Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72 results about "Context transfer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
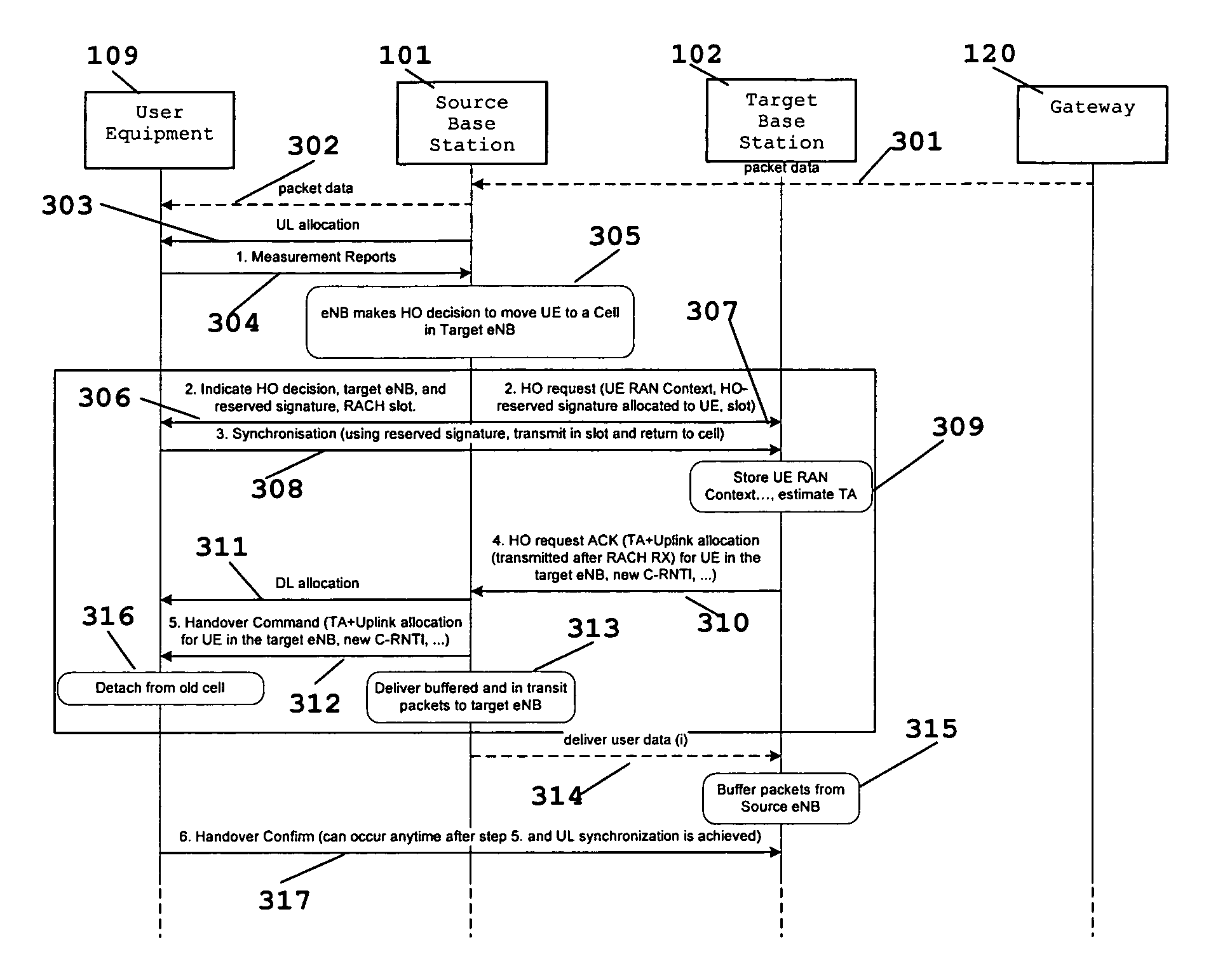
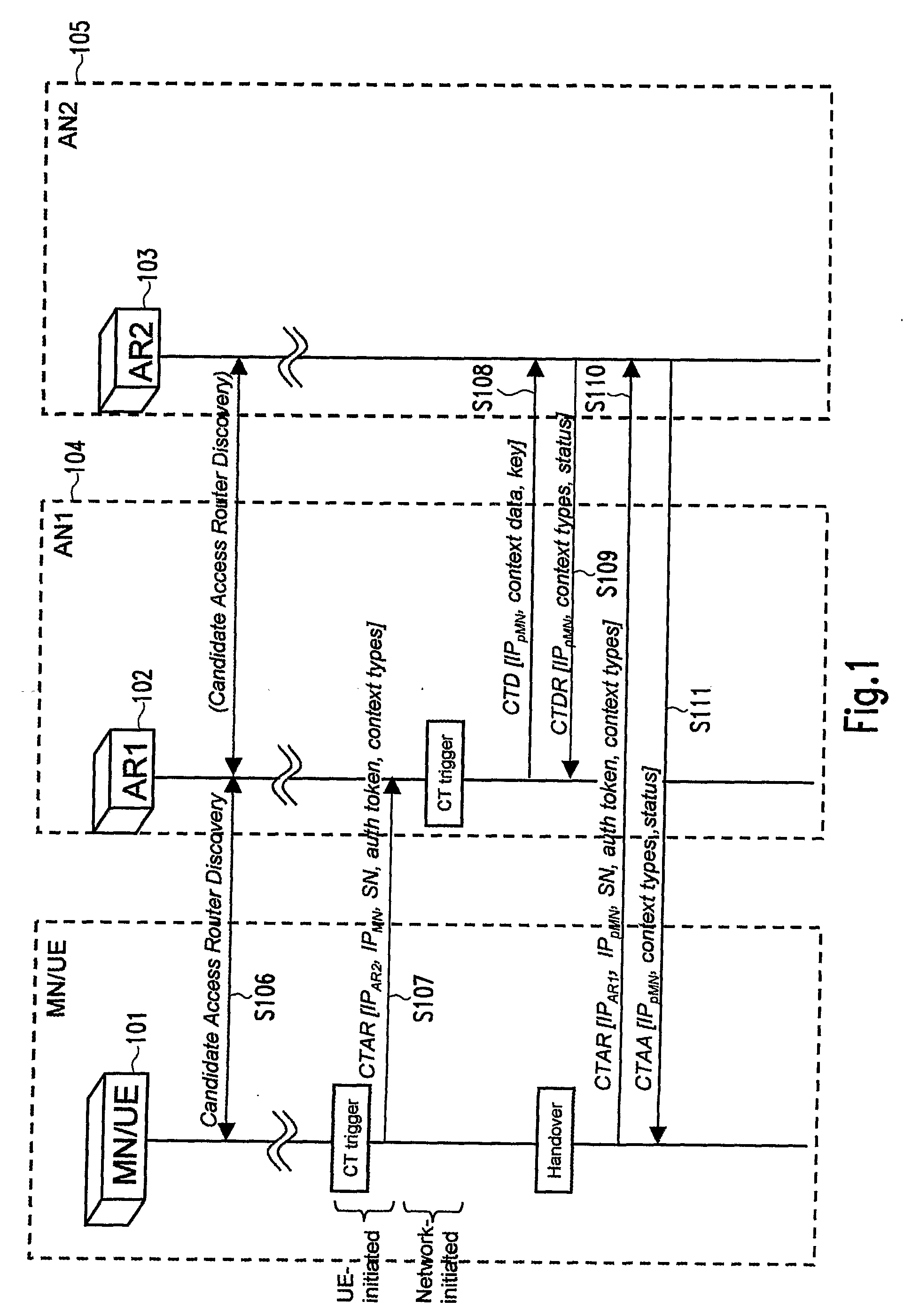
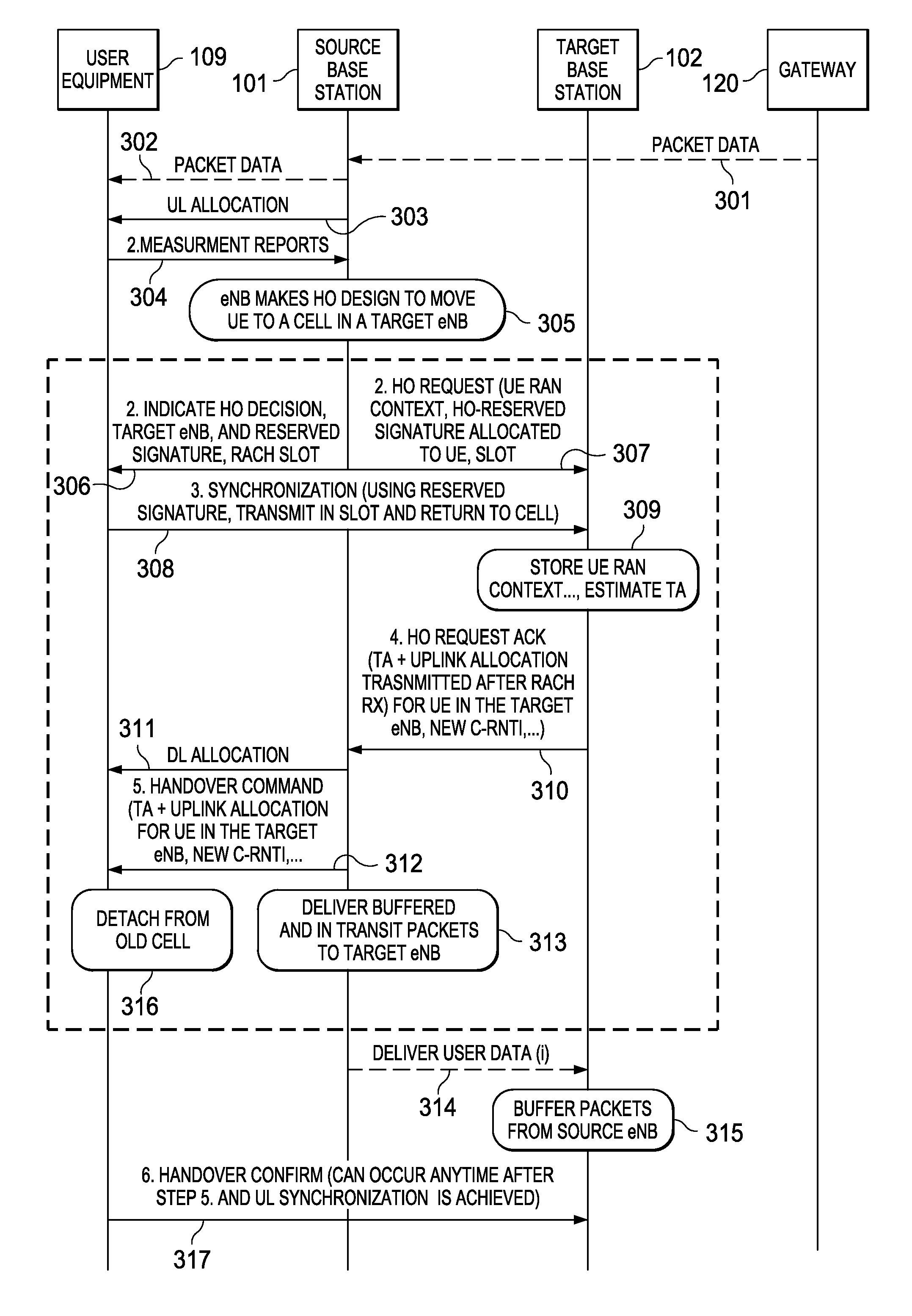
Pre-Synchronization Method for Hard Handovers in Wireless Networks
ActiveUS20080267131A1Handover interruption time is reducedReduce RACH/UL synchronization latencyTime-division multiplexRadio/inductive link selection arrangementsCurrent cellUser equipment
A pre-synchronization method in which the source cell chooses a signature for the user equipment (mobile) to use in the target cell for RACH access, and instructs the user equipment to perform RACH access and return to the current cell before a handover command (break command) is issued. This causes parallel execution of the UL synchronization process with the context transfer process among the two base stations.
Owner:APPLE INC
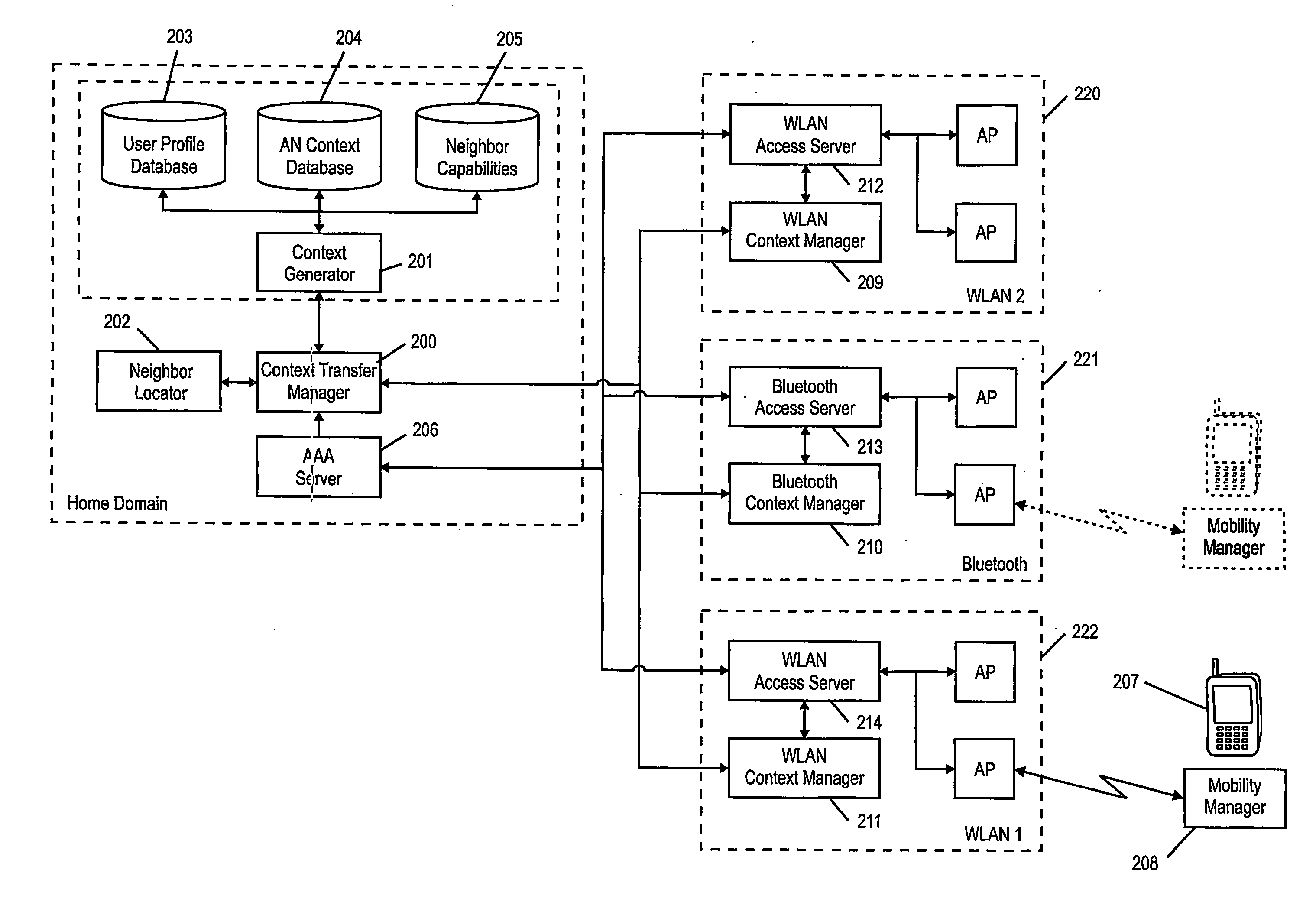
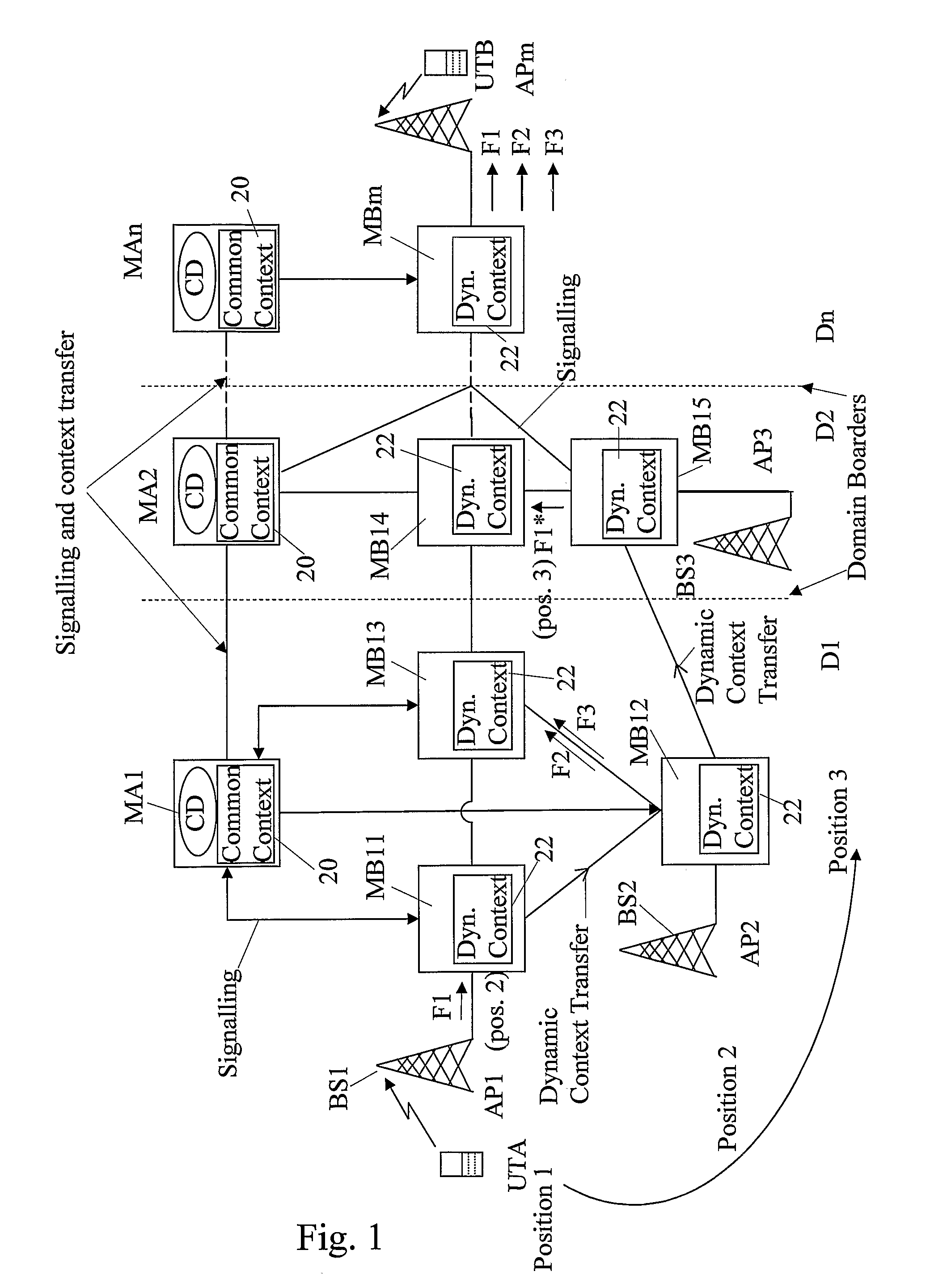
Contex transfer in a communication network comprising plural heterogeneous access networks
ActiveUS20070110009A1Easy mappingNetwork topologiesRadio/inductive link selection arrangementsAccess networkContext based
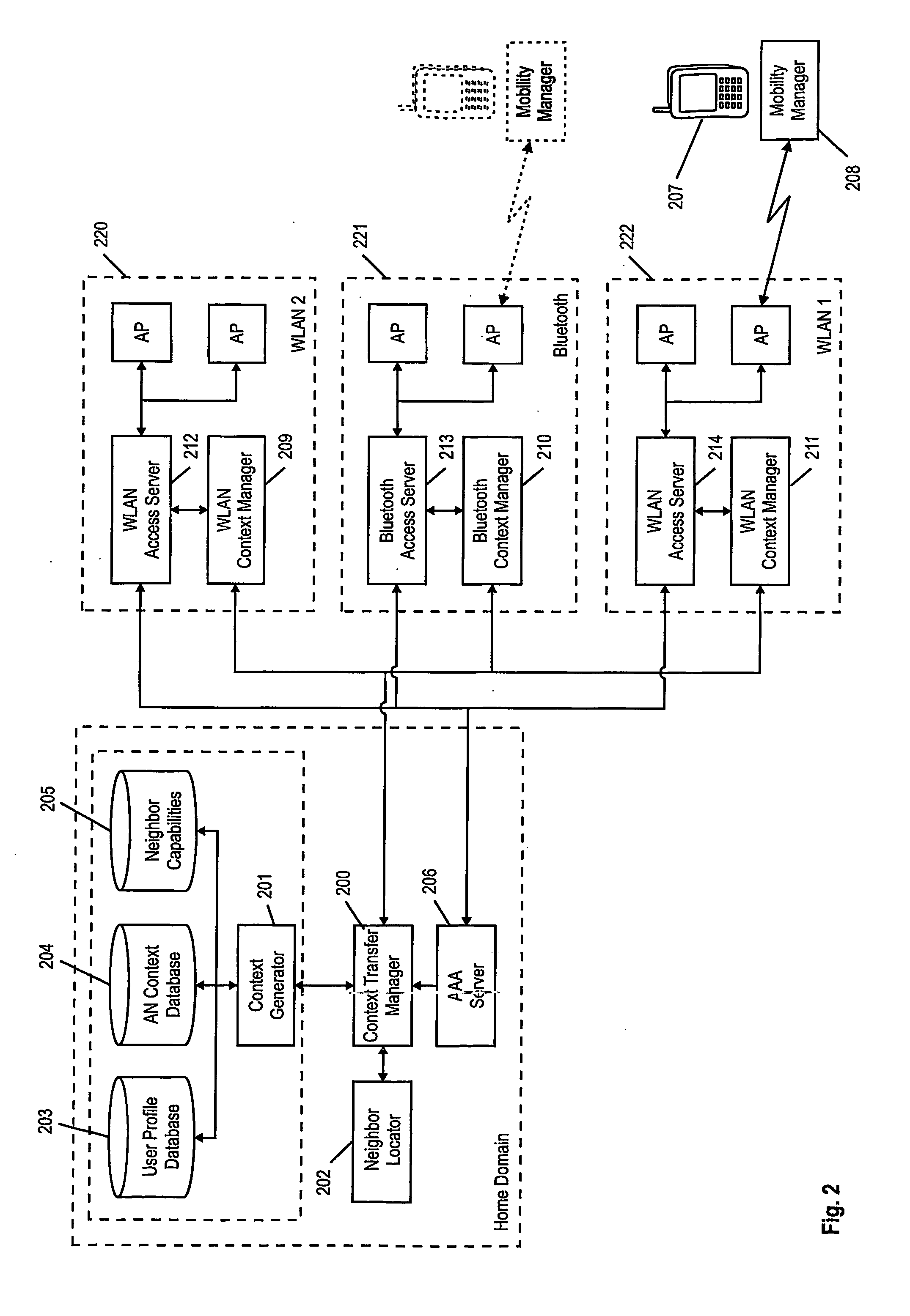
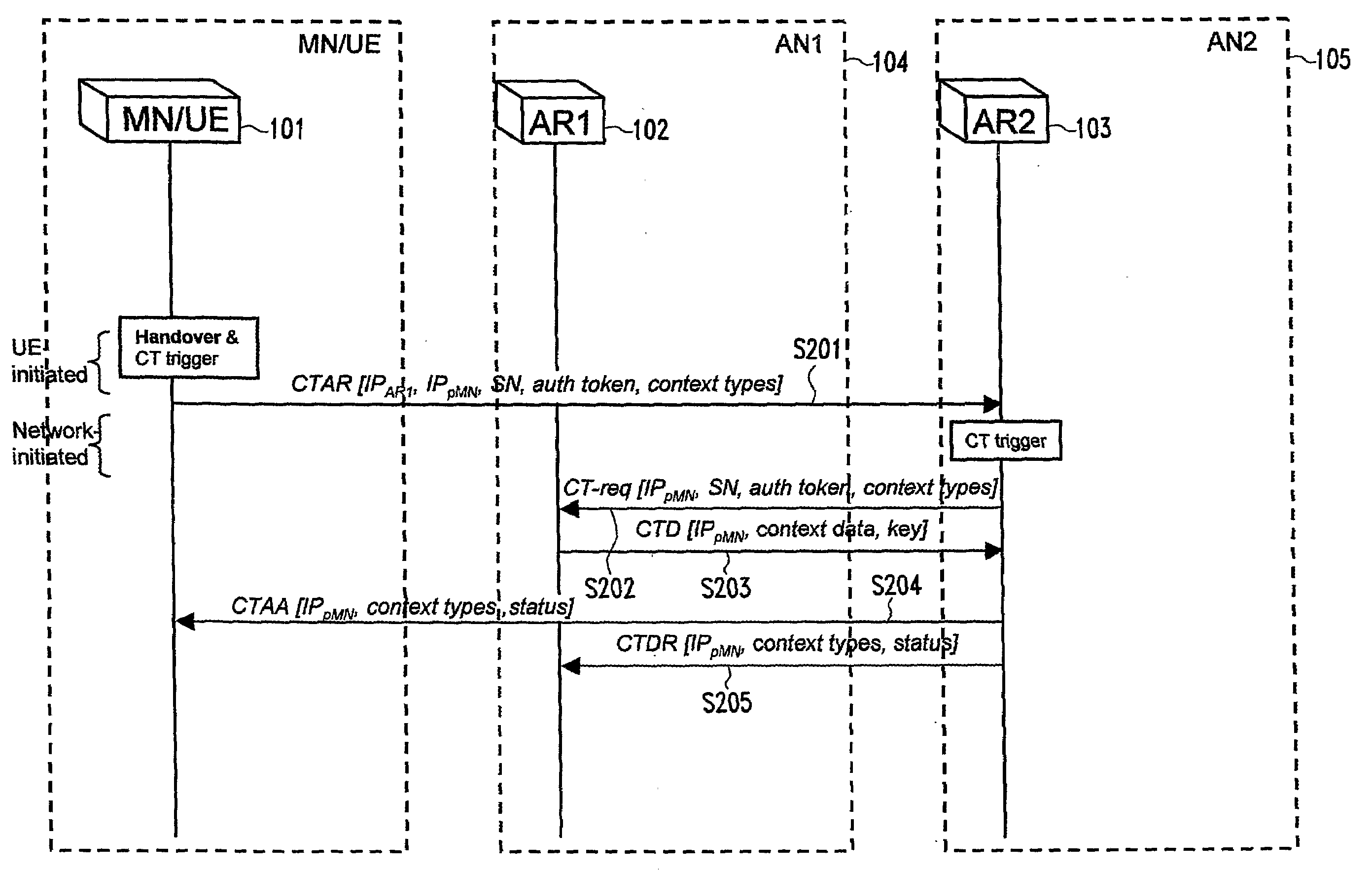
The present invention relates to a method for a context transfer in a communication network comprising a plurality of heterogeneous access networks, (220, 221, 222) wherein a mobile terminal is attached to one of the access networks. Further, the present invention relates to a context transfer manager performing the method (220, 600). Moreover, the present invention relates to a mobile terminal specially adapted to perform the provided method for a context transfer. To facilitate a context transfer between heterogeneous access networks, the present invention introduces a context transfer manager generating at least one context based on capabilities and paramneters associated to the mobile terminal and capabilities and parameters of the neighboring access networks taking into account the respective access technology (FIG. 5). Further the context transfer manager is common to the heterogeneous access networks in the communication network and performs the context transfers related to a particular mobile terminal.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Protocol context transfer in a mobile communication system
ActiveUS7508792B2Overcome negative influenceError preventionData switching by path configurationControl communicationsMobile communication systems
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
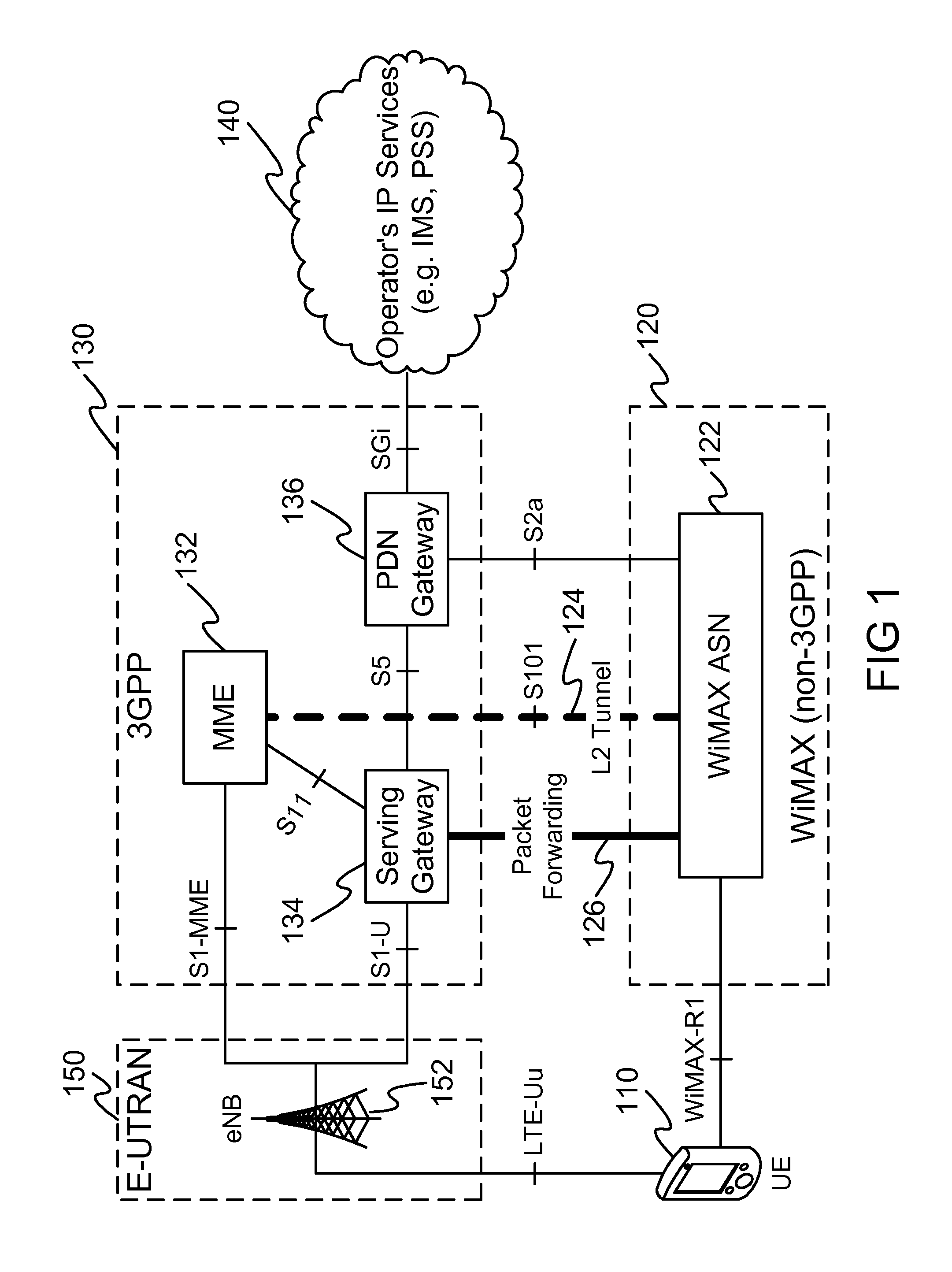
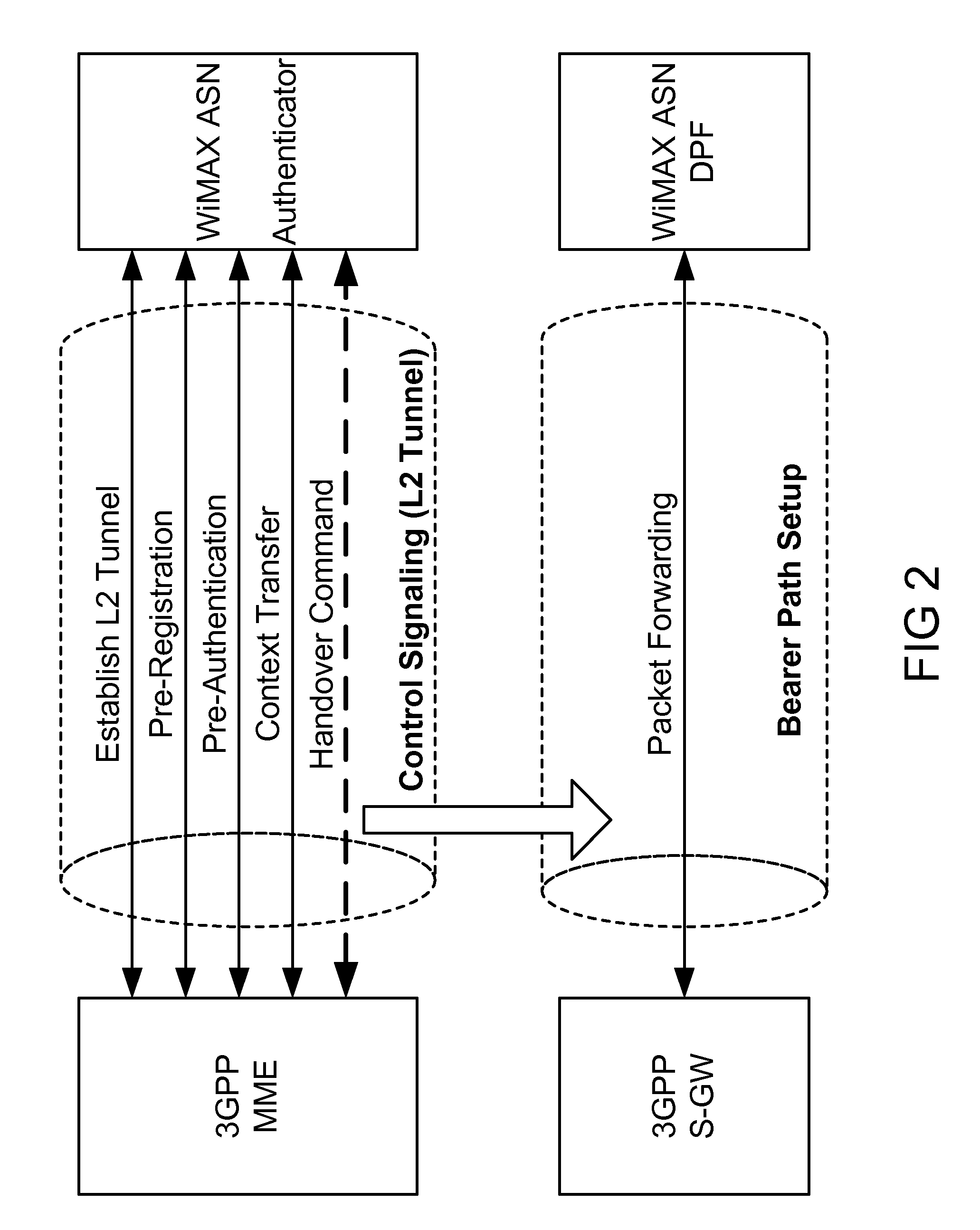
L2 Tunneling-based Low Latency Single Radio Handoffs
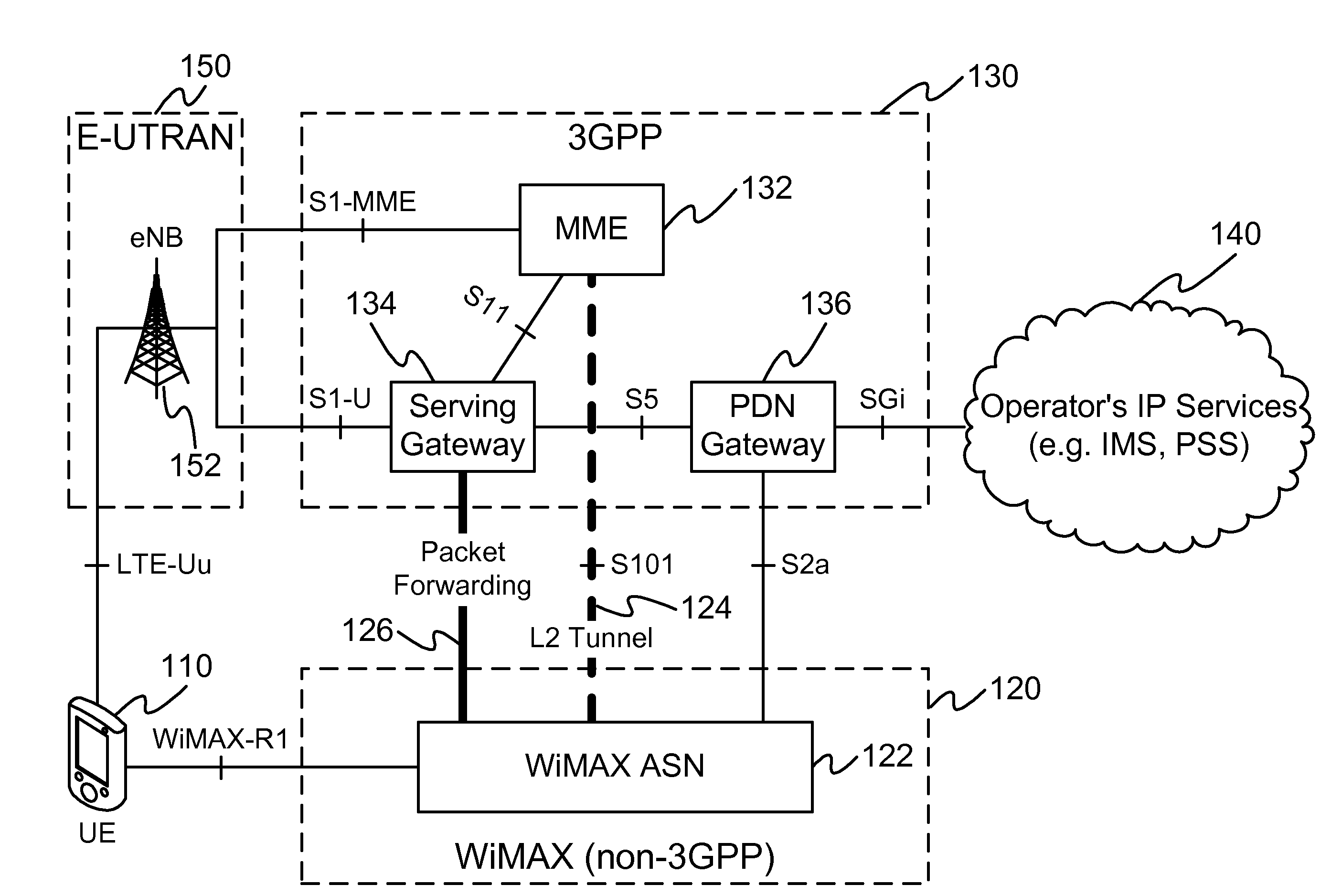
An example of this invention provides low latency handovers between Mobile WiMAX and 2G / 3G / LTE networks with only a single radio transmitting at any given point in time, by establishing L2 tunnel between 3GPP MME and WiMAX ASN for control plane signaling to perform pre-registration, pre-authentication and context transfer to the target network, while UE maintains its connection to the source network, and by setting up bearer path for packet forwarding between Servicing Gateway and WiMAX ASN. An example of this invention uses a virtual eNB to facilitate low latency L2 handoffs to legacy 2G / 3G networks with minimum impact to SGSN and MME.
Owner:TAHOE RES LTD
Protocol context transfer in a mobile communication system
ActiveUS20070081492A1Overcome negative influenceError preventionData switching by path configurationControl communicationsMobile communication systems
The present invention relates to a method for controlling a radio cell change of a communication terminal from a first radio cell to a second radio cell, wherein the first and the second radio cell is controlled by at least one base station of a mobile communication system. The present invention further provides a base station and a communication system comprising a plurality of base stations and a communication terminal adapted to execute the control method. To overcome negative impacts of data loss and delay during a cell change procedure the protocol context of a retransmission protocols are transferred from a source base station to a target base station upon an cell change of a communication terminal in issue.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Wireless security system and method
ActiveUS7373508B1Key distribution for secure communicationDigital data processing detailsClient-sideComputer science
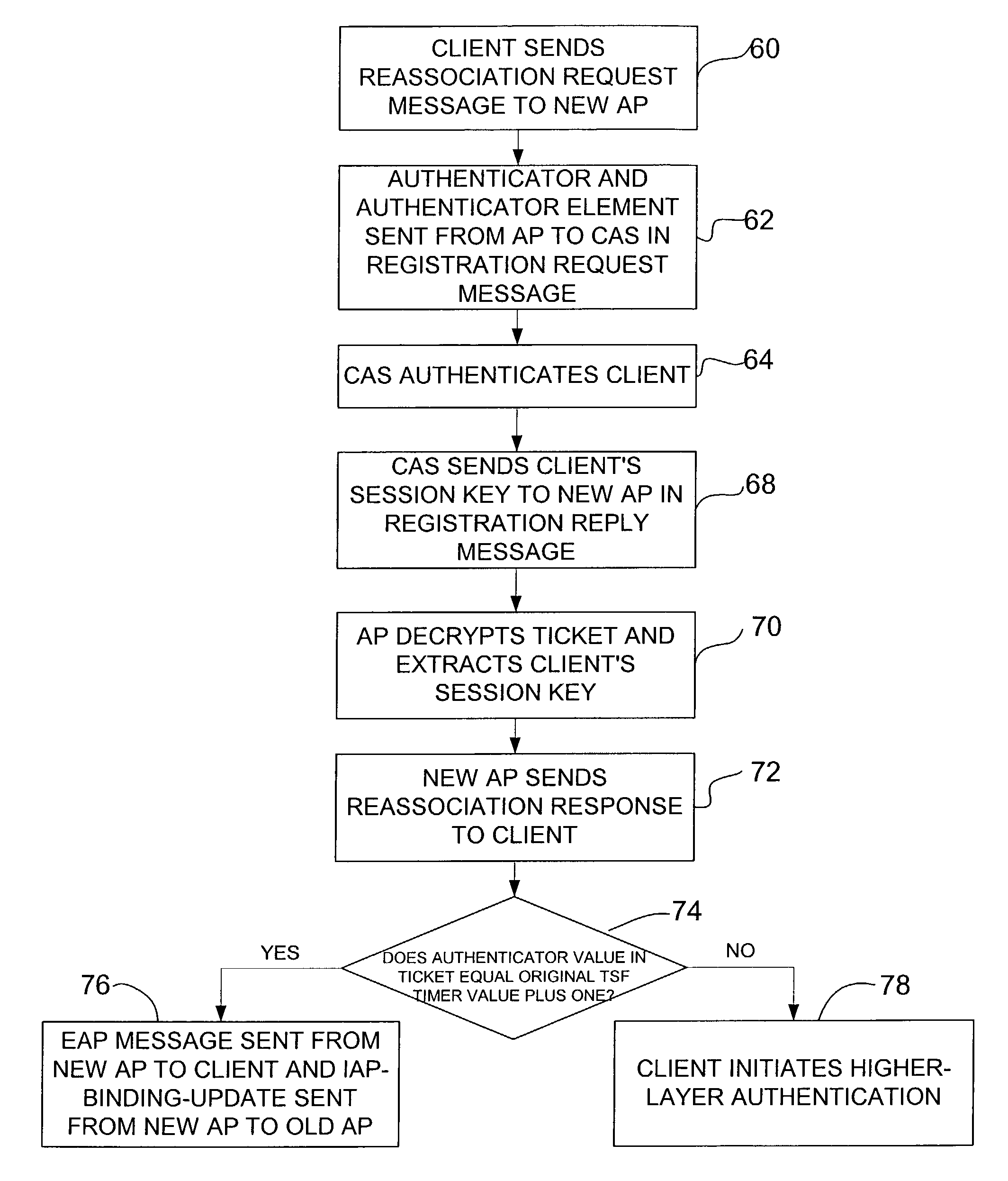
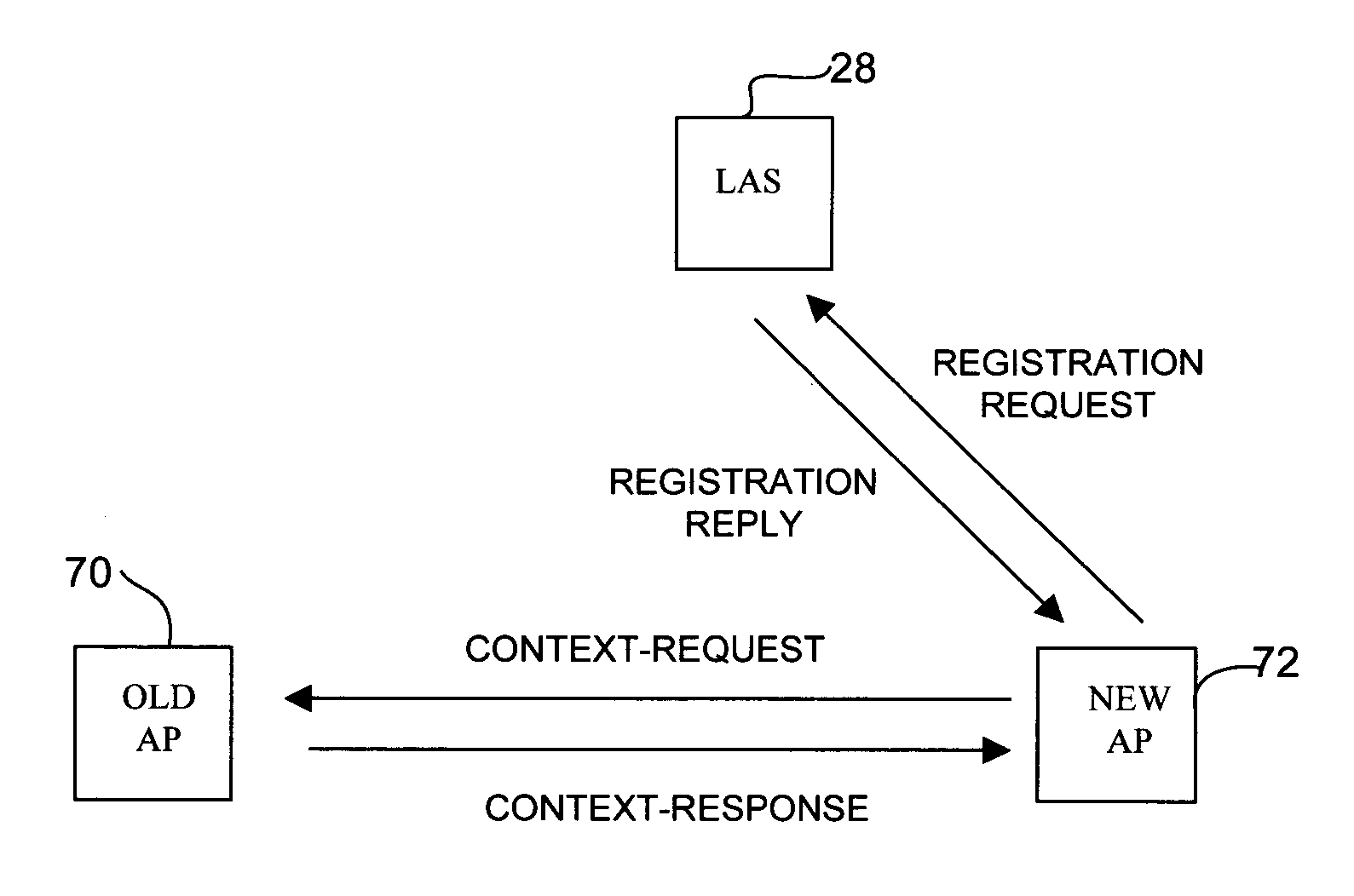
A method for reauthentication during client roaming in a wireless network system. The network has at least one access server and a plurality of access points registered with the access server. The method includes receiving a registration request at the access server from a new access point for a roaming client registered with the access server and sending a client's session key to the new access point in a registration reply upon authentication of the registration request. The client's session key is configured for use by the new access point to authenticate the client and establish keys for the client. A method for secure context transfer during client roaming is also disclosed.
Owner:CISCO TECH INC
System and method for handoff processing
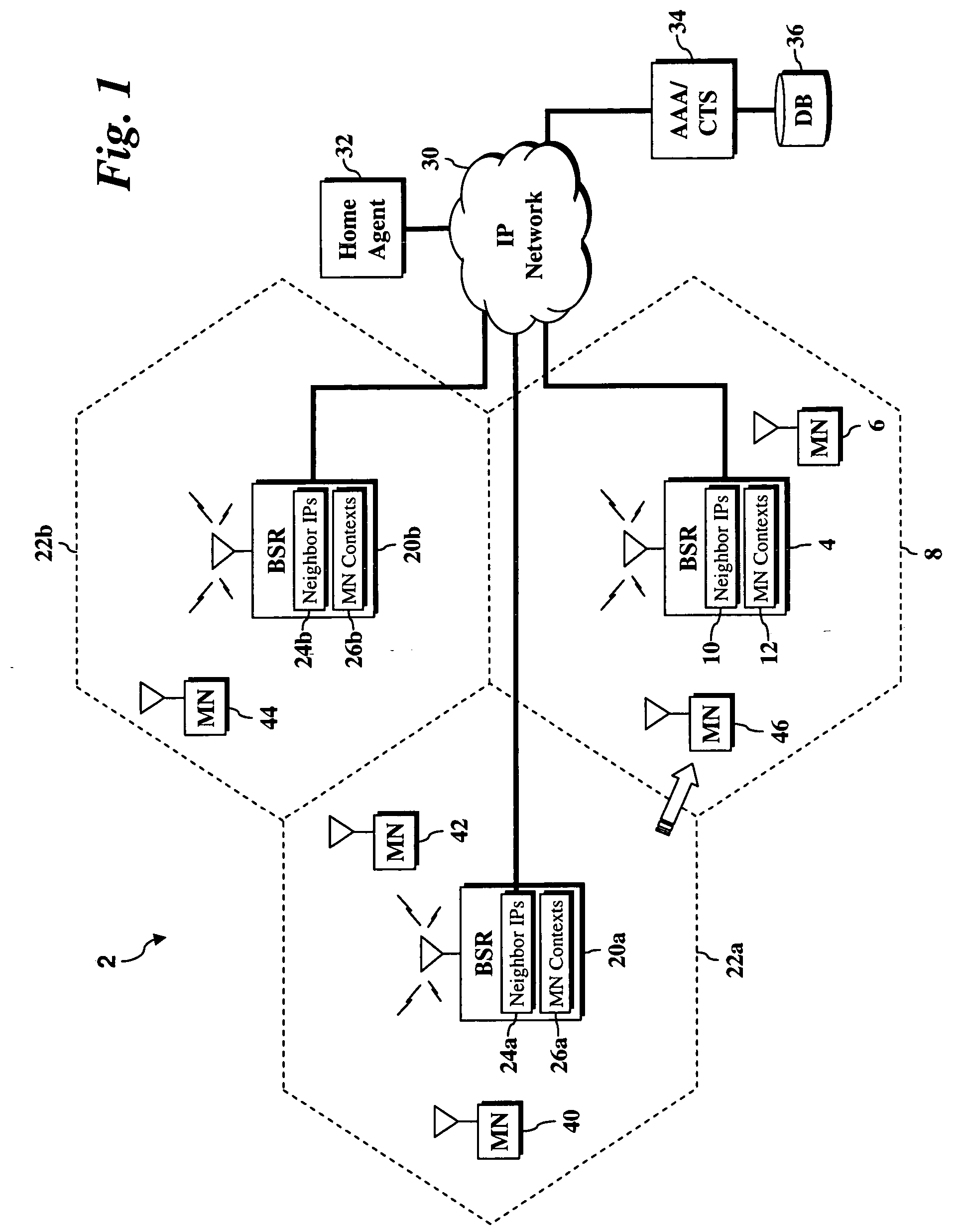
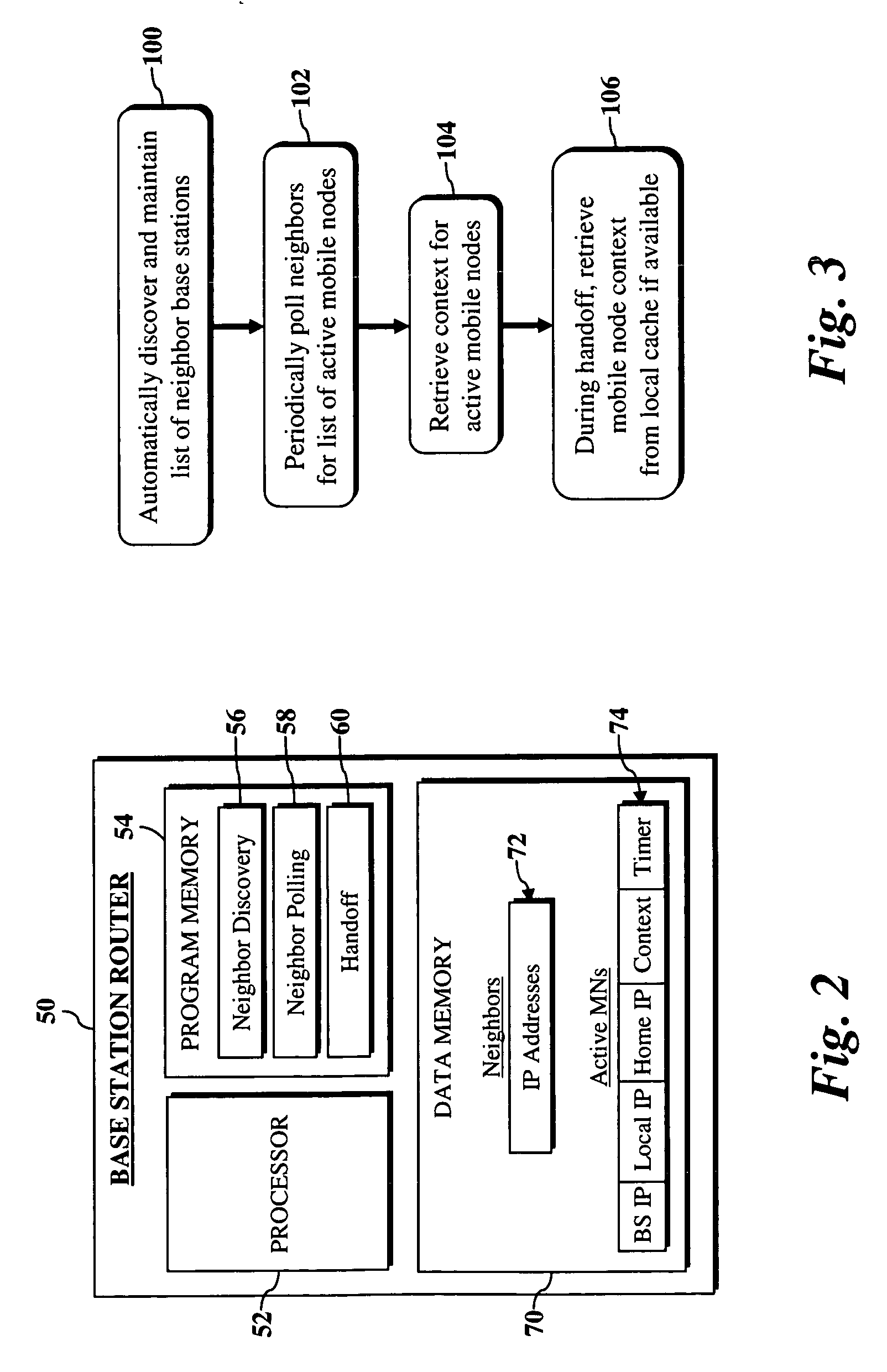
ActiveUS20060056351A1Complete understandingEnhanced advantageData switching by path configurationWireless network protocolsLocal memoriesContext transfer
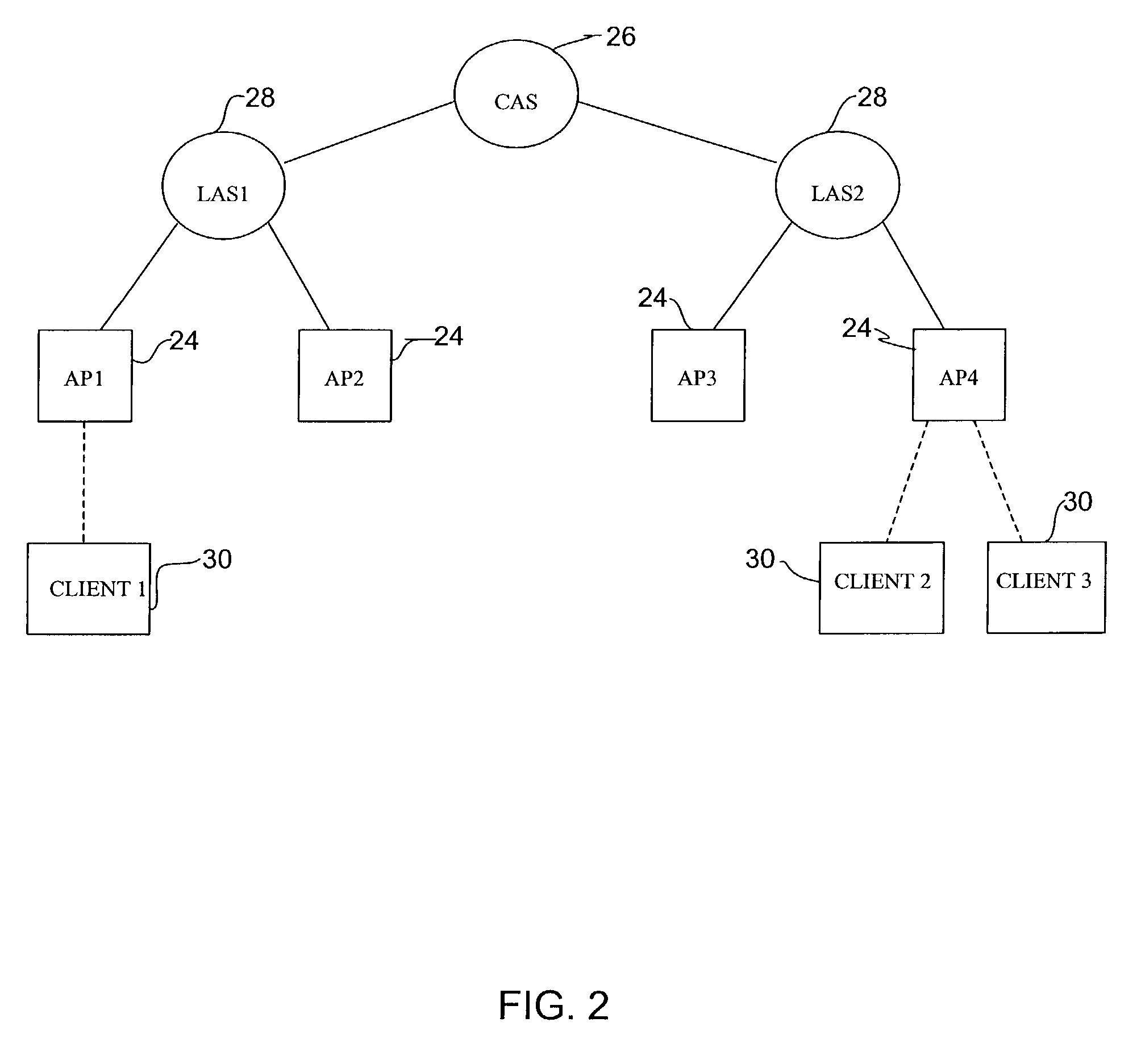
A system and method for optimizing handoff processing in networks with fully collapsed base station routers is disclosed. In accordance with exemplary embodiments of the present invention, handoff processing is optimized by allowing base station routers to automatically discover, and maintain lists of, their neighbor base station routers. Using the list of discovered neighbor base station routers, a base station router polls its neighbors for a list of all active users. The base station router then polls the Context Transfer Server (CTS) database for these users' contexts. Accordingly, instead of polling the. CTS database during handoff, the present invention allows a base station router to activate the context from local memory.
Owner:NEXTEL COMMUNICATIONS
Context transfer in search advertising
A computer-implemented method is disclosed for determining a type of landing page to which to transfer web searchers that enter a particular query, the method comprising: classifying a landing page as one of a plurality of landing page classes with a trained classifier of a computer based on textual content of the landing page; determining, by the computer, characteristics of one or more query to be associated with the landing page; and choosing, with the computer, whether to retain or to change classification of the landing page to be associated with the one or more query based on relative average conversion rates of advertisements on a plurality of manually-classified landing pages when associated with the characteristics of the one or more query.
Owner:R2 SOLUTIONS
System and method for handoff processing
ActiveUS7272123B2Data switching by path configurationWireless network protocolsLocal memoriesContext transfer
A system and method for optimizing handoff processing in networks with fully collapsed base station routers is disclosed. In accordance with exemplary embodiments of the present invention, handoff processing is optimized by allowing base station routers to automatically discover, and maintain lists of, their neighbor base station routers. Using the list of discovered neighbor base station routers, a base station router polls its neighbors for a list of all active users. The base station router then polls the Context Transfer Server (CTS) database for these users' contexts. Accordingly, instead of polling the CTS database during handoff, the present invention allows a base station router to activate the context from local memory.
Owner:NEXTEL COMMUNICATIONS
Context transfer systems and methods in support of mobility
InactiveUS7050793B1Network traffic/resource managementSpecial service for subscribersDistributed computingContext transfer
Owner:APPLE INC
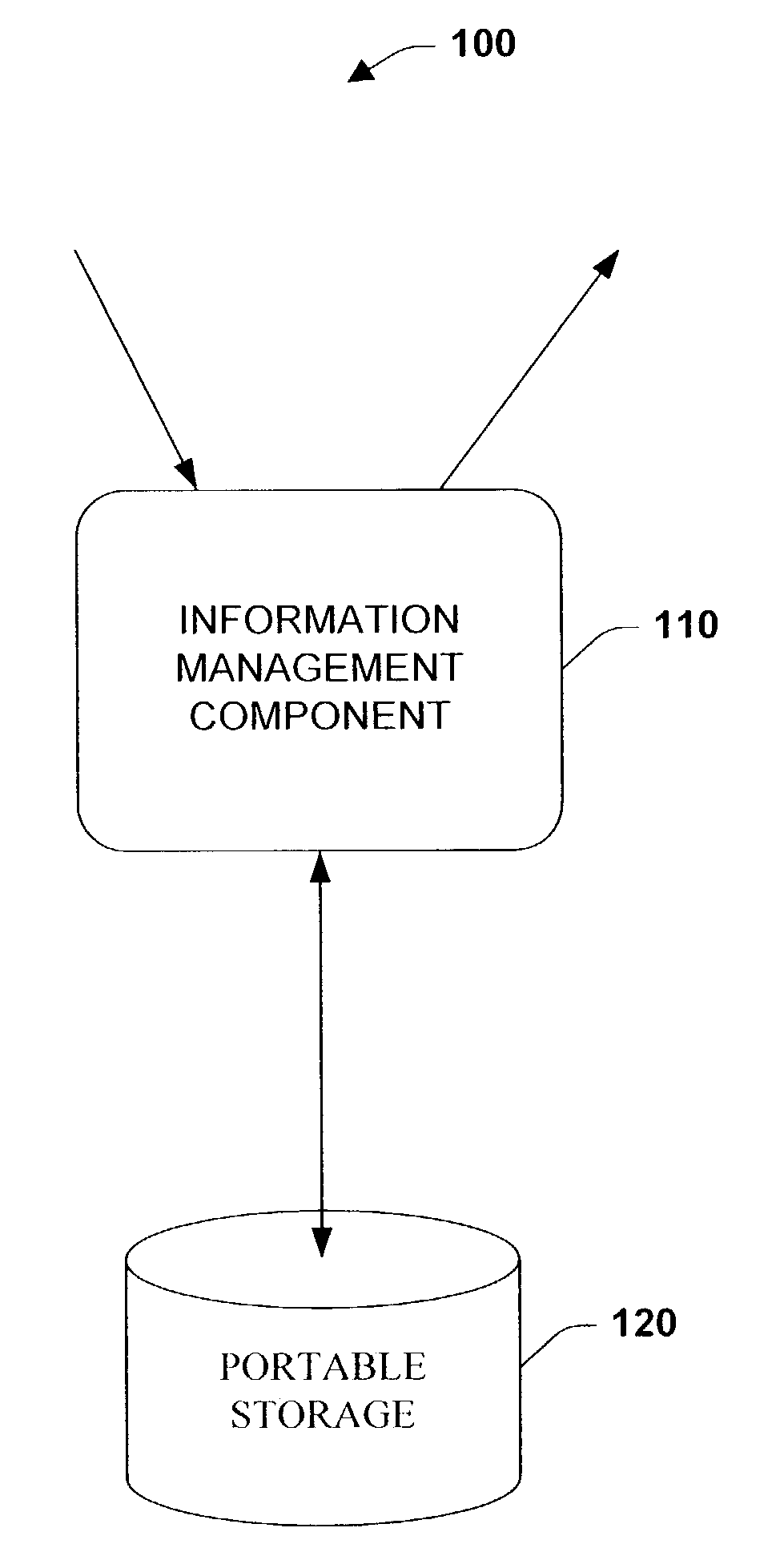
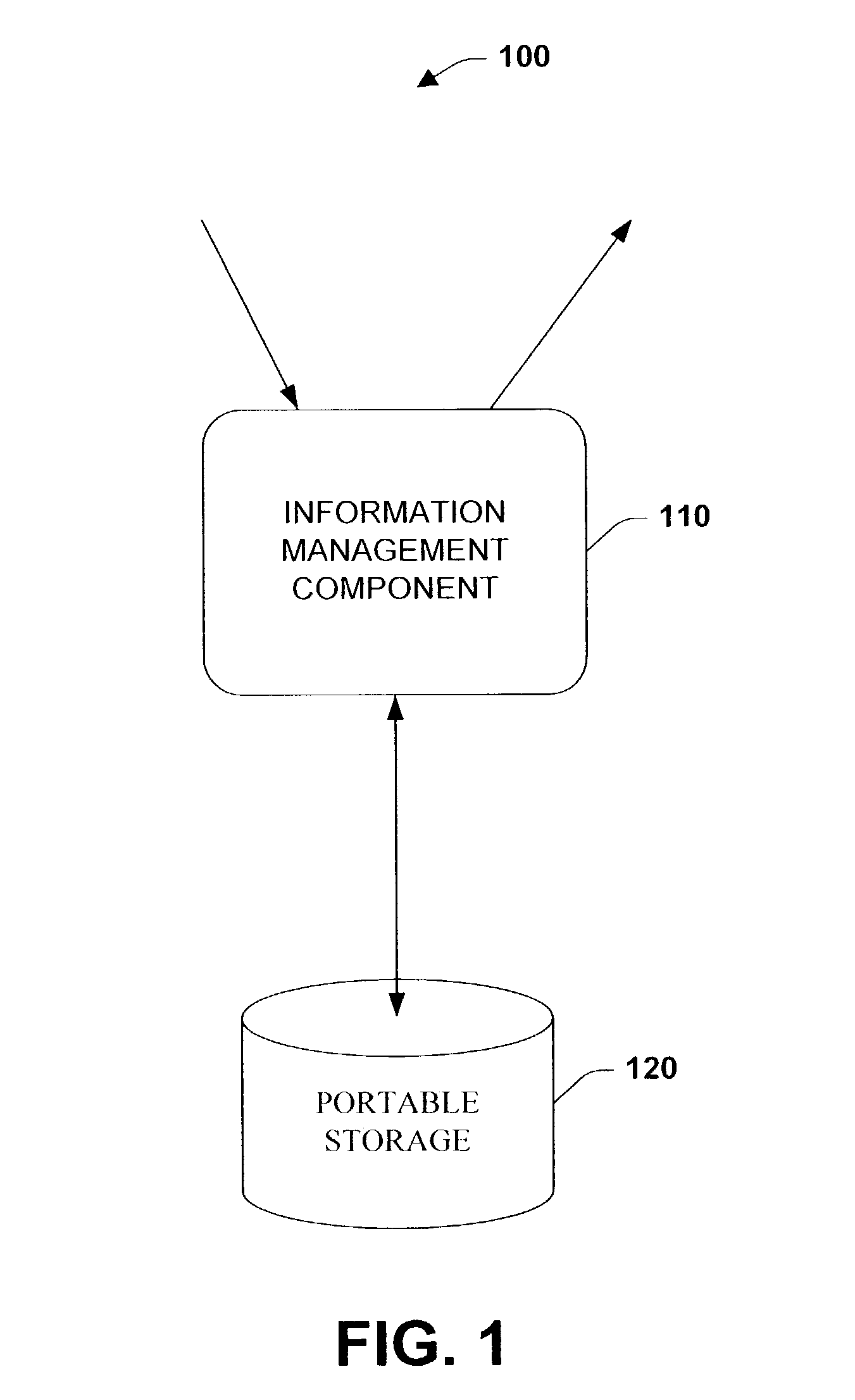
Systems and methods to port controller state and context in an open operating system
InactiveUS7050859B1Reduce manual configurationShorten the timeNumerical controlMicroprogram loadingOperational systemCombined use
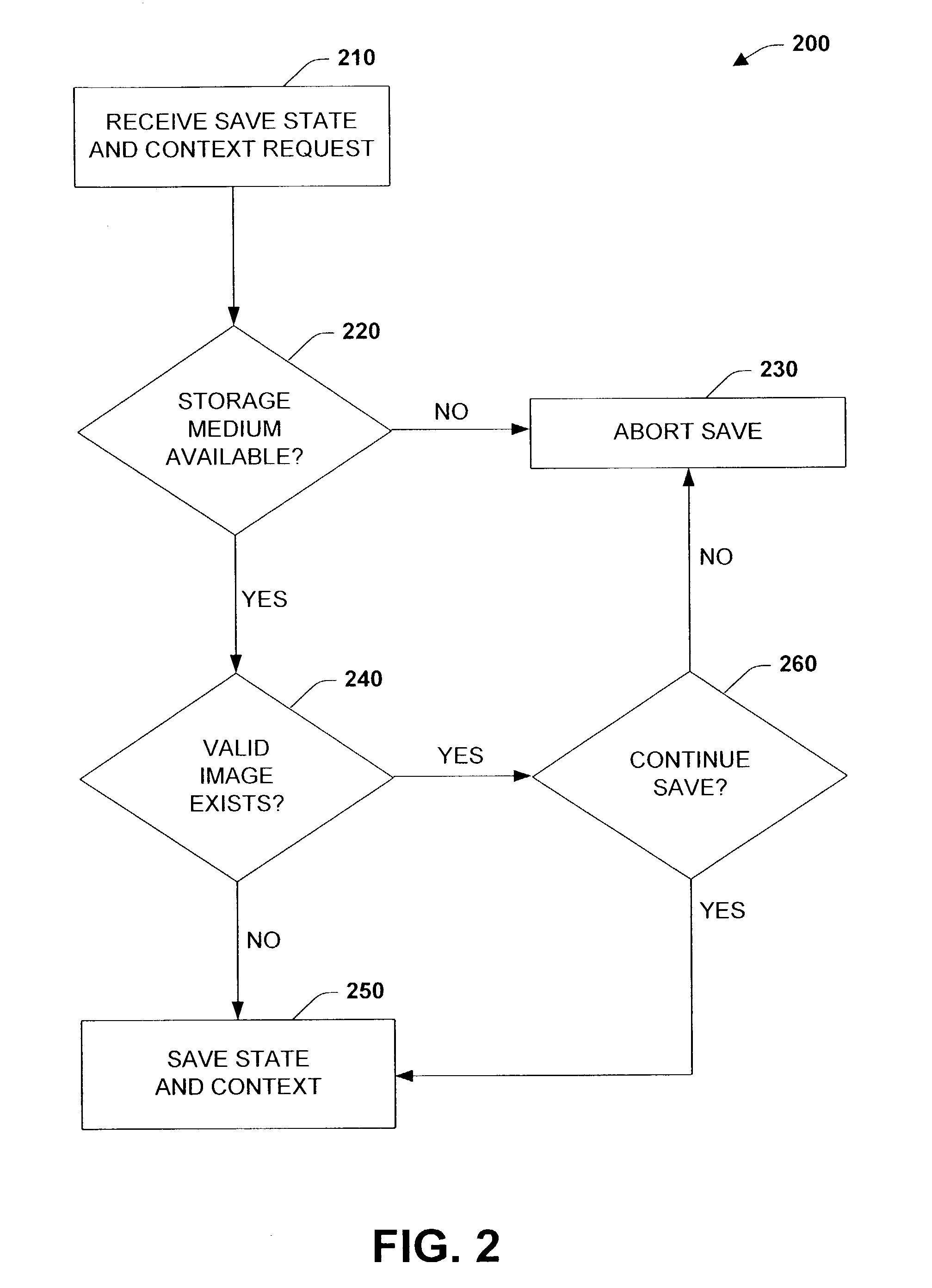
The present invention relates to systems and methods to port controller state and context via non-volatile portable memory to controllers employing an open operating system. The present invention provides for saving a controller's state and context, for example after the controller has been suitably configured. The saved image can then be employed for subsequent controller startups to resume a particular state and context, utilized during maintenance to return a controller to a previously saved state and context, and employed to efficiently configure similar controllers via porting and / or loading the saved image to the similar controllers, which mitigates manual controller configuration. The present invention can be employed in connection with various industrial controller designs, memory configurations, and data transfer techniques. In addition, the present invention provides for serial and / or concurrent state and context transfers between controllers and memory devices.
Owner:ROCKWELL AUTOMATION TECH
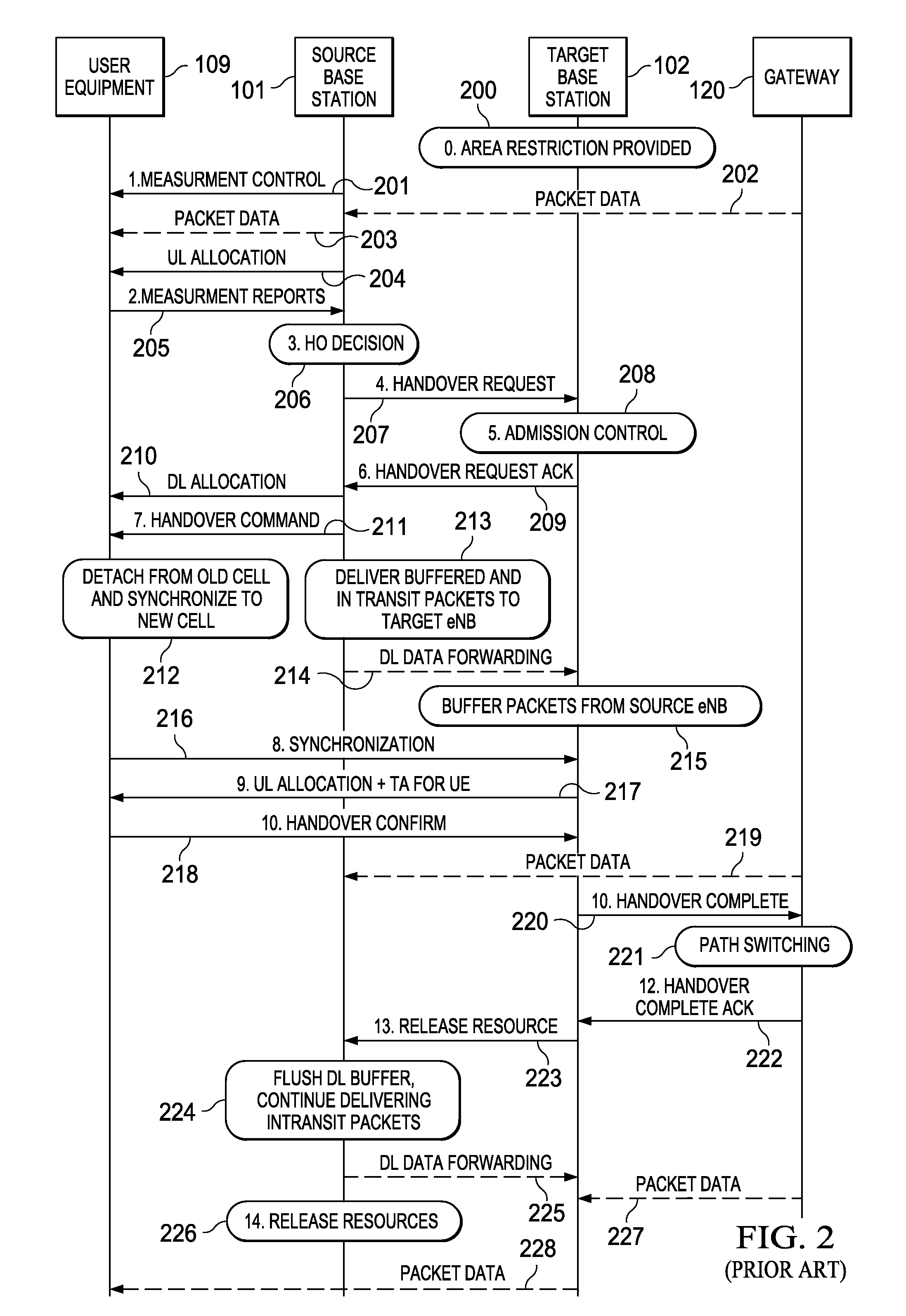
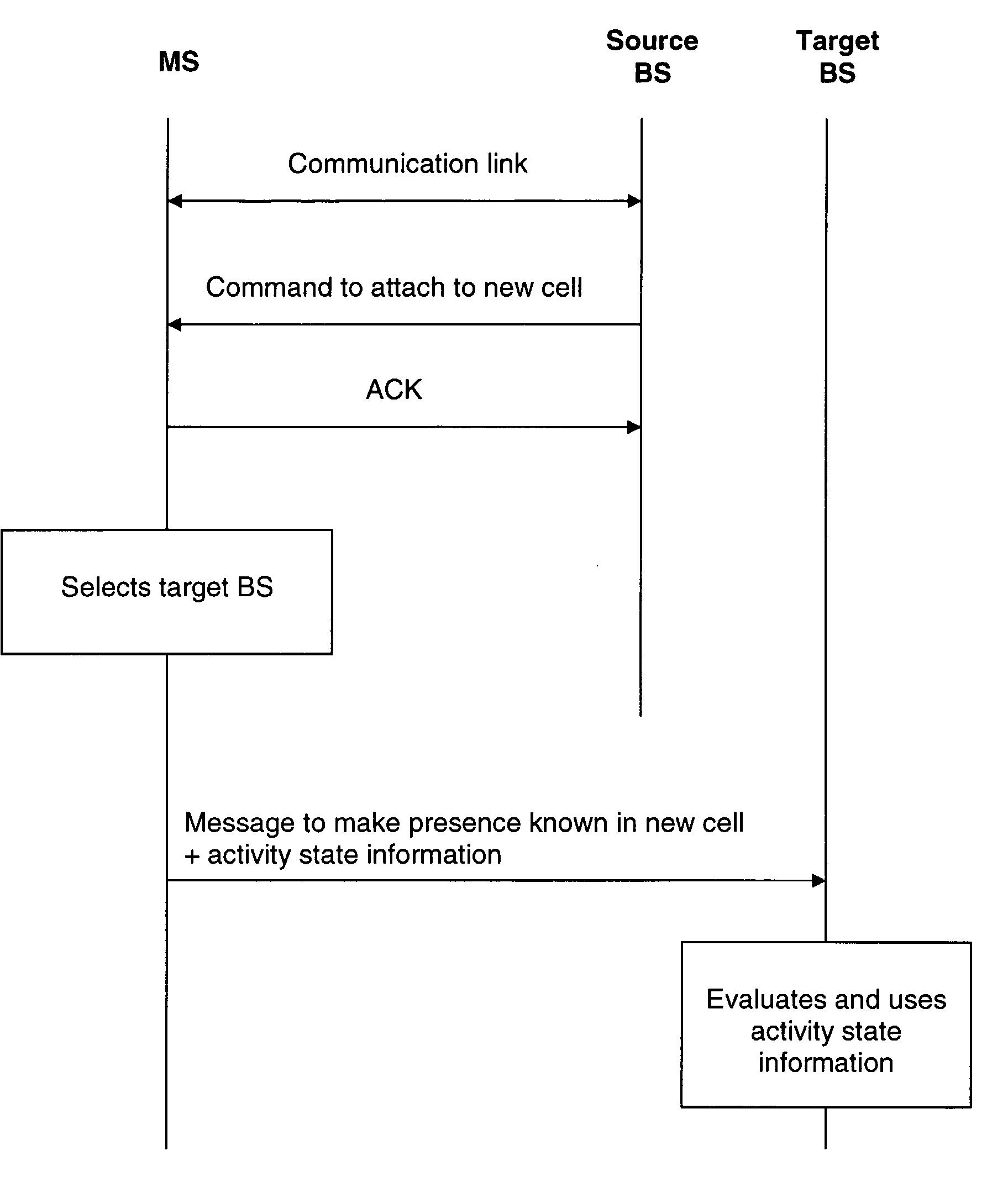
Handover of a mobile station
InactiveUS7916697B2Relieve pressureMinimize the numberWireless commuication servicesData switching networksCommunications systemMobile station
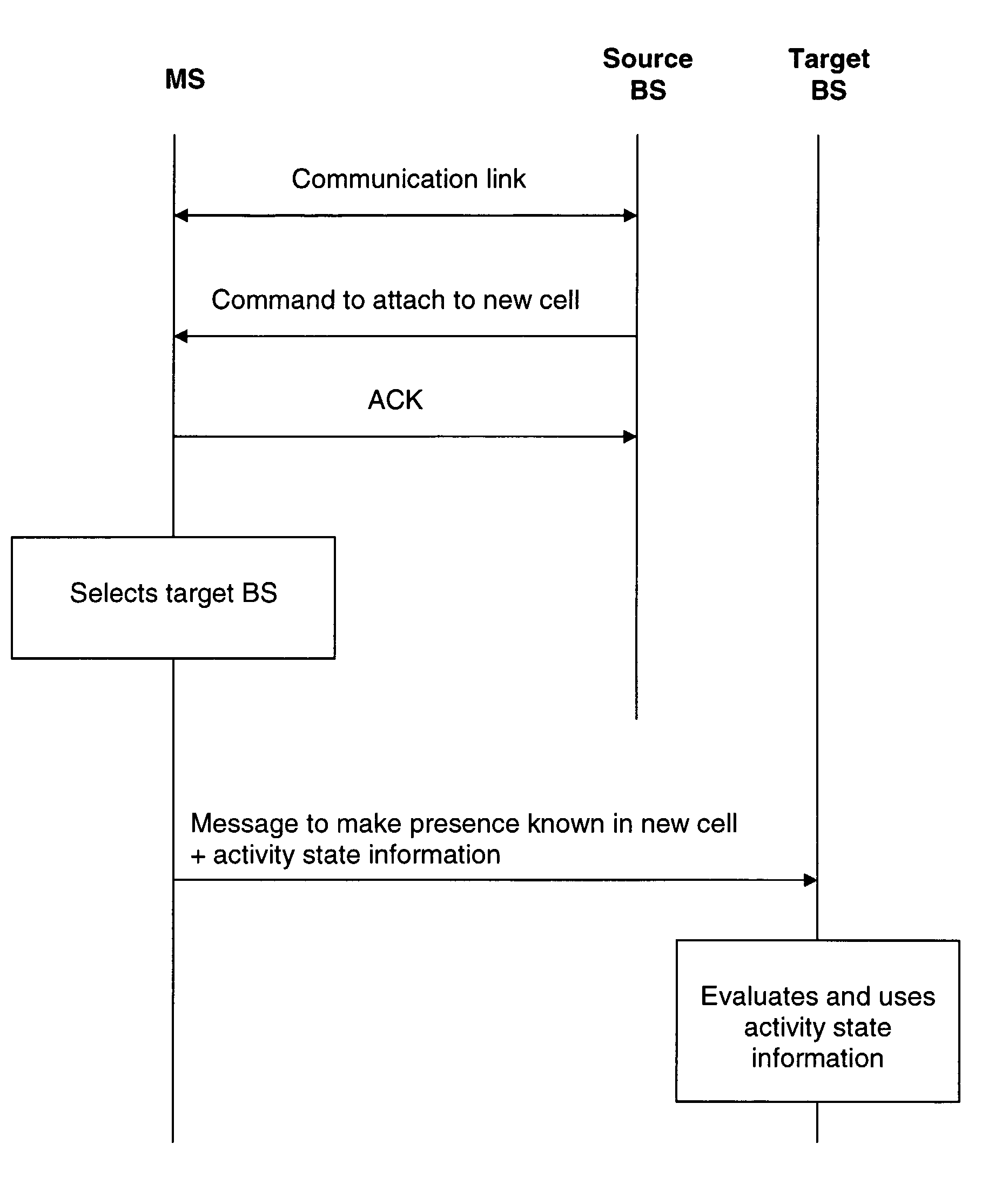
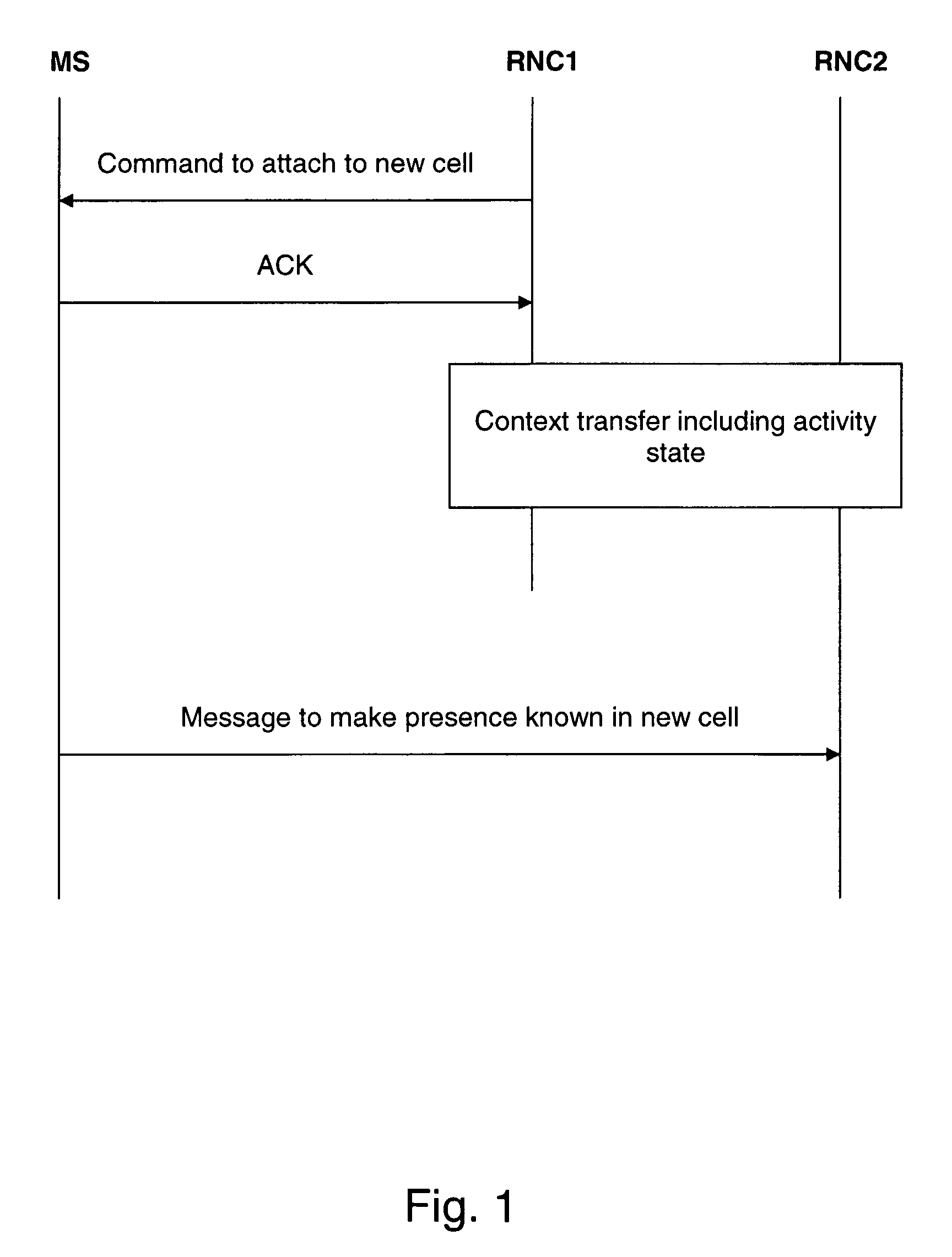
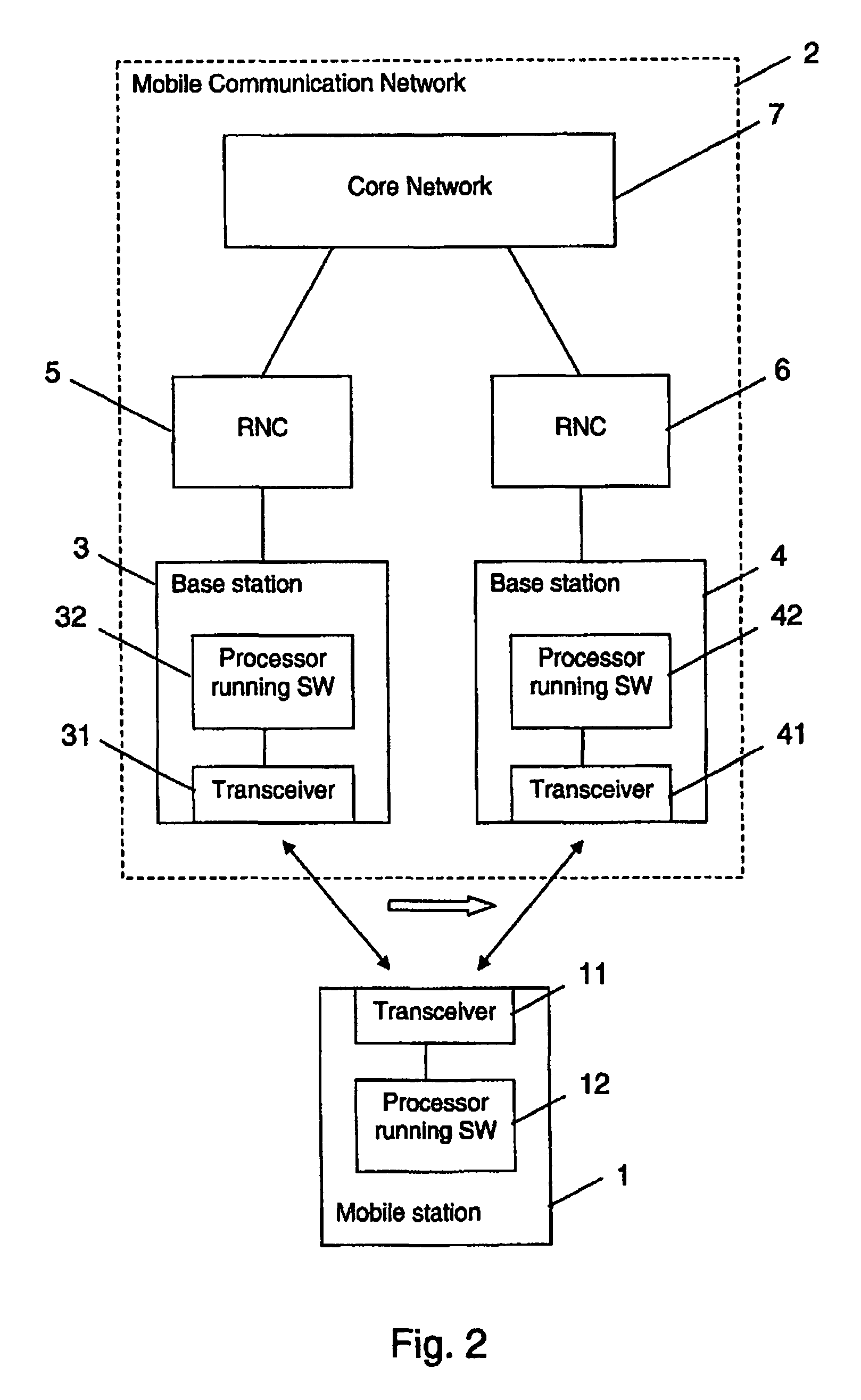
The invention relates to a method for supporting a handover of a mobile station 1 from a first radio access unit 3, 8 of a wireless communication network 2 to a second radio access unit 4, 9 of a wireless communication network 2. In order to improve a context transfer in the case of a handover of the mobile station 1, the mobile station 1 transmits information about its activity state to the second radio access unit 4, 9 when it is to be handed over to the second radio access unit 4, 9. The invention relates equally to such a mobile station, to such a second radio access unit, to a wireless communication system comprising such a mobile station and such a second radio access unit, and to a software code causing the transfer of information at the mobile station.
Owner:NOKIA TECH OY
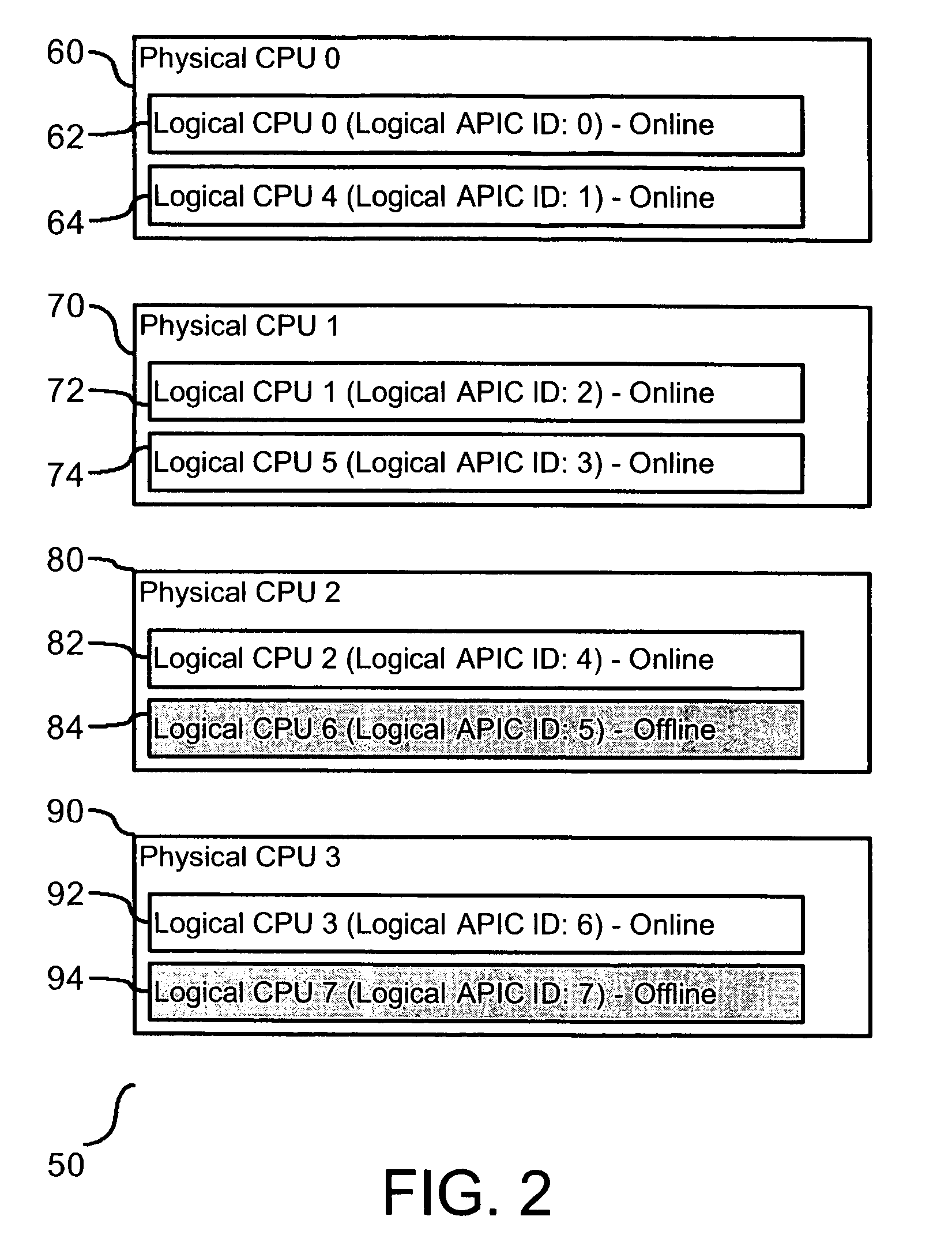
High availability multi-processor system
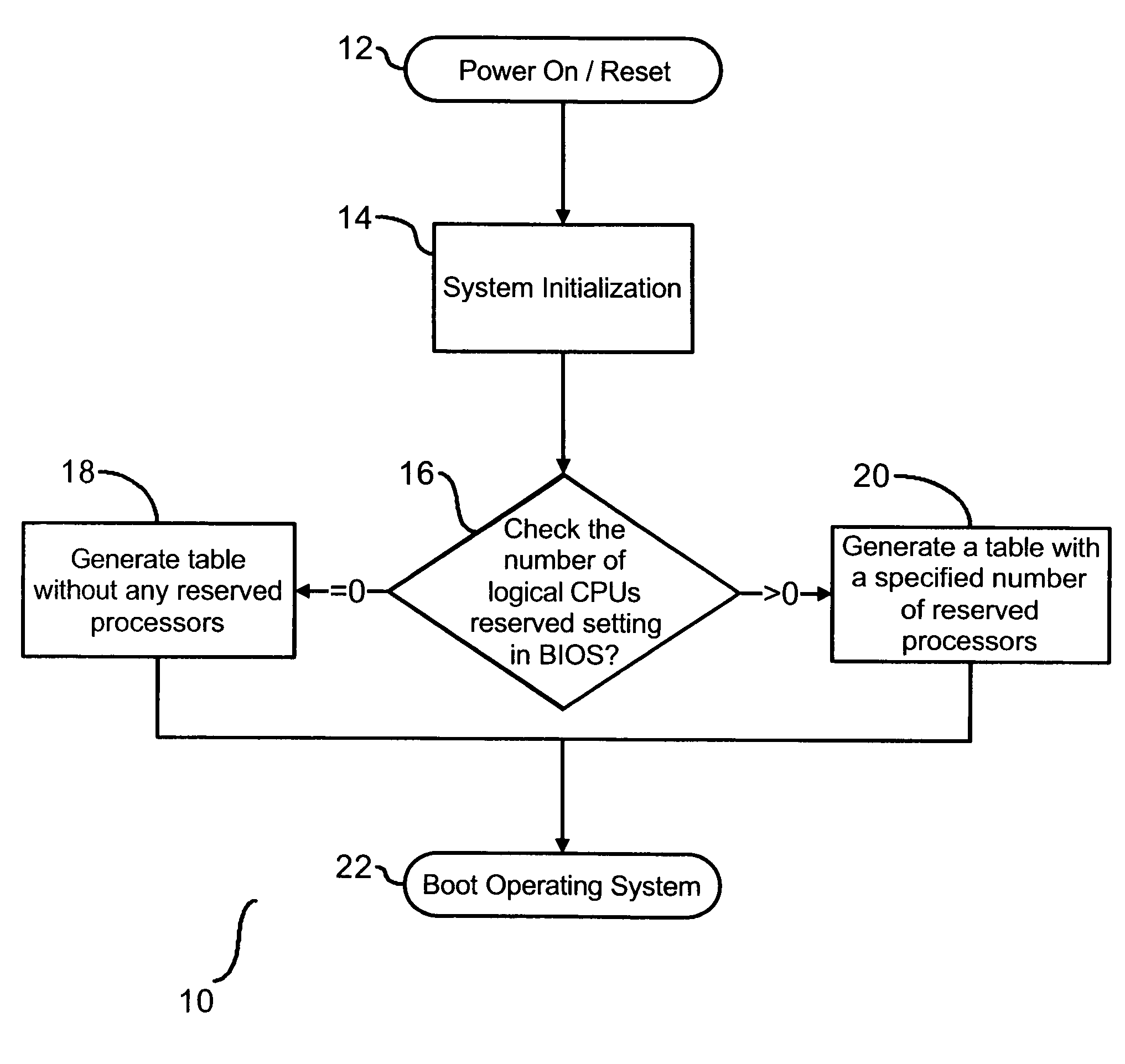
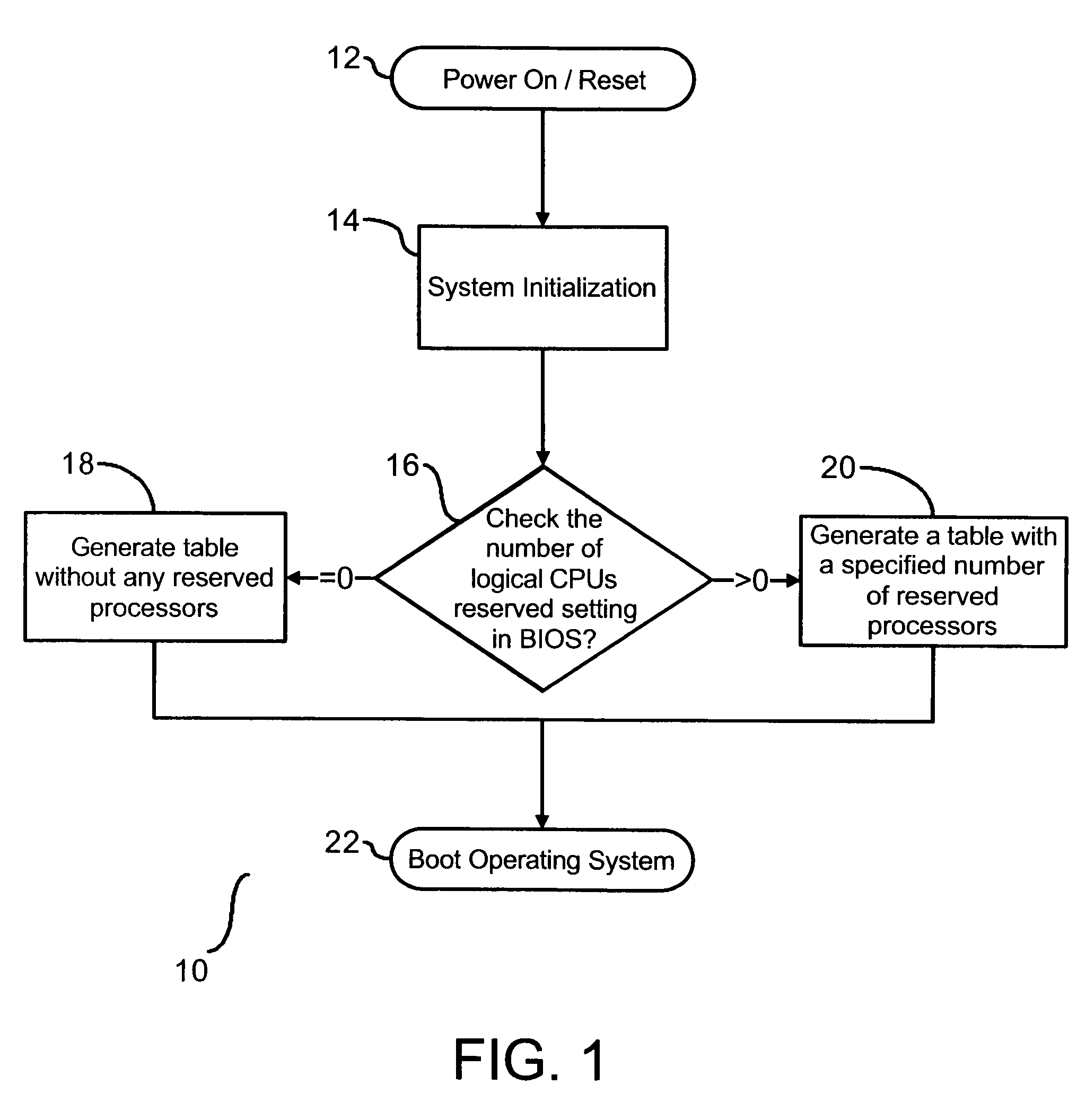
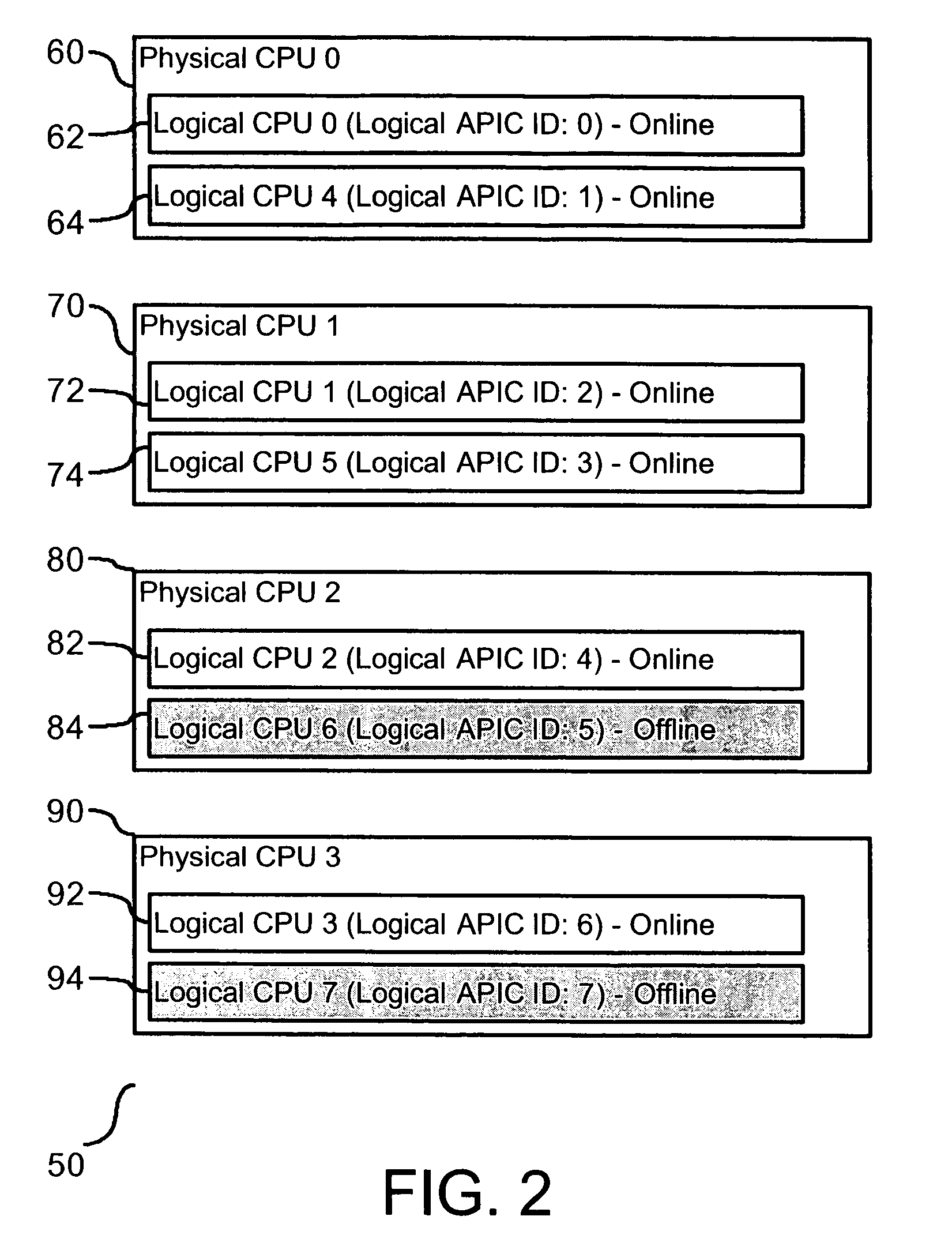
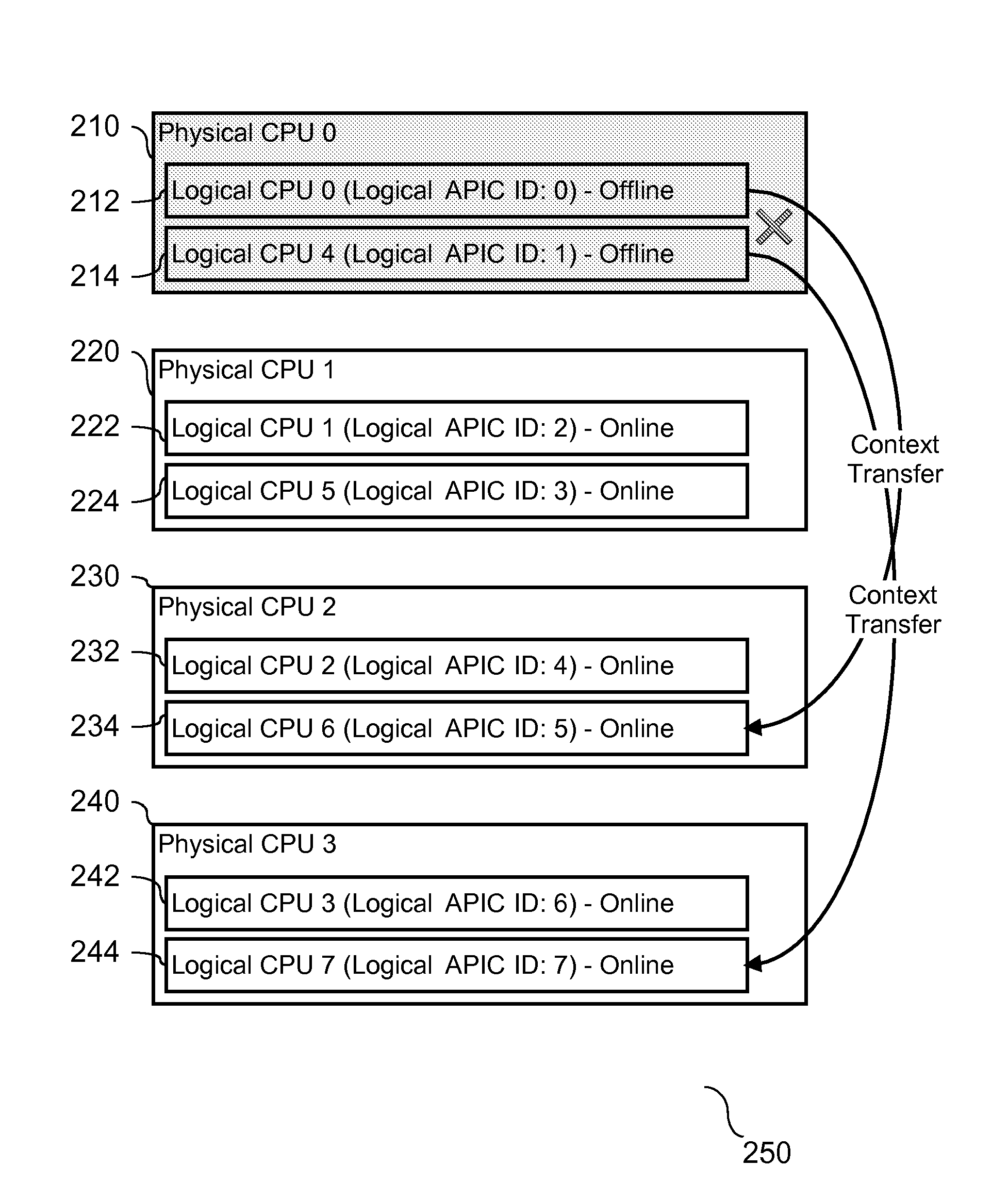
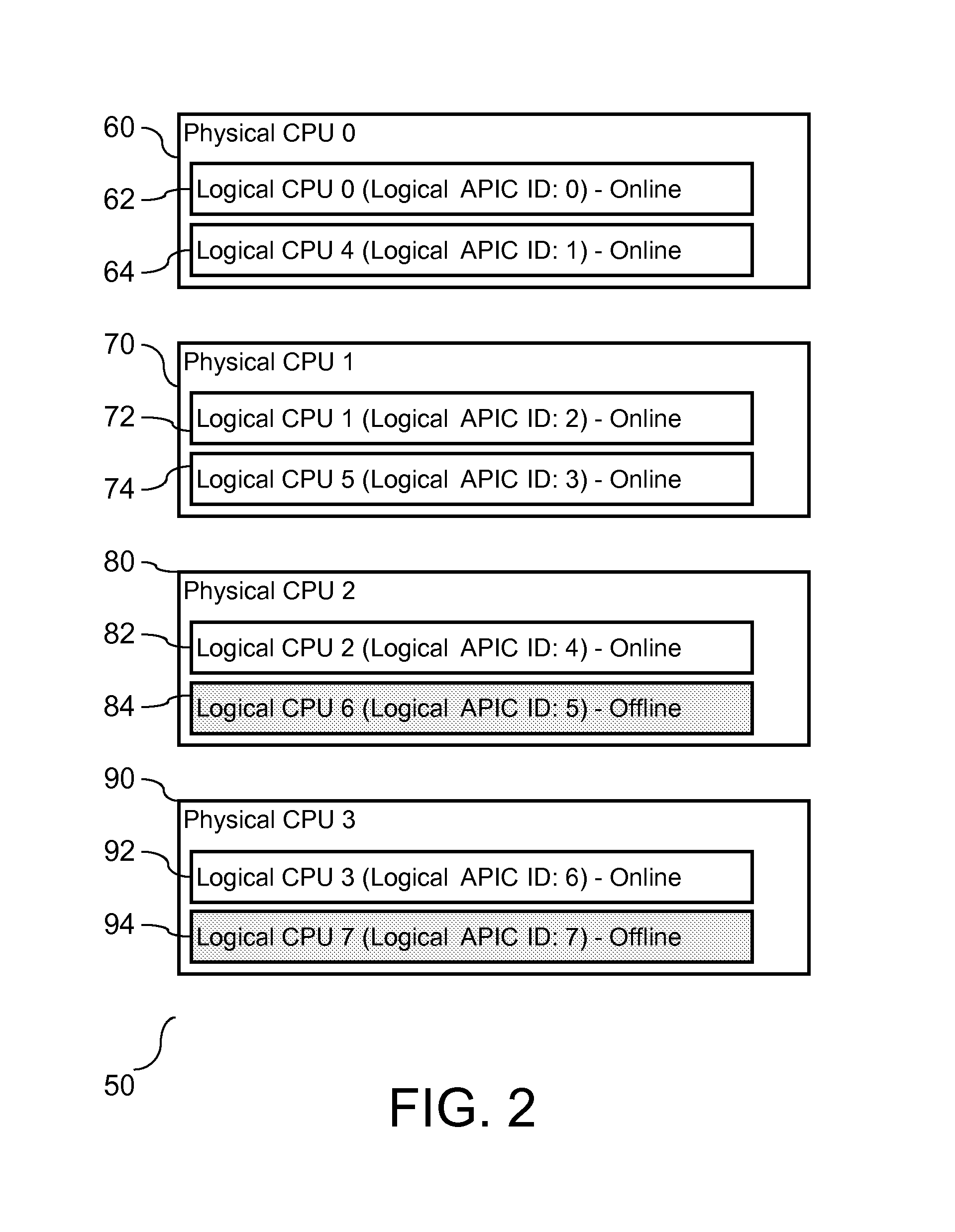
A method and system are provided for enabling replacement of a failed processor without requiring redundancy of hardware. The system is a multiprocessing computer system that includes one or more processor chips. Each processor chip may include one or more logical processors. During system initialization, one or more logical processors may be reserved in an inactive state. In the event an error is detected on a logical or physical processor, one or more reserved logical processors may have execution context transferred from the processor experiencing the error. Thereafter, the active processor is designated as inactive and replaced by the inactive processor to which the execution context has been transferred.
Owner:IBM CORP
A robust processing method for header compression U mode error
InactiveCN1996941AQuickly return to normal working conditionCompatibleNetwork traffic/resource managementData switching by path configurationRobust Header CompressionReal-time computing
Owner:HUAWEI TECH CO LTD
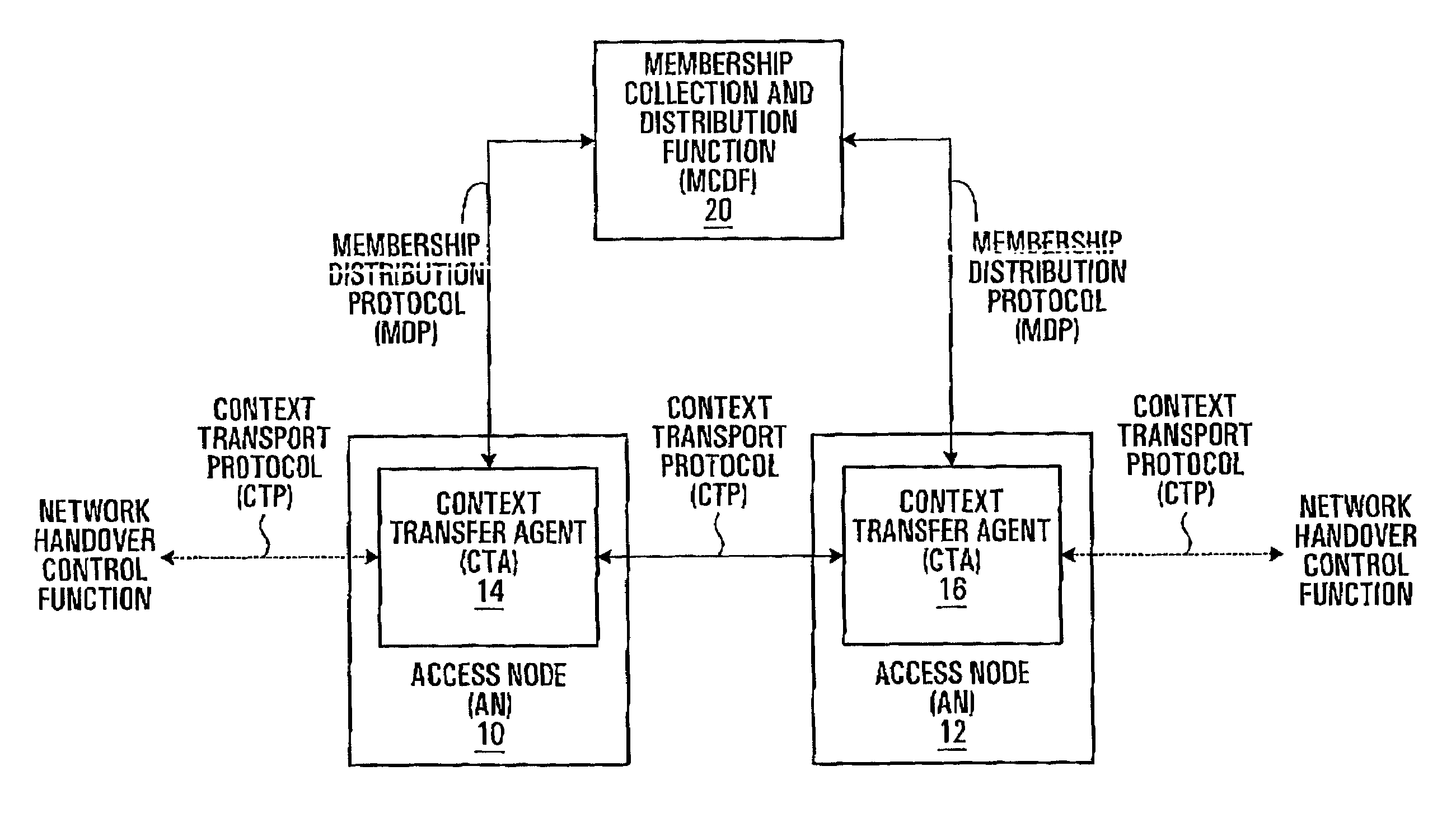
Inter-domain context transfer using context transfer managers
InactiveUS20090216906A1Simplify network managementGood informationConnection managementMultiple digital computer combinationsAccess networkHeterogeneous network
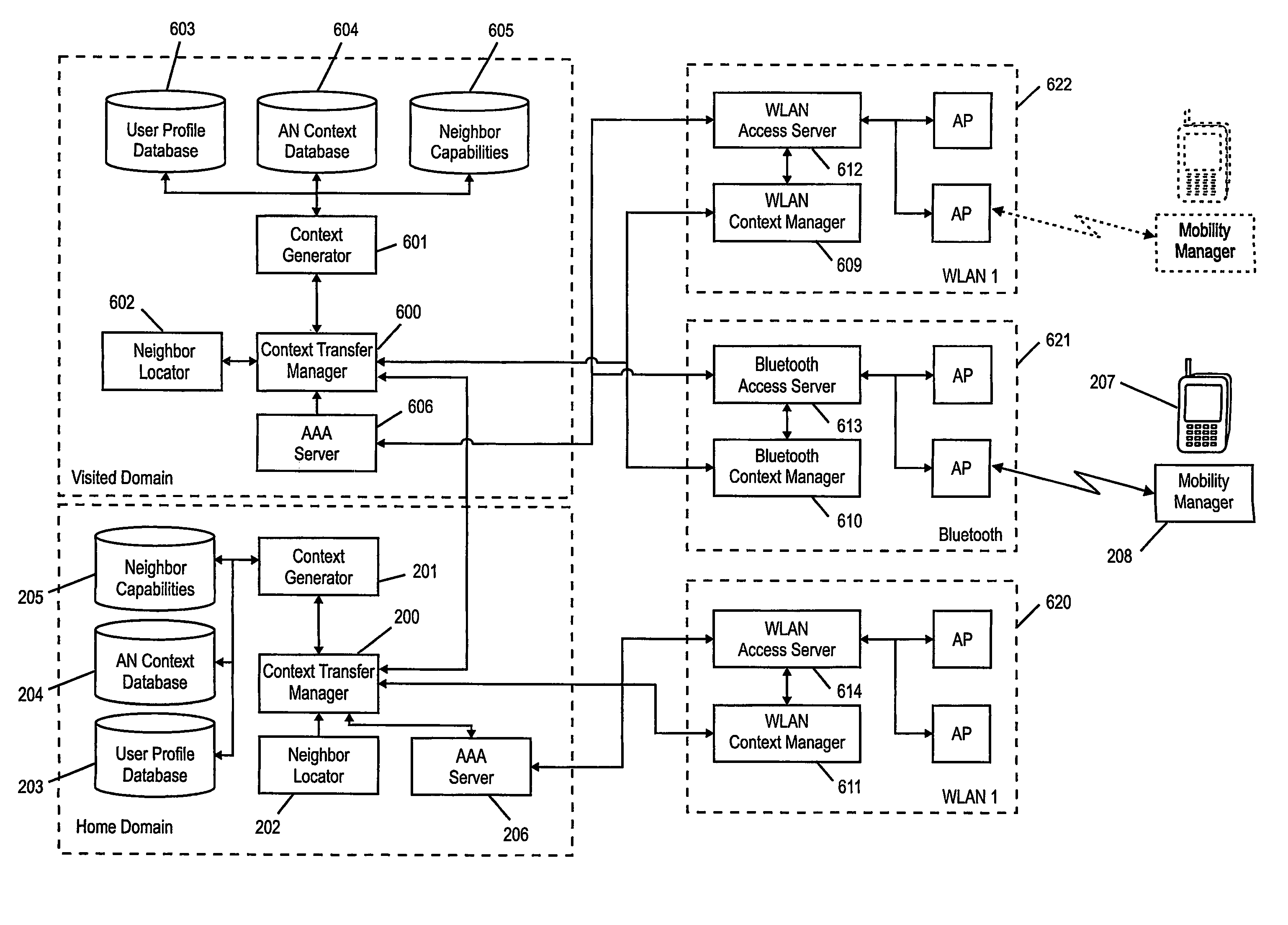
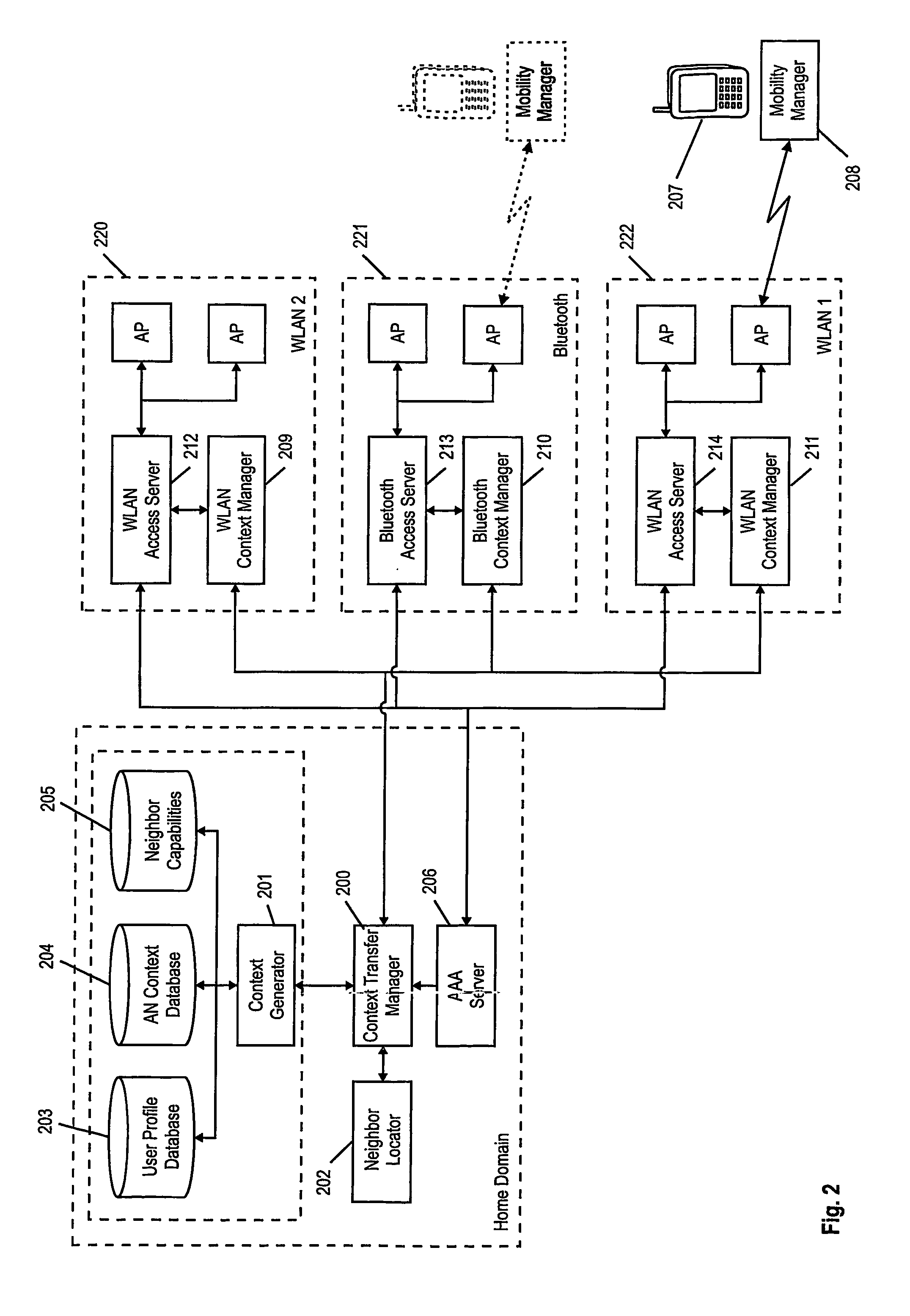
A method and apparatus for improved context transfer in heterogeneous networks is presented. Context information is collected from source entities in a first access network by a context transfer manager and transmitted to a context transfer manager of a second access network which forwards the context information to target entities therein, in one of the context transfer managers at least a part of the context information is translated from a format supported in the first access network to another format supported in the second access network. The method may be carried out proactively preceding a handover or reactively following a handover. In one embodiment, context transfer within one access domain is performed directly between access routers, whereas context transfer between different access domains is performed via the context managers. In another embodiment, beacons from access points are counted in order to determine candidates for a pending handover.
Owner:OPTIS WIRELESS TECH LLC
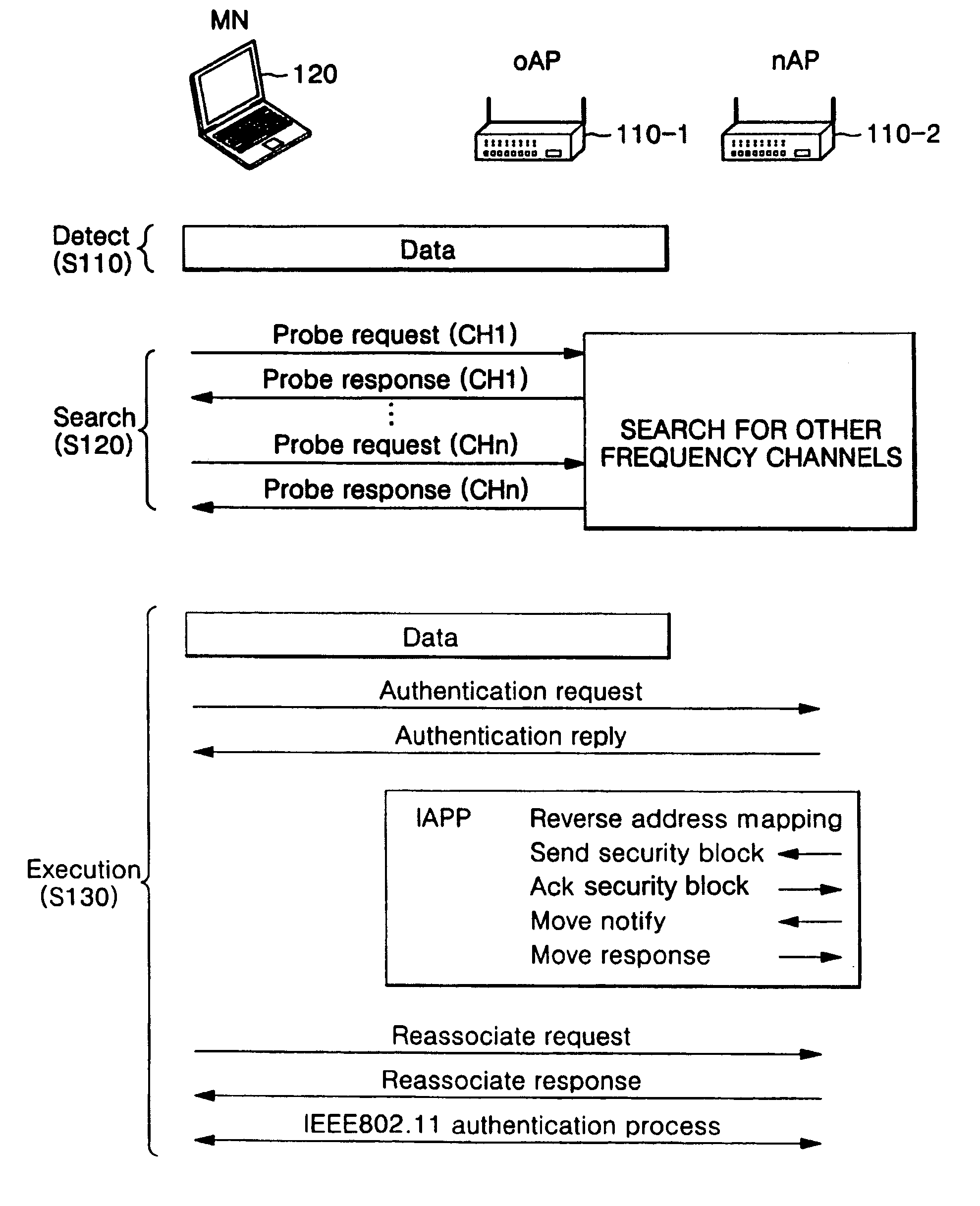
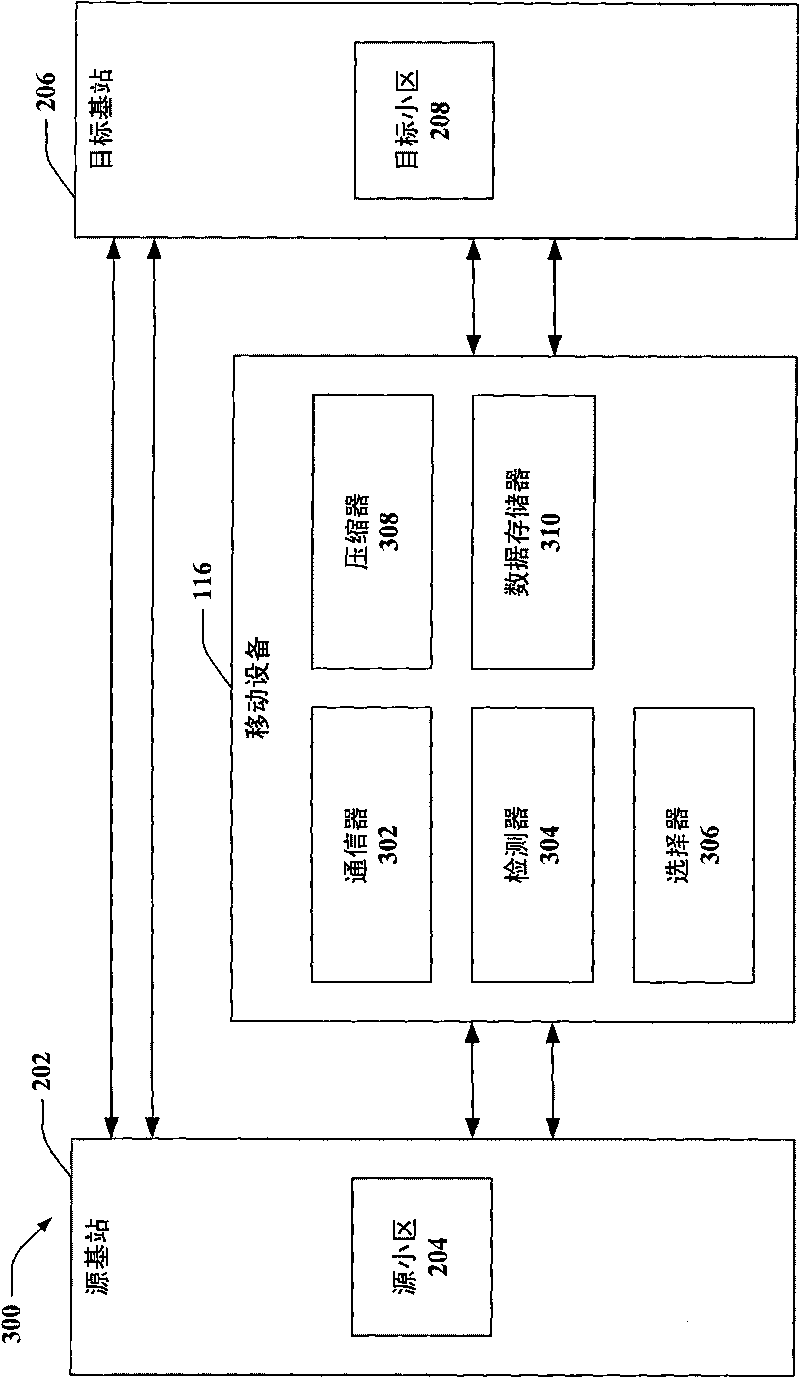
Pre-synchronization method for hard handovers in wireless networks
ActiveUS8218500B2Shorten the timeSimple methodTime-division multiplexWireless commuication servicesCurrent cellUser equipment
A pre-synchronization method in which the source cell chooses a signature for the user equipment (mobile) to use in the target cell for RACH access, and instructs the user equipment to perform RACH access and return to the current cell before a handover command (break command) is issued. This causes parallel execution of the UL synchronization process with the context transfer process among the two base stations.
Owner:APPLE INC
High availability multi-processor system
Owner:INT BUSINESS MASCH CORP
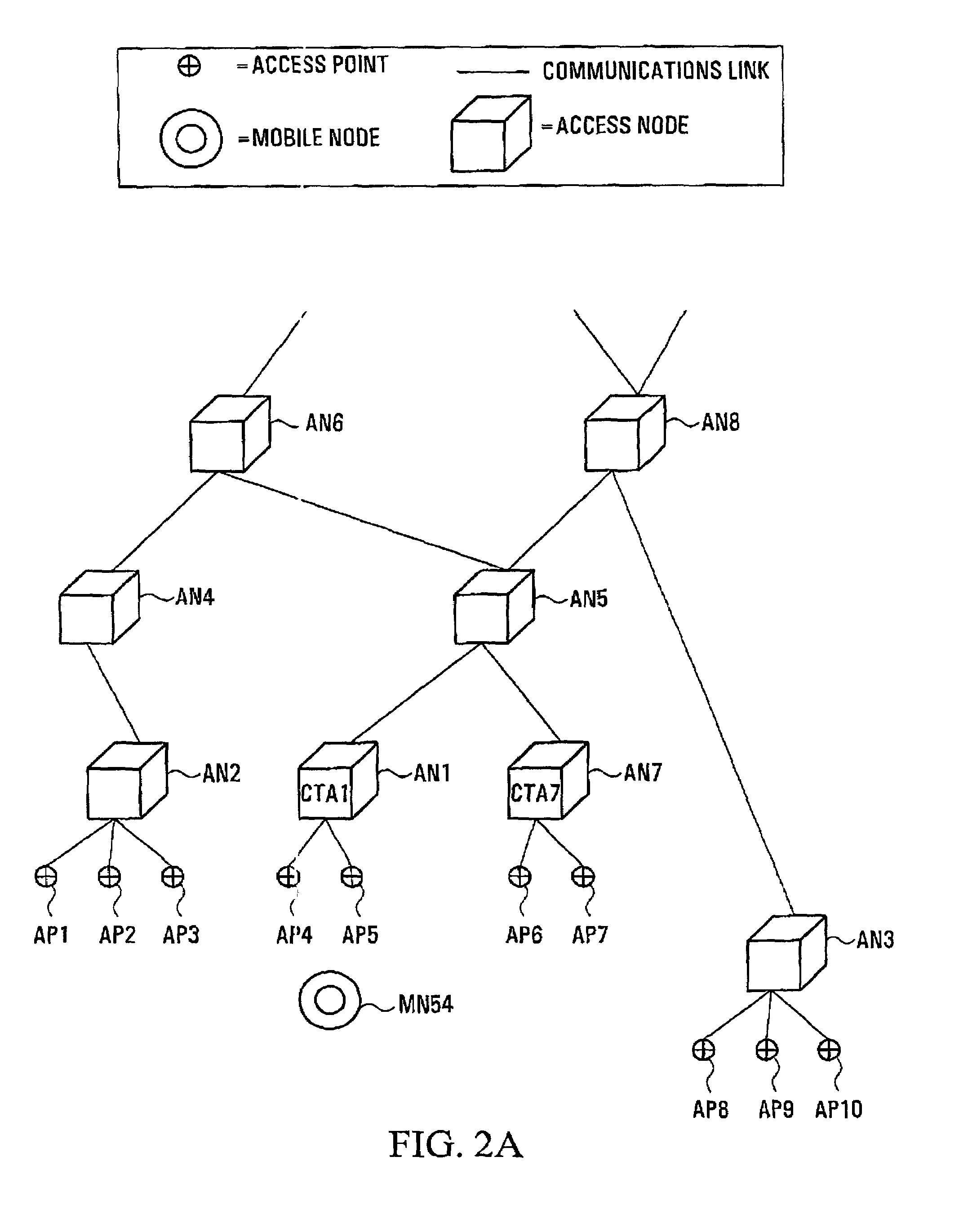
Transferring context during hand-over of mobile node in a wireless network
InactiveUS20060133320A1Reduce unnecessary useNetwork topologiesData switching by path configurationWireless mesh networkContext based
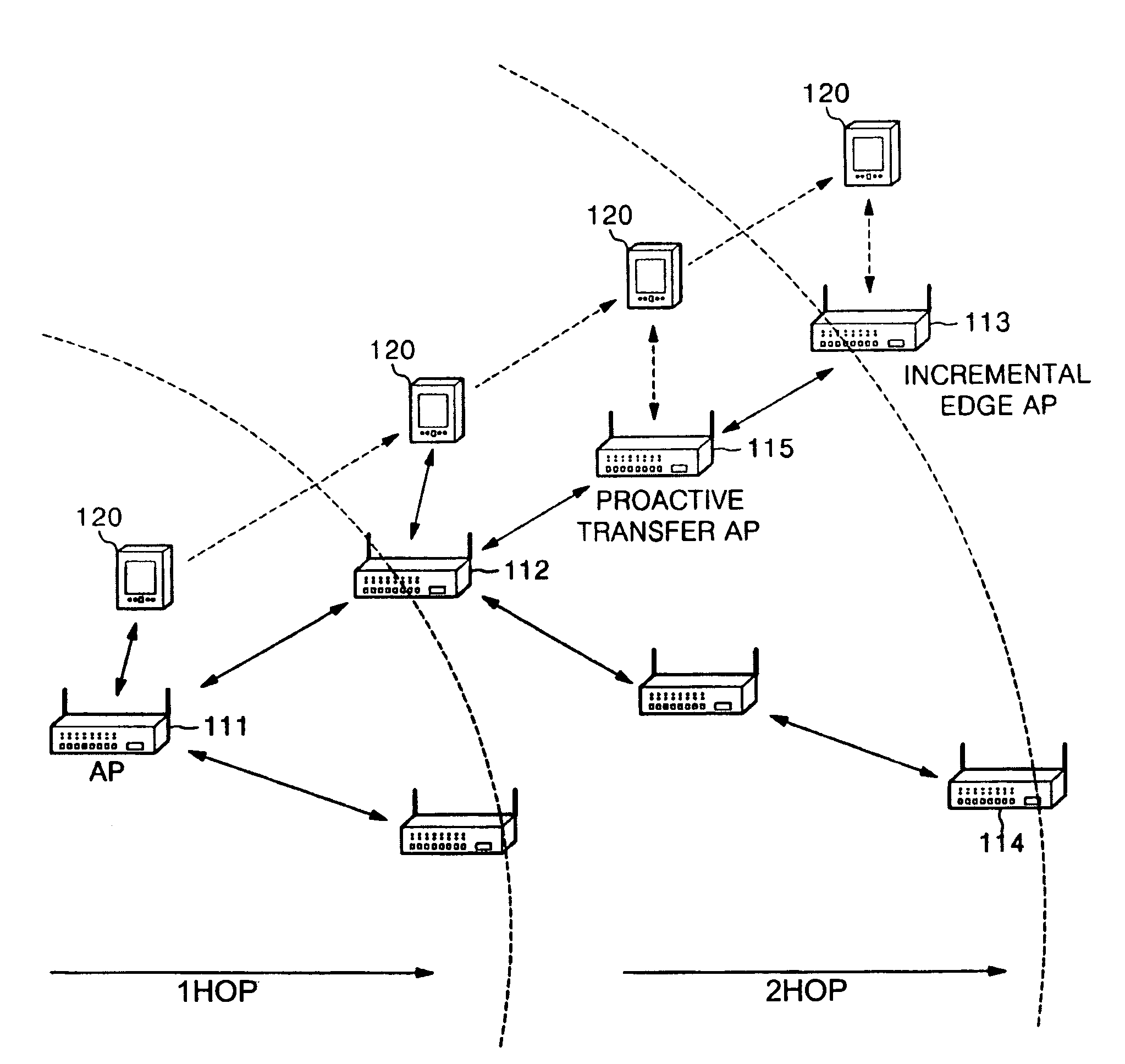
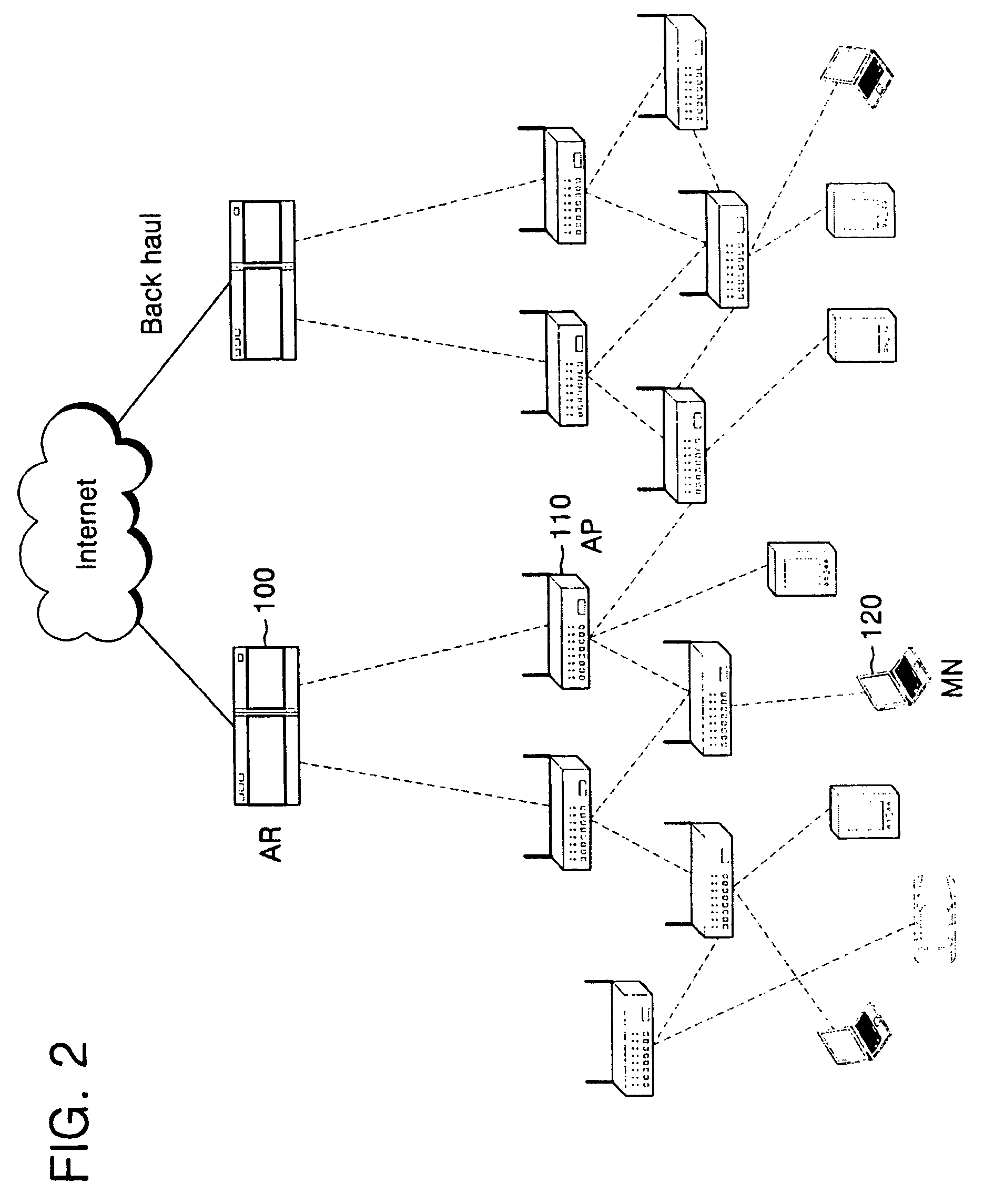
In transferring a service context during hand-over of a mobile node located in a wireless mesh network, transfer boundaries are set according to positions spaced from an initial Access Point (AP) to which the mobile node is initially connected to, AP types being determined based upon the set transfer boundaries. Prior to hand-over of the mobile node in response to its movement, a service context is transferred to APs arranged in a moving direction of the mobile node based upon context transfer policies according to the determined AP types.
Owner:SAMSUNG ELECTRONICS CO LTD
Handover of a Mobile Station
InactiveUS20080160999A1Relieve pressureMinimize the numberRadio/inductive link selection arrangementsWireless commuication servicesCommunications systemMobile station
The invention relates to a method for supporting a handover of a mobile station 1 from a first radio access unit 3, 8 of a wireless communication network 2 to a second radio access unit 4, 9 of a wireless communication network 2. In order to improve a context transfer in the case of a handover of the mobile station 1, the mobile station 1 transmits information about its activity state to the second radio access unit 4, 9 when it is to be handed over to the second radio access unit 4, 9. The invention relates equally to such a mobile station, to such a second radio access unit, to a wireless communication system comprising such a mobile station and such a second radio access unit, and to a software code causing the transfer of information at the mobile station.
Owner:NOKIA TECHNOLOGLES OY
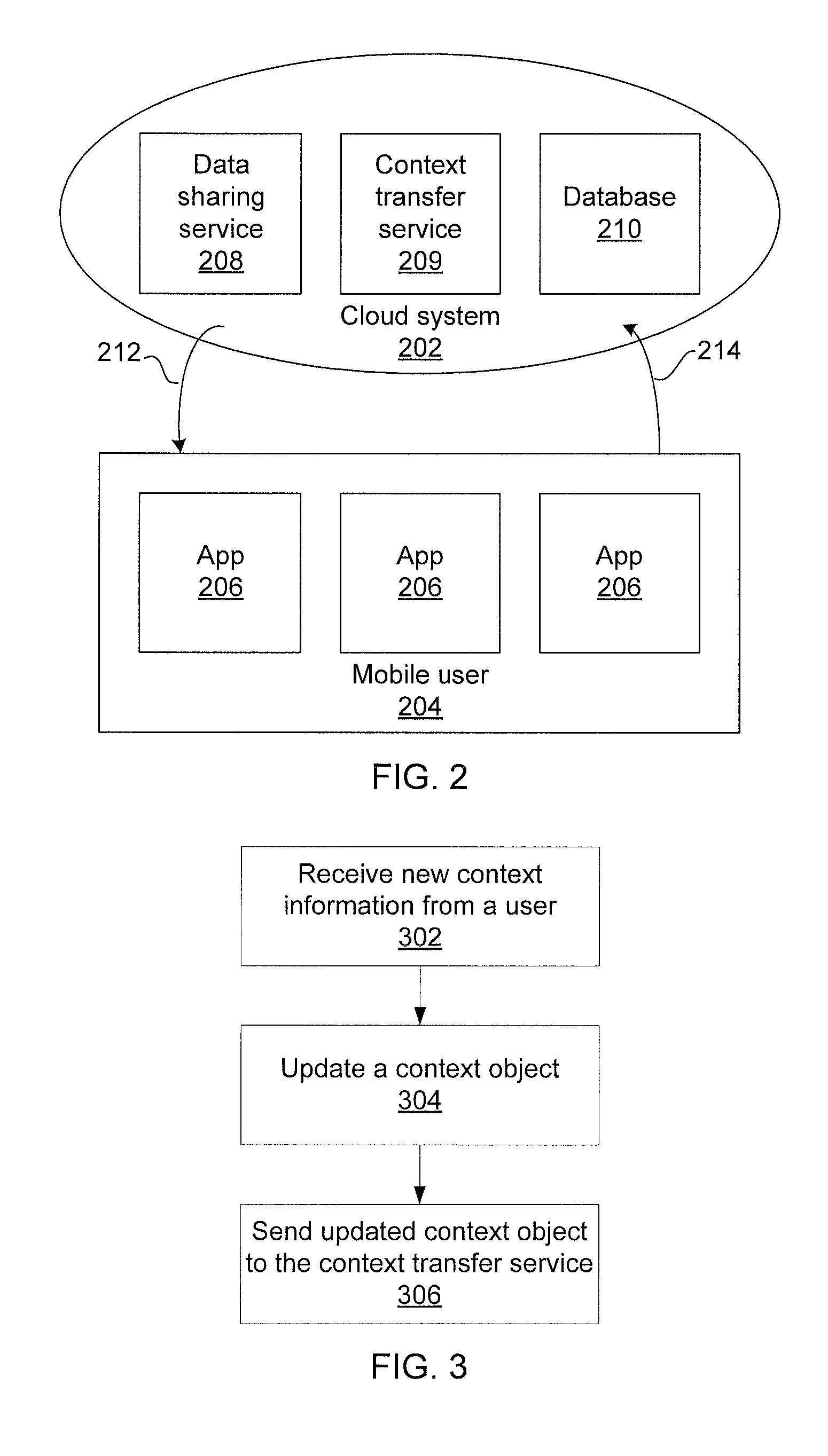
Seamless context transfers for mobile applications
InactiveUS20130226878A1Digital data information retrievalDigital data processing detailsTimestampData mining
Methods and systems for seamless context transfers include receiving a context object from one or more applications, where the context object including updated context information for a user having an associated timestamp; entering the updated context information into a context information database; determining entries of the context information database for the user having a timestamp older than a predetermined threshold using a processor; purging the determined entries from the context information database; and sending an updated context object to one or more applications that reflects a current state of the context information for the user.
Owner:NEC LAB AMERICA
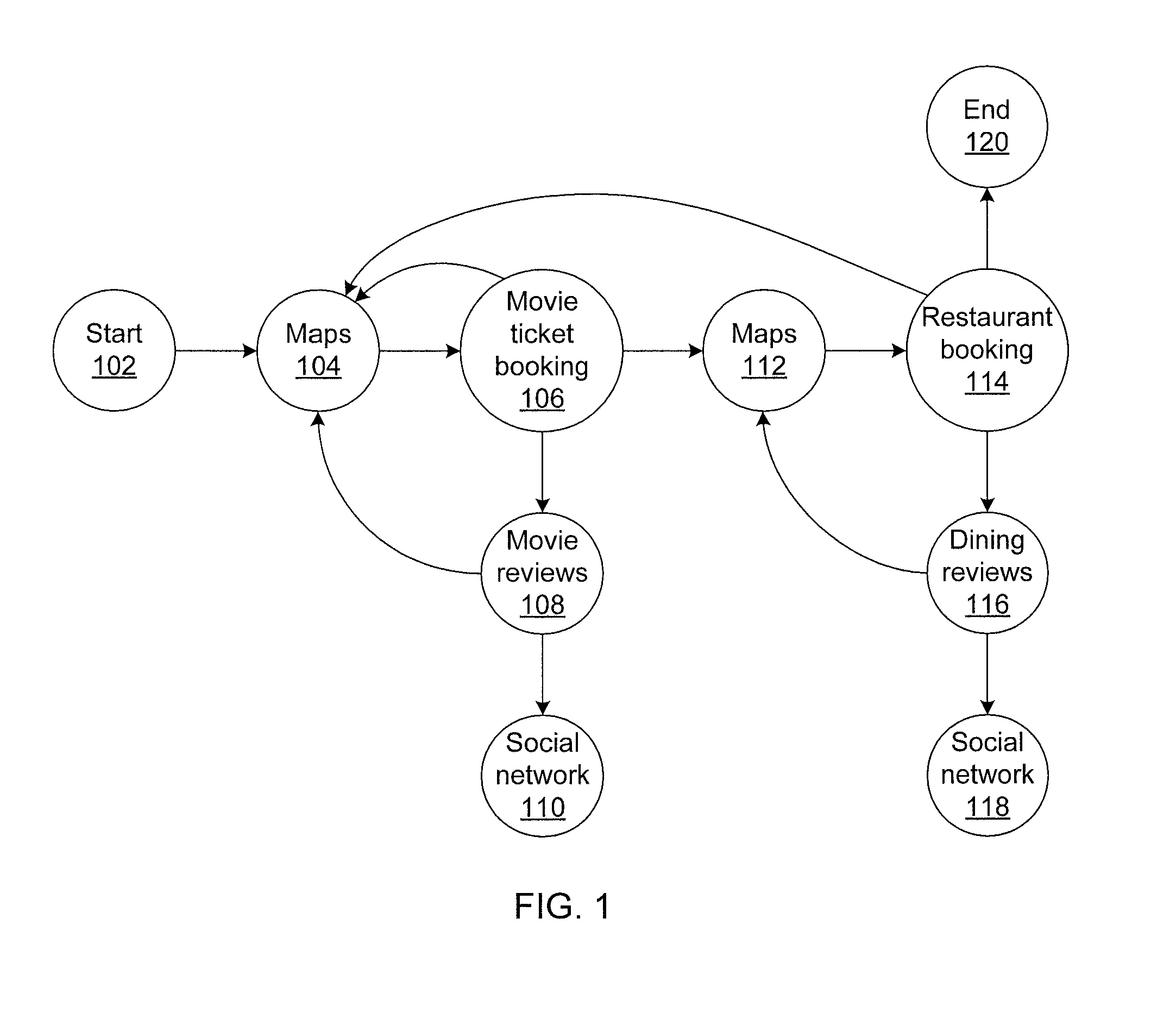
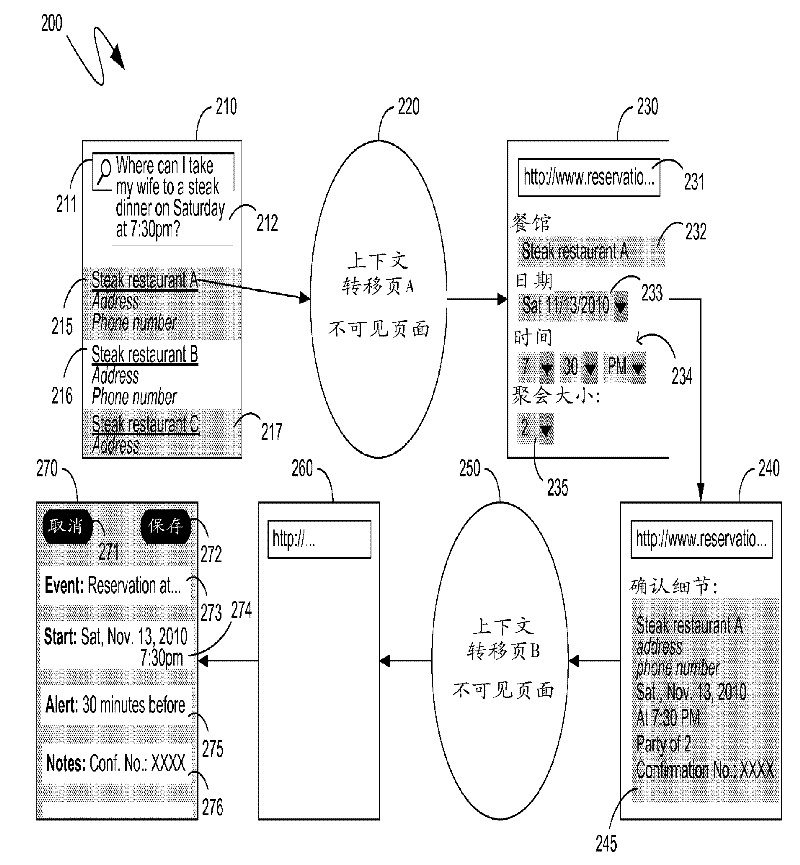
Automated task completion by flowing context
Providing context to a target minimizes the amount of information that a user must input. Context transfer pages receive context and reformat for the target. Selection of links to such pages provide context which is then reformatted and provided to the target to pre-populate information for the user. A return link can be specified to enable the target to return further context upon user interaction completion. The return link can specify further context transfer pages which can use the returned context to direct the performance of convenience actions, including invoking other applications on the user's computing device and entering information into them. The context transfer pages can themselves collect information from the user to provide appropriate interfaces without requiring resource investment from the target.
Owner:MICROSOFT TECH LICENSING LLC
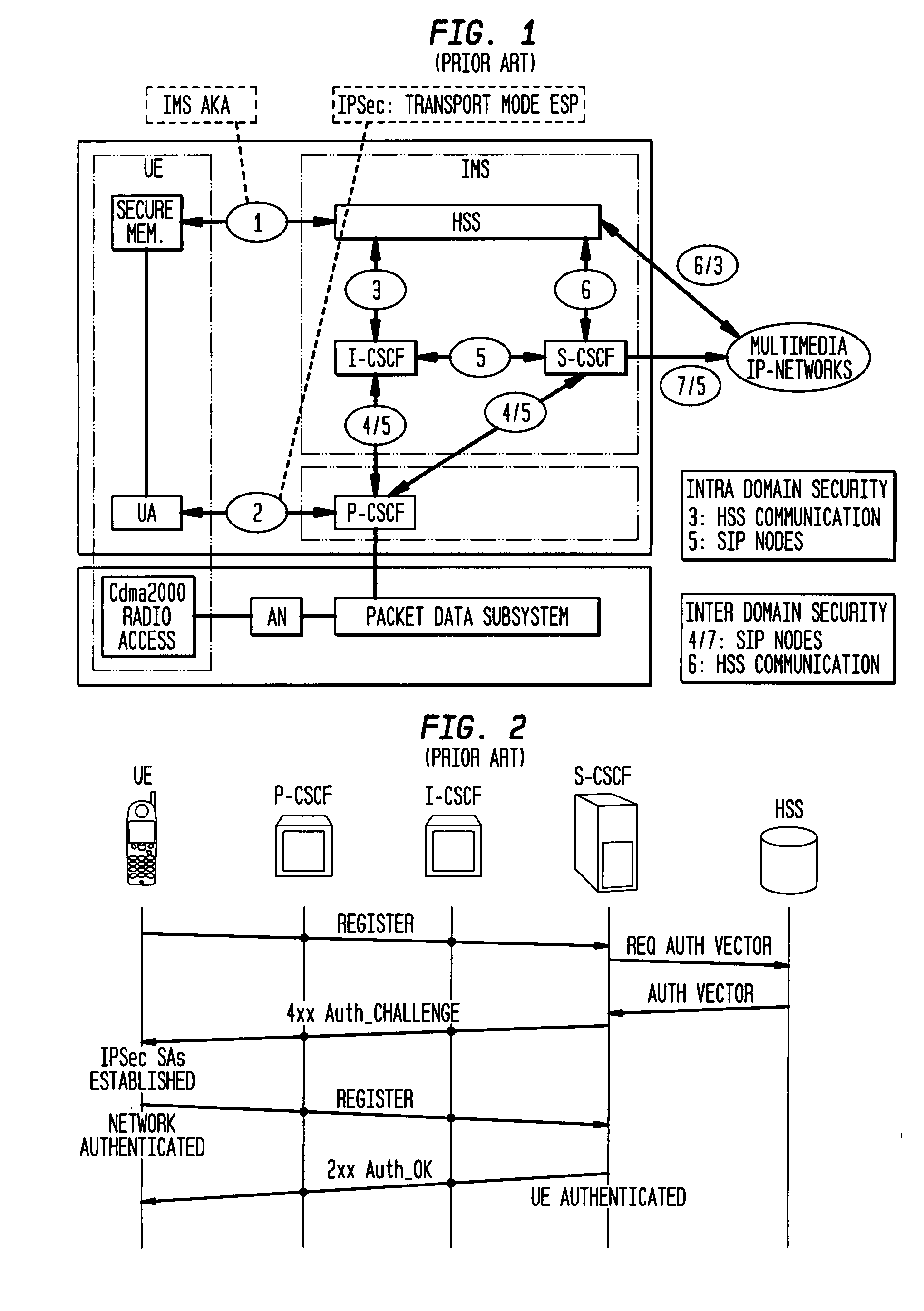
Security optimization for IMS/MMD architecture
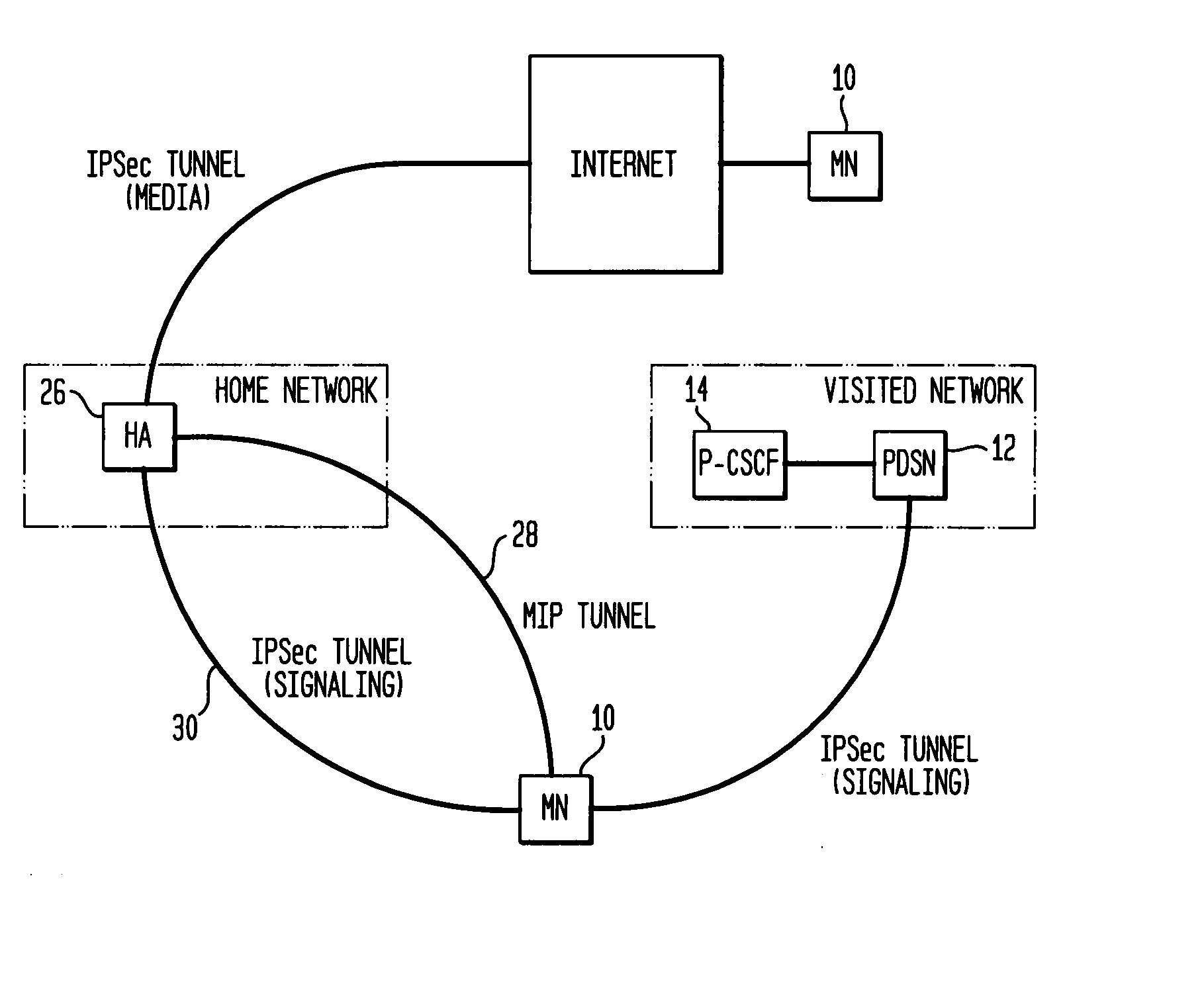
ActiveUS20080072310A1Shorten the timeReducing tunnel overheadMultiple digital computer combinationsProgram controlIPsecContext transfer
A mechanism by which handoff delay can be minimized while not compromising the IMS / MMD security and also protecting the media if required by certain applications is presented. Methods for mitigating delay during SA re-association and mitigating the IPSec tunnel overhead for signaling and media at the Mobile Node are given. In one embodiment, SA keys can be transferred from the old P-CSCF to new P-CSCF, enabling the establishment of SAs before Mobile Node physically moves to the new subnet in a network. Proactive handover is used. In another embodiment, SA keys are transferred from S-CSCF to new P-CSCF. In this case, the SA keys are transferred to the new P-CSCF by S-CSCF through a context transfer mechanism well in advance so that SAs may be established before Mobile Node physically moves to new subnet. In another embodiment, methods for mitigating IPSec tunnel overhead are presented.
Owner:TELCORDIA TECHNOLOGIES INC +1
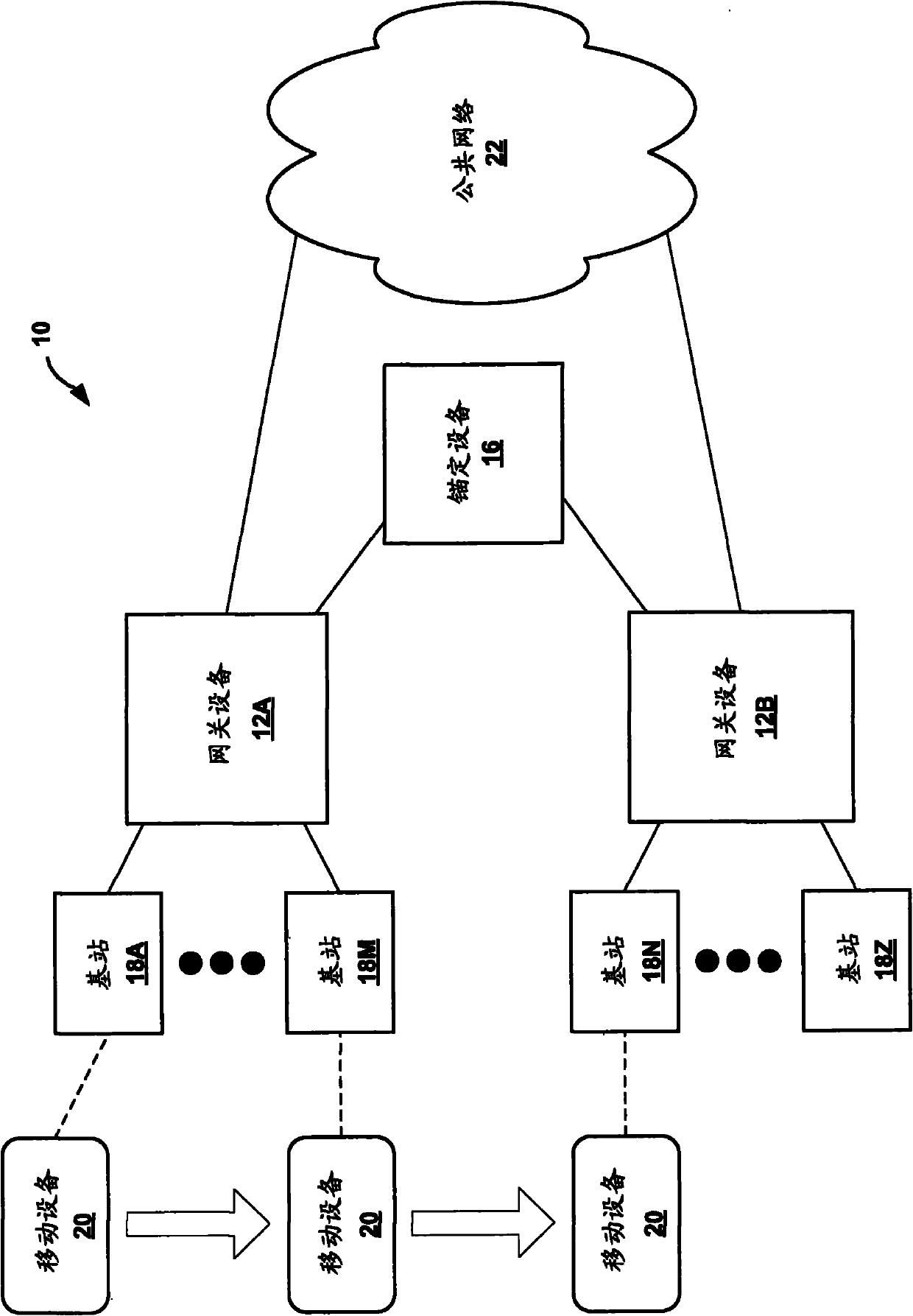
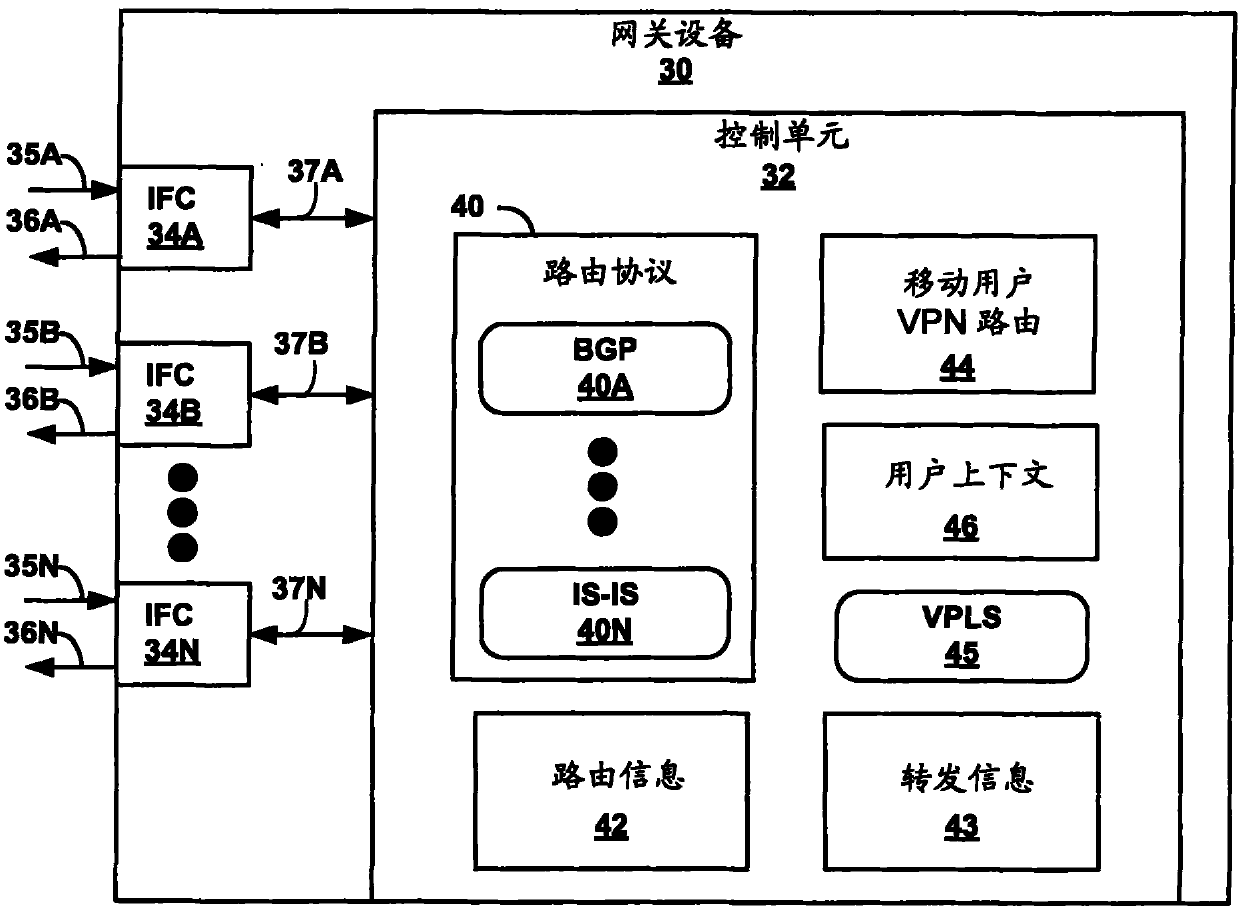
Network-based macro mobility in cellular networks using an extended routing protocol
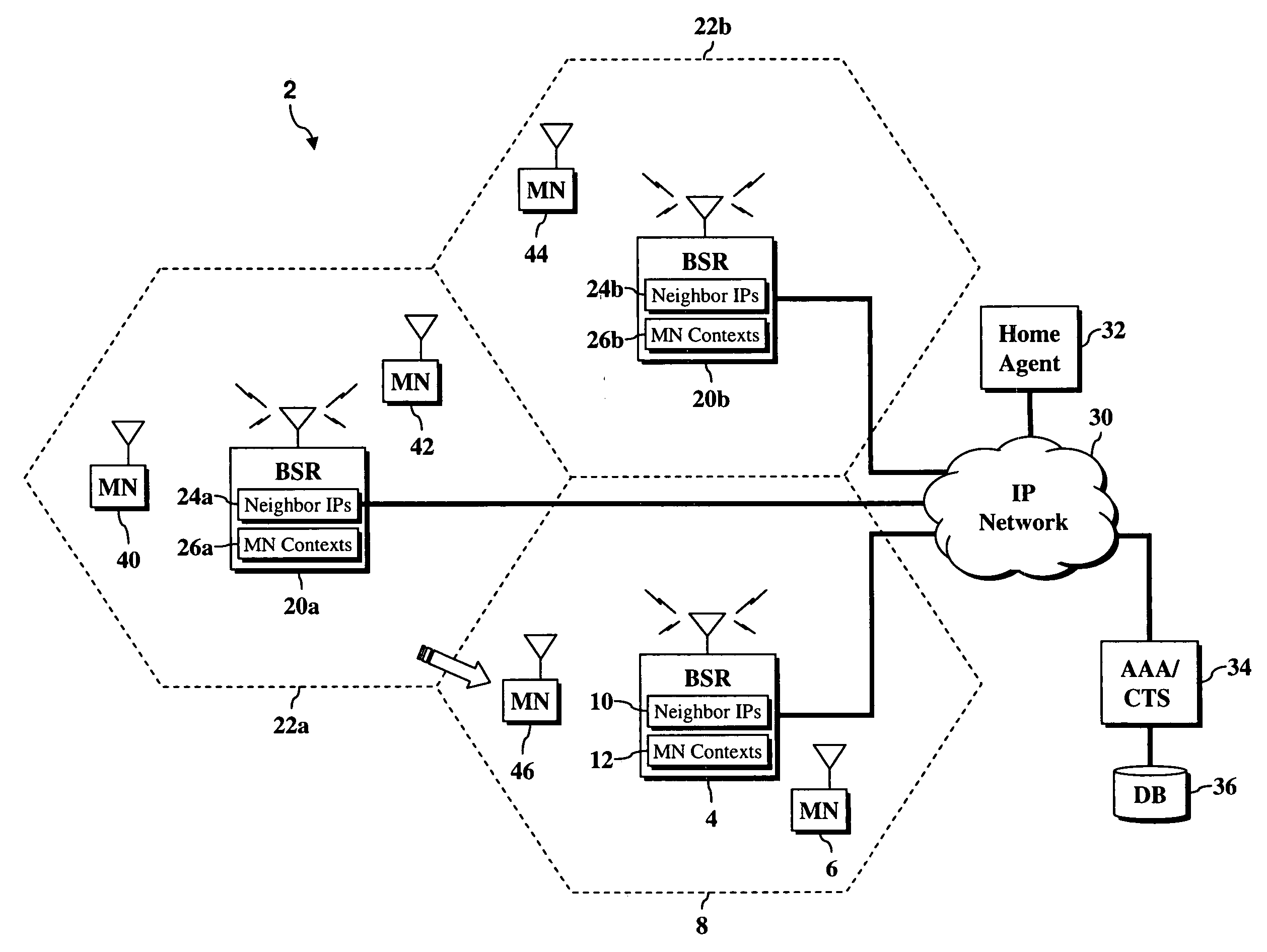
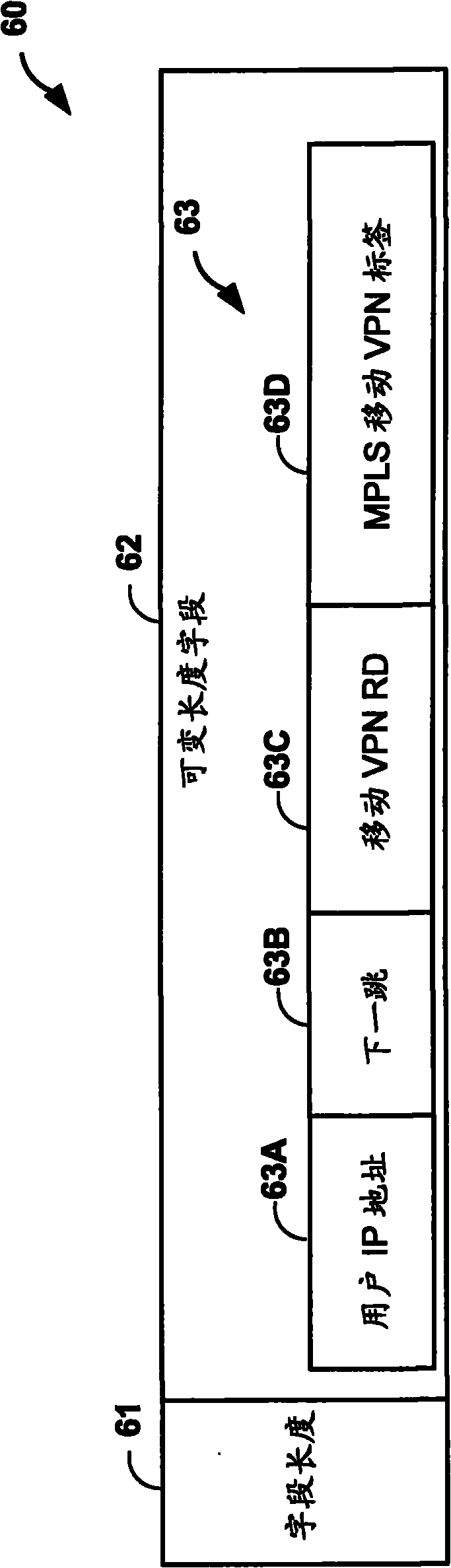
A new architecture provides network-based mobility in cellular networks that is built on Internet Protocol (IP) / Multiprotocol Label Switching (MPLS) technologies, such as Virtual Private Local Area Network (LAN) Service (VPLS), the Border Gateway Protocol (BGP) and BGP MPLS Layer 3 Virtual Private Networks (VPNs). The architecture consists of several building blocks that provide functionality for different aspects of cellular network mobility. One building block is network-based macro mobility in IP / MPLS networks. The macro mobility techniques described herein are built on extensions to a routing protocol such as BGP. Another building block relates to transferring subscriber context between network devices while preserving the IP address of the subscriber. The techniques described herein provide a subscriber context transfer mechanism for mobile subscriber management that is built on extensions to a routing protocol such as BGP. Another building block of the mobility architecture is network-based micro mobility based on VPLS.
Owner:JUMIPER NETWORKS INC
Context transfer in a communication network comprising plural heterogeneous access networks
ActiveUS7688785B2Easy mappingNetwork topologiesWireless commuication servicesAccess networkRadio access network
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
Compression static and semi-static context transfer
Systems, methodologies, and devices are described that facilitate transferring a subset of compression context from a source base station to a target base station during an inter-base station handover of a mobile device to facilitate establishment of compression context between the mobile device and target base station. The source base station can transfer a subset of compression context comprising static and semi-static context to the target base station during inter-base station handover to at least partially establish compression context between the mobile device and target base station prior to or during handover. The source base station can transmit, to the mobile device, indicator information related to compression context transferred. The target base station can at least partially establish compression context based on received subset of compression context to facilitate efficient communication with the mobile device and can establish any remaining portion of compression context with the mobile device after handover.
Owner:QUALCOMM INC
Wireless security system and method
InactiveUS7885410B1Key distribution for secure communicationUnauthorised/fraudulent call preventionClient-sideDirect communication
A method for providing private sidestream transmissions between a first and second client in a wireless network generally includes sending a location discovery request from a first client to an access point and receiving a location discovery response from the access point. The response includes a ticket encrypted with a session key of the second client and containing a sidestream key. The method further includes sending a direct communication request from the first client to the second client. The request includes the ticket and an authenticator encrypted with the sidestream key. A direct communication response including an updated authenticator is received from the second client. A method and apparatus for secure context transfer during client roaming are also disclosed.
Owner:CISCO TECH INC
High Availability Multi-Processor System
A method and system are provided for enabling replacement of a failed processor without requiring redundancy of hardware. The system is a multiprocessing computer system that includes one or more processor chips. Each processor chip may include one or more logical processors. During system initialization, one or more logical processors may be reserved in an inactive state. In the event an error is detected on a logical or physical processor, one or more reserved logical processors may have execution context transferred from the processor experiencing the error. Thereafter, the active processor is designated as inactive and replaced by the inactive processor to which the execution context has been transferred.
Owner:INT BUSINESS MASCH CORP
Transferring context during hand-over of mobile node in a wireless network
InactiveUS7542449B2Reduce unnecessary useNetwork topologiesData switching by path configurationWireless mesh networkContext based
Owner:SAMSUNG ELECTRONICS CO LTD
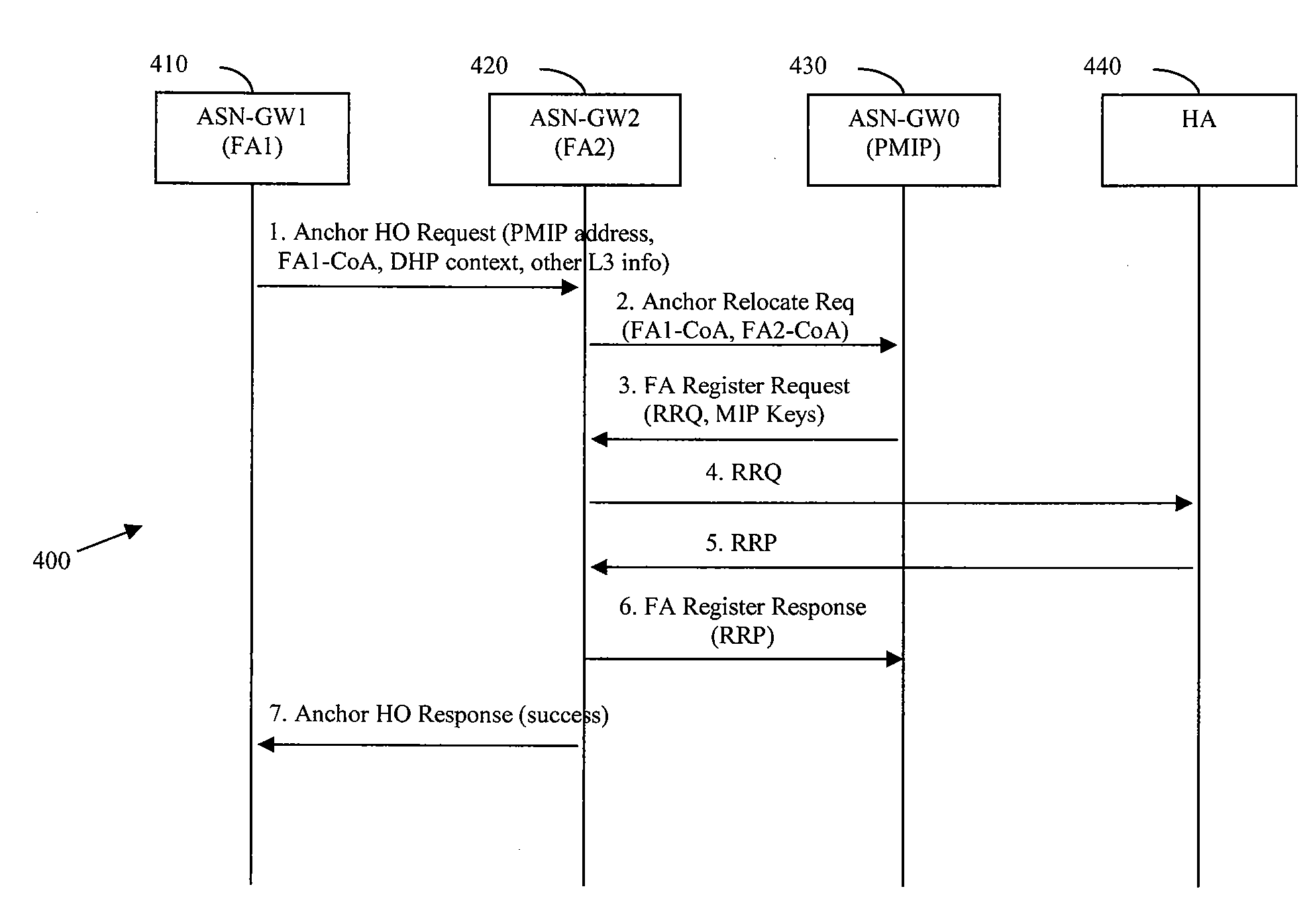
System For FA Relocation With Context Transfer In Wireless Networks
ActiveUS20080273496A1Data switching by path configurationMultiple digital computer combinationsWireless mesh networkForeign agent
A system for foreign agent relocation in a wireless network. The system comprises at least one first foreign agent; at least one second foreign agent; and at least one mobile node. Relocation negotiation is performed to determine whether foreign agent relocation of the mobile node from the at least one first foreign agent to the at least one second foreign agent is agreed, and foreign agent relocation is performed if the foreign agent relocation is agreed.
Owner:FUTUREWEI TECH INC
Method and system for handling context of data packet flows
InactiveUS7706325B2Facilitates session management and chargingOrganized and controlledConnection managementWireless network protocolsSession controlMiddlebox
Owner:UNWIRED PLANET
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com