Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
359 results about "Security context" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
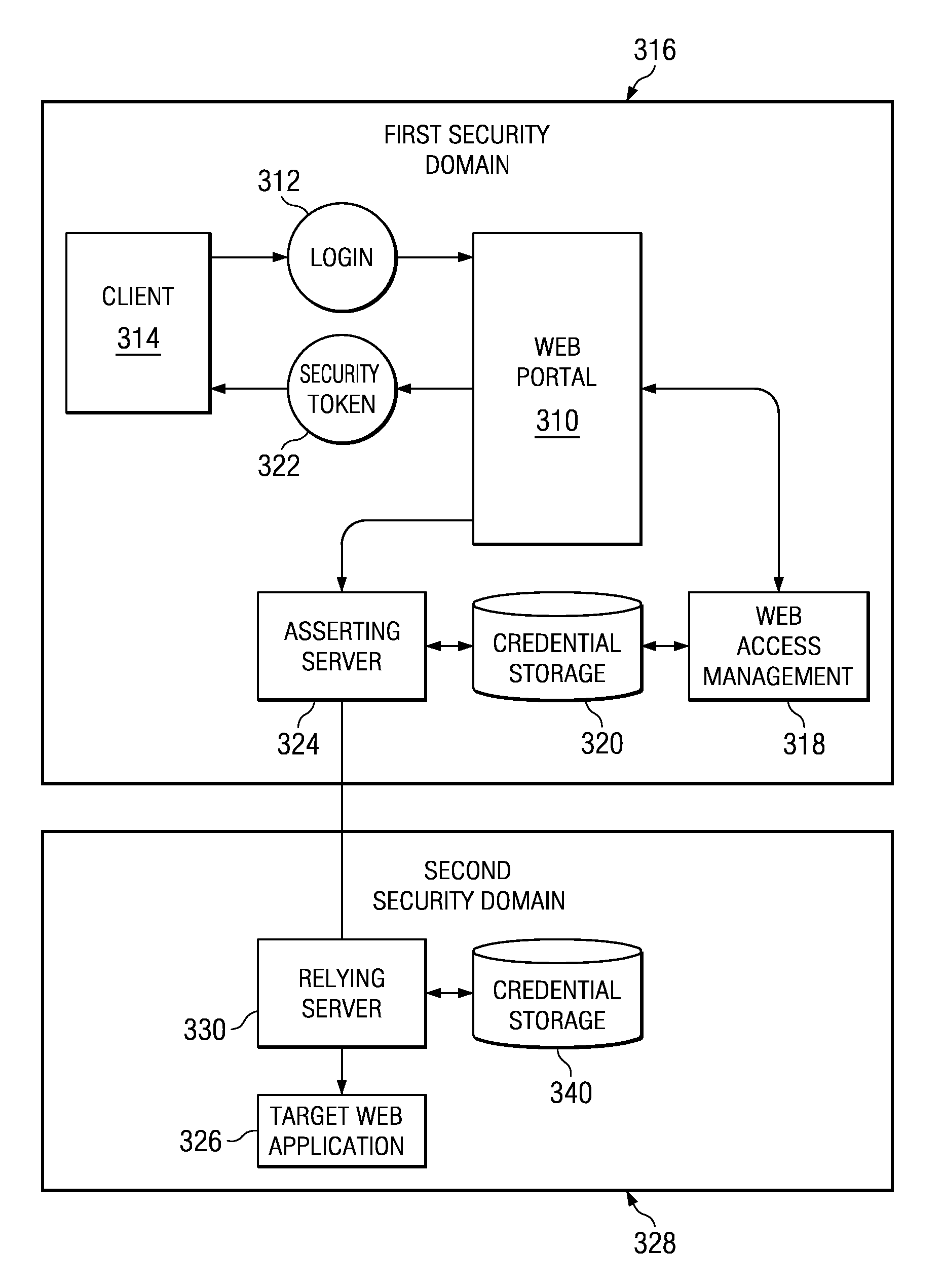
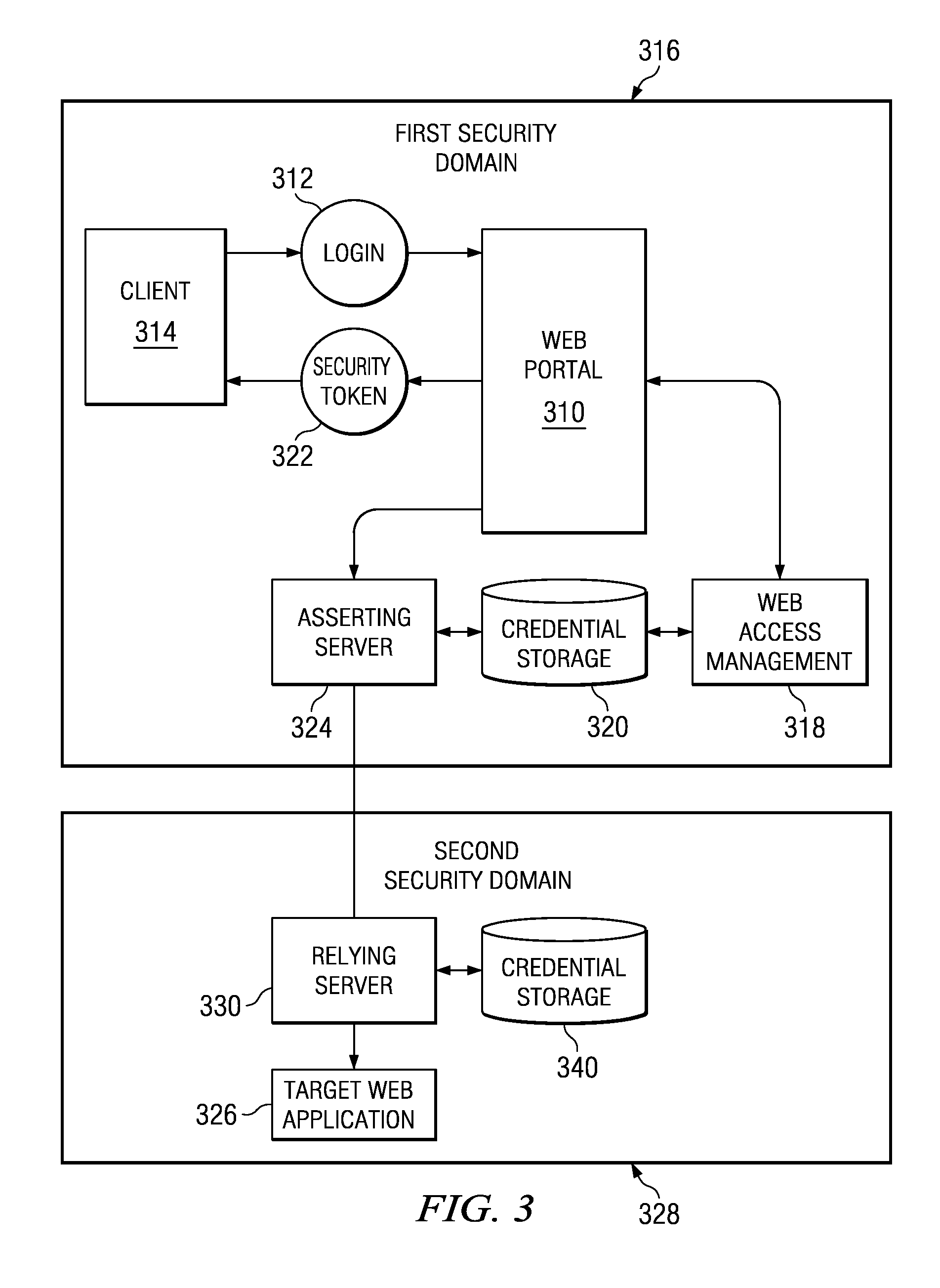
Security contexts are a message security feature and are configured by way of message security bindings. On the client side, the security context is tied to a particular channel. It is configured using the WS_SECURITY_CONTEXT_MESSAGE_SECURITY_BINDING. Behavior and lifetime of the context are determined by the channel.
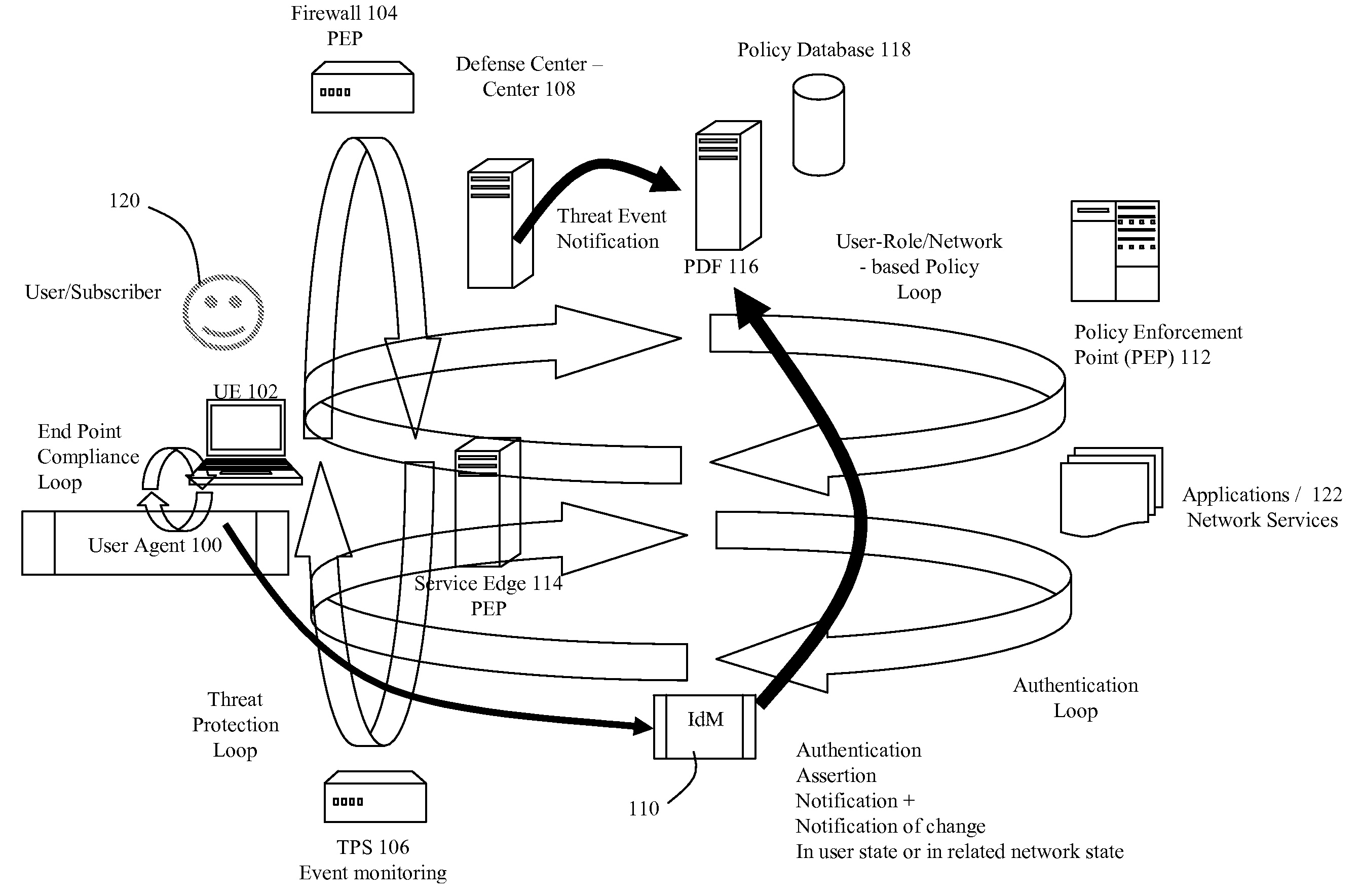
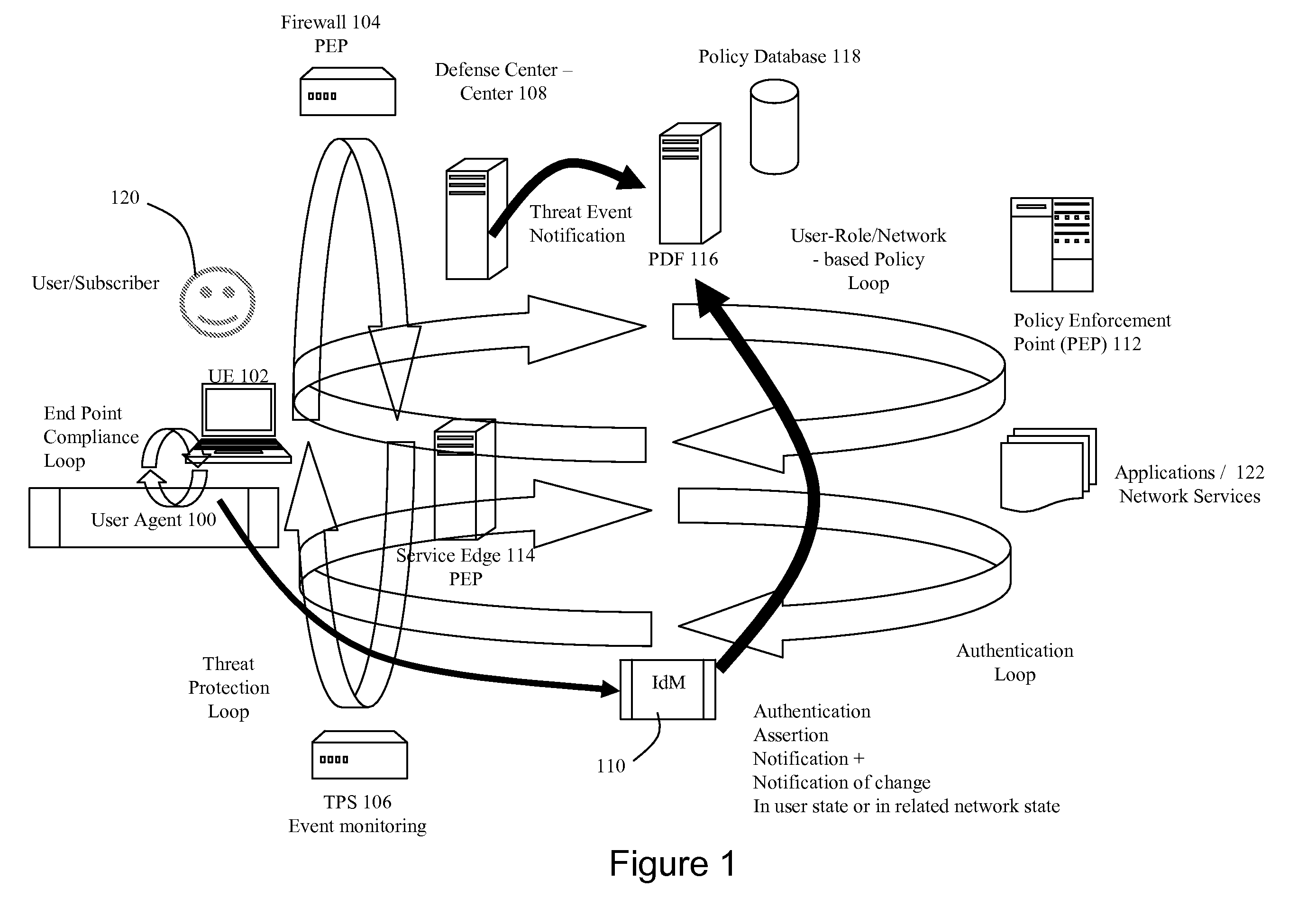
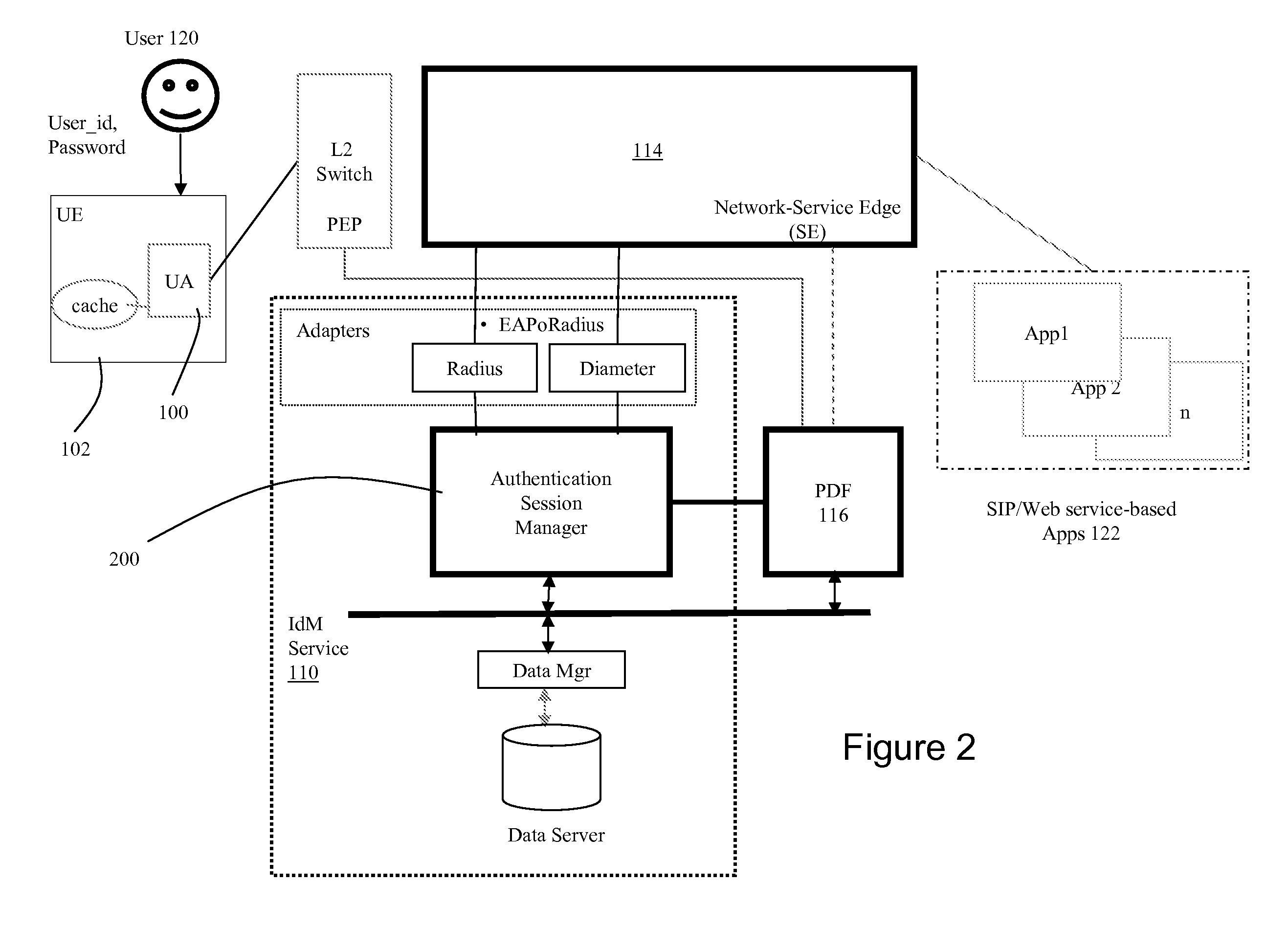
Dynamic Network Identity and Policy management
InactiveUS20070150934A1Network resource is limitedSpecial data processing applicationsSecurity arrangementTarget ResponsePassword
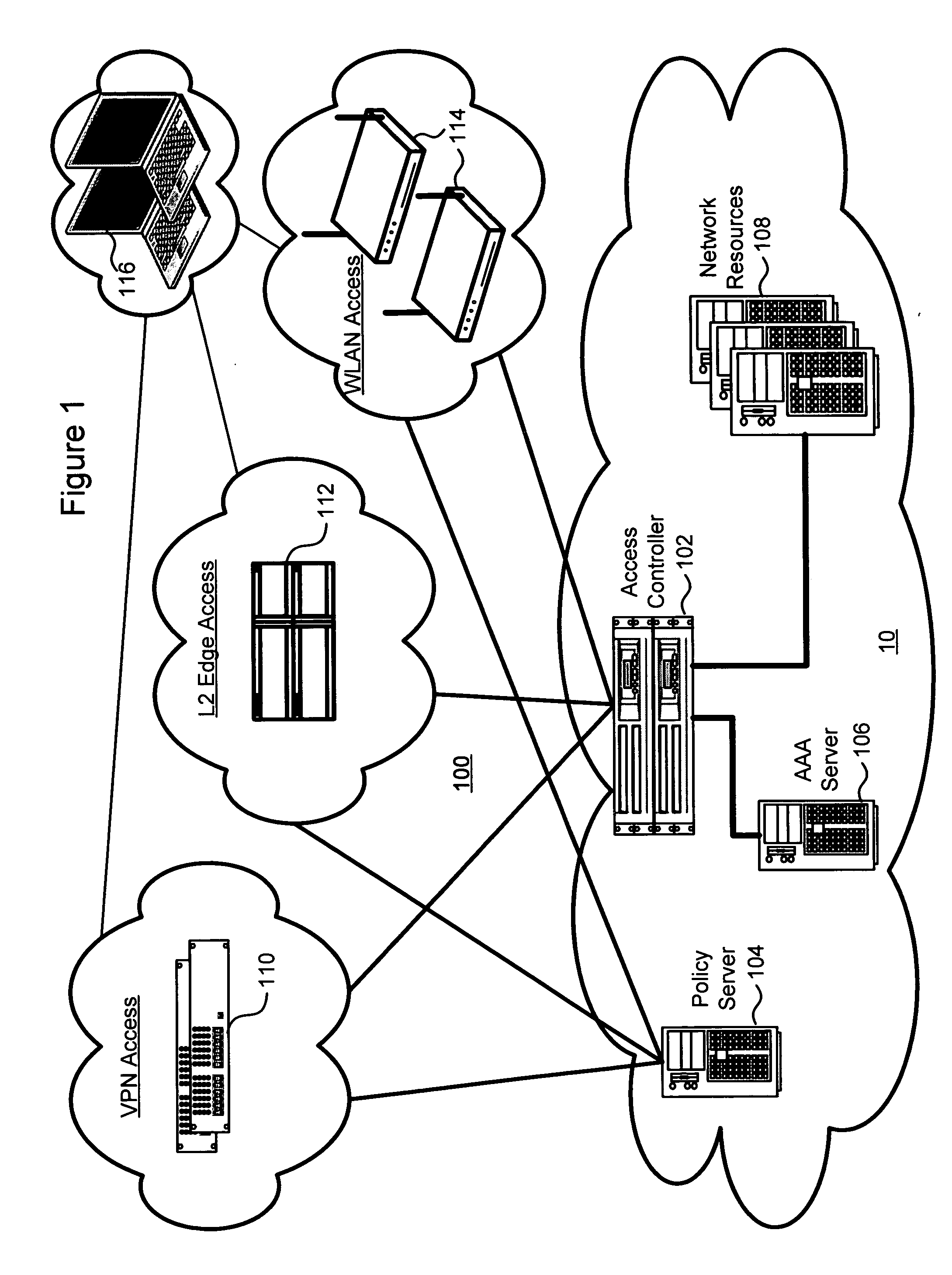
Network policies are managed based at least in-part on user / entity identity information with: a state monitor operable to monitor for state change events in user / entity state and related, network state or in traffic pattern and traffic flow state; an identity manager operable to obtain and validate user credentials; and a policy manager operable in response to a state change event detected by the state monitor (either the identity manager or a defense center) to select a policy based in-part on the user identity obtained by the identity manager or security context obtained by the defense center, and to prompt application of the selected policy. The policies are indicative of user / device authorization entitlements and restrictions to utilization of certain network resources, network services or applications. Dynamic policy selection and targeted responses can be used, for example, against a user who gains network access with stolen user ID and password, and subsequently attempts malicious behavior. In particular, the malicious behavior is detected and identified, and the malicious user can then be restricted from abusing network resources without adversely affecting other users, groups, network devices, and other network services.
Owner:NORTEL NETWORKS LTD
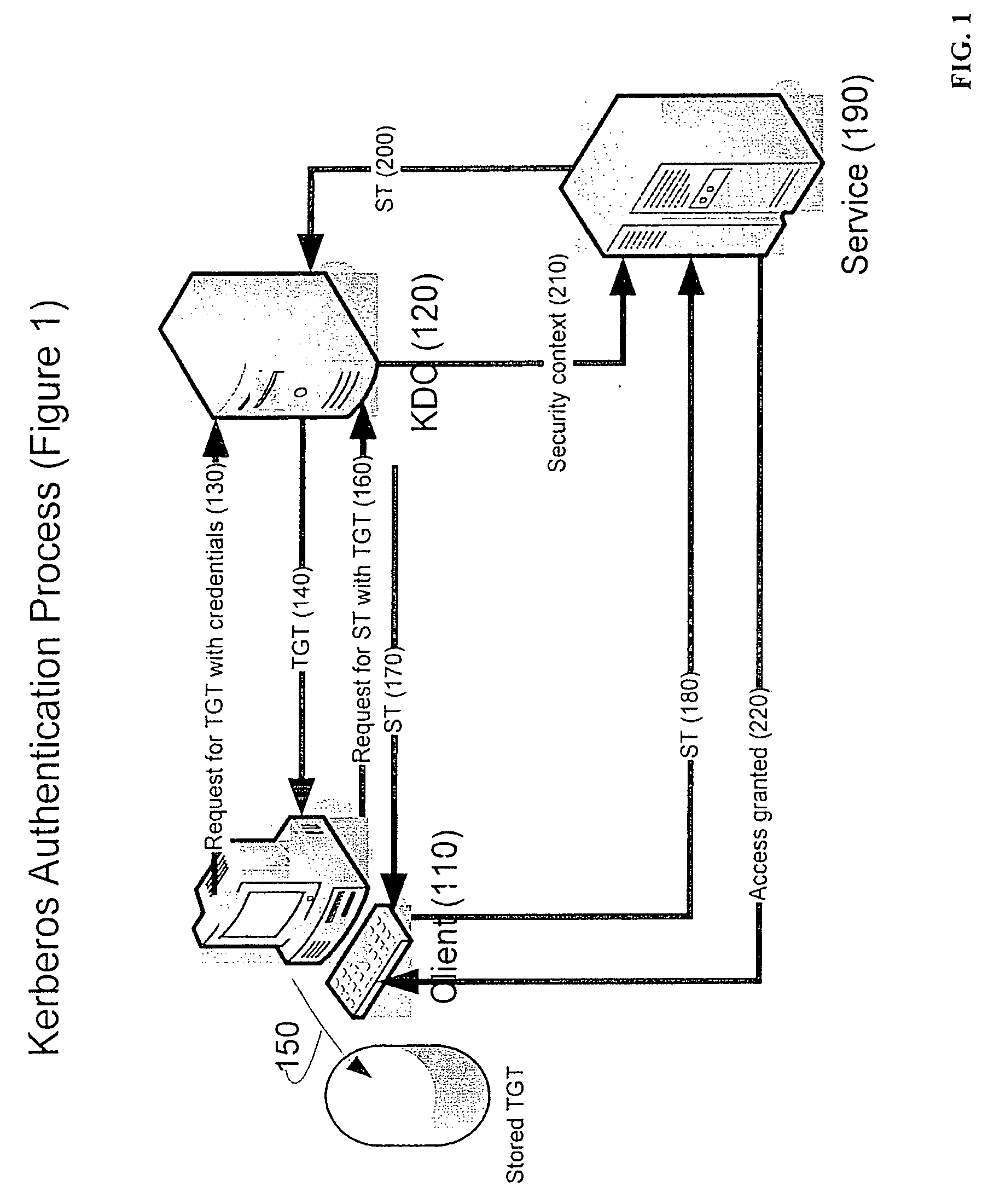
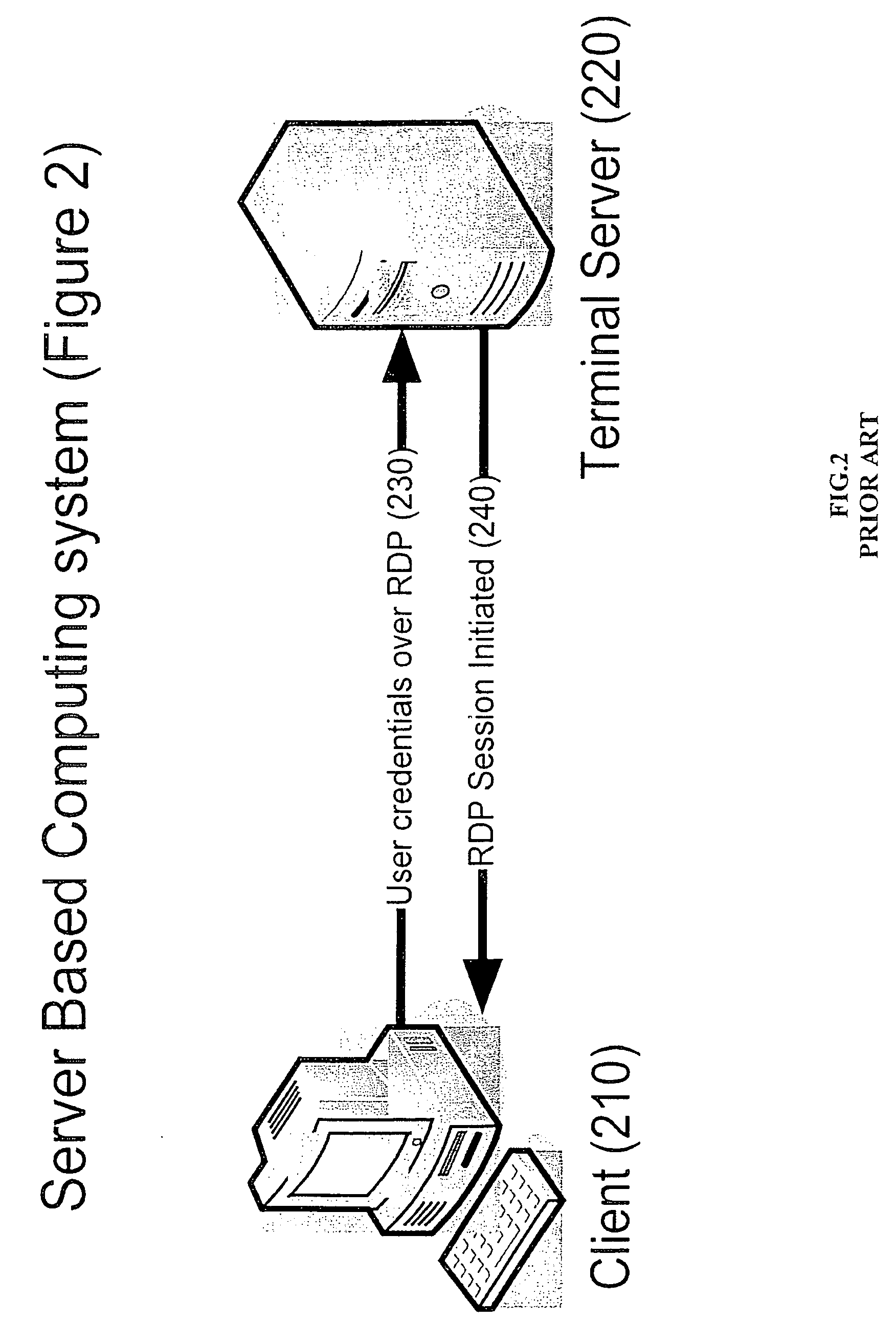
Single sign-on to remote server sessions using the credentials of the local client
InactiveUS20060230438A1Smooth connectionDigital data processing detailsMultiple digital computer combinationsTerminal serverClient server systems
A method for single sign-on in a client-server system including a server and a client and a remote presentation protocol based on ITU T.120, communicates between the client node and the server. The client obtains a ticket for a user operating the client. The ticket identifies the security context of the user on the client. Upon connecting the client to the server, the ticket is transferred from the client to the server. The server authenticates the ticket with a security authority and when authenticated the server receives from the security authority a security context for the ticket. When the client so requests, applications are launched using that security context. Preferably, the server is a Microsoft Terminal Server and the remote presentation protocol is Microsoft Remote Desktop Protocol (RDP). The ticket transfer preferably uses a channel within the remote presentation protocol, such as an RDP virtual channel.
Owner:ERICOM SOFTWARE
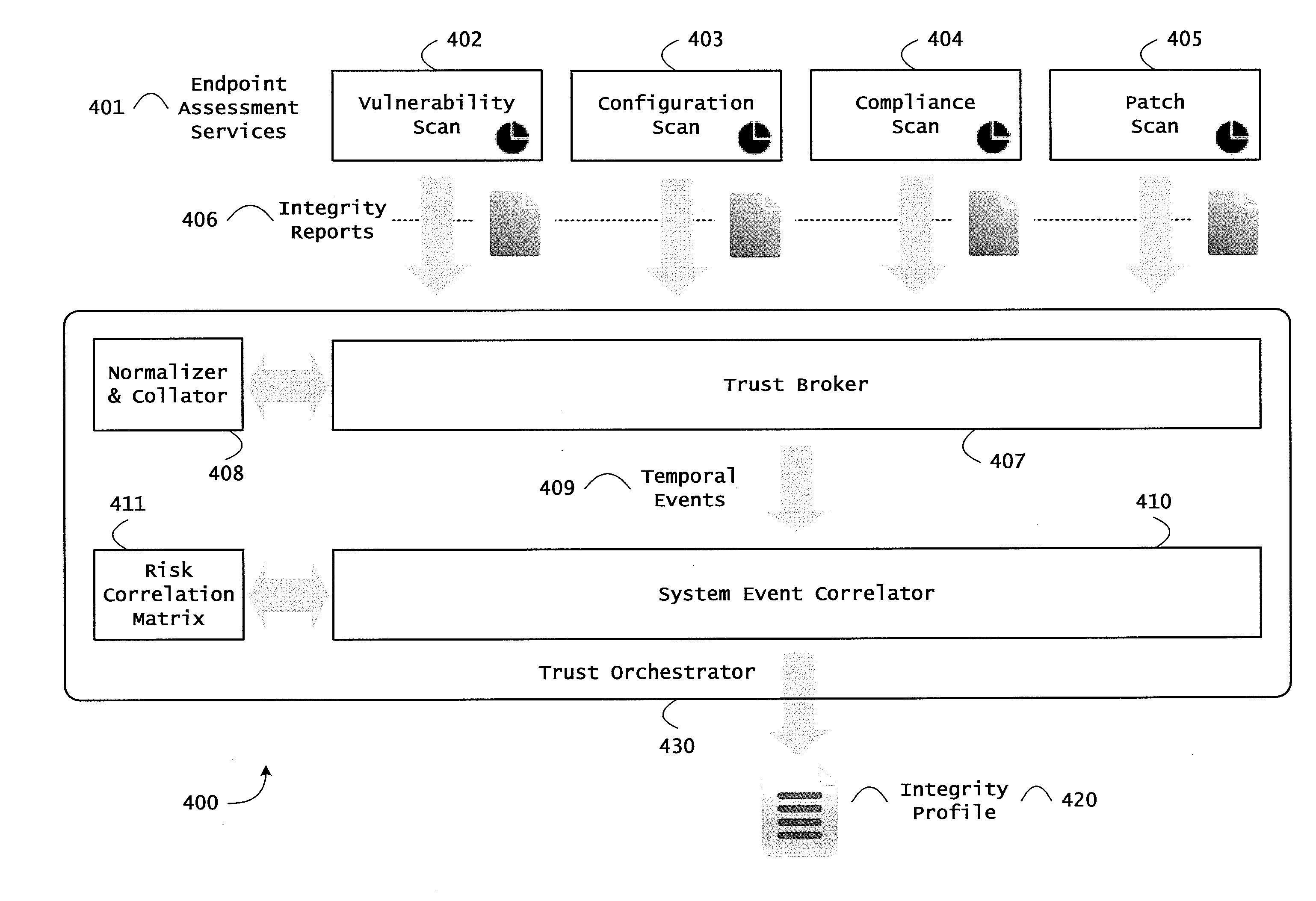
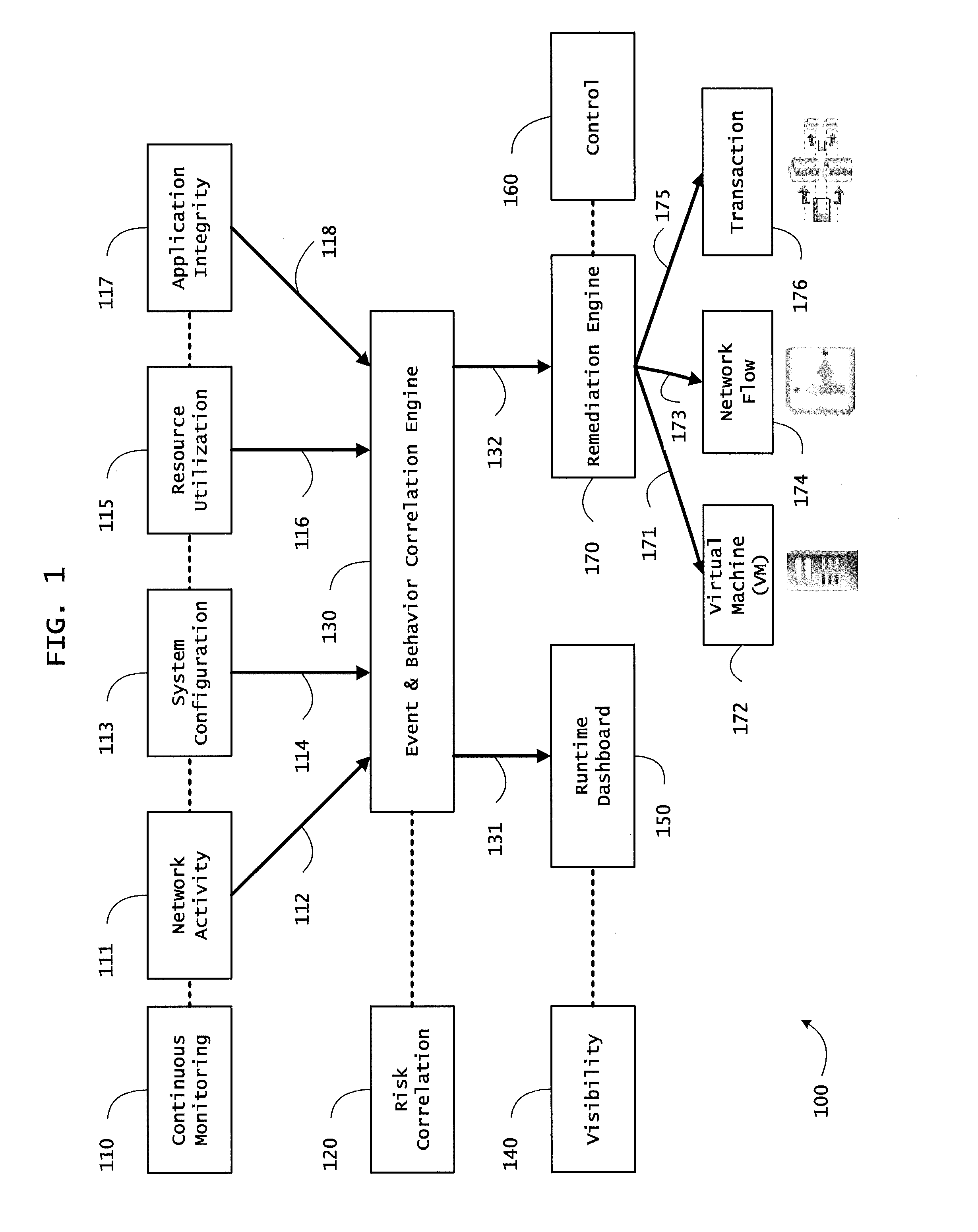
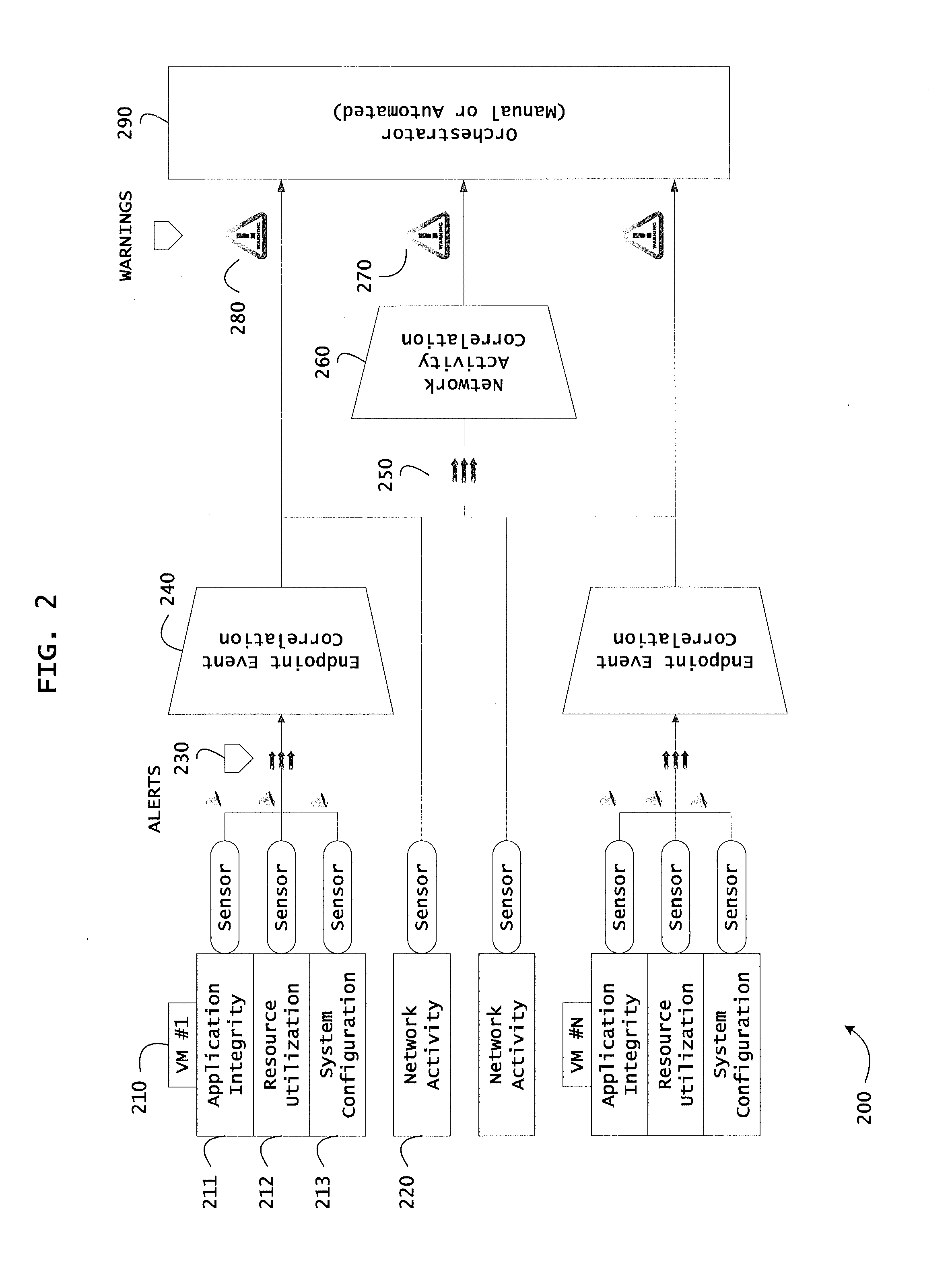
Systems and methods for network flow remediation based on risk correlation
ActiveUS20130298230A1Memory loss protectionError detection/correctionResource utilizationSystem configuration
Instrumented networks and platforms having target subjects (devices, transactions, services, users, organizations) are disclosed. A security orchestration service generates runtime operational integrity profiles representing and identifying a level of threat or contextual trustworthiness, at near real time, of subjects and applications on the instrumented target platform. Methods and systems are disclosed for network flow and device / platform remediation in response to reconnaissance-based intelligence correlation based on network monitoring, to accomplish network flow remediation and device / platform remediation. In an embodiment, a system receives system warnings and endpoint threat intelligence. The system correlates risk based on inputs from sensory inputs that monitor network activity, system configuration, resource utilization, and device integrity. The system then performs a calculus of risk on a global security context including endpoint assessment reports and sends system warnings based upon the endpoint threat intelligence. The system includes a remediation engine for receiving real time directives to control the device.
Owner:TAASERA LICENSING LLC
Method for secure access to multiple secure networks
ActiveUS7506170B2Easy to separateEliminate needUser identity/authority verificationUnauthorized memory use protectionOperational systemApplication software
Disclosed is a method for providing secure access to multiple secure networks from a single workstation. The architecture can use multiple layers of protection to isolate applications running at different security levels. The first means of isolation is a virtual machine monitor that isolates multiple operating systems running within separate virtual machines on the host operating system. The second layer is the use of multiple user security contexts on the host operating system to isolate each virtual machine. The third level of protection is a highly secured and restricted host operating system where all unnecessary services are removed and user actions are restricted to just the virtual machine monitor using software restriction policies. Finally, the operating system and virtual machine monitor can be run from read-only media to prevent any changes by an attacker from persisting.
Owner:MICROSOFT TECH LICENSING LLC
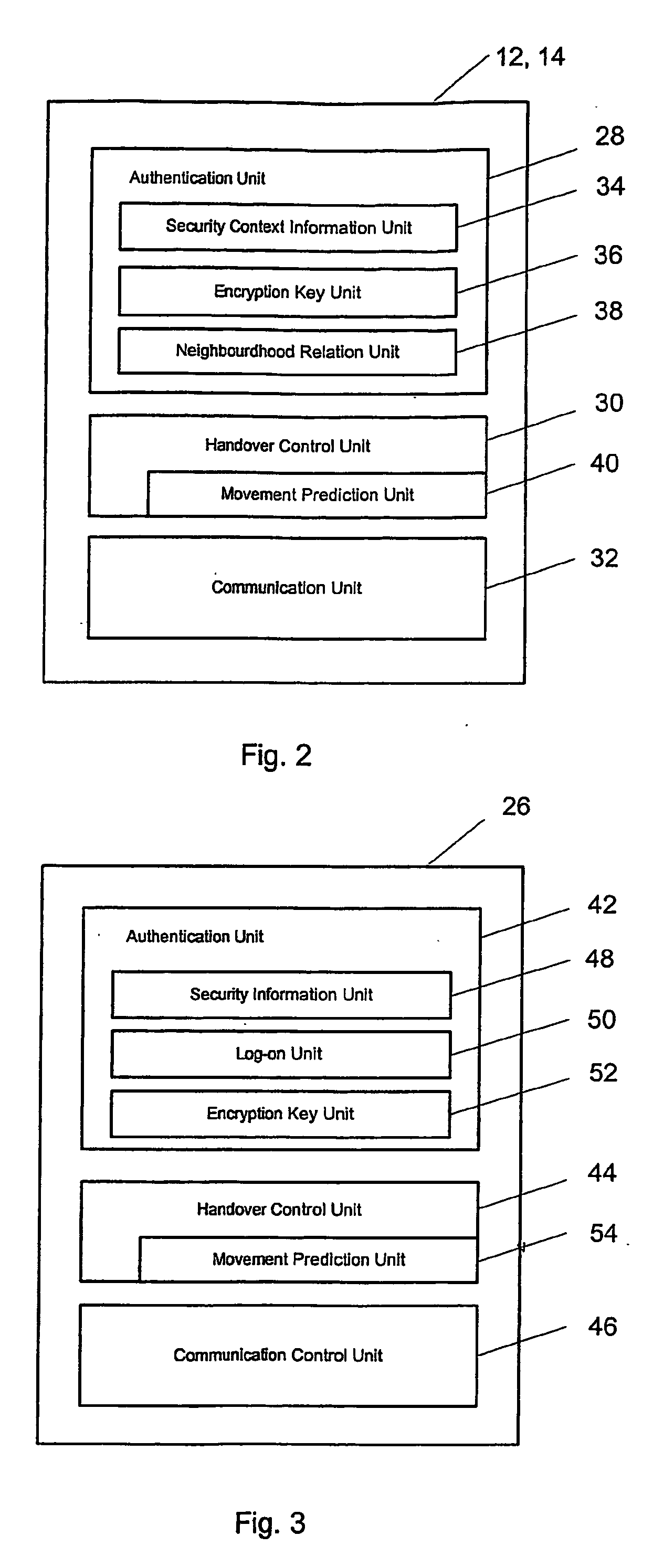
Secure intra-and inter-domain handover
ActiveUS20070064647A1Fast and secure handoverConnection securityNetwork traffic/resource managementUnauthorised/fraudulent call preventionHandoff controlFast handover
To achieve a secure and fast handover in a distributed mobile communication environment (10), the control functionality is lying at the borderline between wireless and wire-bound communication network elements, and it is proposed to, firstly, execute a mutual authentication between a mobile device (26) and a new access point (14) using security context information previously transmitted to the new access point. Then, after successful mutual authentication, a handover will be executed from the current access point (12) to the new access point (14).
Owner:NTT DOCOMO INC
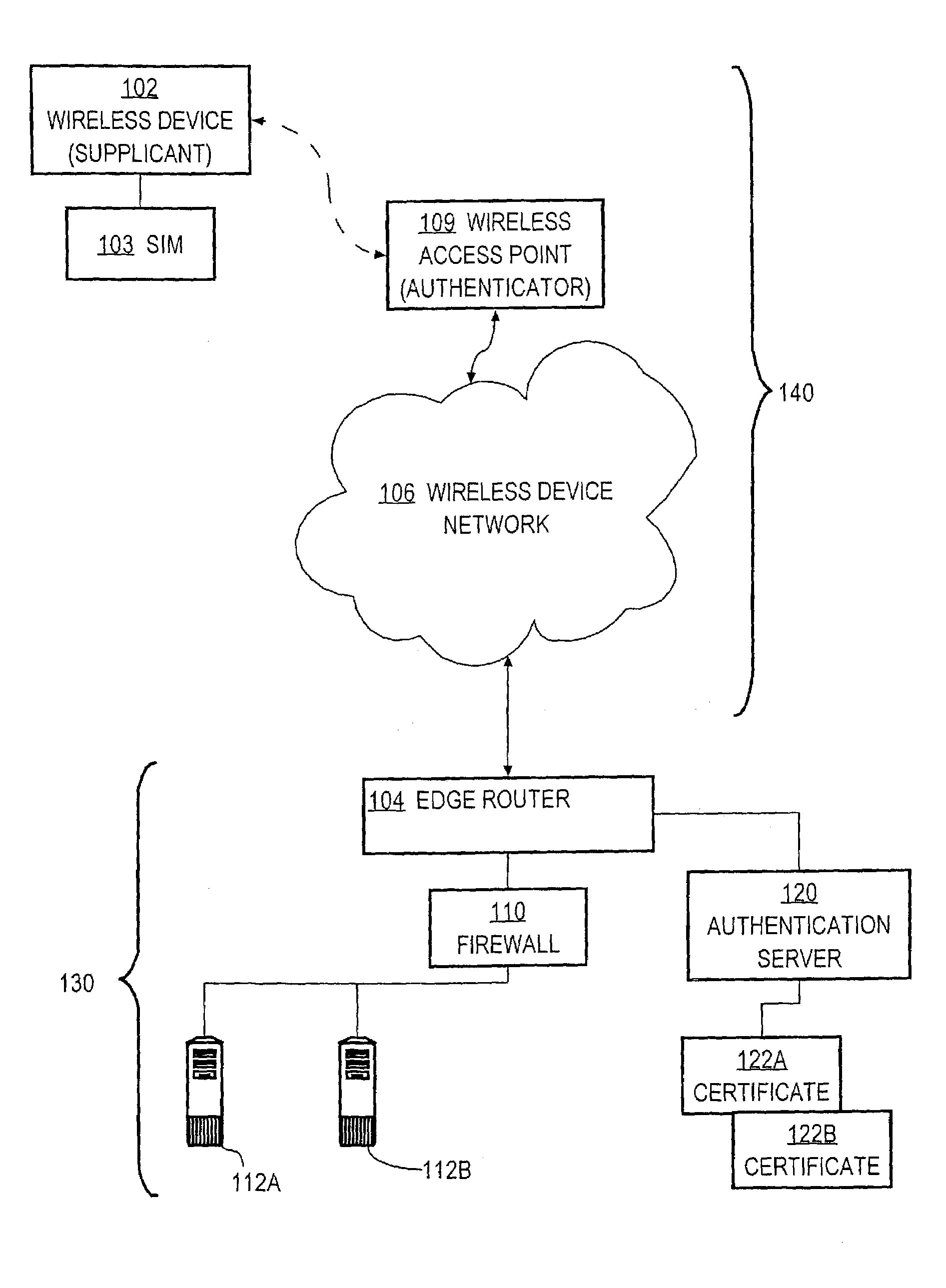
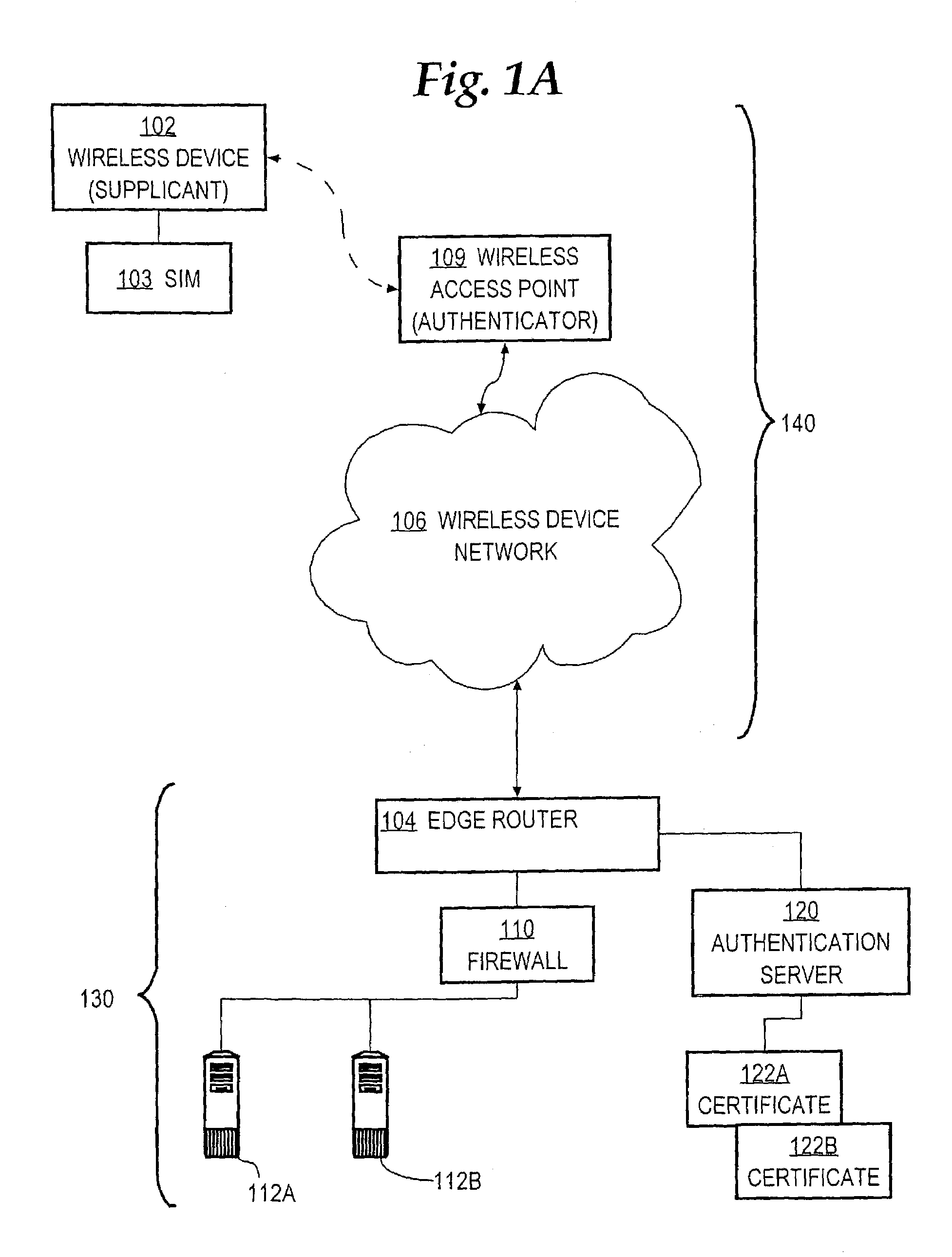
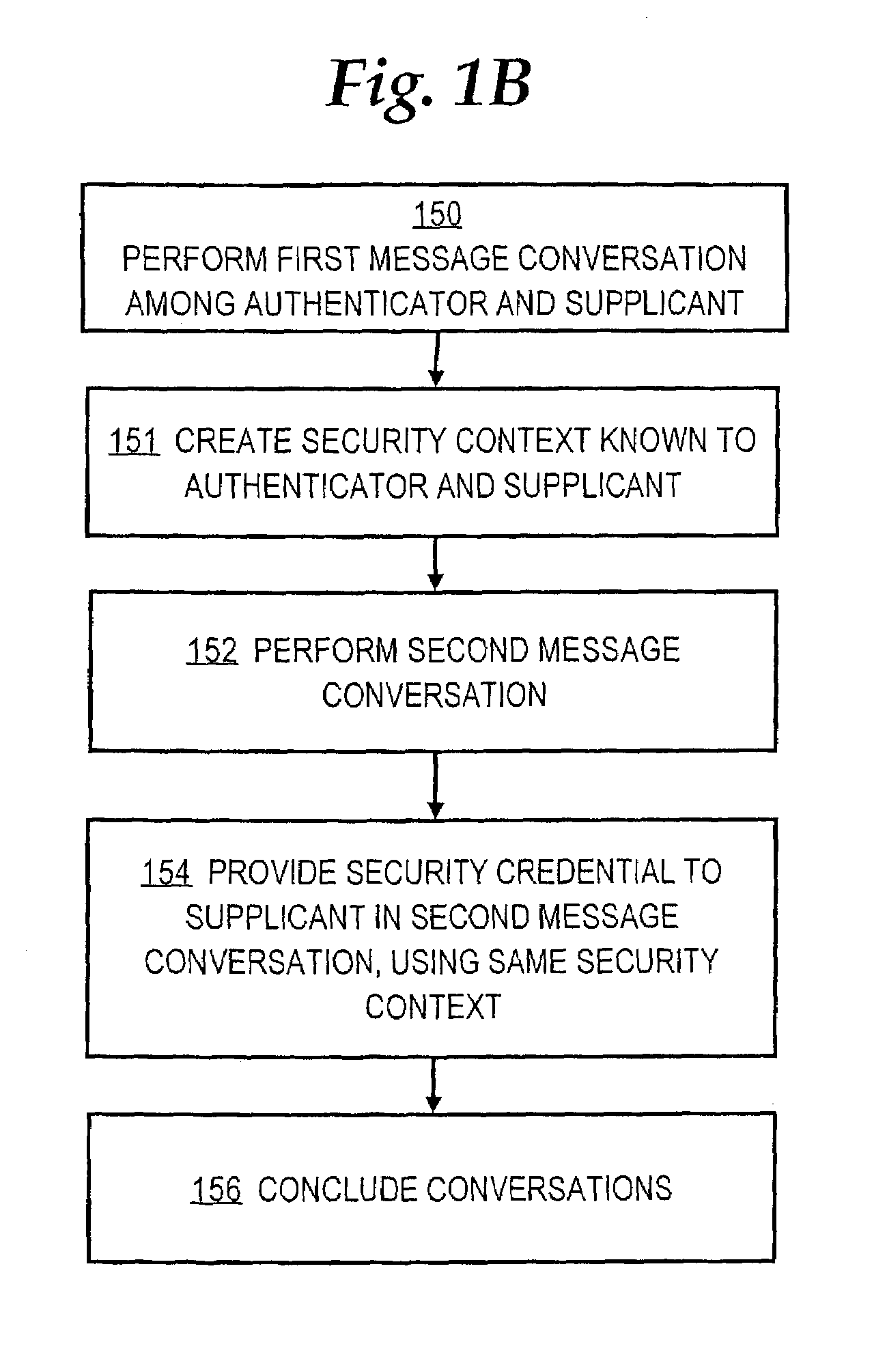
Method and apparatus for communicating credential information within a network device authentication conversation
InactiveUS7171555B1Digital data processing detailsUser identity/authority verificationSecurity contextAuthentication
A method is disclosed for communicating a security credential within a network device authentication conversation. An authenticator that is coupled to a supplicant through a network performs a first message conversation resulting in creating a security context that is known to the authenticator and the supplicant. A second message conversation is initiated. The second message conversation is cryptographically protected using the same security context. A security credential is provided to the supplicant in the second message conversation. The second message conversation and first message conversation are then concluded. Specific embodiments can bootstrap digital certificates, public / private key pairs, and other credentials to supplicants, in-band, within an EAP-SIM or EAP-AKA conversation and without initiating a new session or exchanging special-purpose keys to protect distribution of the credentials.
Owner:CISCO TECH INC
Establishment of security context
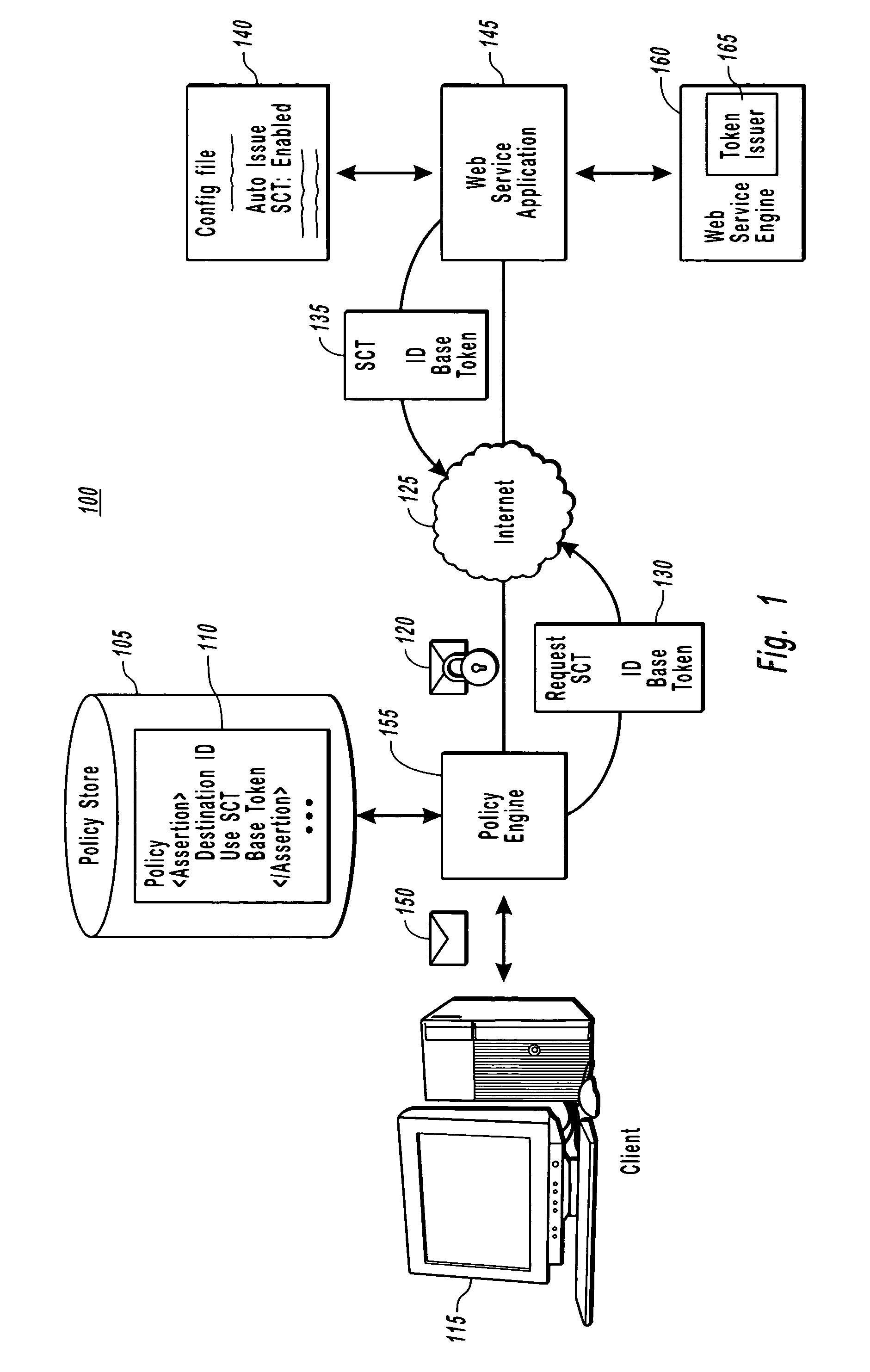
The present invention provides for maintaining security context during a communication session between applications, without having to have executable code in either application for obtaining or generating a security context token (SCT) used to secure the communication. On a service side, a configuration file is provided that can be configured to indicate that automatic issuance of a SCT is enabled, thereby allowing a Web service engine to generate the SCT upon request. On the client side, when a message is sent from the client application to the service application, a policy engine accesses a policy that includes assertions indicating that a SCT is required for messages destined for the Web service application. As such, the policy engine requests and receives the SCT, which it uses to secure the message.
Owner:MICROSOFT TECH LICENSING LLC
Securing sensitive information with a trusted proxy frame
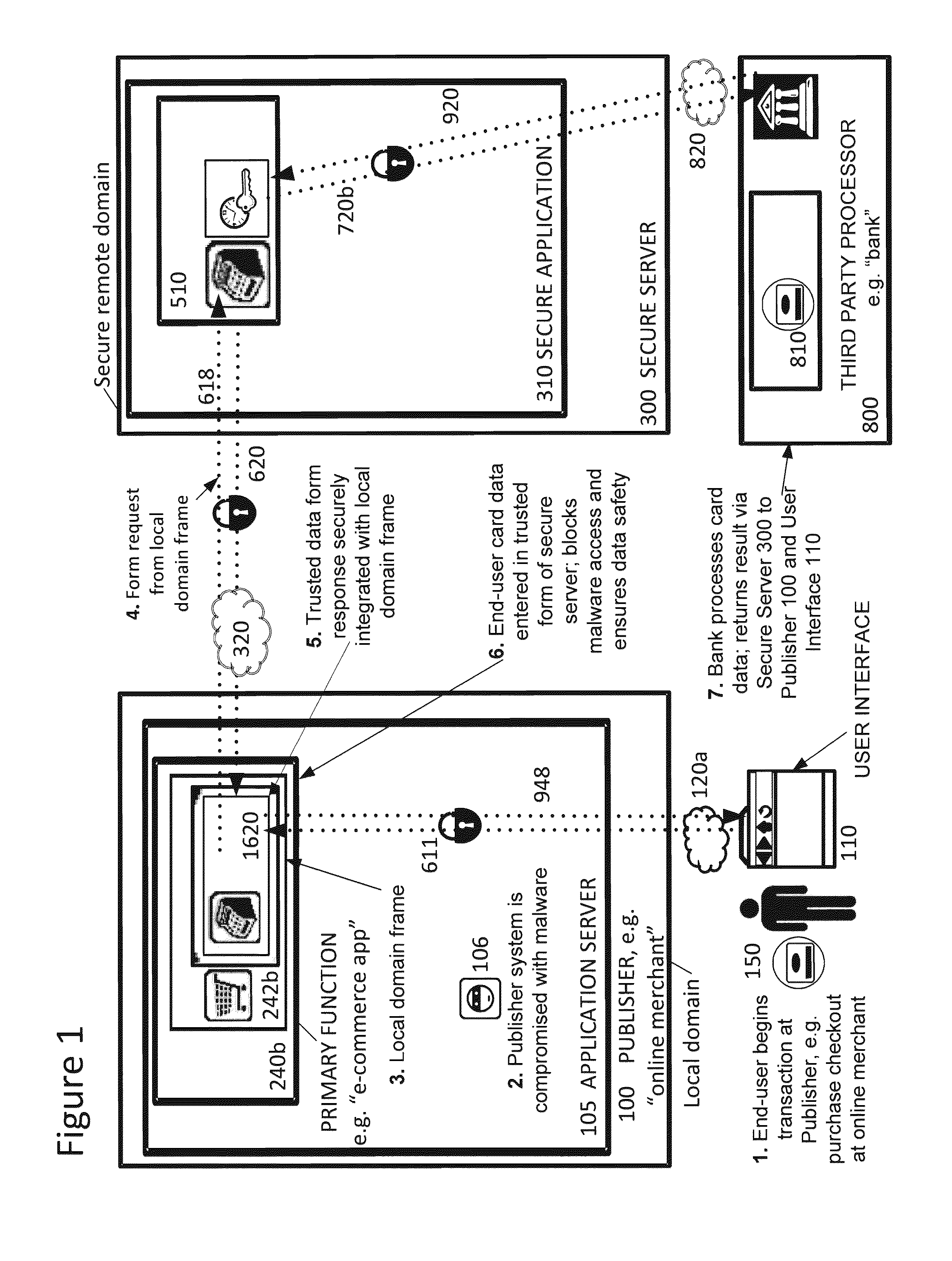
InactiveUS20120089481A1Rapid deploymentInformation securityDigital data processing detailsUser identity/authority verificationThird partyInternet privacy
A system and method for secure transmission of sensitive end user information from an Internet portal operated by a publisher to a third party data processor. The publisher provides a content portal such as an e-commerce or healthcare information site. A third party data processor such as a bank or healthcare organization requires the sensitive information for a data processing function. In response to the requirement for sensitive information, a trusted proxy frame is invoked from a secure server operative to securely communicate the sensitive information. The trusted proxy frame is displayed in a secure context in the end user's browser and receives input of the sensitive information. The sensitive information is encrypted and communicated through the secure server to the third party data processor. Results of this processing are transmitted to the publisher through a novel callback process that enables the publisher to execute its data processing functions, as if it was in possession of the sensitive information, but without actual access to the sensitive information. The third party data processor returns an acknowledgement of processing of the sensitive information.
Owner:CHAIN REACTION ECOMMERCE
Wireless security system and method
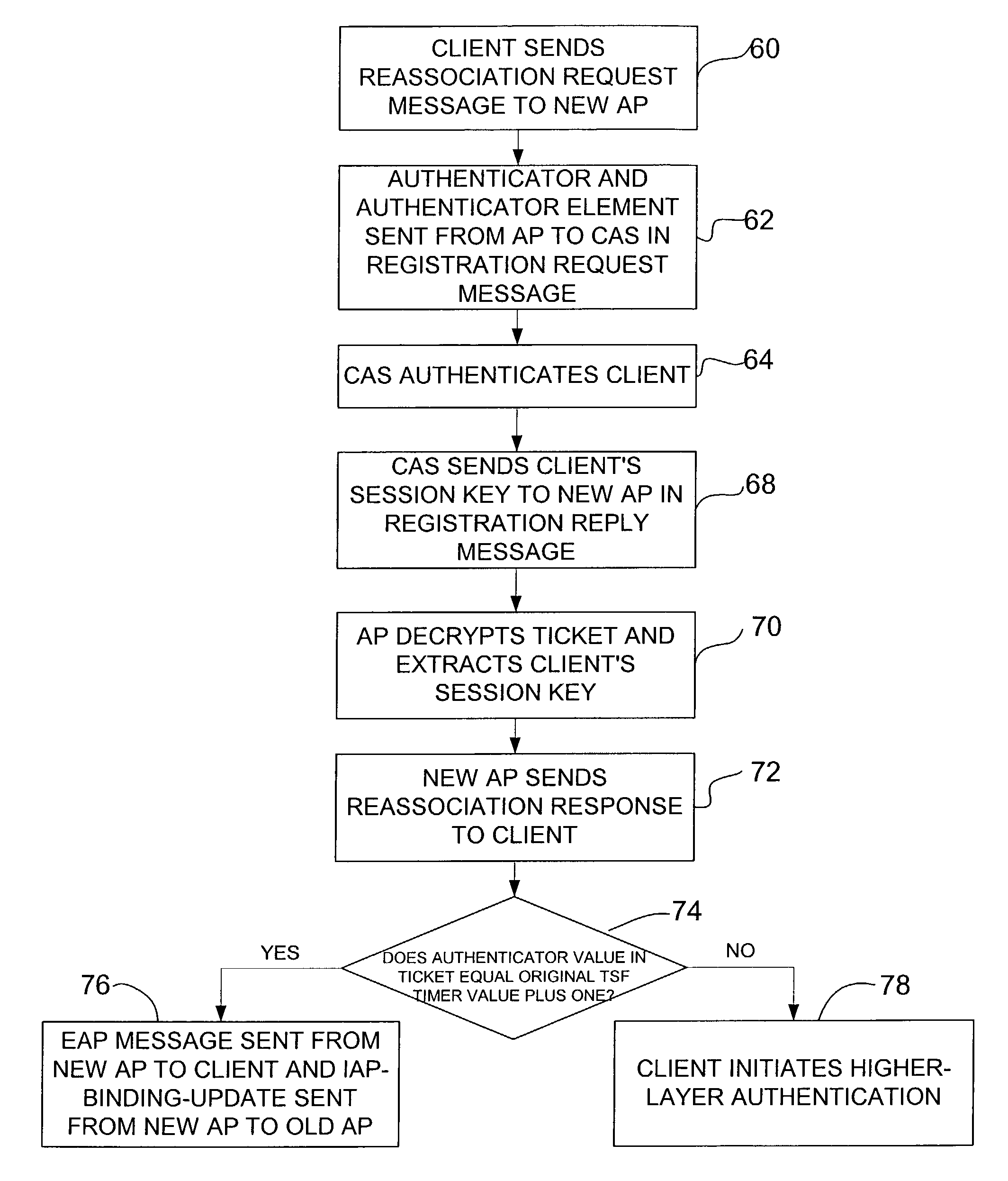
ActiveUS7373508B1Key distribution for secure communicationDigital data processing detailsClient-sideComputer science
A method for reauthentication during client roaming in a wireless network system. The network has at least one access server and a plurality of access points registered with the access server. The method includes receiving a registration request at the access server from a new access point for a roaming client registered with the access server and sending a client's session key to the new access point in a registration reply upon authentication of the registration request. The client's session key is configured for use by the new access point to authenticate the client and establish keys for the client. A method for secure context transfer during client roaming is also disclosed.
Owner:CISCO TECH INC
Systems and methods for providing an fully functional isolated execution environment for accessing content
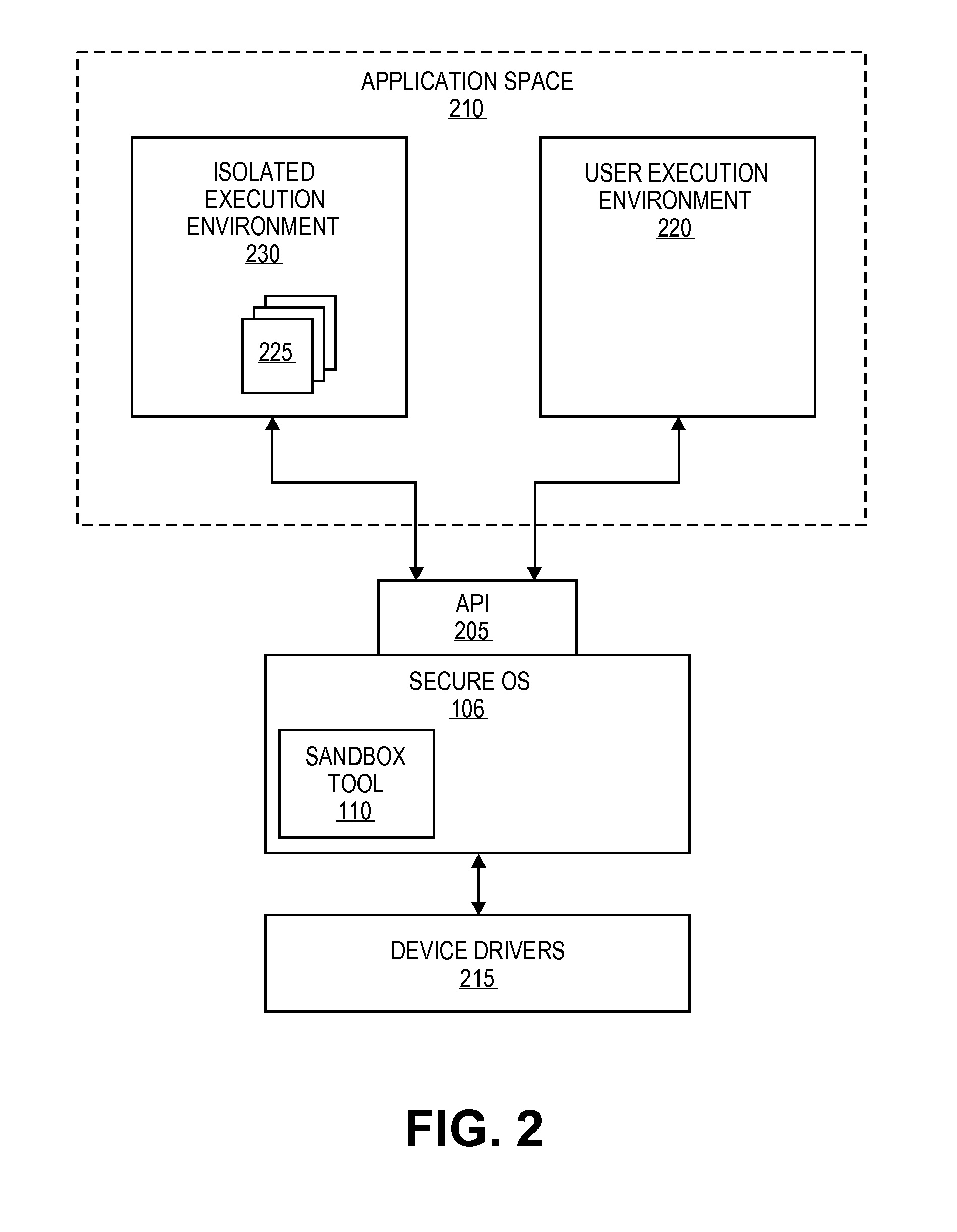
ActiveUS20110296487A1Input/output for user-computer interactionDigital data processing detailsOperational systemSecurity policy
A sandbox tool can cooperate with components of a secure operating system to create an isolated execution environment for accessing content without exposing other processes and resources of the computing system to the untrusted content. The sandbox tool can create the isolated execution environment with an assigned security context of the secure operating system. The security context can define the security policies applied by the operating system to the isolated execution environment, thereby, defining the levels of access the isolated execution environment has to the resources of the computing system.
Owner:RED HAT
Method for secure access to multiple secure networks
ActiveUS20050268336A1Easy to separateEliminate needUser identity/authority verificationUnauthorized memory use protectionOperational systemWorkstation
Disclosed is a method for providing secure access to multiple secure networks from a single workstation. The architecture can use multiple layers of protection to isolate applications running at different security levels. The first means of isolation is a virtual machine monitor that isolates multiple operating systems running within separate virtual machines on the host operating system. The second layer is the use of multiple user security contexts on the host operating system to isolate each virtual machine. The third level of protection is a highly secured and restricted host operating system where all unnecessary services are removed and user actions are restricted to just the virtual machine monitor using software restriction policies. Finally, the operating system and virtual machine monitor can be run from read-only media to prevent any changes by an attacker from persisting.
Owner:MICROSOFT TECH LICENSING LLC
Memory management system and method for providing physical address based memory access security
InactiveUS6823433B1Memory adressing/allocation/relocationUnauthorized memory use protectionManagement unitComputerized system
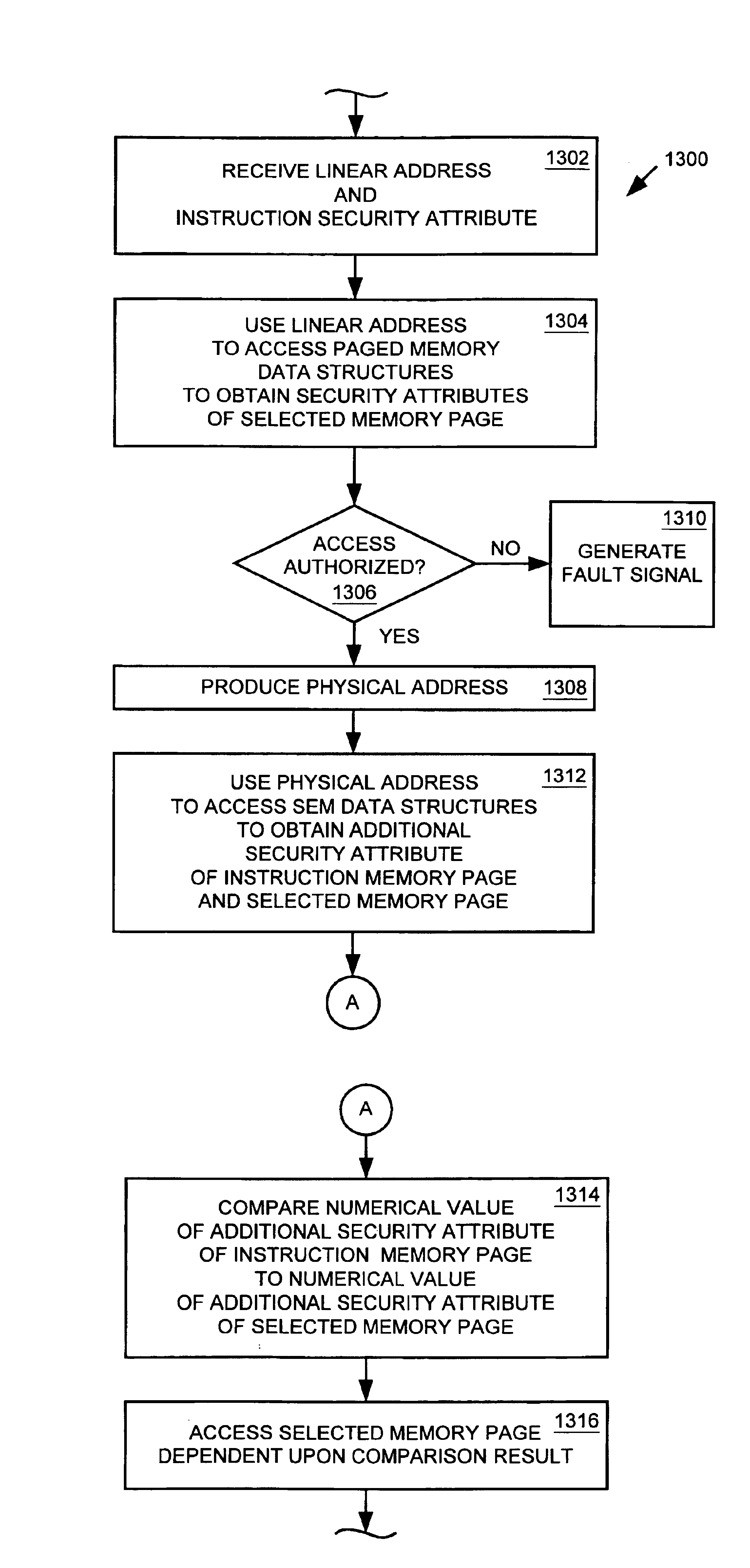
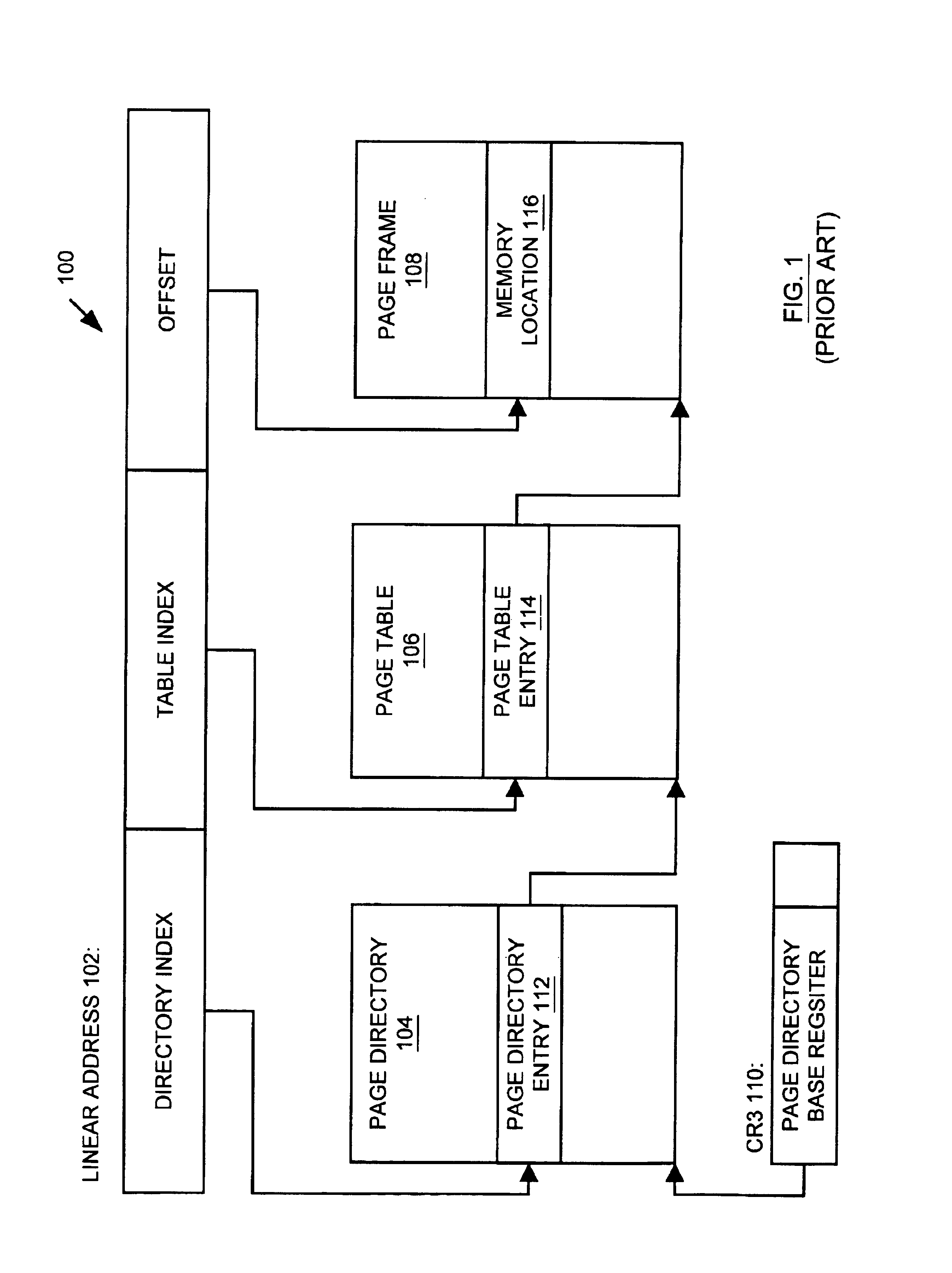
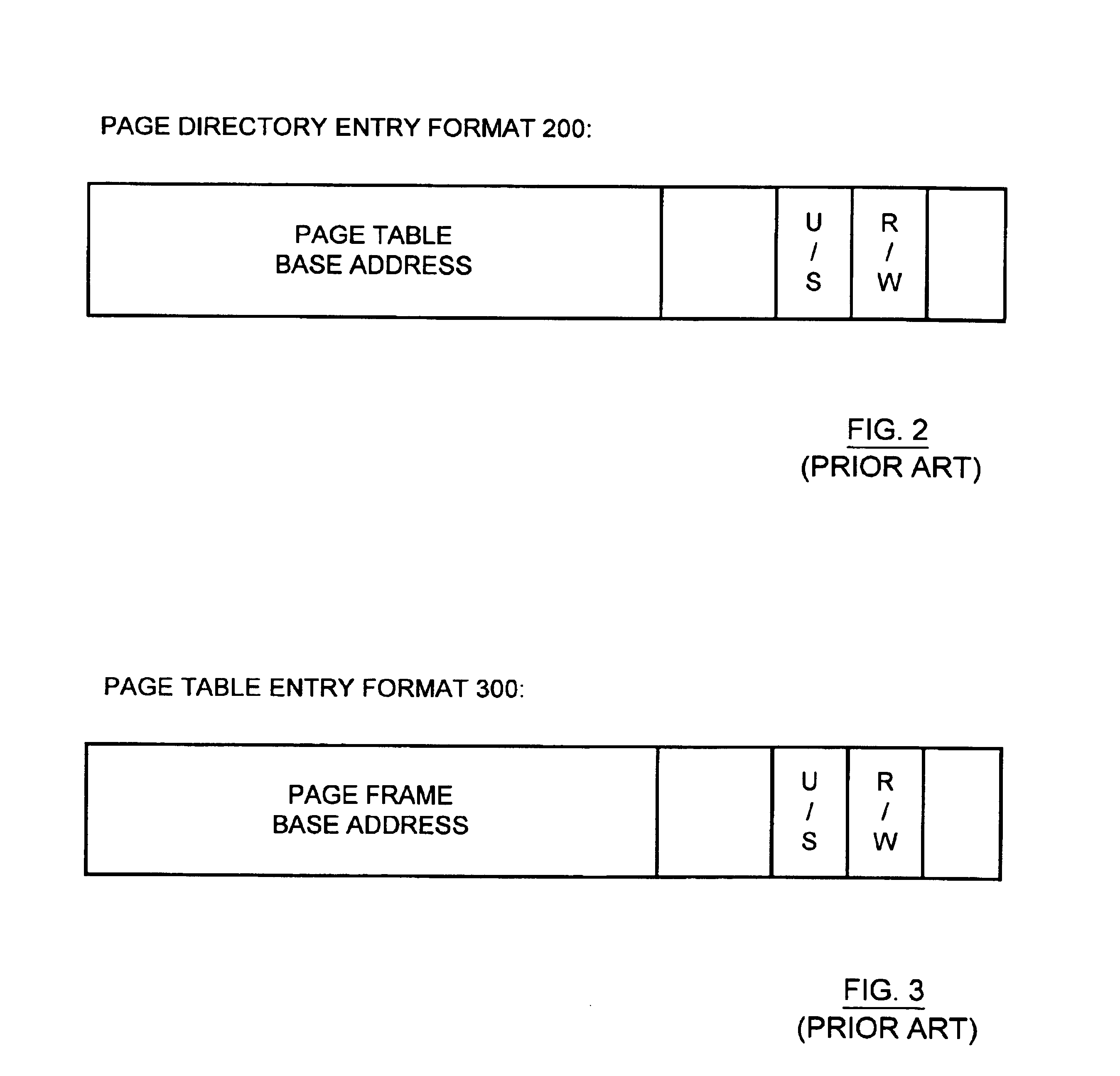
A memory management unit (MMU) is disclosed for managing a memory storing data arranged within a plurality of memory pages. The MMU includes a security check unit (SCU) receiving a physical address generated during execution of a current instruction. The physical address resides within a selected memory page. The SCU uses the physical address to access one or more security attribute data structures located in the memory to obtain a security attribute of the selected memory page, compares a numerical value conveyed by a security attribute of the current instruction to a numerical value conveyed by the security attribute of the selected memory page, and produces an output signal dependent upon a result of the comparison. The MMU accesses the selected memory page dependent upon the output signal. The security attribute of the selected memory page may include a security context identification (SCID) value indicating a security context level of the selected memory page. The security attribute of the current instruction may include an SCID value indicating a security context level of a memory page containing the current instruction. A central processing unit (CPU) is described including an execution unit and the MMU. A computer system is described including the memory, the CPU, and the MMU. A method is described for providing access security for a memory used to store data arranged within a plurality of memory pages. The method may be embodied within the MMU.
Owner:GLOBALFOUNDRIES US INC +1
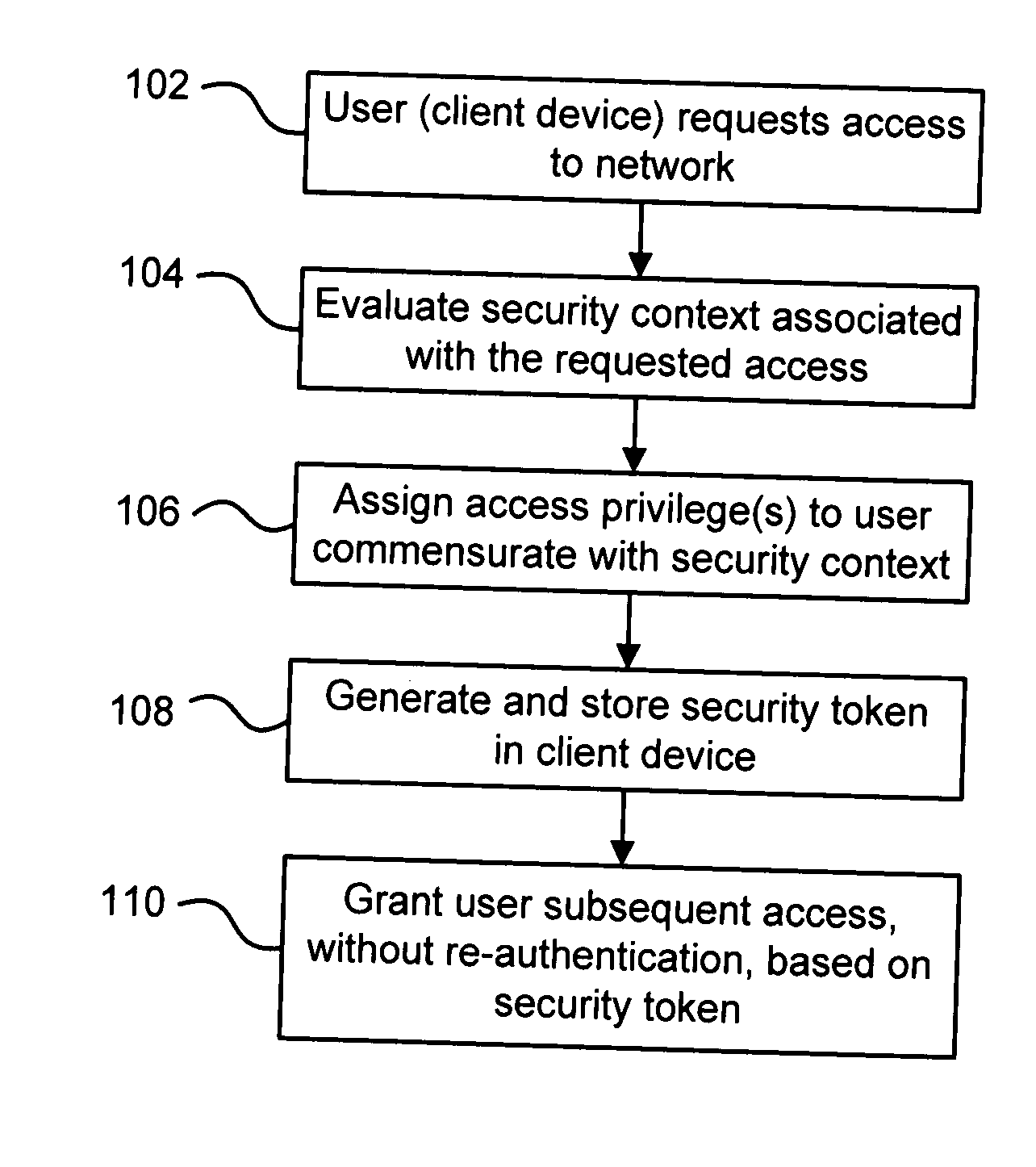
Technique for providing secure network access
ActiveUS20070011725A1Digital data processing detailsUser identity/authority verificationClient-sideSecurity context
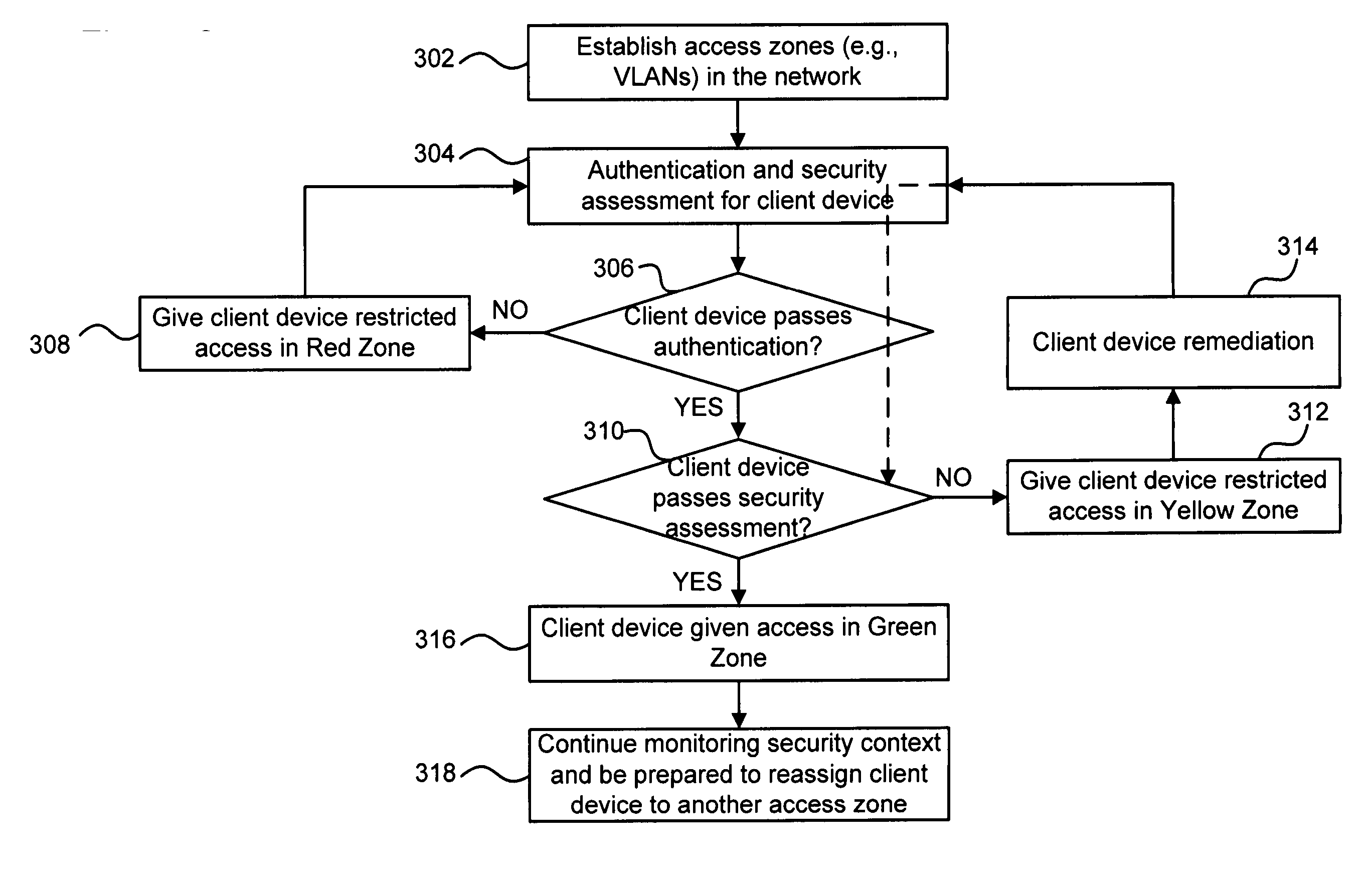
A technique for providing secure network access is disclosed. In one particular exemplary embodiment, the technique may be realized as a method for providing secure network access. The method may comprise establishing a plurality of access zones in a network, wherein client devices assigned to different access zones have different access privileges and are isolated from one another. The method may also comprise assigning a client device to one of the plurality of access zones based on an assessment of a security context associated with the client device and a connection of the client device to the network.
Owner:AVAYA INC
Systems and methods for integrating access control with a namespace
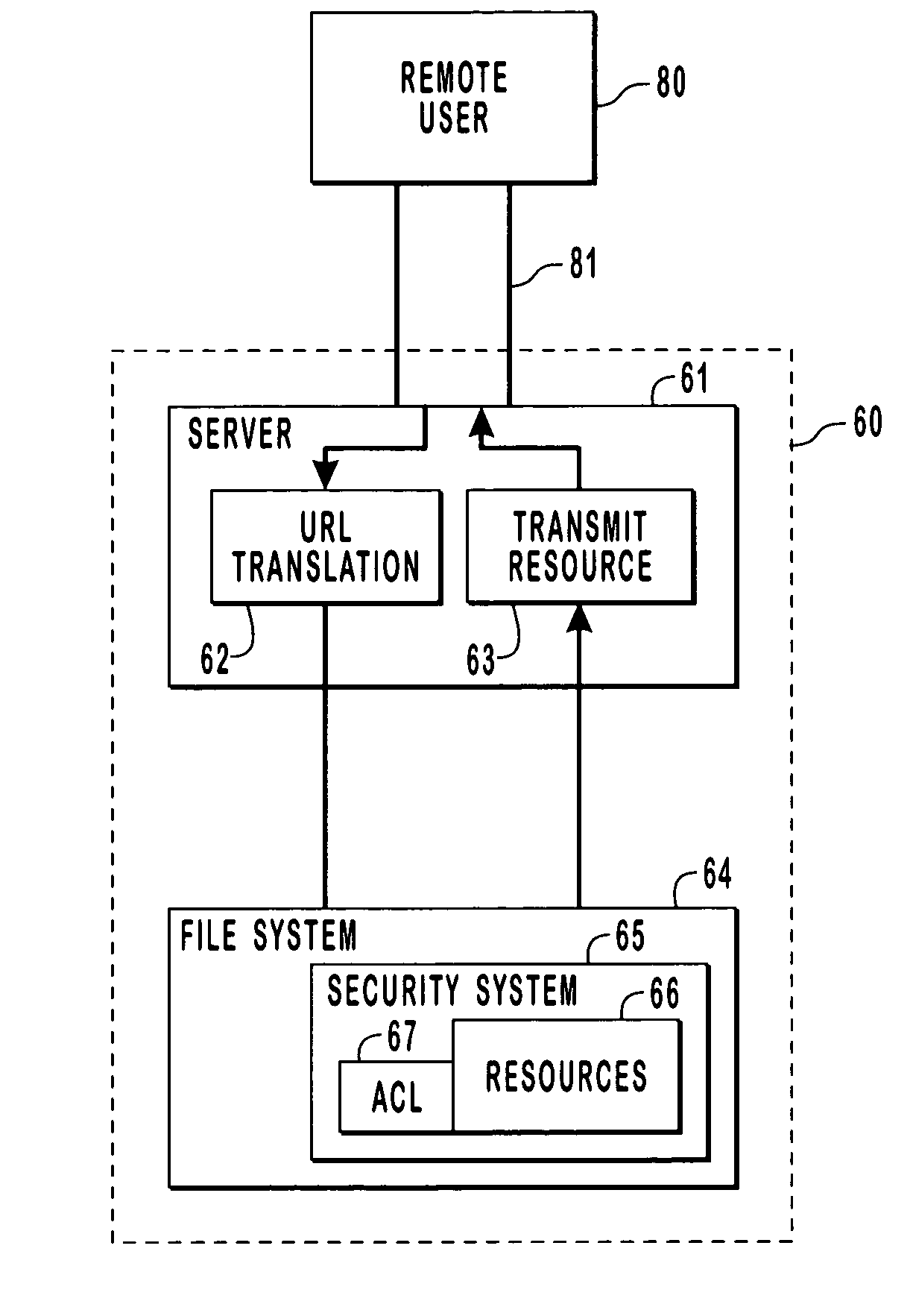
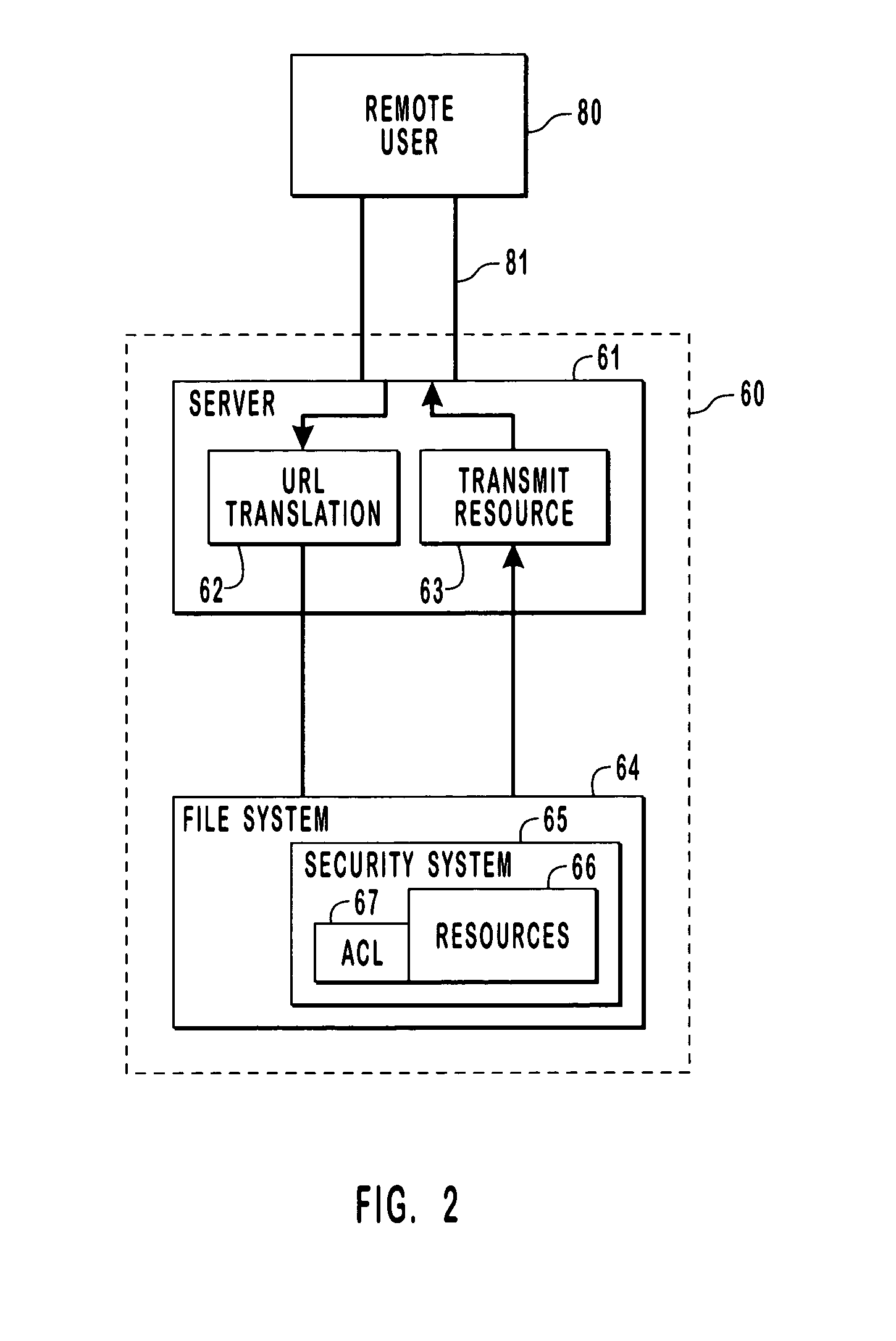
InactiveUS7065784B2Digital data processing detailsUser identity/authority verificationComputer resourcesData access control
Provided are methods and systems for integrating the access controls of computer resources into a namespace or domain. For a remote user, a computer network or system is a namespace represented by a URL. In order to enforce the access controls of the computer network being accesses, a remote user is impersonated by a server of the computer system such that access requests to the resources of a system are made by the server in the security context of the remote user. By impersonating the remote user, the actual rights of the remote user are being presented to the access controls rather than the rights of the server. In this manner, the access control of the system can be enforced directly on the remote user and the access control is effectively extended to the namespace.
Owner:MICROSOFT TECH LICENSING LLC
Preserving data protection and enabling secure content awareness in query services
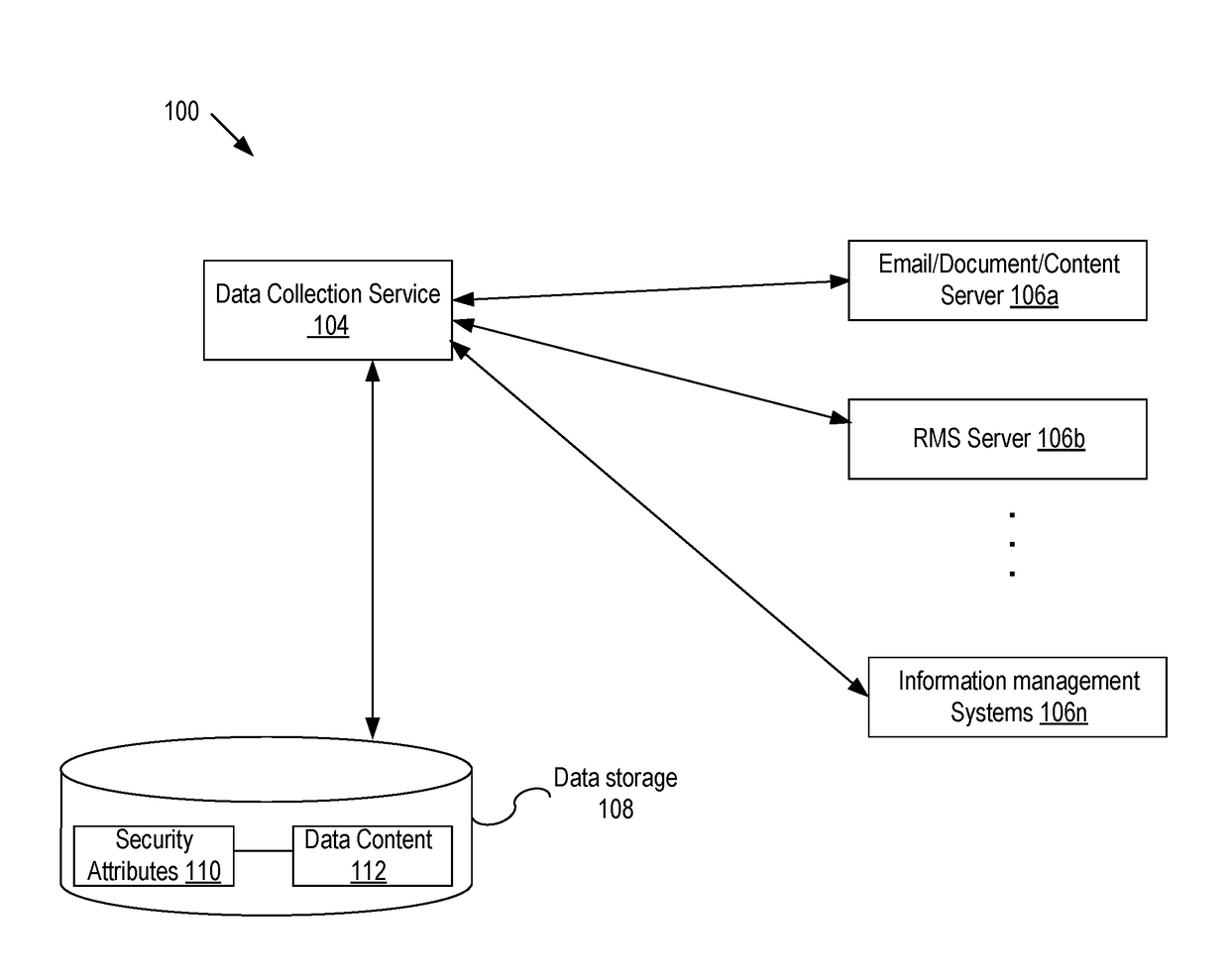
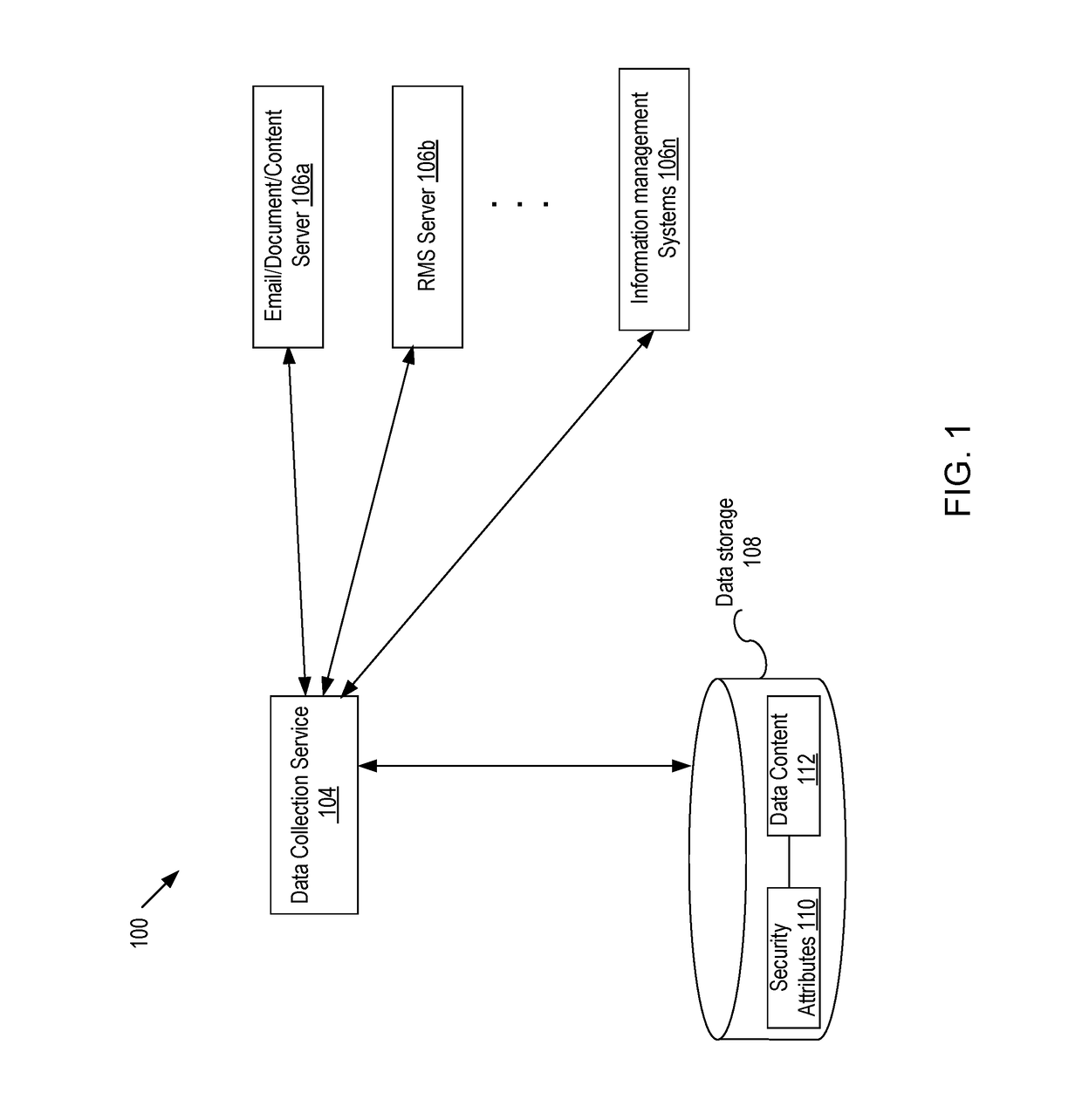
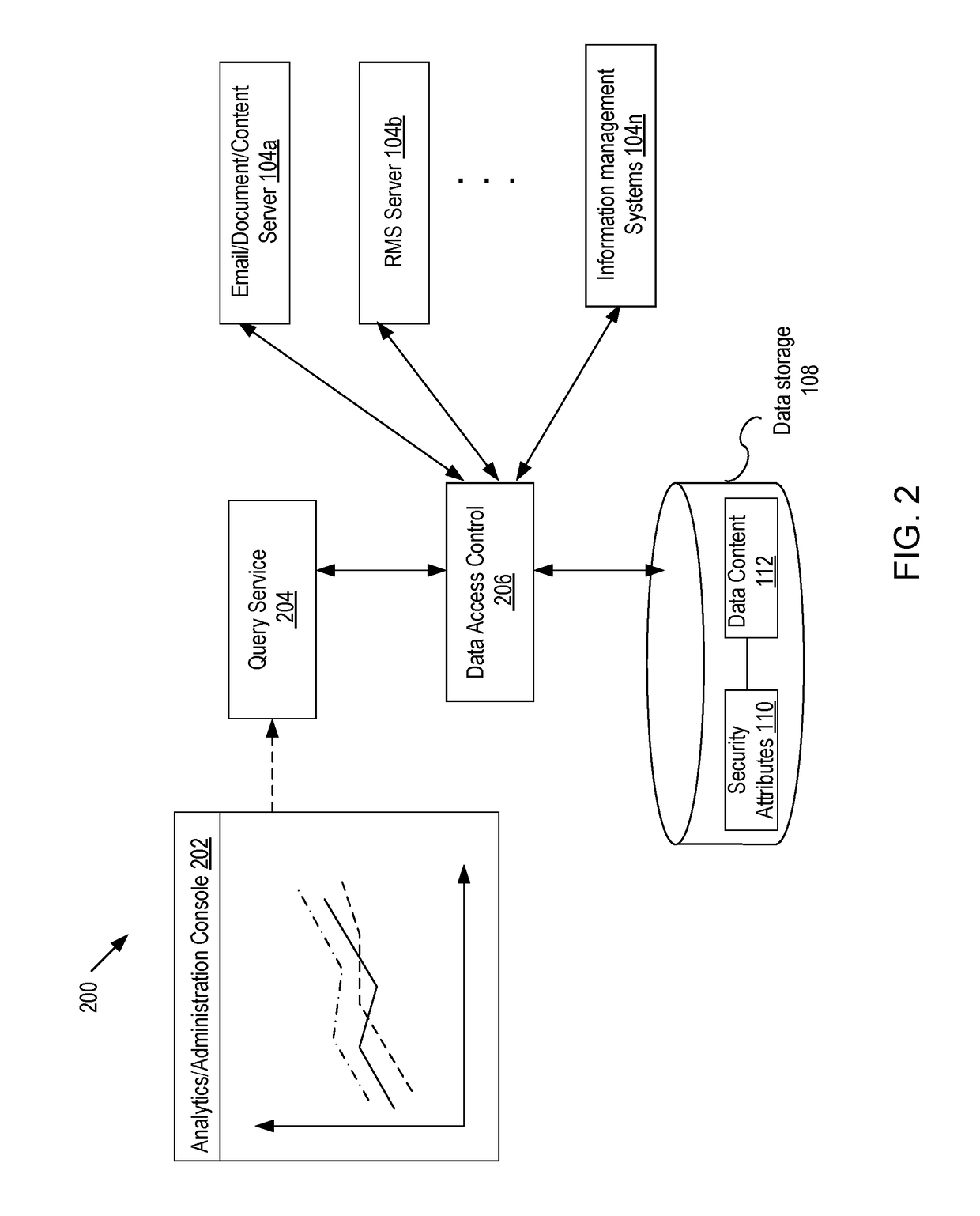
ActiveUS20170300702A1Digital data information retrievalDigital data protectionInternet privacyData source
Embodiments of the present disclosure include systems and methods for providing query service of secured contents. A data collection service collects data and security context associated with the data from a data source and stores the data with the security attributes in a datastore, where the security attributes are derived from the security context and used to determine access to the data so that access to the data is consistent with the security context. Upon receiving a query and a user context of a requester making the query of the datastore, a set of query results is obtained. Based on the user context and security attributes, it is determined whether the requestor has a proper right to access the query results. If the requestor has a proper right to access the query results, access to the query results is granted.
Owner:QUEST SOFTWARE INC
Message security processing system and method for web services
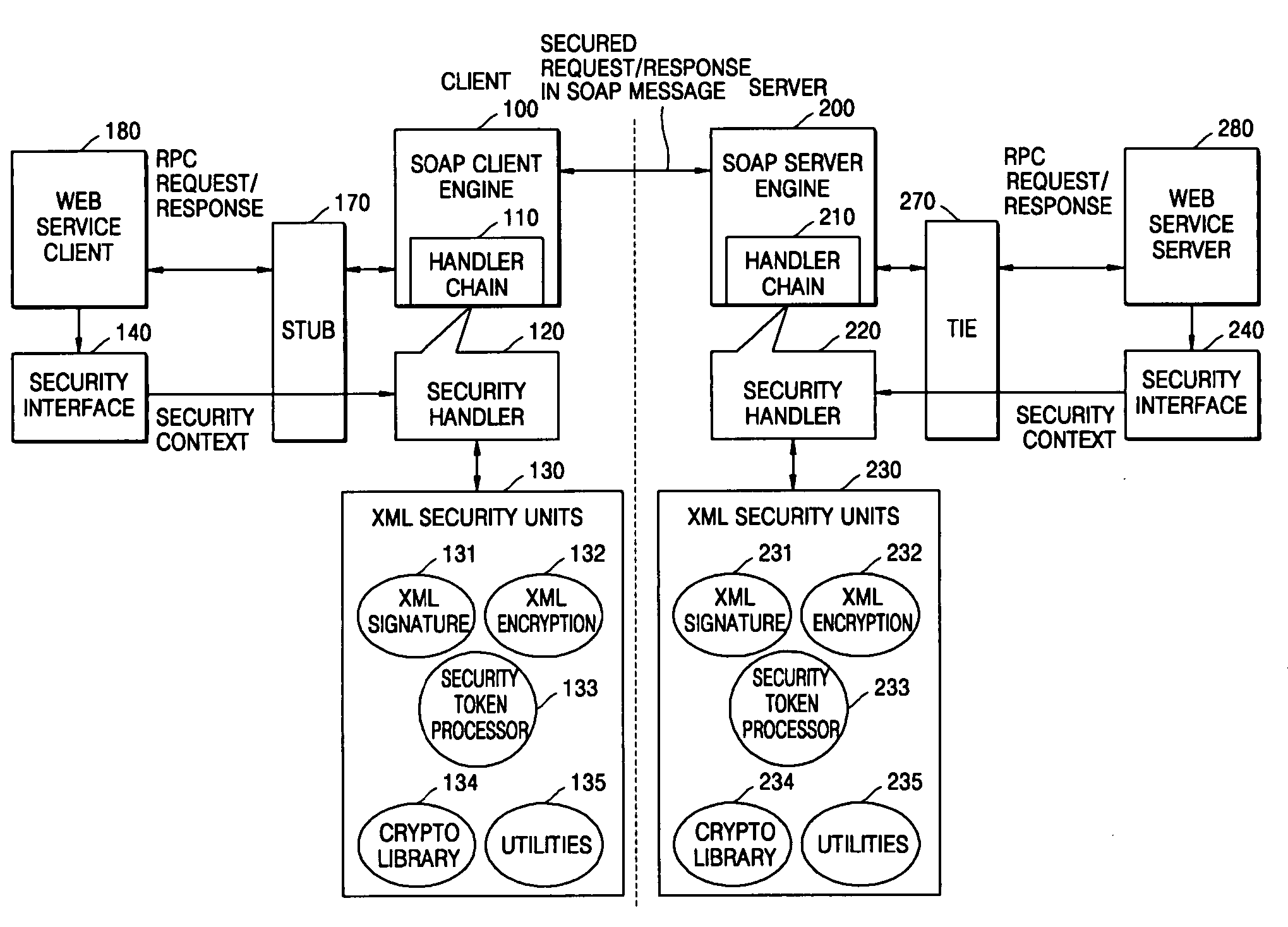
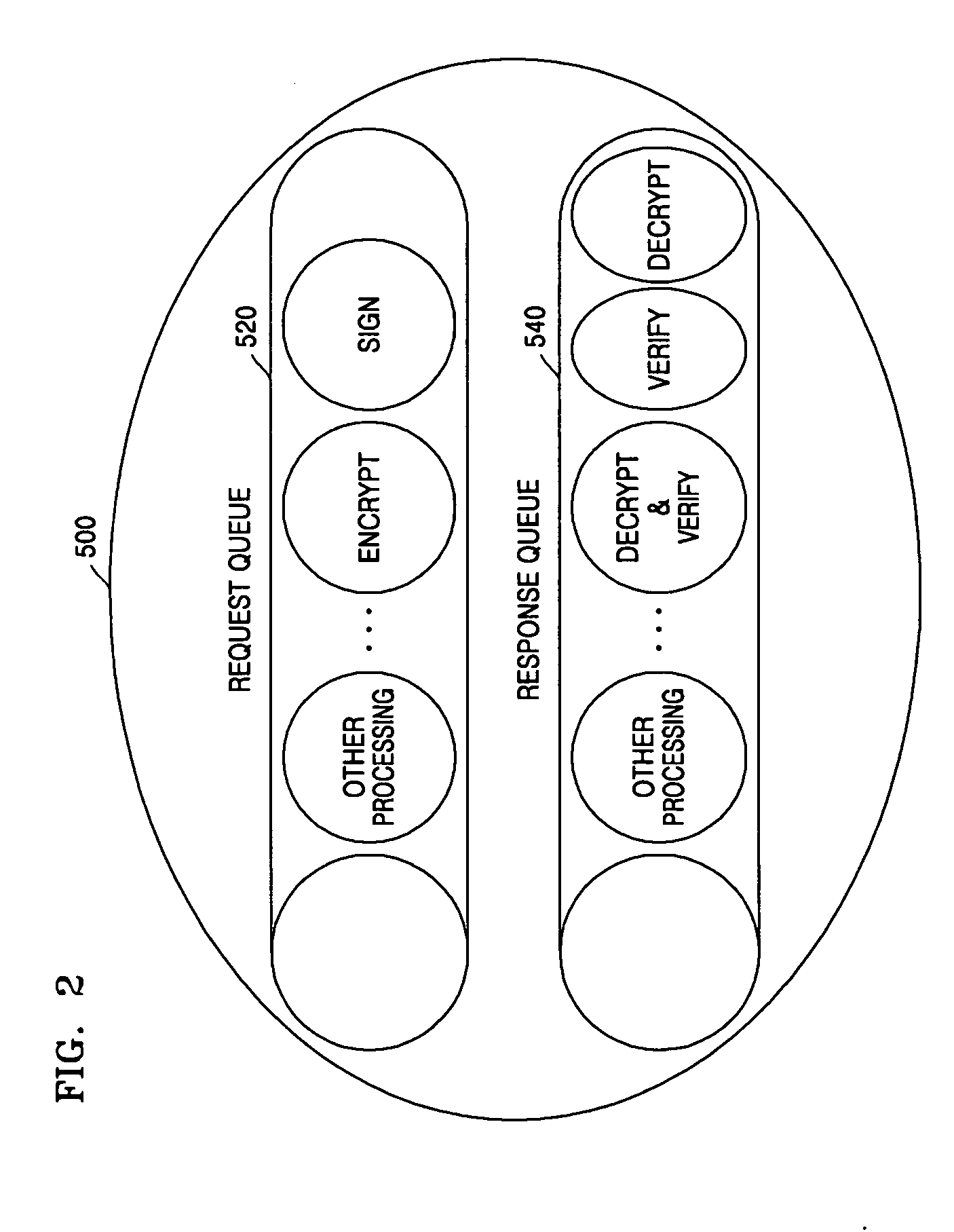
InactiveUS20050144457A1User identity/authority verificationDigital computer detailsTimestampWeb service
A message security processing system and method for Web services are provided. In the message security processing system in which messages are exchanged between a client and a server with a SOAP-RPC format, each of the client and the server includes: a security interface allowing information related to digital signature, encryption, and timestamp insertion to be set in a security context object for an application program to meet security requirements of the client or the server; a security handler receiving the security context object from the security interface, and performing security processing of a request message by calling security objects stored in a request queue of the security context object one by one in order or performing security processing of a response message by calling security objects stored in a response queue of the security context object one by one in order; and an XML security unit supporting an XML security functions by called by the security handler.
Owner:ELECTRONICS & TELECOMM RES INST
Technique for authenticating network users
ActiveUS20070169171A1Digital data processing detailsUser identity/authority verificationNetizenClient-side
Owner:AVAYA INC
Method for IMSI privacy protection of mobile communication system
ActiveCN107580324ATo achieve the purpose of privacy protectionHigh security requirementsSecurity arrangementNetwork data managementPrivacy protectionChange control
Disclosed is a method for IMSI privacy protection of a mobile communication system. A function entity includes UE, an access and mobility management function (AMF), a trusted UDM / AUSF, a trusted SMF and a trusted UPF. The UE is used for executing IMSI change behavior and initiating a network attachment request and completes a new security context negotiation based on a new IMSI at the same time. The AMF is used for replacing IMSI information and its associated GUTI information in a CP mode or a UP mode, and completes the secure context negotiation again based on the new IMSI. The UDM / AUSF is used for generating new IMSI information for UE. The SMF is used for notifying the trusted UPF to generate inband IMSI change control information under the UP mode. According to the invention, the difficulty of an attacker tracing a specific user or deriving real identity of the user is increased, the requirement for legal monitoring in the world is not violated, and at the same time, no consumption of an additional IMSI identification space is introduced.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Communications system
InactiveUS20130035056A1Emergency connection handlingAssess restrictionCommunications systemCellular communication systems
A cellular communications system is provided in which a user device maintains and provides a last non-emergency security context to a core network when moving from a network that provided restricted services to a network that provides unrestricted services. In this way, re-authentication of the user device can be avoided in the network that provided unrestricted services.
Owner:LENOVO INNOVATIONS LTD HONG KONG
Method and apparatus for providing a flexible and scalable context service
InactiveUS20030018692A1Simple technologyPromote exchangeMultiprogramming arrangementsMultiple digital computer combinationsEngineeringSecurity context
A flexible and extensible context server for collecting, maintaining, and disseminating context information is disclosed. The context server receives requests from requesters for context information via a secure context server interface (SCS API). Communication between the requesters and the context server is conducted by means of predetermined forms. The requests received at the SCS API are passed to a mediator, which collects data from various context drivers. Each context driver is coupled to the mediator, and collects predetermined type of context information from at least one context information source. The mediator determines the appropriate context driver which can handle the request, based on its type. Operation of the context server is also controlled by a set of context utilities, including a context cache for storing recently obtained context information, a privacy engine for storing privacy preferences and an event engine for event handling.
Owner:IBM CORP
Identity assertion token principal mapping for common secure interoperability
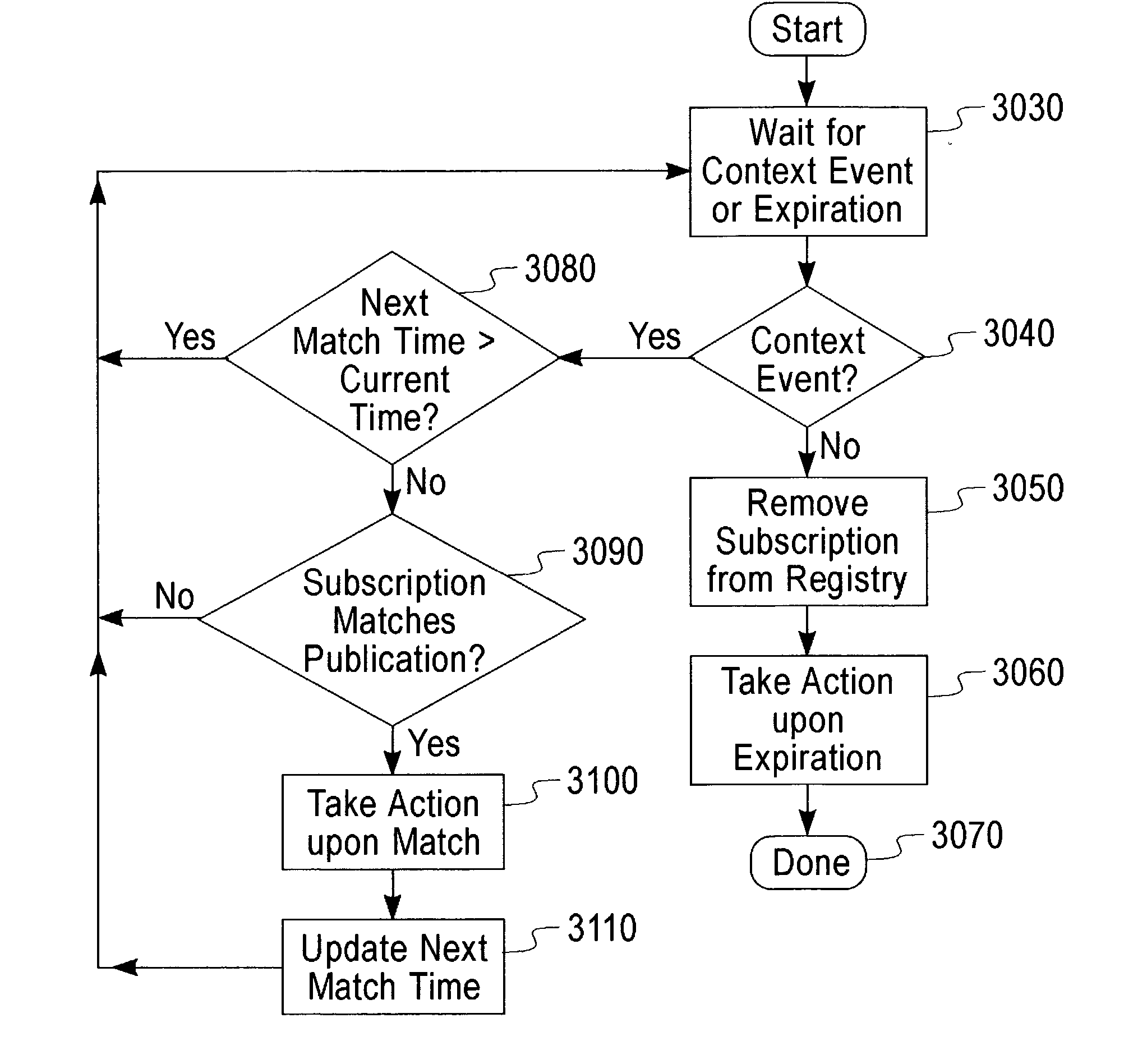
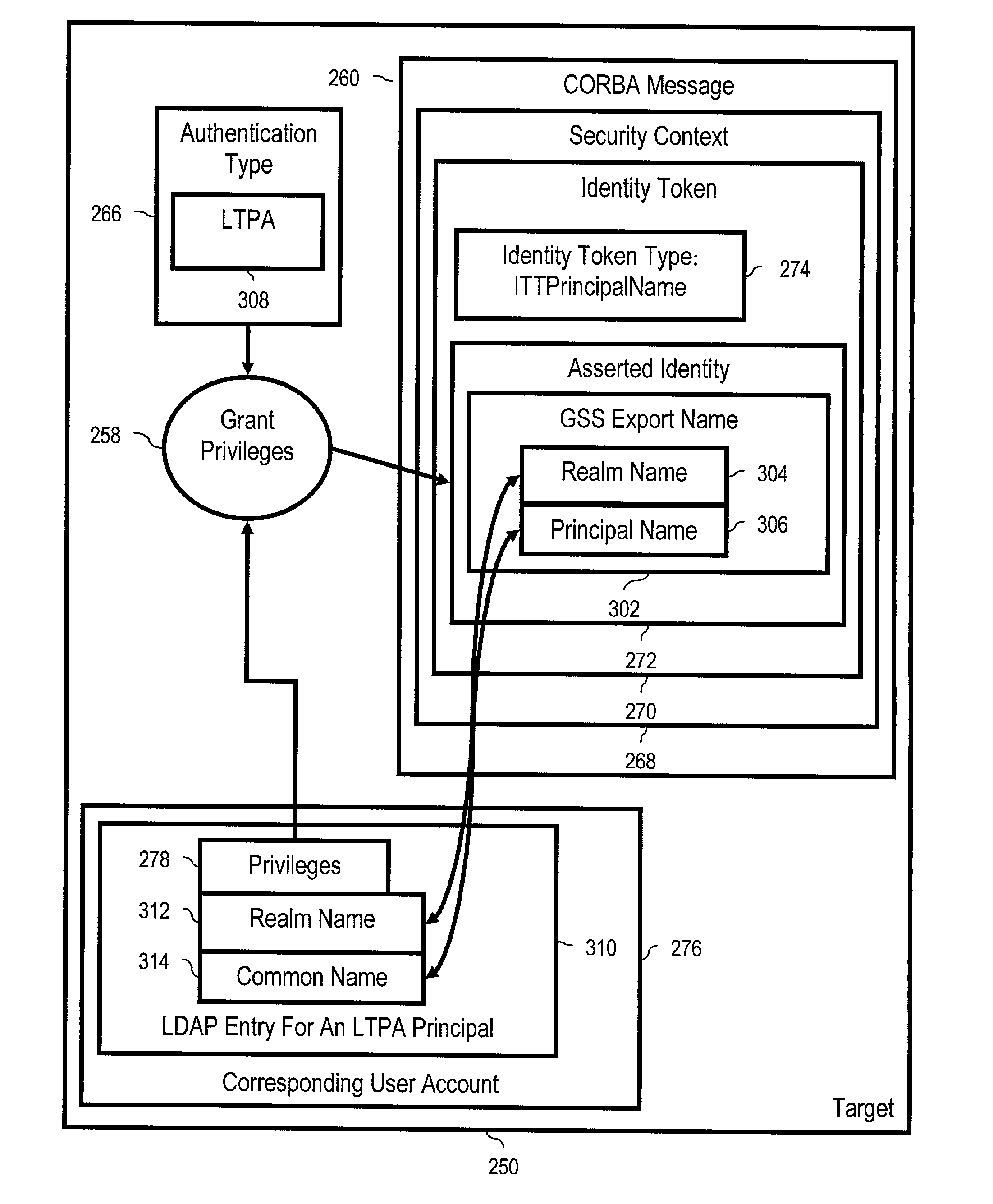
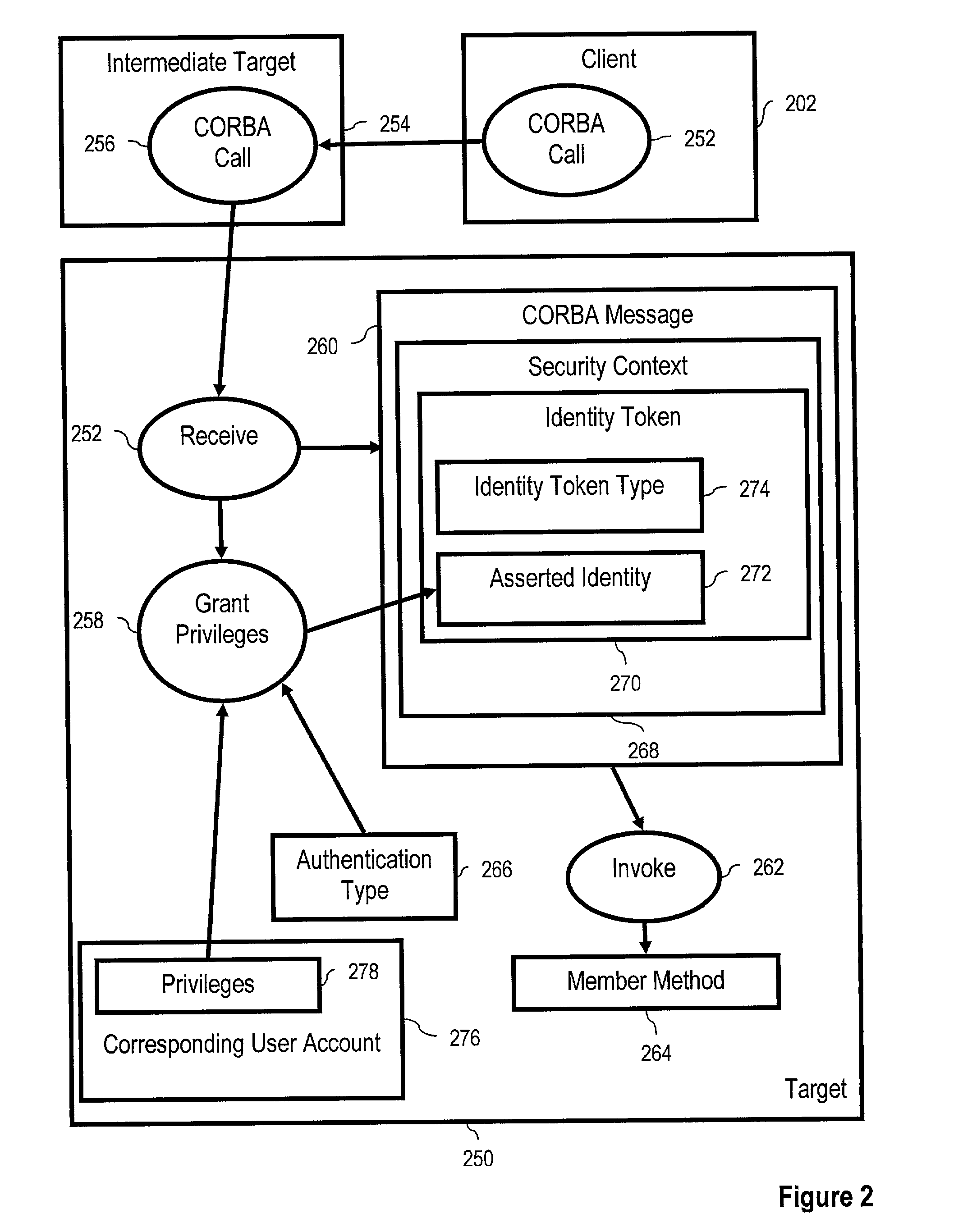
Identity token principal mapping, including receiving in a target system a CORBA message invoking a member method on the target system, the message including a security context including an identity token including an asserted identity, the identity token having an identity token type, the target system having an authentication type, and granting to the asserted identity, in dependence upon the authentication type and in dependence upon the identity token type, authorization privileges of a corresponding user account in the target system.
Owner:IBM CORP
System and method for multi-context policy management
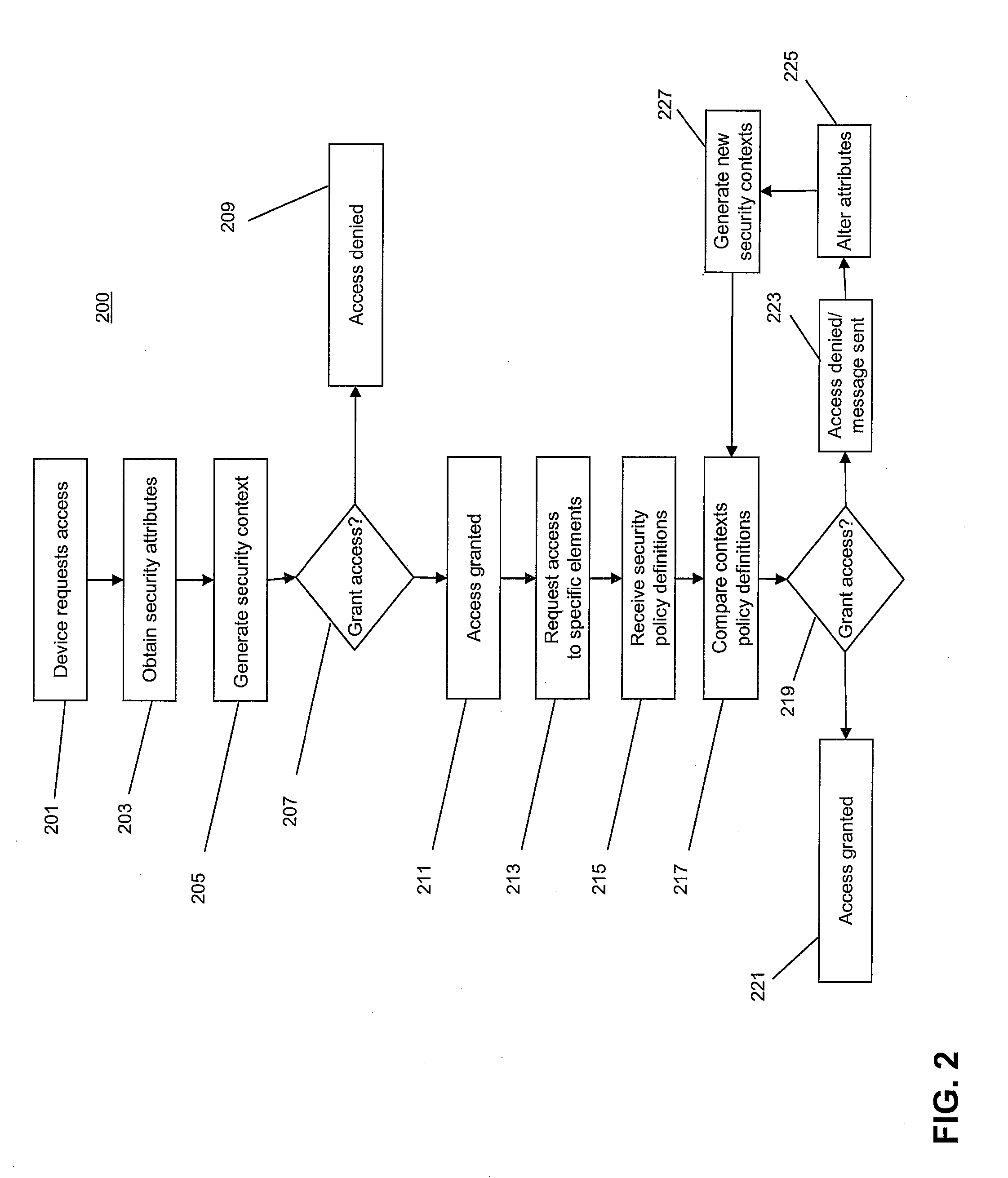
ActiveUS20080155649A1Enhanced Access ControlImprove control configurationComputer security arrangementsTransmissionSecurity policy managementSecurity context
The invention provides systems and methods for multi-context security policy management in a networked computing infrastructure. The invention includes generating a plurality of security contexts regarding different security characteristics of the communication between a computing device and the networked computing infrastructure. The computing device then requests access to at least one specific element of the computing infrastructure. The security policy definitions of the at least one specific element are compared with one or more of the security contexts to determine whether access to the specific elements should be granted.
Owner:COMP ASSOC THINK INC
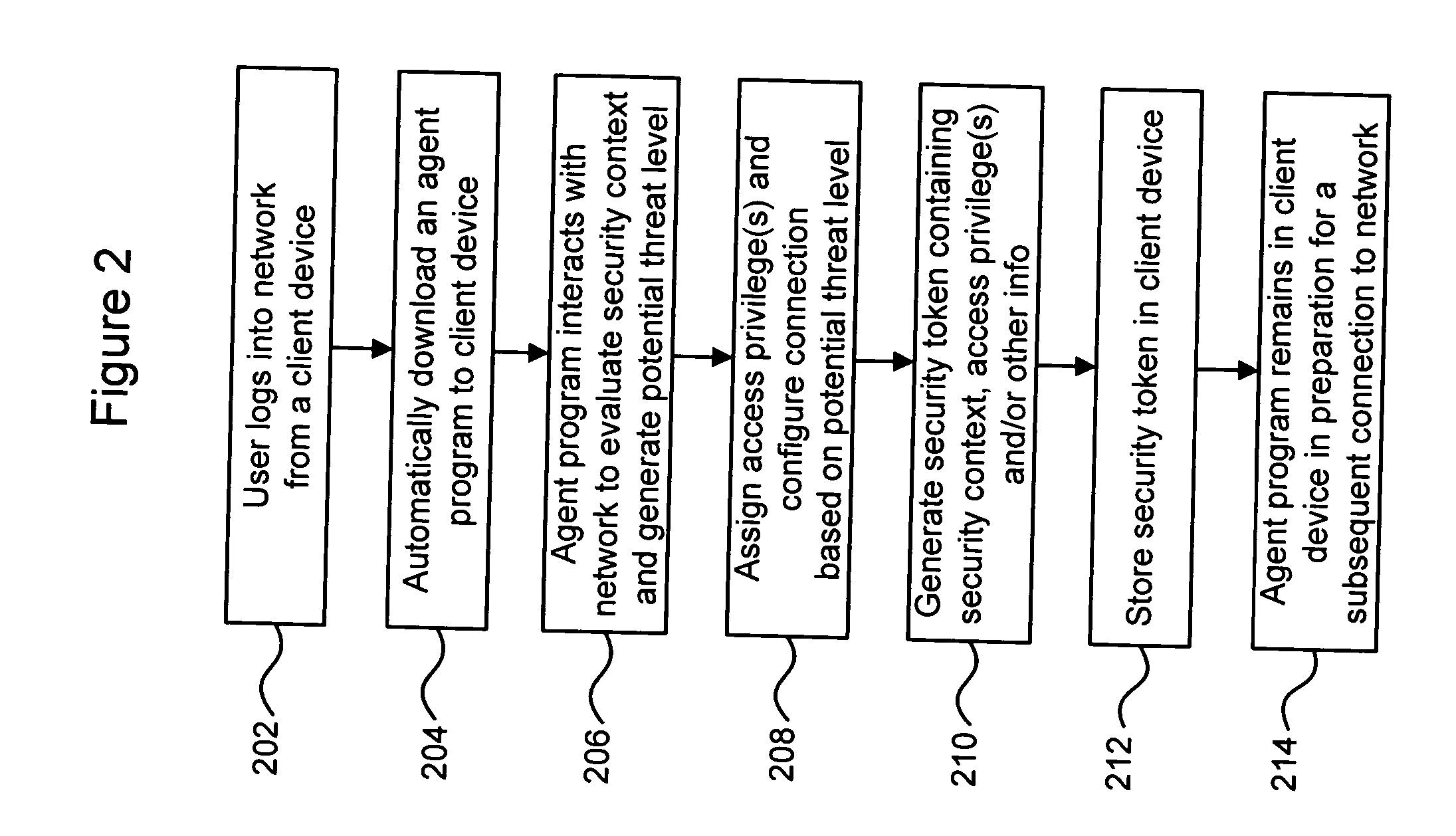
System and method for downloading security context elements governing execution of downloadable and distributable agents
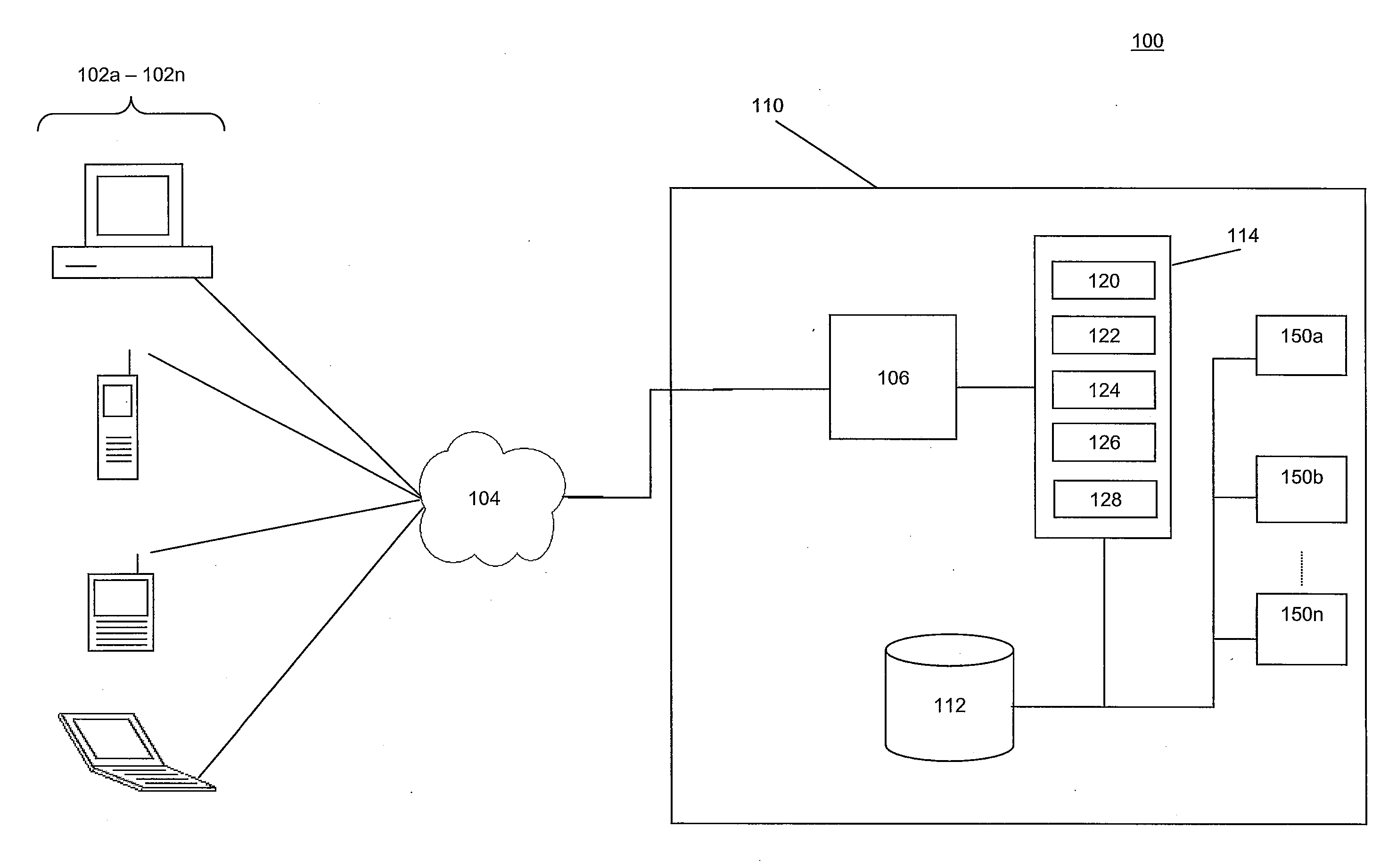
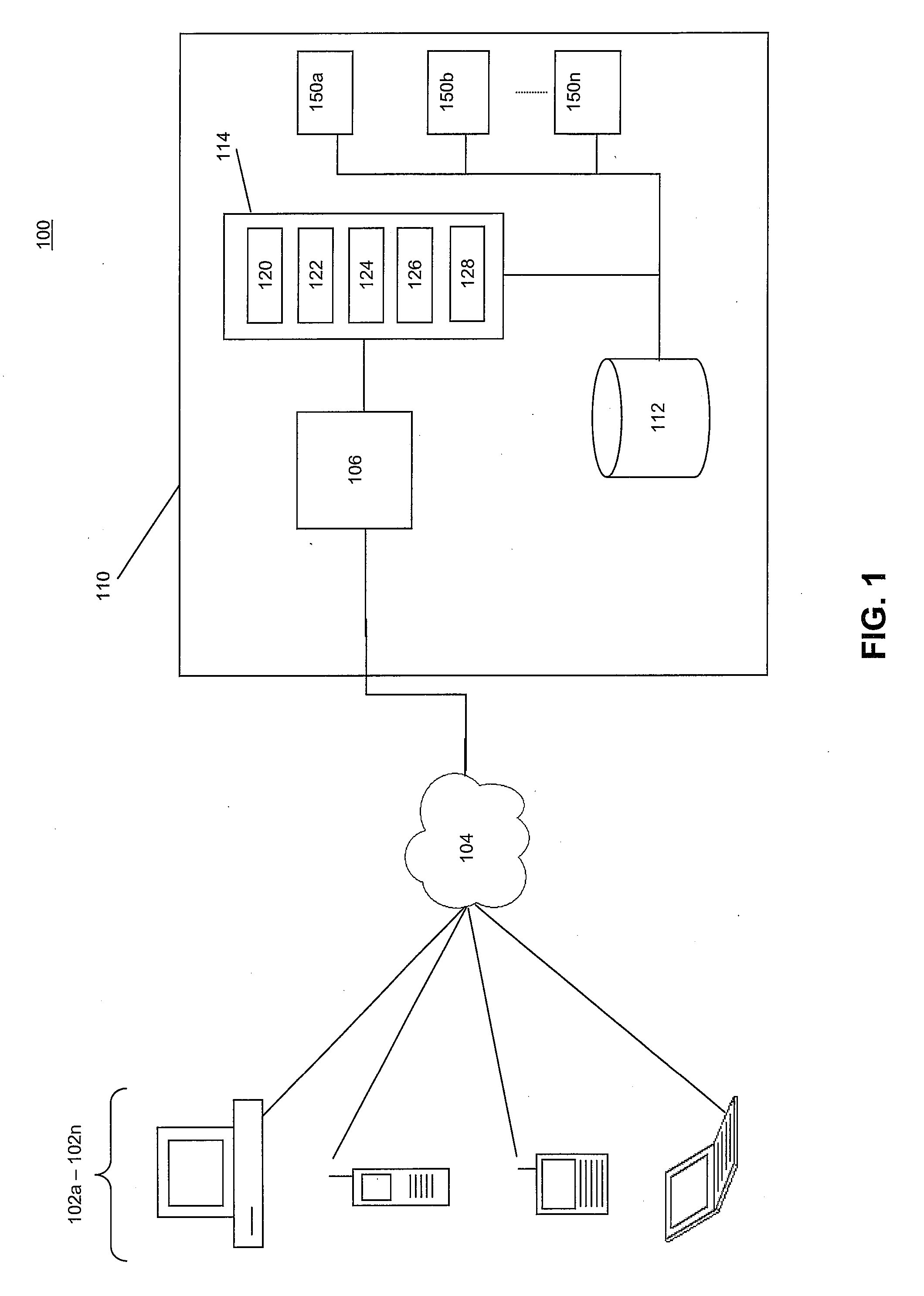
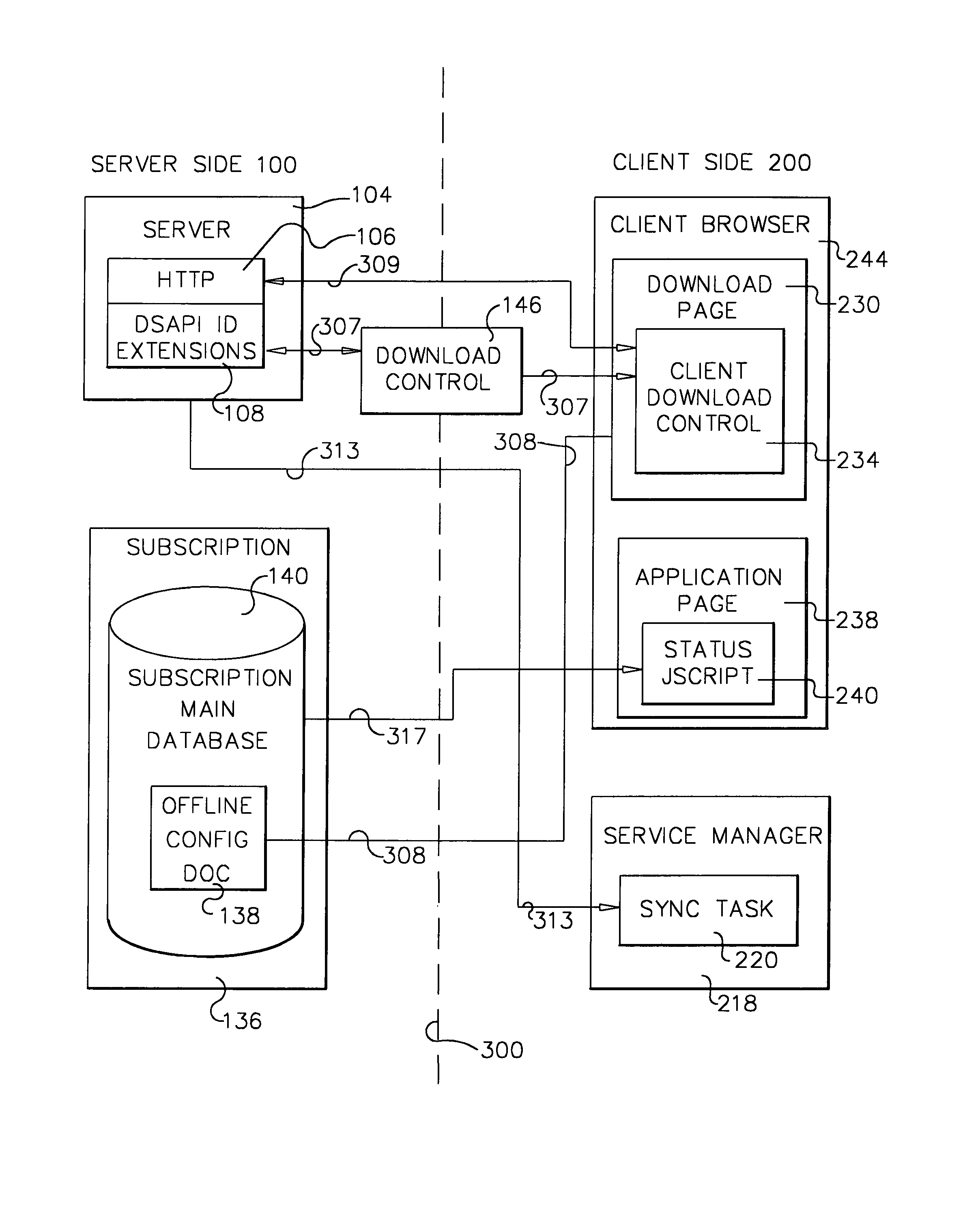
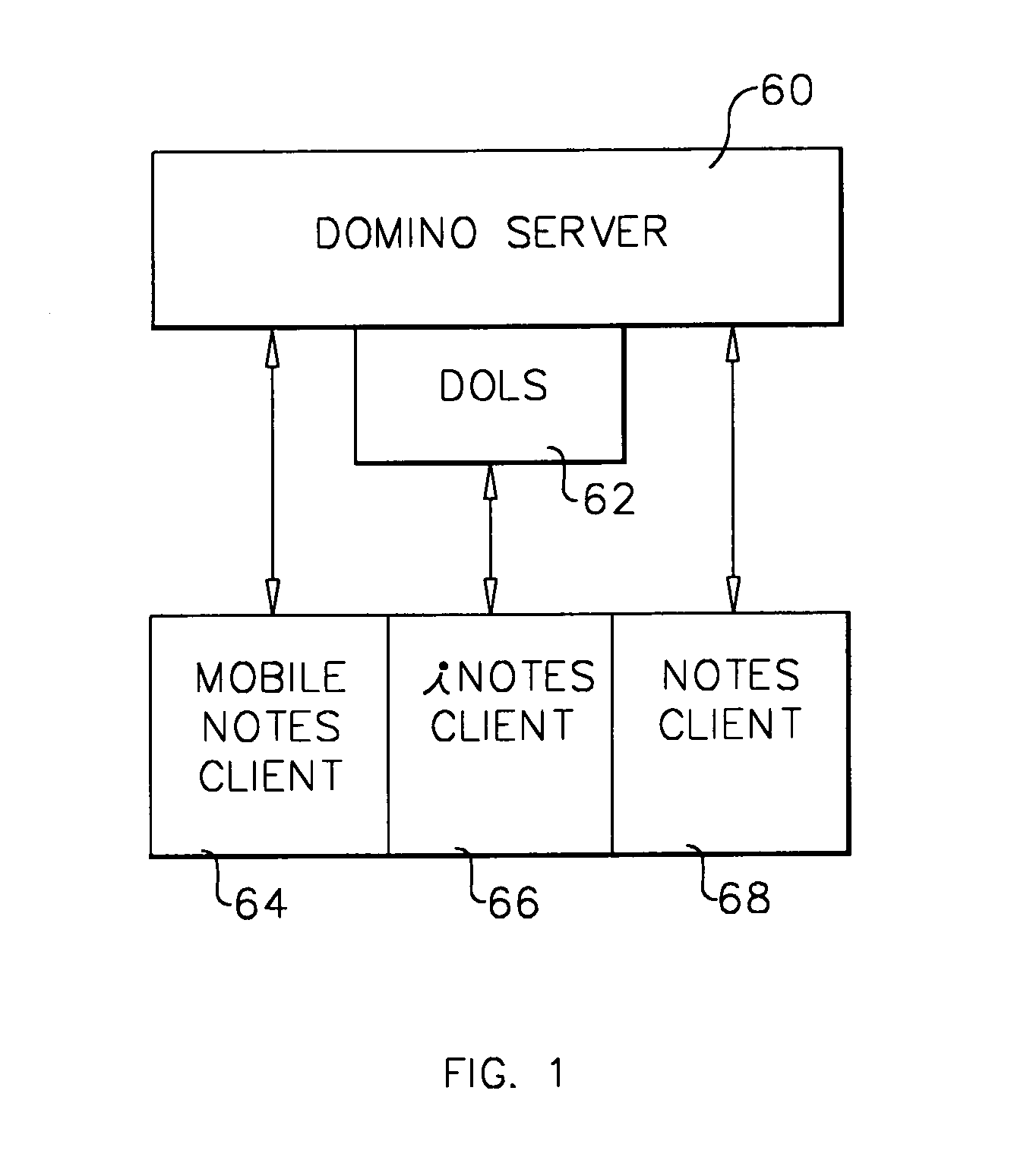
ActiveUS7360082B1Optimize workflowSynchronising transmission/receiving encryption devicesUser identity/authority verificationPartial applicationApplication software
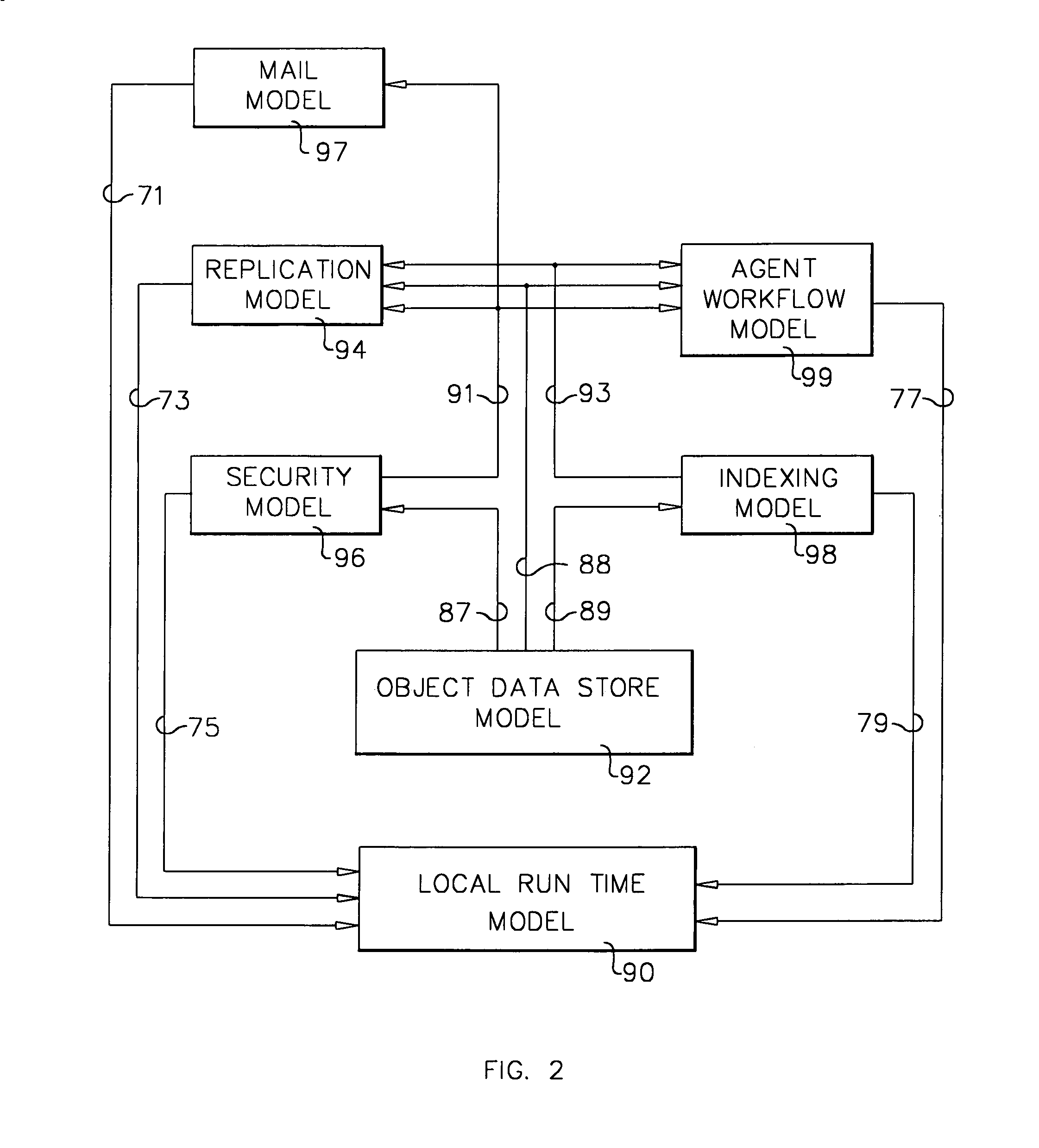
A workflow, enterprise, and mail-enabled application server and platform supports distributed computing and remote execution of web applications. Lotus Domino online services (DOLS) is used by a web site administrator to configure Internet Notes (iNotes) clients to auto download from server, thus providing iNotes clients with web access using HTTP with various browsers, and with local processing and replication. A local run time model comprises a hierarchy of models including object data store model, security model, indexing model, replication model, agent workflow model and mail model. DOLS provides a layered security model that allows flexibility for controlling access to all or part of an application. The highest level of security is managed through a database access control list (ACL). Further refinements within the security model provide access to specific documents, and their views, forms or folders, and include read access lists, write access lists, form access lists and readers and authors fields.
Owner:GOOGLE LLC
Method for secure delegation of trust from a security device to a host computer application for enabling secure access to a resource on the web
ActiveUS20070056025A1Easy accessDigital data processing detailsUser identity/authority verificationWeb serviceApplication software
Secure authentication of a user on a host computer to a web server including a security device acquiring trust or a security context from the web server. The security device is operable of providing an X.509 certificate to a browser plug-in on the host computer. The browser plug-in on the host computer performing authentication of the security device and in response providing user credentials to the security device. The security device performing authentication of the user and requests a security context from the web server. In response, the web server provides a security context to the security device. The security device delegates the web server trust by transmitting the context to the host computer and enabling the user to securely access resources on the web server.
Owner:GEMPLU
Security context sharing
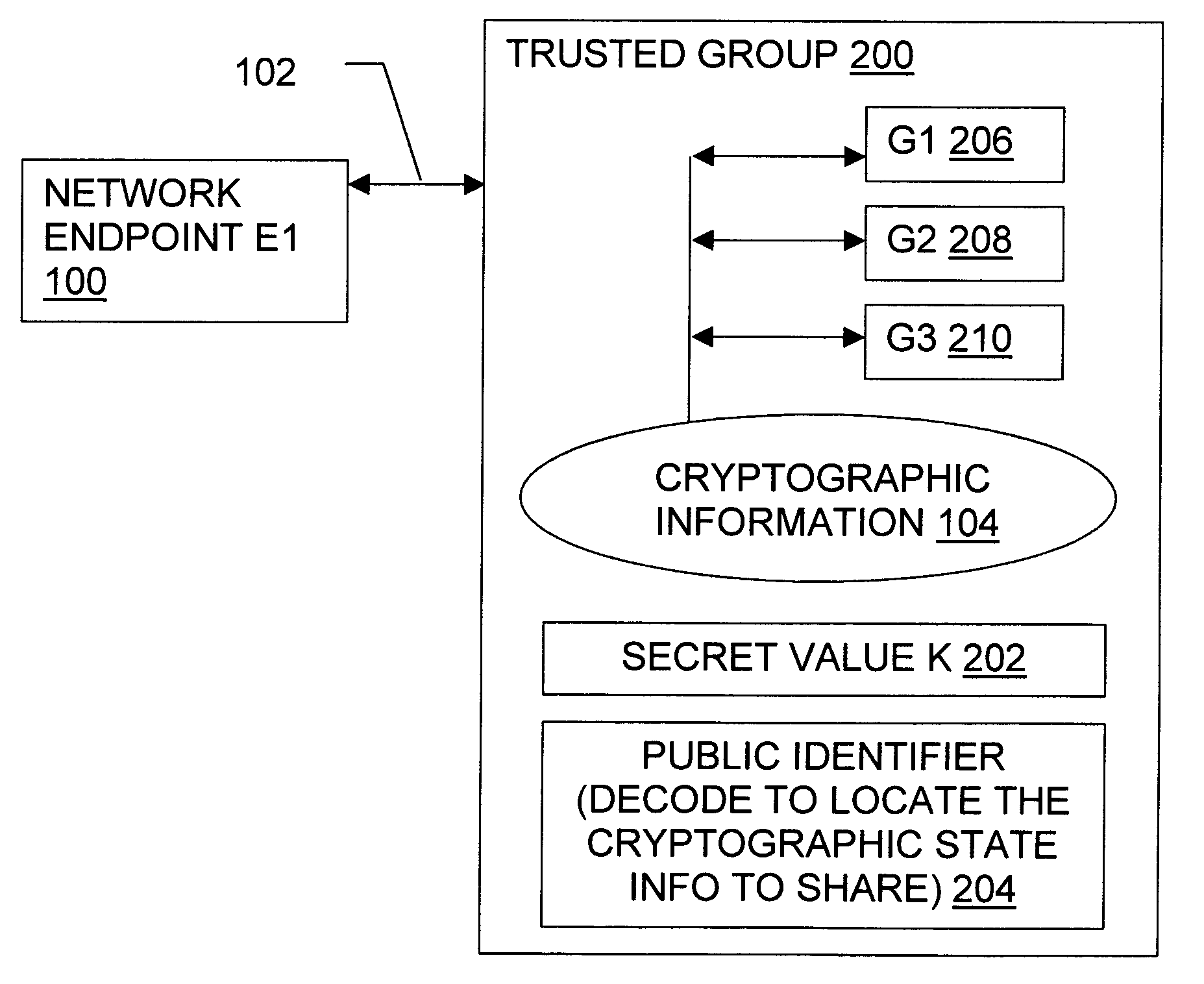
ActiveUS7240202B1Expand accessUser identity/authority verificationSecret communicationHash functionSecurity context
Owner:APPLE INC
Method and System for User Management of Authentication Tokens
ActiveUS20090293108A1Digital data processing detailsMultiple digital computer combinationsData processing systemWeb site
A computer implemented method, a computer program product, and a data processing system manage a set of federated log-in authentications at secure web sites. A client logs into a security context using a first alias from a list of existing federated single sign-on authentication aliases associated with an account. Responsive to logging into the security context, the client can receive the list of existing federated single sign-on authentication aliases. The client can then manage the list of authentication aliases.
Owner:DAEDALUS BLUE LLC
Providing context-based visibility of cloud resources in a multi-tenant environment
InactiveUS20150200958A1Memory loss protectionError detection/correctionVisibilityEnvironment of Albania
A secure tag generation service is associated with a cloud infrastructure. This service establishes a security context for a particular cloud tenant based on a tenant's security requirements, one or more cloud resource attributes, and the like. The security content is encoded into a data structure, such as a tag that uniquely identifies that security context. The tag is then encrypted. The encrypted tag is then propagated to one or more cloud management services, such as a logging service. When one or more cloud resources are then used, such use is associated with the encrypted security context tag. In this manner, the encrypted tag is used to monitor activities that are required to meet the security context. When it comes time to perform a security or compliance management task, any cloud system logs that reference the encrypted security context tag are correlated to generate a report for the security context.
Owner:IBM CORP
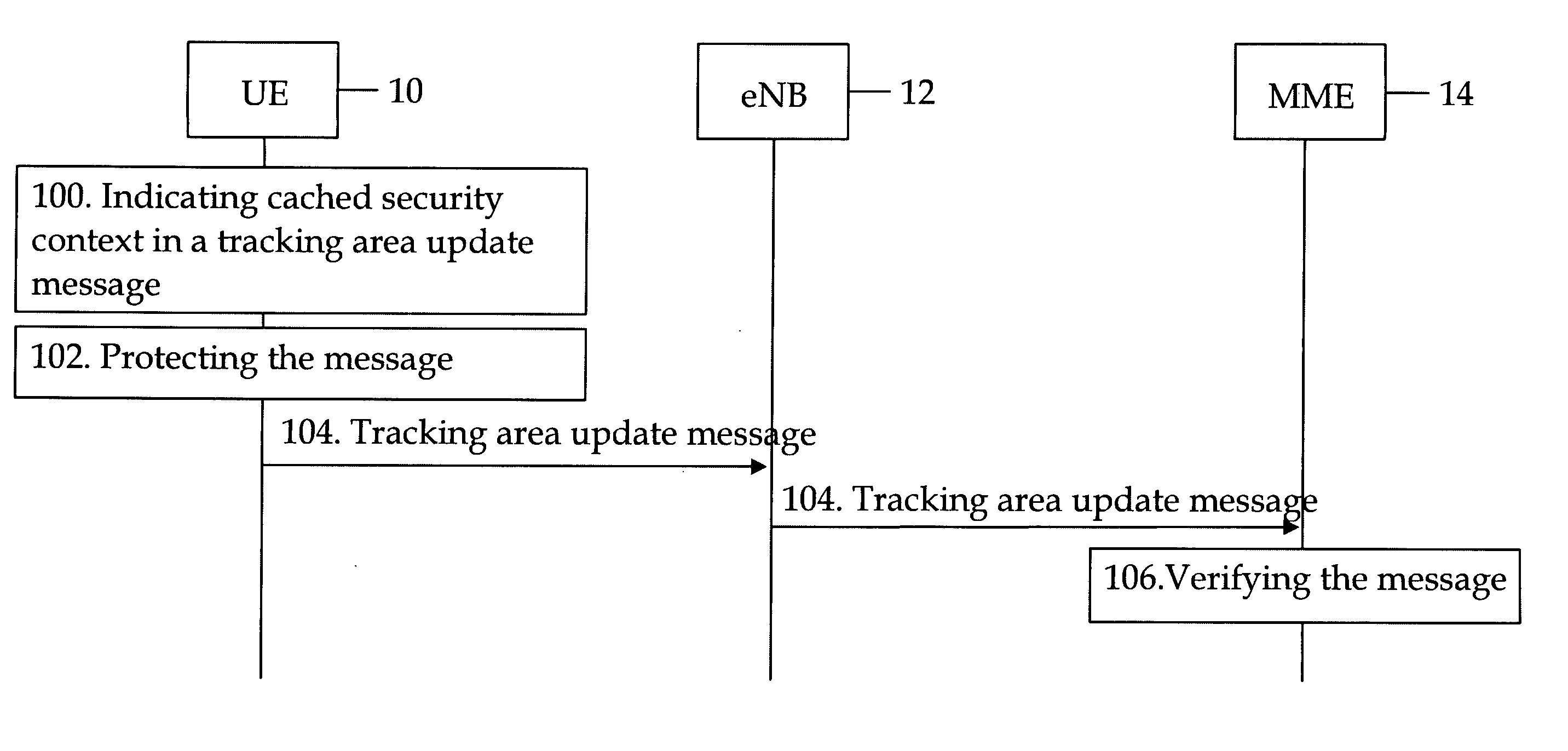
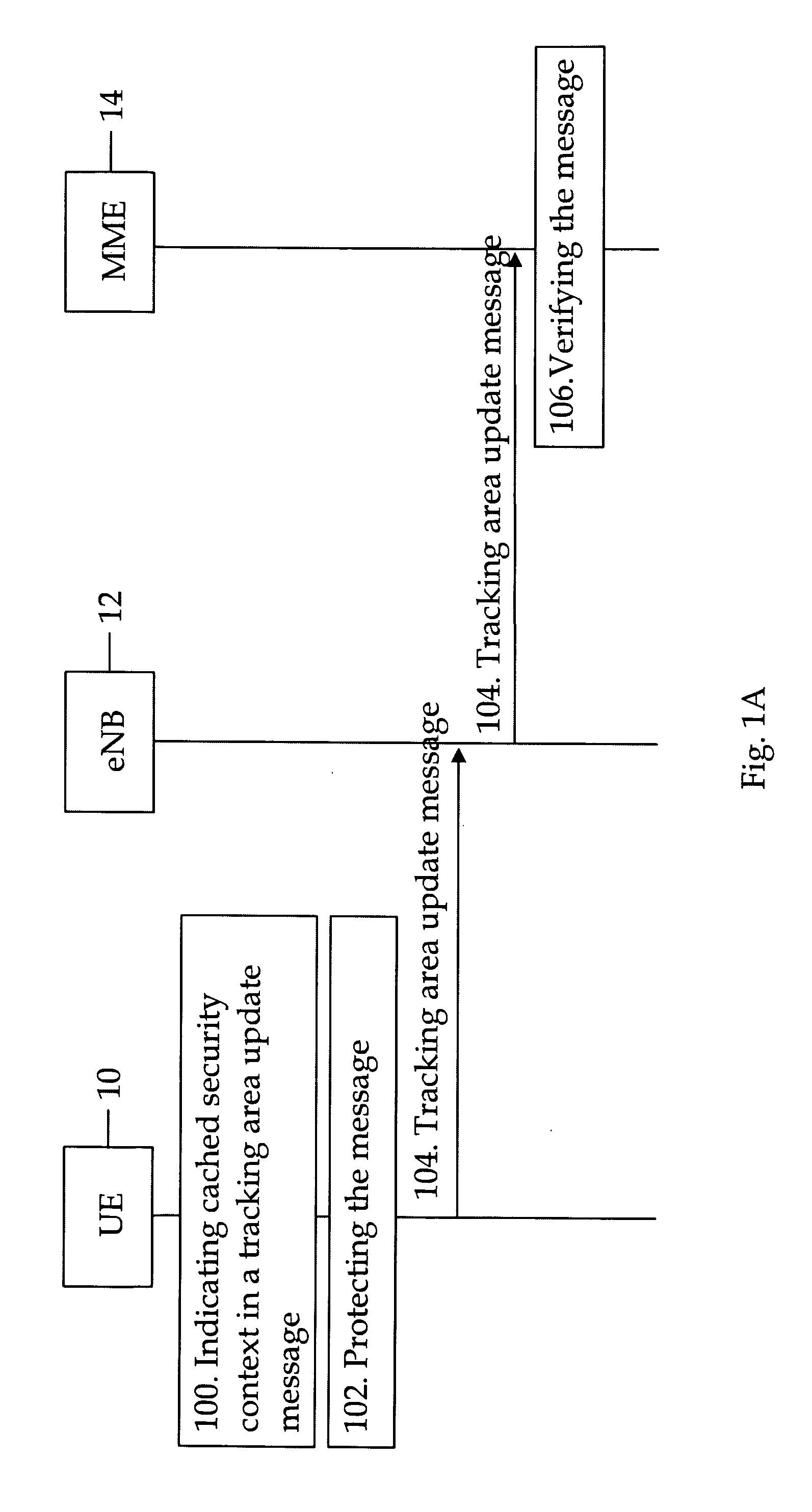
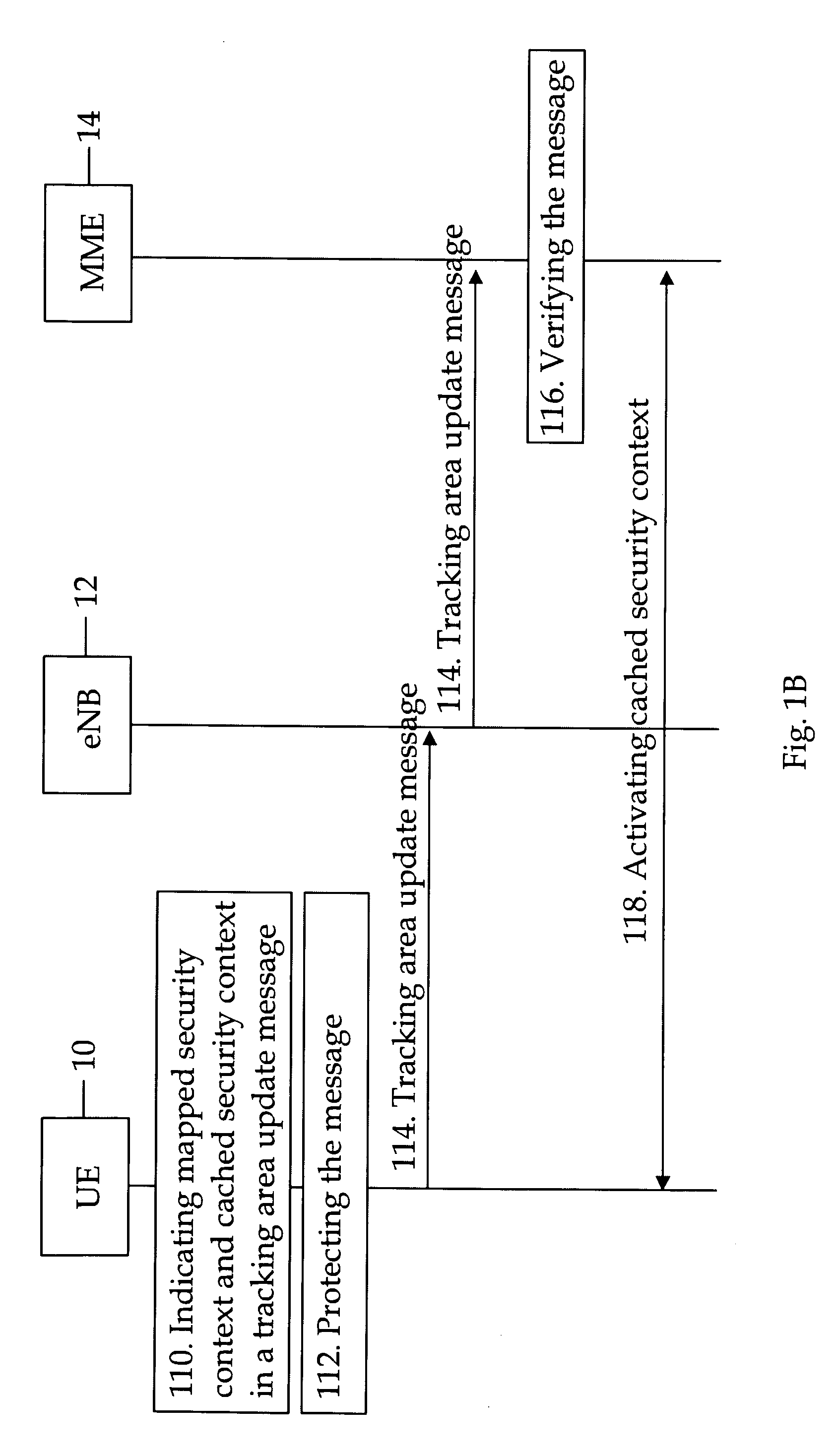
Intersystem mobility security context handling between different radio access networks
ActiveUS20090271623A1User identity/authority verificationSecurity arrangementRadio access networkMobile security
A method and apparatus for intersystem mobility security context handling between different radio access networks which can include a receiver configured to receive a tracking area update message from a user terminal. The message can include a first key identifier configured to identify a mapped security context and a second key identifier configured to identify a cached security context. A verifier can be configured to verify the tracking area update message with a key identified by the first or second key identifier.
Owner:NOKIA TECHNOLOGLES OY
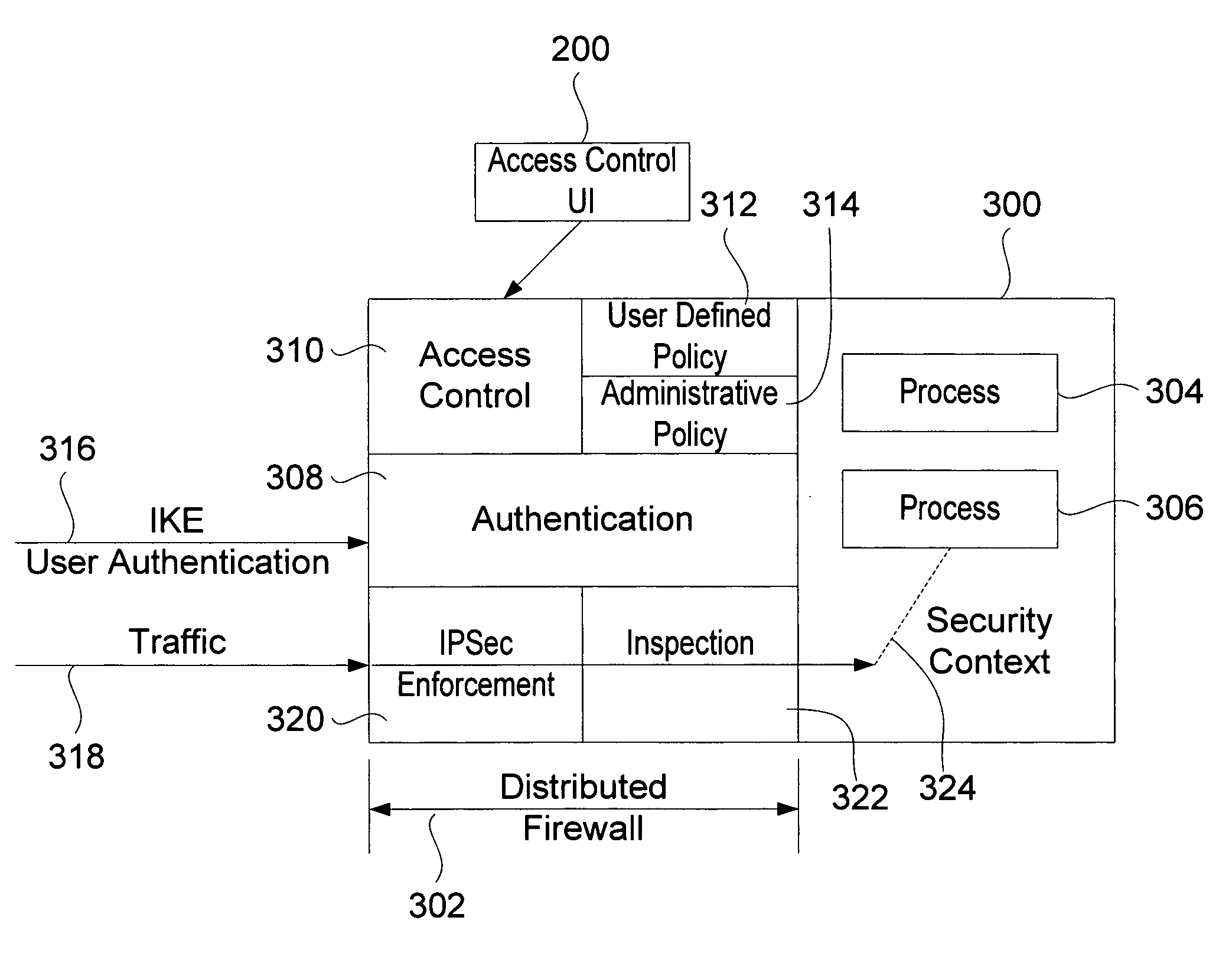
Method for providing user authentication/authorization and distributed firewall utilizing same
InactiveUS20060015935A1Multiple digital computer combinationsProgram controlKey exchangeThe Internet
The distributed firewall performs user authentication at a first level to establish a user security context for traffic from that user, and an authority context provides authorization for subsequent traffic. This authority context may be based on an underlying policy for particular types of traffic, access to particular applications, etc. Additionally, the system includes the ability to allow a user / process / application to define its own access control. The linking of the user security context from the traffic to the application is accomplished by enabling IPSec on a socket and forcing the socket to be bound in exclusive mode. The most common policy definitions may be included by default. Extensions of the Internet key exchange protocol (IKE) to provide the desired user authentication plus application / purpose are also provided. The architecture includes pluggable authorization module(s) that are called after IKE has successfully authenticated the peer, but before the connection is allowed to complete.
Owner:MICROSOFT TECH LICENSING LLC
Establishment of security context
InactiveUS7533265B2User identity/authority verificationComputer security arrangementsCommunications securityInternet privacy
The present invention provides for maintaining security context during a communication session between applications, without having to have executable code in either application for obtaining or generating a security context token (SCT) used to secure the communication. On a service side, a configuration file is provided that can be configured to indicate that automatic issuance of a SCT is enabled, thereby allowing a Web service engine to generate the SCT upon request. On the client side, when a message is sent from the client application to the service application, a policy engine accesses a policy that includes assertions indicating that a SCT is required for messages destined for the Web service application. As such, the policy engine requests and receives the SCT, which it uses to secure the message.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com