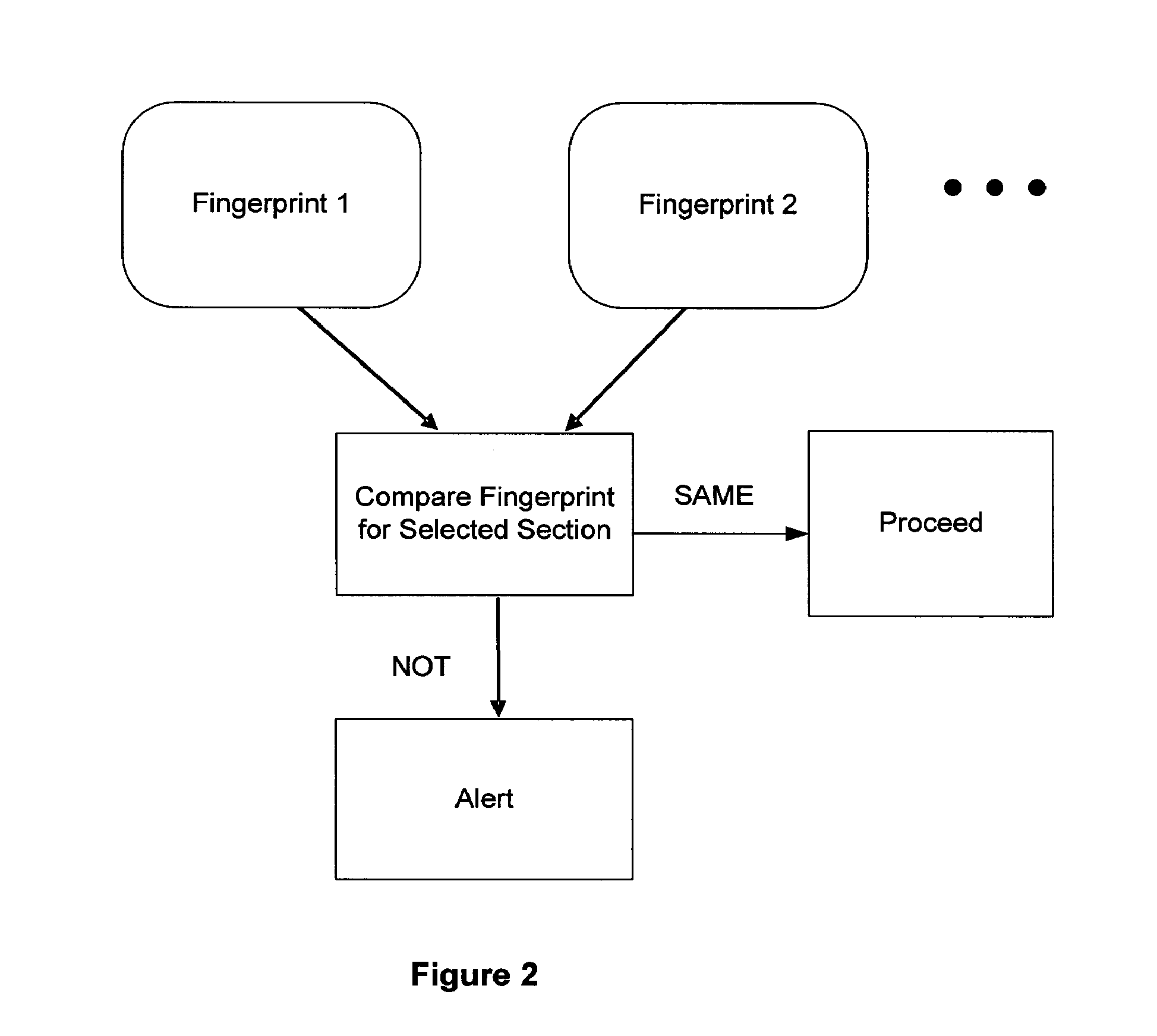
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
762 results about "Session ID" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
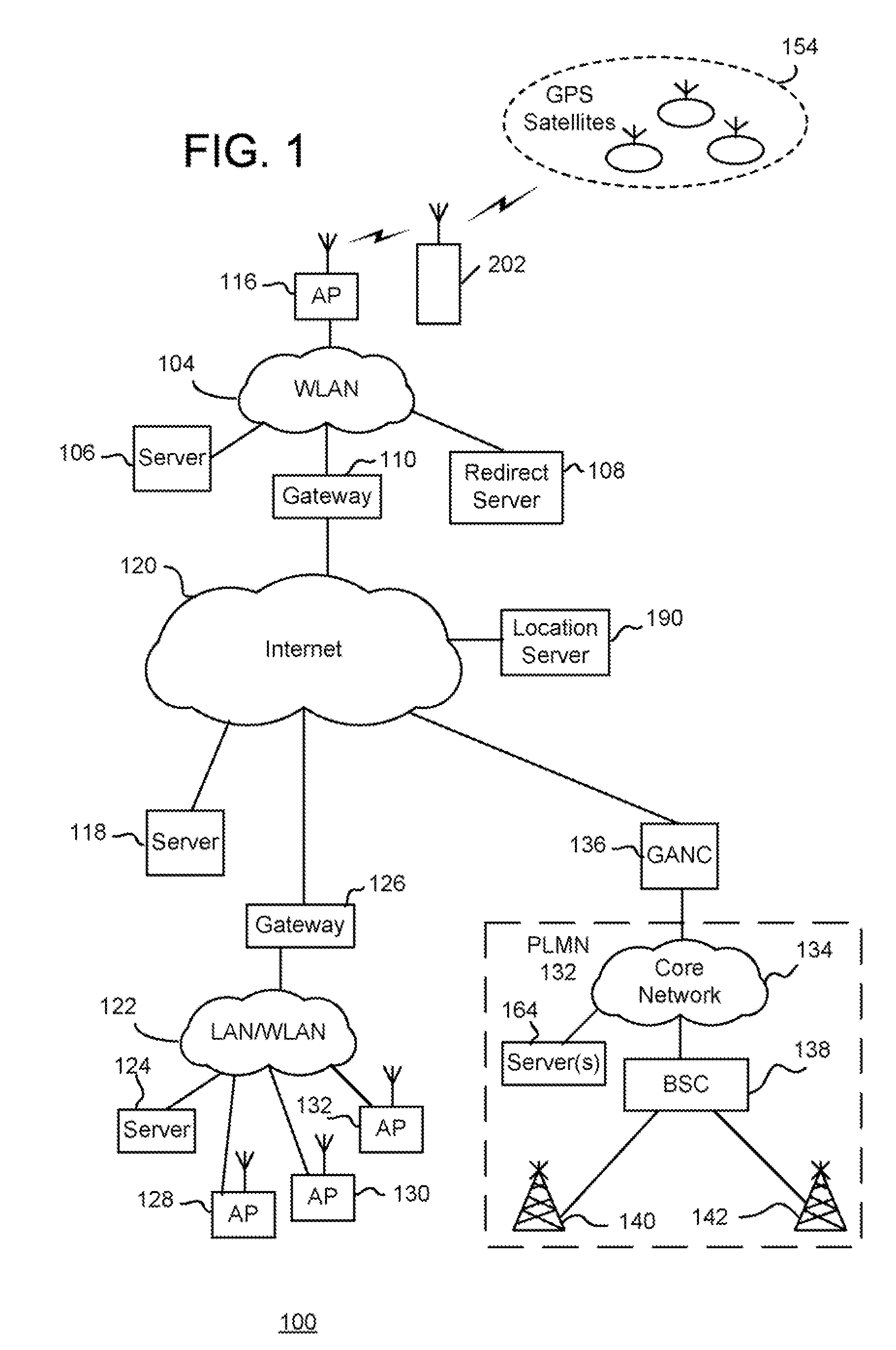
In computer science, a session identifier, session ID or session token is a piece of data that is used in network communications (often over HTTP) to identify a session, a series of related message exchanges. Session identifiers become necessary in cases where the communications infrastructure uses a stateless protocol such as HTTP. For example, a buyer who visits a seller's website wants to collect a number of articles in a virtual shopping cart and then finalize the shopping by going to the site's checkout page. This typically involves an ongoing communication where several webpages are requested by the client and sent back to them by the server. In such a situation, it is vital to keep track of the current state of the shopper's cart, and a session ID is one way to achieve that goal.
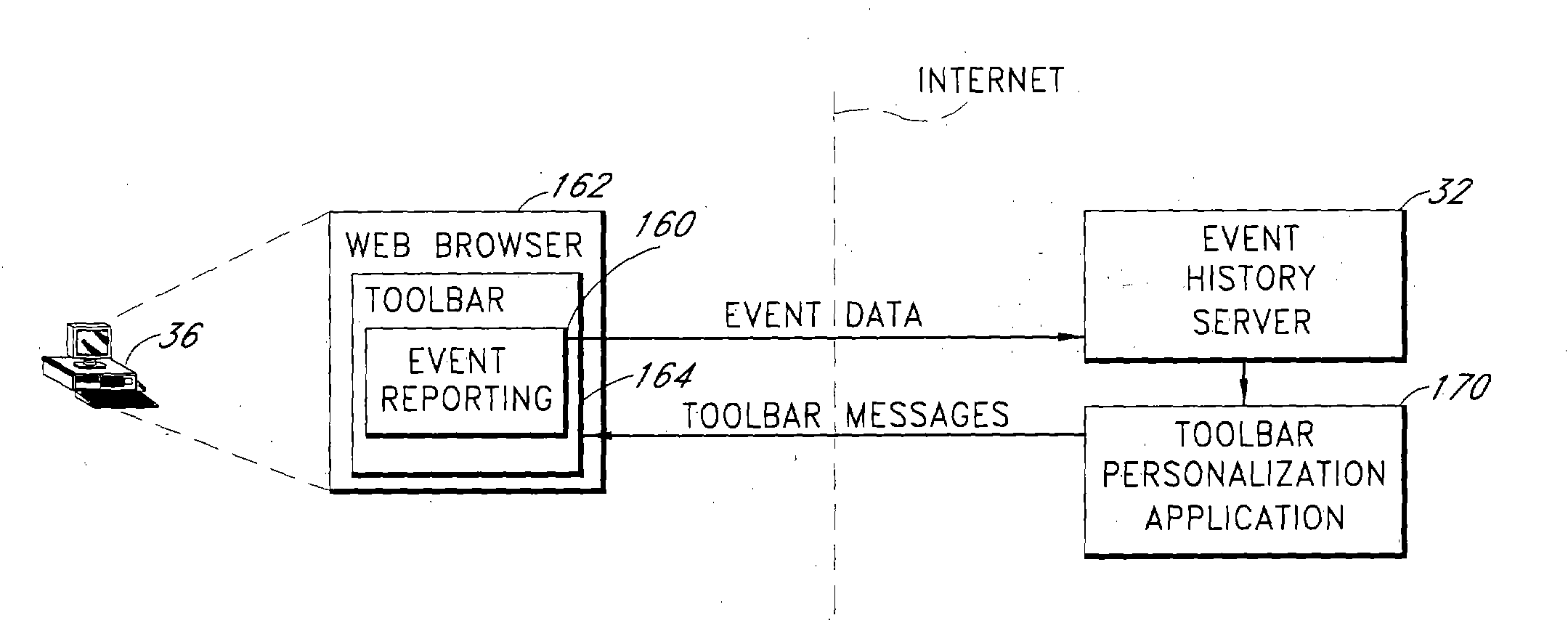
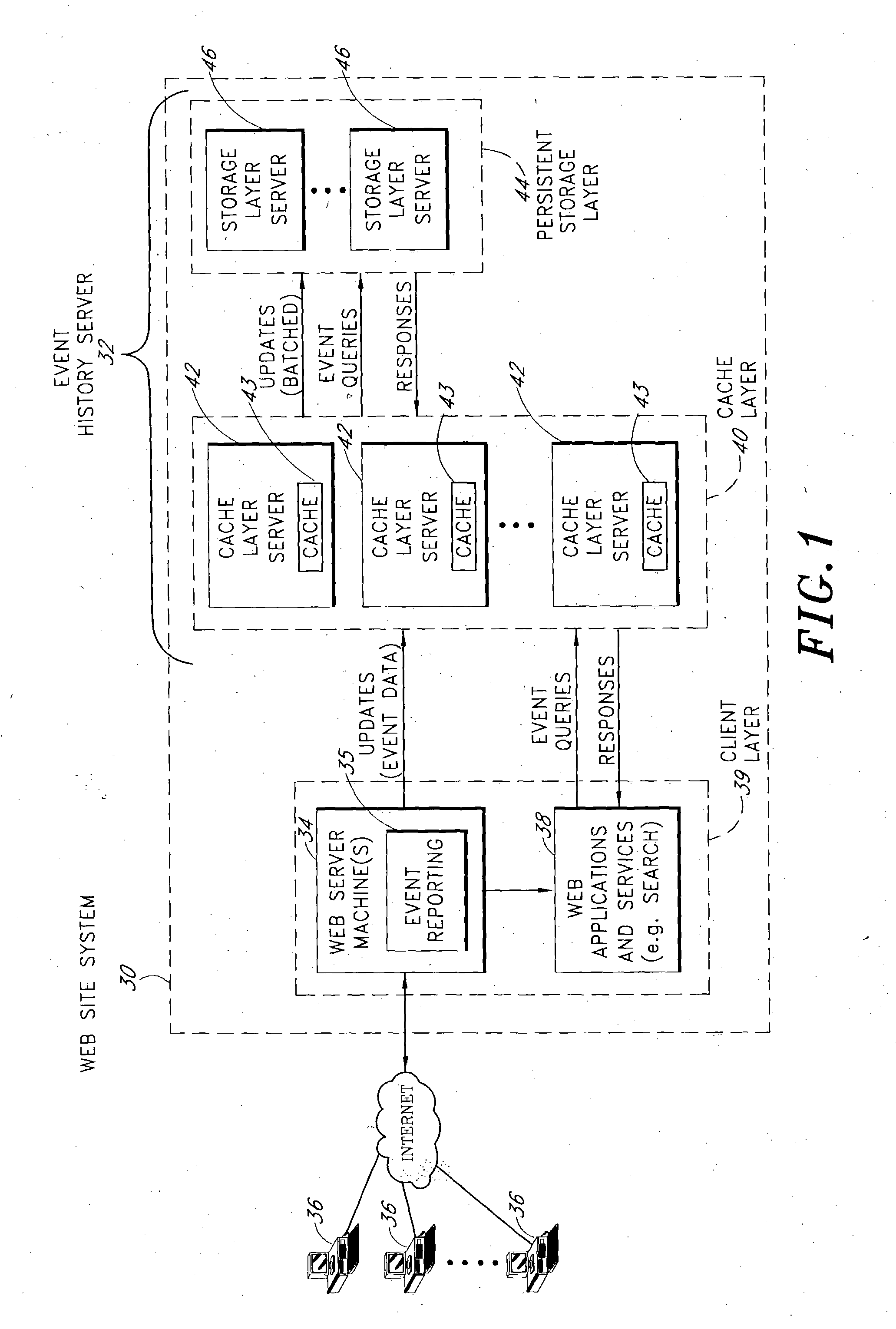
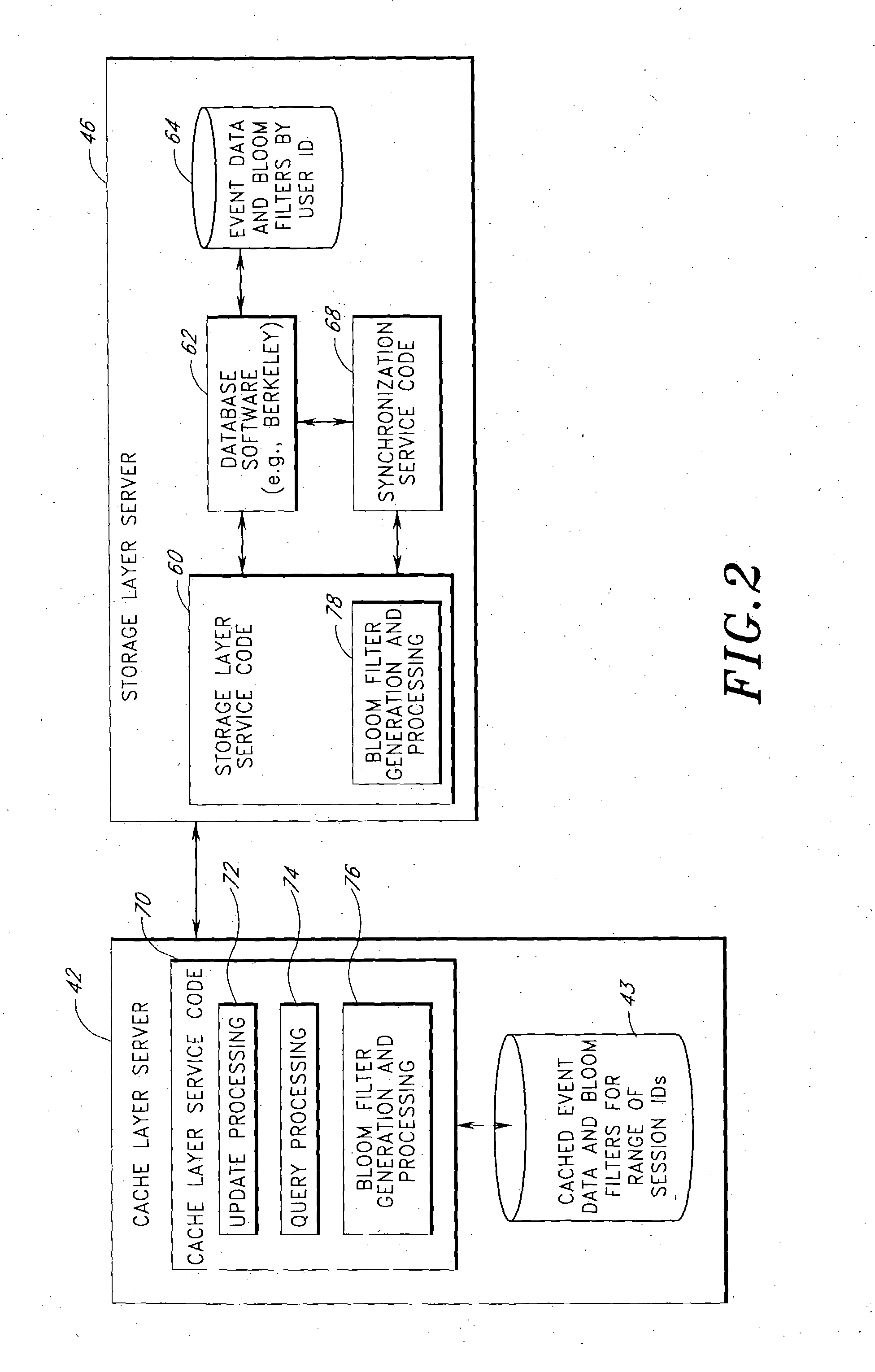
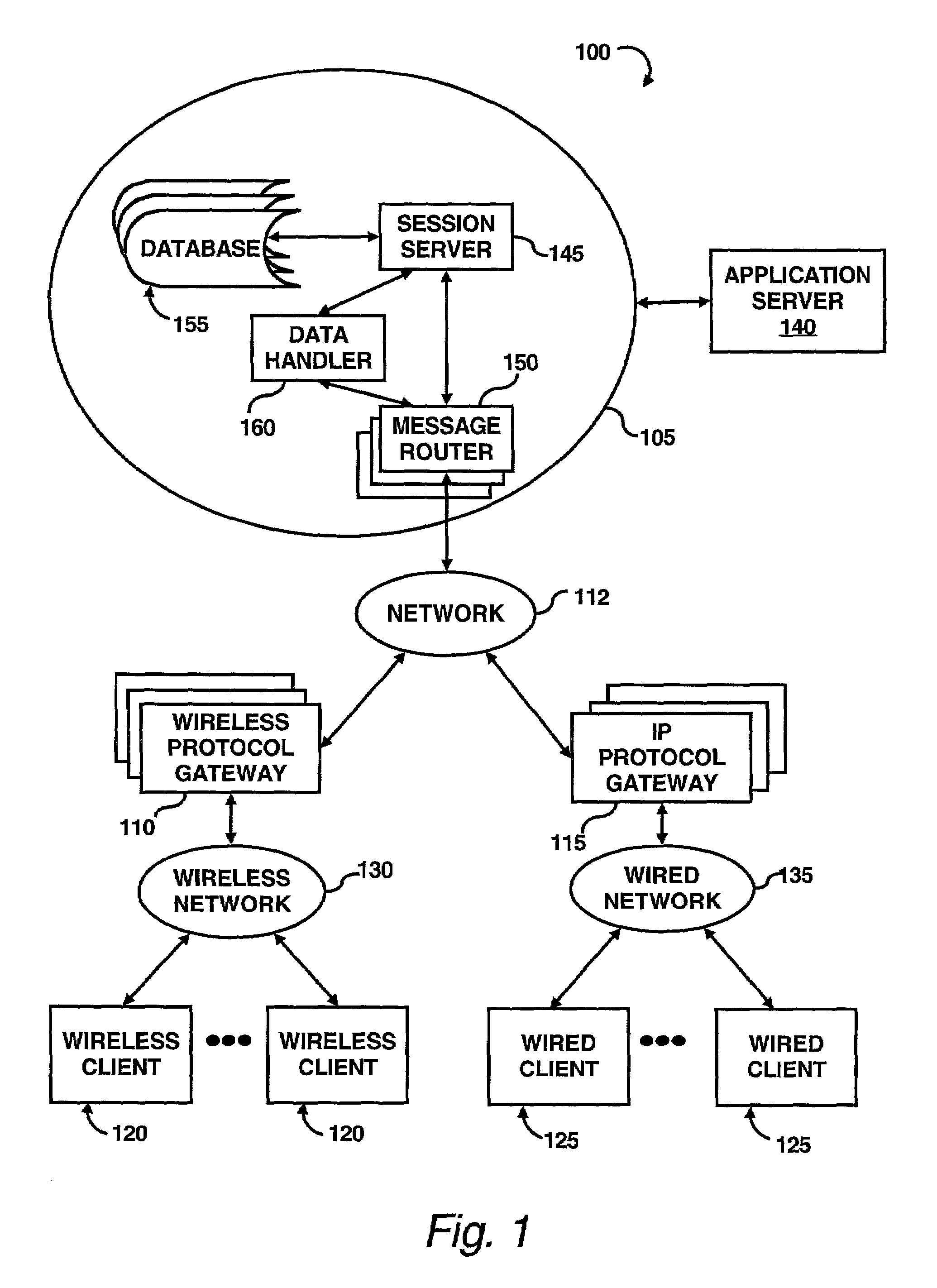
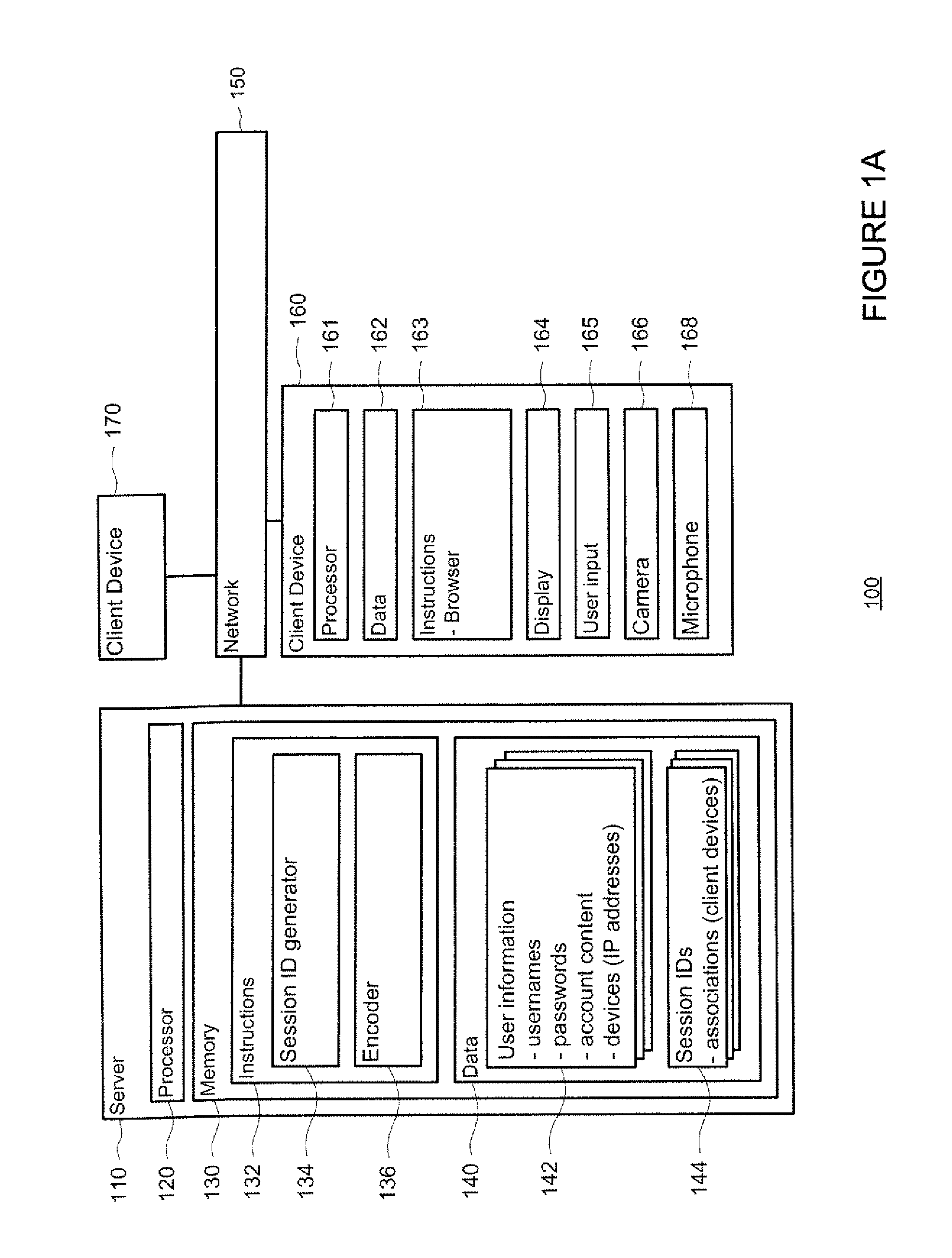
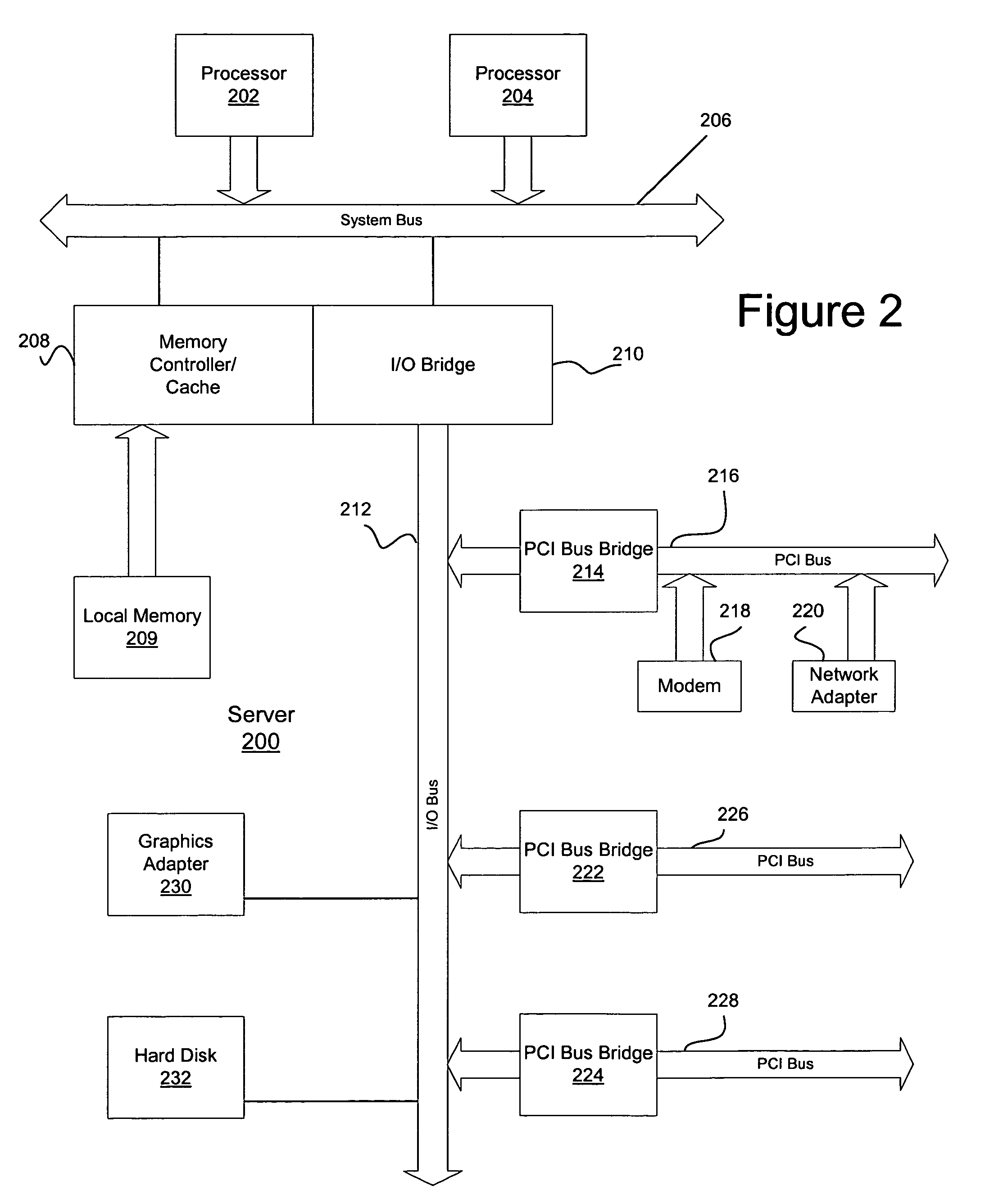
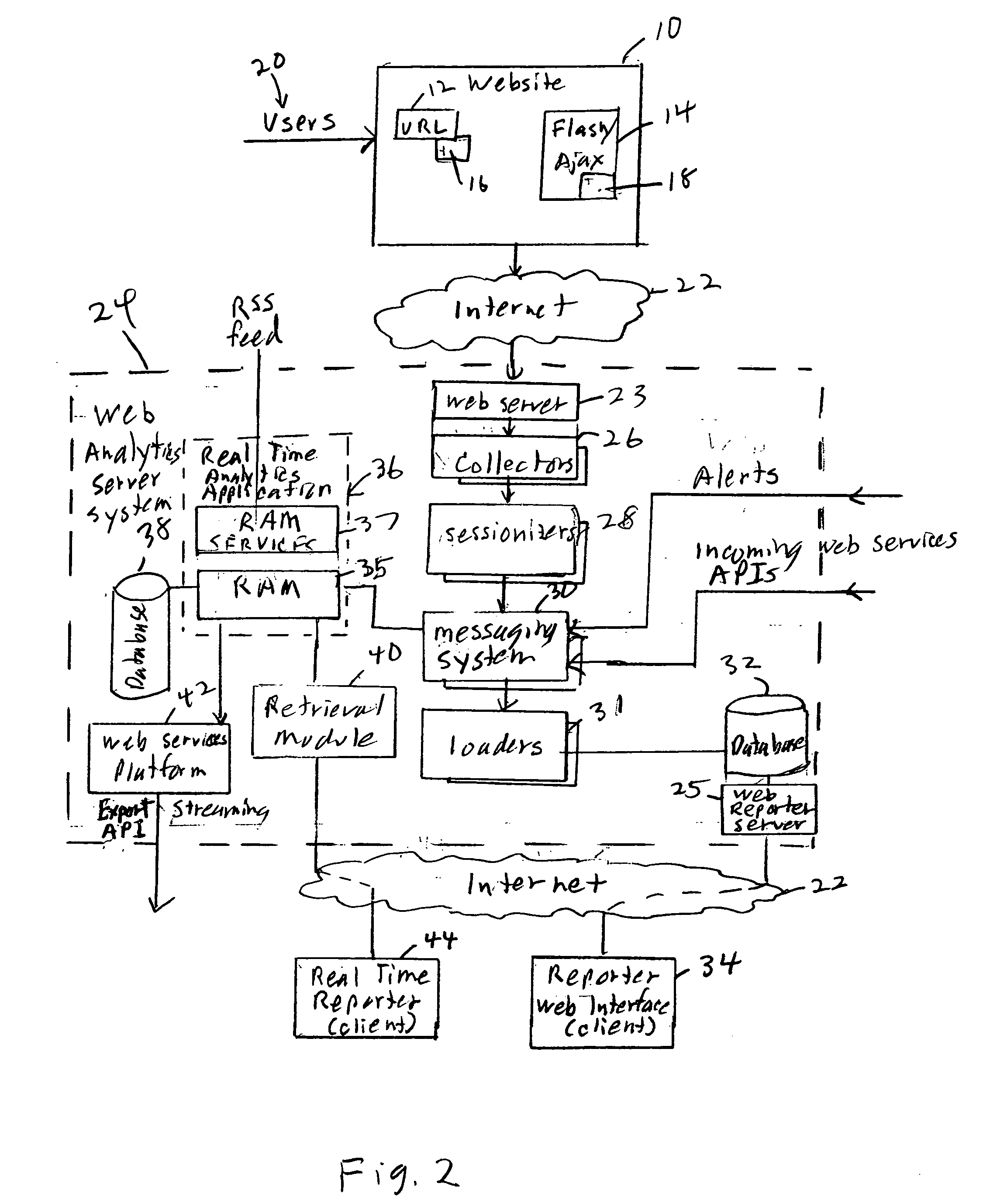
Server architecture and methods for persistently storing and serving event data
ActiveUS20050033803A1Effective evaluationMultiple digital computer combinationsWebsite content managementWeb siteEvent type
A web site system includes an event history server system that persistently stores event data reflective of events that occur during browsing sessions of web site users, and makes such data available to other applications and services in real time. The server system may, for example, be used to record information about every mouse click of every recognized user, and may also be used to record other types of events such as impressions and mouse-over events. The event data of a particular user may be retrieved from the server system based on event type, event time of occurrence, and various other criteria. In one embodiment, the server system includes a cache layer that caches event data by session ID, and includes a persistent storage layer the persistently stores the event data by user ID. Also disclosed are various application features that may be implemented using the stored event data.
Owner:AMAZON TECH INC
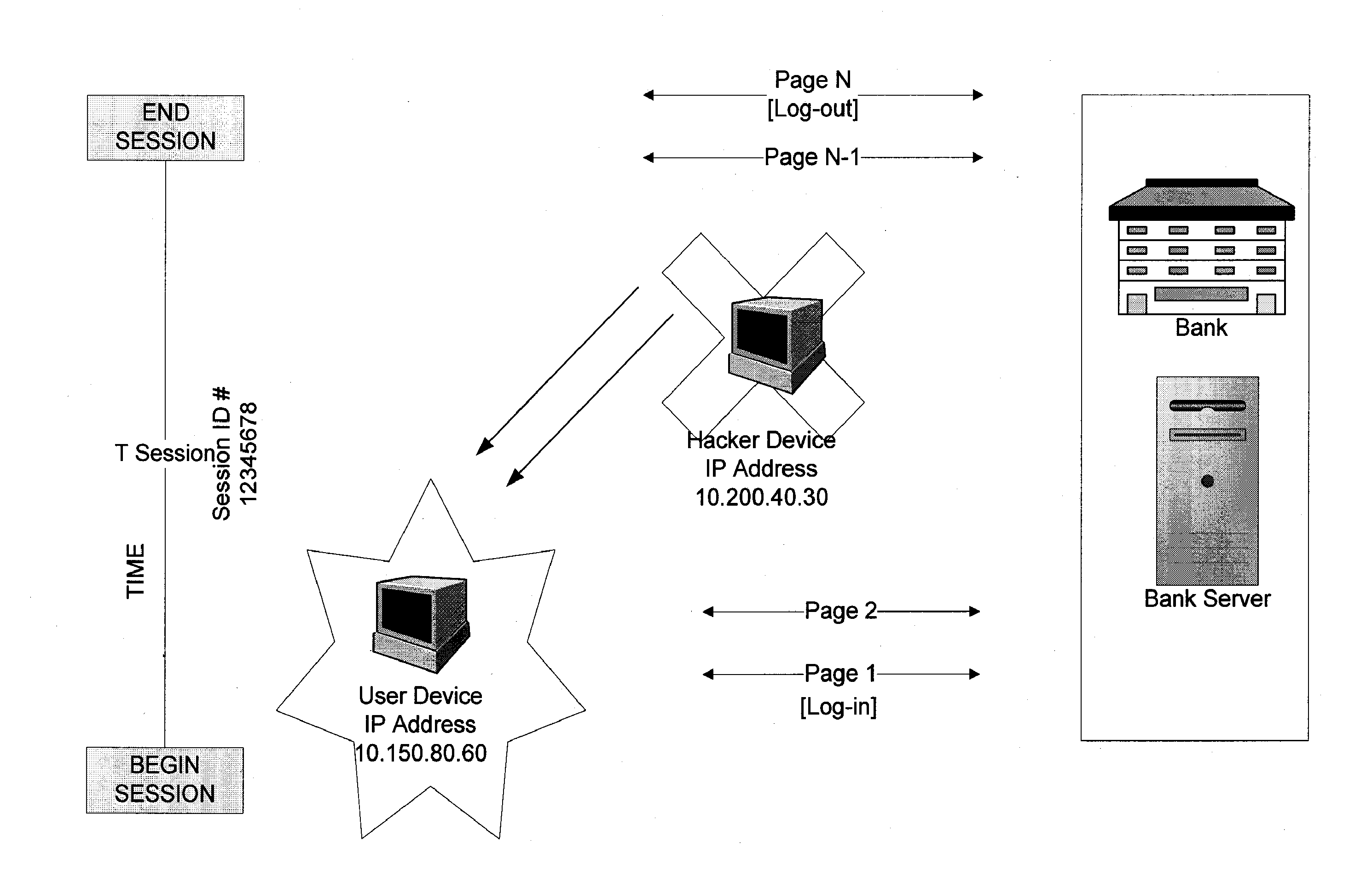
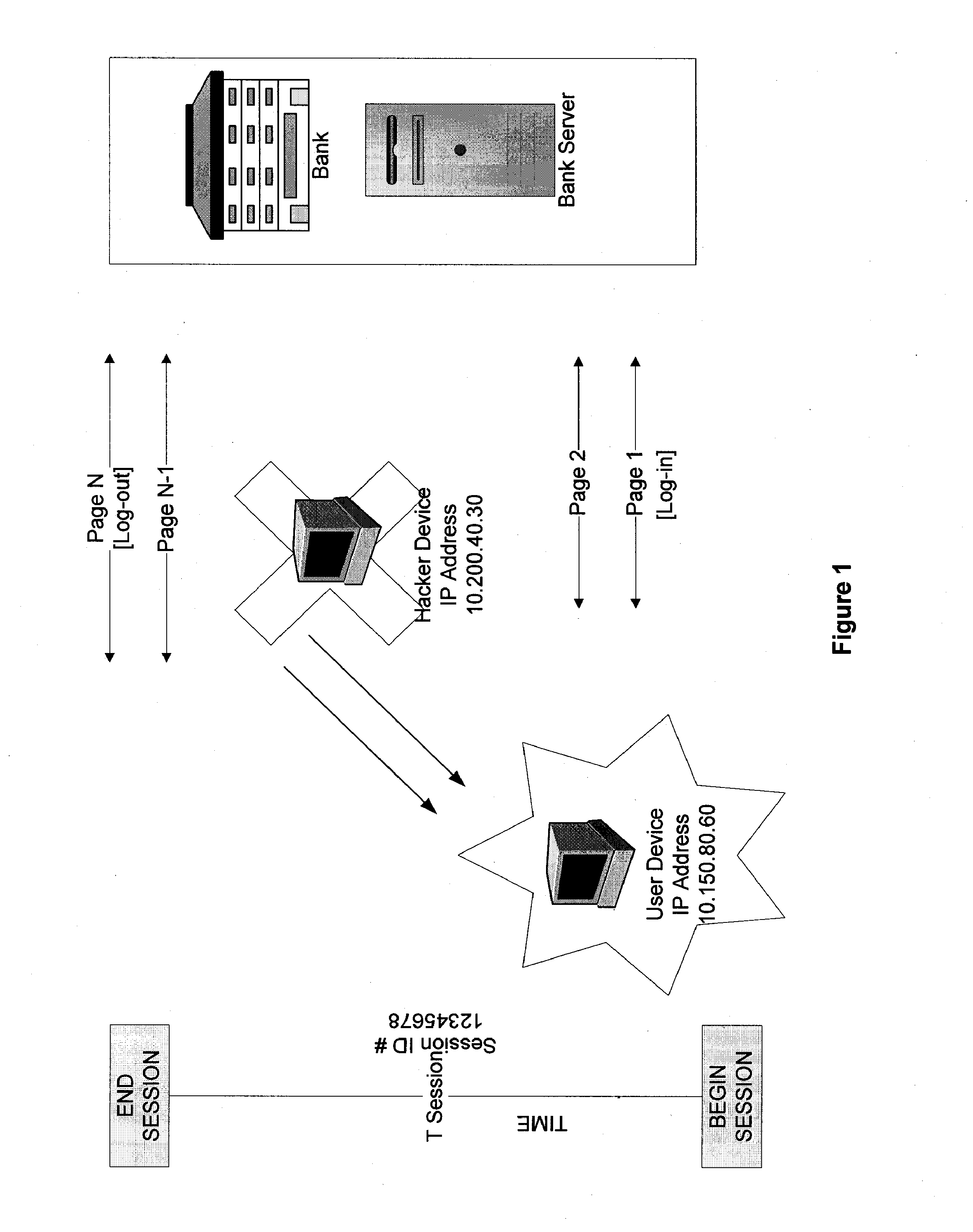
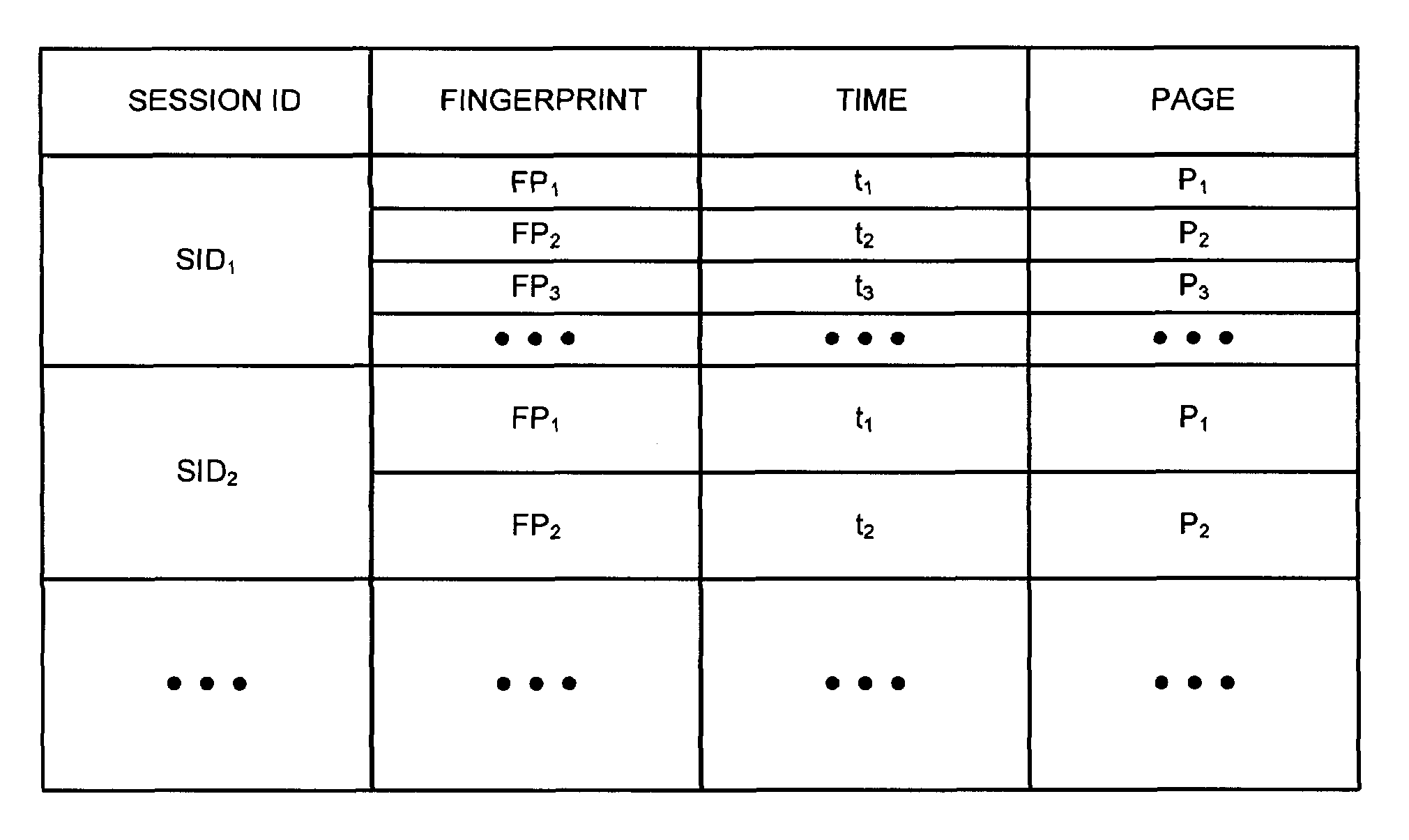
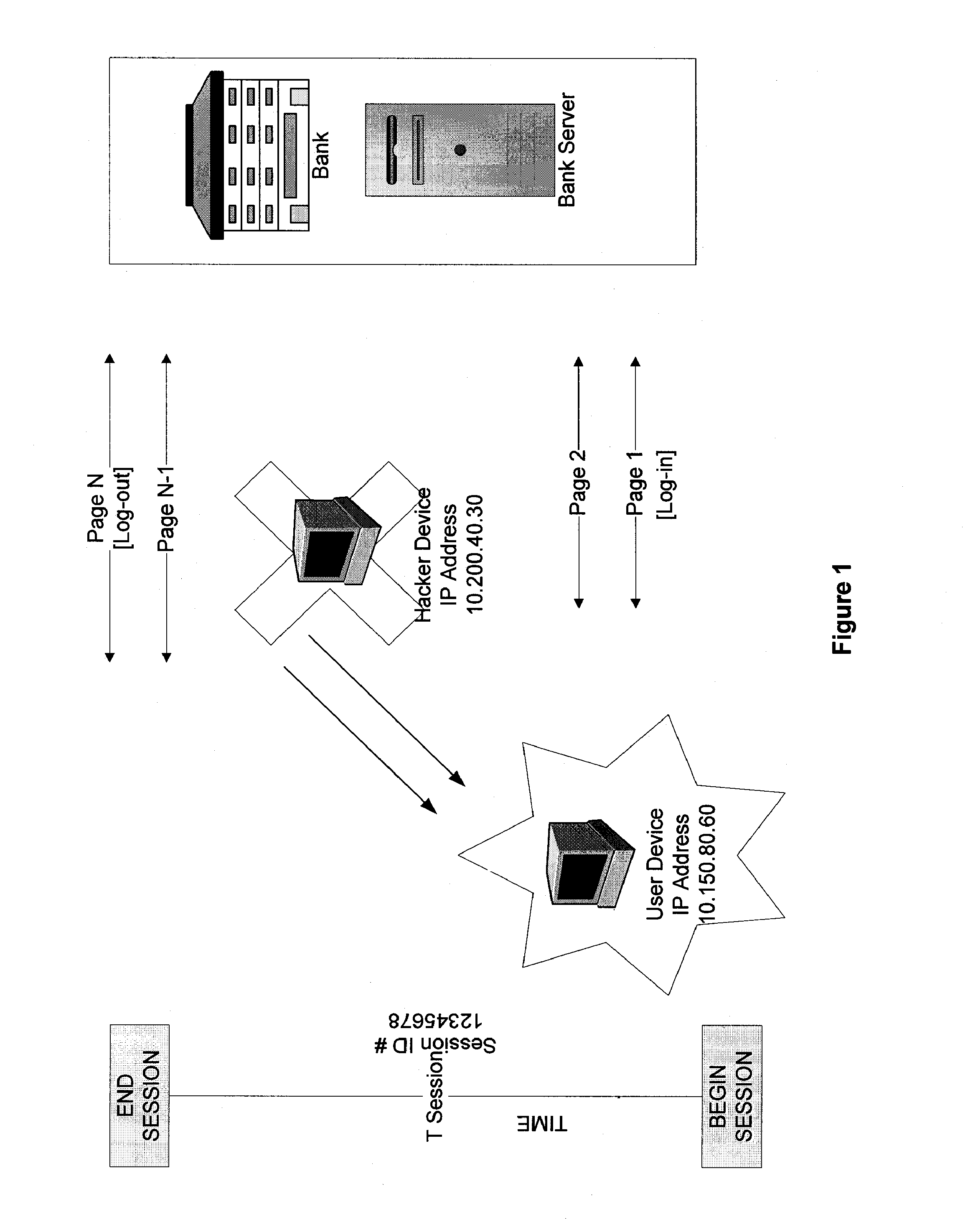
Systems and methods for detection of session tampering and fraud prevention
ActiveUS20070234409A1Secure performanceIdentify theftMemory loss protectionError detection/correctionMan-in-the-middle attackOperating system
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
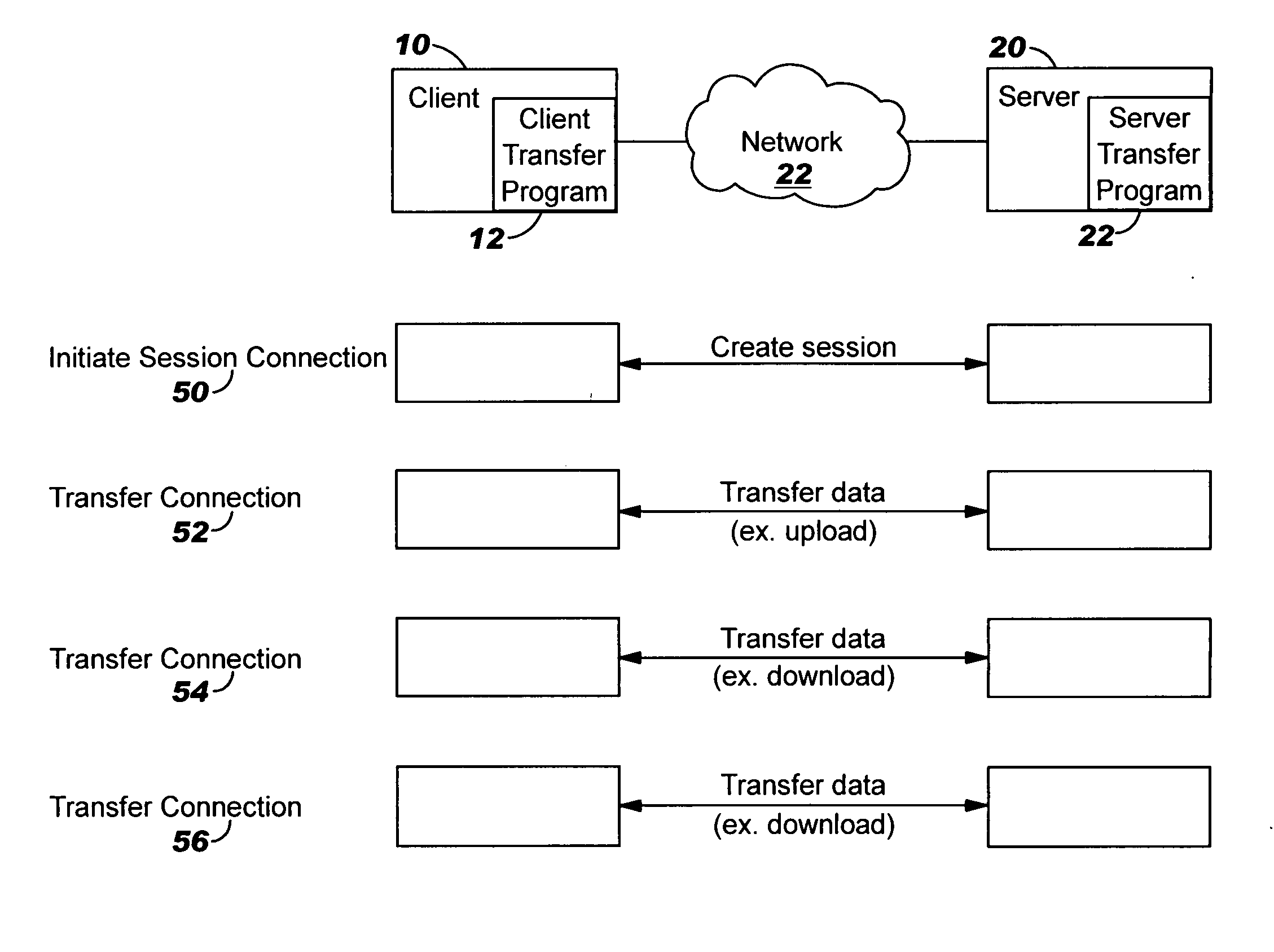
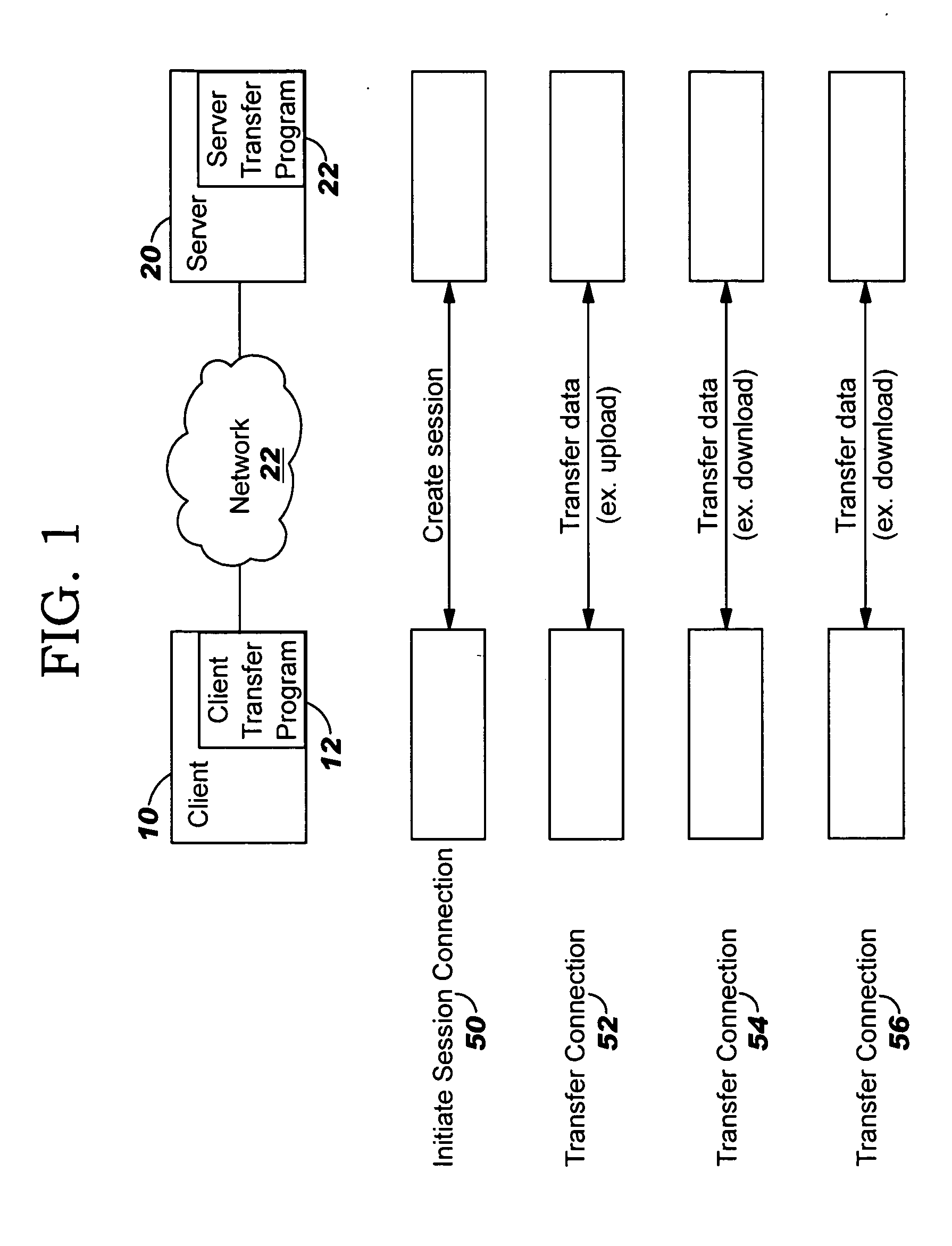
System, method and program for protecting communication
ActiveUS20050273592A1Digital data processing detailsUser identity/authority verificationComputer hardwareSession ID
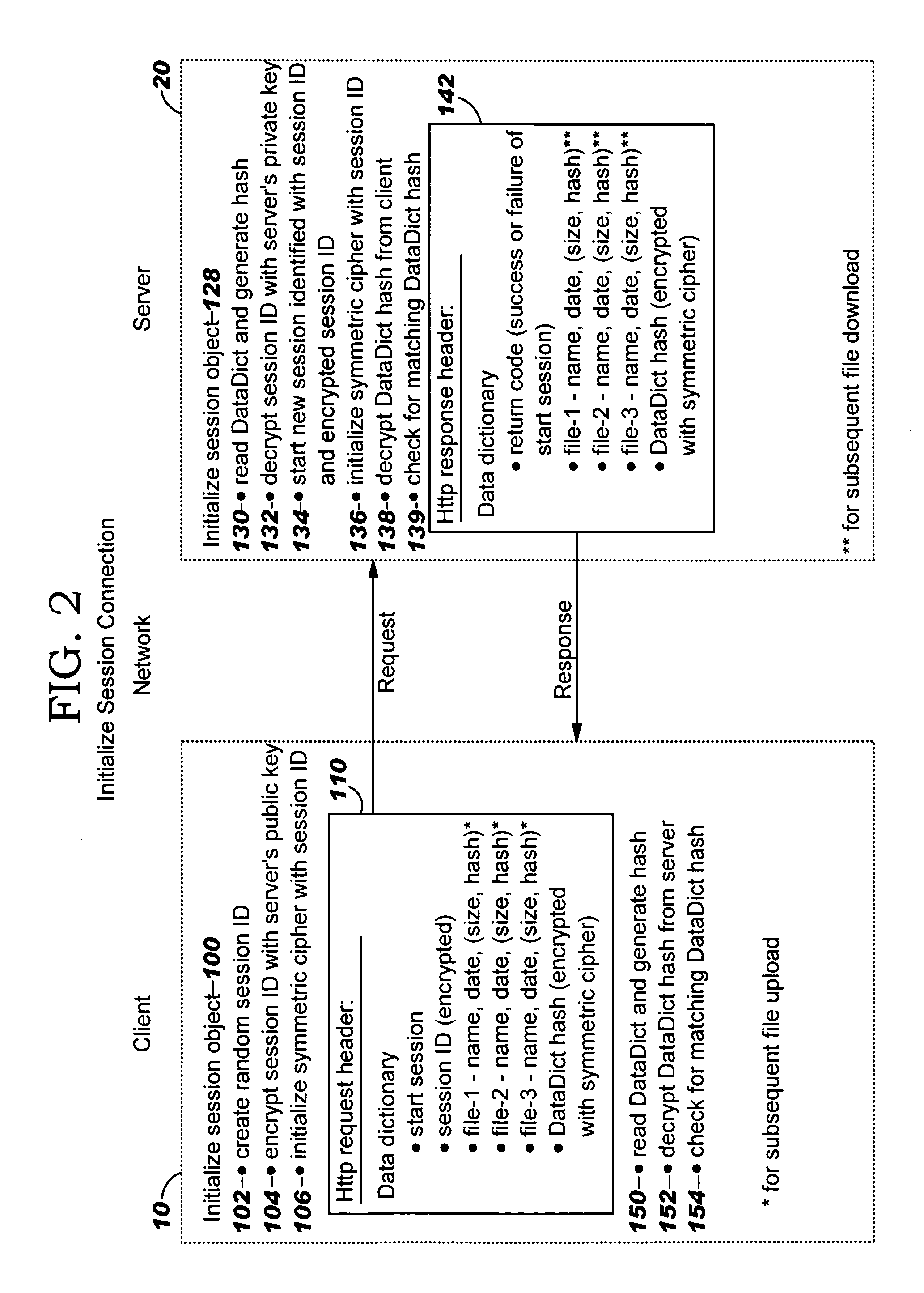
A method for transferring data between a first computer and a second computer. The first computer sends a first request to the second computer in a first connection. The first request includes a request to start a session, an encrypted ID of the session, and an encrypted hash value for information in the first request. The information in the first request comprises the request to start the session and the encrypted session ID. The second computer receives the first request, and as a result, decrypts the encrypted hash value in the first request, independently determines a hash value for the information in the first request and compares the independently determined hash value to the decrypted hash value. If there is match, the second computer starts a session with the first computer. Subsequently, the first computer sends a second request to the second computer in a second connection in the session. The second request includes a request to download or upload data of a file, an encrypted ID of the session, an identity of the file to at least partially upload or download, and an encrypted hash value for information in the second request. The information in the second request comprises the request to download or upload data, the encrypted session ID and the file identity. The second computer receives the second request in the session, and as a result, decrypts the encrypted hash value in the second request, independently determines a hash value for the information in the second request and compares the independently determined hash value to the decrypted hash value. If there is match, the second computer processes the request to at least partially download or upload the file.
Owner:KYNDRYL INC
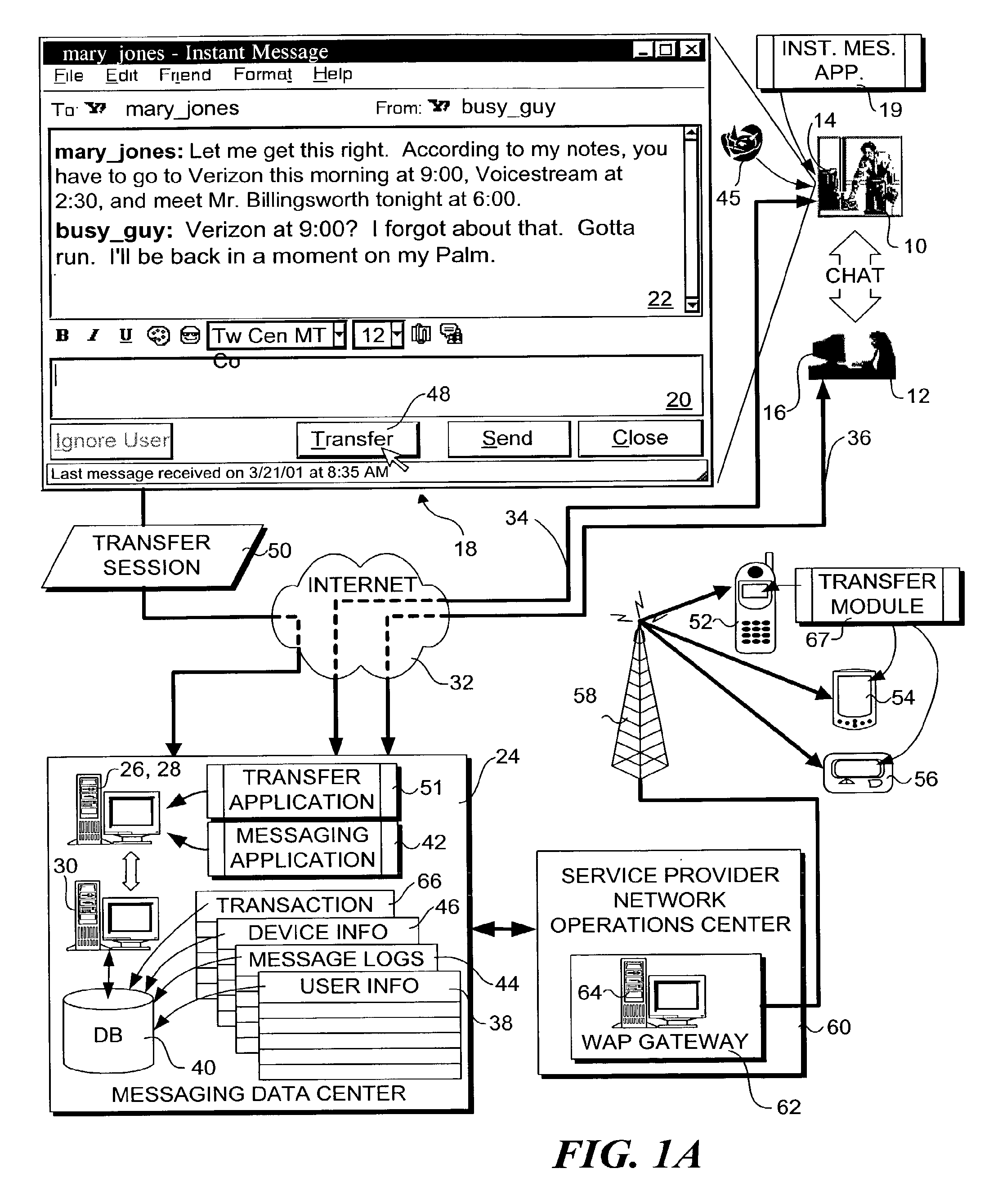
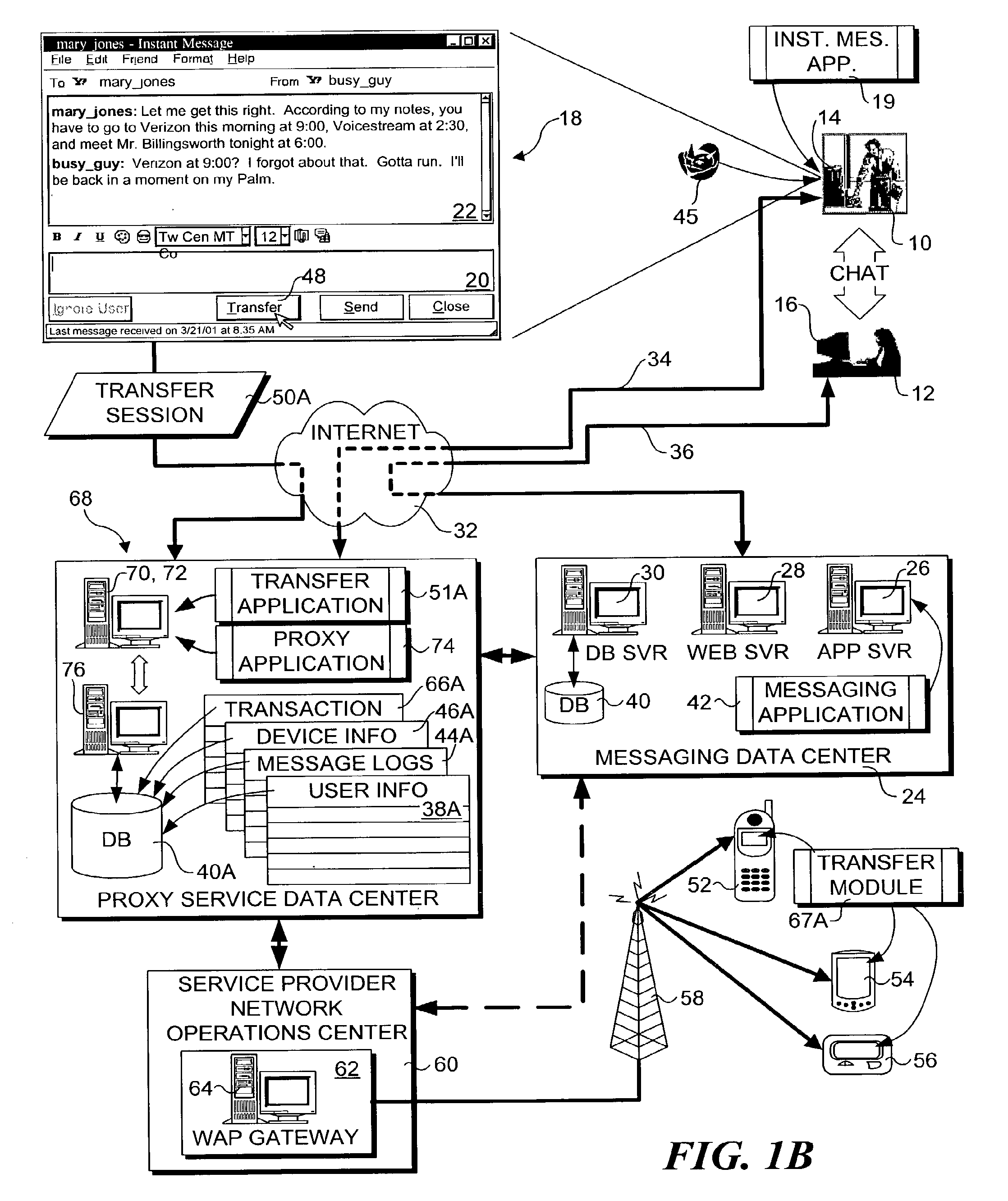
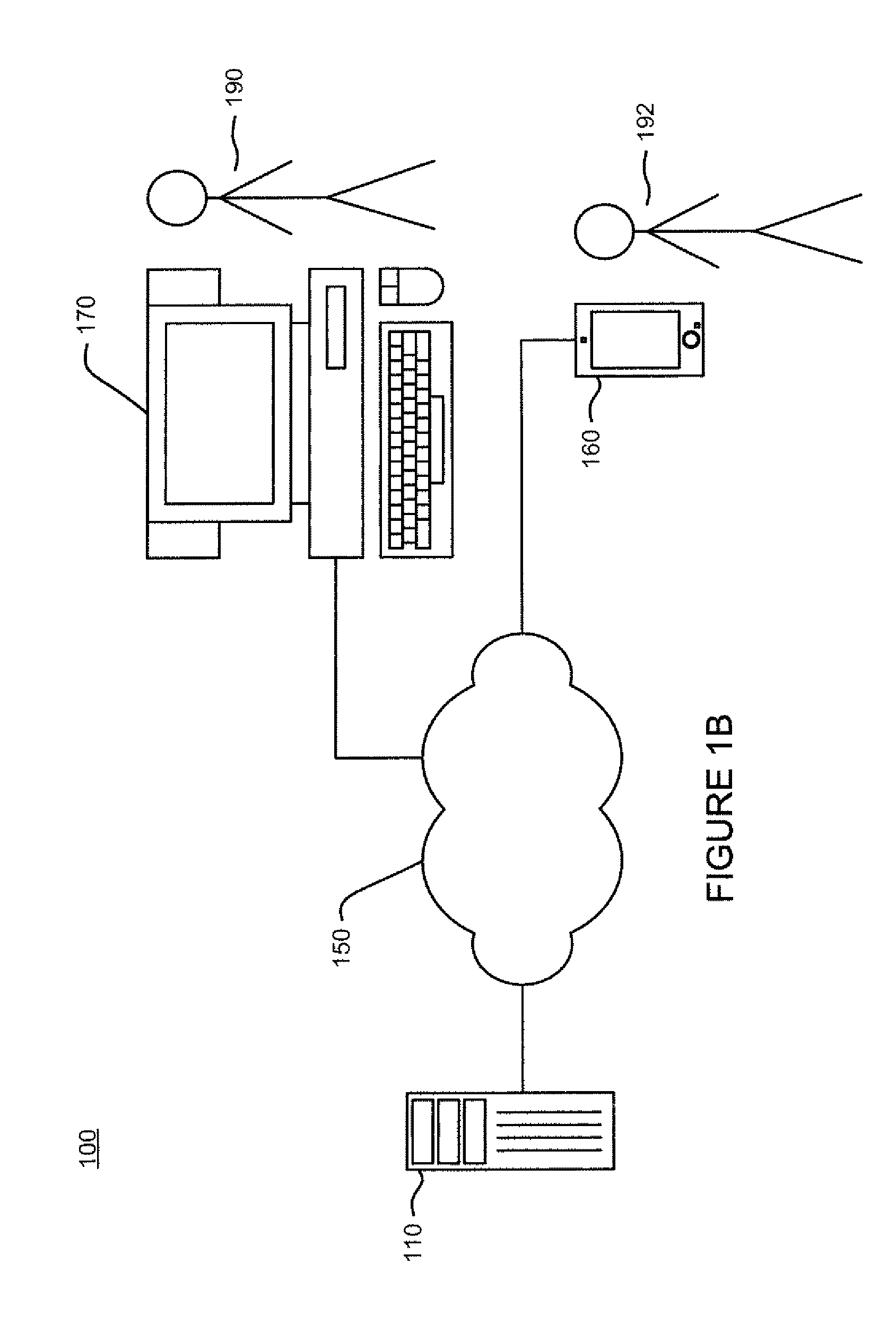
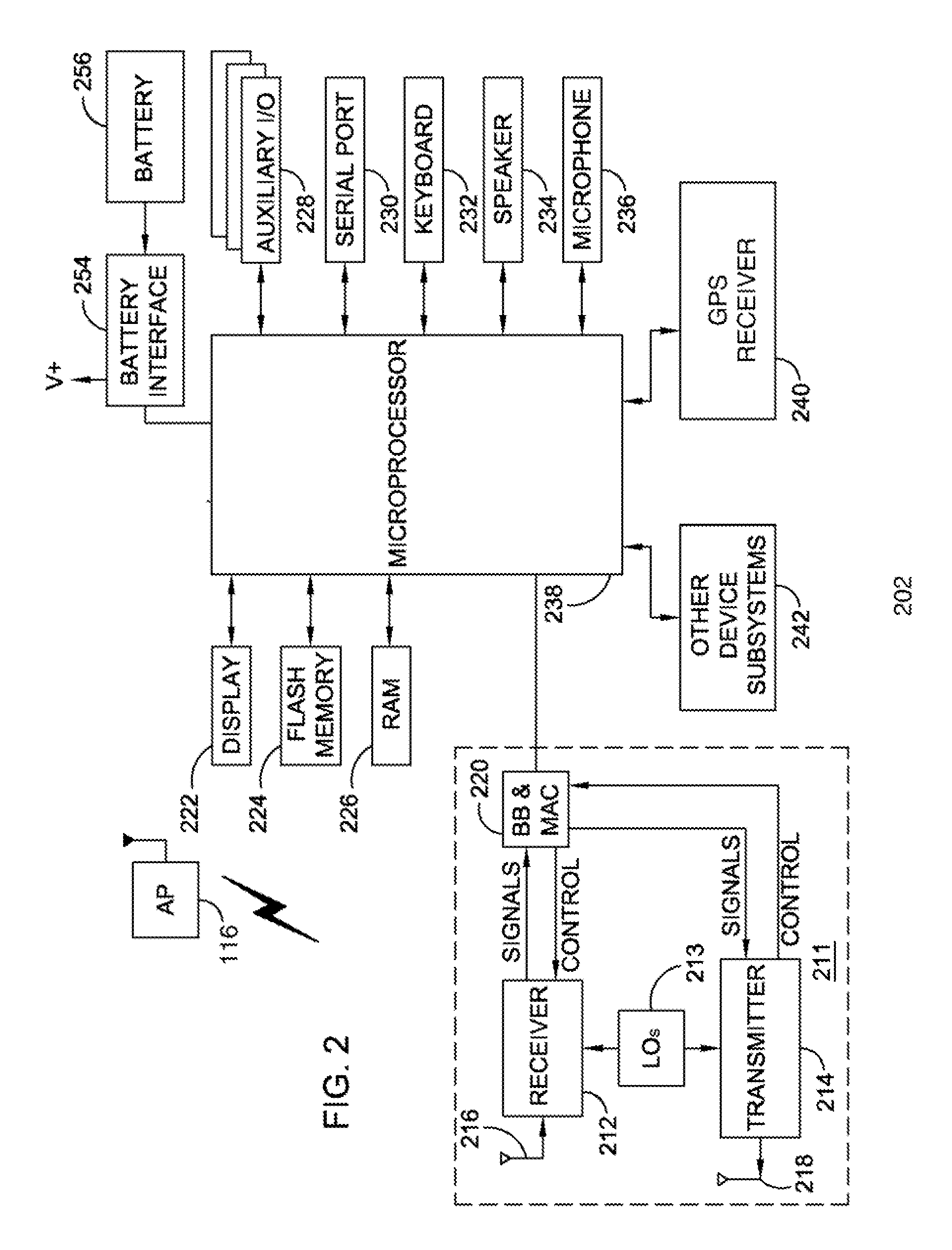
Method and system for transferring a computer session between devices
InactiveUS7487248B2Multiple digital computer combinationsTransmissionComputer SessionPersonal computer
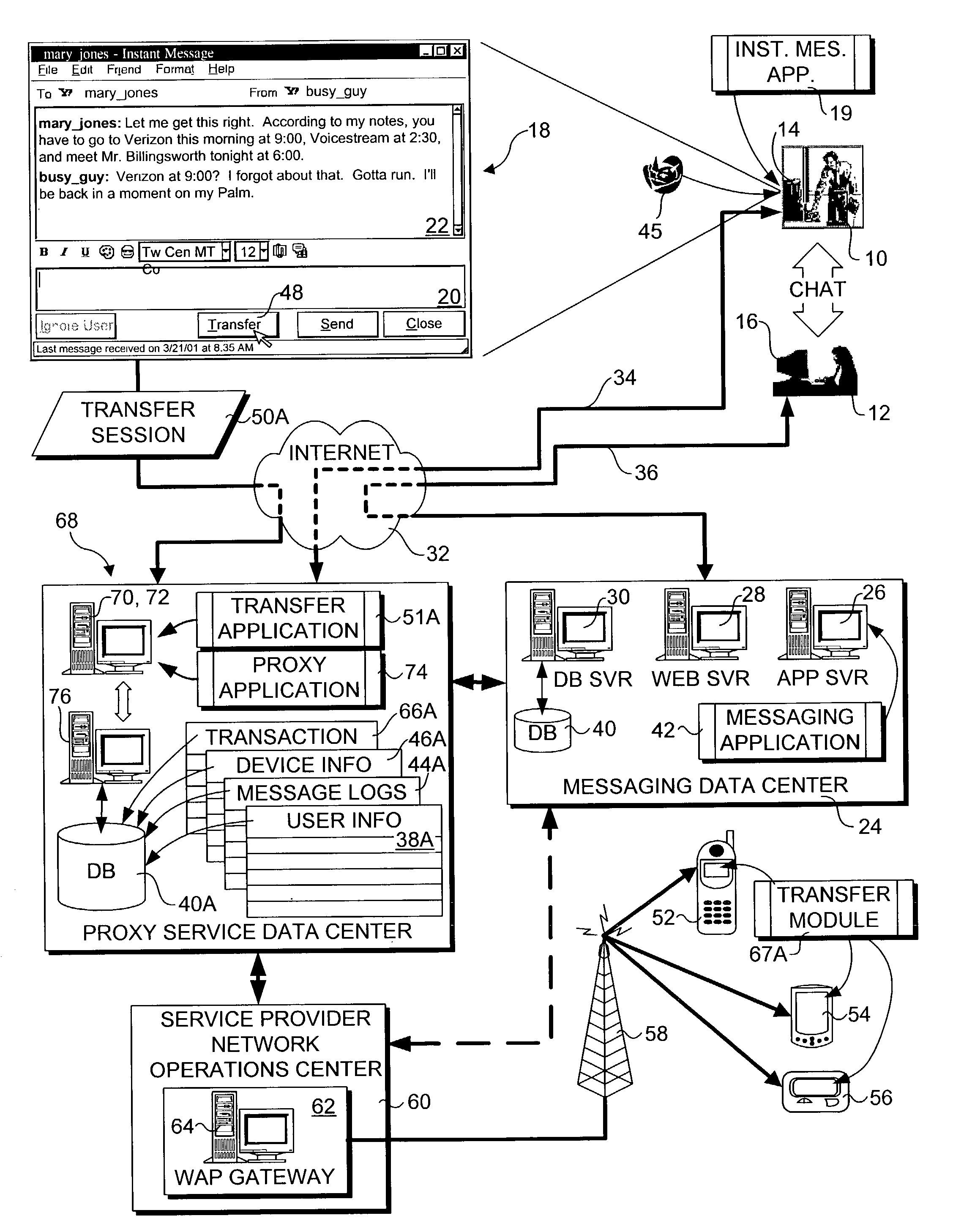
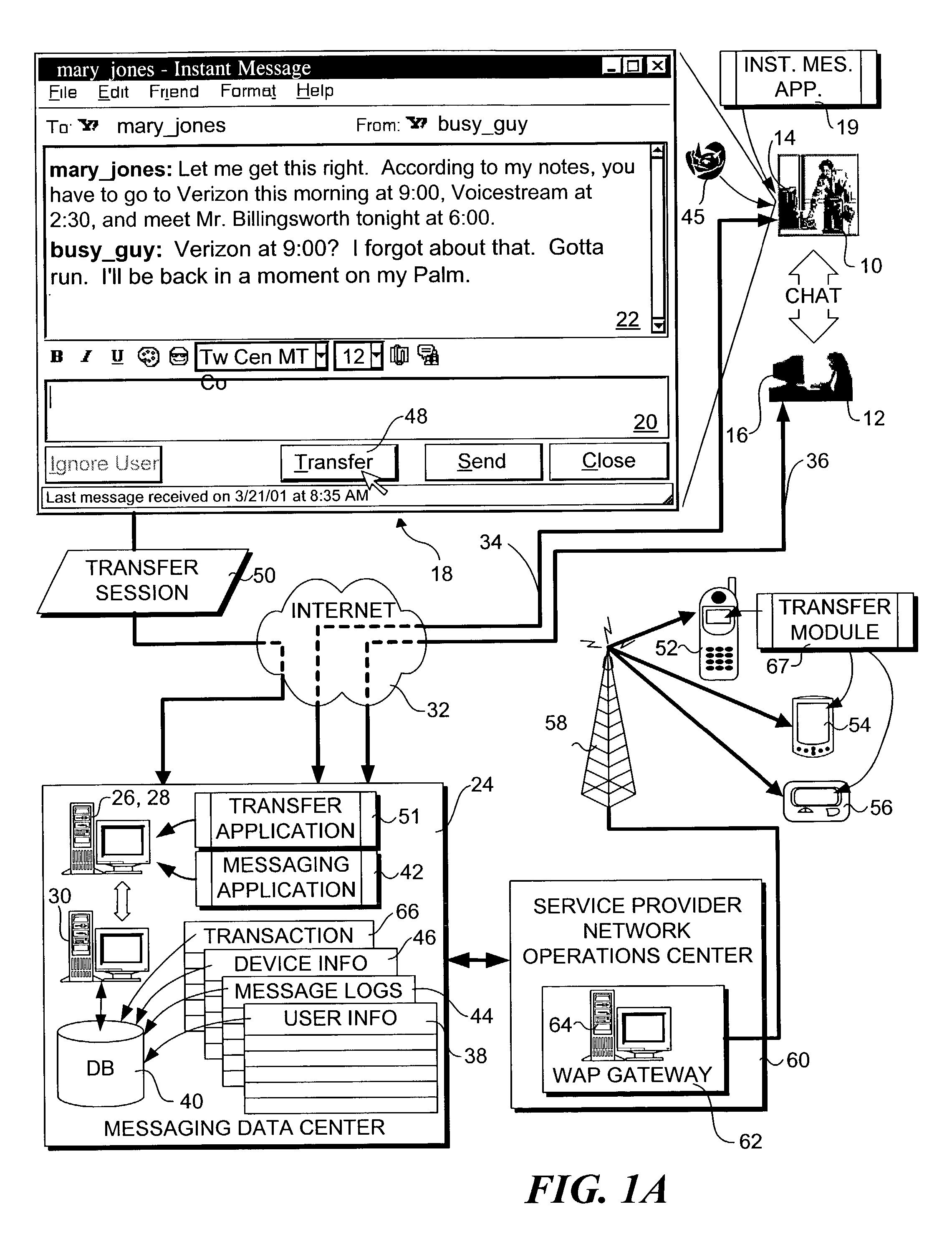
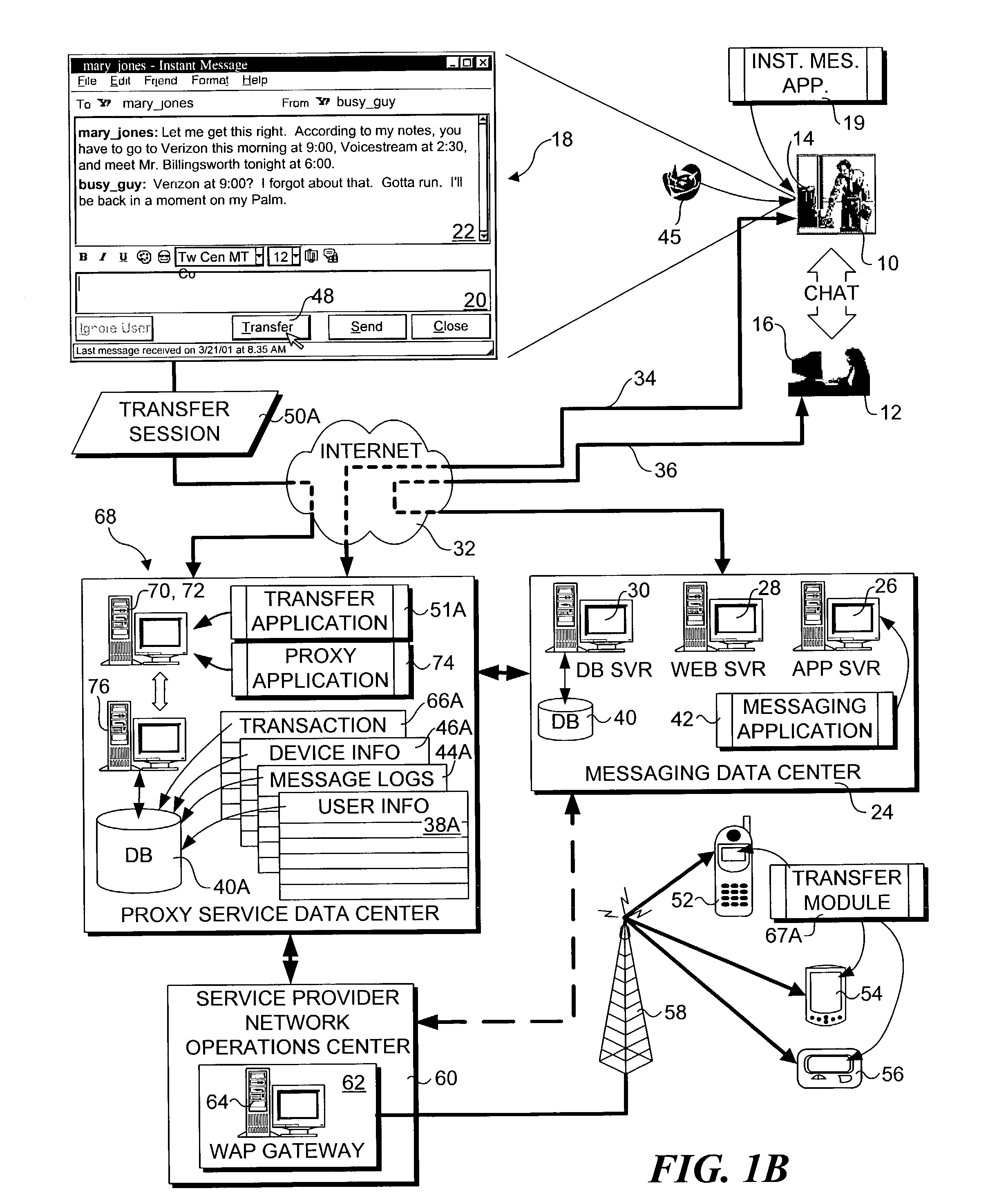
A method and system for transferring a computer session between devices, such as a land-line device to a wireless device. A user launches a computer session on a first device, such as a personal computer. The user may then selectively transfer the computer session to another device, such as a wireless device, through activation of a triggering signal or other transfer request means. In response, the context of the computer session is determined as it is being performed on the first device, and corresponding context data is transferred to the second device. An applicable application on the second device is opened and loaded with applicable context data to continue the session. Several session transfer mechanisms, including use of an online service, proxy mechanisms, and peer-to-peer communication links, are disclosed.
Owner:CONTEMPORARY DISPLAY LLC
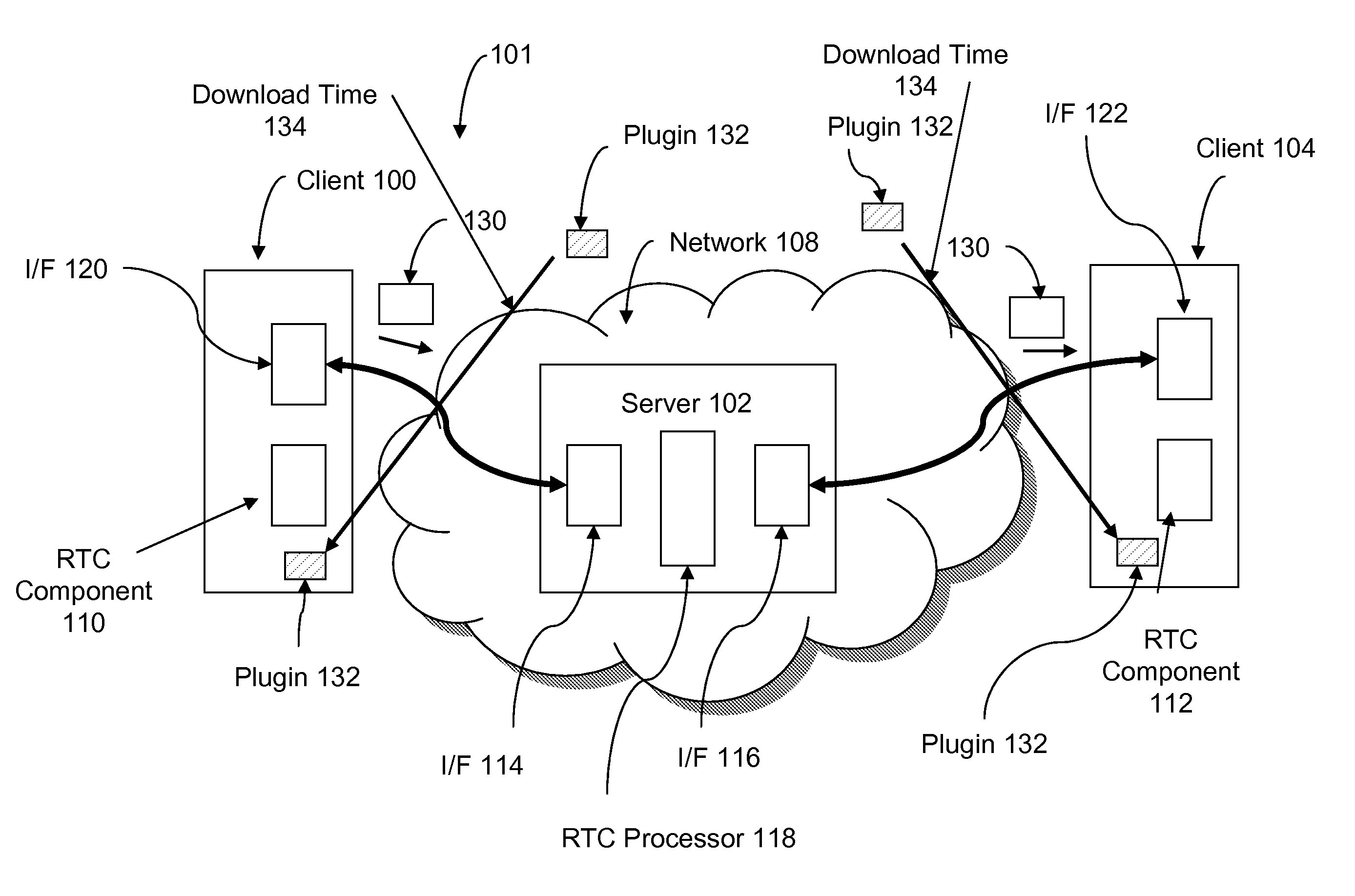
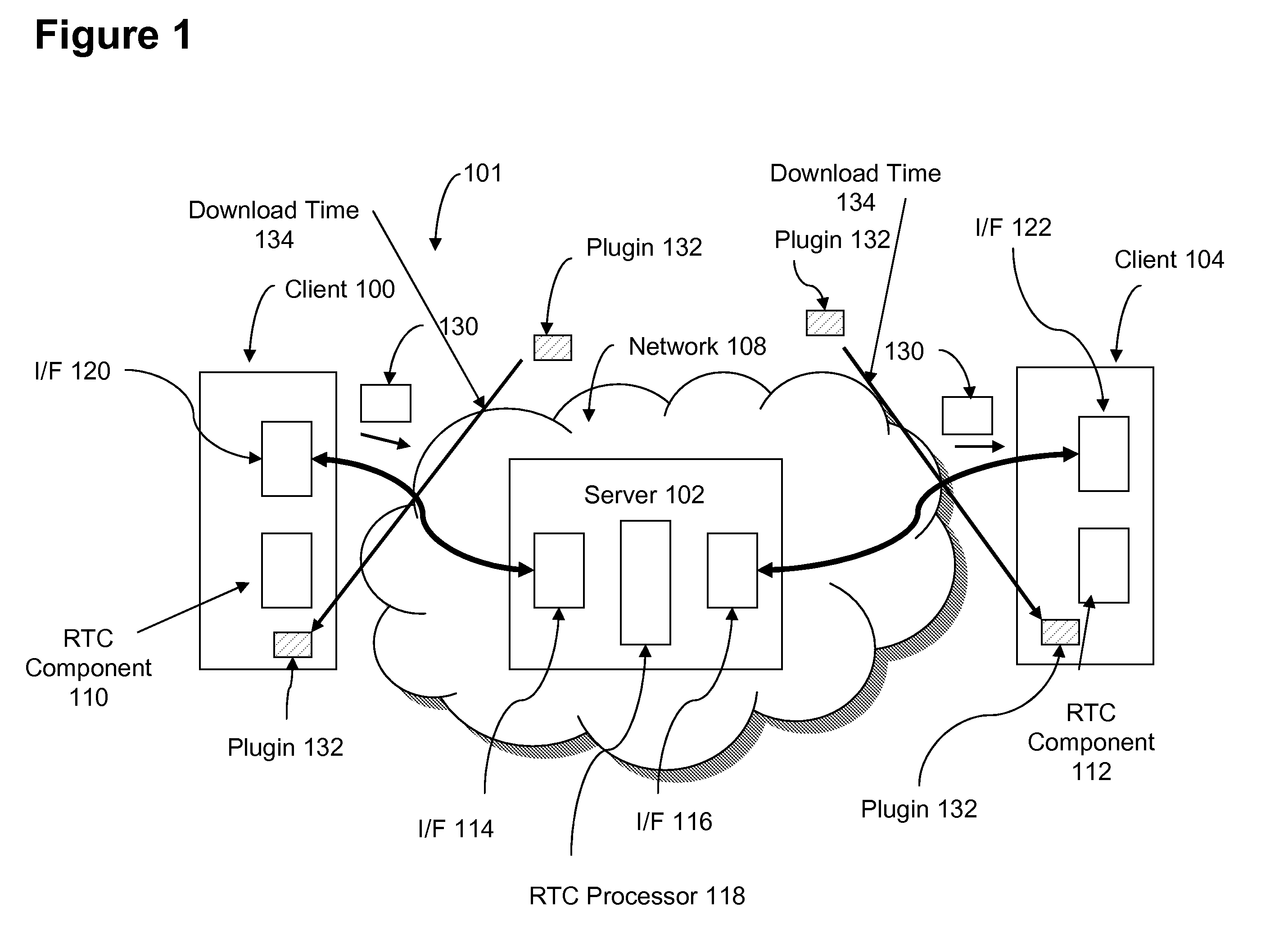
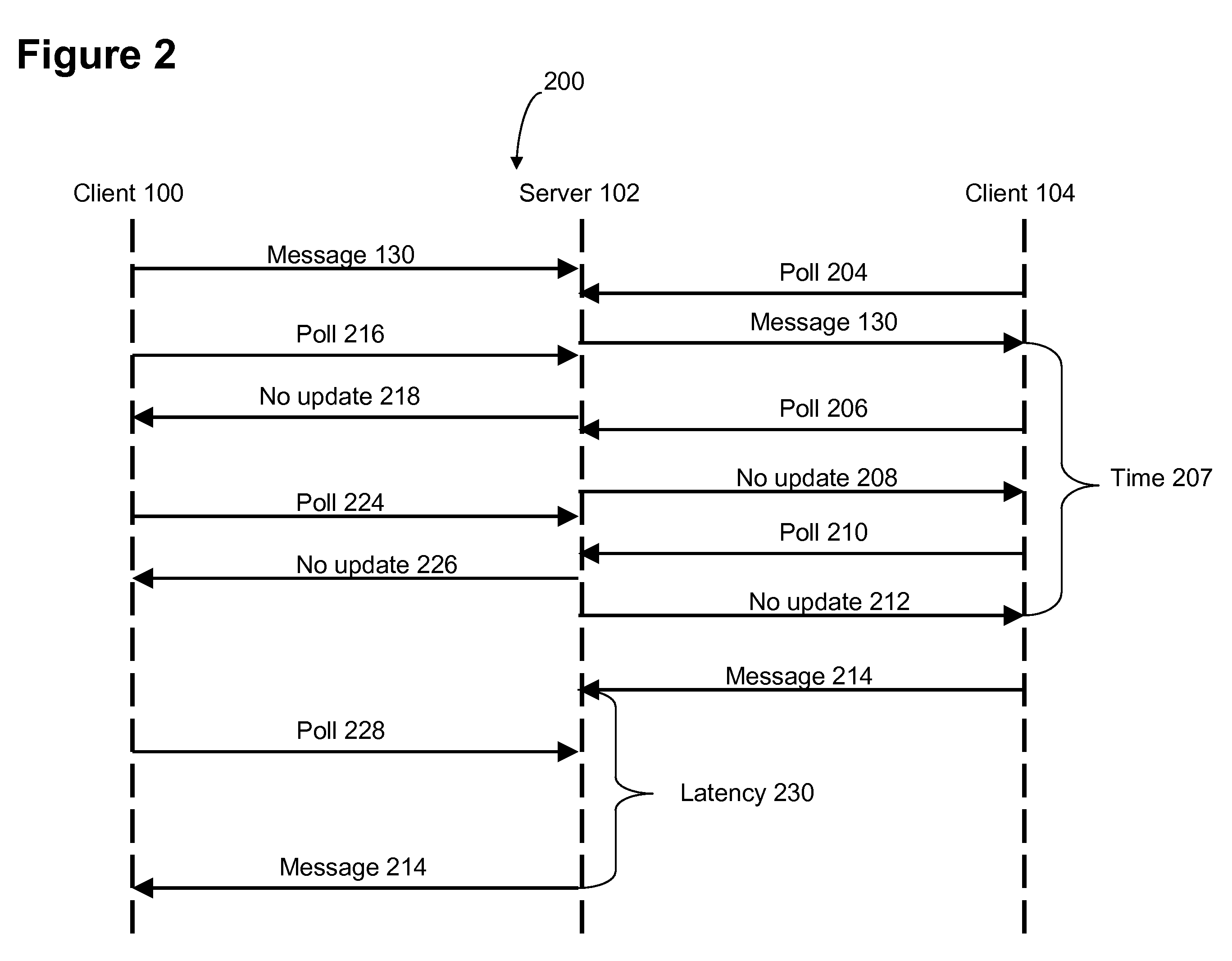
System and method for achieving highly scalable real-time collaboration applications using HTTP
InactiveUS20080147834A1Highly scalable and highly responsiveHighly scalable and highly responsive RTC serviceDigital computer detailsTransmissionApplication serverApplication software
A highly scalable and highly responsive RTC system uses asynchronous or non-blocking I / O and HTTP response queuing to avoid server overload. The system distinguishes between two types of requests: an update request and a change request. An update request is a request used to fetch an update or change notification. A change request is a request to change some data related to the real-time session. For a given RTC session, the server first checks whether any updates exist for an update request. If an update exists, the server code can send an immediate response to the client. However, if no update exists, the server code application sets a well-defined HTTP response header, and then responds. Once the server code application responds, all application server resources are freed, and the application server is free to handle the next requests without blocking any thread. The existence of the well-defined response header, allows the lower level networking code to queue the response, allowing it to be later addressed by the RTC session ID. This way, the HTTP response can be delayed (queued) without blocking a thread in the application server. A Change Request is a request used to change some data related to the real-time session. Such requests would typically be tied to an action within a given RTC session (e.g., adding text to a chat, changing a slide, etc.). When these actions are sent to the server, the server-side application can determine whether the request affects the queued responses that are awaiting change notifications. In the case of a change, the notification response is computed, and then an API call into the lower-level network flushes all queued responses awaiting updates in the session. Therefore this mechanism is used to trigger the responses to complete, thus providing immediate updates to clients.
Owner:IBM CORP
Transferring sessions between devices
InactiveUS20090138606A1Multiple digital computer combinationsTransmissionComputer SessionPersonal computer
Methods and apparatus for transferring a communication and computer session between devices. A user launches a communication session on a first device, such as a personal computer. The user may then selectively transfer the communication session to another device, such as a wireless device, through activation of a triggering signal. In response, the context of the communication session is determined as it is being performed on the first device, including a type of the communication session. The communication session is then transferred to the second device by launching a new communication session on the second device and transferring the context of the communication session corresponding to the first device to the new communication session on the second device. The communications session is continued via use of the first device as a proxy for the second device.
Owner:CONTEMPORARY DISPLAY LLC
Method and device for determining the physical location and identity of a user
InactiveUS20030236120A1Selection is limitedPayment architectureApparatus for meter-controlled dispensingSession IDRestricted activity
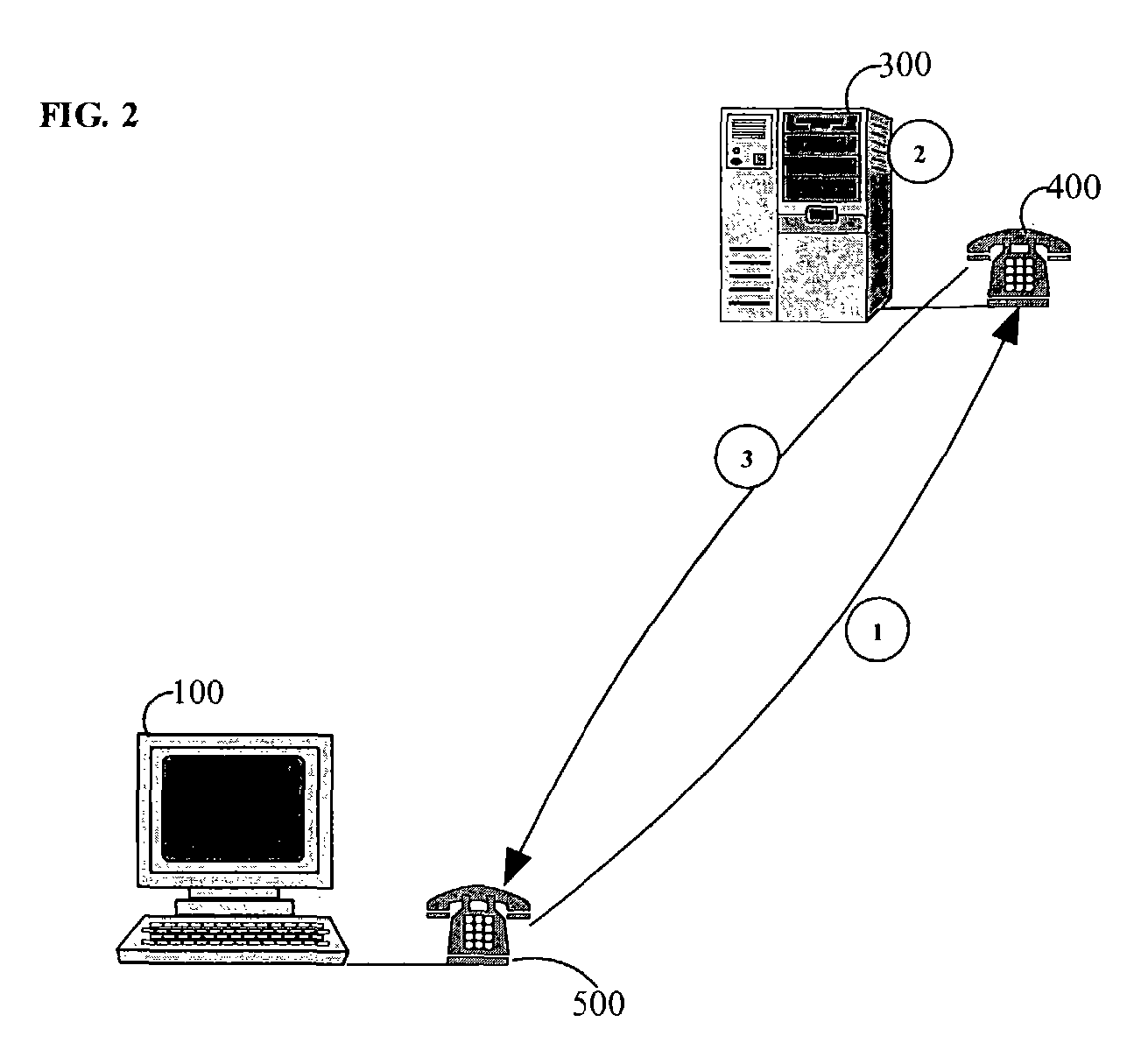
A method and a device is described for determining the physical location and / or identity of network users and for preventing certain undesired users for participating in-or getting access to restricted activities, services or information. When a user accesses a service provider's website, an encrypted session ID is stored on the user's electronic device or computer. The user's electronic device or computer is then coupled to the service provider's server through a phone connection and the session ID is transferred to the service provider over the phone line for verification. By using Caller ID technology the user's telephone number is identified, and by analyzing the phone number the location of the player is determined. If the location satisfied the service provider's and any official regulator's requirements the available service options are then determined depending on the user's specific location. The available service options-if any-are then displayed on the user's electronic device or computer.
Owner:REECE KENNETH +1
Group registration device, group registration release device, group registration method, license acquisition device, license acquisition method, time setting device, and time setting method
InactiveUS20090151006A1Simplify the registration processExecuted sufficientlyDigital data processing detailsUser identity/authority verificationDatabaseLicense
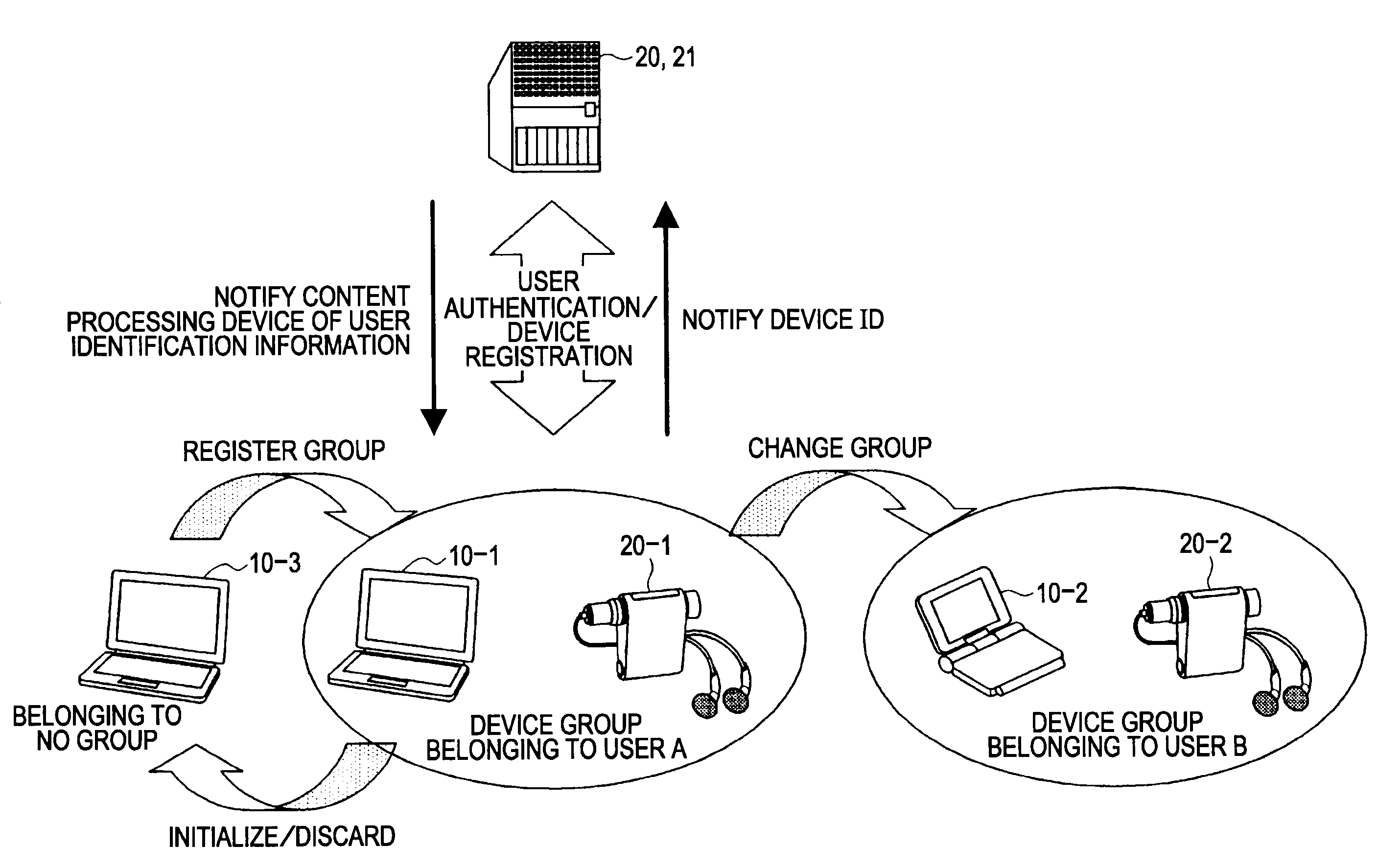
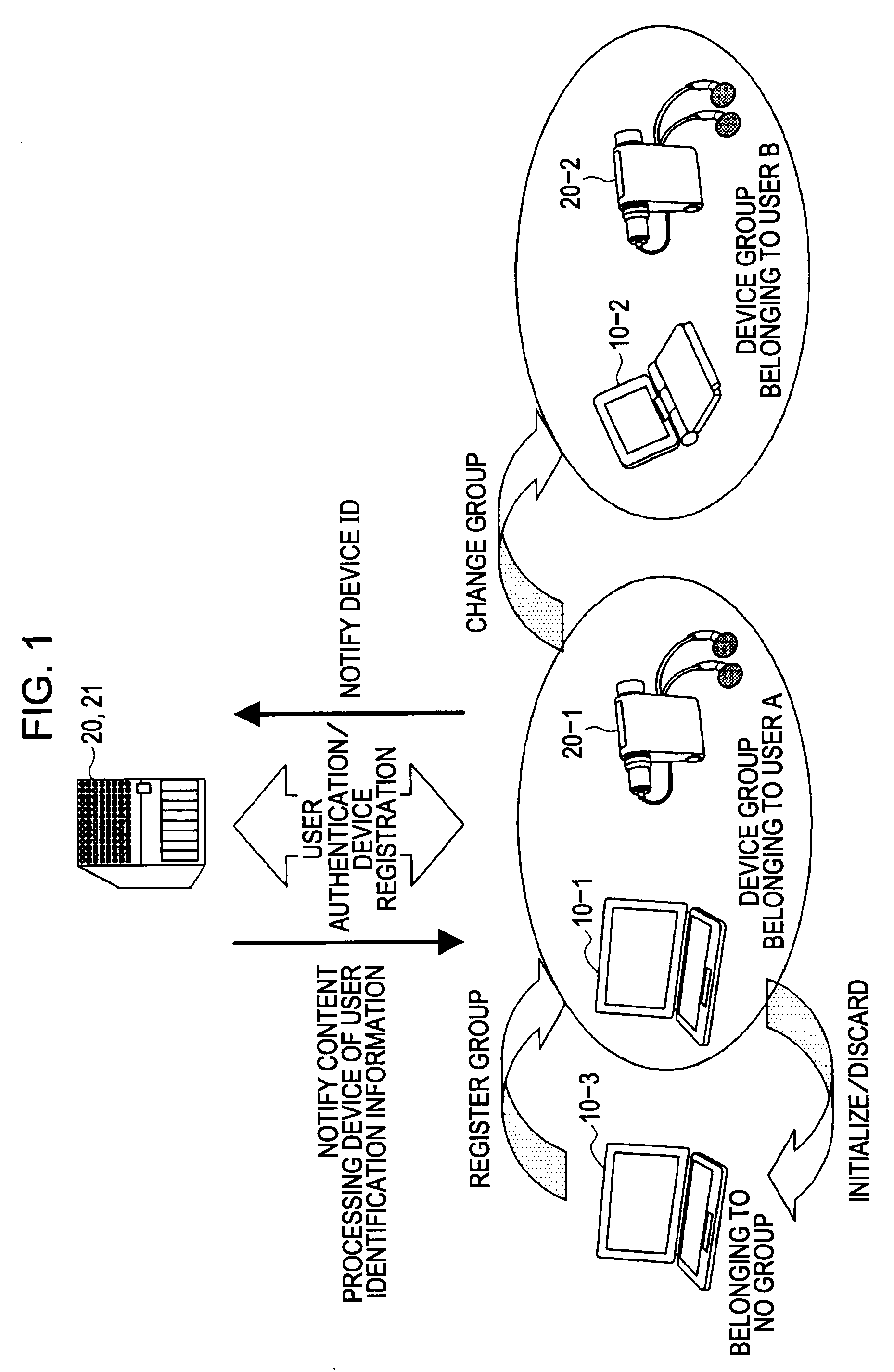
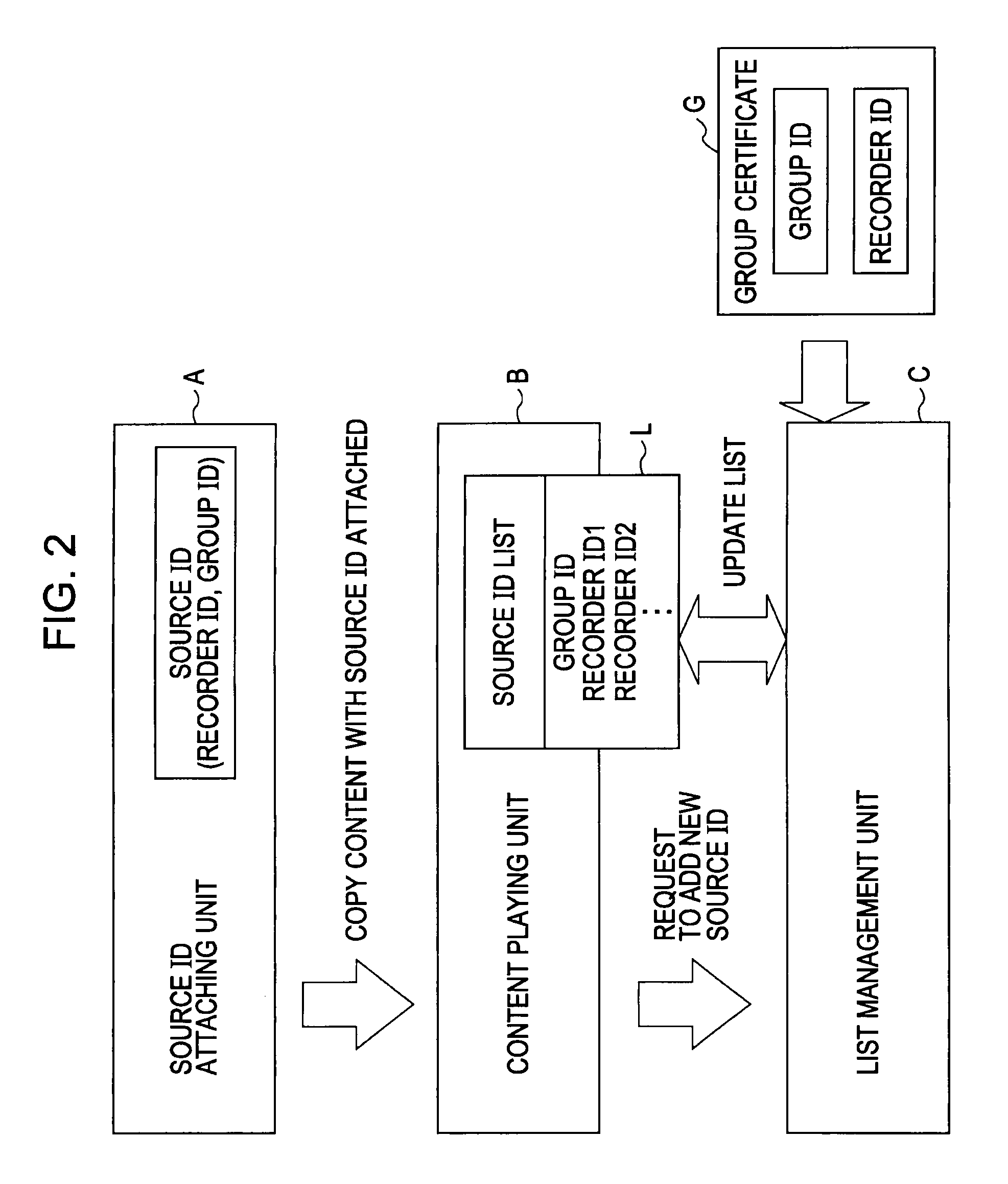
There is provided a group registration device or the like which is capable of simplifying registration processing to readily perform group registration while retaining secure registration processing.A group registration device 10 includes a registration request detecting unit, a session ID generating unit for generating a session ID, a registration request message sending unit, a registration reply message receiving unit, a verification unit 231 for verifying non-redundancy of a message, and a storage unit 241 for storing an ID list included in a registration reply message in a storage region so as to be associated with a group ID. Within the same registration session, the registration request message is sent once, the registration reply message is received once, and processing is restricted to sending of the registration request message and receiving of the registration reply message.
Owner:SONY CORP
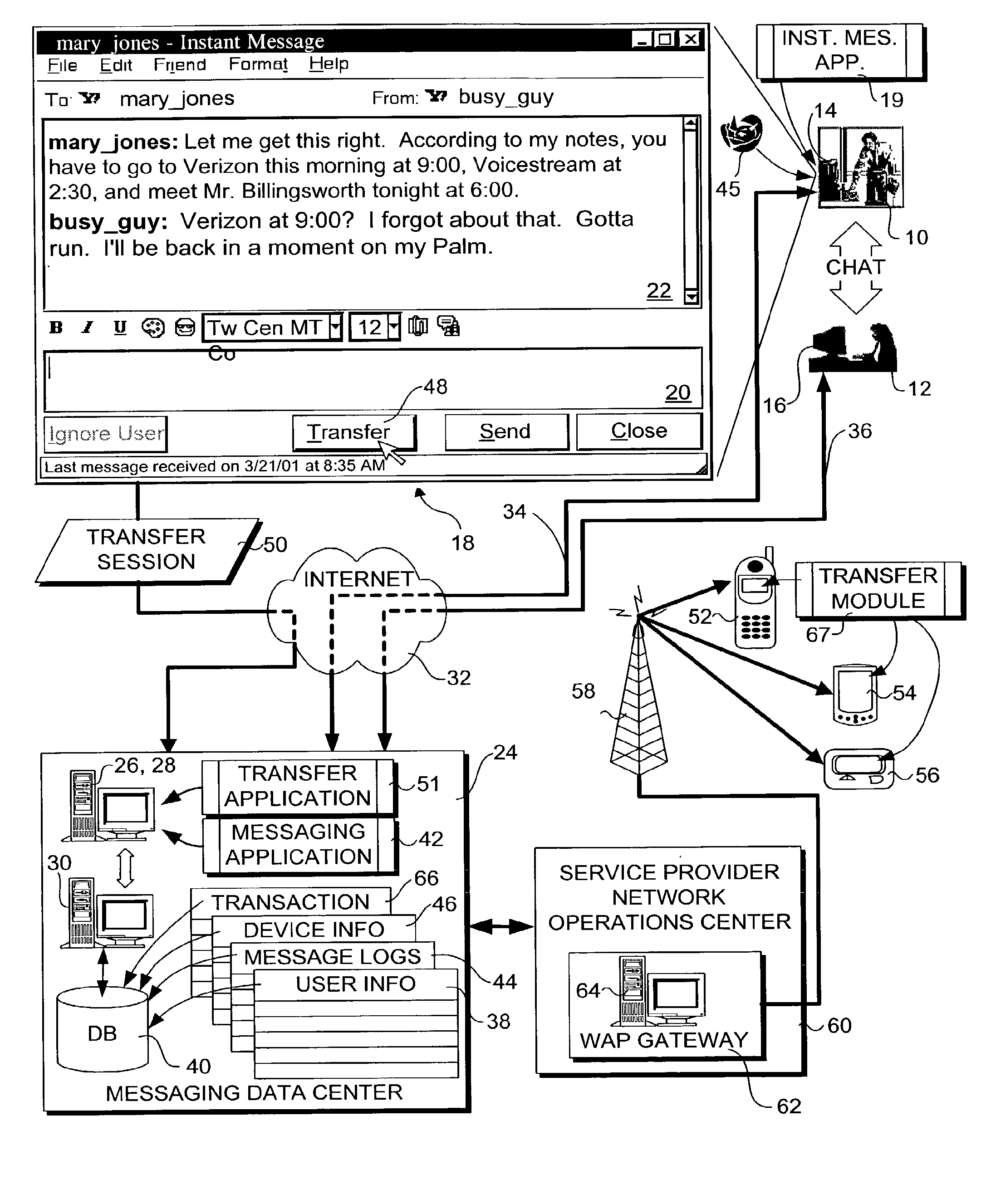
System for automated, mid-session, user-directed, device-to-device session transfer system
InactiveUS7191233B2Multiple digital computer combinationsSecuring communicationDiagnostic Radiology ModalityPager
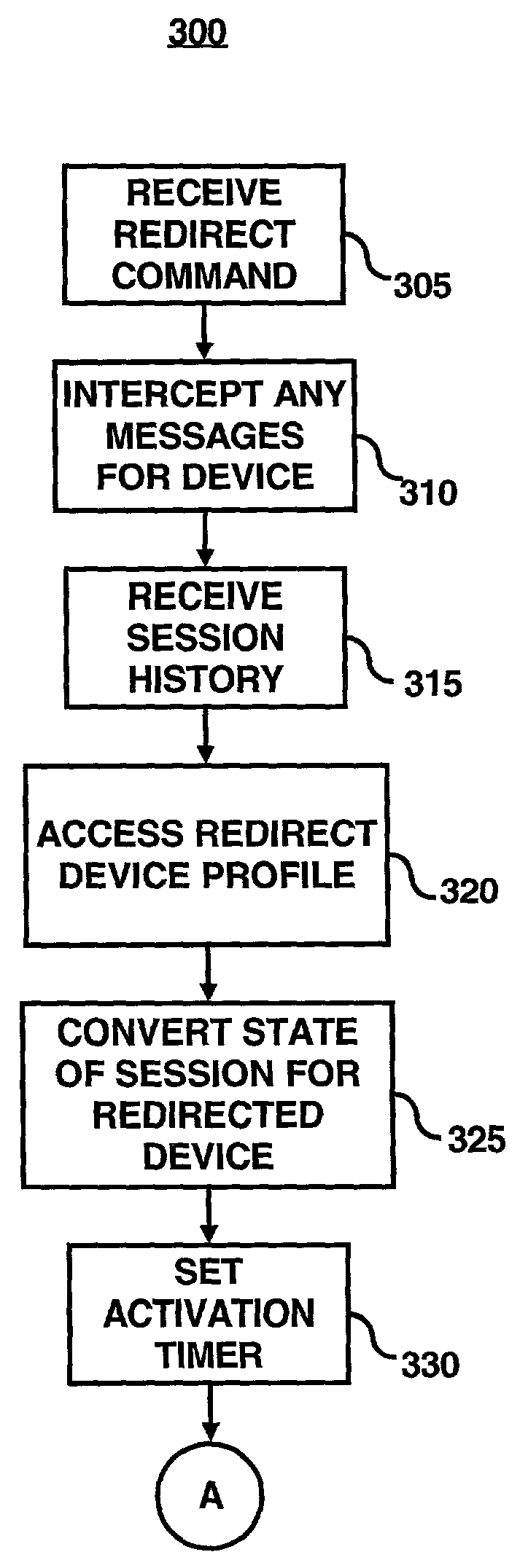
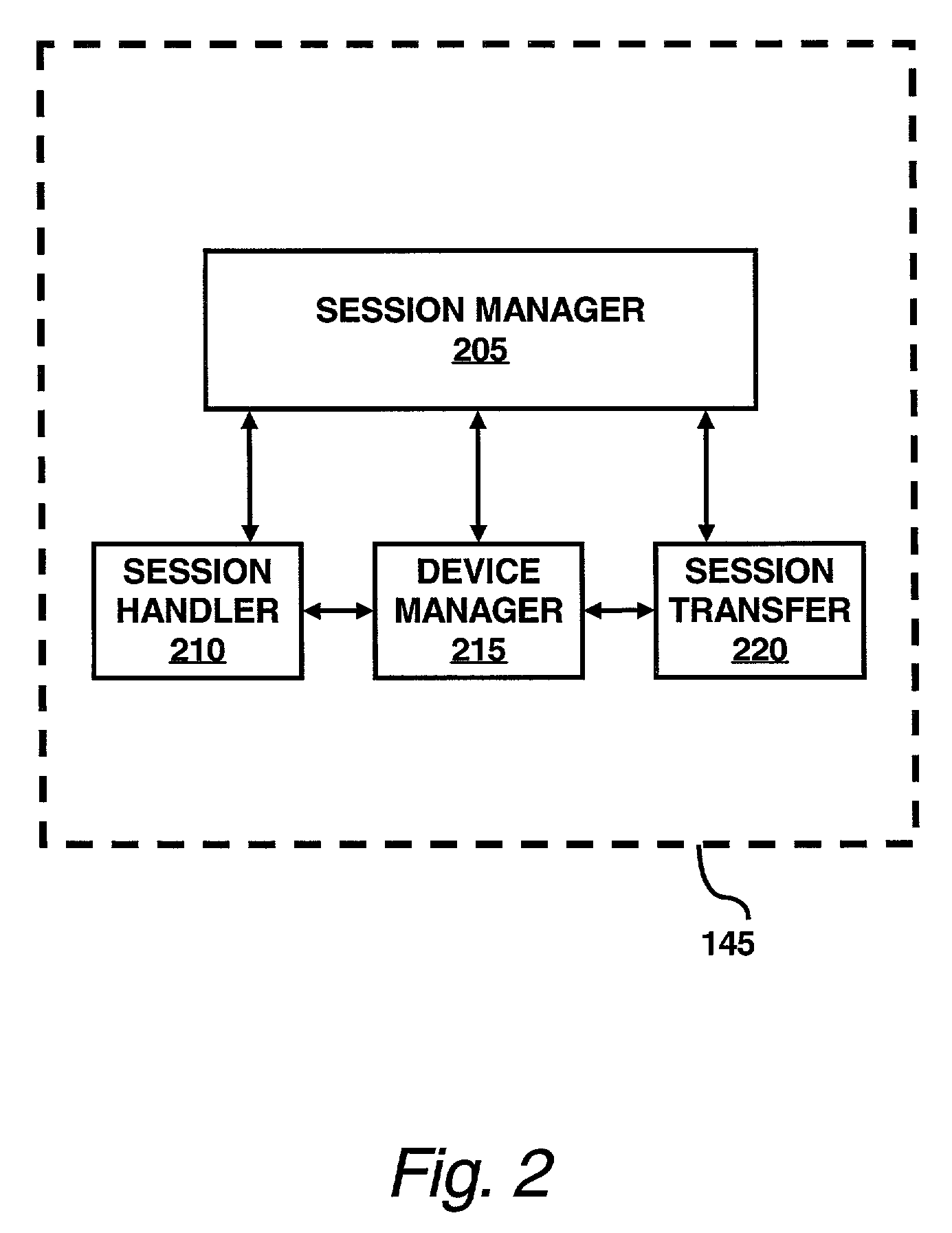
A session transfer module of a session server provides the capability to a user to direct a transfer of an on-going session from one device to another device while maintaining the session. The session transfer module is invoked by a user in a way consistent with the user interface of the client application, including by a graphical user command, a command line prompt, or a voice command. The client provides a selection of possible devices that may receive the redirected session. The session transfer module receives the selected device with the session redirect command over a communication network. The communication network may be wired (e.g., public switched telephone network (“PSTN”), Internet, etc.,) a wireless network (e.g., digital telephone network, pager network, etc.,) or a combination of the wired and wireless networks. The session transfer module may be configured to discontinue the session with the current device and to block any subsequent messages of the transferring session from reaching the device. The session transfer module may be further configured to access a device profile from a device profile database to convert the blocked messages into a format compatible to the format and / or modality of the redirected device. The session transfer module may be further configured to push the session to the redirected device in response to an activation (e.g., log-on) of the redirected device by the user. Alternatively, the session transfer module may be further configured to push the session back to the device in response to a time-out in the activation of the redirected device.
Owner:CRFD RES
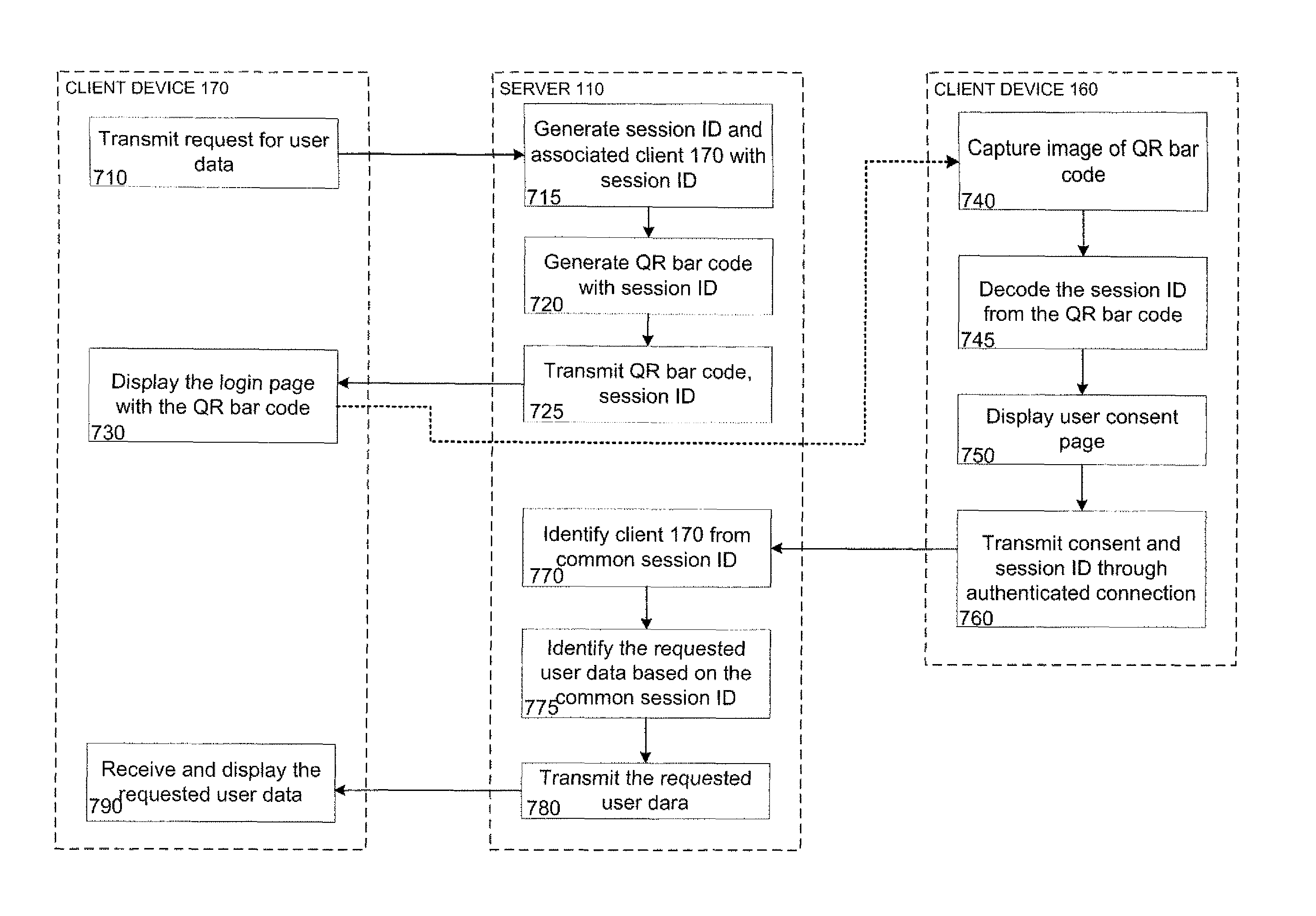
Out-of band authentication of browser sessions
Systems and methods provide a user with secure access to a web site at a first client device without having to enter login information, such as a username and password, at that device. For example, the first device may request access to user information from a server system. The server may generate a session ID, associate it with the first device, and encode it into a bar code that is displayed at the first device. Using camera functions, a second client device may identify and decode the bar code to determine the session ID. The login information may be entered into the second device in order to establish a secure connection with the server. The second device may transmit the session ID to the server system. The server may identify the first client device based on the common session ID and transmit the requested user information to the first device.
Owner:GOOGLE LLC
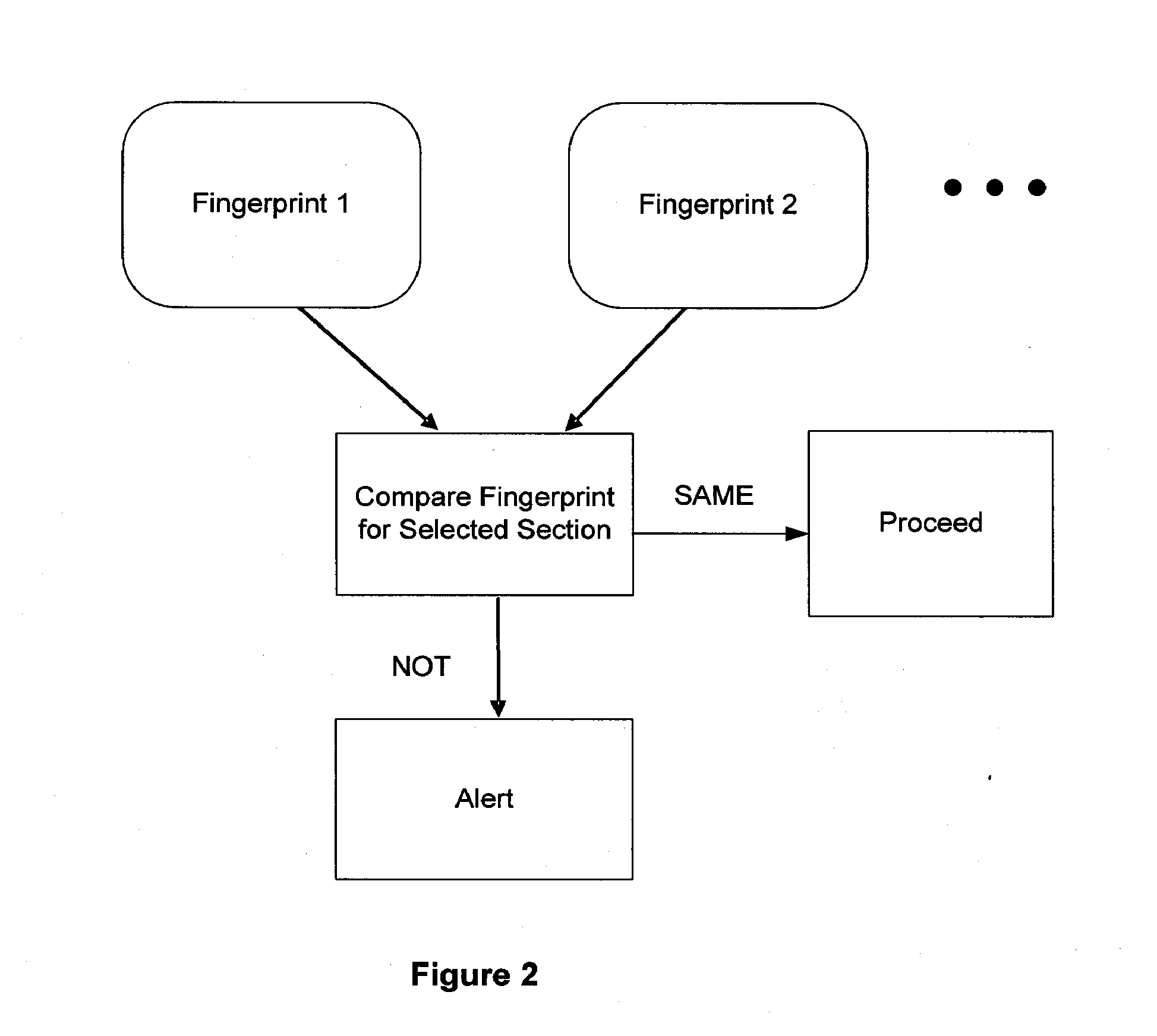
Systems and methods for detection of session tampering and fraud prevention
ActiveUS8151327B2Memory loss protectionDigital data processing detailsMan-in-the-middle attackOperating system
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
Controlling access to a network using redirection
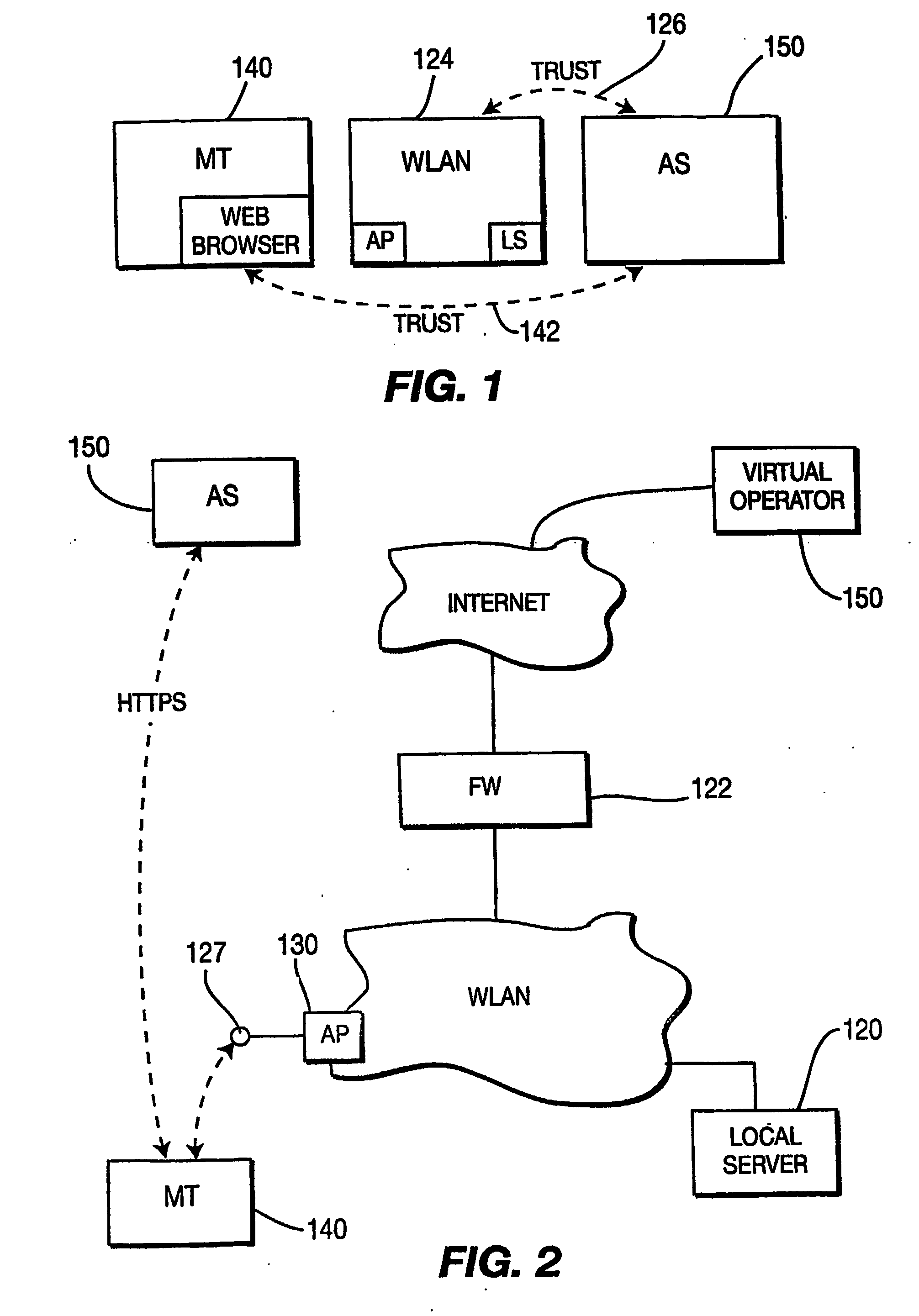
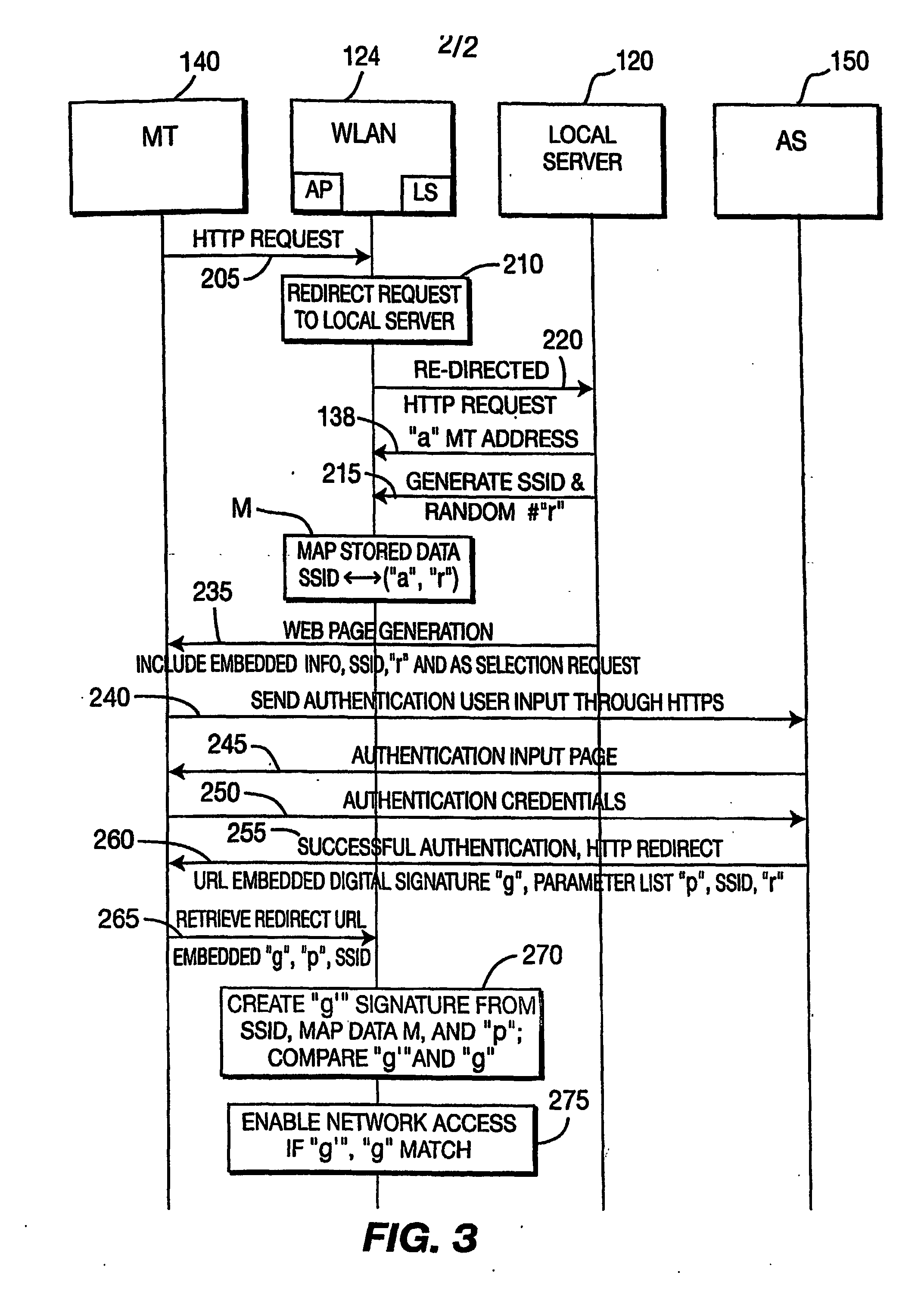
InactiveUS20070113269A1Error prevention/detection by using return channelAssess restrictionWeb browserDigital signature
A mechanism to improve the security and access control over a network, such as a wireless local area network (“WLAN”), that takes advantage of web browser interactions without requiring explicit separate communication session between a hot spot network and a service provider network. The method comprises receiving a request to access the WLAN from a mobile terminal (MT) / client disposed within a coverage area of the WLAN. The access point (AP) of the network associates a session ID and randomized number with an identifier associated with the MT and stores data mapping the session ID to the identifier of the MT and randomized number. The local server transmits an authentication request in the form of a web page, which includes the session ID and randomized number, to the MT. The AP receives from the MT a digitally signed authentication message, a parameter list containing user credential information, session ID, and randomized number concerning the MT, the authentication message being digitally signed using the session ID and randomized number together with the parameter list. The AP correlates the session ID and parameter list received from the MT and, using the stored mapping data, generates a local digital signature for comparison with the received digitally signed authentication message for controlling access of the MT to the WLAN.
Owner:THOMSON LICENSING SA
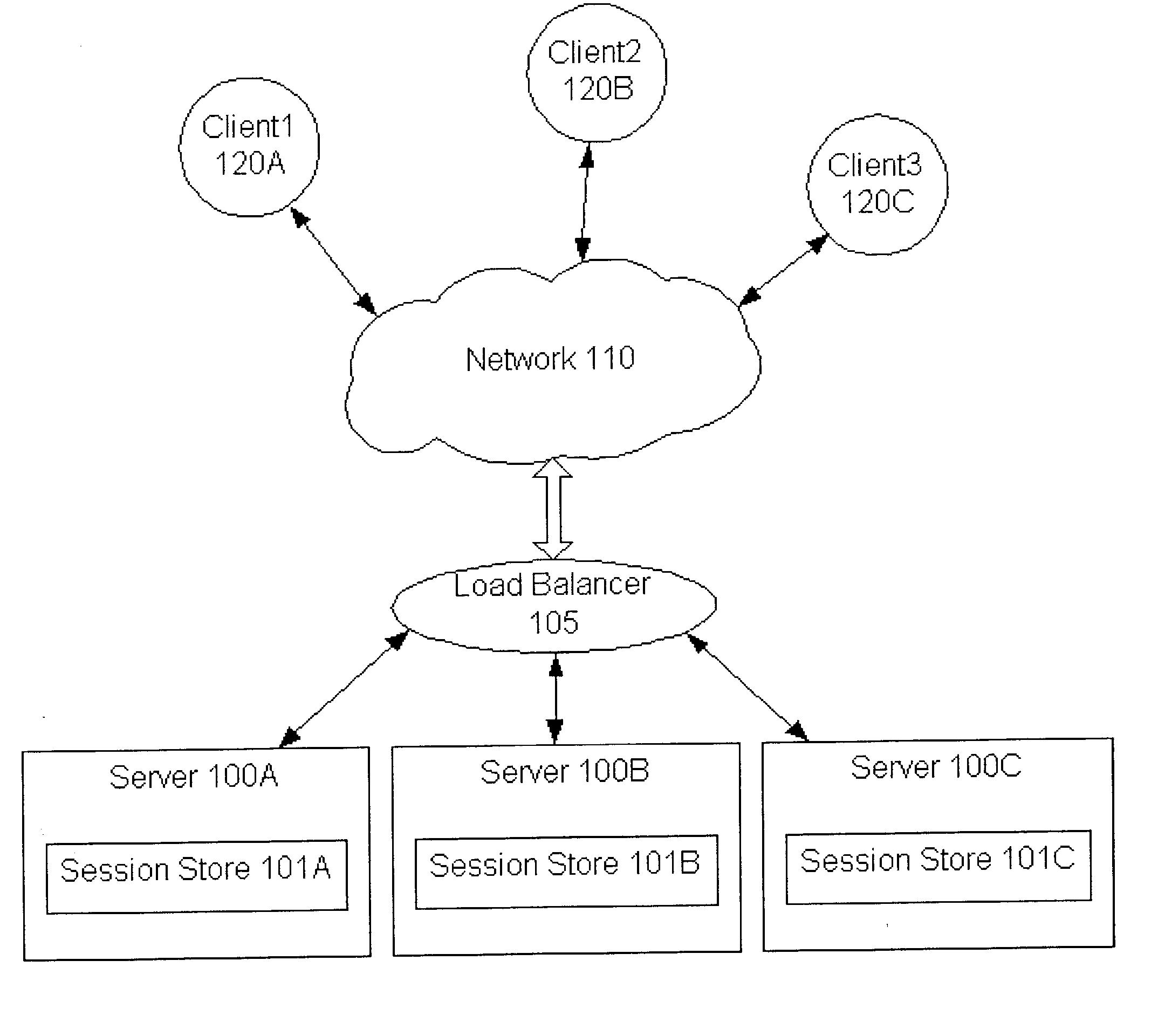
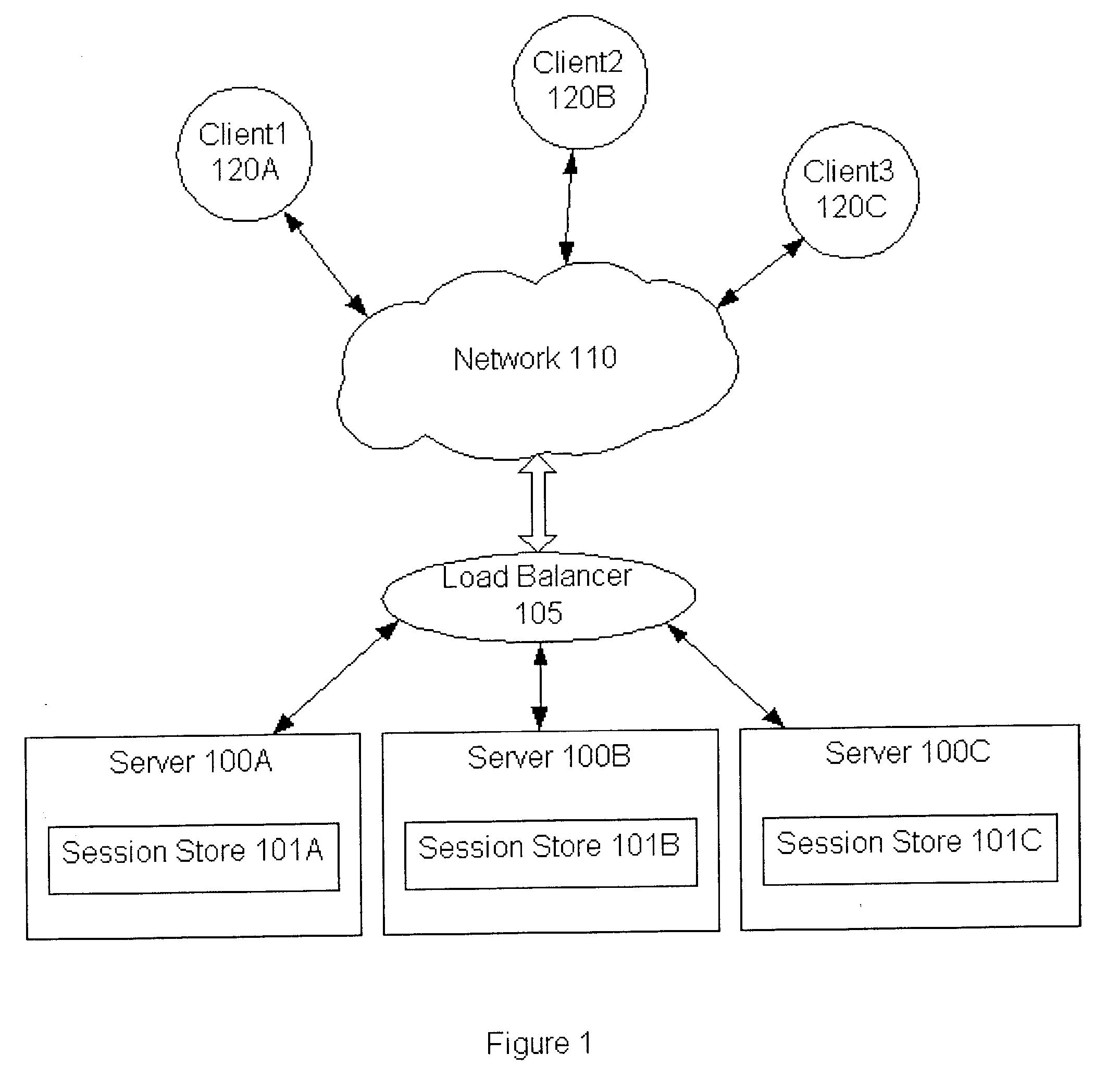
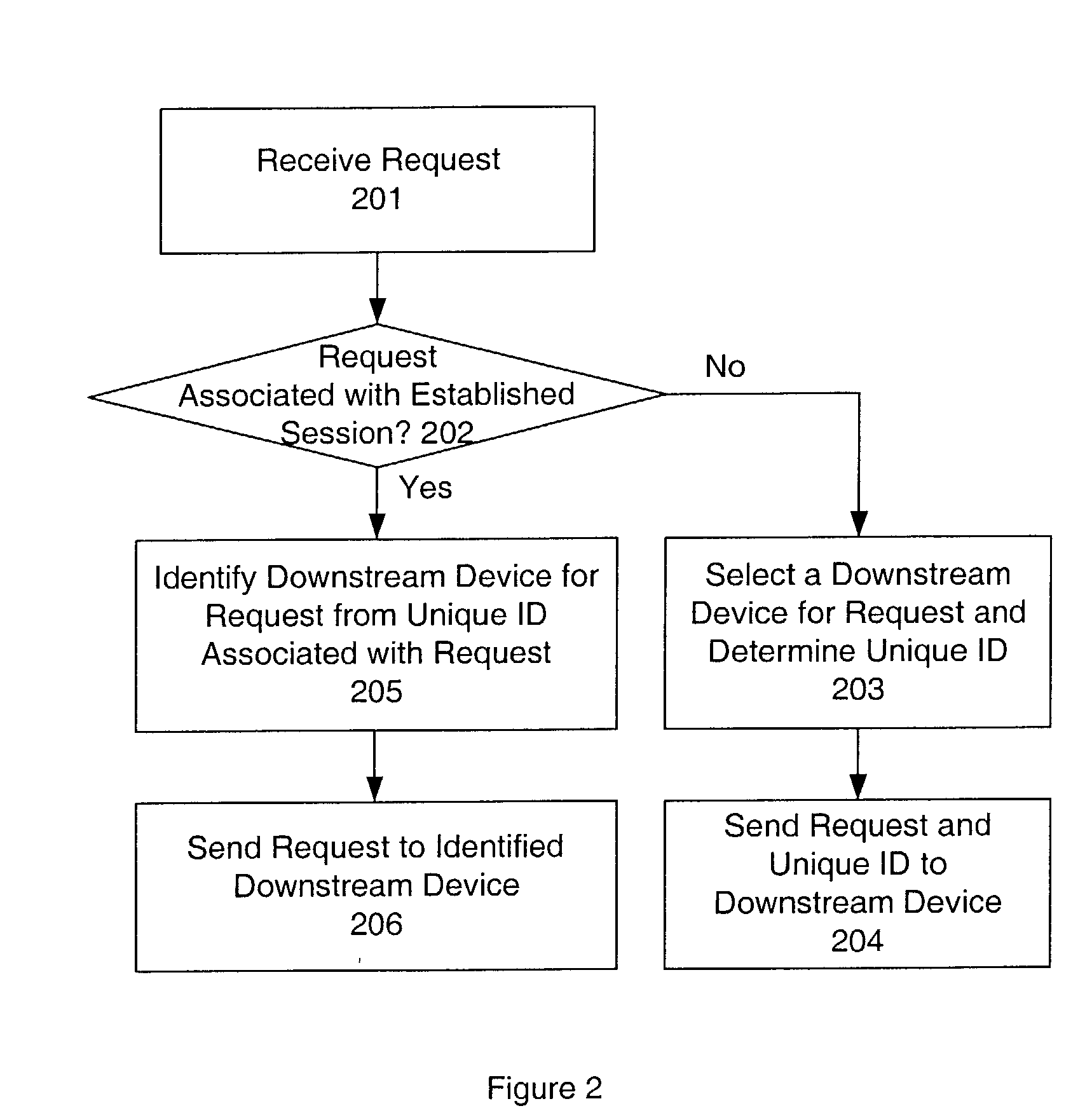
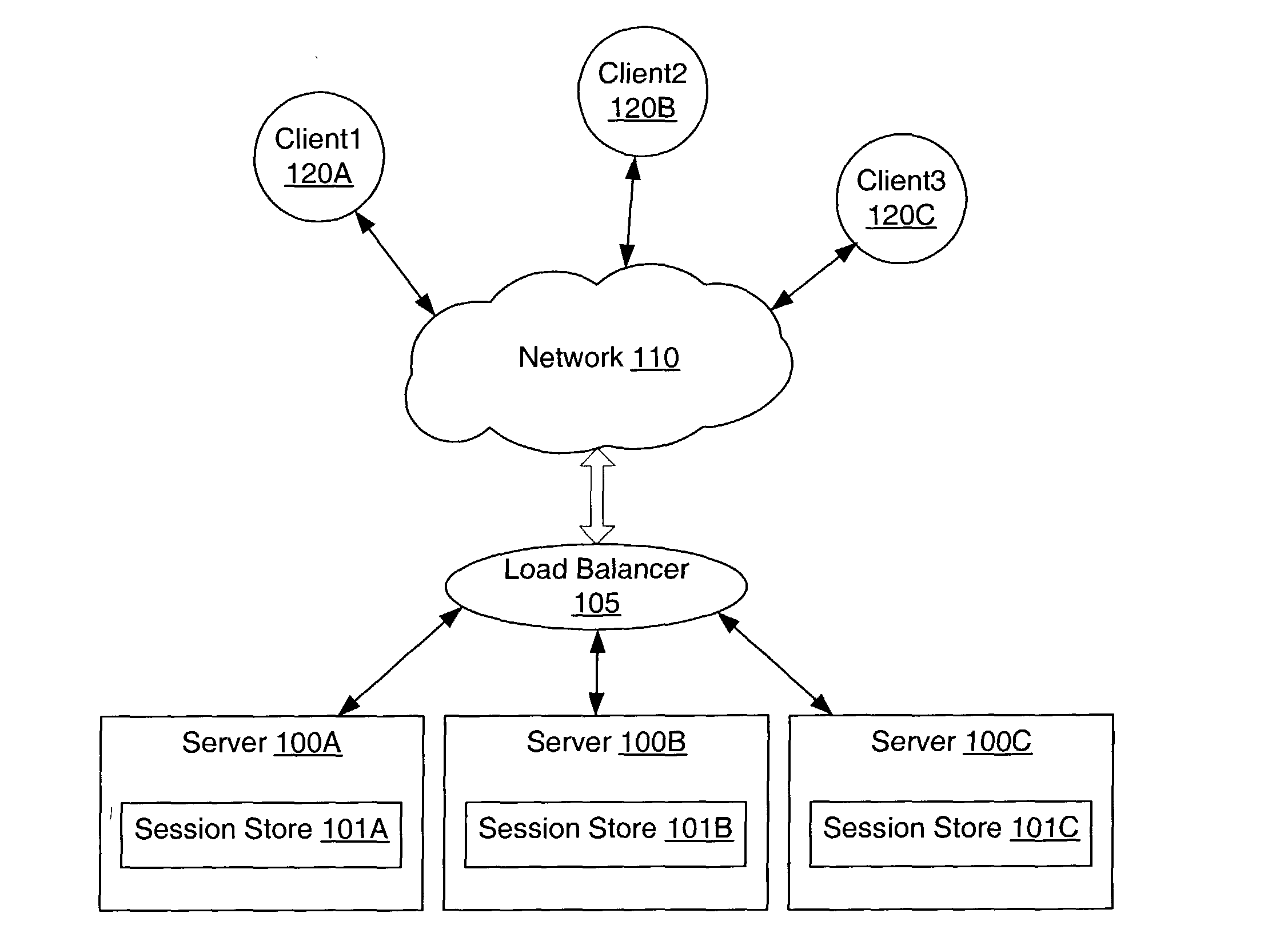
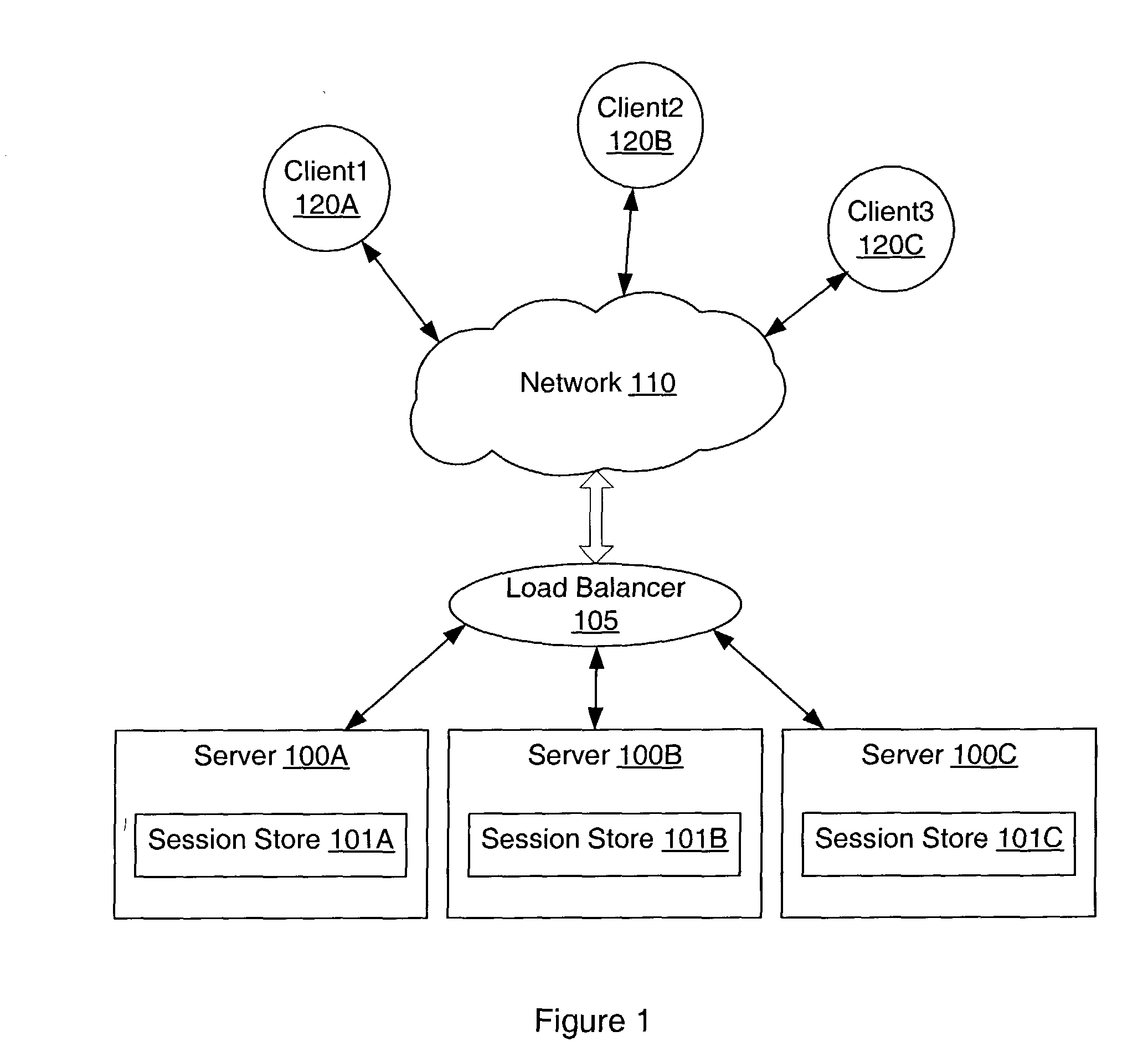
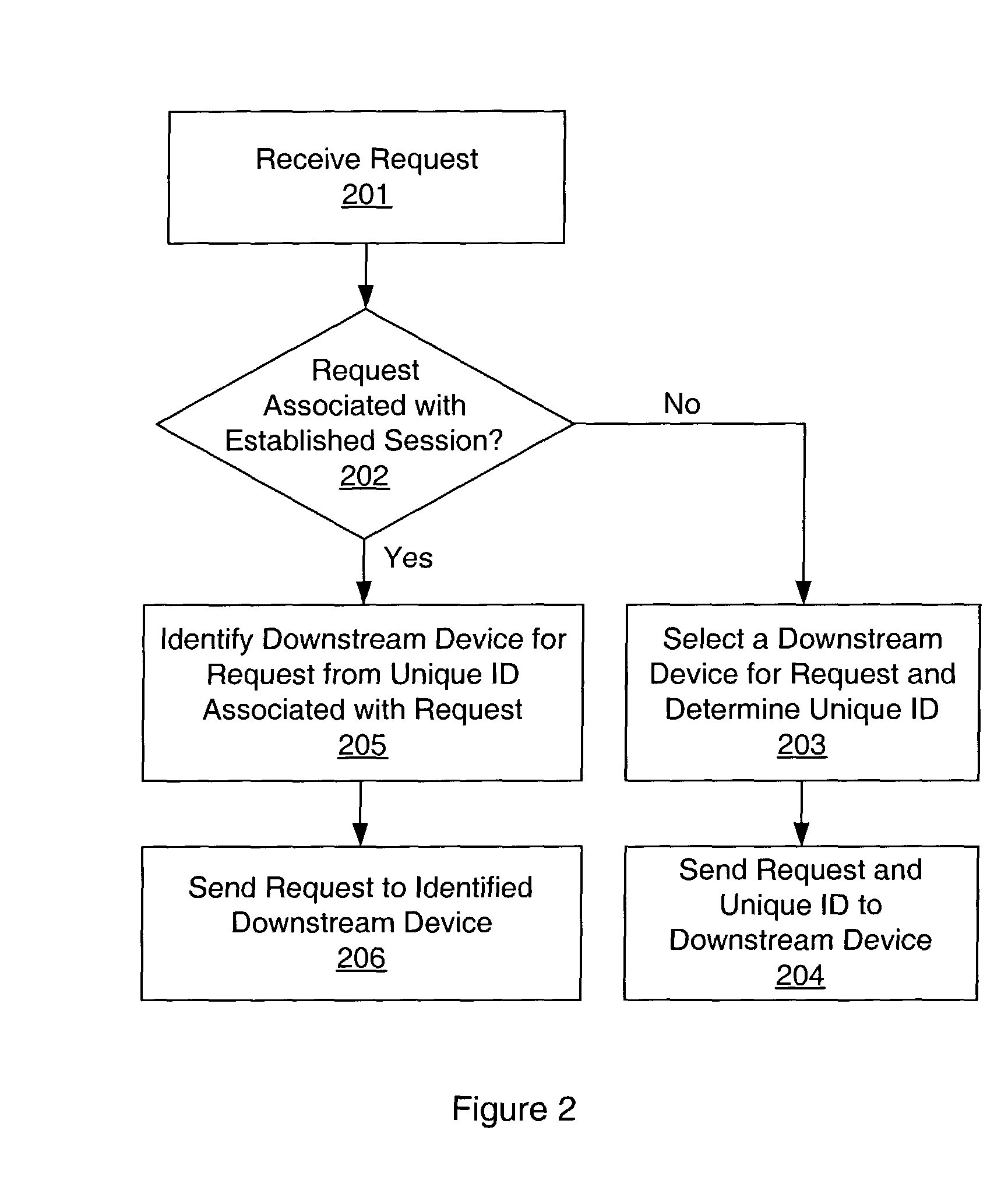
System and method for sticky routing of requests within a server farm
An upstream device, such as a load balancer or router within a server farm, may perform sticky routing of session requests to the servers handling those sessions by generating unique ID(s) identifying how requests may be routed through the server farm. Upstream devices through which travels a request that is not associated with a session on a server of the server farm may generate one or more unique IDs identifying how the request is routed through the server farm. The server handling the request may form a session ID and return that session ID and the unique ID(s) to the client that originated the new request and session. Clients may then send the session ID and unique IDs with clients requests for that session. Upon receiving requests corresponding to established sessions, the upstream devices may then identify routing information from the unique ID(s) and route the request accordingly.
Owner:ORACLE INT CORP
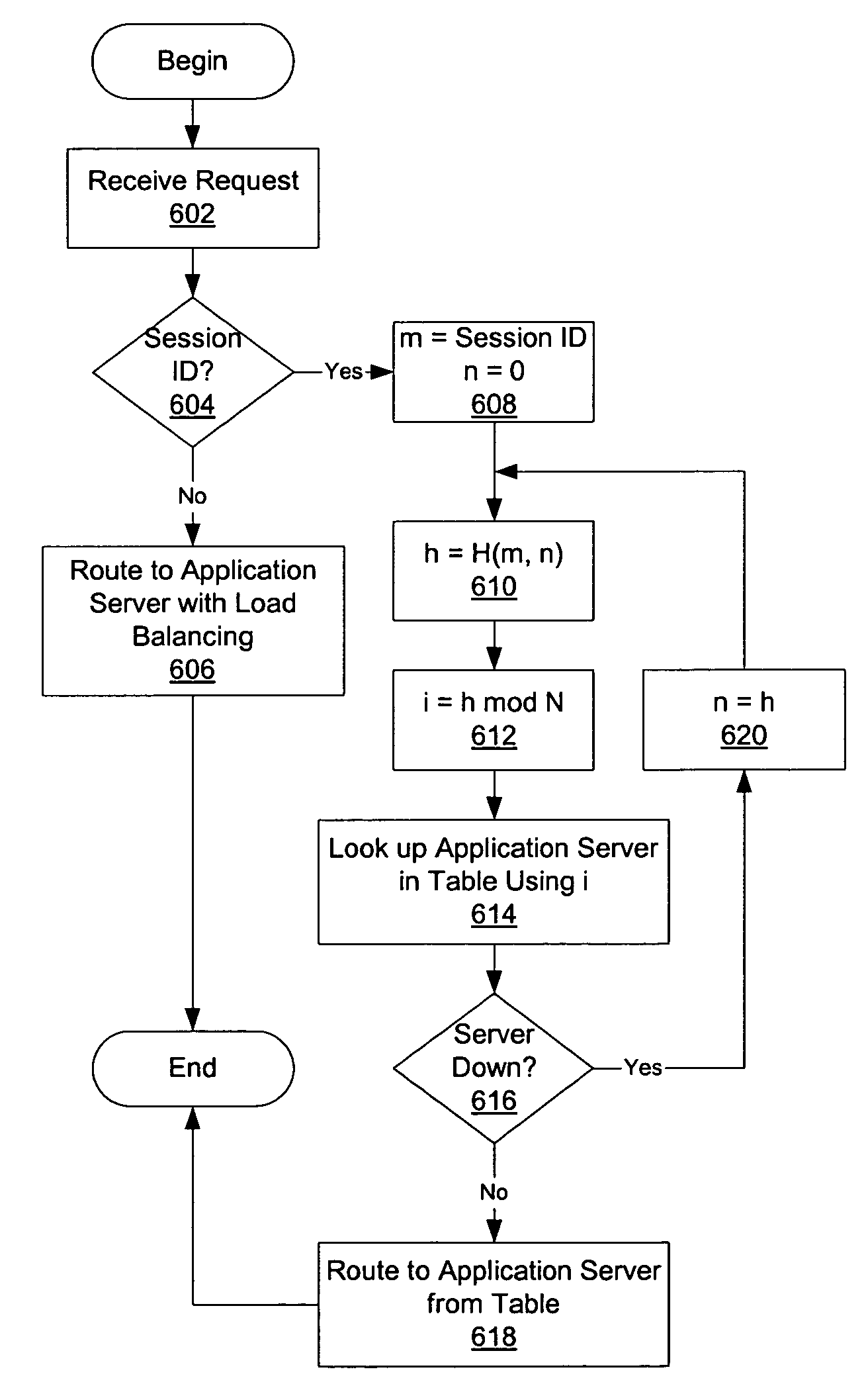
Method and apparatus for affinity of users to application servers
A method and apparatus route hypertext protocol requests to one of a plurality of application servers, which share a database through a backend database management system. The application servers store session data in the database. Hence, if a subsequent request is routed to a different application server, the session data is available through the backend database management system. One or more web servers perform routing of requests to the application server. When a request is received that is accompanied by a session ID, routing is performed by utilizing a hash function on the session ID. The resulting hash value is mapped to an application server. A hash function on a session ID will always result in the same hash value; therefore, the request will always be routed to the same application server. However, if an application server is non-functional, a new hash based on the previous hash is computed until a functional application server is selected.
Owner:DAEDALUS BLUE LLC
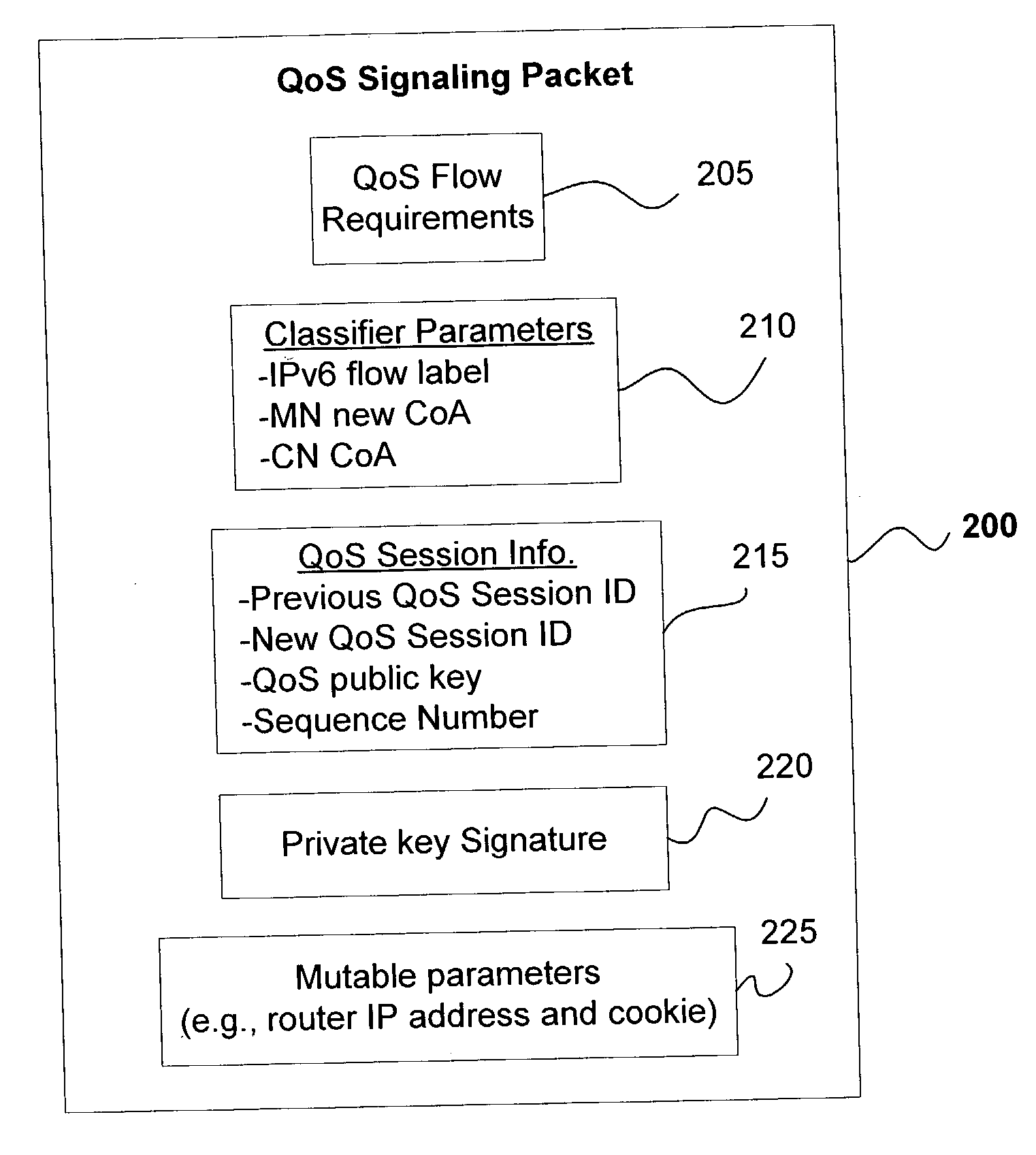
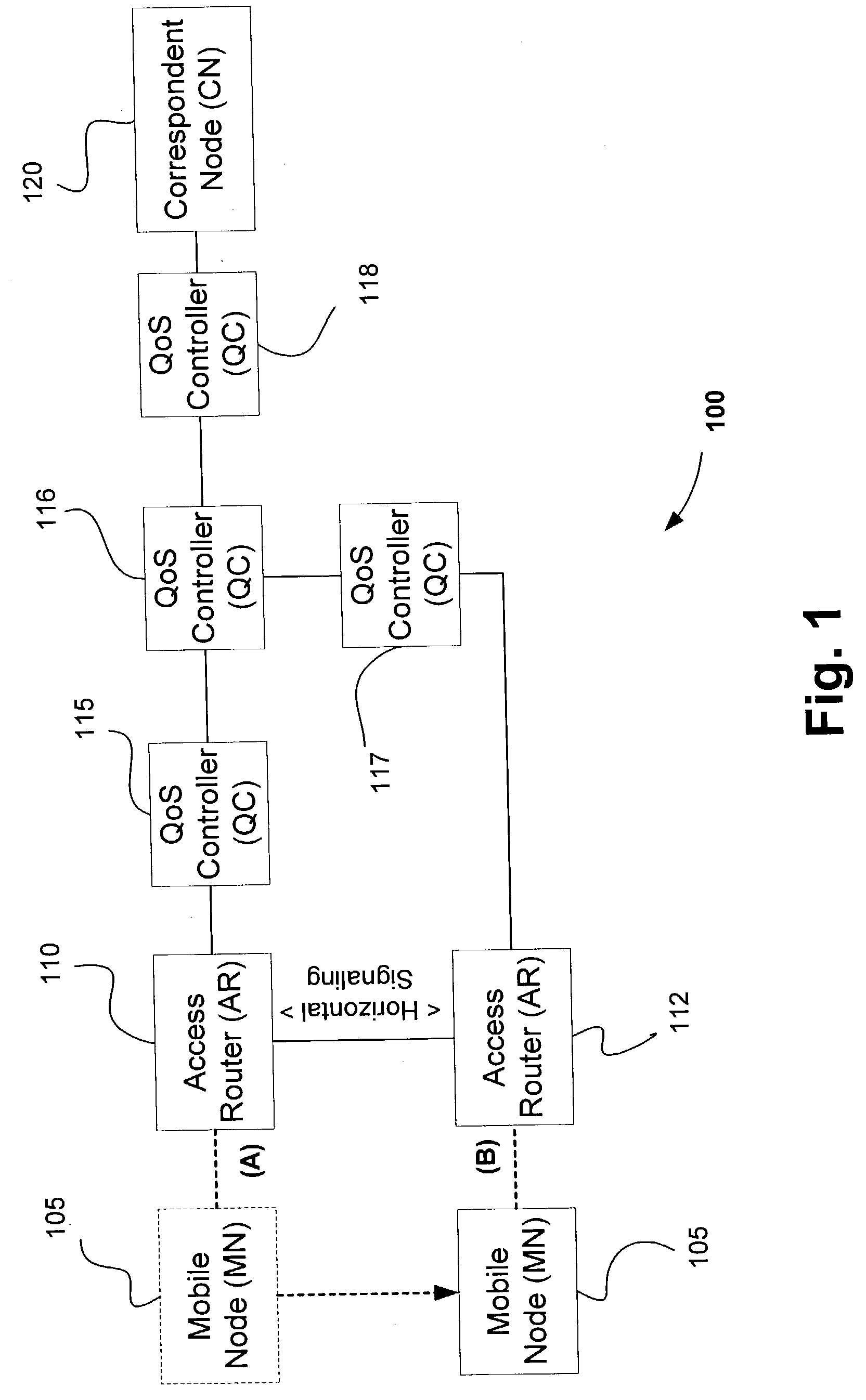
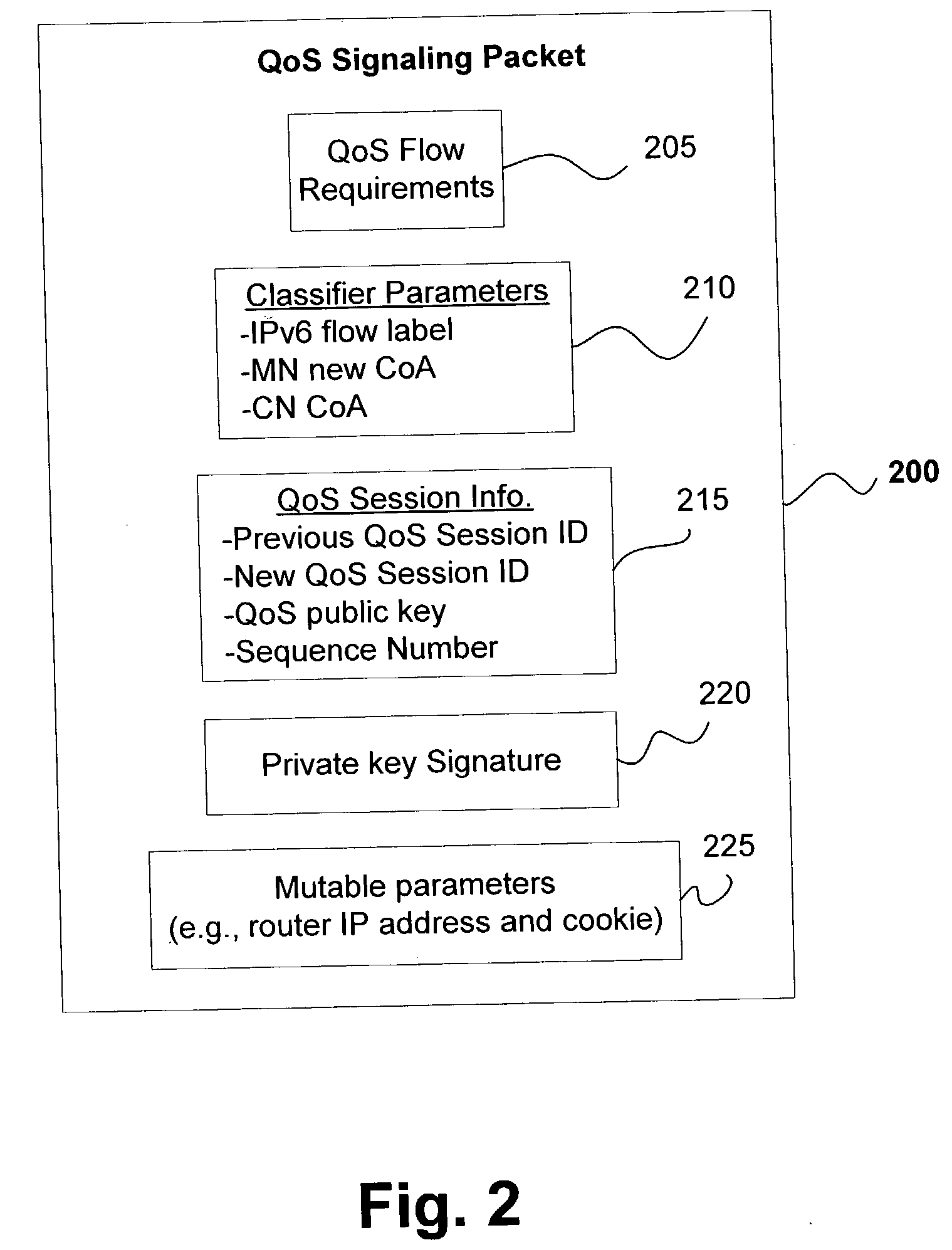
QoS signaling for mobile IP
ActiveUS20040008689A1Overcomes drawbackNetwork traffic/resource managementConnection managementQuality of serviceDatapath
A quality of service (QoS) signaling packet for arranging QoS connections upon handoff between a mobile node (MN) and a correspondent node (CN) using Internet Protocol (IP), the signaling packet includes one or more QoS flow requirements, one or more classifier parameters, QoS session identification information composed of a previous QoS session ID, a new QoS session ID, and a sequence number. The QoS session IDs are used for establishing a new data path and for added security against spoofing, can be composed of a key-based signature combination of a mobile node's new care of address (CoA) and the sequence number. The packet may also include a previous node address and a cookie, both of which are inserted by a previous node. The previous router address is used for backtracking communications and establishing / updating flow tables while the cookie is used for authentification of node-to-node messages.
Owner:INTELLECTUAL VENTURES I LLC
Authentication method, authentication system, and authentication server
InactiveUS20070044146A1Low costReduce buildRandom number generatorsUser identity/authority verificationService provisionValidation methods
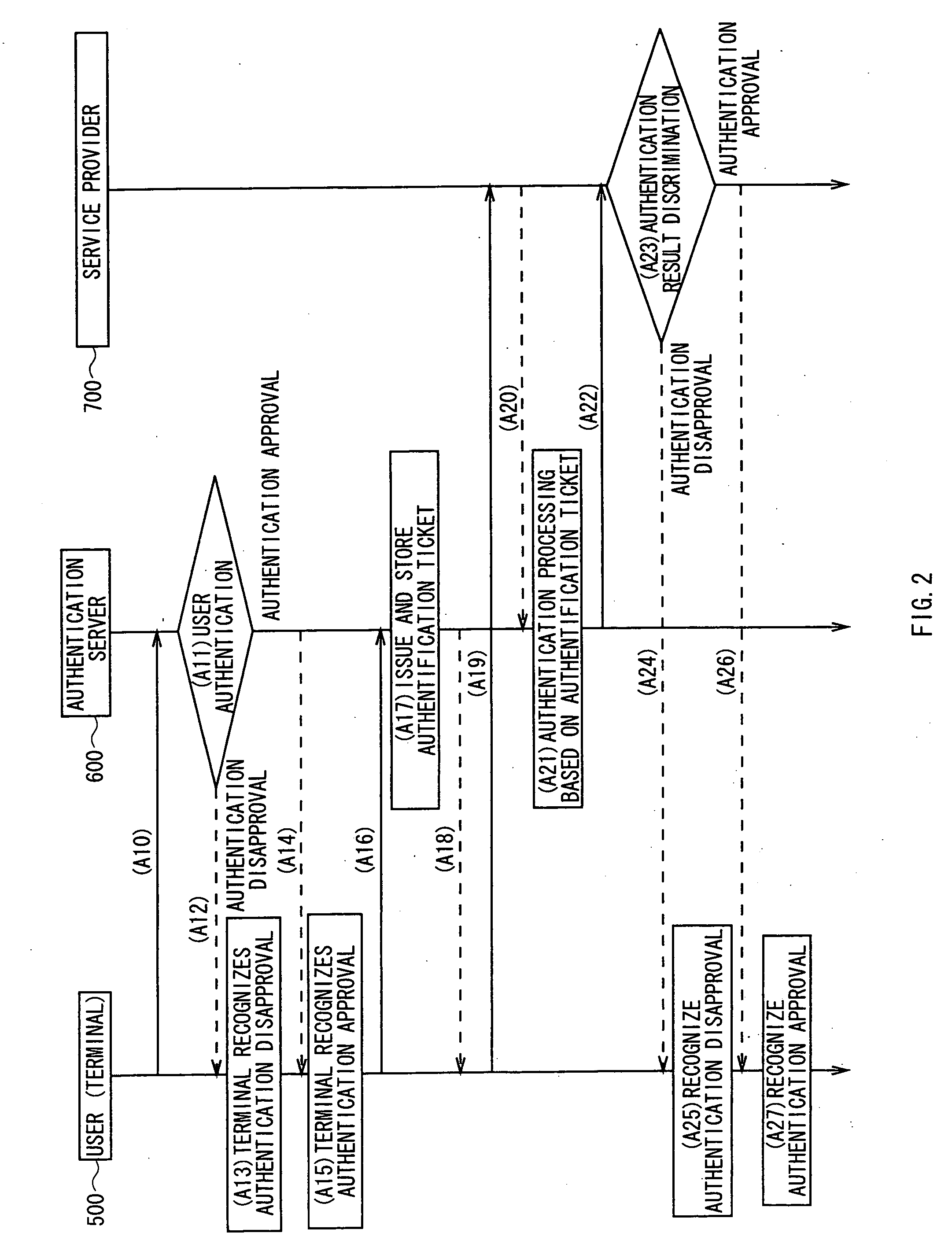
A user authentication processing is performed and an authentication session ID is returned to a terminal 500 (A14). An authentication server 600 issues and stores an authentication ticket (A17). The authentication ticket and authentication session are returned to the terminal 500 (A18). A user 100 transmits a request of service provision and the authentication ticket to a service provider's server 700, and the service provider's server 700 transmits the authentication ticket to the authentication server 600 (A20). The authentication server 600 performs an authentication processing of the authentication ticket (A21), and the authentication result is notified (A22). In the case of the authentication approval, a service session ID is issued together with the notification of authorization (A23). When receiving the notification of the authentication approval, the terminal 500 performs an establishment processing of the session using the received service session ID, and stores the service session ID (A27).
Owner:SONY CORP
Topical dynamic chat
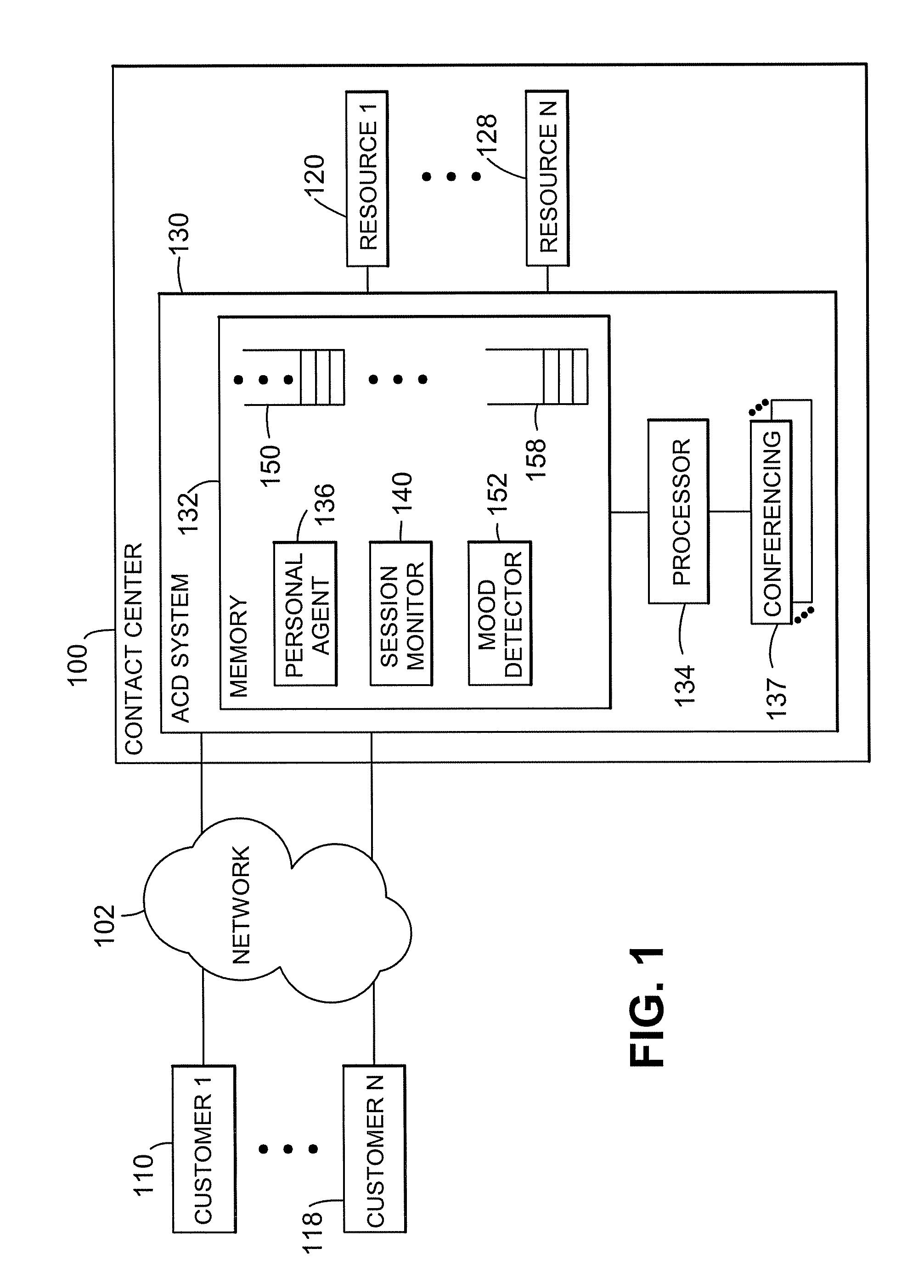
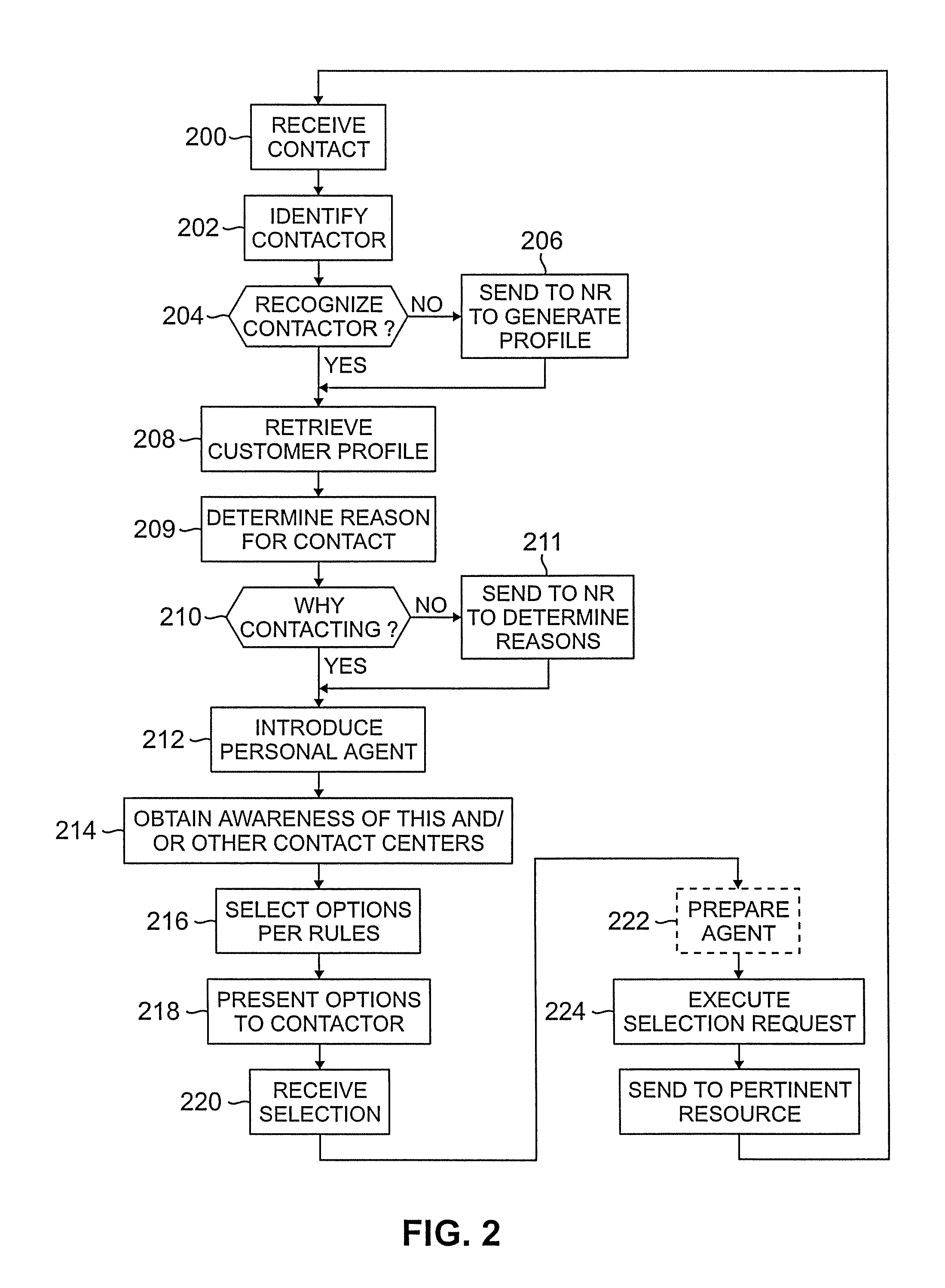
ActiveUS7336779B2Easy to useReduce in quantitySpecial service for subscribersManual exchangesContact centerSession ID
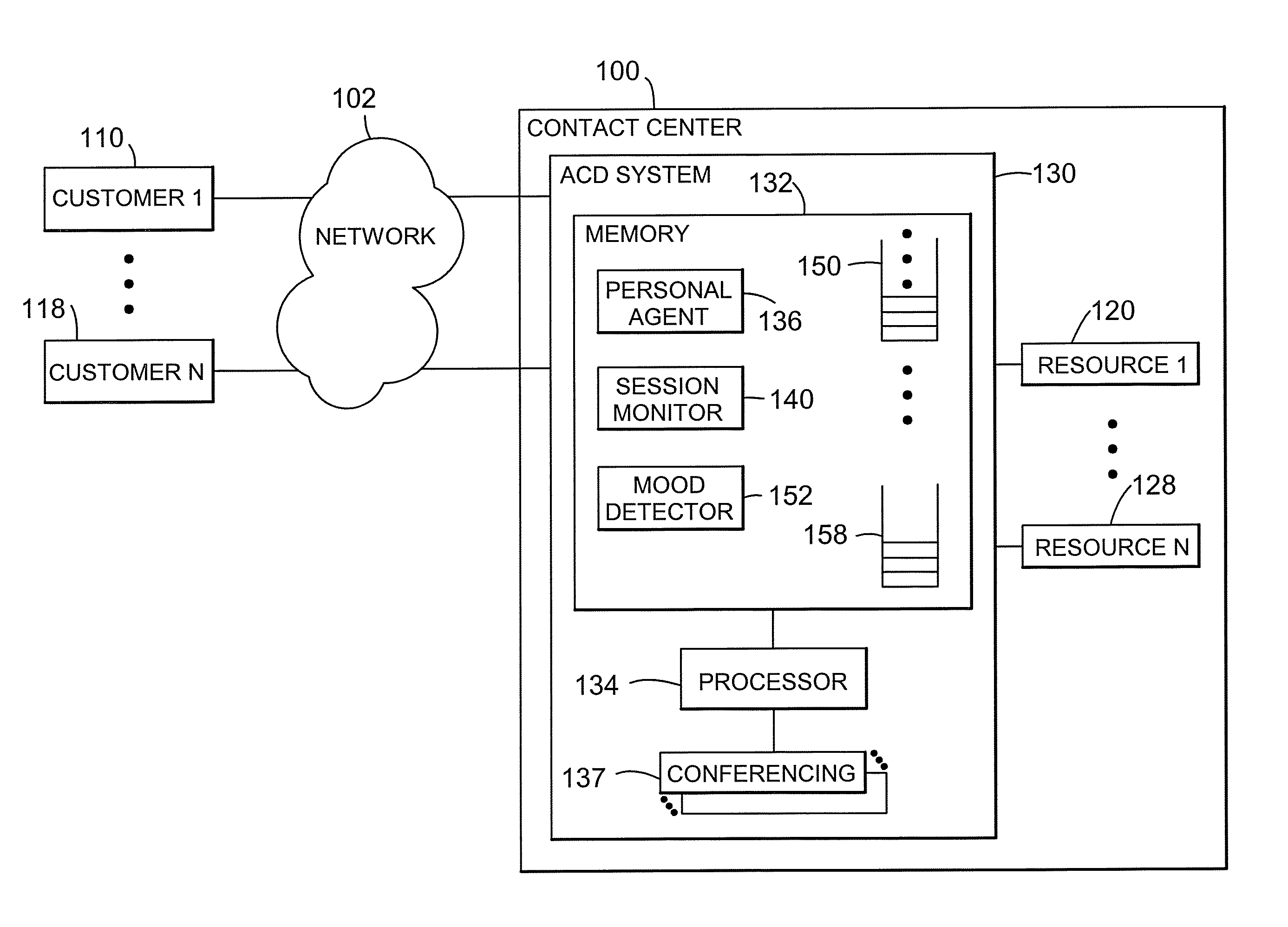
The present invention is directed to a customer contact 100 in which a session monitor 140 identifies and implements multi-customer sessions. A conferencing function 136 connects the plurality of customers 110-118 simultaneously to the same resource and / or to each other. Participation in the sessions can be mandatory or optional. The sessions can be created continually or periodically, such as when the contact center 100 is in an session mode. The sessions can be closed or open to new customers after commencement.
Owner:AVAYA INC
Establishing sessions with defined quality of service
ActiveUS20070002832A1Facilitate communicationFacilitate multimedia serviceNetwork traffic/resource managementConnection managementComputer hardwareQuality of service
The present invention allows different types of communication applications to cooperate with an associated communication client to facilitate communications having a defined quality of service. The communication client may establish an authorized virtual circuit having a defined quality of service through a network using a first session establishment protocol on behalf of the communication application. Once the authorized virtual circuit is established, the communication application may establish one or more communication sessions, which may support different types of multimedia services, through the virtual connection. In one embodiment, the virtual connection extends through the local access network, which may be supported by an IP multimedia subsystem (IMS). The communication client may use the Session Initiation Protocol (SIP) as the first session establishment protocol to establish the virtual circuit through the local access network.
Owner:MICROSOFT TECH LICENSING LLC
Session manager for web-based applications
ActiveUS20060212589A1Multiple digital computer combinationsTransmissionCommunications managementSession management
A communication manager for web-based applications receives indications of application time outs via a callback mechanism. During session initiation, the communication manager provides a termination address to an application along with a session ID. If the session times out due to inactivity, the application may signal the communication manager that the session ID is invalid by sending a message to the termination address. Alternatively, when a communication manager establishes communication sessions for several applications with a common external terminal, the communication manager may receive messages identifying terminal activity at one of the applications and may signal to the other applications to keep their sessions active.
Owner:SAP AG
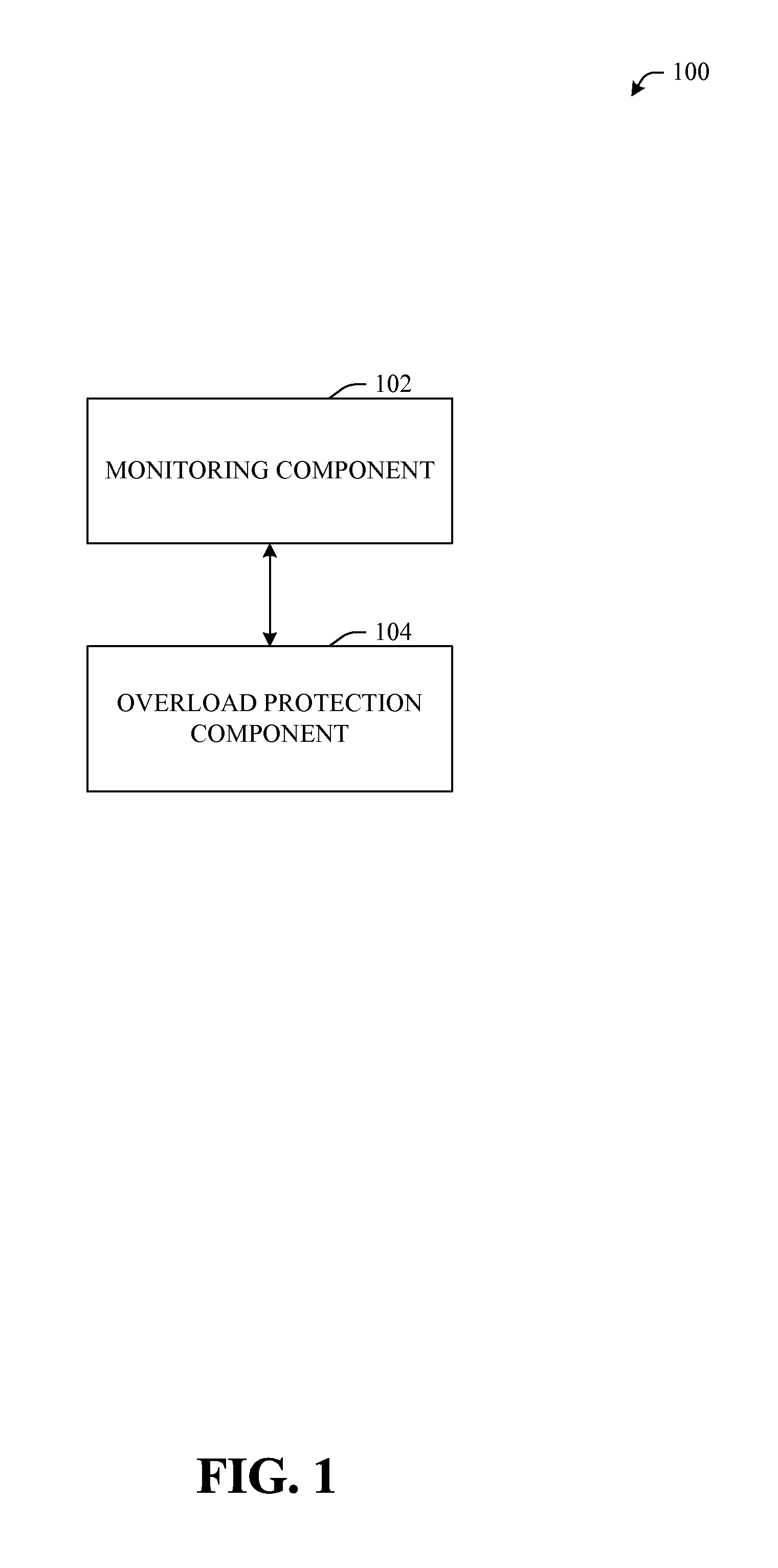
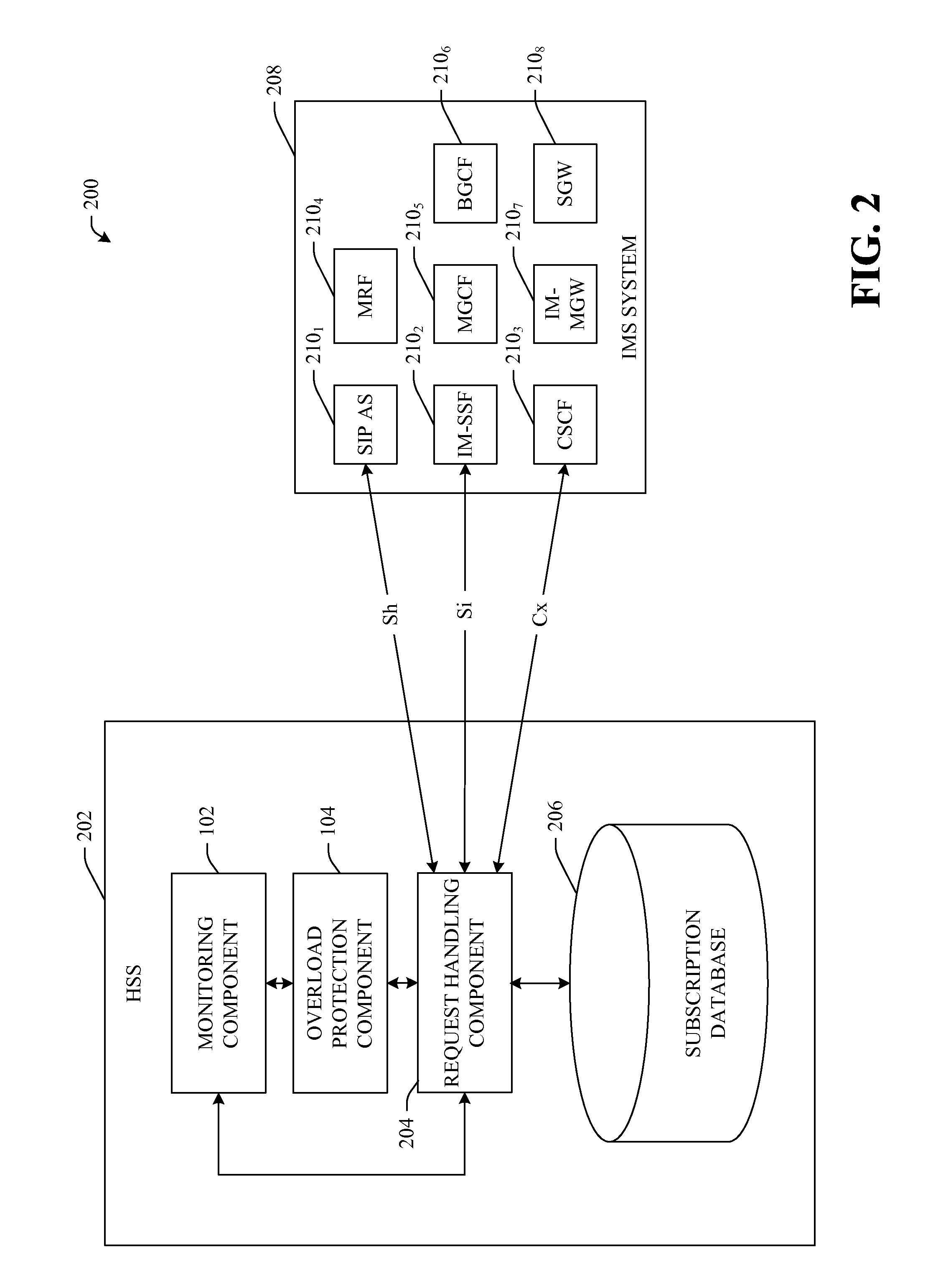
Methods to improve overload protection for a home subscriber server (HSS)
ActiveUS20110295996A1Improve efficiencyEasy to handleMultiple digital computer combinationsProgram controlComputer scienceSession ID
A system and methodology that facilitates improving performance of a Home Subscriber Server (HSS) during overload conditions, by embedding a unique Application Session Identifier (app session ID) within multiple requests associated with a single call processing session is provided. Moreover, the system includes an overload protection component that identifies whether an incoming request is associated with previously processed requests based in part of the app session ID embedded within the incoming request. When the HSS is overloaded, the incoming requests that initiate a new call processing session and are not associated with previously processed requests are rejected / dropped before incoming requests that are associated with requests that have been previously processed.
Owner:AT&T INTPROP I L P
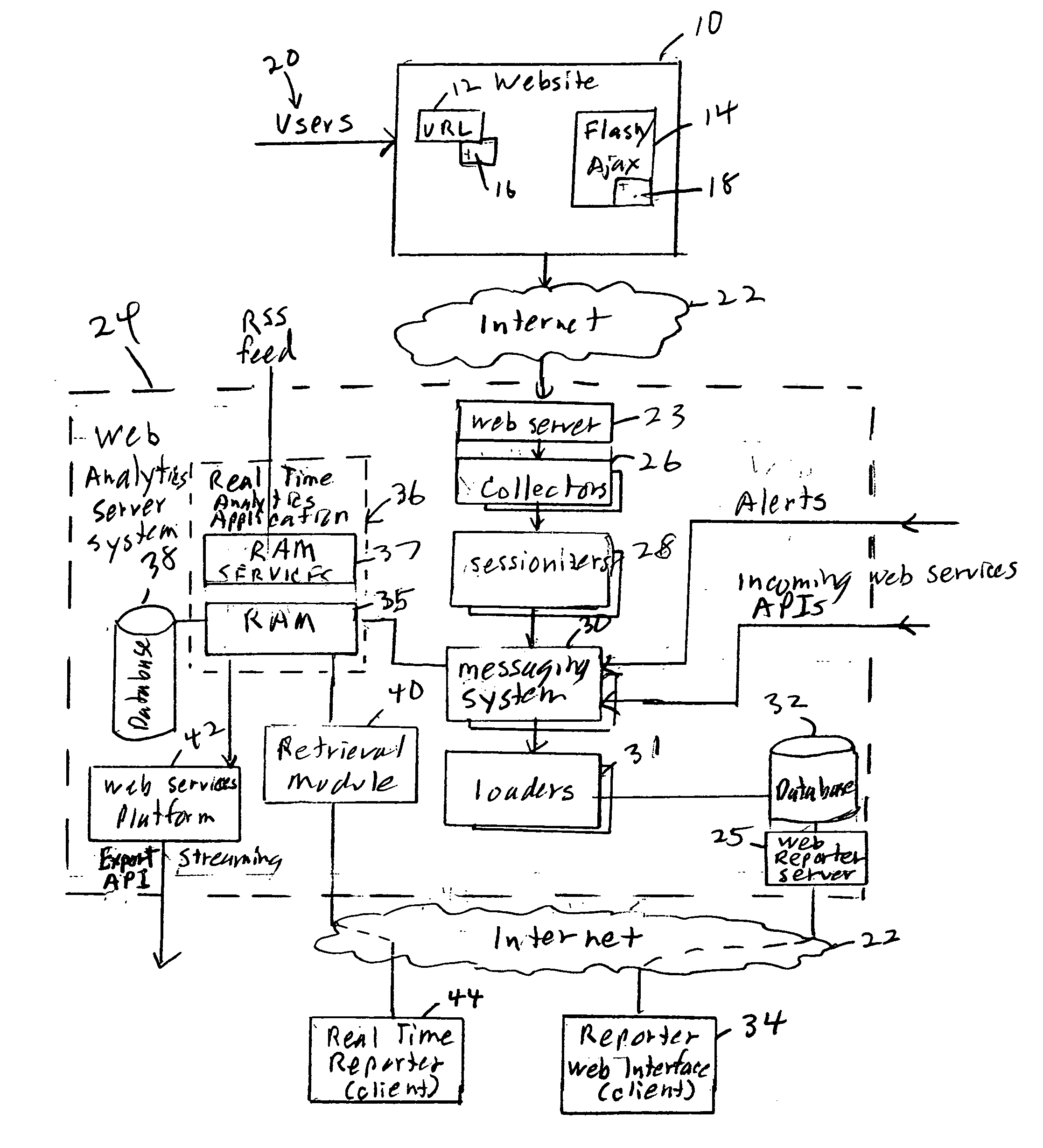
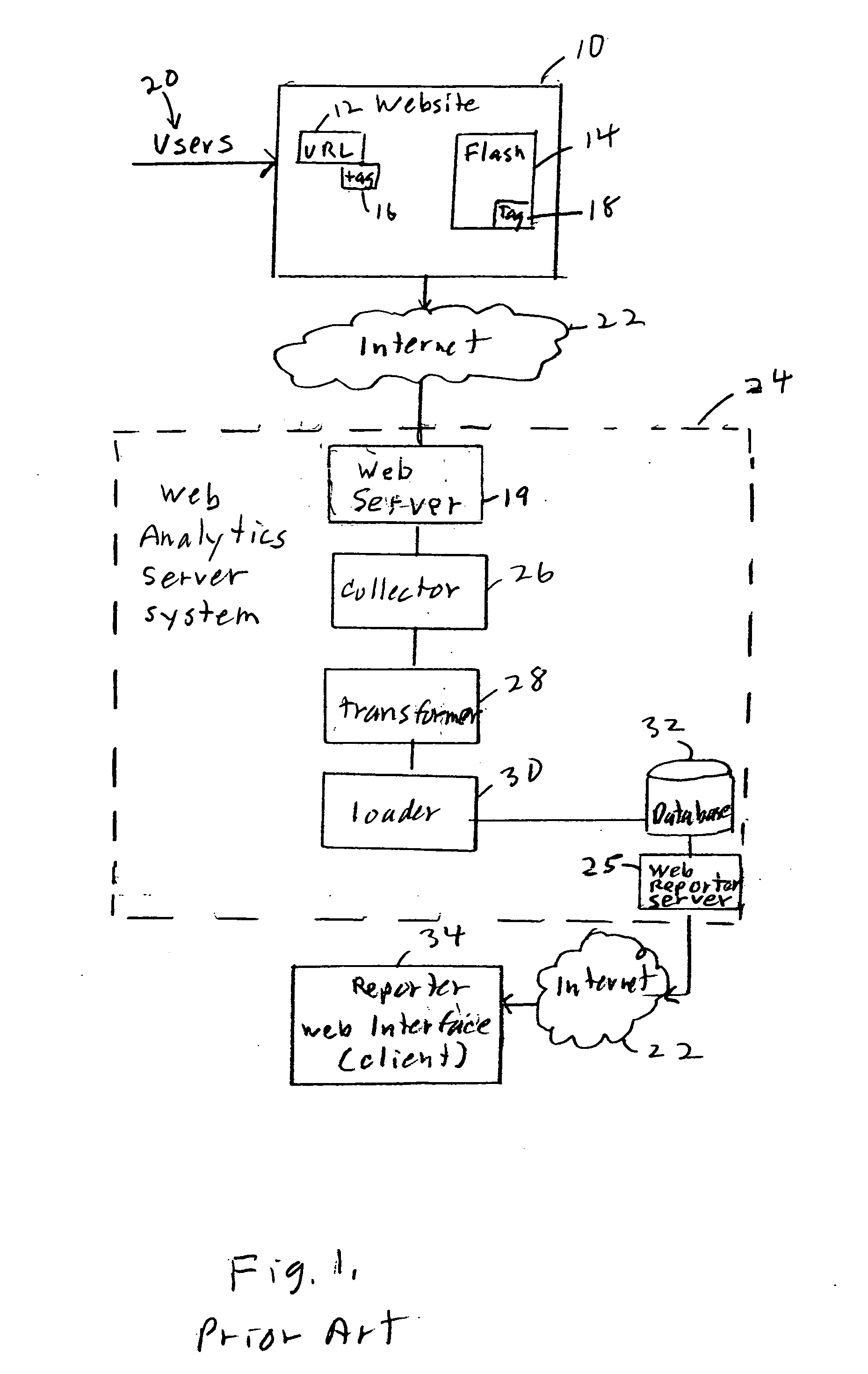
Session based web usage reporter
ActiveUS20080086558A1Speeds up presentationError detection/correctionDigital computer detailsTransformerSession ID
A system groups the data into sessions to allow tracking and evaluation of individual user behavior. By grouping clicks of a user in a session, the pattern of clicks can be observed, such as which path or pattern of clicks leads to a purchase. In particular, the session data is organized by session, using session transformers or “sessionizers,” before it is provided for database storage, enabling real-time session based analytics.
Owner:ACOUSTIC LP
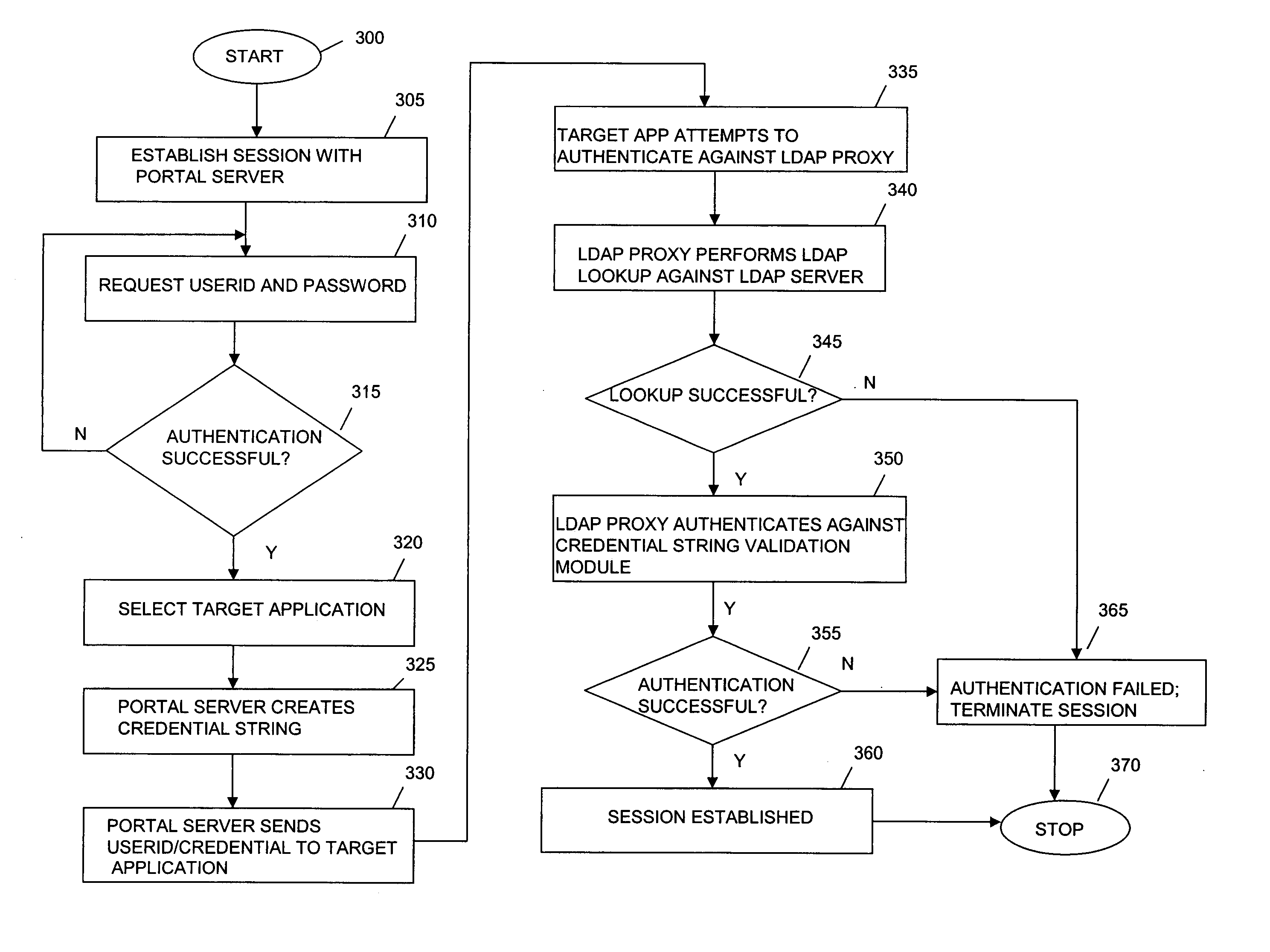
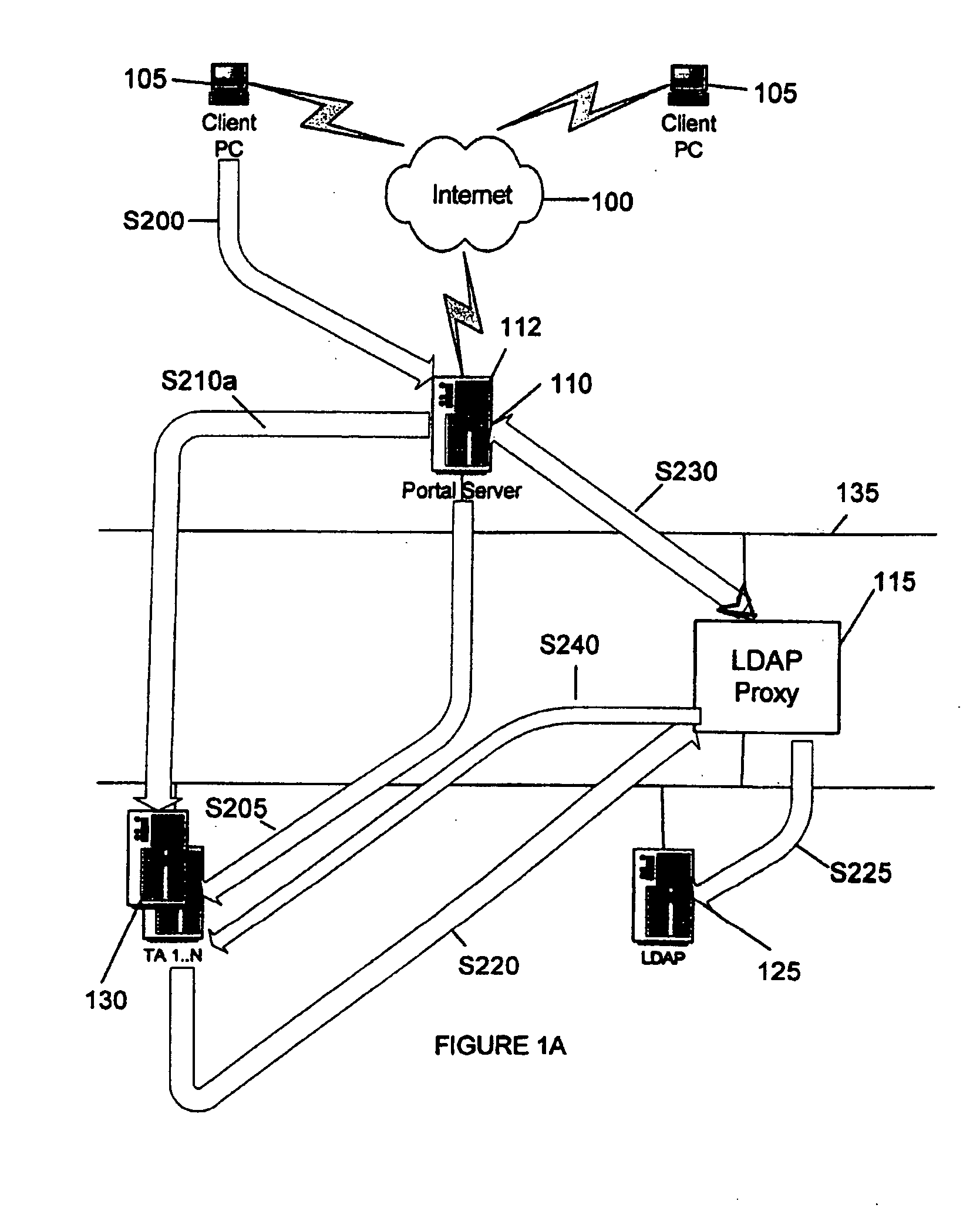
System and method of providing credentials in a network
InactiveUS20050198501A1Digital data processing detailsUser identity/authority verificationPasswordValidator
A method and system is provided to provide single sign on (SSO) functionality in a network that avoids storing a user's credentials in persistent storage. A session may be initiated with a portal which sends a session ID derivative as a credential string instead of a user's password to a target application. When the target application attempts to authenticate the user, by sending a request to a LDAP directory, the request is intercepted by a LDAP proxy that instead validates the UserID with the LDAP directory and the password is validated by a credential validator component which verifies with the portal that the credential string presented as the user password has been produced from the active session ID. In an embodiment, the credential string validator validates each short-living credential only once and upon detecting a second validation request for the same string, initiates a security breech process. A target application proxy may also be employed to terminate all sessions with the UserID when duplicate session requests occur.
Owner:IBM CORP
Methods And Apparatus For Use In Establishing A Data Session Via An Ad Hoc Wireless Network For A Scheduled Meeting
In one illustrative example, data for an appointment is saved in memory. The data include start data corresponding to a start date and time of the appointment, an identifier or address of at least one other mobile device, and at least one of a session ID or key. When a current date and time matches the start date and time, the mobile device grants permission to share, with another mobile device, location information indicating a location of the mobile device. The mobile device also receives location information indicating a location of the other mobile device. When the location information indicates that the locations are within a predetermined range of each other, the mobile device connects in an ad hoc wireless network with the other mobile device with use of the session ID or key, for the communication of one or more files in a secure data session.
Owner:MALIKIE INNOVATIONS LTD
System and method for secure sticky routing of requests within a server farm
ActiveUS20040024880A1Multiple digital computer combinationsTransmissionNetwork addressingNetwork address
Upstream devices, such as load balancers or routers, within a server farm, may be configured to route requests to the servers handling sessions for those requests using a secure (e.g. encrypted) unique ID or network address received with requests identifying how requests may be routed through the server farm. Upstream devices or a server receiving a request that is not associated with a session may generate a unique ID or select a network address identifying how the request is routed through the server farm. The server handling the request forms a session ID and returns that session ID and the unique ID to the client that originated the request. Encryption may be performed on network addresses or session IDs. Upon receiving a request corresponding to an established session, an upstream device may then decrypt routing information from the encrypted unique ID or network address and send the request downstream accordingly.
Owner:ORACLE INT CORP
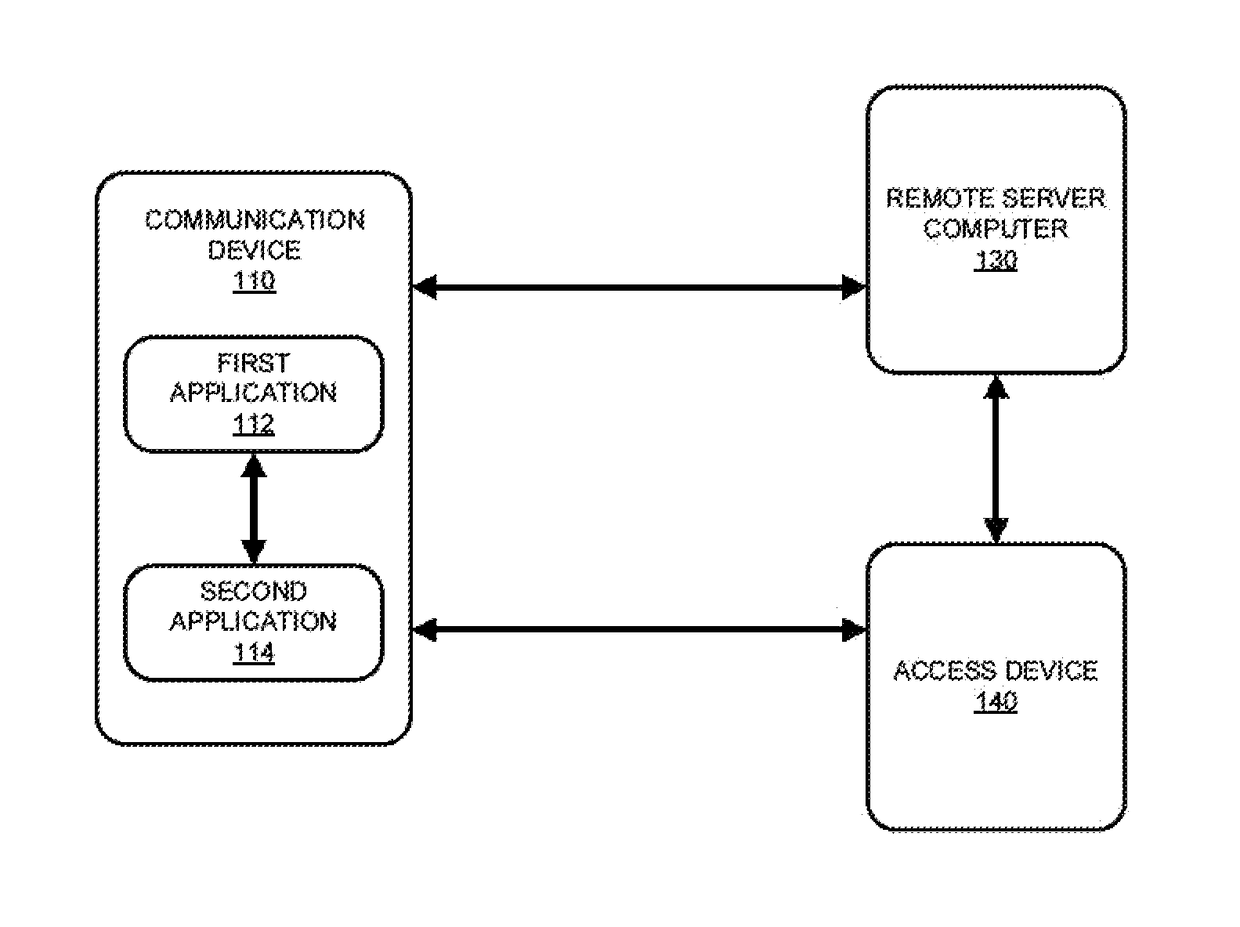
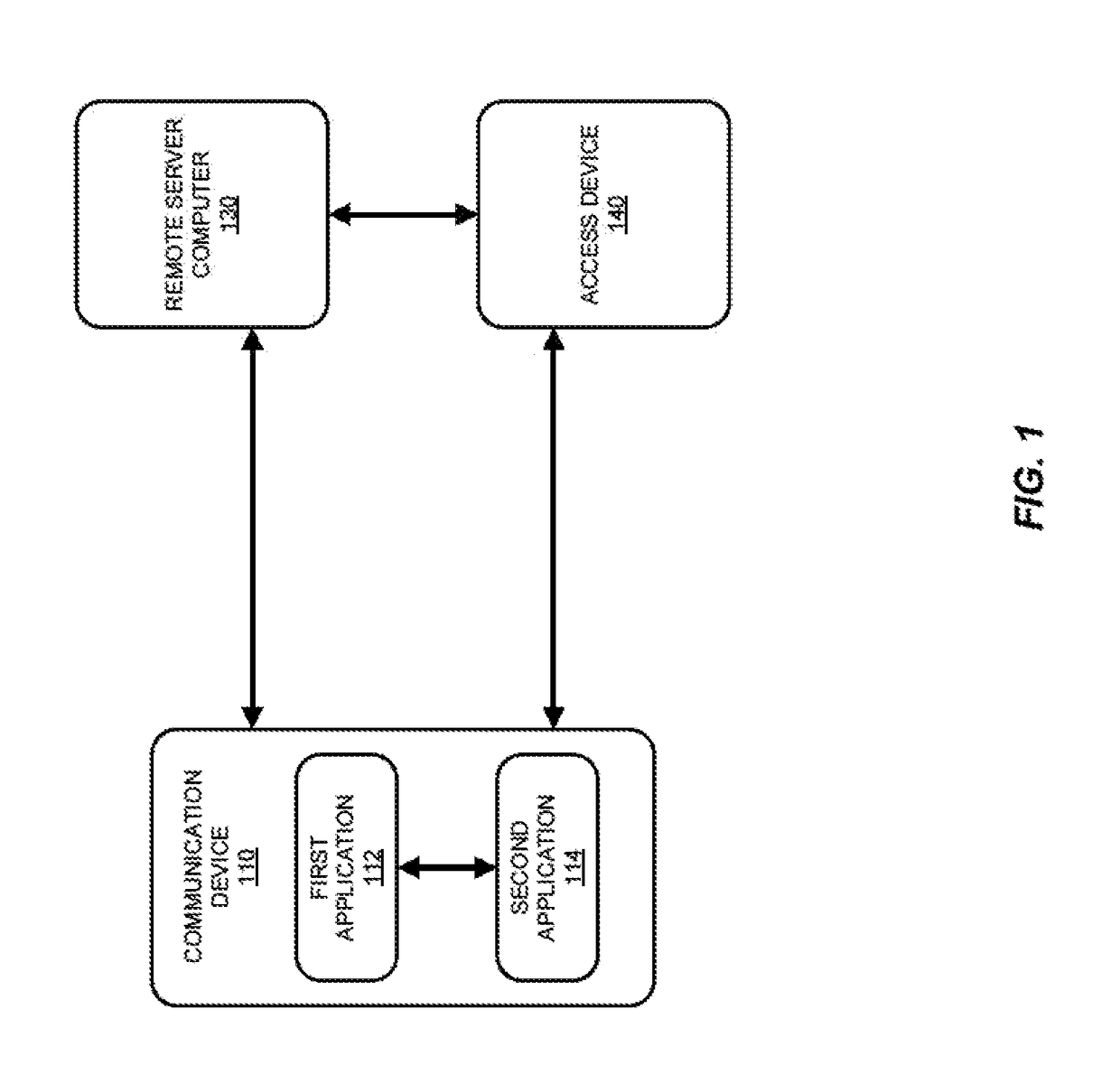
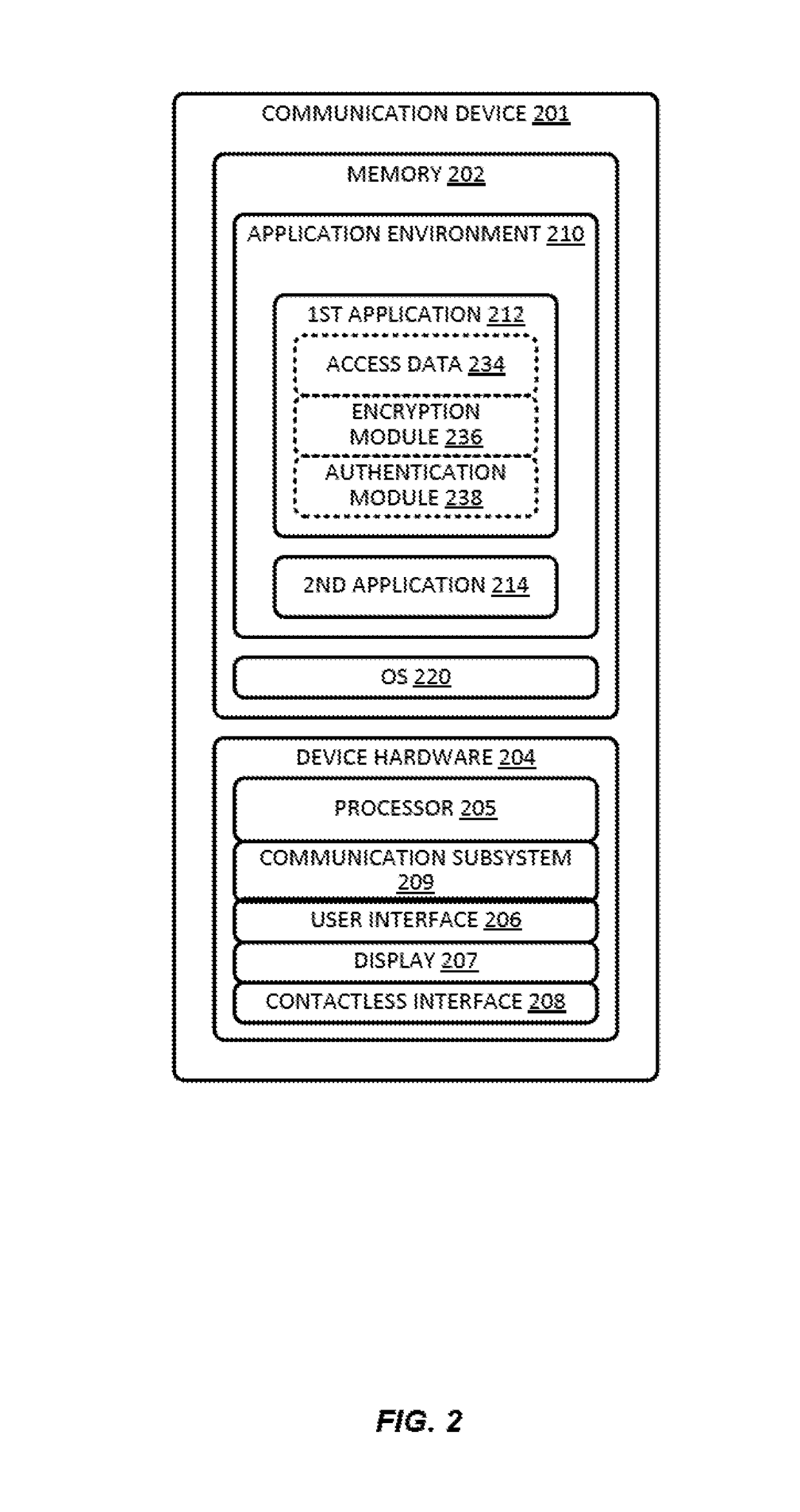
Systems and methods for device push provisioning
ActiveUS20170201520A1Accurate trackingAccurate associationTransmissionSecurity arrangementUser inputUser identifier
Techniques for provisioning access data may include receiving, by a first application installed on a communication device, user input selecting an account to provision to a second application installed on the communication device. The first application may invoke the second application and send a session identifier (ID) to the second application. The second application may send a user ID associated with the second application, a device ID, and the session ID to the first application. The first application may then generate encrypted provisioning request data and send the encrypted provisioning request data to the second application. The second application may send the encrypted provisioning request data to a remote server computer to request access data that can be used to access a resource. The second application may receive the access data provided by the remote server computer based on validation of the encrypted provisioning request data.
Owner:VISA INT SERVICE ASSOC
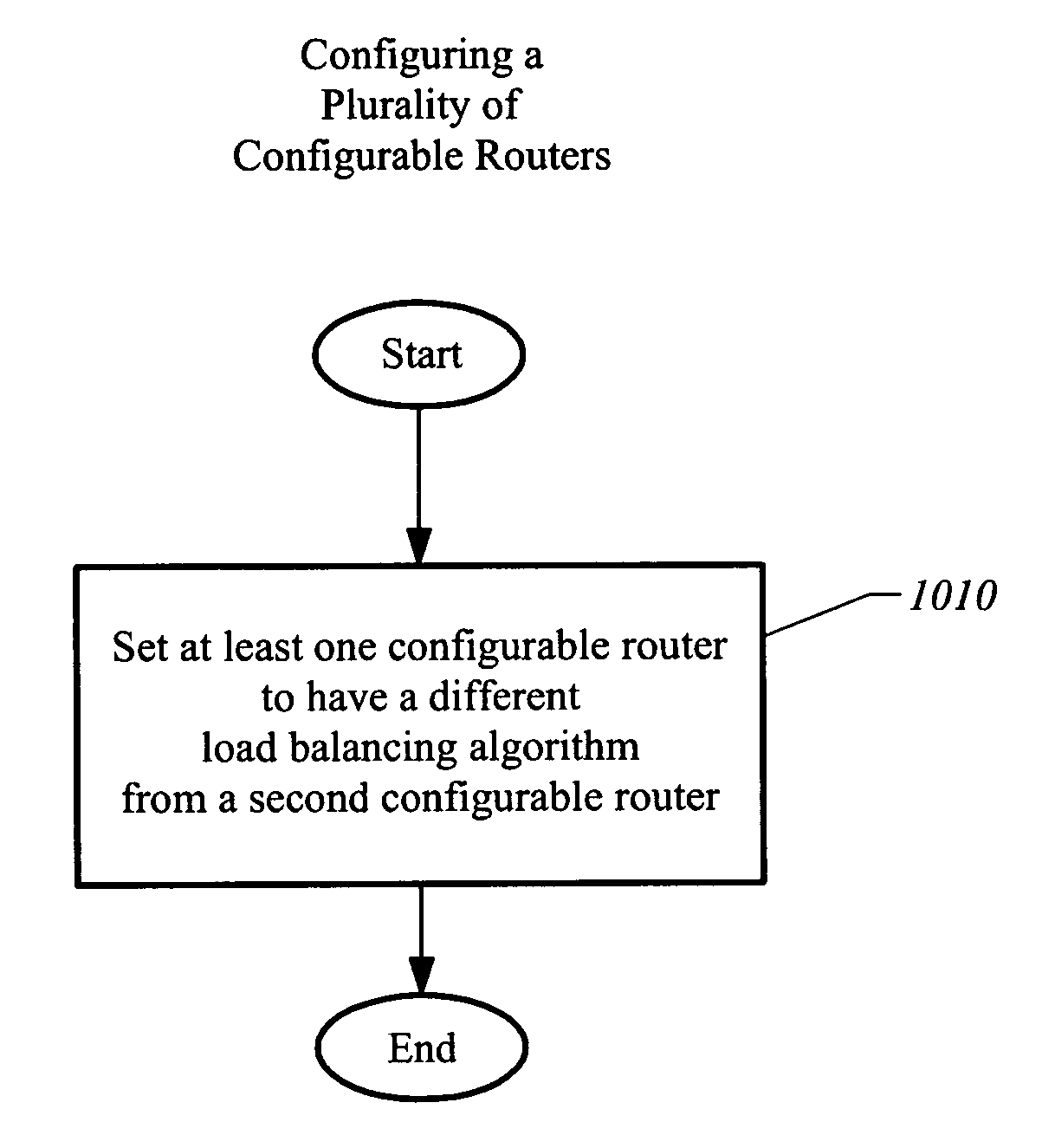
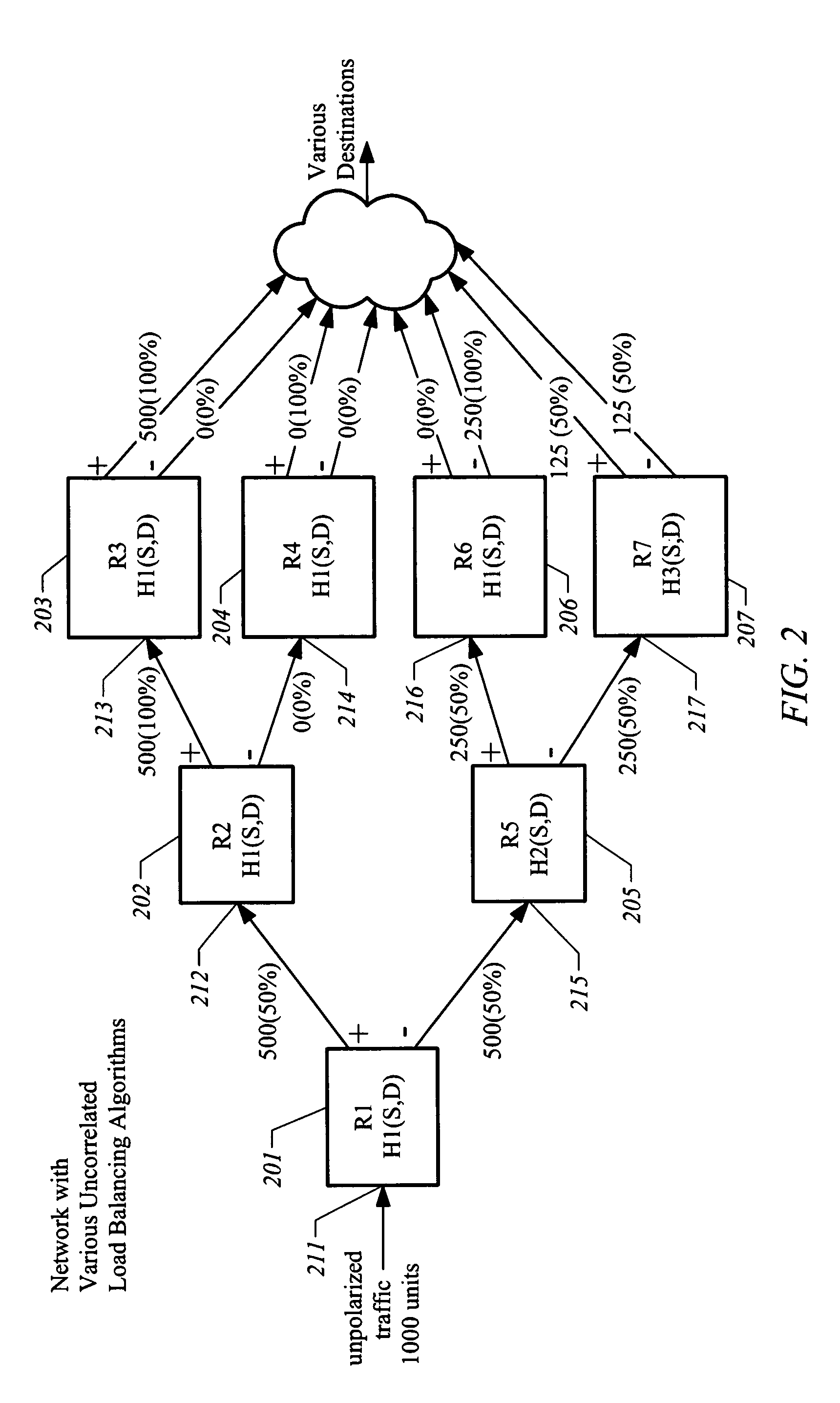
Method and apparatus for per session load balancing with improved load sharing in a packet switched network
InactiveUS6980521B1Increase traffic sharingReduce systematic unequal distribution of trafficMultiplex system selection arrangementsError preventionTraffic capacityAlgorithm Selection
Systems and methods for implementing per-session load balancing of packets that increase traffic sharing and reduce systematic unequal distribution of traffic are provided by virtue of one embodiment of the present invention. A method for operating a selected router is provided that uses a load balancing algorithm that is configured to de-correlate distribution of sessions among the active paths at the selected router relative to distributions of sessions of other algorithms at other routers of said network. Packets arriving at the selected router are assigned to an output path according to the load balancing algorithm. A method of routing a packet received at a router having an associated identifier is provided. The source address and a destination address of the packet are obtained. An output path is selected according to a load balancing algorithm that uses the associated identifier, the source address, and the destination address as inputs, and the packet is routed to the output interface associated with the selected output path. A look-up table that is configured using the identifier can be used in selecting the output path. A router storing an identifier assigned to the router is provided; the identifier is used in determining per-session routing of incoming packets.
Owner:CISCO TECH INC
Enhanced system for controlling service interaction and for providing blending of services
InactiveUS20070201665A1OptimizationEasy to useSpecial service for subscribersTransmissionCommunications systemMessage type
A service broker system is presented for mediating events or messages to be sent to or received from a plurality of applications to control service interaction and to provide service blending in a communications system. The service broker system includes steplet functional components that determine a desired mediation for feature interaction or service blending associated with an event or message, along with a message manager component with a dispatcher for the steplet functional components, where the message manager creates and maintains a unique message object for a received request message. A user and end point data manager component is provided to obtain user data and endpoint data and to bind attribute data to a user ID associated with a current service session, and a session context component for binding attribute data to session ID associated with the current service session. In one embodiment, the system includes two or more message manager components individually associated with a different message type.
Owner:WSOU INVESTMENTS LLC
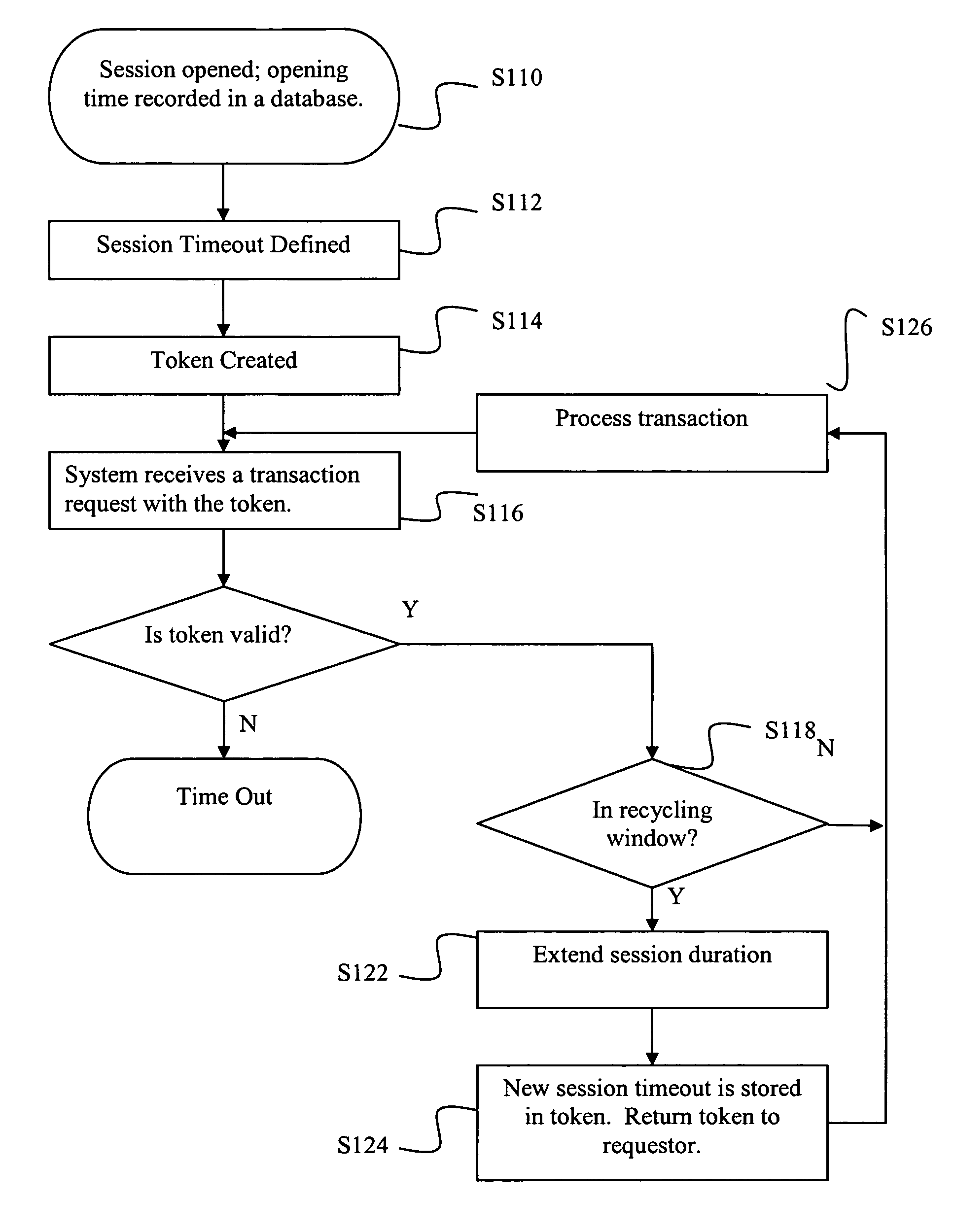
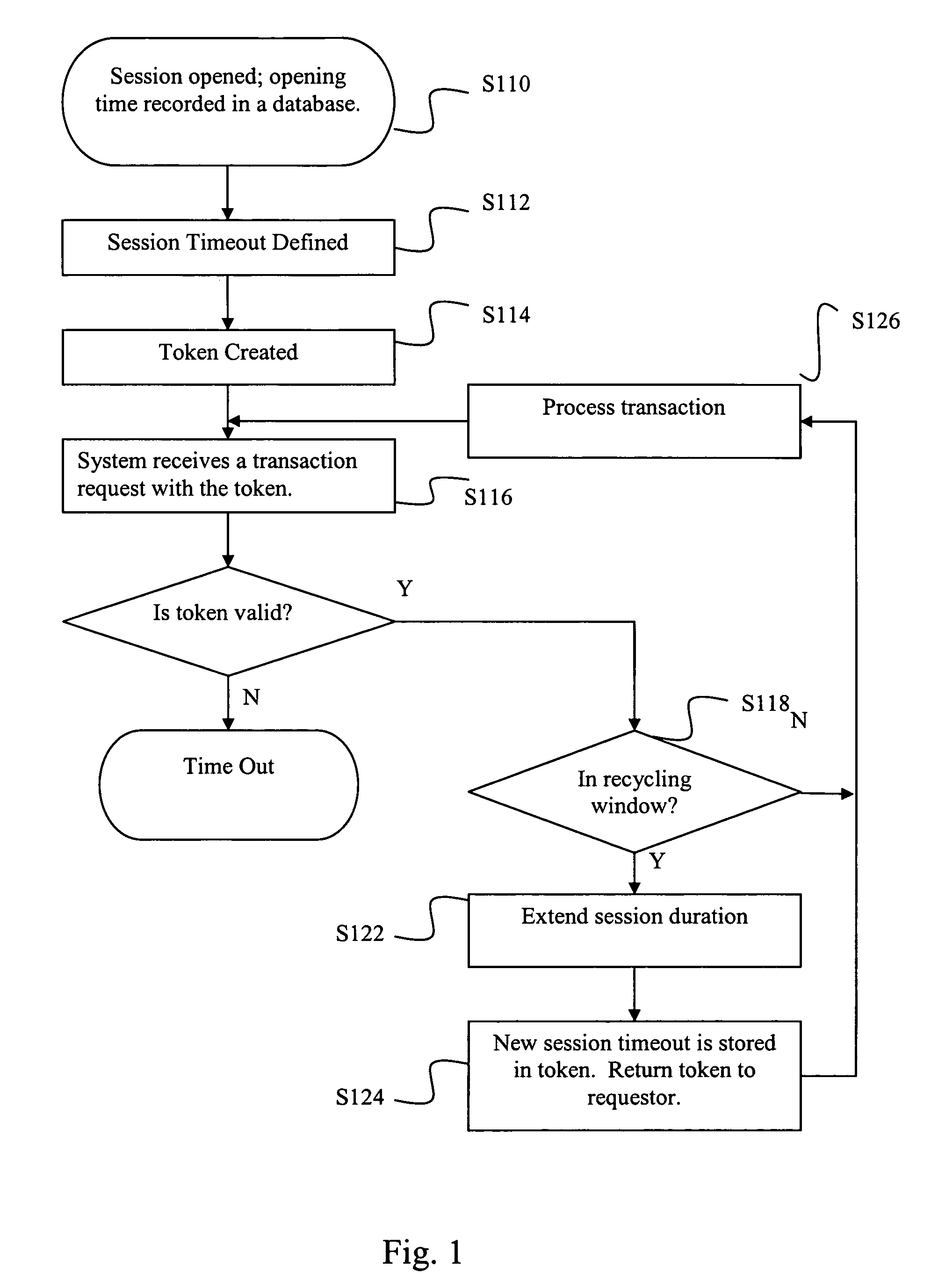
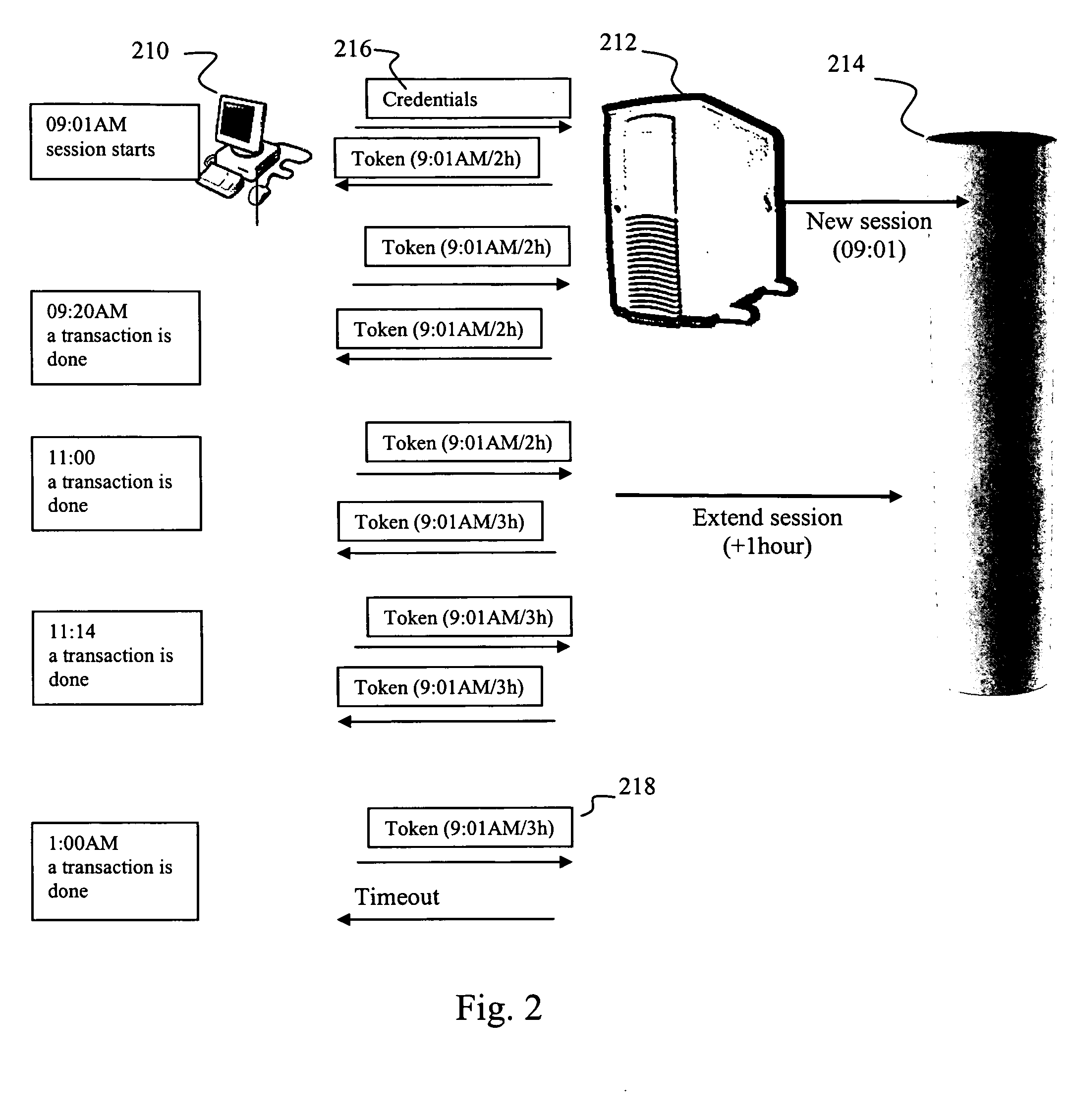
System and method for extending sessions
ActiveUS20080159318A1Reduce loadImproves database responsivenessData switching by path configurationComputer security arrangementsComputer SessionOperating system
A system and method of managing computer sessions are provided. The preferred method opens a session (such as for access to a database) and creates a token that includes a session opening time and a measure of the session duration. If the token is used within a predefined time window before the end of the session, the session is extended by updating the token to reflect a new session duration. The time window and duration of a session extension may be adjusted according to usage patterns of the system. The session may be extended recursively. The token expires when the last of the session extensions expires.
Owner:AMADEUS S
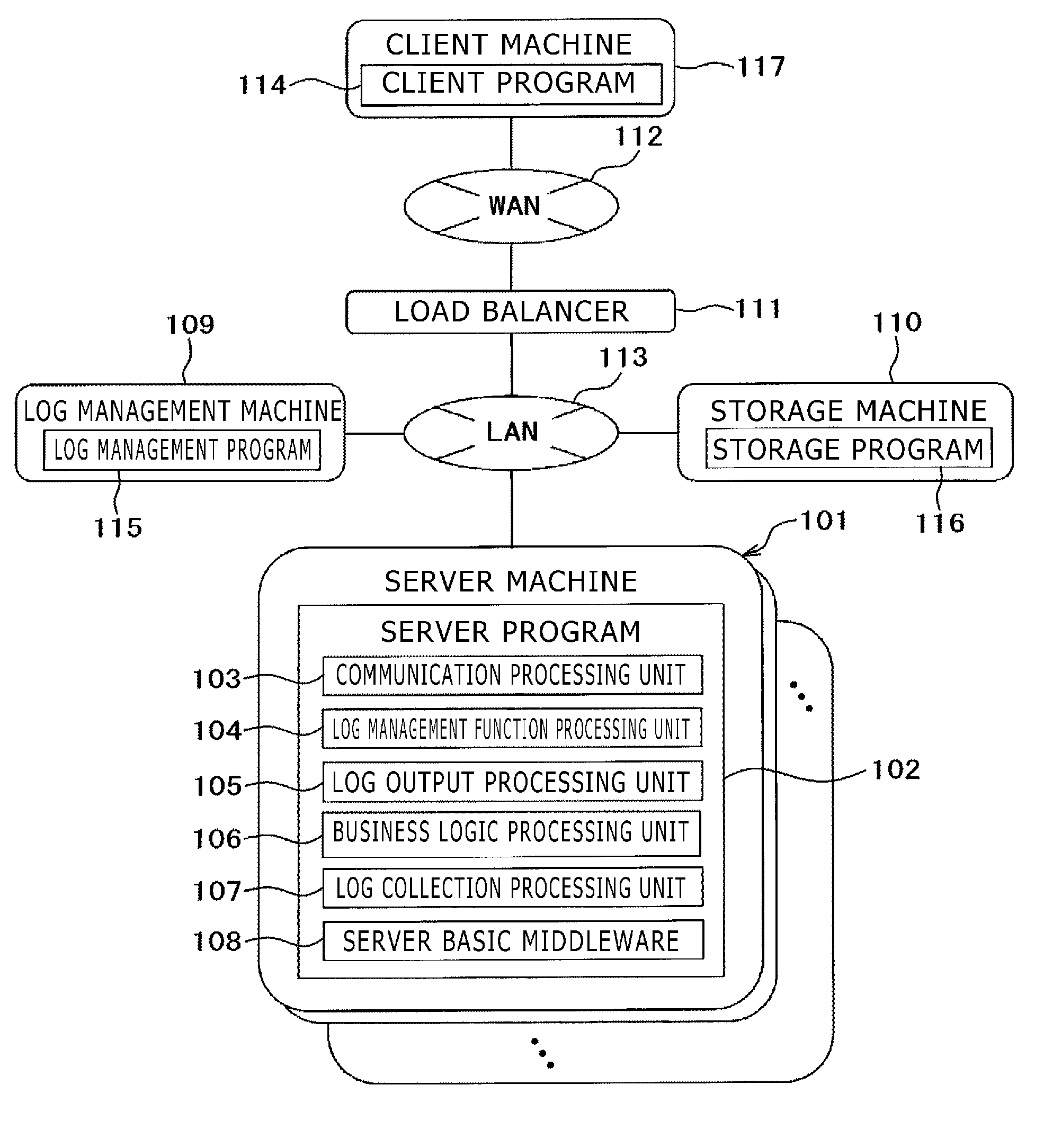
Log management system and log management method
InactiveUS20140108087A1Effectively includesWithout deteriorating productivity of developmentResourcesLog managementUser identifier
A server system generates one thread with respect to a request for a process, and at the time, a thread local storage that is a dedicated area in which data used for the thread is stored is secured on a main storage device. Log tracking information that can uniquely identify output of a log from the start of output of the log to the end of output of the same is held in the thread local storage during a process of a session ID, a user ID, and a sequence number. When the log is output, the log tracking information is added to the log data to be output to an auxiliary storage device.
Owner:HITACHI SOFTWARE ENG
Secure web server system for unattended remote file and message transfer
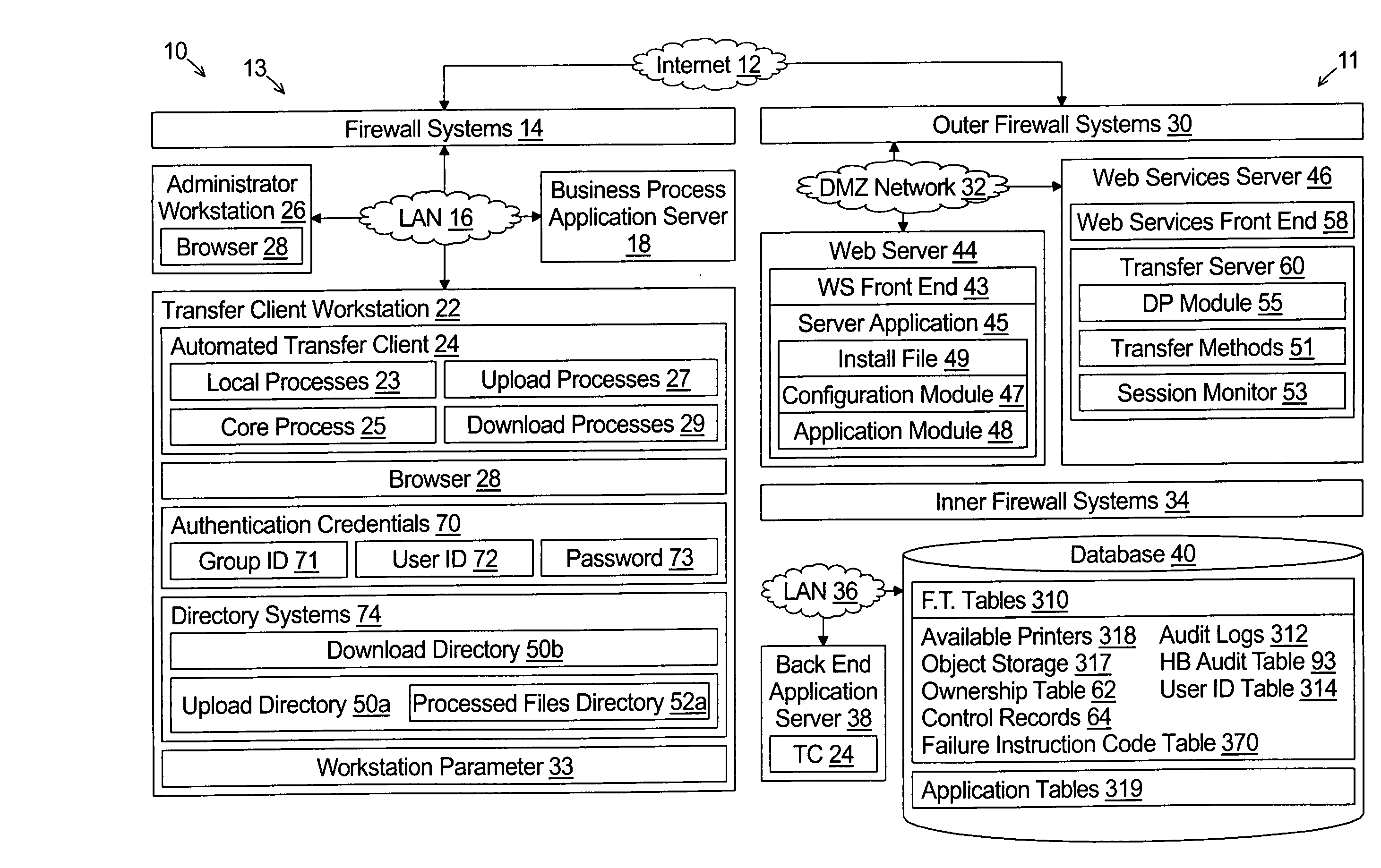
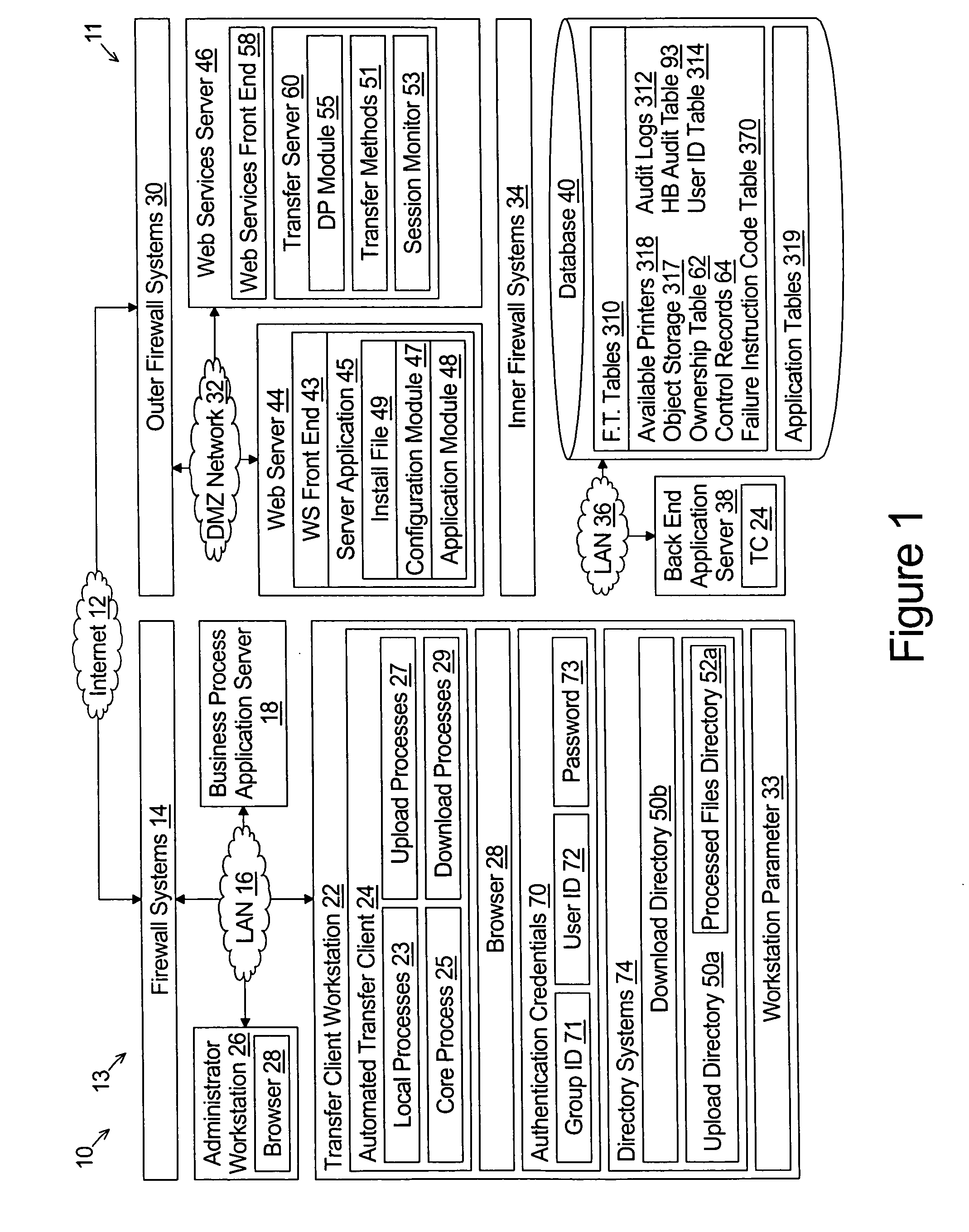
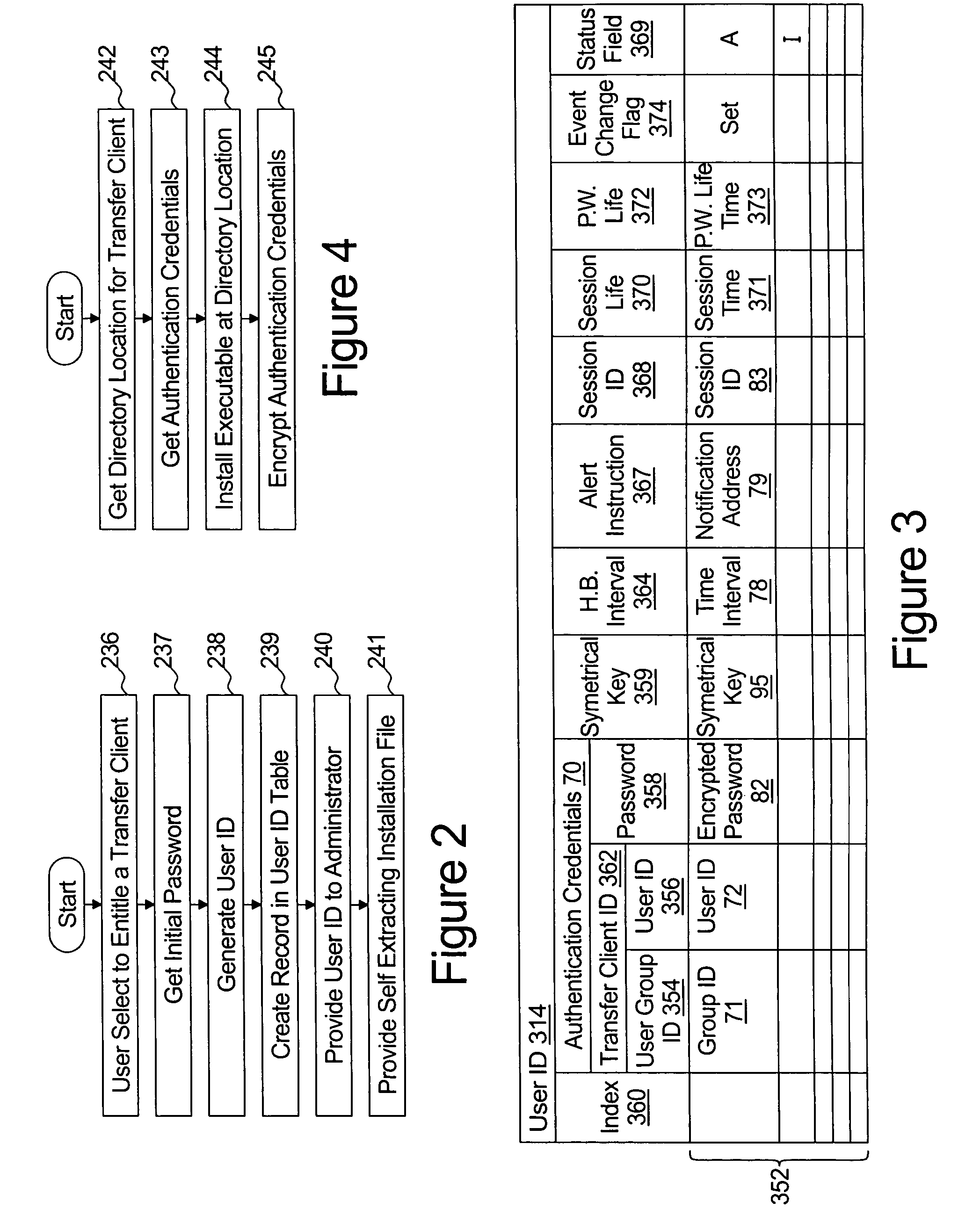
A system provides for the secure exchanging files with a remote transfer server over an open network such as the Internet. The system comprises a database with file transfer tables, a hypertext transport protocol (HTTP) server, and a web services server. The HTTP server is coupled to the database and provides web pages to an HTTP client to obtain file transfer event parameters and identification of a remote file transfer client to which the file transfer event parameters are associated. The file transfer event parameters are stored in the file transfer tables in association with the identification of the remote file transfer client. The web services server comprising a plurality of transfer methods. The transfer methods comprises: i) a method for associating a remote transfer client with a session ID; ii) a method for providing to the remote transfer client the file transfer event parameters that are associated with the remote transfer client in response to receiving a method call from the remote transfer client; and ii) a method call for executing a file exchange with the remote transfer client in response to receiving a method call from the remote transfer client that includes the file transfer parameters.
Owner:BOTTOMLINE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com