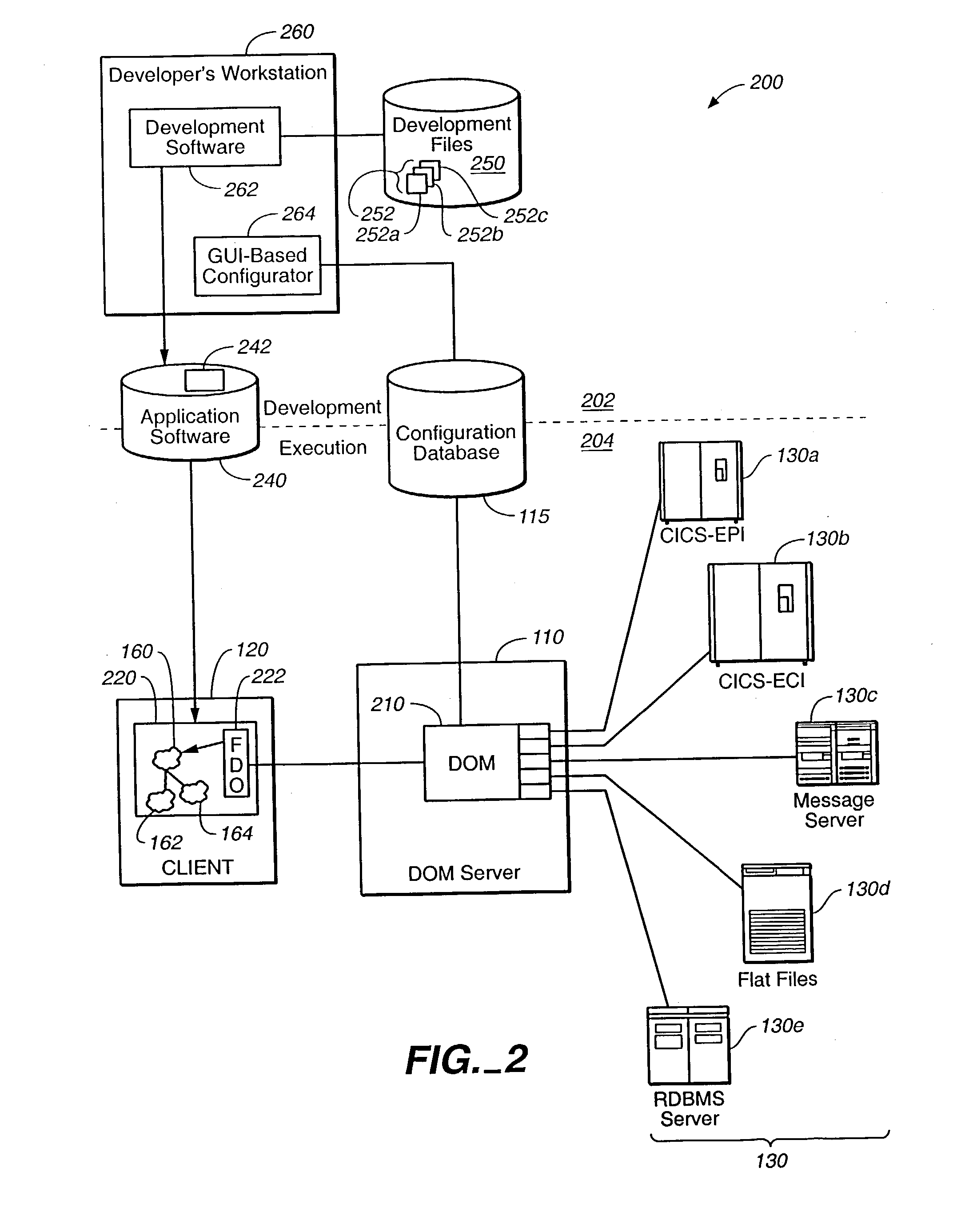
Method and apparatus for data item movement between disparate sources and hierarchical, object-oriented representation
InactiveUS20030120600A1Data processing applicationsDatabase management systemsObject typeSoftware engineering
Data moves between multiple, disparate data sources and the object-oriented computer programs that process the data. A data access server is interposed between the object-oriented programs and the data sources, and acts as an intermediary. The intermediary server receives requests for data access from object-oriented computer programs, correlates each request to one or more interactions with one or more data sources, performs each required interaction, consolidates the results of the interactions, and presents a singular response to the requesting computer program. The consolidated response from the intermediary server contains data items requested by the computer program, information regarding the hierarchical topology that relates the data items, and an indication of the possible object types that might embody the data items. The application program receives the consolidated response and builds an object hierarchy to embody the data items and to interface them to the rest of the application program. The class of an object used to embody data items is selected at execution time from a list of possible candidates.
Owner:BANK OF AMERICA CORP
Balanced binary tree-based method for detecting collisions in large-scale virtual environment
InactiveCN101593366AHigh precisionSolve the degradation problem3D modellingTime complexityBinary tree
The invention relates to a balanced binary tree-based method for detecting collisions in a large-scale virtual environment. According to the characteristics of large object quantity and complex object types in a large-scale visual environment, the method adopts an expanded balanced binary tree to improve a bounding volume hierarchy tree, accelerates the detection of object collisions and reduces time complexity, caused by environmental changes, of tree reconstruction for overcoming the drawbacks of the conventional bounding volume hierarchy method in the real-time detection of collisions in a dynamic environment. The method adopts different bounding volumes according to hierarchy, combines the simplicity and compactibility of the bounding volumes, and improves a collision method as well as the accuracy of collision detection. Concrete processing flow is described in drawings in the abstract.
Owner:BEIHANG UNIV
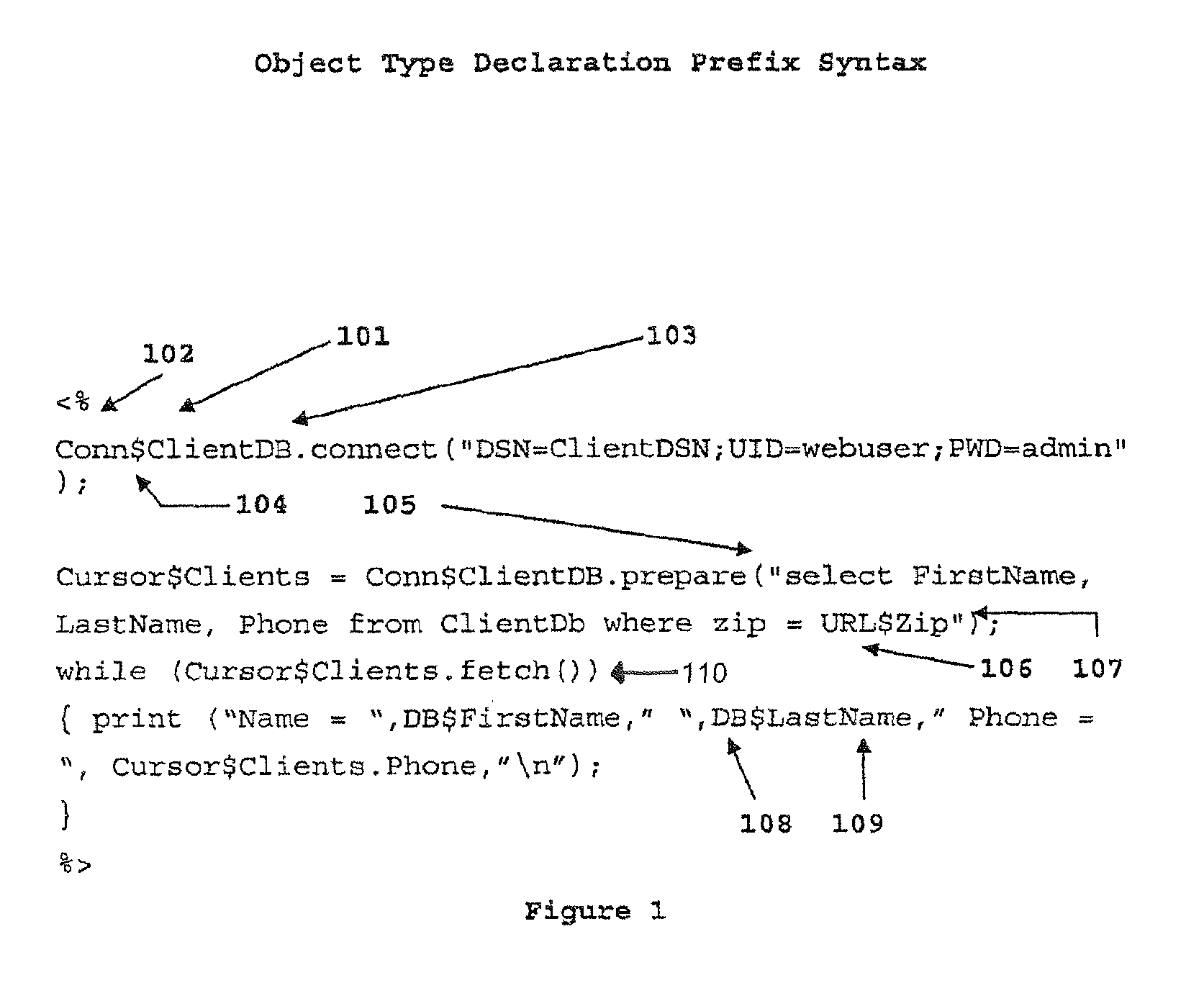
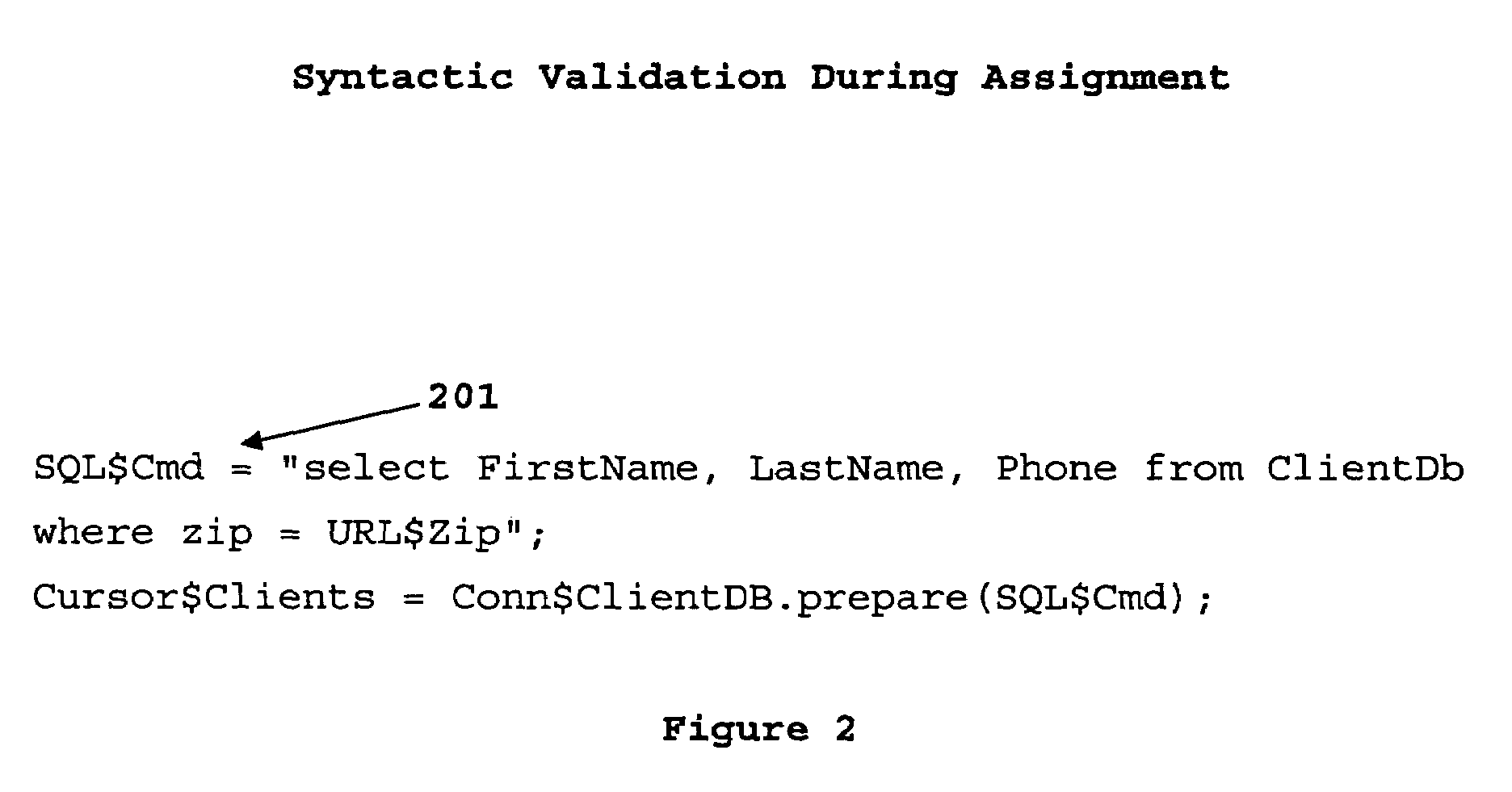
Object type-declaration prefix syntax
InactiveUS7539973B2Sure easyIncrease speedSoftware engineeringSpecific program execution arrangementsSelf-documentingUniform resource locator
A programming language syntax that embeds object type declaration in the object name. The objects are self-documenting because its object type is embedded in each object. In one embodiment, the object type-declaration prefix precedes the object name and explicitly declares the object type information. For example, a SQL object FirstName, may be implemented as SQL@FirstName, a URL object may be implemented as URL@FirstName, environment object from an environment table may be implemented as ENV@user.
Owner:HODGE BRUCE
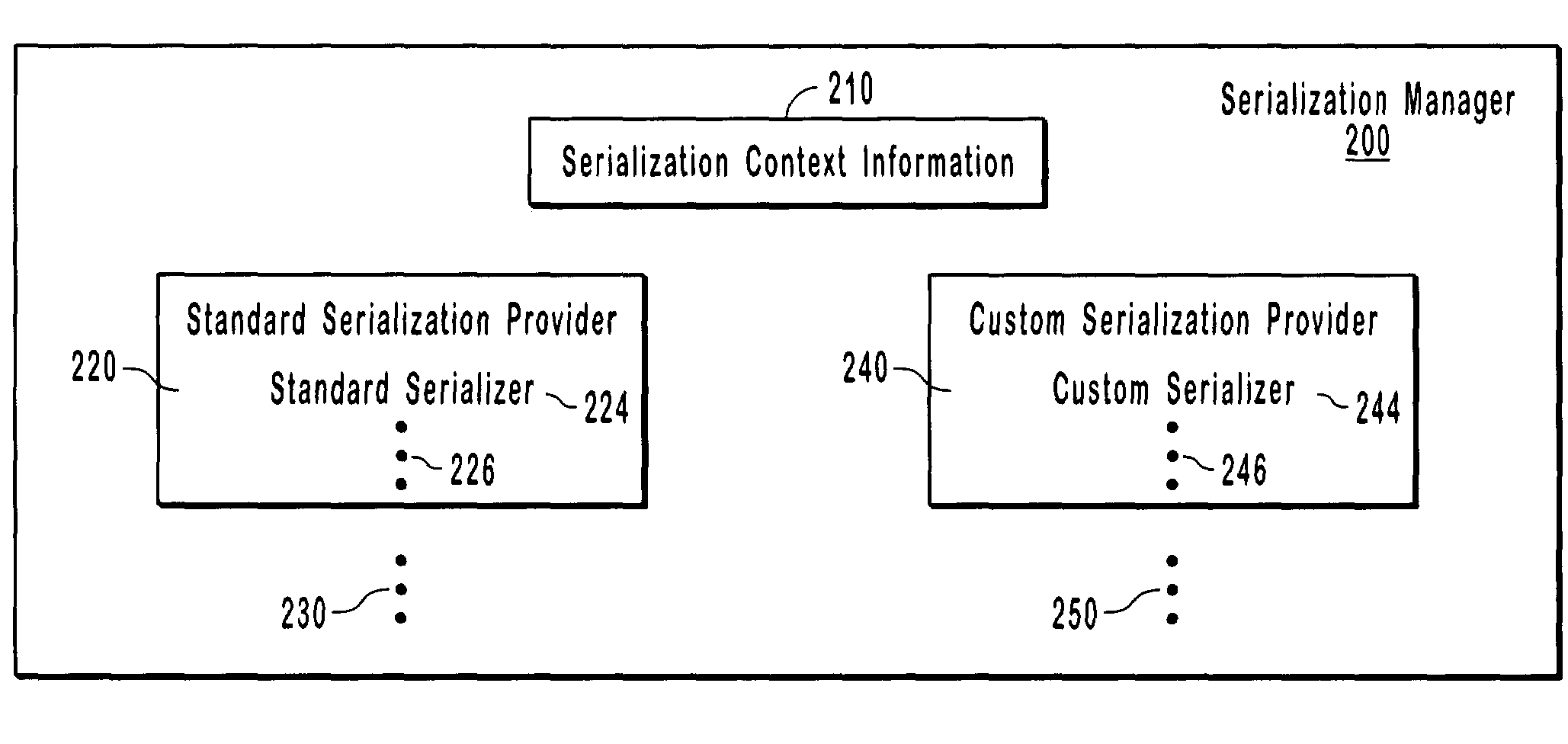
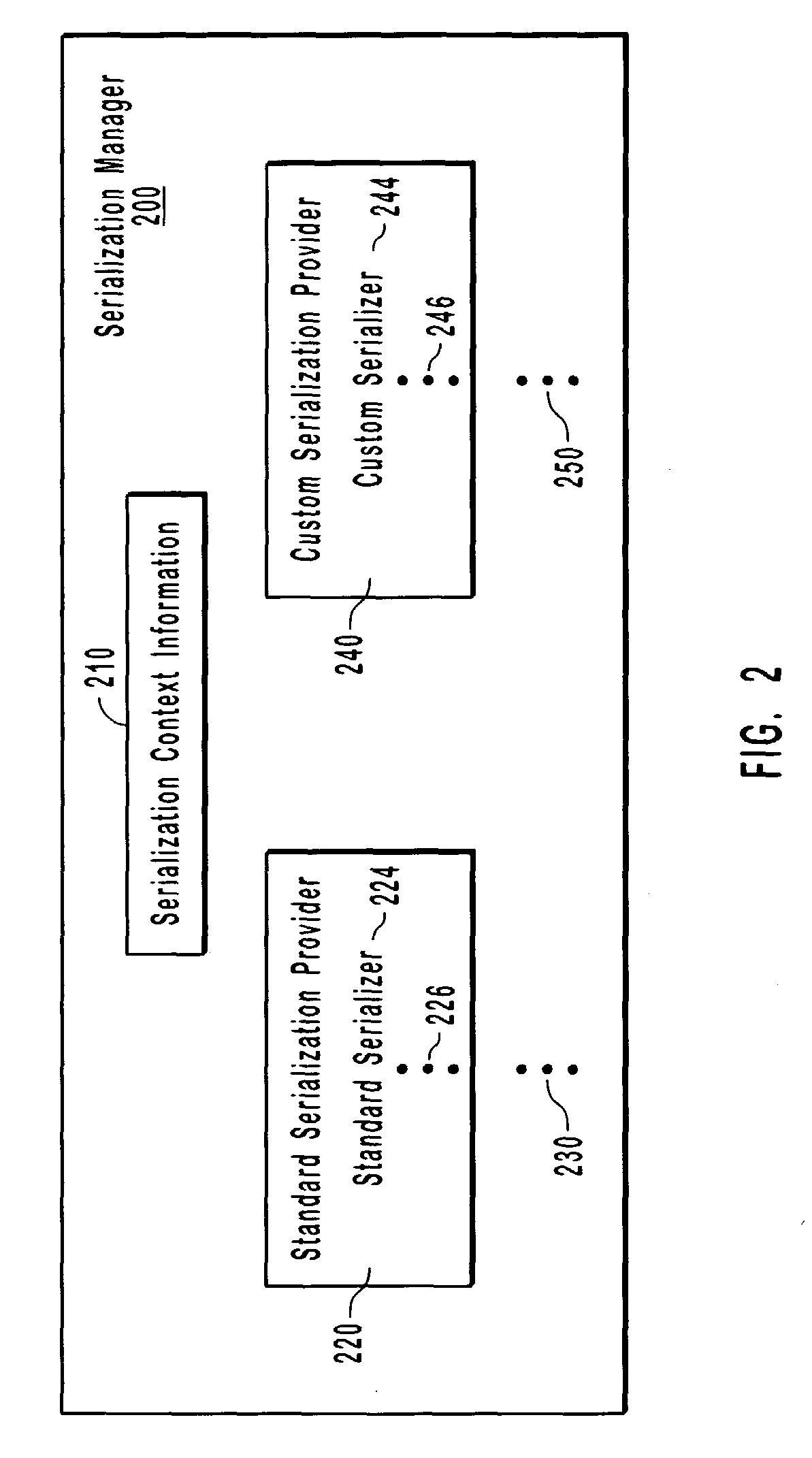
Modular object serialization architecture
InactiveUS7325226B2Transformation of program codeSpecific program execution arrangementsComputer architectureEngineering
Methods, systems, and computer program products to serialize user interface objects having custom object types and serialization formats. A serialization manager may coordinate standard serialization providers to identify standard serializers for standard object types or serialization formats, and as needed, may be extended by loading custom serialization providers to identify custom serializers for custom object types or serialization formats, which may not be covered by the standard serialization providers. From available serialization providers, the serialization manager identifies a serializer for a particular serialization format and object type. The object, custom or standard, is serialized using the identified serializer to a custom or standard format, including source code representations, XML representations, etc. Certain serialization formats produce a snippet of code without producing a class representation of an object; to help coordinate and enhance modularity among serializers and their providers; the serialization manager may maintain and share context information.
Owner:MICROSOFT TECH LICENSING LLC
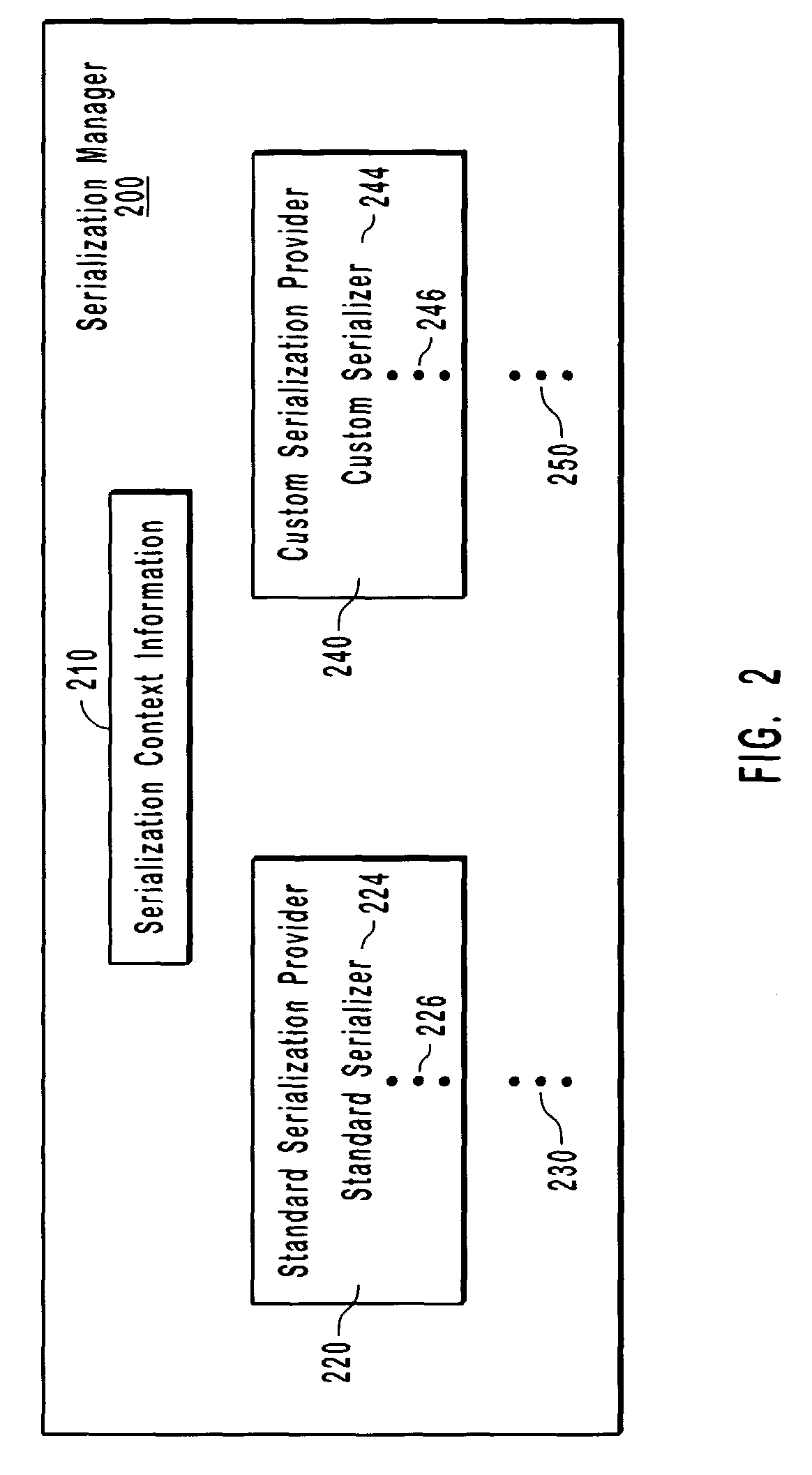
Modular object serialization architecture
InactiveUS20040261008A1Achieve modularityTransformation of program codeSpecific program execution arrangementsModularitySerialization
Methods, systems, and computer program products to serialize user interface objects having custom object types and serialization formats. A serialization manager may coordinate standard serialization providers to identify standard serializers for standard object types or serialization formats, and as needed, may be extended by loading custom serialization providers to identify custom serializers for custom object types or serialization formats, which may not be covered by the standard serialization providers. From available serialization providers, the serialization manager identifies a serializer for a particular serialization format and object type. The object, custom or standard, is serialized using the identified serializer to a custom or standard format, including source code representations, XML representations, etc. Certain serialization formats produce a snippet of code without producing a class representation of an object. To help coordinate and enhance modularity among serializers and their providers; the serialization manager may maintain and share context information.
Owner:MICROSOFT TECH LICENSING LLC
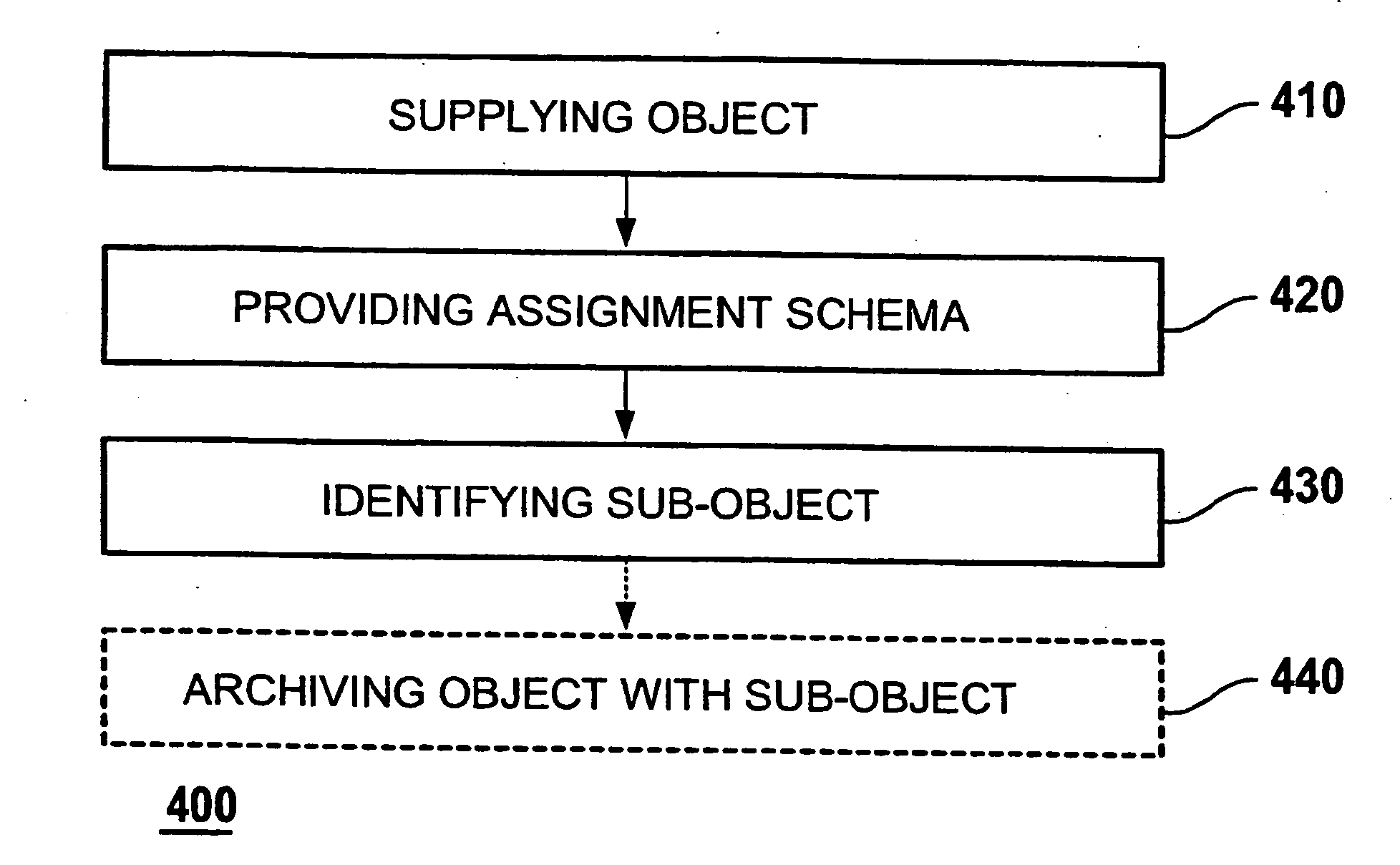
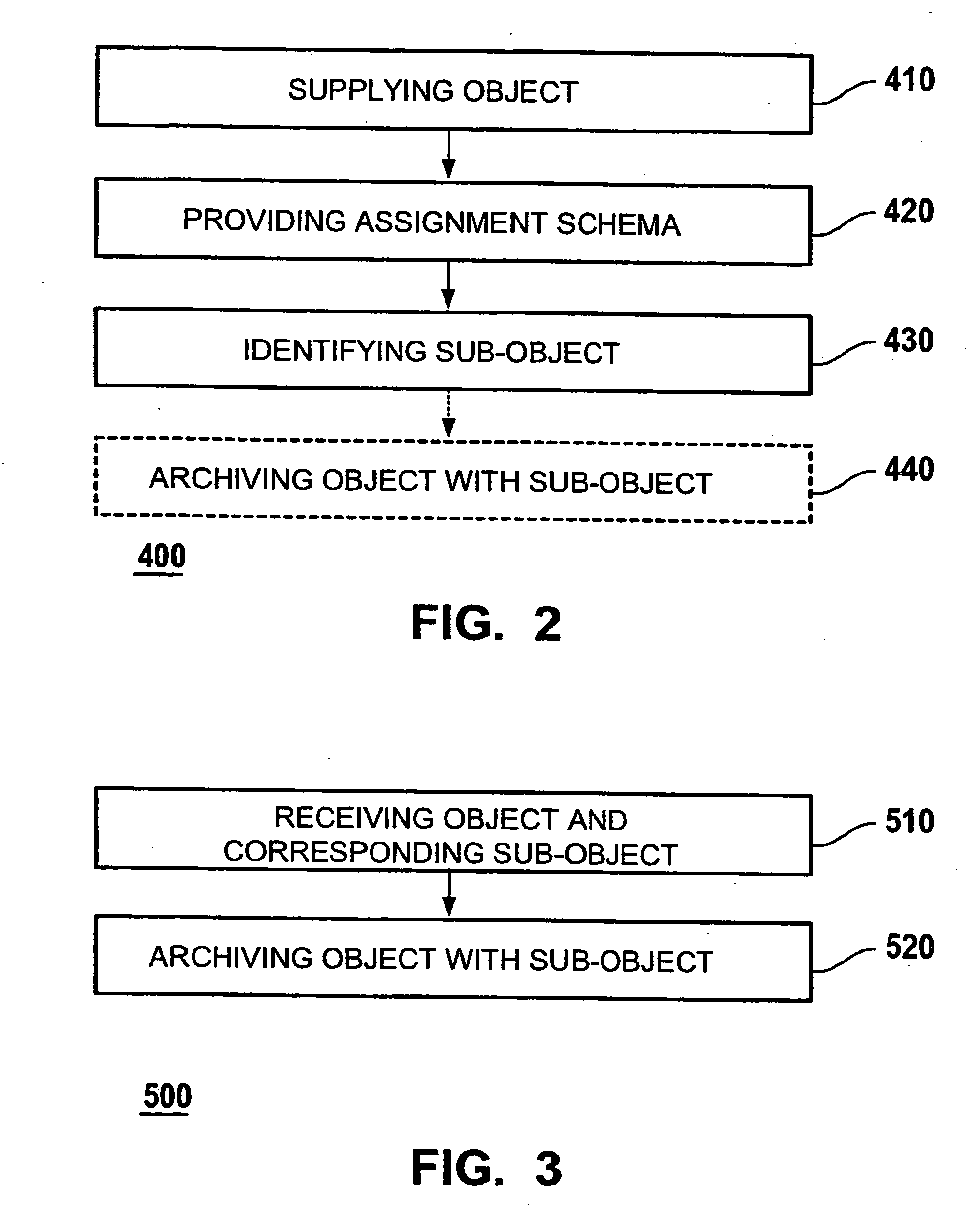
Method and computer system for identifying objects for archiving
ActiveUS20060235906A1Increase flexibilityEliminate needDigital data processing detailsError identificationSystem identificationComputer science
Methods and computer systems are provided for identifying objects for archiving out of a plurality of objects. A first computer system supplies a plurality of objects for archiving. Each object may have an object type and at least one sub-object. Further, an assignment scheme may be provided, which assigns a plurality of sub-object types to the object type. A computer program may identify at least one sub-object for archiving with the object by using the assignment scheme. A second computer system may receive data for archiving from the first computer system. The data may comprise the object and the at least one sub-object that are identified by the first computer system for archiving. The second computer system may store the data.
Owner:SAP AG
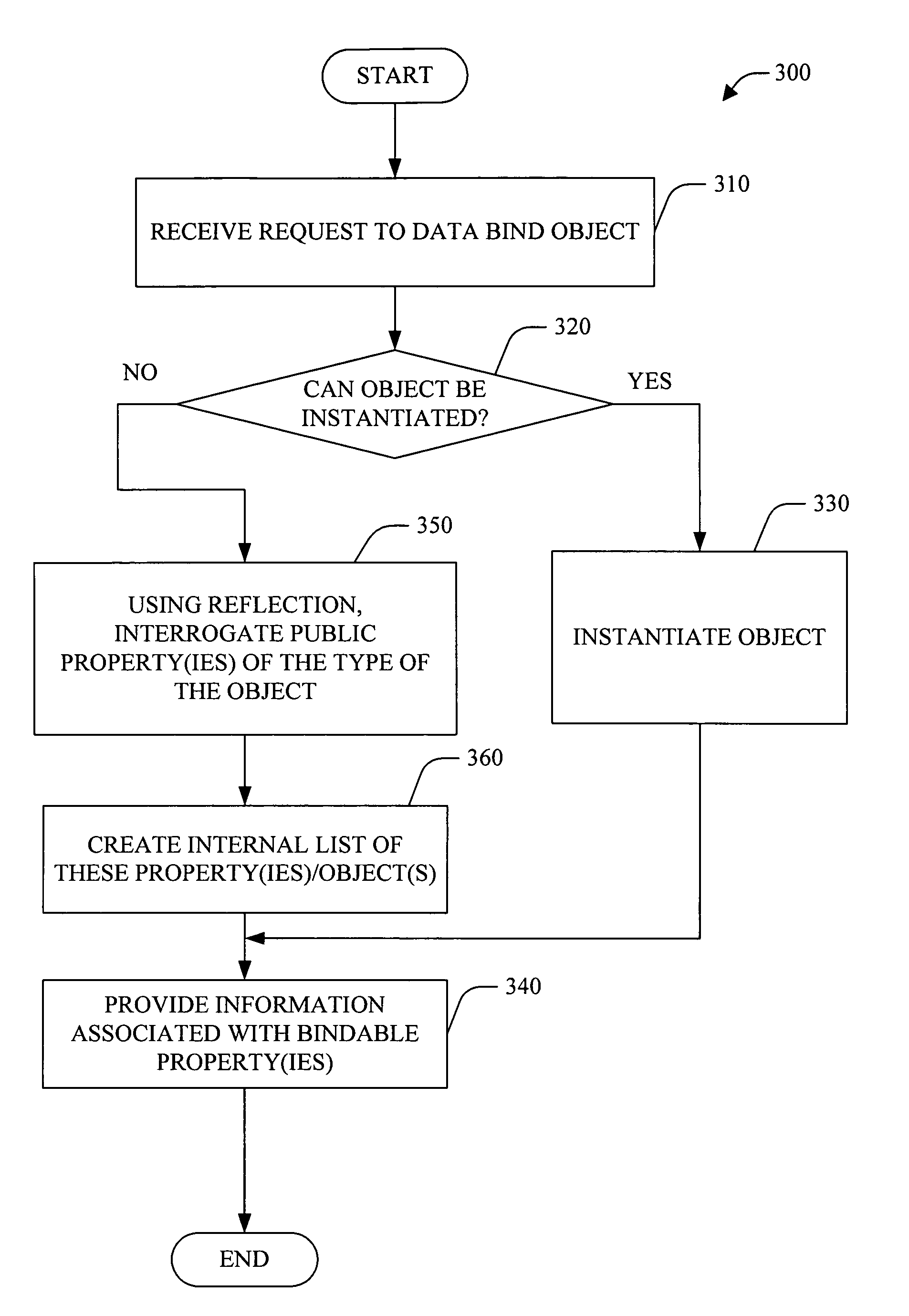
Binding to types
A system and method for system and method data binding to type(s) of object(s) is provided. The system can be employed in a software application development environment to facilitate data binding to types of entity(ies) rather than instance(s) of the entity(ies). The system includes a binding source component that supports the ability to set its data source to a type, rather then a specific instance. For example, when the data source is changed, the binding source component can evaluate whether the data source (e.g., object) can be instanced and whether the data source (e.g., object) supports necessary designer interface(s). If the type isn't supported by the designer, using reflection, the binding source component can interrogate the public properties of the type. Additionally, the binding source component can analyze complex object(s).
Owner:MICROSOFT TECH LICENSING LLC
Determining whether a JAVA object has been scan-missed by a garbage collector scan
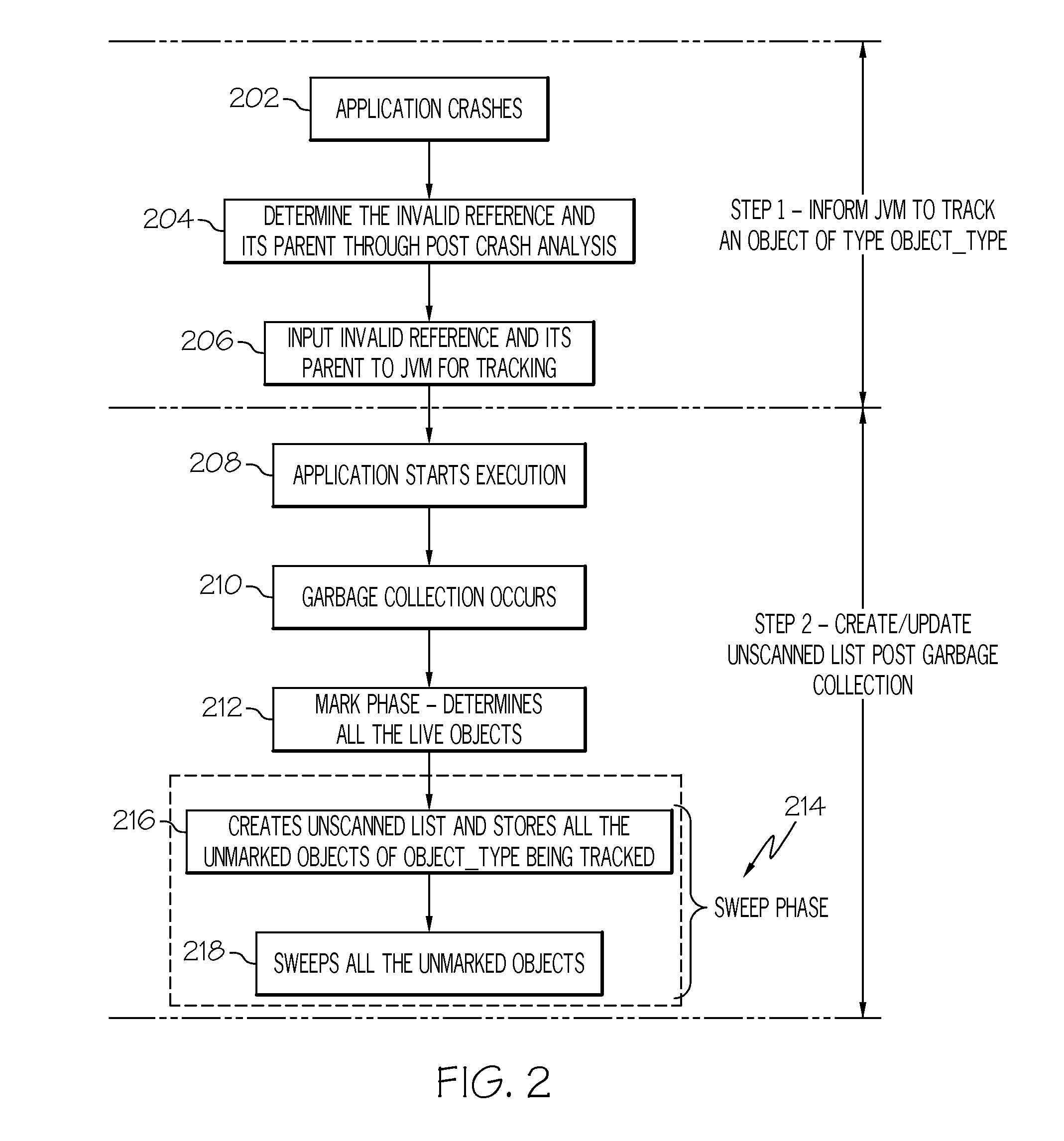
InactiveUS20120158801A1Special data processing applicationsMemory systemsProgramming languageRelevant information
A Java object is scan-missed during the mark phase of a garbage collection cycle. A list of any unscanned objects, comprising all objects of a particular object type, is created during a sweep phase of the garbage collection cycle. After the garbage collection cycle is completed, and the application resumes, for every PUTFIELD / GETFIELD operation on the object type that is part of a specific parent object, a comparison is made with the relevant information in the unscanned objects list. A scan-miss is identified by determining whether the current object being referenced by the application is a part of the unscanned object list that has been created during the sweep phase of the garbage collection cycle.
Owner:IBM CORP
Building complex hierarchical queries
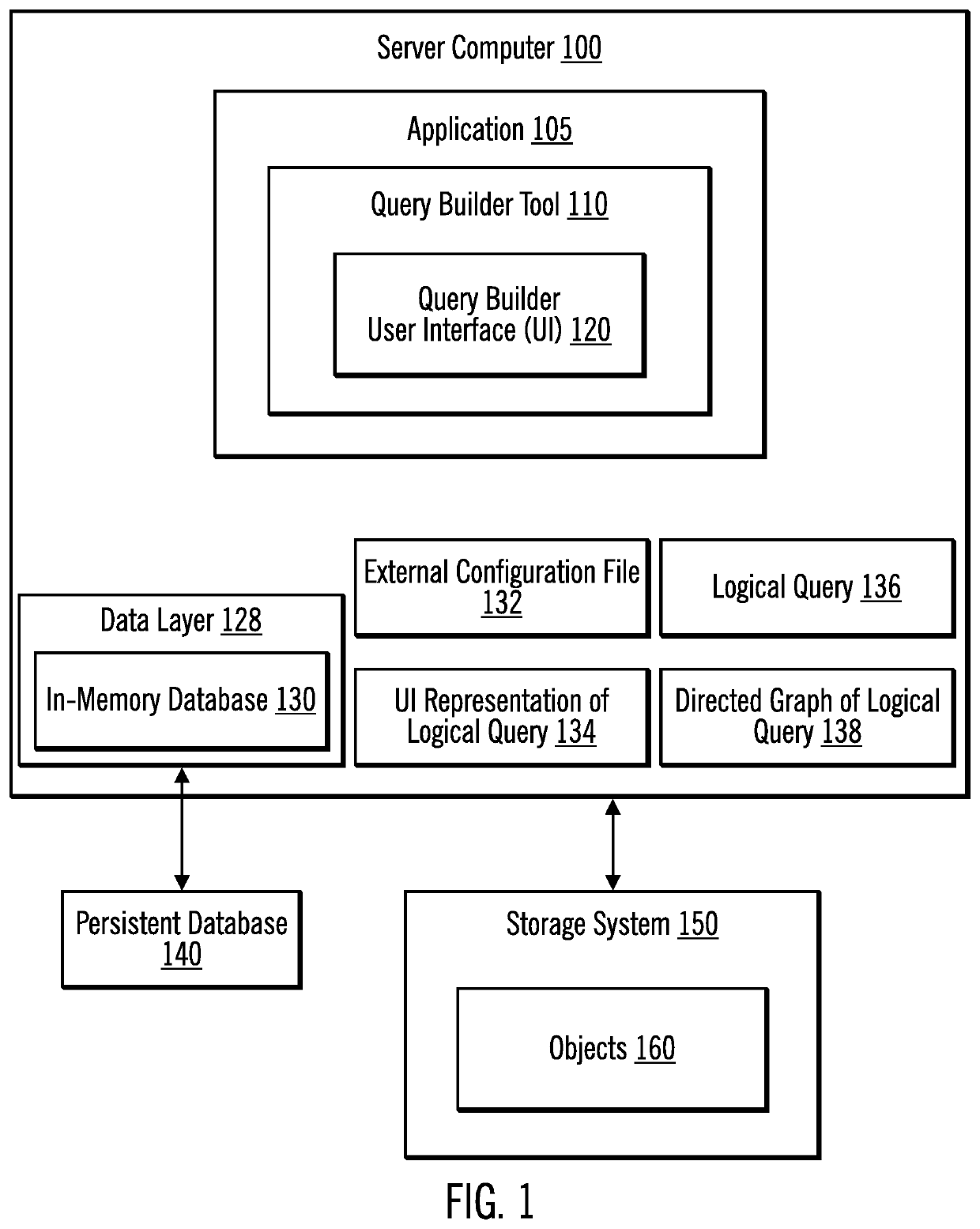
ActiveUS10649989B2Avoid difficult choicesQuickly and easily visualizeOther databases indexingSpecial data processing applicationsObject typeLogical query
Provided are a computer program product, system, and method for building complex hierarchical queries. A User Interface (UI) representation of a logical query is received, wherein the UI representation describes object types, relationships between the object types, and attributes of the object types. The UI representation is translated to a logical query. The logical query is converted to data layer calls to retrieve objects having the object types, the relationships between the object types, and the attributes of the object types. The objects are received. Then, a directed graph is generated using the identified objects.
Owner:IBM CORP
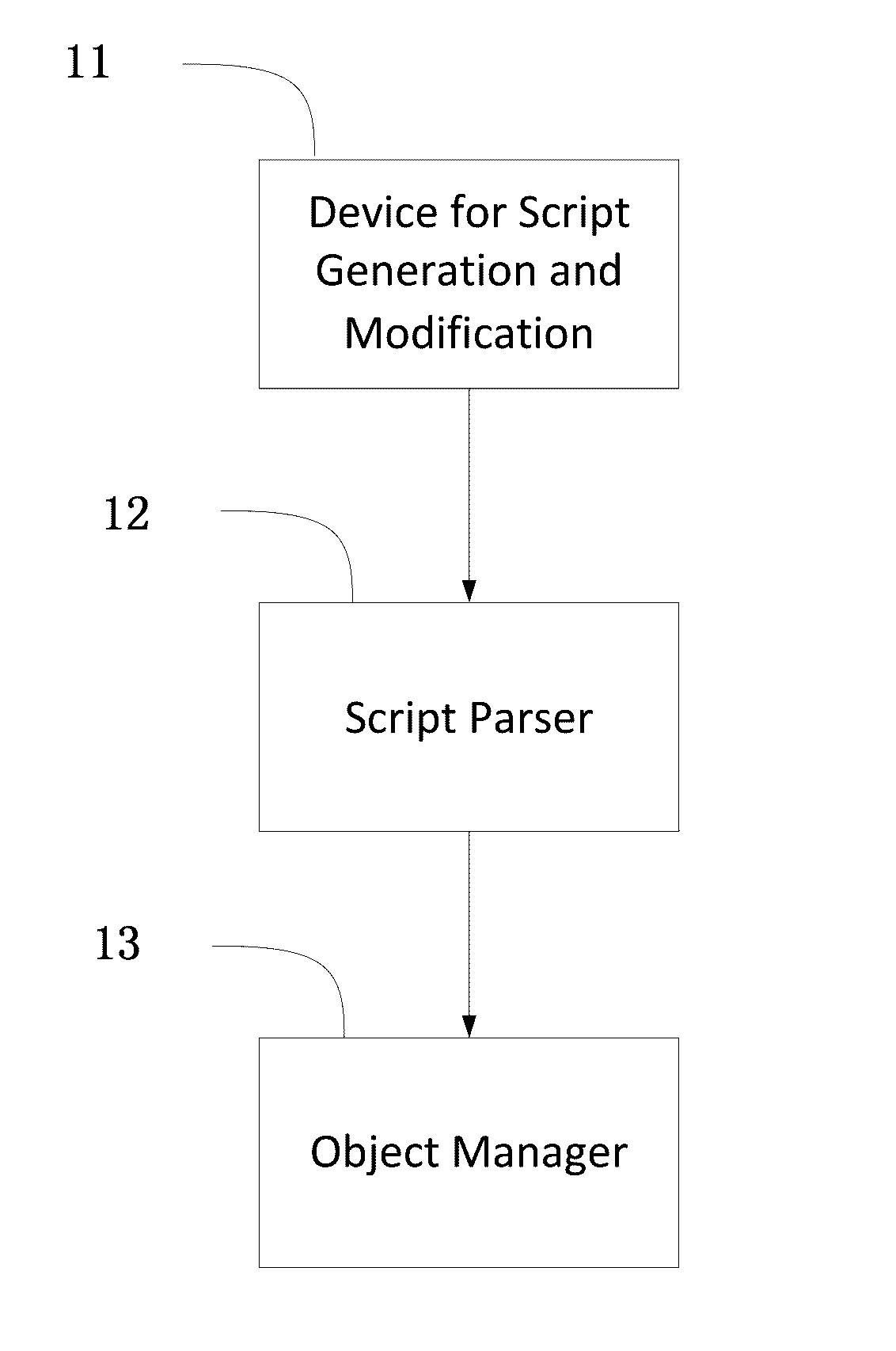
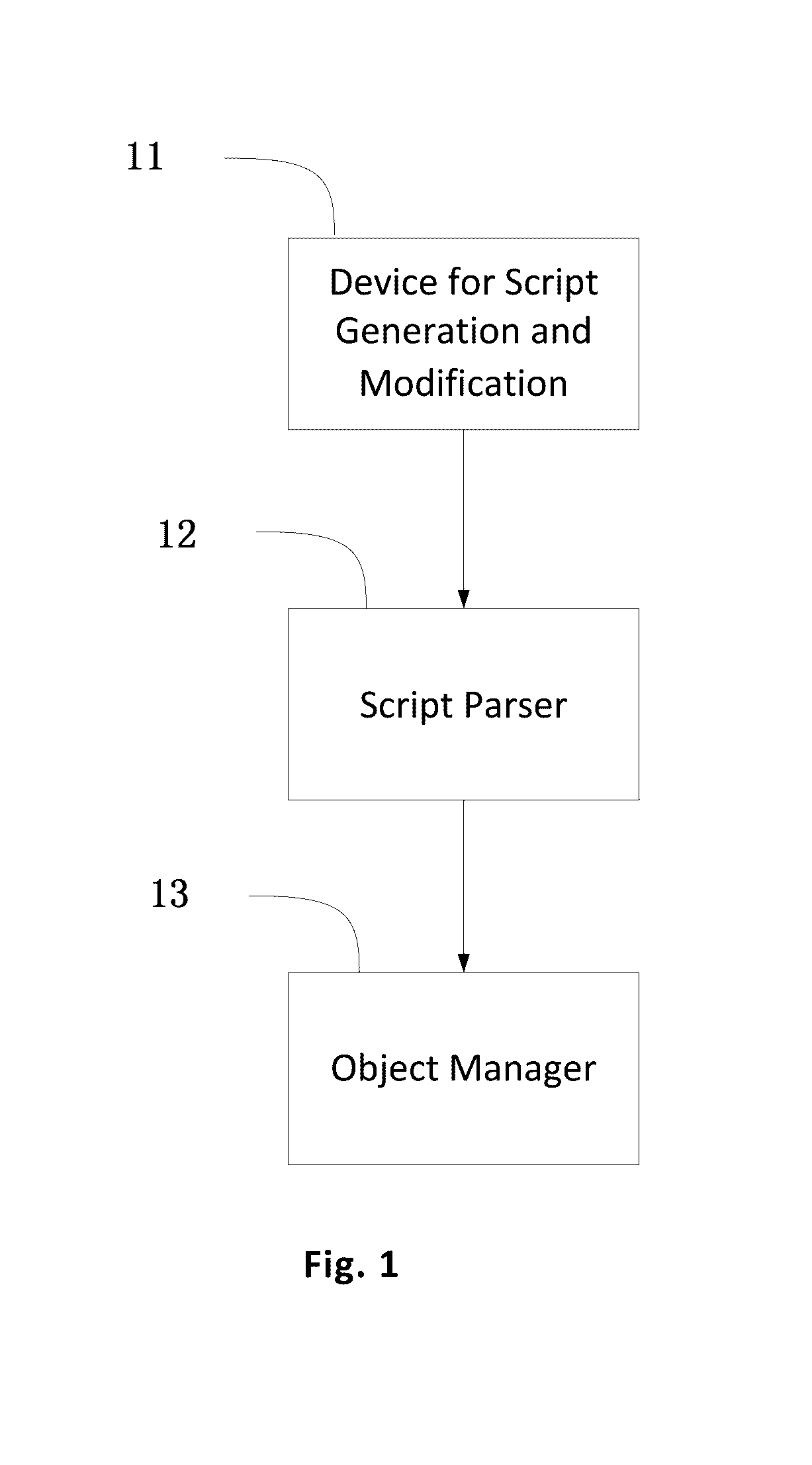
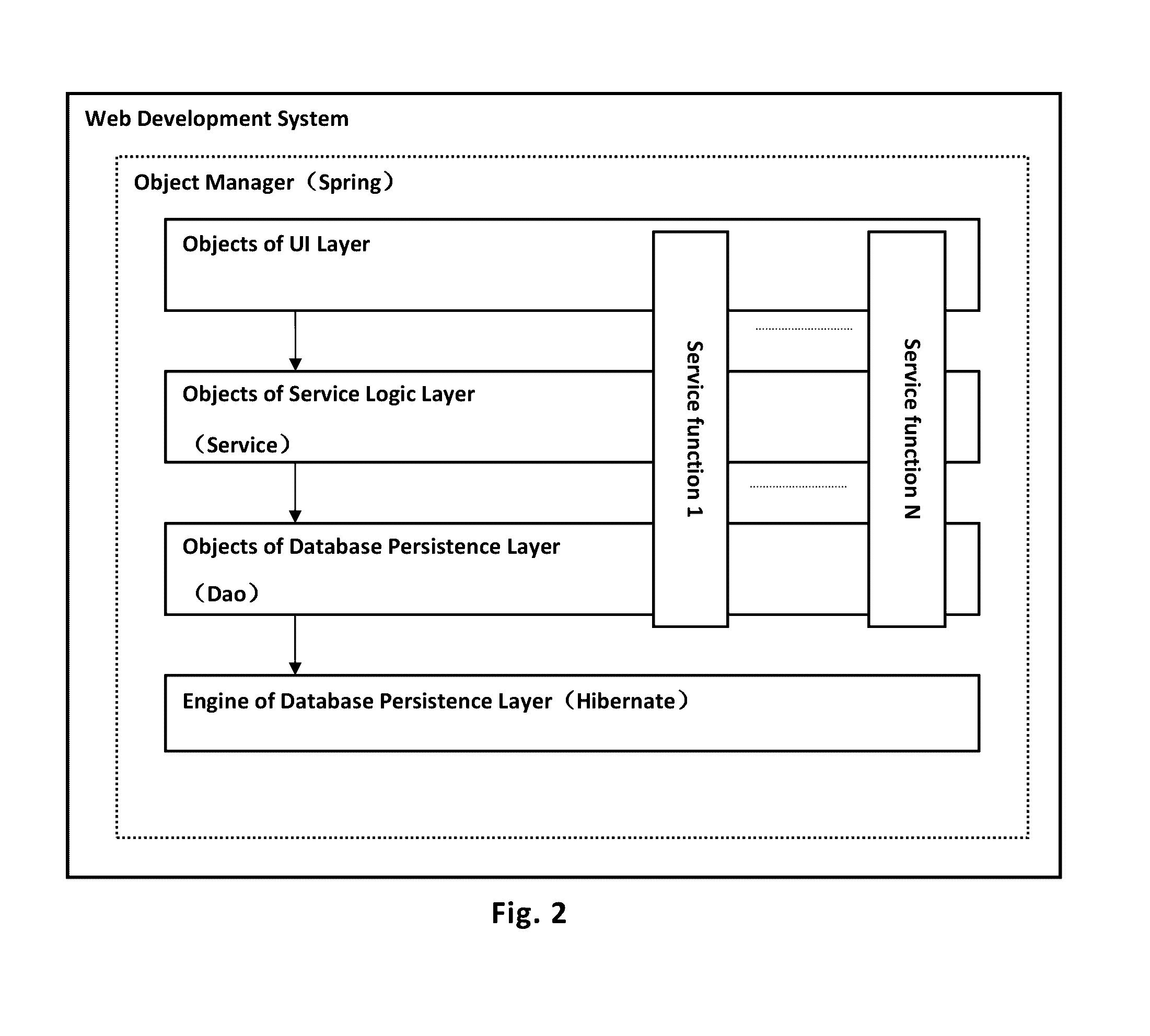
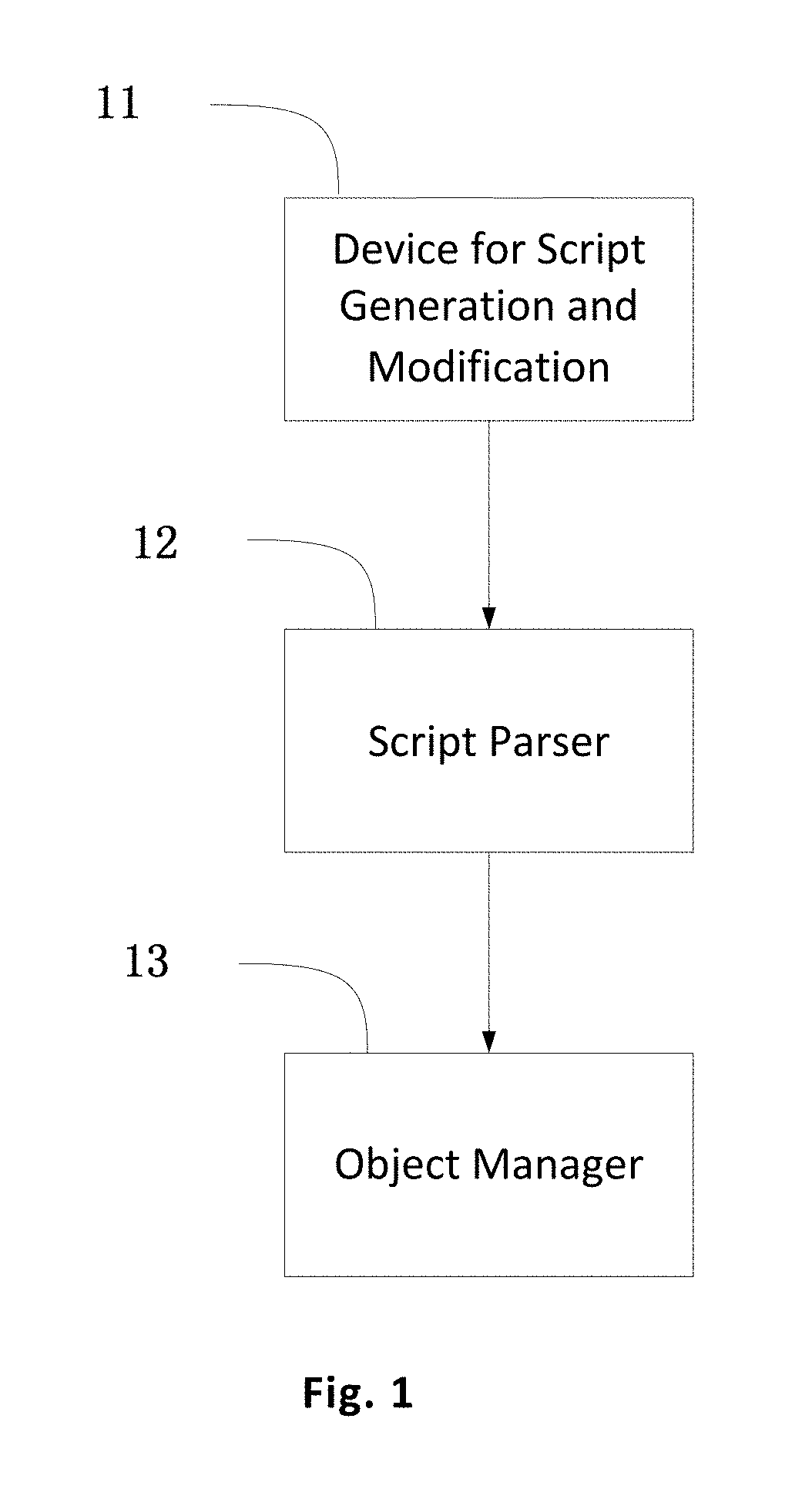
Development method for web development system, and web development system
ActiveUS20160299745A1Improve securityQuick buildProgramming languages/paradigmsProgram loading/initiatingObject typeSoftware engineering
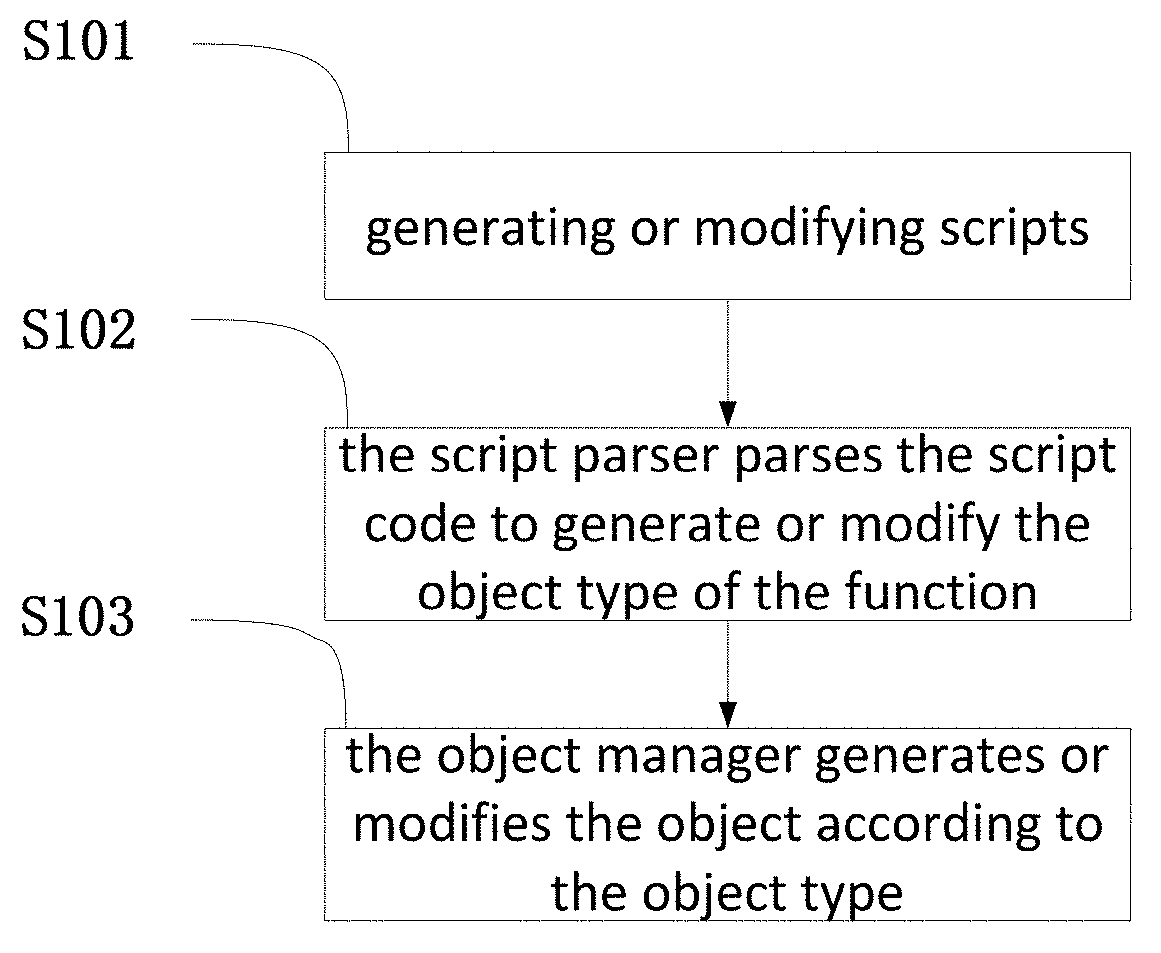
A web development method for a web development system includes, in a running state of the web development system, generating or modifying script code used to perform a predetermined function; parsing, by a script parser, the generated script code or the modified script code to correspondingly generate an object type which performs a new function, or to modify the object type which performs an existing function; and generating a new function object or modifying the existing function object, by an object manager, according to the generated object type which performs the new function or the modified object type which performs the existing function, and organizing the invoking relationships between the new function object and other objects, or, invoking relationships between the modified function object and other objects, so as to generate or modify the predetermined function when the web development system is operating.
Owner:ZHANG JIE +1
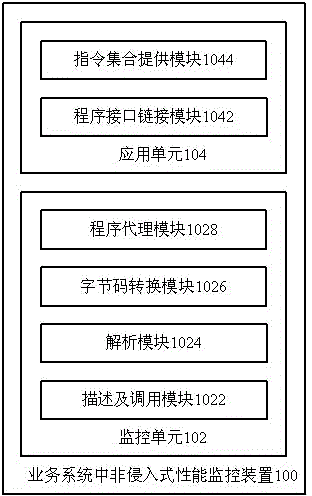
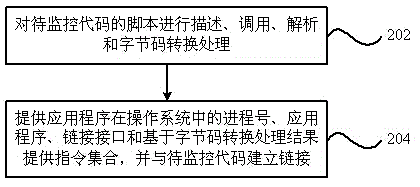
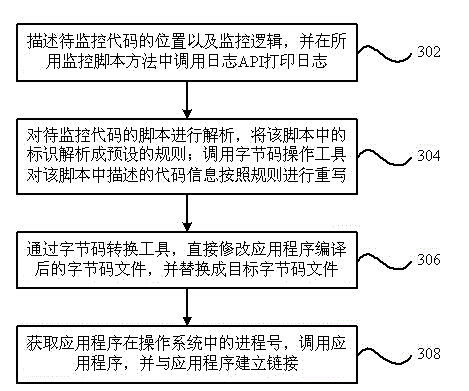
Non-intrusive performance monitoring device and method for service system
The invention provides a non-intrusive performance monitoring device for a service system. The non-intrusive performance monitoring device comprises a monitoring unit and an application unit, wherein the monitoring unit is used for conducting describing, calling, analyzing and bytecode conversion on the script of a code to be monitored; the application unit is used for providing a process number of an application program in an operating system, the application program and a link interface, and providing an instruction set on the basis of the bytecode conversion result, and a link is established between the application unit and the code to be monitored. The invention further provides a non-intrusive performance monitoring method for the service system. According to the technical scheme, on the basis of existing non-intrusive performance monitoring modes, a single-object type can be fully utilized for completing non-intrusive performance monitoring on a multi-object type, and a general and unified monitoring thought of non-intrusive performance monitoring in which the multi-object type participates is figured out.
Owner:YONYOU NETWORK TECH
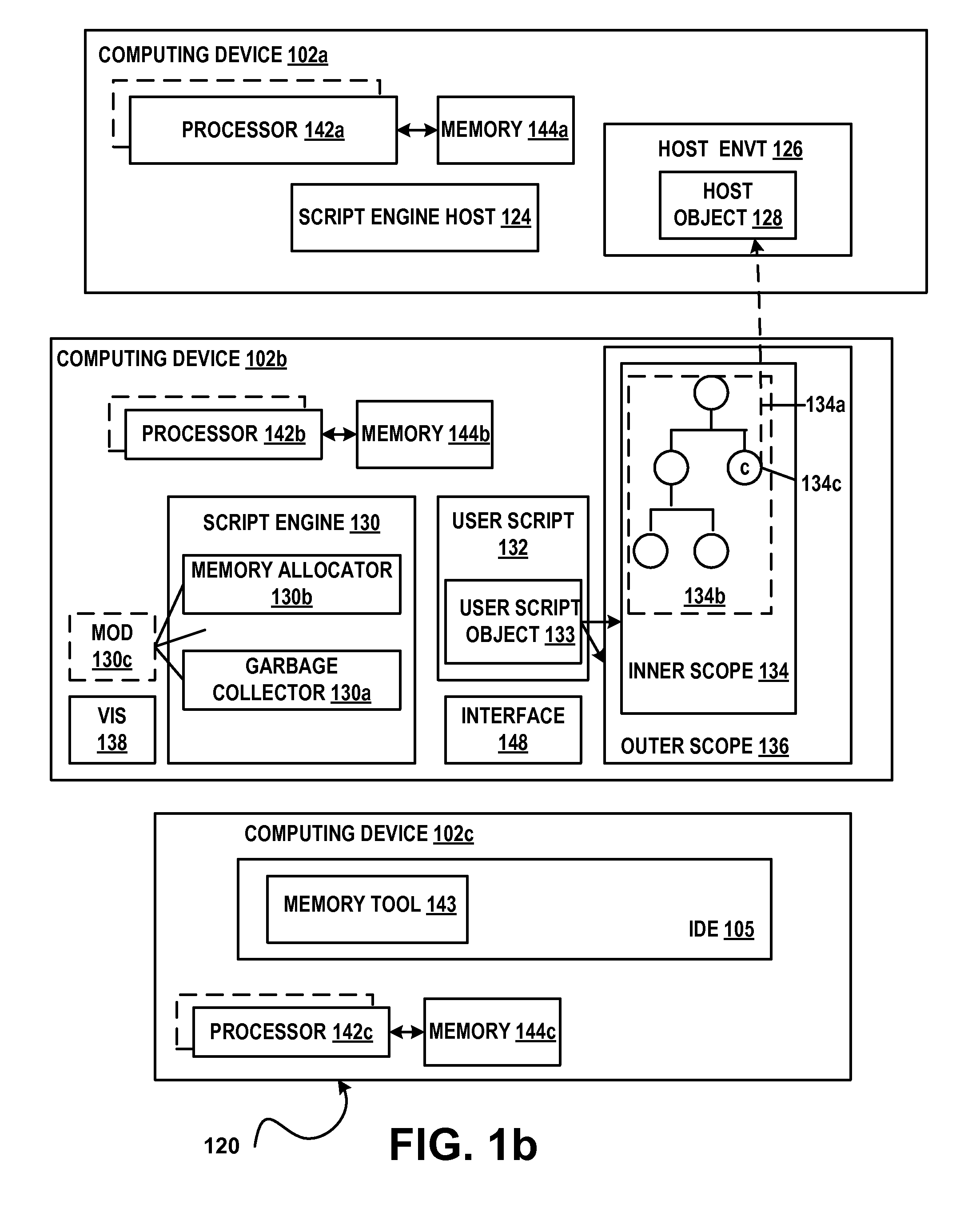
Memory usage data collection and analysis for dynamic objects
ActiveUS20130246417A1Digital data processing detailsError detection/correctionThird partyInformation object
A script engine for a dynamic language can collect memory allocation information for dynamic objects created by the scripting engine and for dynamic objects created by the script engine host. A native interface can be exposed to a client comprising a software development tool. The software development tool can be a third-party tool. In response to a query, the script engine can take a snapshot of a garbage collector heap and return an object record for each dynamic object in the heap. The object information can include memory allocation information, object type and other information. Multiple snapshots can be taken and the delta between snapshots can be determined and sent to a requestor.
Owner:MICROSOFT TECH LICENSING LLC
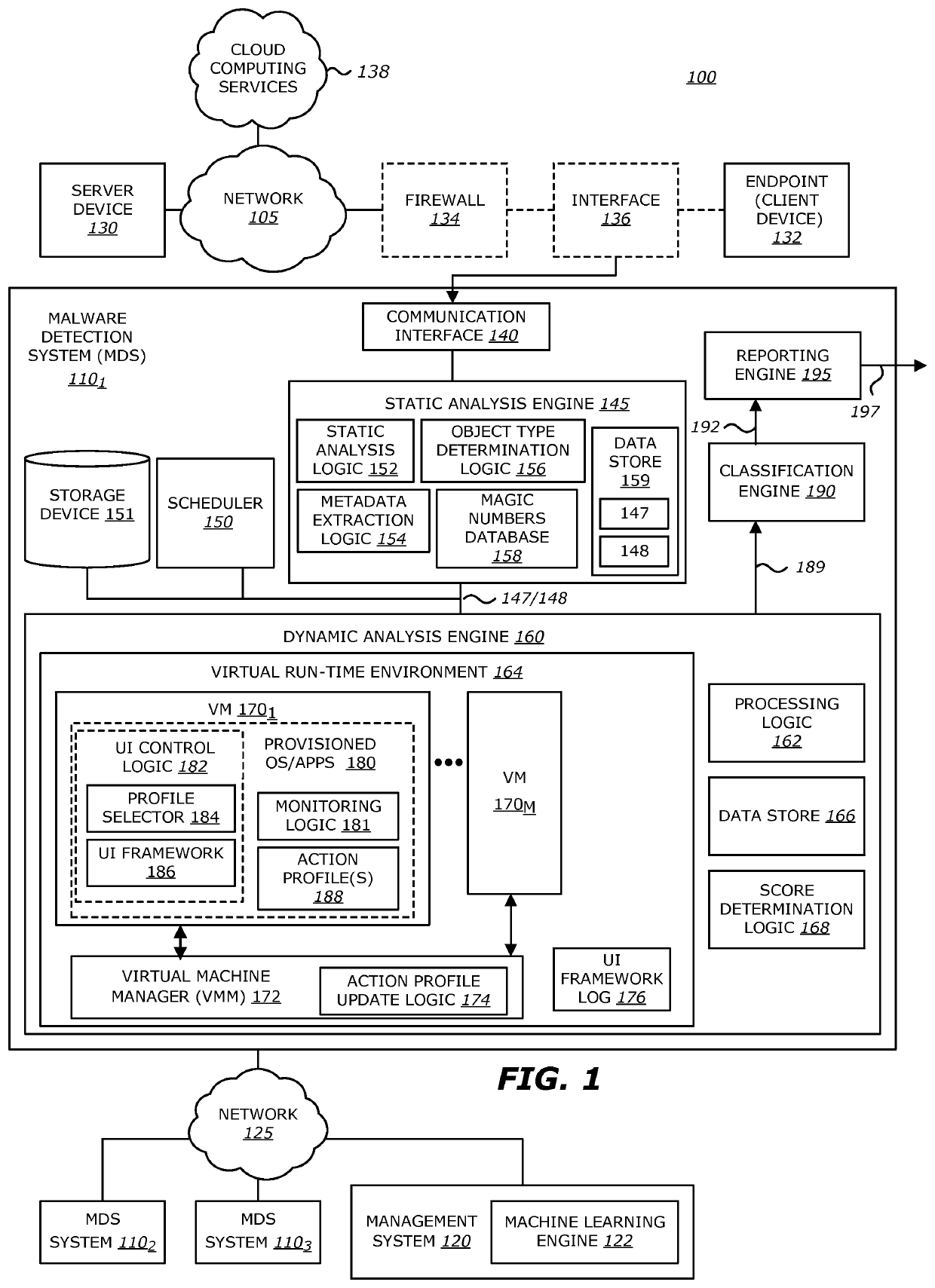
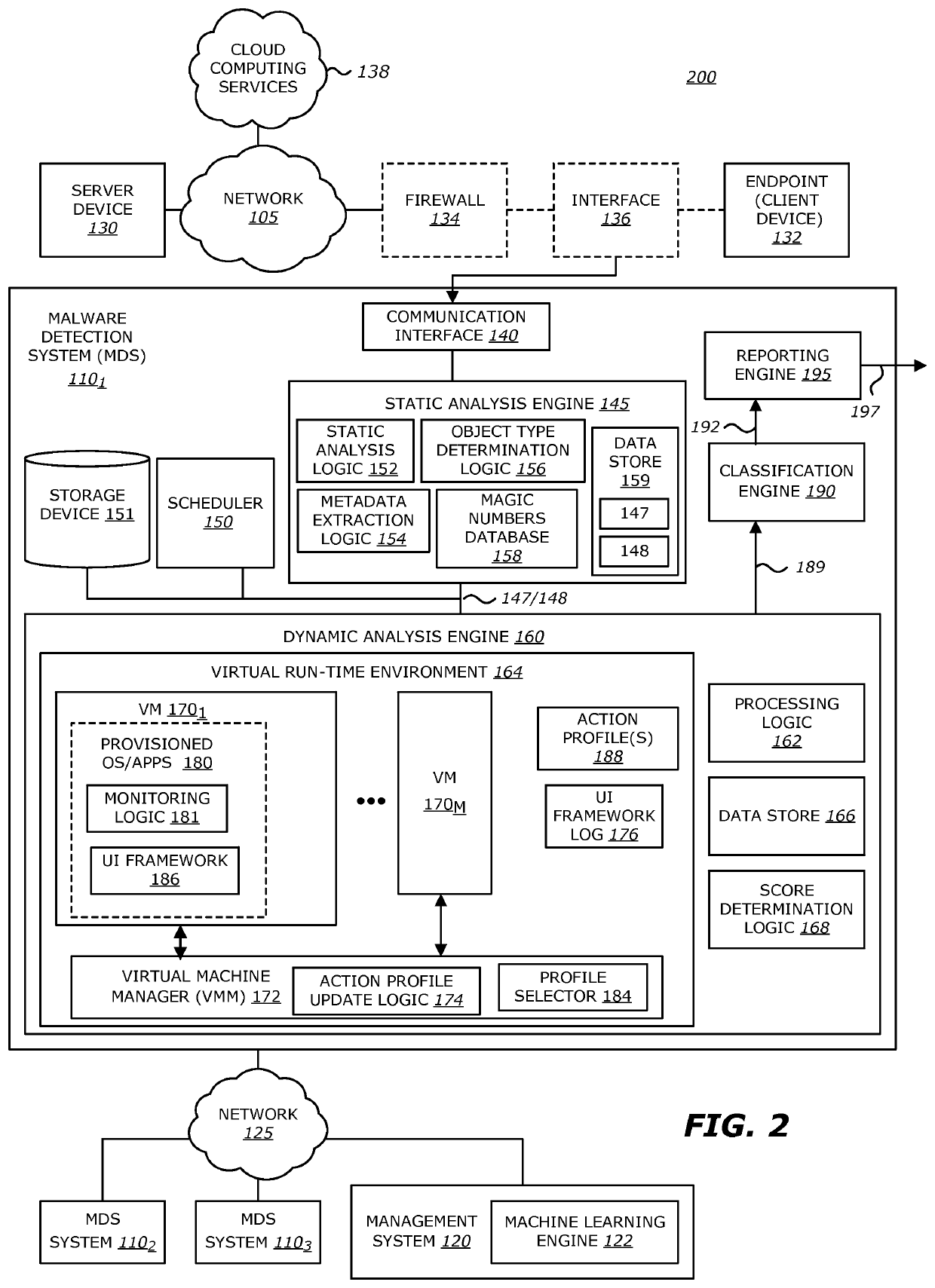
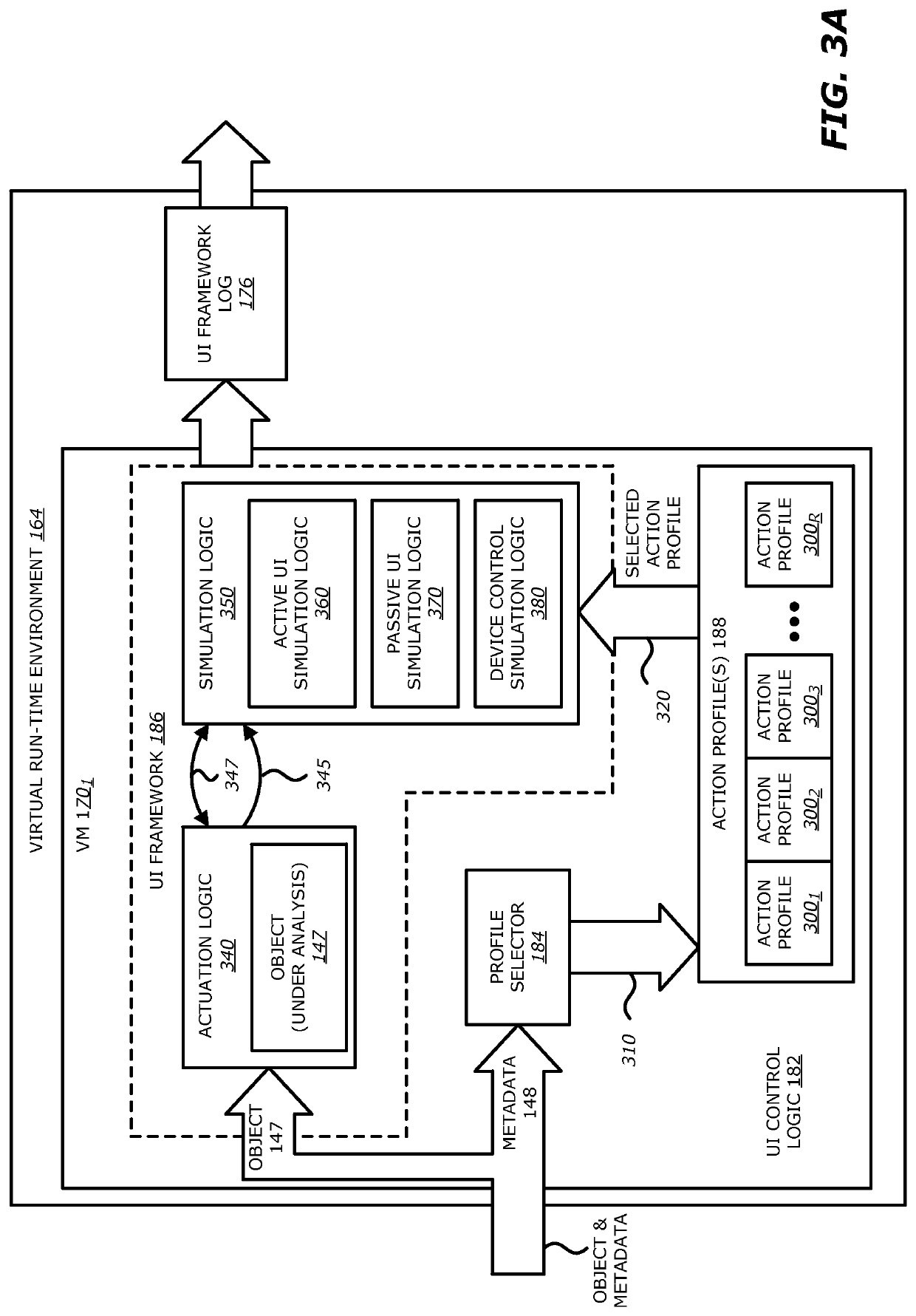
Intelligent context aware user interaction for malware detection
According to one embodiment, a malware detection system is integrated with at least a static analysis engine and a dynamic analysis engine. The static analysis engine is configured to automatically determine an object type of a received object. The dynamic analysis engine is configured to automatically launch the object after selecting an action profile based on the object type. The dynamic analysis engine is further configured to, provide simulated user interaction to the object based on the selected action profile either in response to detecting a request for human interaction or as a result of a lapse of time since a previous simulated human interaction was provided.
Owner:FIREEYE SECURITY HLDG US LLC
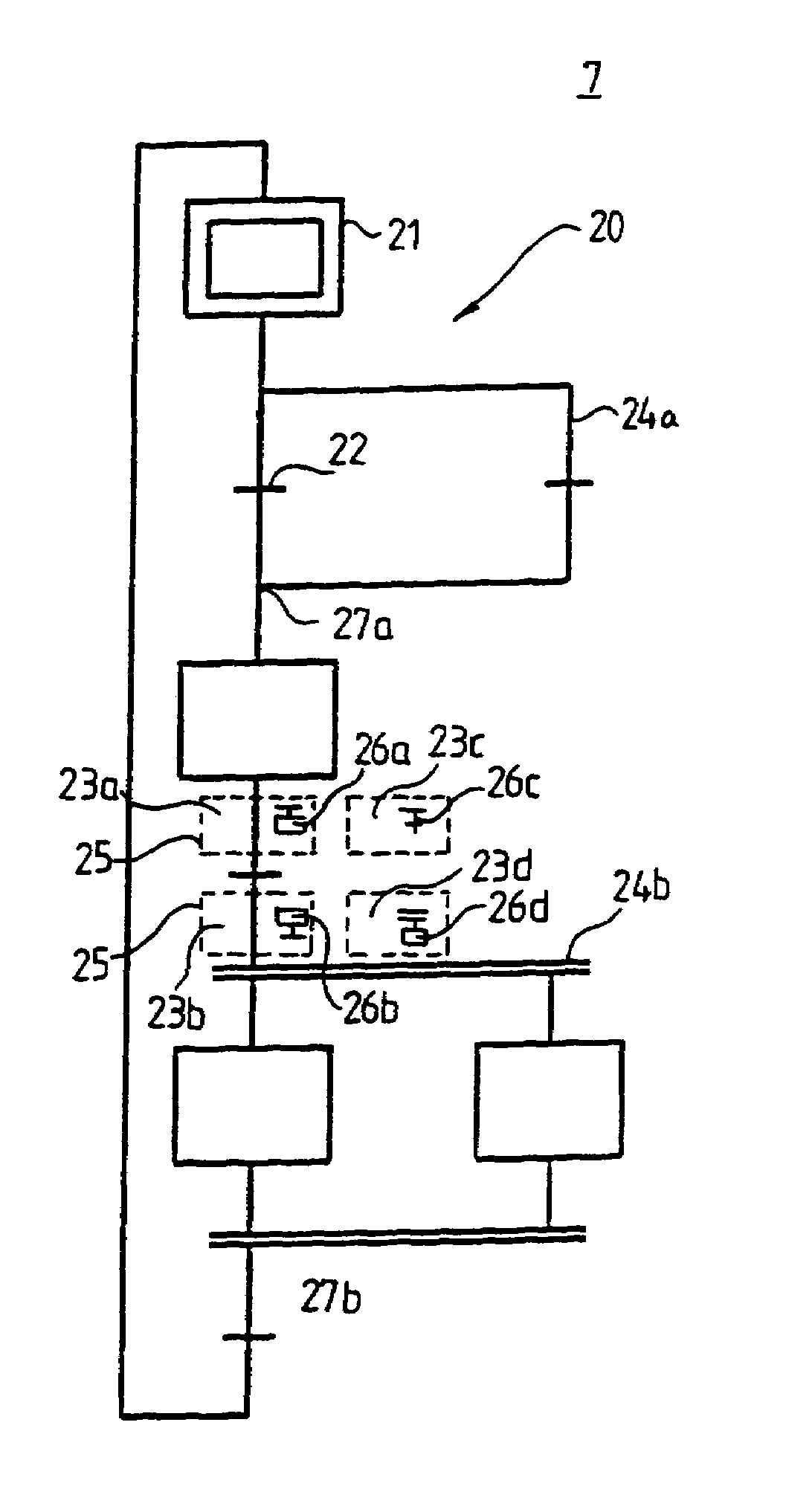
Method for inserting objects into a working area in a computer application
InactiveUS7071952B1Simple procedureEliminate needCathode-ray tube indicatorsComputer programmed simultaneously with data introductionInput selectionDisplay device
The present invention relates to a method for facilitating the insertion of an object in a working area on a computer display, and is implemented in a computer application software. The method comprises the steps of indicating at least one subarea of the working area where an object is insertable, indicating an object type in association with each subarea, an object of said object type being insertable in said subarea, receiving input from the user selecting one of the at least one subarea, and inserting in the selected subarea an object of the type that is indicated at the selected subarea. Through this method, the user only needs to provide one single piece of input in order to insert an object in a valid location in a working area.
Owner:ACTCON CONTROL
Method, system and product for determining standard Java objects
InactiveUS7539975B2Decompilation/disassemblySpecific program execution arrangementsObject ClassAnalysis tools
Owner:IBM CORP
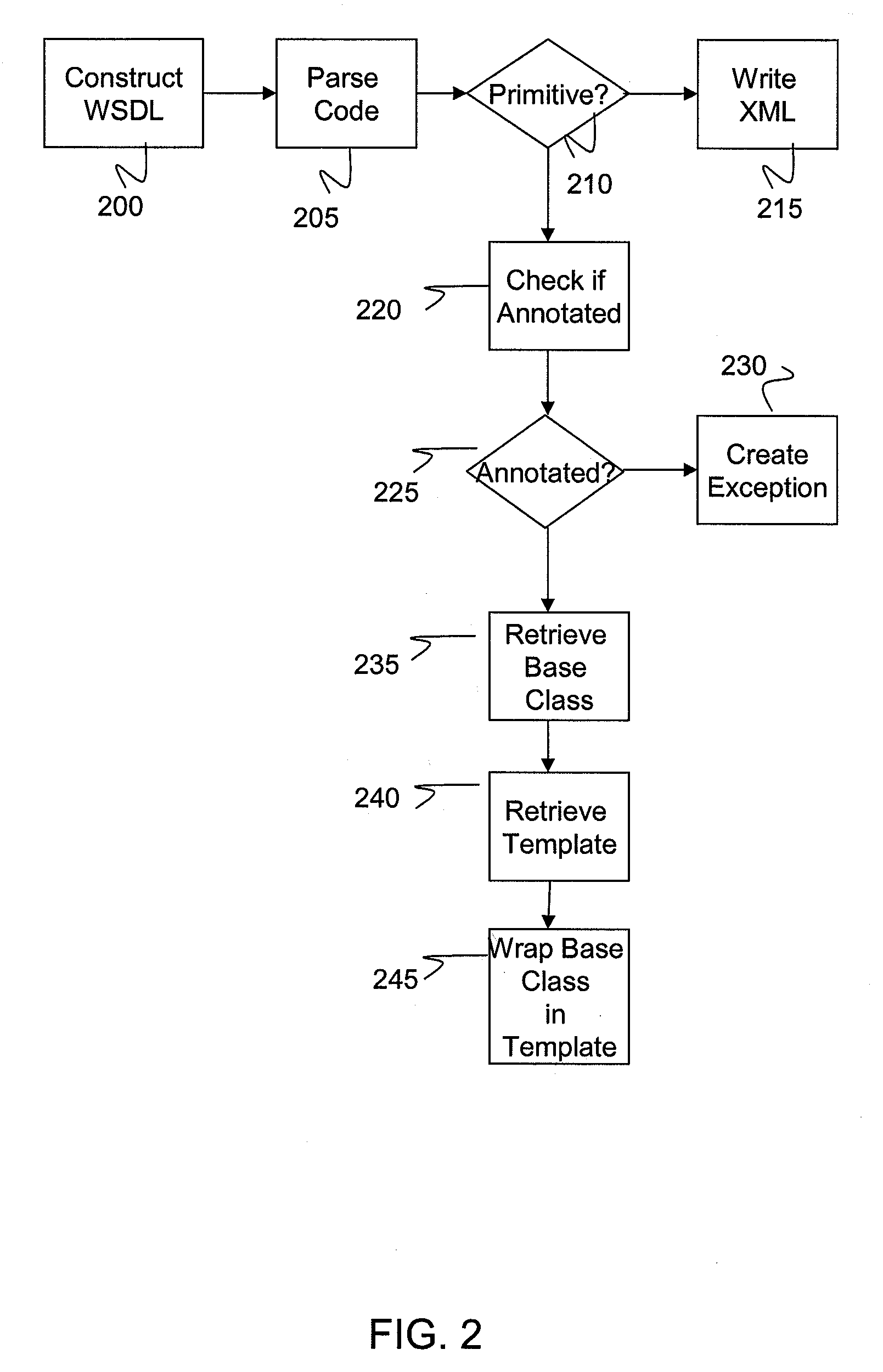
System and method of reconstructing complex custom objects
A system and method is provided for reconstructing one or more collections of objects across platforms. More particularly, Java Annotations are used to assist a Web Services Description Language (WSDL) wizard in reconstructing a collection of objects. In implementation, the system and method parses the object types such that a wizard can recreate or reconstruct the collection of objects for use by a receiving service. The method comprises reconstructing a collection using one or more annotations that document a base object of the collection.
Owner:KYNDRYL INC
Methods, systems and apparatus for clear texturing
Disclosed are a method and system of rendering clear texturing on a media substrate. According to one exemplary method, one or more parameters are provided by a user, via a UI (User Interface), to control the clear texturing process, wherein the parameters are associated with, but are not limited to, media sheet area coverage, object type the clear texturing process is to be performed on and maximum / minimum percentage of clear material to be used for rendering the clear texturing.
Owner:XEROX CORP
Extensible universal code generation system and method
PendingCN111859861AGuaranteed correctnessUniqueness guaranteedNatural language data processingCode generationInformatization
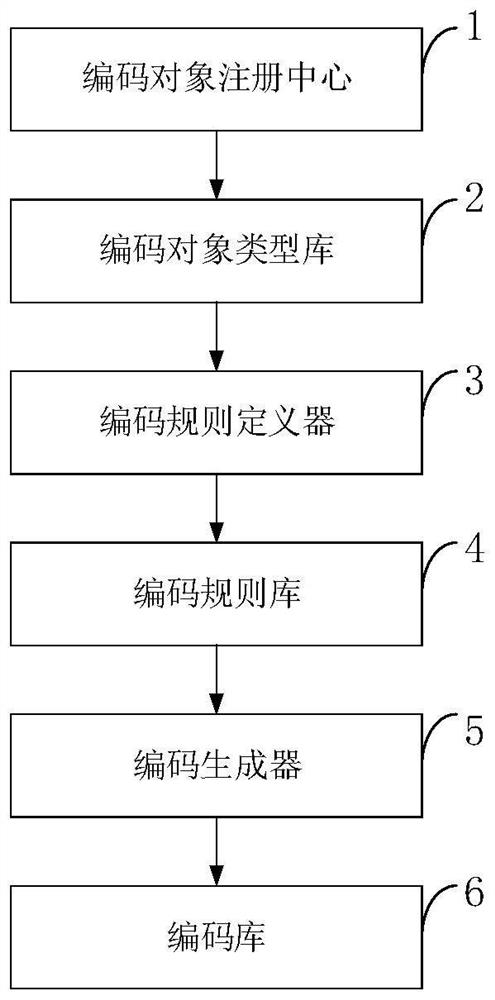
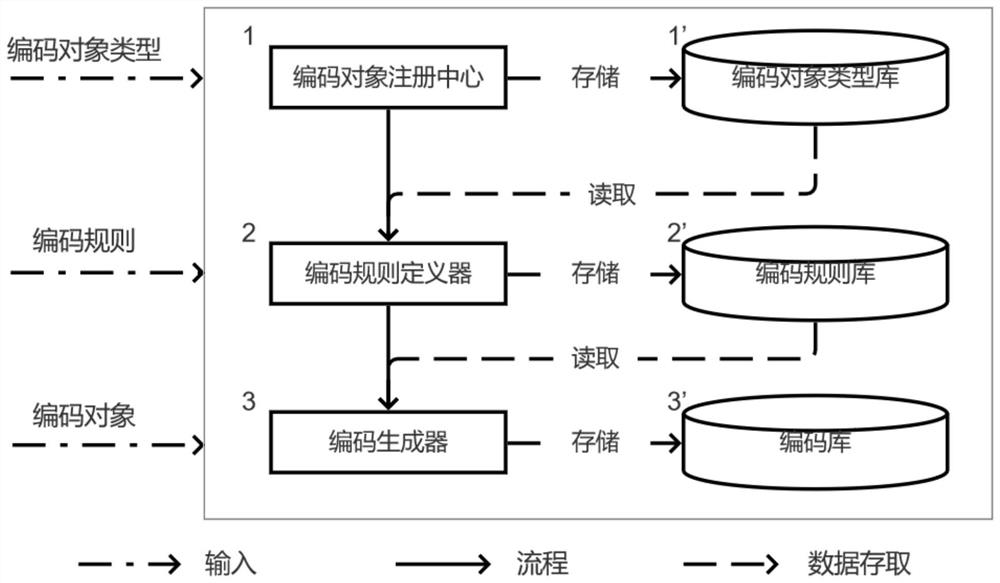
The invention belongs to the technical field of computer science informatization, and discloses an extensible universal code generation system and method, and the method comprises the steps that a code object registration center manages all object type information needing to be coded; the coding rule definition device defines a coding rule; a code generator obtains a corresponding attribute valuefrom an object to be coded according to the definition of a coding rule, obtains a new code value through attribute calculation, code conversion and fragment combination, and distributes the new codevalue to a code applicant, wherein the coding object type library stores all registered object types; the encoding rule base stores all encoding rule definitions; the code library stores the code andgenerates an object attribute value of the code. According to the invention, a new coding object type can be dynamically registered according to business requirements, a coding generation rule is customized, a new code is generated, the management of the coding object type, the coding rule and the code is provided, and the correctness, uniqueness and consistency of the code are ensured.
Owner:HUAZHONG UNIV OF SCI & TECH +1
Method for manipulating objects in a SOA registry
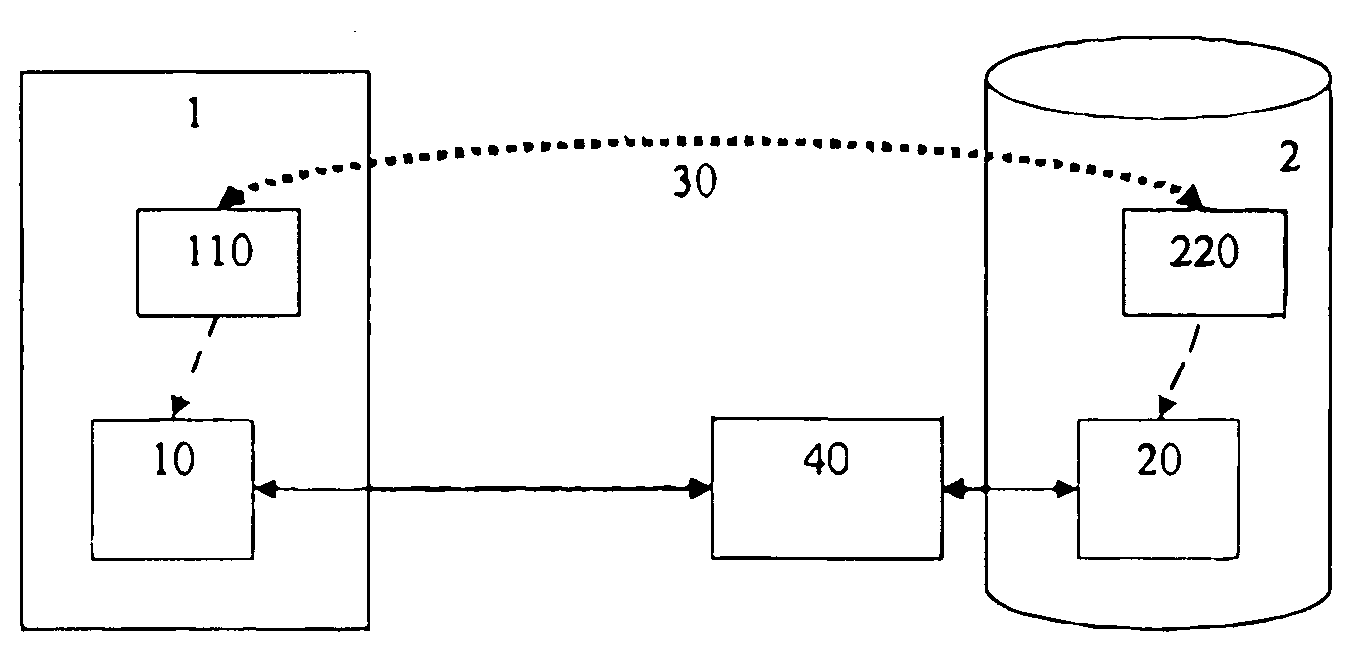
ActiveUS20100094905A1Flexible adaptationDigital data processing detailsSpecial data processing applicationsApplication objectDatabase
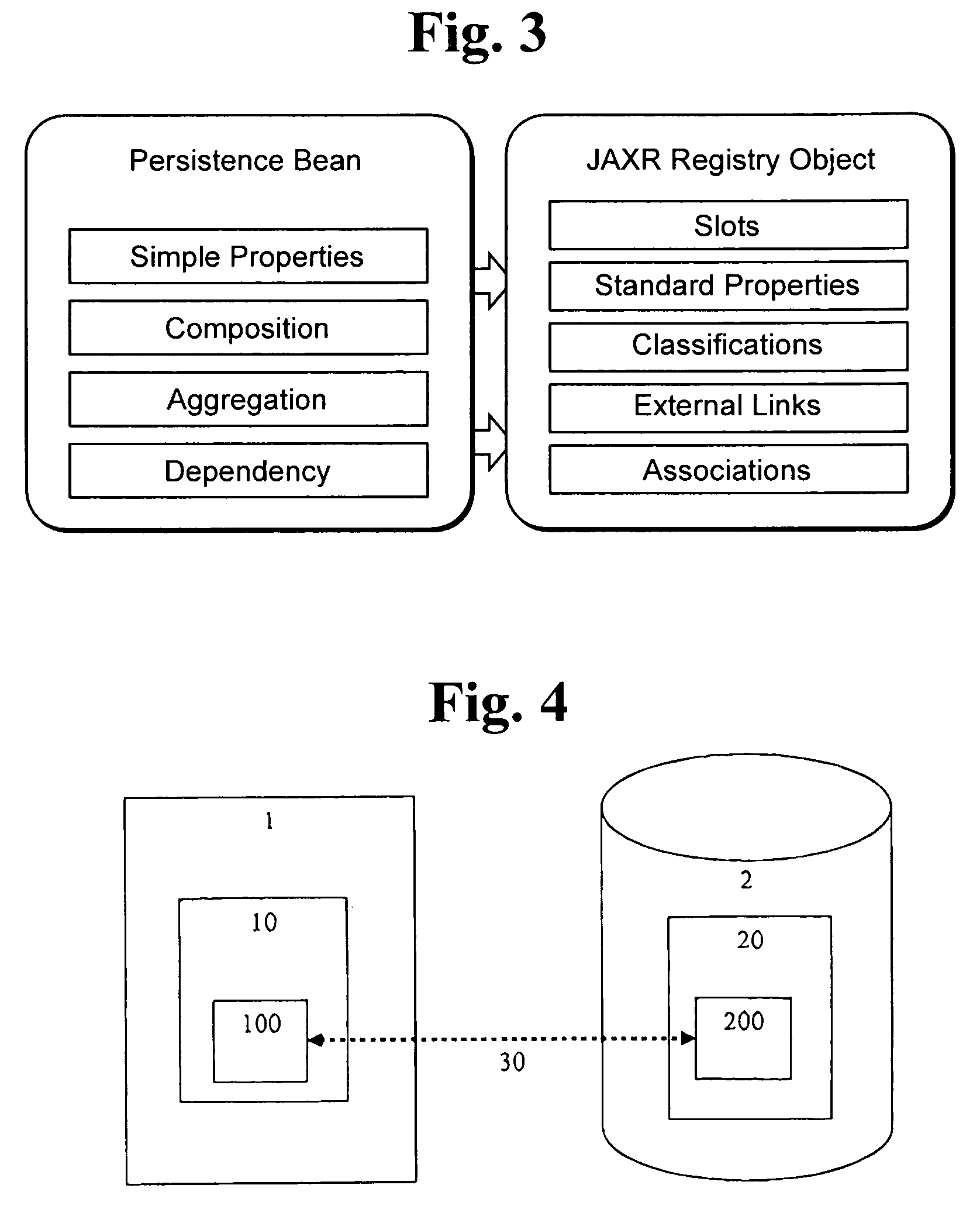
The present invention concerns a method for manipulating at least one registry object (20) of a SOA registry (2) by an application (1), the at least one registry object (20) being accessible through a Java API for XML registries (JAXR) (40), the method comprising the following steps:a defining a mapping (30) between at least one registry object type (220) and at least one application object type (110), wherein the mapping (30) is described by one or more Java annotations,b. instantiating the at least one application object type (110) to provide the application (1) with at least one application object (10) corresponding to the at least one registry object (20); andc. manipulating the at least one application object (10) by the application (1), the manipulation causing a related manipulation of the corresponding at least one registry object (20) through the JAXR (40).
Owner:SOFTWARE AG
Systems and methods for modeling processing procedures
ActiveUS20070078867A1High potential for savingSave storage spaceDigital data processing detailsSoftware designAlgorithmFunctional Relationship
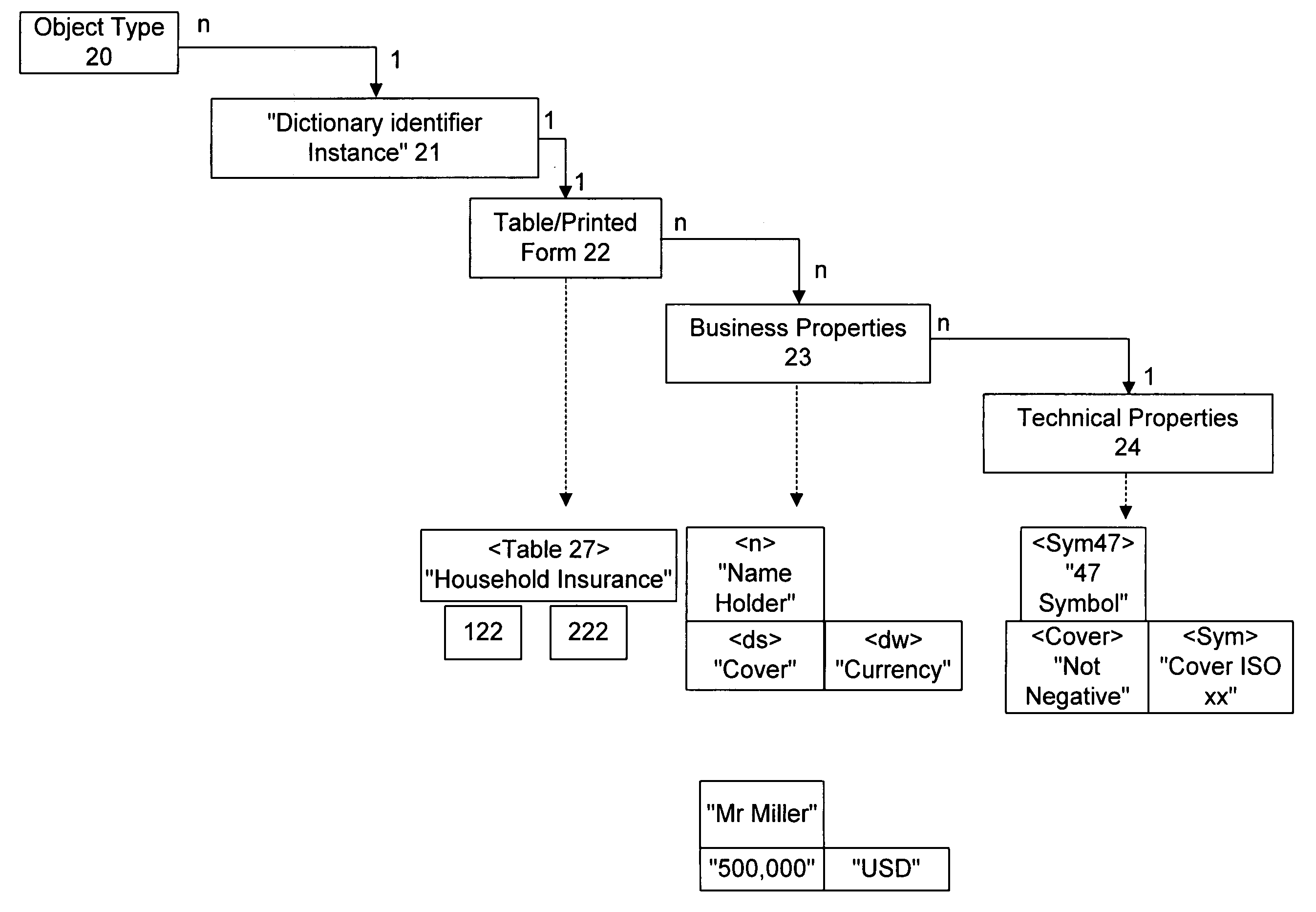
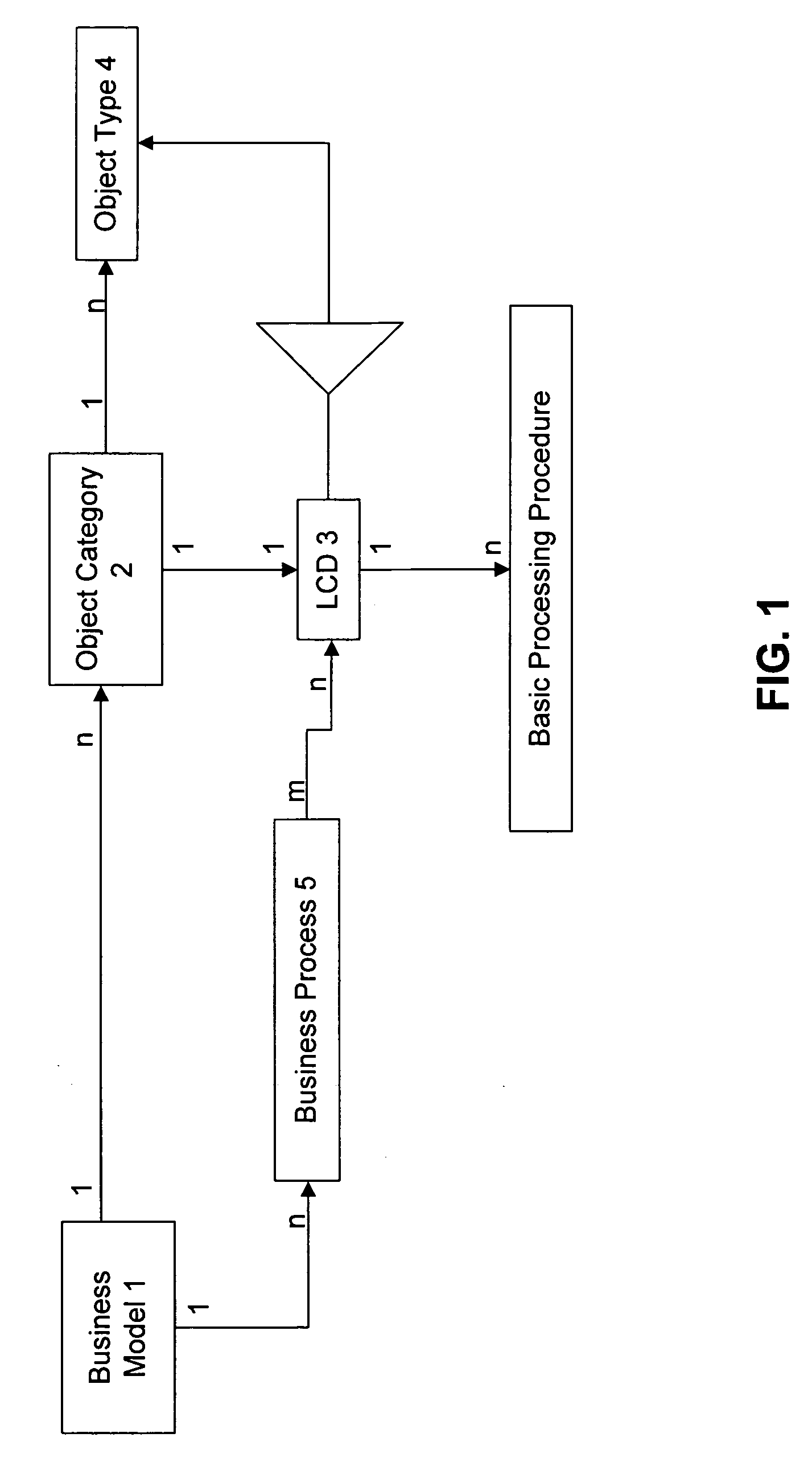
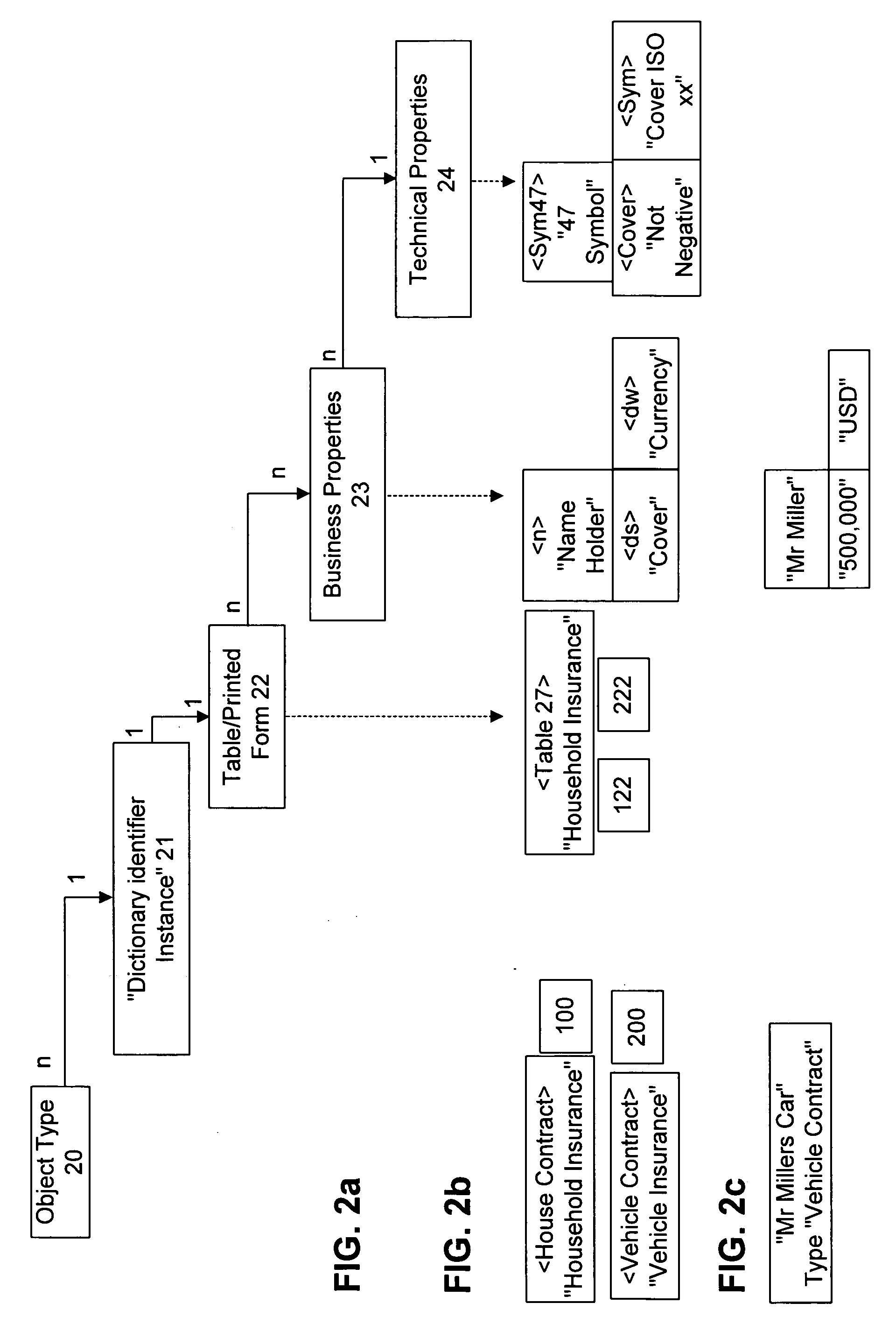
Systems and methods are provided for implementation of a processing procedure on an object allocated to an object category as an instance of an object type. In one embodiment, a computerized method is provided. The method may include breaking the object into separately processable, hierarchically classifiable sub-objects as instances of corresponding sub-object types, processing at least a part of the sub-objects with respective predetermined partial processing procedures specific to each sub-object type. The method may further include processing results obtained from processing the sub-objects and combining the results via a functional relationship in a processing procedure of higher rank than the partial processing procedures. An object-specific processing result may then be derived for the processing procedure.
Owner:SAP AG
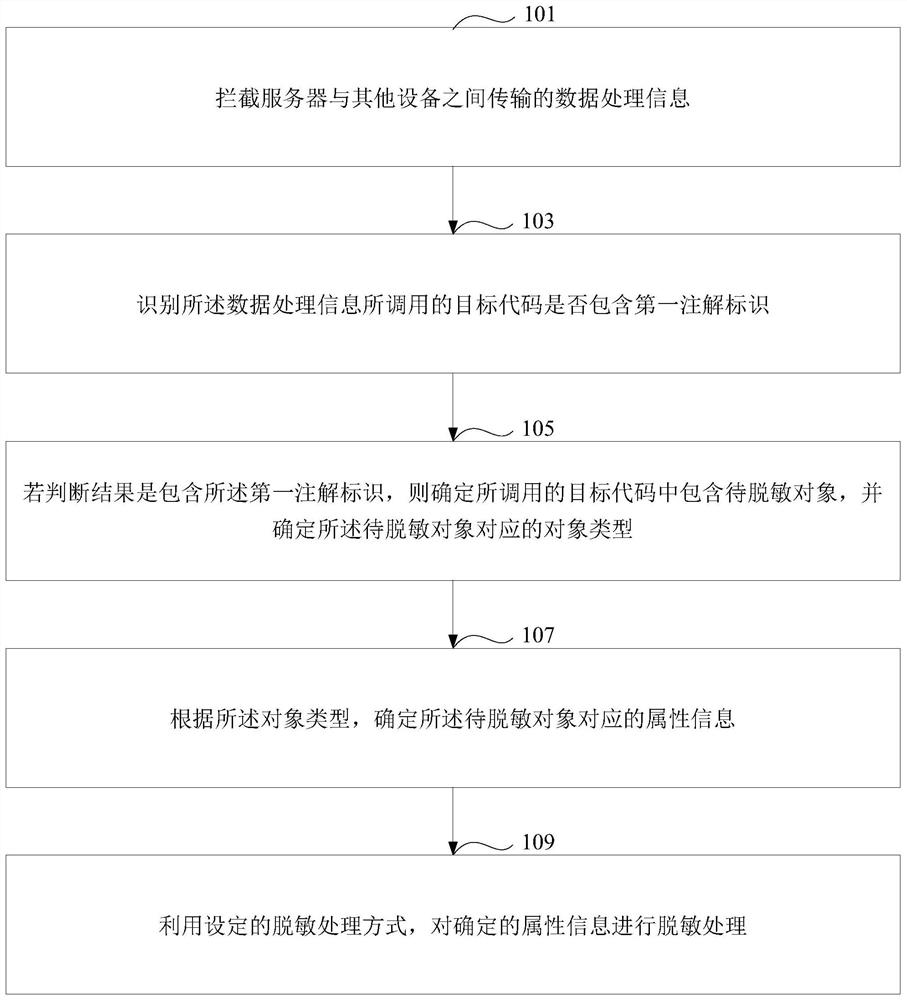
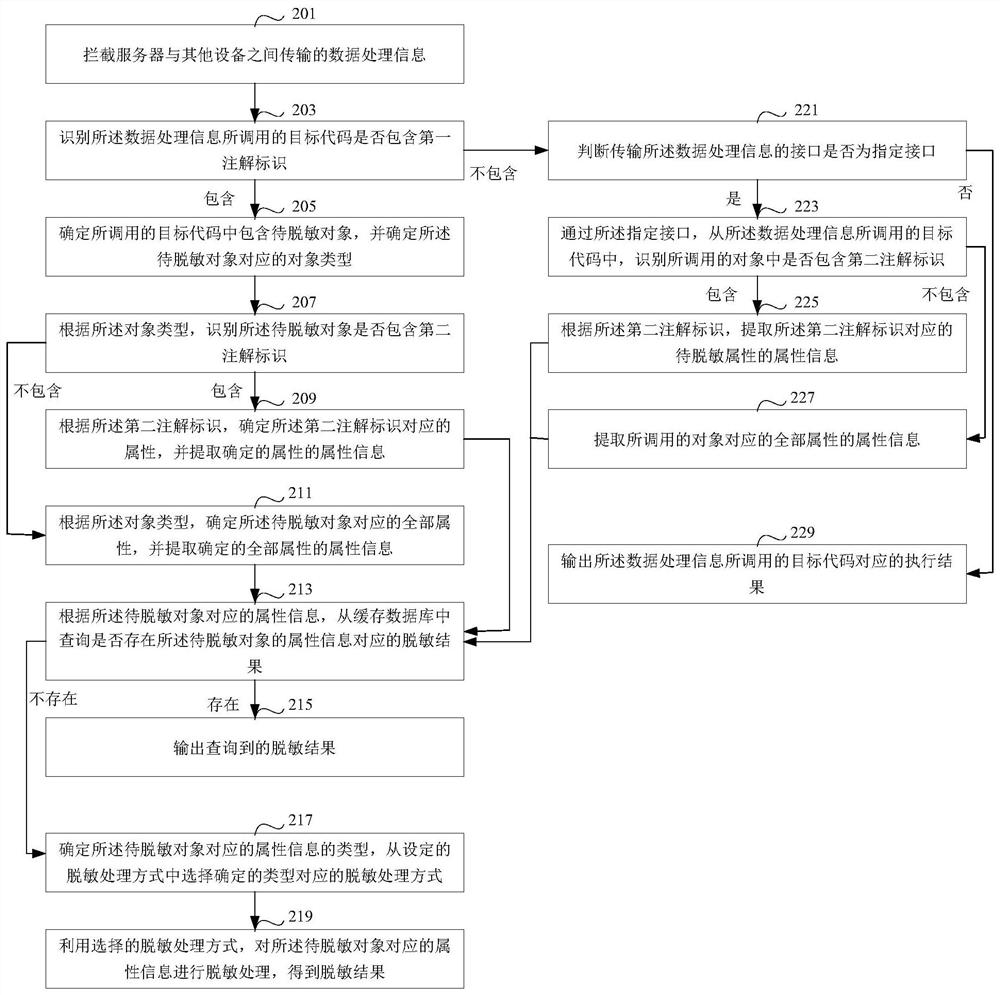
Desensitization processing method and device, medium and electronic device
PendingCN112307509ATimely desensitization protectionSave resourcesDigital data protectionData informationEngineering
The invention discloses a desensitization processing method and device, a medium and an electronic device, and the method comprises the steps: intercepting data processing information transmitted between a server and other devices, and recognizing whether a target code called by the data processing information comprises a first annotation identification or not; if the judgment result is that the first annotation identifier is contained, determining that the called target code contains the to-be-desensitized object, and determining an object type corresponding to the to-be-desensitized object;determining attribute information corresponding to the to-be-desensitized object according to the object type; and performing desensitization processing on the determined attribute information by using a set desensitization processing mode. Under the condition of not changing the source program code, whether the to-be-desensitized object is contained or not is recognized by intercepting the data information, and if the to-be-desensitized object is contained, desensitization processing is started, so the quick execution of the target code of data processing can be ensured, equipment resources consumed by execution are saved, and desensitization protection can be performed on sensitive data in time.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
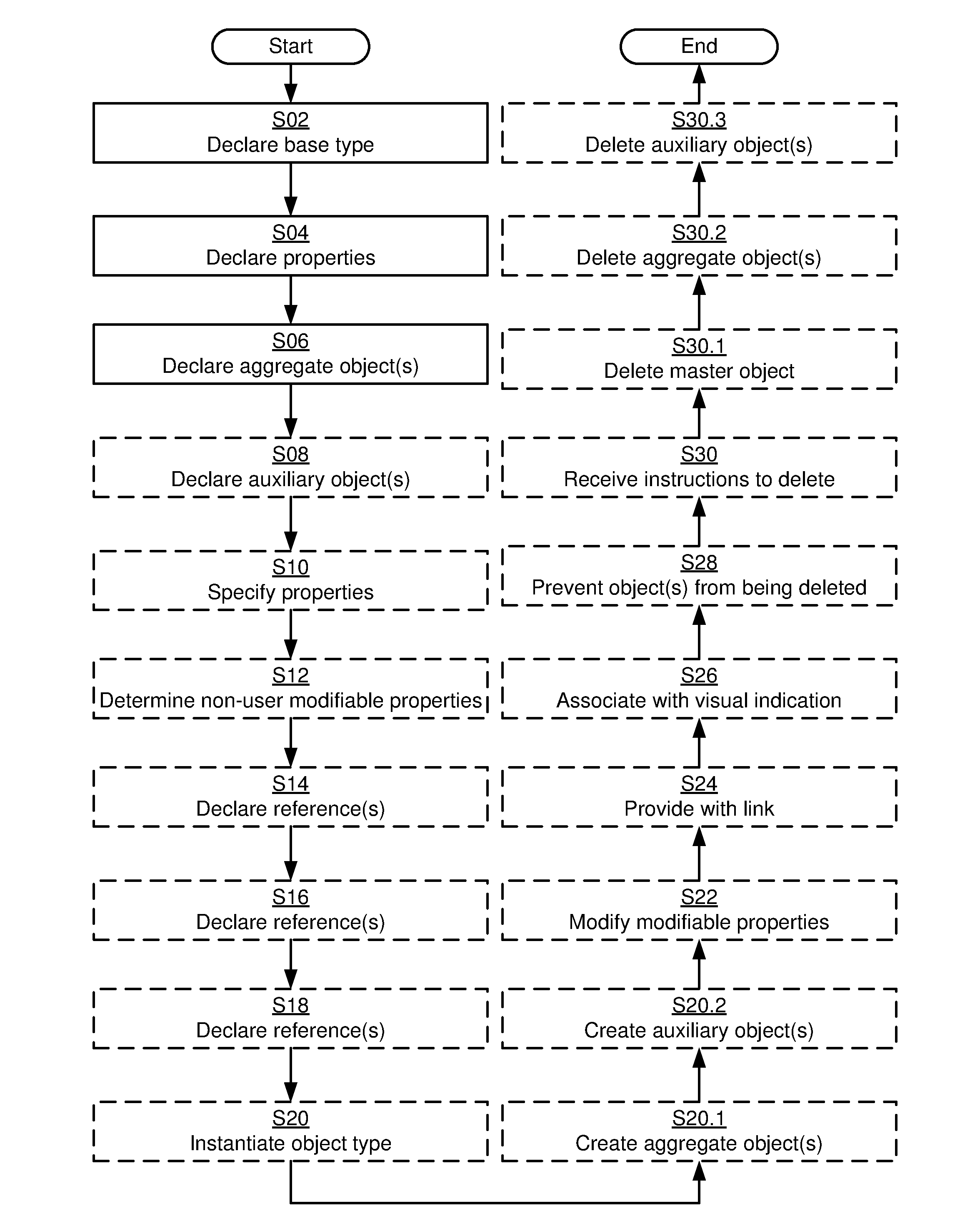
Definition of objects in object-oriented programming environments
InactiveUS20130275941A1Easy to useSoftware designSpecific program execution arrangementsObject structureObject-oriented programming
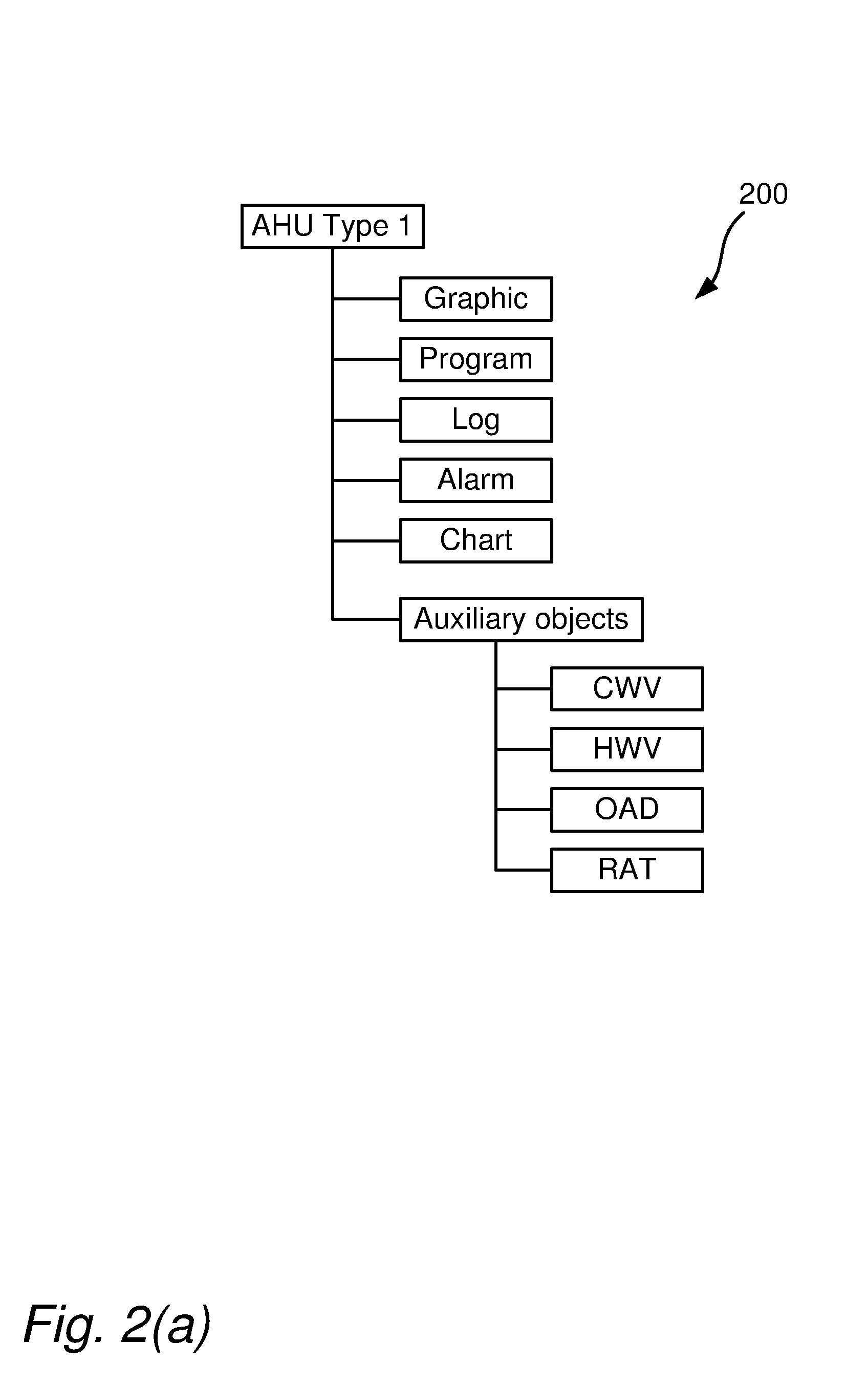
In an object-oriented programming environment having a hierarchical object structure an object type is defined by declaring different types of objects and properties associated therewith. A base type is declared. Properties for the base type are declared. A set of aggregated objects comprising individual objects of different types is declared. The set of aggregated objects is to be instantiated in a master object created from the object type. A set of auxiliary objects comprising individual objects of different types and associated with the object type is declared. The individual objects of the set of auxiliary objects are to be instantiated in respective locations in the hierarchical object structure.
Owner:SCHNEIDER ELECTRIC BUILDINGS LLC
Robotic process control system
ActiveUS10691113B1Easy to controlFacilitating object interactivity and communicationProgramme-controlled manipulatorComputer controlSoftware engineeringEvent object
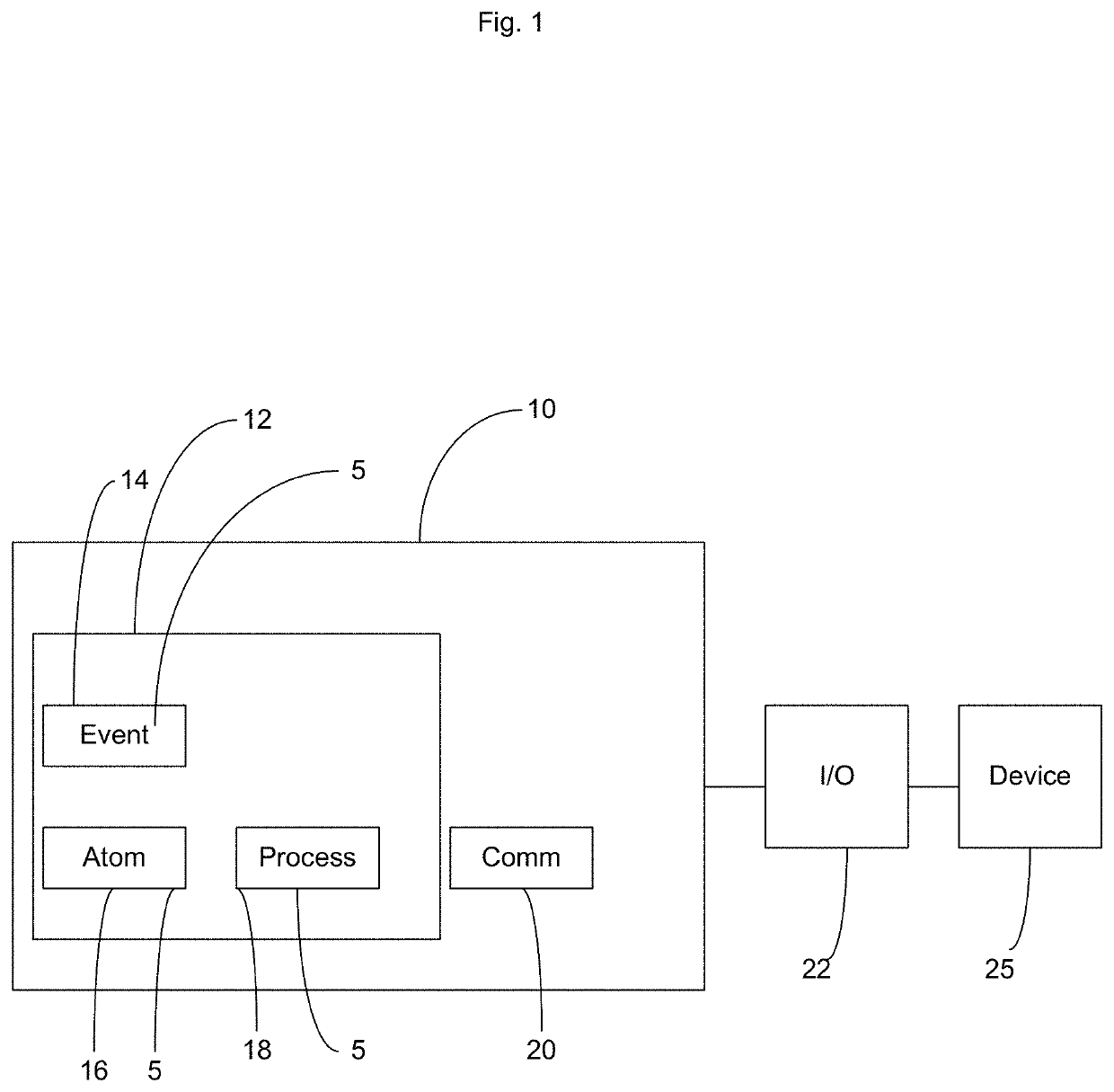
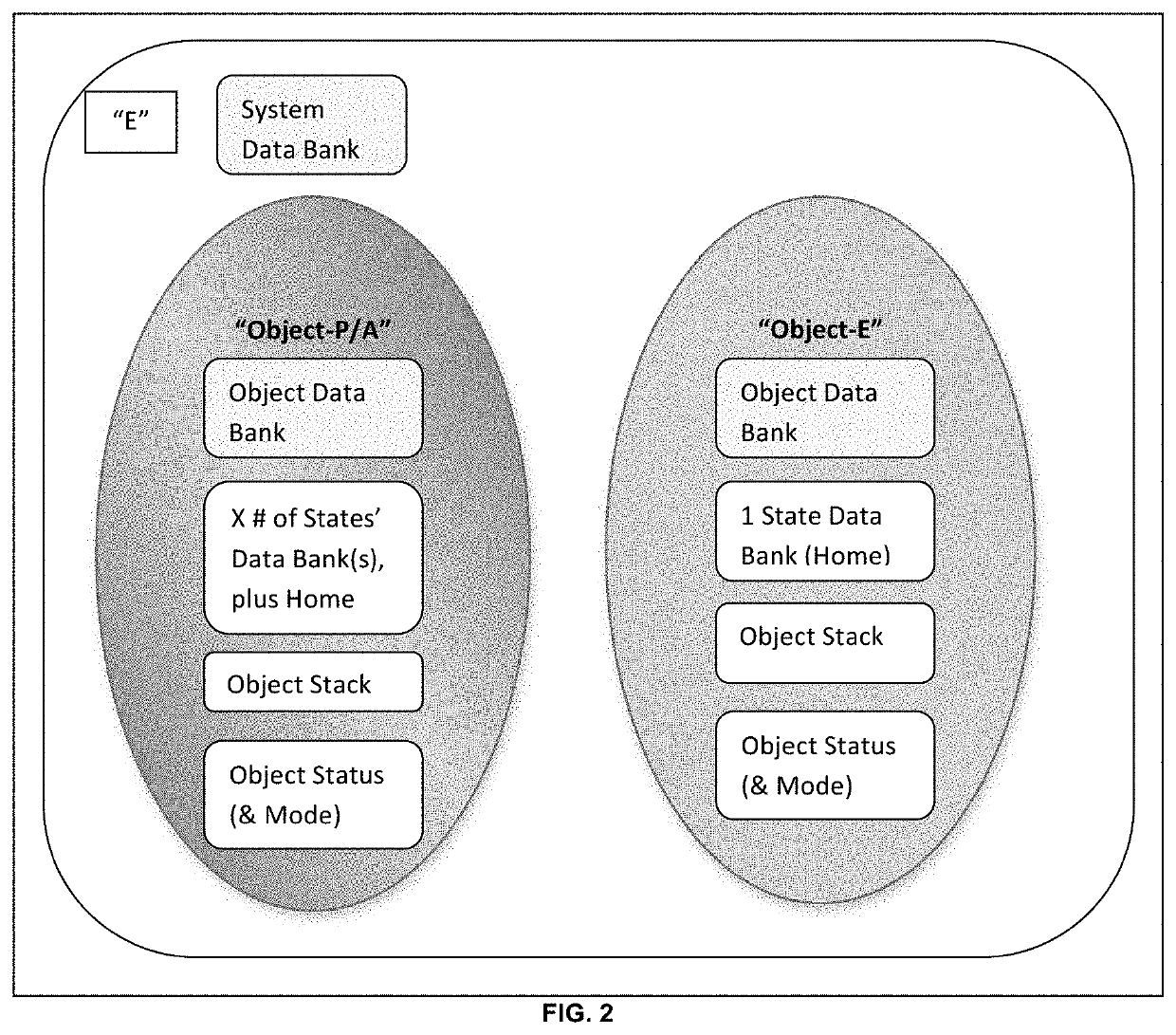
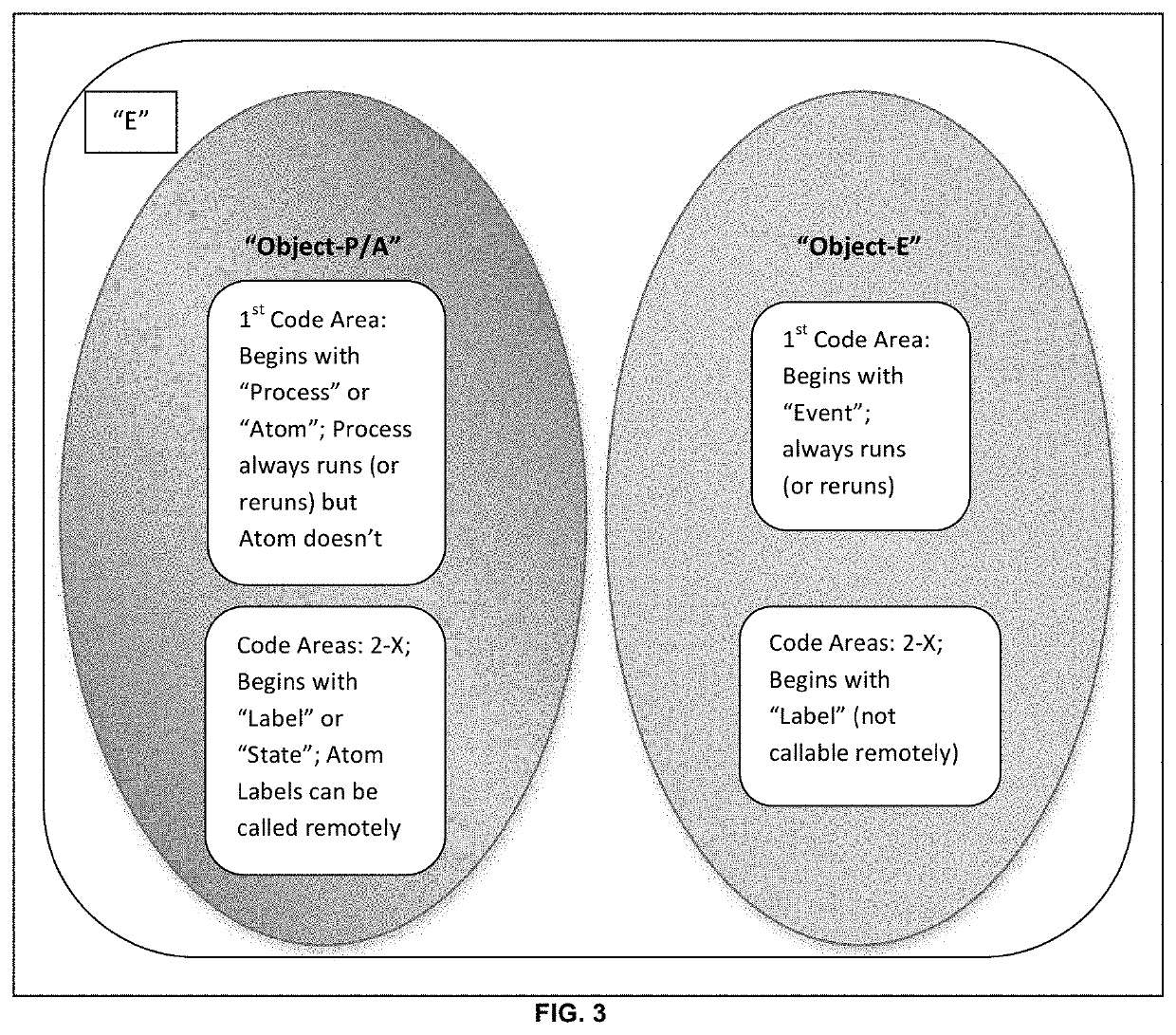
A robotic process control system that is operable to provide automation of at least one electromechanical device wherein the programming language of the present invention utilizes commands, rules and argument within a virtual environment to provide control of an electromechanical device. The present invention includes an object oriented methodology facilitated by the software thereof that defines three object types being an atom object type, a process object type and an event object type. The object types reside in a virtual environment hosted on a computing device that is operably coupled to the electromechanical device wherein the object types are representative of the electromechanical device or a portion thereof. The present invention utilizes a programming language that utilizes English language statements and further creates digitope data for all of the objects within the present invention. The methodology of the present invention examines spatial relations between all of the objects.
Owner:BERGMAN ANTHONY
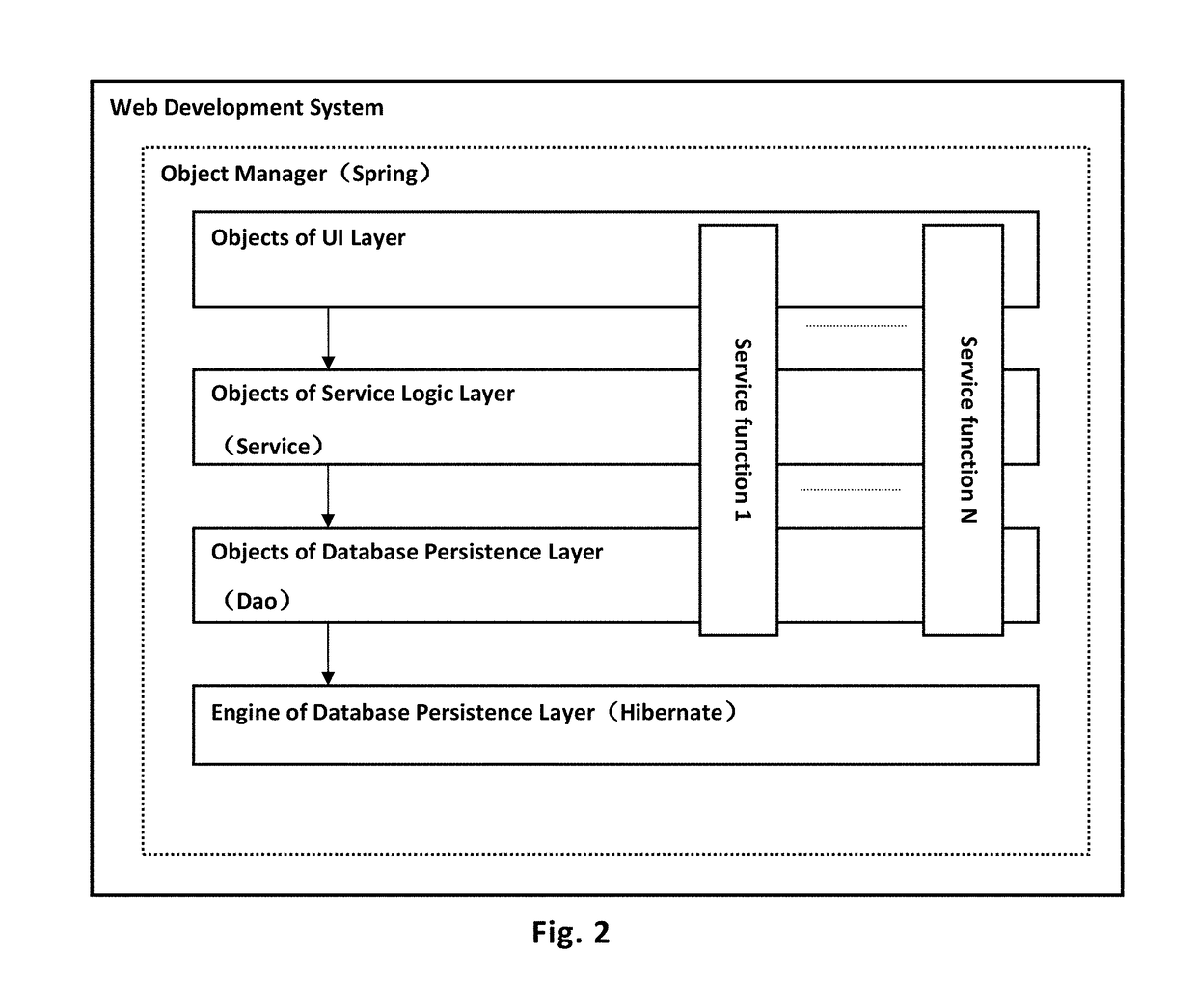
Web development system
ActiveUS9904522B2Improve securityQuick buildProgramming languages/paradigmsProgram loading/initiatingWeb applicationObject type
The present invention provides a web development system. In a running state of a web application being developed, the development system generates or modifies a script code used to perform a predetermined function. The development system includes a script parser that parses the generated script code or the modified script code to correspondingly generate an object type which performs a new function, or to modify the object type which performs an existing function. The development system also includes an object manager that generates a new function object or modifies the existing function object according to the generated object type and organizes the invoking relationships between the new or modified function object and other objects, so as to generate or modify the predetermined function when the web application is operating.
Owner:ZHANG JIE +1
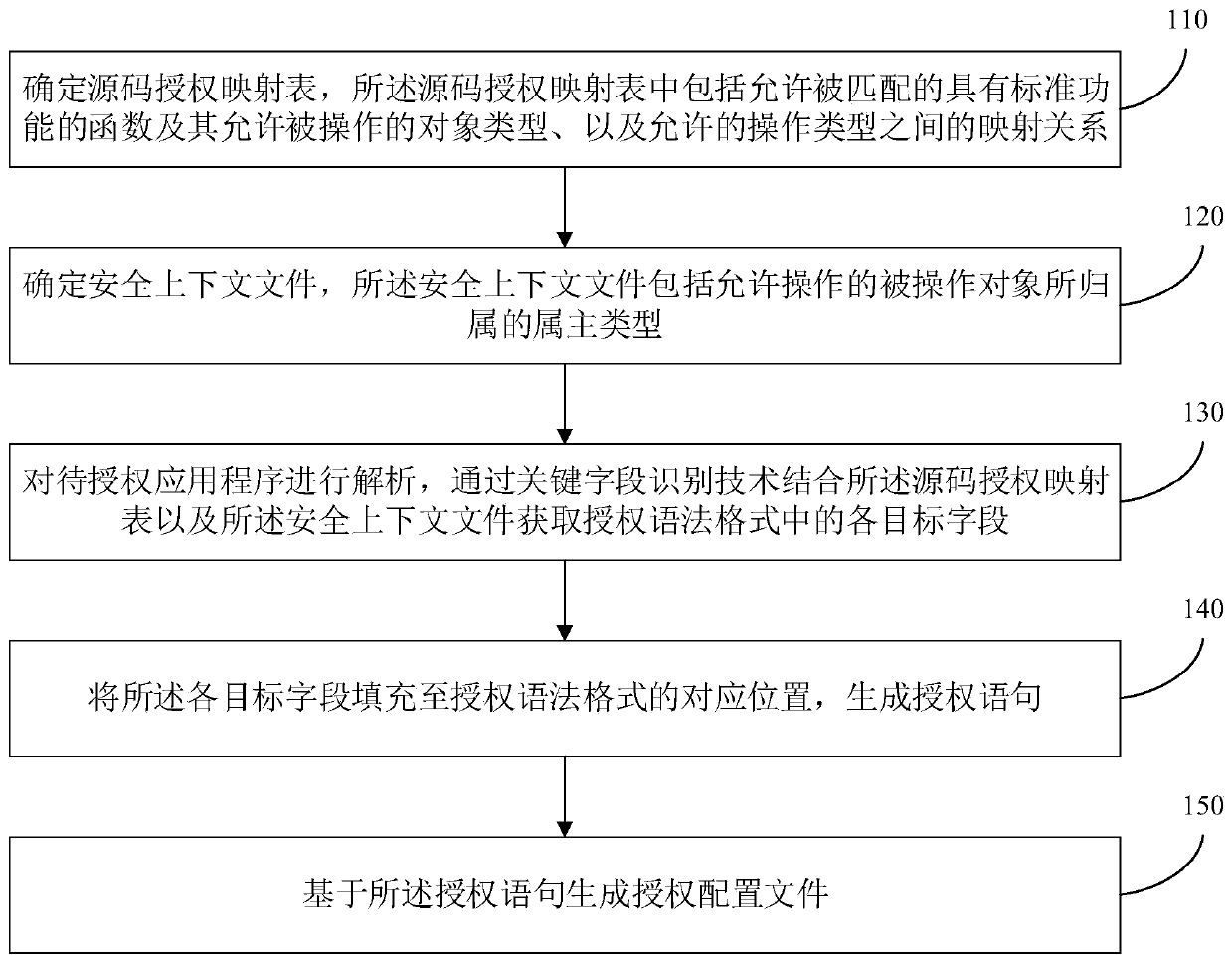
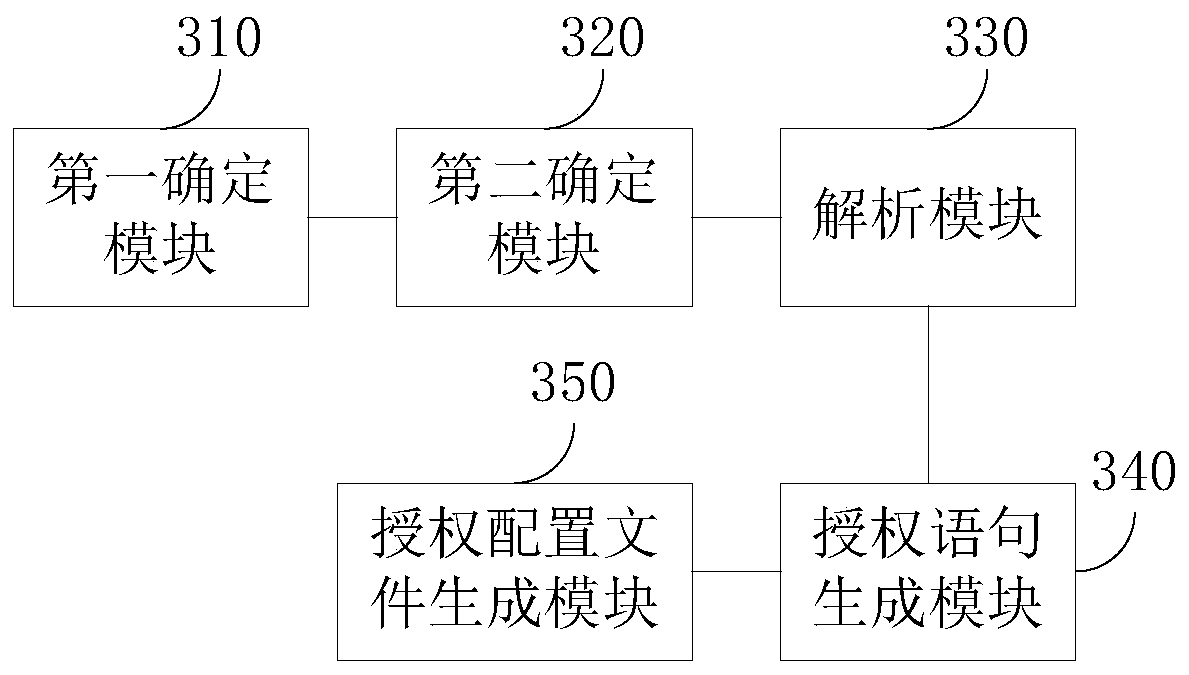
Authorization configuration file generation method and device, equipment and storage medium
ActiveCN110727476ARealize automatic generationImprove authorization efficiencyProgram loading/initiatingProgram/content distribution protectionObject typeApplication procedure
The embodiment of the invention discloses an authorization configuration file generation method and device, equipment and a storage medium, and the method comprises the steps: determining a source code authorization mapping table which comprises a function which is allowed to be matched and has a standard function, an object type which is allowed to be operated by the function, and a mapping relation between allowed operation types; determining a security context file, wherein the security context file comprises an owner type to which the operated object allowed to be operated belongs; analyzing a to-be-authorized application program, and combining the source code authorization mapping table and the security context file through a key field identification technology to obtain each target field in an authorization syntax format; filling each target field into a corresponding position of the authorization grammar format to generate an authorization statement; and generating an authorization configuration file based on the authorization statement. By adopting the technical scheme, the purposes of automatically generating the SELinux authorization configuration file, improving the authorization efficiency and saving human resources are achieved.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com