Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
211results about How to "Easy mapping" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
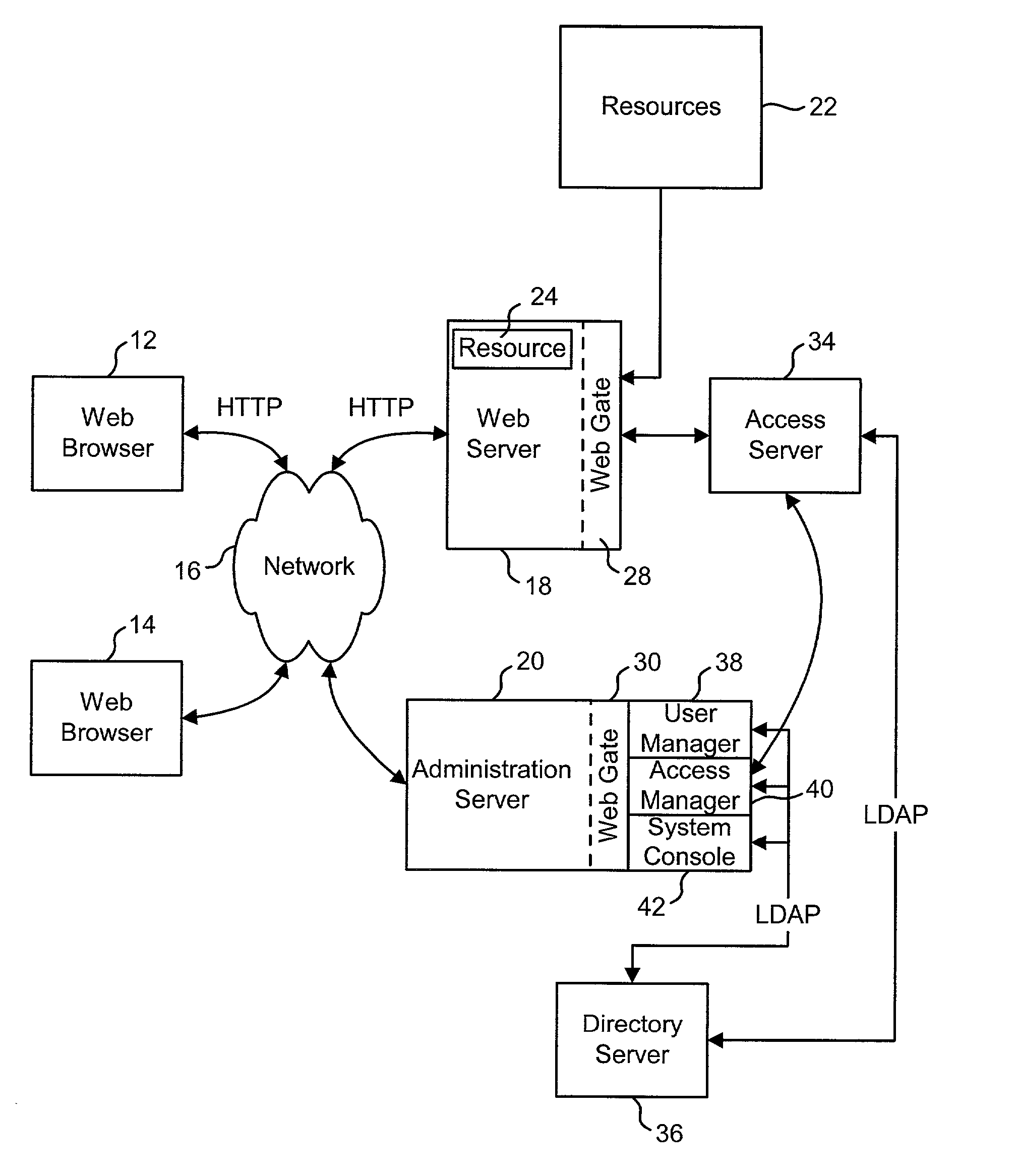
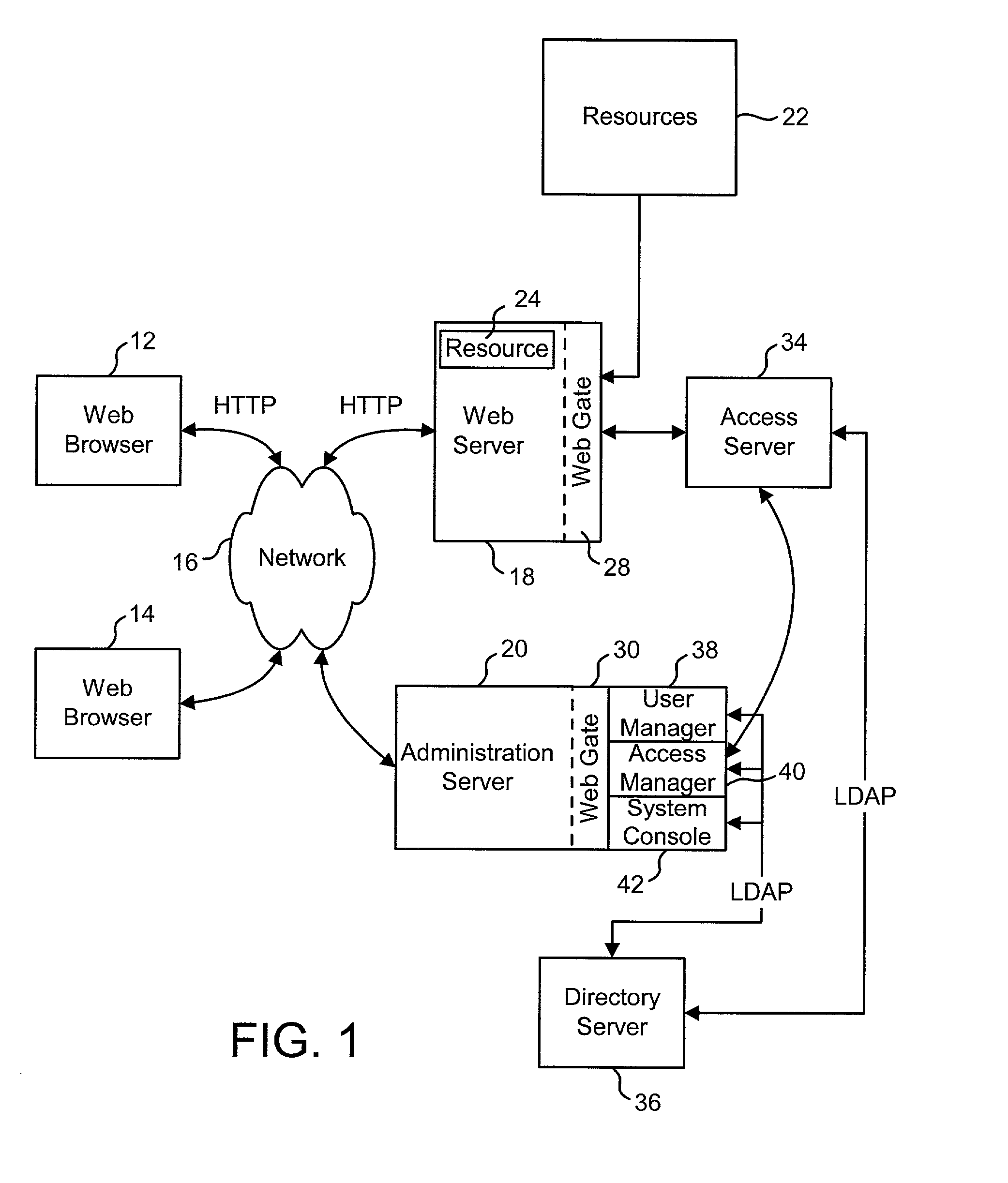
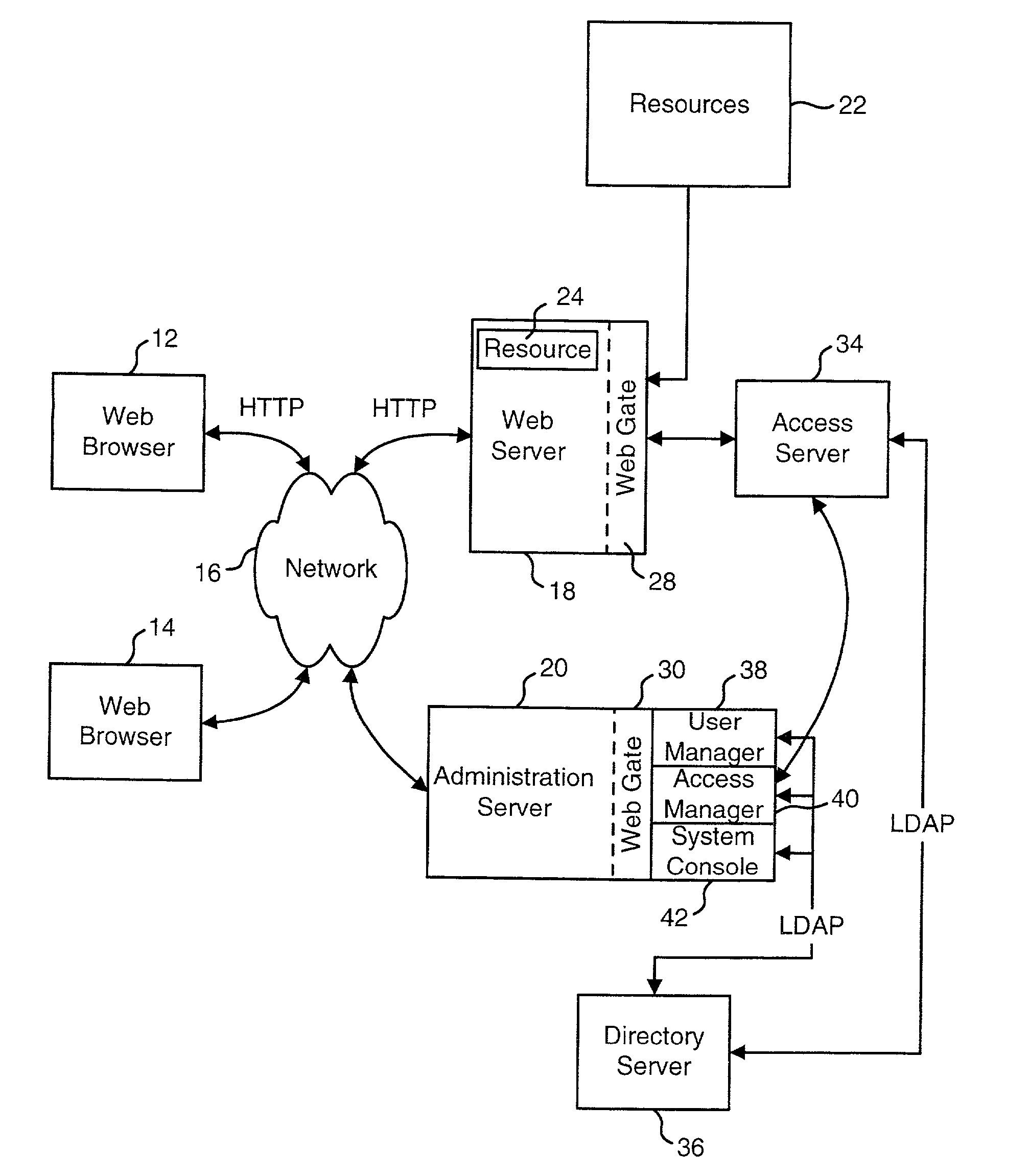
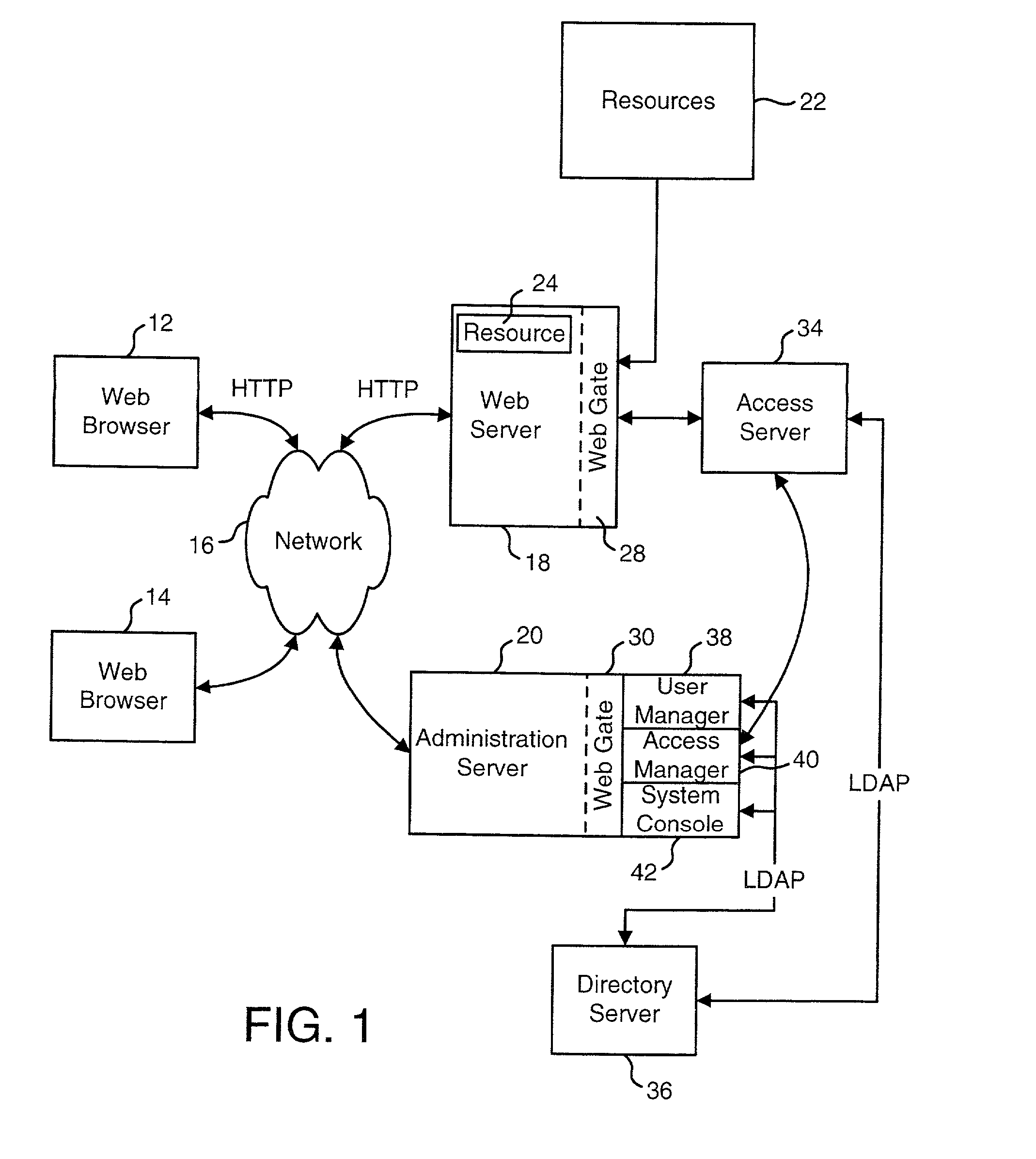
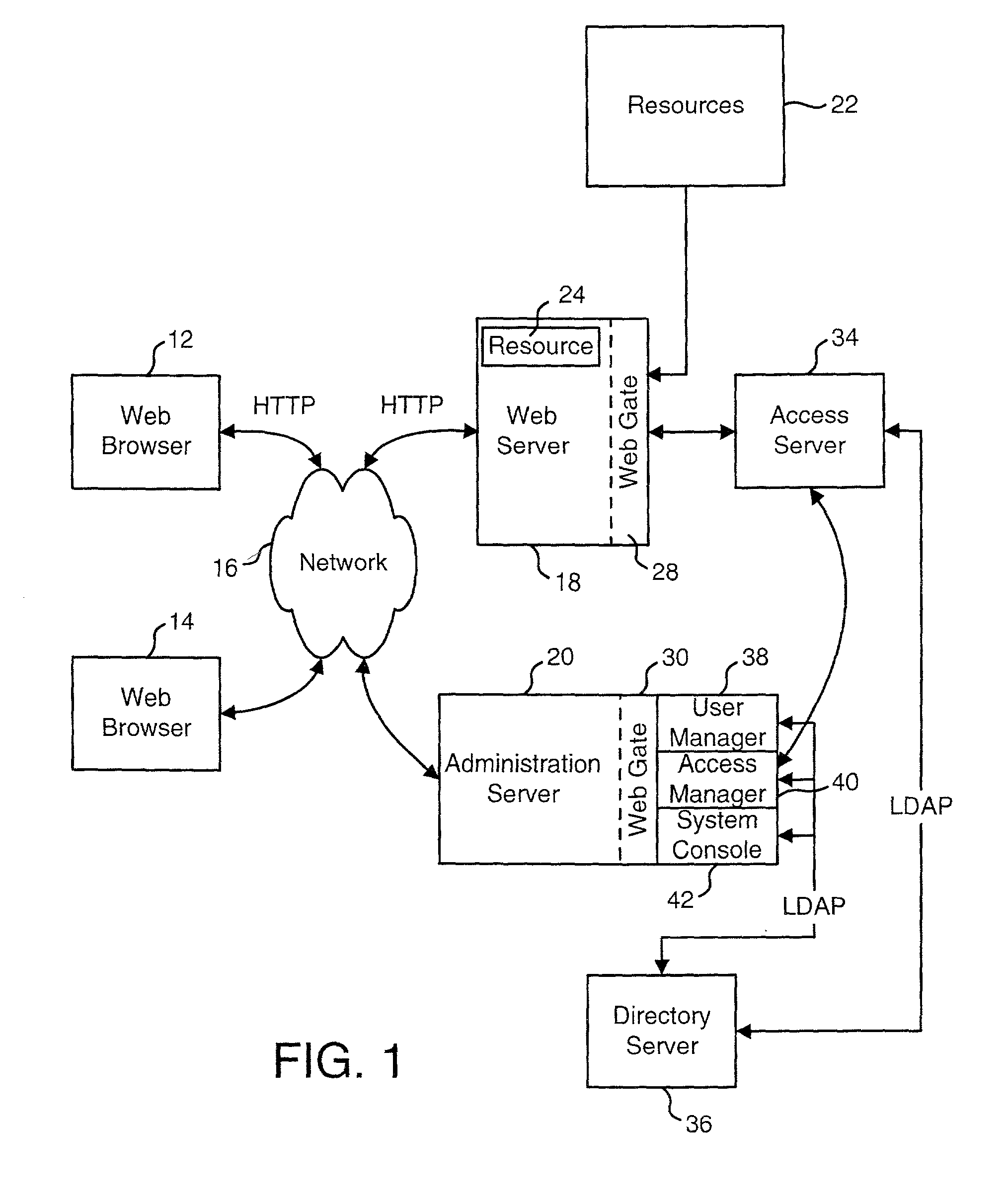
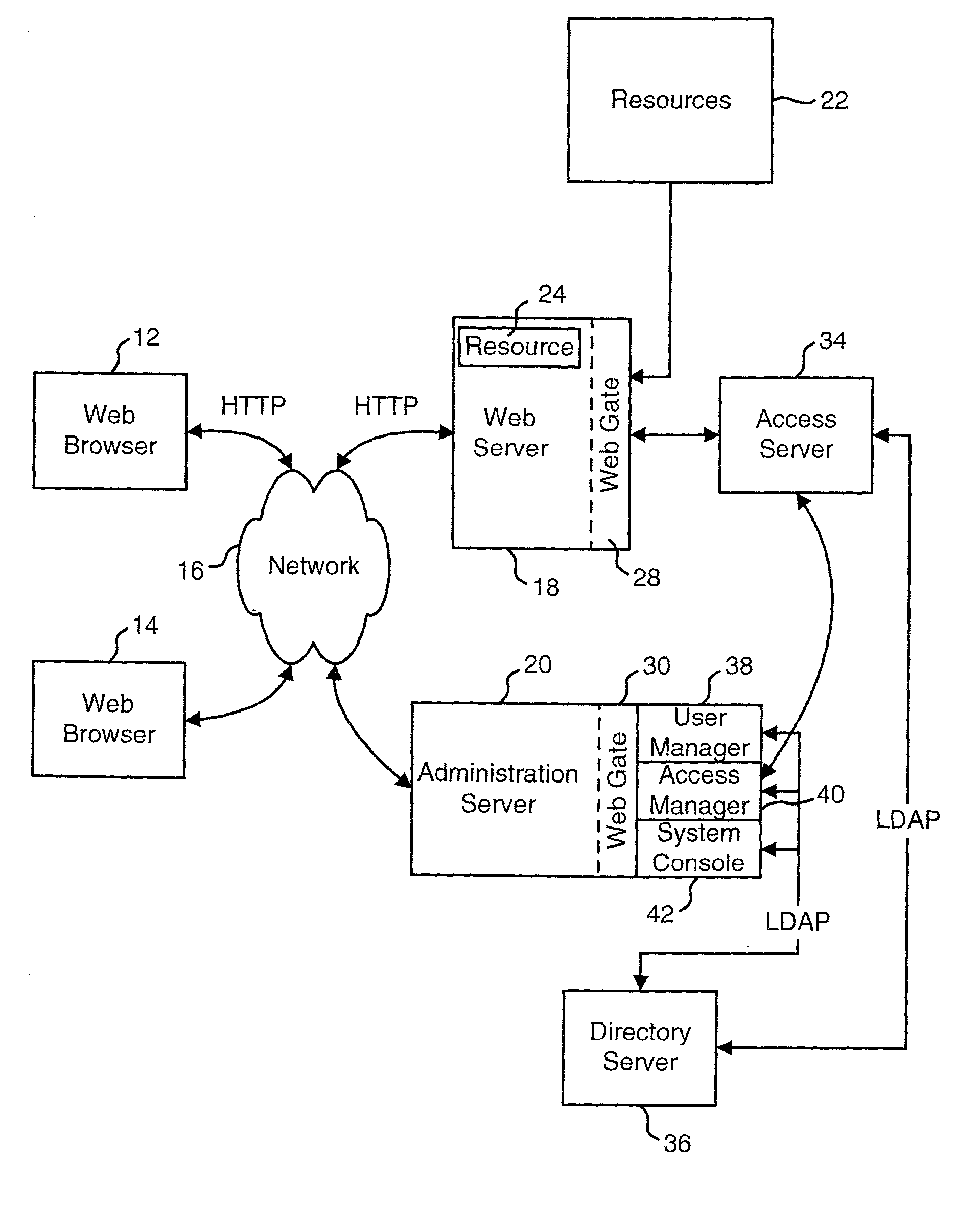
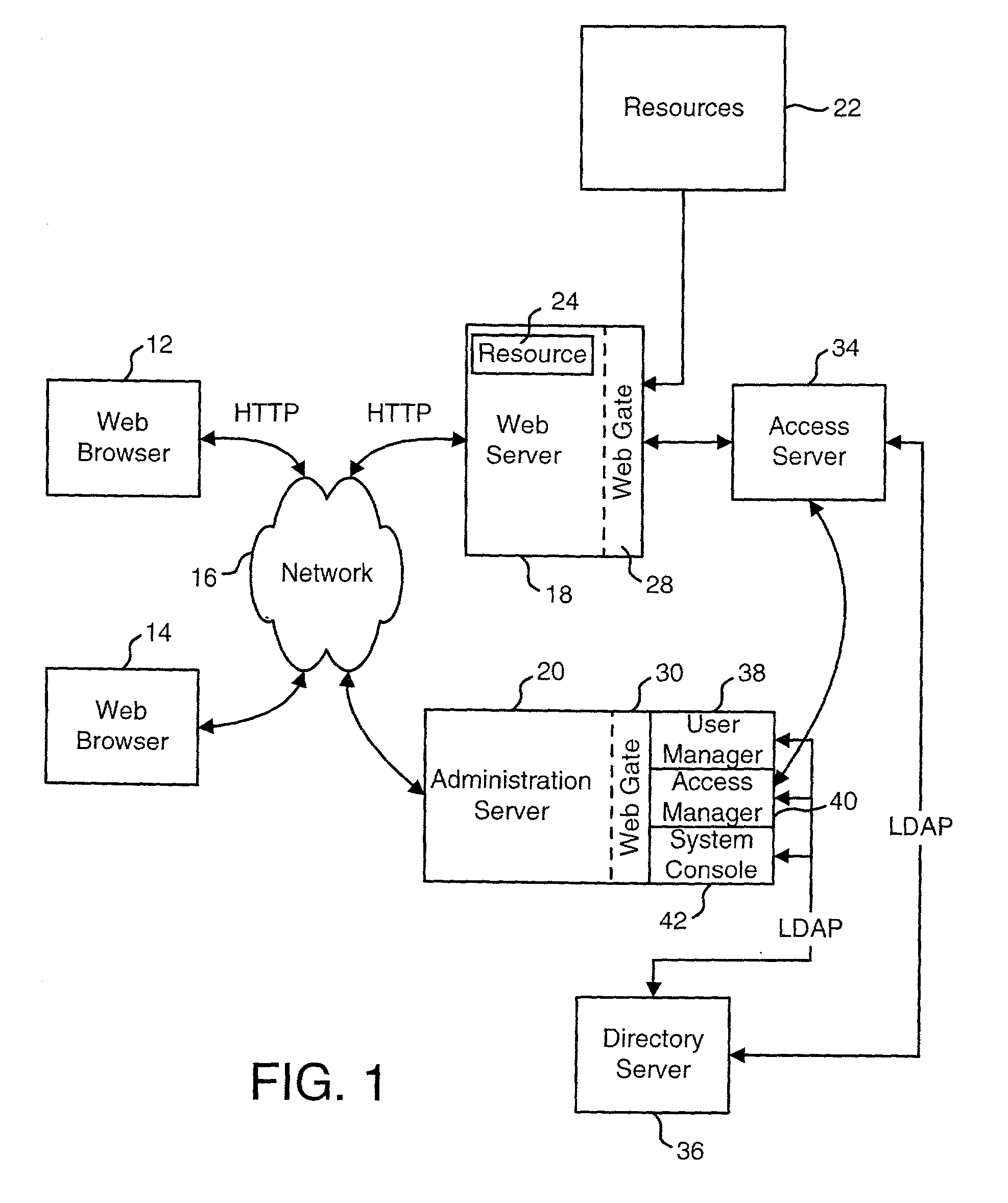
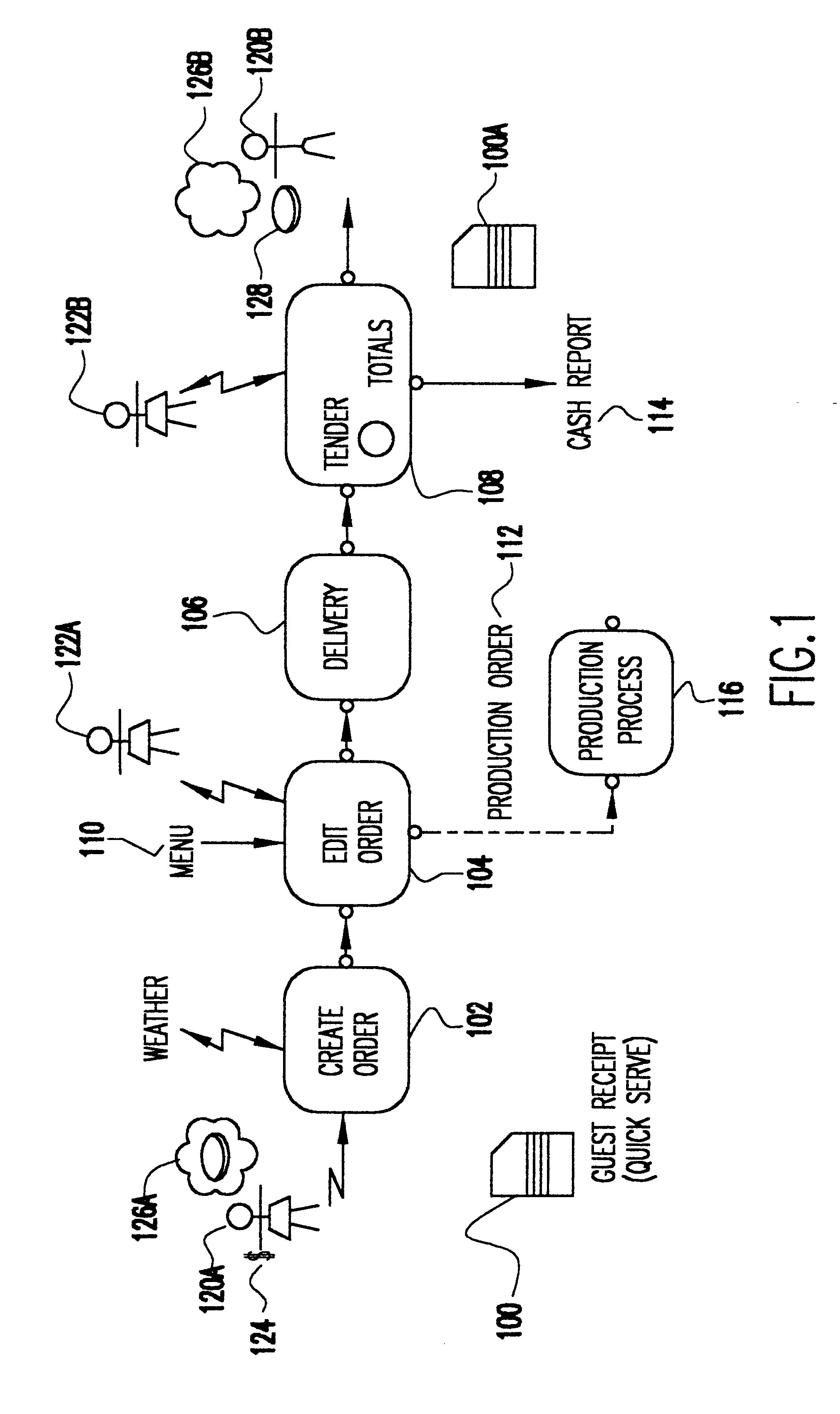
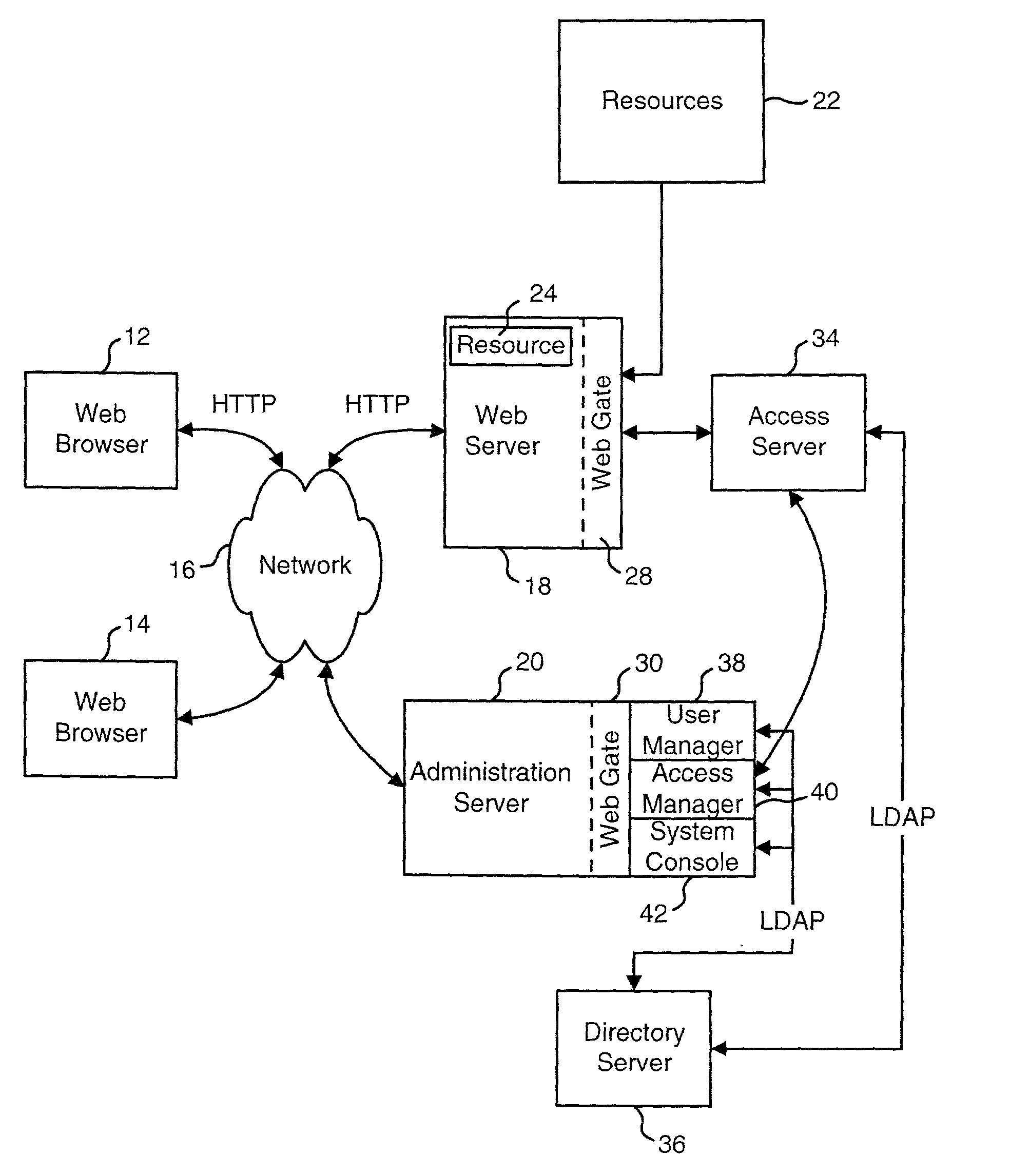
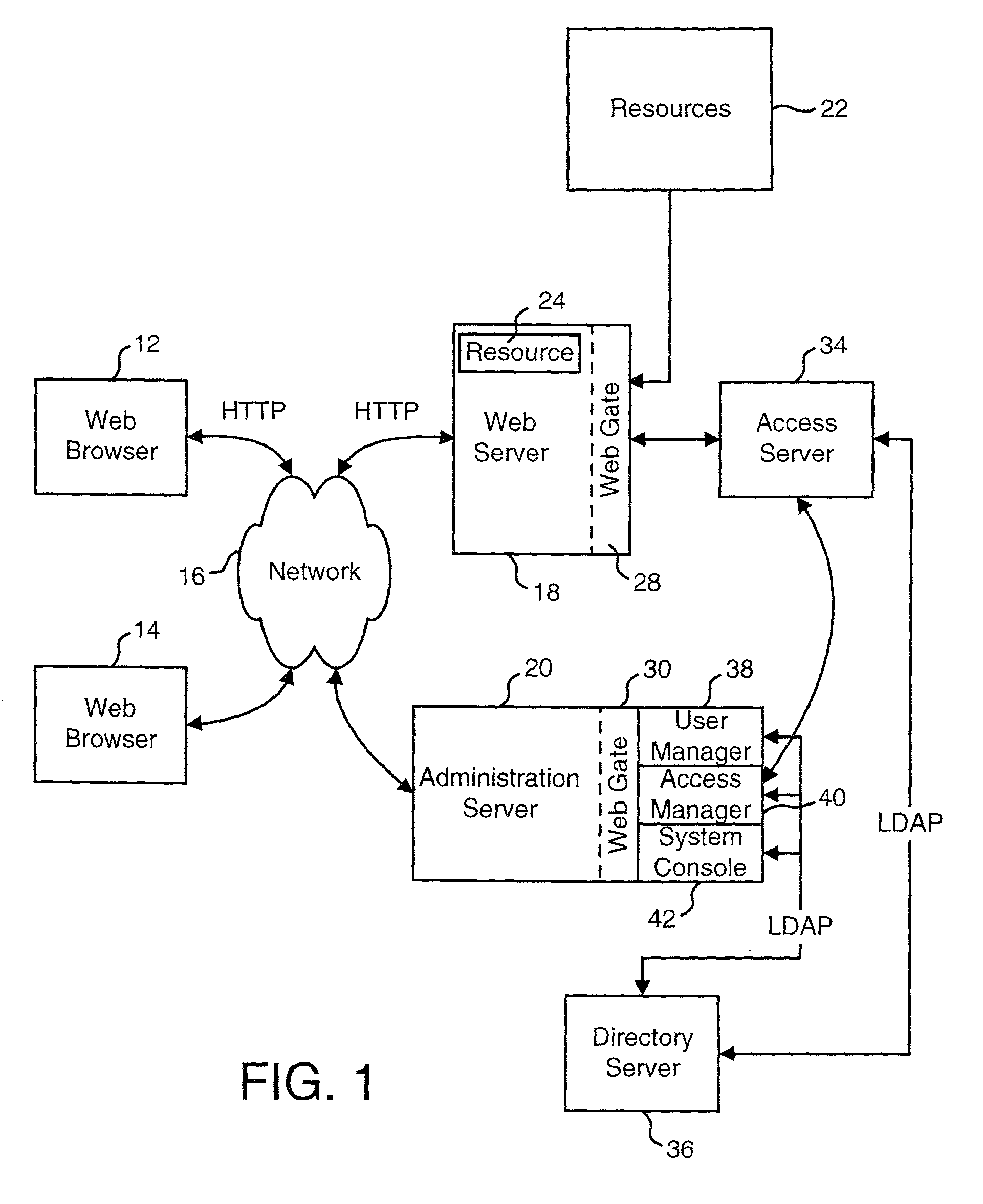
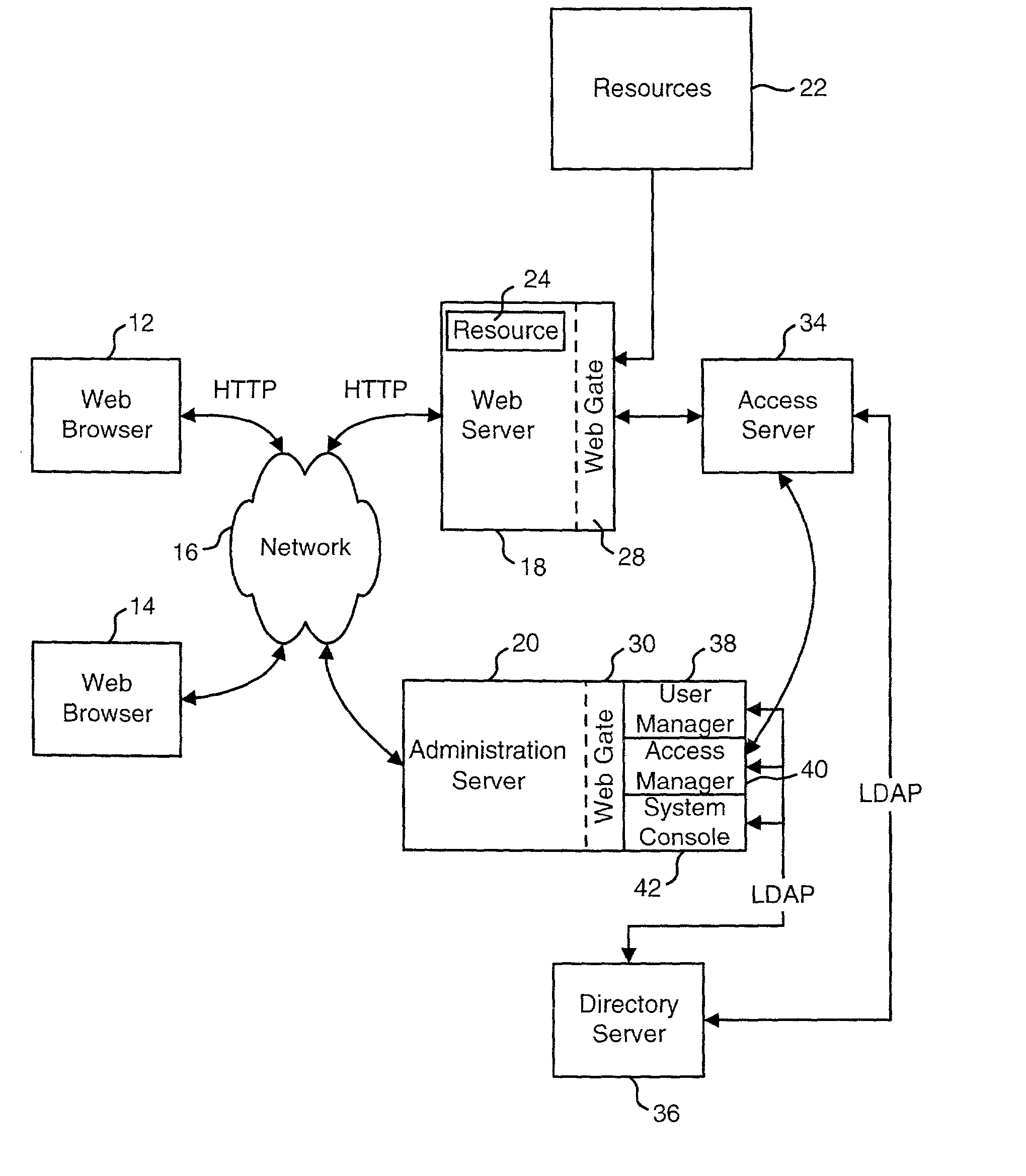
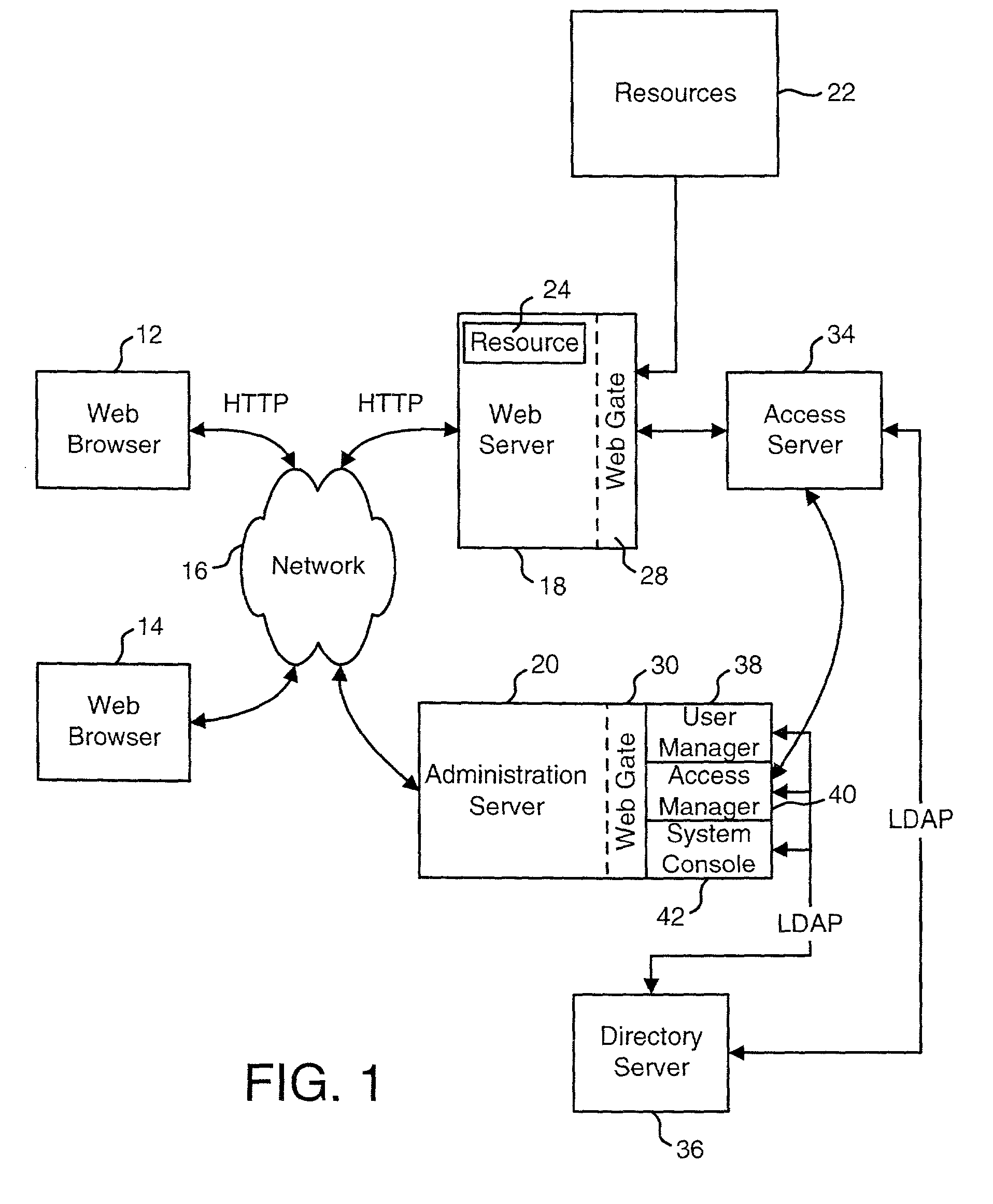
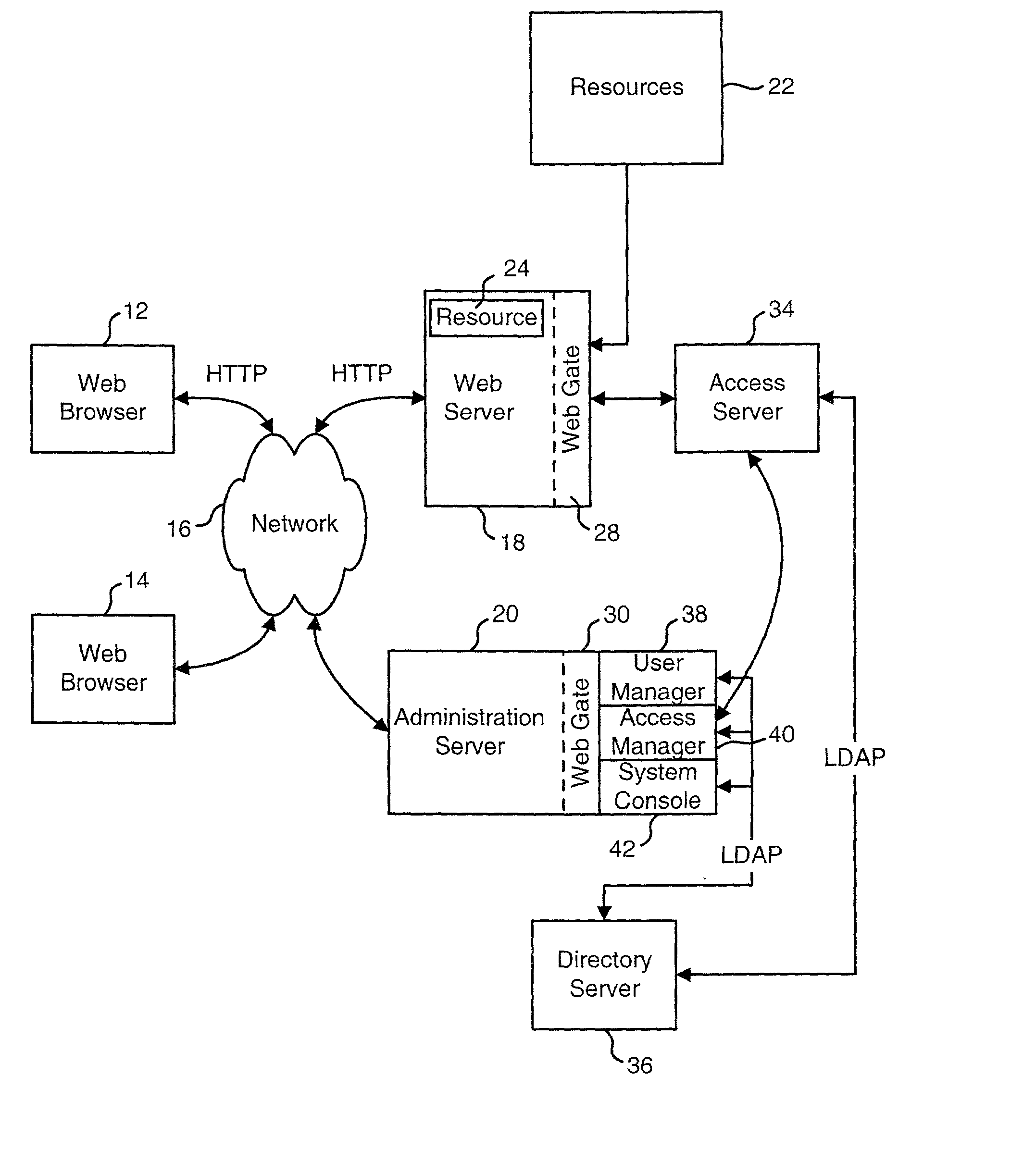
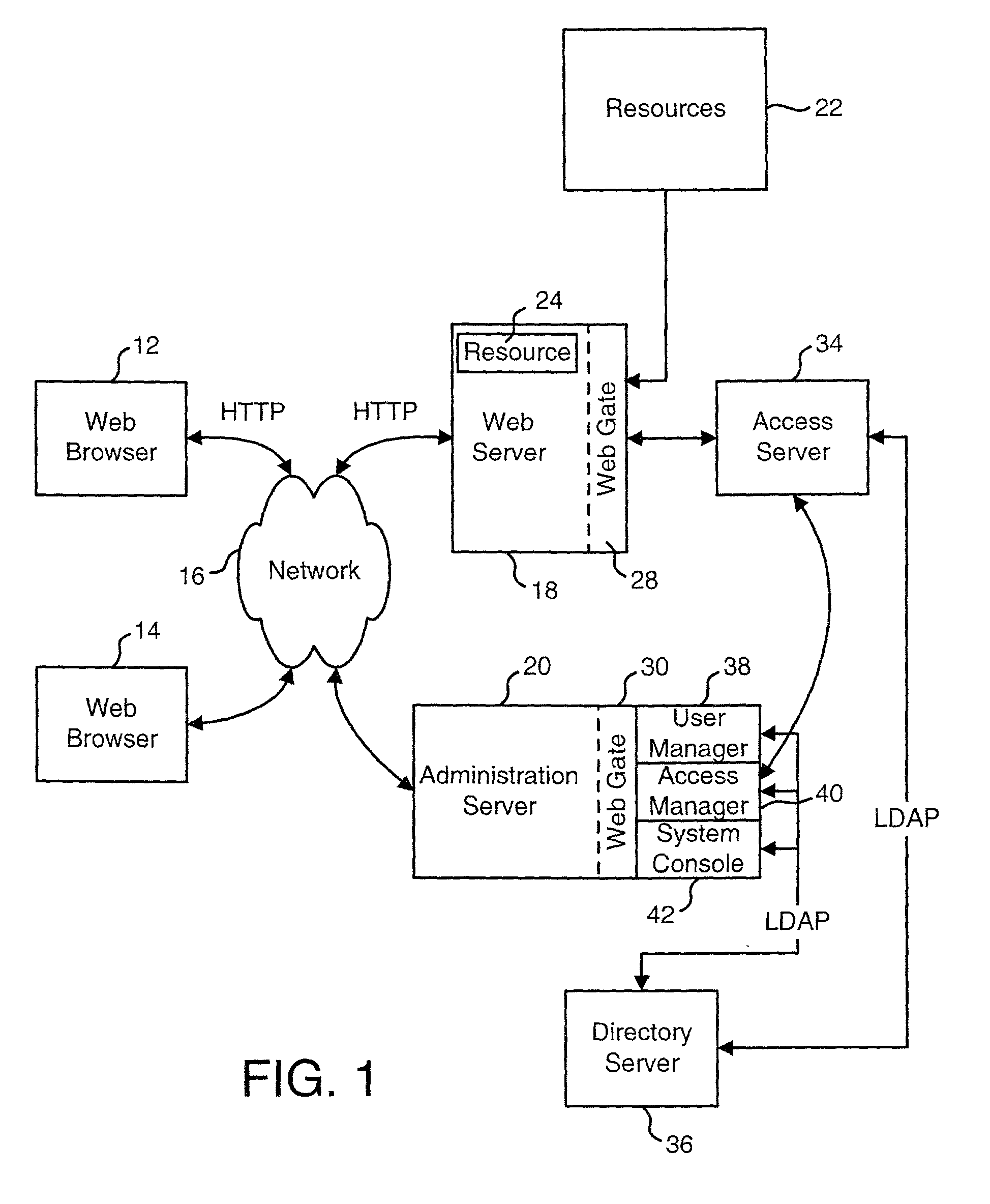
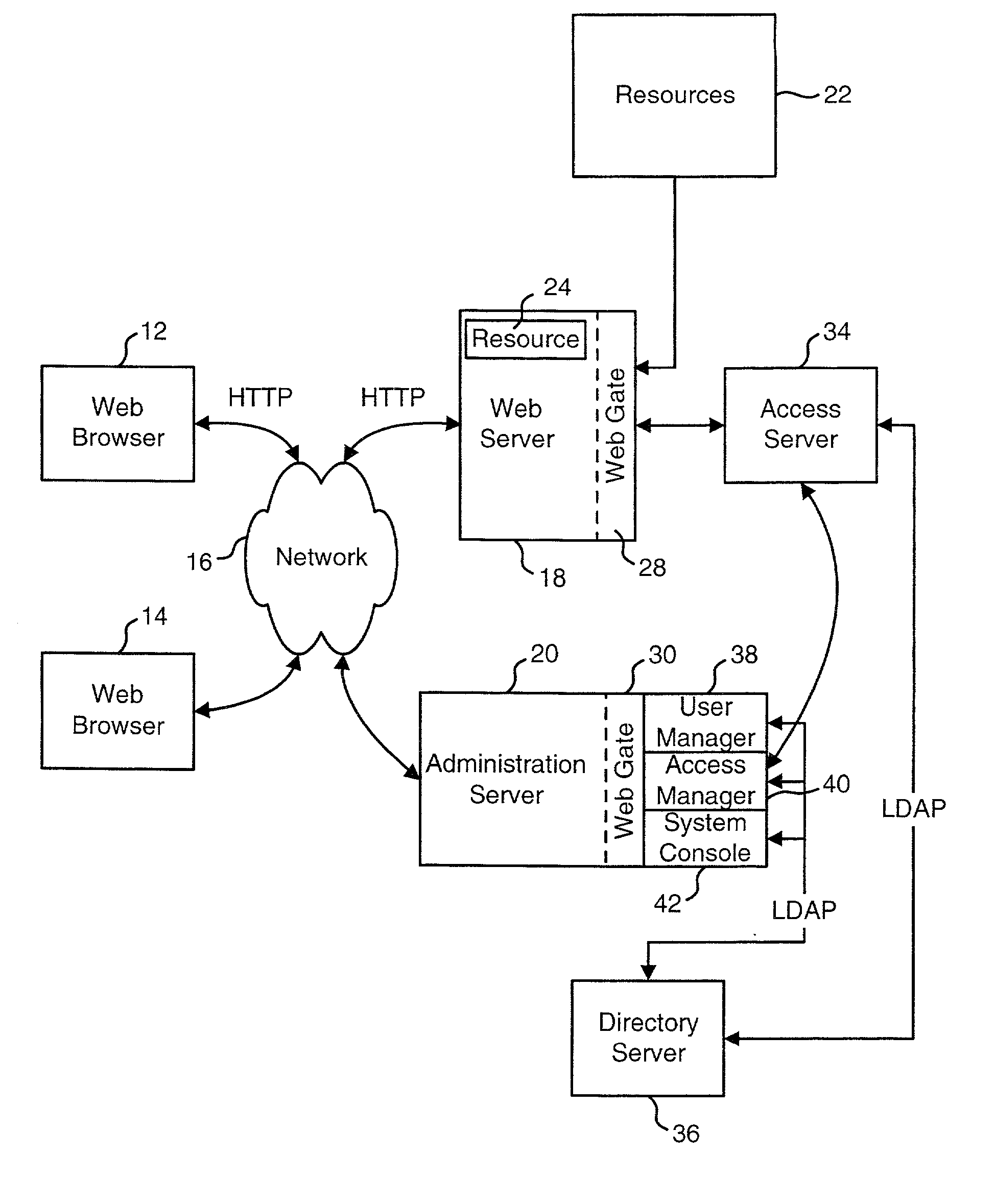
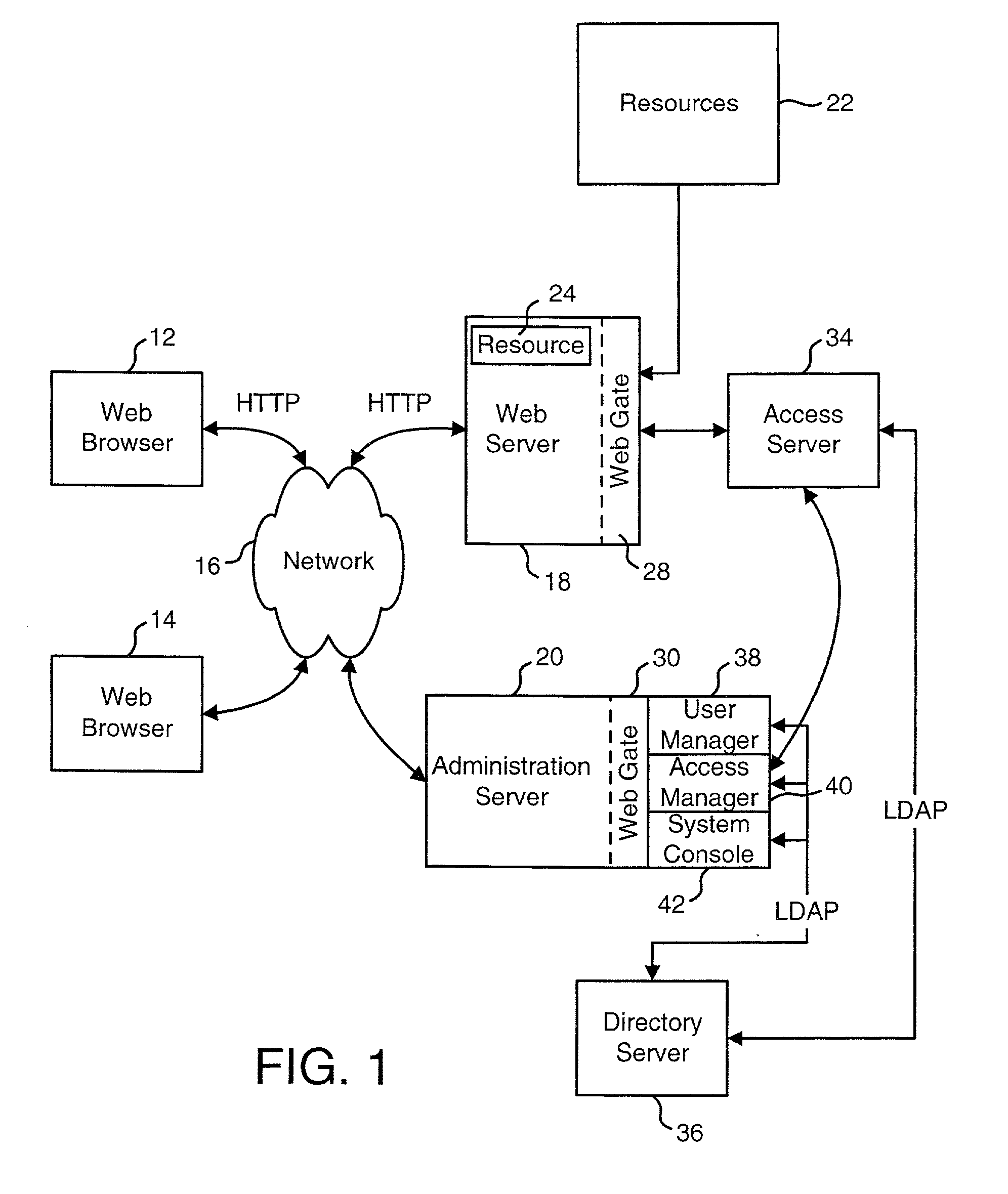
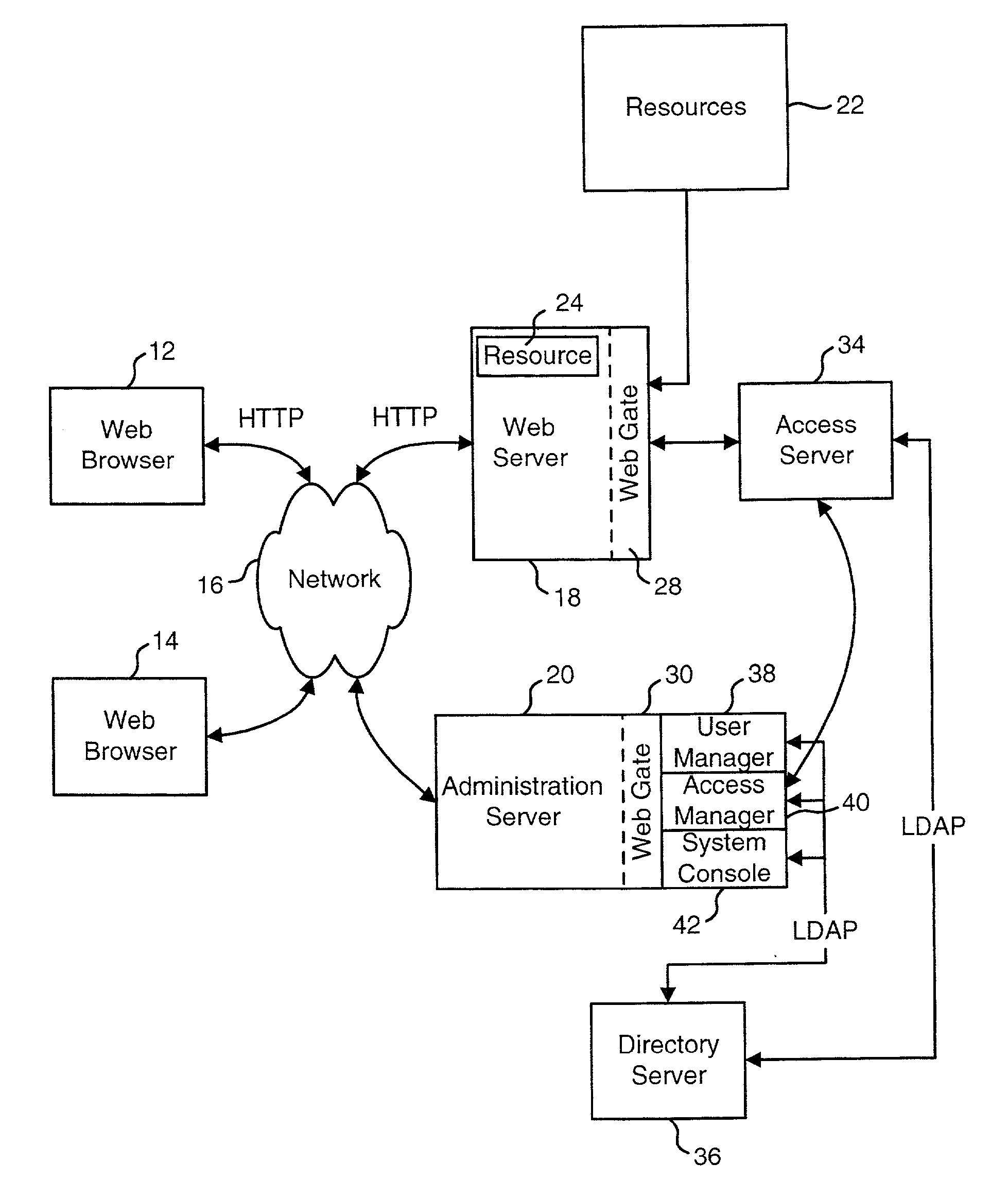
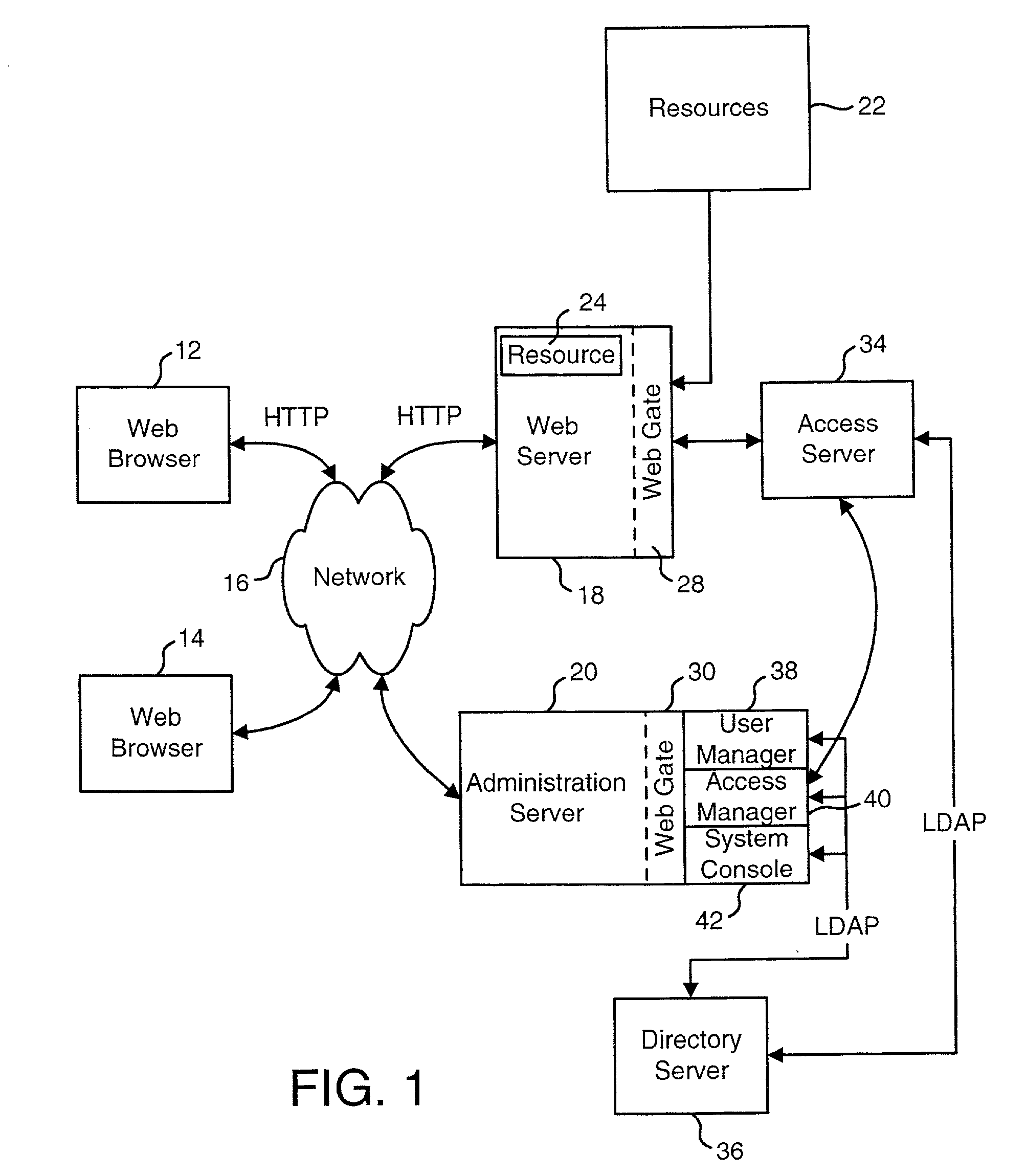
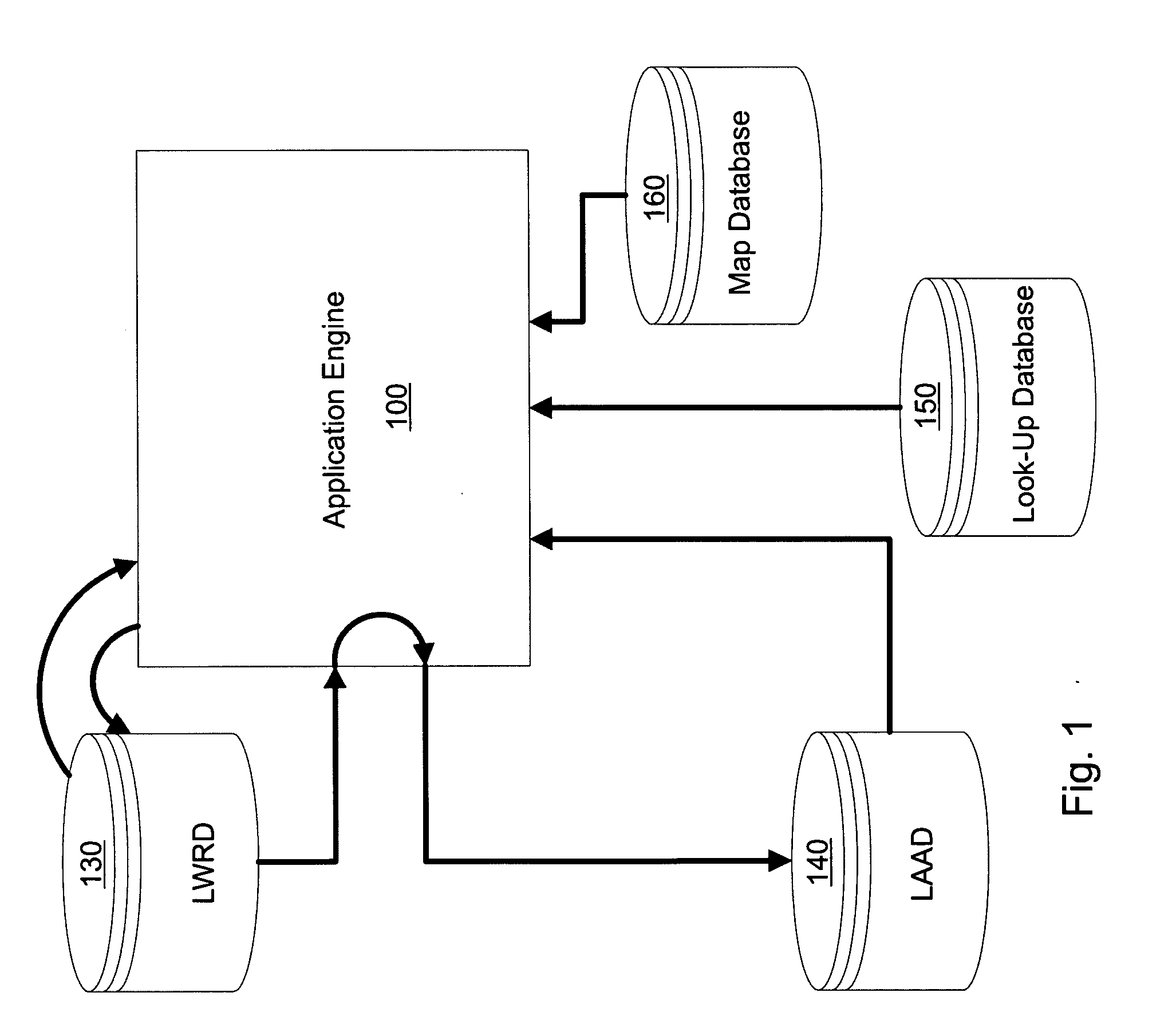
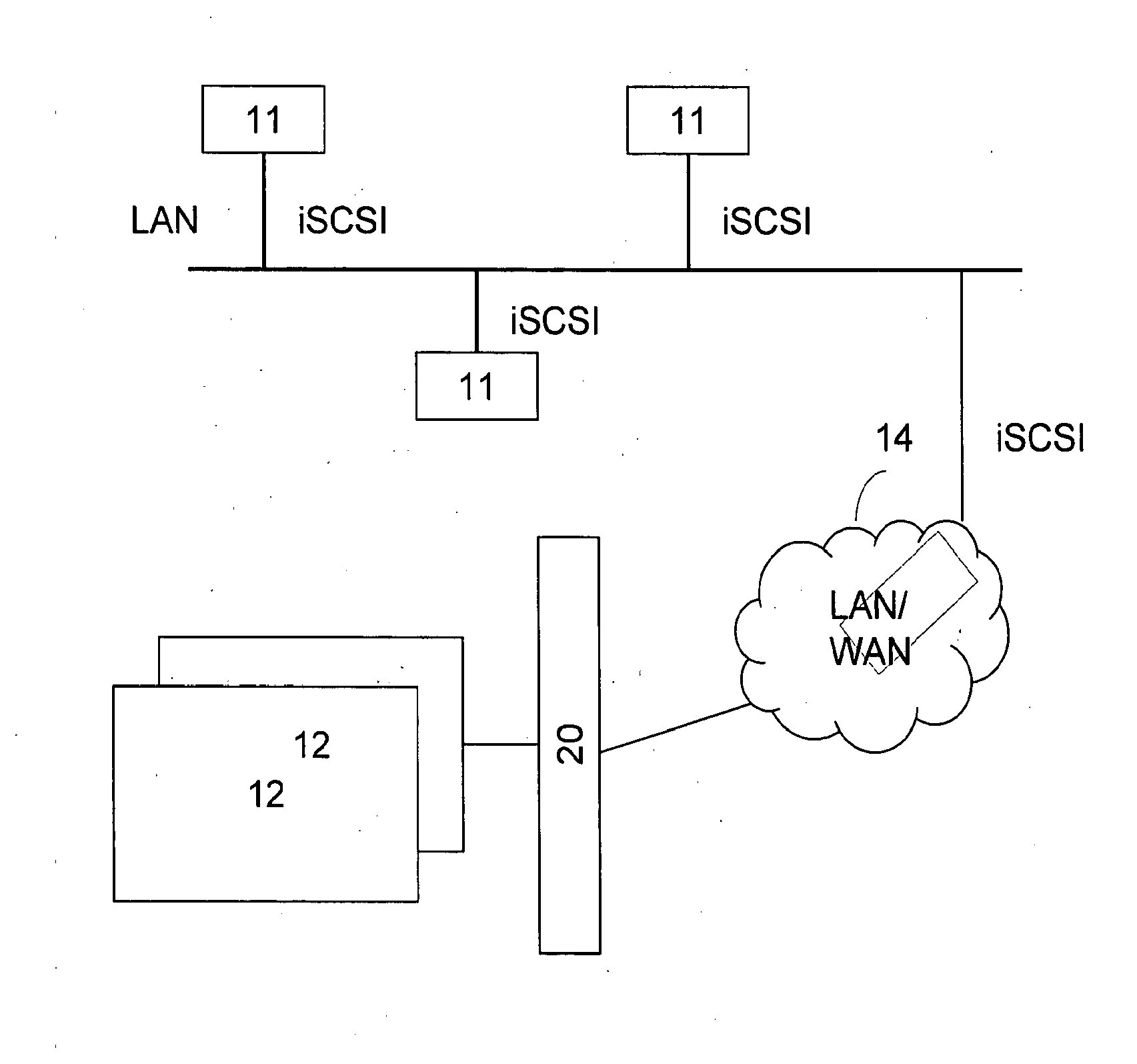
Access system interface
InactiveUS20030074580A1Easy mappingEasy to useDigital data processing detailsUser identity/authority verificationWeb serviceApplication software
An access system provides identity management and / or access management services for a network An application program interface for the access system enables an application without a web agent front end to read and use contents of an existing encrypted cookie to bypass authentication and proceed to authorization. A web agent is a component (usually software, but can be hardware or a combination of hardware and software) that plugs into (or otherwise integrates with) a web server (or equivalent) in order to participate in providing access services.
Owner:ORACLE INT CORP
User Authentication
InactiveUS20020112155A1Easy mappingDigital data processing detailsUser identity/authority verificationInternet privacyUser authentication
The present invention authenticates a user for multiple resources distributed across multiple domains through the performance of a single authentication. User access requests for a protected resource in a first domain are received and redirected to a second domain. User authentication is performed at the second domain. In one embodiment, the system transmits an authentication cookie for the second domain to the user after authentication at the second domain. In another embodiment, the system further redirects subsequent resource requests for resources in the first domain or a third domain to the second domain. The second domain confirms the user's authentication for applicable portions of the first, second, and third domains using the cookie.
Owner:ORACLE INT CORP
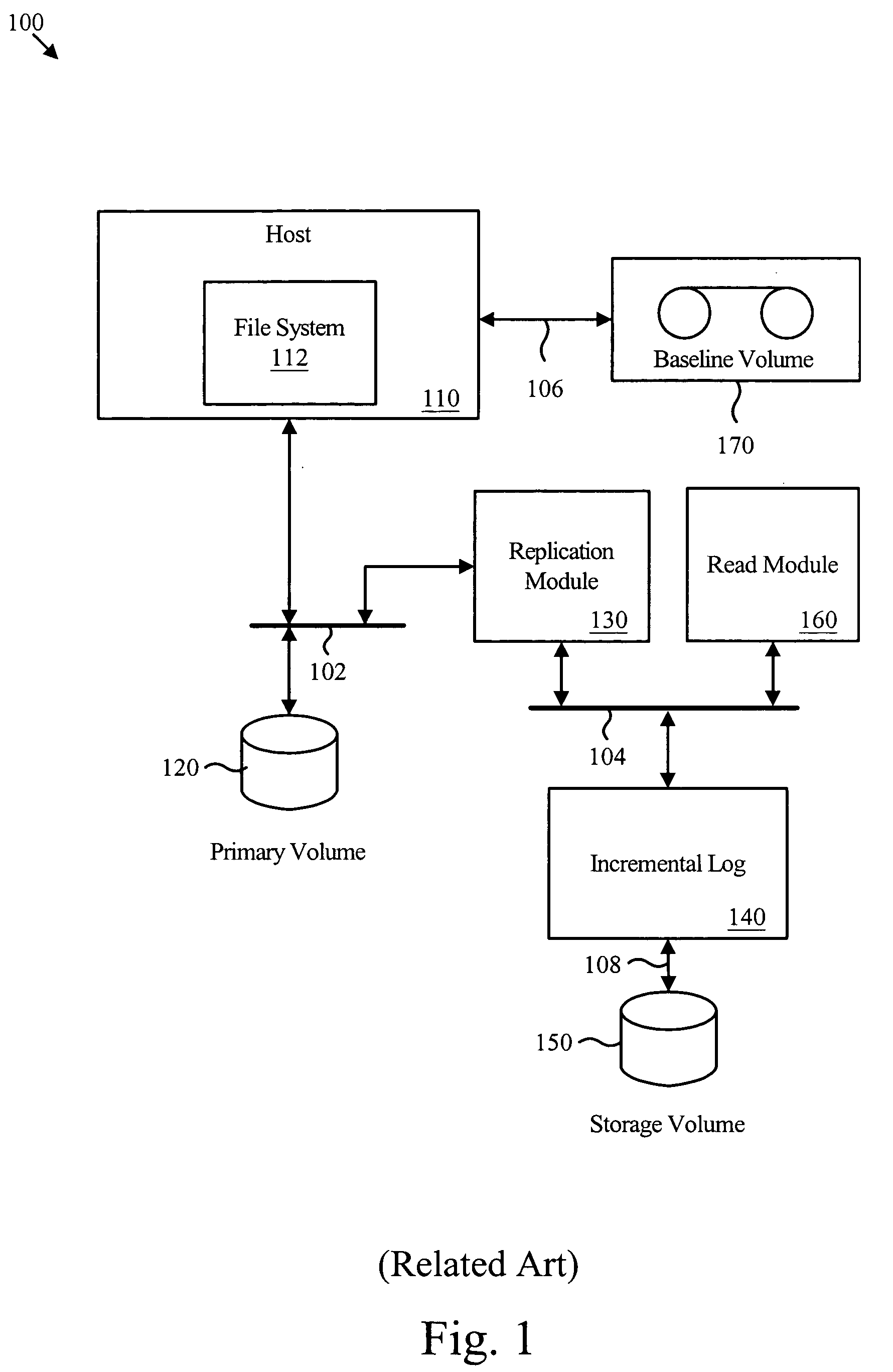
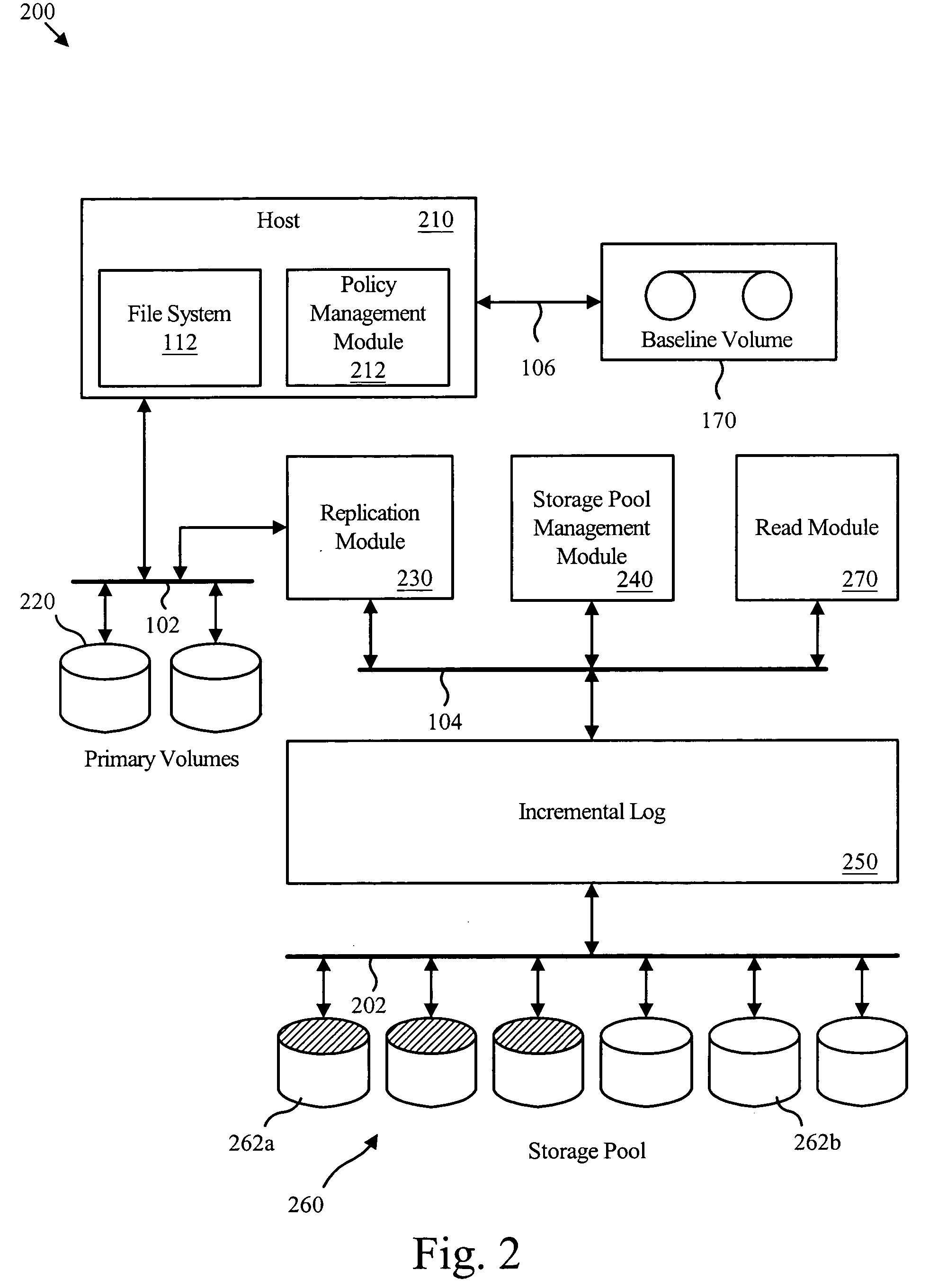
Virtual incremental storage apparatus method and system
InactiveUS20050108292A1The process is simple and effectiveSave storage spaceInput/output to record carriersError detection/correctionPhysical addressLookup table
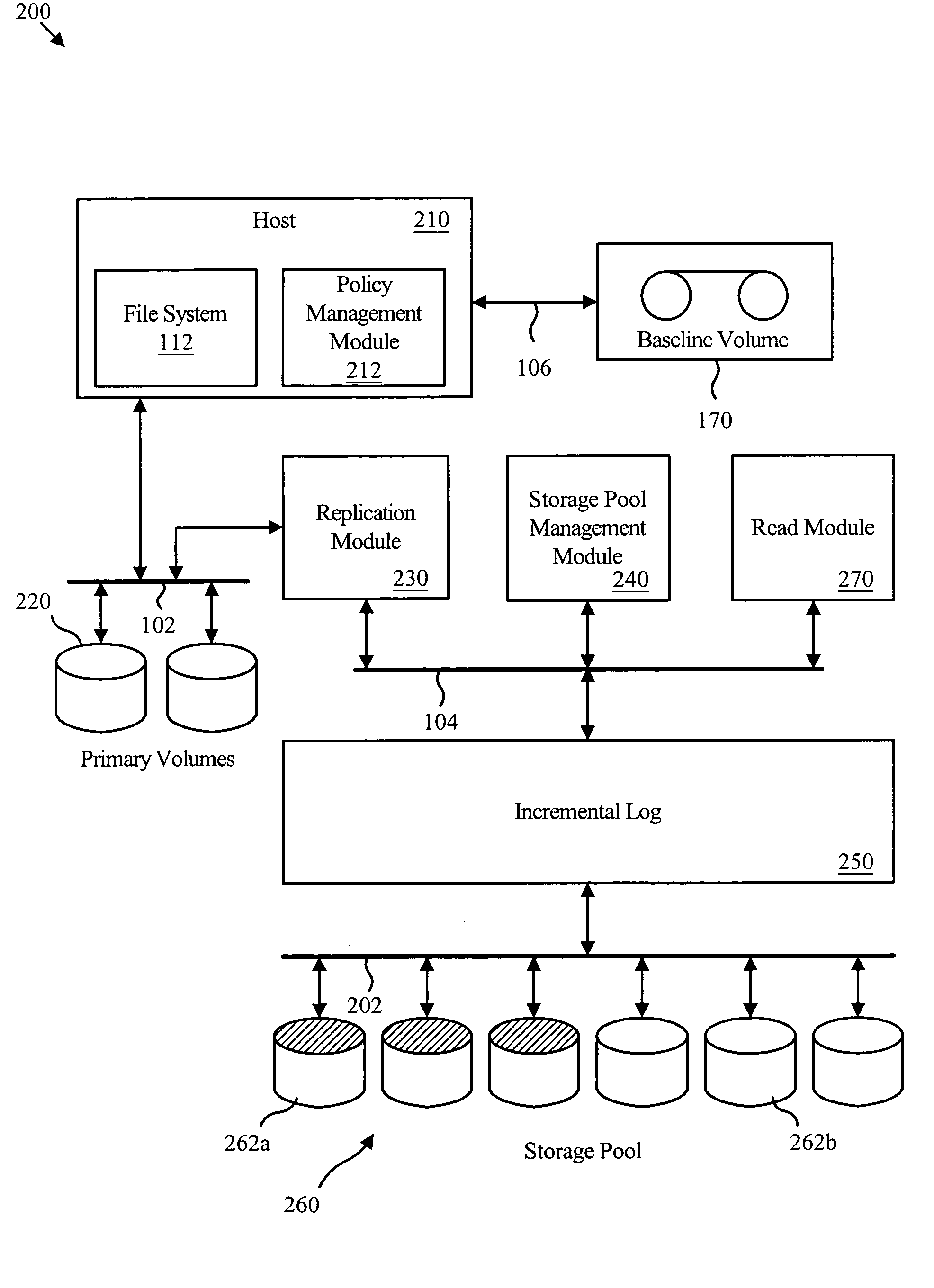
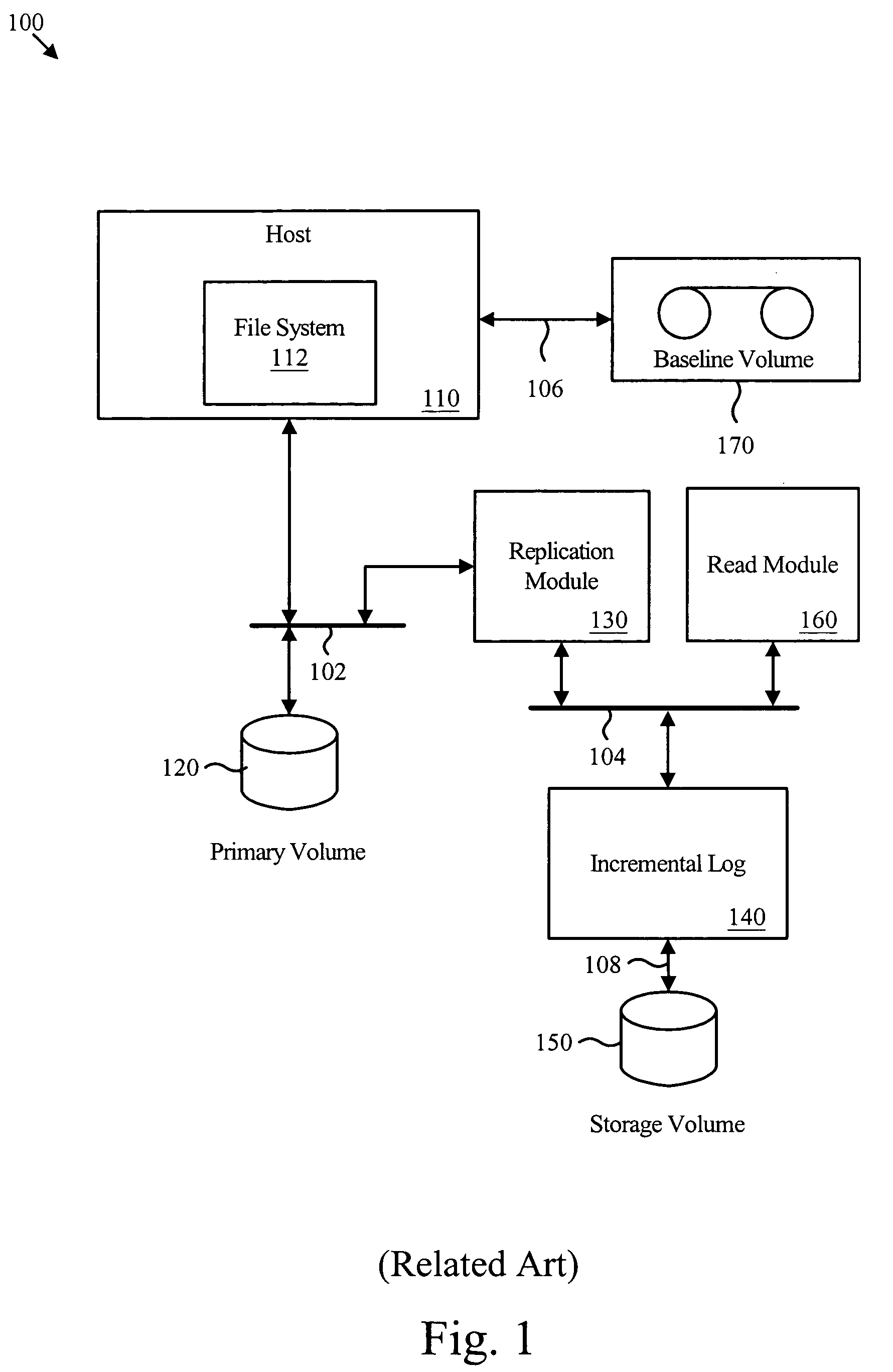
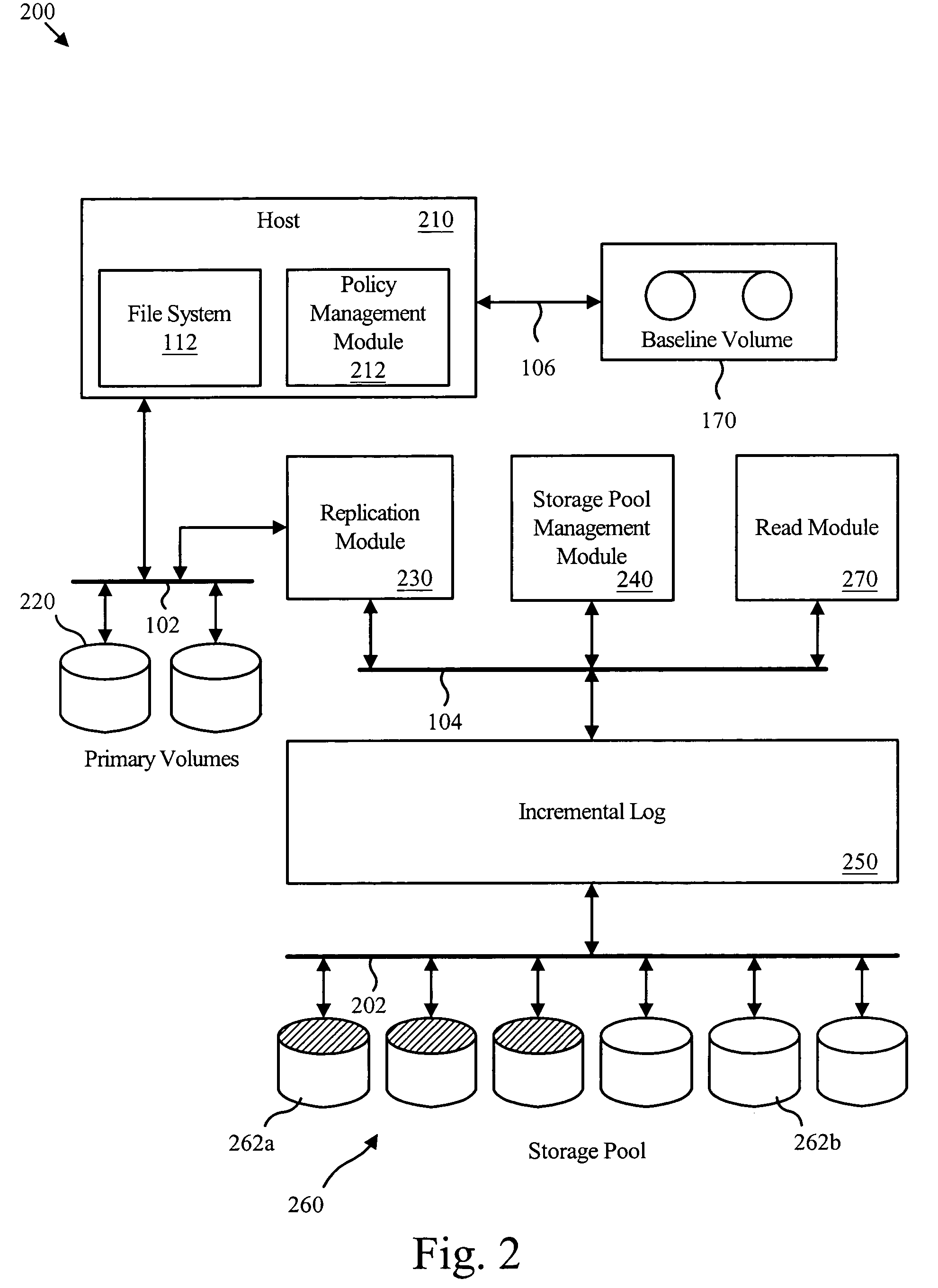
An apparatus for managing incremental storage includes a storage pool management module that allocates storage volumes to a virtual volume. Also included is an incremental log corresponding to the virtual volume, which maps virtual addresses to storage addresses. The apparatus may also include a replication module that sends replicated data to the virtual volume and a policy management module that determines allocation criteria for the storage pool management module. In one embodiment, the incremental log includes a lookup table that translates read and write requests to physical addresses on storage volumes within the virtual volume. The replicated data may include incremental snapshot data corresponding to one or more primary volumes. The various embodiments of the virtual incremental storage apparatus, method, and system facilitate dynamic adjustment of the storage capacity of the virtual volume to accommodate changing amounts of storage utilization.
Owner:IBM CORP
Intrusion threat detection
ActiveUS20020112185A1Easy mappingMemory loss protectionDigital computer detailsComputer securityRule engine
A system is disclosed that can be used to monitor for an attempted intrusion of an access system. The system detects an access system event in the access system and determines whether the access system event is of a type that is being monitored. If the access system event is of a type that is being monitored, the system reports information about the access system event. This information can be used by a rules engine or other process to determine if the access system event was part of an attempted intrusion of the access system.
Owner:ORACLE USA
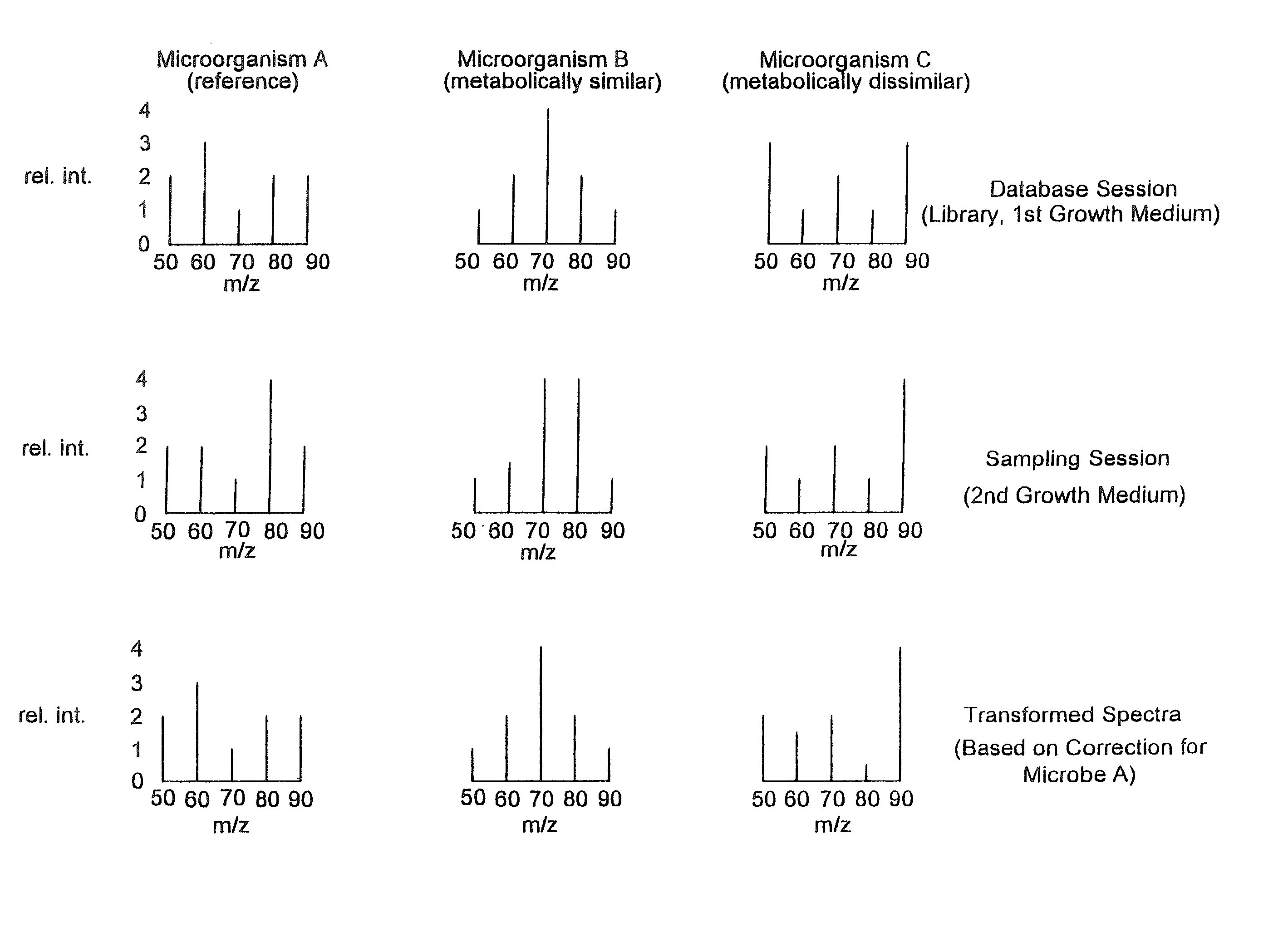
Microbial identification databases
InactiveUS20020138210A1Easy mappingComponent separationBiological testingMicroorganismMass spectral database
Methods of compensating for drift in fingerprint spectra of microorganisms caused by changes in their environment are disclosed. These methods of compensating for drift permit identification of microorganisms from their fingerprint spectra regardless of the environment from which the microorganisms are obtained. Furthermore, the disclosed methods may be used to construct coherent databases of fingerprint spectra that may be expanded even though the standard database conditions are no longer experimentally achievable. In particular embodiments, methods of compensating for drift in pyrolysis mass spectra, constructing coherent pyrolysis mass spectral databases, and identifying bacteria from their pyrolysis mass spectra are disclosed.
Owner:HEALTH & HUMAN SERVICES THE GOVERNMENT OF THE US SEC THE DEPT
Query string processing
ActiveUS20020099671A1Easy mappingData processing applicationsDigital data processing detailsData matchingQuery string
A system is disclosed that is used to provide access management for resources on a network. The system makes use of query data from a URL (or another identification or request) to identify the appropriate access rule. Examples of an access rule include an authentication rule, an authorization rule, or an audit rule. The system can be configured to require the query data to match order dependent variables or order independent variables. In one option, the system can include two levels of rules and the query data can be used to identify first level rules, second level rules or both.
Owner:ORACLE INT CORP
System and method for automatically editing captured images for inclusion into 3D video game play
InactiveUS6894686B2Add funImprove realismVideo gamesSpecial data processing applicationsGame playerAnimation
A video / computer game machine maps external images onto animated game players in a game program. An image of a person's face may be mapped onto the head of an animated game player. The person may then play the game using the animated game player having a face that appears to be that of the person. Similarly, images of other persons can be mapped on other animated game players that appear in the video game program. Improved realism of video games is obtained by enabling individuals to create animated game players that have features, e.g., a facial image, of the individual or that were selected and imported by the individual.
Owner:NINTENDO CO LTD +1
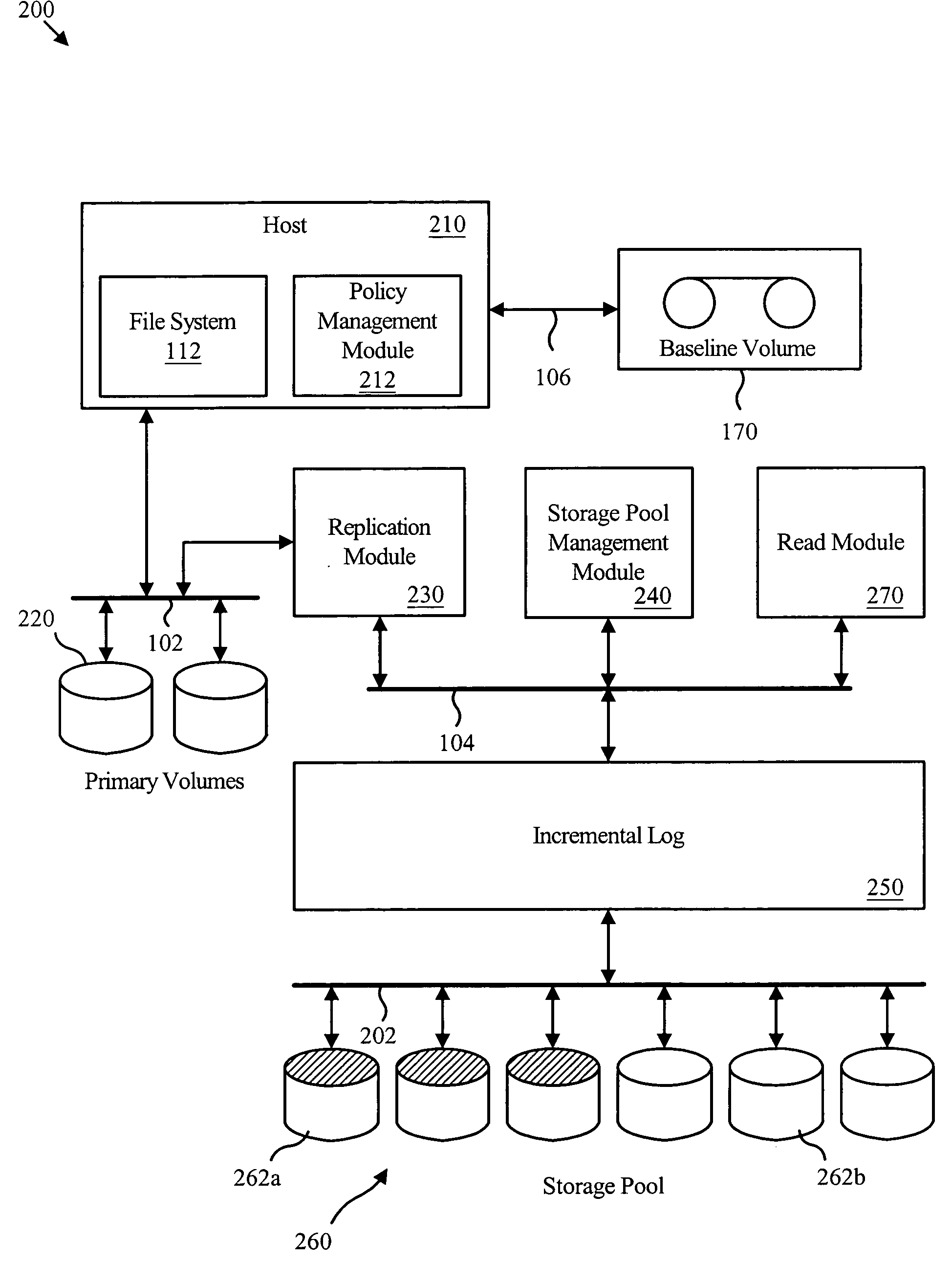
Virtual incremental storage method
InactiveUS7412583B2Reduce complexityImprove performanceInput/output to record carriersMemory loss protectionStorage poolOperating system
A method for managing incremental storage includes a storage pool management module that allocates storage volumes to a virtual volume. Also included is an incremental log corresponding to the virtual volume, which maps virtual addresses to storage addresses. The method may also include a replication module that sends replicated data to the virtual volume and a policy management module that determines allocation criteria for the storage pool management module. In one embodiment, the incremental log includes a look up table that translates read and write requests to physical addresses on storage volumes within the virtual volume. The replicated data may include incremental snapshot data corresponding to one or more primary volumes. The various embodiments of the virtual incremental storage method facilitate dynamic adjustment of the storage capacity of the virtual volume to accommodate changing amounts of storage utilization.
Owner:INT BUSINESS MASCH CORP
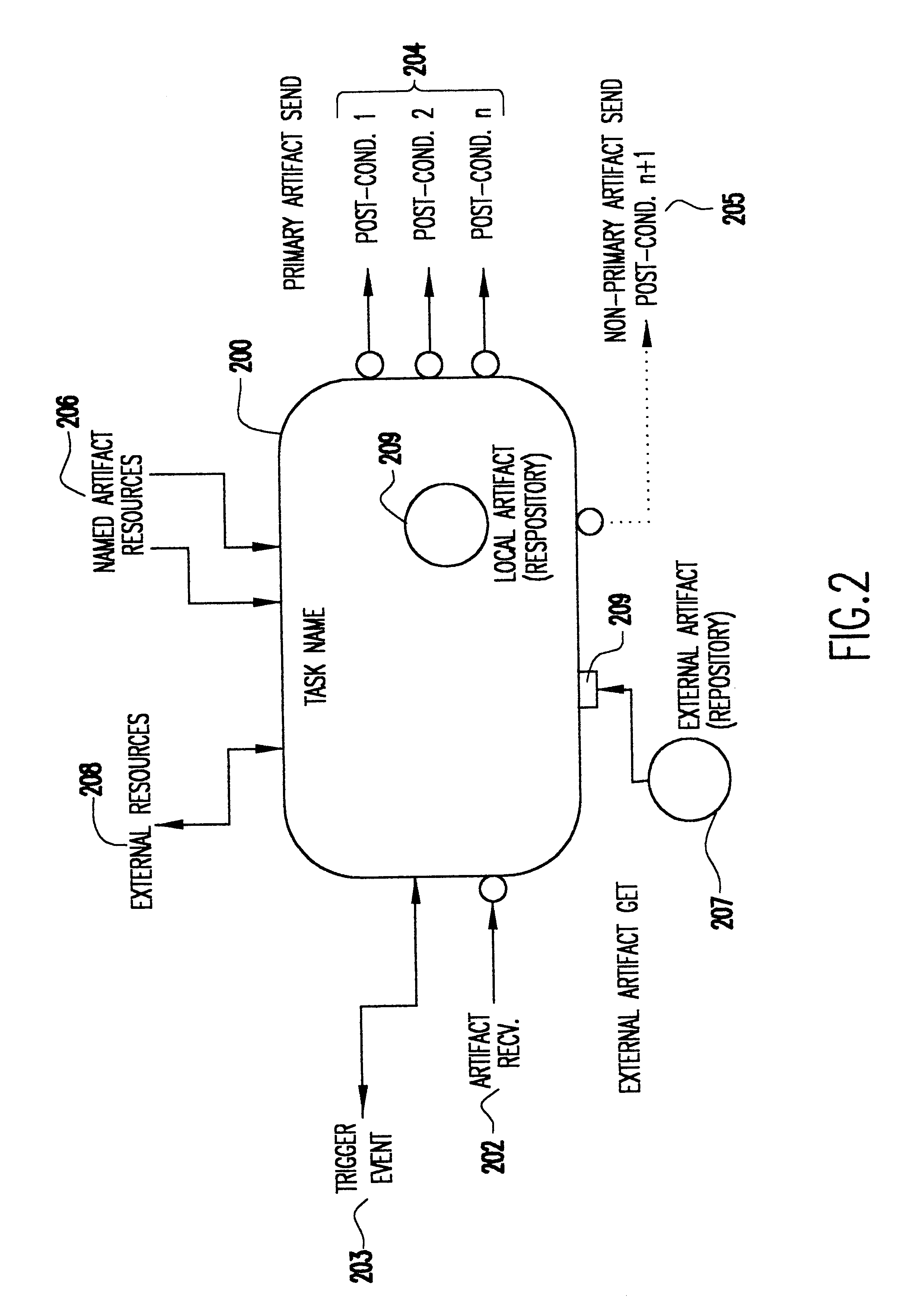
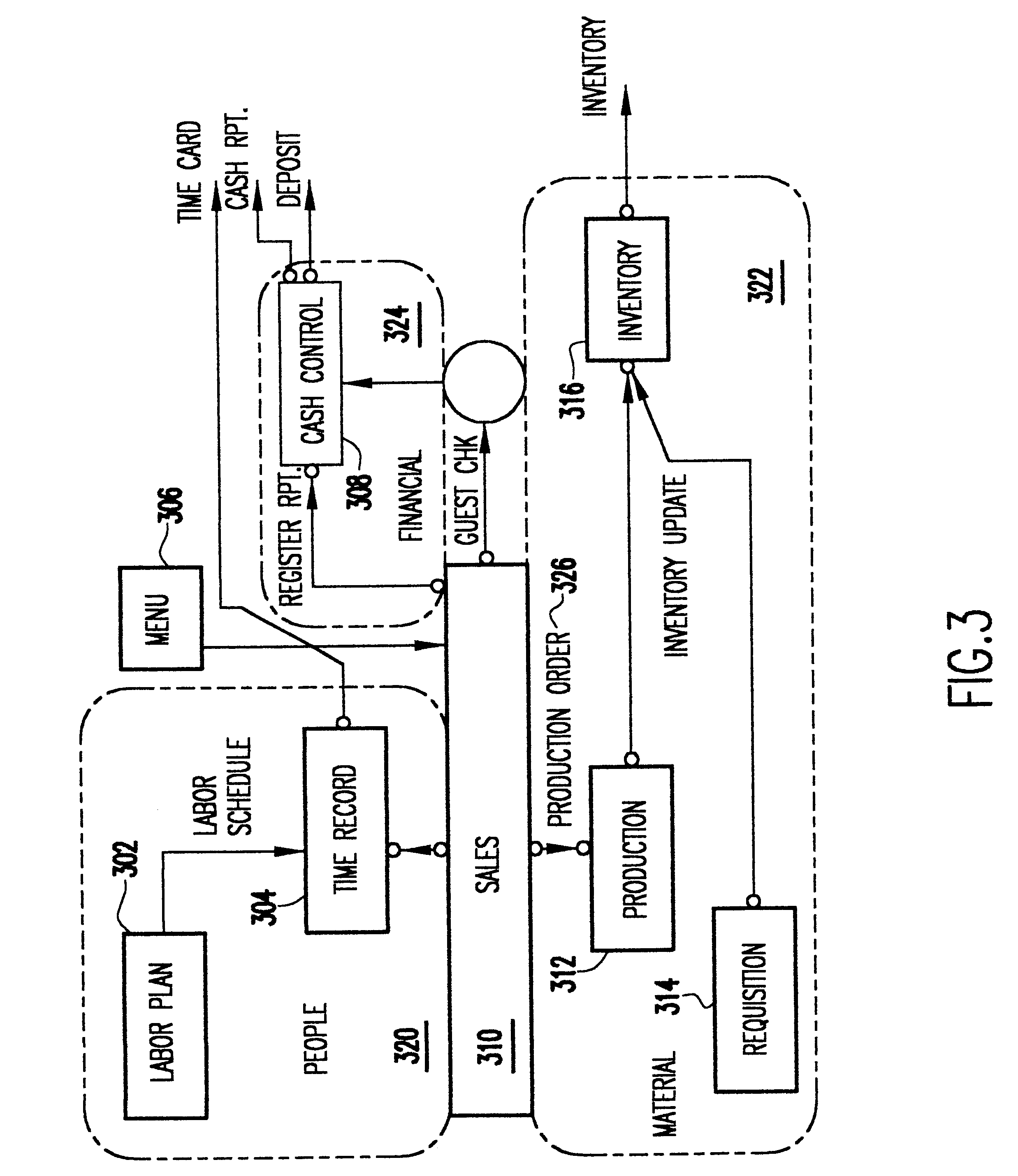
Method and system for specifying and implementing automation of business processes
InactiveUS6662355B1Easily and efficiently developEasy mappingExecution for user interfacesMemory systemsModularitySales force management system
A method s for specifying and implementing automation of business processes where the specification is independently manipulable by both the business process owner and technical implementers, and resulting technical elements can be tested for compliance with every detail in the specification. The method creates a single shared model suitable for understanding and execution in both the business and technical domains by focusing on the specification problem in the area of business automation. The solution to the specification problem lies in Information, Function, Flow (IFF or IF<2>) factorization of business processes. Models of the business are constructed by way of the IF<2 >modeling methodology. This is a complete model which includes, by construction, external specifications of each task included in the business model. The modularization problem is solved by preserving the partitioning of the system created in the business model. The automation system implements concrete modules that uniquely and directly correspond to particular elements whose external specification is determined by the business model.
Owner:GOOGLE LLC
Logging access system events
ActiveUS20020116642A1Easy mappingDigital data protectionSpecial data processing applicationsLibrary scienceAccess management
A system is disclosed that logs access system events. When an access system event occurs, a log entry is created for the access system event. Information from an identity profile is stored in the log entry. The identity profile pertains to a first user. The first user is the entity who caused or was involved with the access system event. In one embodiment, the access system includes identity management and access management functionality.
Owner:ORACLE INT CORP
Providing data to applications from an access system
ActiveUS20020091798A1Easy mappingDigital data processing detailsDigital data protectionStructure of Management InformationDirectory structure
An access system is disclosed that can provide data to a downstream application. In one embodiment, the data is provided as header variables associated with an HTTP request. Other embodiments can use other protocols and other means for transmitting the data. The data provided to the downstream applications include information about the user accessing the application. In one embodiment, the data provided to the downstream application includes information from an identity profile stored in an LDAP directory structure.
Owner:ORACLE INT CORP
Wavelocker for Improving Laser Wavelength Accuracy in WDM Networks
InactiveUS20110135301A1Easy mappingMaintaining full visibilityMultiplex system selection arrangementsWavelength-division multiplex systemsLasing wavelengthOptoelectronics
The present invention includes novel techniques, apparatus, and systems for optical WDM communications. Various wavelocker apparatus and methods are disclosed that measure the frequency offsets between signal lasers and reference lasers. The measured offsets are used to adjust the signal laser frequencies to meet their target frequencies. The absolute accuracy of the reference laser frequency is improved by measuring the absorption of the reference laser by a gas cell with known fixed absorption lines versus the reference laser frequency. Apparatus and methods are disclosed to cover scenarios in which the reference laser polarization is aligned with the signal lasers, as well as those in which the reference laser polarization is not aligned with the signal lasers. The wavelocker apparatus may or may not be located at the same network site as the signal lasers.
Owner:VELLO SYST +1
Access tester
ActiveUS20020165960A1Easy mappingDigital data processing detailsAnalogue secracy/subscription systemsIp addressGraphical user interface
The Access Tester allows an administrator, or any other authorized user, to determine who or what entities have access to a resource, whether a particular individual or set of individuals have access to a resource under certain conditions and whether the authorization rules associated with a resource operate as intended. In one embodiment, an administrator uses a graphical user interface to enter access information. Exemplar access information includes one or more URLs identifying the resource(s), one or more request methods, one or more IP addresses, date and time restrictions, and an identification of one or more users. The Access Tester determines whether the identified users are authorized to access the resource(s) associated with the URL(s) using the request methods, during the date and time provided.
Owner:ORACLE INT CORP
Context Driven Topologies
InactiveUS20090063557A1Easy mappingExact matchDigital data processing details2D-image generationTopology informationNetwork structure
Owner:ACCURACY & AESTHETICS
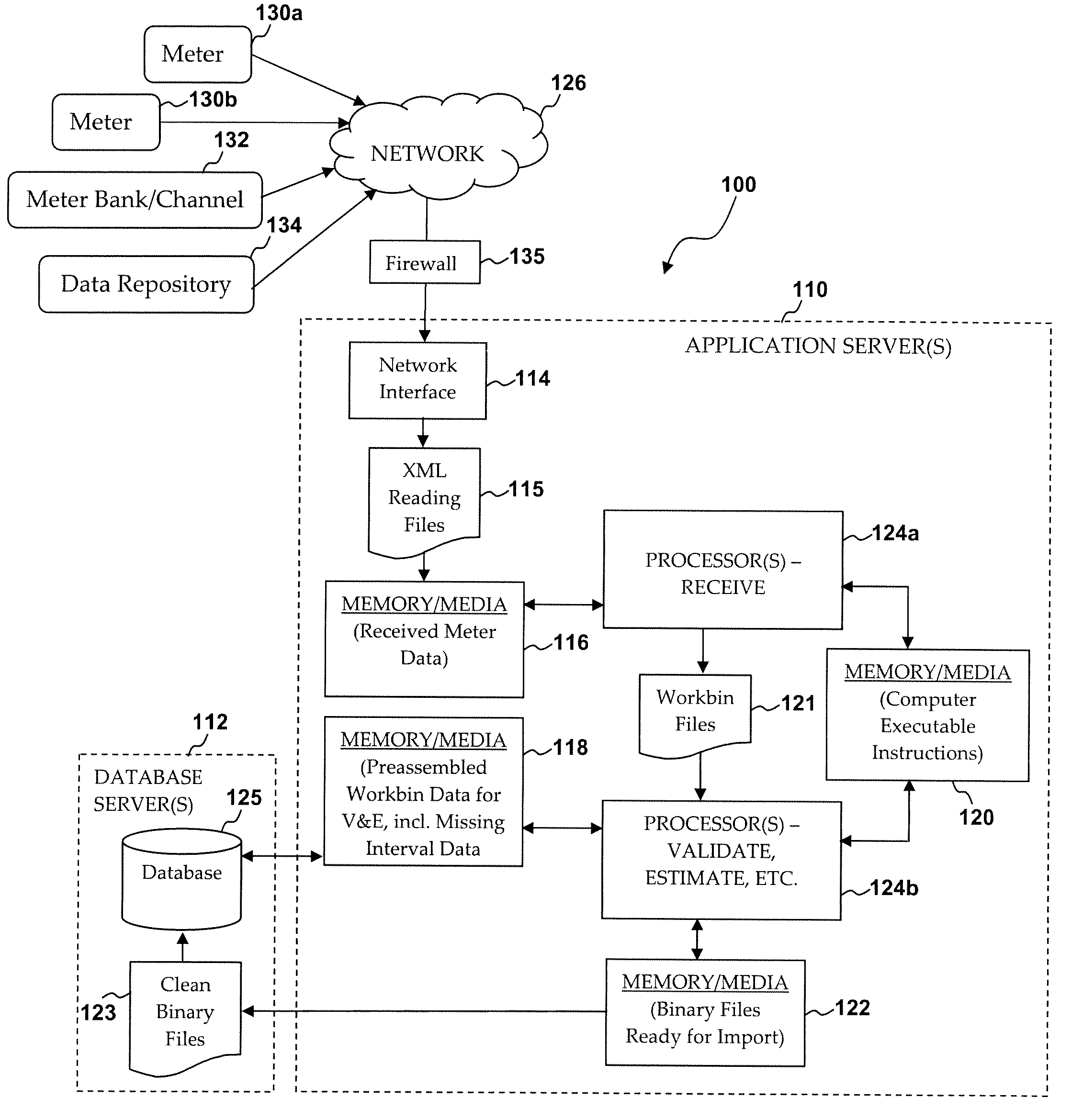
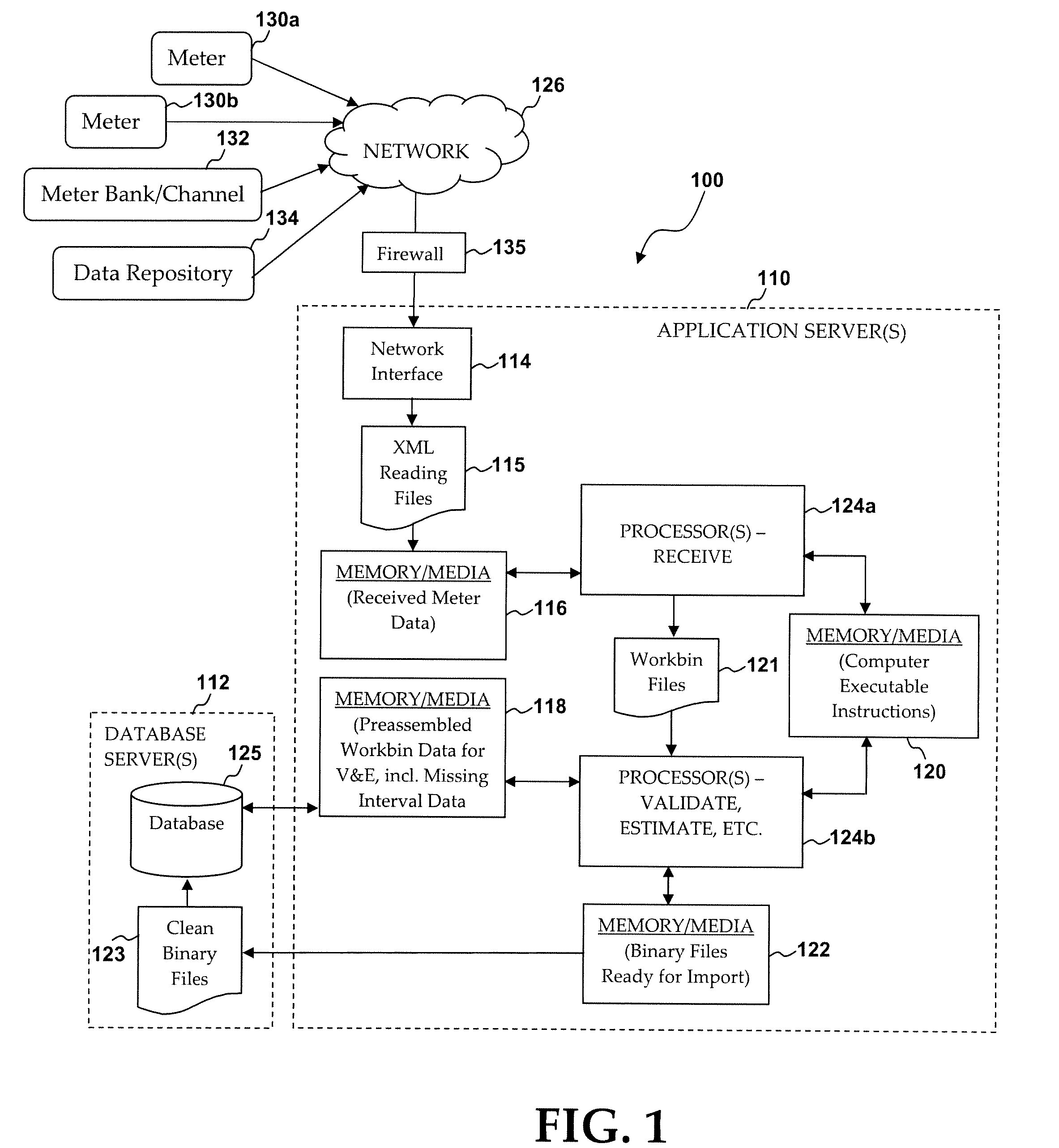
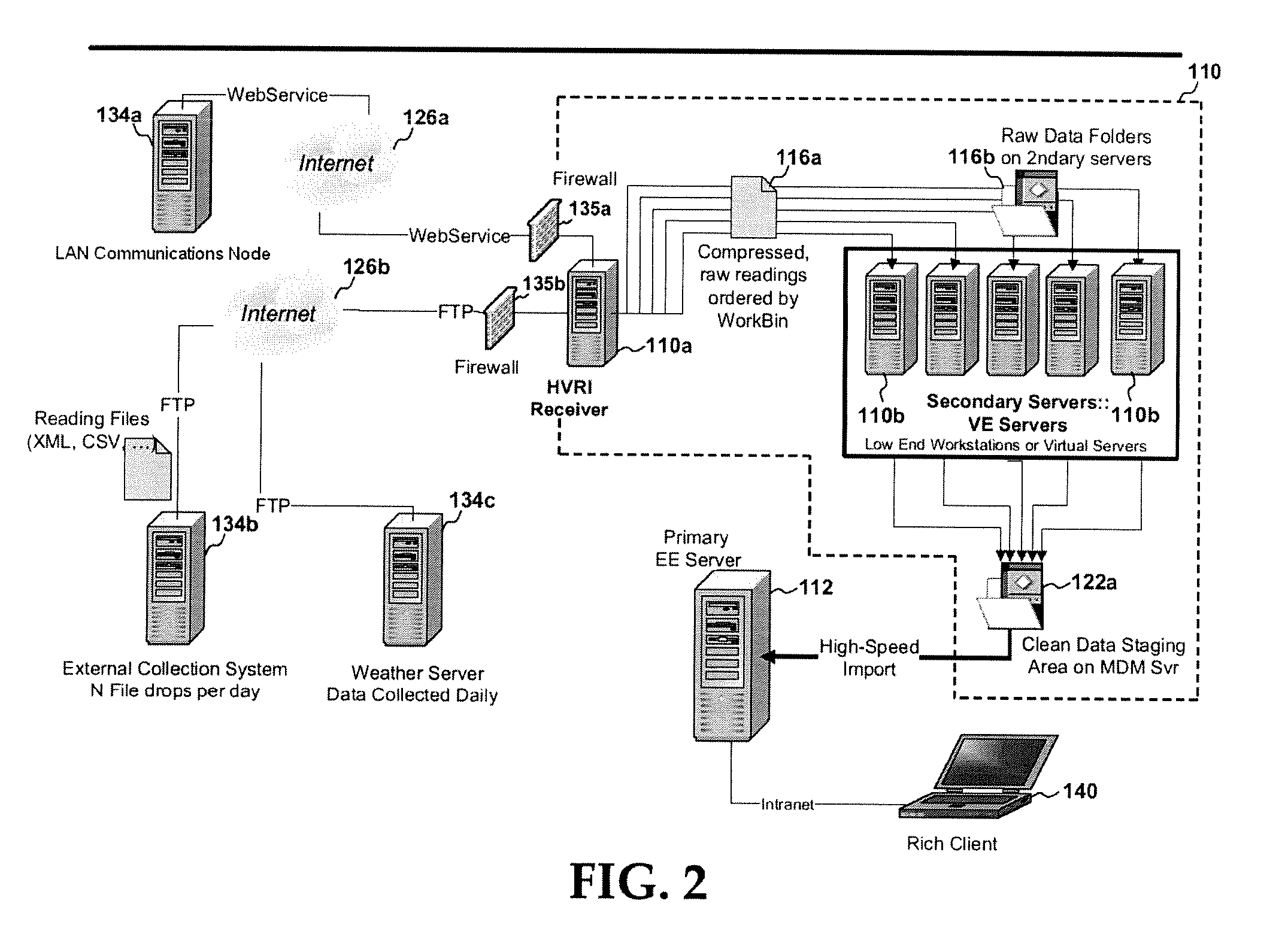
System and method of high volume import, validation and estimation of meter data
ActiveUS20100117856A1Efficient collectionReduce the amount of solutionElectric signal transmission systemsTariff metering apparatusApplication serverMeter data management system
A meter data management system includes one or more application servers configured to receive, validate and estimate received meter data. The one or more application servers may include various memory / media elements for storing raw and transformed meter data as well as software in the form of computer-executable instructions, which are executed by a processor to implement a variety of functions, including establishing a mapping between the plurality of external devices and a plurality of preconfigured processing workbins (e.g., collections of meter channels in the same time zones), transforming the received meter data into a plurality of data files identified by timing parameter and workbin, validating data provided in each data file, estimating missing or invalid data, and automatically writing validated (and optionally estimated) data as import files to a database server. Such clean data files are then imported to one or more dedicated databases installed on the database server.
Owner:ITRON
Cache flushing
InactiveUS20020112083A1Easy mappingData processing applicationsDigital data protectionComputerized systemAccess management
The present invention provides cache flushing of selected data while leaving remaining cached data intact. Data can be flushed from caches distributed across various components of a network-based computer system. These caches can contain various types of data. In one embodiment, the caches exist in an Access System and contain user identity profile information. In another embodiment, the caches exist in an Access Management System and contain authentication, authorization, or auditing rules. A system in accordance with the invention detects a change to data residing on a server and transmits a synchronization record to a component of the system. The synchronization record identifies the changed data. The system flushes the changed data identified by the synchronization record from caches of the component.
Owner:ORACLE INT CORP
Post data processing
InactiveUS20020120599A1Easy mappingDigital data processing detailsUnauthorized memory use protectionDatum referenceAuthorization
The present invention matches sets of authentication, authorization, and auditing rules to resources in an Access System based on the contents of POST data received in HTTP POST requests. The system of the present invention receives a POST request and matches a set of rules to a resource using POST data referenced by the HTTP request. In one embodiment, the matching is performed by accessing required matching data. A portion of the POST data is selected and compared with the required data. If all of the required data is matched to the POST data, then the resource is successfully matched. The present invention further authorizes a user to access resources in an Access System based on the contents of POST data. An authorization rule is retrieved and authorization is performed using the POST data. If the authorization is successful, the system grants the user access to the resource.
Owner:ORACLE INT CORP
Method and software for mobile data collection having managed workflow
InactiveUS20060288014A1Reduce data volumeOvercome excessive storage spaceDigital data processing detailsResourcesGps receiverMobile worker
A computerized method for collecting information on geo-spatially distributed assets. The method includes managed workflow so that work crews are automatically informed of the work that needs to be done and can report back to management when the work is completed. Mobile workers use a network-disconnected mobile computing device for data collection that includes a GPS receiver for use in generating a map showing the user's position in relation to the asset. An asset attribute database having a vertical database schema permits live-entry of the collected data without the need for confirmation, thereby speeding data entry and reducing the likelihood of data loss in the event of power failure, etc. The vertical database schema also permits data collection forms to be changed without updating the underlying database structure. The vertical database schema is converted to a relational database schema for management reporting purposes.
Owner:AGRIGIS
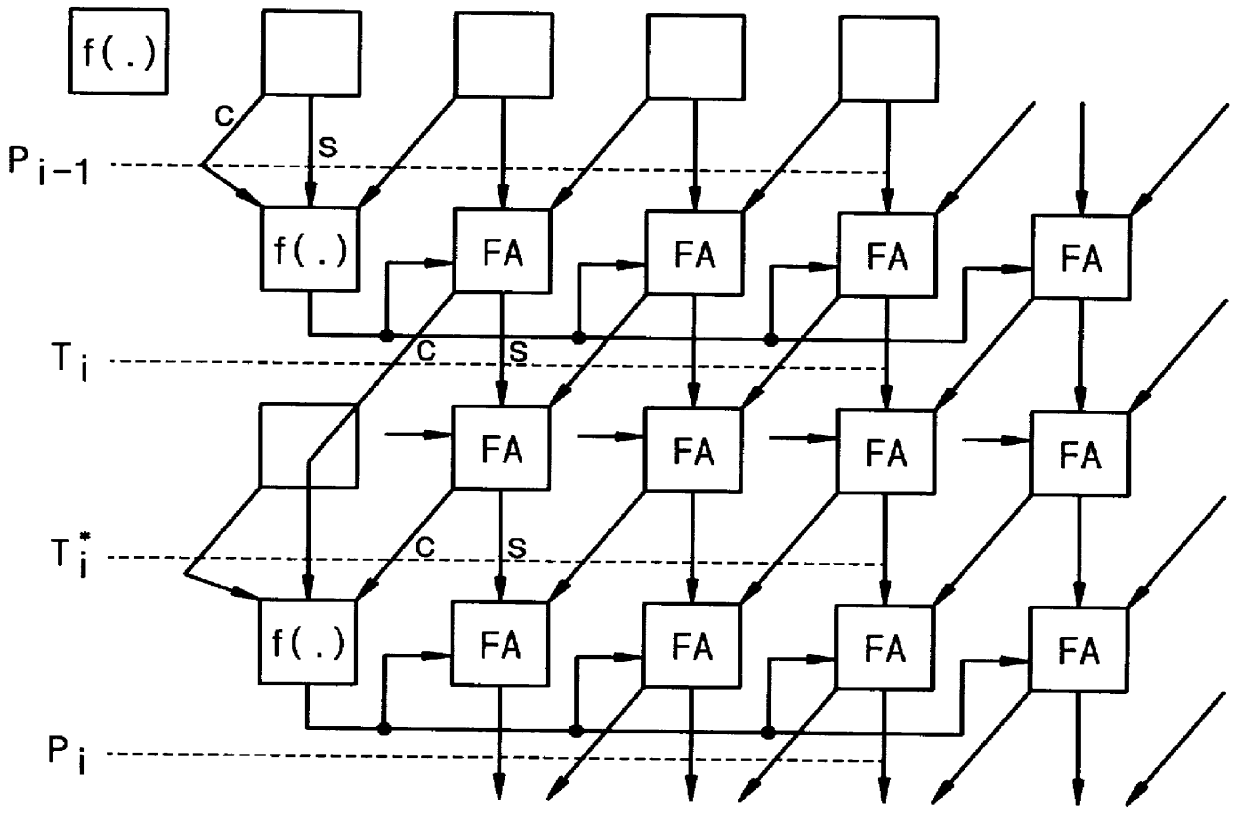
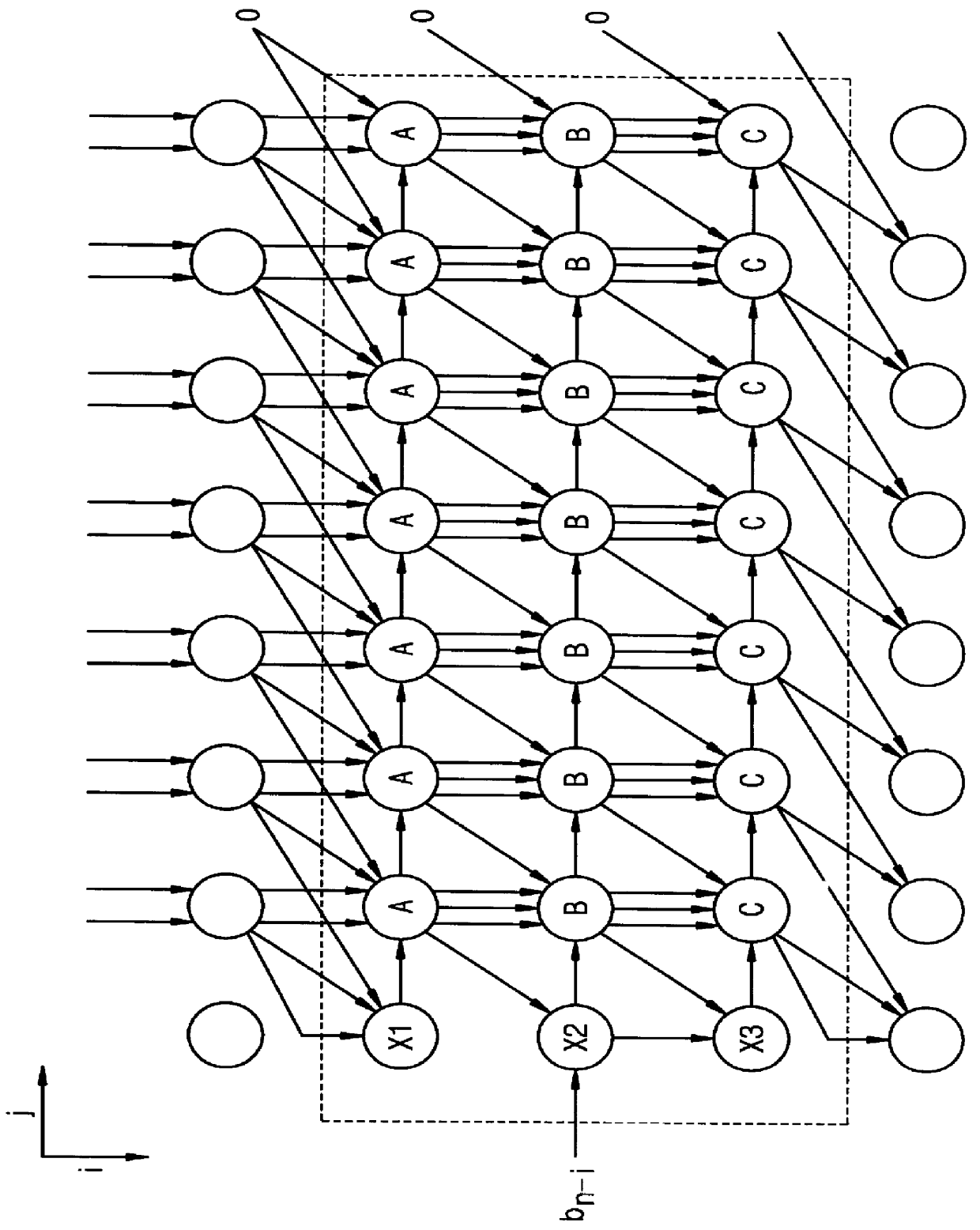
Device and method for modular multiplication
InactiveUS6151393AEasy mappingImprove performanceComputations using contact-making devicesComputation using non-contact making devicesEngineeringFine grain
A method and apparatus are disclosed for performing modular multiplication. Modular multiplication in accordance with the present invention includes precalculating a 2's complement of a given modulus and multiples of the 2's complement and calculating a total magnitude of end-around carries during the modular multiplication. The calculated multiples are selected depending on the total magnitude of the end-around carries, and the selected multiples are added. The disclosure includes array structures in accordance with the present invention. The invention includes an algorithm designed for Rivest-Shamir-Adelman (RSA) cryptography and based on the familiar iterative Homer's rule, but uses precalculated complements of the modulus. The problem of deciding which multiples of the modulus to subtract in intermediate iteration stages has been simplified using simple look-up of precalculated complement numbers, thus allowing a finer-grain pipeline. Regularity and local connections make the algorithm suitable for high-performance array implementation in FPGA's (field programmable gate arrays) or deep submicron VLSI's.
Owner:SAMSUNG ELECTRONICS CO LTD
Methods and apparatuses for selecting levels of detail for objects having multi-resolution models in graphics displays
InactiveUS6400372B1Easy mappingCathode-ray tube indicators3D modellingMajor and minorApplication software
The level of detail selected for each object in a scene is determined based upon a variable normalized risk parameter which may be supplied by the application. A recursive composite parent object process is invoked upon the two children of the scene object in order to allocate graphics resources to objects A and B. Primary and secondary hit value means corresponding to objects A and B are computed. The hit value means are the average sum of hit values recorded for all the leaf objects contained by the objects over a predetermined number of frames. The statistical variances of the primary hit value and secondary hit value are also computed over the previous predetermined number of frames in order facilitates the mapping of the normalized risk parameter to a non-normalized risk parameter indicating the optimal risk for objects A and object B. A quadratic parametric variance equation is solved for the optimal fraction of the remaining graphics resources to be allocated to object A. The optimal fraction is multiplied by the available graphics resources, resulting in the resources allocated to object A; the remaining graphics resources are to object B. If either object A or B is a leaf object, the level of detail is selected for object A or B as the level of detail associated with object A or B requiring the greatest amount of graphics resources not exceeding the resources allocated to object A or B. If either object A or B is a composite parent object, the recursive parent object process is invoked on the two children of object A or B with the available graphics resources for the instantiation of the recursive parent object process set to the graphics resources allocated to object A or B. After levels of detail for all objects in the scene has been achieved, the method according to the present invention renders all leaf objects.
Owner:XEROX CORP
Method and system for compression of data for block mode access storage
InactiveUS20080313371A1Easy mappingDigital data processing detailsMemory adressing/allocation/relocationOriginal dataData access
For use in a storage network comprising a plurality of network elements and operable with a block mode access storage protocol, a method of operating a compression system operatively coupled to at least one computer and to one or more storage devices configured as at least one storage logical unit accommodating data compressed by the compression system, the computer, the storage devices and the compression system are configured as separate network elements. According to the method, the compression system is configured to hold a virtual logical unit, the virtual logical unit is configured to virtually represent in non-compressed form the compressed data stored in the at least one storage logical unit. The size of the virtual logical unit corresponds to an estimated size of raw data which, being compressed, would substantially amount to a size of the storage logical unit. The method includes intercepting one or more data access-related requests from the at least one computer addressed to said storage logical unit, addressing the requests to the virtual logical unit, and facilitating mapping between the compressed data and their virtual representation at the virtual logical unit.
Owner:STORWIZE
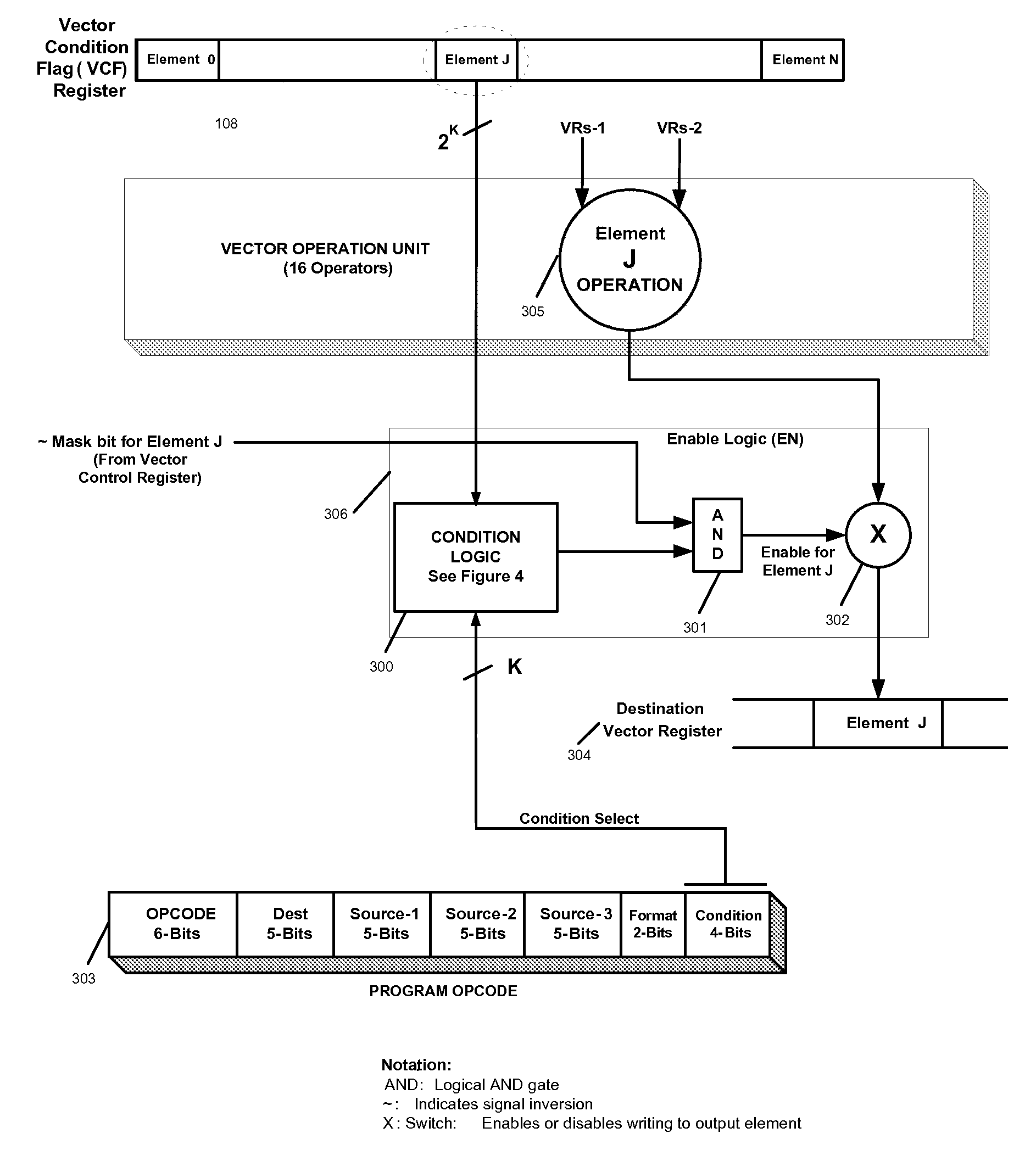
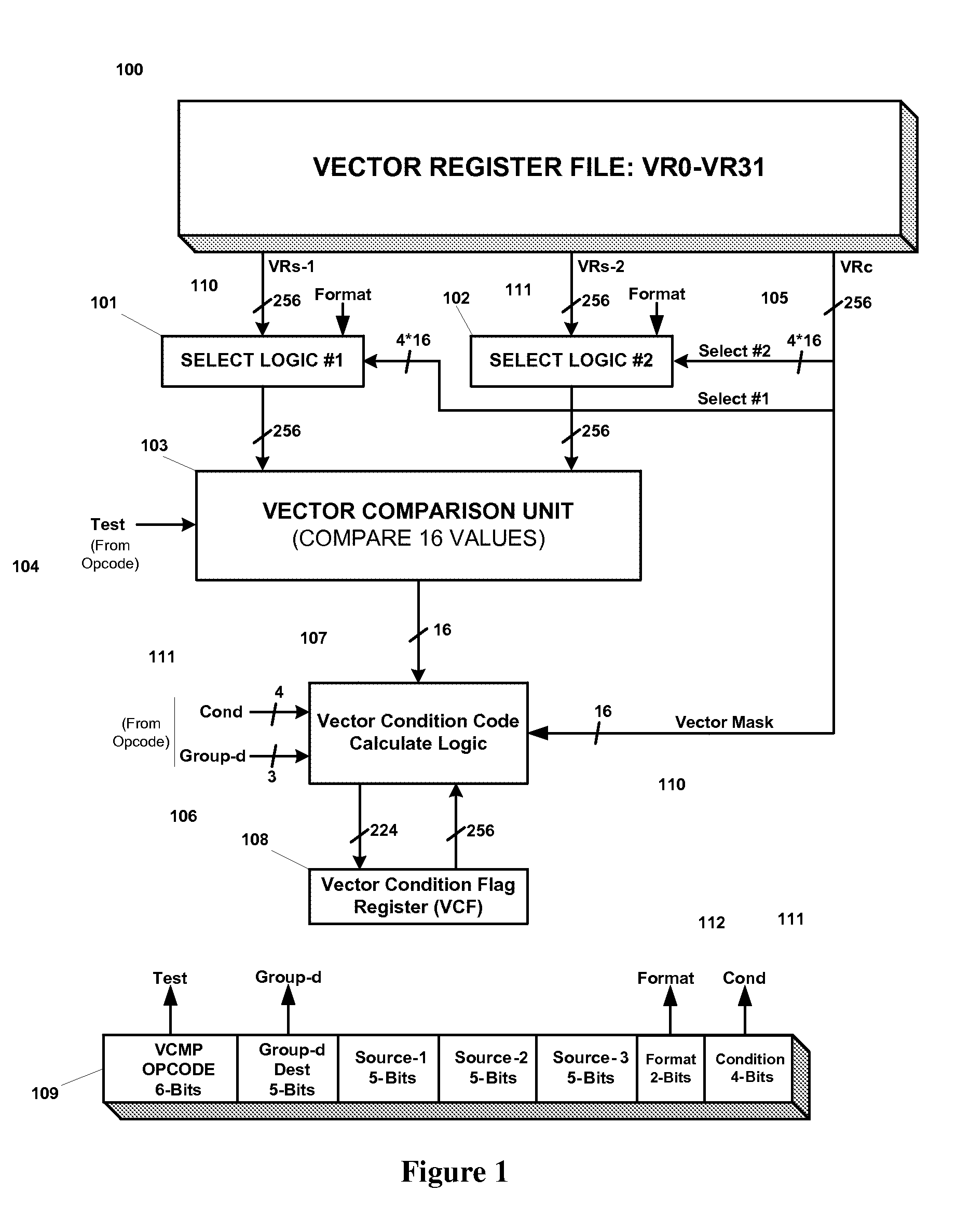
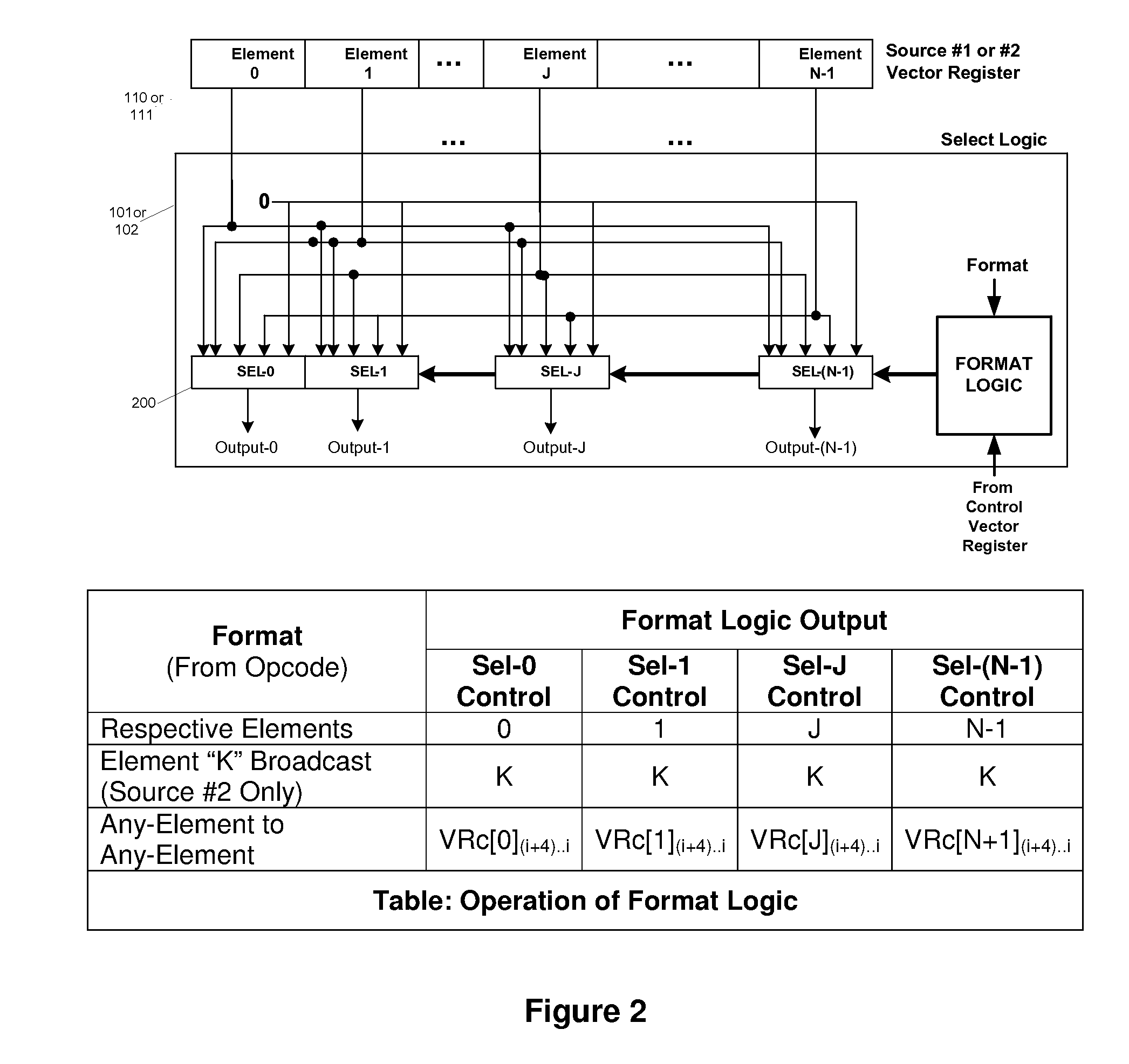
Efficient handling of vector high-level language conditional constructs in a SIMD processor
InactiveUS7793084B1Minimize the numberLow costConditional code generationDigital computer detailsVector elementSimd processing
The present invention provides an efficient method to implement nested if-then-else conditional statements in a SIMD processor, which requires only one vector compare instruction for both if and else parts of the conditional construct. No stack and stack-handling instructions are needed for vector condition codes. Two condition code flag bits representing if and else parts of testing per element provide for nesting of multiple if-then-else. All SIMD instructions are conditional including the vector compare instruction, and this provides a method for aggregating multiple conditions in nested if-then-else statements. M full levels of if-then-else nesting requires (2M−1) nodes or vector test instructions and 2M+1 condition code flags per vector element. Also, capability to compare any element of first source vector register with any element of second source vector is provided.
Owner:CUE BIOTECH
System and methods for obstacle mapping and navigation
InactiveUS8712679B1Facilitates “ ”Improve abilitiesDirection finders using radio wavesComputer controlSpatial changeComputer science
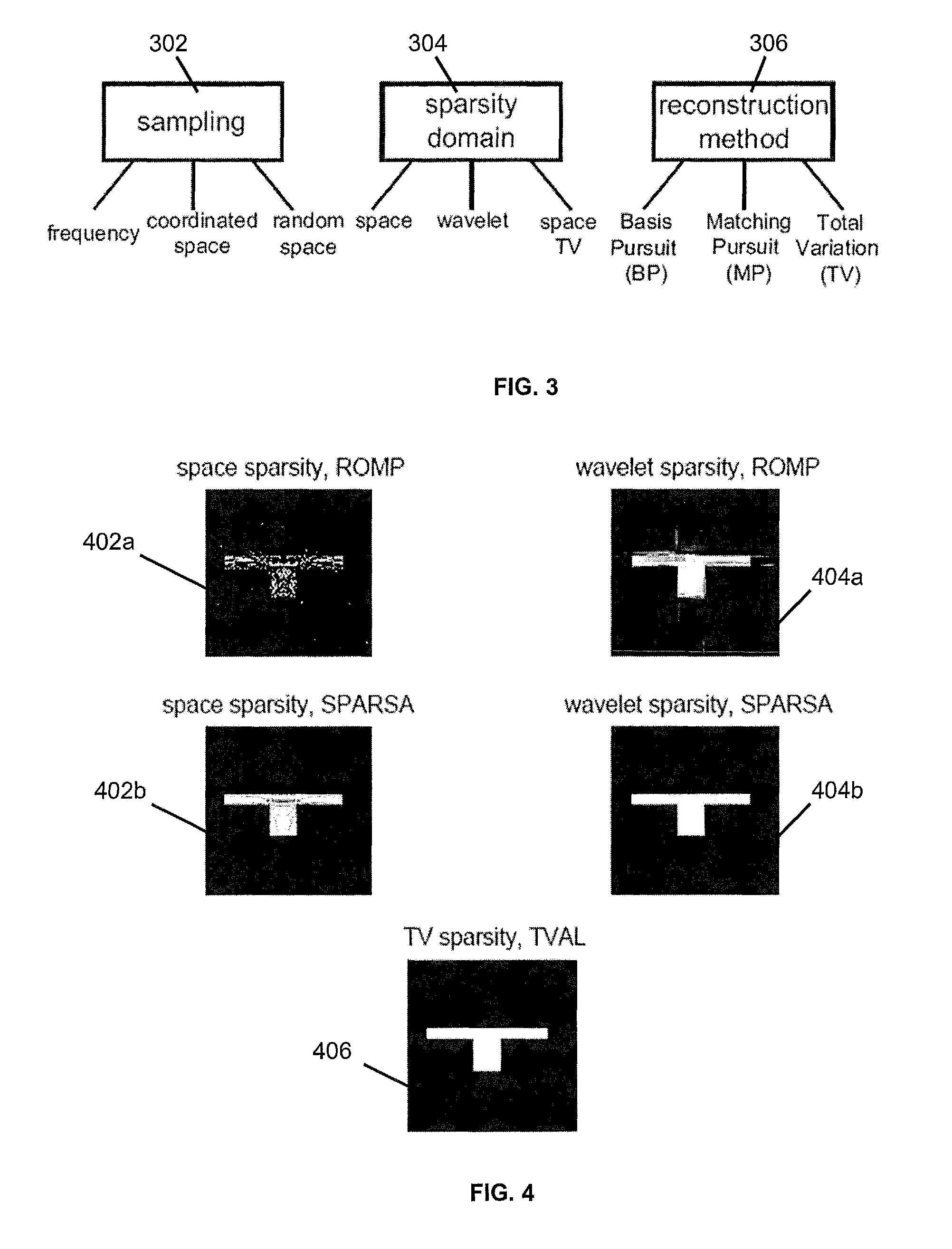
A system and methods for building a map non-invasively (i.e. mapping of occluded and non-occluded obstacles) based on a small number of wireless channel measurements. Approaches for building an obstacle map are based on coordinated space, random space and frequency sampling, such that the sparse representation of the map in space, wavelet or spatial variations, are exploited in order to build the map with minimal sensing.
Owner:STC UNM
Quantum processor with instance programmable qubit connectivity
ActiveUS20160335558A1Process controlControl complexityQuantum computersDigital computer details2d arrayControl system
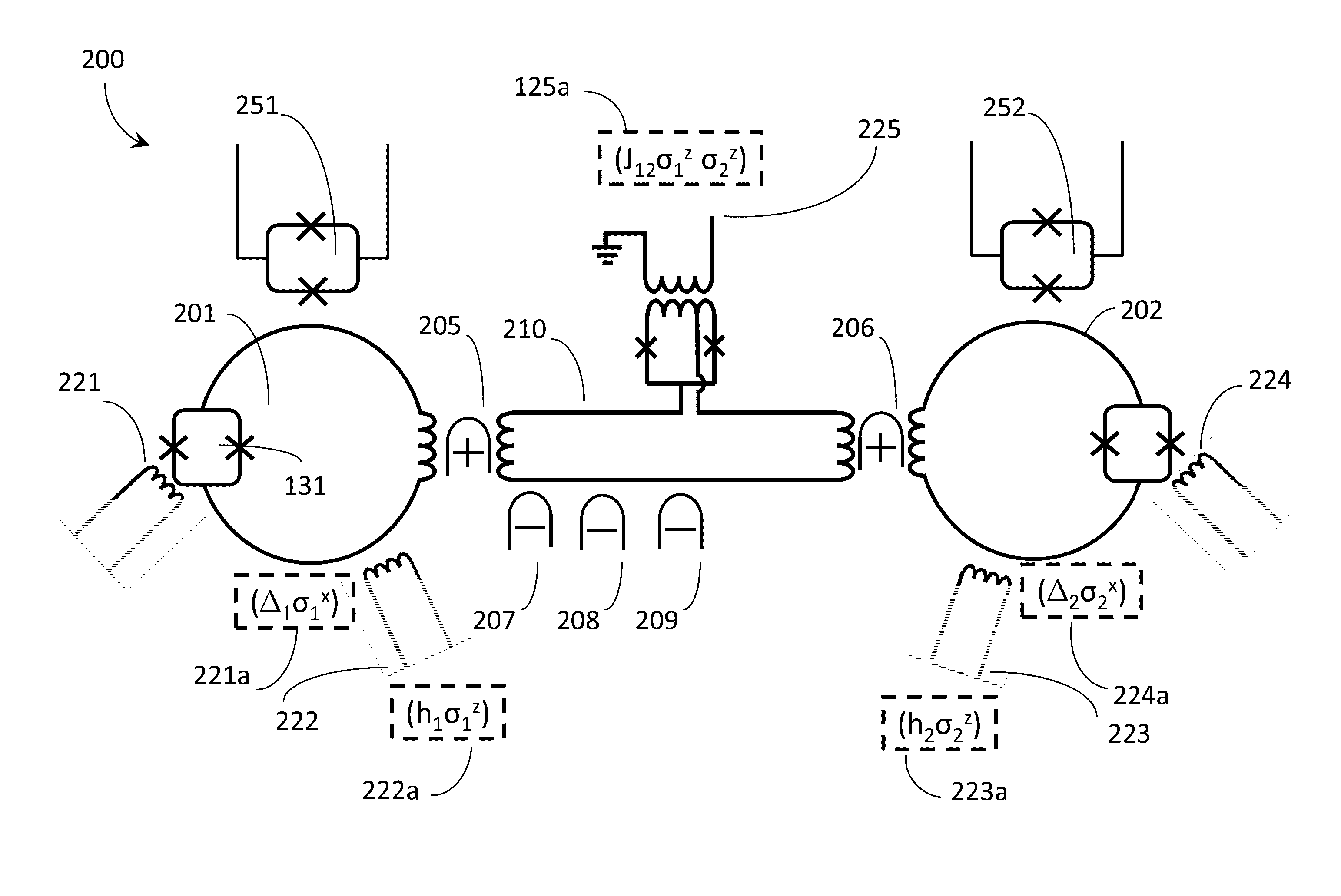
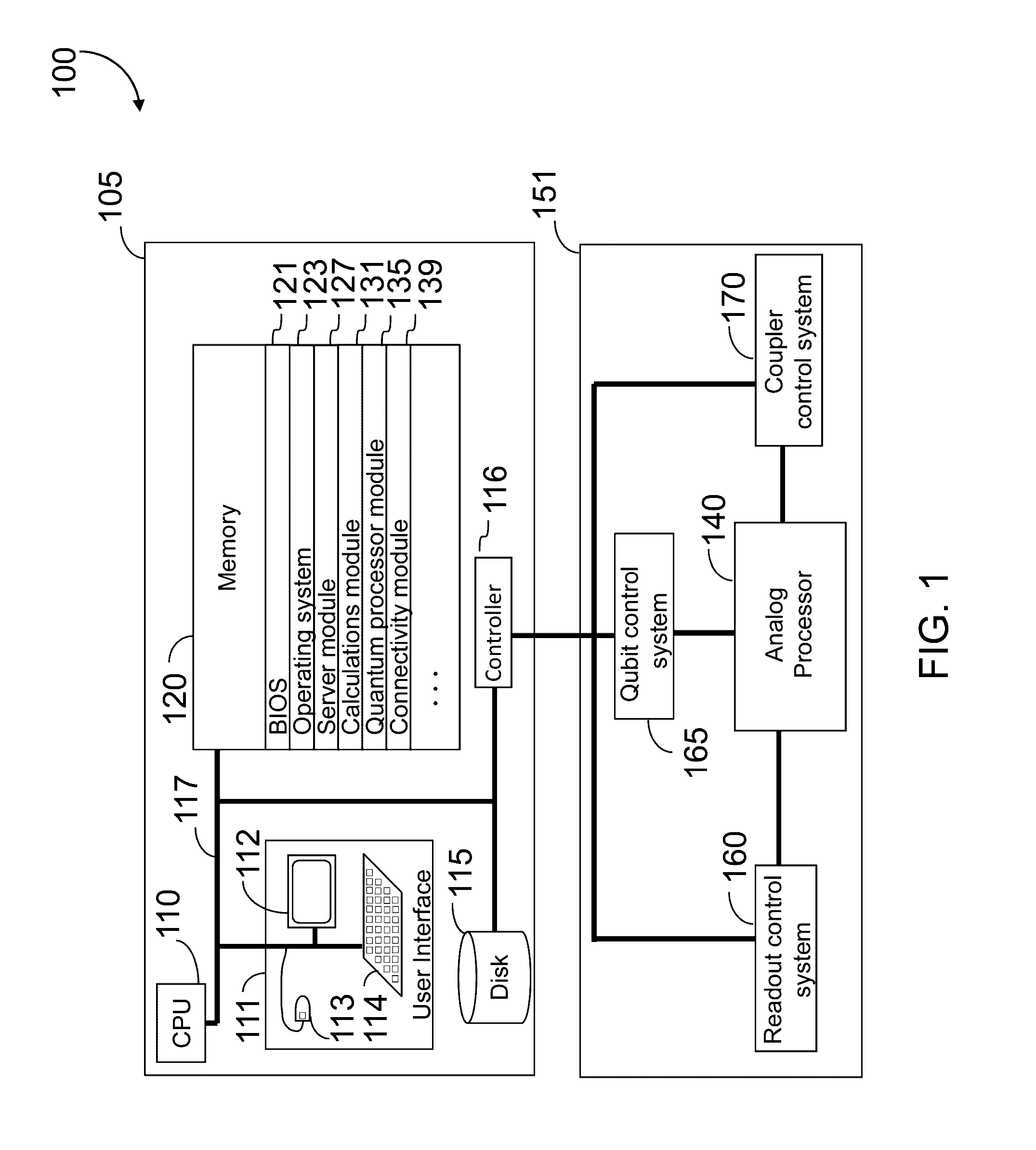
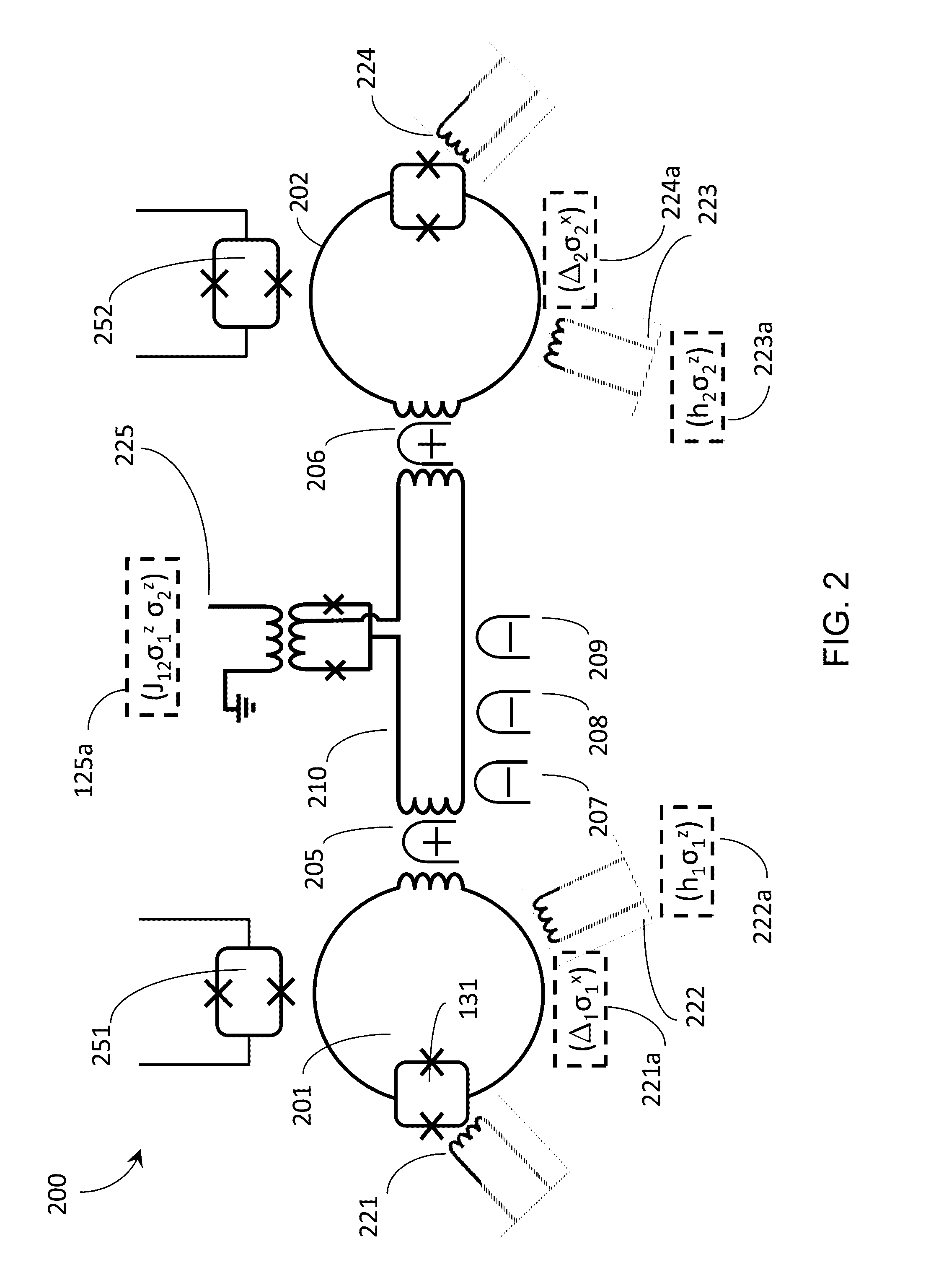
In a quantum processor some couplers couple a given qubit to a nearest neighbor qubit (e.g., vertically and horizontally in an ordered 2D array), other couplers couple to next-nearest neighbor qubits (e.g., diagonally in the ordered 2D array). Couplers may include half-couplers, to selectively provide communicative coupling between a given qubit and other qubits, which may or may not be nearest or even next-nearest-neighbors. Tunable couplers selective mediate communicative coupling. A control system may impose a connectivity on a quantum processor, different than an “as designed” or “as manufactured” physical connectivity. Imposition may be via a digital processor processing a working or updated working graph, to map or embed a problem graph. A set of exclude qubits may be created from a comparison of hardware and working graphs. An annealing schedule may adjust a respective normalized inductance of one or more qubits, for instance to exclude certain qubits.
Owner:D WAVE SYSTEMS INC
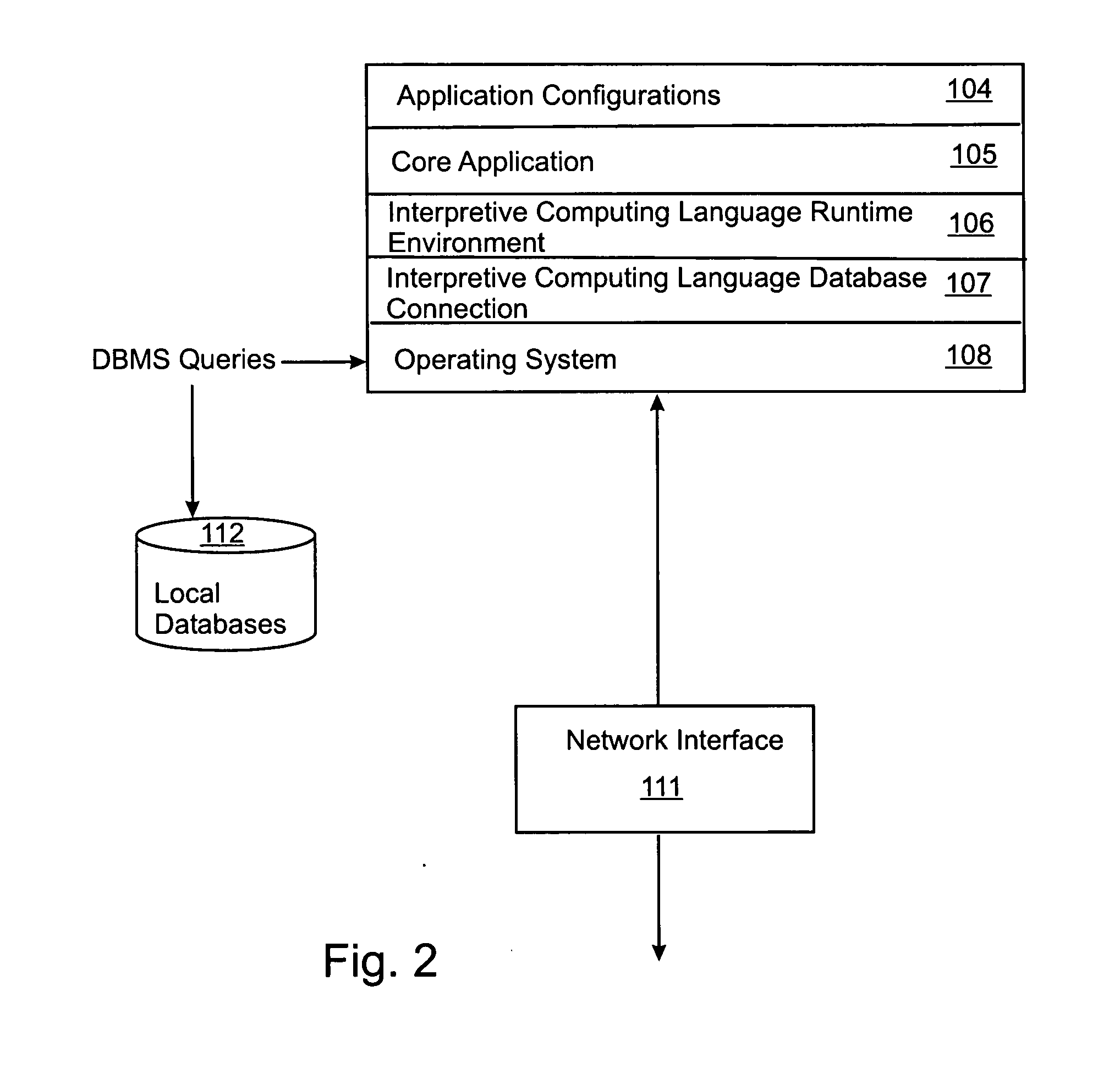
Relational schema format
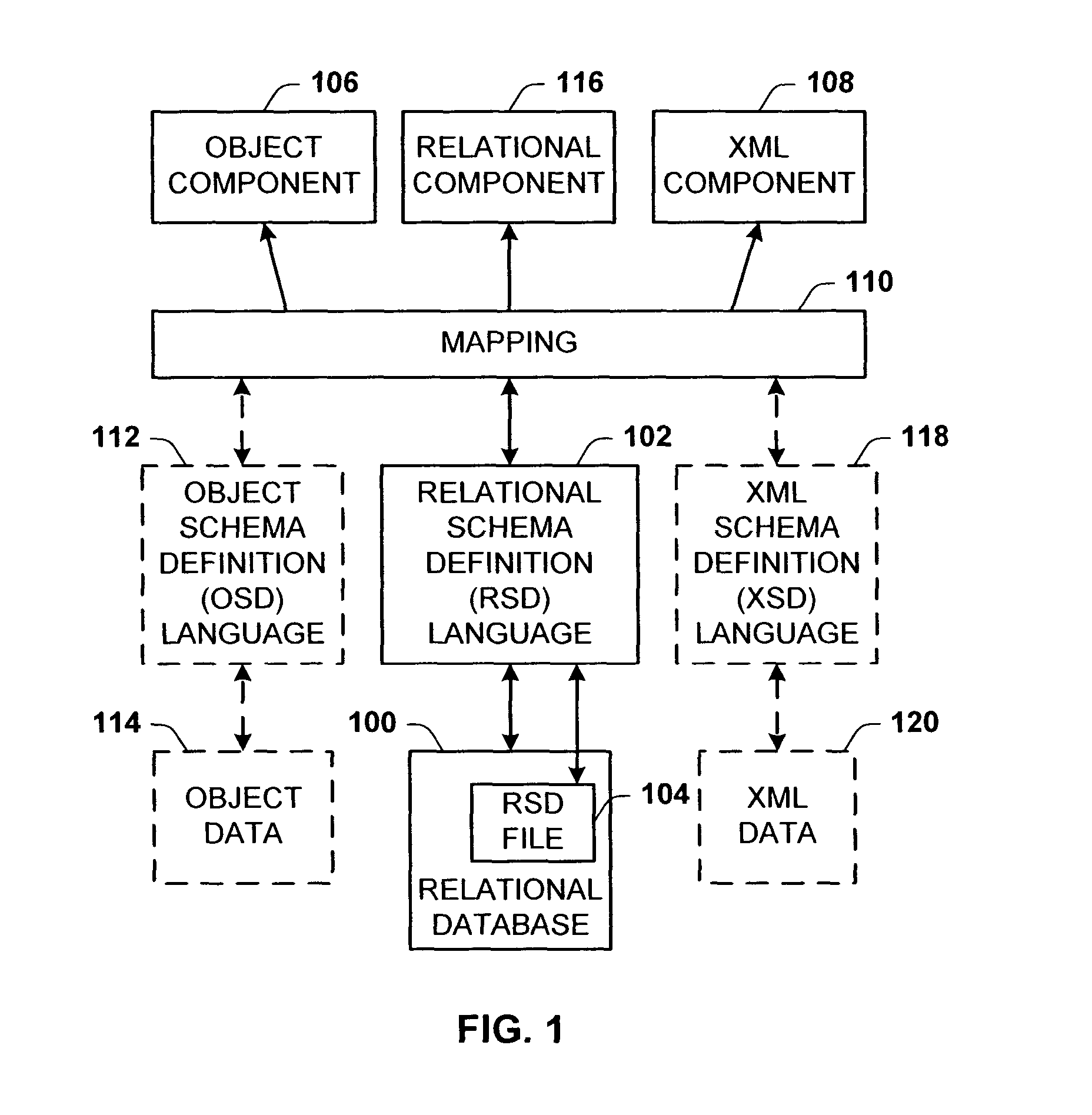
InactiveUS7403956B2Easy mappingEasy to processData processing applicationsDigital data processing detailsRelational databaseInterface description language
A Relational Schema Definition (RSD) language that uses metadata of the relational database to generate an implementation-neutral or implementation-specific format that represents the precise database structure and data. The RSD language is a declarative description language such that an RSD file can then be used offline in a disconnected environment to reconstruct and use the database.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for providing a distributed querying and filtering system
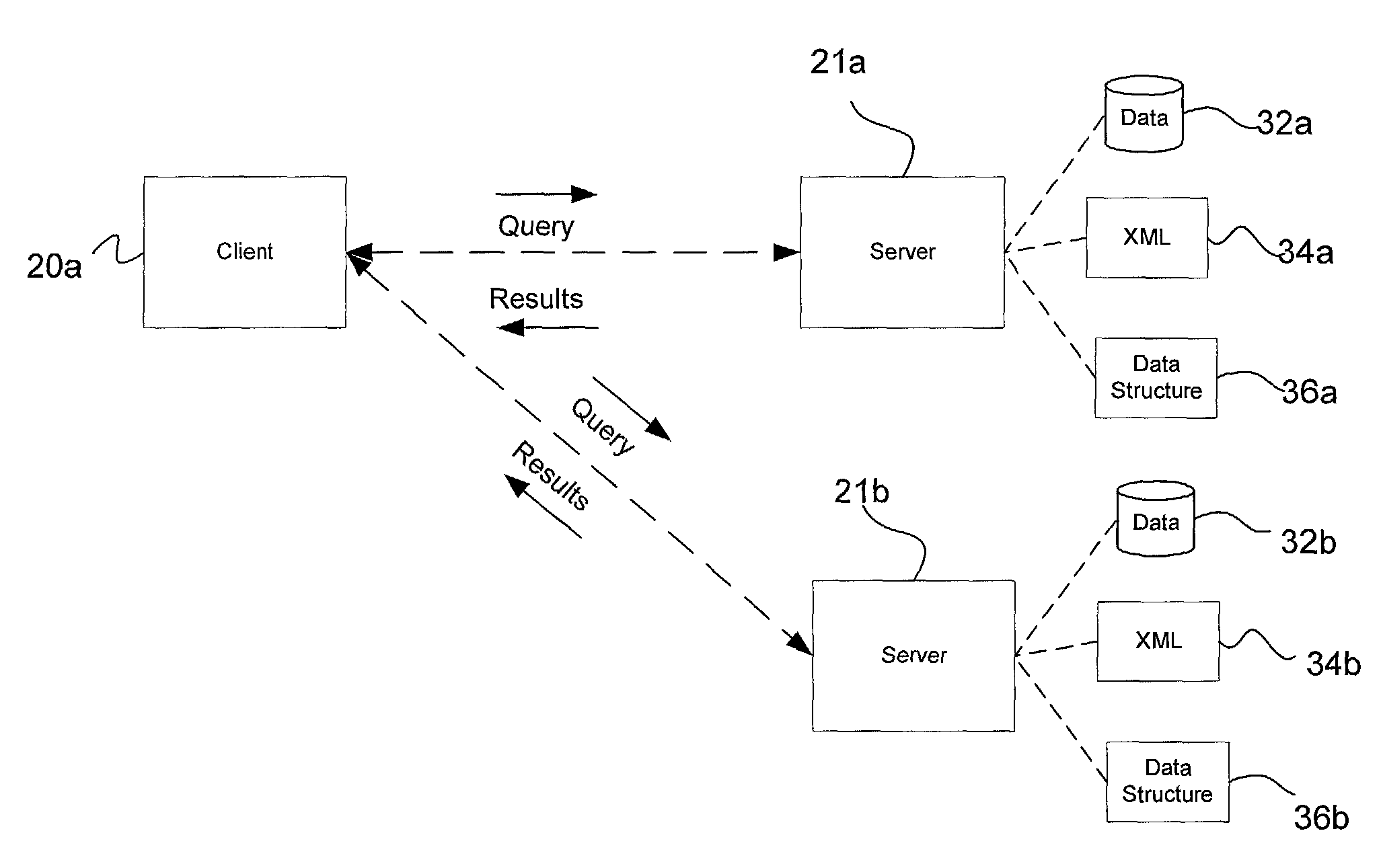
InactiveUS7475058B2Easy mappingSpeech analysisSemi-structured data mapping/conversionFilter systemDocument preparation
In a distributed system querying and navigating data structures, databases, and XML documents in uniform and extensible manner is provided. Queries are defined that provide type information to a variety of digital objects. As such, the underlying data format is abstracted thereby allowing a single query to apply to multiple digital devices even though the multiple digital devices store their data in a different native format.
Owner:MICROSOFT TECH LICENSING LLC
Technique for compressing columns of data
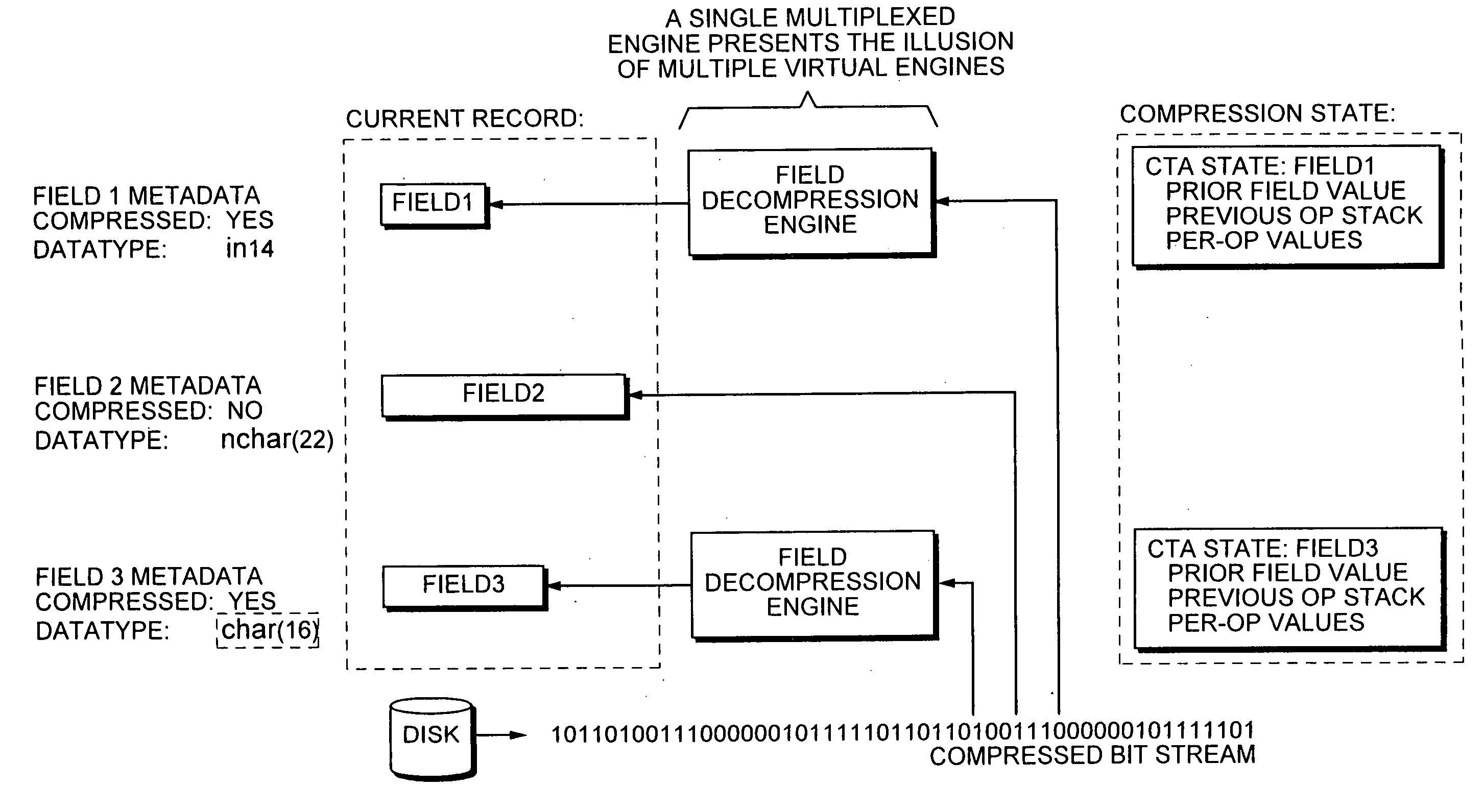
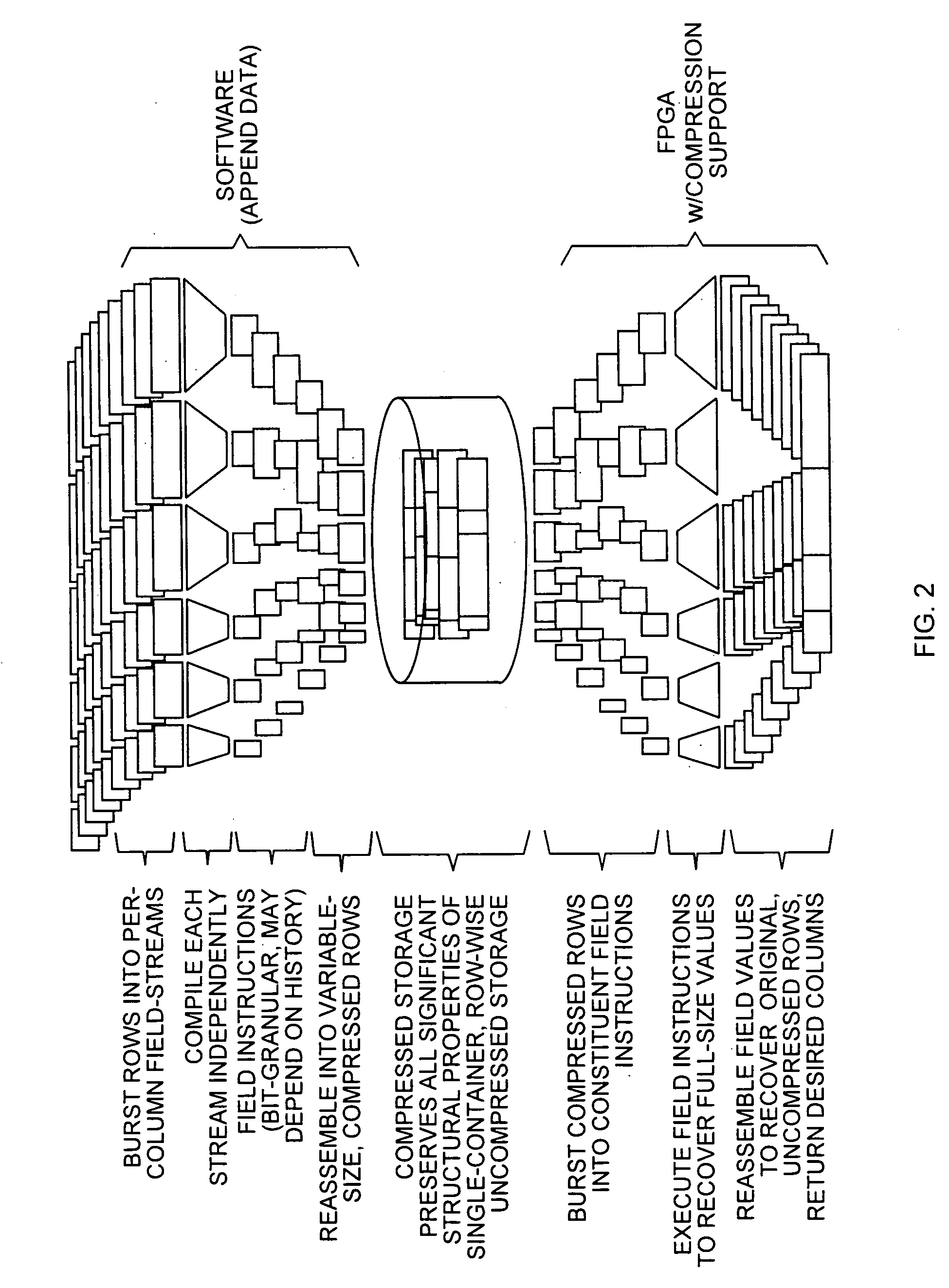
ActiveUS20080222136A1Further efficiencyEasy mappingDigital data information retrievalDigital data processing detailsData valuePast history
An approach for providing compression of a database table that uses a compiled table algorithm (CTA) that provides leverage. Data within any given column in adjacent rows is often the same as or closely related to its neighbors. Rather than storing data in each column of each row as a specific integer, floating point, or character data value, a field reconstruction instruction is stored that when executed by a decompression engine can reconstruct the data value. The field reconstruction instruction may be bit granular and may depend upon past history given that the data compression engine may preserve state as row data is streamed off a storage device.
Owner:EDISON VAULT LLC
Wind Turbine and Method for the Automatic Correction of Wind Vane Settings
InactiveUS20080111379A1Precise alignmentSimple processWind motor controlWind motor combinationsPrevailing windsTurbine
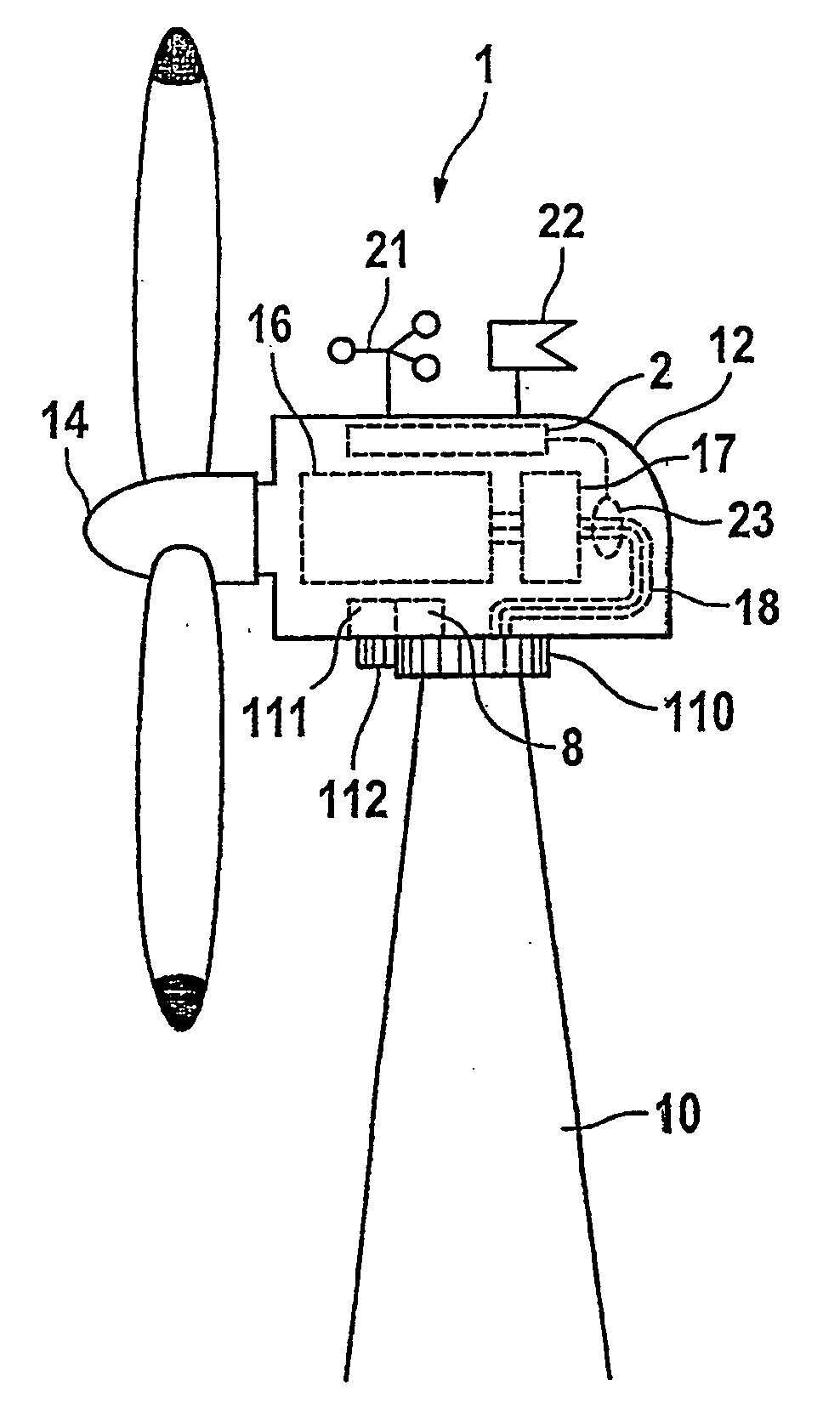
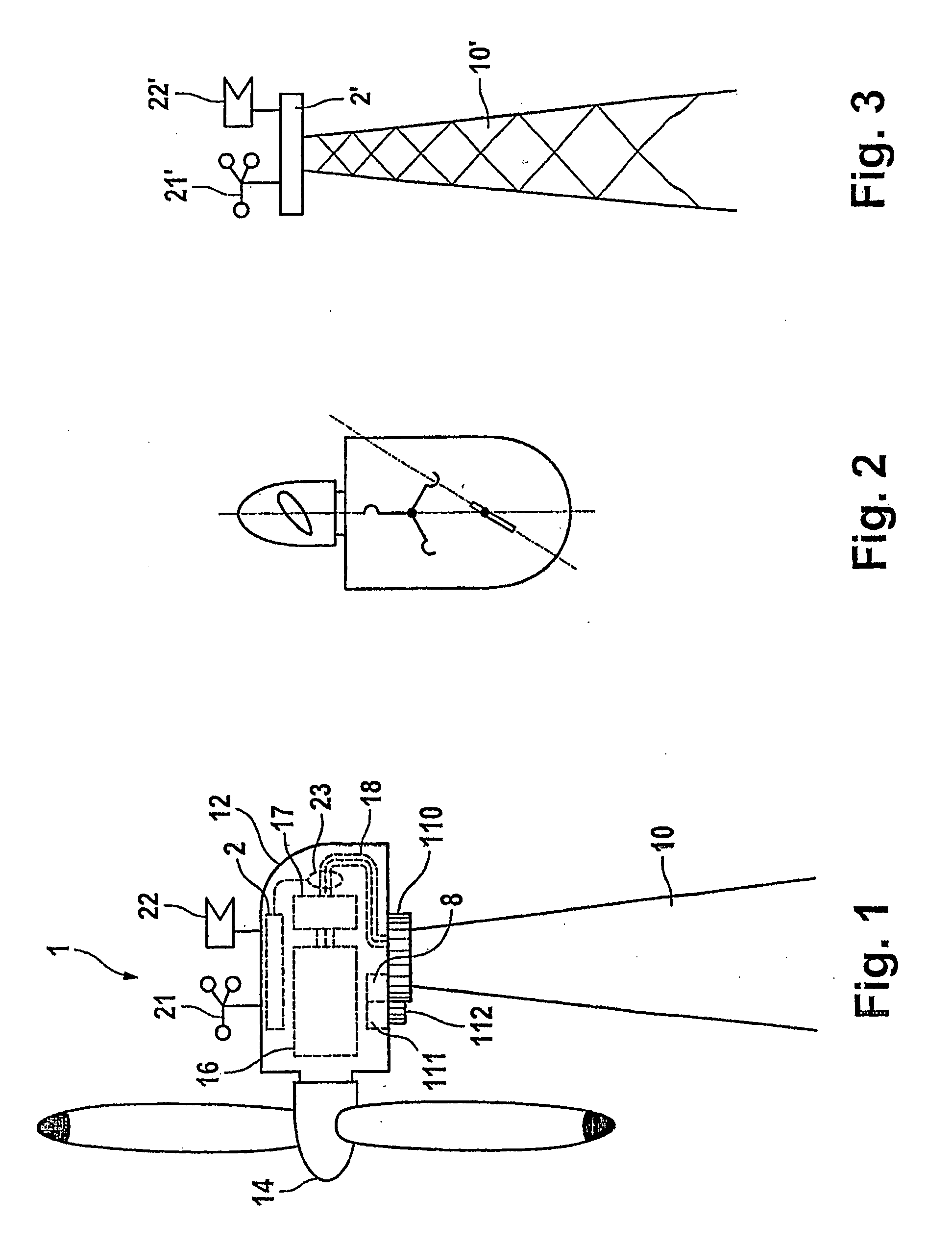
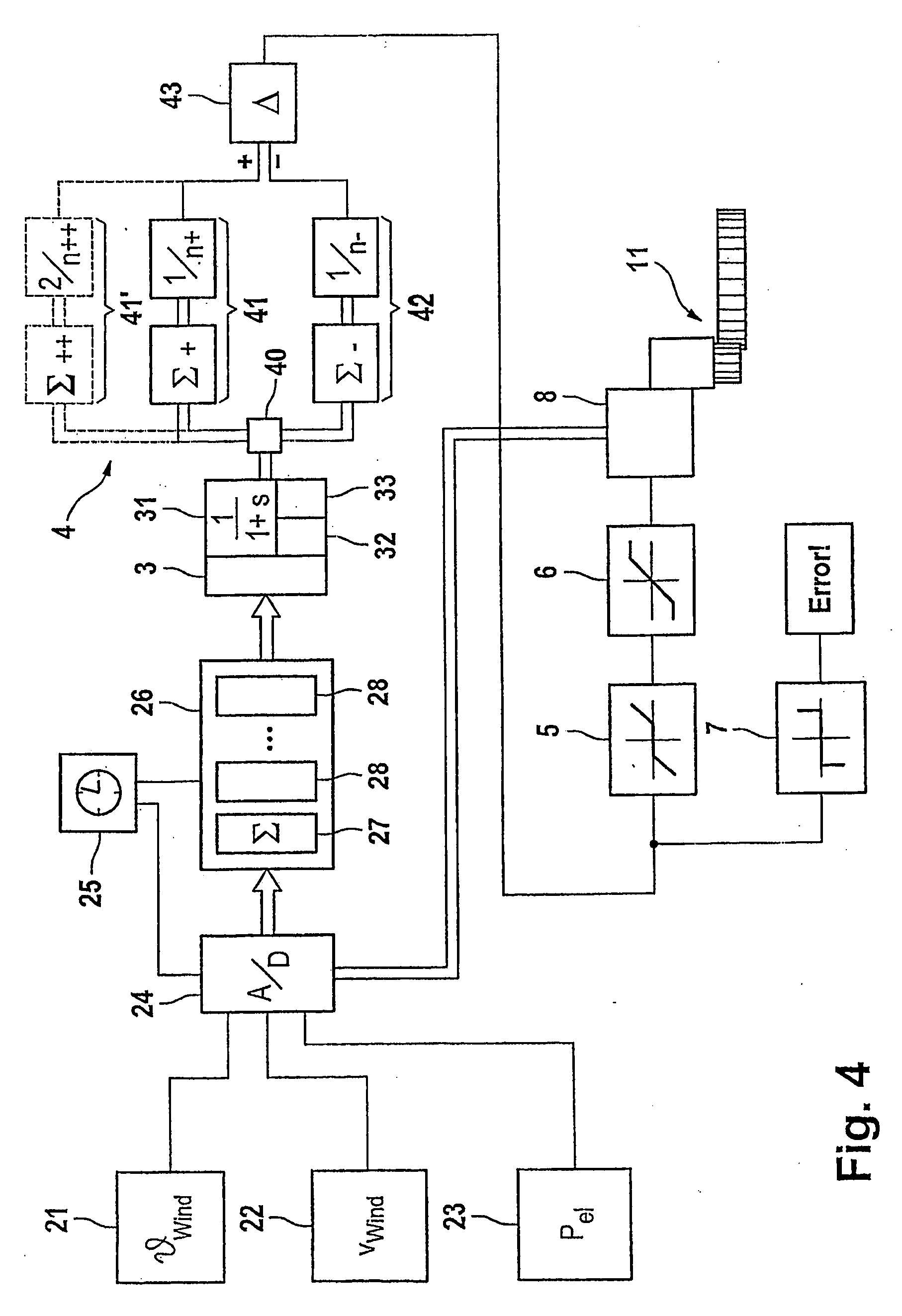
The invention relates to a wind turbine comprising a machine housing (12) equipped with a rotor (14), which is mounted to pivot on a sub-structure (10). Wind parameters and an electromechanical quantity are determined by means of measuring devices (21, 22, 23). To enable the machine housing (12) to track the wind, the wind turbine is equipped with a pivoting device (11) comprising a controller (8). The wind turbine is also equipped with a calibration module (2), which is configured to determine an effective mass of the electromechanical quantity using the wind speed. In addition, the turbine comprises an evaluation device (4) comprising a classifier (40), which is used to form a first average value for a first class, for which the wind direction is positive and a second average value for a second class, for which the wind direction is negative. A difference is determined by means of a comparator and a calibration signal is emitted to the controller (8) of the pivoting device (11). The invention permits an autonomous calibration of the controller (8) for the tracking of the machine housing (12) and thus reduces the risk of an erroneous positioning of the rotor (14) in relation to the wind direction, irrespective of the prevailing wind conditions. The invention is particularly stable in relation to variable wind forces and directions, especially in the presence of gusts.
Owner:SENVION GMBH
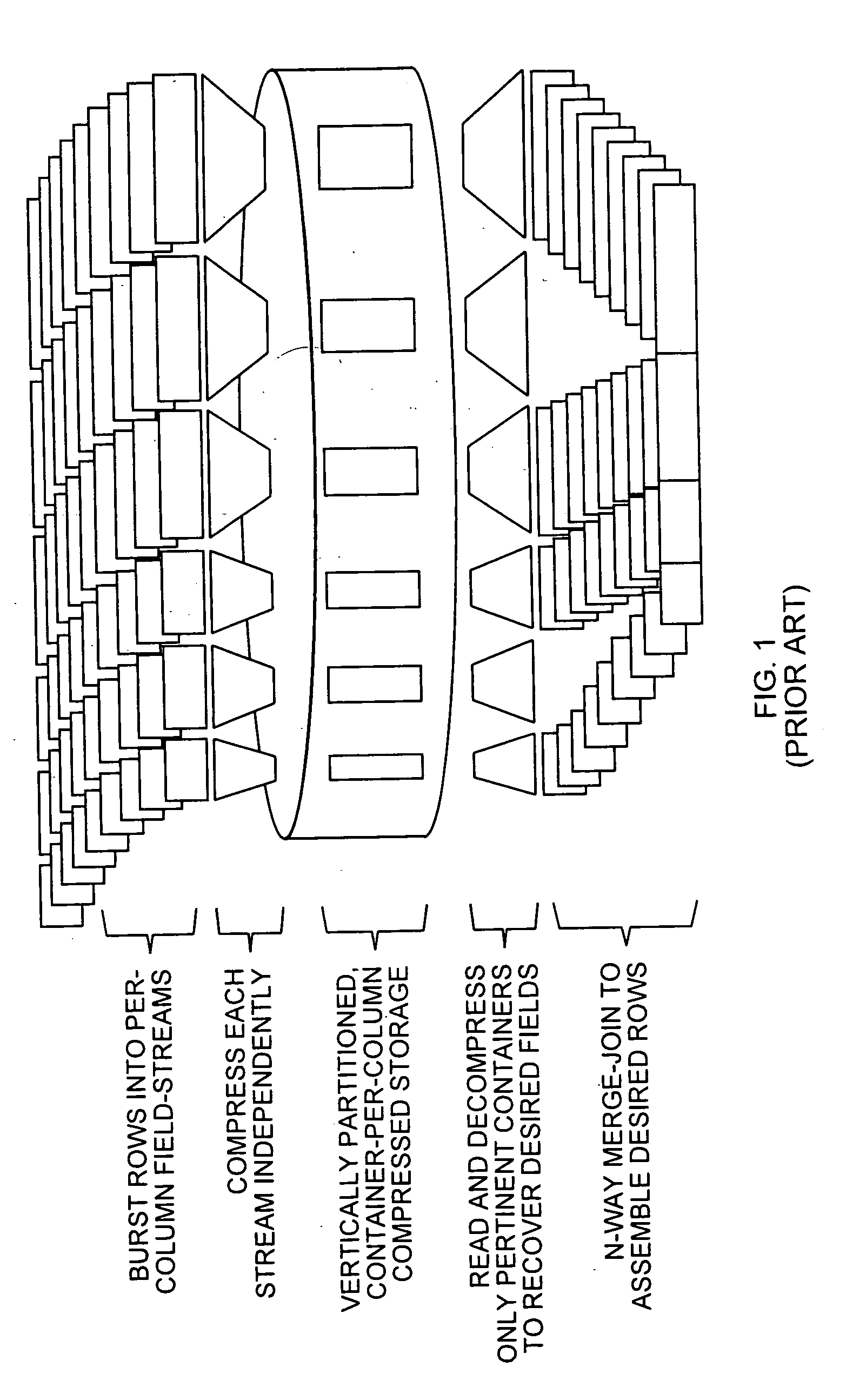
Systems and methods for compression of data for block mode access storage
InactiveUS20110219144A1Easy mappingDigital data information retrievalMultiple digital computer combinationsStructure of Management InformationParallel computing
Owner:IBM CORP
Context driven topologies
InactiveUS8543573B2Easy mappingExact matchDigital data processing details2D-image generationTopology informationNetwork structure
Information is analyzed and developed by creating consolidated representations of groups of data, which are associated with context information, comprising information about relationships between the groups of data, to create representations of the groups of data. The context information is embedded as symbols in descriptions of at least some of the groups of data. The symbols are used in mapping hierarchical relationships between the groups of data. Representations having commonalities are consolidated. A data network structure having network components comprising groups of data, representations and / or consolidated representations is stored. A data network structure display is created with sounds, light, forms, textures and / or colors, and is analyzed using signal processing or mathematical techniques to review context information associated with the network components without reference to groups of data in the network components. The display analysis creates new information, which is stored for retrieval by a plurality of users.
Owner:ACCURACY & AESTHETICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com