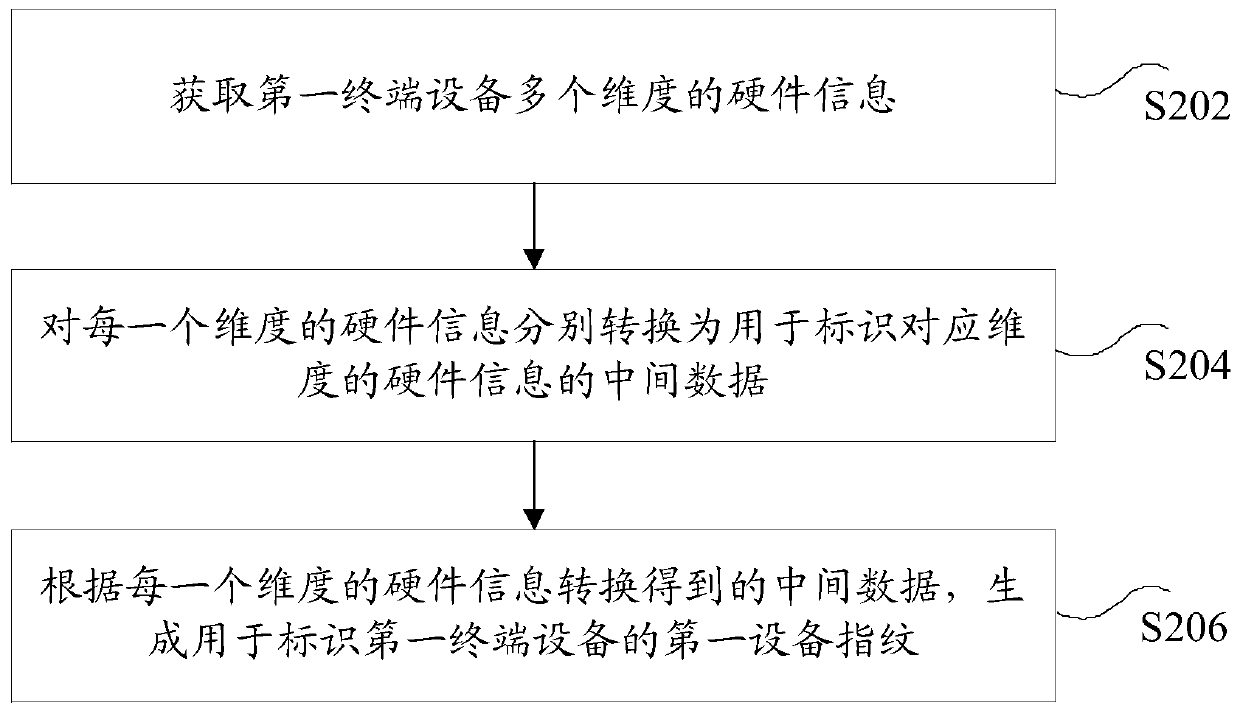
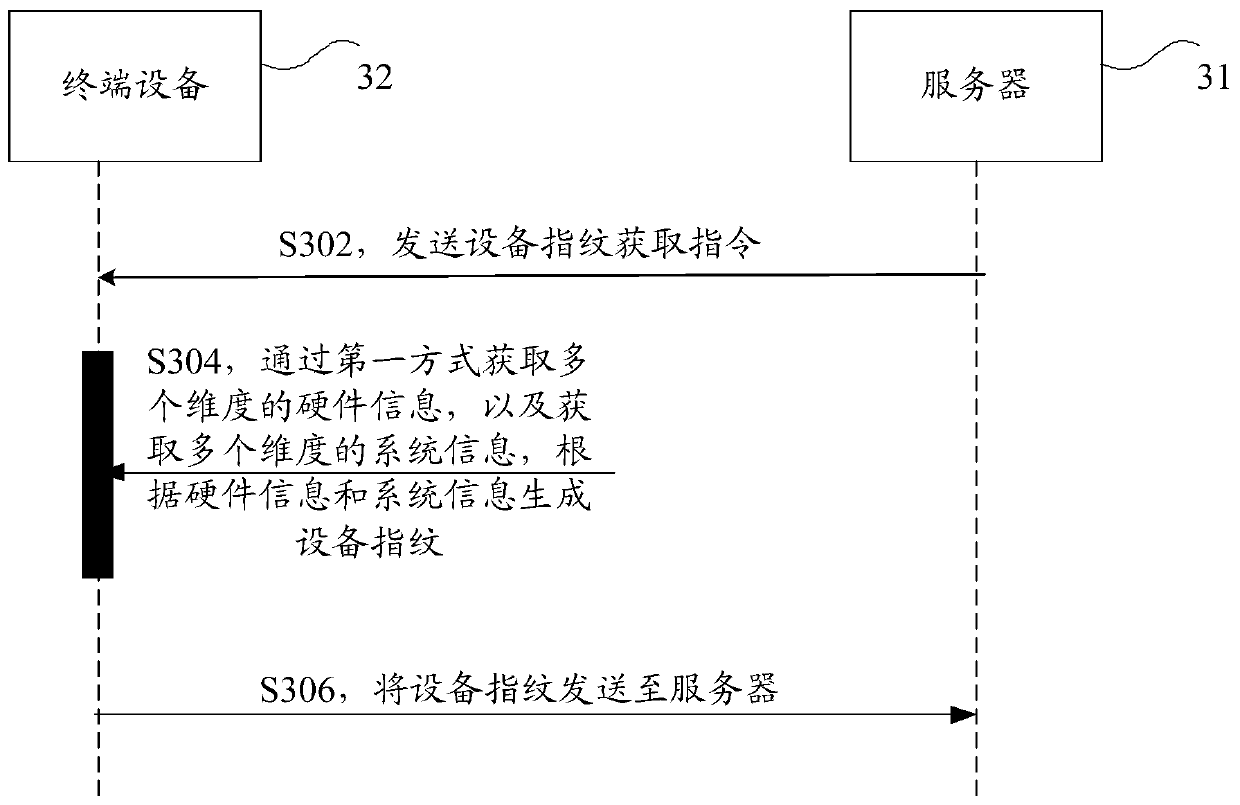
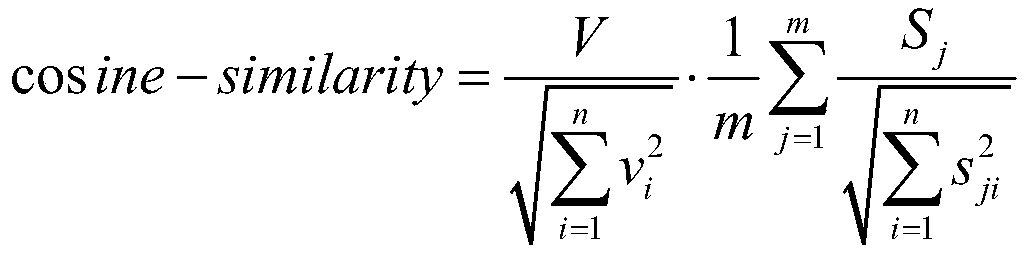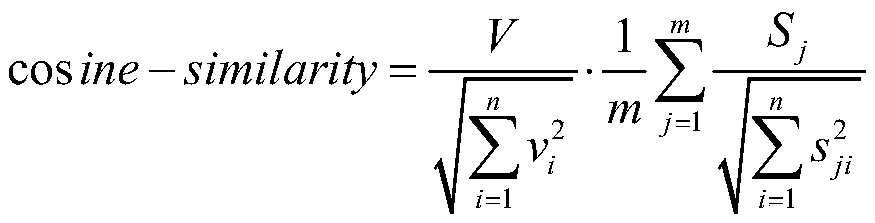Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
335 results about "Device fingerprint" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
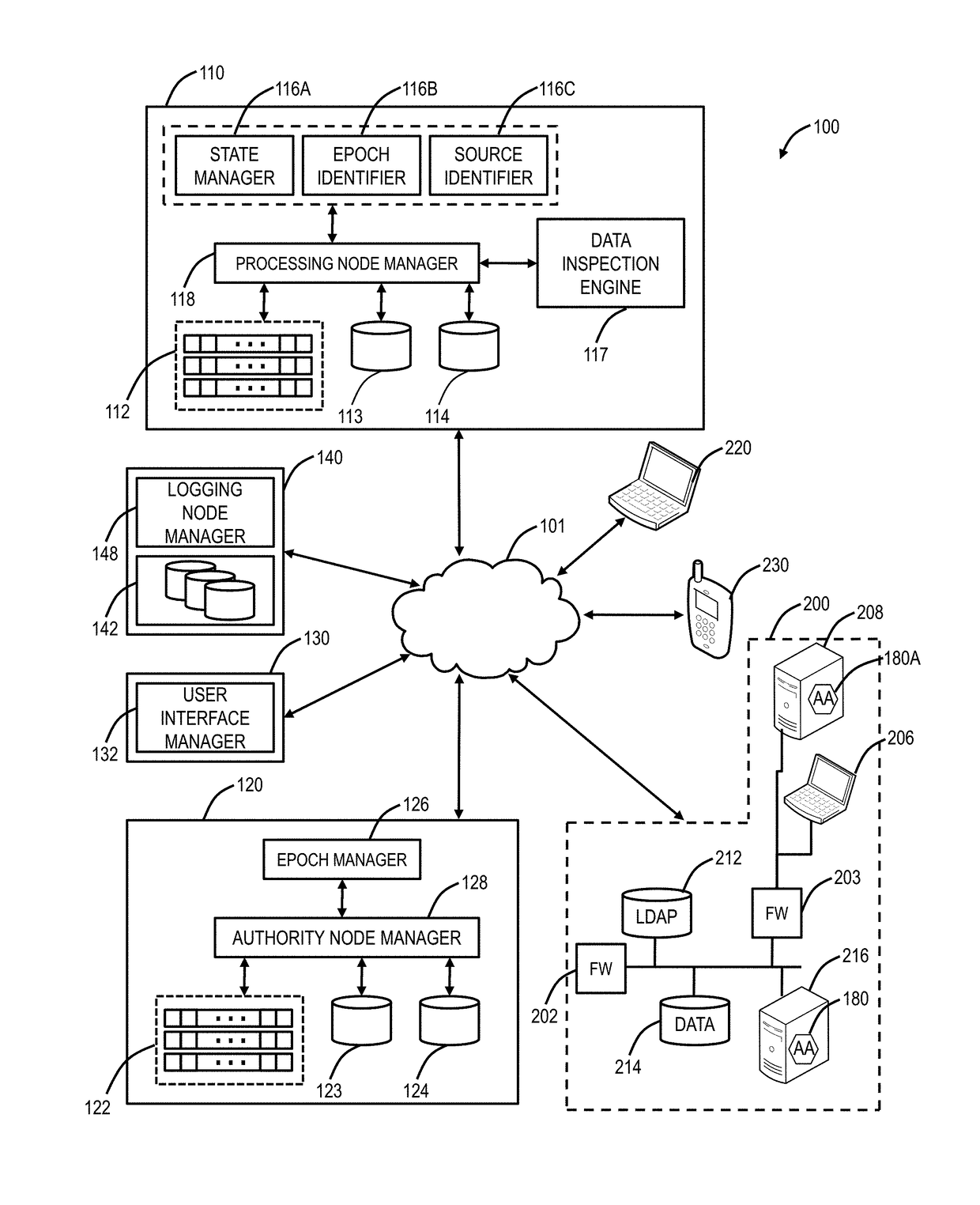
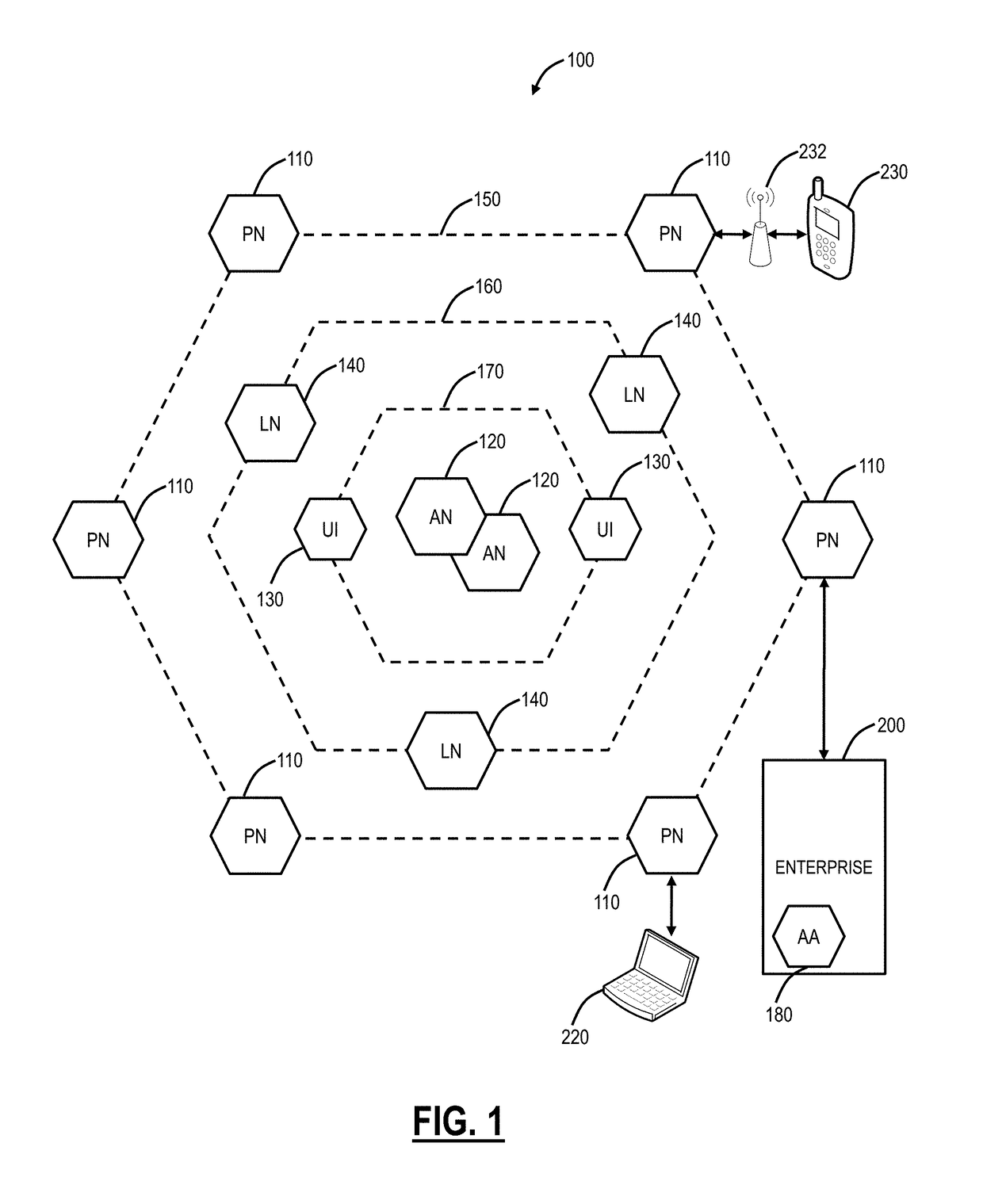
A device fingerprint, machine fingerprint, or browser fingerprint is information collected about a remote computing device for the purpose of identification. Fingerprints can be used to fully or partially identify individual users or devices even when persistent cookies (and also zombie cookies) can't be read or stored in the browser, the client IP address is hidden, and even if one switches to another browser on the same device. This may allow a remote application to detect and prevent online identity theft and credit card fraud, but also to compile long-term records of individuals' browsing histories even when they're attempting to avoid tracking, raising a major concern for internet privacy advocates. Some computer security experts consider the ease of bulk parameter extraction offered by web browsers to be a security hole.
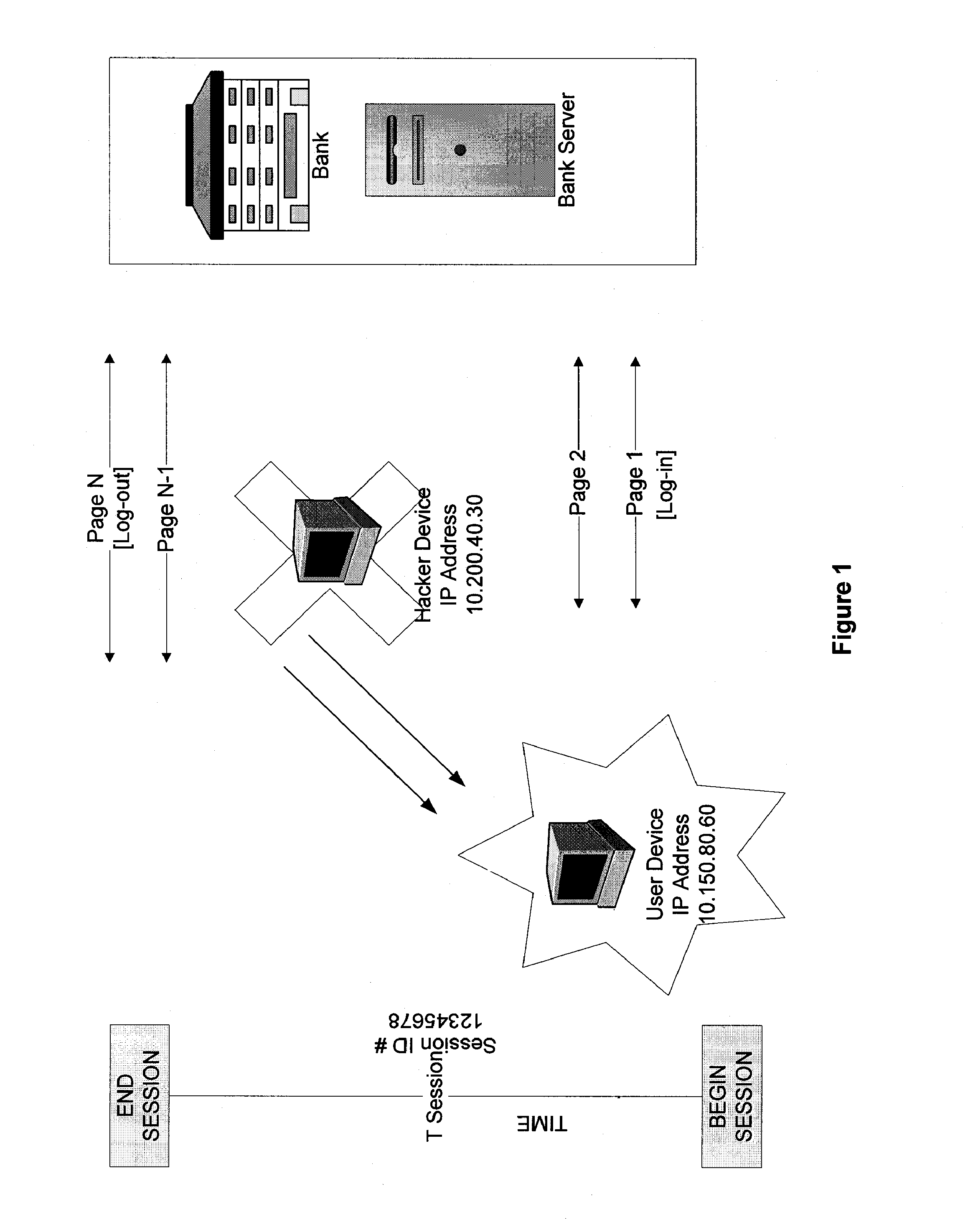
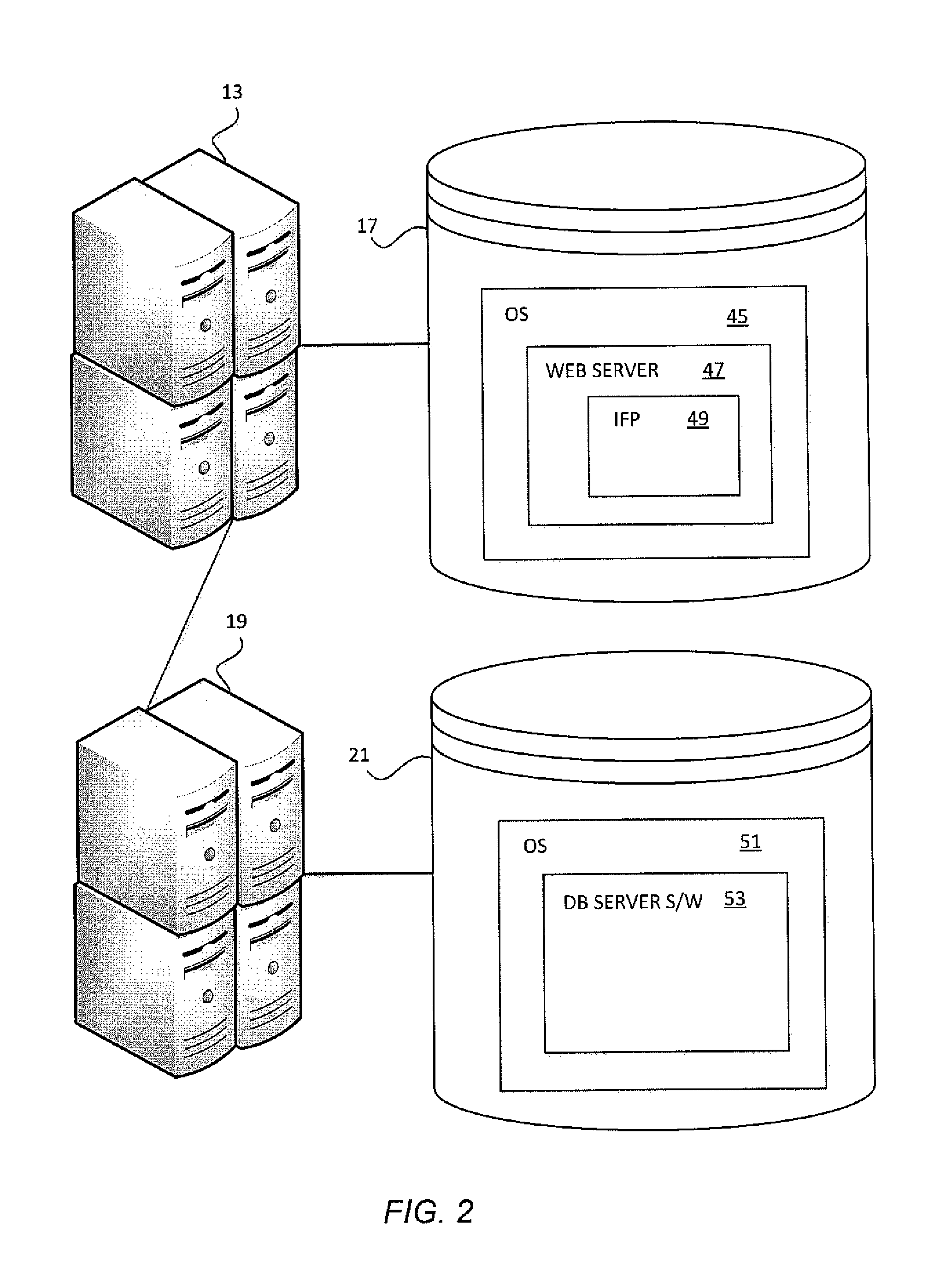
Systems and methods for detection of session tampering and fraud prevention
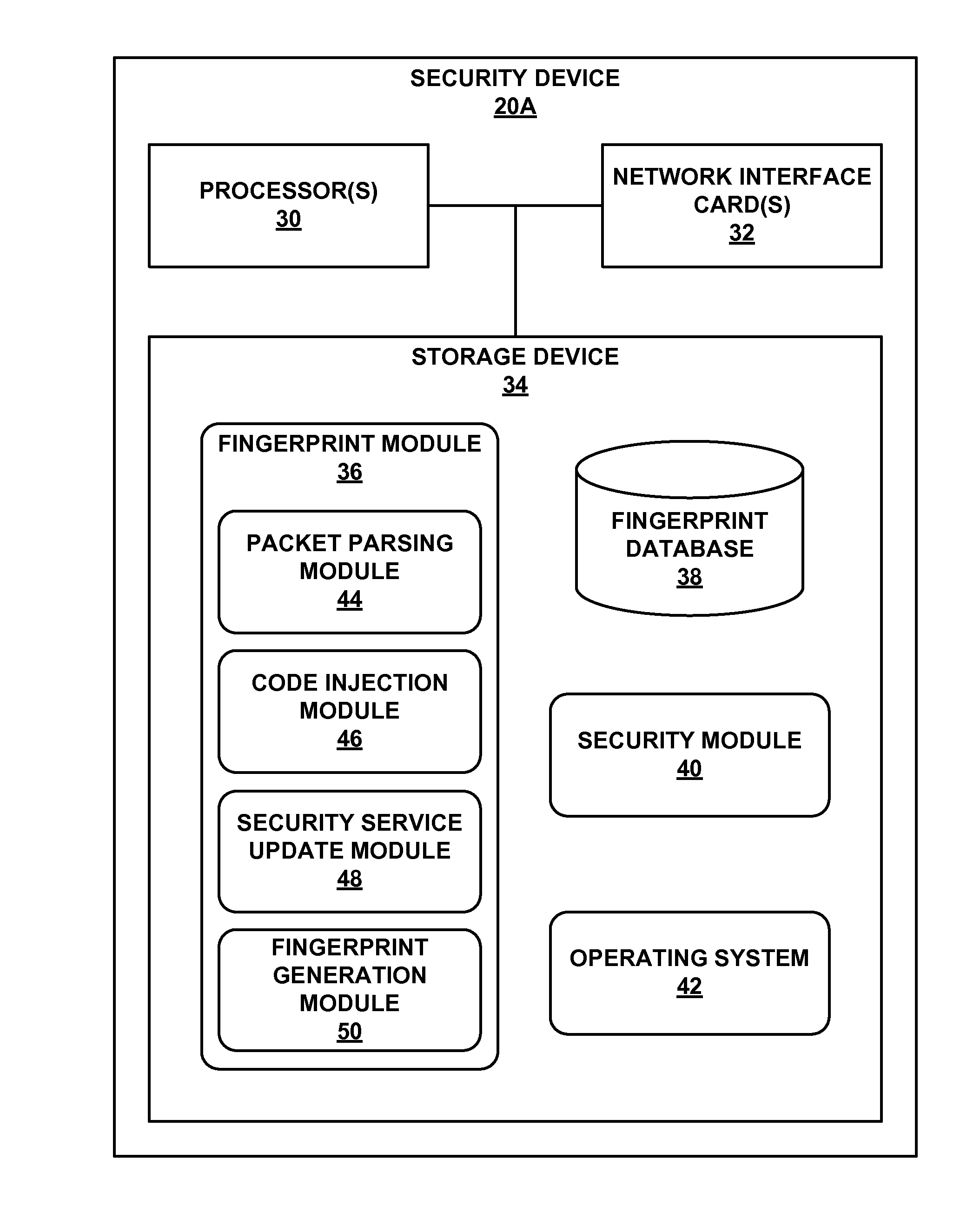
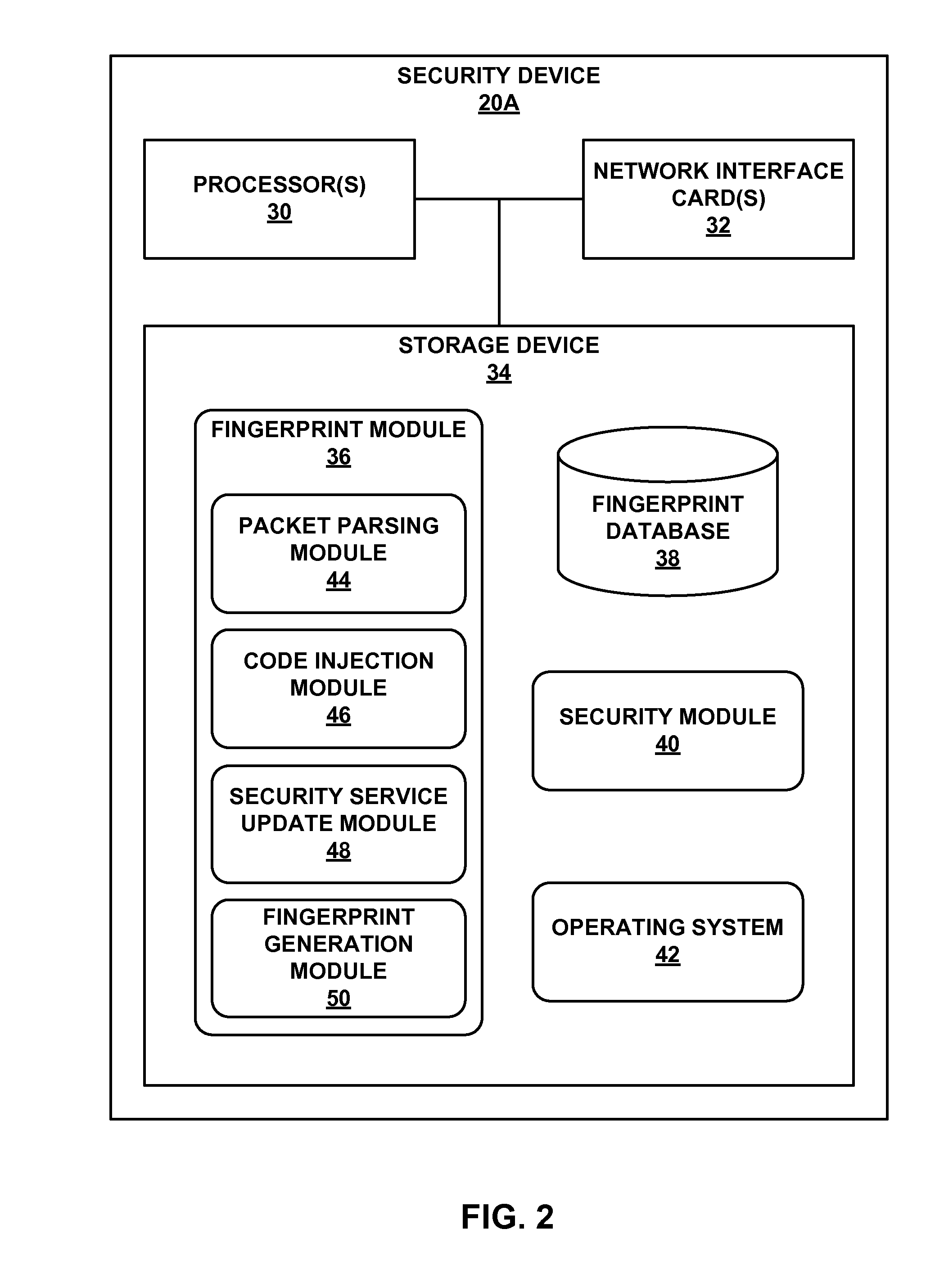
ActiveUS20070234409A1Secure performanceIdentify theftMemory loss protectionError detection/correctionMan-in-the-middle attackOperating system
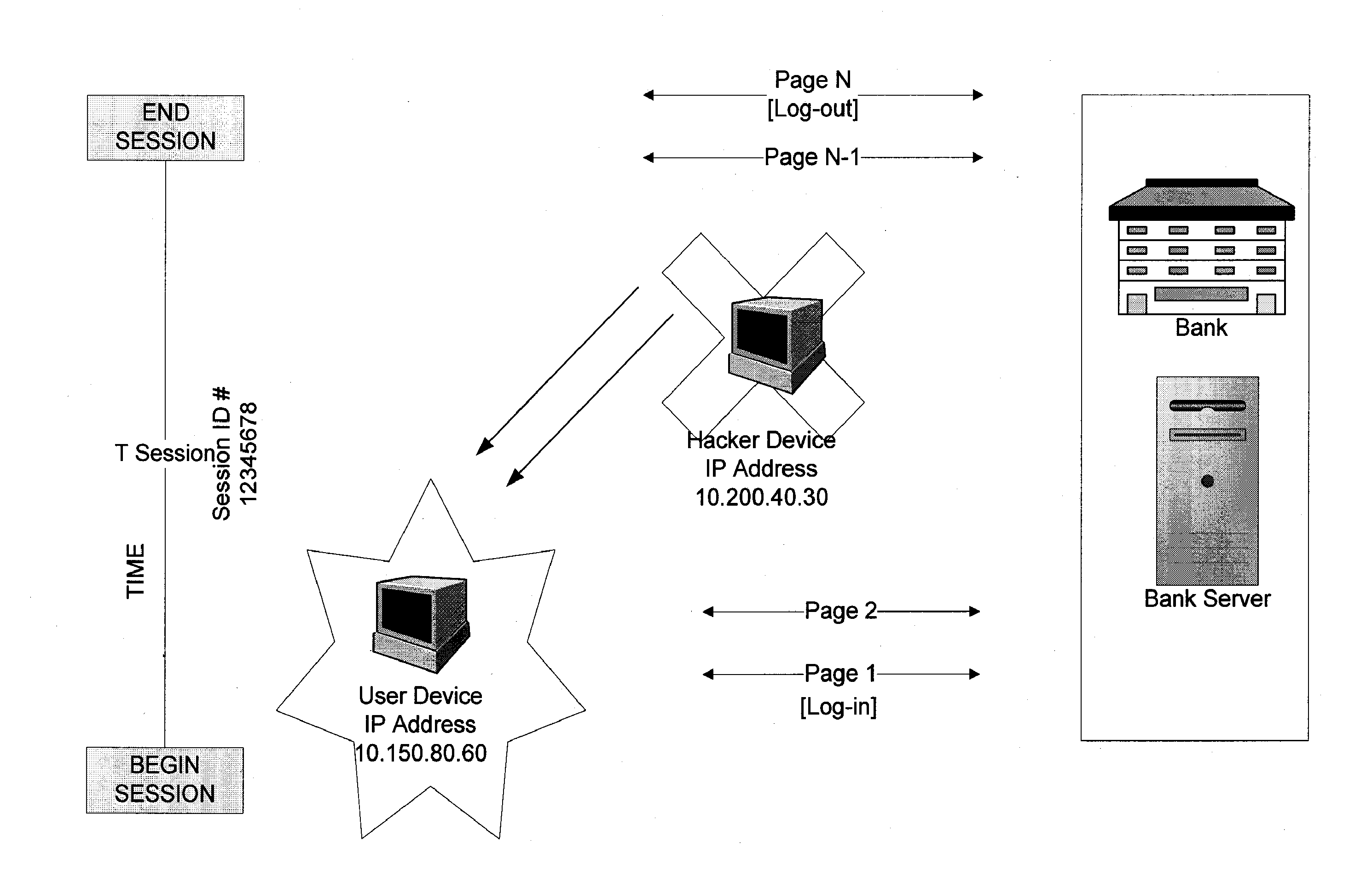
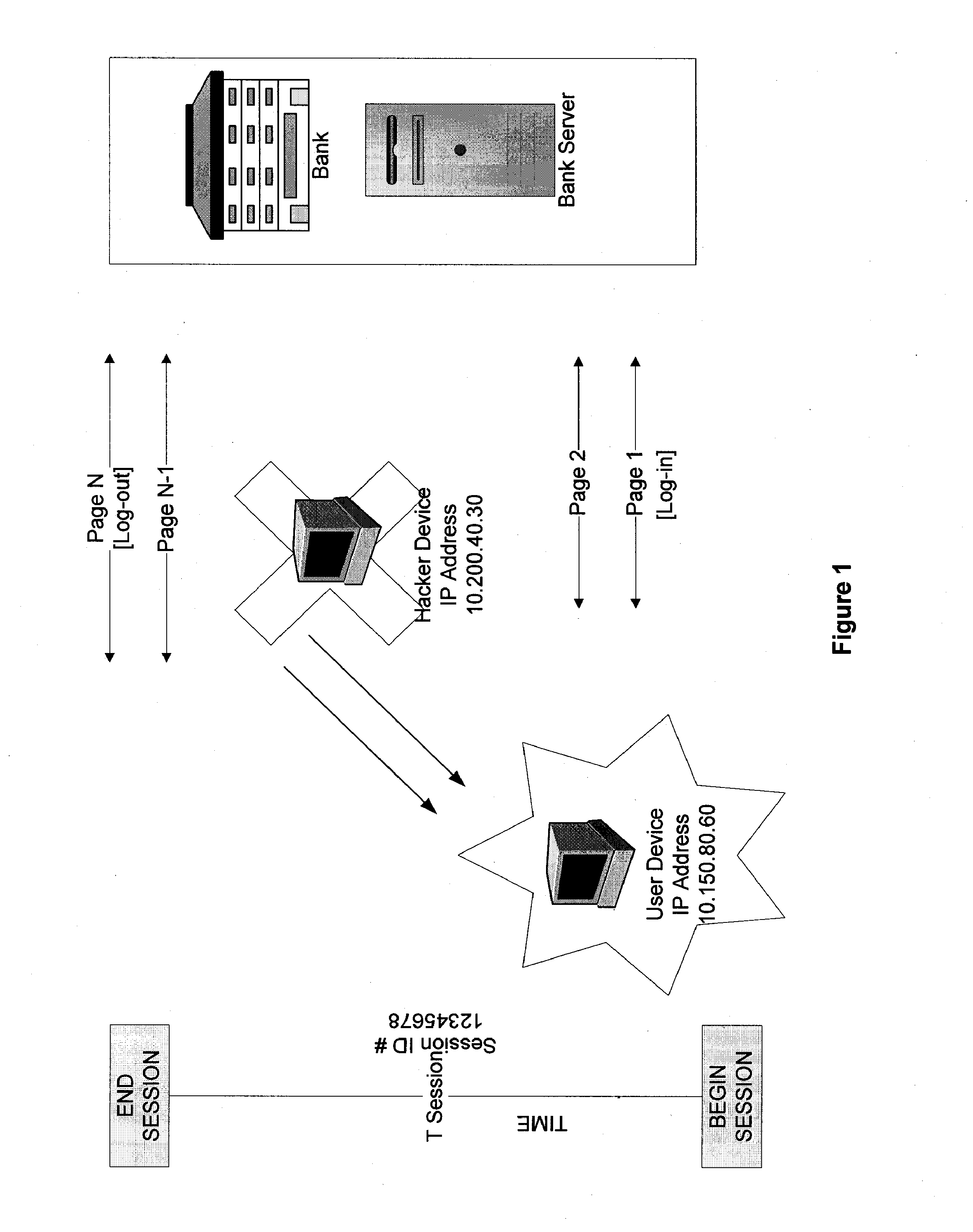
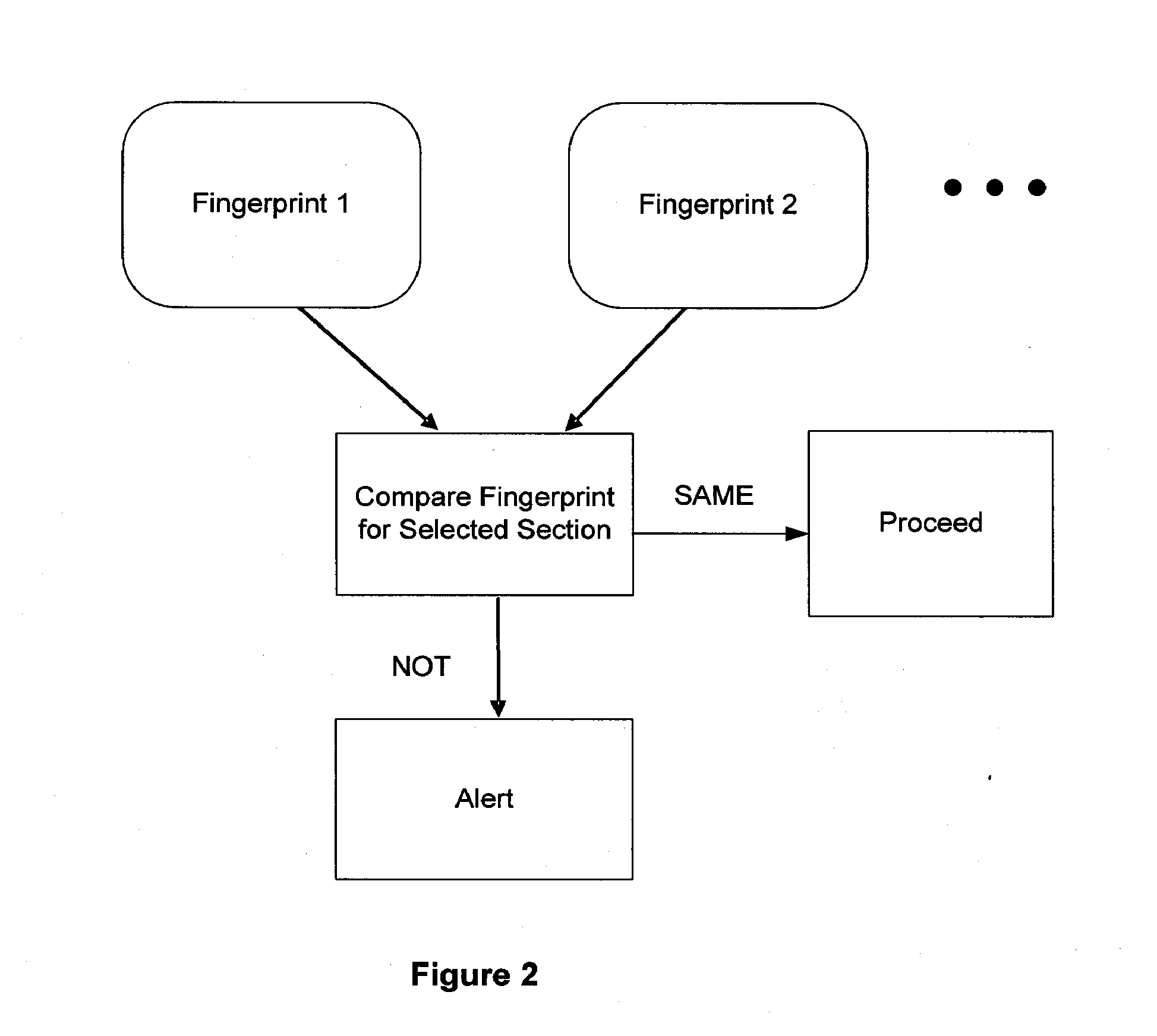
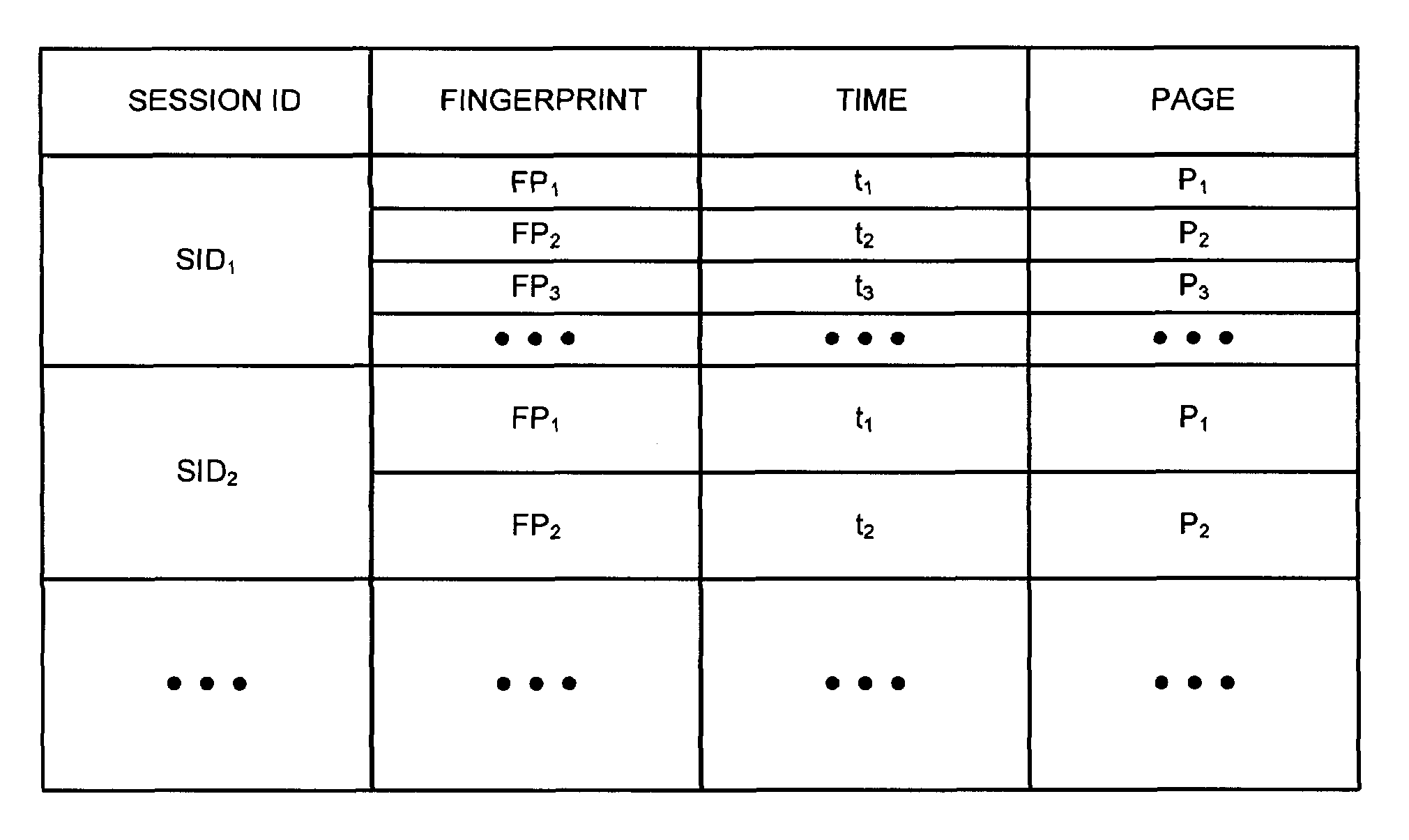
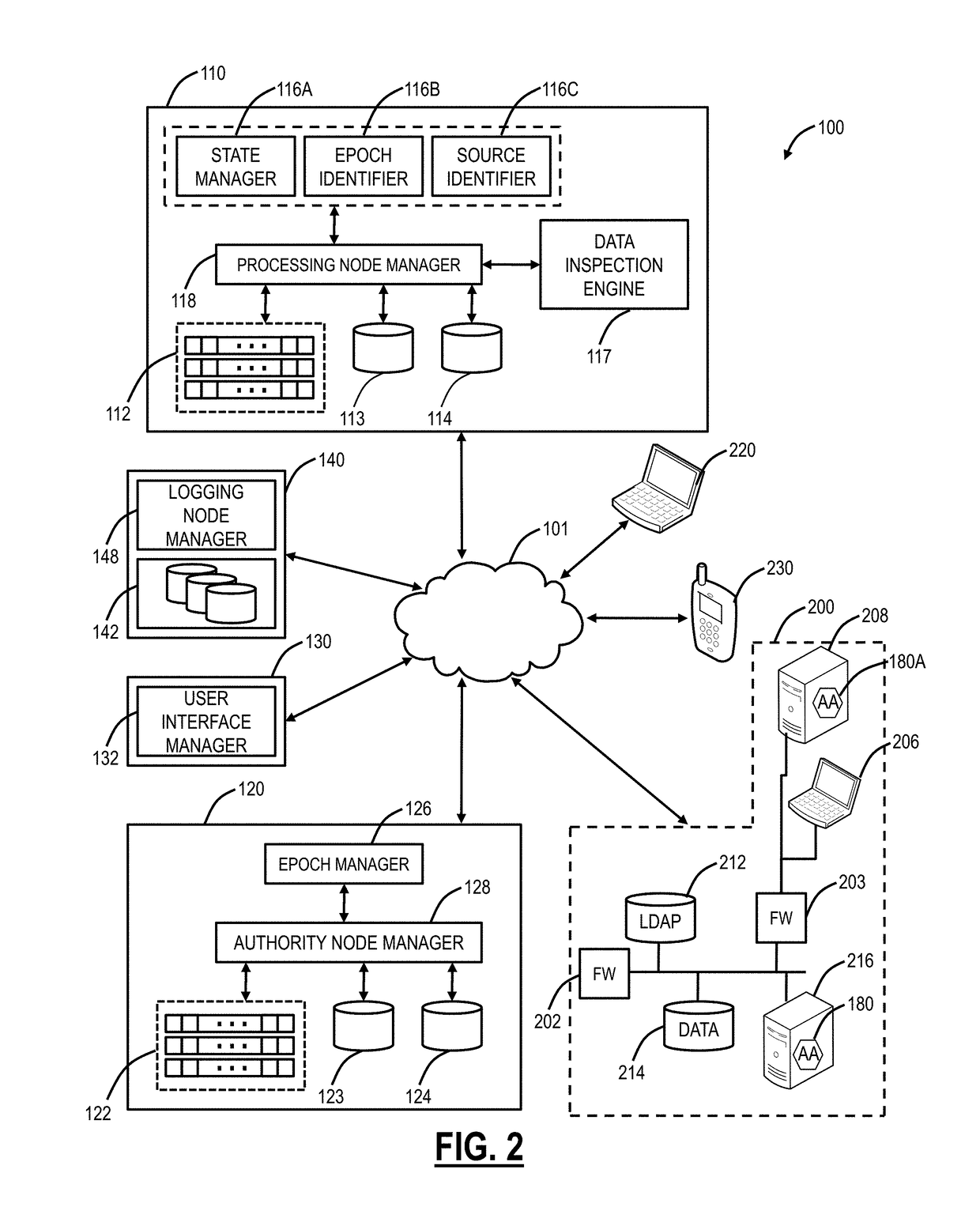
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
Systems and methods for detection of session tampering and fraud prevention
ActiveUS8151327B2Memory loss protectionDigital data processing detailsMan-in-the-middle attackOperating system
The invention provides methods and apparatus for detecting when an online session is compromised. A plurality of device fingerprints may be collected from a user computer that is associated with a designated Session ID. A server may include pages that are delivered to a user for viewing in a browser at which time device fingerprints and Session ID information are collected. By collecting device fingerprints and session information at several locations among the pages delivered by the server throughout an online session, and not only one time or at log-in, a comparison between the fingerprints in association with a Session ID can identify the likelihood of session tampering and man-in-the middle attacks.
Owner:THE 41ST PARAMETER
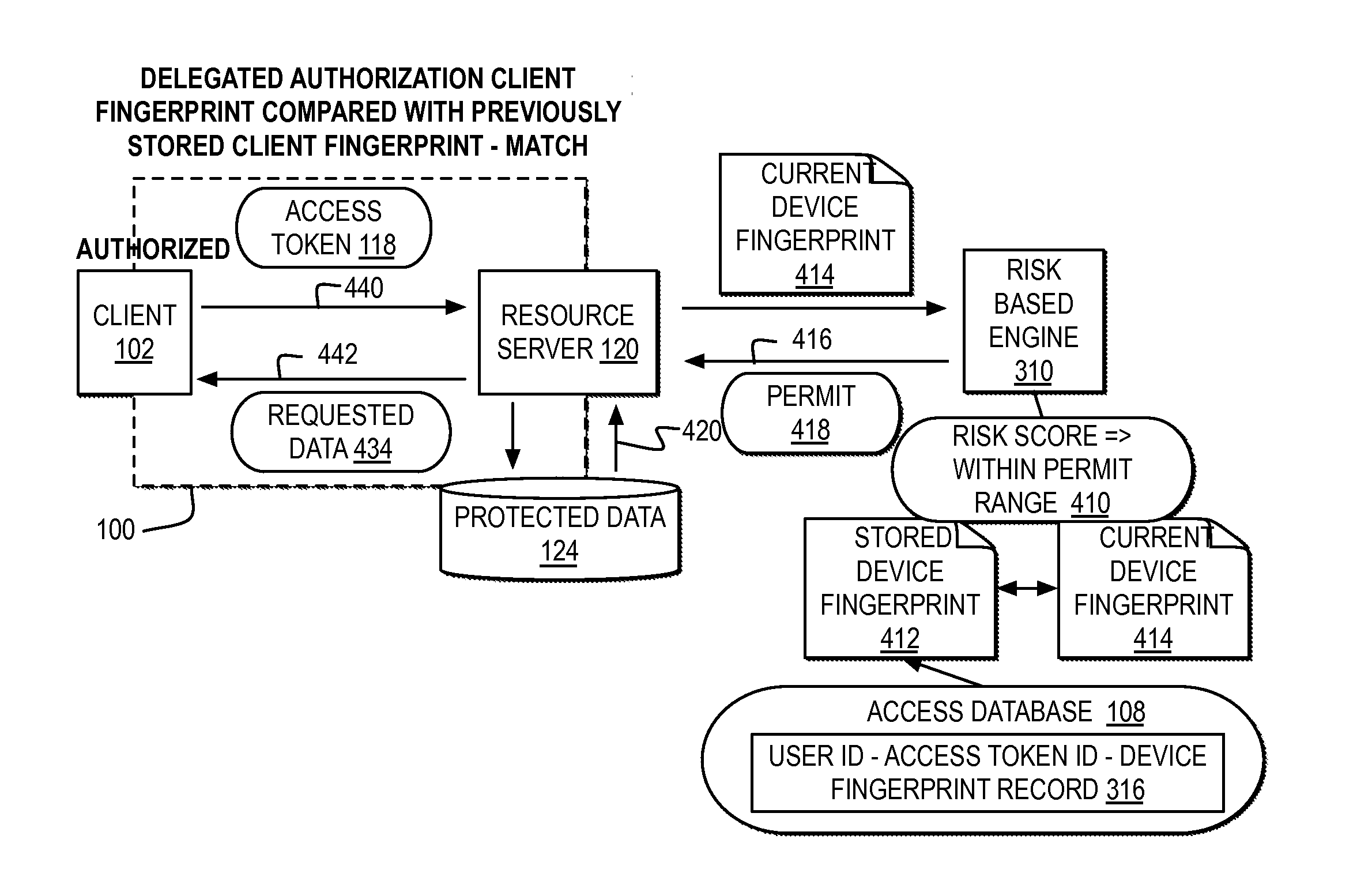
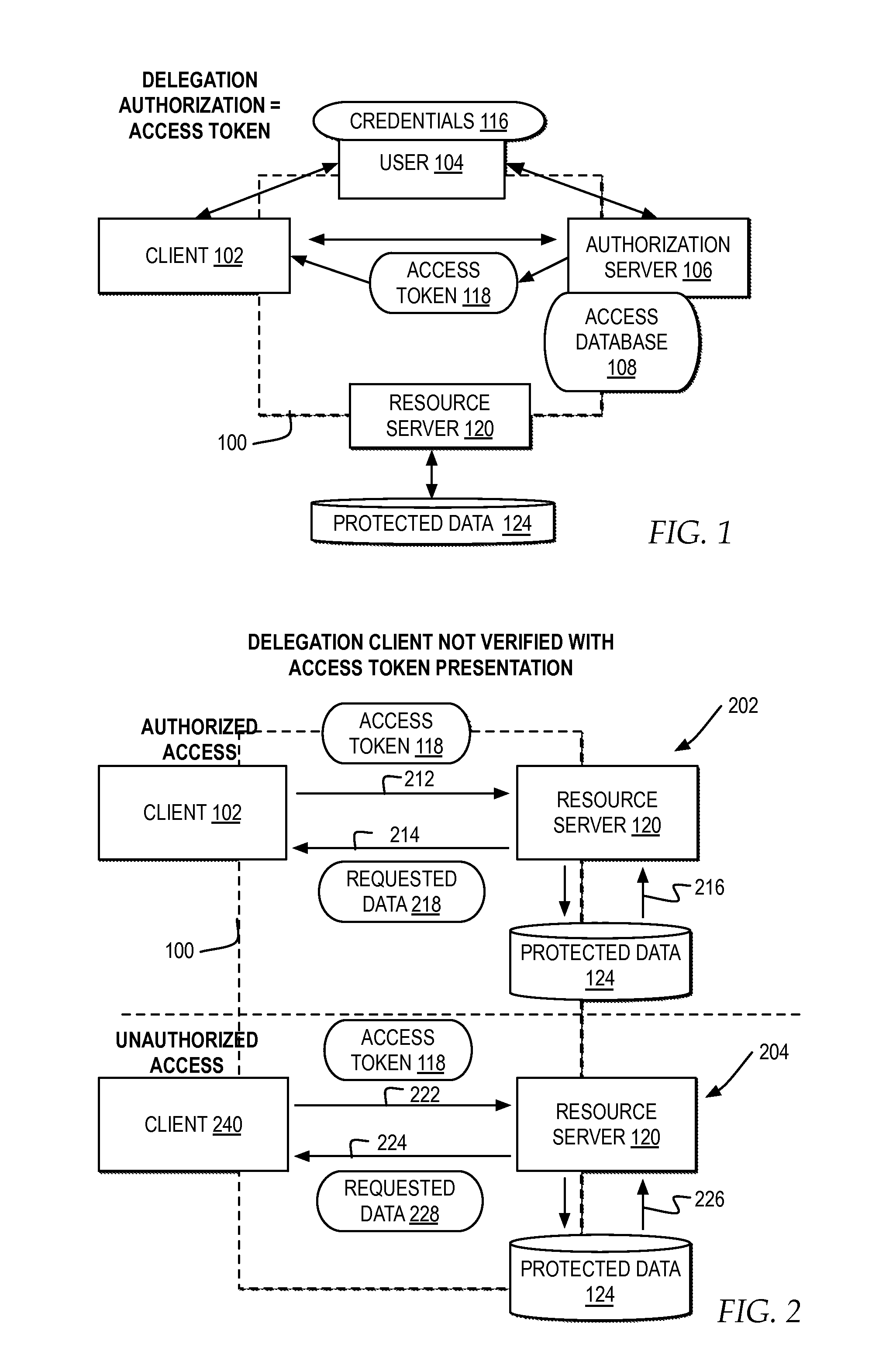
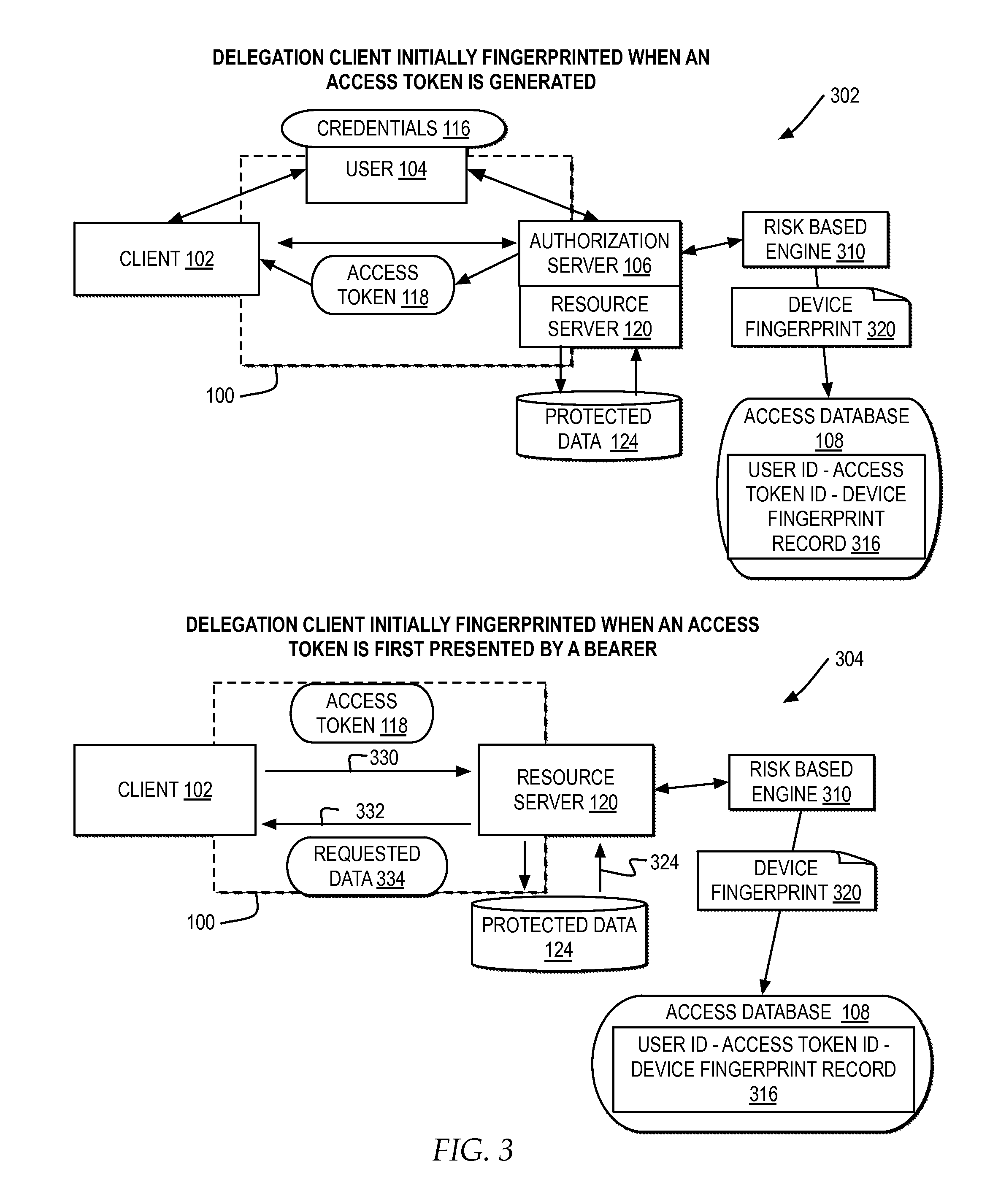
Identifying and destroying potentially misappropriated access tokens
ActiveUS20150150110A1Digital data processing detailsMultiple digital computer combinationsAccess tokenDevice fingerprint
A computer receives a request for protected user data with an access token presented by a client as authorization for the client to access the protected user data in a delegated environment. The computer parses the request to create a device fingerprint identifying the device submitting the request for the client. The computer compares the device fingerprint of the request to a previously stored device fingerprint of an authorized device associated with the access token. The computer automatically determines whether to identify the access token as potentially misappropriated based on the comparison of the device fingerprint of the request to the previously stored device fingerprint.
Owner:IBM CORP
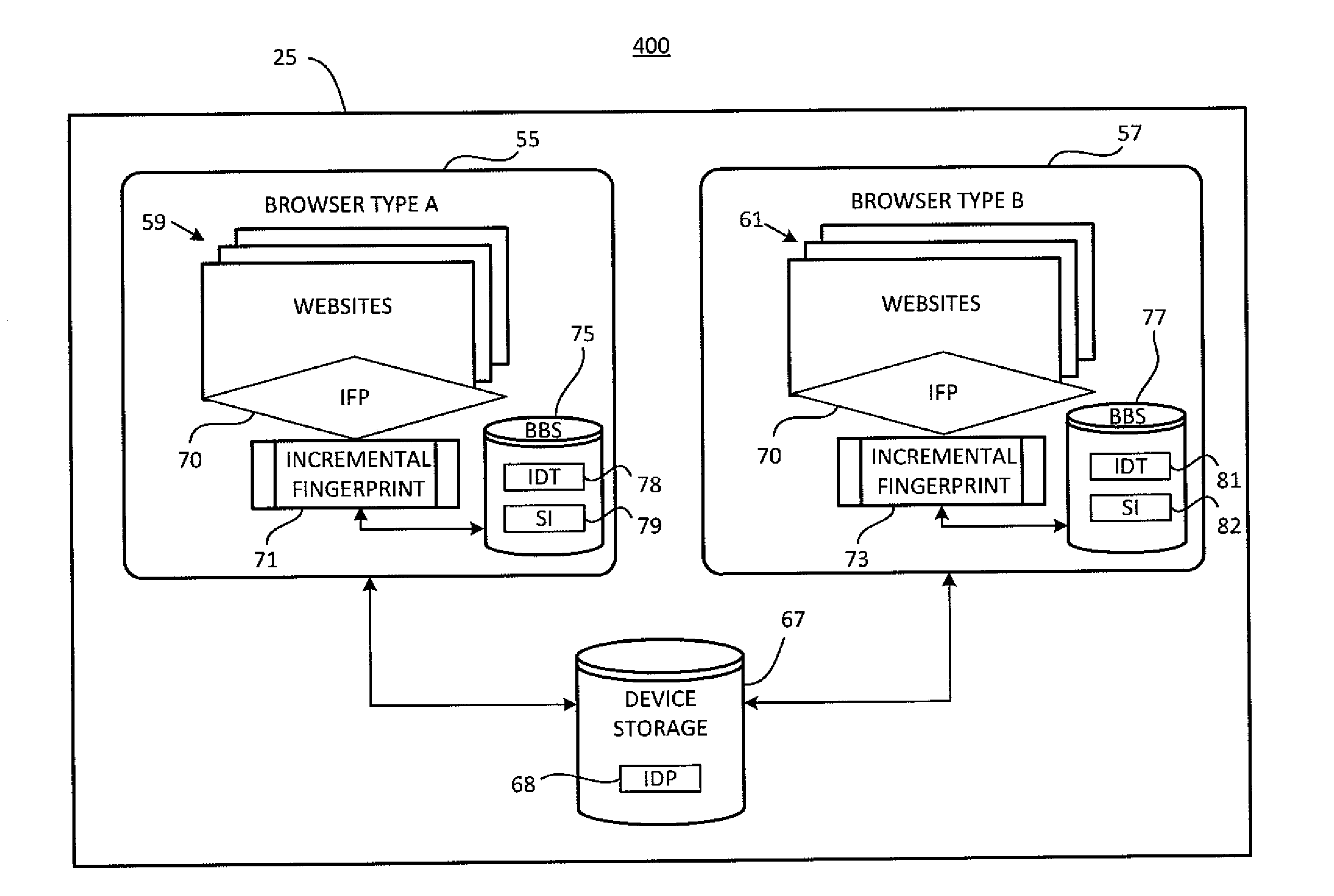
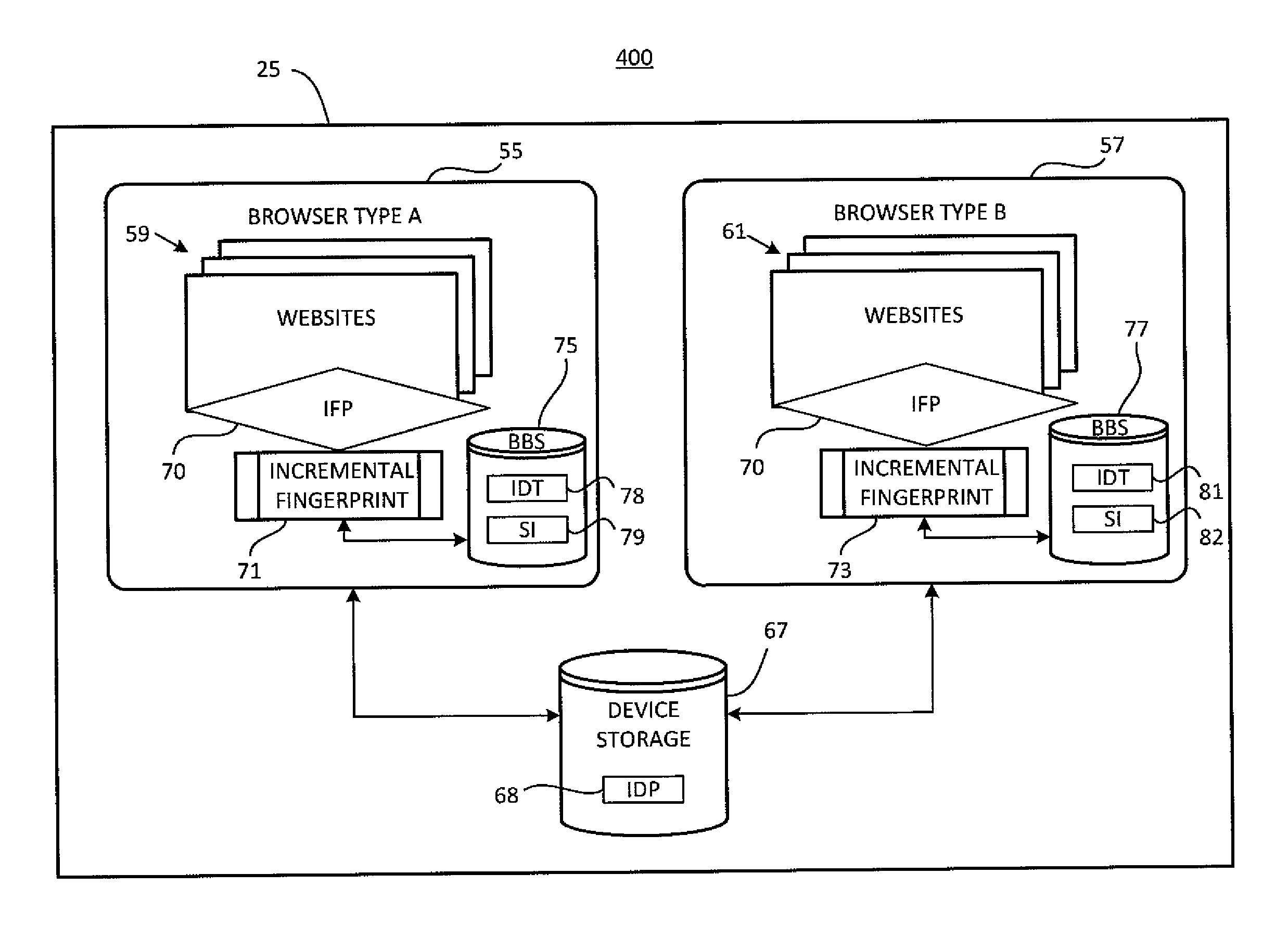
Incremental browser-based device fingerprinting
ActiveUS20120215896A1Digital computer detailsDigital data authenticationWeb browserTheoretical computer science
A method for incrementally fingerprinting a computing device includes steps for executing device-identification code programmed to retrieve a complete set of device configuration metrics from a web browser of the computing device, interrupting execution of the device-identification code after retrieval of a first subset of the device configuration metrics, generating a partial device fingerprint from the first subset, generating a temporary device identifier from the partial device fingerprint, and generating a subset indicator identifying the device configuration metrics that compose the first subset. Additional steps include writing the temporary device identifier and the subset indicator to browser-based storage of the computing device, resuming execution of the device-identification code, querying the browser-based storage for presence of the temporary device identifier, and retrieving, responsive to detecting the temporary device identifier, a second subset of the device configuration metrics, the second subset comprising device configuration metrics not identified by the subset indicator.
Owner:ADSTRA INC
Attack detection and prevention using global device fingerprinting
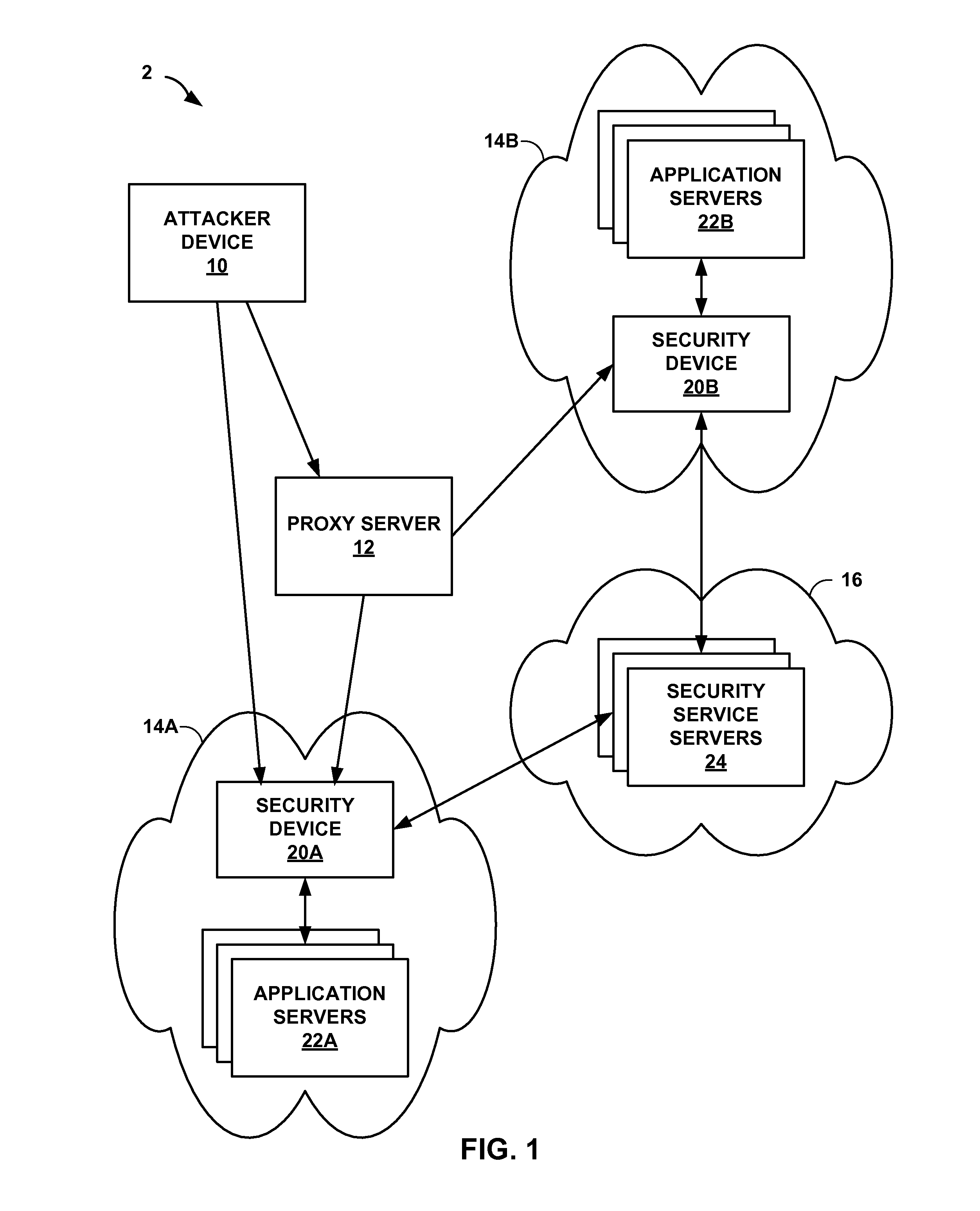
ActiveUS20140283061A1Spread quicklyReduce attackMemory loss protectionError detection/correctionTraffic capacityComputer module
This disclosure describes a global attacker database that utilizes device fingerprinting to uniquely identify devices. For example, a device includes one or more processors and network interface cards to receive network traffic directed to one or more computing devices protected by the device, send, to the remote device, a request for data points of the remote device, wherein the data points include characteristics associated with the remote device, and receive at least a portion of the requested data points. The device also includes a fingerprint module to compare the received portion of the data points to sets of data points associated with known attacker devices, and determine, based on the comparison, whether a first set of data points of a first known attacker device satisfies a similarity threshold. The device also includes an security module to selectively manage, based on the determination, additional network traffic directed to the computing devices.
Owner:JUMIPER NETWORKS INC
Psychographic device fingerprinting
ActiveUS20120072546A1Broadcast components for monitoring/identification/recognitionComputer security arrangementsMagnetocardiography deviceComputer science
A system for generating a psychographic device fingerprint includes a server in communication with a network and memory storing a program which, when executed by the server, performs steps for (a) detecting reception at a computing device of media content delivered via the network, (b) reading device elements stored on the computing device, (c) reading a geographic indicator from the computing device, (d) reading a content indicator identifying the media content, (e) determining a timing parameter associated with reception of the content at the computing device, and (f) deriving from the device type, the geographic indicator, the content indicator, and the timing parameter, the psychographic device fingerprint as computer readable code uniquely identifying a user of the computing device. The steps may further include recording media content received by multiple computing devices, and generating a viewership report relating computing devices and psychographic device fingerprints to the media content received.
Owner:UNILOC 2017 LLC
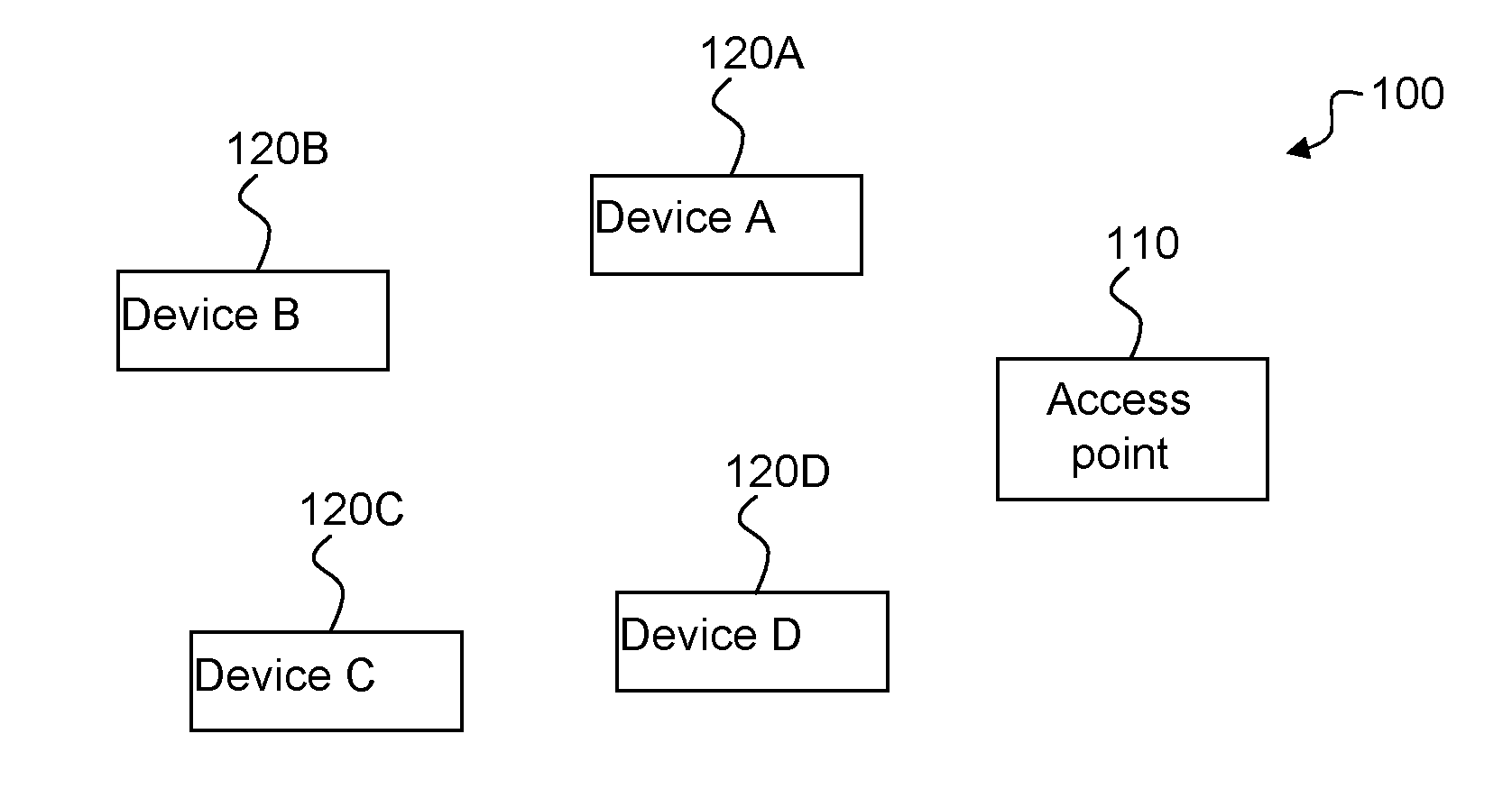
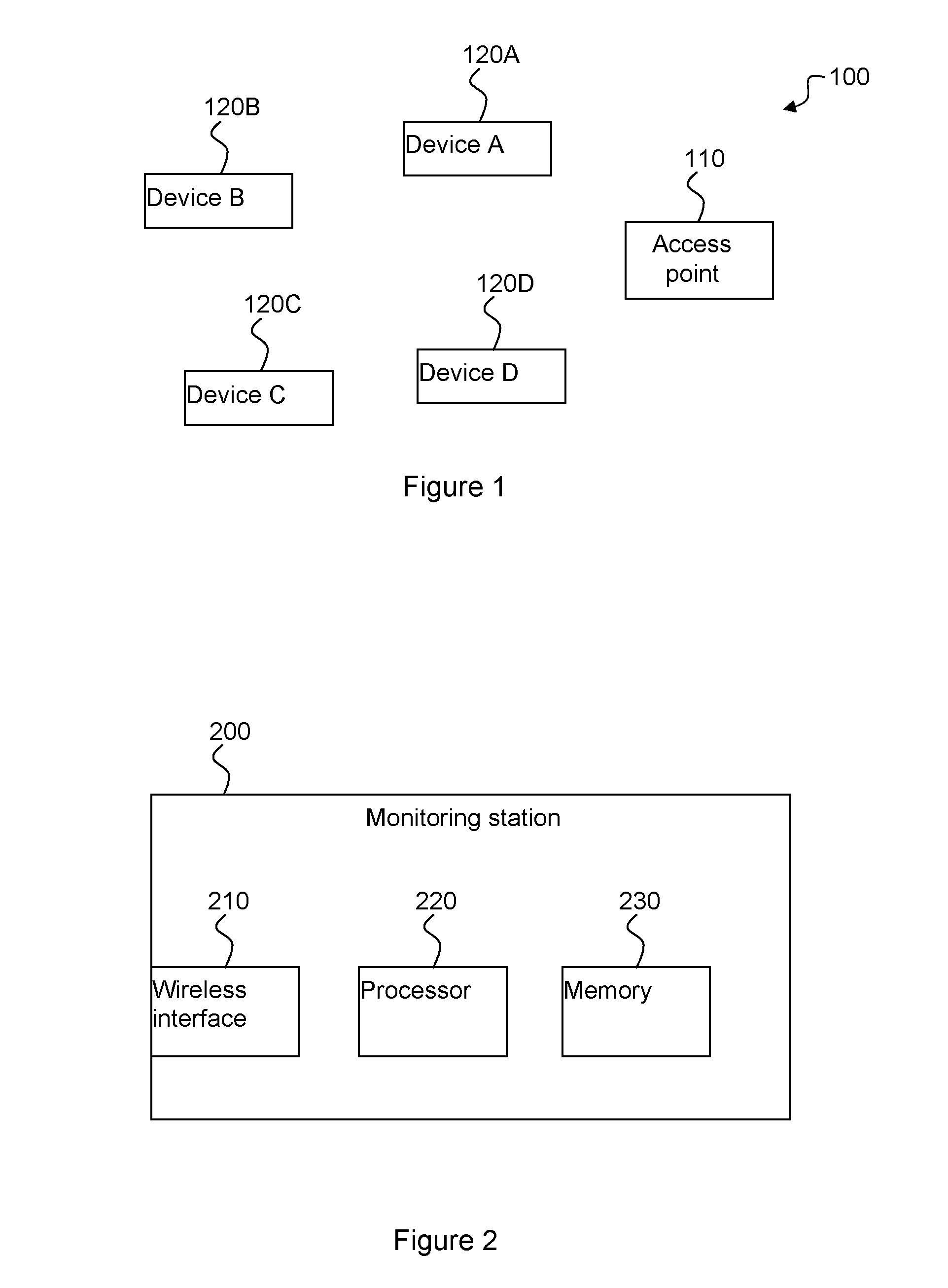
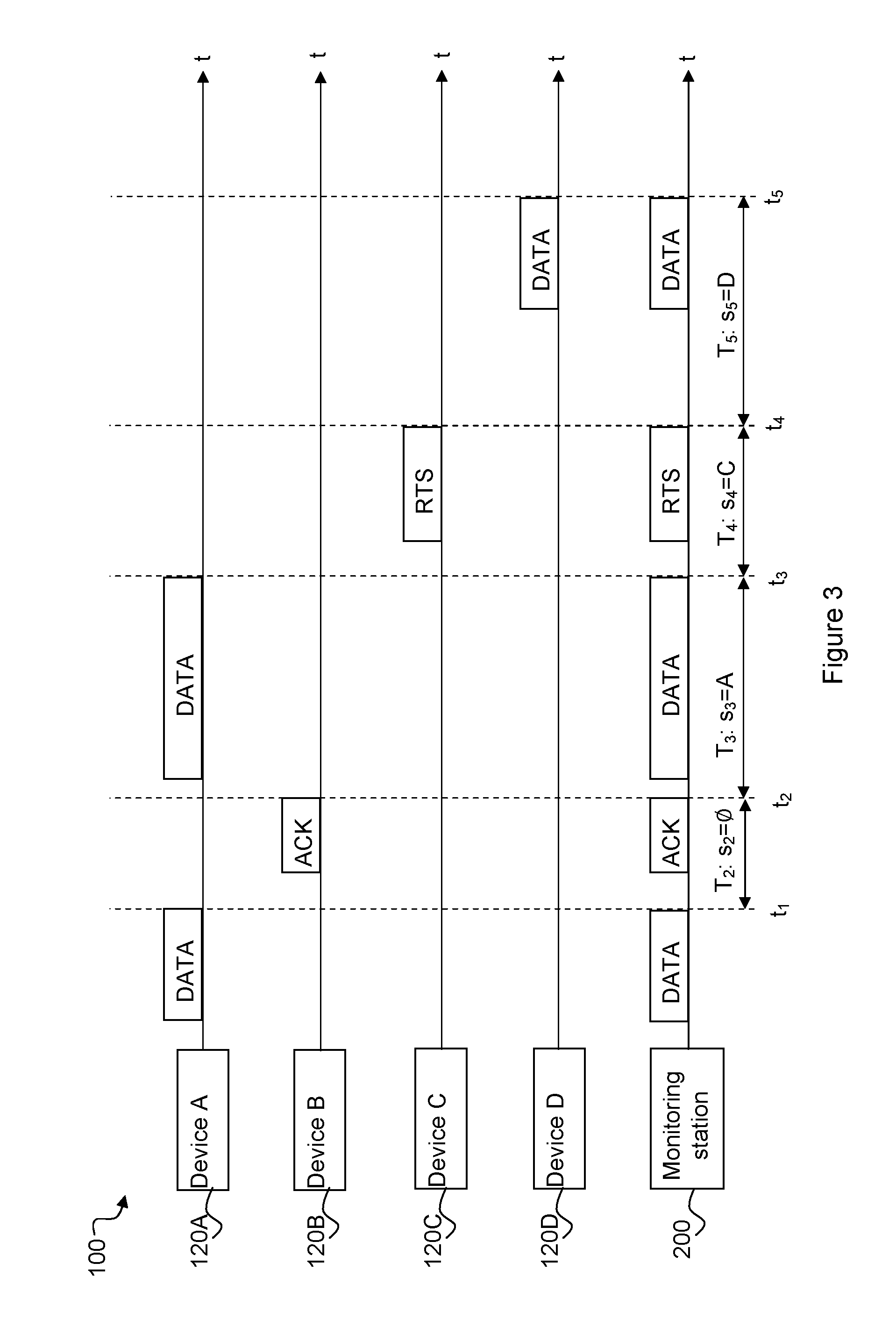
Method and device for fingerprinting of wireless communication devices
ActiveUS20130242795A1Error preventionFrequency-division multiplex detailsArrival timeComputer science
A method for fingerprinting wireless devices and a method for using a device fingerprint for identifying wireless devices. A monitoring station listens to a channel. For each received frame, the station measures the inter-arrival time from the end of the previously received frame to the end of the present frame, if possible, the station obtains the identity of the sender of the frame. If the sender is known, then the station stores the inter-arrival time in a histogram for the sender; the histogram becomes the fingerprint for the sender. Identification of a device begins by obtaining a number of inter-arrival times for an unknown sender and then matching these to stored fingerprints using a suitable similarity measure. The invention is particularly suitable for IEEE 802.11 and may for example be used to detect so-called MAC spoofing and as an additional layer of an identification protocol.
Owner:INTERDIGITAL CE PATENT HLDG
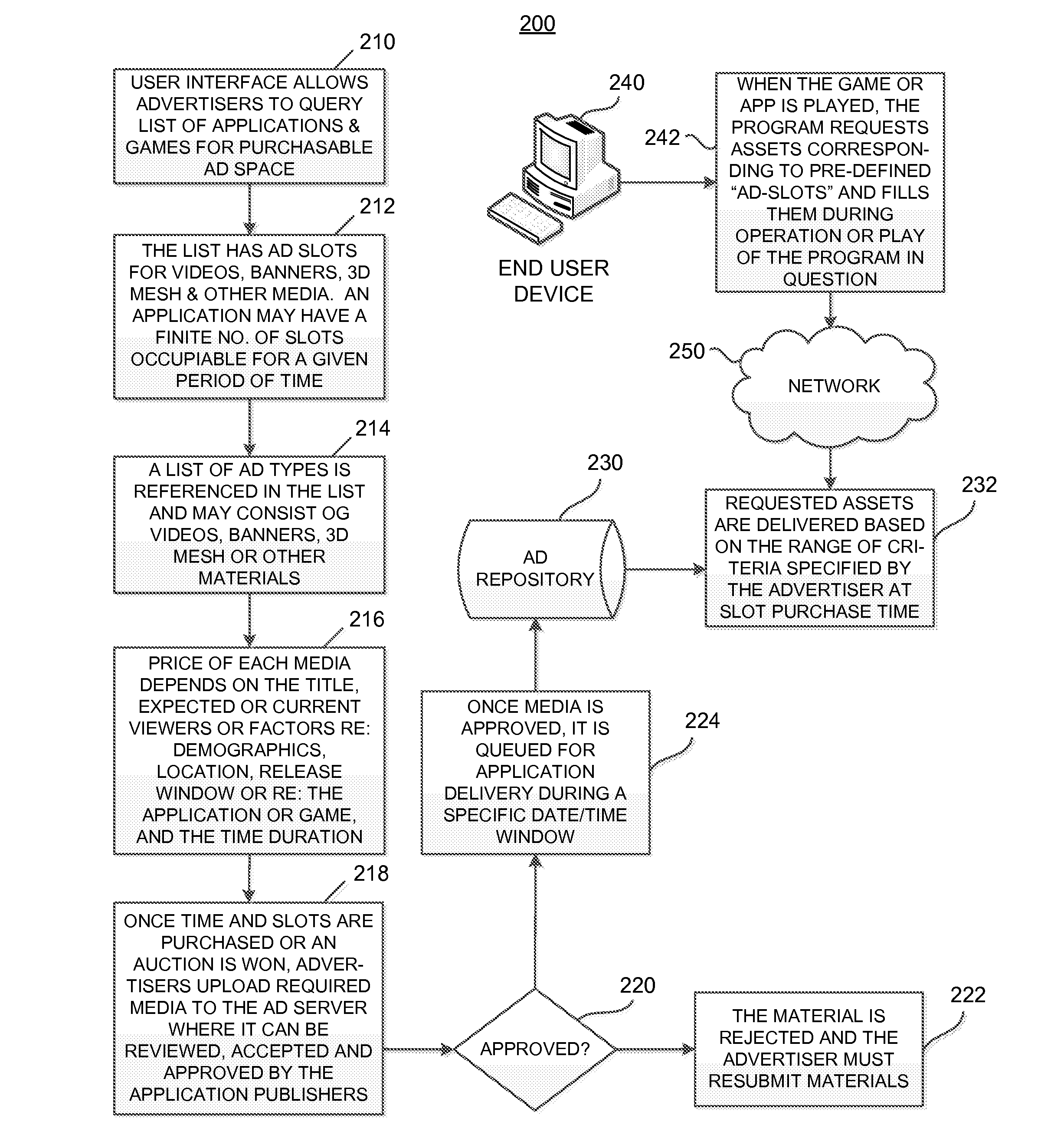
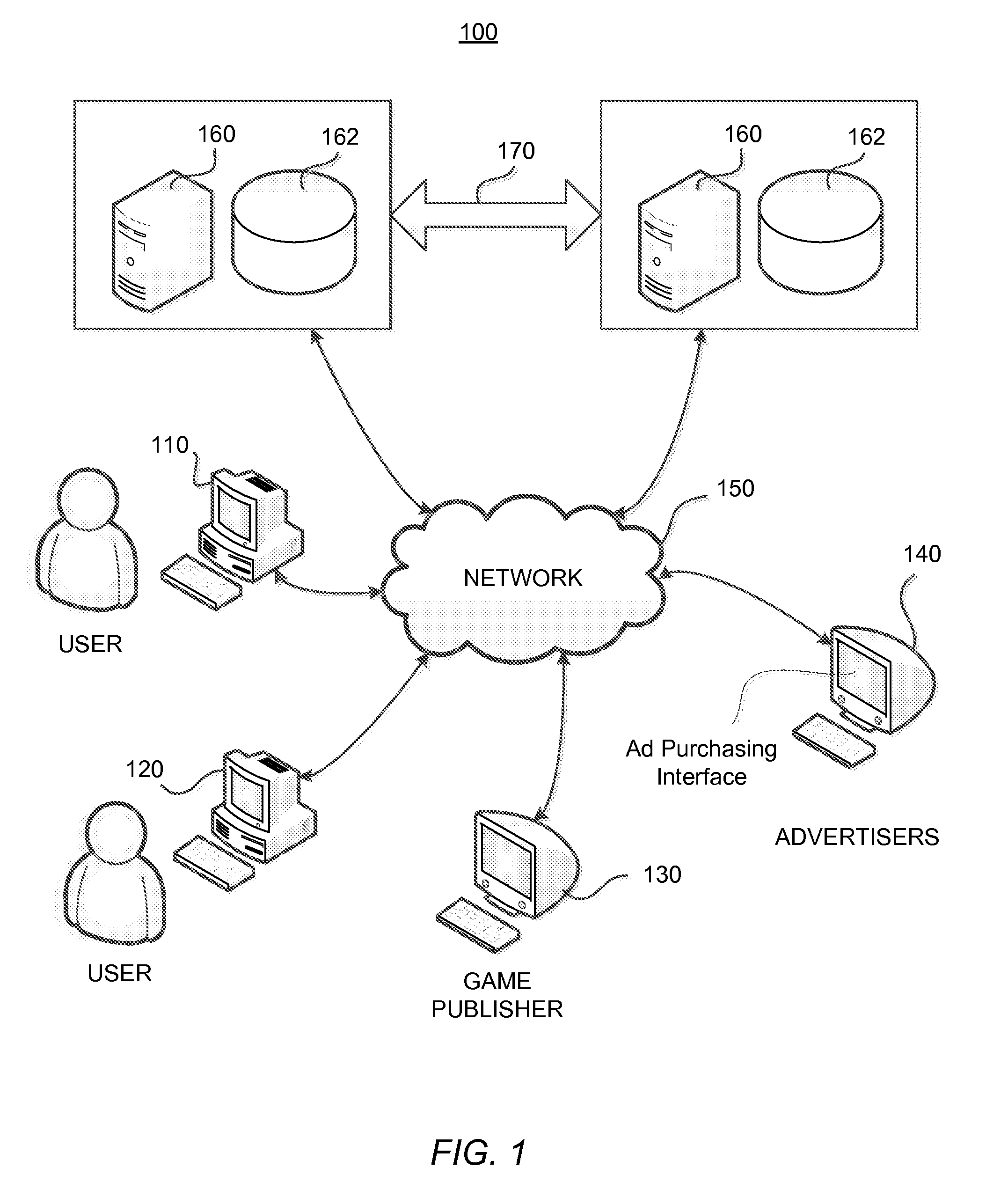
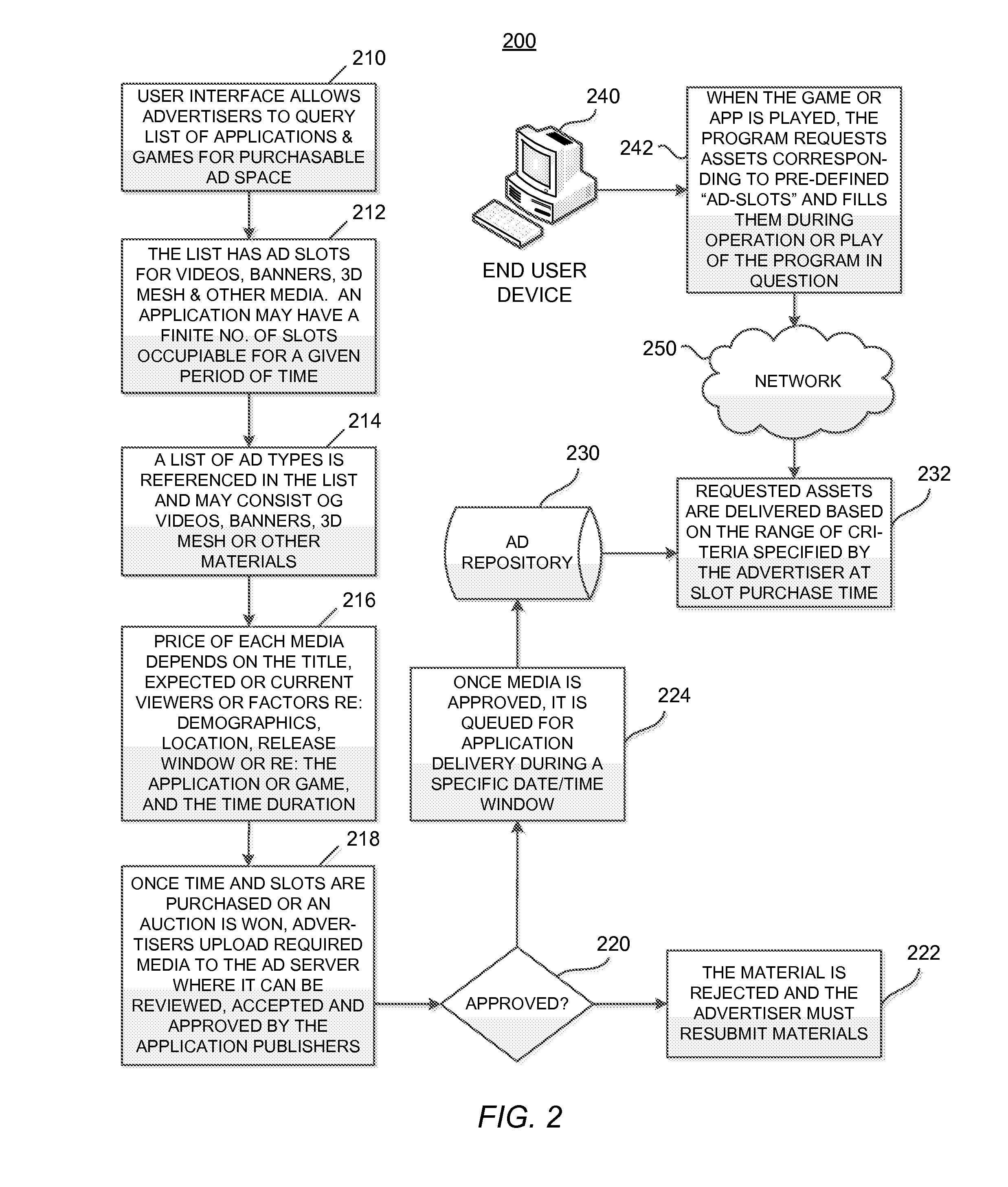
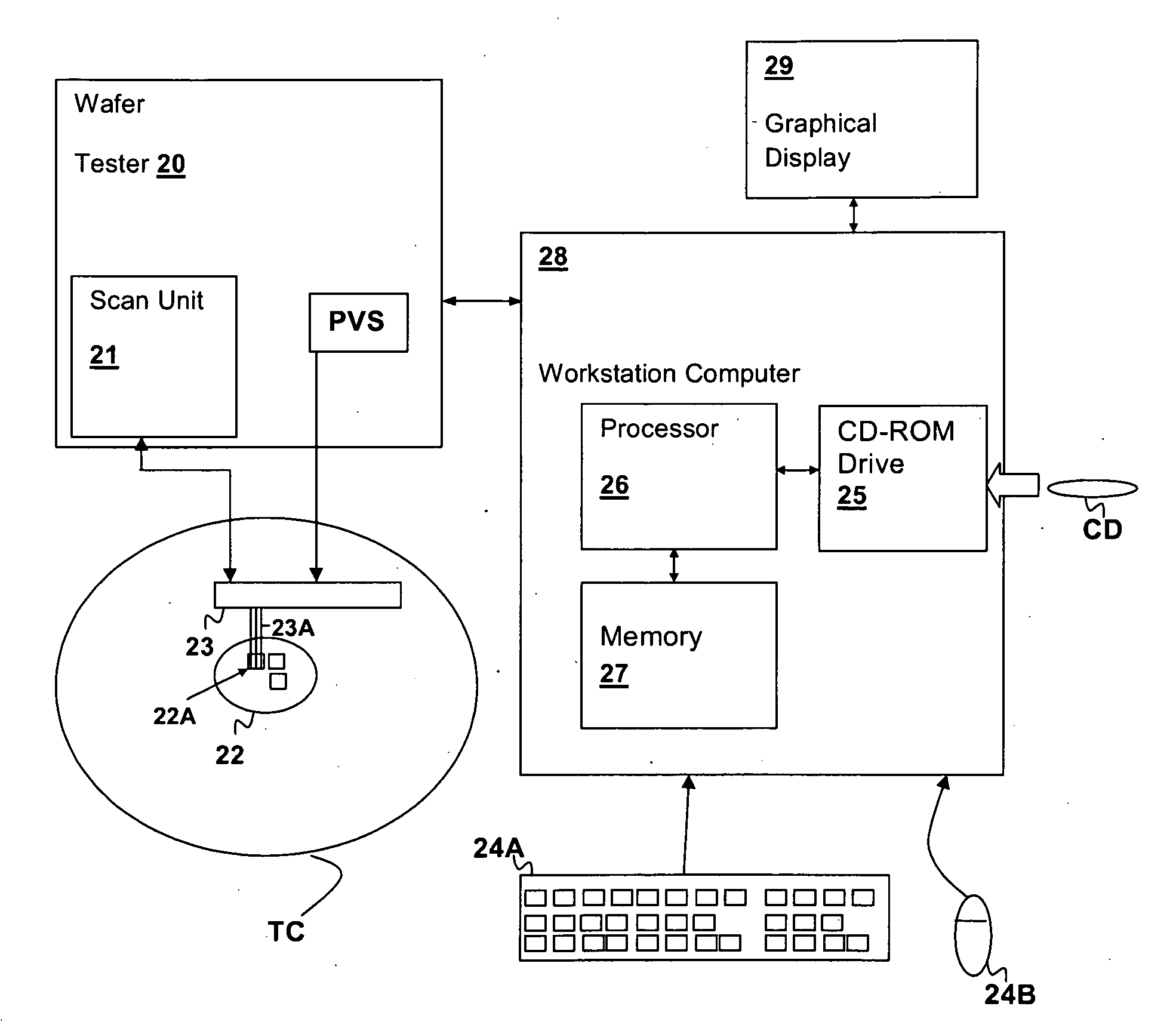
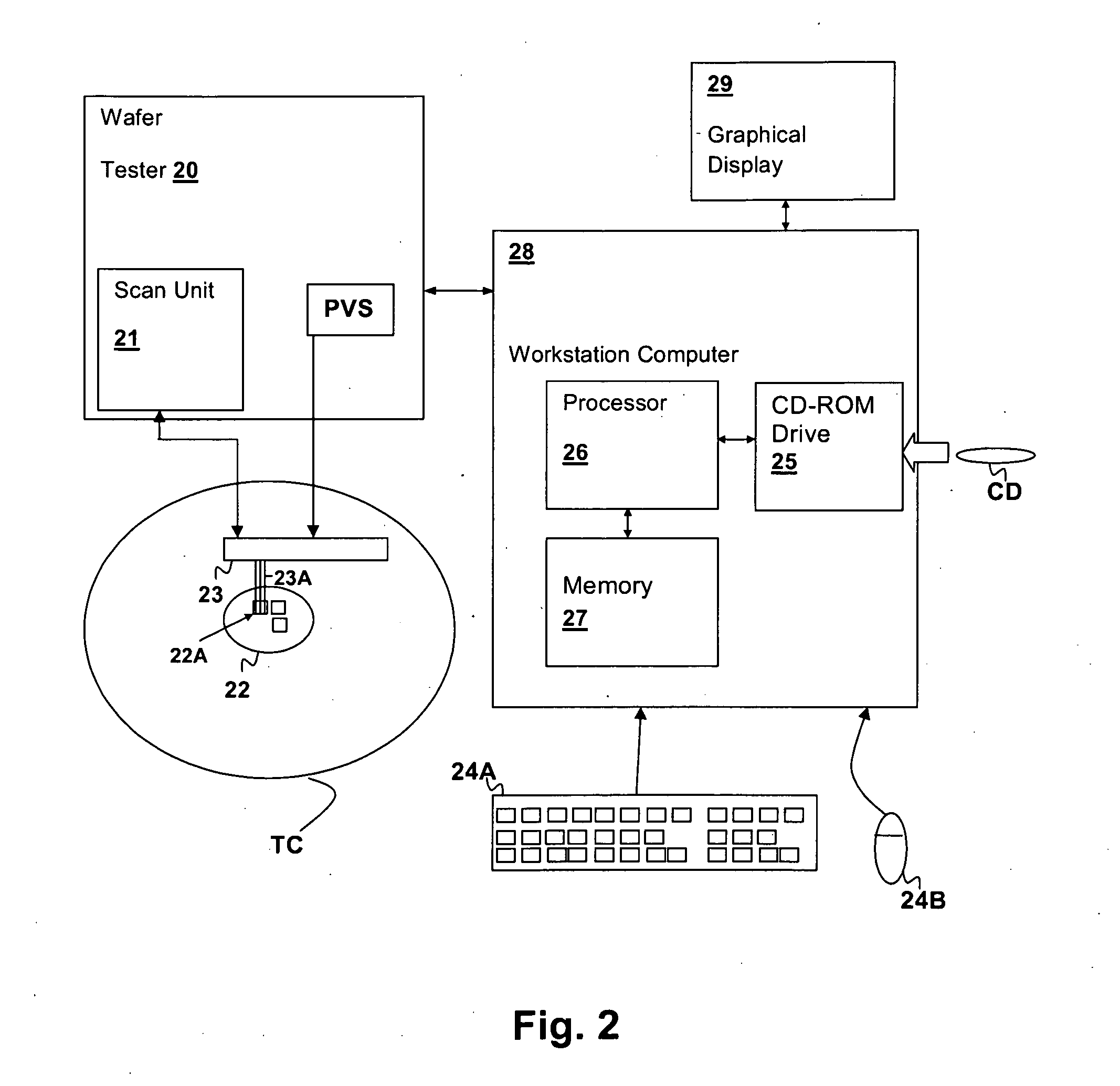
Systems and Methods for Providing an Interface for Purchasing Ad Slots in an Executable Program
A system for providing an interface for purchasing ad slots in an executable program operable at a plurality of clients. The system comprises a network interface disposed to receive data associated with an ad slot in the executable program and information associated with the plurality of clients operating the executable program, the plurality of clients each identified by a device fingerprint. The system also comprises a memory holding program instructions operable for determining a price for the ad slot based at least on the data and information associated with the plurality of clients and providing an interface for purchasing the ad slots. The interface identifies at least the executable program, the ad slot and the determined price.
Owner:UNILOC LUXEMBOURG
Incremental browser-based device fingerprinting
ActiveUS8601109B2Multiple digital computer combinationsDigital data authenticationWeb browserTheoretical computer science
A method for incrementally fingerprinting a computing device includes steps for executing device-identification code programmed to retrieve a complete set of device configuration metrics from a web browser of the computing device, interrupting execution of the device-identification code after retrieval of a first subset of the device configuration metrics, generating a partial device fingerprint from the first subset, generating a temporary device identifier from the partial device fingerprint, and generating a subset indicator identifying the device configuration metrics that compose the first subset. Additional steps include writing the temporary device identifier and the subset indicator to browser-based storage of the computing device, resuming execution of the device-identification code, querying the browser-based storage for presence of the temporary device identifier, and retrieving, responsive to detecting the temporary device identifier, a second subset of the device configuration metrics, the second subset comprising device configuration metrics not identified by the subset indicator.
Owner:ADSTRA INC
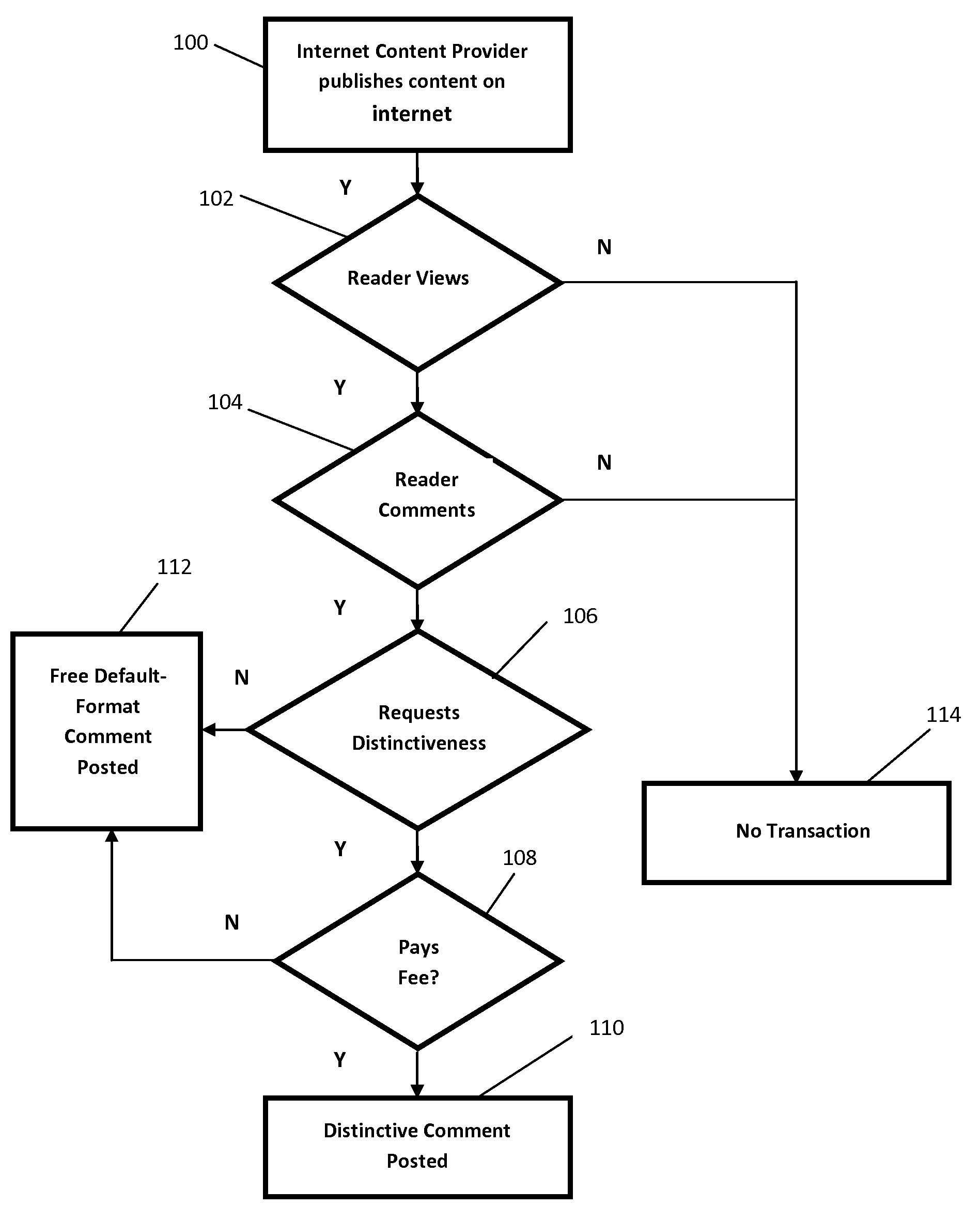
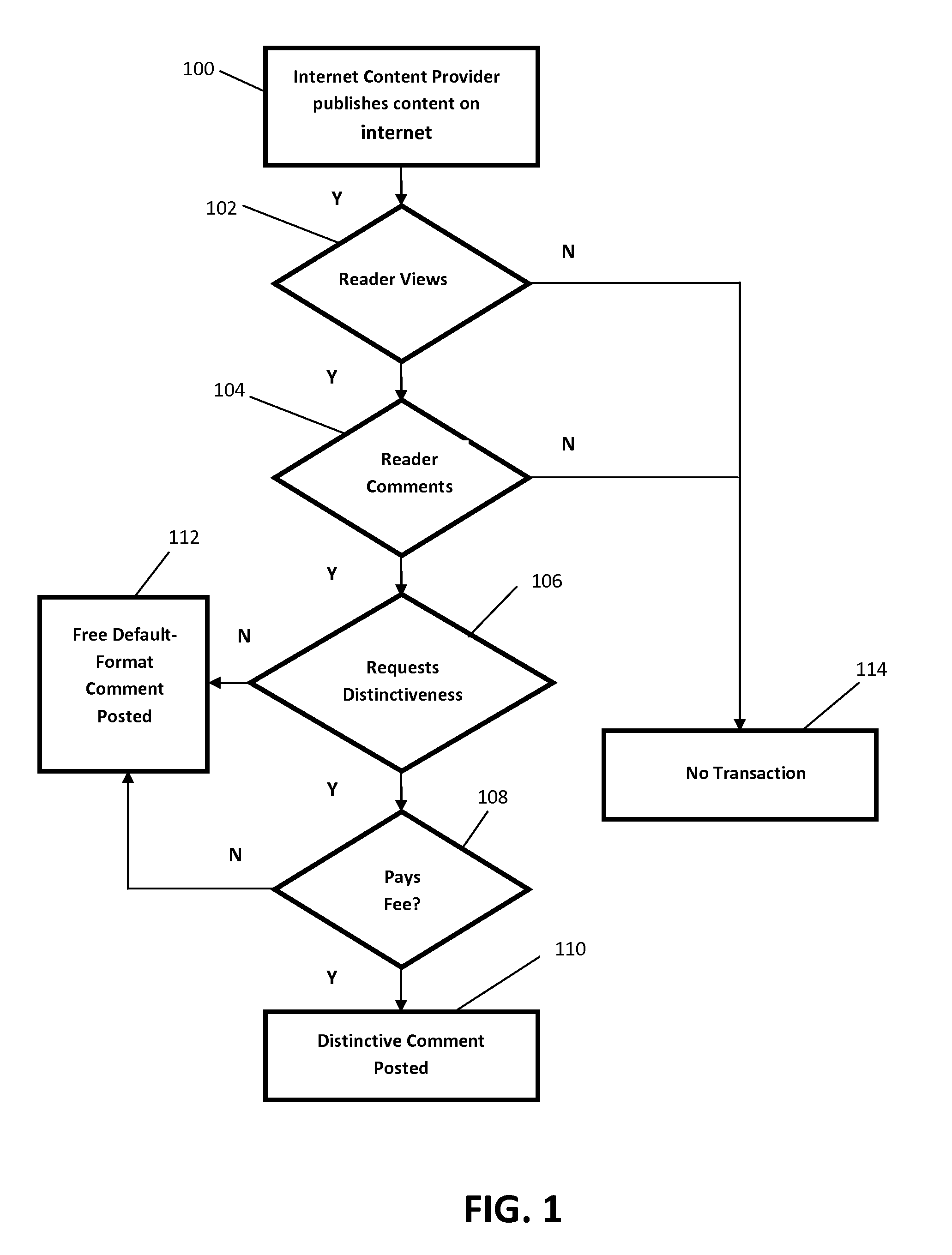
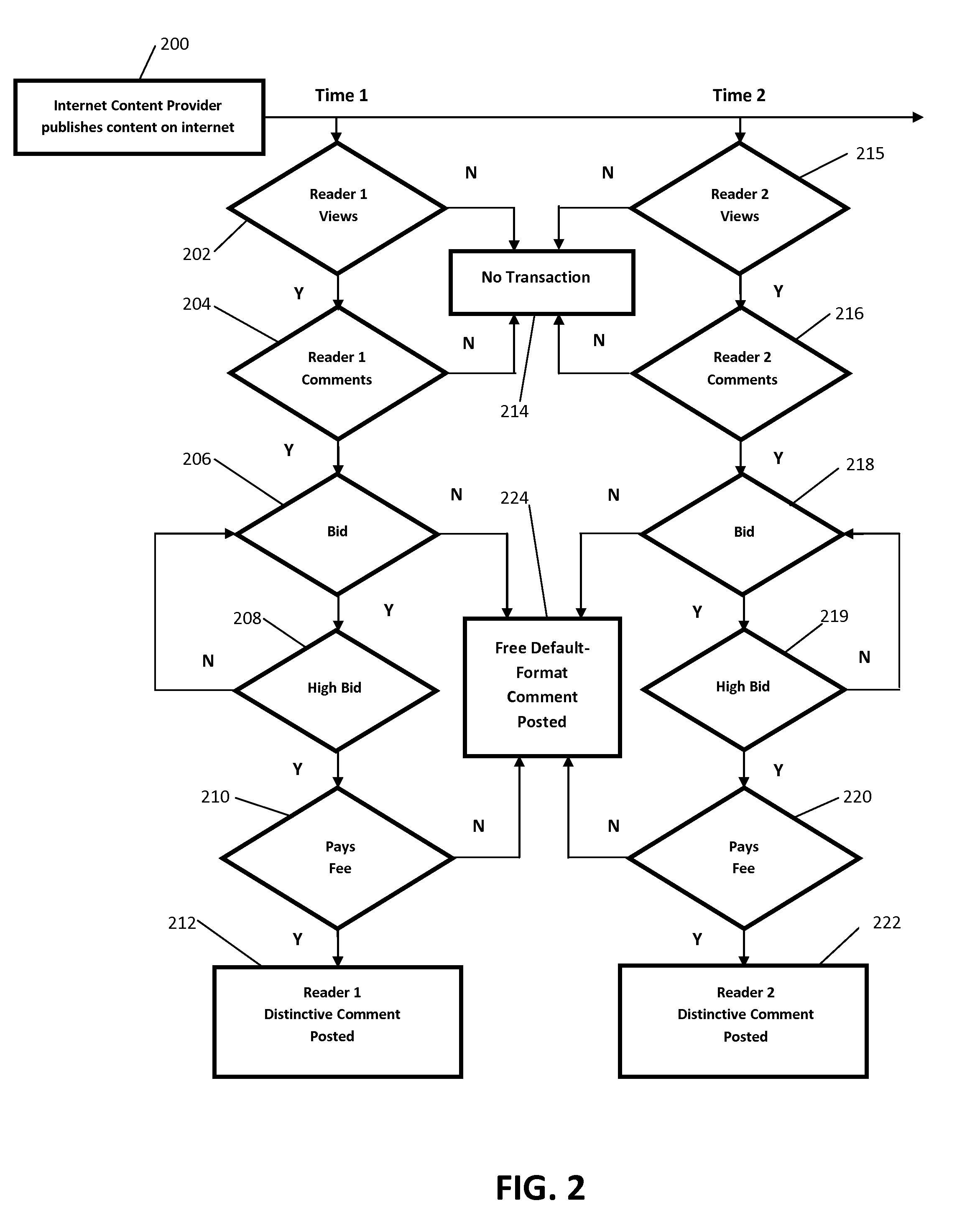
Universal one-click online payment method and system
A computer system for facilitating an online purchase and sale transaction. The computer system includes computing devices and executable instructions associated with each of an internet content provider, a client system, and a third party administrator. The client system comprises a device fingerprint identifiable by the third party administrator, wherein the third party administrator computer system administers the purchase and sale transaction based on receiving account and payment account information associated with the internet content provider and the client system, respectively. The third party administrator authorizes payment upon a request received from the client system for which it identifies the device fingerprint.
Owner:IP3 2021 SERIES 600 OF ALLIED SECURITY TRUST I
Multidimensional risk profiling for network access control of mobile devices through a cloud based security system
Systems and methods implemented in a cloud node in a cloud based security system for network access control of a mobile device based on multidimensional risk profiling thereof include receiving posture data from the mobile device; determining a device fingerprint and a risk index of the mobile device based on the posture data; and, responsive to a request by the mobile device for network resources through the cloud based security system, performing a multidimensional risk analysis based on the device fingerprint and the risk index and allowing or denying the request based on the multidimensional risk analysis.
Owner:ZSCALER INC
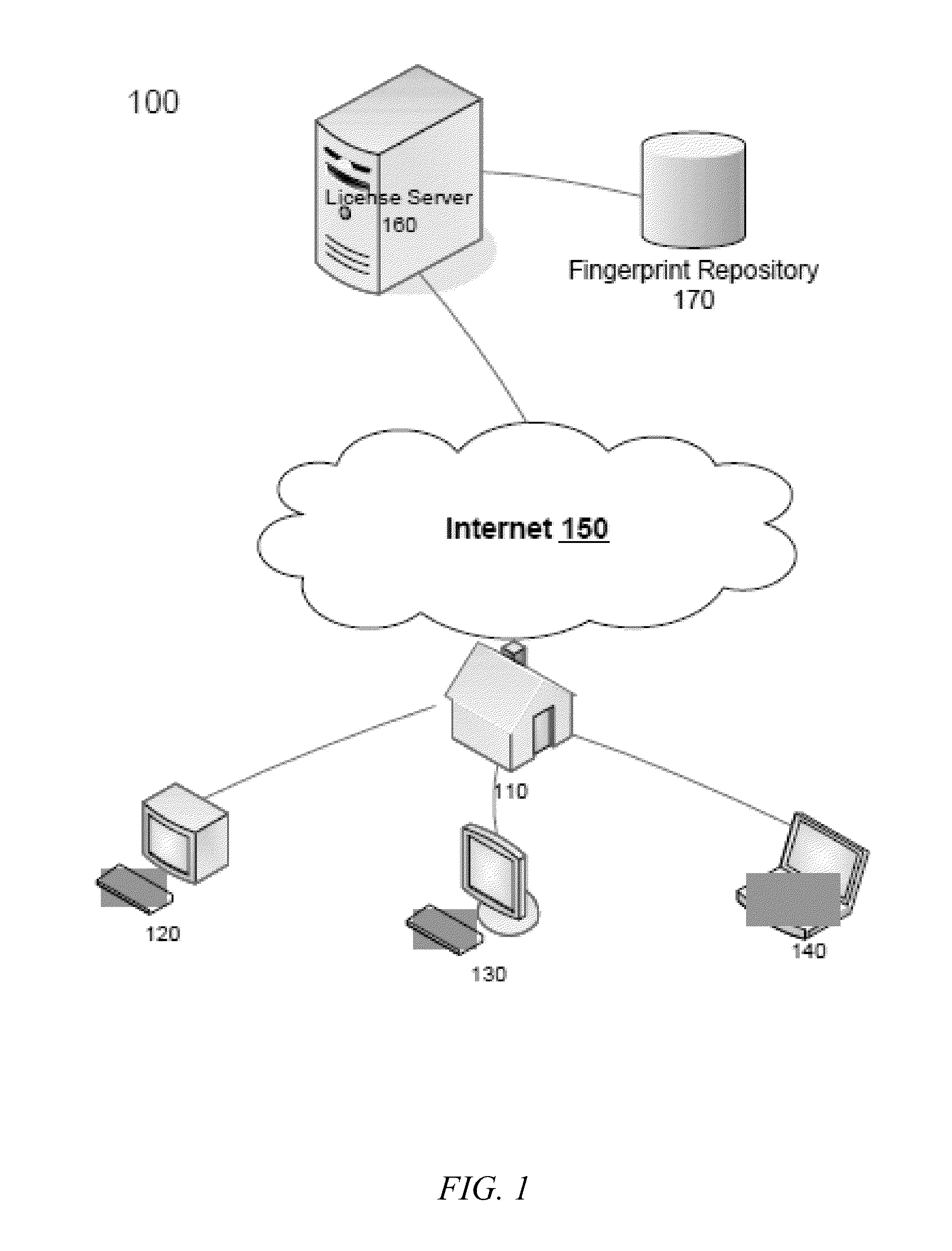
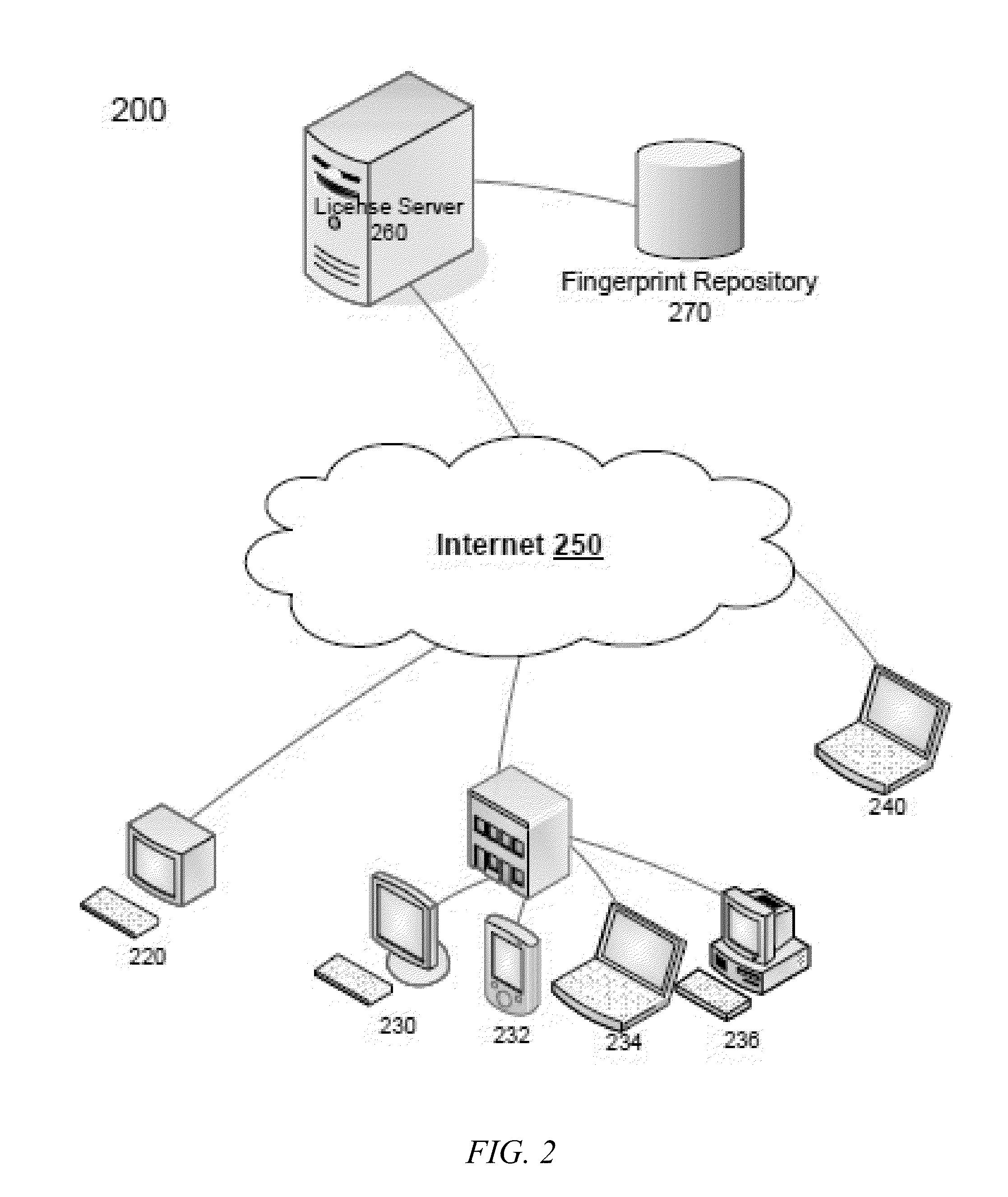
Systems and Methods for Determining Authorization to Operate Licensed Software Based on a Client Device Fingerprint
InactiveUS20100333213A1Digital data processing detailsDigital computer detailsClient-sideAuthorization
Methods and systems disclosed herein may be used to determine if licensed software has been previously installed or used on a device by monitoring an identifier associated with the device on which the licensed software is to be installed or used. Prior to operation of licensed software, a client device requires authorization from a license server. The license server may retrieve a unique identifying device fingerprint from the client device to authorize installation of the software based on a probabilistic comparison of the identifier with stored device identifiers subject to a license. If the comparison yields a match and if total instances of retrieval of the retrieved device fingerprint does not exceed licensed rights, the authorization is granted.
Owner:UNILOC LUXEMBOURG
Multidimensional risk profiling for network access control of mobile devices through a cloud based security system
A server configured to profile a mobile device for a cloud-based system, includes a network interface, a data store, and a processor communicatively coupled to one another; and memory storing computer executable instructions, and in response to execution by the processor, the computer-executable instructions cause the processor to, based on communication to a client application on the mobile device, cause the client application to collect data associated with the mobile device; receive the collected data; and determine a device fingerprint and a risk index for the mobile device based on the collected data, wherein the device fingerprint is utilized to uniquely identify the mobile device and the risk index is utilized to manage the mobile device
Owner:ZSCALER INC
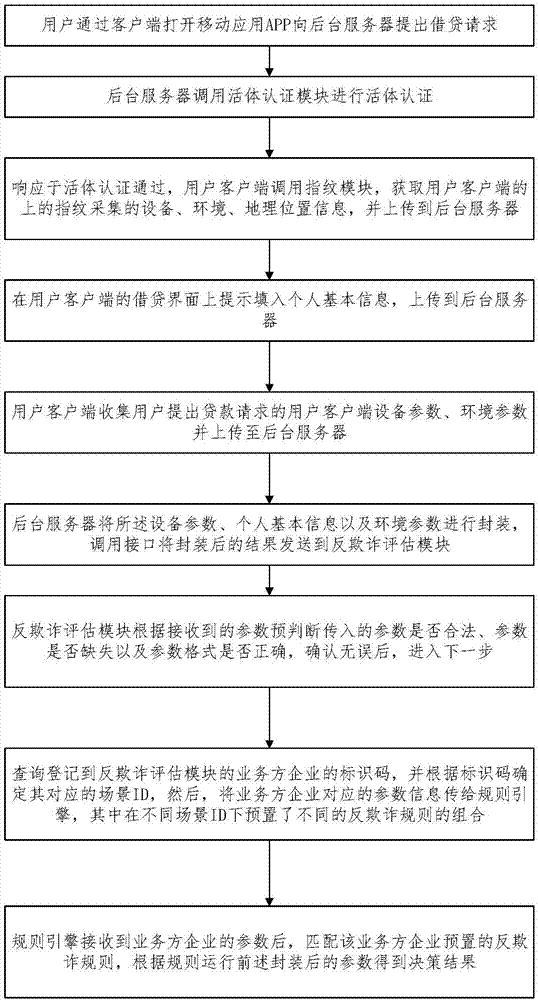
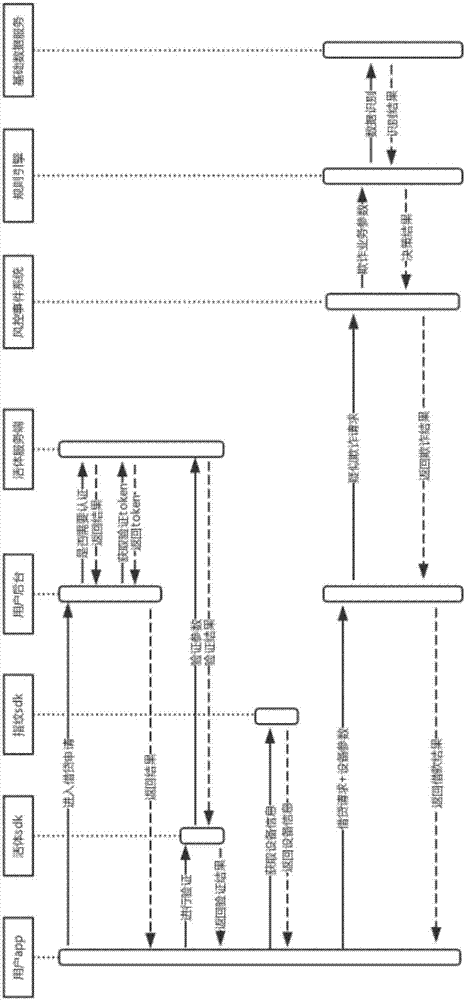
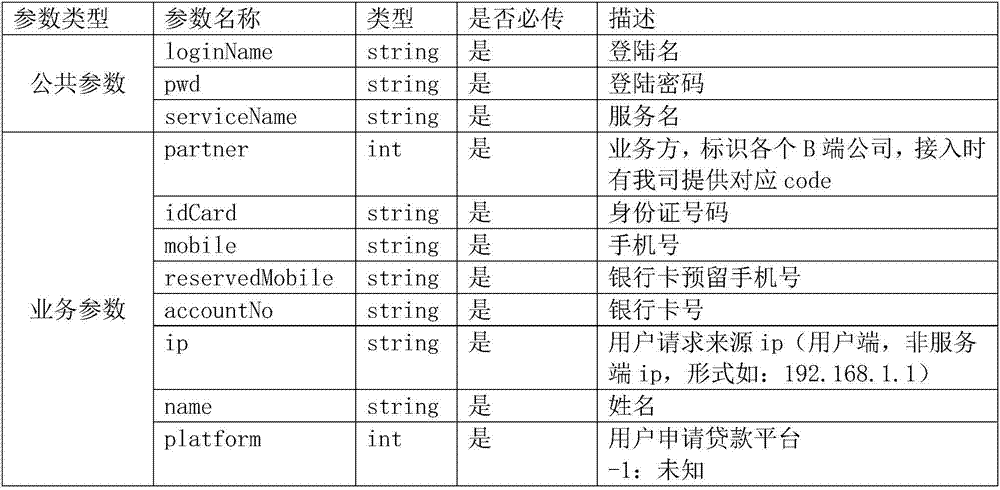
Loan risk fusion assessment method and system
The present invention provides a loan risk fusion assessment method and system. The method includes the steps of: living body verification; device fingerprint, device information, personal basic information and environmental information acquisition; and policy-based fusion judgment. With the loan risk fusion assessment method and system adopted, the examination and approval flow of the pre-loan risk of a loan application is realized; on the basis of the comprehensive judgment of device information, personal basic information and environmental information, the pre-loan risk can be identified and analyzed according to risk policies and levels of specific different cooperative enterprises; and an expected risk control effect can be realized.
Owner:小视科技(江苏)股份有限公司
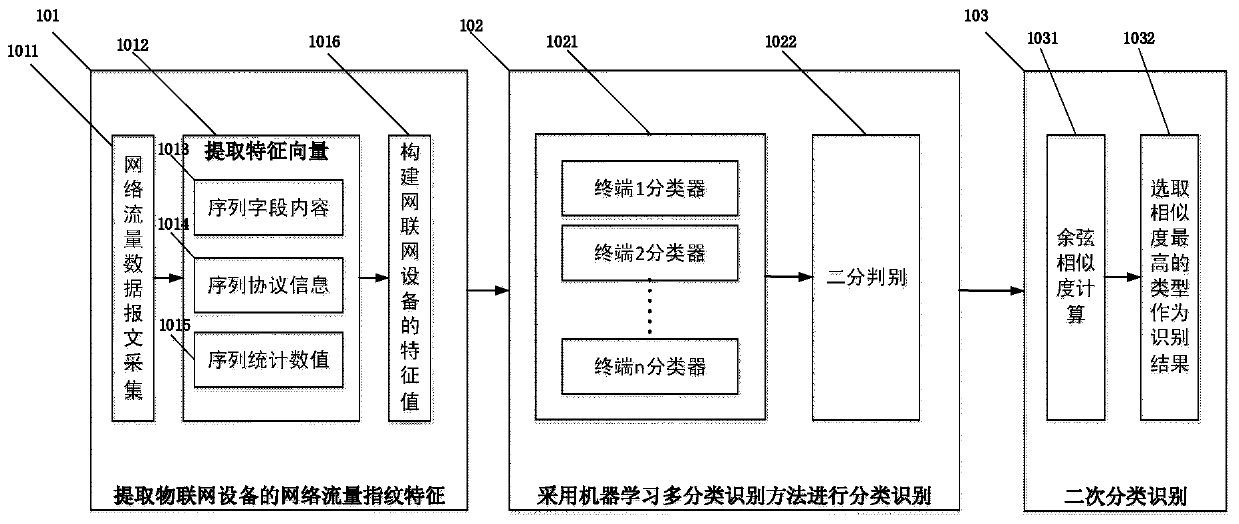
Network flow fingerprint feature two-stage multi-classification Internet of Things device identification method
ActiveCN110380989AProne to identification confusionEfficient identificationData switching networksThe InternetRecognition algorithm
The invention discloses a network flow fingerprint feature two-stage multi-classification Internet of Things device identification method, belongs to the technical field of Internet of Things device access control, and the algorithm extracts network flow features from network flow and matches and identifies accessed Internet of Things devices. The algorithm mainly comprises the following steps: firstly, acquiring N pieces of network message data when an Internet of Things device starts an access stage, and extracting features from three dimensions of sequence field contents, sequence protocolinformation and sequence statistical values to serve as device fingerprint features; using a one-to-many multi-classification machine learning architecture to perform preliminary identification on theto-be-detected Internet of Things device; and if a plurality of identification results appear in the preliminary identification, inputting the results into a maximum similarity comparison module forsecondary classification identification, and selecting the type with the highest similarity as a final identification result. According to the method, the problem that identification overlapping is easy to occur when the existing identification algorithm is used for identifying the Internet of Things device is solved, and the identification accuracy and uniqueness are improved.
Owner:SOUTHEAST UNIV
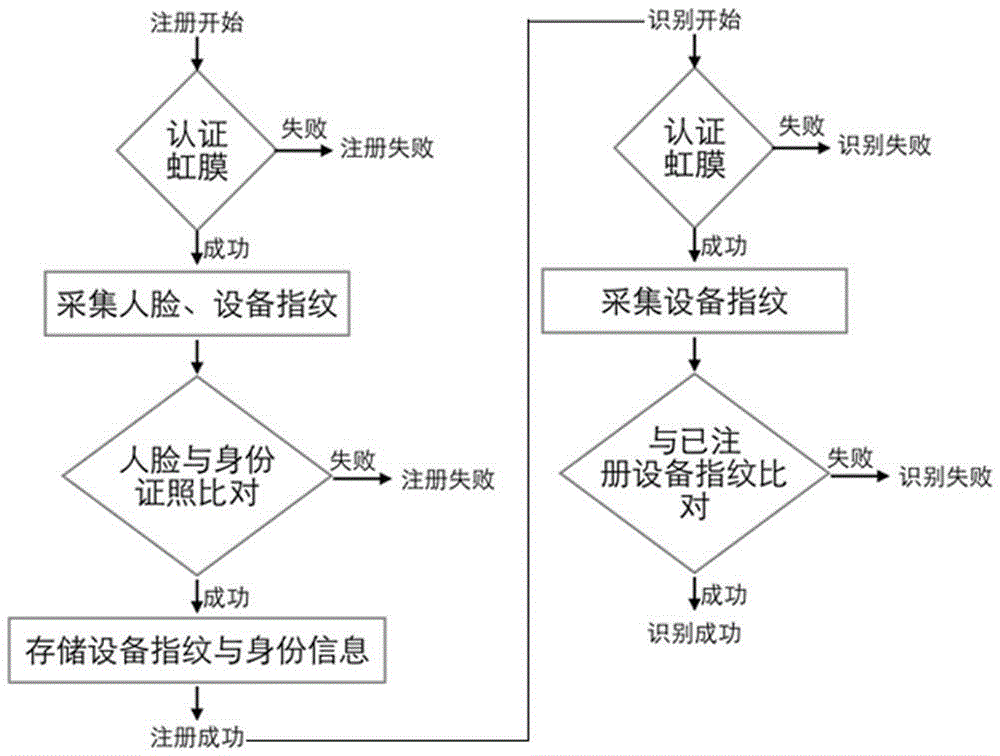
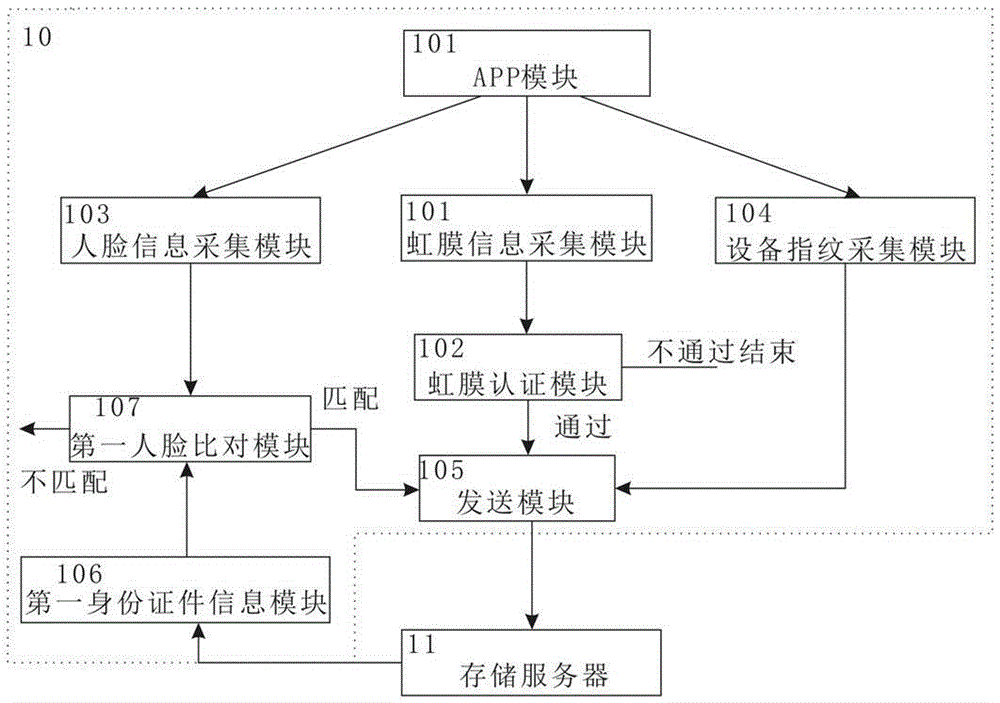
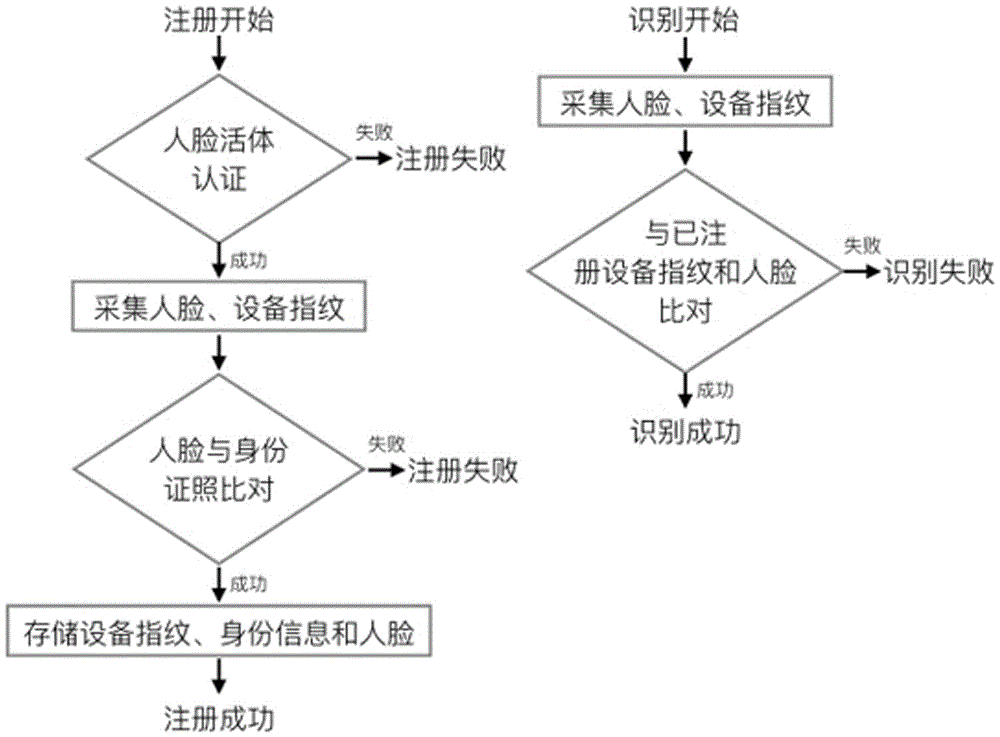
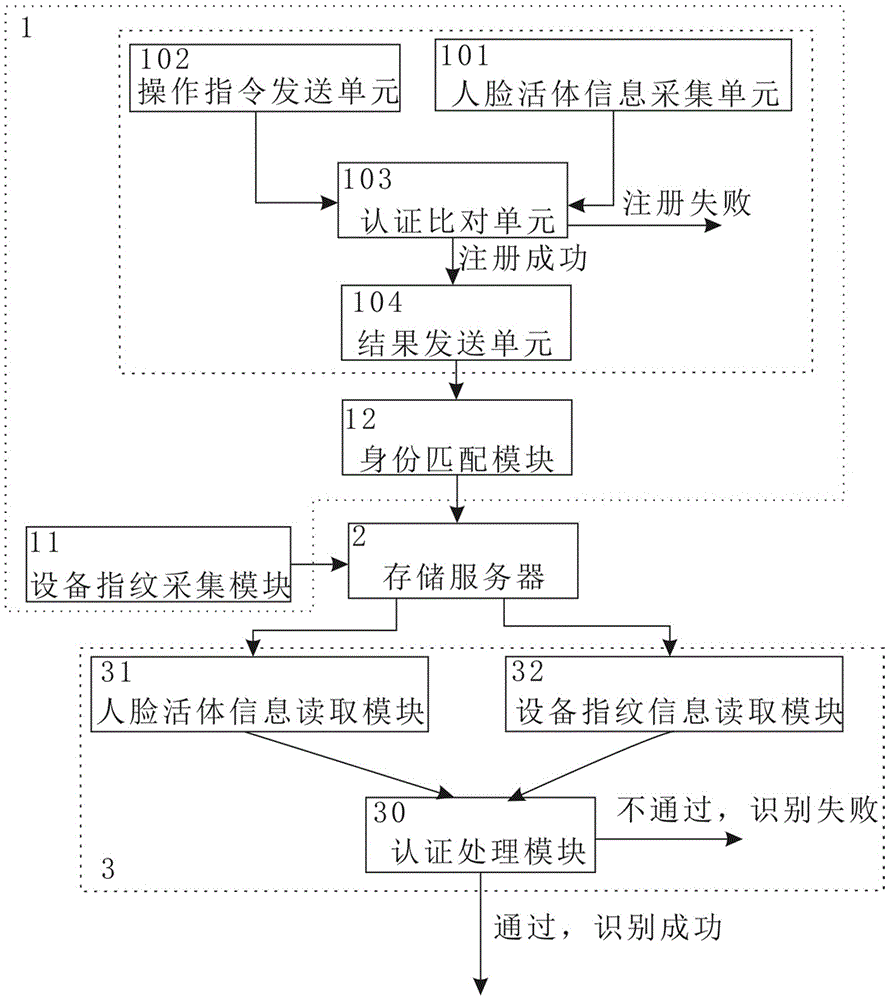
Identity recognition method and system based on multi-biometric feature in combination with device fingerprint
ActiveCN105279416AGuaranteed accuracyRealize real-name authenticationDigital data authenticationIdentity recognitionAuthentication server
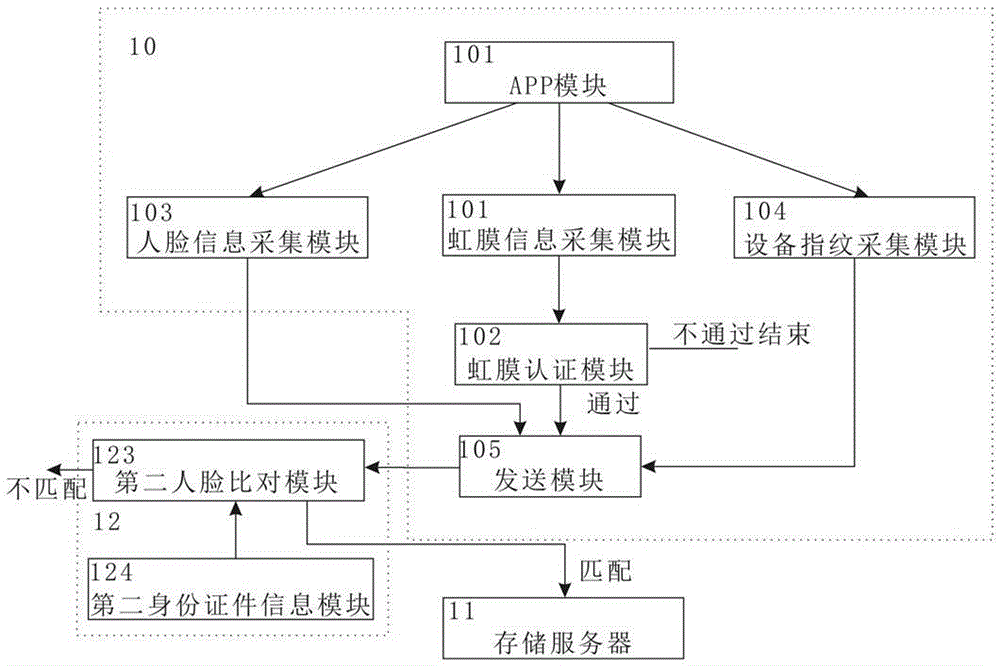
The present invention discloses an identity recognition method and system based on a multi-biometric feature in combination with a device fingerprint. The method comprises two main steps of registration authentication and user identification, and the system comprises a smart phone, a storage server and an authentication server; the smart phone is connected with an input end of the storage server, and an output end of the storage server is connected with the authentication server; and the smart phone is interconnected with the authentication server. The method disclosed by the present invention comprises two main sections of the registration authentication and the user identification, and by means of iris local authentication, the two main sections can confirm that an operator of a phone is an owner of the phone; human face information acquired at the same time as the iris local authentication can be confirmed as human face information of the owner of the phone, thereby ensuring accuracy of registered user information. According to the method and the system disclosed by the present invention, a smart phone iris recognition technology and a smart phone device fingerprint technology are combined, so that effects of network real person and real name authentication as well as high network account security and login convenience and the like are achieved.
Owner:SHANGHAI CHUANZHI FINANCE INFORMATION SERVICE CO LTD
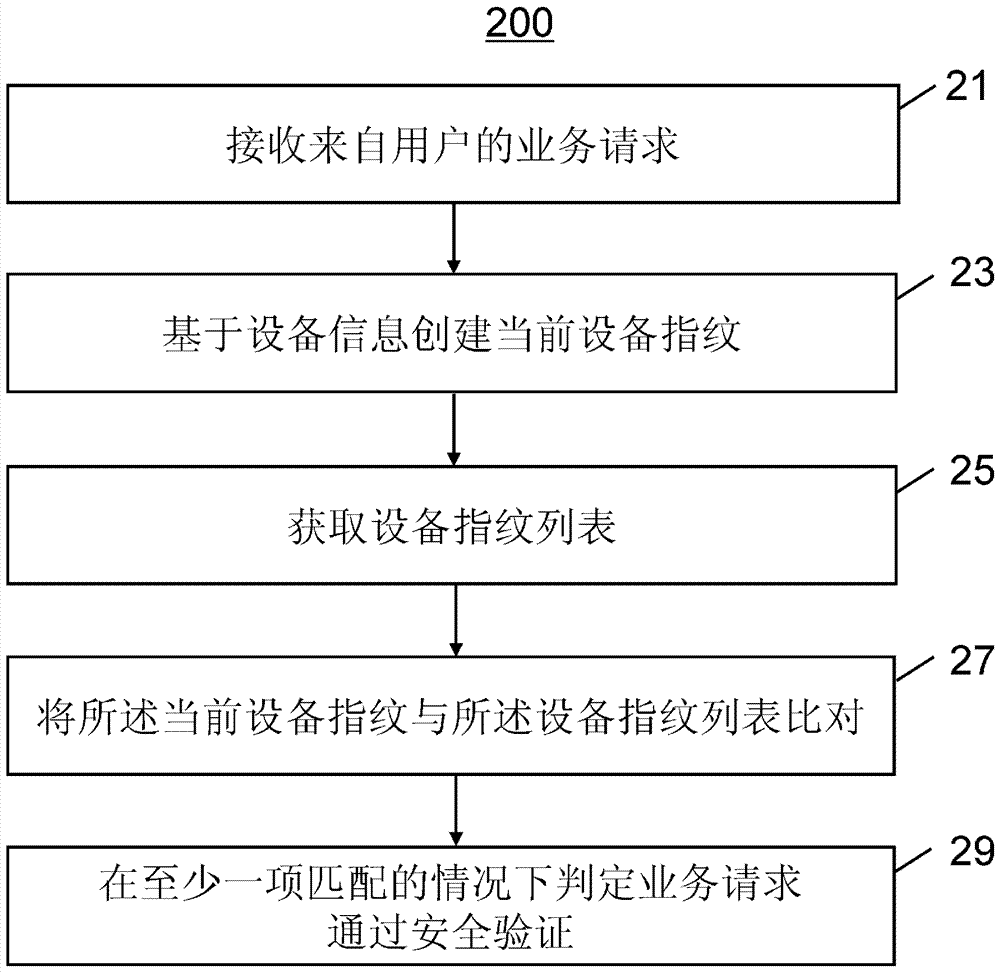
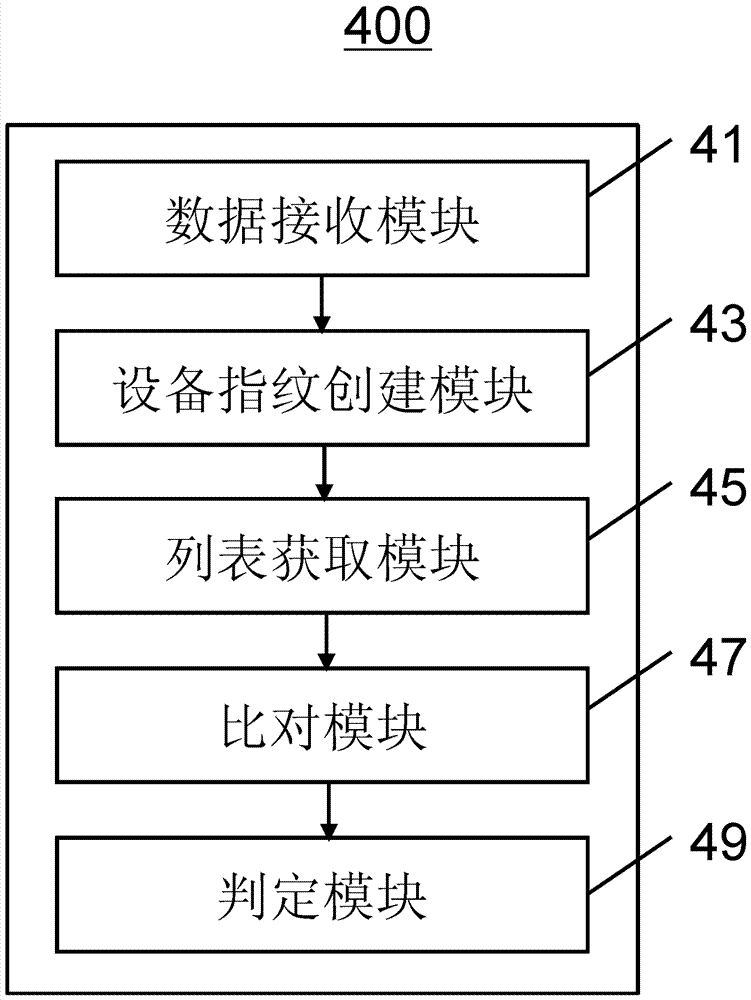
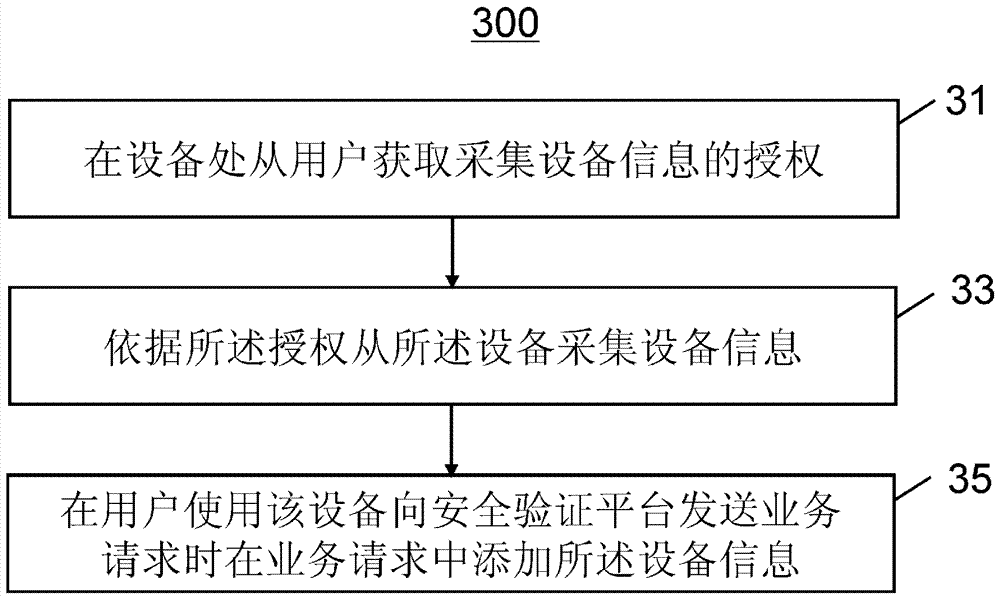
Safety verification method, platform, device and system
The invention provides a safety verification method. The safety verification method includes: receiving a service request from a user, wherein the service request includes user information and device information; creating a current device fingerprint on the basis of the device information; acquiring a device fingerprint list, wherein the device fingerprint list includes pre-stored device fingerprints of all the devices associated with the user; comparing the current device fingerprint and the device fingerprint list; and determining that the service request passes through safety verification when at least one items of the current device fingerprint and the device fingerprint list match each other, wherein the device information includes a device hardware parameter and device use information data, and the device fingerprint is a device model which is created according to the device hardware parameter and the device use information data. The invention provides a corresponding safety verification platform, a corresponding safety verification method which is implemented on a user device, a corresponding safety verification device, and a safety verification system.
Owner:CHINA UNIONPAY
Temperature-Profiled Device Fingerprint Generation and Authentication from Power-Up States of Static Cells
A method, system and computer program product for generating device fingerprints and authenticating devices uses initial states of internal storage cells after each of a number multiple power cycles for each of a number of device temperatures to generate a device fingerprint. The device fingerprint may include pairs of expected values for each of the internal storage cells and a corresponding probability that the storage cell will assume the expected value. Storage cells that have expected values varying over the multiple temperatures may be excluded from the fingerprint. A device is authenticated by a similarity algorithm that uses a match of the expected values from a known fingerprint with power-up values from an unknown device, weighting the comparisons by the probability for each cell to compute a similarity measure.
Owner:IBM CORP
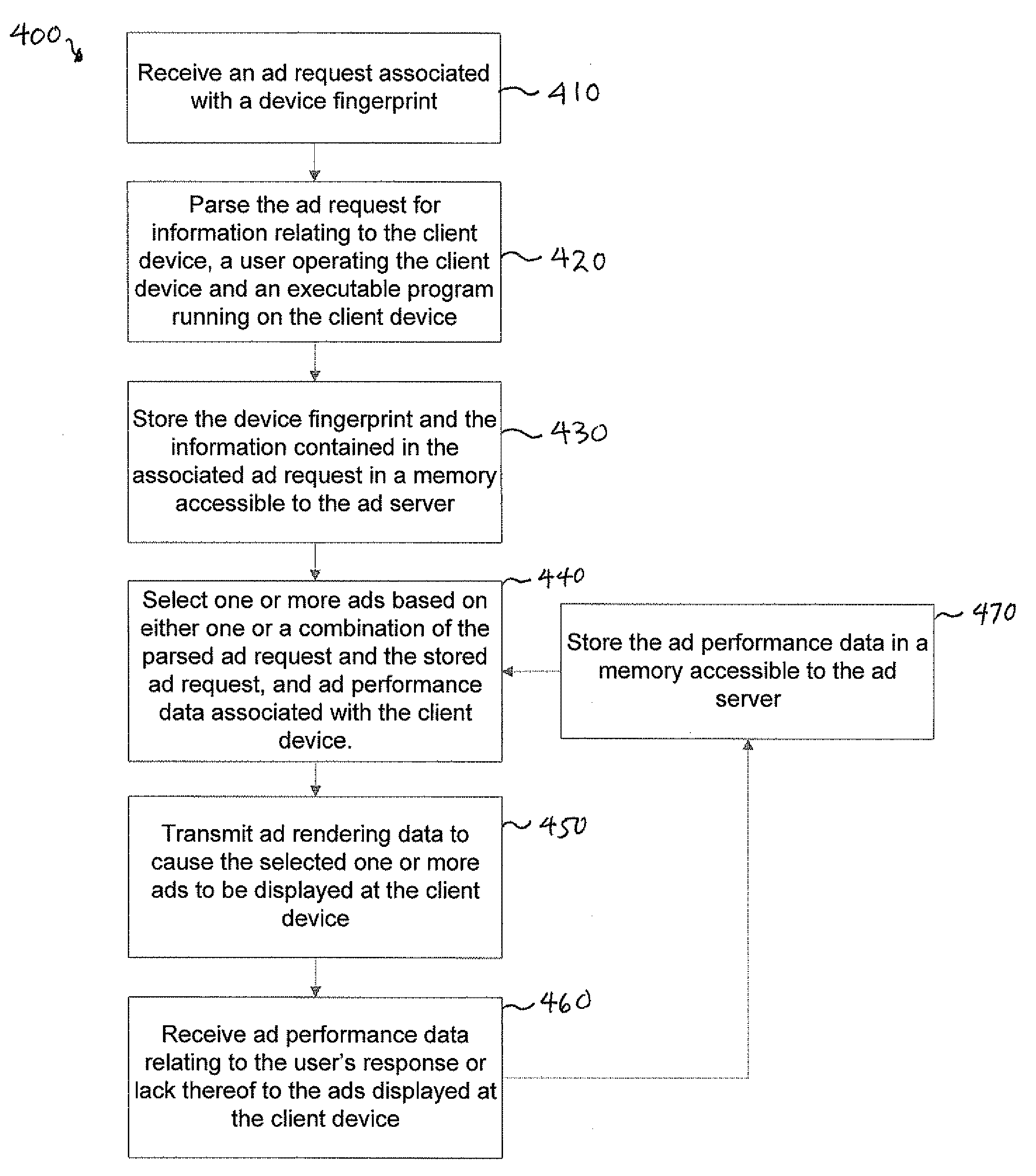
Methods and Systems for Dynamic Serving of Advertisements in a Game or Virtual Reality Environment
A system for dynamically serving ads to one or more client devices in connection with the operation of an executable program. The system comprises a network interface disposed to receive an ad request associated with a device fingerprint that uniquely identifies a client device. The ad request comprises information relating to any one or more of the client device, a user operating the client device and an executable program operating on the client device. The system further comprises a memory and a processor, in communication with the network interface and the memory, the processor configured for operating the program instructions. The program instructions stored in the memory are operable for parsing the information in the ad request, selecting one or more ads based at least in part on the parsed information, and transmitting ad rendering data to cause the one or more ads to be displayed at the client device.
Owner:UNILOC LUXEMBOURG
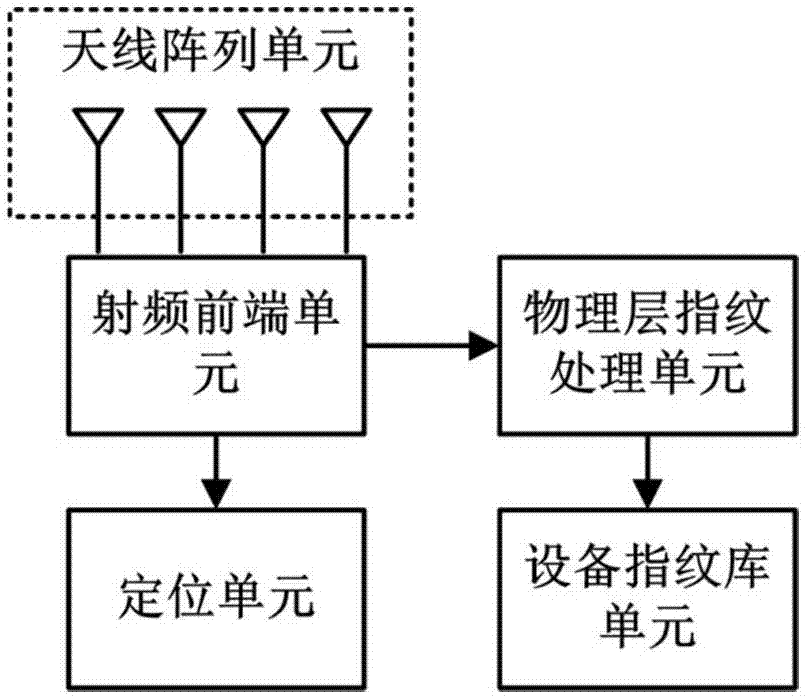
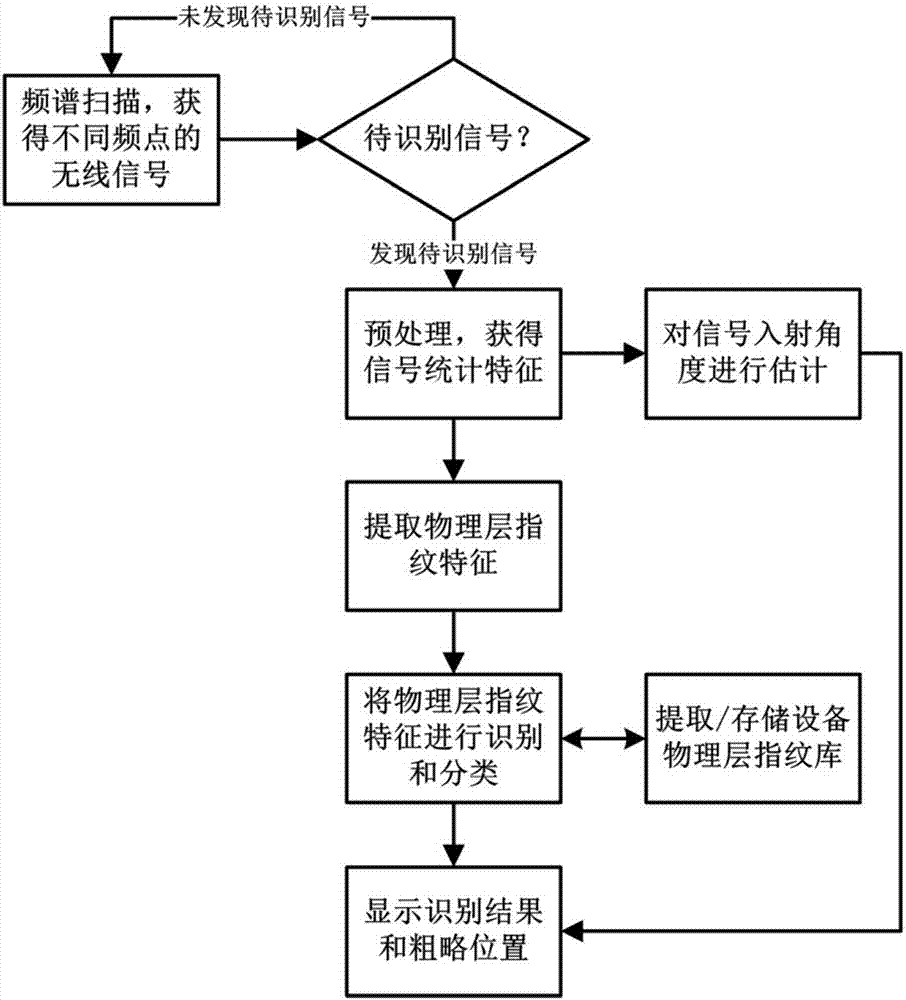
Target identification and positioning system and method based on physical fingerprint feature of device
ActiveCN107368732AImplement extractionAchieving identifiabilityDigital data authenticationWireless communicationPattern recognitionAngle of incidence
The present invention discloses a target identification and positioning system and method based on the physical fingerprint feature of a device. The system comprises an antenna array unit, a radio frequency front-end unit, a physical layer fingerprint processing unit, a device fingerprint library unit and a positioning unit. The method comprises the following steps that: the radio frequency front-end unit performs signal scanning on a certain frequency band; when a signal on the required identification frequency band is scanned, the signal is preprocessed and a physical layer fingerprint feature is extracted on a to-be-identified signal; the obtained physical layer fingerprint feature is identified and compared with the physical layer fingerprint feature stored in a system library to determine whether the physical layer fingerprint feature has been already in the system library and to determine the identity of the device; and the positioning unit estimates the angle of incidence of the acceptation signal and the distance of the signal source. According to the system and method provided by the present invention, through the physical layer fingerprint feature, identification of the identity with a single target source is realized, and the system and method are applied to the related technologies based on the physical layer security.
Owner:NANJING INST OF CYBER TECH CO LTD
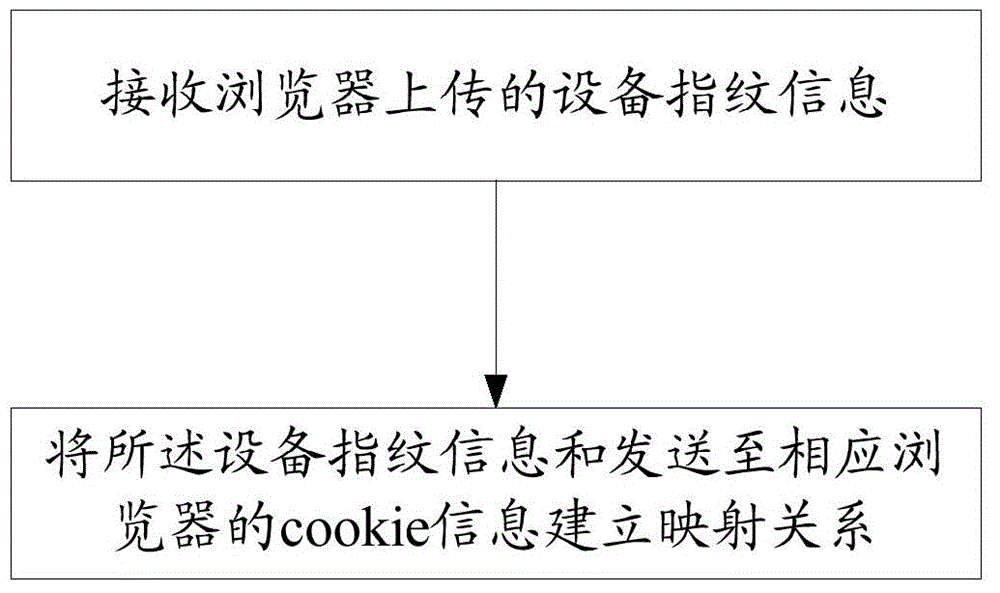
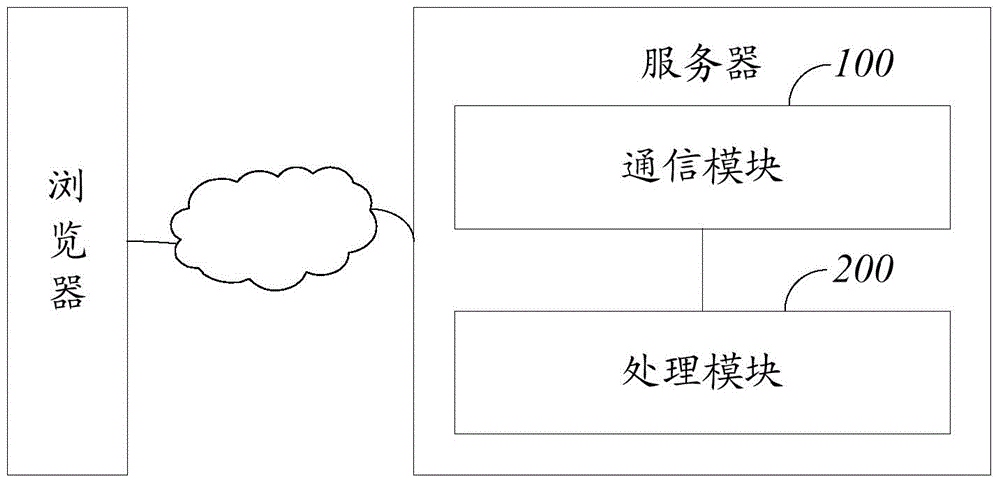
Browser-based user behavior tracking method and device
The invention discloses a browser-based user behavior tracking method and device. The method includes the following steps that: device fingerprint information uploaded by a browser is received; and a mapping relation is established between the device fingerprint information and cookie information sent to the corresponding browser. According to the browser-based user behavior tracking method and device of the invention, the device fingerprint information of a client is acquired, and the mapping relation is established between the cookie information of the browser of the client and the device fingerprint information, and therefore, after the cookie information of the browser of the client is cleared, the behavior of the user can be tracked through recovering the mapping relation.
Owner:ALIBABA GRP HLDG LTD
Method and system for authorizing remote access to customer account information
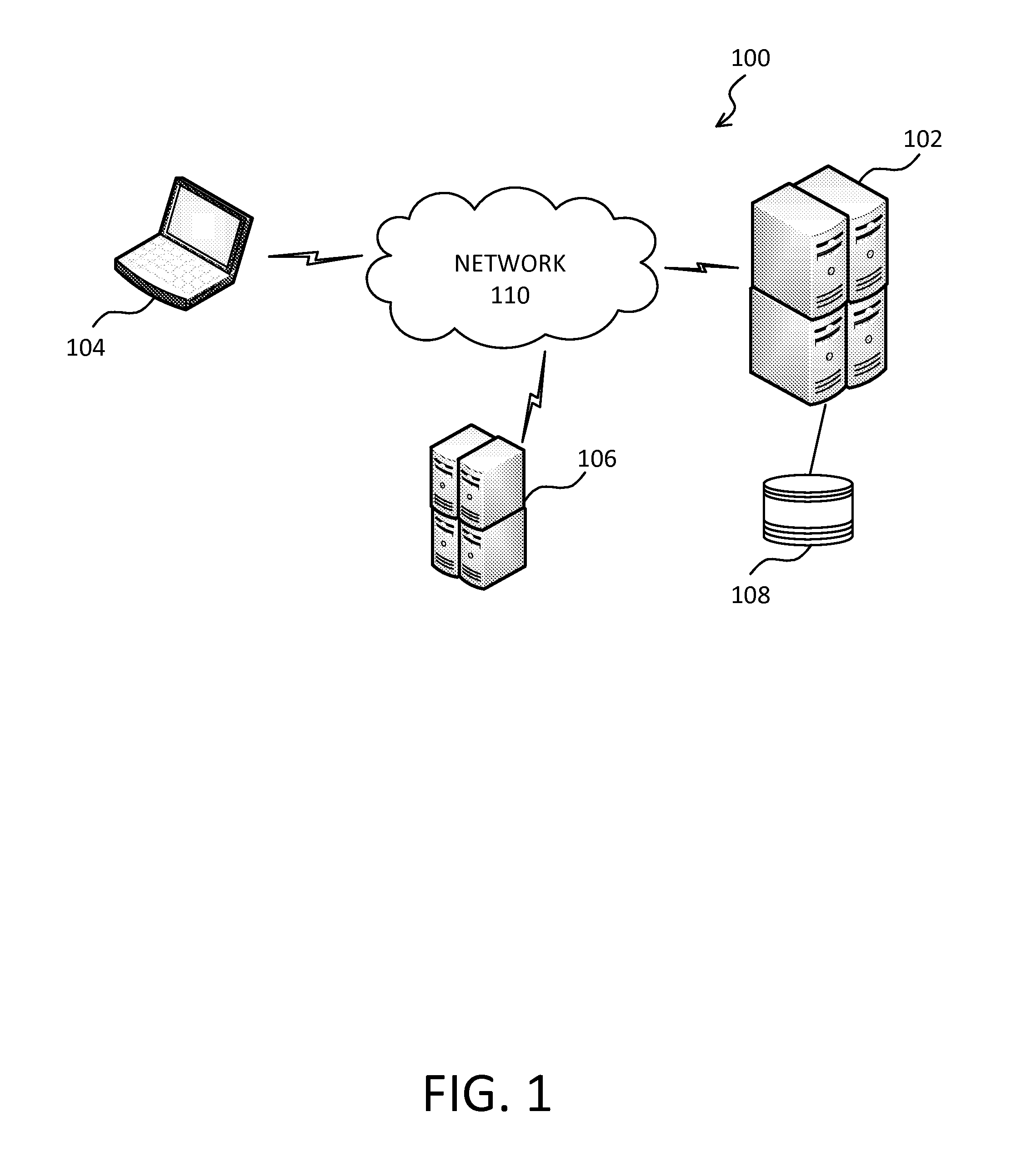
ActiveUS20130167203A1High level of assuranceCustomer relationshipDigital data processing detailsCustomer informationRemote computing
System for authorizing a request for remote access to customer account information includes a server configured to receive the request via a network from a remote computing device, a database storing the customer account information accessible by the server, and memory accessible by the server and storing a customer notification program which, when executed by the server, performs steps for (a) identifying, responsive to the server receiving the request, the remote computing device by a device fingerprint and by a requesting location, (b) determining whether the device fingerprint matches any of a number of device fingerprints authorized to access the customer account information, and (c) sending, responsive to determining a mismatch between the device fingerprint and each of the previously authorized device fingerprints, a notification of the request to a customer-specified address, the notification indicating (i) the request, (ii) identity of the remote computing device, and (iii) the requesting location.
Owner:UNILOC 2017 LLC
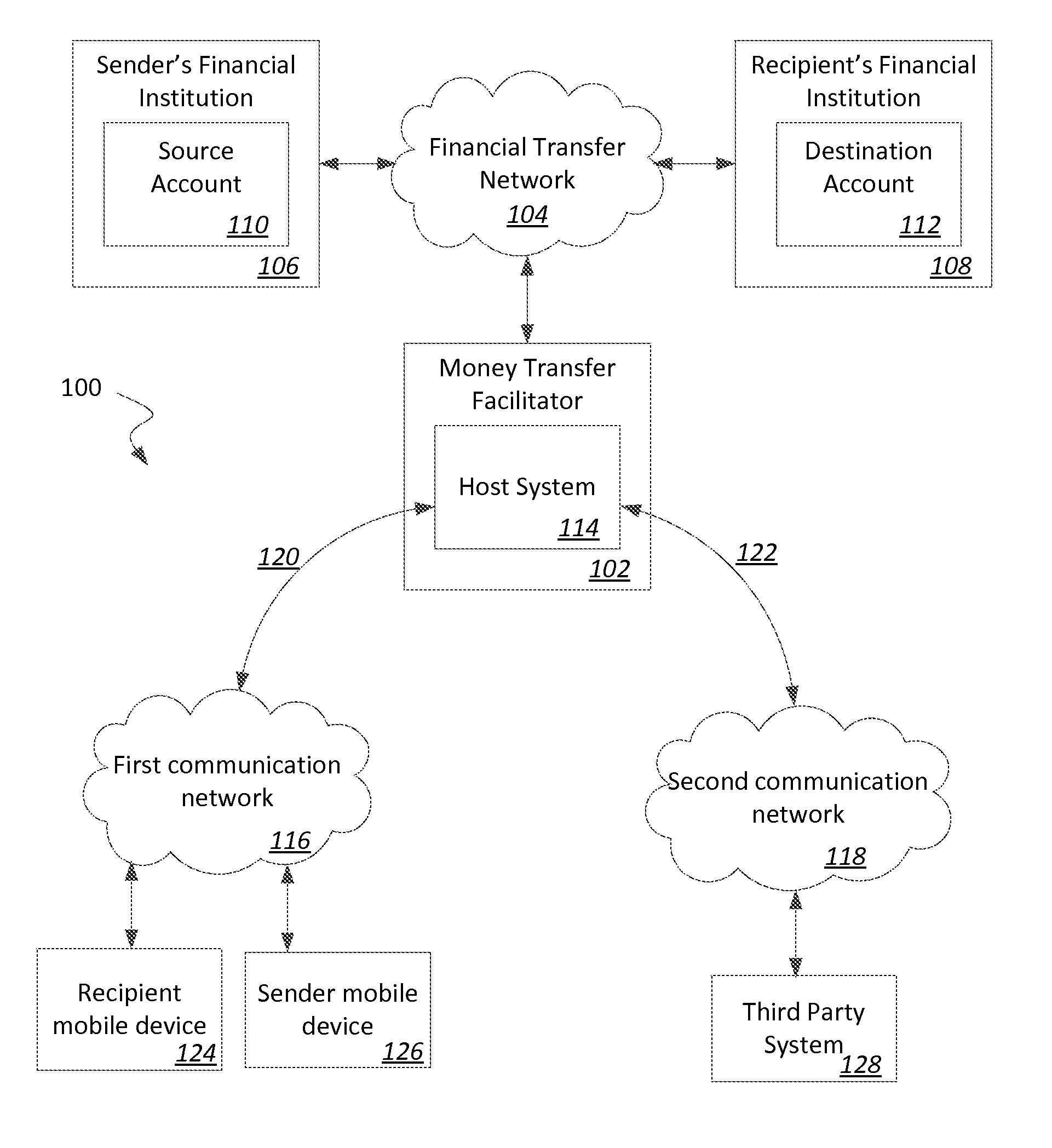
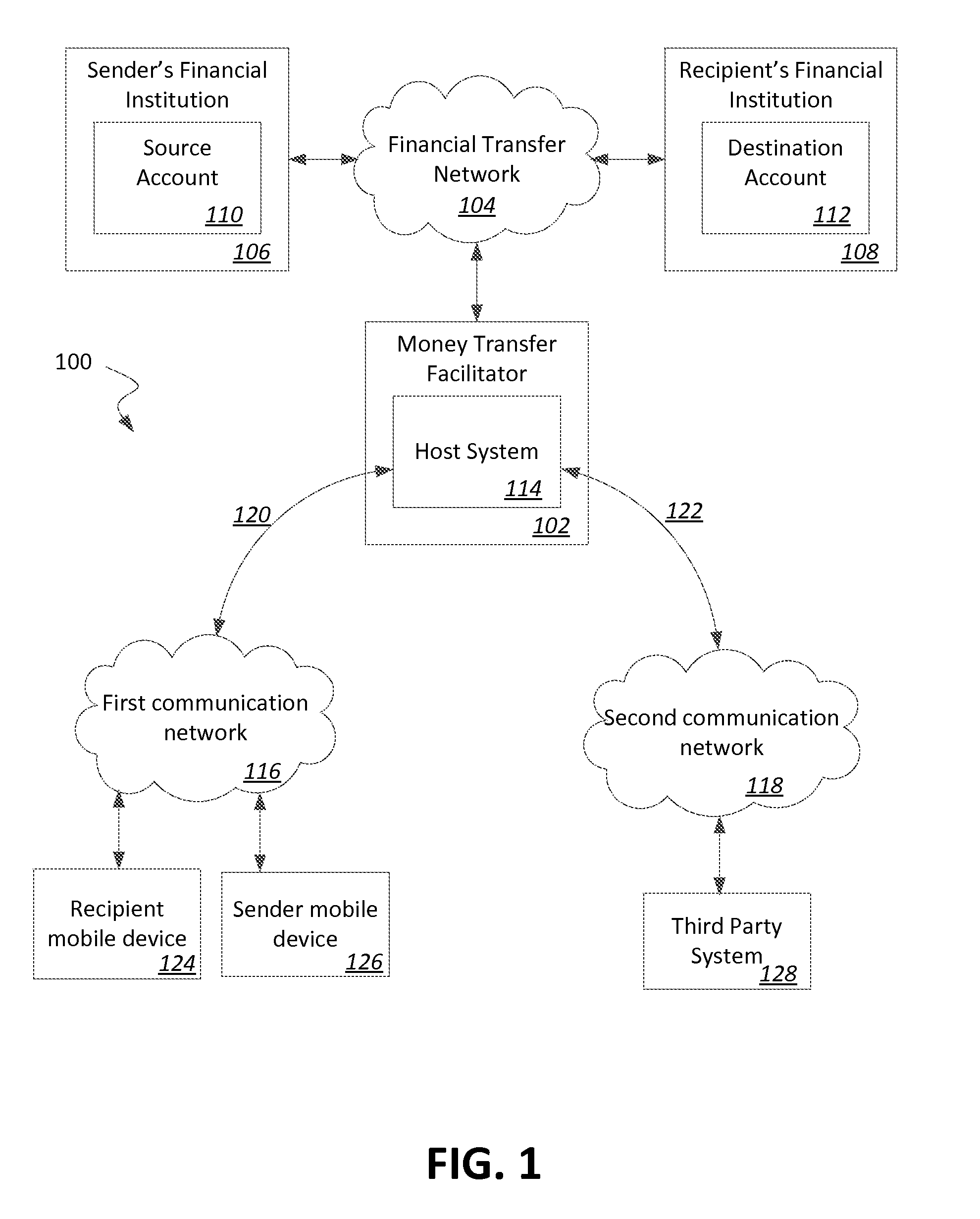
Methods and systems for validating mobile devices of customers via third parties
ActiveUS20160127898A1Digital data processing detailsMultiple digital computer combinationsThird partyUniform resource locator
A method for authenticating a mobile device in real-time. The method includes detecting the mobile device, sending a text message containing a unique uniform resource locator (“URL”) to the mobile device, and detecting an access of the unique URL by the mobile device through a first communication path. In response to detecting the access of the unique URL, requesting and subsequently receiving, by the host system in real-time, a phone number and a subscriber identification ID associated with the mobile device through a second communication path distinct from the first communication path, and a device fingerprint of the mobile device through the first communication path. The method further includes initiating a risk analysis based on the phone number, the subscriber ID, and the device fingerprint and determining an authentication status of the mobile device based on the risk analysis.
Owner:THE WESTERN UNION CO
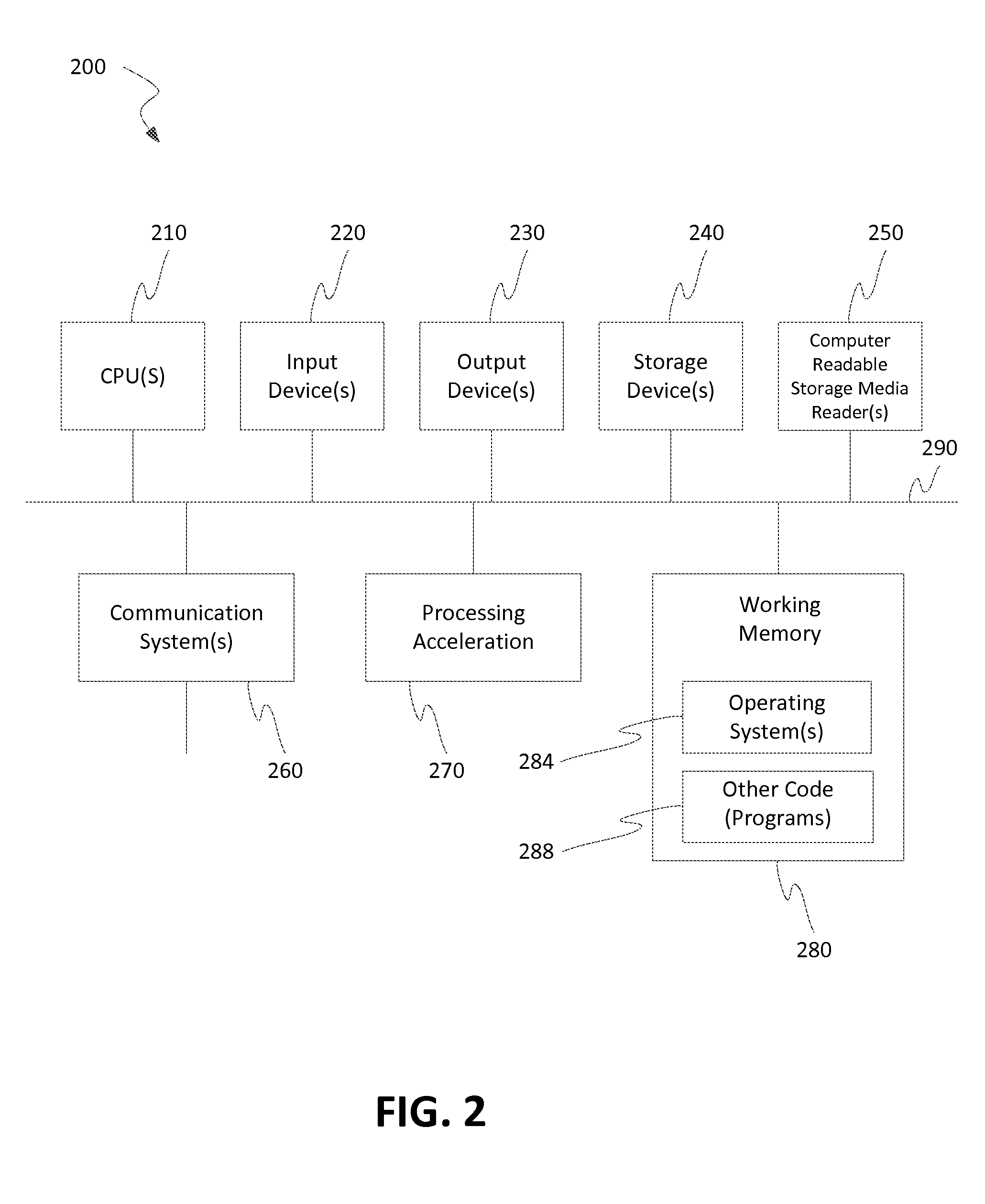
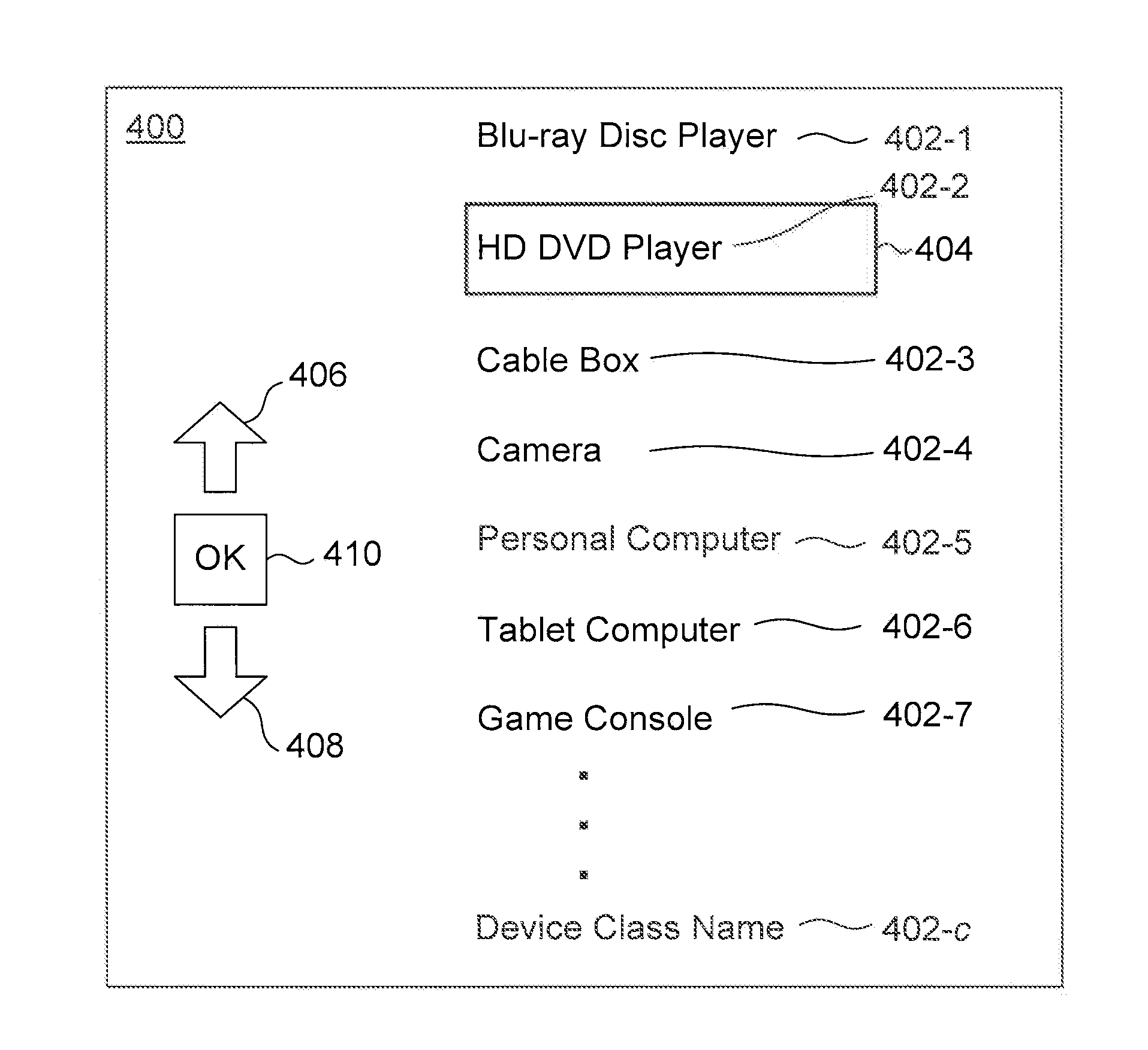
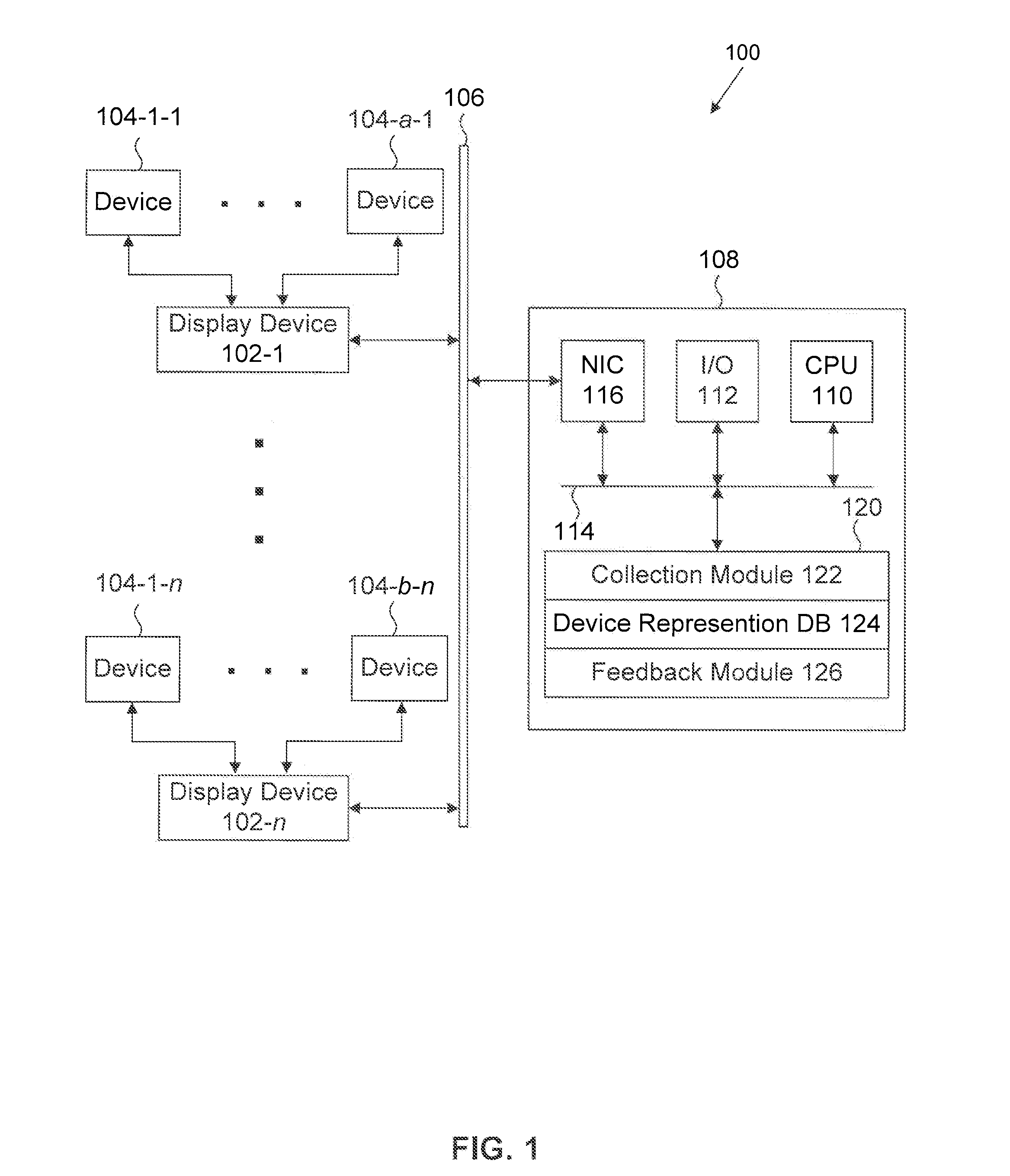
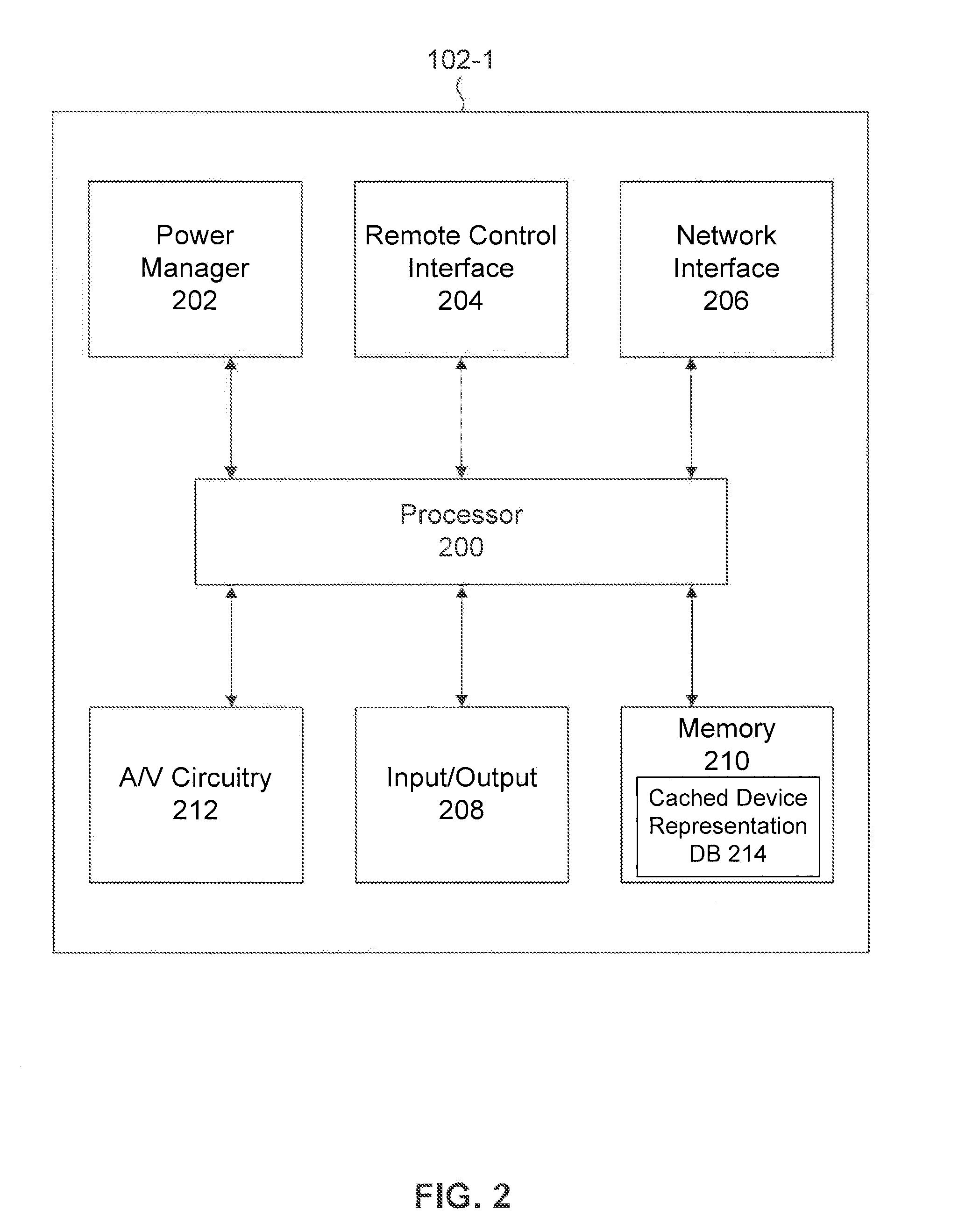
Providing A Representation For A Device Connected To A Display Device
ActiveUS20160180806A1Cathode-ray tube indicatorsSelective content distributionNetwork connectionDisplay device
Disclosed herein are system, apparatus, article of manufacture, method, and / or computer program product embodiments for providing a representation to a connected device. An embodiment operates by recognizing a new device connected to a display device, collecting device fingerprint information from the new device, and requesting a device class representation information determined based on the device fingerprint information. Another embodiment operates by receiving device fingerprint information from a display device via a network connection, wherein the device fingerprint information is collected from a device connected to a display device, and providing device class representation information to the display device via the network connection, when the device class representation information corresponding to the device fingerprint information is available.
Owner:ROKU INCORPORATED
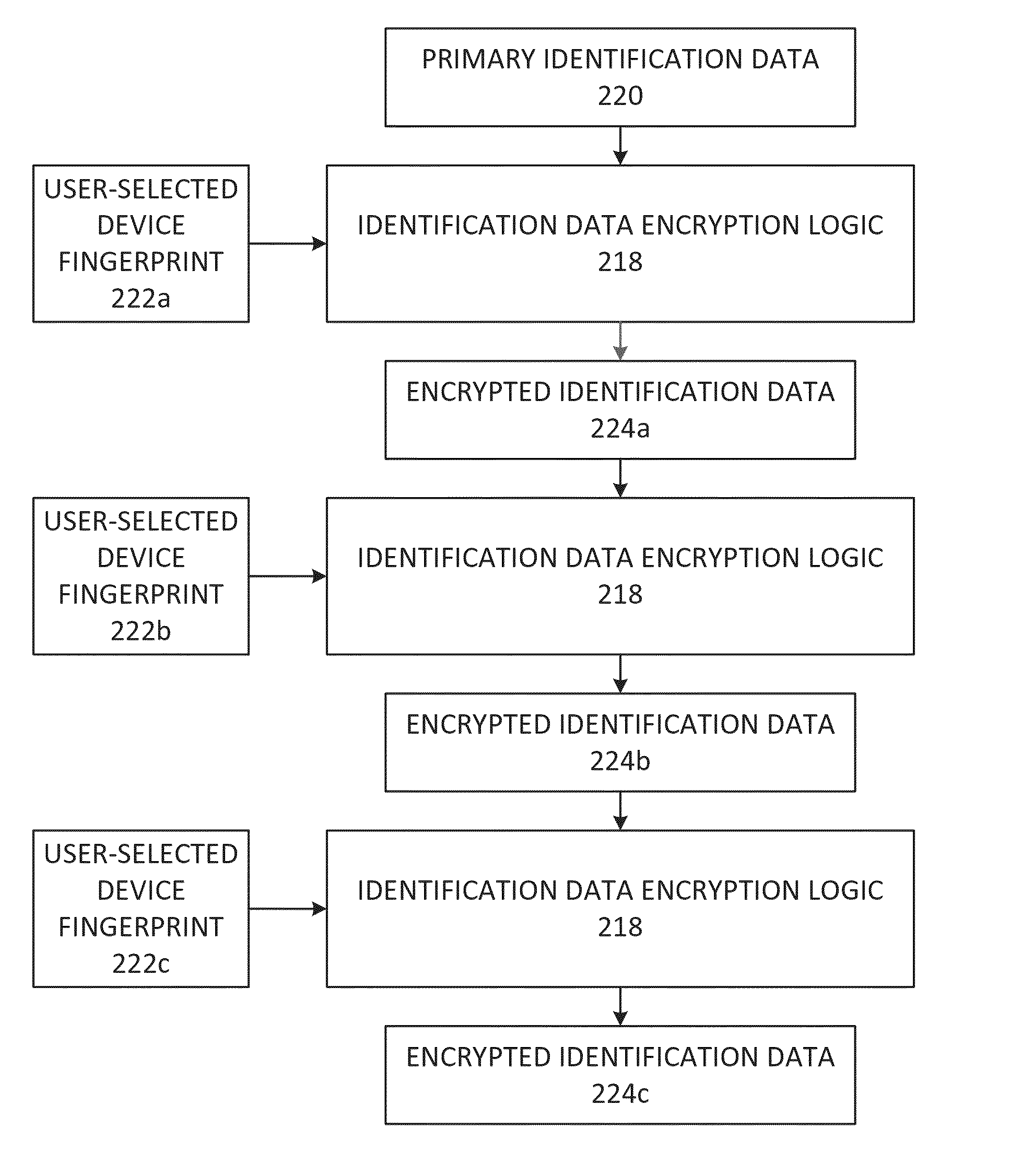
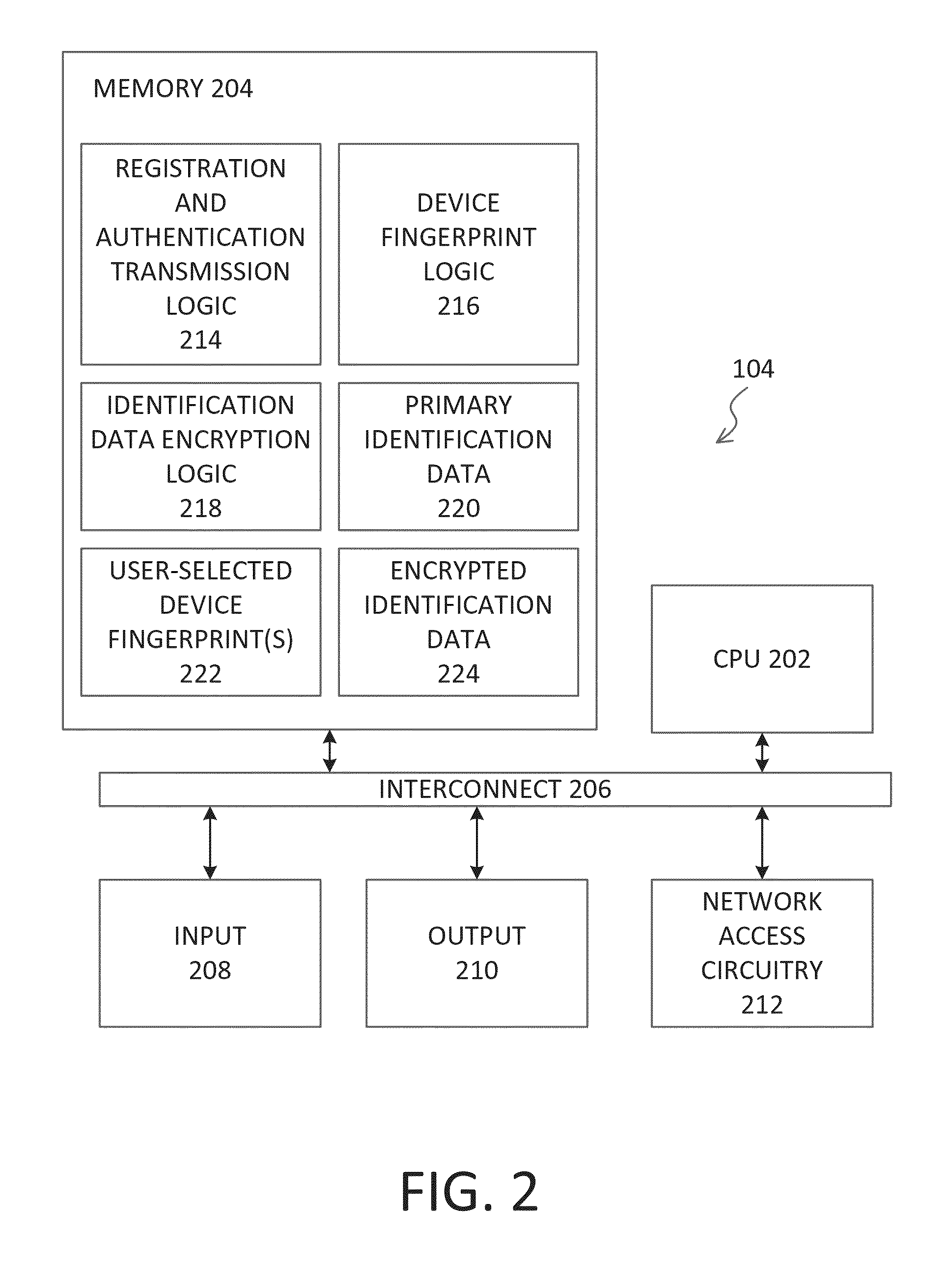
Registration and authentication of computing devices using a digital skeleton key
ActiveUS20140281561A1Digital data processing detailsMultiple digital computer combinationsAuthentication informationDevice fingerprint
A method for registering a computing device to a user account using at least one user-selected fingerprintable device externally accessible to the computing device including transmitting a registration information request to the computing device, receiving at least one device fingerprint of the at least one user-selected fingerprintable device accessible by the computing device, and primary identification data of the computing device, generating a skeleton key, recording the primary identification data, and associating the skeleton key and the primary identification data with the user account. A method for authenticating the computing device including transmitting an authentication information request to the computing device, receiving an encrypted identification data from the computing device, decrypting the encrypted identification data using a skeleton key associated with the user account, comparing the decrypted identification data with a primary identification data associated with the user account, and authenticating the computing device.
Owner:ATREUS LABS LLC
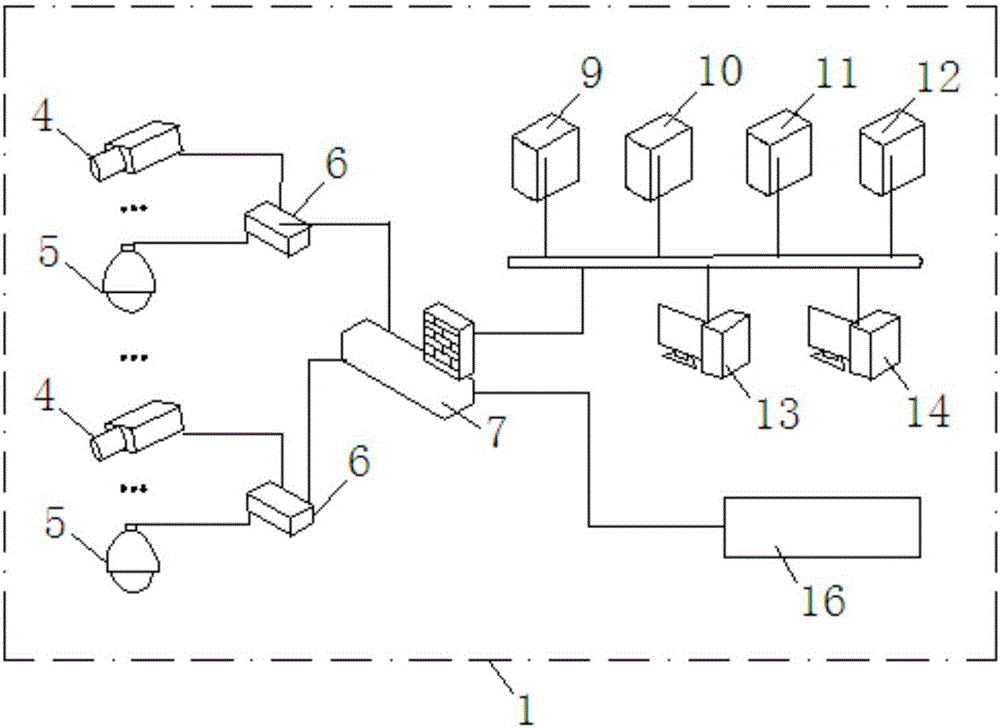
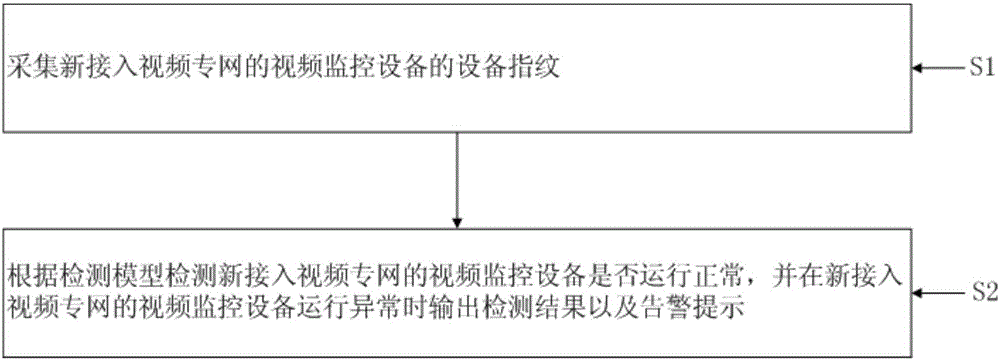
Terminal abnormity detection method
ActiveCN106789935AAvoid data breachesPrevent illegal intrusionClosed circuit television systemsData switching networksVideo monitoringOperational system
The invention provides a terminal abnormity detection method, and belongs to the technical field of private network access device monitoring management. At least one video monitoring device is connected to a video private network; each video monitoring device has a unique device fingerprint, and the device fingerprint is a feature item set corresponding to an operating system of the video monitoring device; before the detecting method, a fingerprint sample library is established, at least one decision rule is preset, the fluctuation range of each decision rule is defined, and a detection model is obtained according to the decision rules via a decision tree algorithm; the method comprises the steps of: acquiring the device fingerprint of the video monitoring device newly connected to the video private network; detecting whether the video monitoring device newly connected to the video private network runs normally according to the detection model, and outputting a detection result and an alarm prompt when the video monitoring device newly connected to the video private network runs abnormally. The method has the advantages of ensuring a trusted terminal is securely and efficiently connected to the video private network, and timely detecting the abnormal device.
Owner:SHANGHAI CHENRUI INFORMATION TECH
Identity identification method and system based on combination of face characteristics and device fingerprint
PendingCN105488495AGuaranteed accuracyEnable login convenienceMatching and classificationSpoof detectionAuthentication serverTwo step
The invention discloses an identity identification method and system based on combination of face characteristics and a device fingerprint. The method includes two steps of registration certification and user identification. The system includes an intelligent mobile phone, a memory server for storing the device fingerprint information of the intelligent mobile phone and the user identity information, and a certificate server for identifying the face in-vivo information and the device fingerprint information of the intelligent mobile phone, the intelligent mobile phone is connected with the input end of the memory server, the output end of the memory server is connected with the certificate server, and the intelligent mobile phone is in interaction connection with the certificate server. Through the combination of intelligent face in-vivo identification technology and intelligent mobile phone fingerprint technology, the effects of network real-person and real-name certification, high network account security, and convenient logging are achieved.
Owner:SHANGHAI CHUANZHI FINANCE INFORMATION SERVICE CO LTD
Method and apparatus for determining device fingerprint according to similarity, and server
ActiveCN107423613AAvoid dependenceImprove accuracyCharacter and pattern recognitionDigital data authenticationDevice PropertiesAlgorithm
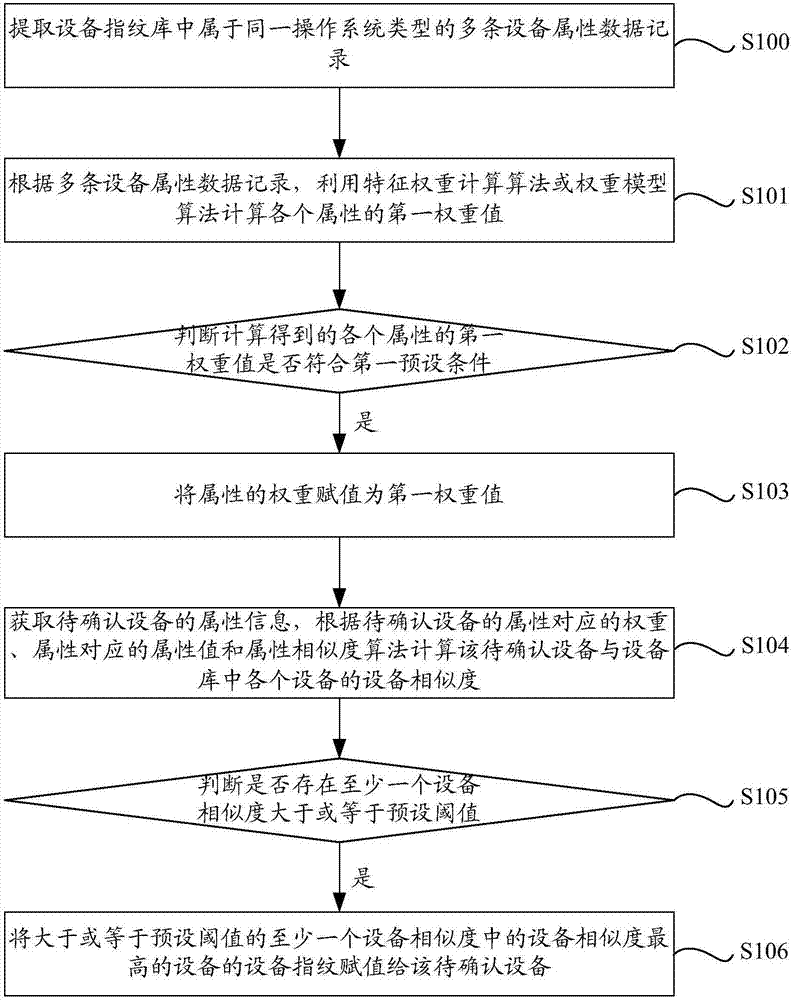
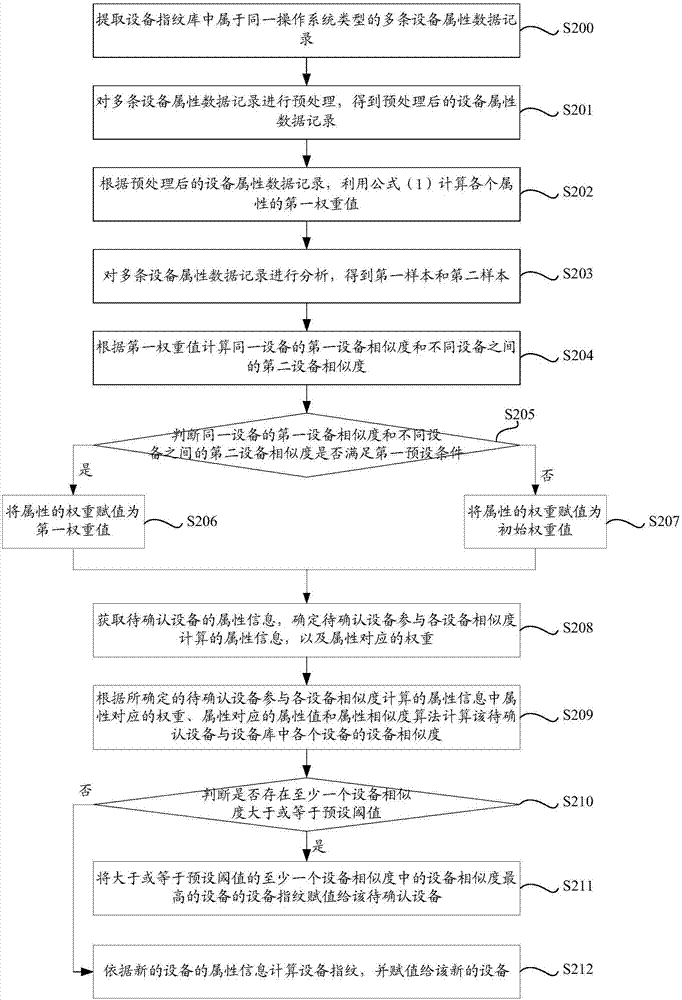
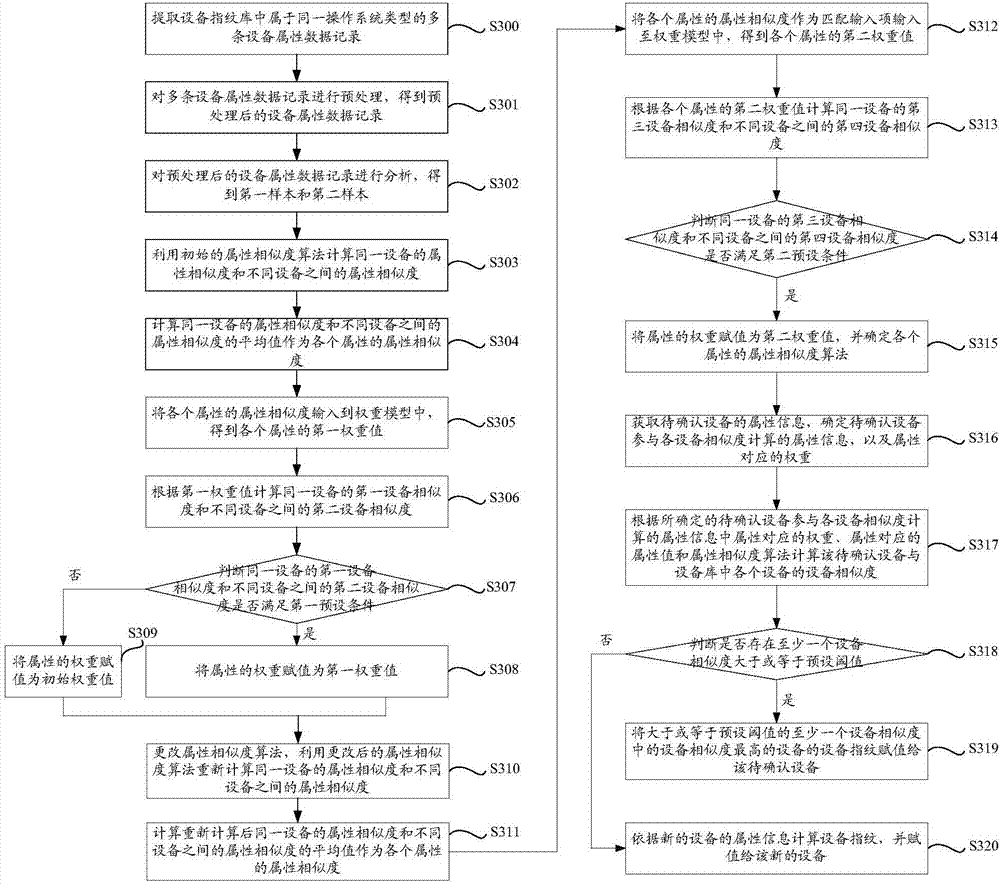
The invention discloses a method and an apparatus for determining a device fingerprint according to similarity, a server and a computer storage medium. According to the method for determining the device fingerprint according to the similarity, provided by an embodiment of the invention, a first weight value of each attribute is calculated by utilizing a characteristic weight calculation algorithm or a weight model algorithm according to device attribute data records, and the weight value of a weight is not set by depending on human experience, so that the dependency on the human experience is avoided, the accuracy of device similarity calculation is effectively improved, and the accuracy of judging whether devices are same or not is improved; and the calculated weight value is verified, so that the accuracy of the device similarity calculation can be further improved.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD +1
Equipment fingerprint acquisition method and device, storage medium and electronic device
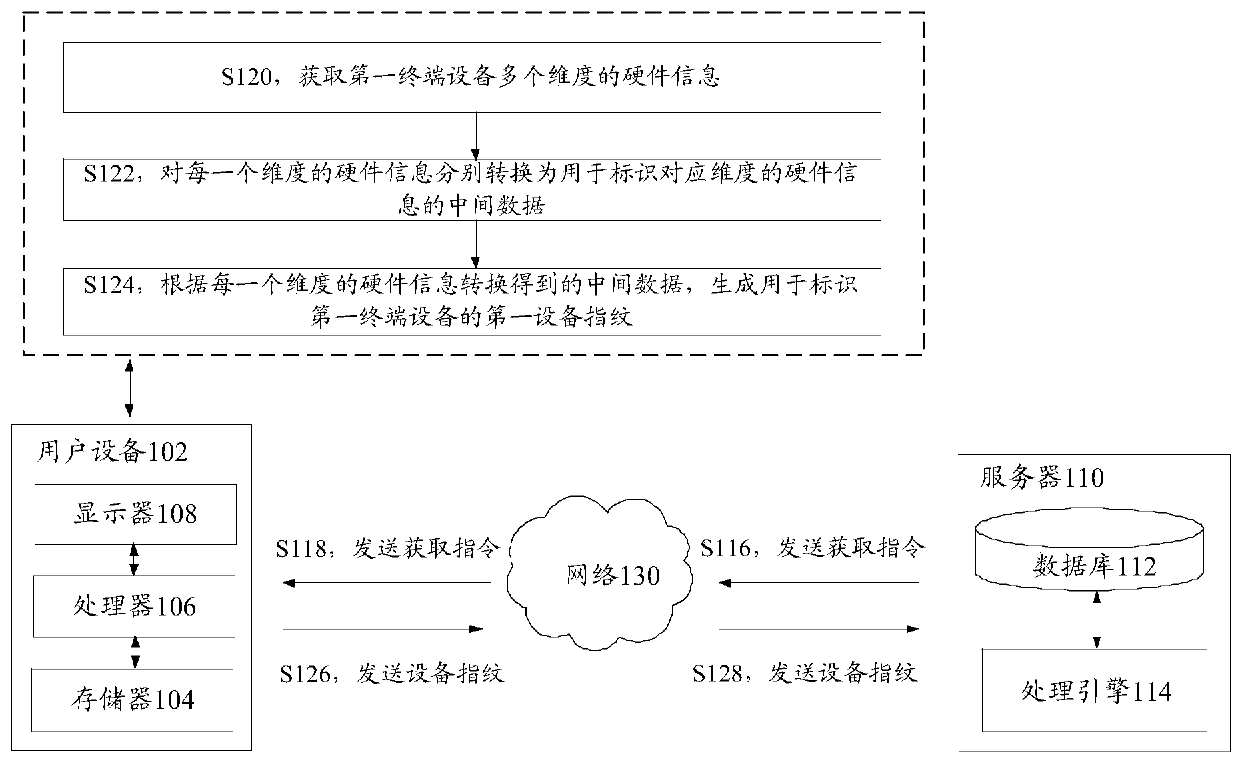
ActiveCN110427785ANot easy to tamper withNot easy to forgeInternal/peripheral component protectionComputer hardwareOperational system
The invention discloses an equipment fingerprint acquisition method and device, a storage medium and an electronic device. The equipment fingerprint acquisition method comprises the following steps: acquiring multi-dimensional hardware information of a first terminal device, wherein the multi-dimensional hardware information is obtained by accessing a kernel layer of the first terminal device in afirst mode, and the first mode is different from a mode of calling a first application programming interface, and the first application programming interface is an application programming interface provided by an operating system of the first terminal device for an application; converting the hardware information of each dimension into intermediate data for identifying the hardware information ofthe corresponding dimension; and generating a first device fingerprint for identifying the first terminal device according to the intermediate data obtained by converting the hardware information ofeach dimension. According to the invention, the technical problem that the equipment fingerprint is easy to counterfeit is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
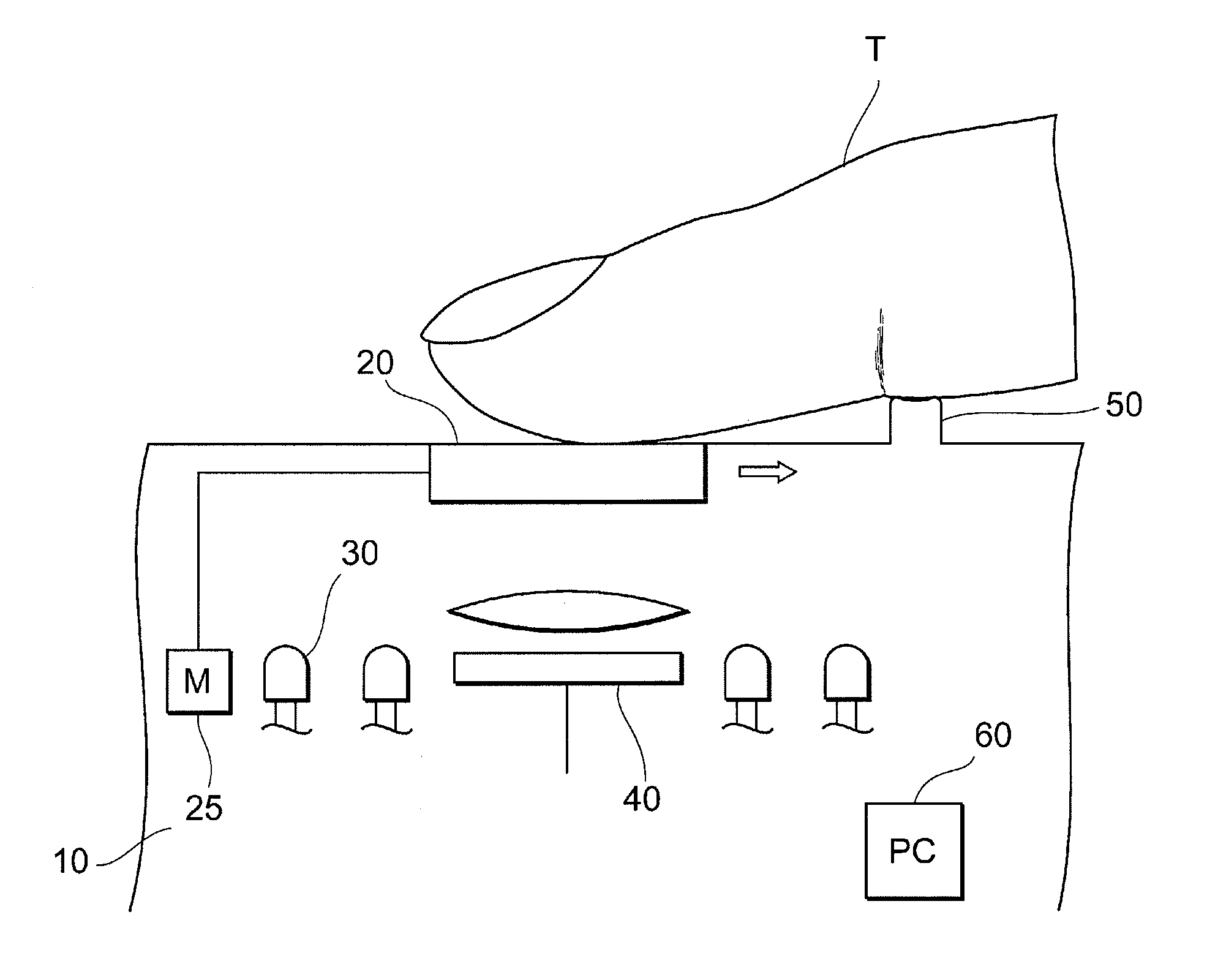
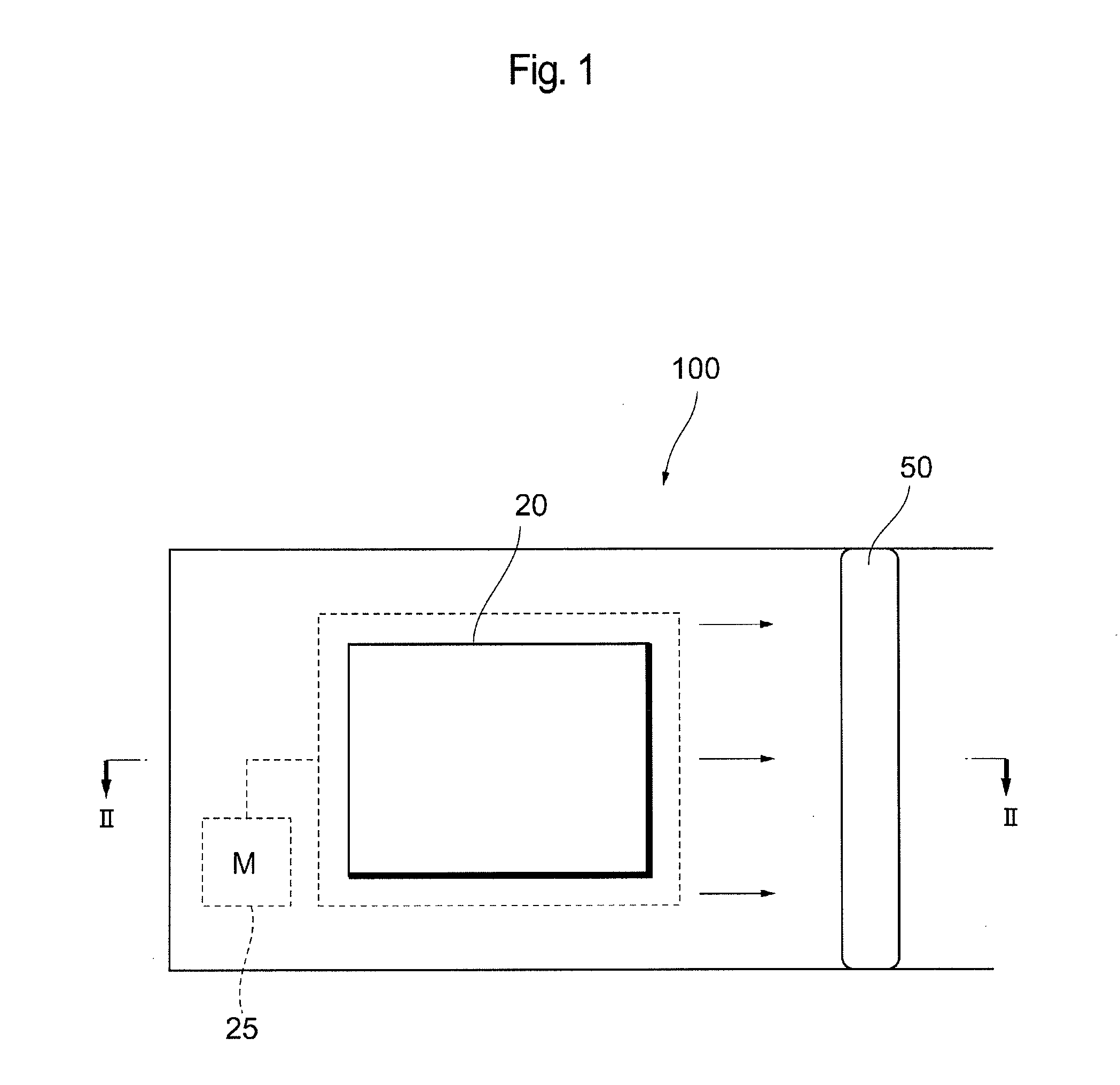
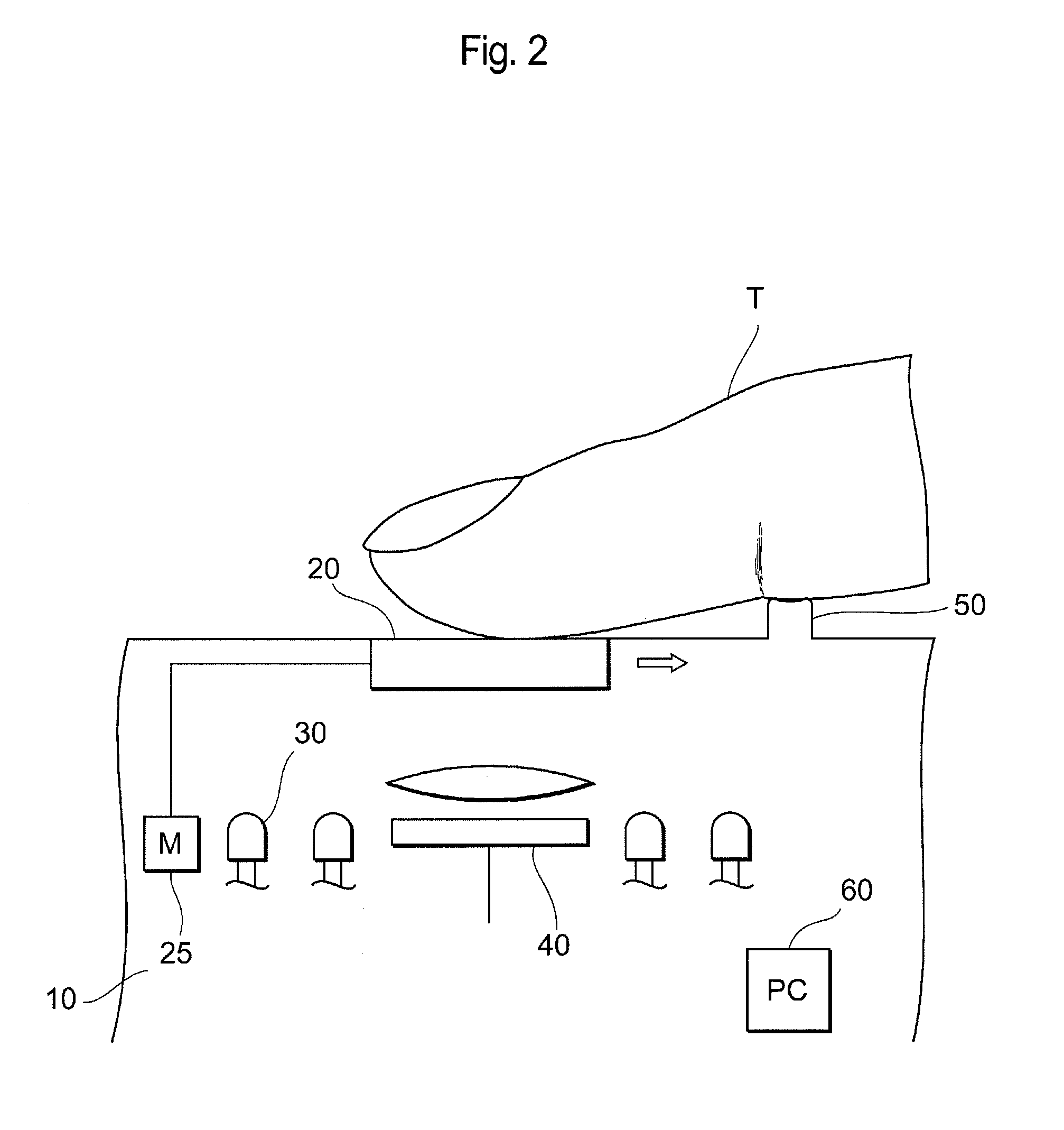
Fake-finger determination device
ActiveUS20120237091A1Improve accuracyImage data processing detailsDetecting live finger characterComputer scienceFingerprint image
Fingerprint images that are required for fake-finger determination can be acquired with a single input operation, and the user-friendliness and the determination accuracy of a fake-finger are improved. This device has moving means for moving a sensor surface, on which a finger as a determination object is placed, relatively to the finger, sensing means for acquiring fingerprint images of the finger before and after the sensor surface is moved, derivation means for obtaining a deformation level of the fingerprint before and after the sensor surface is moved based on two types of fingerprint images obtained by the sensing means, storage means for storing a deformation threshold related to the deformation level of the fingerprint to determine whether the finger on the sensor surface is a real finger or a fake-finger, and determination means for determining whether the finger placed on the sensor surface is a real finger or a fake-finger based on comparison results of the deformation level of the fingerprint obtained by the derivation means and the deformation threshold.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com