Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
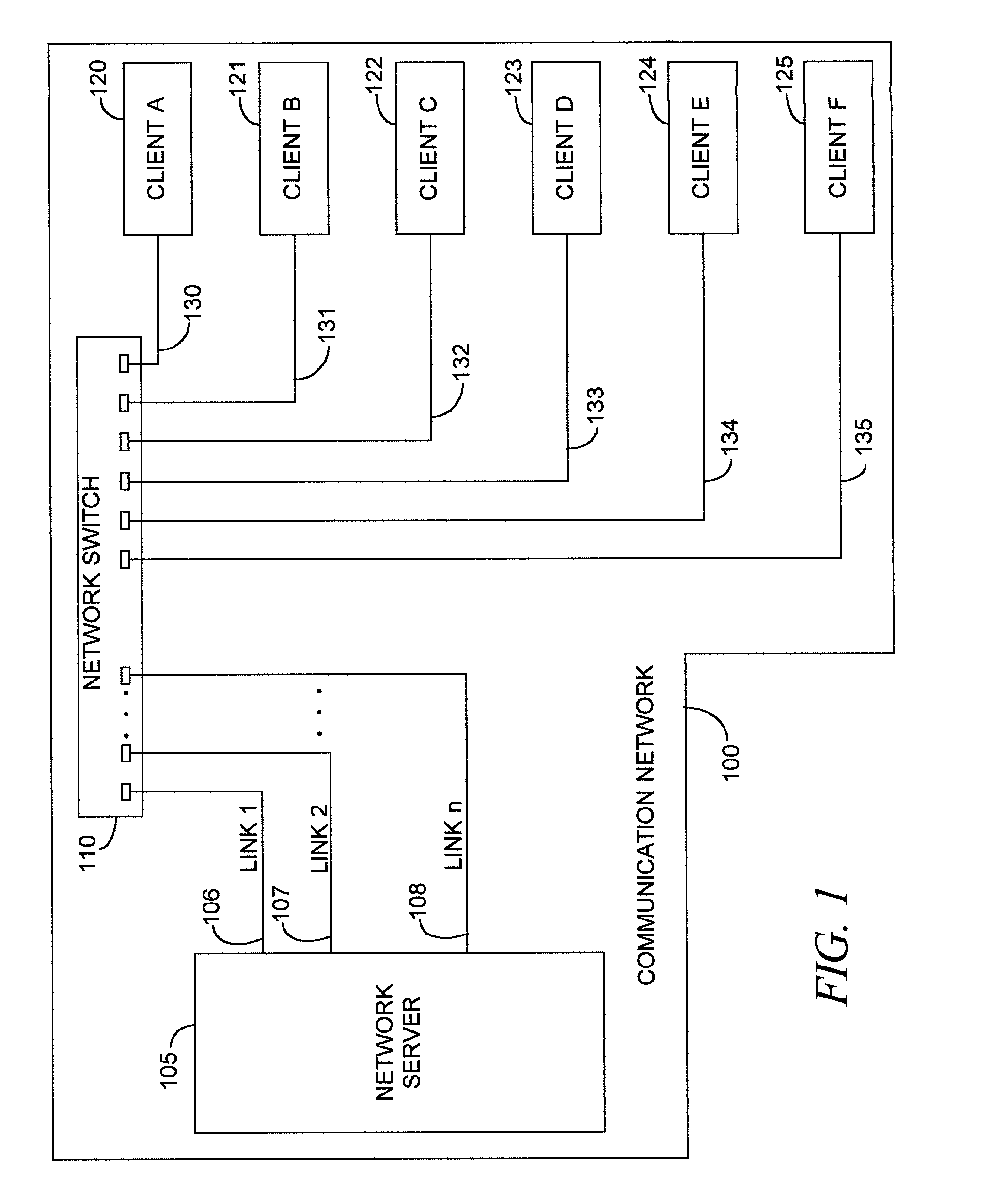
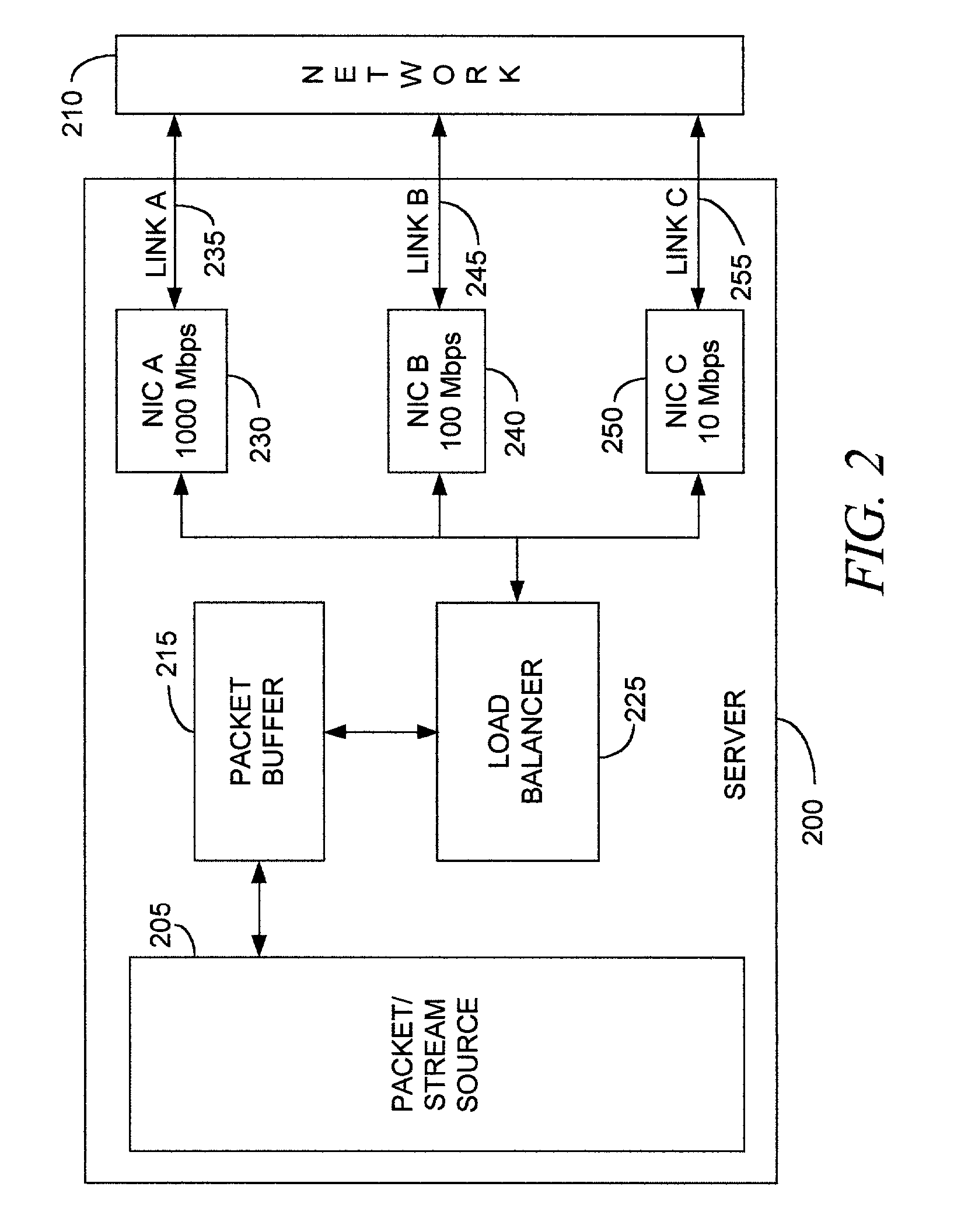
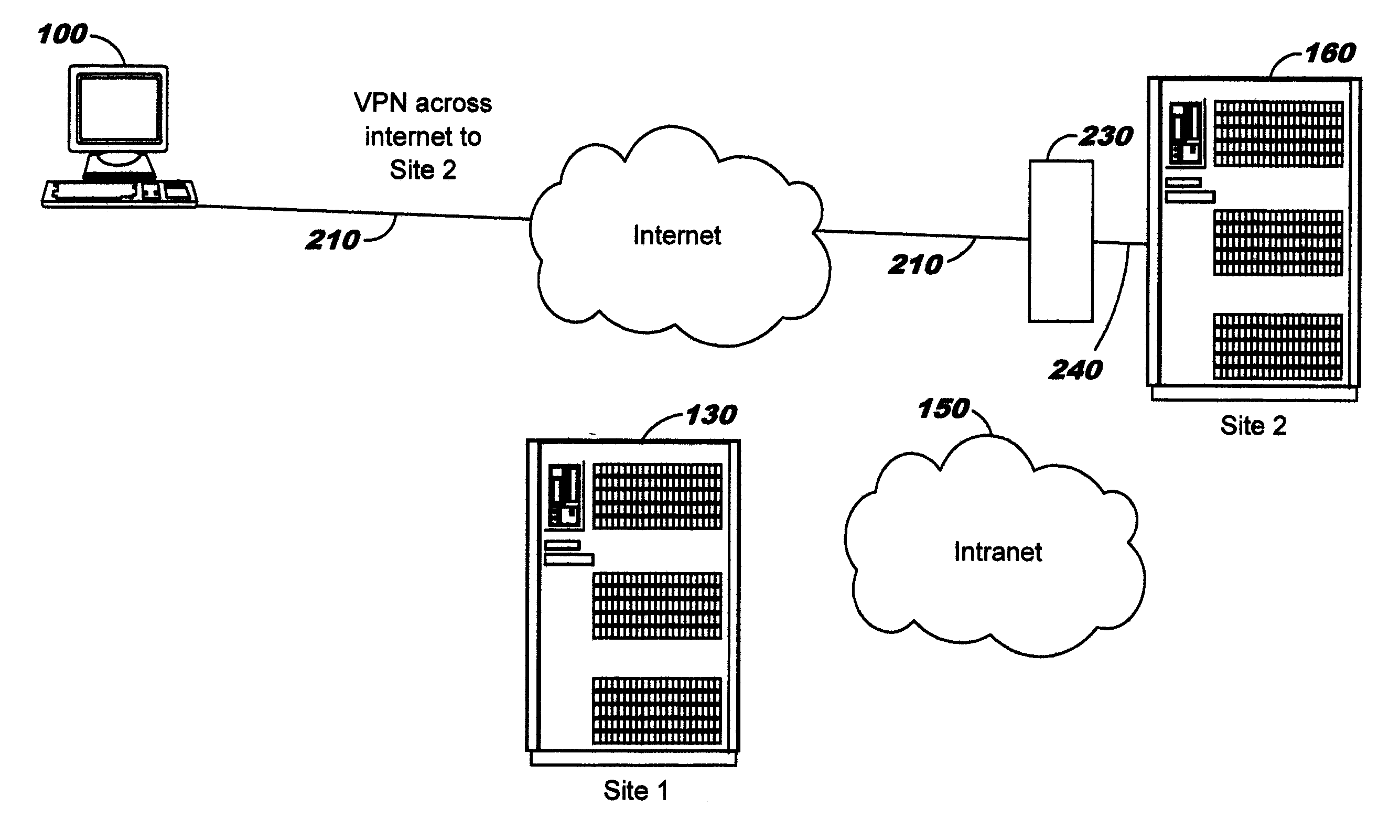
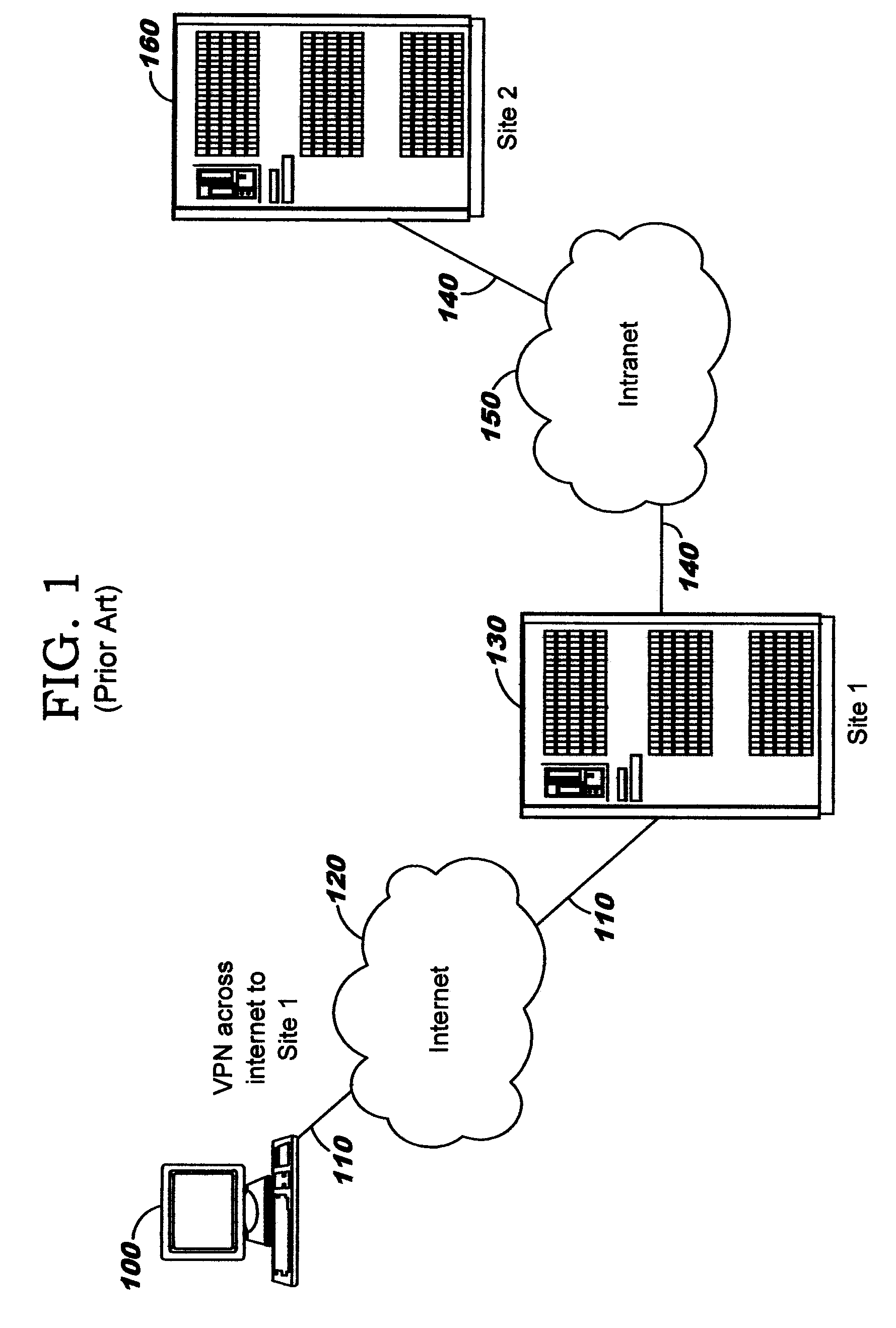
620 results about "Dynamical network" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
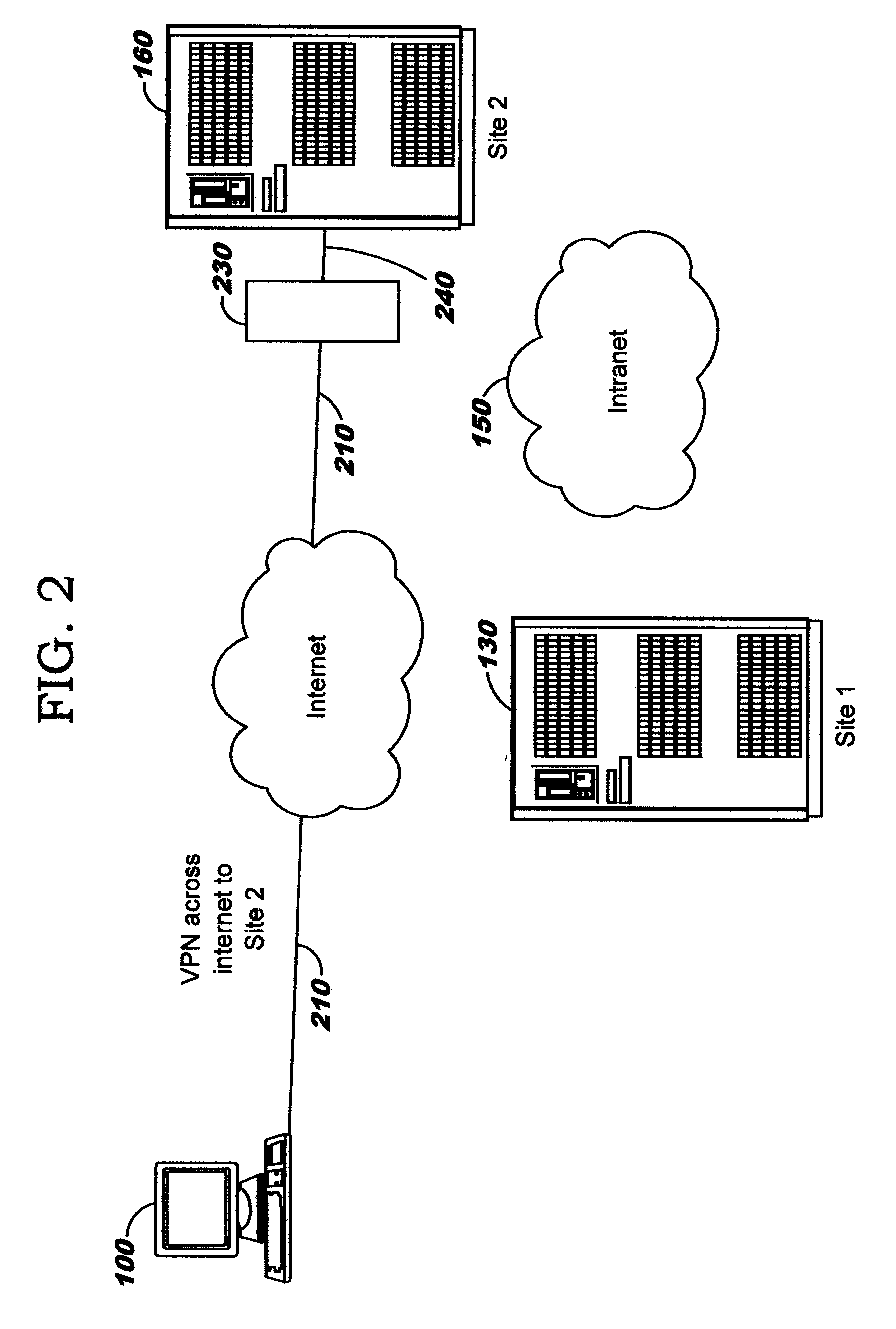
Dynamic Network Solutions (DNS), established in 1996, is a technology consulting firm with professionals committed to serving Maryland, Virginia, D.C., and Florida. Our business currently has over 150 various clients whom we serve in various ways.
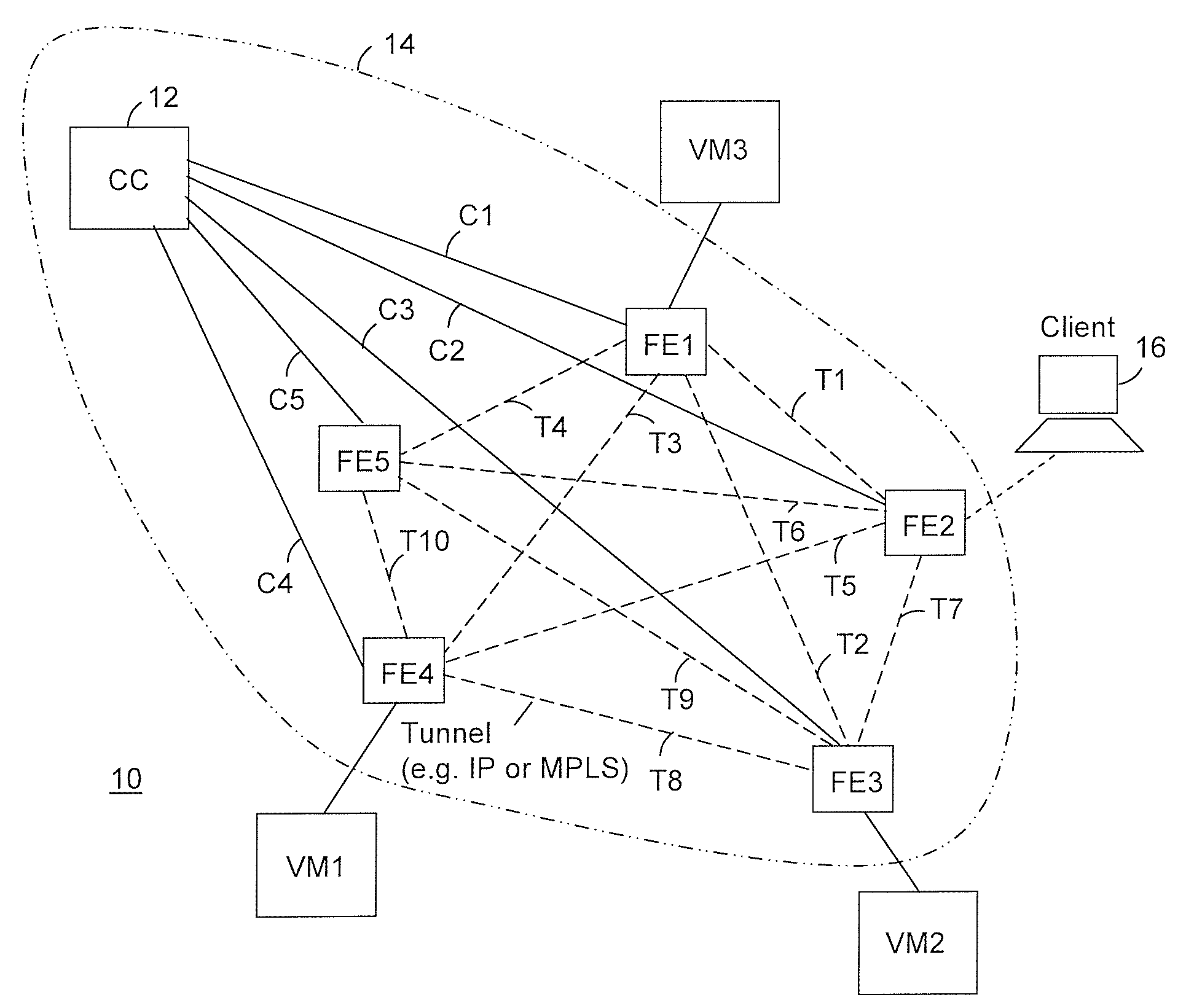
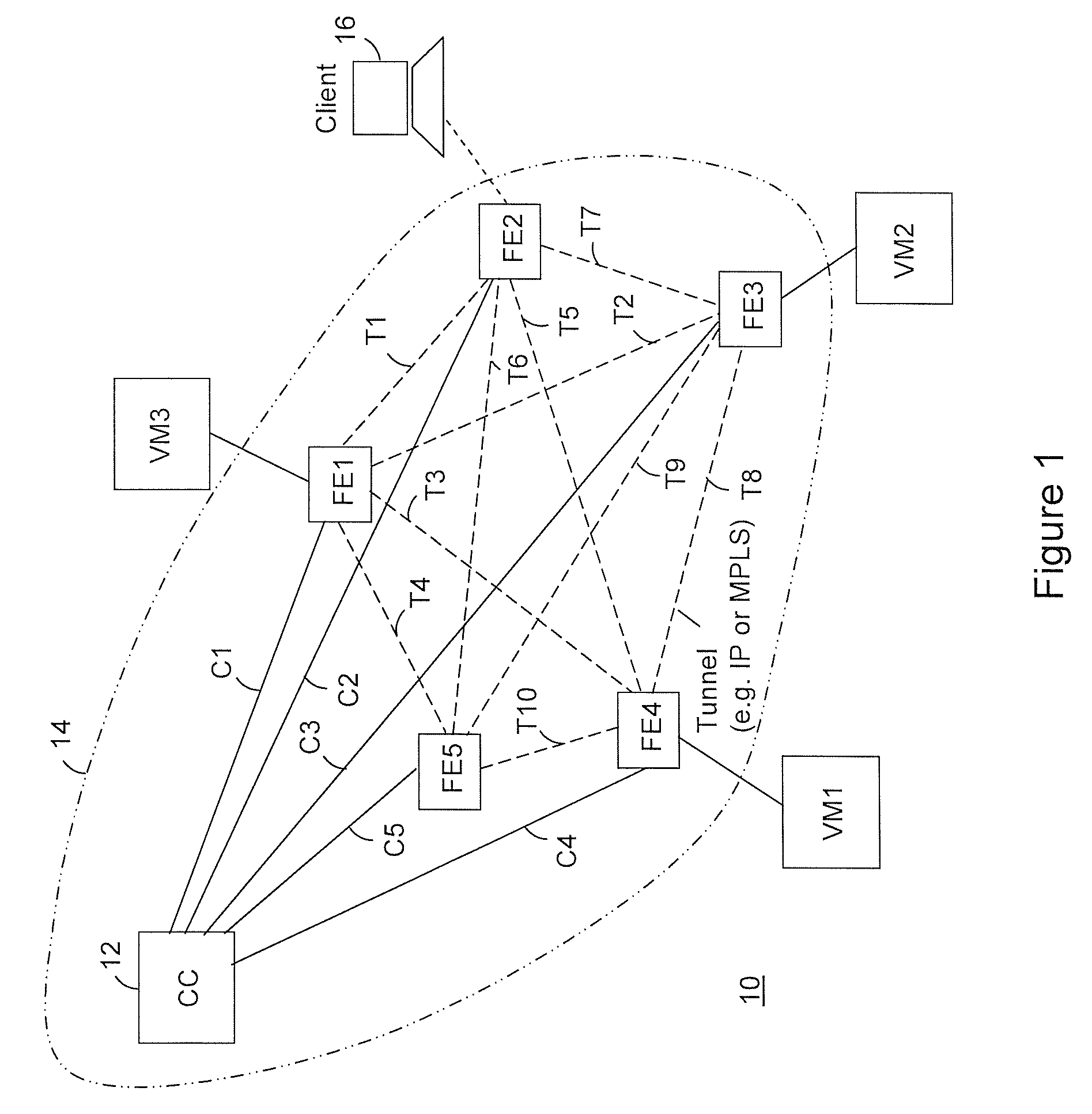
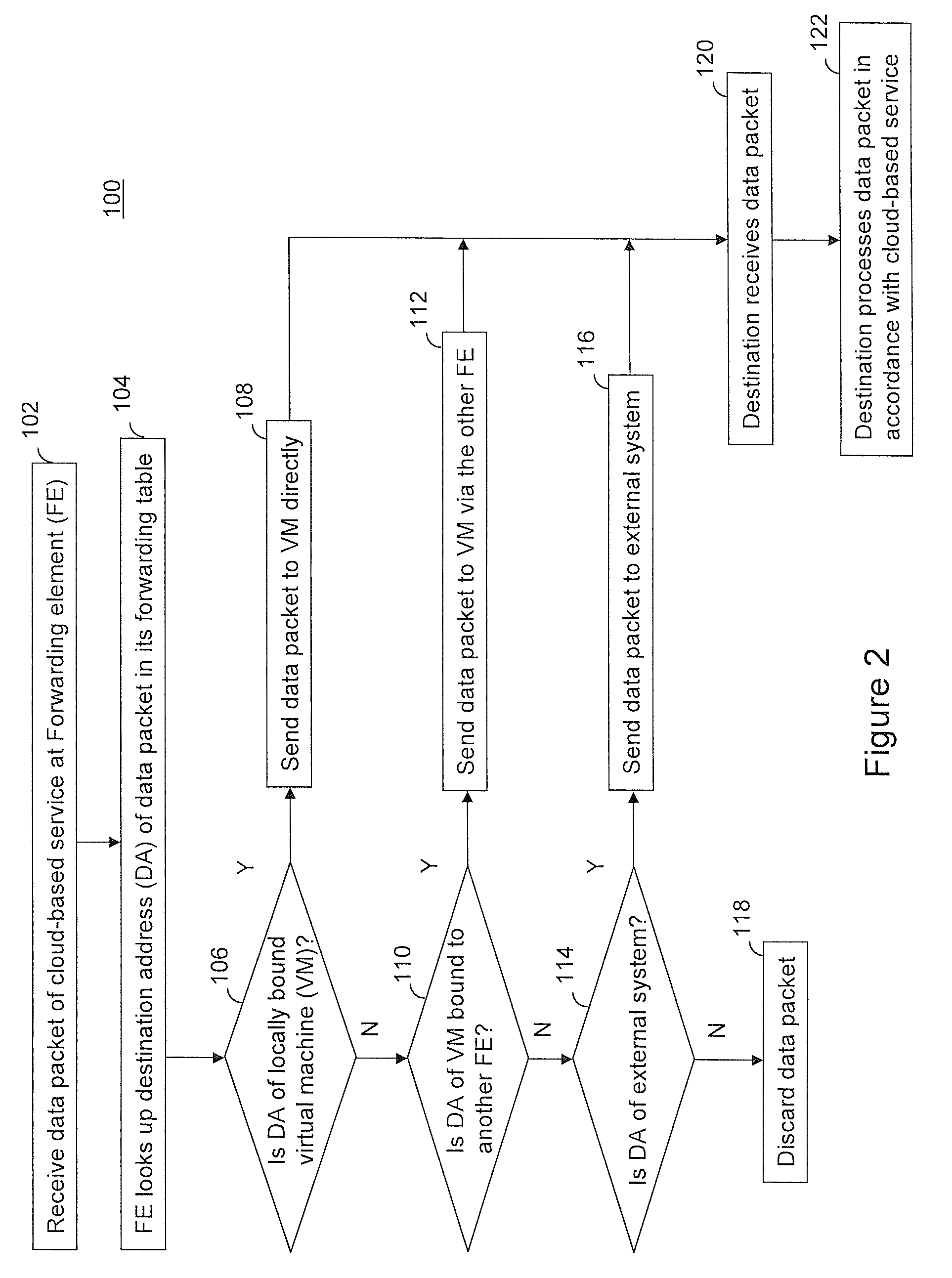
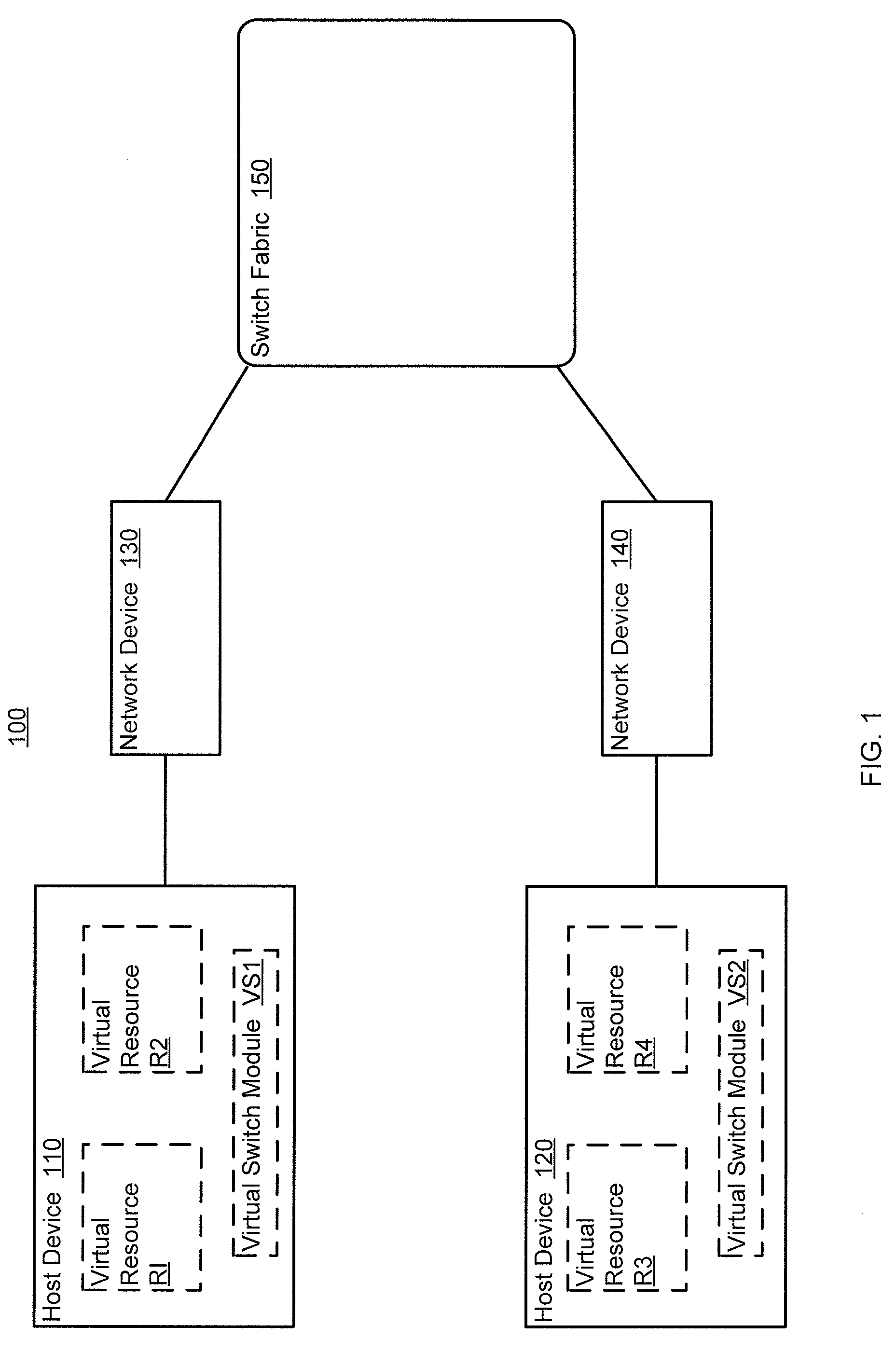
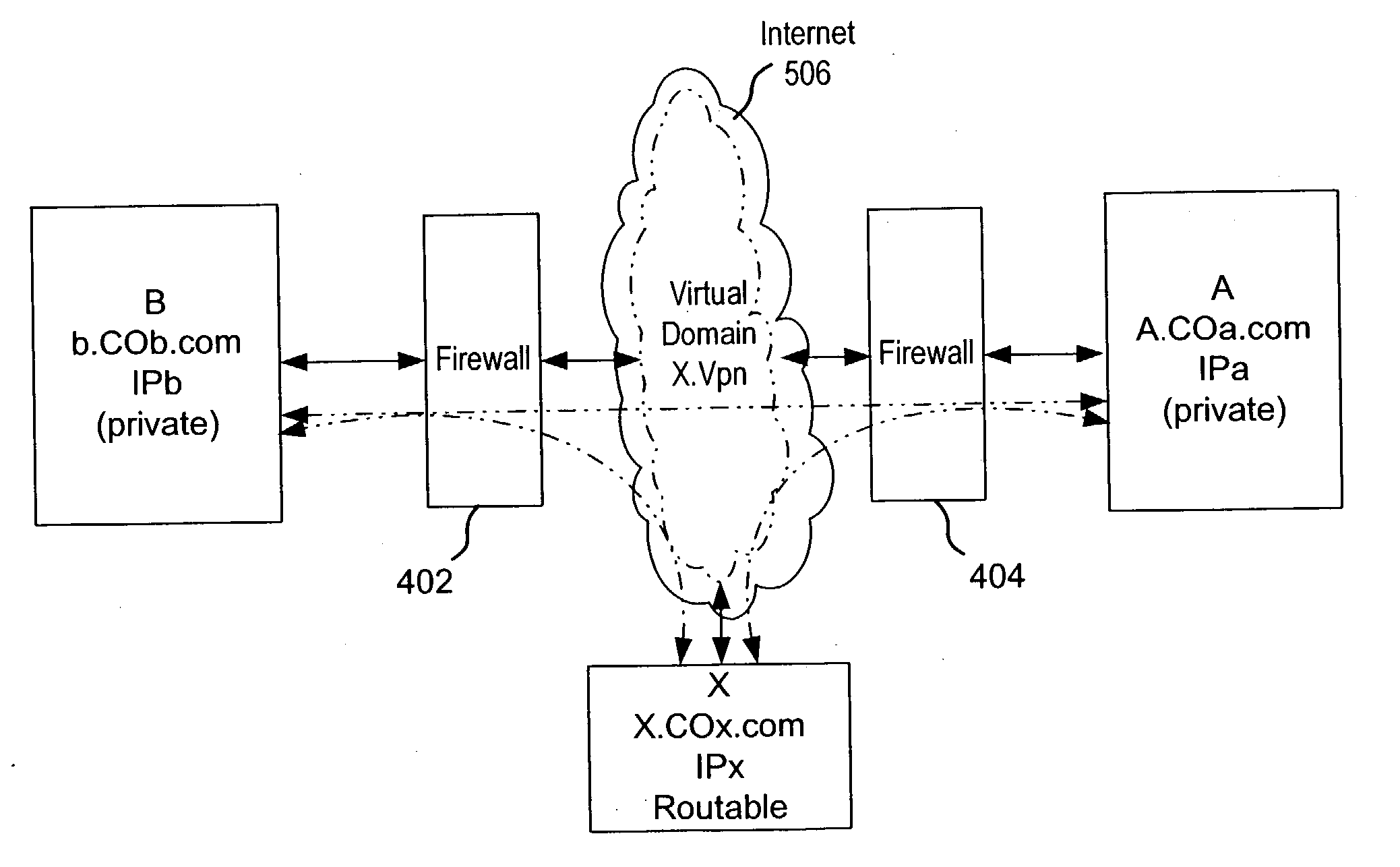
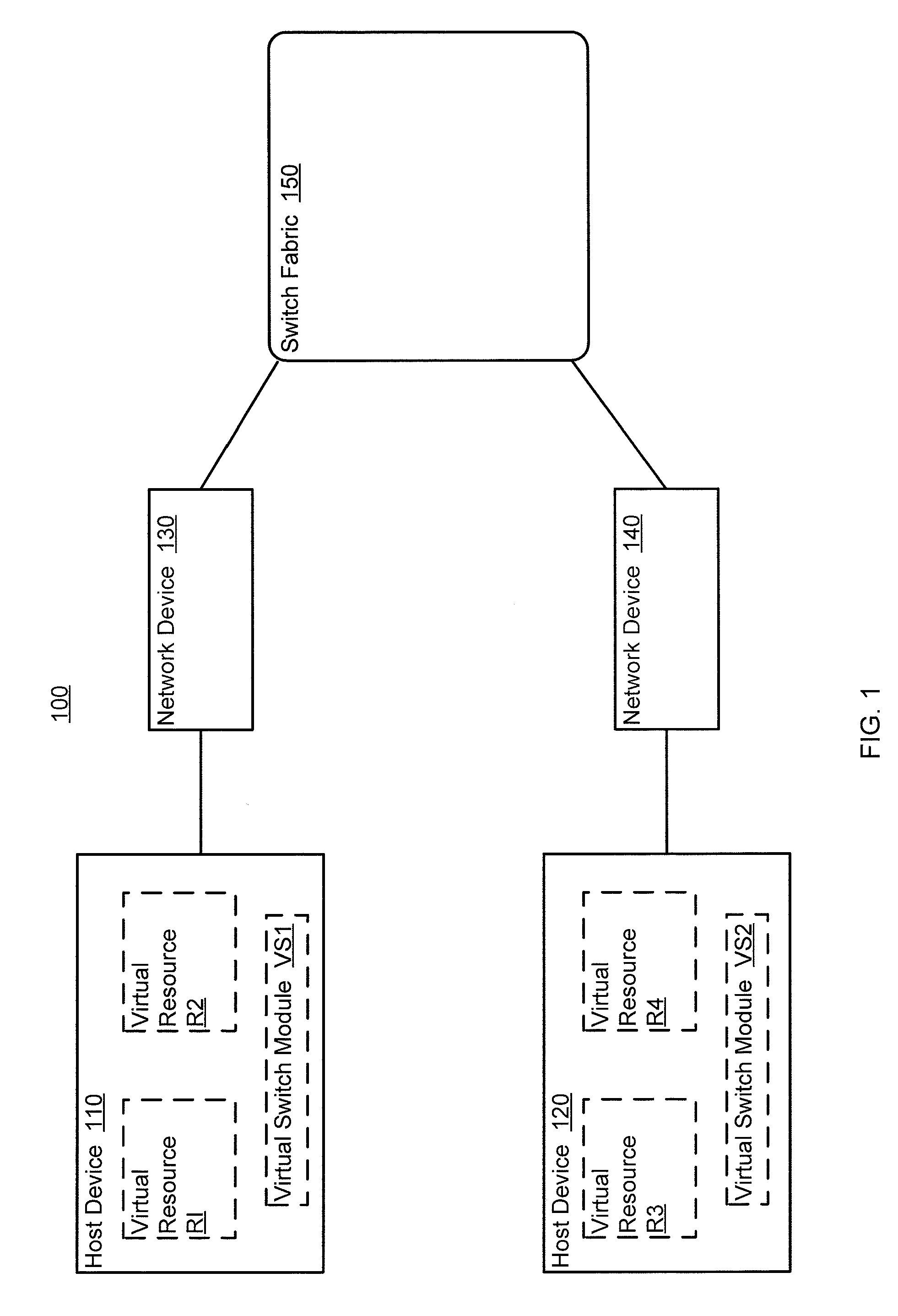
Providing cloud-based services using dynamic network virtualization
ActiveUS20100322255A1Network supportFaster service provisioningData switching by path configurationProgram controlCloud baseIp address
The invention is directed to providing cloud-based services using dynamic network virtualization. Embodiments of the invention provide a cloud-based service over a system that has a dynamic network virtualization architecture. The architecture includes a set of distributed forwarding elements with centralized control, and at least one virtual machine that is bound to one of the forwarding elements. These features enable the virtual machine to be migrated across a wide area network while maintaining its original IP address and service continuity.
Owner:ALCATEL LUCENT SAS
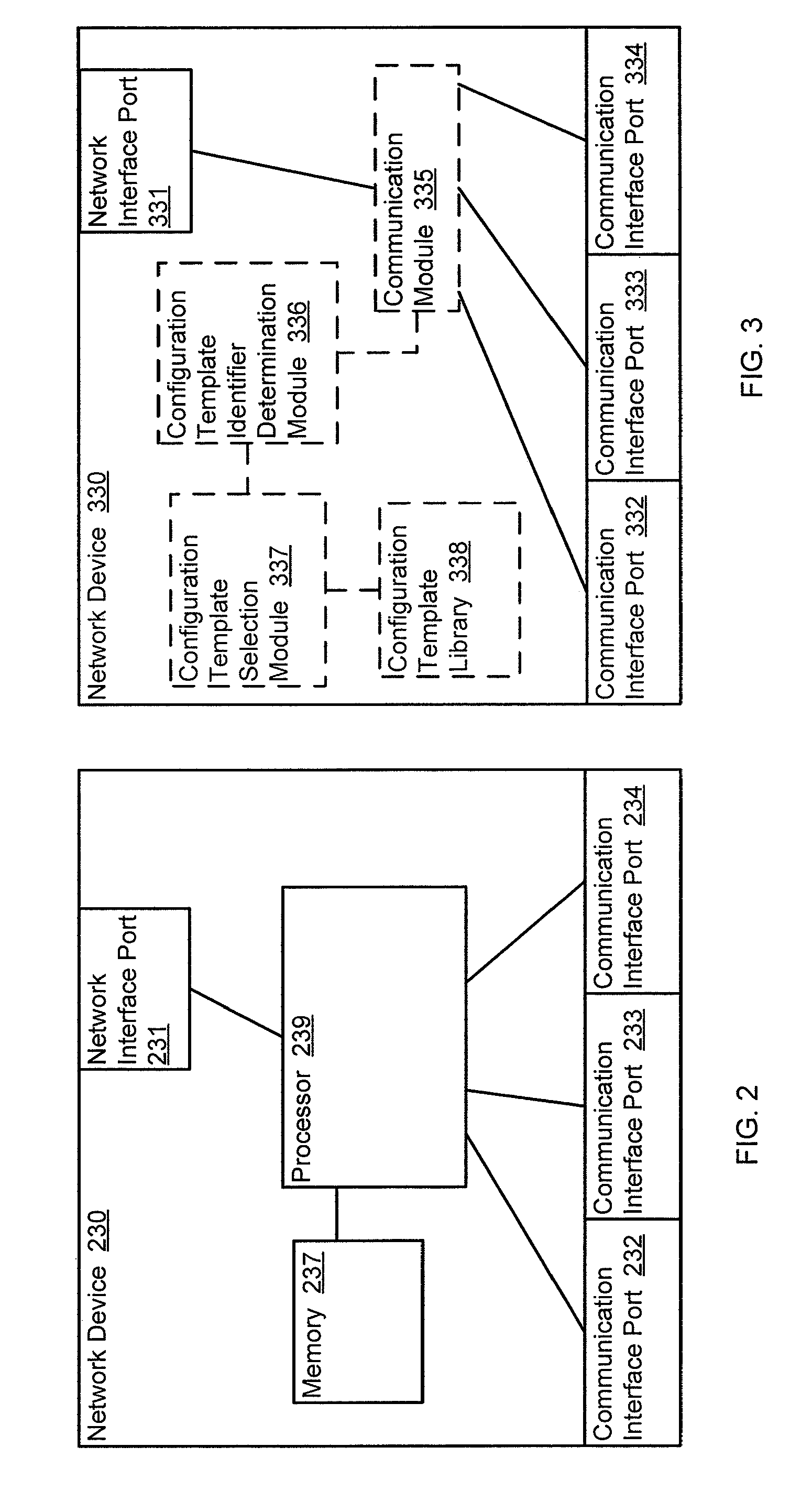
Methods and apparatus for distributed dynamic network provisioning
ActiveUS20100165877A1Digital computer detailsData switching by path configurationTemplate basedDevice Identifiers
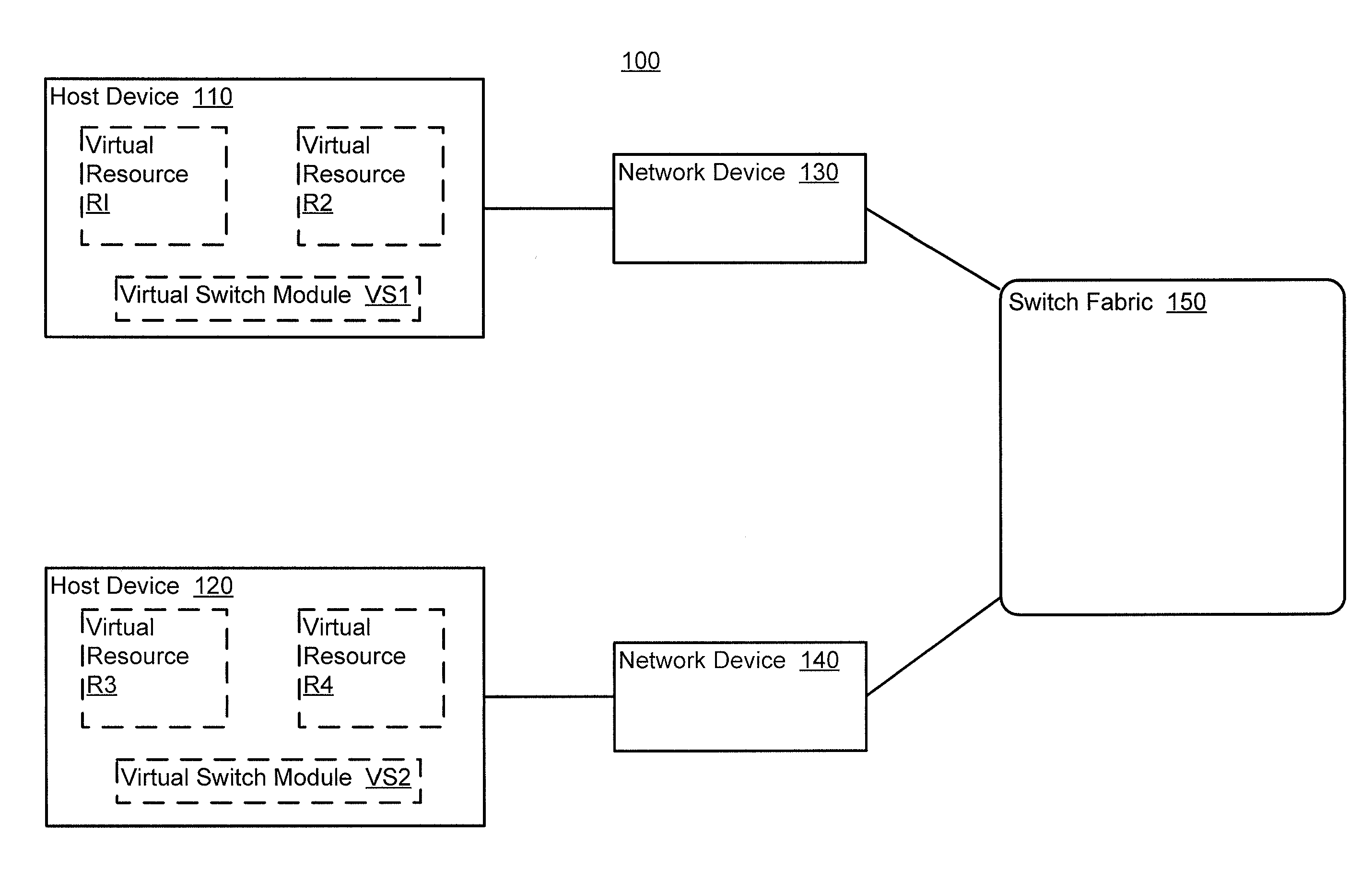
In one embodiment, a method includes receiving a device identifier associated with a virtual resource, determining a configuration template identifier based on the device identifier, and selecting a configuration template from a library of configuration templates based on the configuration template identifier. The receiving, determining, and selecting are at a network device. The virtual resource is hosted by a host device. The device identifier is received from the host device.
Owner:JUMIPER NETWORKS INC
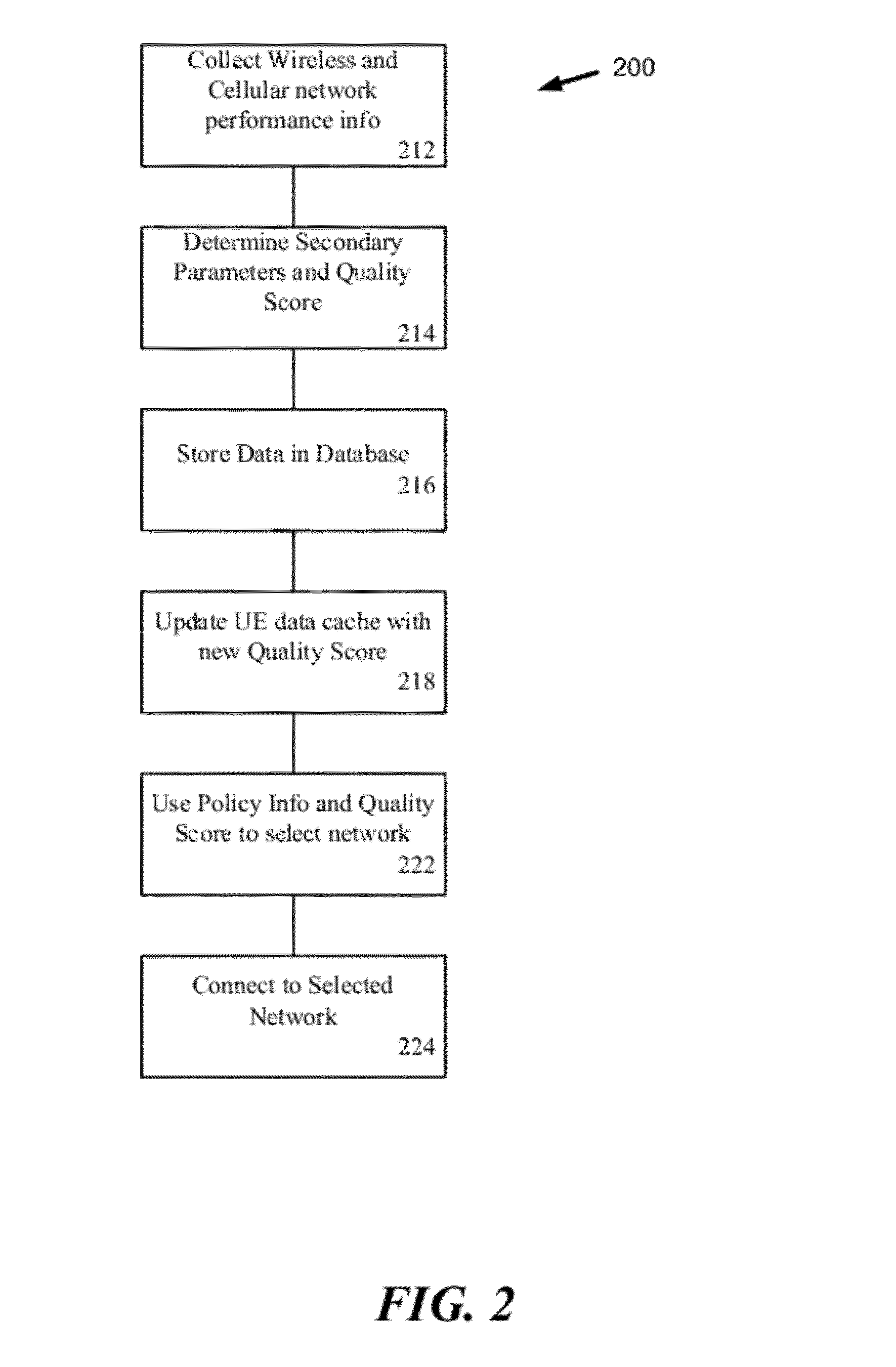
Dynamic Network Connection System and Method
ActiveUS20120196644A1Reduce error rateReduce noiseAssess restrictionRadio transmissionNetwork connectionChoice making
A method and system for selecting a network to establish a connection to from a set of available network includes a network database providing historical information about each of the networks and sends the database information to end user terminals. The end user terminals monitor real-time performance information about each of the available networks and can send this information to the network database. The end user terminals also include network connection policy information which can be used to make the selection decision. The end user terminal determines a network quality score for each available network as a function of the historical information from the network database, the real-time performance information about each available network and the network connection policy information. The end user terminal can select the available network as a function of the network quality score, for example, selecting the available network with the highest network quality score.
Owner:WEFI
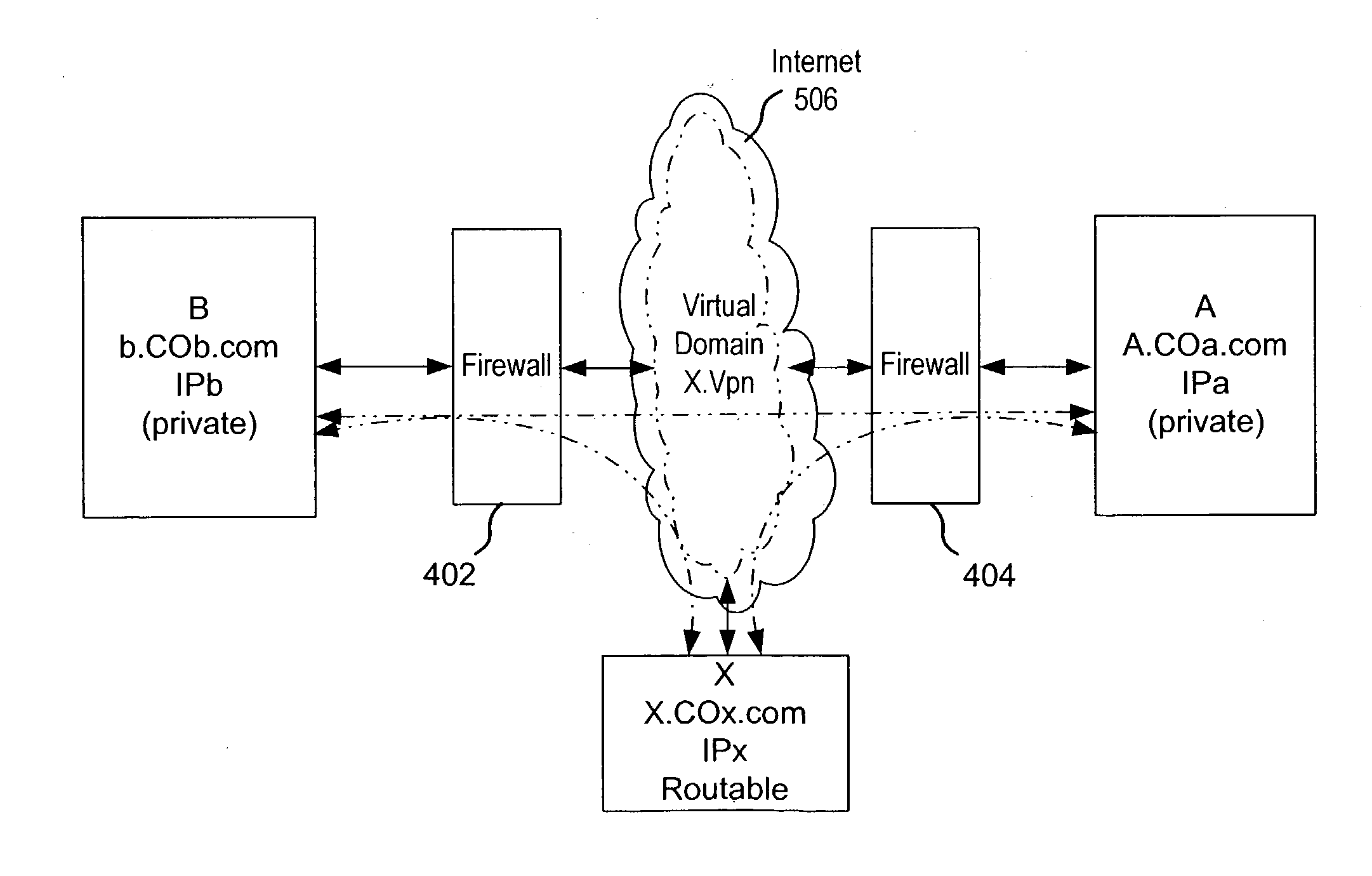
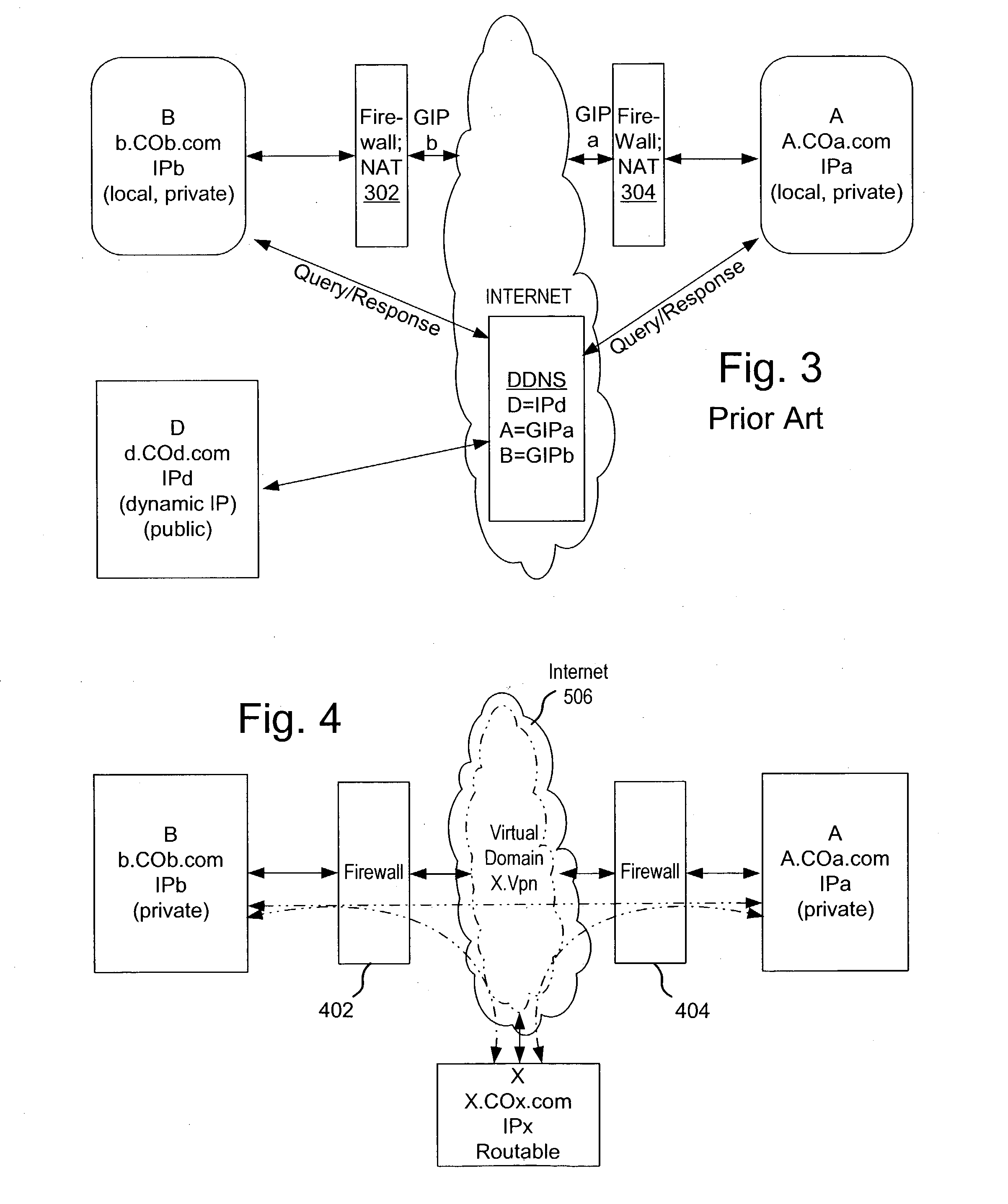
Secure virtual community network system
ActiveUS20040249911A1Convenient introductionMultiple digital computer combinationsOffice automationPrivate networkPublic network
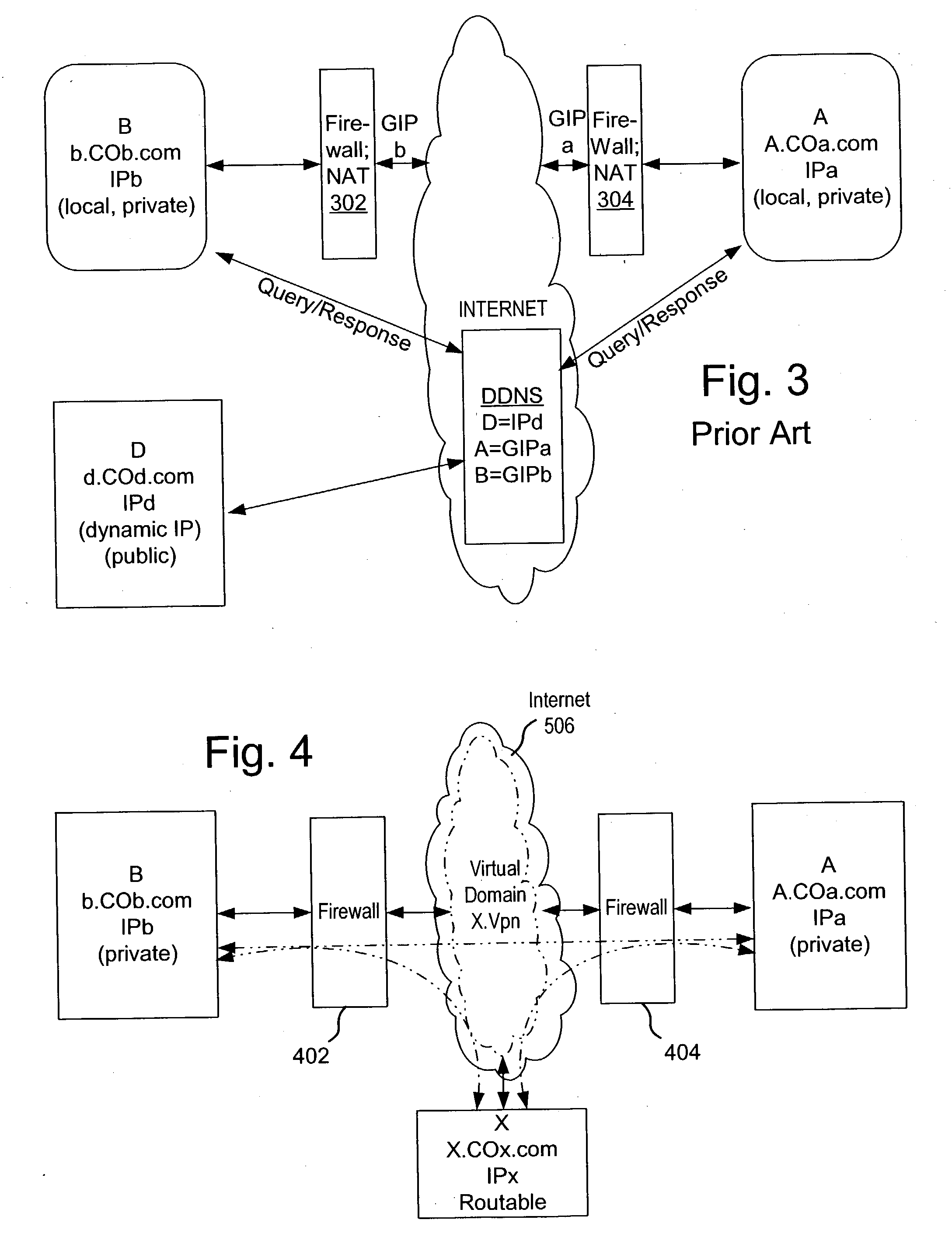
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:F POSZAT HU
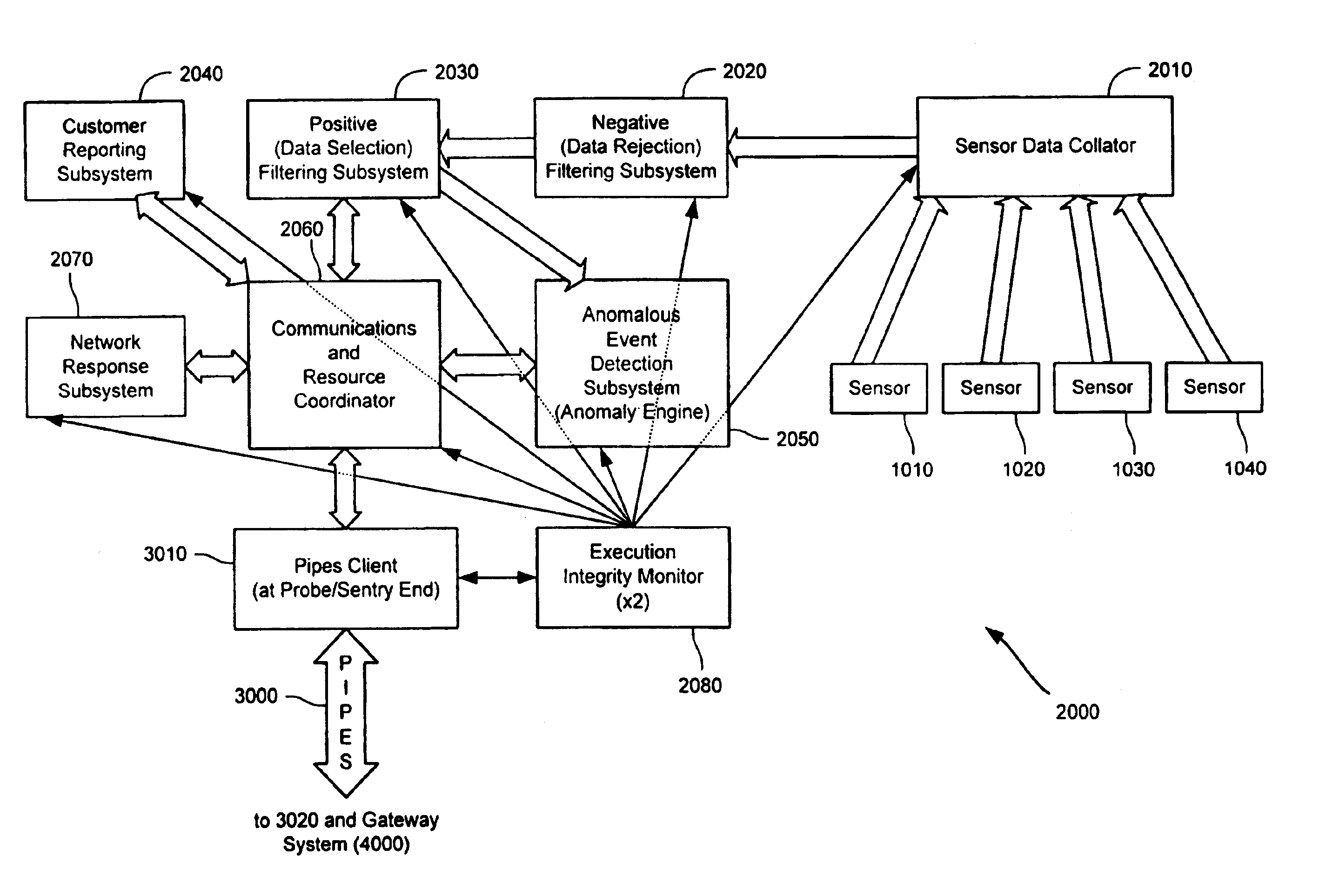
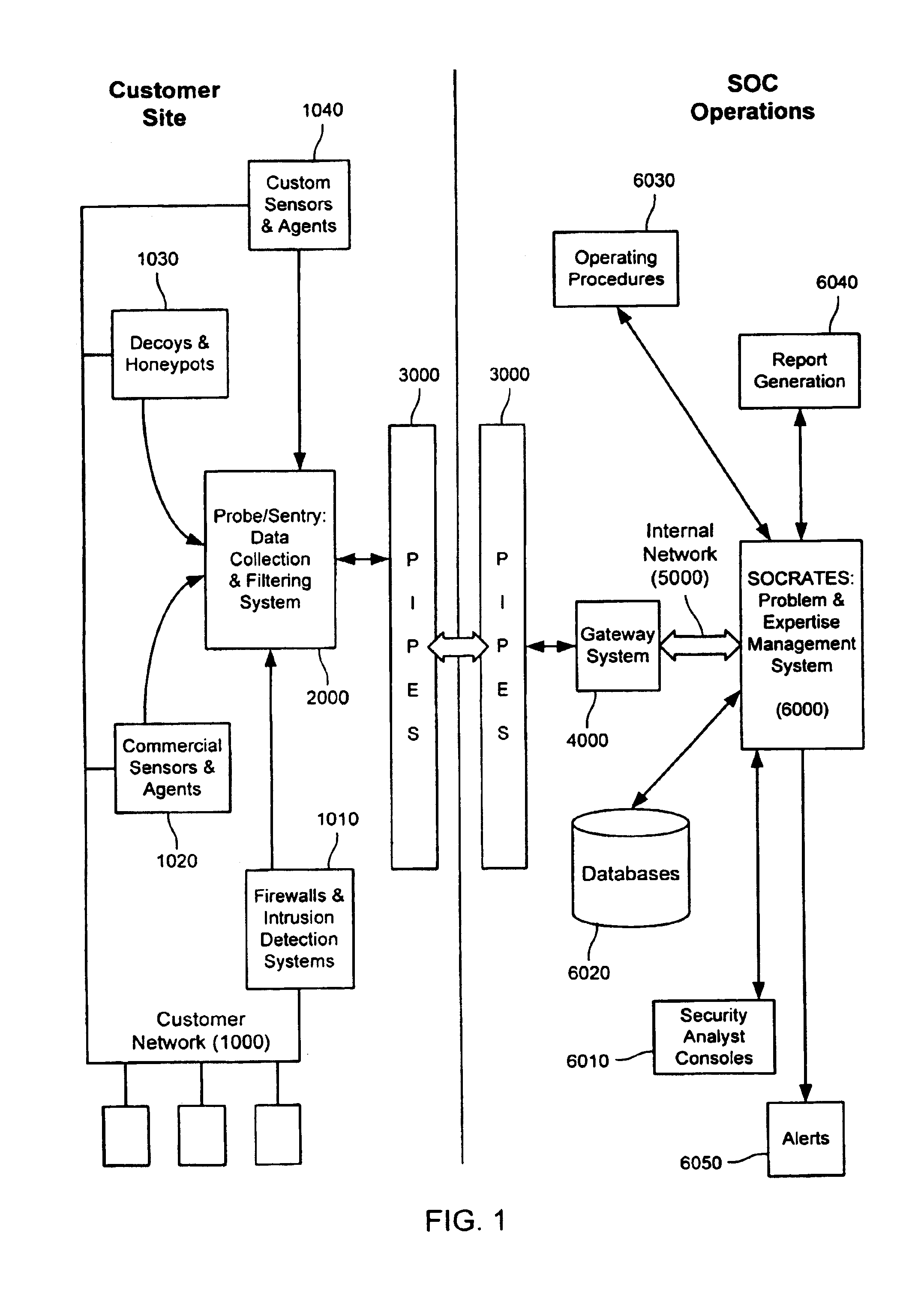
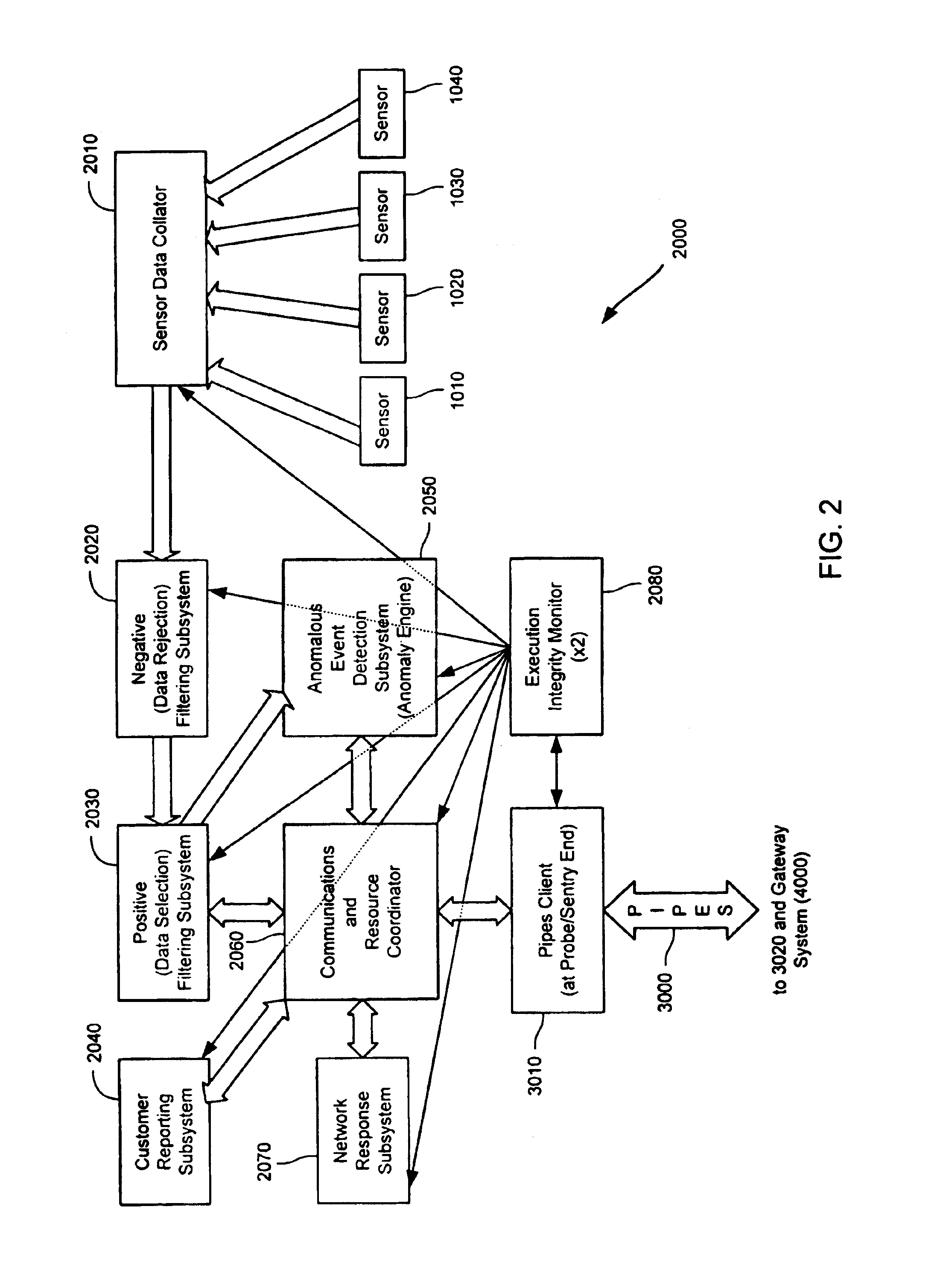
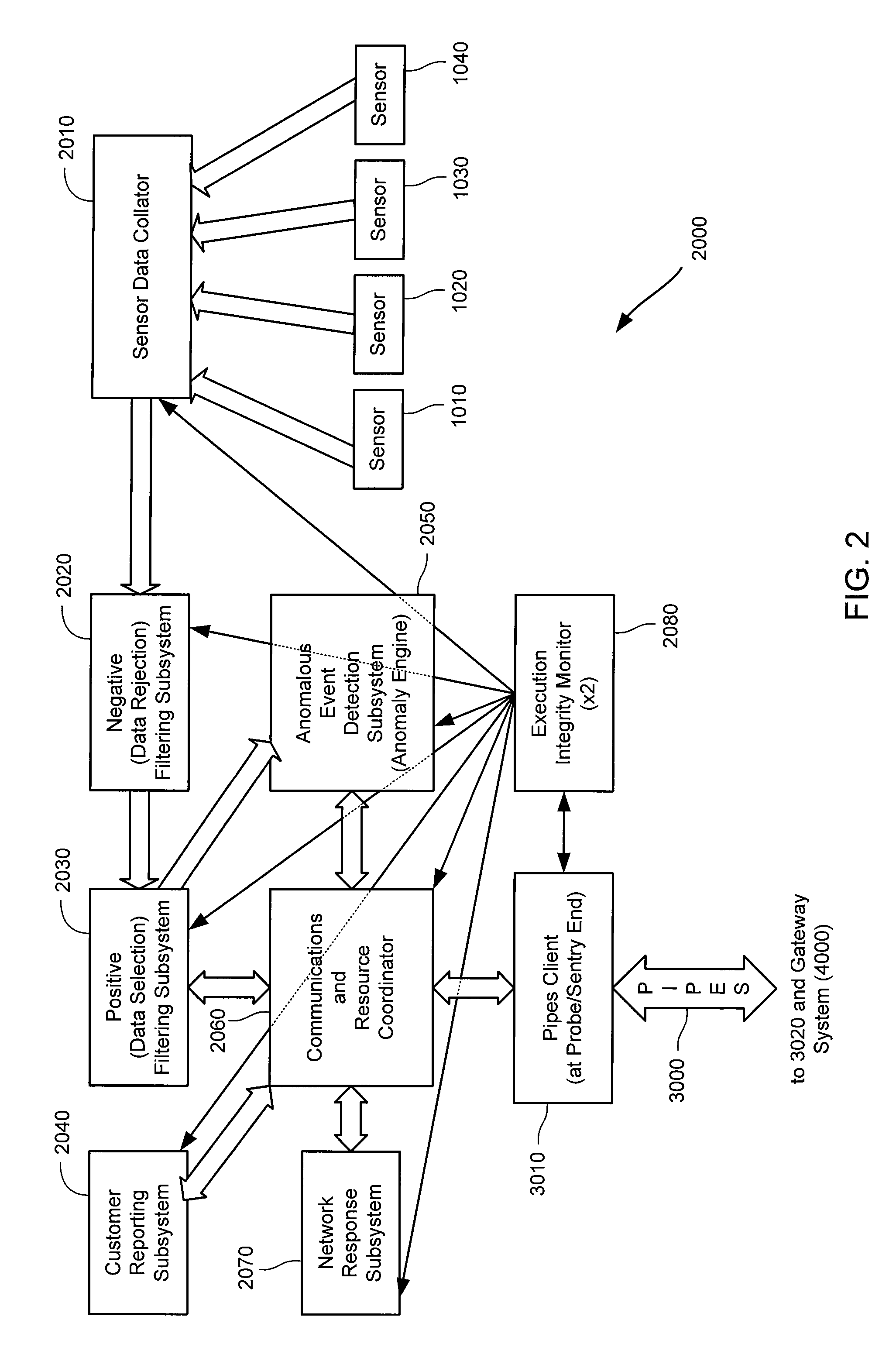
Method and system for dynamic network intrusion monitoring, detection and response
InactiveUS7159237B2Eliminate false positivesIncrease in sizeMemory loss protectionDigital data processing detailsProblem resolutionVulnerability
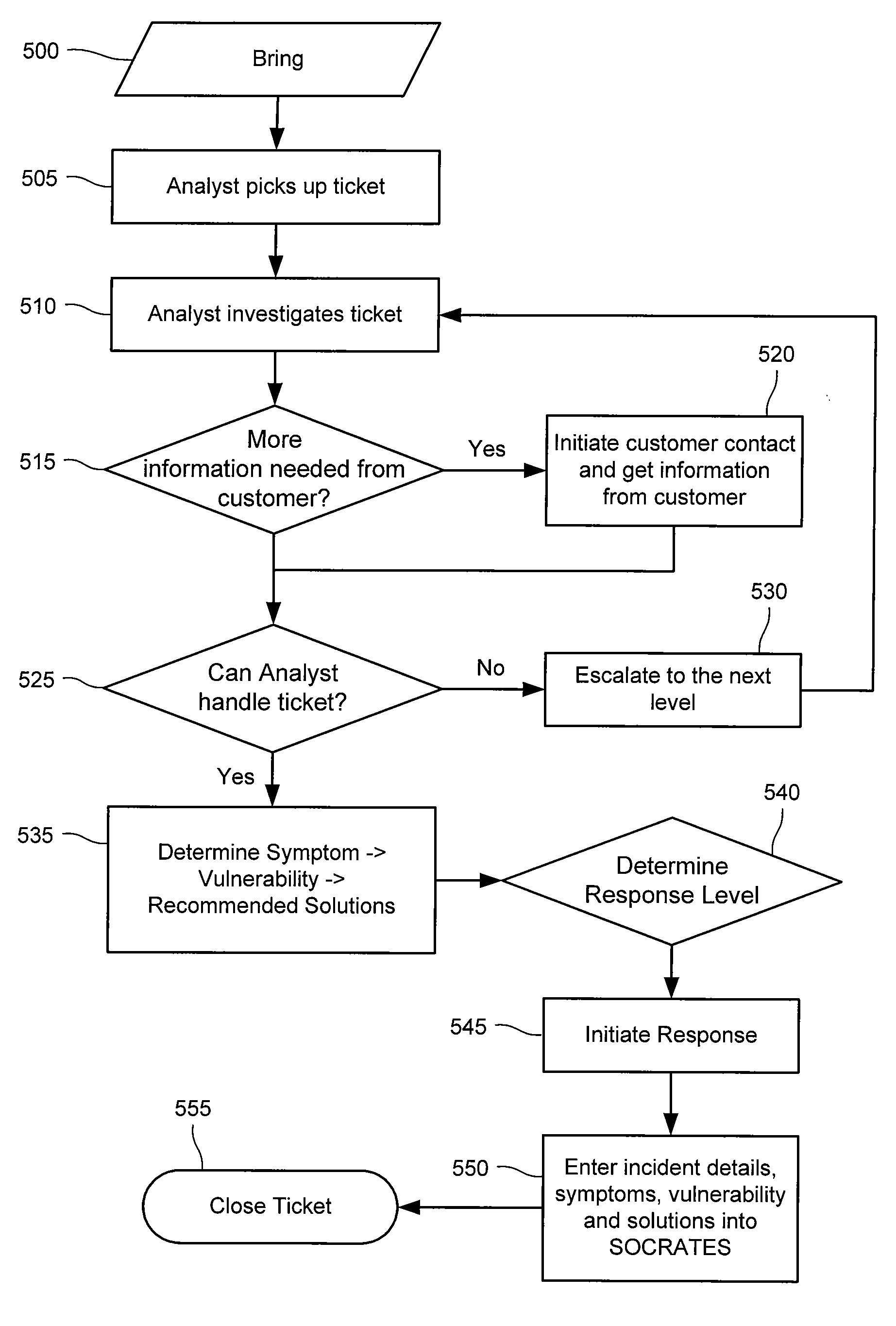
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
Mobile ad hoc extensions for the internet
InactiveUS6845091B2Easy to addImprove robustnessError prevention/detection by using return channelNetwork traffic/resource managementTTEthernetNetwork measurement
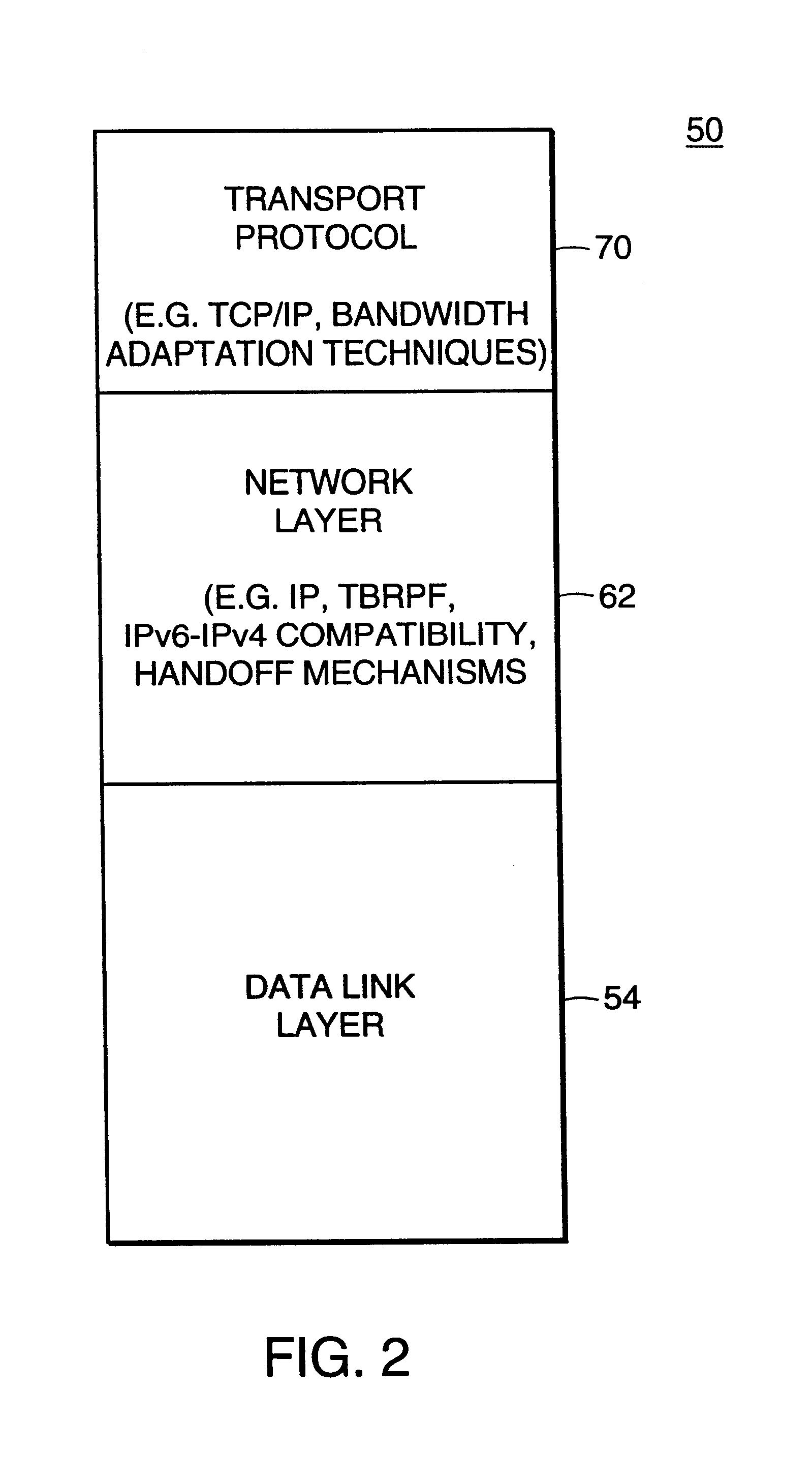
Described is an internetworking system having various mobile ad hoc extensions to the Internet that are particularly suited to the dynamic environment of mobile ad hoc networks. The internetworking system includes any combination of a link-state routing protocol for disseminating topology and link-state information over a multi-hop network comprised of nodes, a neighbor discovery protocol that can detect the appearance and disappearance of new neighbor nodes, an address format that facilitates deployment of IPv6 nodes in a predominantly IPv4 network infrastructure, a queuing mechanism that can update information upon resuming interrupted communications between nodes, and dynamic network measurement techniques for adaptively using wireless bandwidth when establishing and maintaining connections between nodes and a server.
Owner:SRI INTERNATIONAL
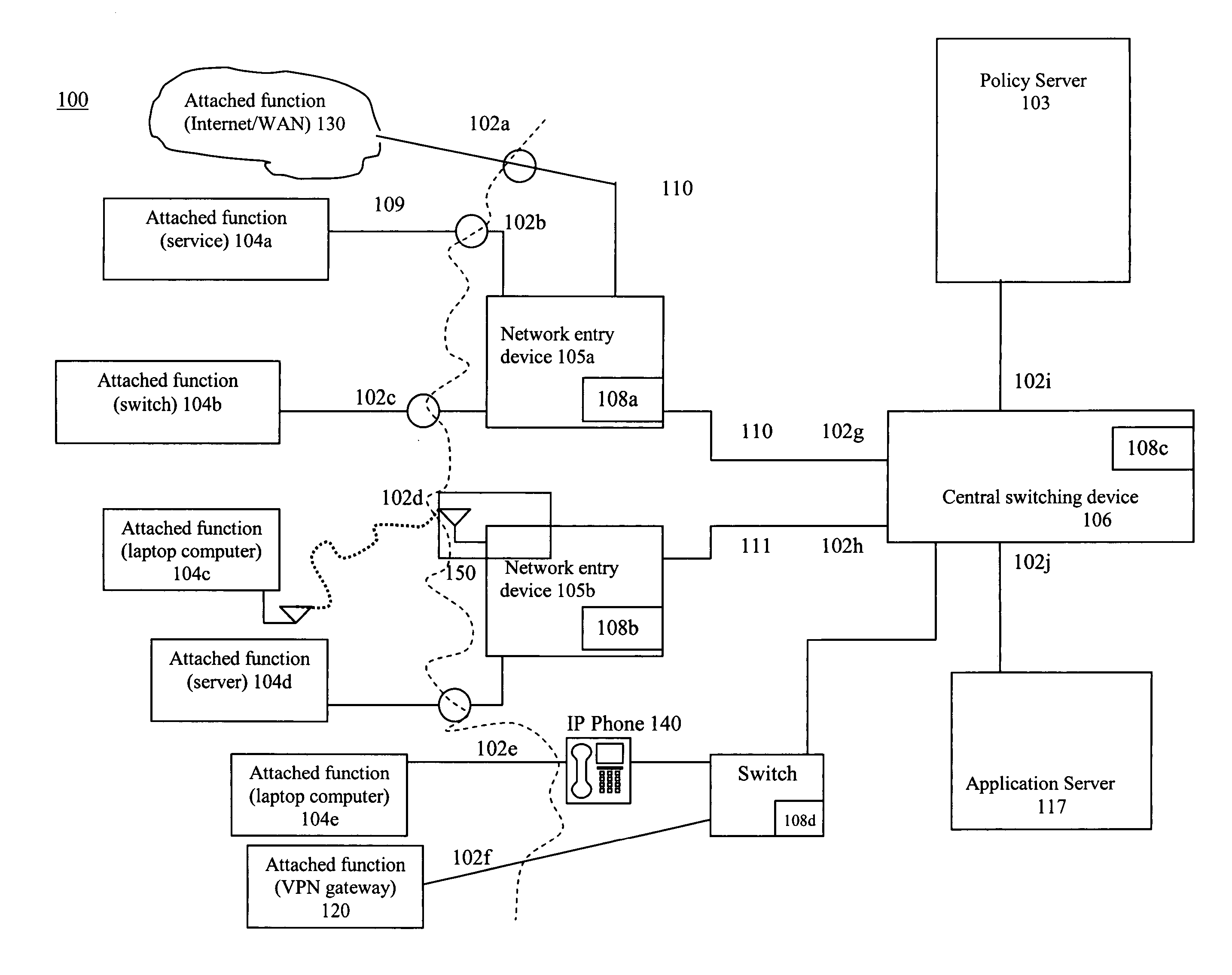
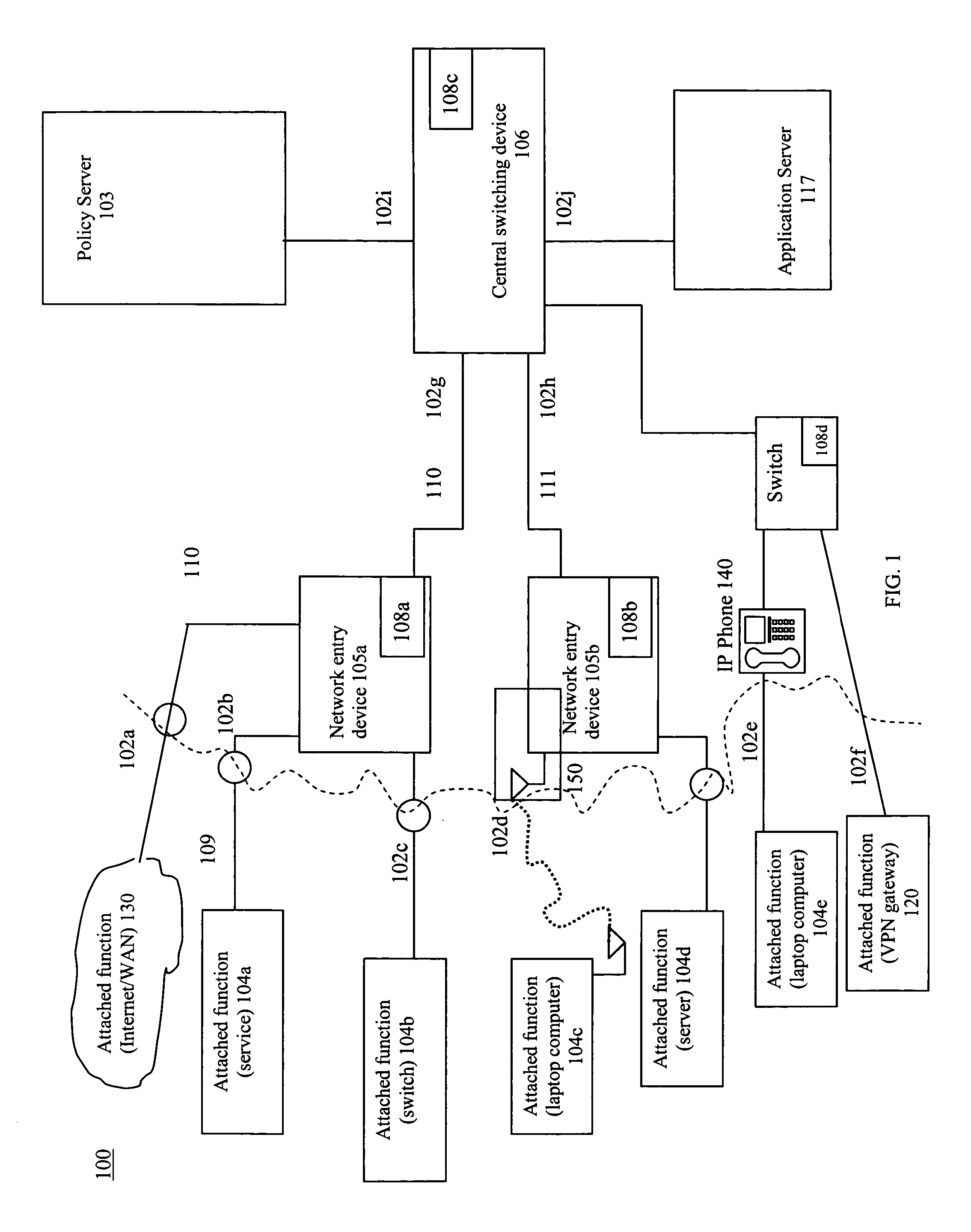
System and method for dynamic network policy management
InactiveUS7526541B2Improve accuracyImprove allocationDigital data protectionMultiple digital computer combinationsNetwork serviceNetwork administrator
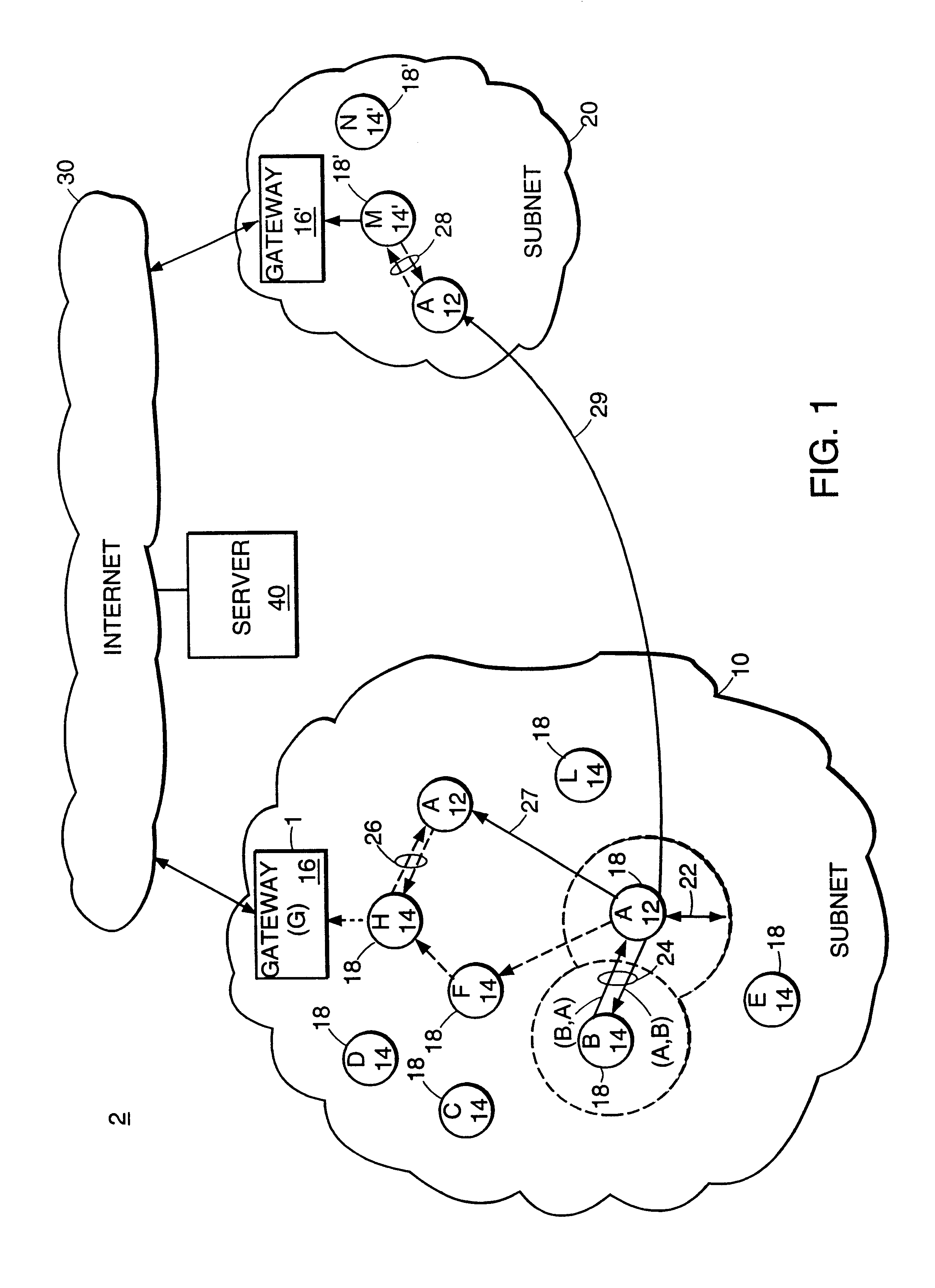
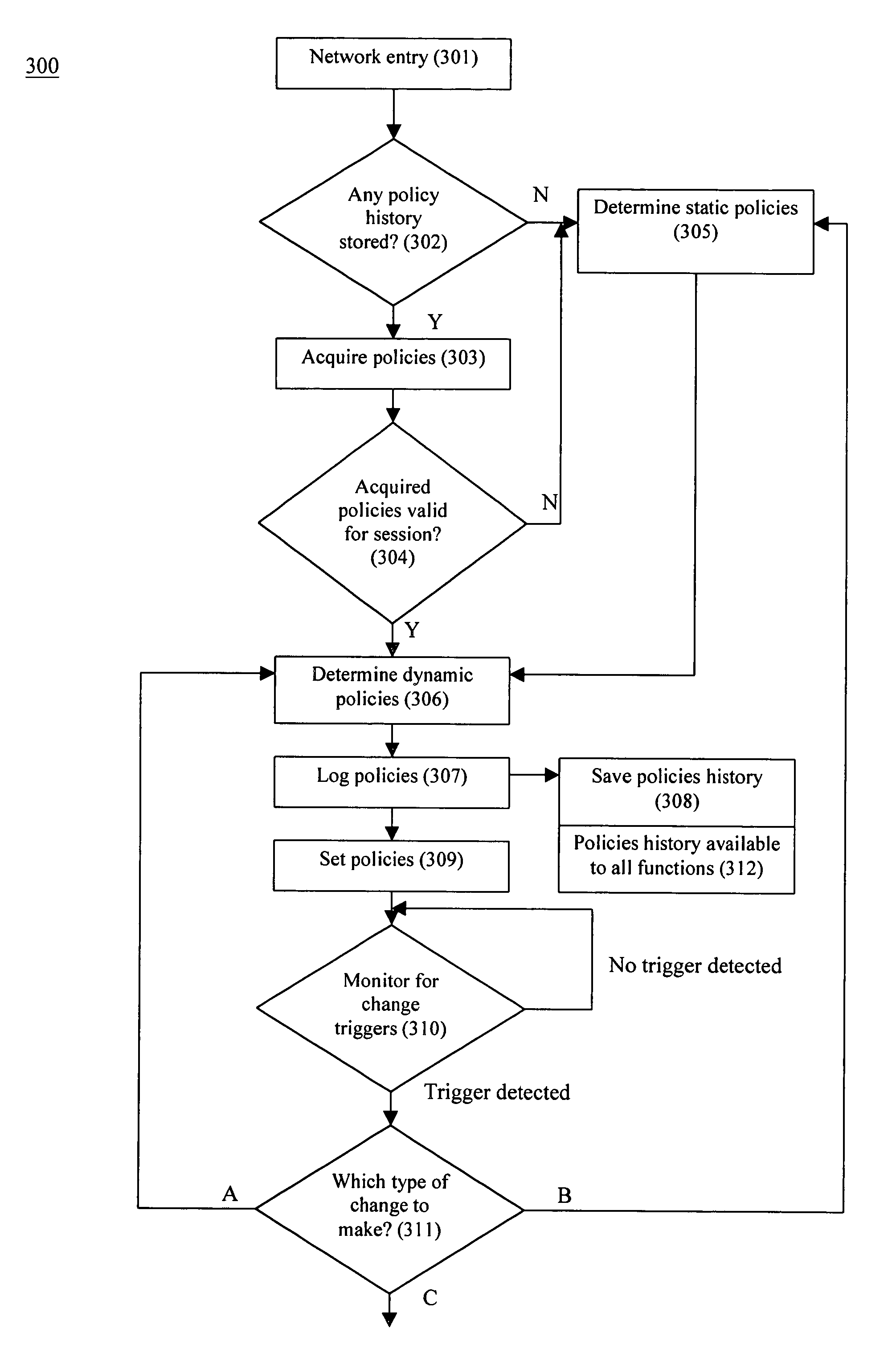
A system and method that provides dynamic network policy management. The system enables a network administrator to regulate usage of network services upon initiation of and throughout network sessions. The system employs a method of identifying selectable characteristics of attached functions to establish static and dynamic policies, which policies may be amended before, during and after any session throughout the network based on the monitored detection of any of a number of specified triggering events or activities. Particular policies associated with a particular identified attached function in prior sessions may be cached or saved and employed in subsequent sessions to provide network usage permissions more rapidly in such subsequent sessions. The cached or saved policy information may also be used to identify network usage, control, and security. The system and method of the present invention provides static and dynamic policy allocation for network usage provisioning.
Owner:EXTREME NETWORKS INC
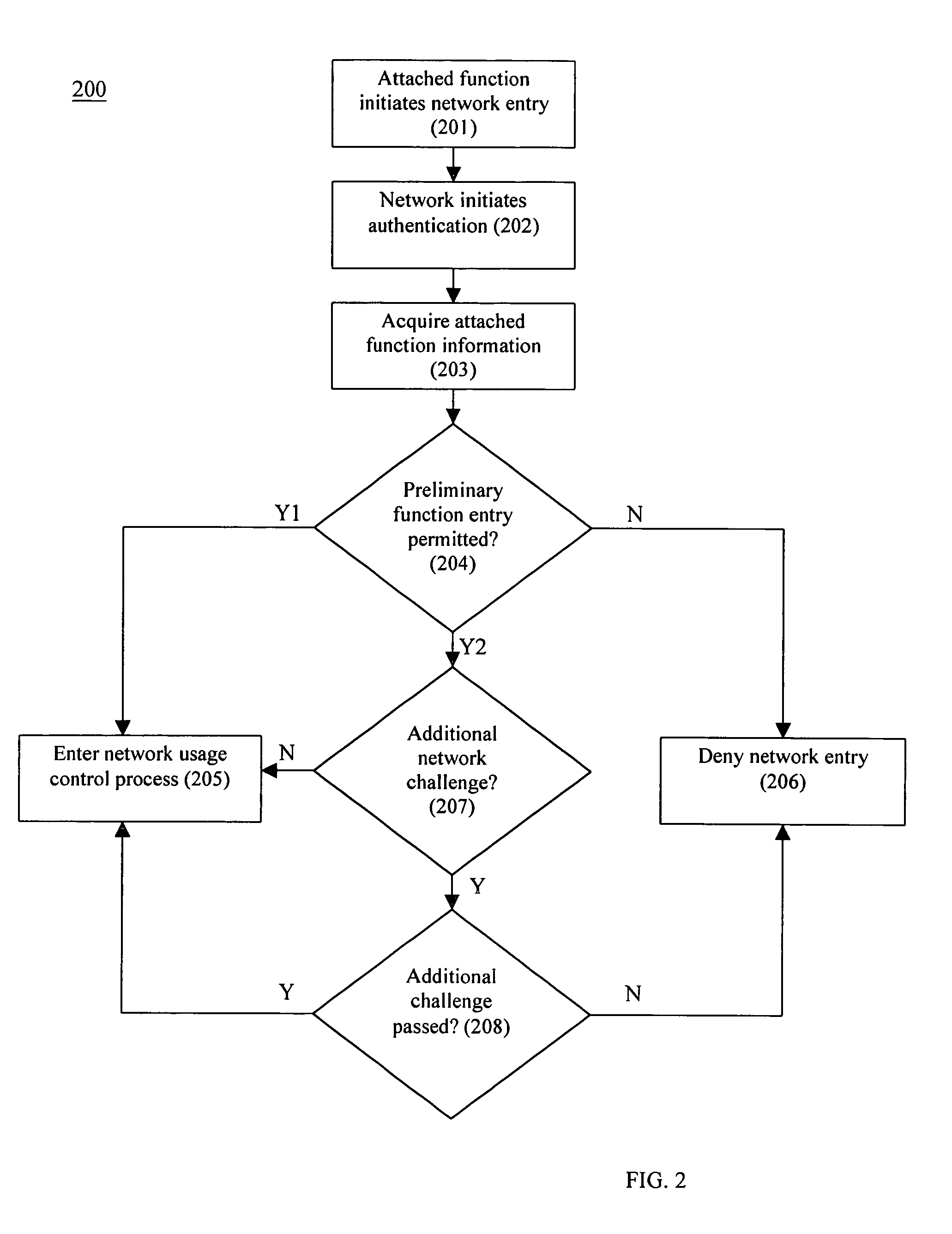
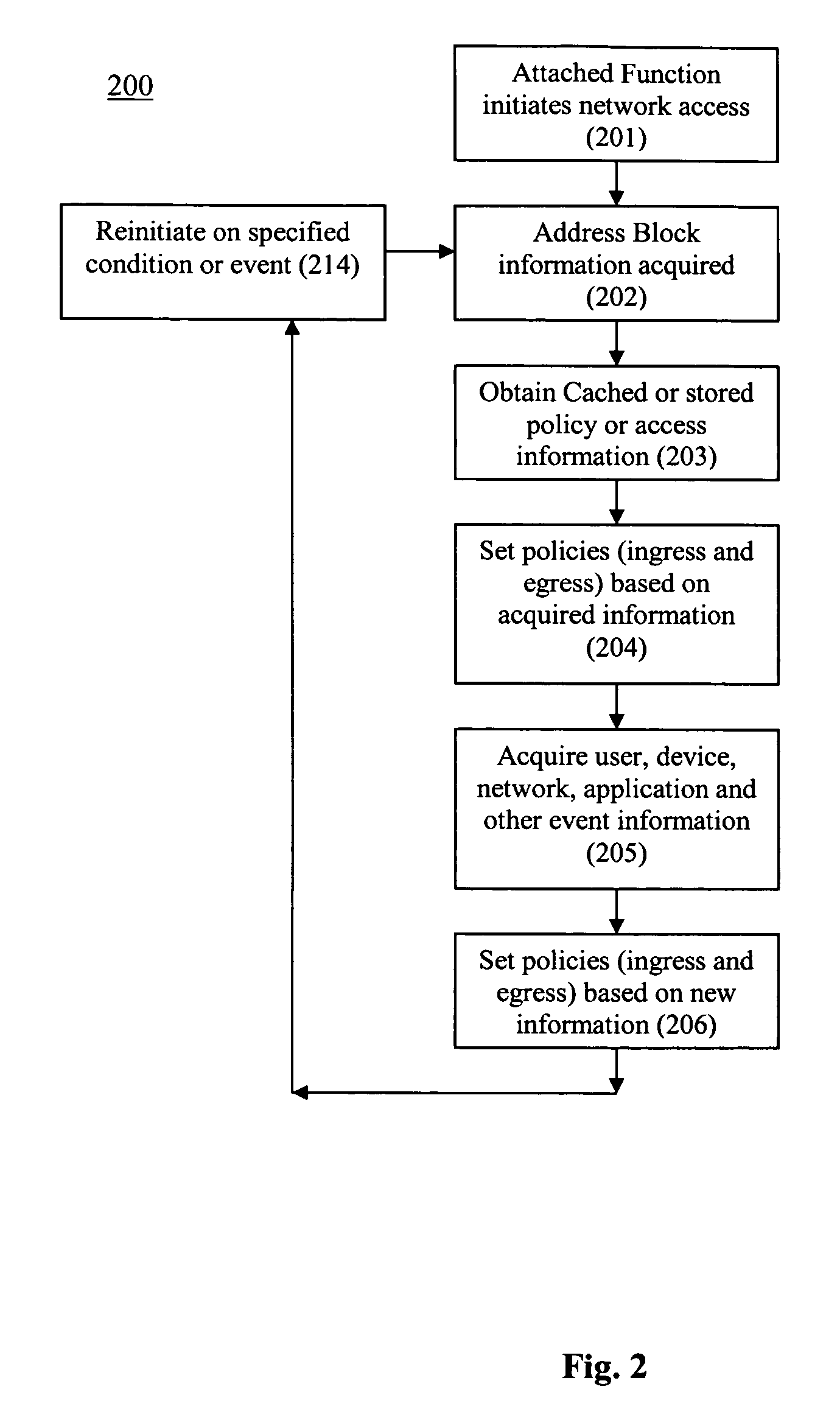
System and method for address block enhanced dynamic network policy management
ActiveUS7945945B2Digital data processing detailsUser identity/authority verificationComputer networkDynamical network
A method, computer readable medium, and system for acquiring address block information for an attached function that initiates network access on a distributed computing network. Additional policy information in acquired concerning the attached function. One or more access policies are set based, at least in part, on the address block information and the additional policy information.
Owner:EXTREME NETWORKS INC
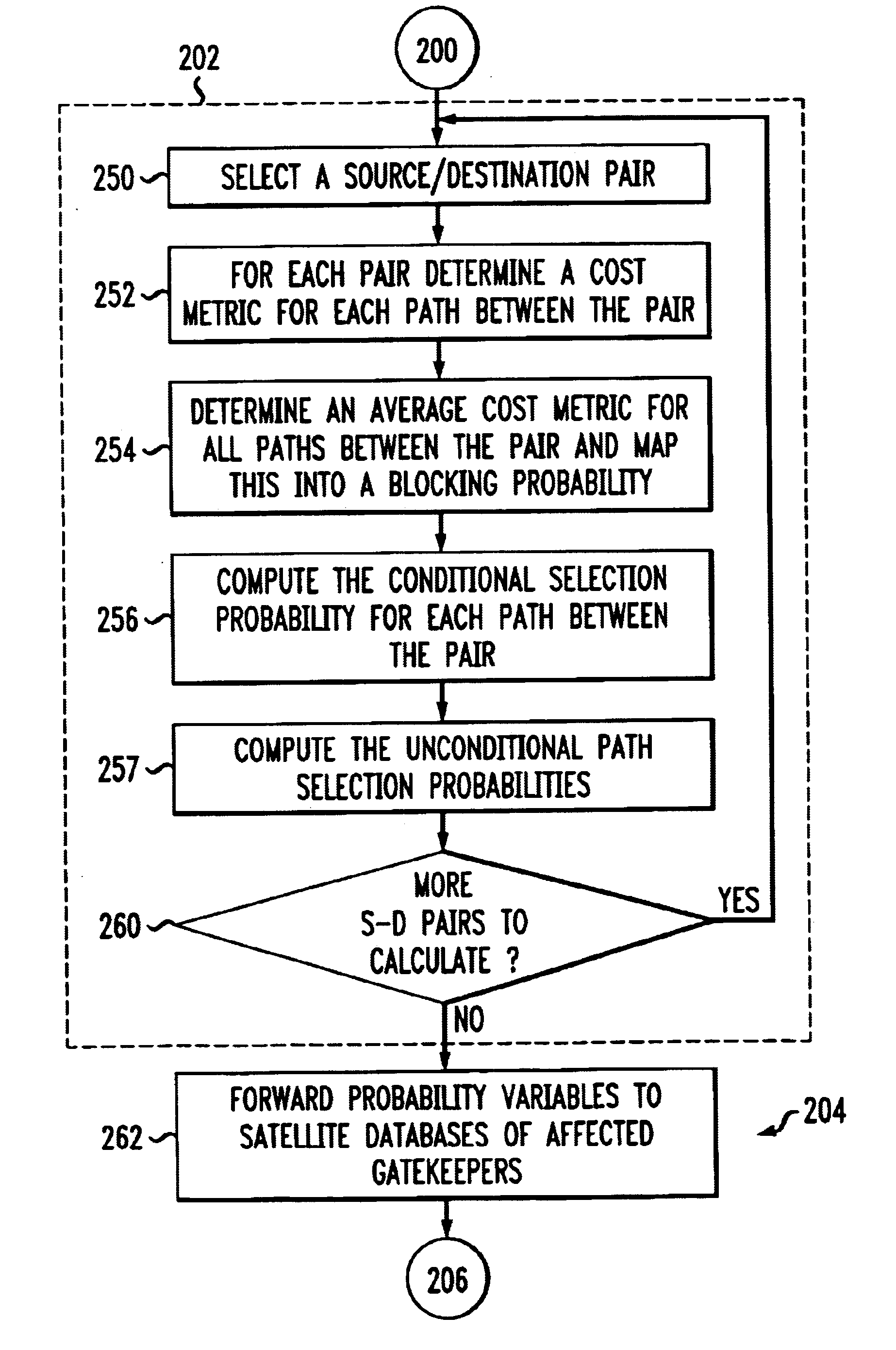
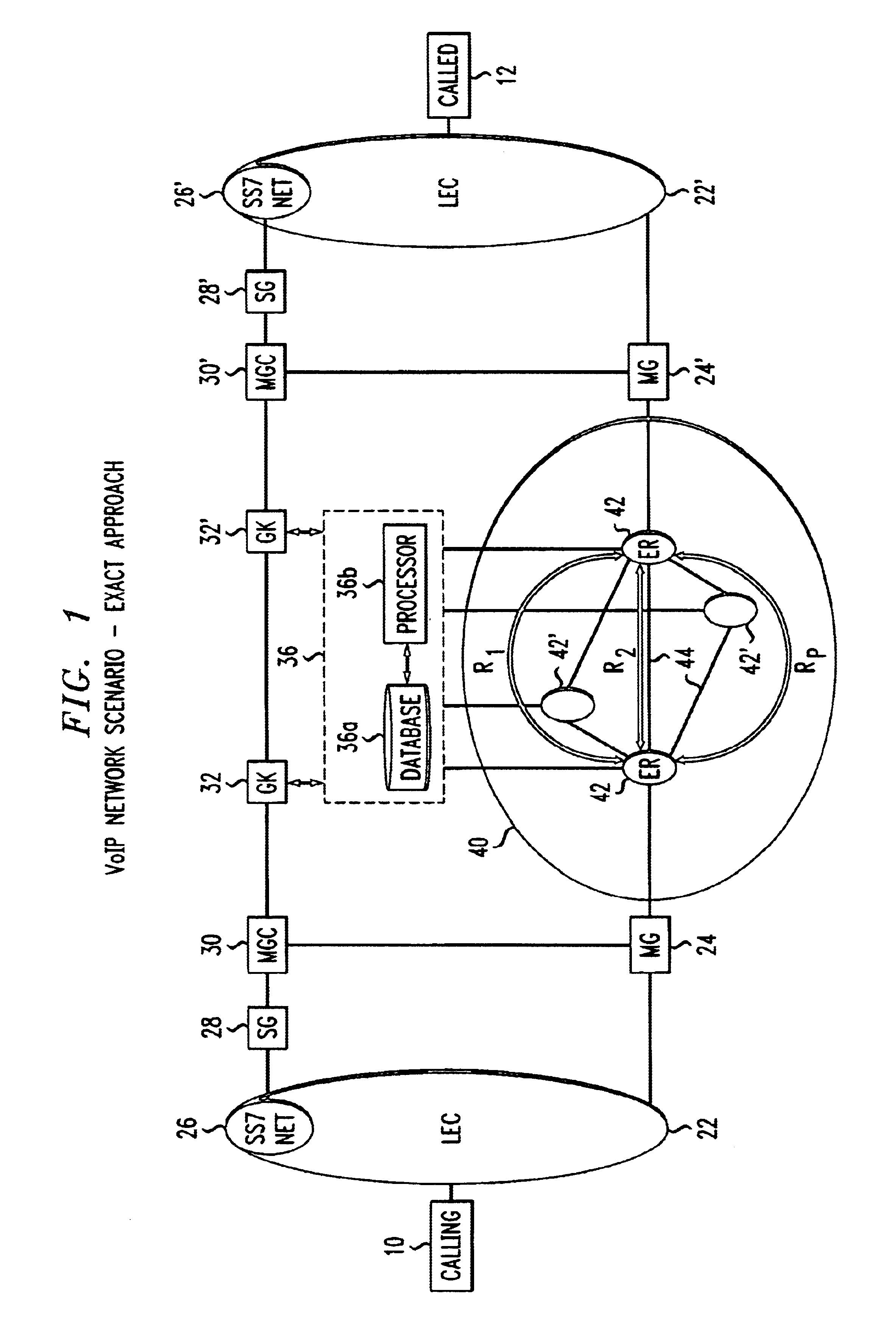
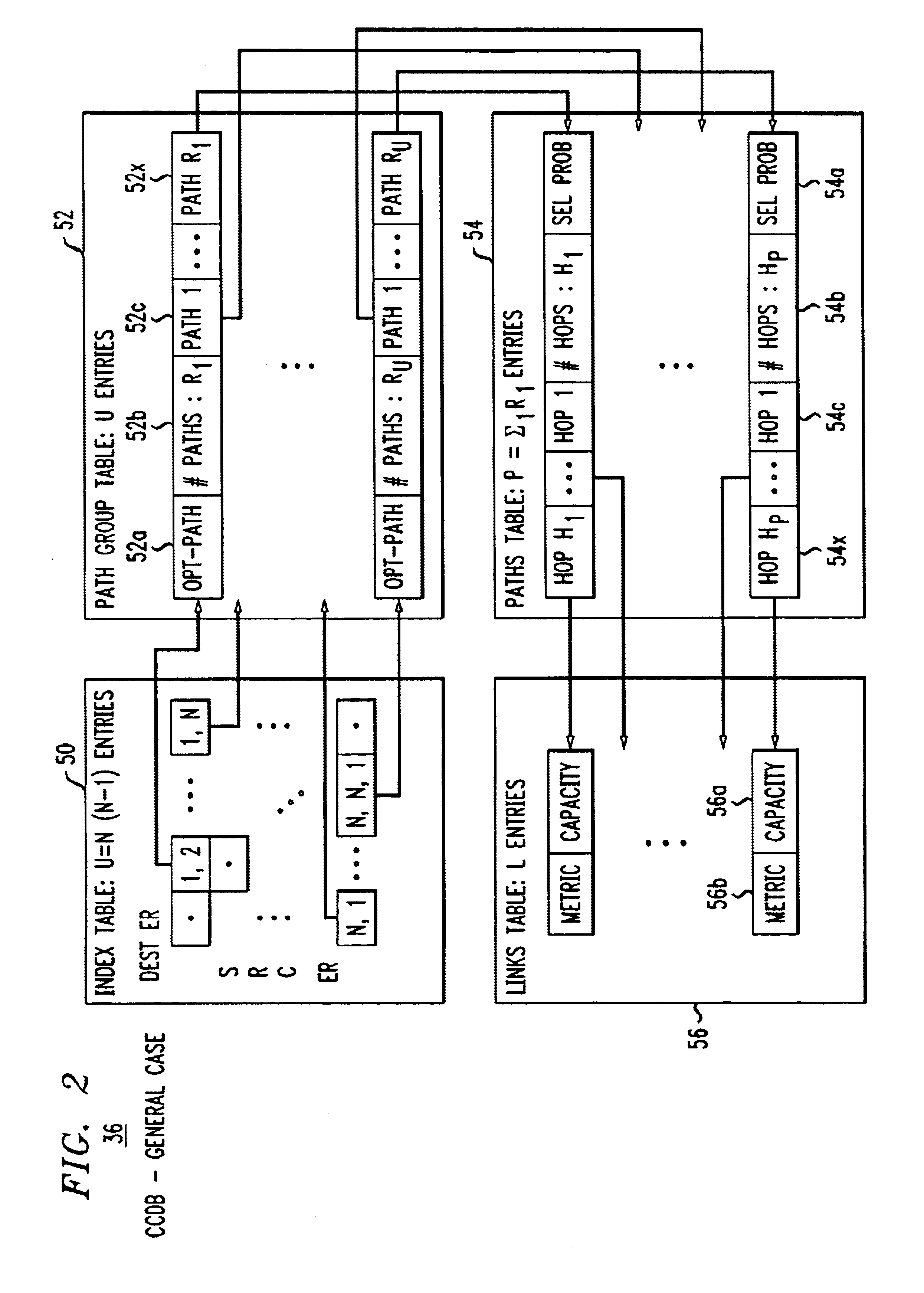
Method and apparatus to provide centralized call admission control and load balancing for a voice-over-IP network
InactiveUS6904017B1Improve service qualityBandwidth sharingInterconnection arrangementsError preventionExtensibilityBalancing network
An admission control and load balancing system controls admission of packet streams or calls to a network and balances the packet traffic across the network, improving quality of service. The system includes a central database which stores information including cost data associated with individual paths and links across the network. A processor, in communication with the database, coordinates the admission control and load balancing decisions, and updates of the database cost data to reflect the dynamic network conditions, based on input from appropriate data sources. In one embodiment, referred to as the exact algorithm, the database is consulted by the admission control points or gatekeepers prior to admitting each arriving packet stream, and the database contents are updated call-by-call to reflect the allocation of resources to each admitted stream. In another embodiment, referred to as the inexact algorithm, control decision as well as database updates occur on a periodic rather than on a call-by-call basis to promote better scalability. In this embodiment, the processor periodically calculates admission decisions based on cost data in the central database. These admission decisions are then periodically forwarded to a satellite database associated with each gatekeeper, for storage and use in admission decisions until the next update epoch.
Owner:LUCENT TECH INC
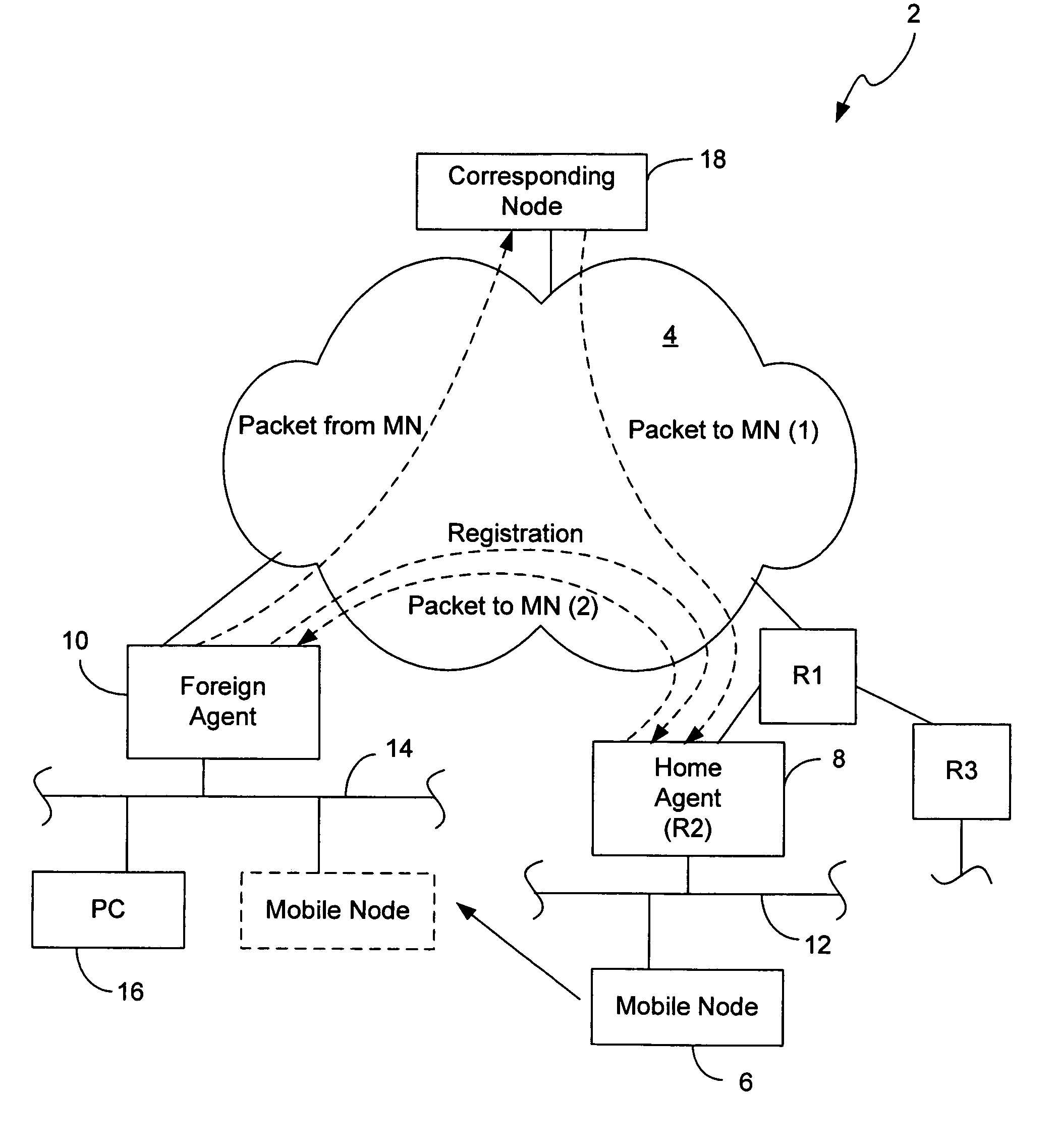
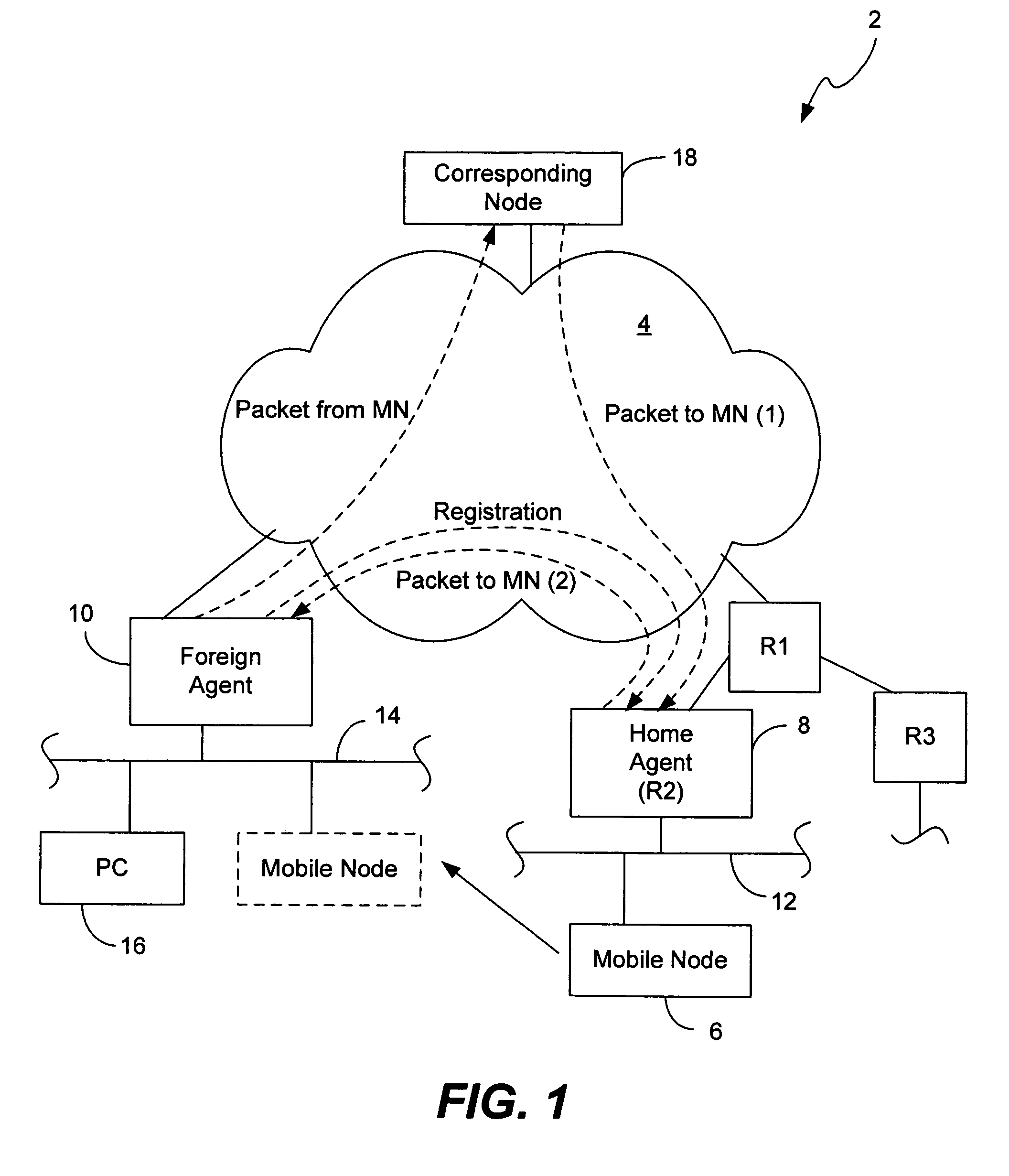
Dynamic network allocation for mobile router
InactiveUS6959341B1Network topologiesMultiple digital computer combinationsComputer networkMobile IP
Methods and apparatus for implementing a Home Agent supporting Mobile IP and being capable of allocating one or more networks to a mobile router which registers with the Home Agent comprise receiving a registration request packet from the mobile router, the registration request packet including a network allocation extension indicating one or more networks being requested by the mobile router from the Home Agent. The one or more networks are allocated to the mobile router corresponding to the network allocation extension of the registration request packet. A registration reply packet including a network allocation extension identifying the one or more networks allocated to the mobile router is then sent to the mobile router.
Owner:CISCO TECH INC
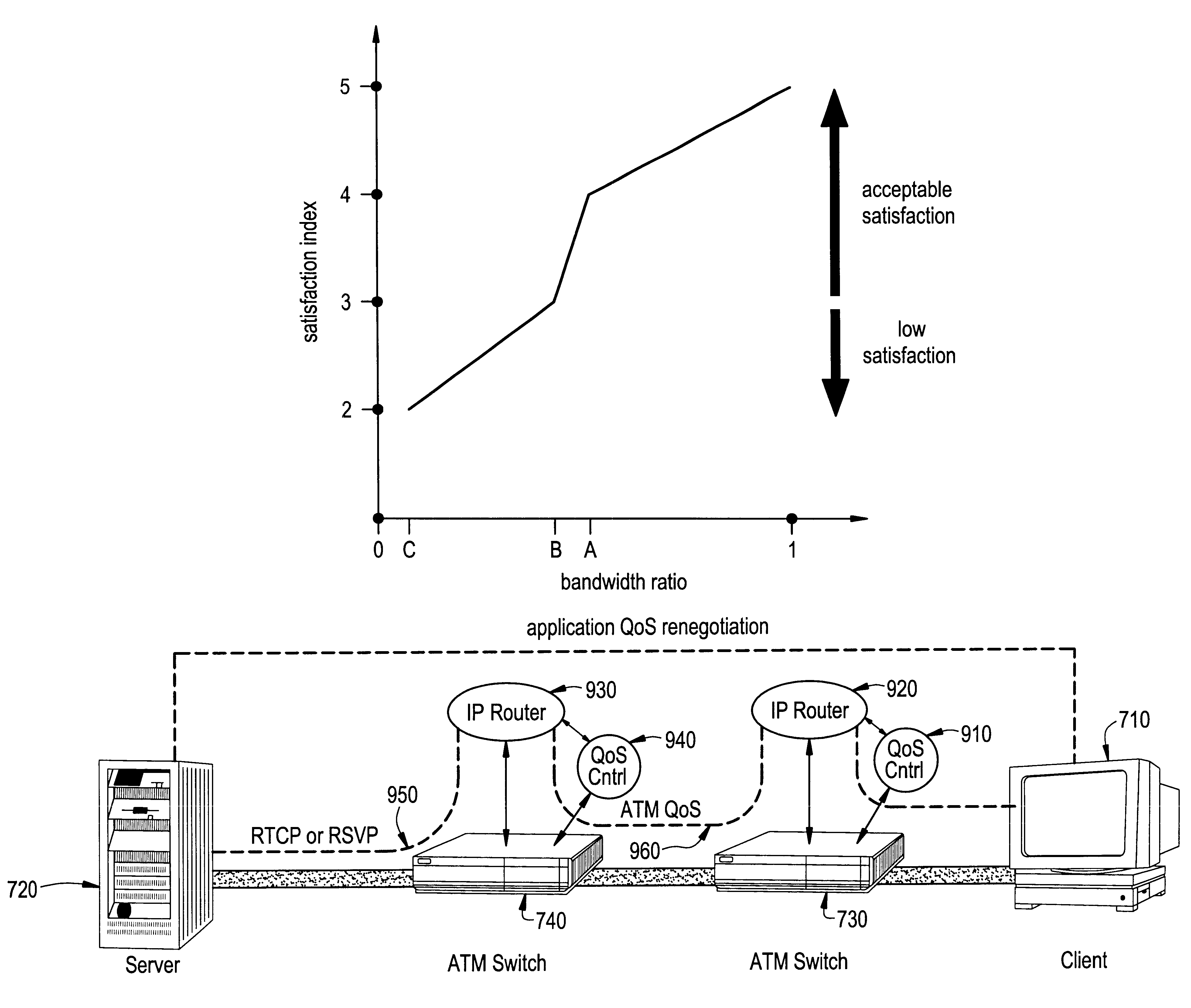
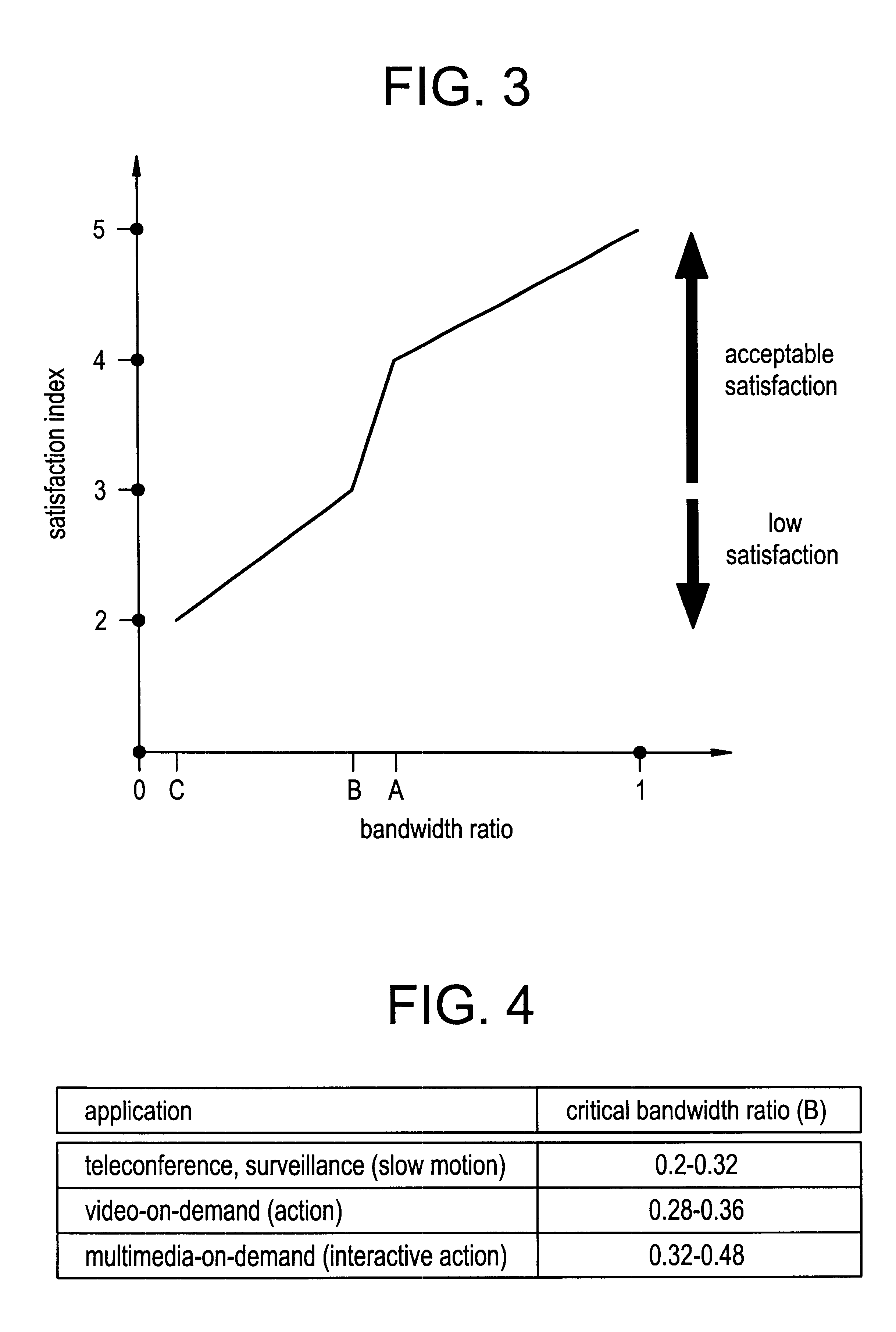
Dynamic network bandwidth allocation for multimedia applications with soft quality-of-service requirements
InactiveUS6404738B1Lower connection costsLow costError preventionFrequency-division multiplex detailsDynamic bandwidth allocationService level requirement
A new concept of soft quality-of-service (soft-QoS) is developed that bridges the gap between the efficient provision of network-level QoS and the requirements of multimedia applications. Soft-QoS is defined by a satisfaction index (a number that rates users' perceptual quality) and a softness profile (a function that captures the robustness of multimedia applications to network congestion). Another aspect of this invention is a bandwidth allocation scheme for multimedia applications with soft-QoS requirements is presented. The implementation of the bandwidth allocation scheme on a network element realizes a soft-QoS controller. The controller uses the connections' softness profiles to compute a bandwidth allocation that maximizes the minimum satisfaction index of active connections.
Owner:JUMIPER NETWORKS INC
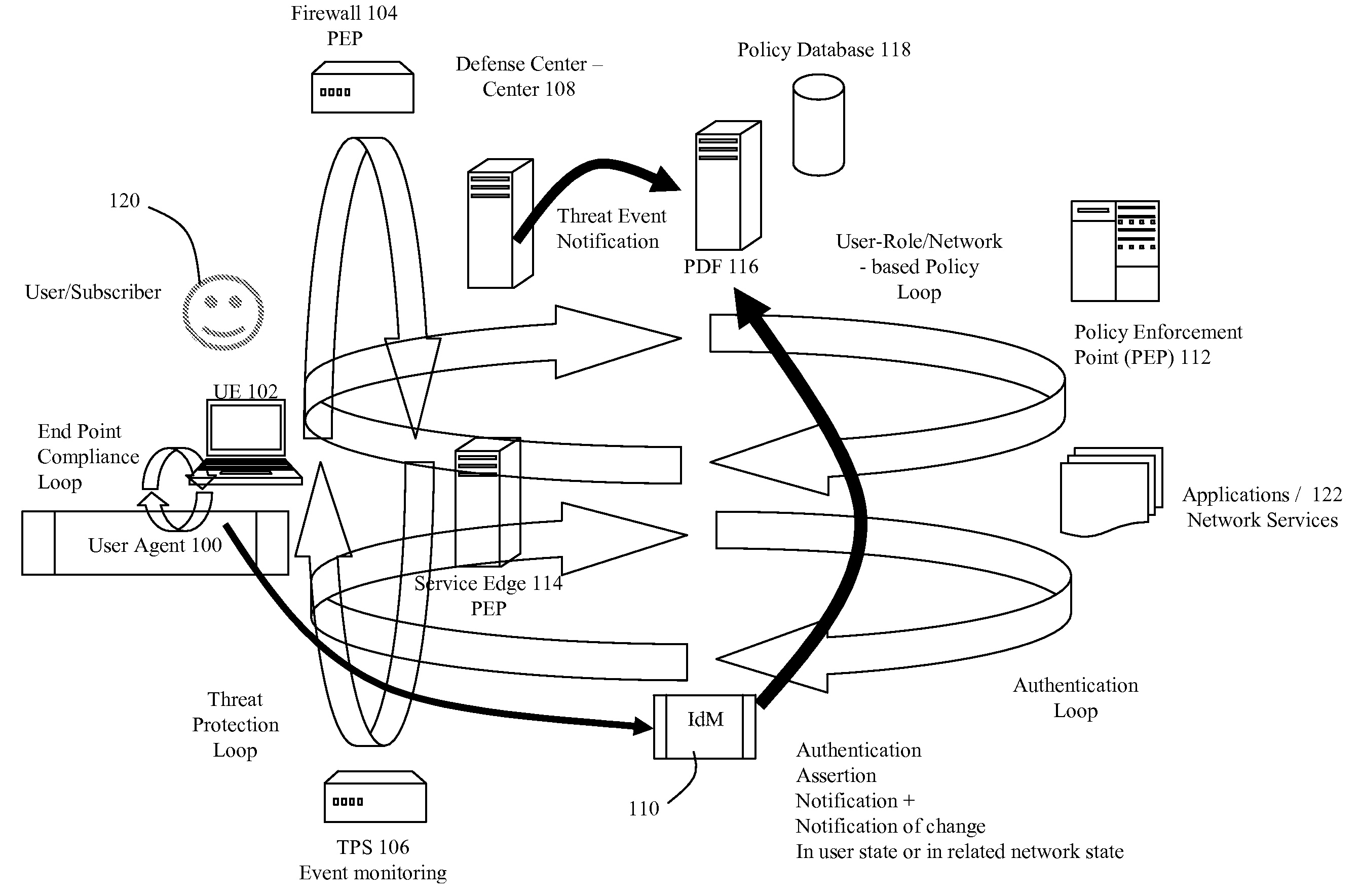
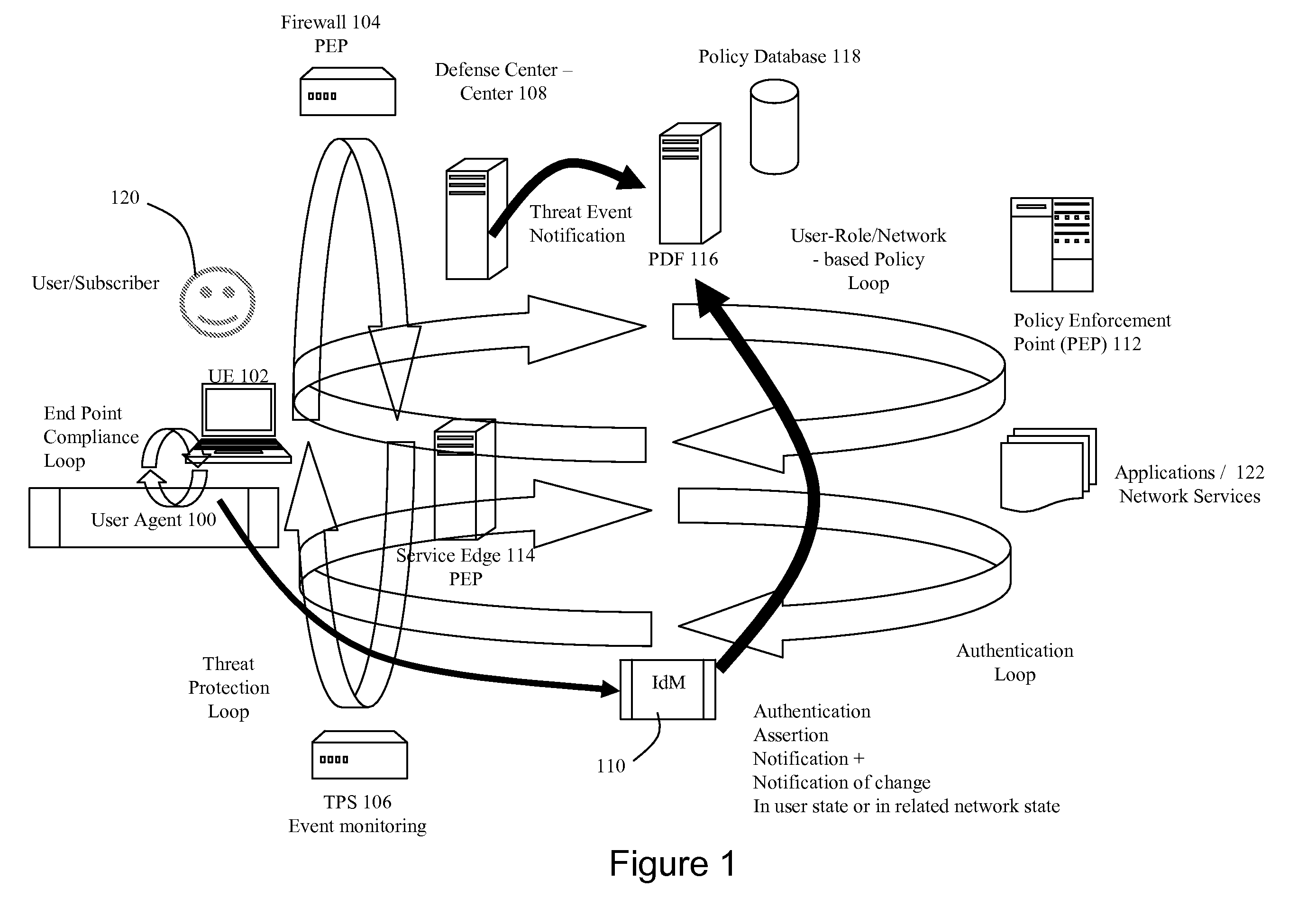
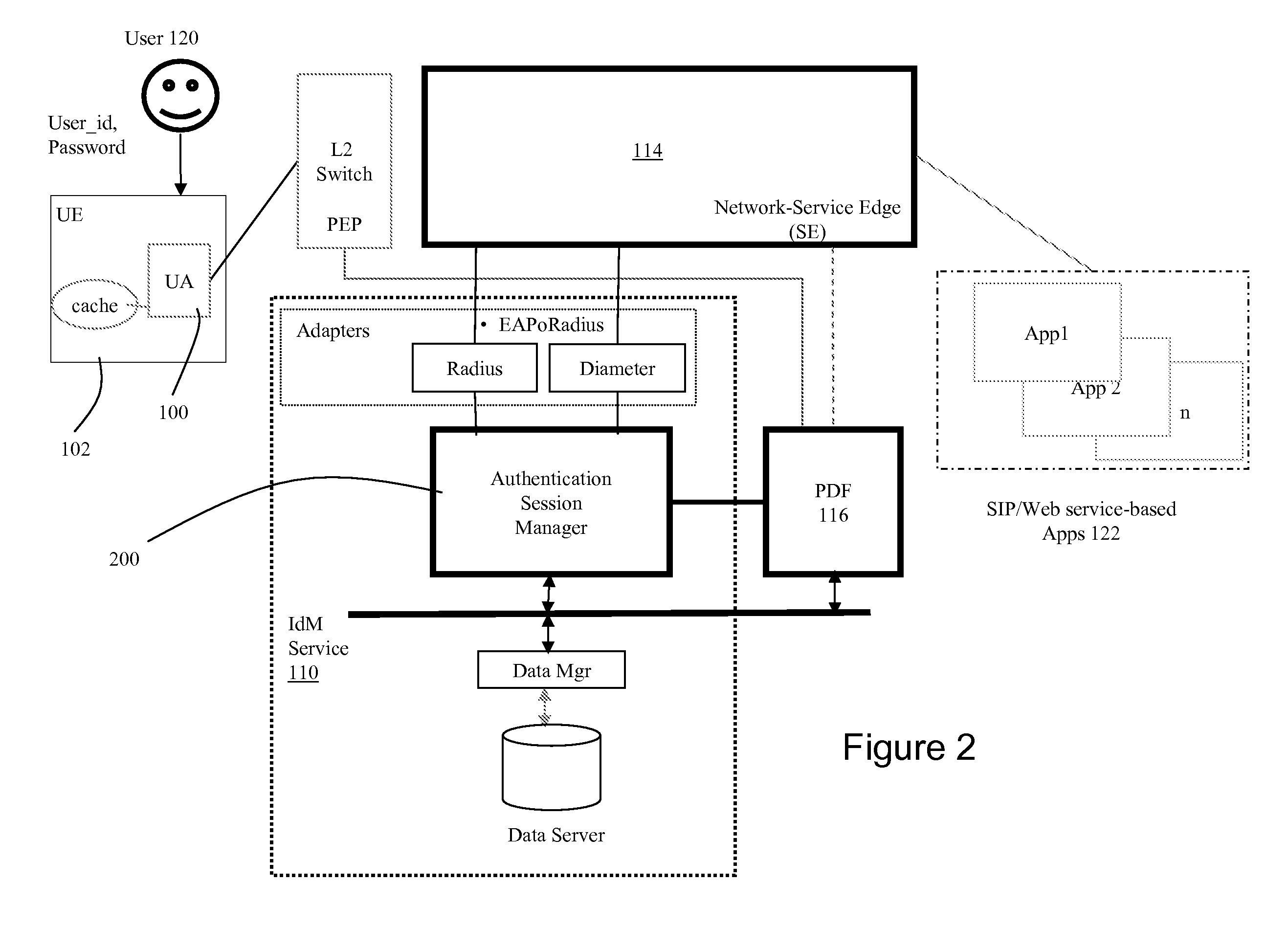
Dynamic Network Identity and Policy management
InactiveUS20070150934A1Network resource is limitedSpecial data processing applicationsSecurity arrangementTarget ResponsePassword
Network policies are managed based at least in-part on user / entity identity information with: a state monitor operable to monitor for state change events in user / entity state and related, network state or in traffic pattern and traffic flow state; an identity manager operable to obtain and validate user credentials; and a policy manager operable in response to a state change event detected by the state monitor (either the identity manager or a defense center) to select a policy based in-part on the user identity obtained by the identity manager or security context obtained by the defense center, and to prompt application of the selected policy. The policies are indicative of user / device authorization entitlements and restrictions to utilization of certain network resources, network services or applications. Dynamic policy selection and targeted responses can be used, for example, against a user who gains network access with stolen user ID and password, and subsequently attempts malicious behavior. In particular, the malicious behavior is detected and identified, and the malicious user can then be restricted from abusing network resources without adversely affecting other users, groups, network devices, and other network services.
Owner:NORTEL NETWORKS LTD
Secure virtual address realm
InactiveUS20040249974A1Convenient introductionMultiple digital computer combinationsTransmissionPrivate networkPublic network
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:INPRO NETWORK FACILITY LLC
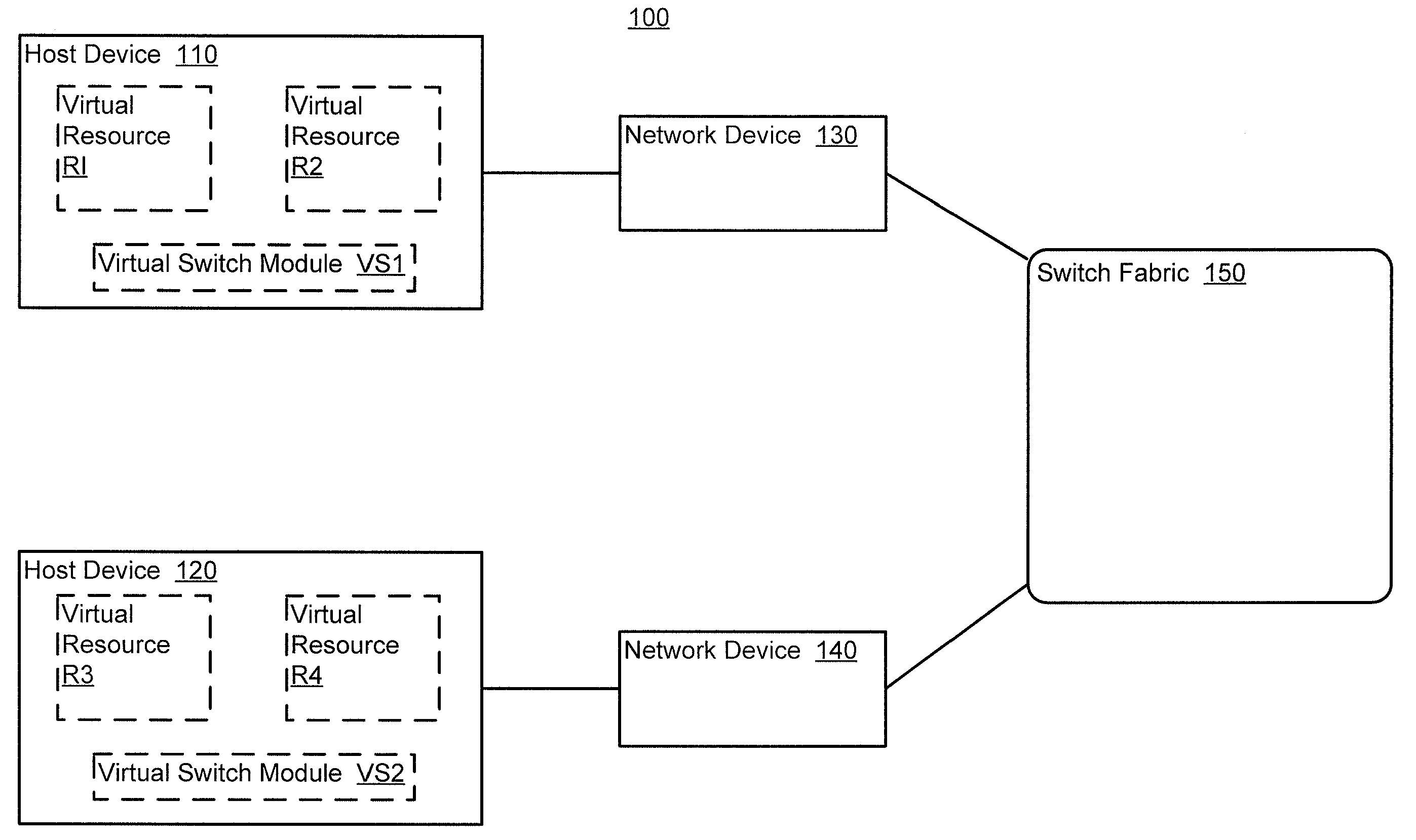
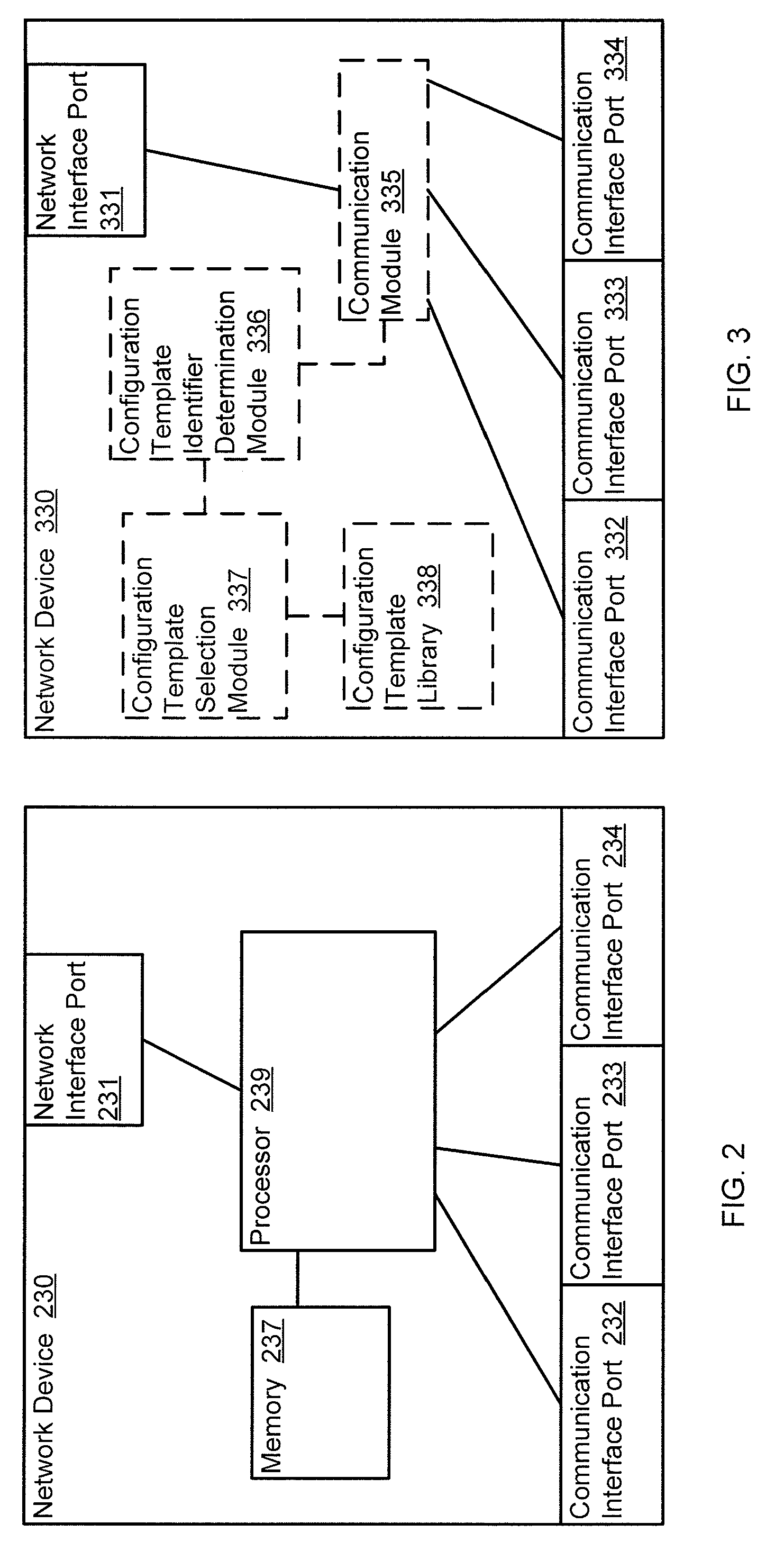
Methods and apparatus for distributed dynamic network provisioning
In one embodiment, a method includes detecting a virtual resource hosted by a host device, selecting a configuration template associated with the virtual resource, and providing a provisioning instruction to a virtual switch module hosted by the host device based on the configuration template. The host device is operatively coupled to a network device. The detecting is at the network device; the selecting is at the network device; and the providing is at the network device. The virtual switch module is in communication with the virtual resource. The configuration template associated with the virtual resource is selected from a library of configuration templates accessible to the network device.
Owner:JUMIPER NETWORKS INC
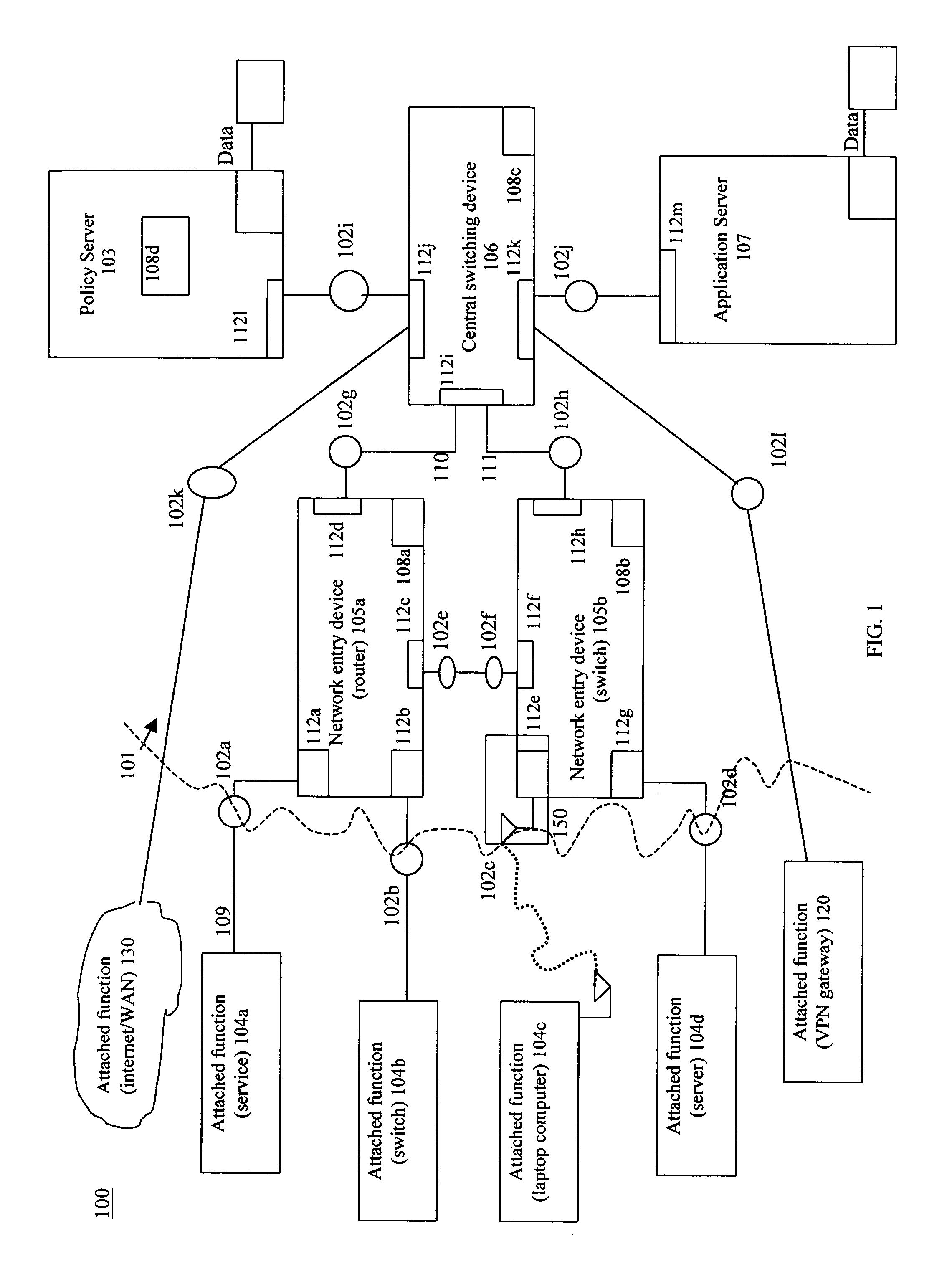
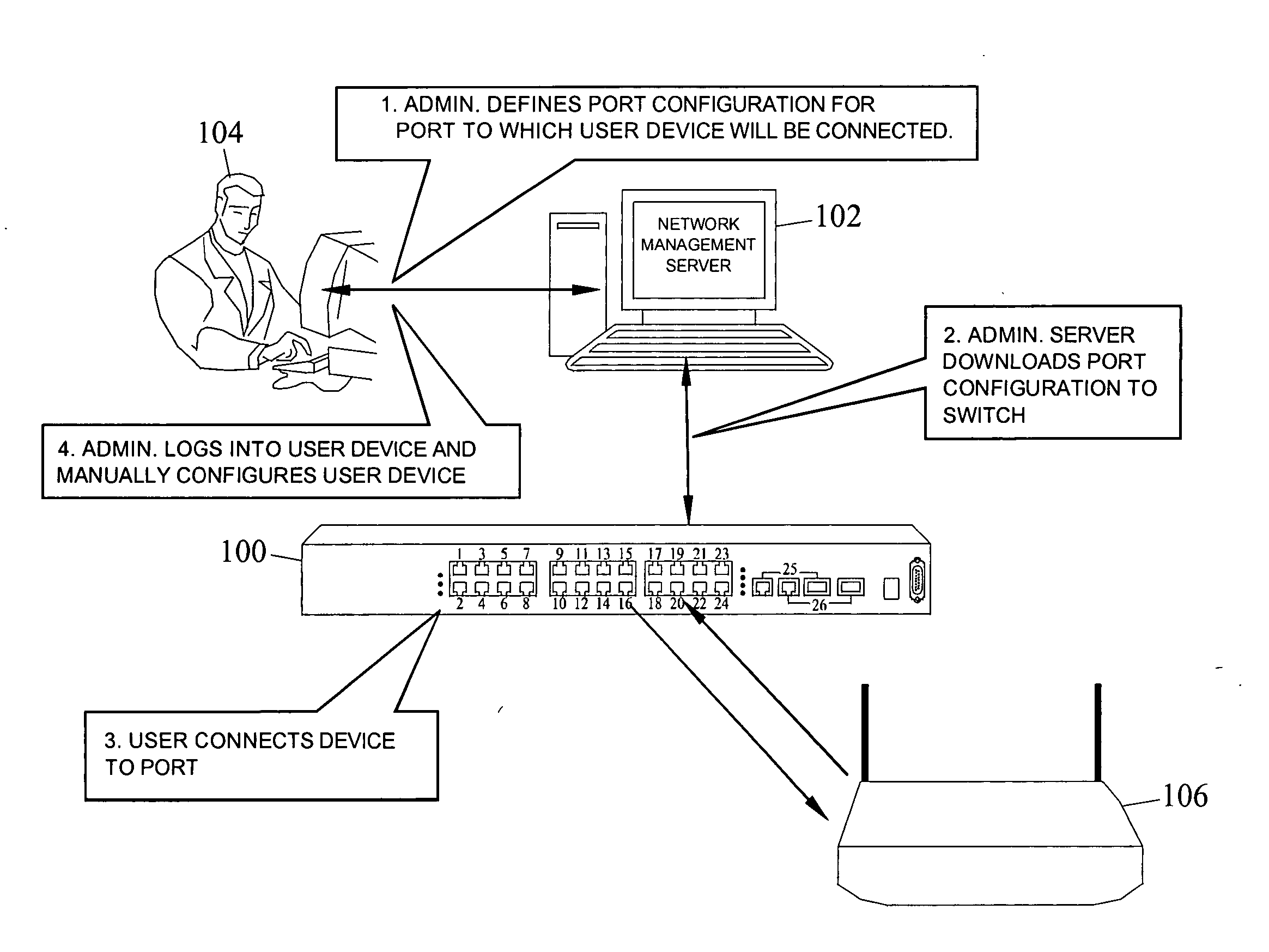
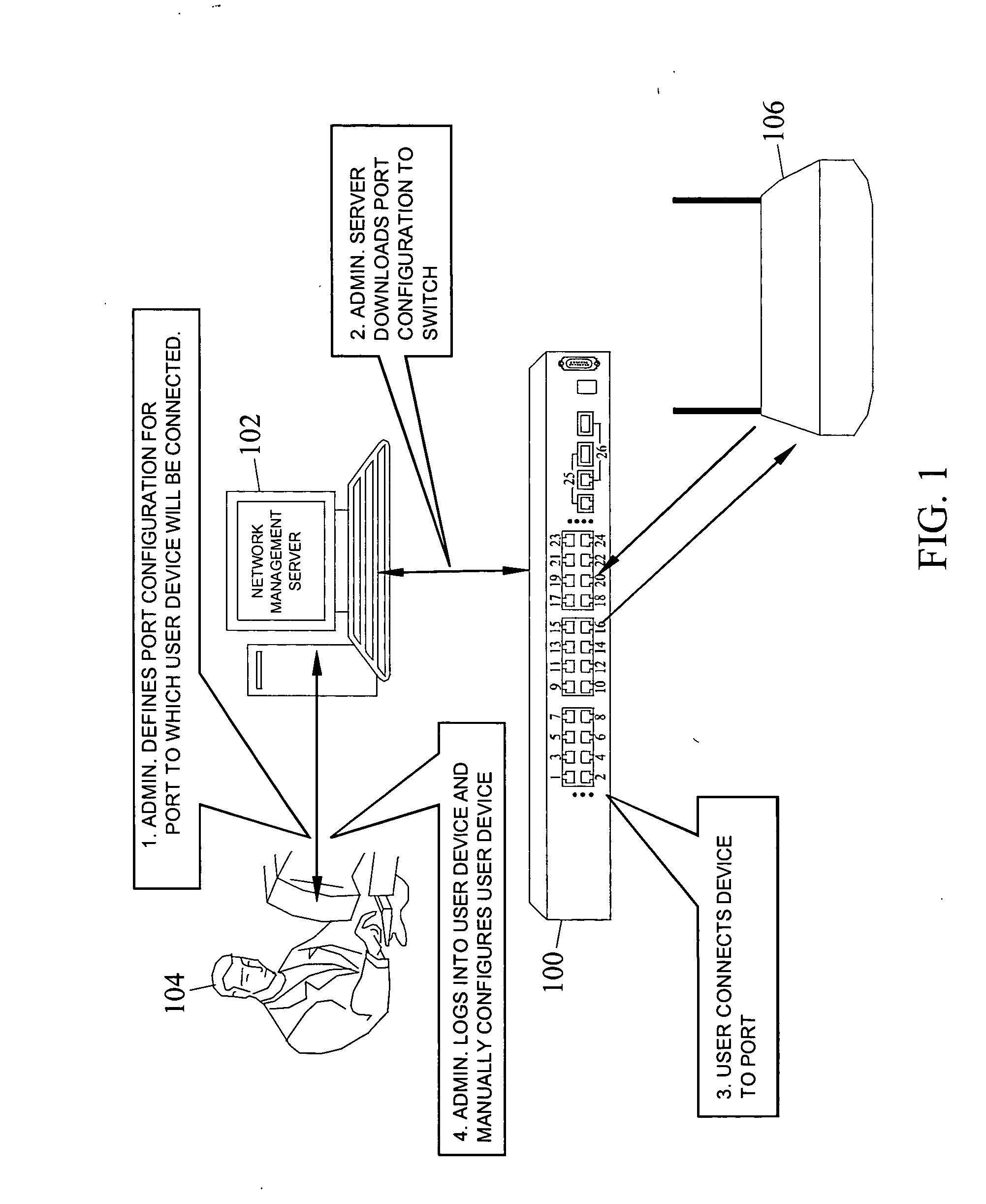
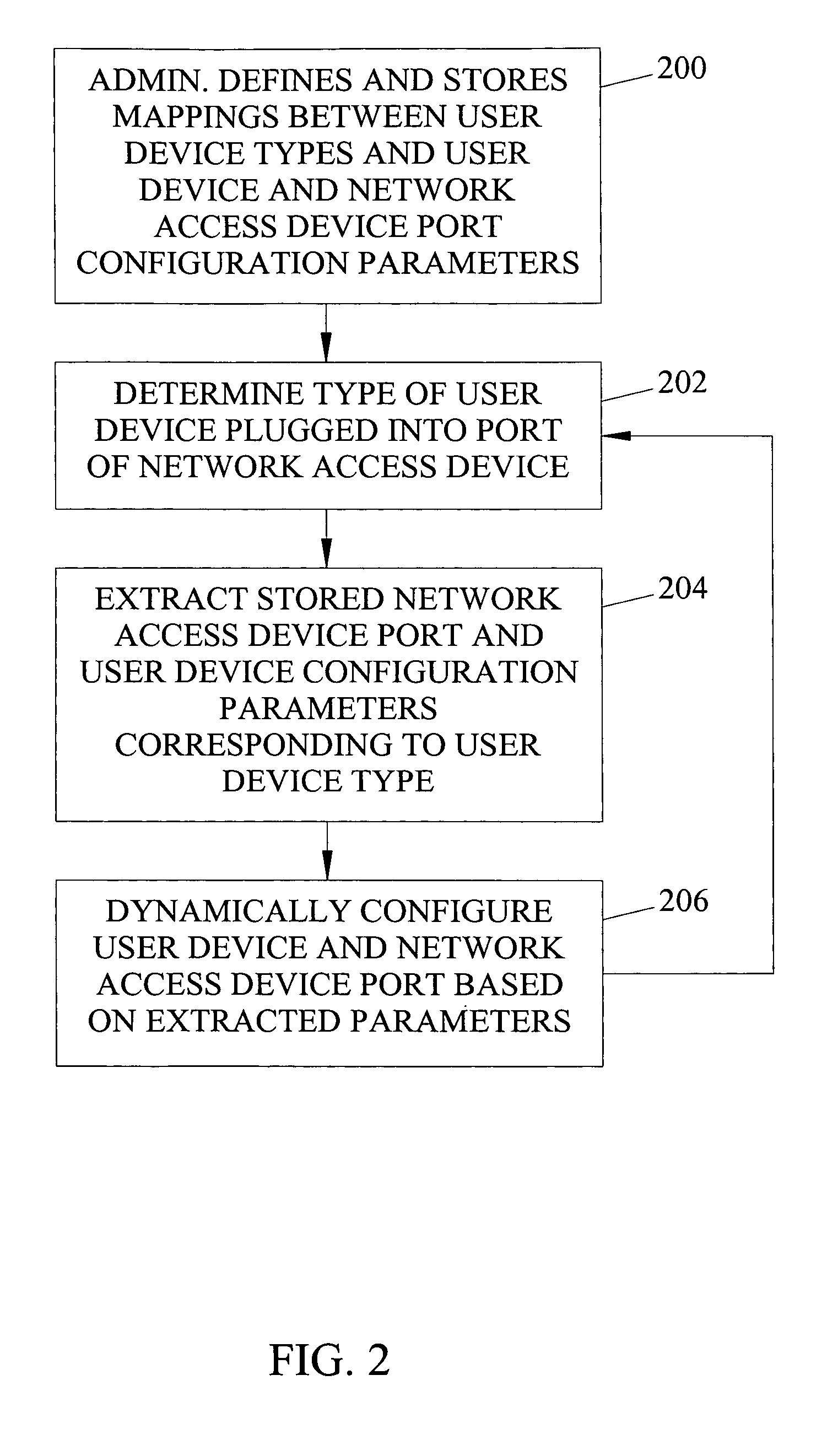
Methods, systems, and computer program products for dynamic network access device port and user device configuration for implementing device-based and user-based policies
Methods, systems, and computer program products for dynamic network access device port and user device configuration are disclosed. According to one method, when a user device is connected to a port of a network access device, the type of user device is determined. The type of user device is used to locate a corresponding port configuration policy. The port to which the device is connected is dynamically configured based on the port configuration policy.
Owner:EXTREME NETWORKS INC
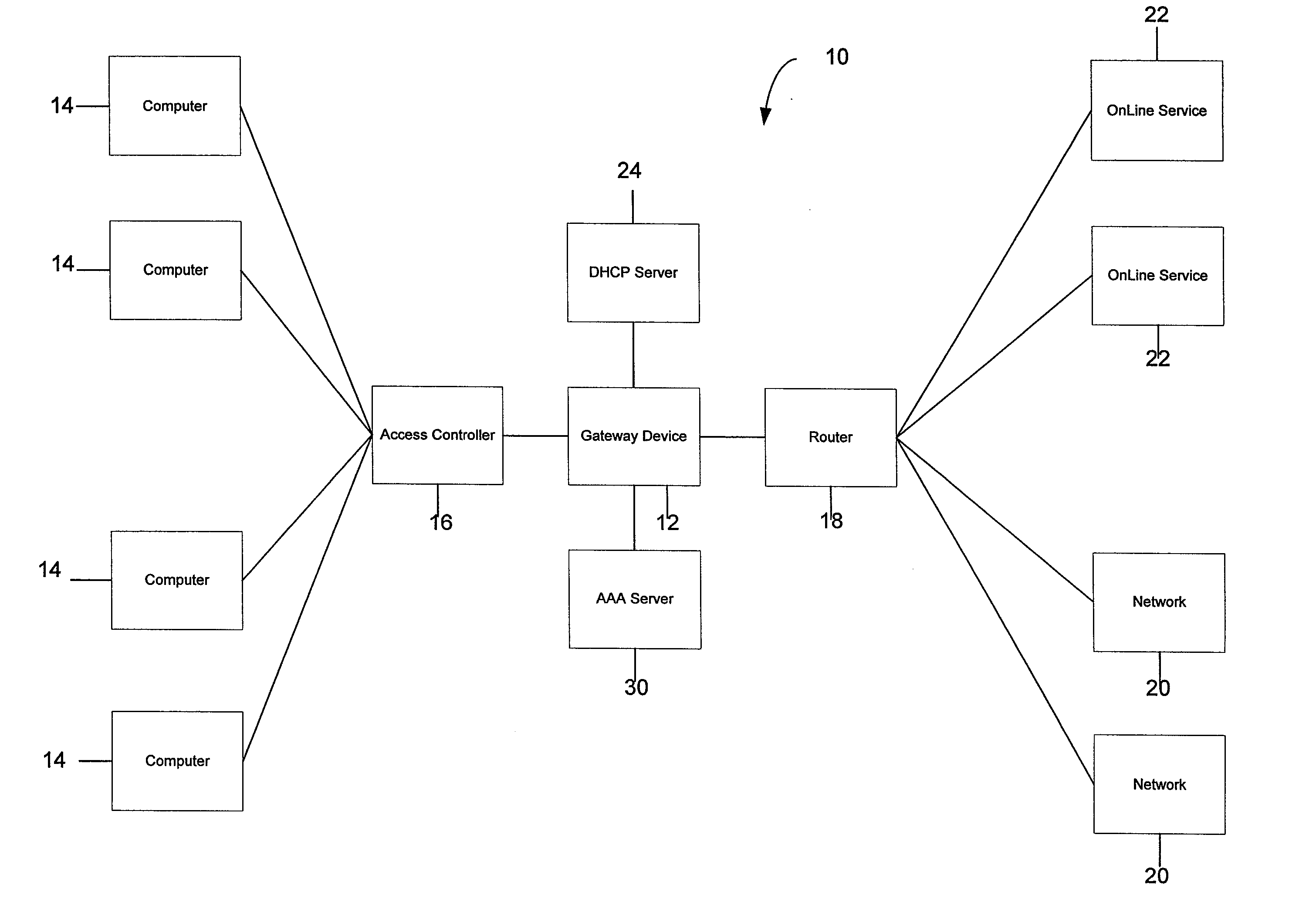
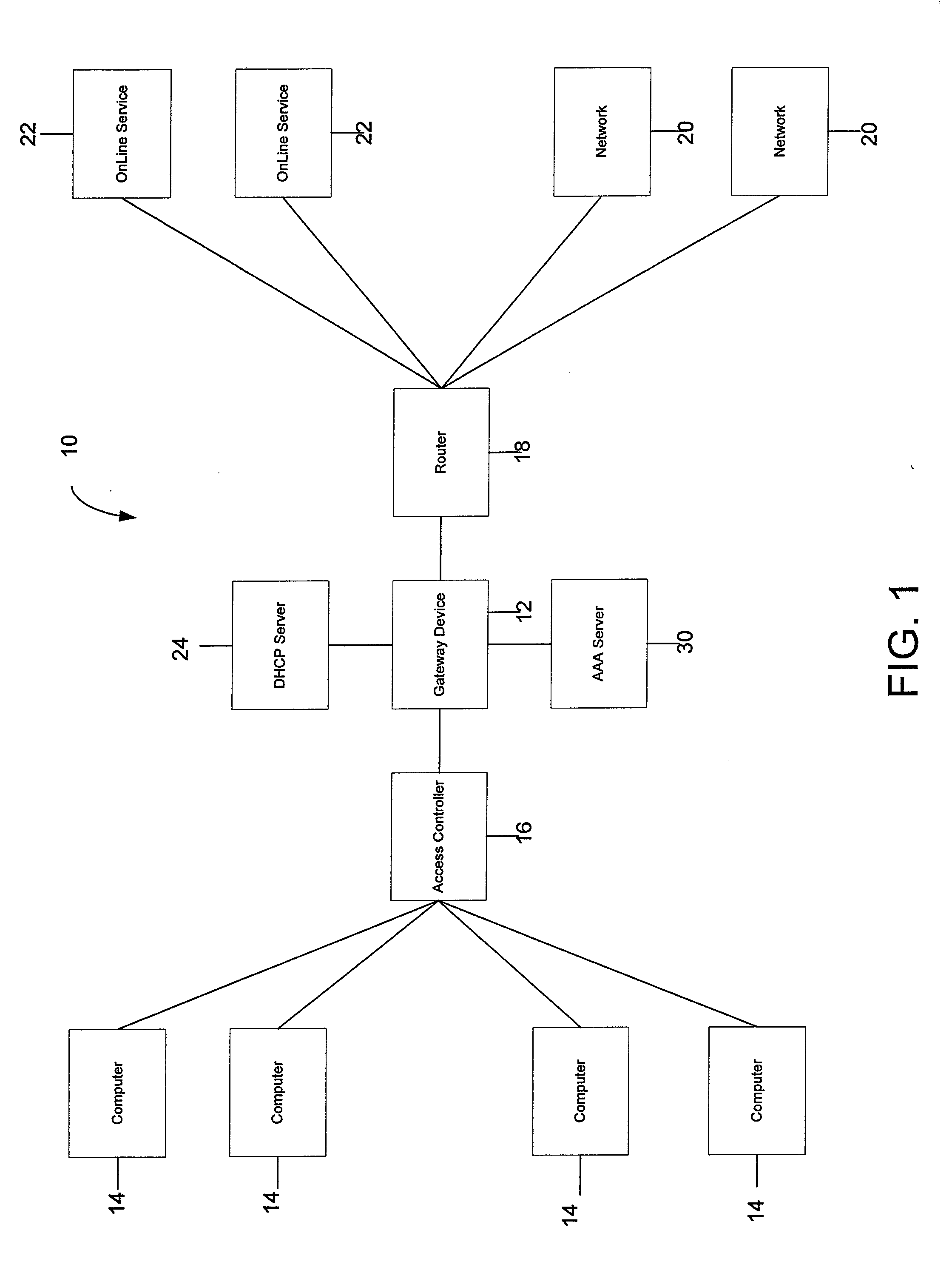
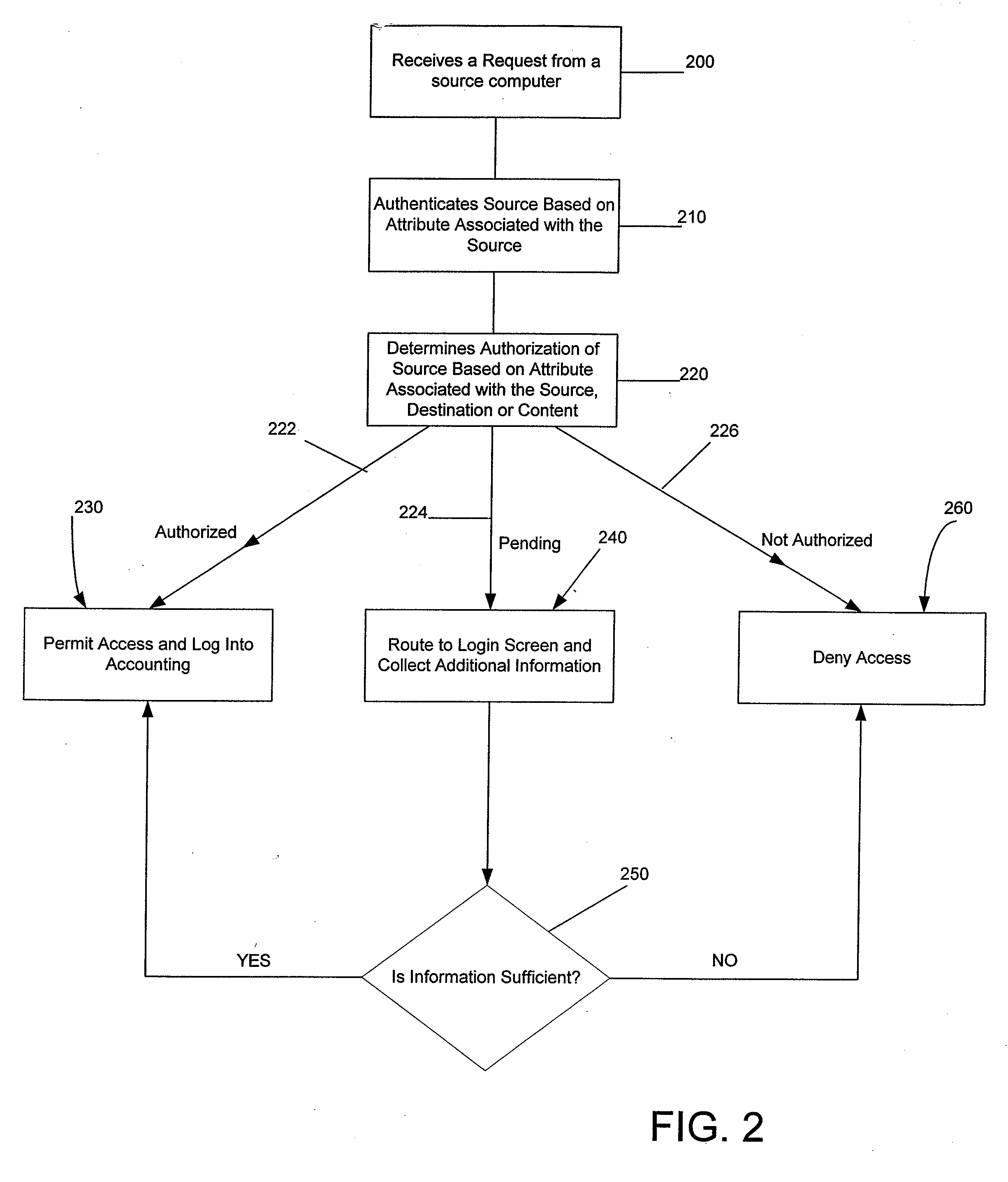
Systems and Methods for Providing Dynamic Network Authorization, Authentication and Accounting
InactiveUS20060239254A1Facilitate transparent accessEasy to addConnection managementData switching by path configurationConfigfsSystem usage
Systems and methods for selectably controlling and customizing source access to a network, where the source is associated with a source computer, and wherein the source computer has transparent access to the network via a gateway device and no configuration software need be installed on the source computer to access the network. A user may be prevented access from a particular destination or site based upon the user's authorization while being permitted to access to other sites that the method and system deems accessible. The method and system can identify a source without that source's knowledge, and can access customizable access rights corresponding to that source in a source profile database. The source profile database can be a remote authentication dial-in user service (RADIUS) or a lightweight directory access protocol (LDAP) database. The method and system use source profiles within the source profile database to dynamically authorize source access to networks and destinations via networks.
Owner:NOMADIX INC
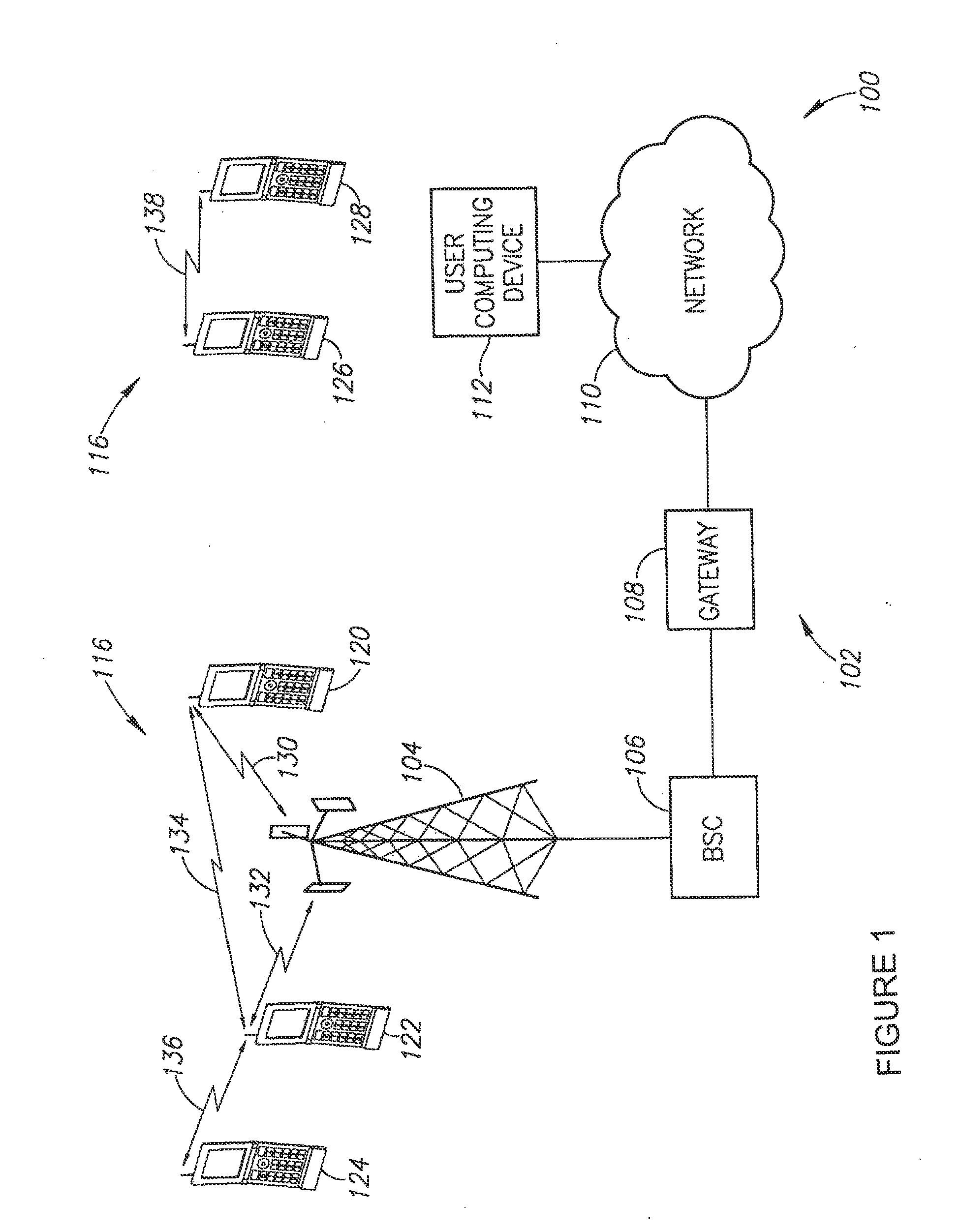
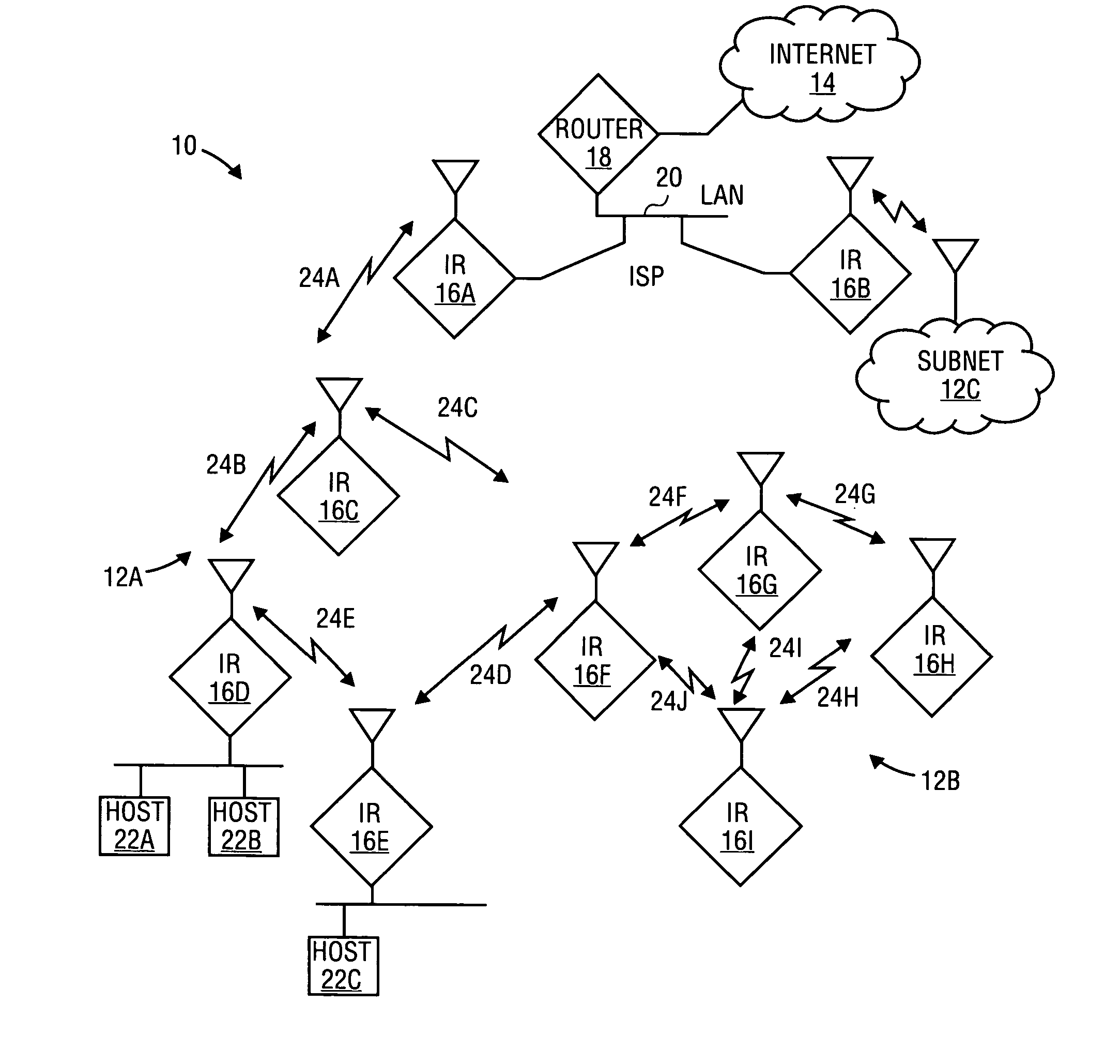
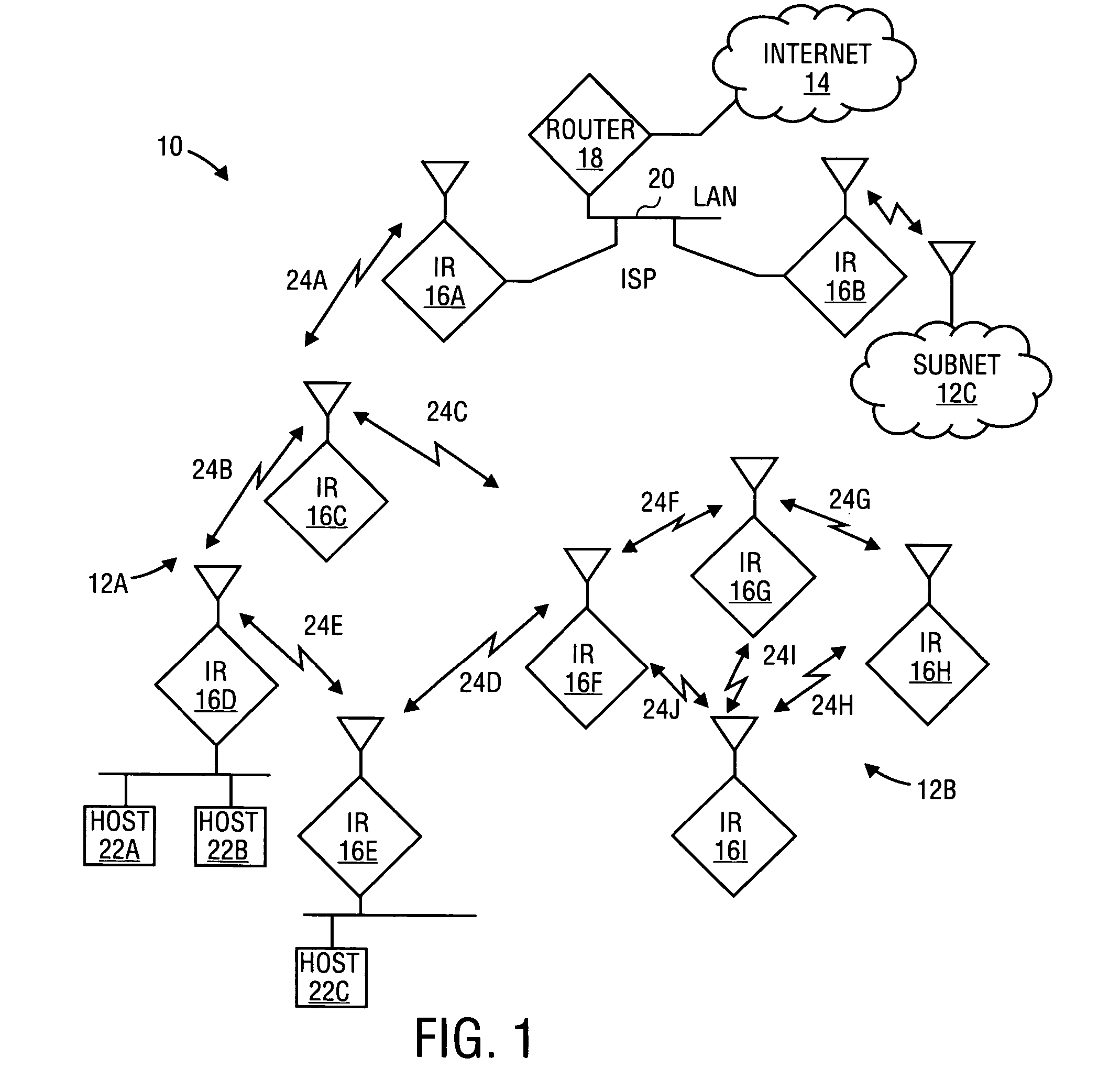
System and method for management of a dynamic network using wireless communication devices
A short-range wireless communication network may be established by direct communication between two or more wireless communication devices. A conventional cellular telephone includes an integrated short-range transceiver. The short-range transceivers of multiple wireless communication devices can be coupled together to form a short-range communication network without utilizing any wireless communication network supported by wireless service providers. The short-range communication network may be extended as additional devices come within range or consolidated as wireless communication devices leave the communication range. The short-range communication network is built upon the proximity of wireless communication devices with each other. Data is disseminated between the wireless communication devices using a data message synchronization process. Messages may also be carried from one wireless network to another as the communication devices are carried by individuals.
Owner:IP INVESTEMENT HOLDINGS LLC
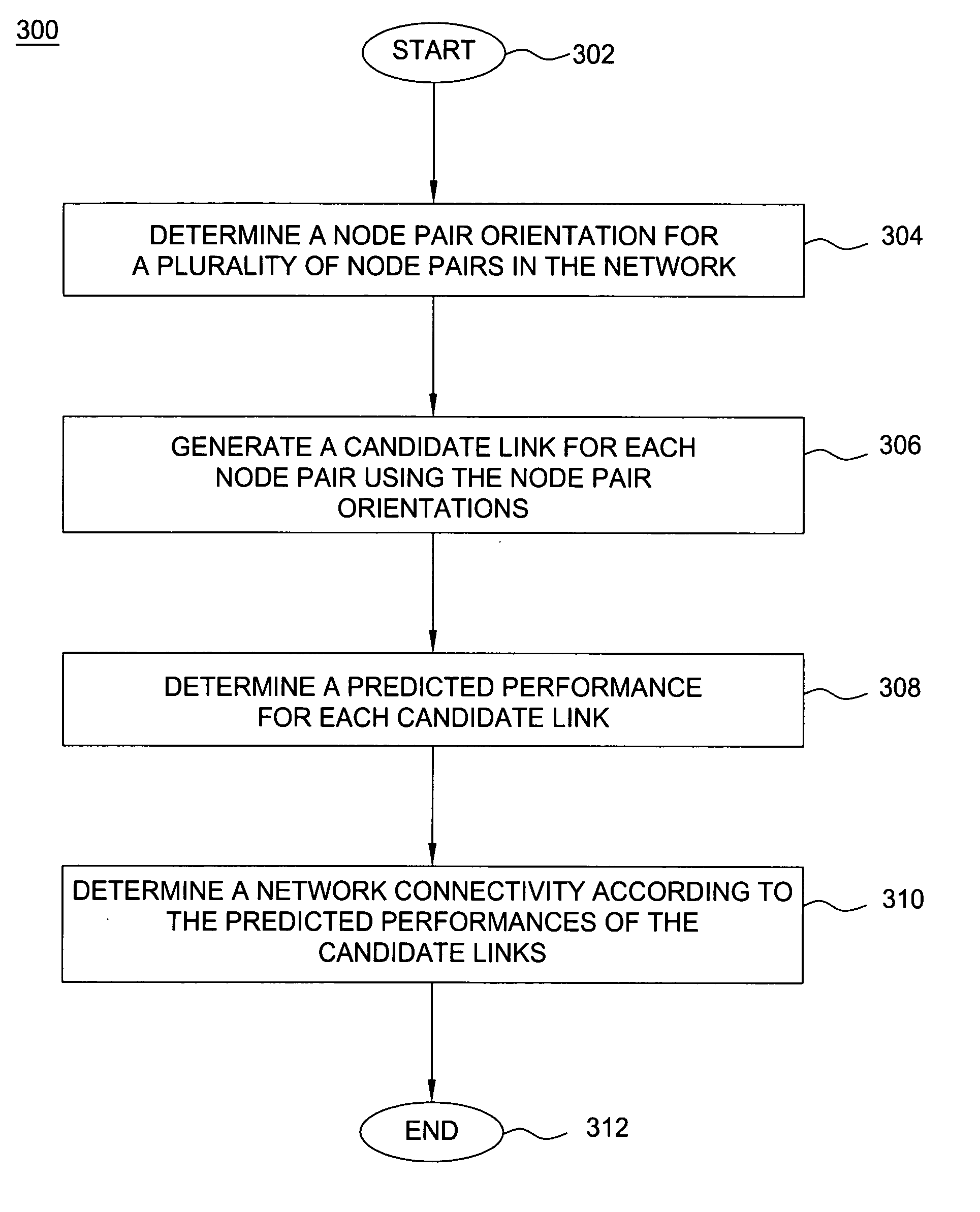
Method and apparatus for identifying network connectivity changes in dynamic networks
InactiveUS20070253341A1Minimize impactOn end-to-end network connectivityError preventionFrequency-division multiplex detailsPredicting performanceNetwork topology
The invention comprises a method and apparatus for determining a network connectivity in a network having a plurality of nodes. In particular, one embodiment of the method includes generating a candidate link for each of a plurality of node pairs, predicting a performance of each candidate link by evaluating an expected impact of at least one condition on each candidate link, and determining the network topology using the predicted performances of the candidate links. The performance of each candidate link may be predicted by identifying at least one condition, determining the expected impact of the at least one condition on the candidate link, and predicting the performance of the candidate link by adjusting an expected performance of the candidate link using the expected impact of the at least one condition on the candidate link.
Owner:WSOU INVESTMENTS LLC
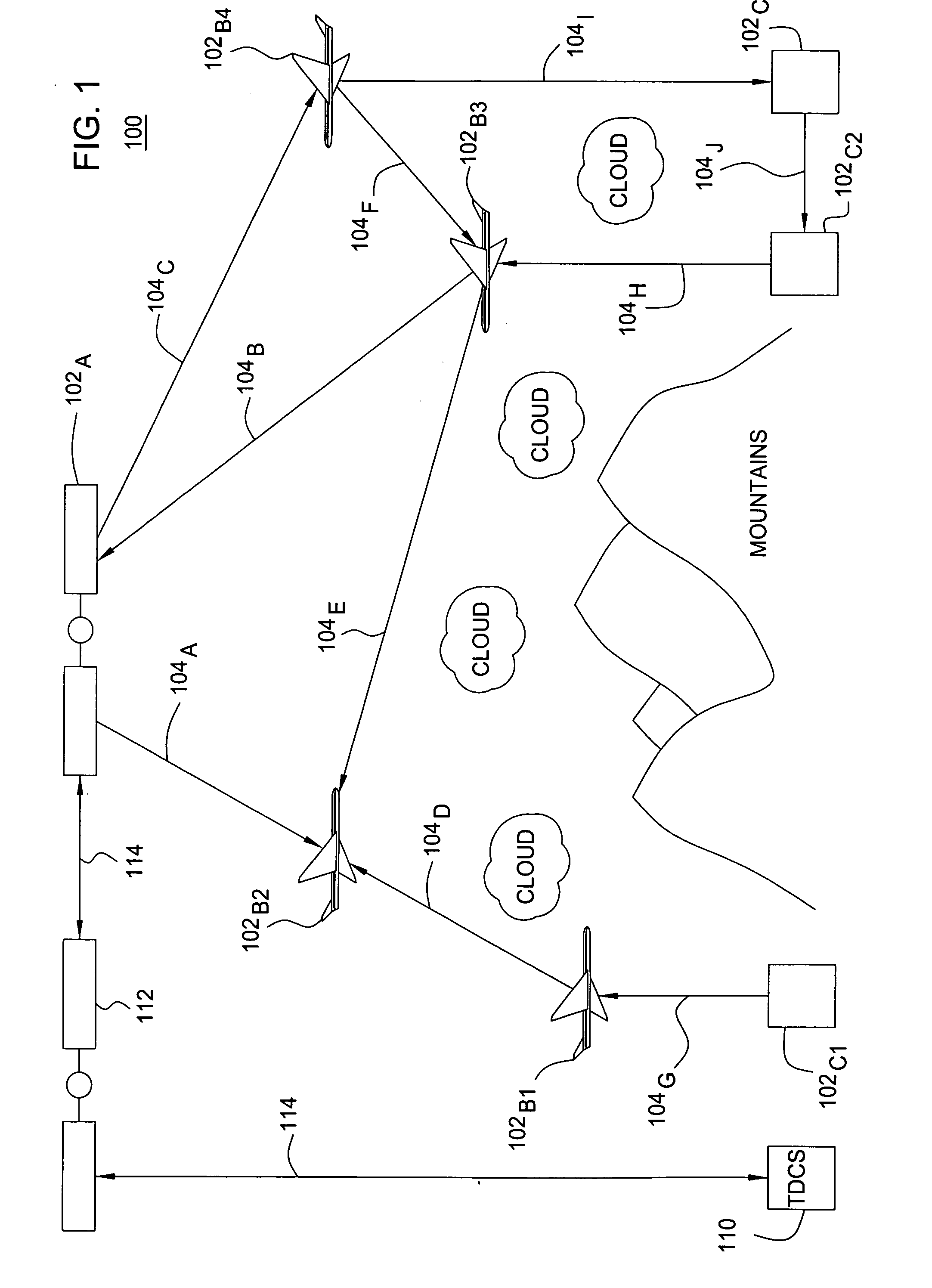
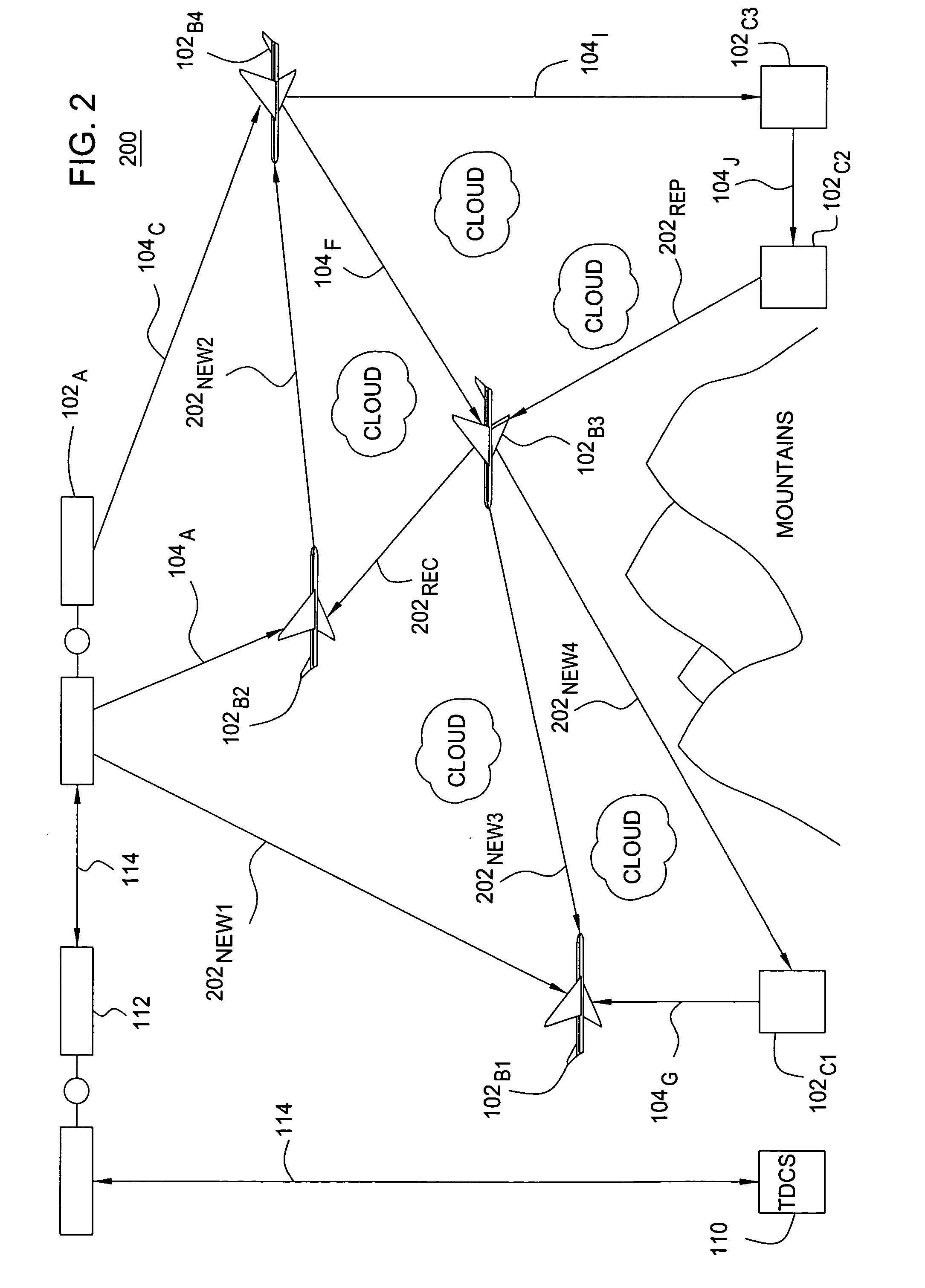
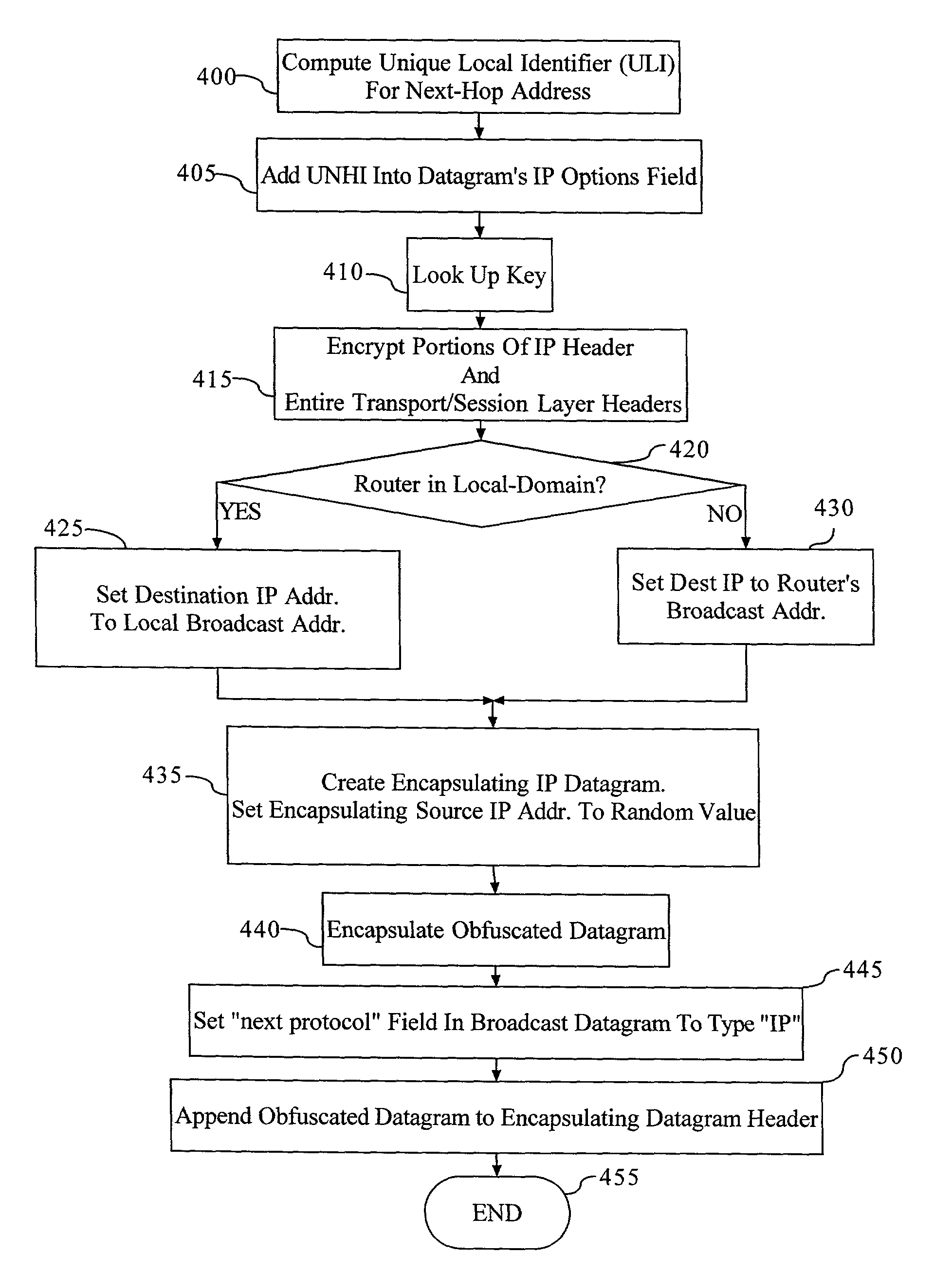
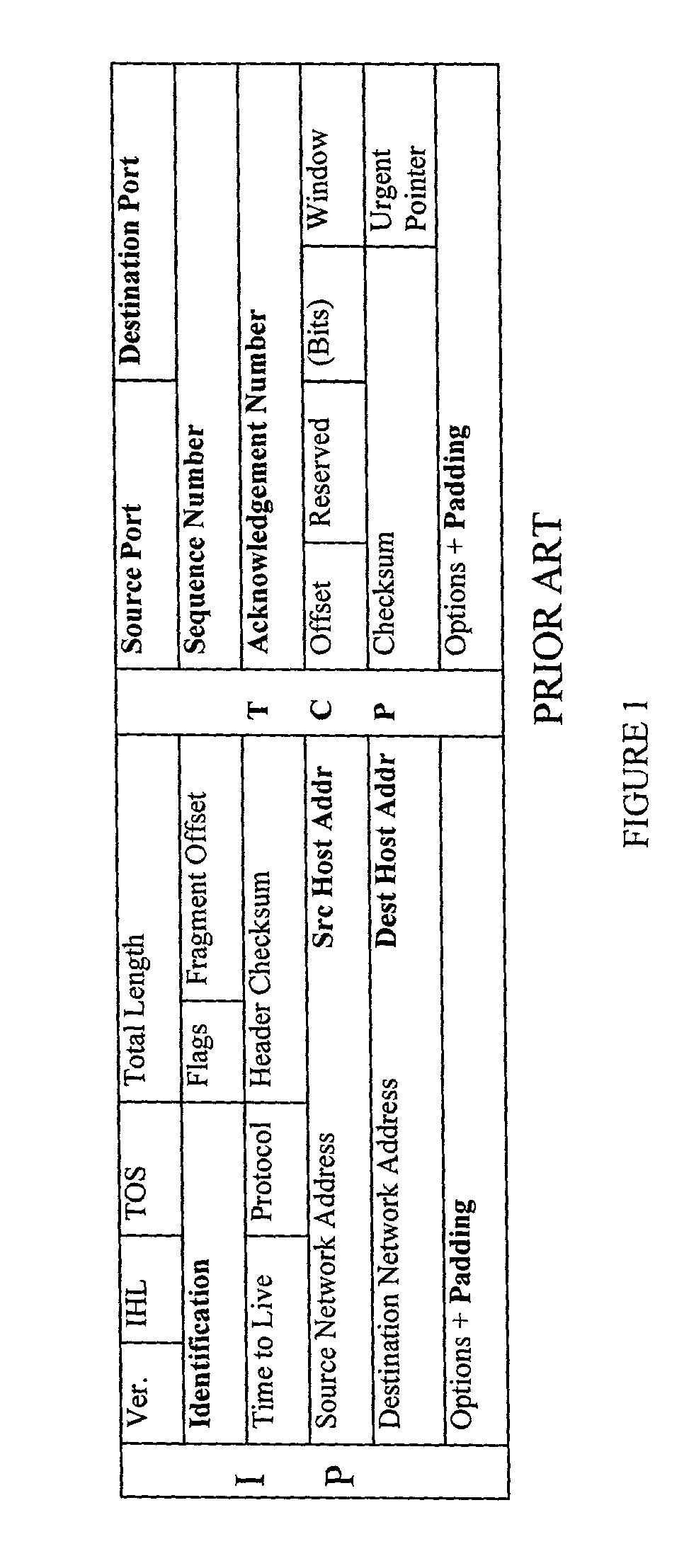
Method and apparatus for anonymous IP datagram exchange using dynamic network address translation
Methods, apparatus, system and computer program are provided for concealing the identity of a network device transmitting a datagram having a network layer header. A unique local identifier and broadcast address are determined in accordance with a next-hop address. A partially encrypted network layer header is determined by encrypting a plurality of identifying portions of the network layer header, where one portion of the network layer header is the unique local identifier. The datagram is encapsulated with another network layer header whose address is set to the broadcast address. The encapsulated datagram can be received and detunneled, and an address of a recipient can be extracted from the network layer header. The datagram is then admitted into a network domain.
Owner:VERIZON PATENT & LICENSING INC +1
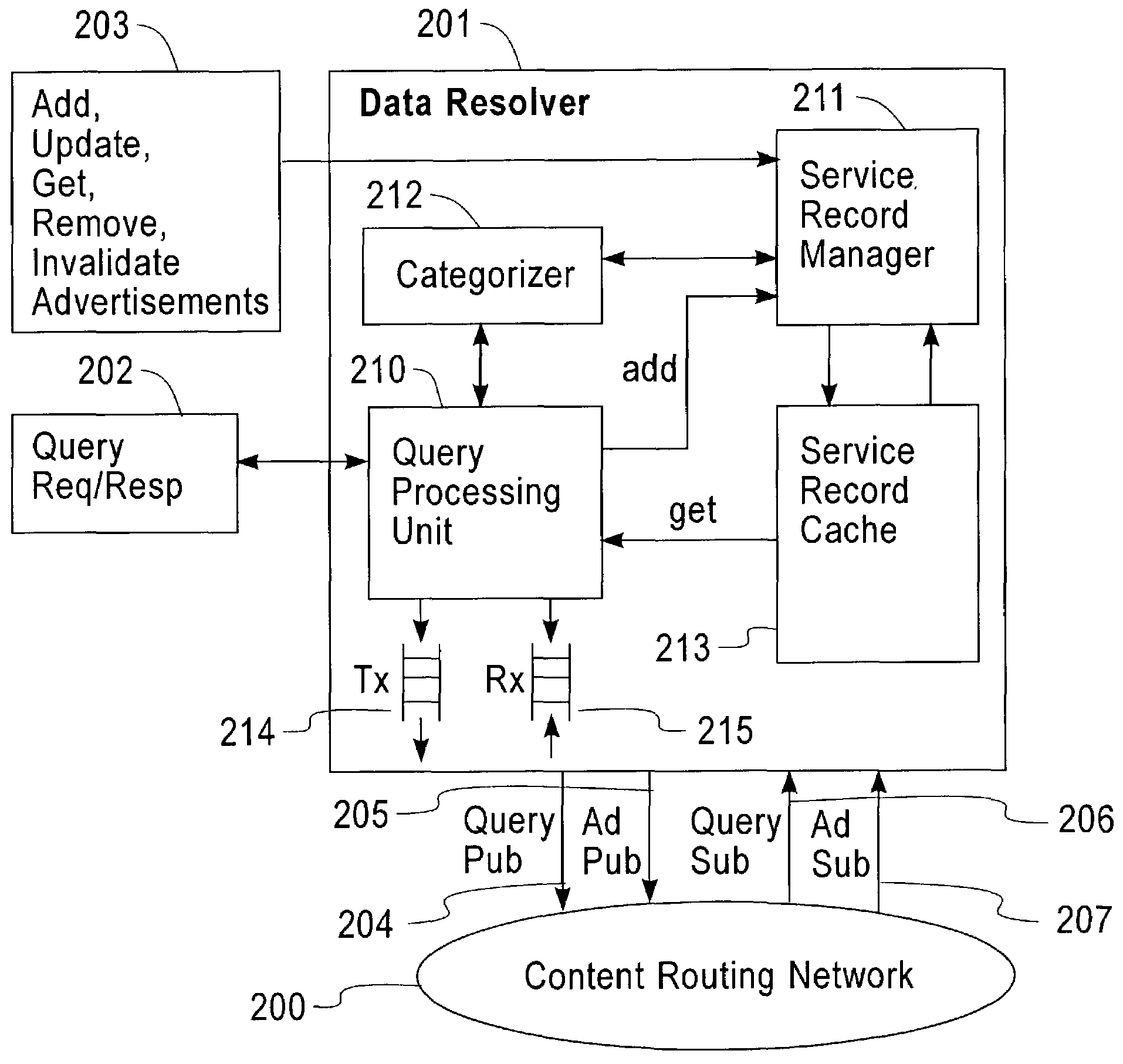
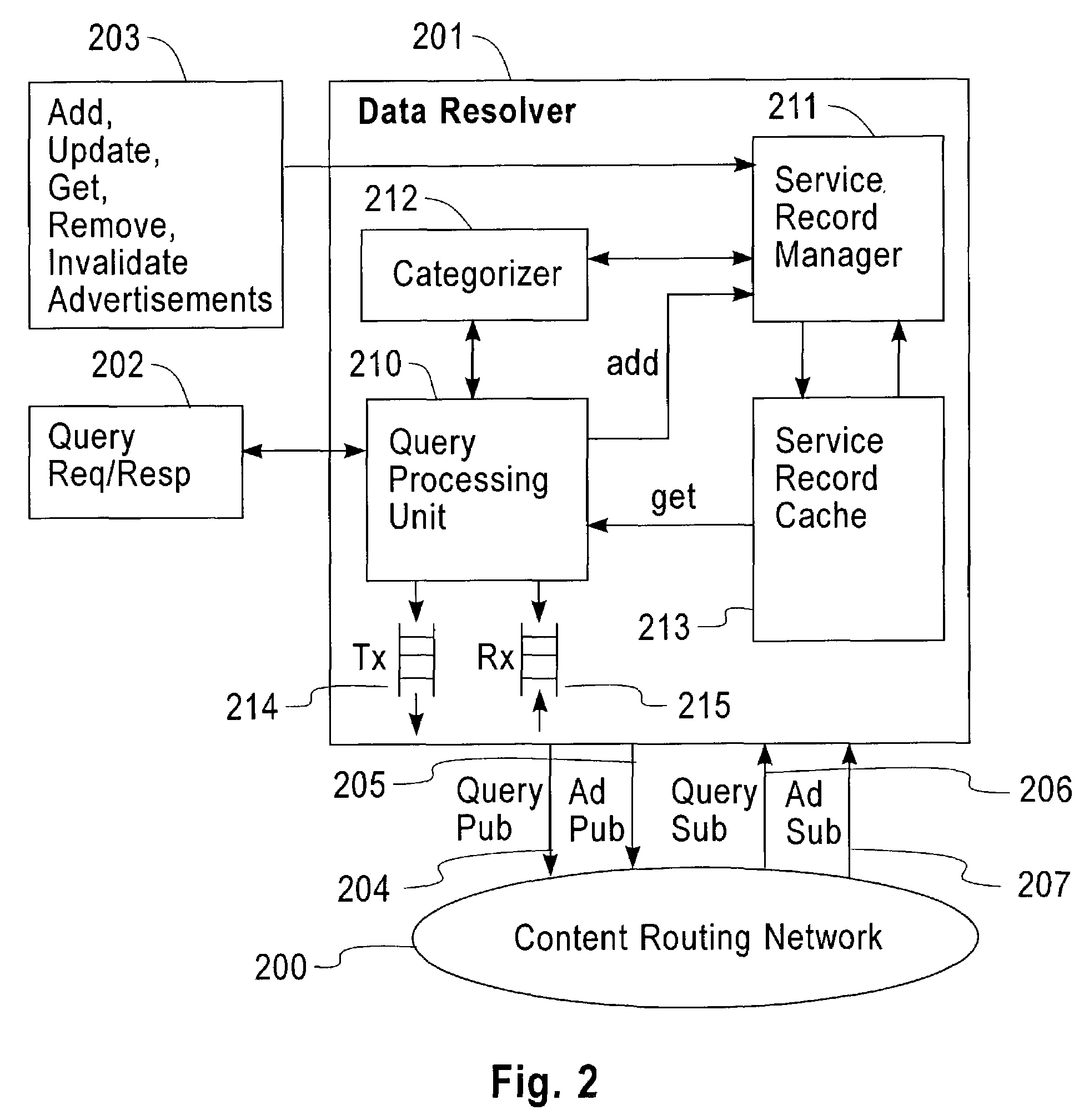
Method and apparatus for discovery of dynamic network services
InactiveUS7181442B2Robustness of data is easilyHigh-performance and scalableData processing applicationsDigital data processing detailsService provisionNetwork service
A framework of a service directory that can handle service records changing rapidly is provided by using a content-based routing network. A directory node for providing the service directory is called a data resolver. The data resolver listens for service advertisements for certain service categories from service providers, and stores such advertisement data in the form of service records in a local cache. If a data resolver receives a query for some services, it first looks in the cache. If the cache contains at least one service record that satisfies the query, the data resolver returns the record. Otherwise, the data resolver issues a secondary query corresponding to the query it received, to other data resolvers connected by the content-based routing network. Simultaneously, the data resolver begins listening for service advertisements (service records) from other data resolvers on the content-based routing network.
Owner:IBM CORP
Automatic quality of service based resource allocation
ActiveUS20050064873A1Network traffic/resource managementConnection managementQuality of serviceTelecommunications link
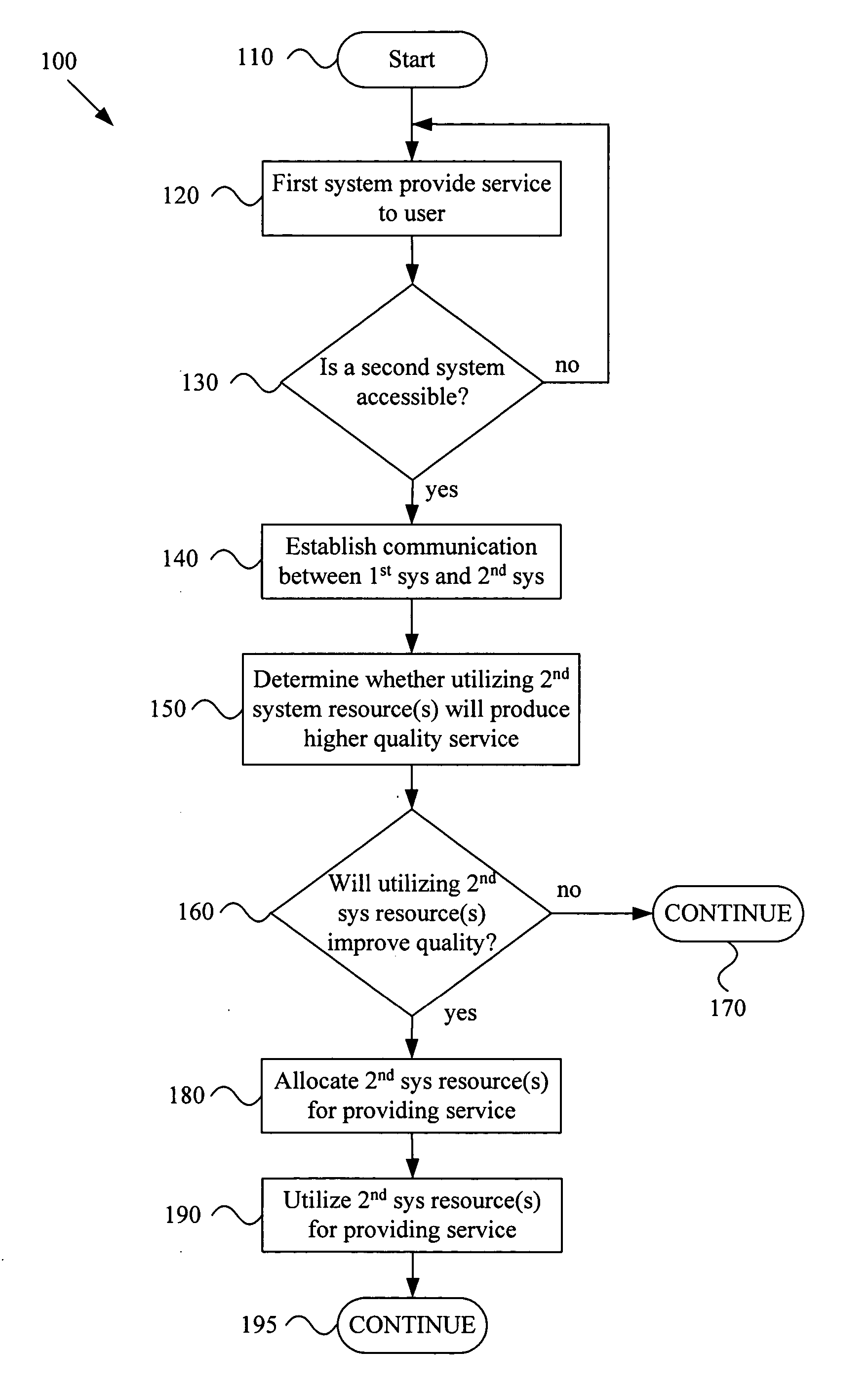
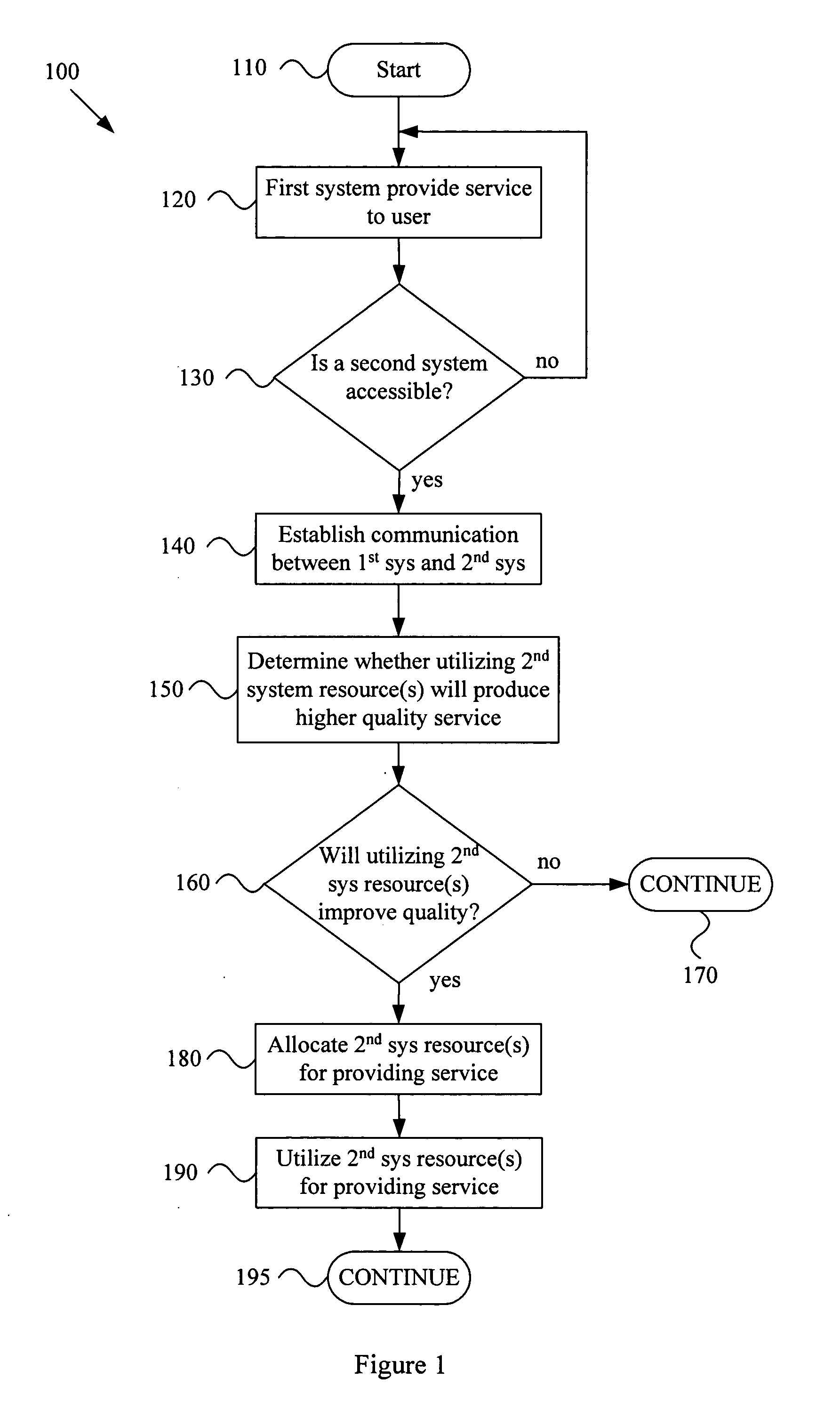
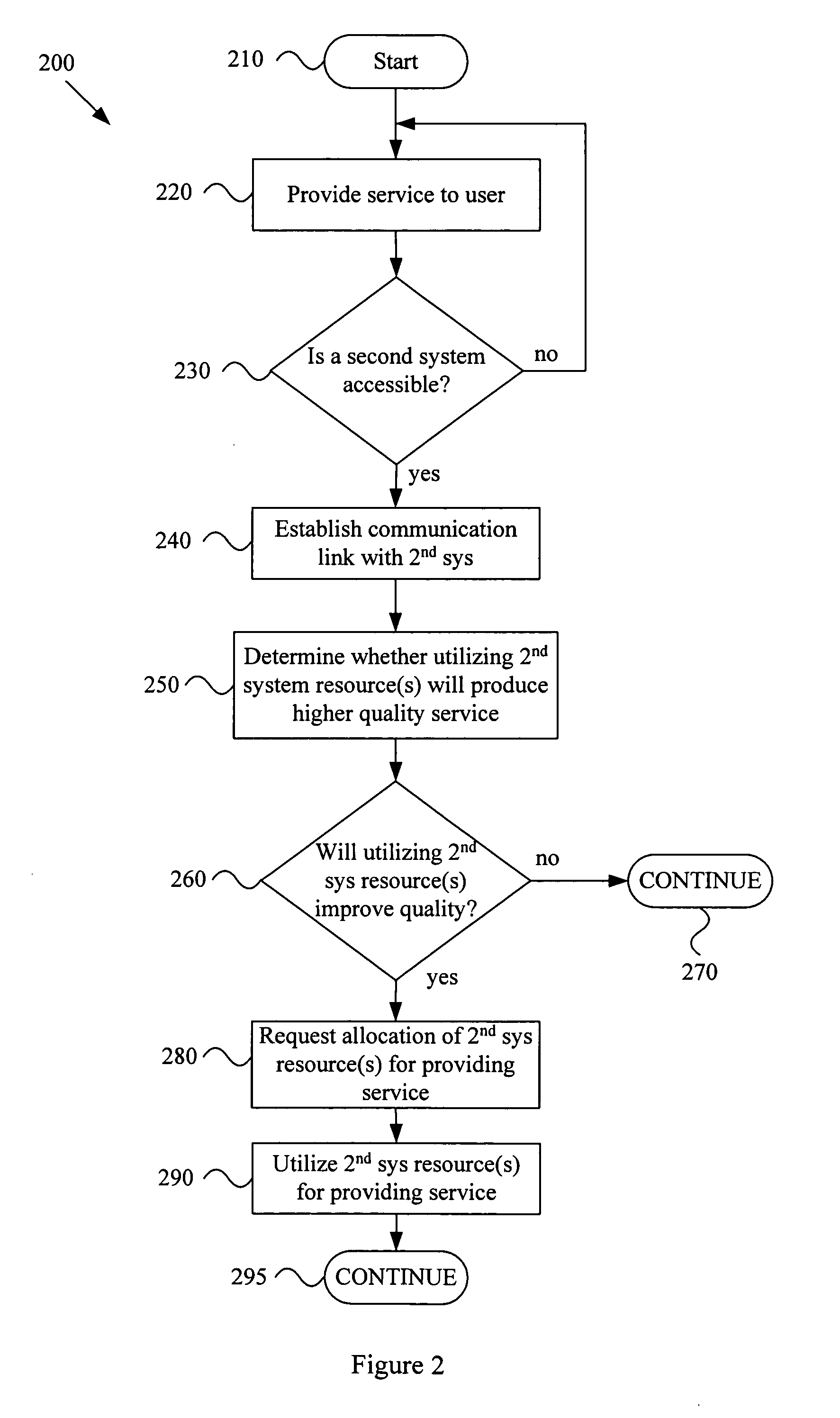
A system and method for providing quality-of-service based network resource allocation and utilization in a dynamic network environment. For example, a wireless communication network may comprise a first system and a second system. The first system may provide a current service to a user at a current quality level. The first system and second system may establish a wireless communication link. At least one of the first and second systems may determine whether utilizing one or more resources of the second system will provide the current service to the user at a higher level of quality than the current quality level. One or more resources of the second system may be allocated for providing the current service to a user at a higher quality level. The allocated resources may be utilized to provide the current service to the user at a higher quality level than the current quality level.
Owner:AVAGO TECH INT SALES PTE LTD
Method and System for Dynamic Network Intrusion Monitoring, Detection and Response
InactiveUS20070162973A1Eliminate false positivesIncrease in sizeMemory loss protectionError detection/correctionData miningProblem resolution
A probe attached to a customer's network collects status data and other audit information from monitored components of the network, looking for footprints or evidence of unauthorized intrusions or attacks. The probe filters and analyzes the collected data to identify potentially security-related events happening on the network. Identified events are transmitted to a human analyst for problem resolution. The analyst has access to a variety of databases (including security intelligence databases containing information about known vulnerabilities of particular network products and characteristics of various hacker tools, and problem resolution databases containing information relevant to possible approaches or solutions) to aid in problem resolution. The analyst may follow a predetermined escalation procedure in the event he or she is unable to resolve the problem without assistance from others. Various customer personnel can be alerted in a variety of ways depending on the nature of the problem and the status of its resolution. Feedback from problem resolution efforts can be used to update the knowledge base available to analysts for future attacks and to update the filtering and analysis capabilities of the probe and other systems.
Owner:BT AMERICAS
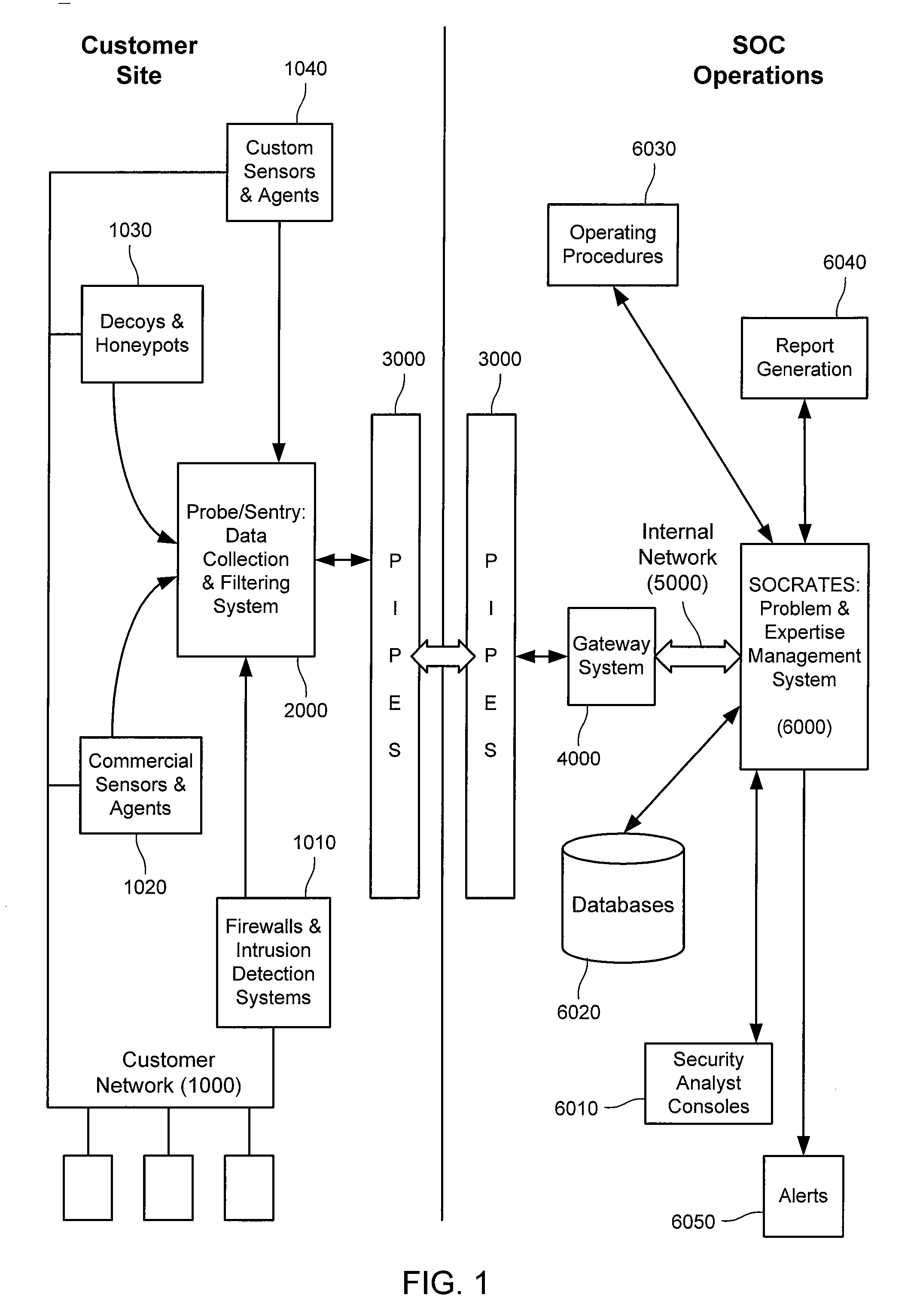
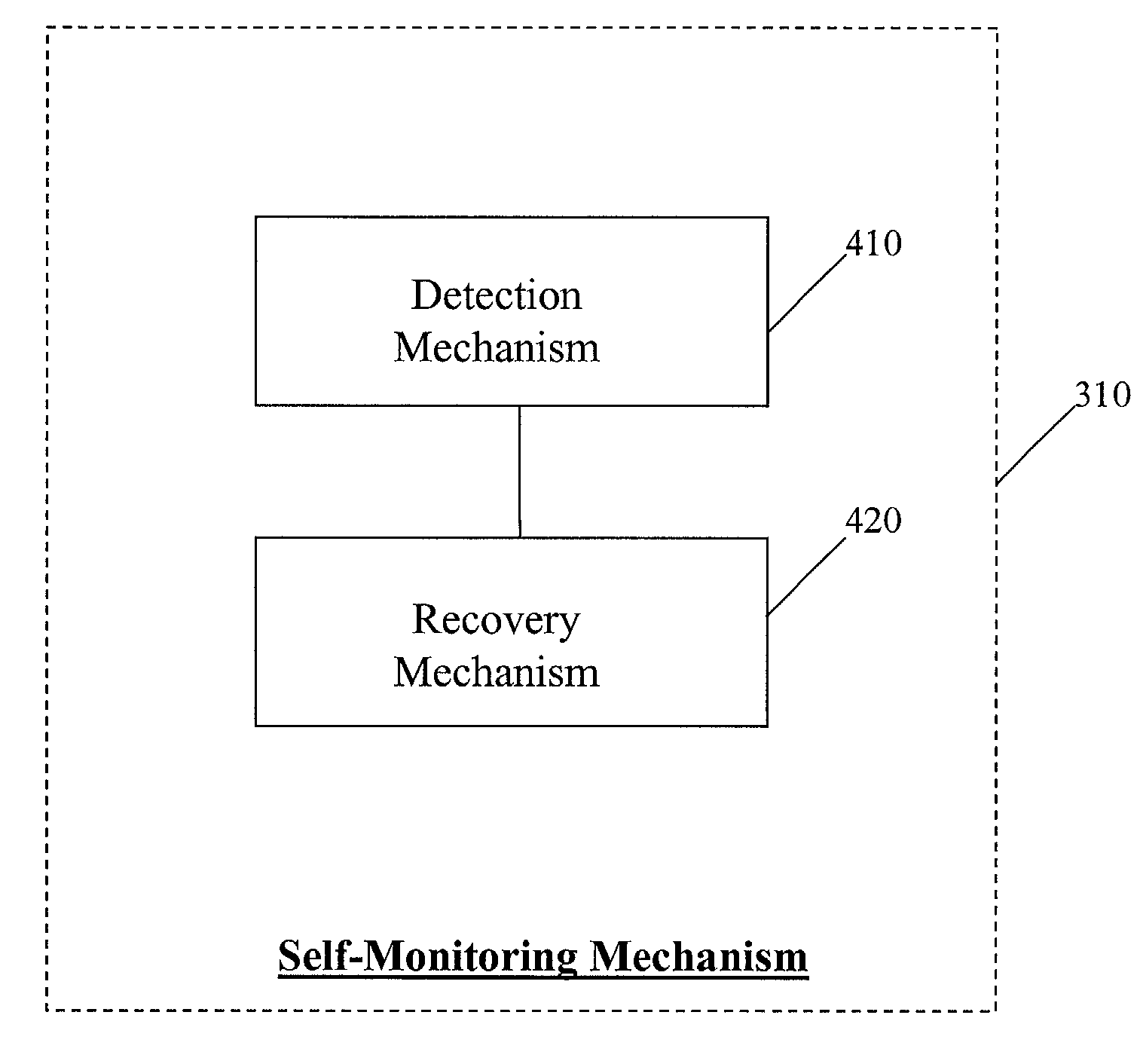
Self-monitoring mechanism in fault-tolerant distributed dynamic network systems
A fault-tolerant server group operating in client-server distributed dynamic network system environment includes a master server and at least one back-up server. The master server registers its mastership in a name server. The master server communicates with the client and the back-up servers. Each server in the fault-tolerant server group has a self-monitoring mechanism, ensuring a consistent mastership. The fault-tolerant server group processes the request from the client to generate a processing result. The processing result is sent from the master server to the client.
Owner:NORTEL NETWORKS LTD
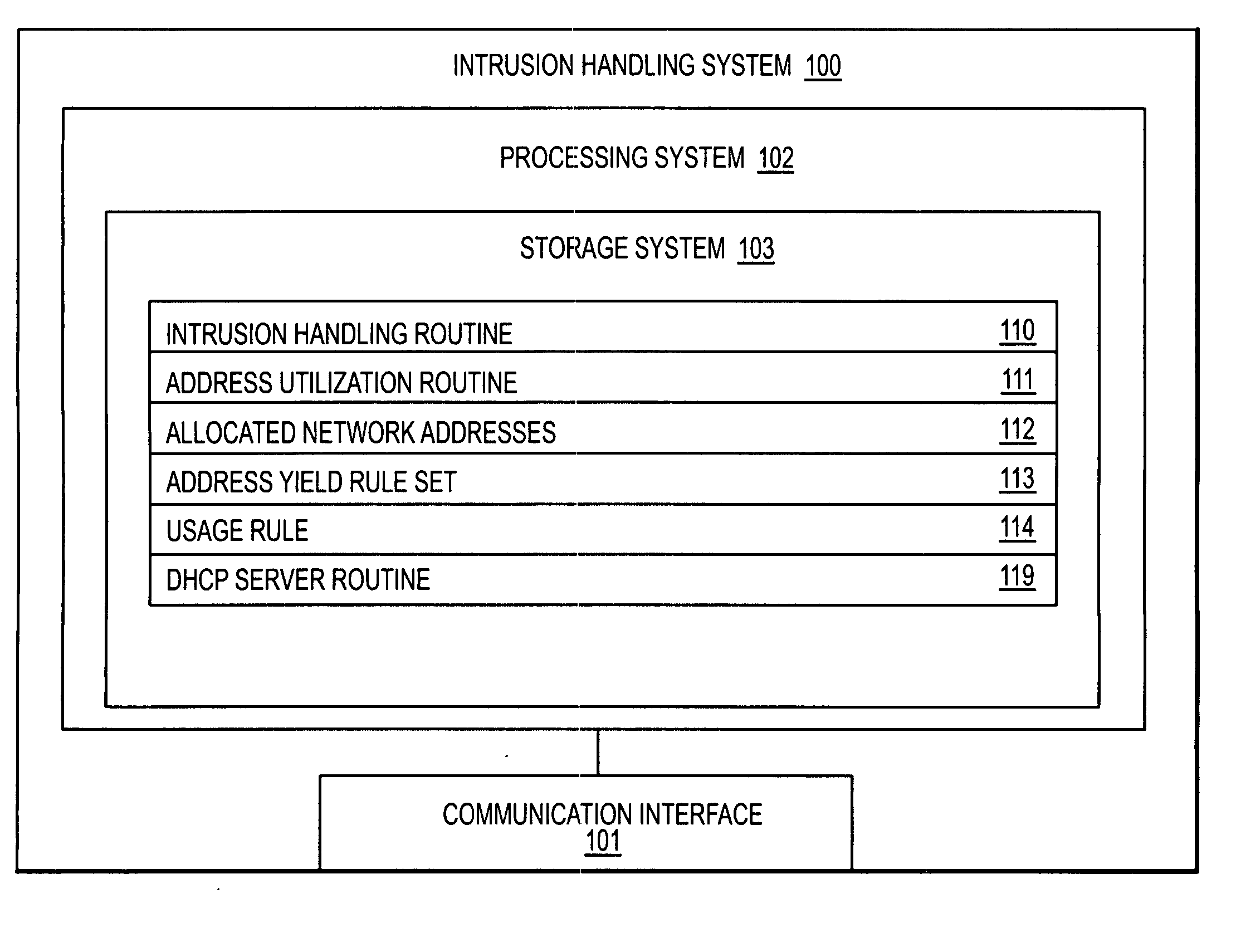
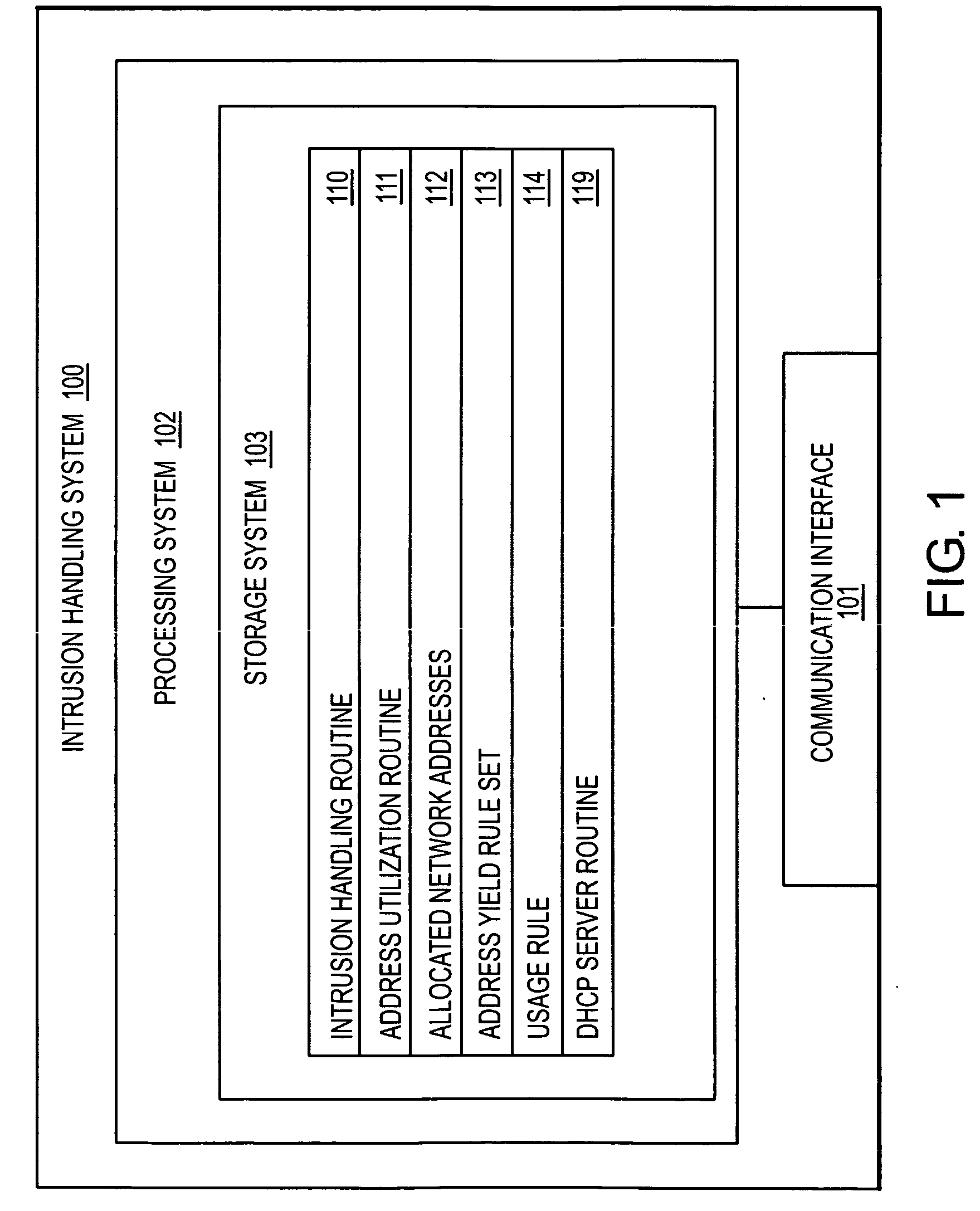
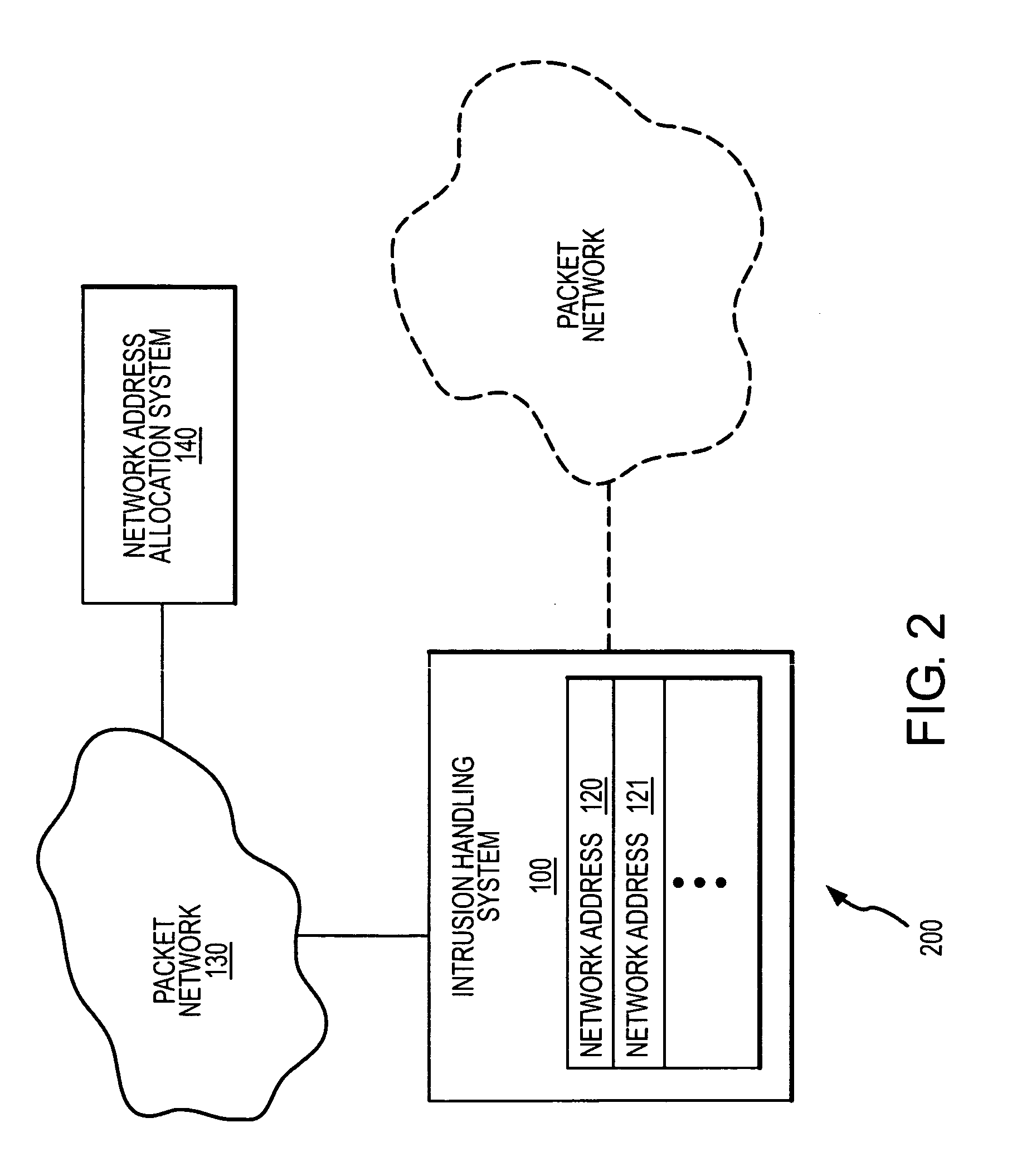
Intrusion handling system and method for a packet network with dynamic network address utilization
InactiveUS20060179485A1Memory loss protectionError detection/correctionCommunication interfaceNetwork addressing
An intrusion handling system for a packet network is provided according to an embodiment of the invention. The intrusion handling system includes a communication interface configured to receive or detect a network event that is directed to a network address. The intrusion handling system further includes a processing system coupled to the communication interface and configured to receive the network event from the communication interface, determine whether to yield the network address, respond to the network event in order to retain the network address, and not respond to the network event in order to yield the network address.
Owner:INTRINSIC SECURITY
Method to realize dynamic networking and resource sharing among equipments
InactiveUS20060155802A1Implement resourcesEasy to useResource allocationMultiple digital computer combinationsDevice registerInode
The invention relates to a method allowing dynamically networking among a plurality of devices to share resource. It includes: installing a software of dynamic networking and resource sharing on each of devices to realize dynamic networking and resource sharing. These devices periodically announce information with multicasting. A device serves as node control device, and announces the message of the existence of the device through multicasting, creates a node. A device can find the node by monitoring announcement message from the node. The device which requests to join into the node device registers its service information that can be provided by the device to the node control device. The device which has joined into the node finds the device providing service by indexing the nodal control device, and obtains desired service from the device by sending a service calling information. The method is applied to home backbone network for performing networking in home network. Then a topology connection structure with master / slave and peer-to-peer modes can be realized. The dynamic networking and resource sharing between the service providing device and the service utilizing device in the home backbone network can be realized.
Owner:LENOVO (BEIJING) LTD
Packet-Based Aggregation of Data Streams Across Disparate Networking Interfaces While Providing Robust Reaction to Dynamic Network Interference With Path Selection and Load Balancing
ActiveUS20130132604A1Packet lossConnection managementMultiple digital computer combinationsData packData stream
System and method for load-balancing a plurality of transmission media. A first plurality of packets of a first stream may be transmitted to a second device on a first transmission medium. It may be determined that current medium utilization of the first transmission medium exceeds a first threshold. The first stream may be selected for transmission on both of the first transmission medium and a second transmission medium based on said determining that current medium utilization of the first transmission medium exceeds the first threshold. A second plurality of packets of the first stream may then be transmitted to the second device using both the first transmission medium and the second transmission medium. A first portion of the second plurality of packets may be transmitted on the first transmission medium and a second portion of the second plurality of packets may be transmitted on the second transmission medium.
Owner:QUALCOMM INC
Methods and systems for a dynamic networked commerce architecture
InactiveUS20060095343A1Easy accessEasy to useDiscounts/incentivesBuying/selling/leasing transactionsClient-sideClient machine
One embodiment of the present invention provides systems and methods, which allow a more efficient shopping experience. A cascading commerce menu provides access to a plurality of product, service, and / or content categories. In one embodiment, the cascading commerce menu is stored on a client computer, thereby providing quick access to the menu.
Owner:LOCAL COM LTD
Dynamic network load balancing over heterogeneous link speed
ActiveUS20020054567A1Error preventionFrequency-division multiplex detailsBalancing networkNetwork link
A method, apparatus, and computer program product for balancing transmission unit traffic over network links, including disposing transmission units into flows; grouping flows into first flow lists, each corresponding to a selected network link; determining a traffic metric representative of a traffic load on the selected network link; responsive to the traffic metric, regrouping flows into second flow lists corresponding to the selected network link, the regrouping balancing the transmission unit traffic among the network links; and transmitting the respective second flow list over the respective selected network link. The invention also can include a method for transmitting transmission units through a network, including receiving a transmission unit from a transmission unit source; classifying the transmission unit according to a predetermined flow characteristic; selecting a preselected network link over which the transmission unit is to be transmitted; and transmitting the transmission unit over the preselected network link.
Owner:AVAGO TECH INT SALES PTE LTD
Dynamic Network Tunnel Endpoint Selection
ActiveUS20090031415A1Facilitate communicationMultiple digital computer combinationsProgram controlClient-sideDynamical network
Dynamically selecting an endpoint for a tunnel into an enterprise computing infrastructure. A client dynamically selects a gateway (which may alternatively be referred to as a boundary device or server) as a tunnel endpoint for connecting over a public network (or, more generally, an untrusted network) into an enterprise computing infrastructure. The selection is made, in preferred embodiments, according to least-cost routing metrics pertaining to paths through the enterprise network from the selected gateway to a destination host. The least-cost routing metrics may be computed using factors such as the proximity of selectable tunnel endpoints to the destination host; stability or redundancy of network resources for this gateway; monetary costs of transmitting data over a path between the selectable tunnel endpoints and destination host; congestion on that path; hop count for that path; and / or latency or transmit time for data on that path.
Owner:A10 NETWORKS
Adaptive communication protocol for wireless networks
InactiveUS7184413B2Network topologiesTime-division multiplexWireless mesh networkNetwork Communication Protocols
A communication protocol that provides link-level and media access control (MAC) level functions for wireless (e.g., ad-hoc) networks and is robust to mobility or other dynamics, and for scaling to dense networks. In a mobile or otherwise dynamic network, any control-packet collisions will be only temporary and fair. In a dense network, the network performance degrades gracefully, ensuring that only a certain percentage of the common channel is consumed with control packets. The integrated protocol allows packets (e.g., data scheduling control packets) to be scheduled in a collision-free and predictable manner (known to all neighbors), multicast packets can be reliably scheduled, as well as streams of delay- or delay-jitter-sensitive traffic. Further, using an optional network code, the scheduling of control packets can appear to observers to be randomized.
Owner:NOKIA TECHNOLOGLES OY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com