Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
465 results about "Data binding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
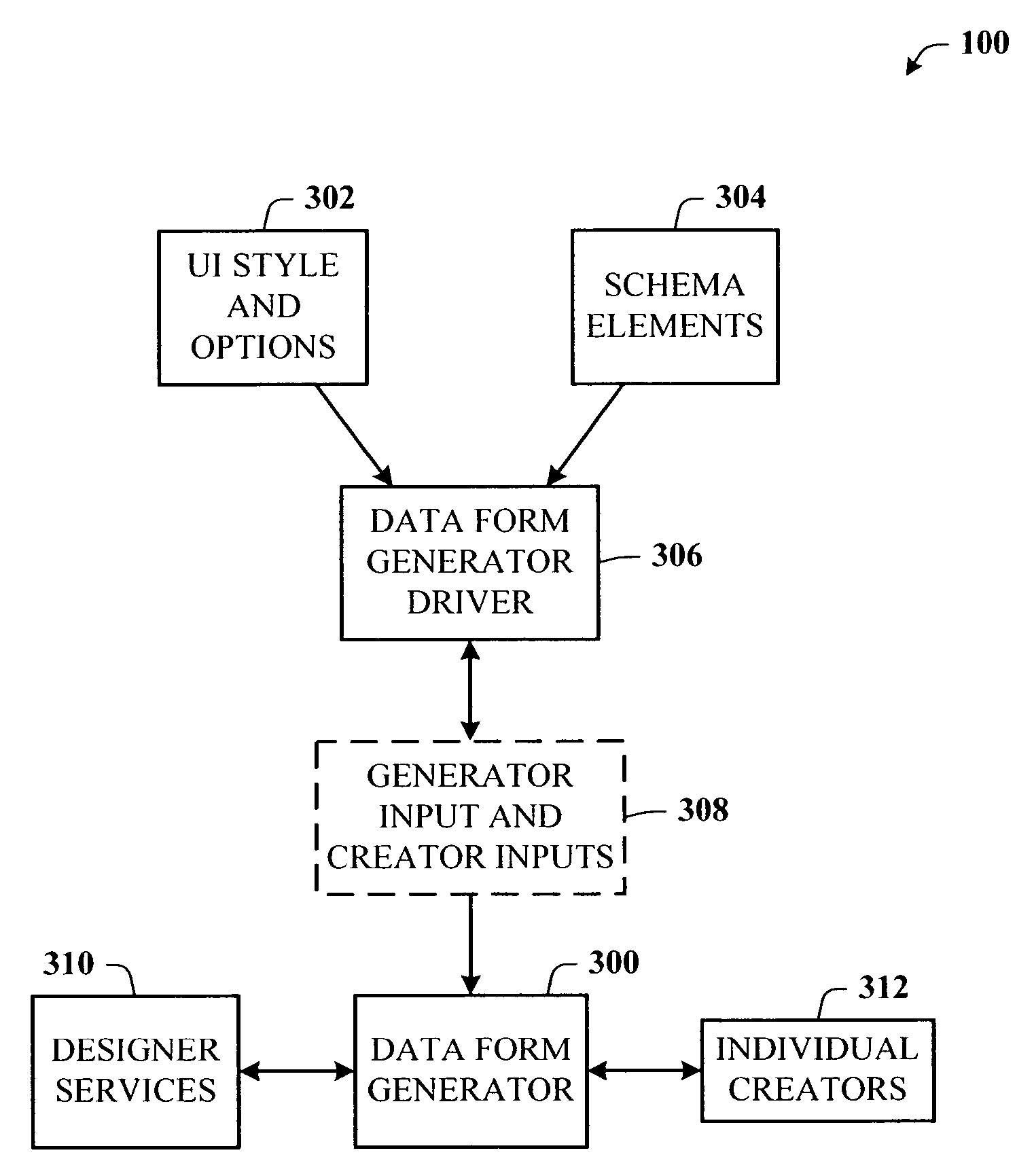
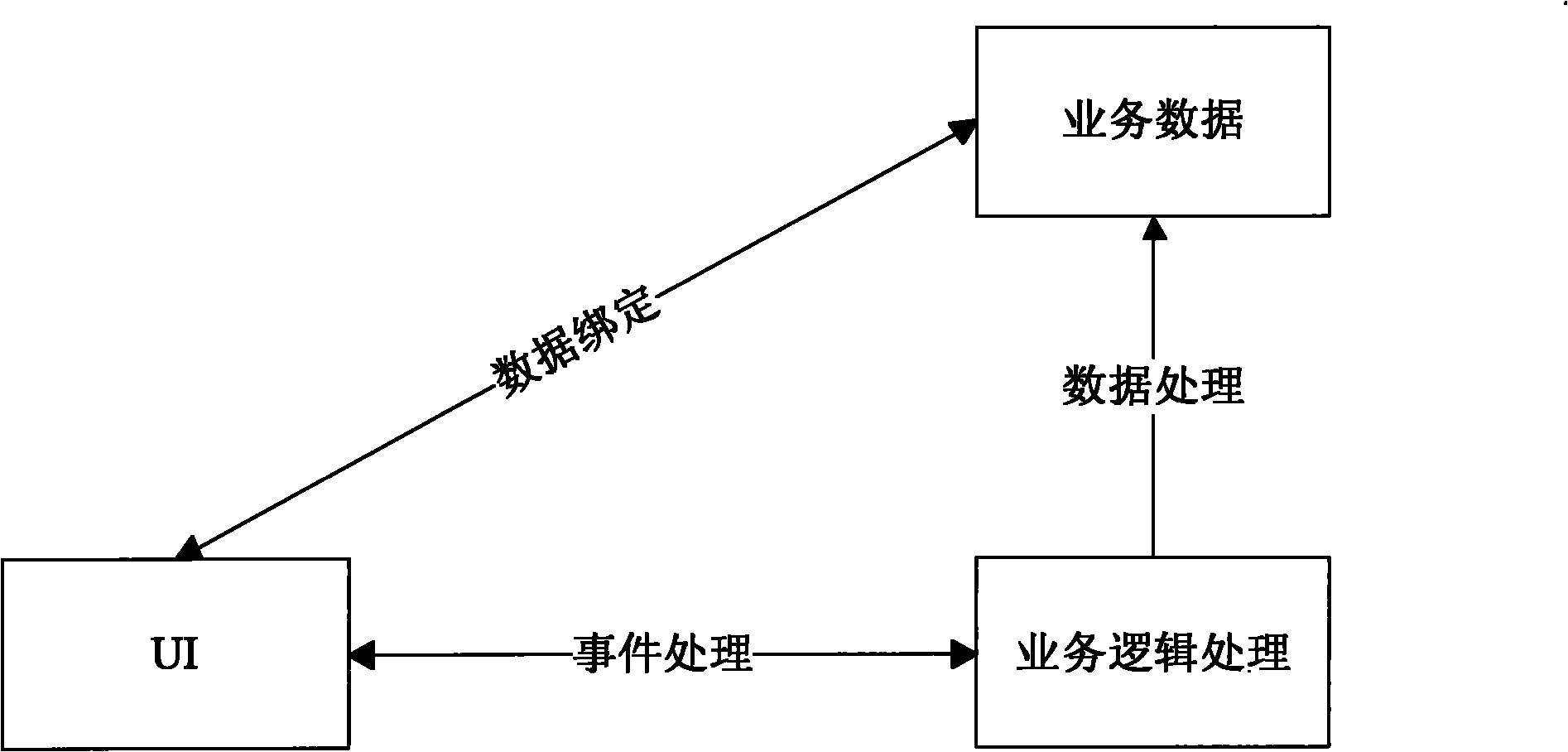
In computer programming, data binding is a general technique that binds data sources from the provider and consumer together and synchronizes them. This is usually done with two data/information sources with different languages as in XML data binding. In UI data binding, data and information objects of the same language but different logic function are bound together (e.g. Java UI elements to Java objects).
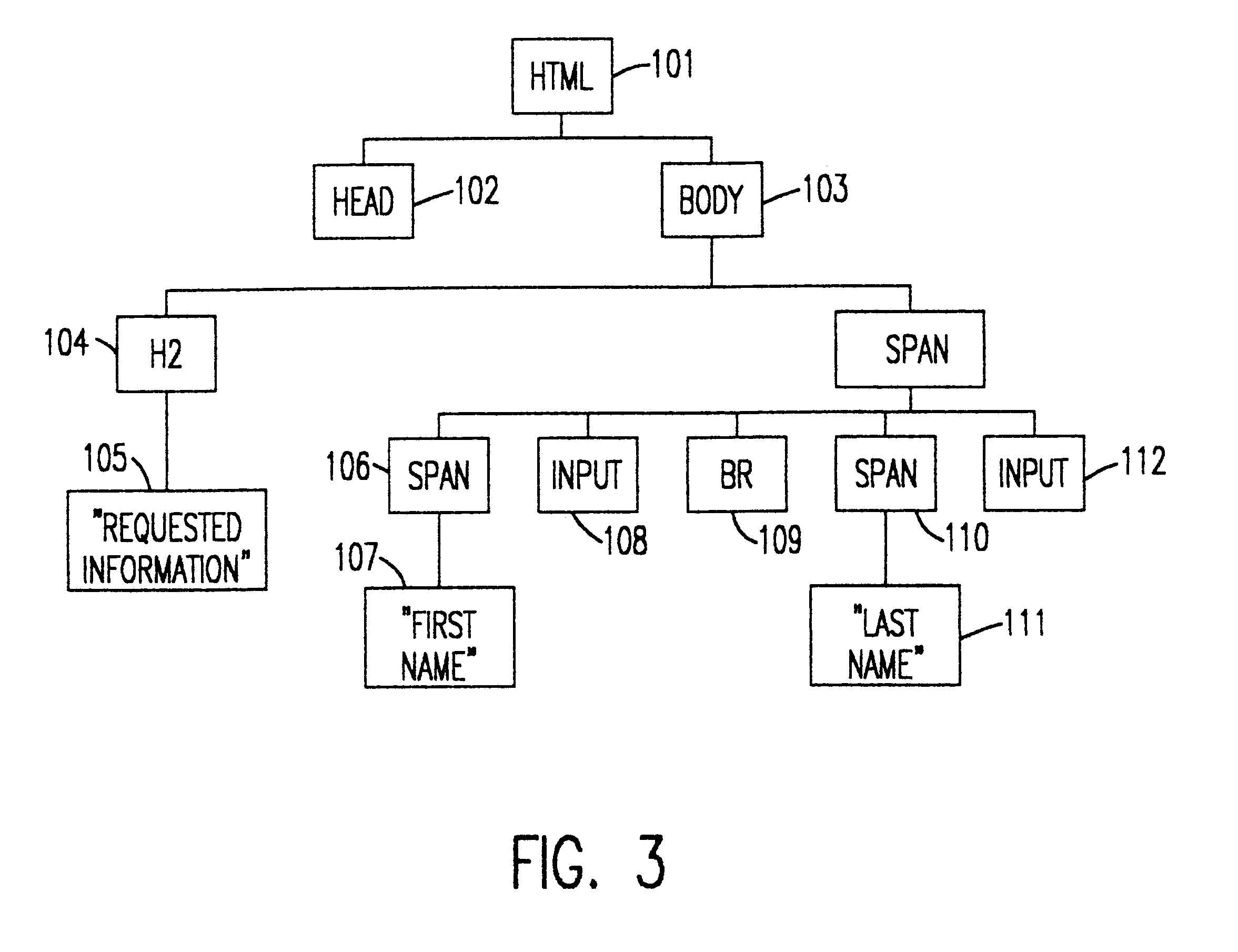
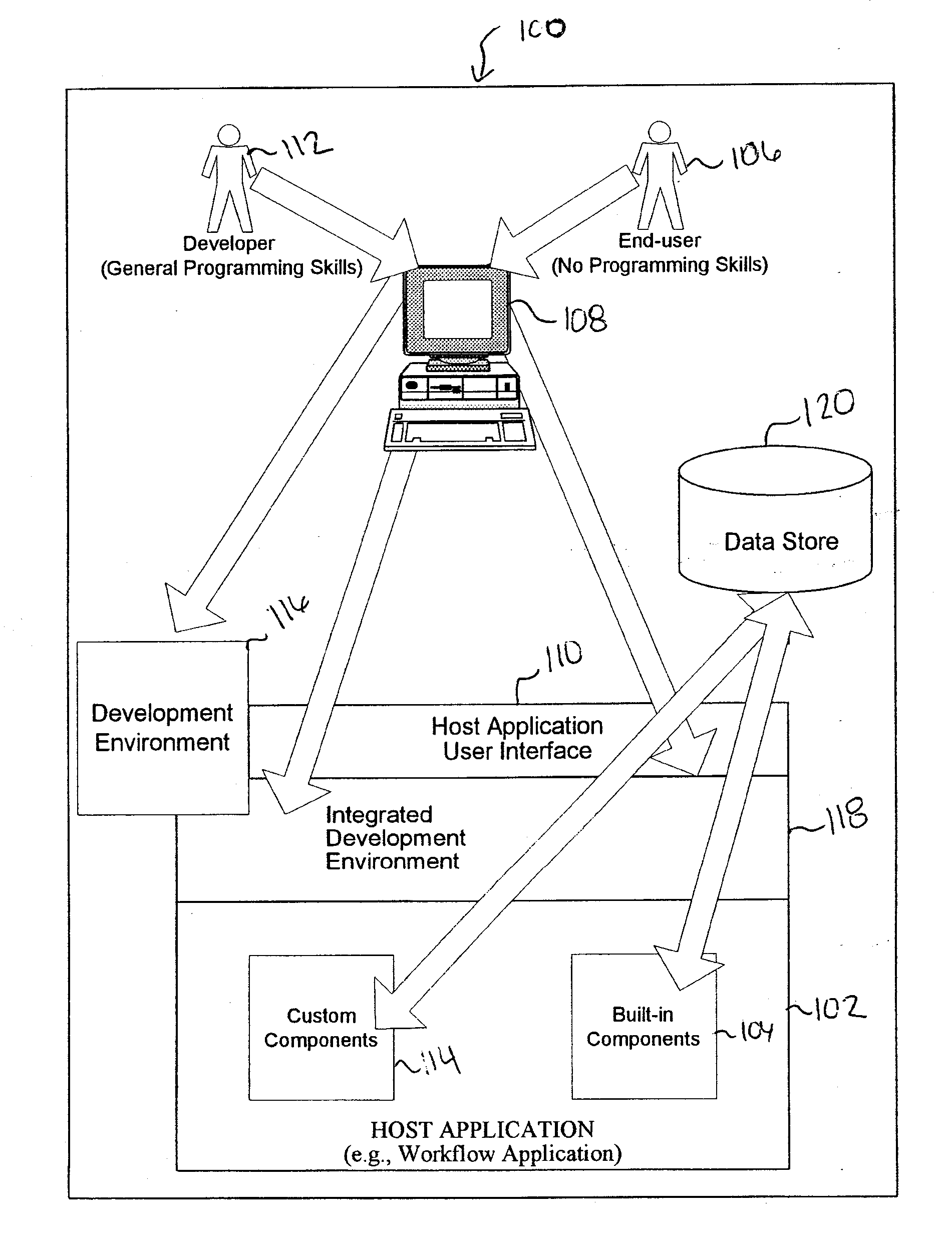
Architecture for creating a user interface using a data schema
InactiveUS20050172261A1Easy to createFast dataSoftware engineeringSpecific program execution arrangementsGraphicsDrag and drop
A rich user interface (UI) development framework that uses the schema of a data source to which it is relevant. The developer is able to rapidly create a data bound UI using a number of familiar gestures, including drag and drop, from the schema in a data tool window, using a designer tasks, or using a data form creation wizard. The system includes a UI generation component that allows a developer to input a number of different controls into the interface using associated control graphics. A data source object, type, or file can be passed to the UI generation component as an input. The developer chooses the desired controls and associates (or binds) the data entity of the data source with the control by any number of gestures.
Owner:MICROSOFT TECH LICENSING LLC
Hierarchical view of data binding between display elements that are organized in a hierarchical structure to a data store that is also organized in a hierarchical structure
InactiveUS6571253B1Increase powerDigital data information retrievalData processing applicationsApplication softwareDocument preparation
A Web browser is used as the rendering engine for the client application. The browser is instructed to load a "page" (some set of instructions that eventually resolves to a sequence of HTML (HyperText Markup Language) tags which instruct the browser regarding the number / nature and layout of the controls desired) which the browser parses to produce a set of controls with the indicated containment hierarchy. These controls may contain definitions of data stores (such as the support for an XML (eXtended Markup Language) tag which produces a W3C compliant DOM (Docunent Object Model) with built-in parsing for XML documents) which may either locally define their data or cause the browser to request the data from a server on the network. Preferably, the browser then passes control to a data binding agent which will examine the controls for specification of desired data binding(s).
Owner:IBM CORP
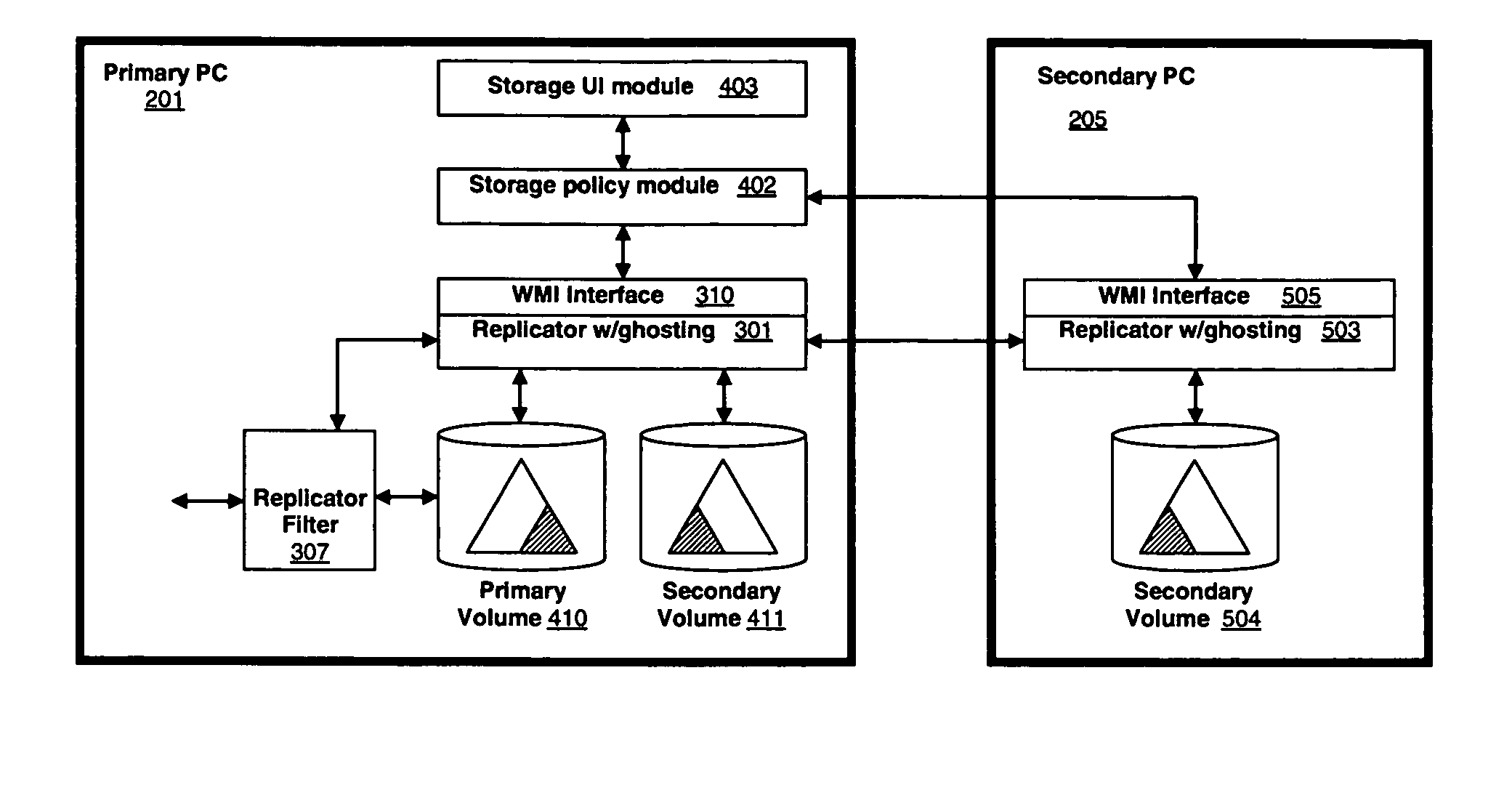
Virtually infinite reliable storage across multiple storage devices and storage services
InactiveUS20060230076A1Improve reliabilityImprove scalabilityError detection/correctionDigital data processing detailsFile systemDistributed File System
A logical file system is described that distributes copies of files across various different physical storage resources yet provides a consistent view to the user of his or her data, regardless of which machine the user is accessing the files from, and even when the user's computer is offline. The distributed file system uses smart data redundancy to enable a virtually infinite amount of storage as long as additional storage resources are made available to the distributed file system. The result is a reliable storage system that does not necessarily tie the user's data to the user's particular computer. Instead, the user's data is associated with the user—for life—or for however long the user would like the data to be maintained, regardless of whether the user's computer or data storage components are replaced or destroyed.
Owner:MICROSOFT TECH LICENSING LLC
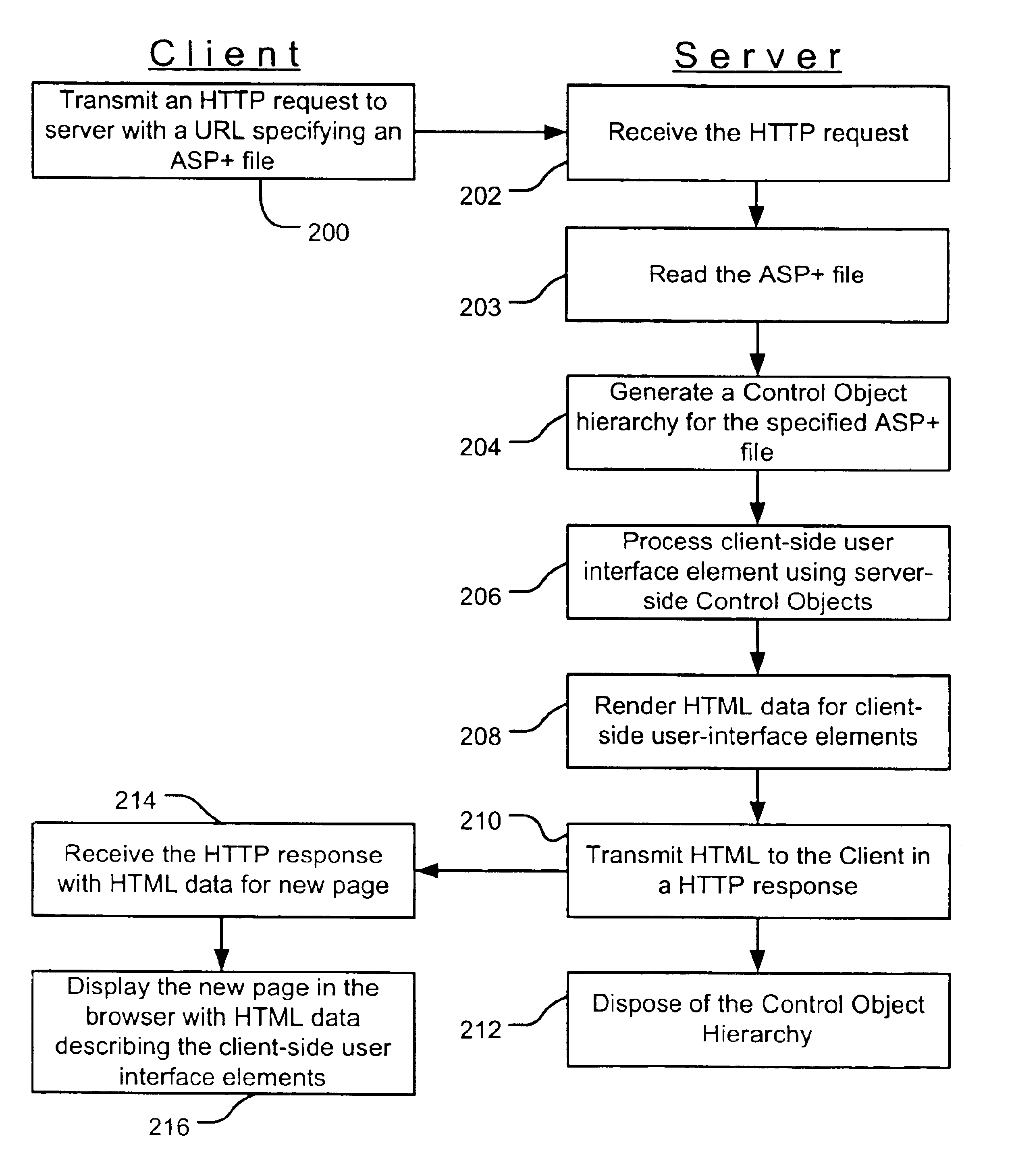
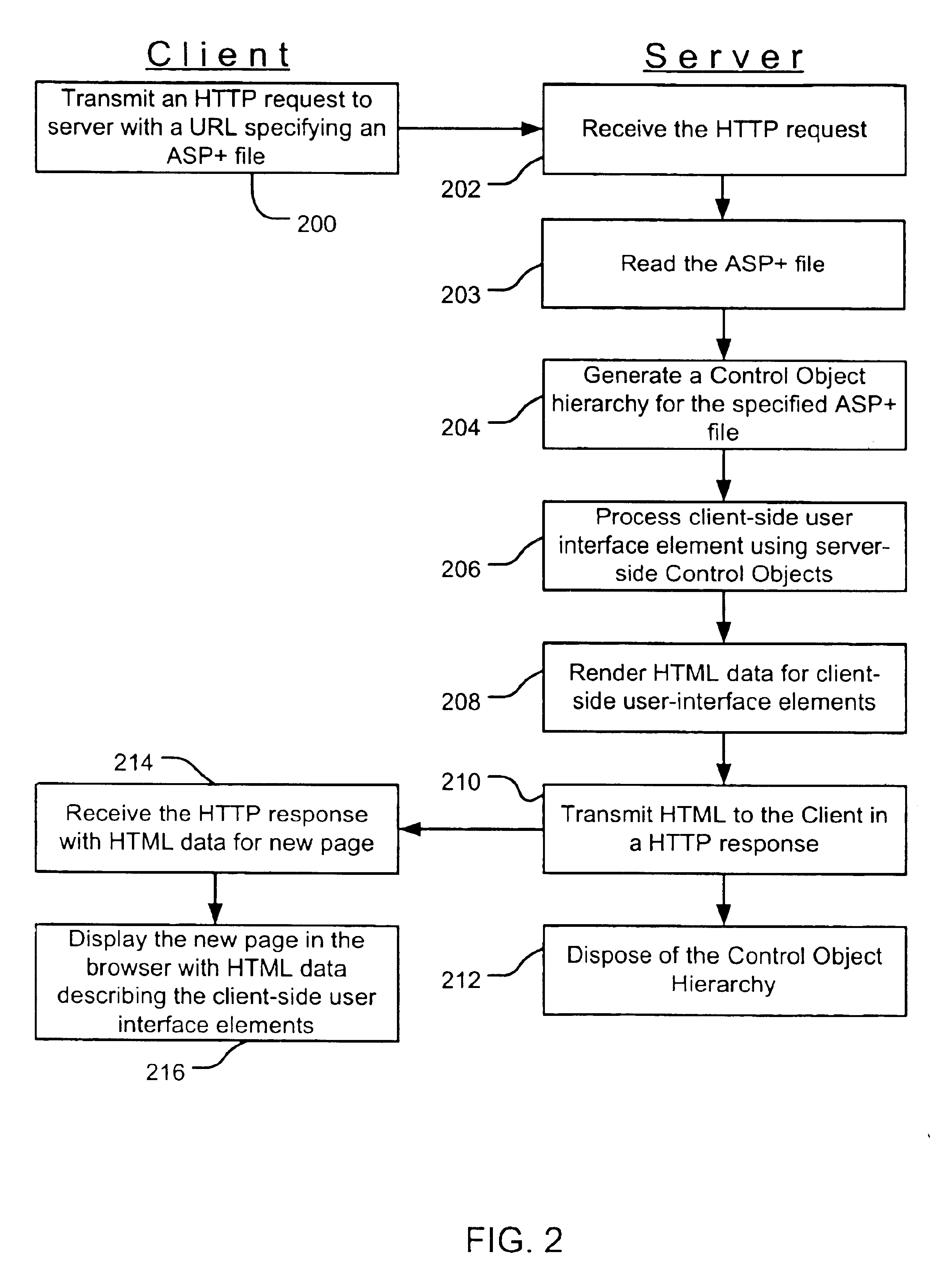
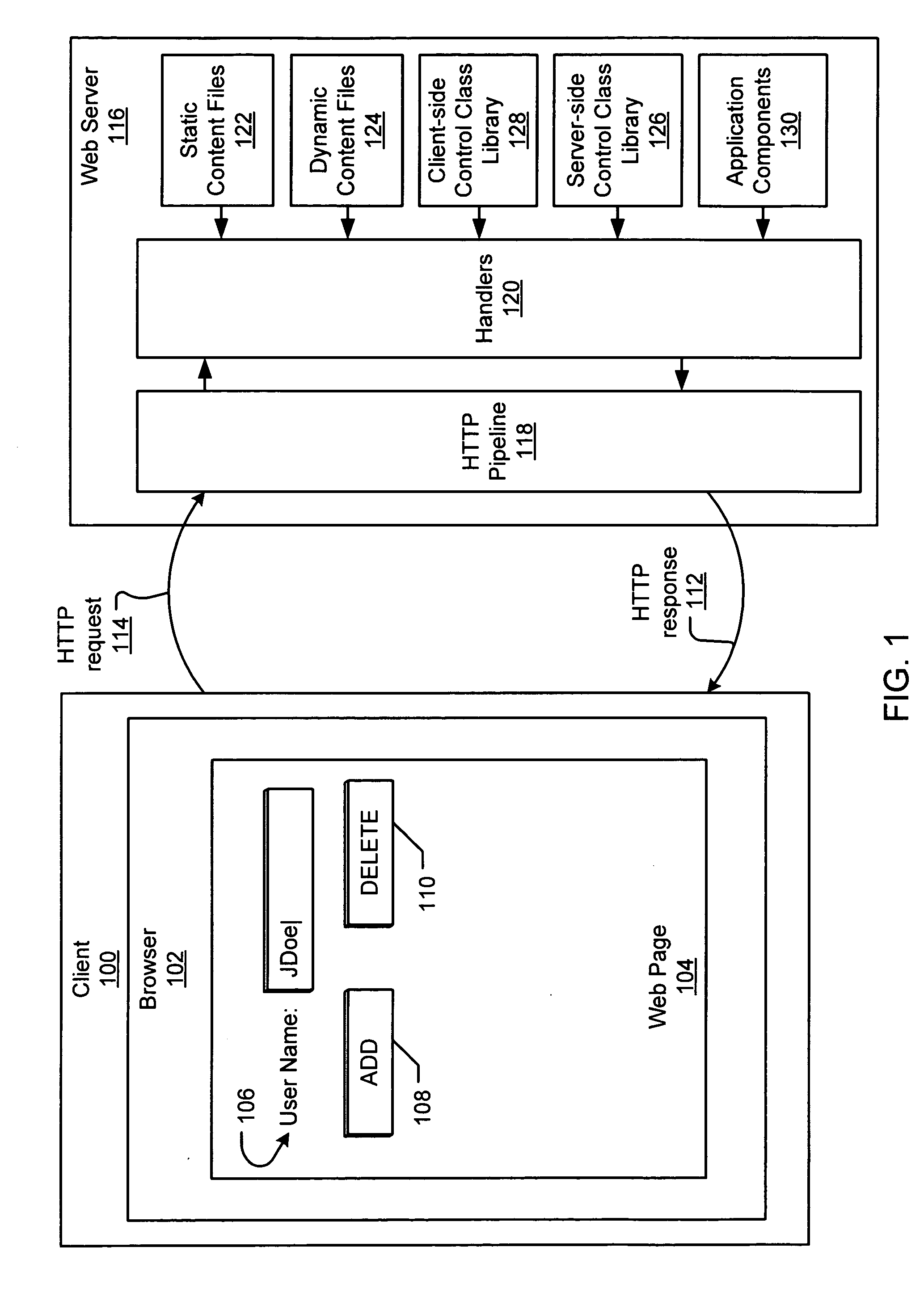
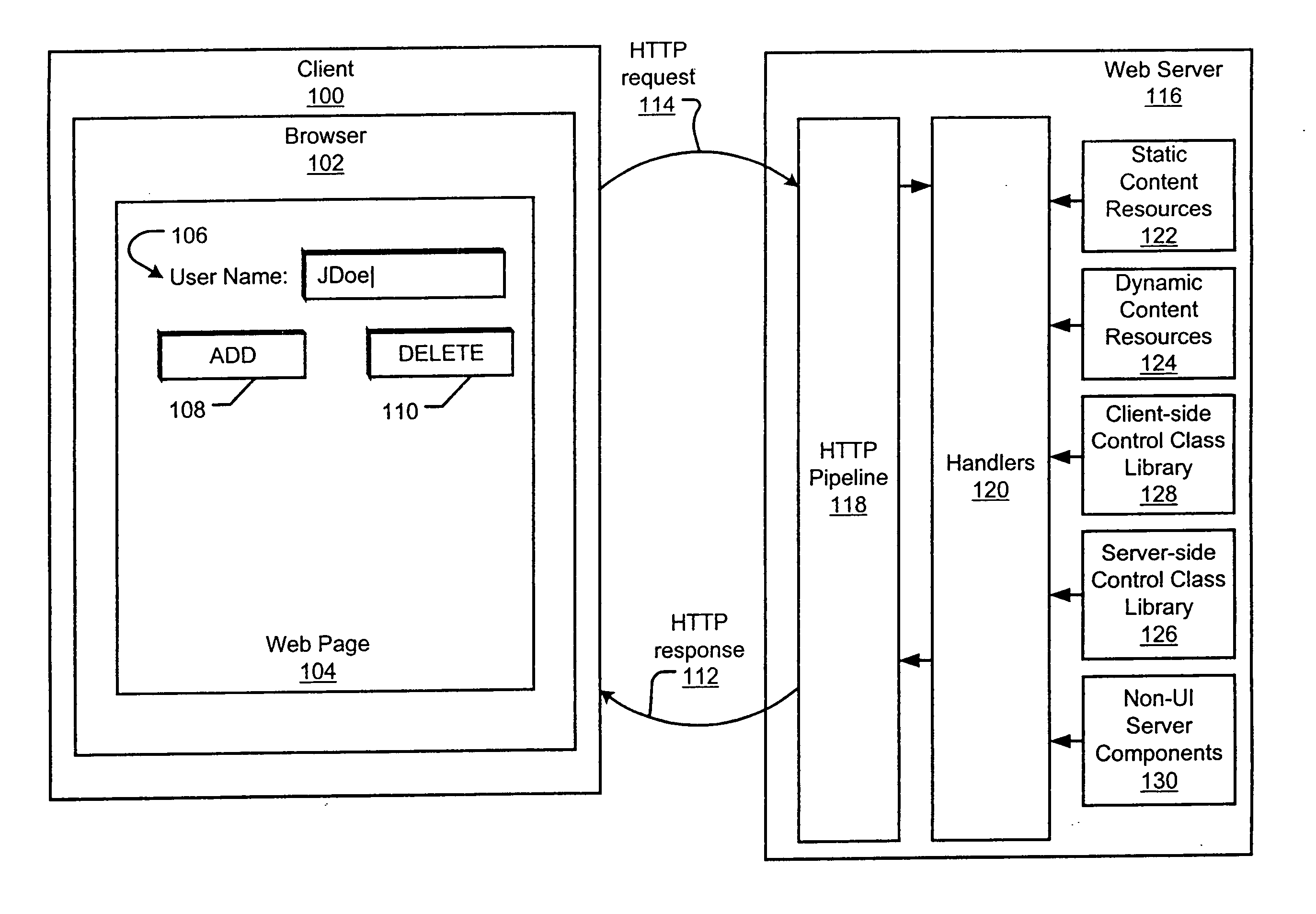
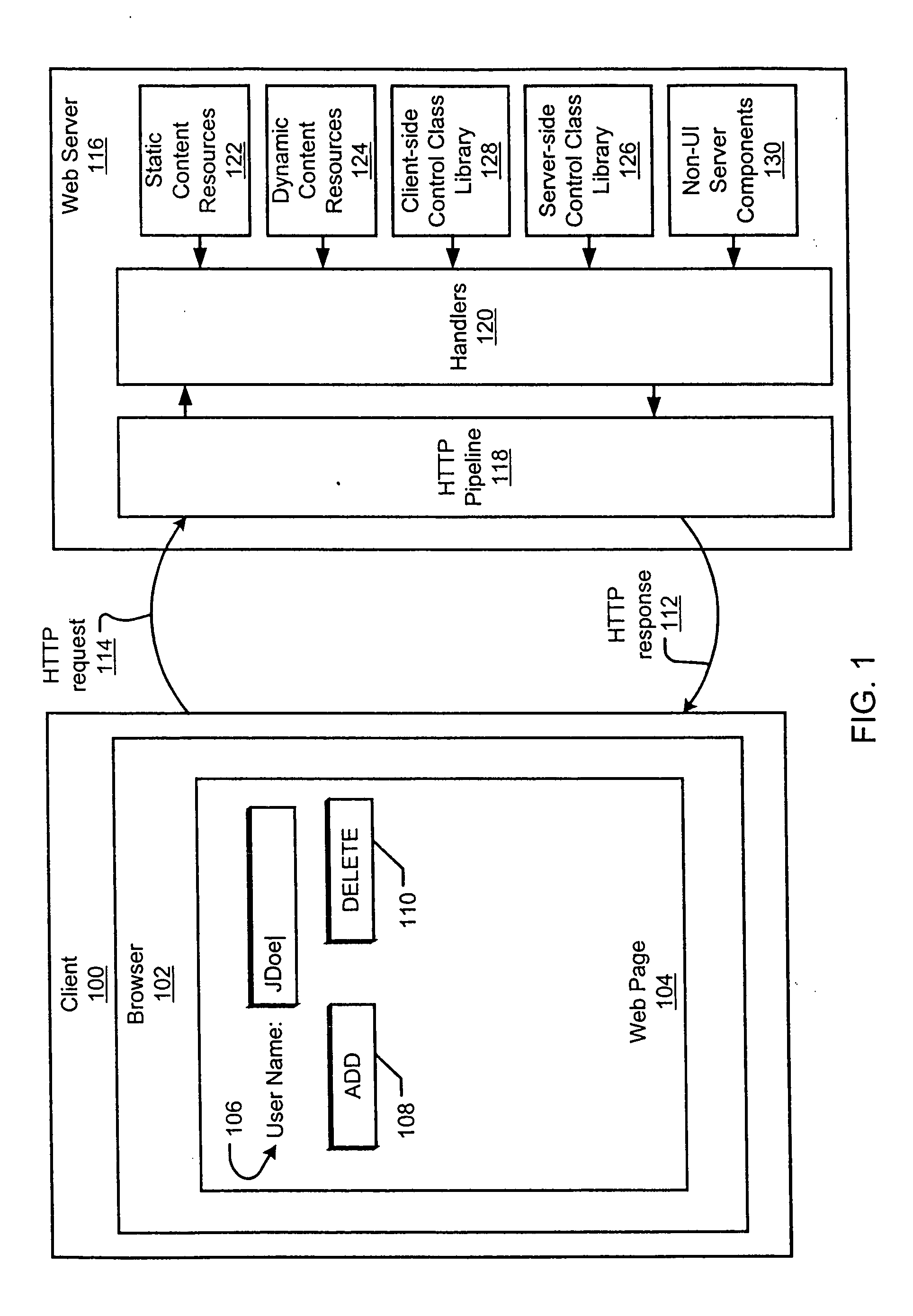
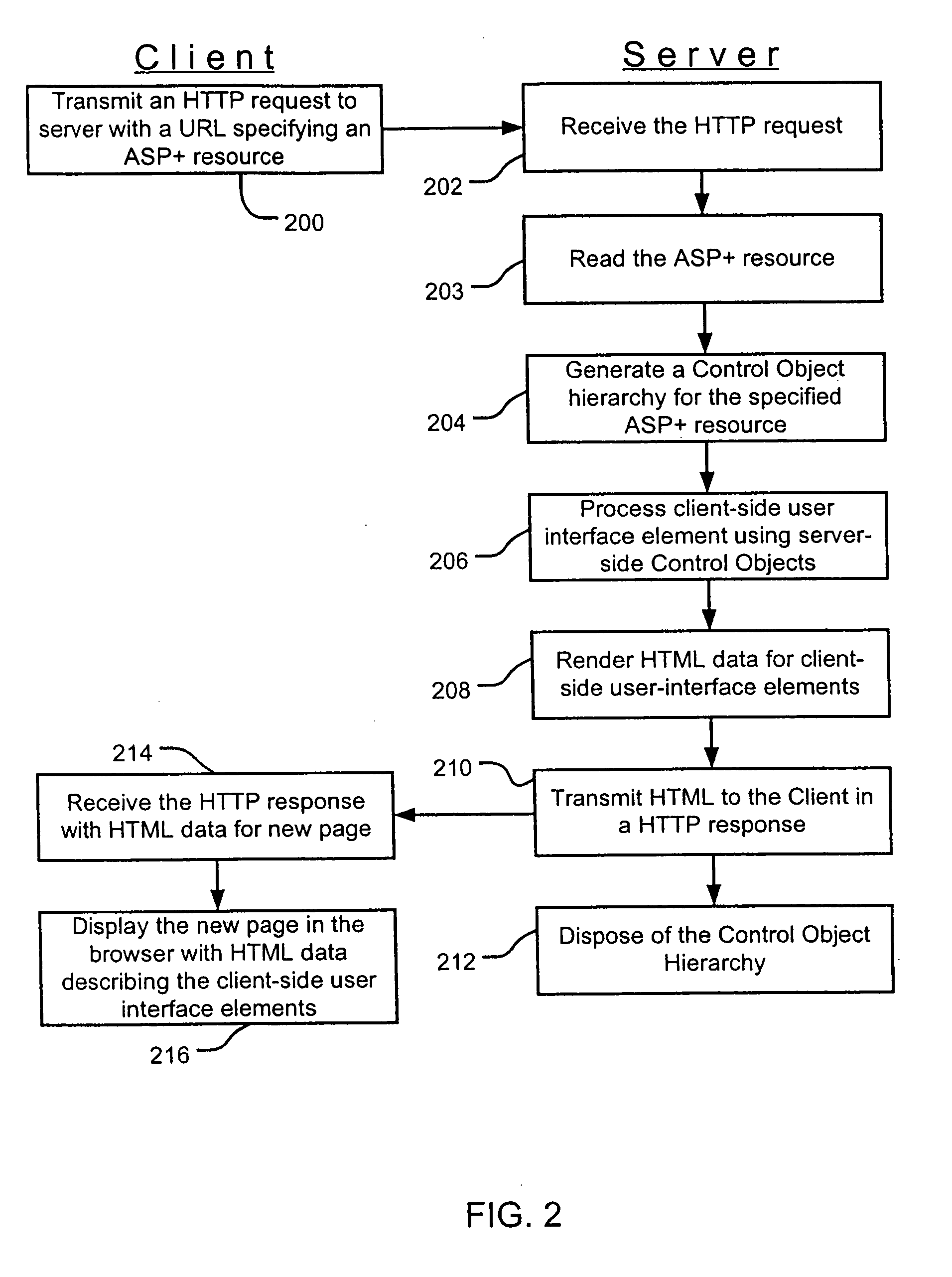
Server-side control objects for processing client-side user interface elements
InactiveUS6961750B1Easy to packMinimizing custom event handlingMultiple digital computer combinationsExecution for user interfacesState managementClient-side
A server-side control object processes and generates a client-side user interface element for display on a web page. Multiple server-side control objects may be combined into a hierarchy of server-side control objects that cooperate to generate the resulting authoring language code, such as HTML, for display of a web page on a client. The operation of processing the client-side user interface element may include at least one of an event handling operation, a postback data handling operation, a data binding operation, and a state management operation. The state management operation relates to the state of a server-side control object.
Owner:MICROSOFT TECH LICENSING LLC
Web-based cross-platform wireless device application creation and management systems, and methods therefor
InactiveUS20120036494A1Efficient and inexpensive processEasy to createMultiple digital computer combinationsSpecific program execution arrangementsTablet computerHabit
The smart phone and tablet applications are akin to news and media websites available on the Internet in that the applications provide the latest content, richest media experience and an evolving community around the brand. The disclosure provides an efficient and inexpensive process and system for creating and managing of software applications for multiple smart phone and tablet platforms via an online platform. The systems and processes facilitate creation of applications, which communicate with a workflow implemented and powered by an online server. The systems also provides a feed server system that continuously fetches content from various feed sources, aggregates content, and maps into a local data model that can be defined dynamically. The applications are containers that request content from the served based on a token that is preinstalled into the application. The containers are built with the mechanism to bind data to layouts dynamically using the scripting code downloaded from an online server. The data, layouts and code can all be changed by the app creator on the fly. Based on the specifications of the device making the request, the token content is preprocessed and served to the application in the correct format for the receiving device. The apps combined with the online app server also provide mechanism to gather analytics about content consumptions habits, location analytics, and application usage patterns all of which could be used to curate content to be served back to the app users.
Owner:GENWI
Usage semantics
InactiveUS6839062B2Improve the level ofFlexible workflowData processing applicationsImage data processing detailsData streamData set
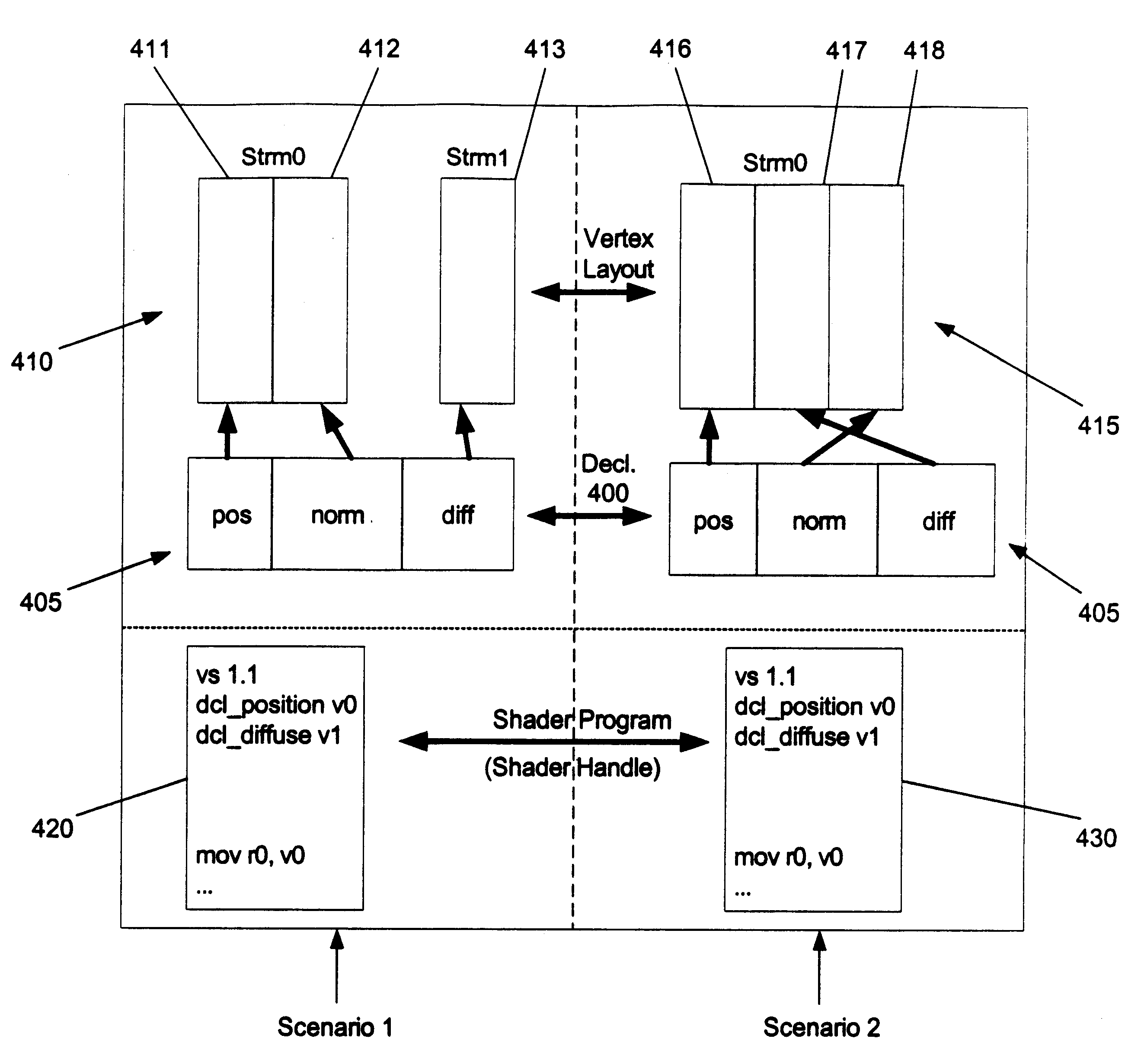
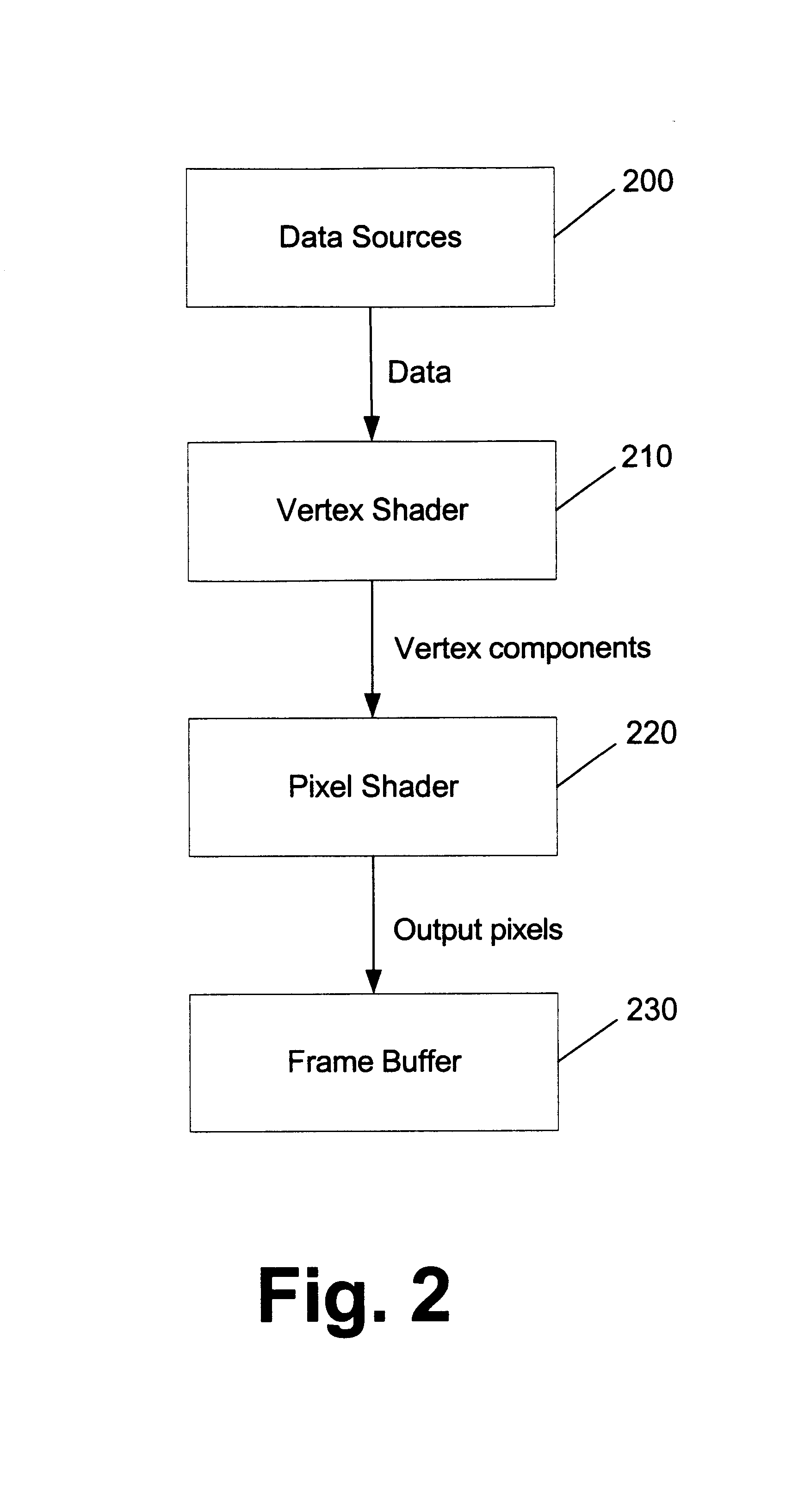
Usage semantics allow for shaders to be authored independently of the actual vertex data and accordingly enables their reuse. Usage semantics define a feature that binds data between distinct components to allow them to work together. In various embodiments, the components include high level language variables that are bound by an application or by vertex data streams, high level language fragments to enable several fragments to be developed separately and compiled at a later time together to form a single shader, assembly language variables that get bound to vertex data streams, and parameters between vertex and pixel shaders. This allows developers to be able to program the shaders in the assembly and high level language with variables that refer to names rather than registers. By allowing this decoupling of registers from the language, developers can work on the language separately from the vertex data and modify and enhance high level language shaders without having to manually manipulate the registers. This also allows the same shaders to work on different sets of mesh data, allowing the shaders to be reused. Generally, semantics can be used as a data binding protocol between distinct areas of the programmable pipeline to allow for a more flexible workflow.
Owner:MICROSOFT TECH LICENSING LLC
Security features in on-line and off-line delivery of applications
InactiveUS20050091534A1Reduce usageDigital data processing detailsHardware monitoringOnline and offlineClient-side
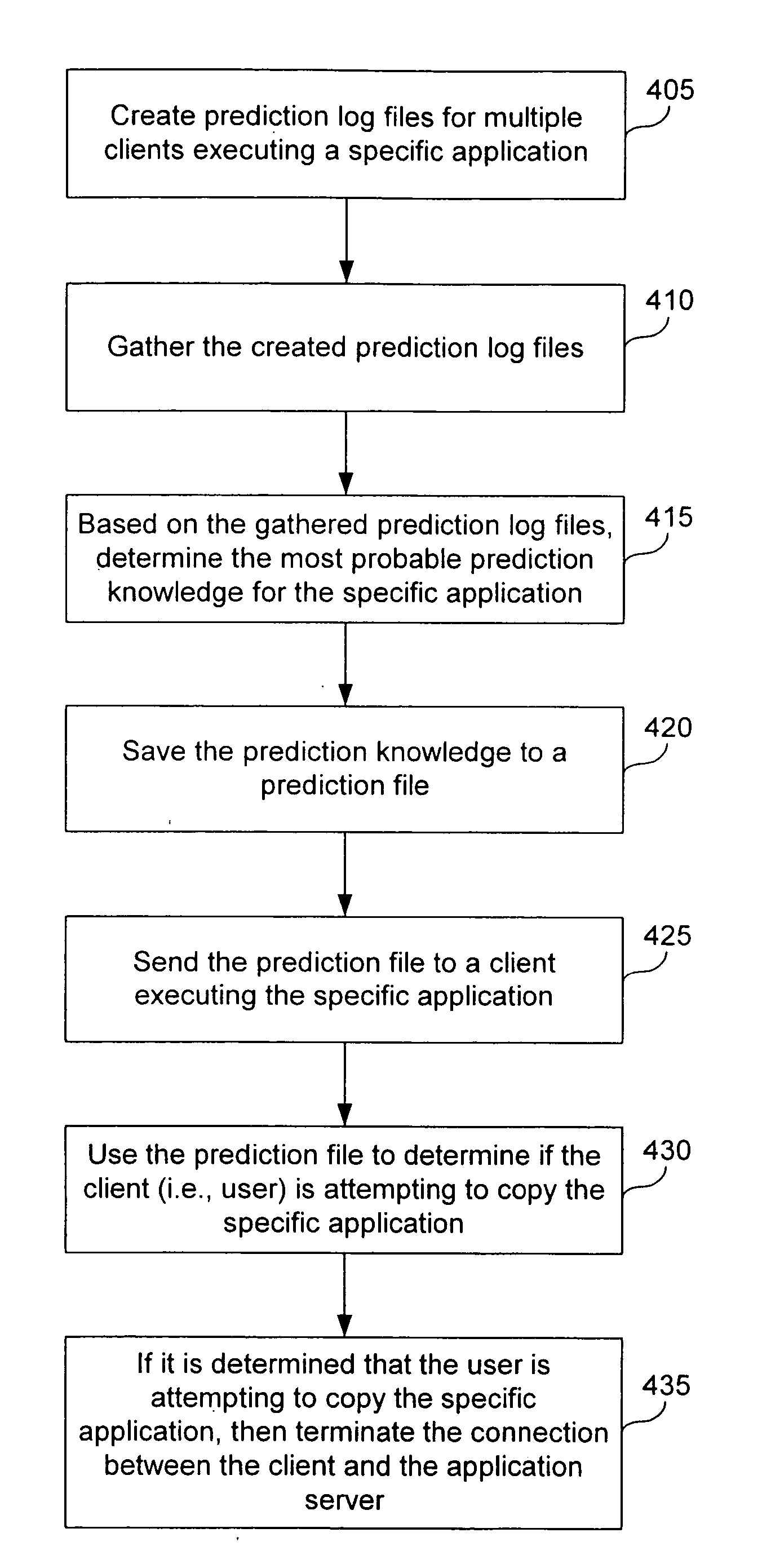
A method and system for determining whether a client is attempting to copy an application or use the application without authorization. First, data for at least one prediction log file for the application is created. Then, based on the at least one prediction log file, prediction knowledge is determined for the application, where the prediction knowledge is stored in a prediction file. The prediction file is then forwarded to the client executing the application. It is then determined by using the predication file whether the client is attempting to copy the application or use the application without authorization. If the client is attempting to copy the application or use the application without authorization, then the client's access to the application is terminated. In an offline mode, usage information is bound to user saved data such that modification of usage information renders user saved data unusable. This prevents unauthorized access to an offline delivered application.
Owner:EXENT TECH
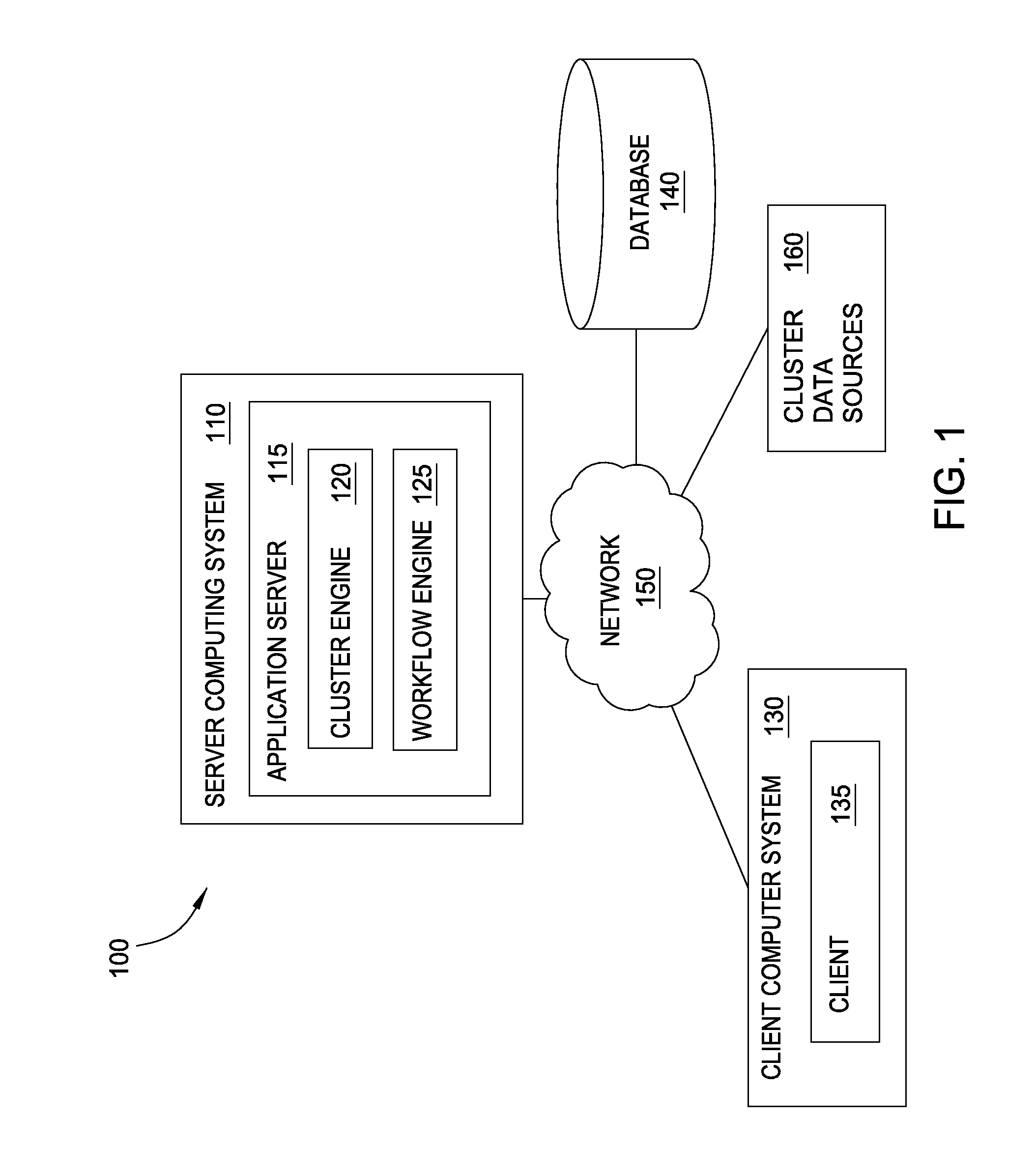
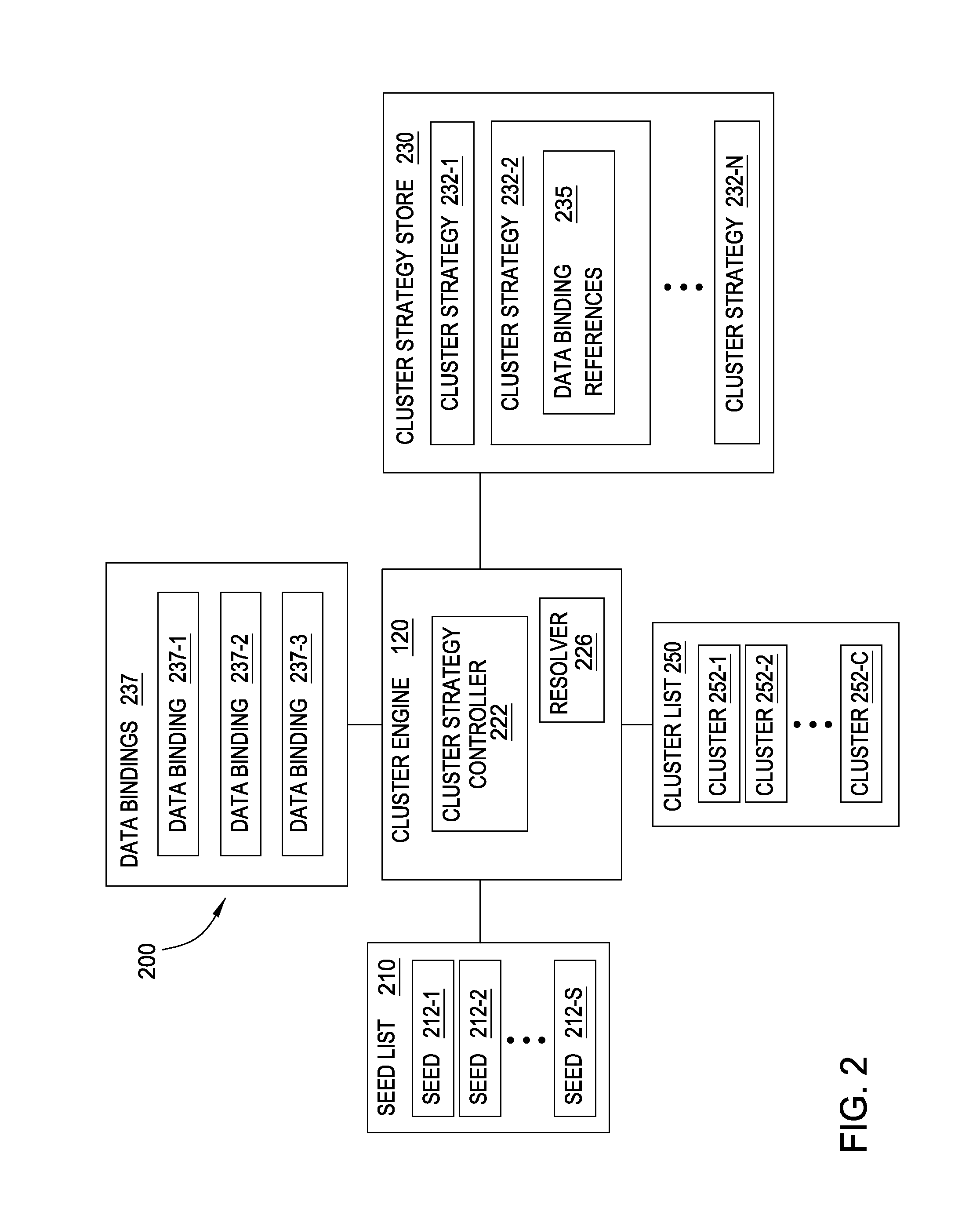
Generating data clusters with customizable analysis strategies
ActiveUS8788405B1Effective starting pointReduce the amount requiredDatabase updatingFinanceSearch protocolAnalytical strategy
Techniques are disclosed for generating a collection of clusters of related data from a seed. Doing so may generally include retrieving a seed and adding the seed to a first cluster and include retrieving a cluster strategy referencing one or more data bindings. Each data binding specifies a search protocol for retrieving data. For each of the one or more data bindings, data parameters input to the search protocol are identified, the search protocol is performed using the identified data parameters, and data returned by the search protocol is evaluated for inclusion in the first cluster.
Owner:PALANTIR TECHNOLOGIES
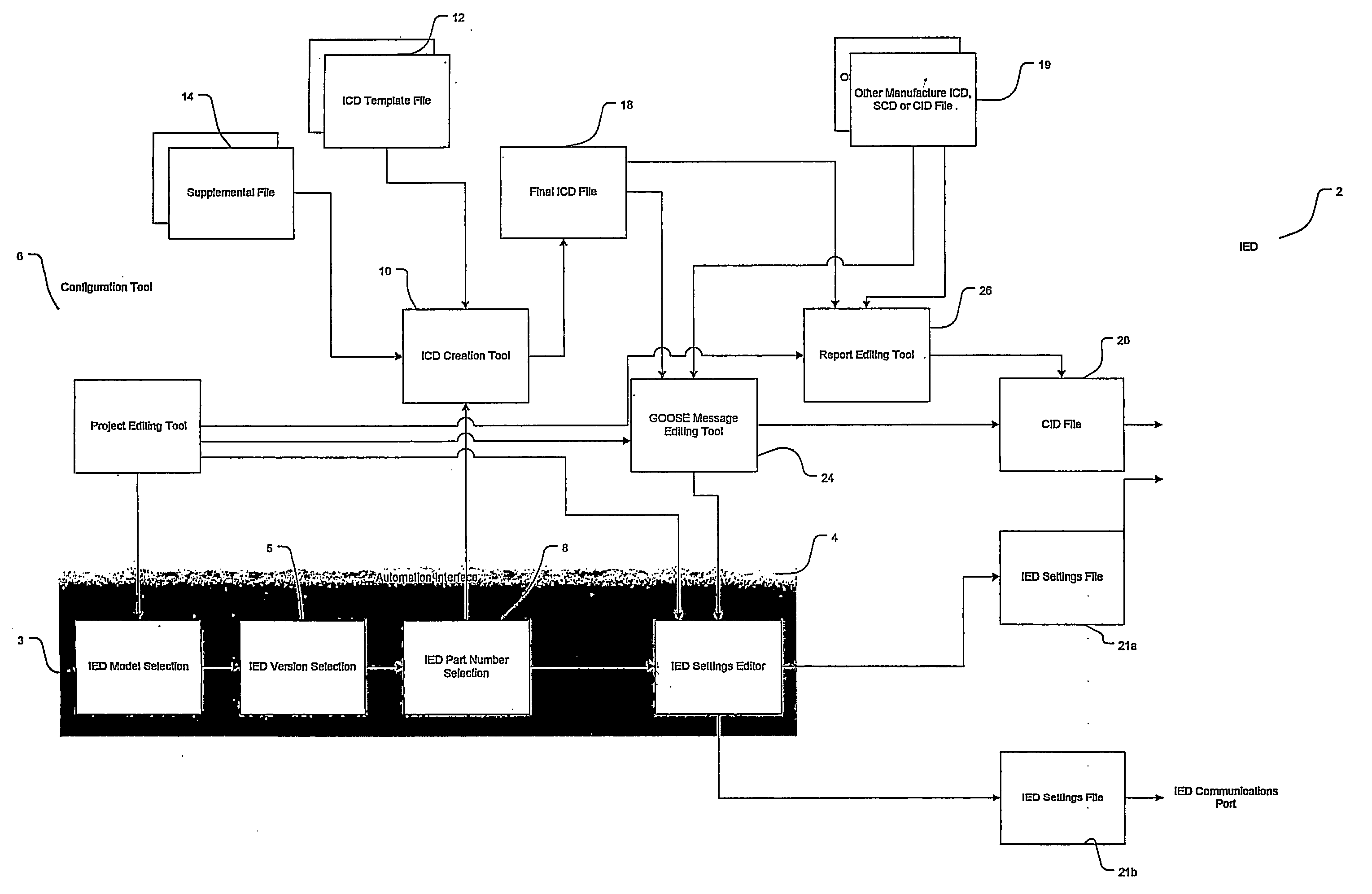
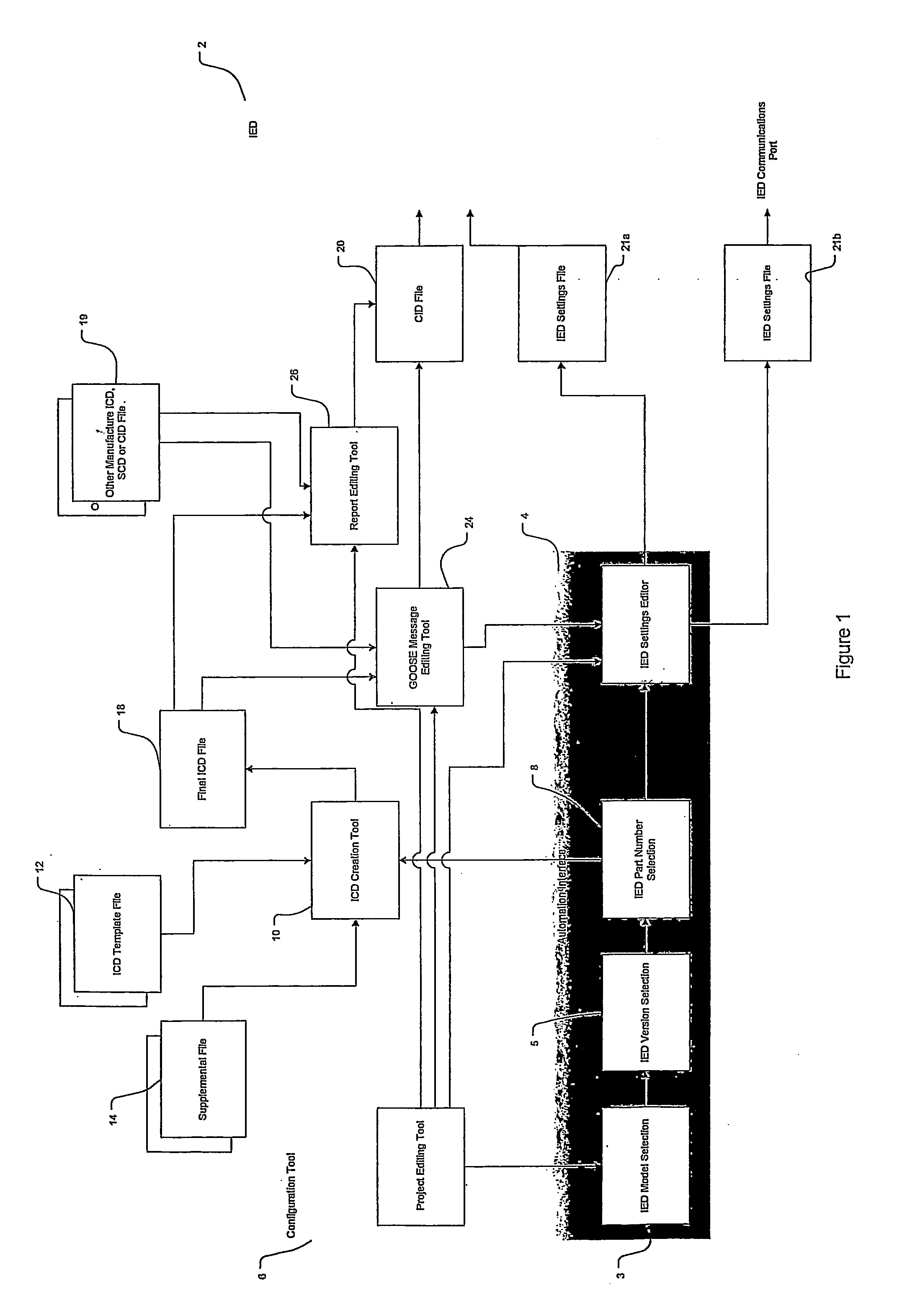
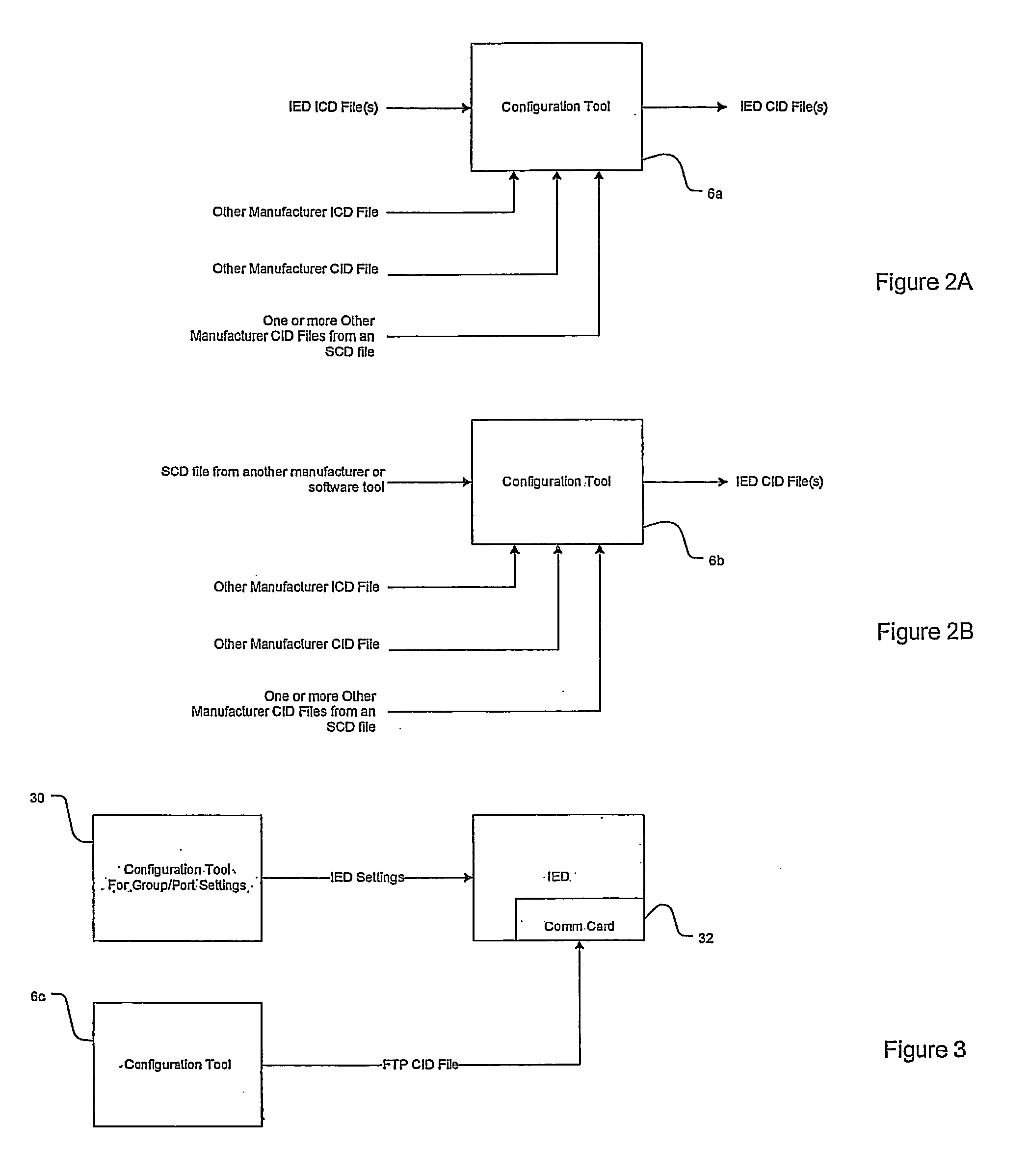
Method of configuring intelligent electronic devices to facilitate standardized communication messages among a plurality of ieds within a network
ActiveUS20080127210A1Optimizing file spaceImprove execution speedCircuit arrangementsTransmissionElectric power systemDynamic data
Provided is a system and method of configuring IEDs to facilitate standardized communication messages among a plurality of IEDs within a power system network based on the IEC 61850 standard. A description file is described for an intelligent electronic device configured in accordance with the IEC-61850 standard. The description file includes a section which indicates which GOOSE message the intelligent electronic device should receive. In yet another embodiment, the description file includes a section which is capable of linking to logic functions of the intelligent electronic device for performing programmable data binding or dynamic data binding. A configuration tool is further provided for editing and creating such description files. A method for selectively receiving messages from an intelligent electronic device configured in accordance with the IEC-61850 standard is also described herein, along with a method for optimizing file space and improving execution speed of an intelligent electronic device configured in accordance with the IEC-61850 standard.
Owner:SCHWEITZER ENGINEERING LABORATORIES
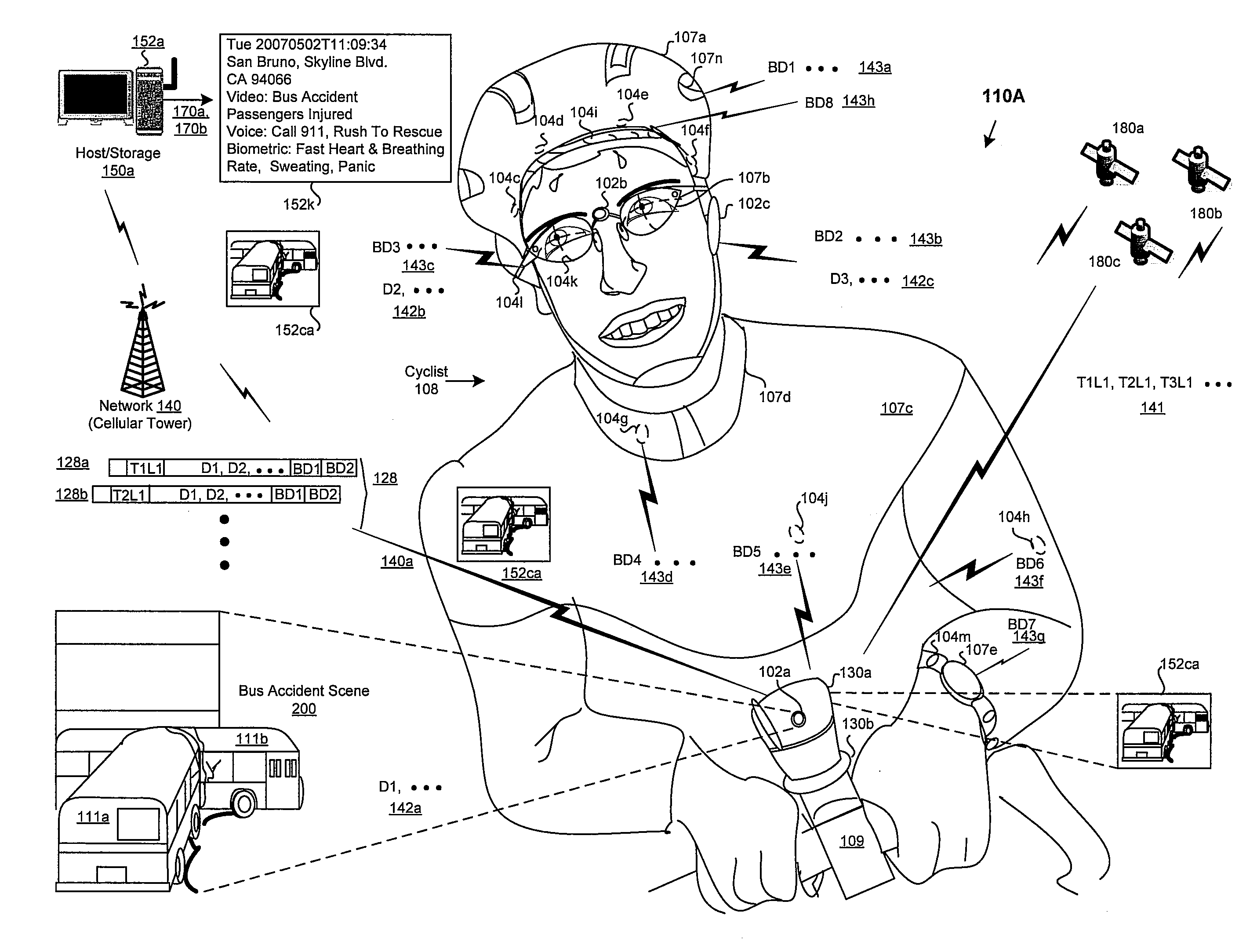
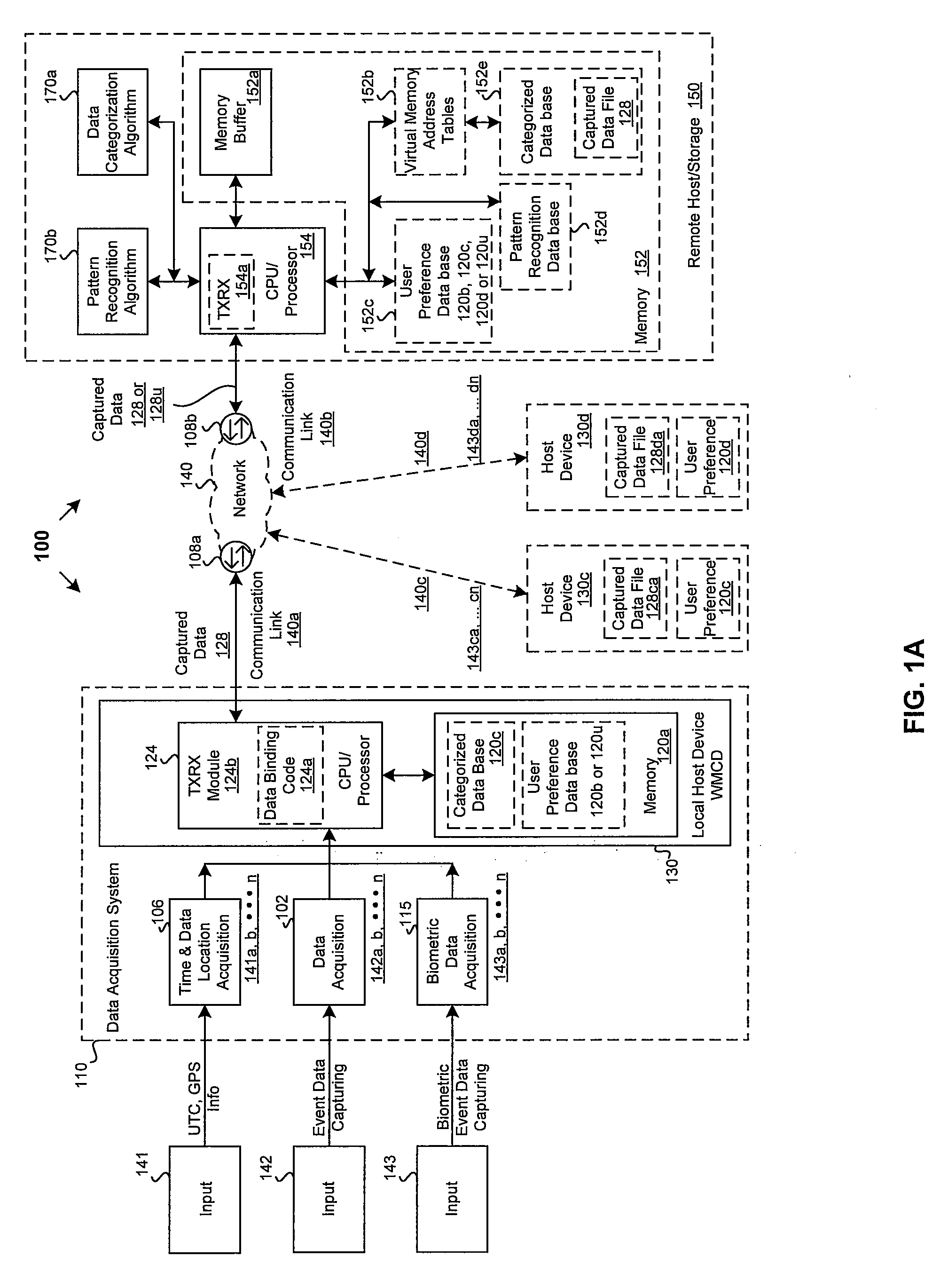
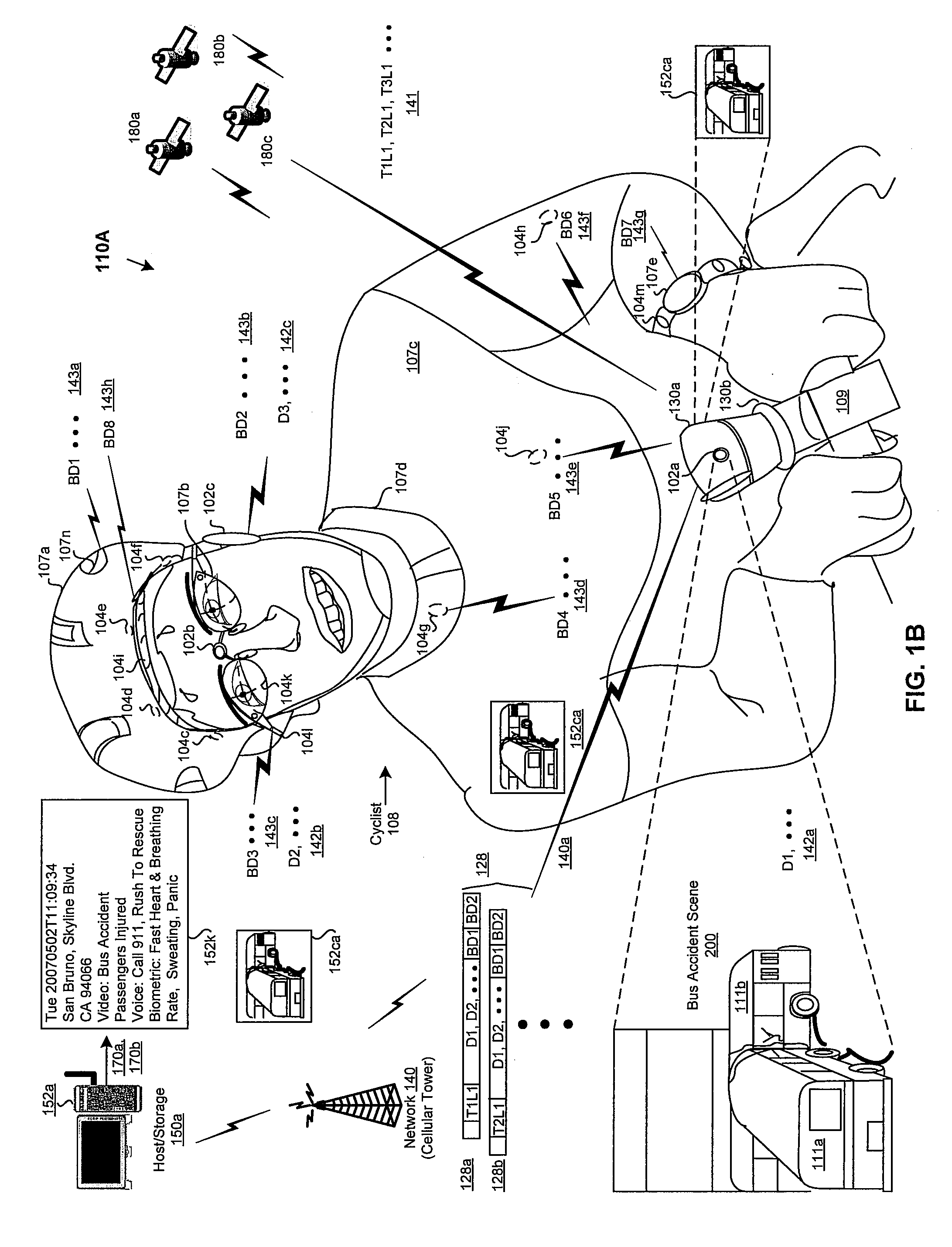
Method and system for processing information based on detected biometric event data
ActiveUS20090023422A1Bioelectric signal measurementUnauthorised/fraudulent call preventionData acquisitionEvent data
A system and method is provided for processing and storing captured data in a wireless communication device based on detected biometric event data. The captured data may be acquired through a data acquisition system with devices or sensors in an integrated or distributed configuration. The captured data may include multimedia data of an event with time, date and / or location stamping, and captured physiological and behavioral biometric event data in response to the event. The captured data may be dynamically stored in a data binding format or as raw data in a local host device or communicated externally to be stored in a remote host or storage. At least one user preference may be specified for linking a biometric event data to the mapped, analyzed, categorized and stored captured data in a database. Captured data may be retrieved by matching biometric event data to at least one user preference from the database.
Owner:AVAGO TECH INT SALES PTE LTD
Server-side control objects for processing client-side user interface elements
InactiveUS20050050164A1Easy to packMinimizing custom event handlingMultiple digital computer combinationsExecution for user interfacesState managementClient-side
A server-side control object processes and generates a client-side user interface element for display on a web page. Multiple server-side control objects may be combined into a hierarchy of server-side control objects that cooperate to generate the resulting authoring language code, such as HTML, for display of a web page on a client. The operation of processing the client-side user interface element may include at least one of an event handling operation, a postback data handling operation, a data binding operation, and a state management operation. The state management operation relates to the state of a server-side control object.
Owner:MICROSOFT TECH LICENSING LLC
Postback input handling by server-side control objects
InactiveUS20060004910A1Multiprogramming arrangementsMultiple digital computer combinationsState managementClient-side
One or more server-side control objects provide server-side processing of postback input received from client-side user interface elements in a request from a client. Such input may include without limitation postback data and postback events generated from a web page on a client and received by a server in an HTTP request. A hierarchy of server-side control objects can cooperate to process the postback input and to generate the resulting authoring language code, such as HTML. Server-side events can also result from the server-side processing of postback input. In addition to processing postback input, server-side processing may include, without limitation, state management of server-side control objects and binding data to and from server-side database. After the processing and generating operations, the server-side control object hierarchy is terminated until a subsequent request is received from the client.
Owner:MICROSOFT TECH LICENSING LLC
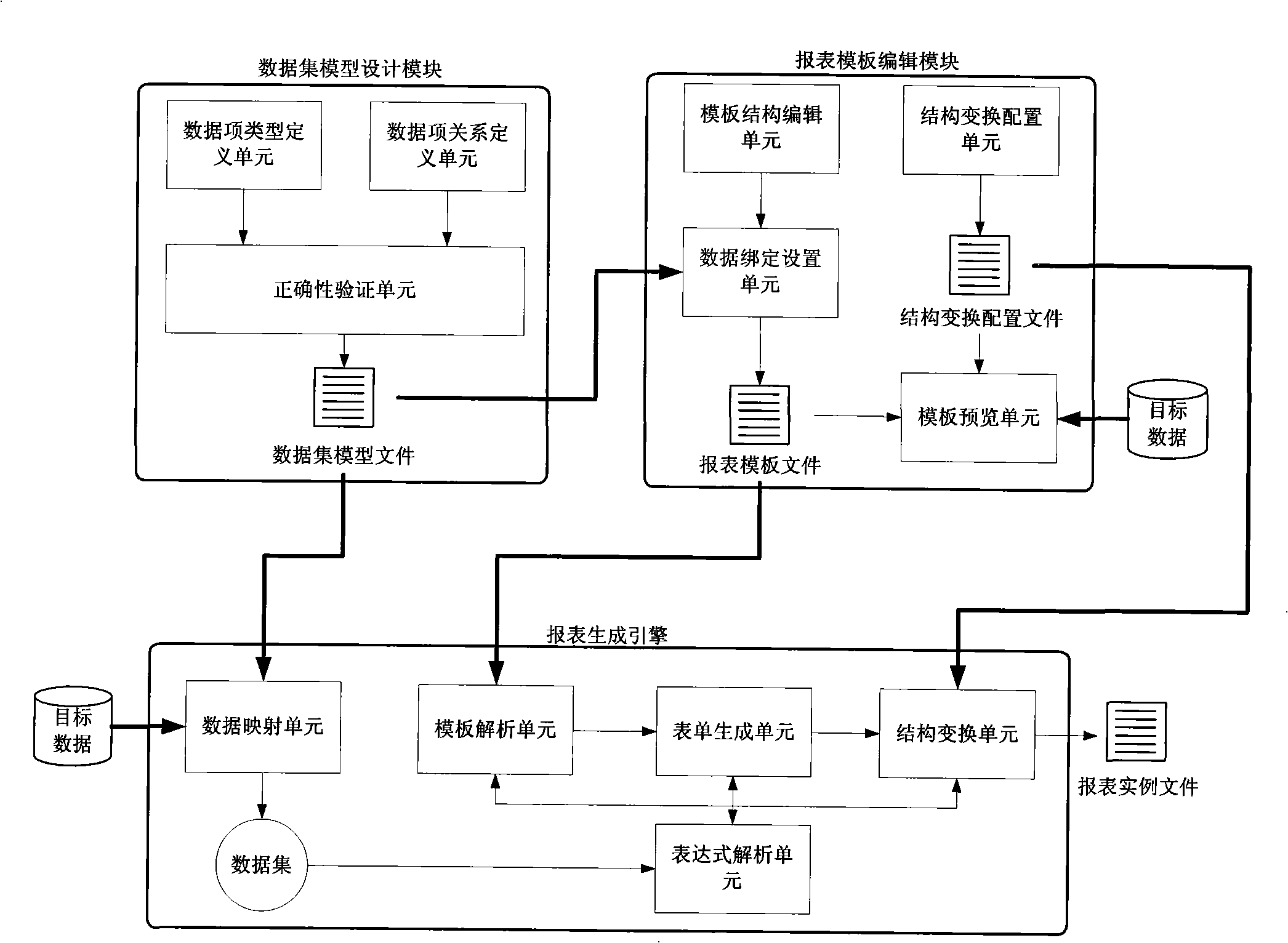
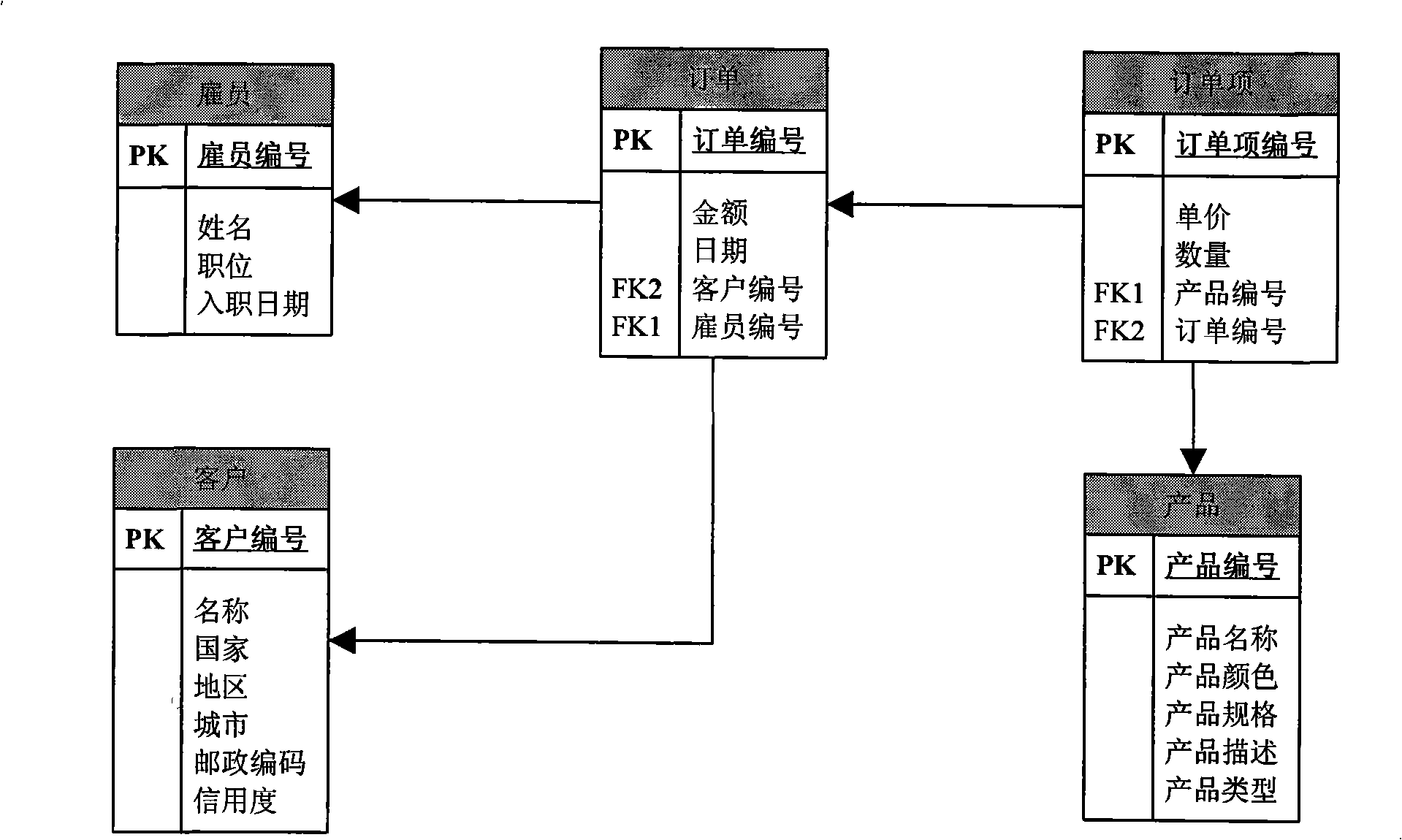
Dynamic report generation method and platform
InactiveCN101308490AEasy to customizePromote generationSpecial data processing applicationsData displayData set
The invention provides a dynamic report generation method and a platform; a data set model defined by business characteristics is used to organize data, extract data model definition, bind data based on the data set model, configure the transformation rules of the report structure, and automatically generate a report instance through a report generator engine, so as to form a report generation method. Data items are organized through the derived relation and the extended relation among the data items; the property of the data items which need to be bound into a report template is designated through path expression when the data is bound. The changes possibly generated during the report structure generation are defined; the report generator engine adjusts the report structure based on the structural transformation rules; as long as new structural transformation rules are added, new data display ways can be added without recoding so as to improve the expansibility of the system. Therefore, the user can adopt different display ways based on the characteristics of different data to enhance the expression ability of the report.
Owner:BEIHANG UNIV
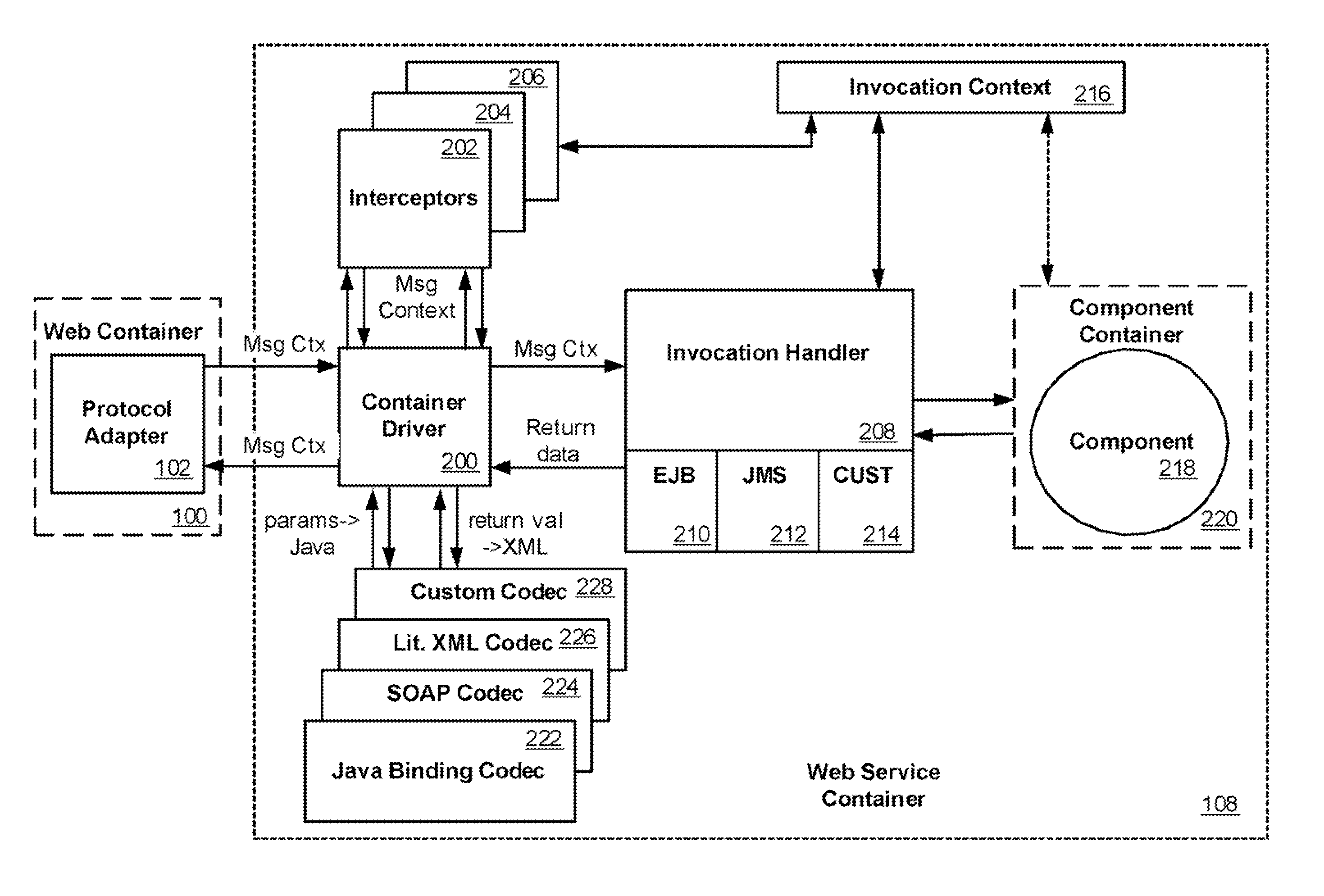
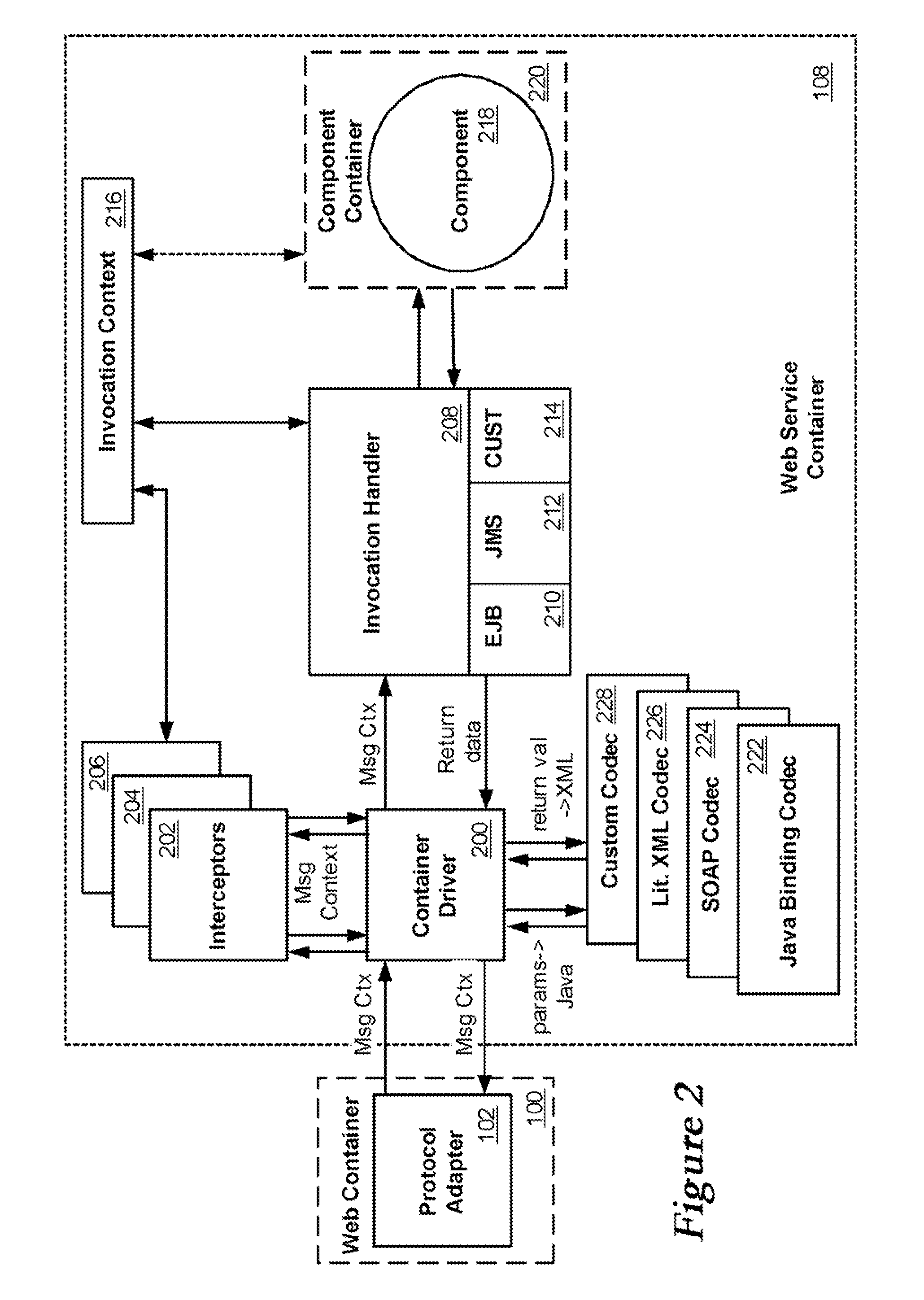
Web services runtime architecture
InactiveUS20070150546A1Multiple digital computer combinationsProgram controlWeb serviceComputer compatibility
A runtime architecture for Web services utilizes a container driver to accept an invoke request for Web services. The container driver performs any necessary data binding / unbinding required to process the invoke request and associated message context, utilizing an appropriate plugin component. An interceptor receives the context information and modifies the message context for Web service compatibility. An invocation handler receives the formatted context information and passes parameters from the message context to the target of the request. The invocation handler processes values returned from the target and passes them to the container driver, which can formulate and return a response, along with the message context, to the client or protocol adapter. This description is not intended to be a complete description of, or limit the scope of, the invention. Other features, aspects, and objects of the invention can be obtained from a review of the specification, the figures, and the claims.
Owner:BEA SYST INC
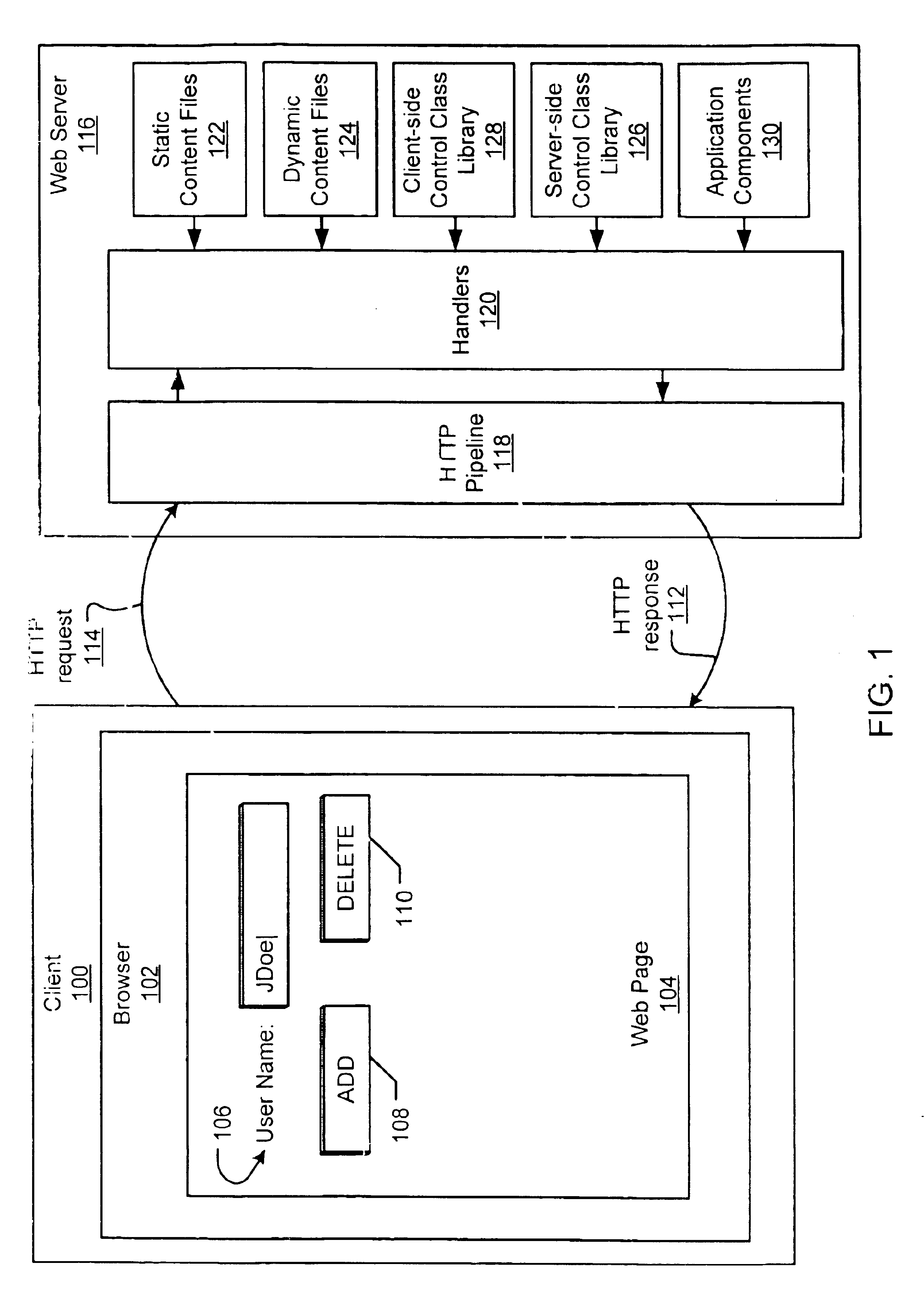
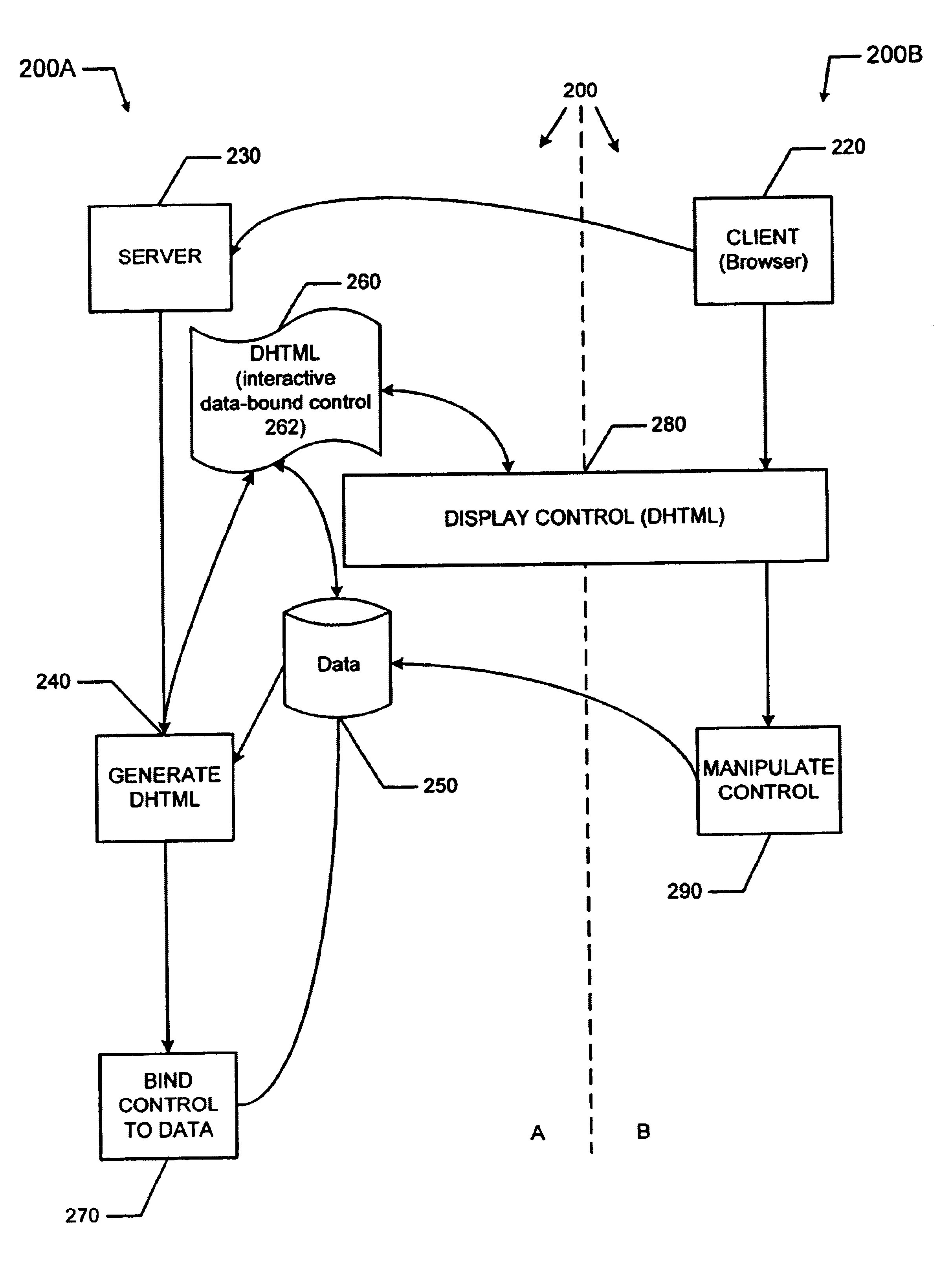
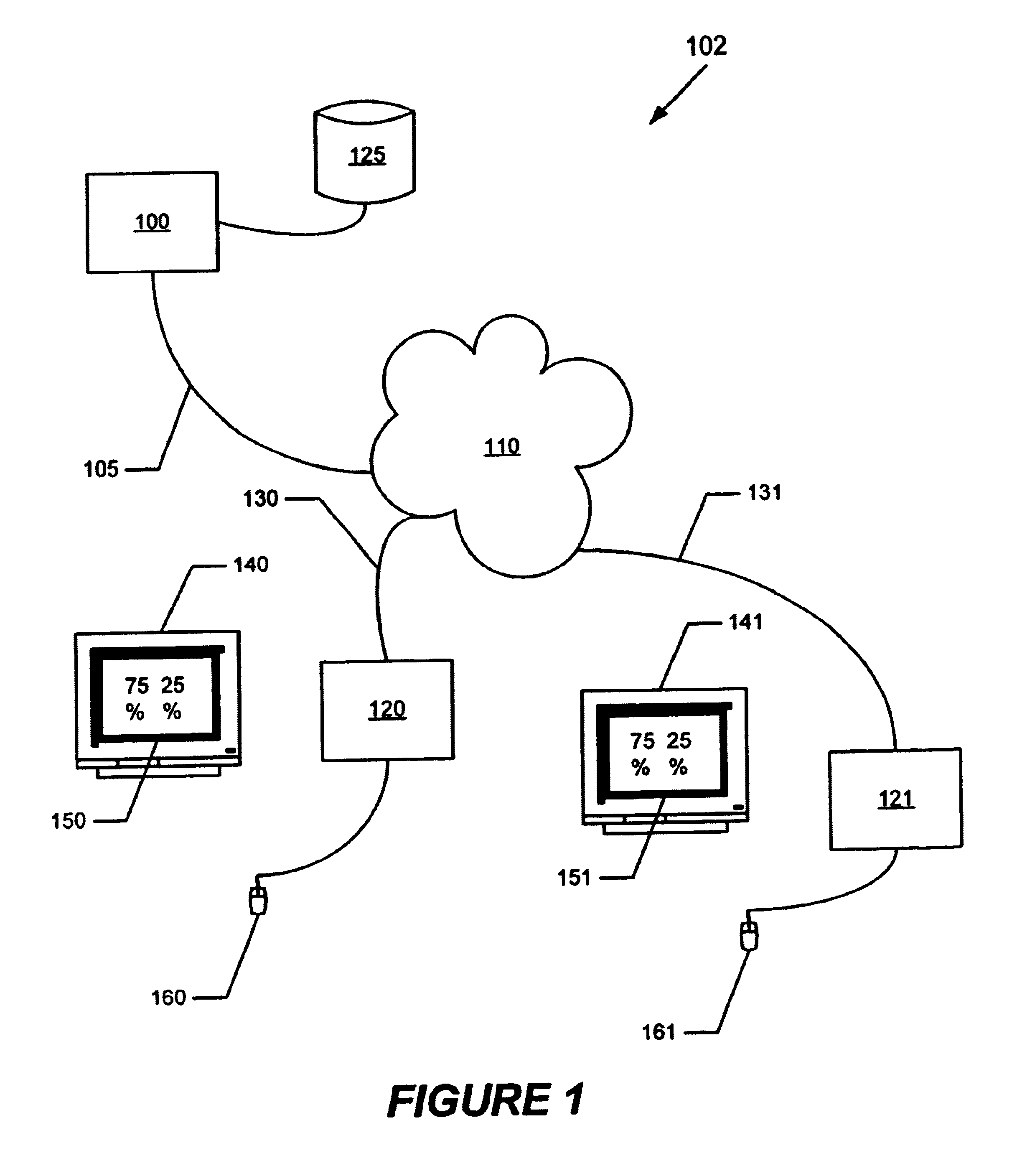
Interactive data-bound control
InactiveUS6674450B1Modify sizeData processing applicationsDigital computer detailsGraphicsThe Internet
A computer system including a server computer system and a client computer system connected to one another over a computer network, such as the Internet, so that graphical controls displayed and able to be manipulated by a user on the client computer system correspond to data stored on the server computer system. When the user makes changes to the graphical controls, the corresponding data is changed on the server computer system. The interactive graphical control binds the data on the server computer system to the graphic controls displayed on the client computer system without use of additional plug-in or other compiled code on the client computer system other than standard browser software such as Microsoft Explorer or Netscape Navigator.
Owner:OPEN INVENTION NEWTORK LLC
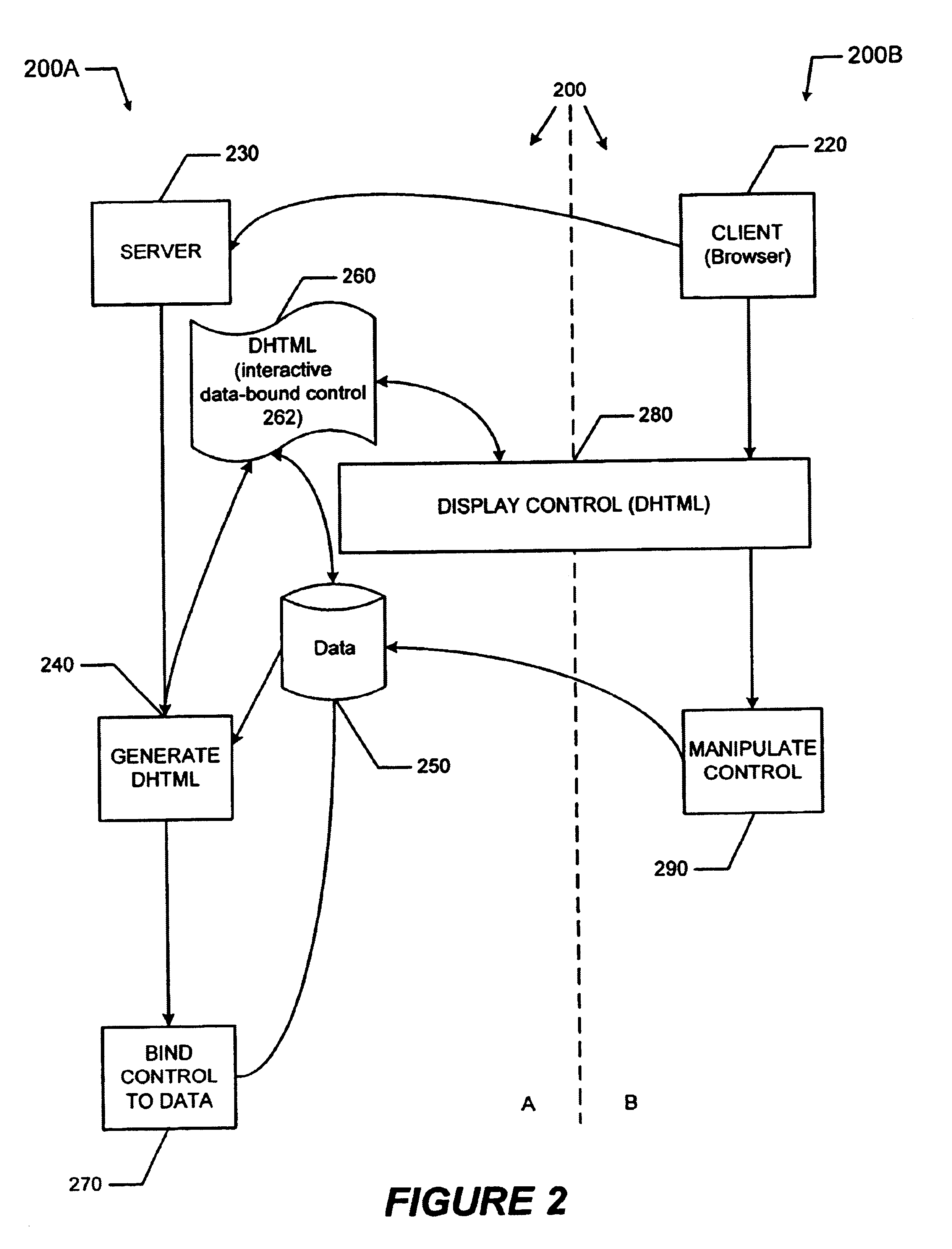
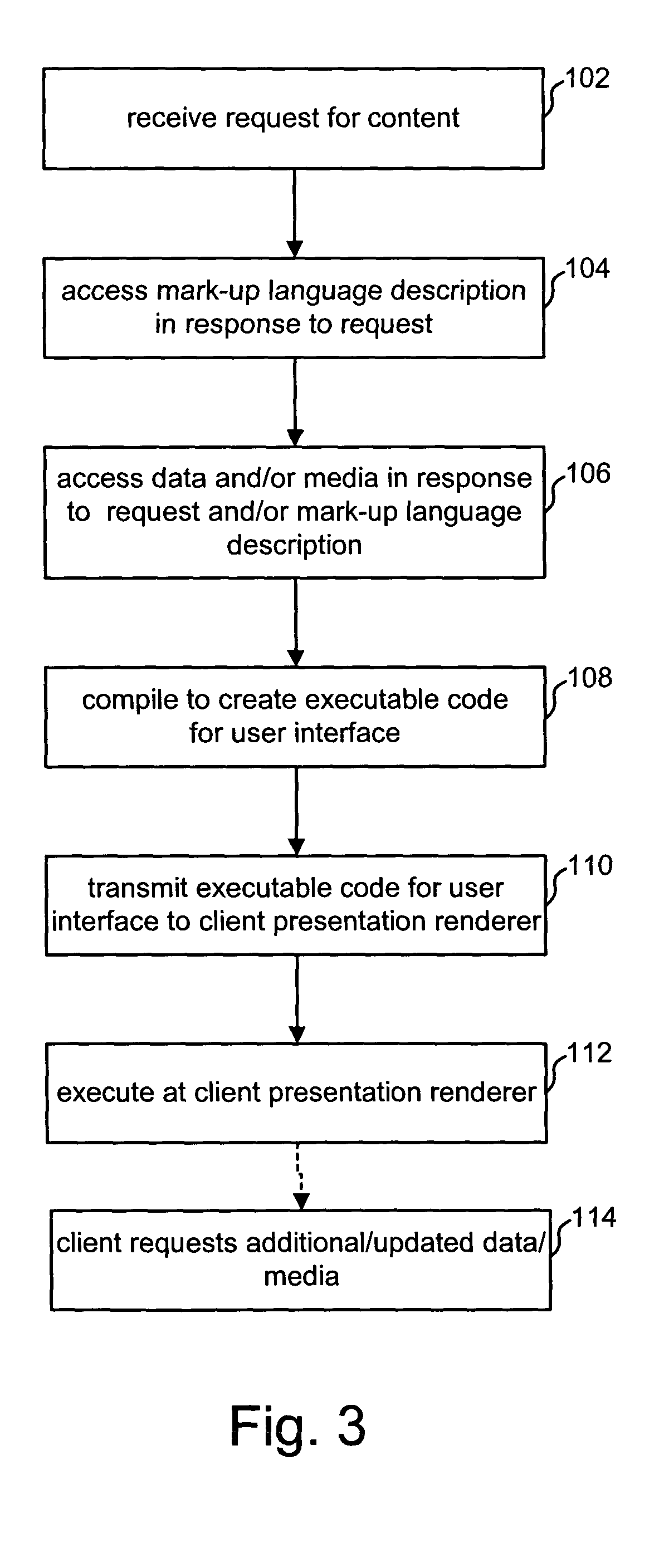
Application data binding
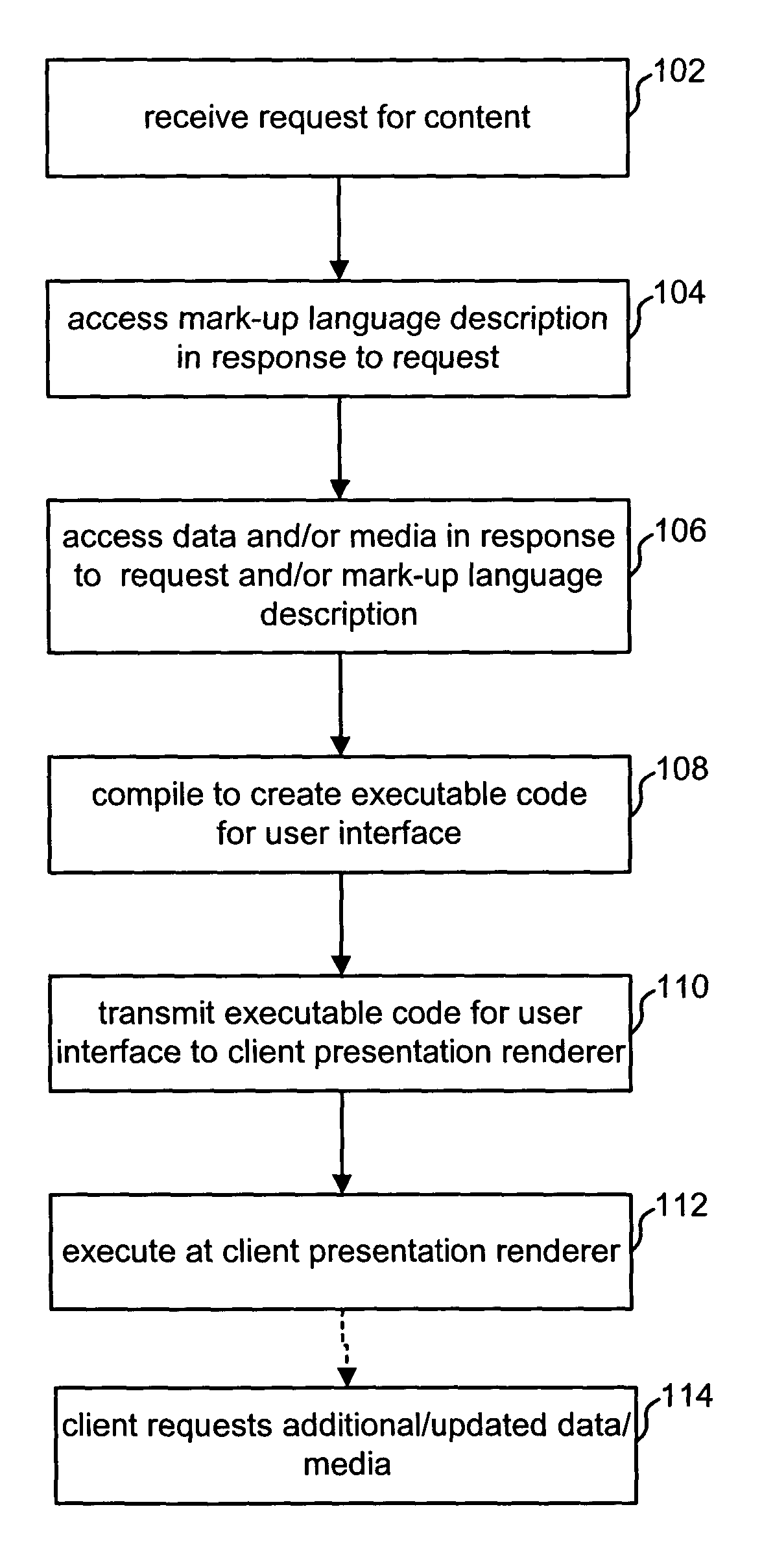
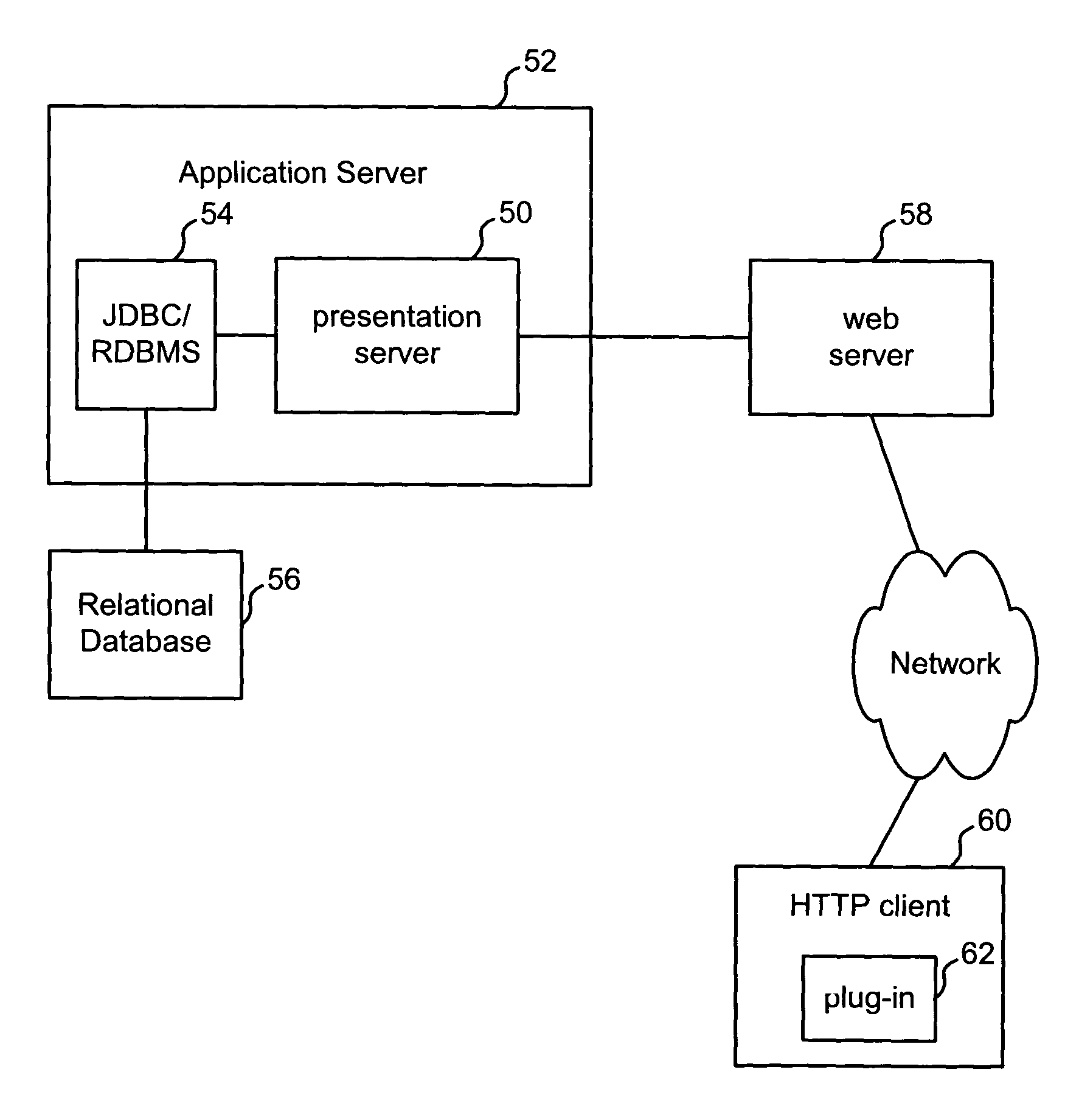
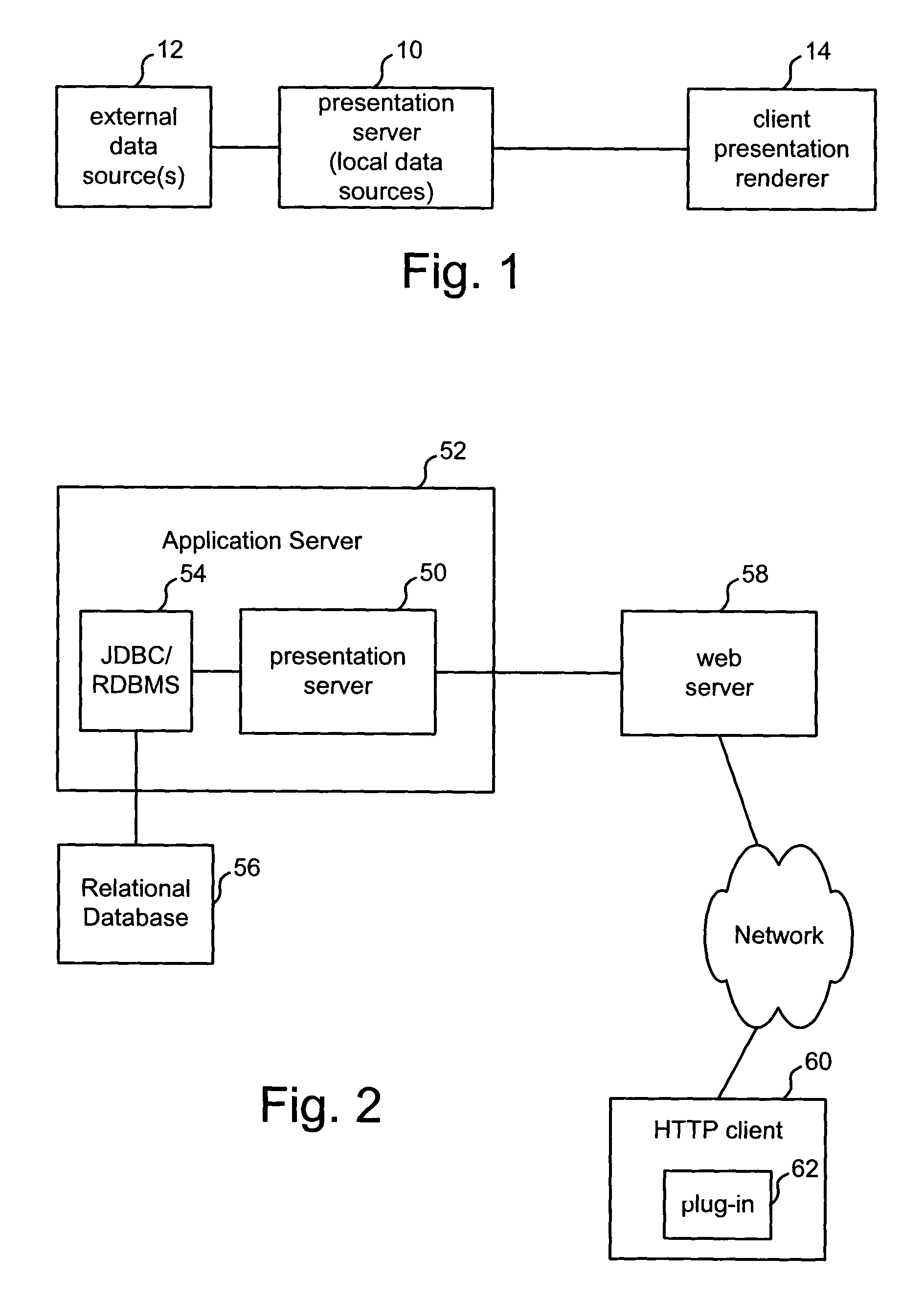
InactiveUS20050038796A1Digital data processing detailsWebsite content managementData fileThe Internet
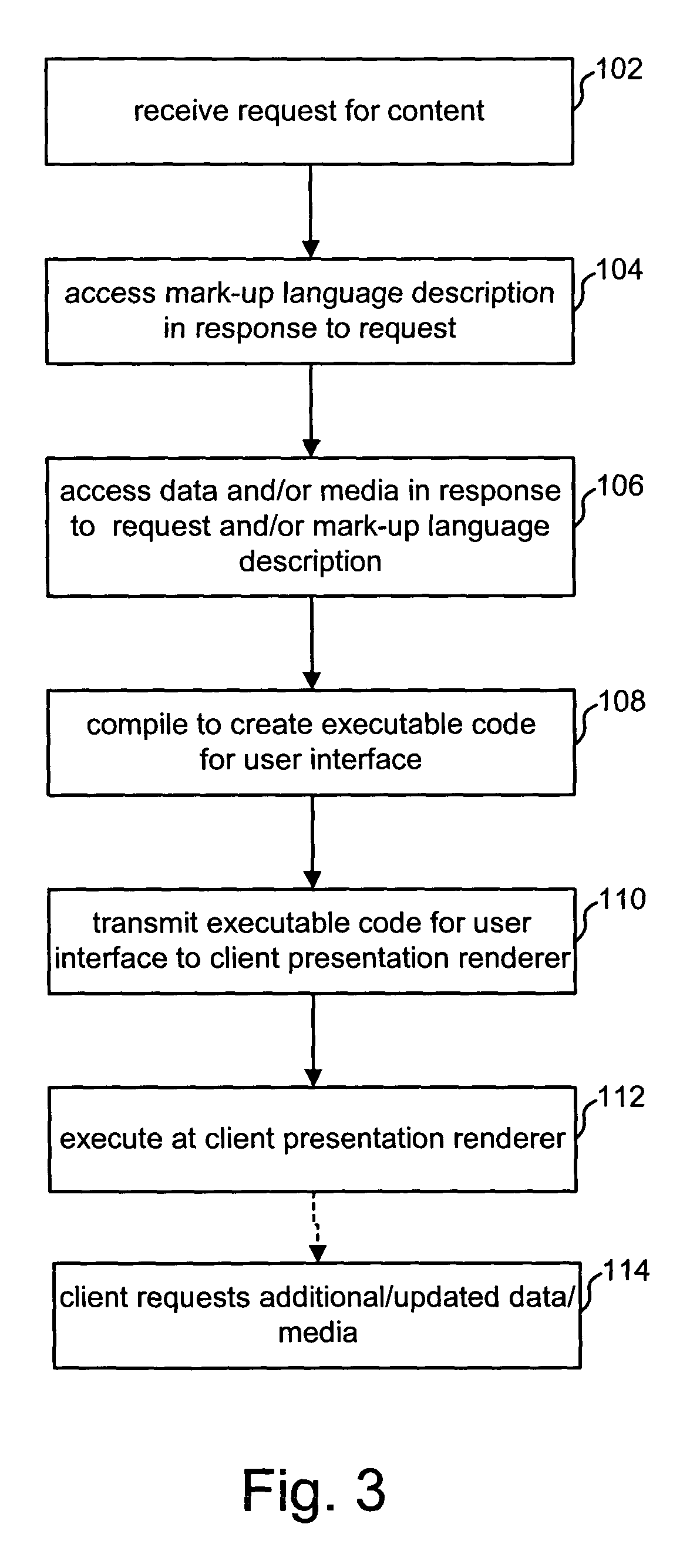
A method and apparatus for providing information by merging of an arbitrarily shaped data source with an arbitrary display hierarchy, including binding data in a source data file to application or content code. In one embodiment, the data source is an XML data file and the application is a rich Internet application provided by a presentation server. The method includes the steps of providing a structured data file; and merging the structured data file with a source file, the source file including at least one display element definition including an expression that refers to an arbitrary position or range within the data file. In another aspect, the invention is an apparatus. The apparatus includes one or more storage devices, and one or more processors in communication with said one or more storage devices. In this aspect, the processors perform a method comprising the steps of: accessing a mark-up language description of said particular content including at least one declaration of data in an XML document; and compiling said mark-up language description of said particular content to create executable code that provides said particular content, said step of compiling is performed at said server in response to said request.
Owner:INTEL CORP
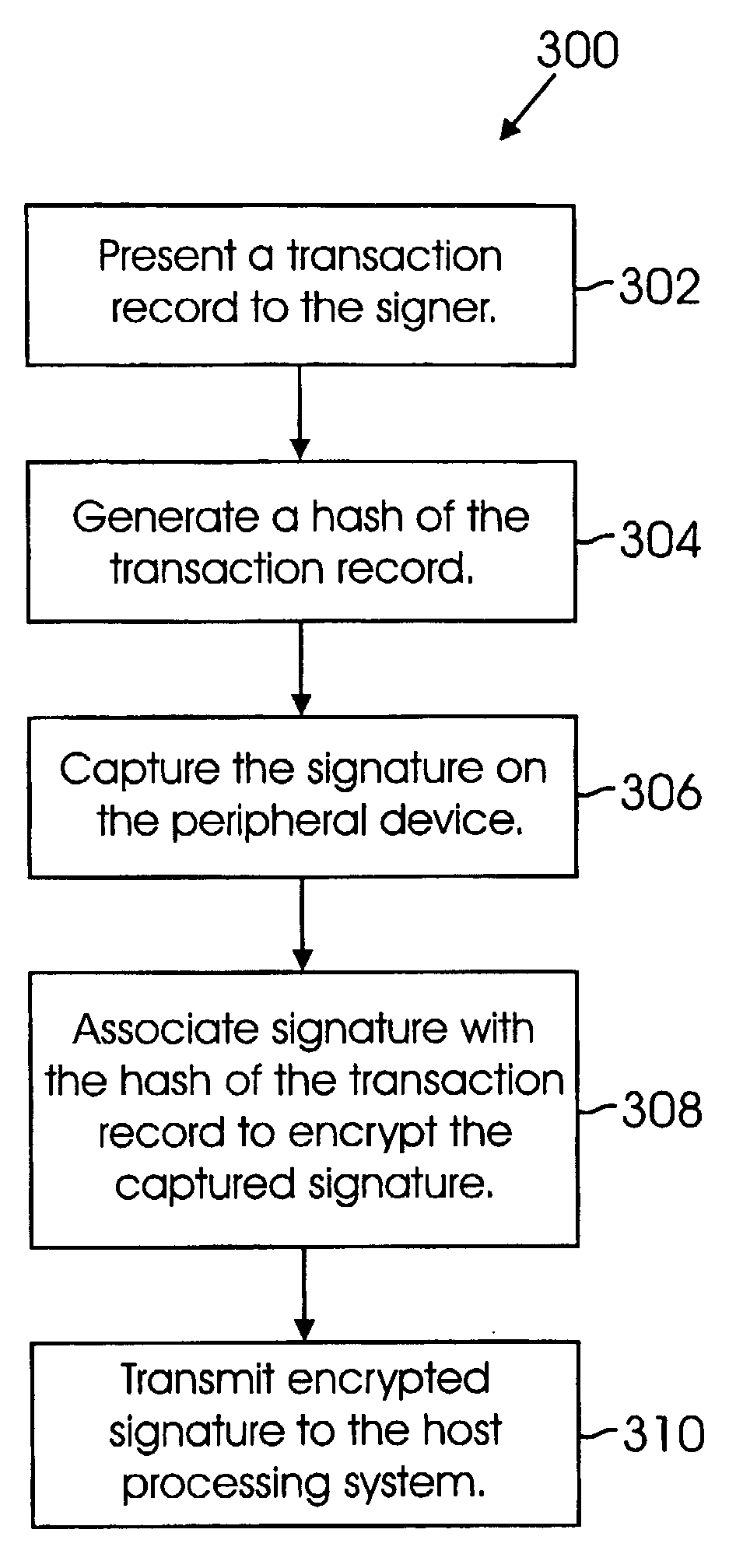
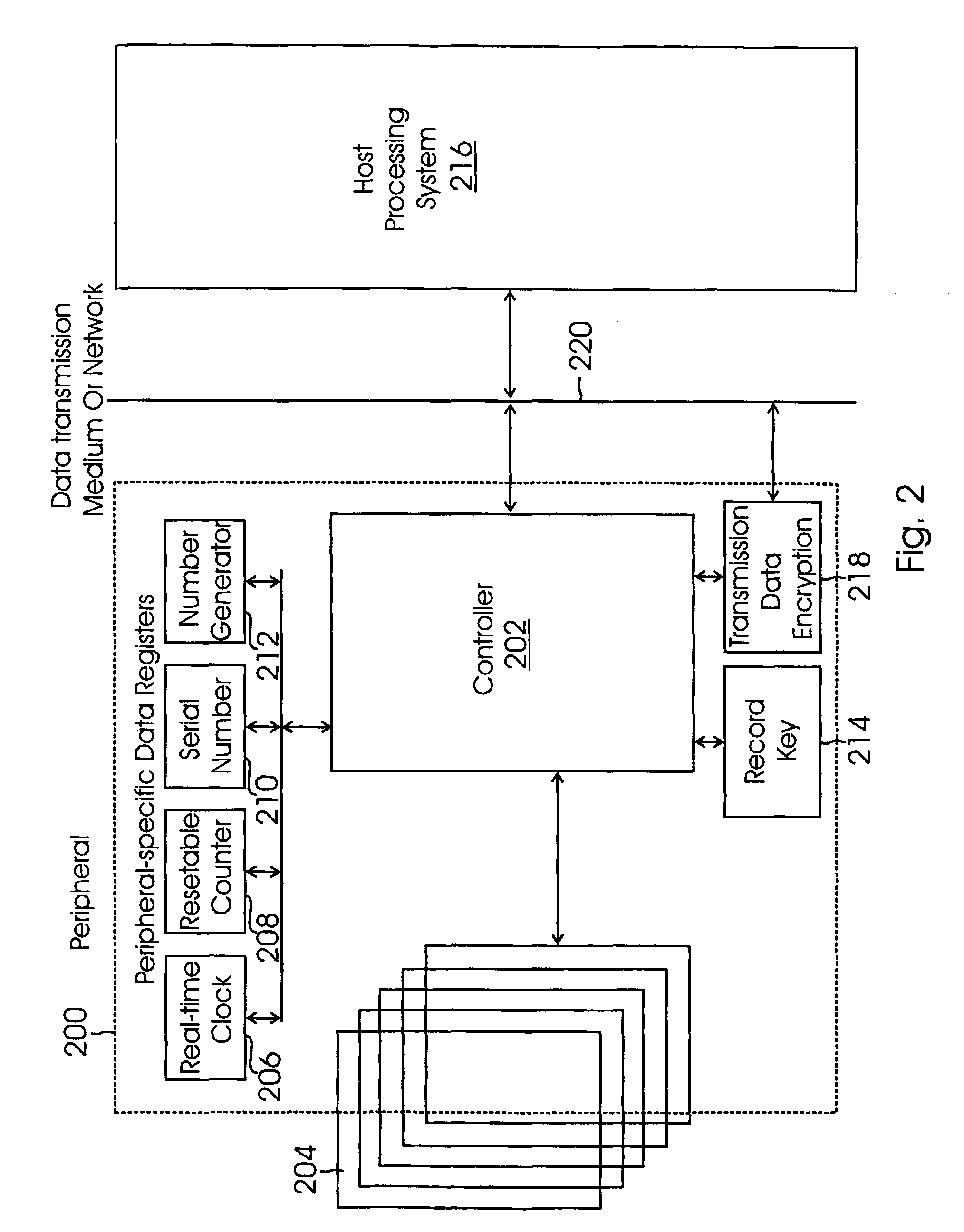
Electronic Signature Security System
ActiveUS20080010218A1Improve securityImprove complianceKey distribution for secure communicationUser identity/authority verificationTransmission mediumData binding
One embodiment of the invention enhances the security of electronic signatures during transmission. A peripheral device, which may be located remotely and separate from a host processing system, captures the signature. The peripheral device then binds the signature to the particular transaction record and transmits it to the host processing system. The host processing system validates or confirms the received signature before accepting the transaction. Binding the signature and record data together at the point-of-use reduces the likelihood that someone may be able to hack into the transmission medium, encrypted or not, and obtain the raw signature data. By binding or associating the signature and transaction record data together at the point-of-use, each transaction has a unique key, further foiling attempts at hacking. In various implementations, rather than associating the whole signature with the transaction record data, signature sample points or segments are encrypted with transaction record data.
Owner:TOPAZ SYST
Method and system for mapping between structured subjects and observers
ActiveUS20050289457A1Digital data information retrievalNatural language data processingGraphicsGraphical user interface
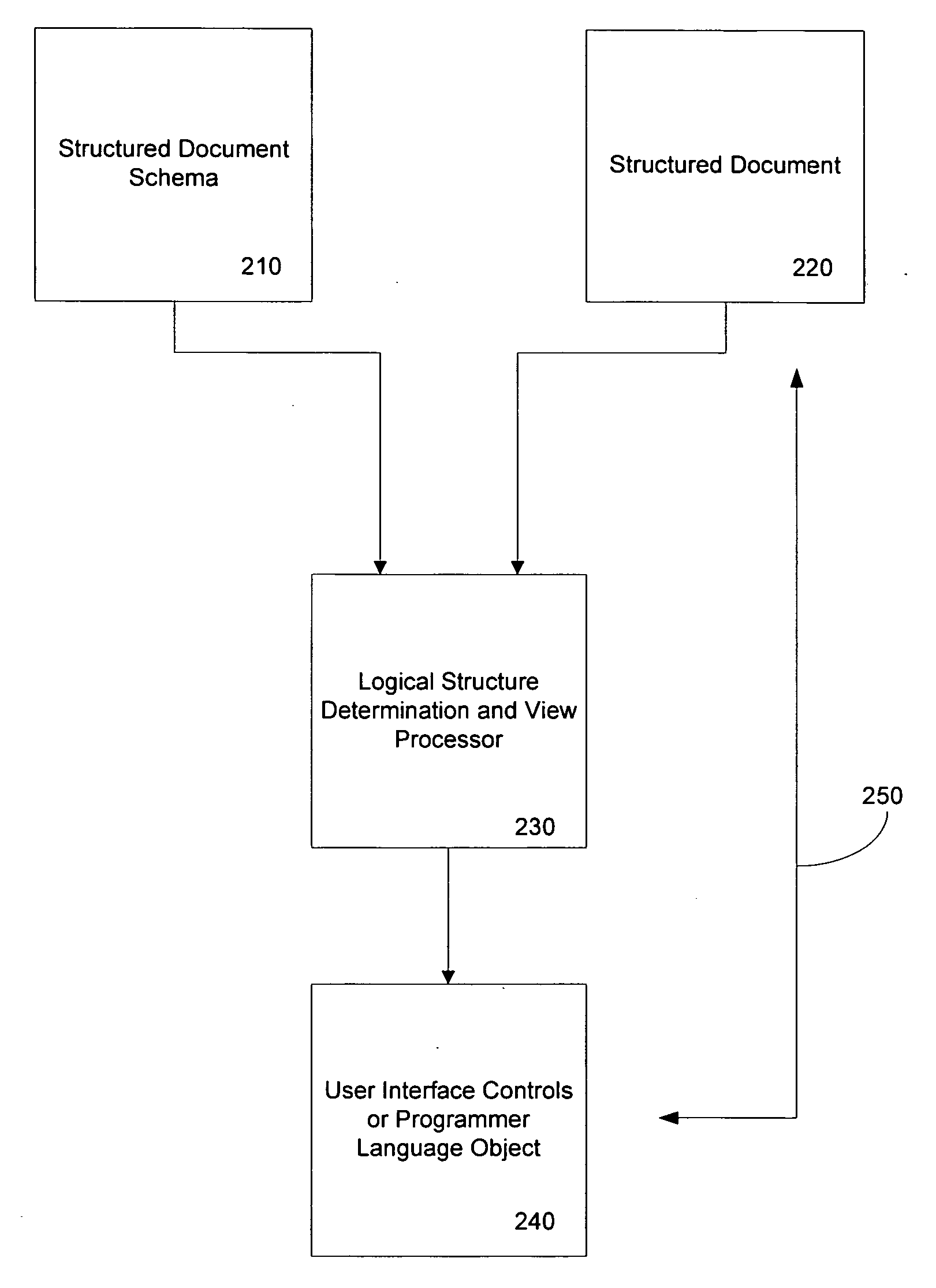
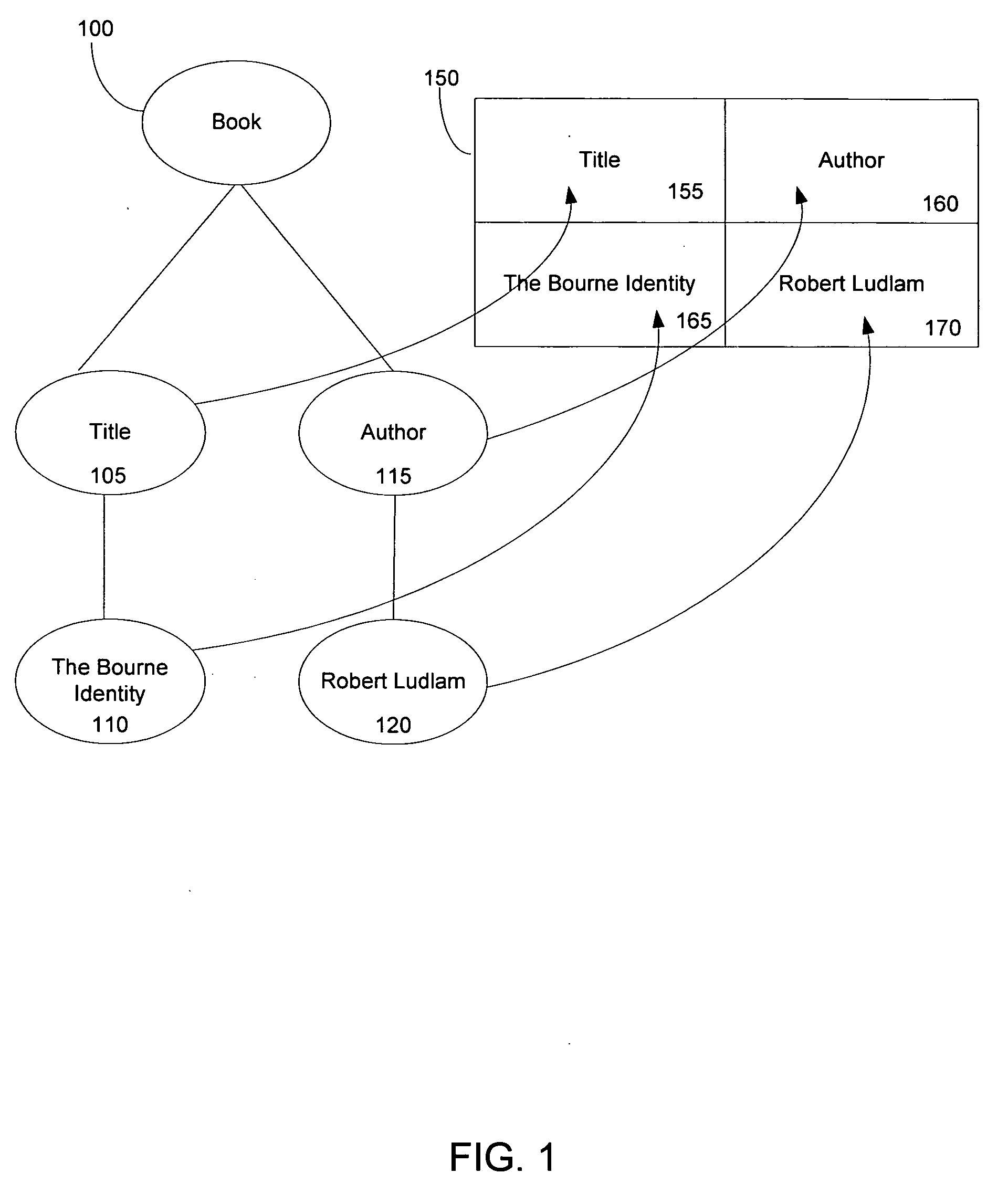
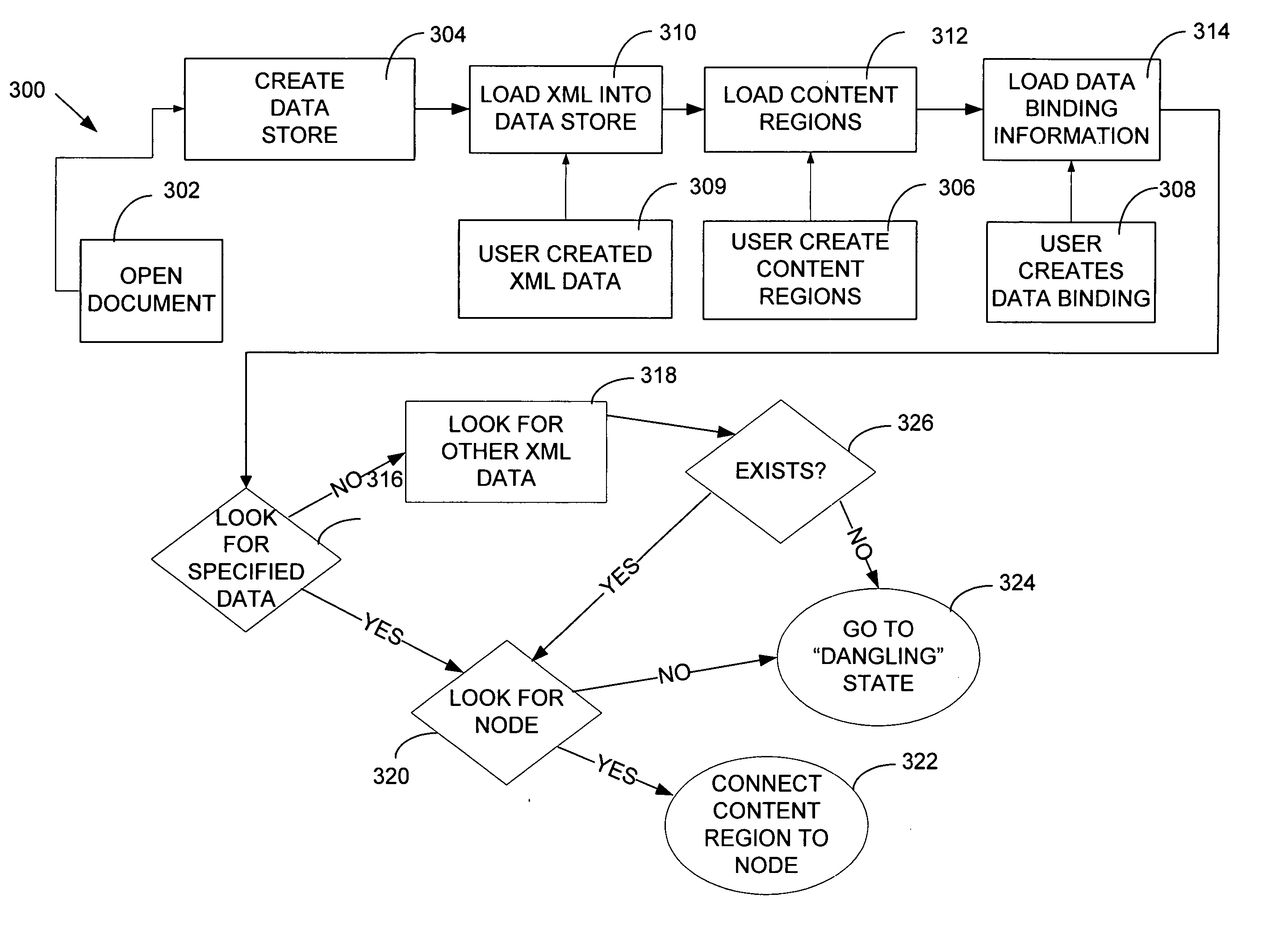
A method of binding elements of a structured document to an observer structure includes obtaining the logical structure of a document. Nodes representing information contained in the document are mapped to an observer structure which can include both a user interface or a programming object. The user interface may be a graphical user interface including a display form of a grid-like structure to contain the structured document information. The data binding which maps the structured document information to the observer form may be directionally controllable such that any change made to the information at the observer may be reflected in the source structured document.
Owner:MICROSOFT TECH LICENSING LLC
Method and system for data binding in a block structured user interface scripting language
InactiveUS7555707B1Natural language data processingSpecial data processing applicationsScripting languageBlock structure
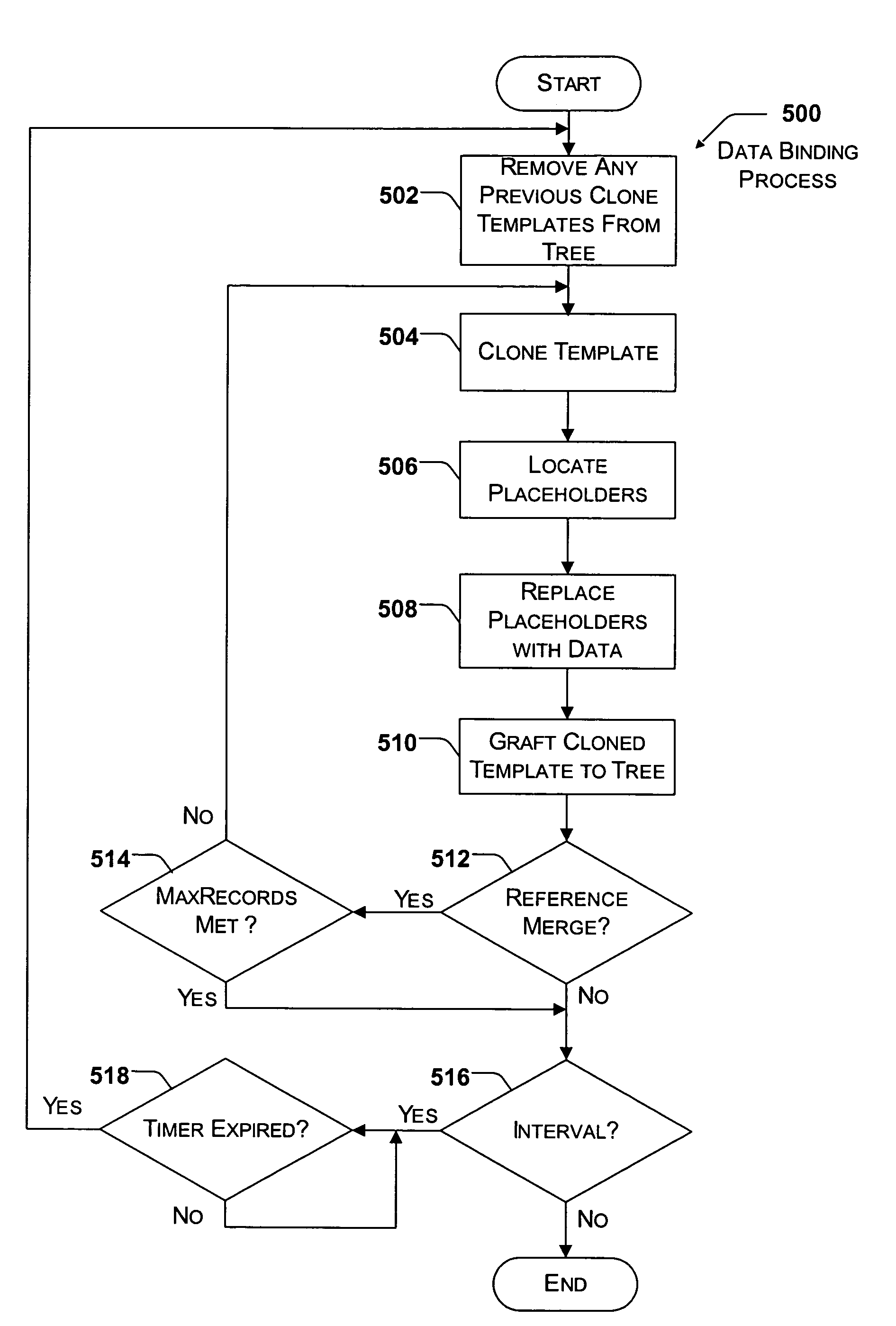
A method and system is generally directed to retrieving data from an external source and binding the data to a structure used in executing a UI script. The external source may be on a local machine located across a network. The UI script is transformed to a tree structure. The relevant portions of the tree structure are cloned and manipulated to insert the data from the external source. The cloned portions of the tree structure are then grafted back into the tree. The tree structure is then used to display the UI corresponding to the UI script that includes the data from the external source.
Owner:MICROSOFT TECH LICENSING LLC
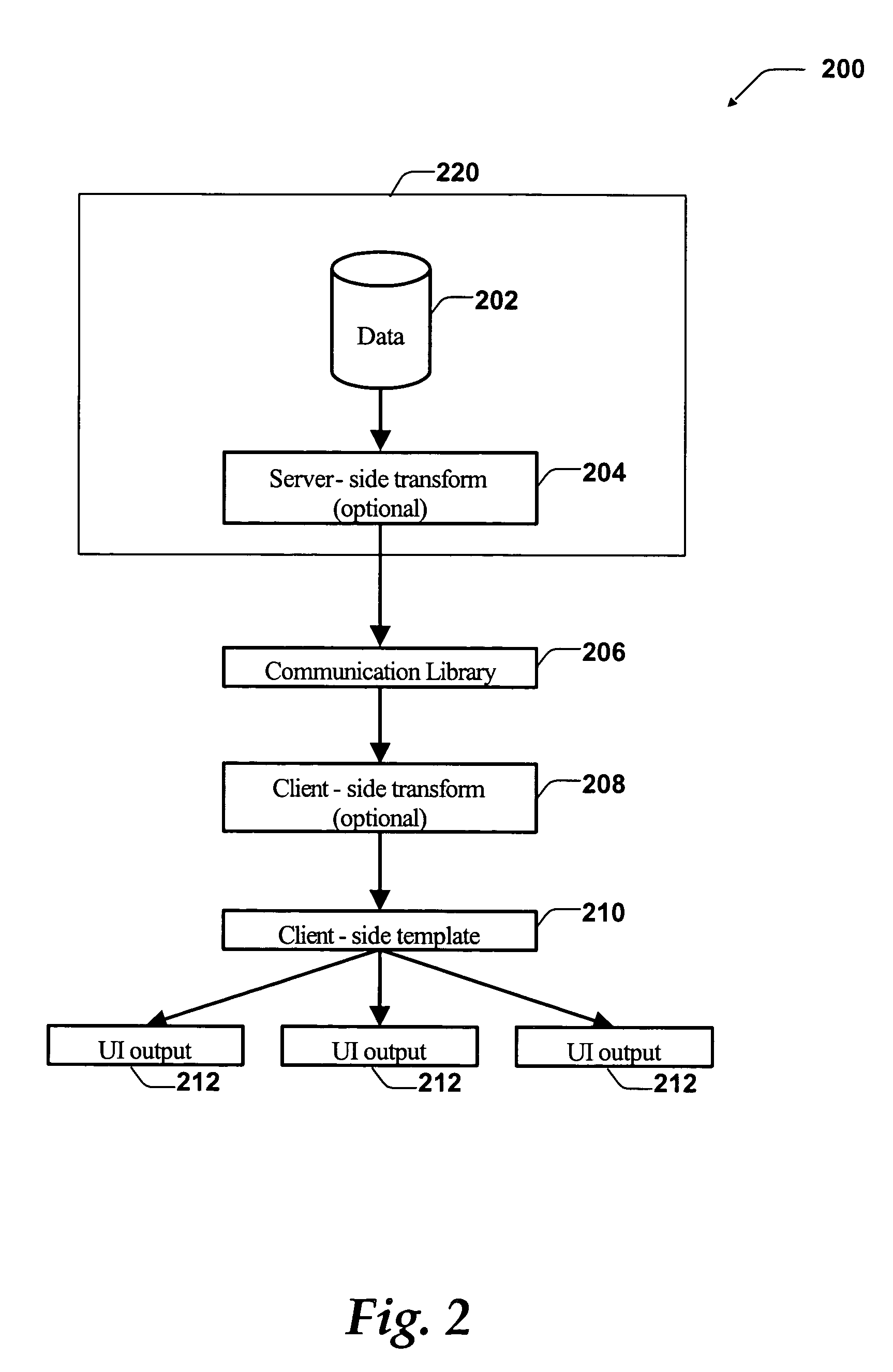
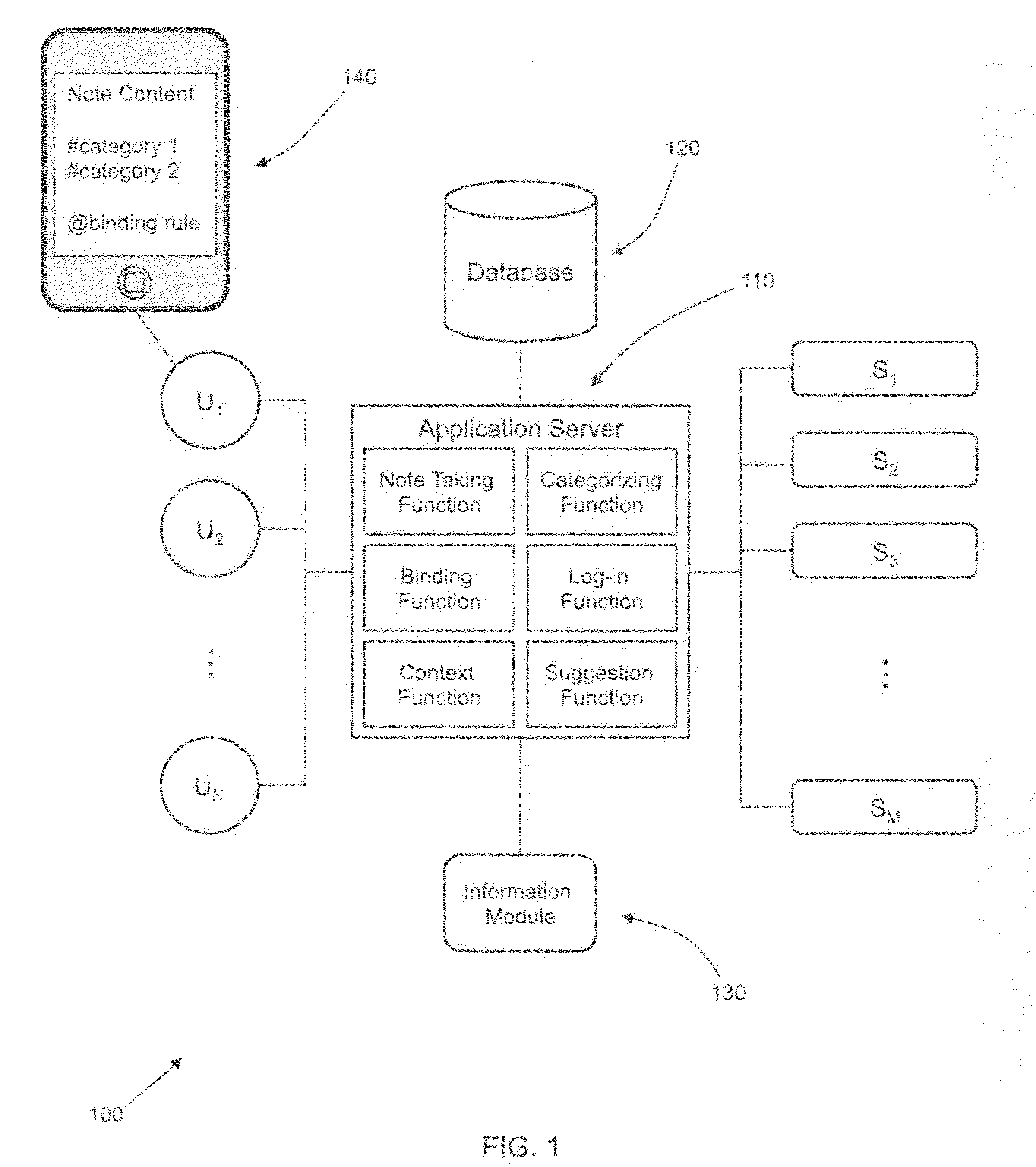
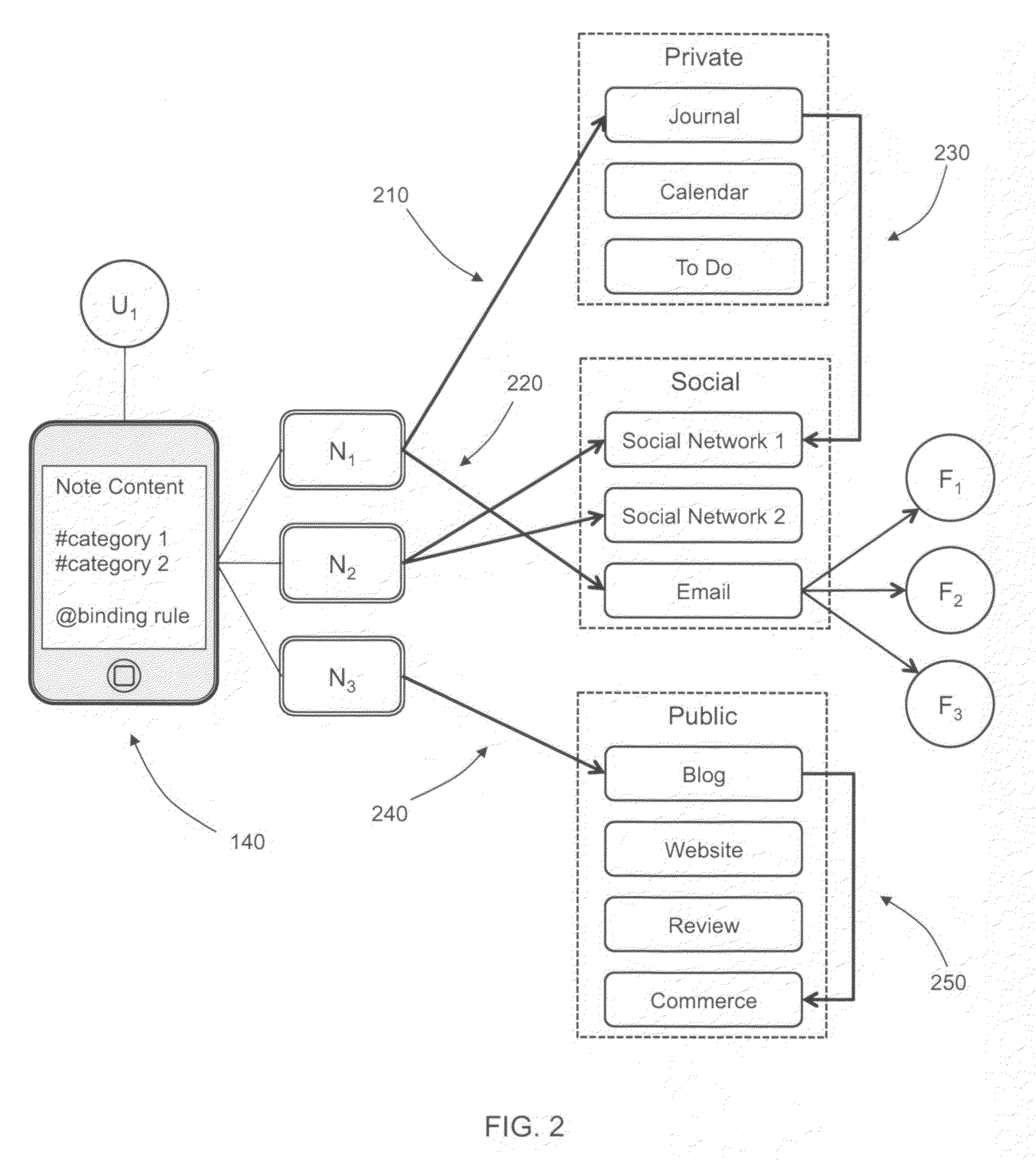
Semantic note taking system
A semantic note taking system and method for collecting information, enriching the information, and binding the information to services is provided. User-created notes are enriched with labels, context traits, and relevant data to minimize friction in the note-taking process. In other words, the present invention is directed to collecting unscripted data, adding more meaning and use out of the data, and binding the data to services. Mutable and late-binding to services is also provided to allow private thoughts to be published to a myriad of different applications and services in a manner compatible with how thoughts are processed in the brain. User interfaces and semantic skins are also provided to derive meaning out of notes without requiring a great deal of user input. Linking physical objects to notes are also provided, such as through QR codes.
Owner:APPLE INC
Enhanced system for controlling service interaction and for providing blending of services
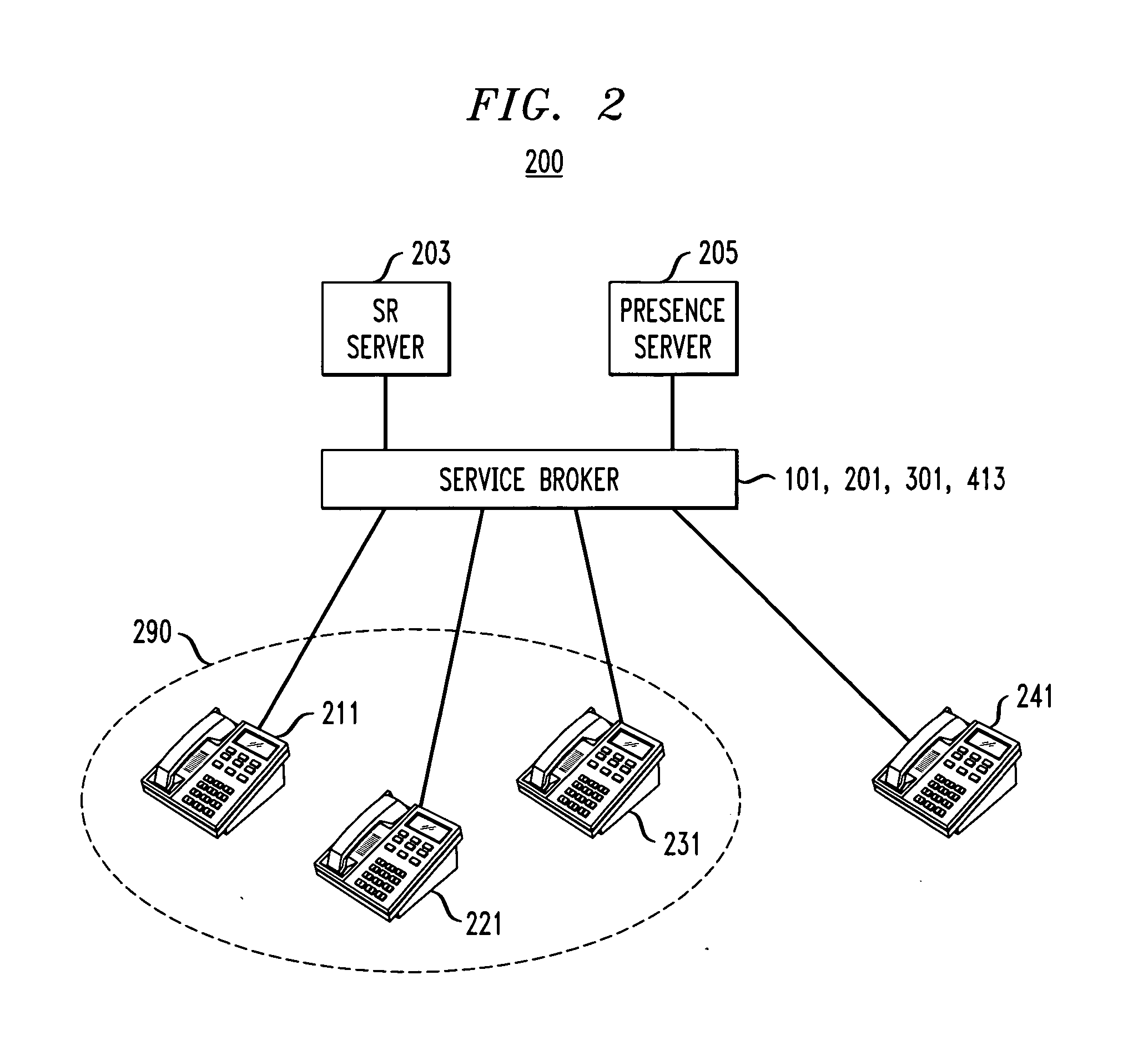
InactiveUS20070201665A1OptimizationEasy to useSpecial service for subscribersTransmissionCommunications systemMessage type
A service broker system is presented for mediating events or messages to be sent to or received from a plurality of applications to control service interaction and to provide service blending in a communications system. The service broker system includes steplet functional components that determine a desired mediation for feature interaction or service blending associated with an event or message, along with a message manager component with a dispatcher for the steplet functional components, where the message manager creates and maintains a unique message object for a received request message. A user and end point data manager component is provided to obtain user data and endpoint data and to bind attribute data to a user ID associated with a current service session, and a session context component for binding attribute data to session ID associated with the current service session. In one embodiment, the system includes two or more message manager components individually associated with a different message type.
Owner:WSOU INVESTMENTS LLC
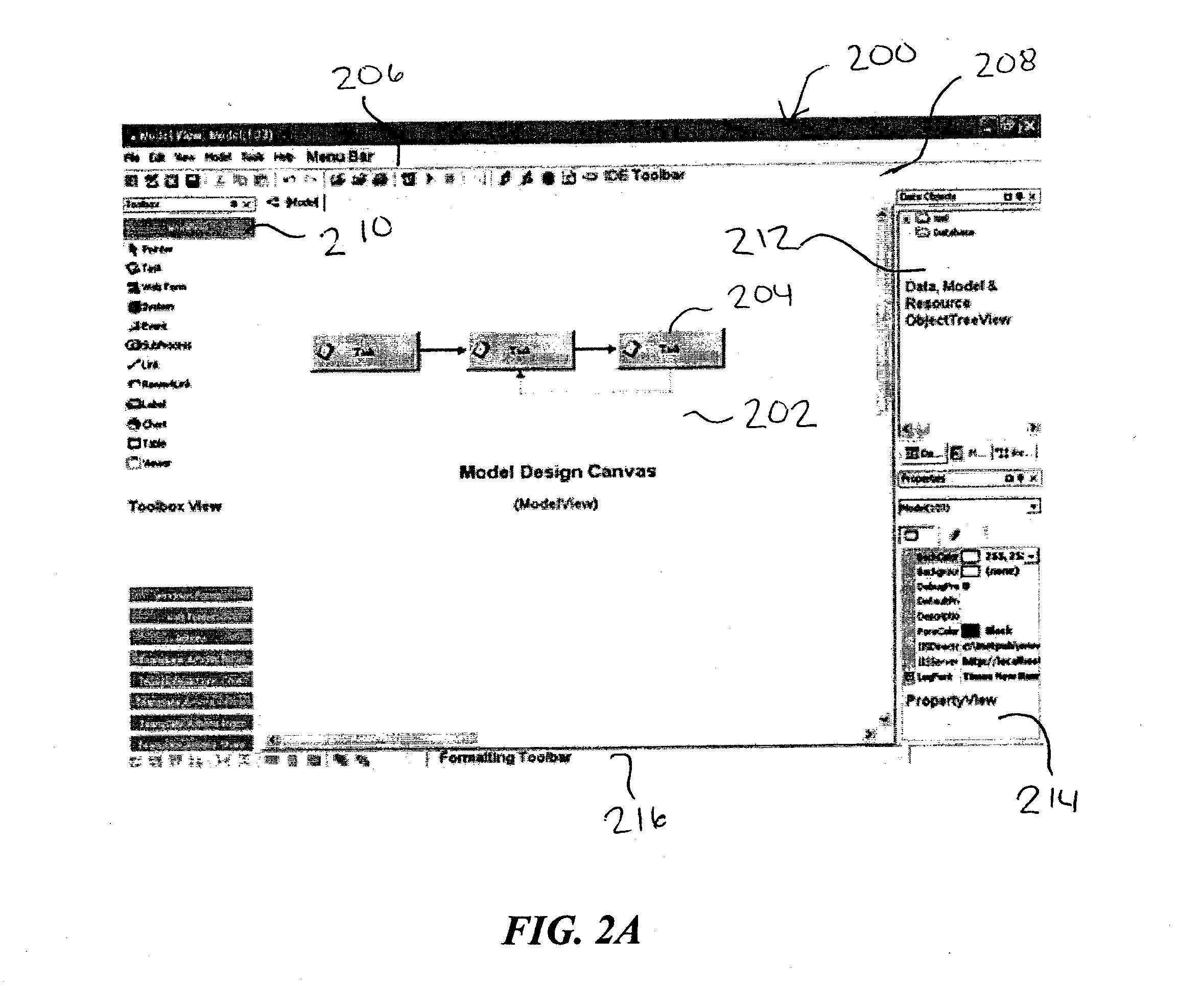
Workflow data binding
A workflow data binding system facilitates binding of a data component to a feature of a software component. Prior to the binding, a graphical indication of the software component and a graphical indication of the feature of the software component are displayed. In addition, an indication of an element of the data component is displayed in a display area approximately adjacent to the displayed software component. The workflow data binding system receives a user input command to bind the data component to the feature of the software component. The user input command may include dragging the indication of an element of the data component from the data component display area to the feature of the software component and subsequently dropping it on the feature. As a result, the workflow data binding system automatically generates script or code that provides executable instructions to bind the feature of the software component to the data component.
Owner:CAPTARIS
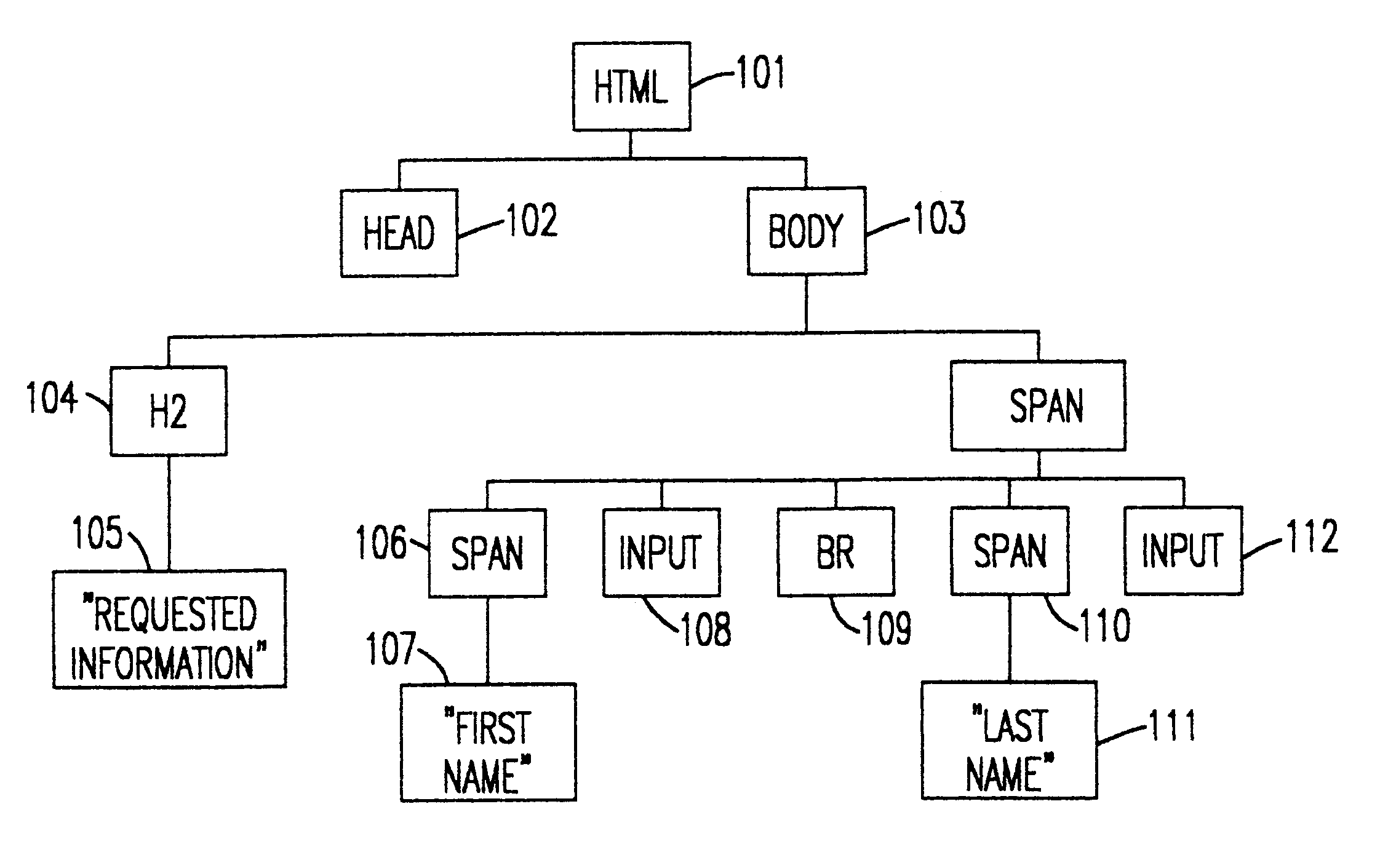
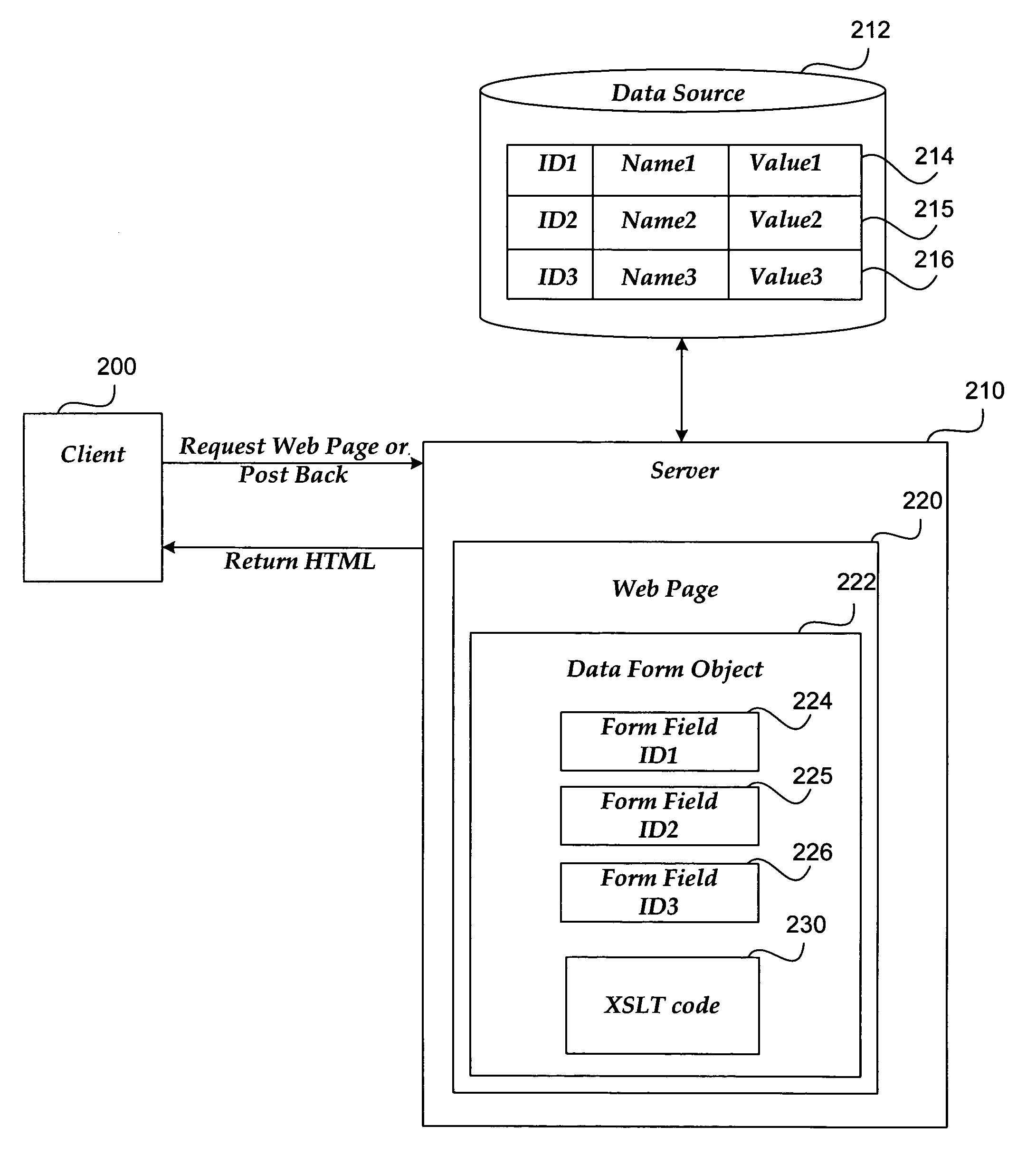
Web-based data form
InactiveUS20060074981A1Natural language data processingSpecial data processing applicationsXSLTData source
A web-based data form enables modifications made to values in the data form to be dynamically implemented in a data source. Form fields of the data form are associated with items in the data source using data binding information. Data from the data source is transformed into intermediate code using Extensible Stylesheet Language Transformation (XSLT) code. Form controls of the data form are instantiated using the intermediate code. Hypertext Markup Language (HTML) is generated from the intermediate code including the form controls.
Owner:MICROSOFT TECH LICENSING LLC
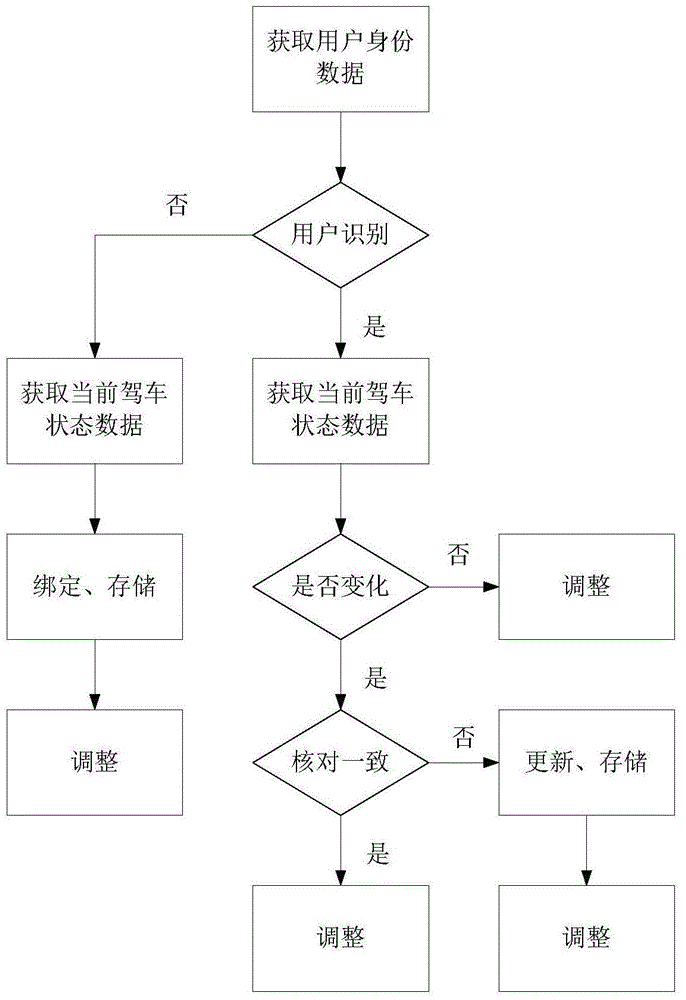
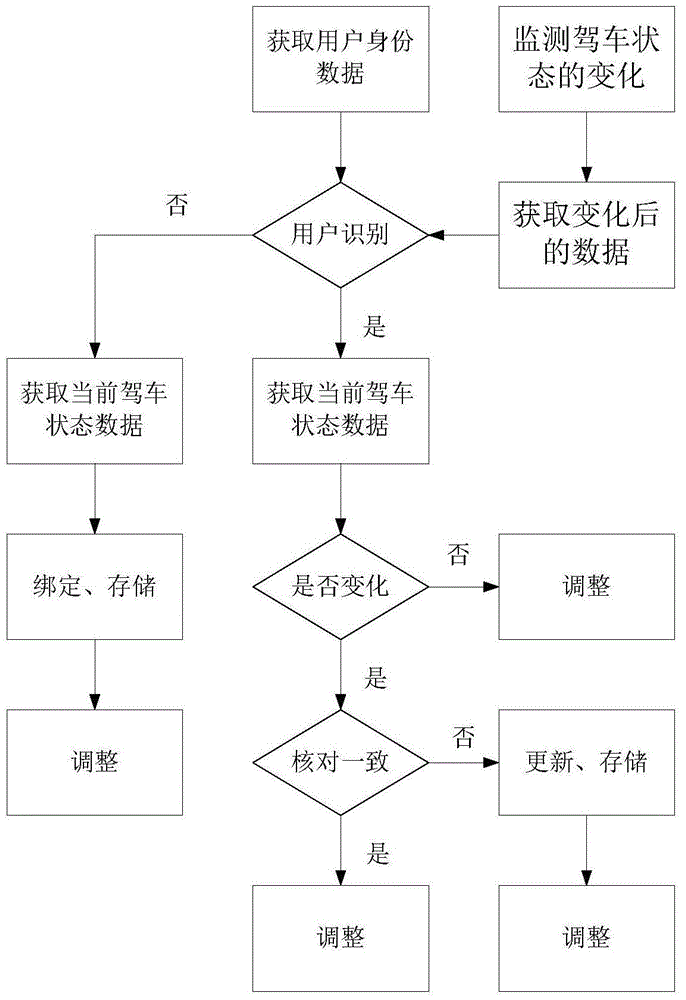
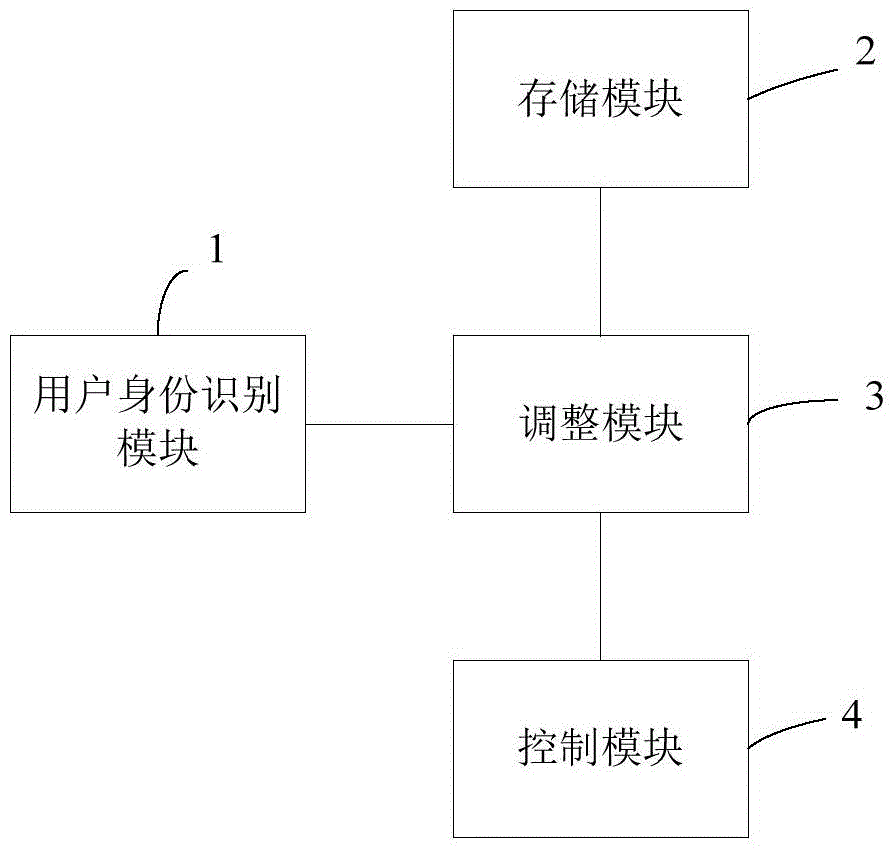
Intelligent driving state adjustment device and method
InactiveCN104816694AImprove experienceShorten the timeElectric/fluid circuitEmbedded systemData Adjustments
The invention discloses an intelligent driving state adjustment device and an intelligent driving state adjustment method. The device comprises a user identity identification module, a storage module, an adjusting module and a control module. The method comprises the steps of 1 obtaining data of the user identity of a current pilot; 2 comparing the obtained data of the user identity with data in a storage system, to check whether the storage system has data corresponding to the data of the user identity; if the storage system does not have data corresponding to the data of the user identity, carrying out the step 3; if the storage system has data corresponding to the data of the user identity, carrying out the step 4; 3 obtaining data of a current driving state, binding the data of the current driving state and the data of the user identity of the current pilot as a new user, and performing storage; 4 adjusting the relevant driving condition according to the data of the driving state corresponding to the data of the user identity. By applying the intelligent driving state adjustment device and the intelligent driving state adjustment method, complex operation does not need, and the user experience is improved.
Owner:SHANGHAI XIUYUAN NETWORK TECH
UI (User Interface) performance and service logic separation method and system
ActiveCN101872305AAchieve mutual independenceSpecific program execution arrangementsState dependentSoftware engineering
The invention discloses UI (User Interface) performance and service logic separation method and system. The method comprises the following steps of: correlating a UI object with a service data object by data binding; correlating the state of the UI object with the state of the service data object by state binding; correlating the action of the UI object with the action of the service data object by action binding; and carrying out united management on the data binding, the state binding and the action binding by logic model binding, therefore, the dynamic and indirect correlation between a UImodule and the service data object can be achieved. By adopting the invention, the mandatory dependence relation between a user interface and logic codes is relieved; the user interface design and the service logic programming can be developed in parallel as two completely independent works in the designing process; and the UI object and the service logic processing object are mutually independent to respectively support dynamic switching of UI views and change a logic processing unit in the software running process.
Owner:YONYOU UP INFORMATION TECH
Method for providing a pluggable custom data binding system
InactiveUS20060123039A1Digital data processing detailsSoftware maintainance/managementXML schemaWeb service
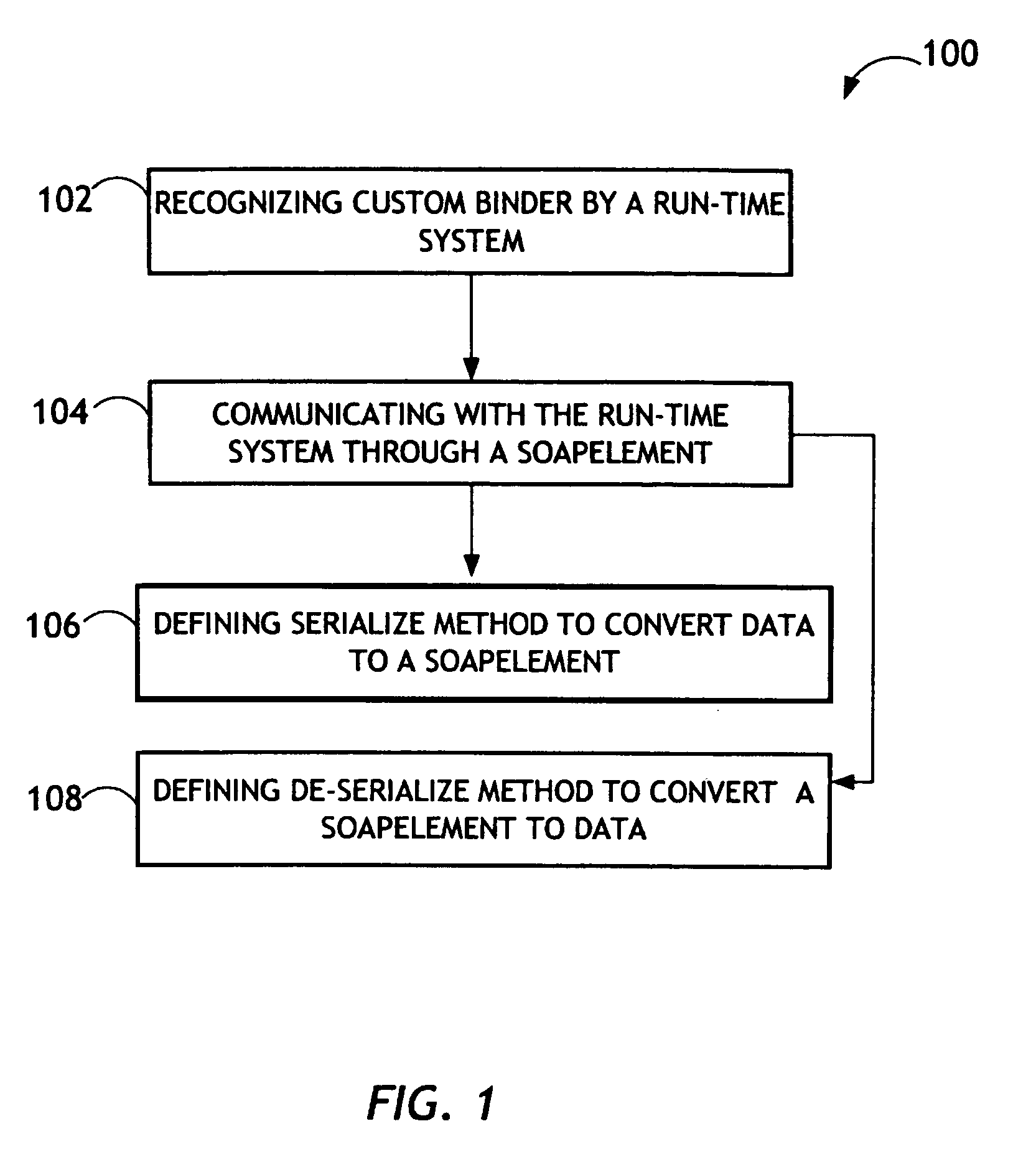
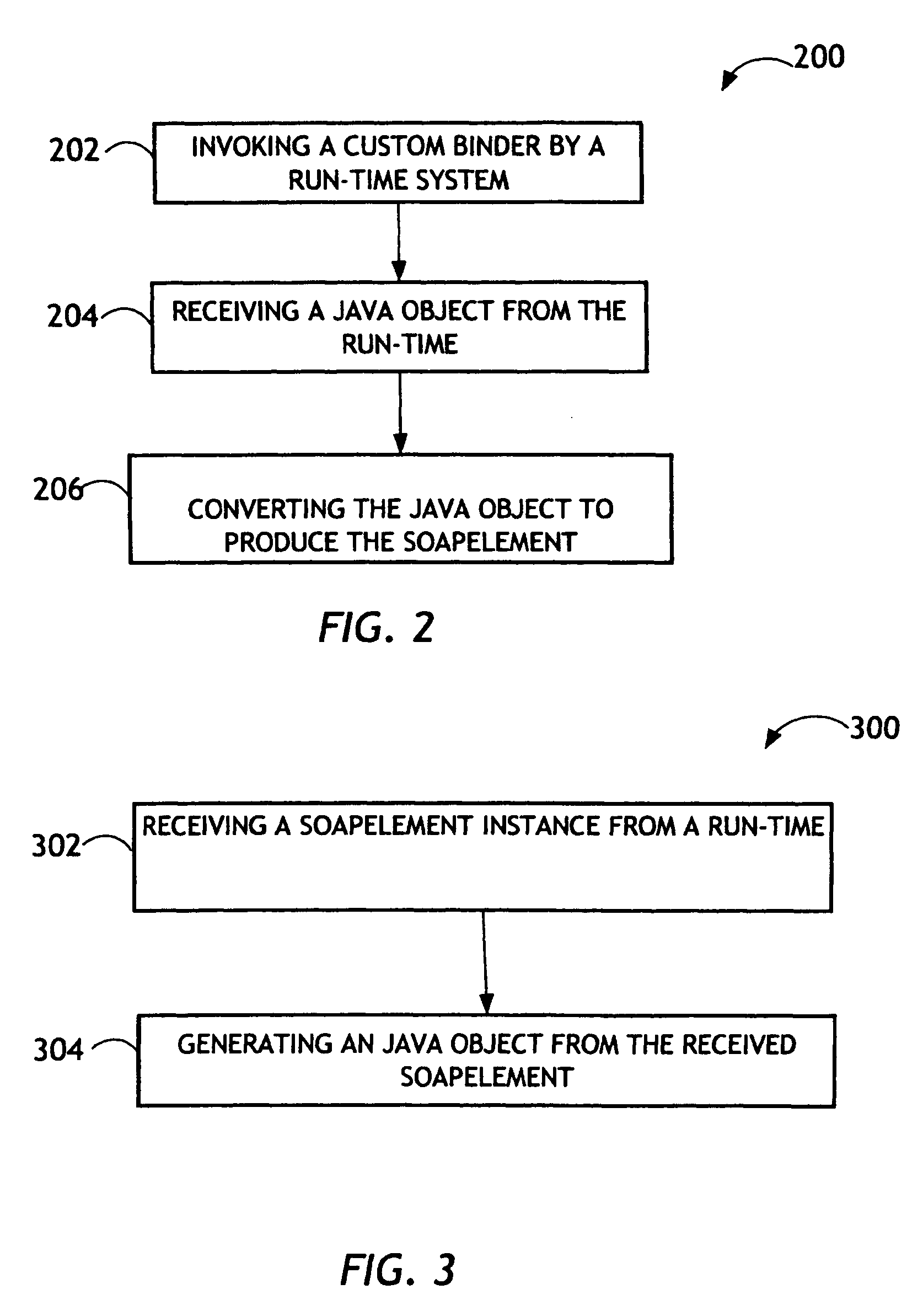
The present invention is directed to a pluggable custom data binding system and method utilizing a generic data structure exchanged between a run-time system and a user define binding logic in Web Service Applications. The custom data binding system may replace the existing mappings for XML schema types. The custom binder is a function that works with the pairing of a particular XML schema type and Java type. The custom binder may define an interface including serialize and de-serialize methods to convert between Java objects and SOAPElements. After the custom binder is plugged into the run-time system, this custom binder may interact with the run-time system through use of SOAPElement. The custom binding provider may aggregate related custom binders to support particular custom data bindings. The custom binding provider may be created for a specific application that has a few XML schema types that are not supported by the JAX-RPC specification.
Owner:LINKEDIN
Application data binding
Owner:INTEL CORP
Programmability for binding data
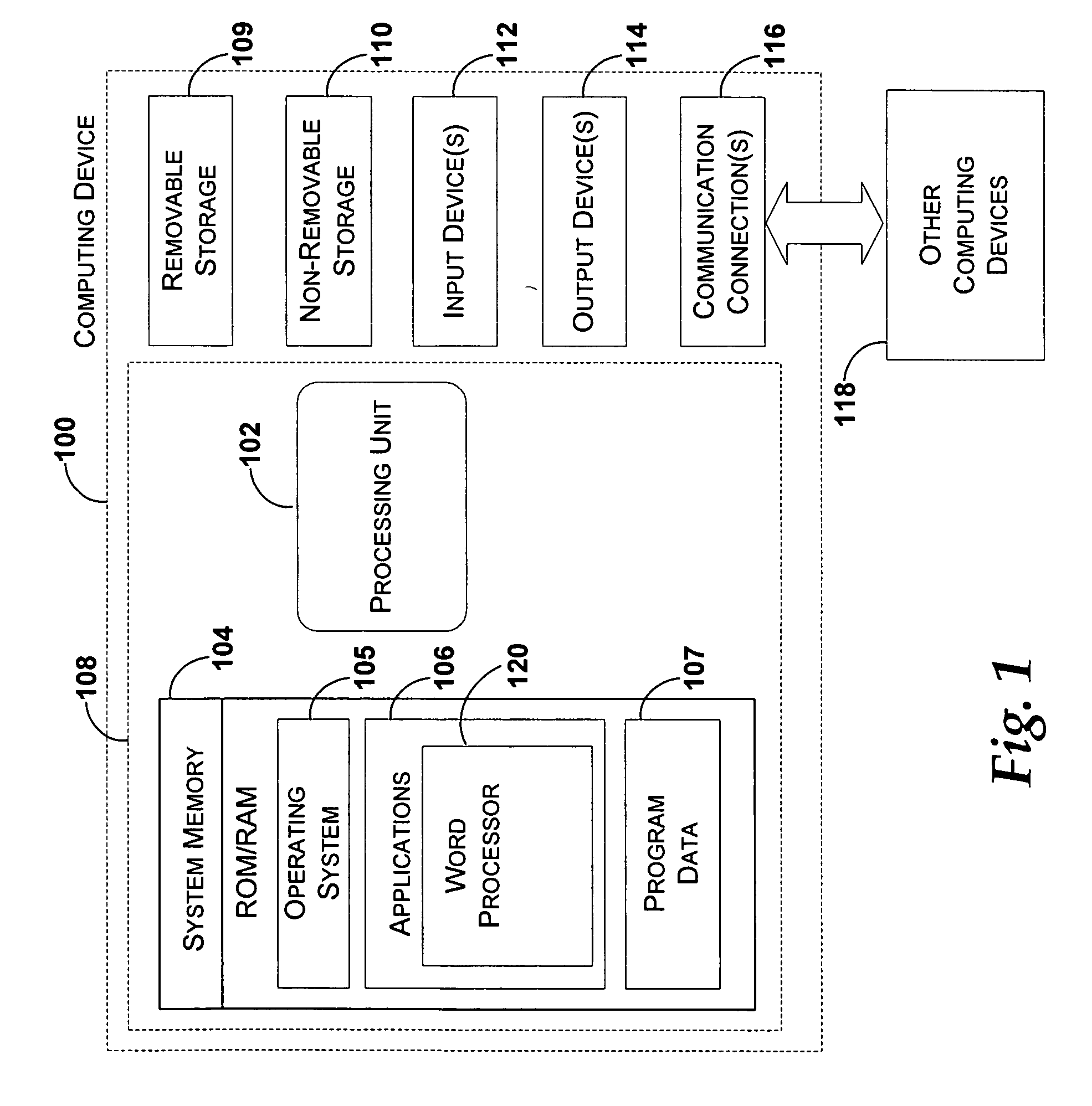
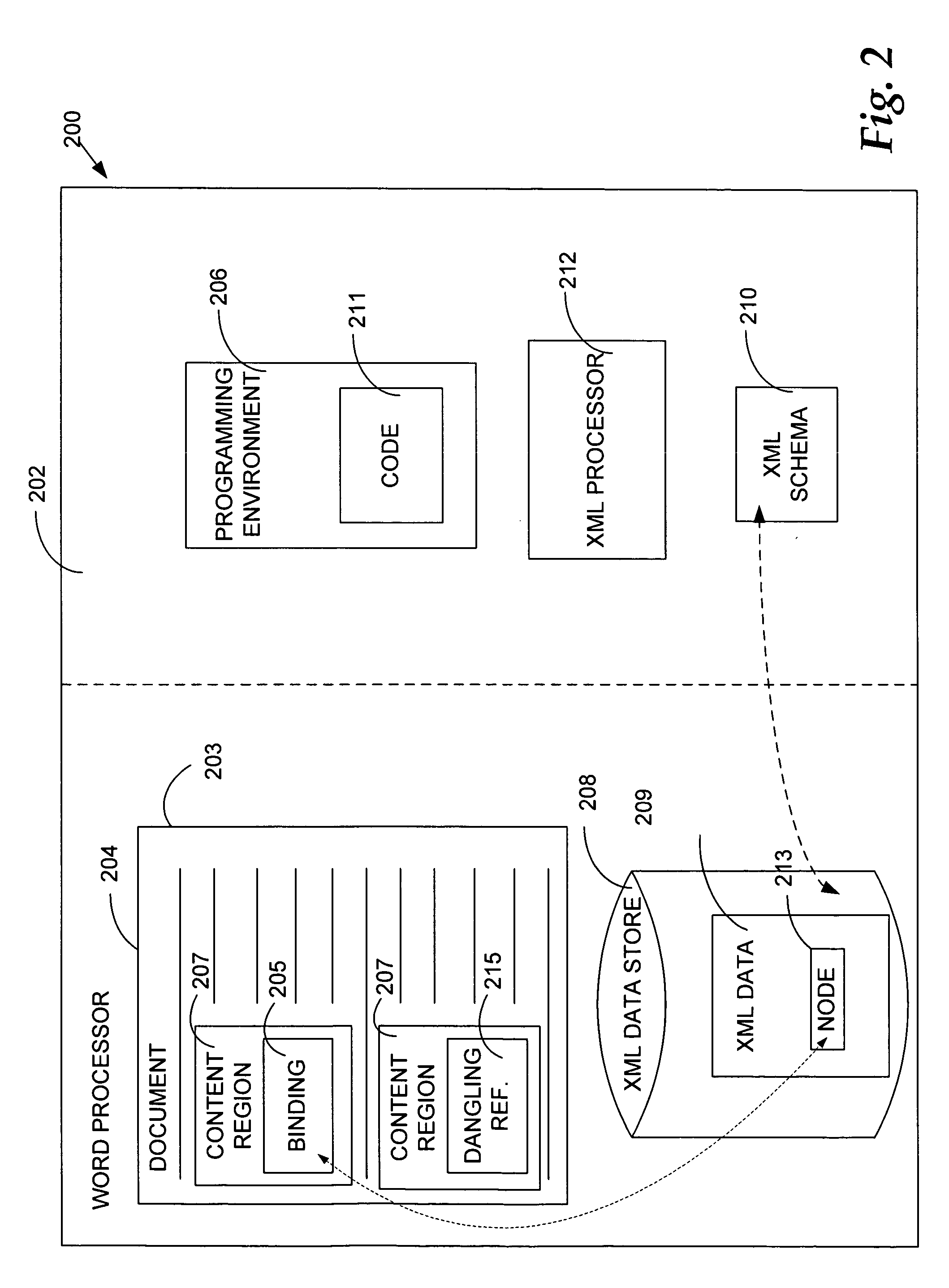
InactiveUS20060195783A1Simplifying and streamlining application developmentSimplify the development processMultiprogramming arrangementsNatural language data processingWord processingData store
An object model allows code to be developed using a programming environment to access the functionality of an application, in a word processing application, for example. The object model may be used to manipulate one or more data bindings in an application. Code may also be developed using a programming environment for reacting to changes, in either direction, of a content region or a node in XML data associated with one or more data bindings. Code may be developed to define data bindings between file content and content within data in a data store. Additionally, code may be developed that reacts to changes within a bound region of a file or within a data store, trapping or intercepting events, such as edits, additions, deletions, etc.
Owner:MICROSOFT TECH LICENSING LLC
Rich data-bound application
InactiveUS20060212842A1Simple taskSoftware engineeringDigital data processing detailsGraphicsSoftware development
In order to allow for application development without requiring extensive graphical design by software developers or extensive software knowledge by graphical designers, applications are separated into a view and a model. Properties in the view and properties in the model are associated through data binding, for example, via a data binding engine. This association allows views to be defined declaratively. Transformations may be necessary to allow the data binding. The data binding allows the data and functionality in the model to be used via the UI as defined in the view. Automatically generated UI and command binding are also enabled.
Owner:MICROSOFT TECH LICENSING LLC
Computer-implemented method and system for binding digital rights management information to a software application
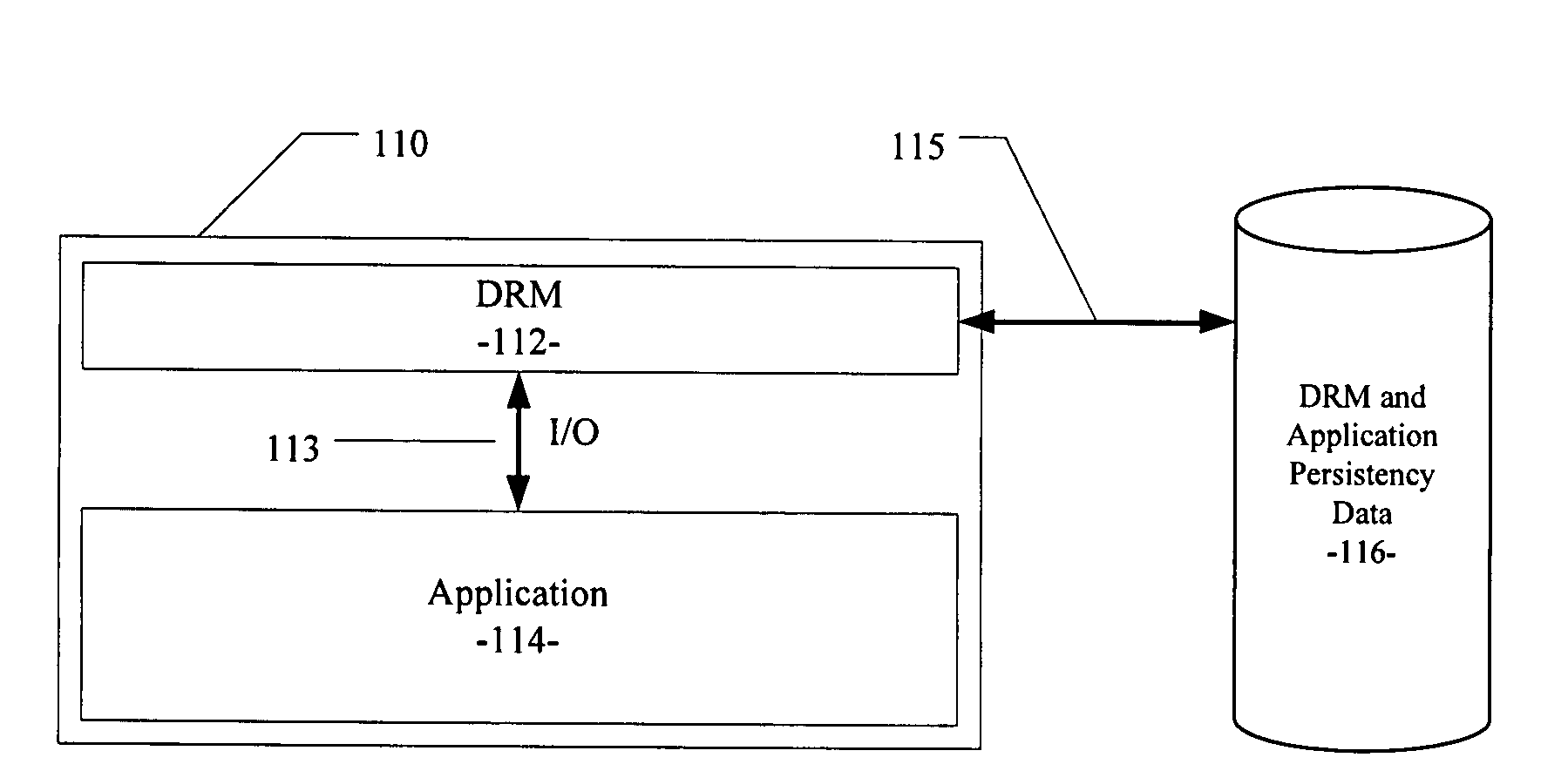
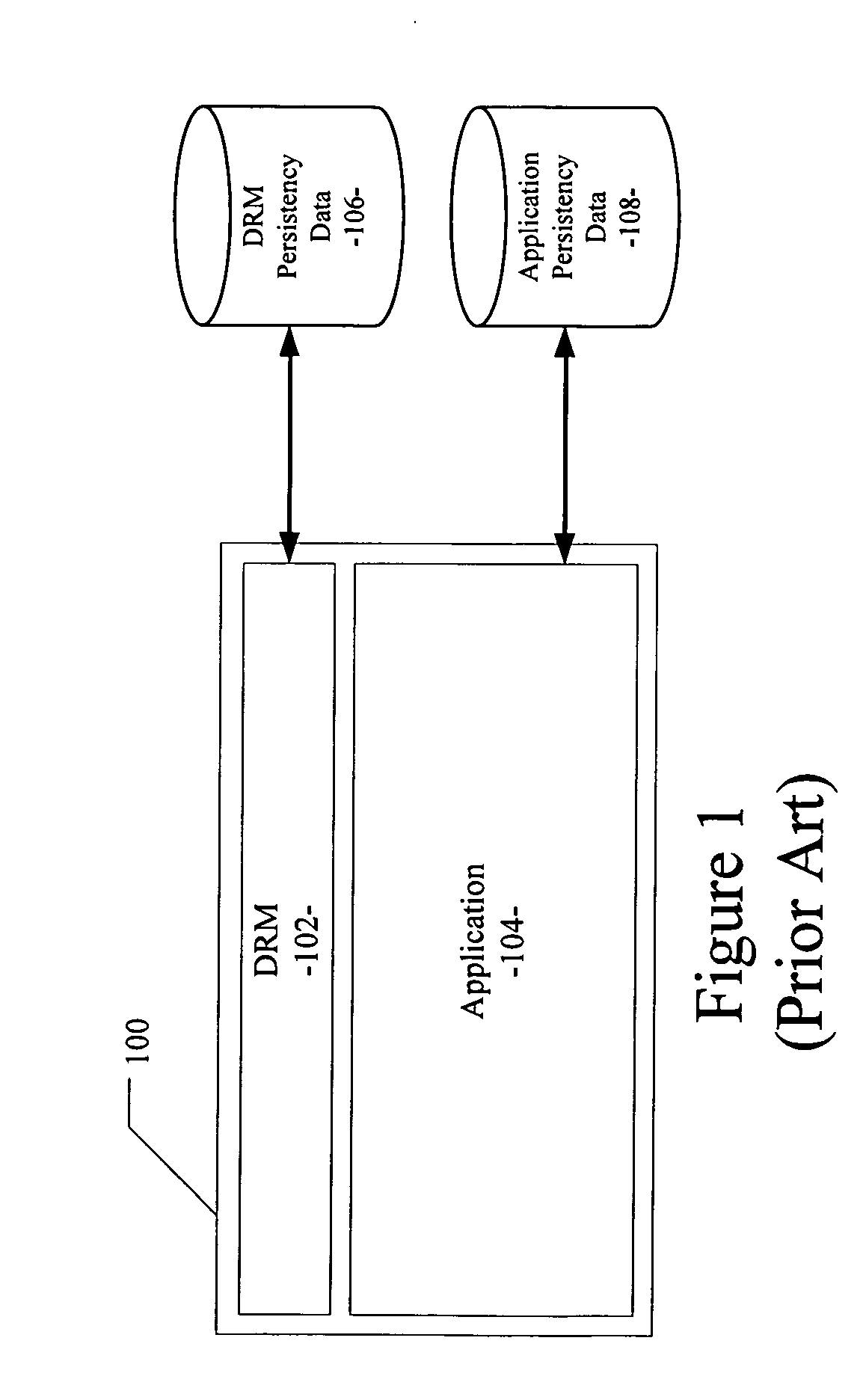
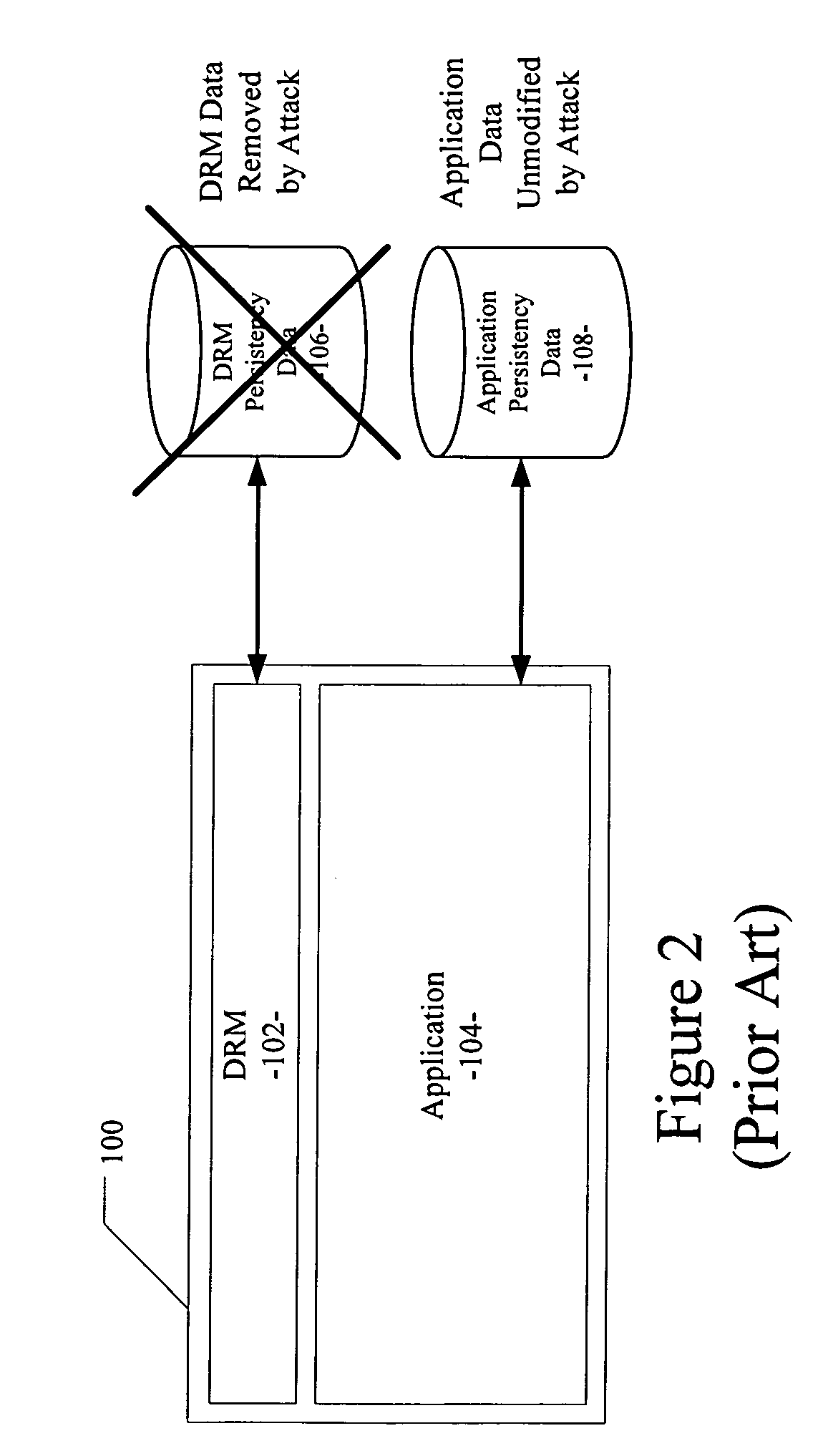
InactiveUS20080086777A1Digital data processing detailsAnalogue secracy/subscription systemsData setRights management
A computer-implemented method and system for binding digital rights management information to a software application are disclosed. The method and system include components operable to insert a digital rights management (DRM) component between a software application component and a persistent data store, intercept a request from the software application component for access to the persistent data store, bind DRM component data with software application component data in a bound data set, and store the bound data set in the persistent data store.
Owner:FLEXERA SOFTWARE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com