Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
136results about How to "Not easy to forge" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
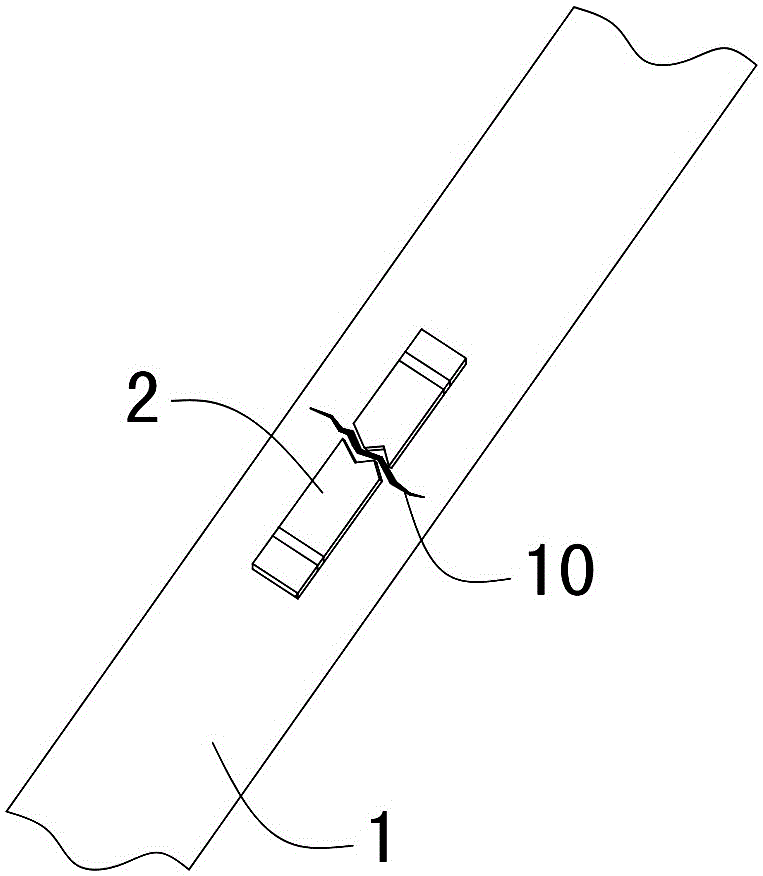
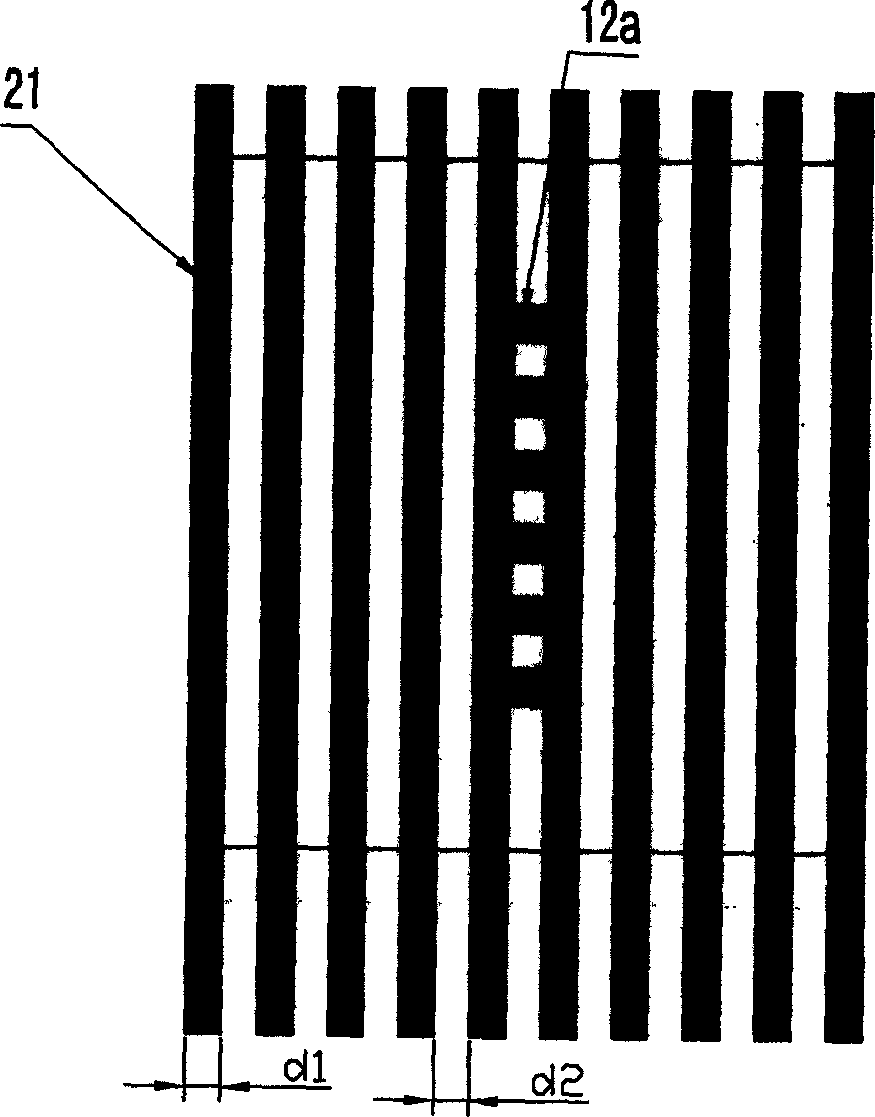
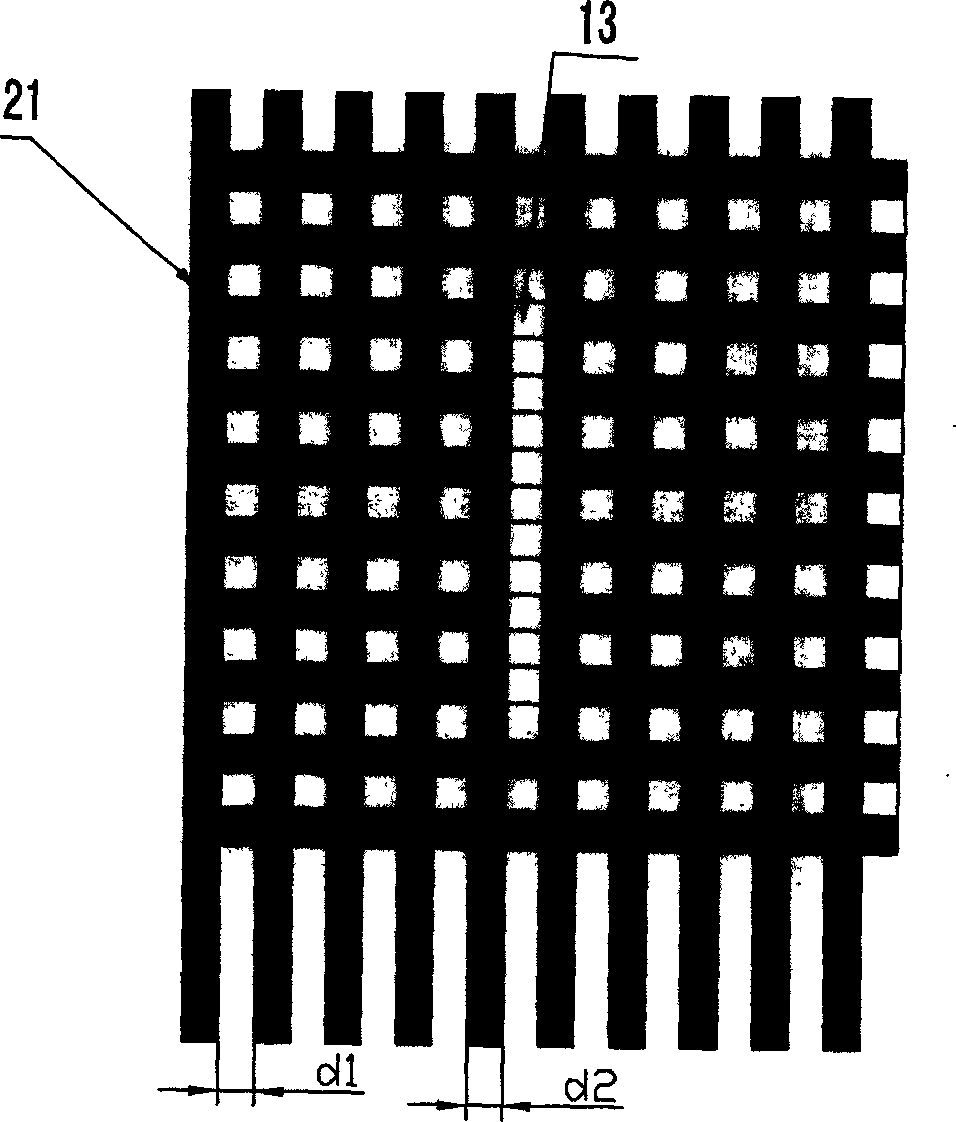
Method for anti false verification based on identification technique in radio frequency, and anti false system
InactiveCN1728162AAdvantage Anti-counterfeitingSecurity advantageKey distribution for secure communicationData processing applicationsLogistics managementValidation methods
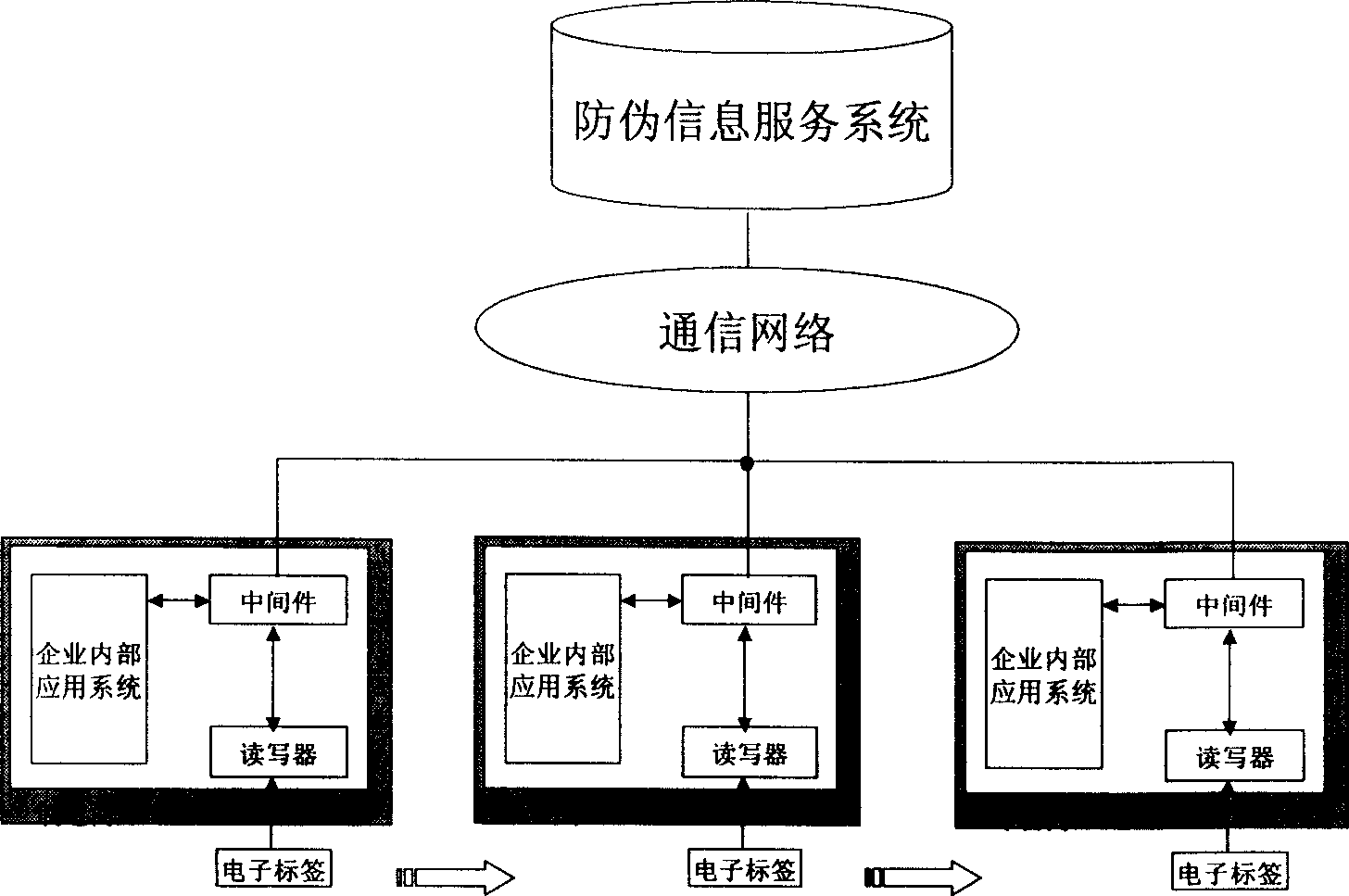
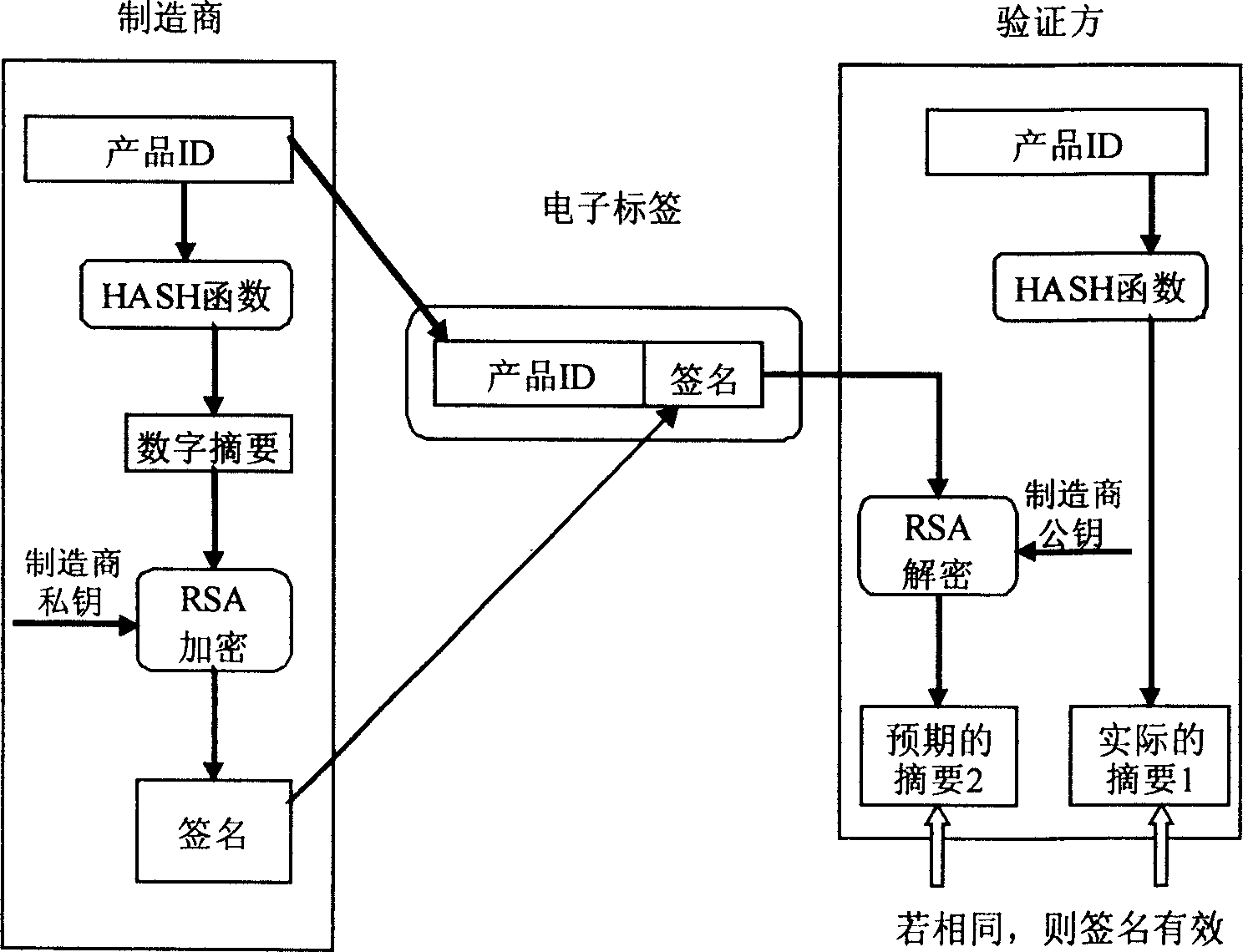
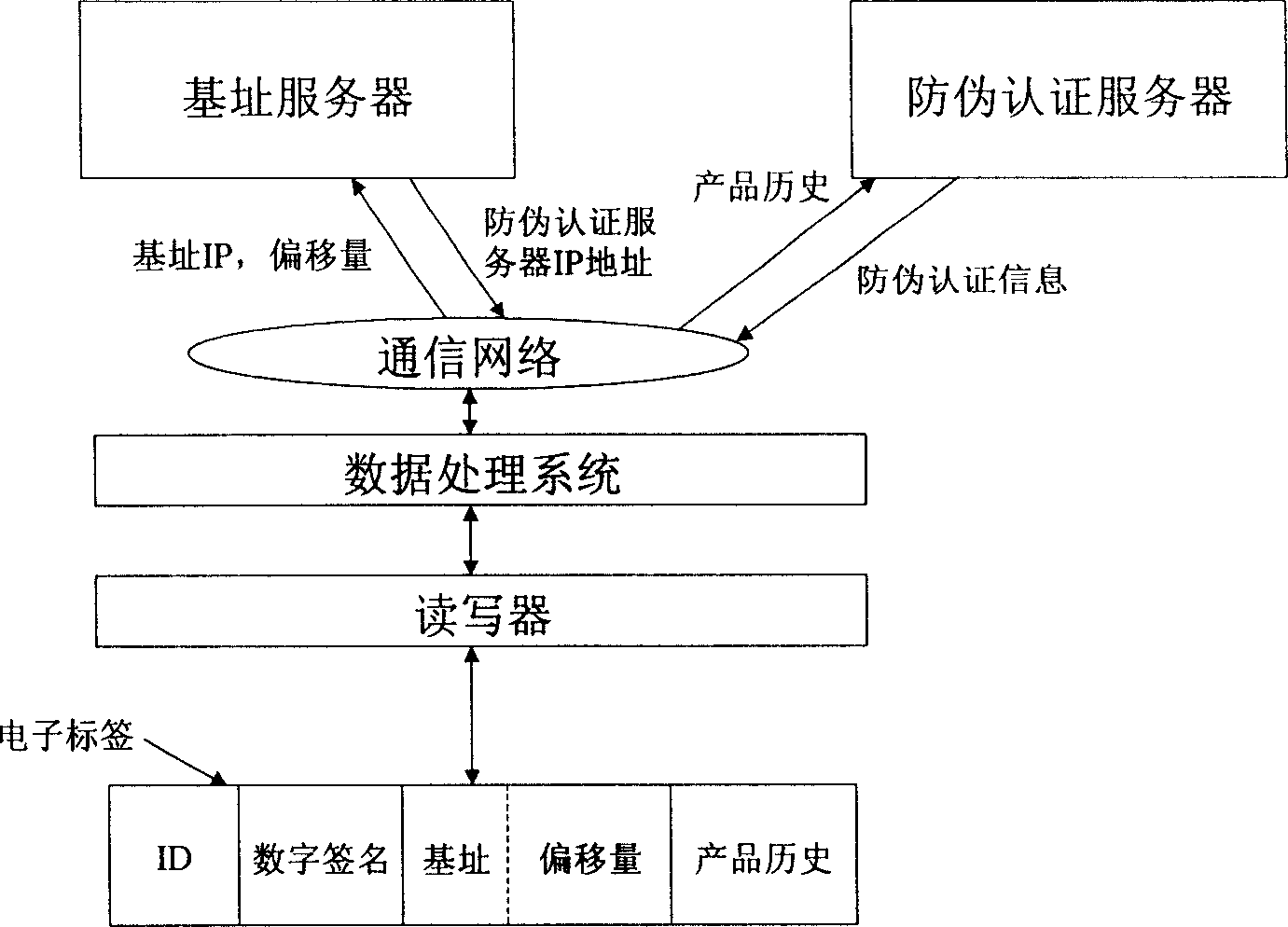
An antifalse system based on radio frequency technology comprises storage with electronic countermark of radio frequency identification, reader / writer and antifalse information service system. The said storage is divided to be four regions of basic information region, digital signature region for storing digital signature generated by ciphering with private key of manufacture, product history region for recording basic data of logistics tracking information, antifalse certifying server address indexing region for storing server address and address offset amount.
Owner:FUDAN UNIV
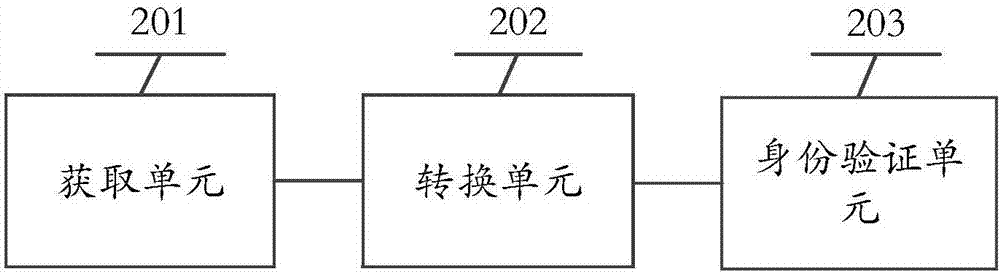
Identity verification method, server and readable storage medium
ActiveCN107483509APrevent malicious callsImprove securityUser identity/authority verificationServer logApplication software
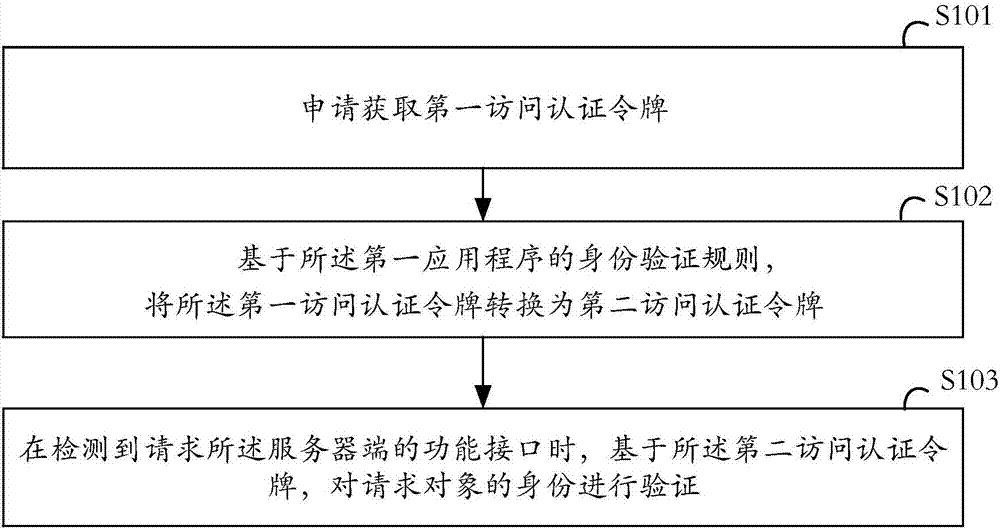
The embodiment of the invention provides an identity verification method, a server and a readable storage medium. The identity verification method is used for preventing a function interface of the server from being called maliciously, and the resource safety of a server-side is improved. The method is applied to the server of a first application program. The method comprises the steps that a first access authentication token is acquired, and the first access authentication token is the access authentication token generated based on a rule corresponding to a second application program when the server logs into the first application program through a small program function of the second application program; based on an identity verification rule of the first application program, the first access authentication token is converted into a second access authentication token; when it is detected that the function interface of the server-side is requested, based on the second access authentication token, an identity of a request object is verified.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
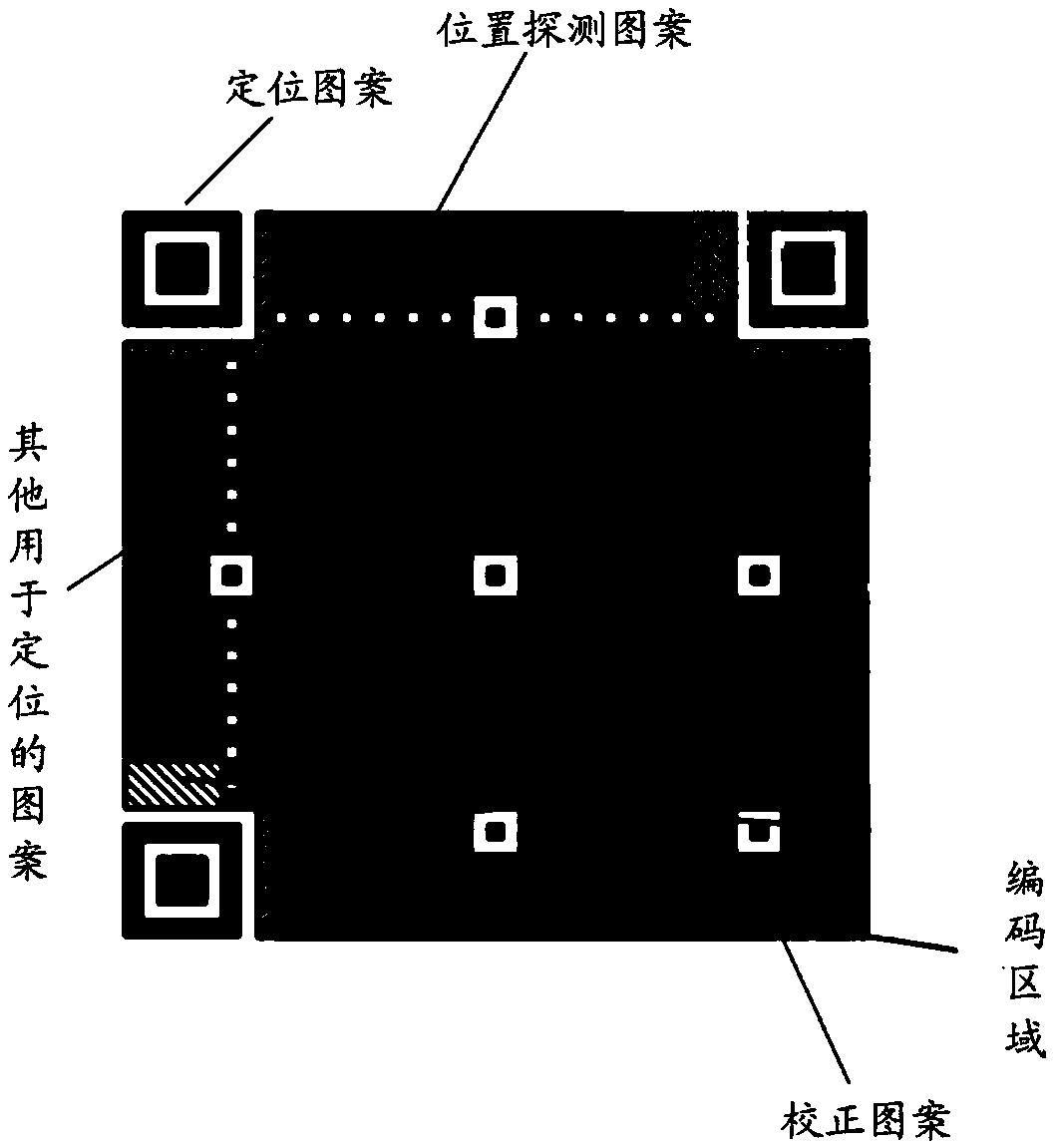
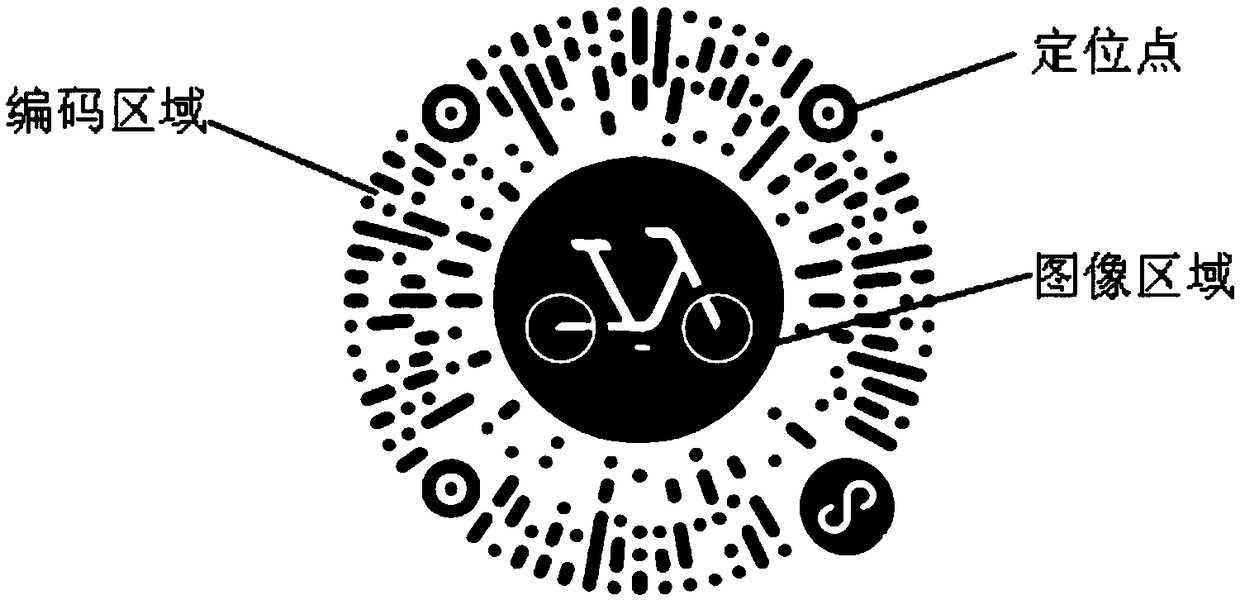
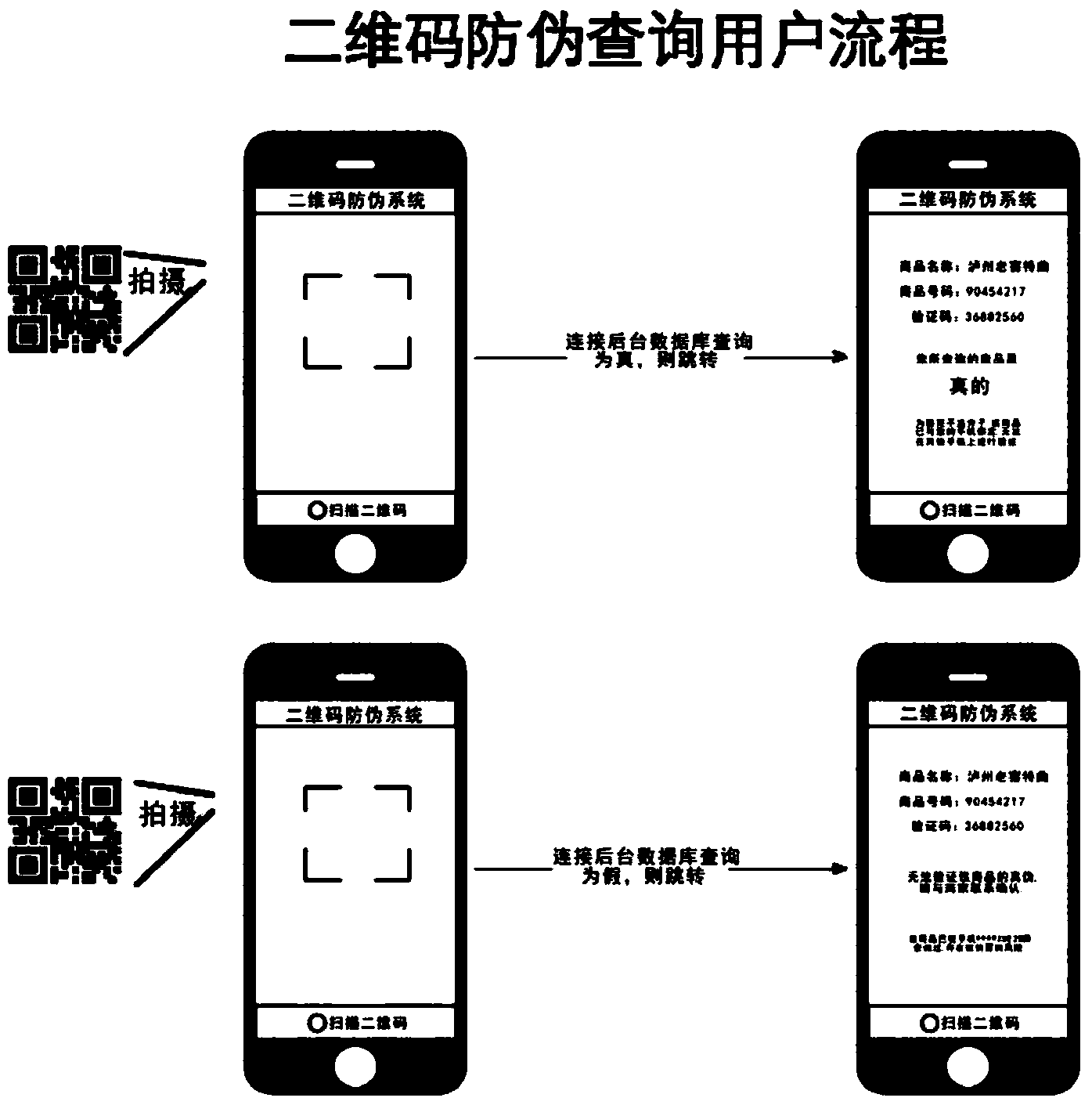
Two-dimensional code, encoding and identification method thereof and product with anti-counterfeiting function
ActiveCN108764420ARich Personalization FeaturesFlexible Personalization FeaturesRecord carriers used with machinesGraphicsDimensional modeling
Owner:CHINA BANKNOTE SECURITY PRINTING TECH RES INST CO LTD +1
Online credit risk assessment method based on long-term using behavior of user
InactiveCN105512938ANot easy to forgeFinanceCharacter and pattern recognitionGeographic siteRisk model
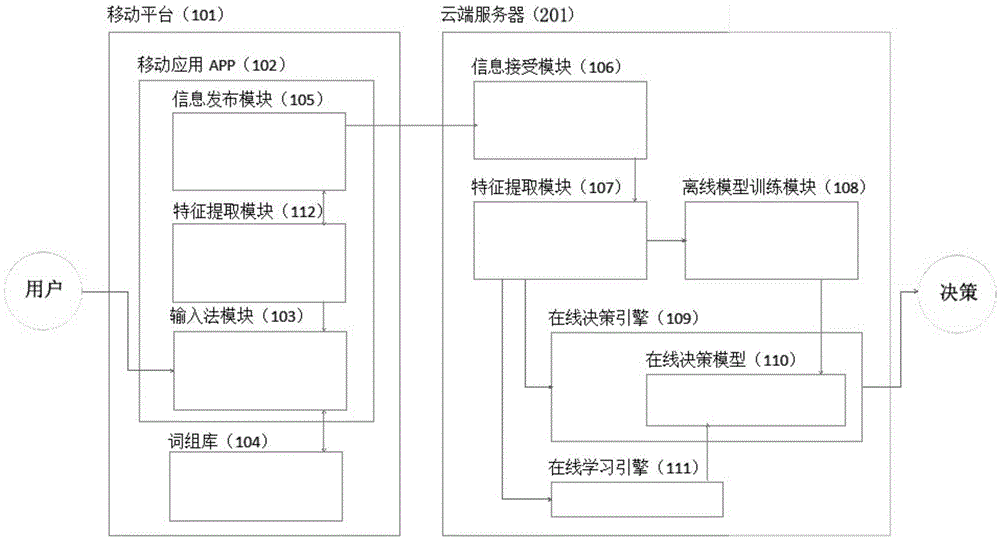
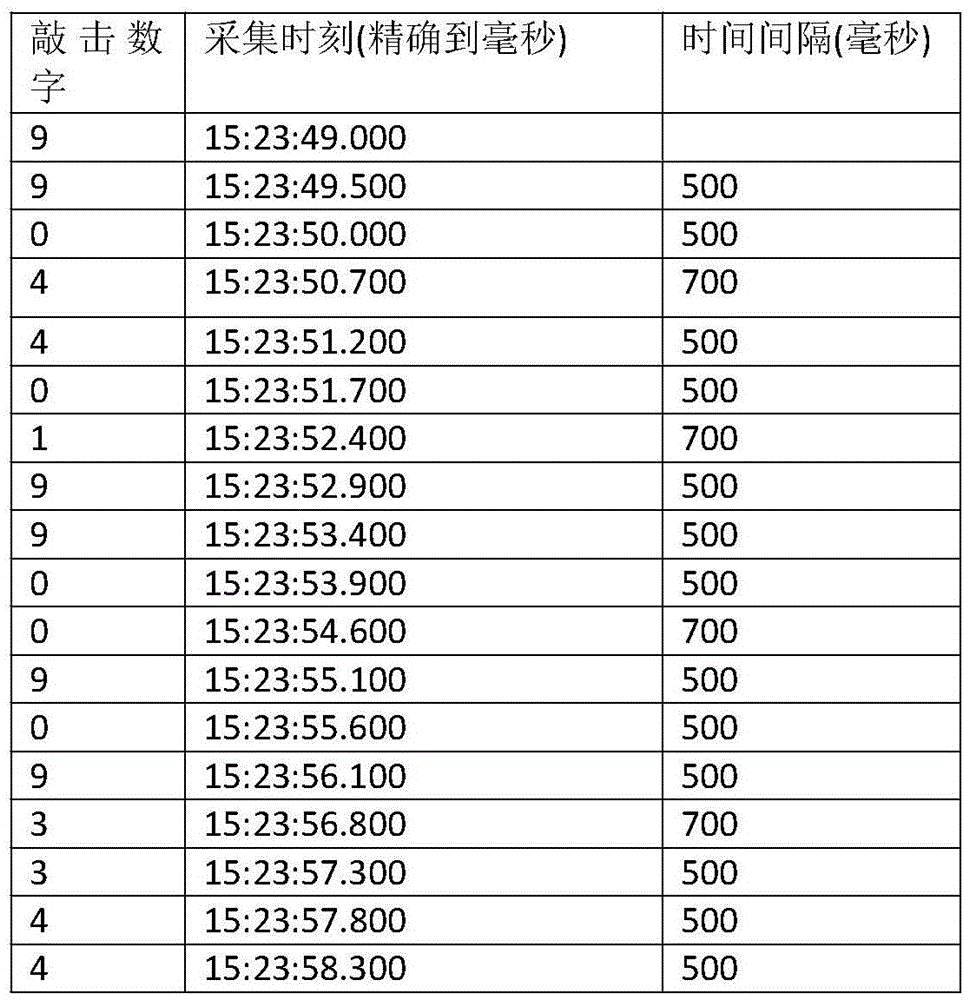
The invention provides an online credit risk assessment method based on the long-term using behavior of a user. The long-term using habit of the user on a mobile application APP is used as an anti-fraud analysis means, effective signals are extracted by acquiring a real-time geographic position, input time, an input method and input hint content which are input by the user when the user fills in a loan application form, and comprise an input method signal, a behavior signal and a phrase selecting signal, then the signals are converted into characteristics, and therefore a decision-making tree or other risk models are utilized to perform classification judgment. On the basis of the original application process, many characteristics can be provided for an anti-fraud algorithm without improving the application complexity degree; the natural using habit of the user is extracted and cannot be faked easily.
Owner:优赛恒创科技发展(北京)有限公司
Face recognition access control method and system based on deep learning
InactiveCN106803301ANot easy to forgeImprove securityCharacter and pattern recognitionIndividual entry/exit registersRecognition algorithmComputer terminal
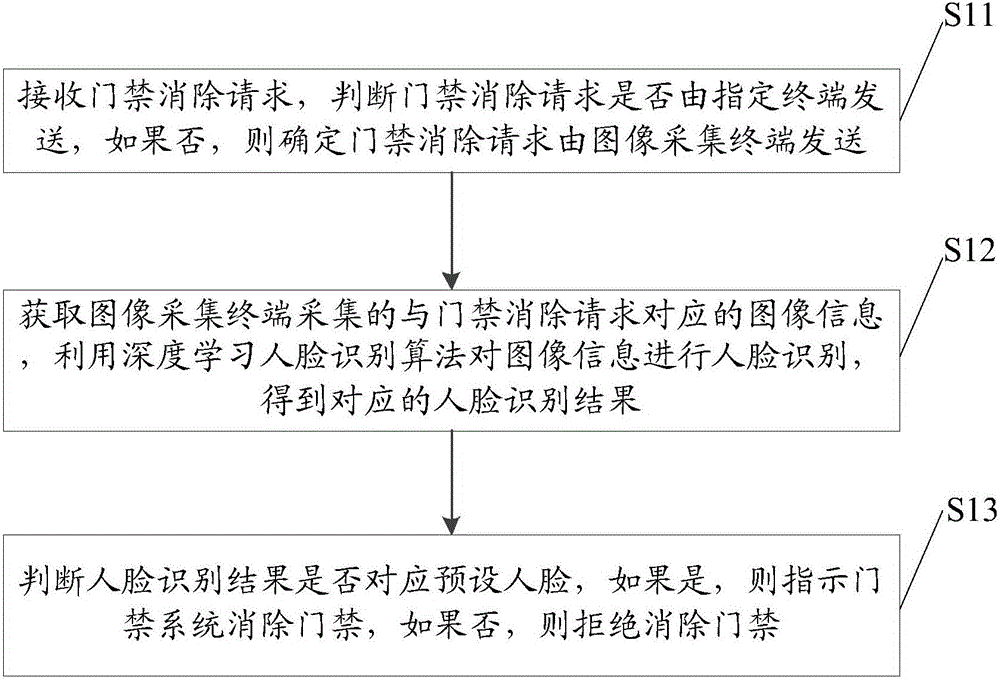
The invention discloses a face recognition access control method and system based on deep learning. The deep learning based face recognition access control method comprises the following steps: receiving an access control cancelling request, judging whether the access control cancelling request is sent by an appointed terminal, and if not, determining that the access control cancelling request is sent by an image acquisition terminal; acquiring image information, corresponding to the access control cancelling request, acquired by the image acquisition terminal, and performing face recognition on the image information by a deep-learning face recognition algorithm to obtain a corresponding face recognition result; judging whether the face recognition result corresponds to a preset face, if so, indicating an access control system to cancel access control, and if not, rejecting access control cancelling. The face can be a unique identity of a person and is not easy to counterfeit, so that according to the invention, the access control system is controlled through the face recognition, and thus the safety of the access control system is greatly improved.
Owner:GUANGDONG UNIV OF TECH
Identification method based on EEG phase synchronization
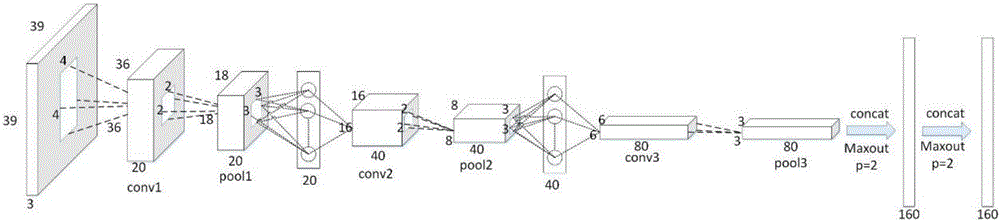
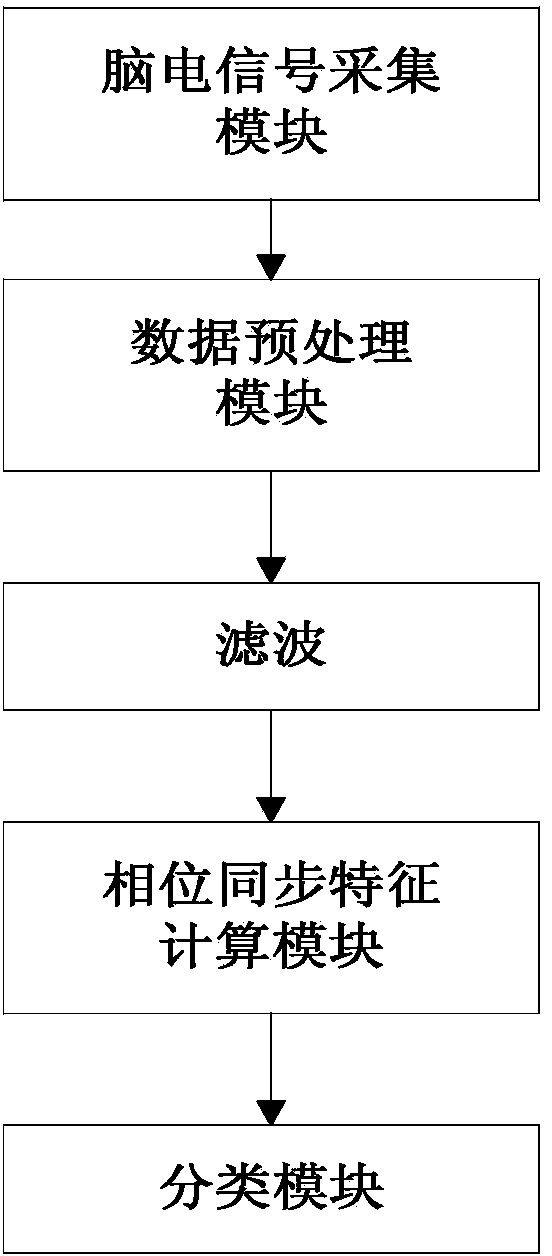
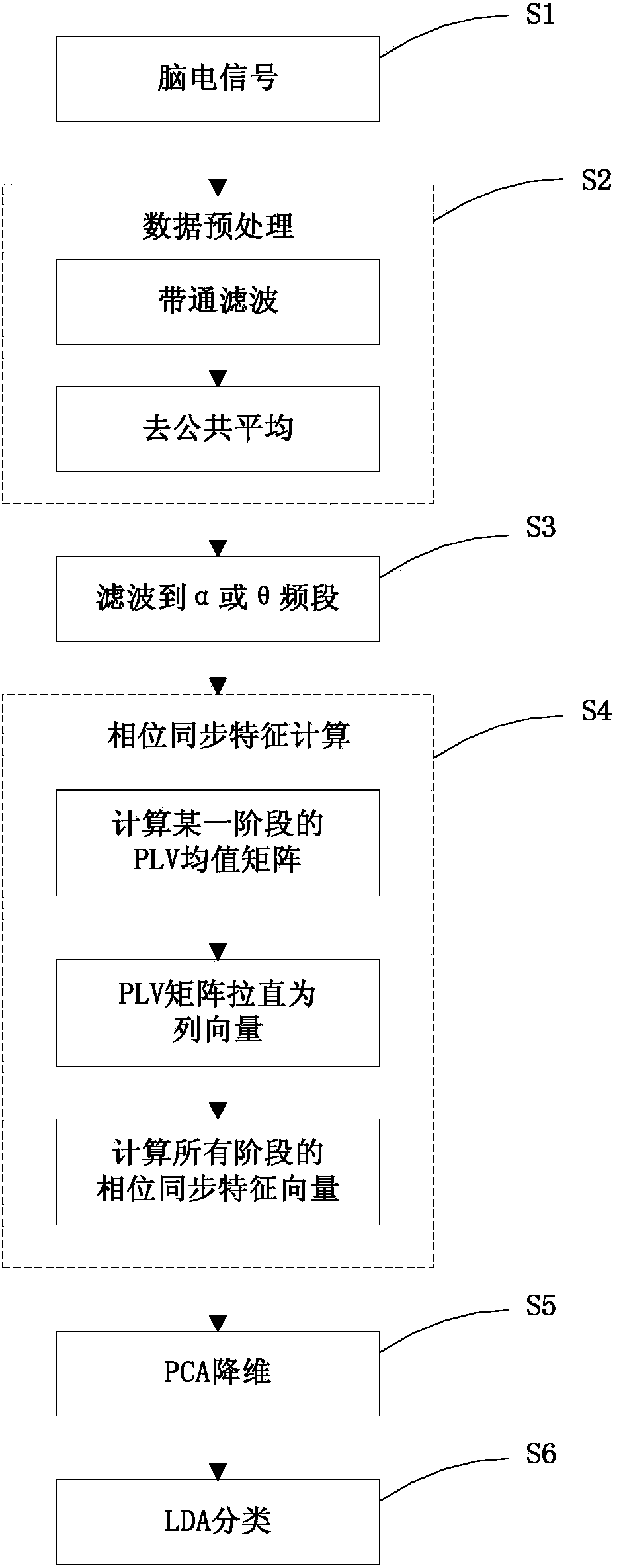
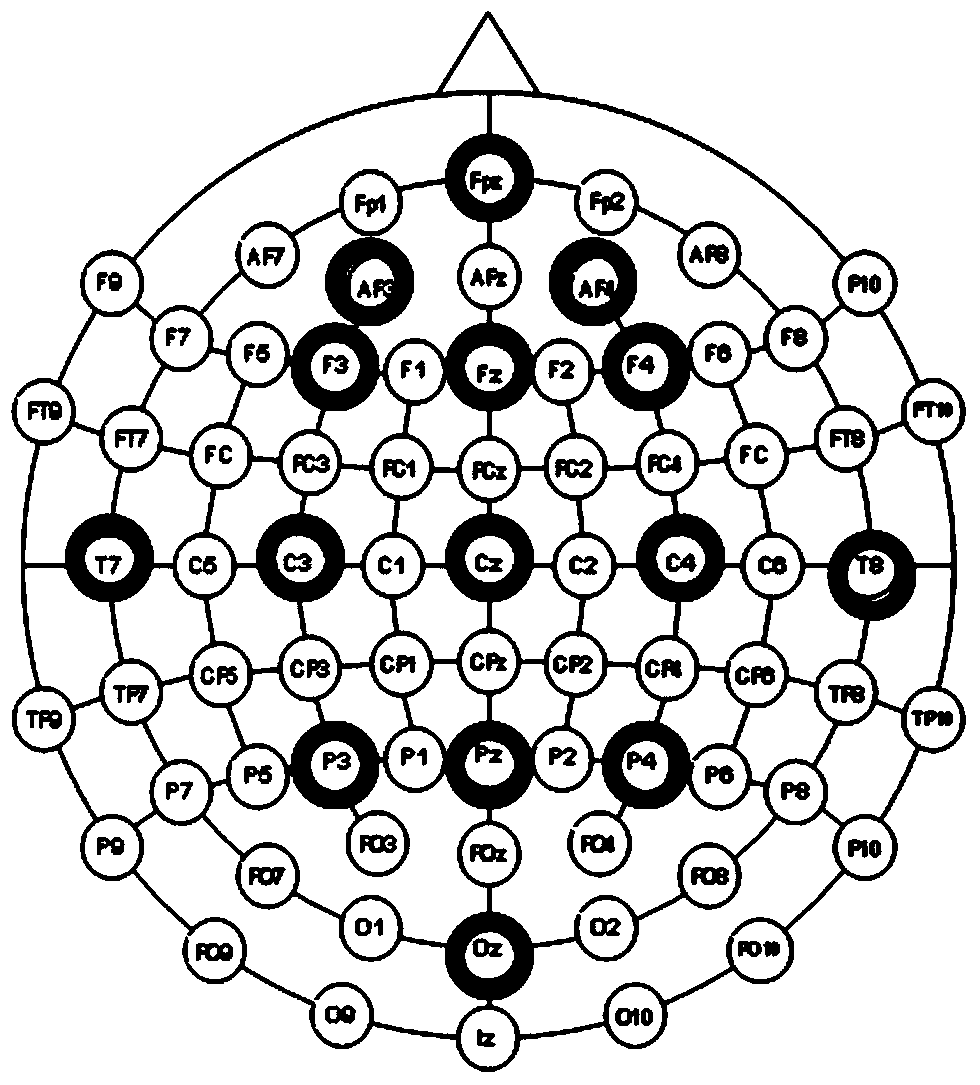
ActiveCN103750844ANot easy to forgeImprove reliabilityPerson identificationSensorsFeature vectorDimensionality reduction
The invention relates to an identification method based on EEG phase synchronization. According to the method, phase synchronization characteristics of EEG are calculated by a phase locking value mainly, and different individuals are identified by means of linear discriminant analysis. The method includes: data collection, data preprocessing, filtering, phase synchronization characteristic calculation, eigenvector dimensionality reduction, eigenvector classification, and classification accuracy calculation. Classification results show that good classification results are obtained by using EEG phase synchronization as biological identification characteristics and different individuals can be effectively identified. Compared with the traditional biological identification characteristics, the EEG phase synchronization characteristics provide better safety and imperceptibility, and the method is applicable to certain persons with physical disabilities or injuries.
Owner:HANGZHOU DIANZI UNIV
Full-circulation type two-dimensional code anti-counterfeiting system and realization method thereof
ActiveCN104992335AAchieve non-reproducibilityWell-thought-outCommerceSensing by electromagnetic radiationLibrary scienceIndustrial engineering
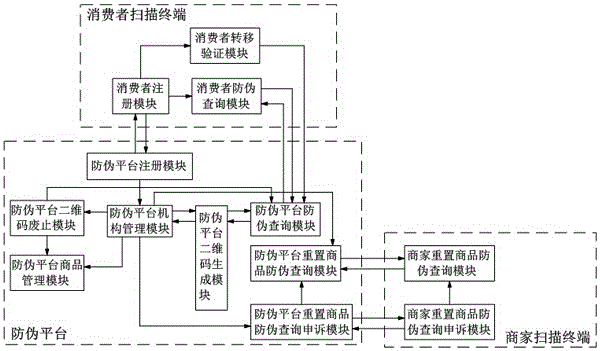
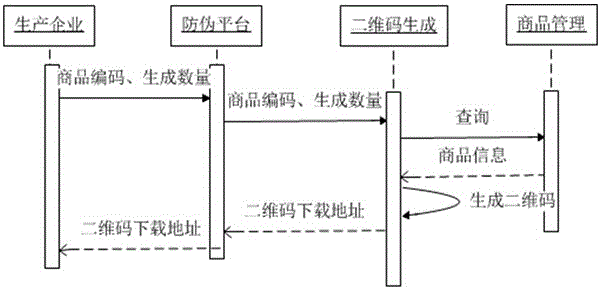
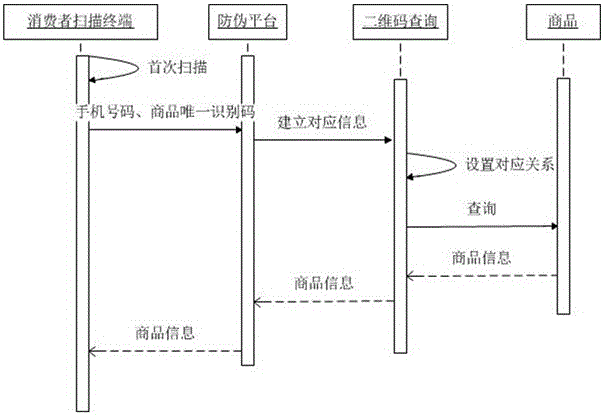
The invention discloses a full-circulation type two-dimensional code anti-counterfeiting system and a realization method thereof. The system comprises an anti-counterfeiting platform, a consumer scanning terminal and a trade company scanning terminal. The anti-counterfeiting platform comprises an anti-counterfeiting platform registration module, an anti-counterfeiting platform mechanism management module, an anti-counterfeiting platform two-dimensional code generation module, an anti-counterfeiting platform anti-counterfeiting query module and an anti-counterfeiting replaced goods anti-counterfeiting query module. The consumer scanning terminal comprises a consumer registration module, a consumer anti-counterfeiting query module and a consumer transfer verification module. The trade company scanning terminal comprises a trade company replaced goods anti-counterfeiting query module. According to the invention, through mutual association and cooperation of each subsystem, an anti-counterfeiting cycle from registration of the anti-counterfeiting platform by production enterprises and trade companies, generation of goods two-dimensional codes and replaced goods anti-counterfeiting queries of the trade companies to verification of the authenticity of goods by consumers and assignees through scanning the two-dimensional codes is realized, the two-dimensional codes can be effectively prohibited from modifications and forgeries, the benefits of the production enterprises, the trade companies and the consumers are protected, and the goods can also be well circulated.
Owner:刘洋
Intelligent warehouse goods management method based on RFID technology
InactiveCN102426682AObvious advantagesImprove work efficiencyCo-operative working arrangementsLogisticsDatabase serverData memory
The invention provides an intelligent warehouse goods management method based on a RFID (Radio Frequency Identification) technology. The method is characterized by comprising the following steps of: firstly, respectively implanting a RFID tag for each goods, registering different ID for each RFID tag, and allocating storage space for each ID in a database server; then, reading the RFID tag on each goods through a mobile RFID reader while registering the goods for storage, storing the goods, registering the goods for delivery and packing the goods; obtaining the ID of the RFID tag, inputting related information of the goods; and transmitting the data to the database server through a management system for storage. The method has the advantages of: (1) quick scanning; (2) excellent penetrability and barrier-free reading; (3) strong contamination resistance and durability; (4) large data memory capacity; (5) miniaturized volume and diversified shape; (6) excellent reusable property; (7) high security.
Owner:SHANGHAI GAOCHENG CREATIVE TECH GRP
Anti-counterfeit label and anti-counterfeit method based on combination of two-dimension codes and RFID chips
ActiveCN104166871AAnti-counterfeiting advantageGood anti-counterfeiting featuresRecord carriers used with machinesDigital signaturePassword
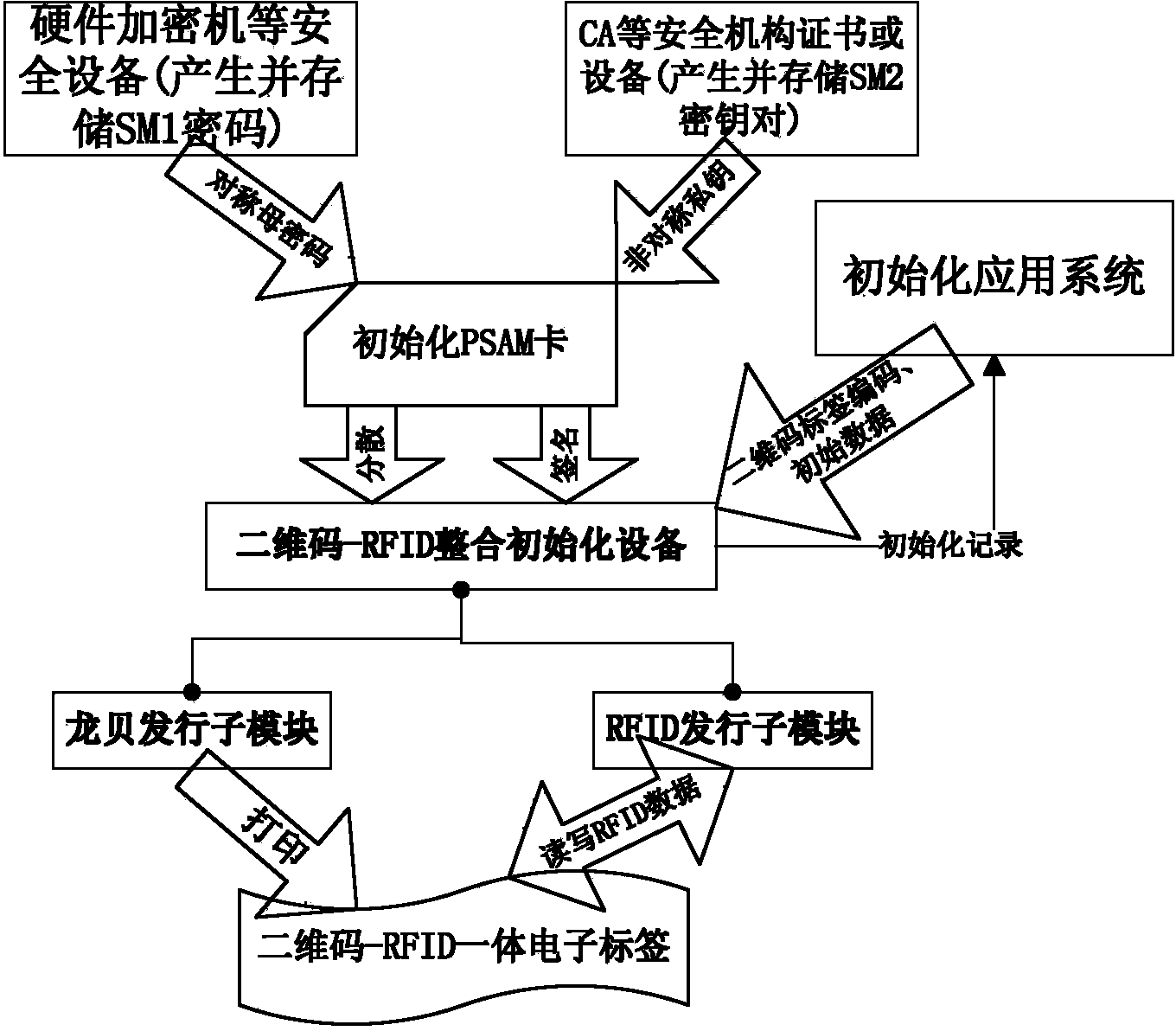
The invention relates to an anti-counterfeit label based on the combination of two-dimension codes and RFID chips. The data area of the two-dimension codes and the data area of the RFID chips are respectively divided into a non-secrecy zone and a secrecy zone, each secrecy zone is divided into multiple secrecy zone bodies, two-dimension code label codes are stored in the non-secrecy zone of the two-dimension codes, and the secrecy zone of the two-dimension codes is divided into a first two-dimension code secrecy zone body for storing protected data needed by a user; RFID label codes are stored in the non-secrecy zone of the RFID chips, and the secrecy zone of the RFID chips is divided into the RFID user secrecy zone body and the RFID password secrecy zone body; in the verification process, access to the RFID password secrecy zone body is achieved firstly to obtain a decoding password of the two-dimension code secrecy zone body, the needed data are obtained from the two-dimension codes, the data, including a digital signature, of the RFID user secrecy zone body are read, the digital signature is regenerated, and two digital digests are verified to finally obtain a result whether to be true or counterfeit or a result whether to be legal or illegal. The defects of a traditional anti-counterfeit technology can be overcome well, and the anti-counterfeit label is difficult to counterfeit.
Owner:SHANGHAI QUANRAY ELECTRONICS
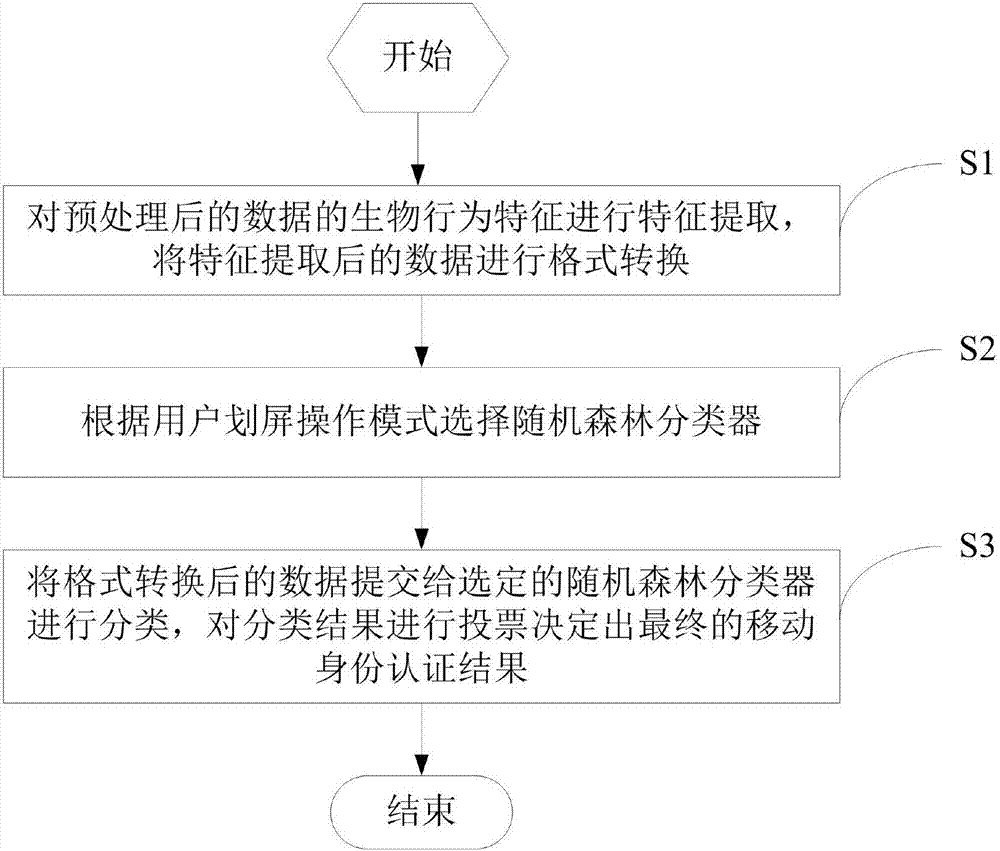
Mobile identity authentication method and system based on screen-sliding habit of user
InactiveCN107194216ANot easy to forgeNo risk of leakageCharacter and pattern recognitionDigital data authenticationClassification resultFeature extraction
The invention discloses a mobile identity authentication method and system based on screen-sliding habit of a user. The method comprises the following steps: S1, carrying out feature extraction on biological behavior features of data after pre-processing, and carrying out format conversion on data after the feature extraction; S2, selecting a random forest classifier according to screen-sliding operation modes of the user; and S3, submitting data after the format conversion to the selected random forest classifier for classification, and carrying out voting on classification results to determine a final mobile identity authentication result. The system of the invention corresponds to the above-mentioned method. The method and system have the characteristics of being able to easily cope with an identity authentication requirement under free screen-sliding operation modes, a high classification accuracy rate and the like.
Owner:CENT SOUTH UNIV
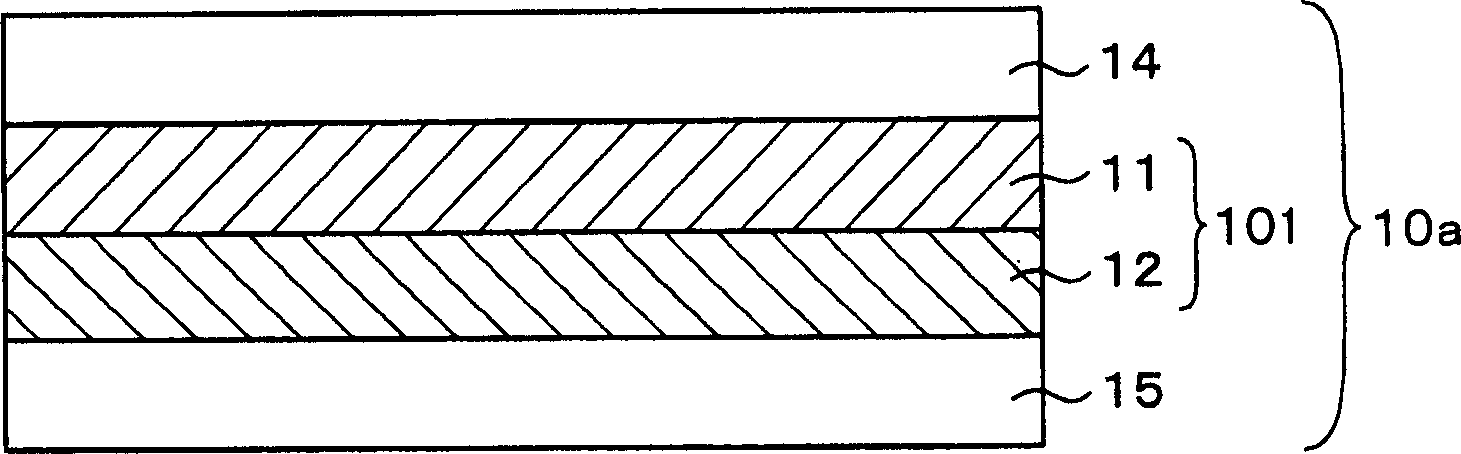
Object identification medium and identification method
ActiveCN1791816AEasy and reliable to identifyNot easy to forgeOther printing matterHolographic light sources/light beam propertiesCholesterolLiquid crystal
The identification medium (10a) has a right-handed circularly polarizing polymer cholesteric liquid crystal layer (11) that reflects specific right-handed circularly polarized light and a left-handed circularly polarized layer (11) that reflects specific left-handed circularly polarized light. A first two-layer body (101) in which cholesteric polymer liquid crystal layers (12) are stacked on each other. The identification medium (10a) is attached on the target object (30). ) when the simple judging device (20) is visually inspected, the color of the right-handed circularly polarizing polymer cholesteric liquid crystal layer (11) can be seen on the right-handed circularly polarizing filter (21) side, and the color of the left-handed circularly polarized One side of the optical filter (22) can see the color of the left-handed circularly polarized polymer cholesteric liquid crystal layer (12). This makes it possible to simply and reliably identify the authenticity of the target object (30) by confirming a special phenomenon produced by the identification medium (10a) which cannot normally be reproduced.
Owner:NHK SPRING CO LTD
Intelligent warehouse cargo management method adopting RFID technology
InactiveCN103761631AObvious advantagesImprove work efficiencyCo-operative working arrangementsLogisticsDatabase serverReusability
The invention provides an intelligent warehouse cargo management method adopting an RFID technology. The method is characterized in that steps are: firstly, implanting an RFID label for each cargo respectively, registering a different ID for each RFID label and distributing a storage space for each ID in a database server; then both after the cargos undergo warehousing registration and warehousing, and when the cargos are undergoing ex-warehouse registration and cargo packing, adopting a mobile RFID reader-writer to read the RFID label on each cargo and obtaining the IDs of the RFIDs and inputting related information of the cargos and sending the data to the database server for storage through a management system. The advantages of the intelligent warehouse cargo management method adopting the RFID technology are: (1): rapid scanning; (2) penetrability and no-screen reading; (3) anti-pollution capability and durability; (4) large memory capacity of the data; (5) volume miniaturization and shape diversification; (6) reusability; (7) security.
Owner:TIANJIN CHUANSHI TECH
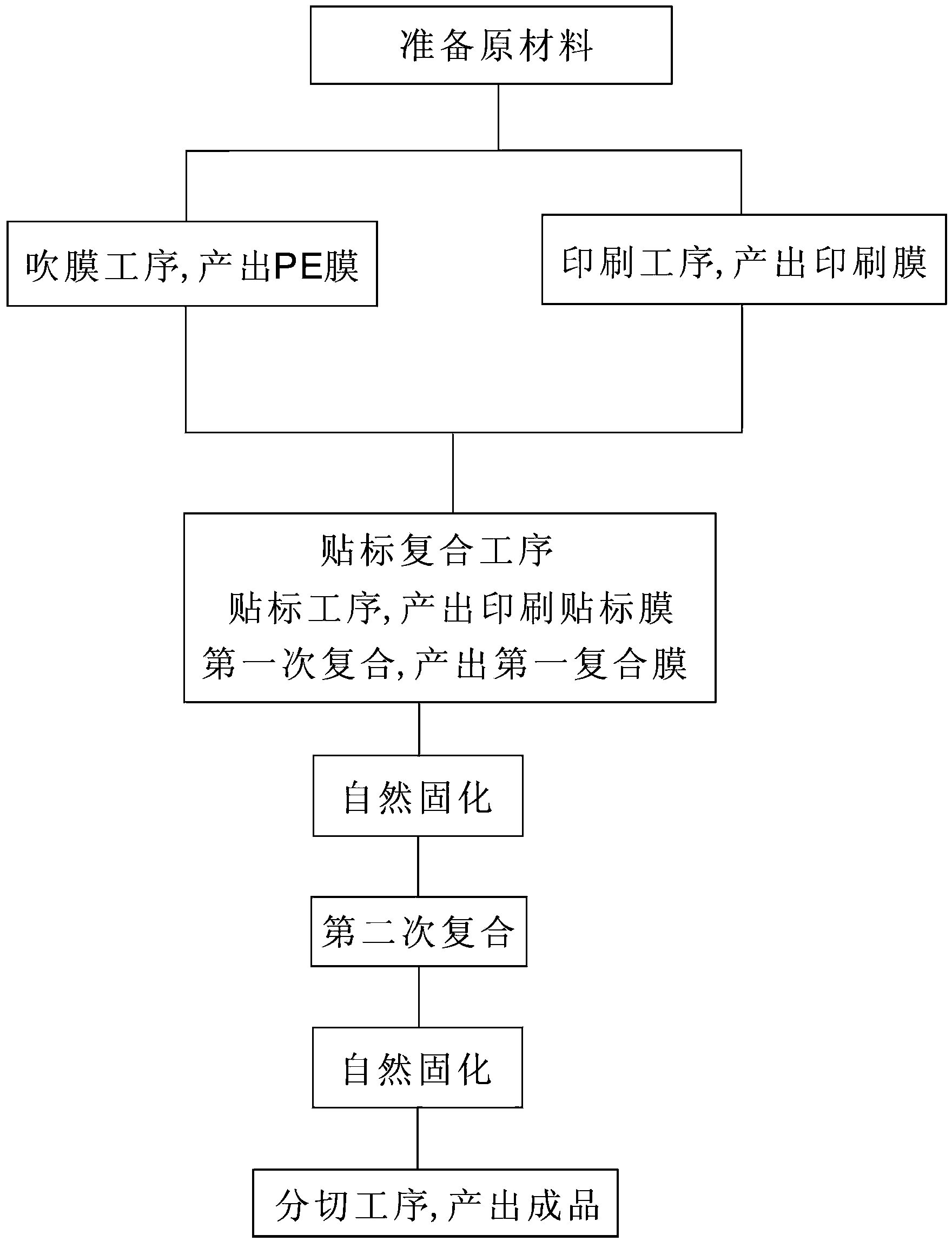
Manufacturing method of paper-plastic composite packaging bag
ActiveCN103407674AStrong anti-counterfeiting functionNot easy to forgeLabelling deformable materialsLamination ancillary operationsMolded pulpComposite film
The invention provides a manufacturing method of a paper-plastic composite packaging bag. The manufacturing method sequentially comprises steps as follows: (1) raw materials are prepared; (2) a film blowing procedure is performed, and a PE (polyethylene) film is produced by resin particles through the film blowing procedure; (3) a printing procedure is performed, and a printing film is produced by a substrate film through the printing procedure; (4) labelling and composition procedures are performed and comprise a labelling procedure, a first composition procedure and a second composition procedure, a labelling film is produced on the printing film through the labelling procedure to form a printing and labelling film, then, first composition of industrial printing paper and the PE film is performed through the first composition procedure, second composition of the printing and labelling film and a first composite film is performed after spontaneous curing of the first composition, and spontaneous curing is performed after the second composition; and (5) a slitting procedure is performed, the spontaneously cured product is slit through the slitting procedure, and a finished product is put in storage. The manufacturing method is simple in technique, the anti-fake capacity is higher, the solvent-free composition strength is high, and the product is environment-friendly.
Owner:HUBEI YUNHE SALT IND PACKAGE
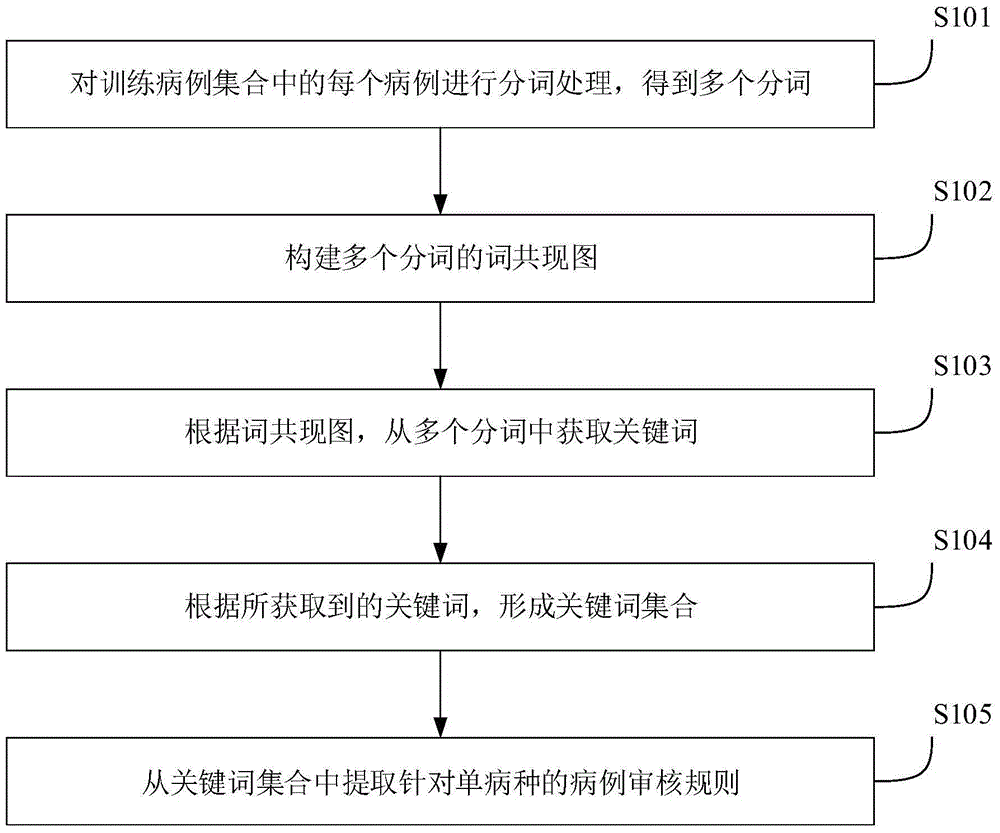
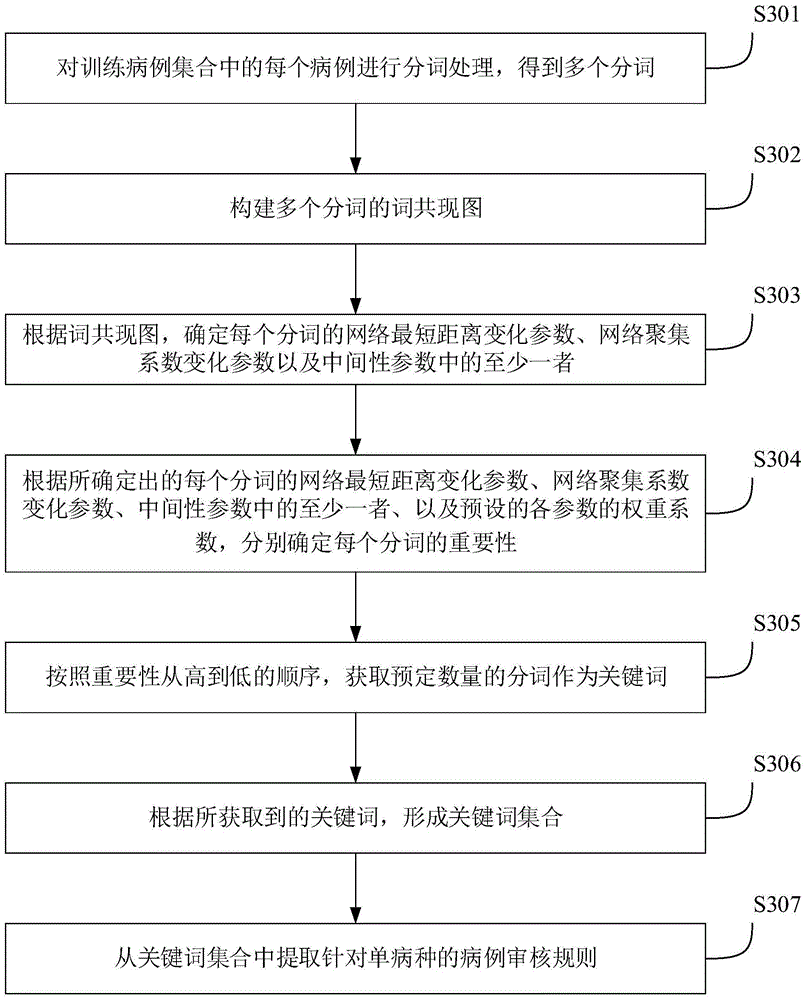
Extracting method and apparatus for case auditing rule, and case auditing method and system
ActiveCN105224807AImprove accuracyEfficient use ofSpecial data processing applicationsMachine learningCo-occurrence
The invention discloses an extracting method and apparatus for a case auditing rule of a single disease, and a case auditing method and system for the single disease. The extracting method comprises the steps of performing word segment processing on each case of a training case set to obtain a plurality of segmented words, wherein the training case set comprises a plurality of cases belonging to preset single disease; establishing a word co-occurrence graph with multiple segmented words, wherein each segmented word is used as a top point of the word co-occurrence graph, and the weight of the side boundary between two top points is the co-occurrence time of the segmented word, corresponding to the two top points, in the training case set; obtaining key words from the multiple segmented words according to the word co-occurrence graph; forming a key word set according to the obtained key words; and extracting the case auditing rule specific to the single disease from the key word set, wherein the case auditing rule is a sequential key word sequence formed by the multiple key words from the key word set. Therefore, the case auditing rule for the single disease can be extracted for realizing the automatic auditing for cases of the single disease.
Owner:NEUSOFT CORP
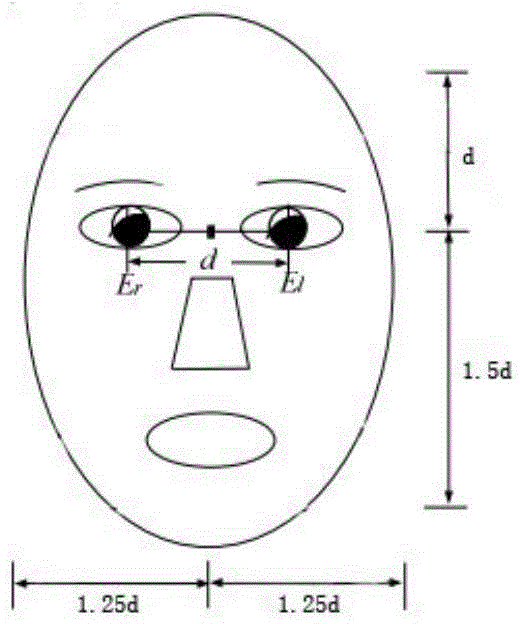
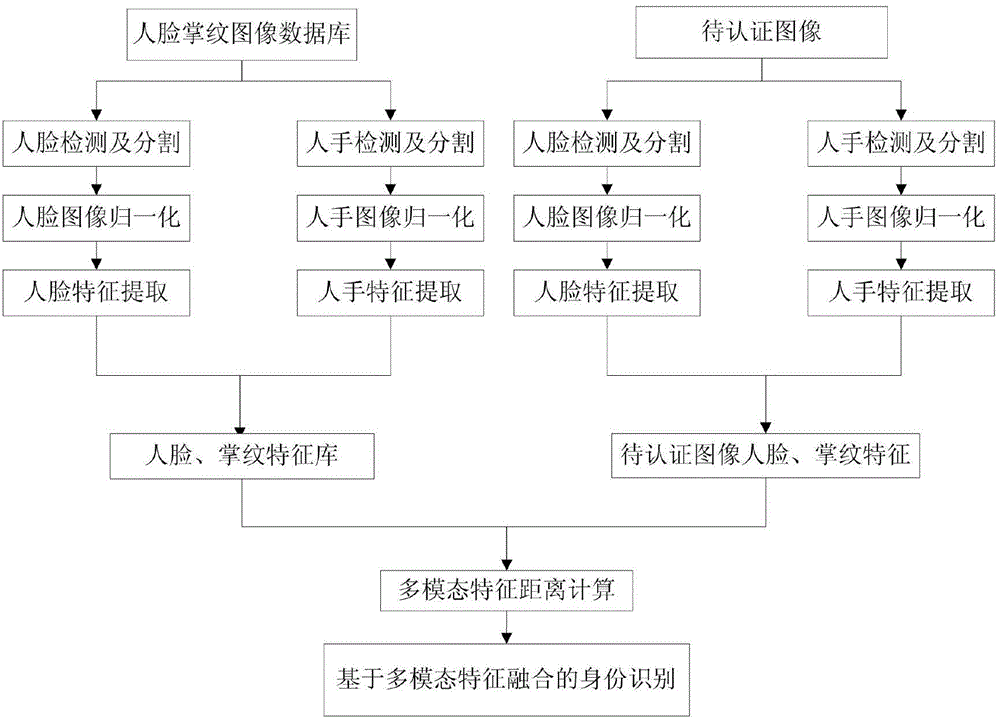
Identity recognition method based on fusion of face characteristic and palm print characteristic
ActiveCN104680154AImprove securityNot easy to forgeCharacter and pattern recognitionPalm printIdentity recognition
The invention discloses an identity recognition method based on multi-mode fusion of face characteristics and palm print characteristics of a single image. The identity recognition method is characterized by comprising the following steps: 1, acquiring the face and the palm print of one same person in one image, and establishing a database; 2, respectively detecting and partitioning face areas and palm print areas of the image, thereby obtaining ROI areas; 3, respectively calculating and authenticating chi-square distance of face characteristics and palm print characteristics of an authenticated image and each image in the database according to a face recognition algorithm and a palm print recognition algorithm; 4, fusing two characteristic distances according to a multi-mode characteristic fusion algorithm, thereby achieving identity recognition of persons. As the face characteristics and the palm print characteristics are fused, the accuracy rate of identity recognition is increased.
Owner:HEFEI UNIV OF TECH
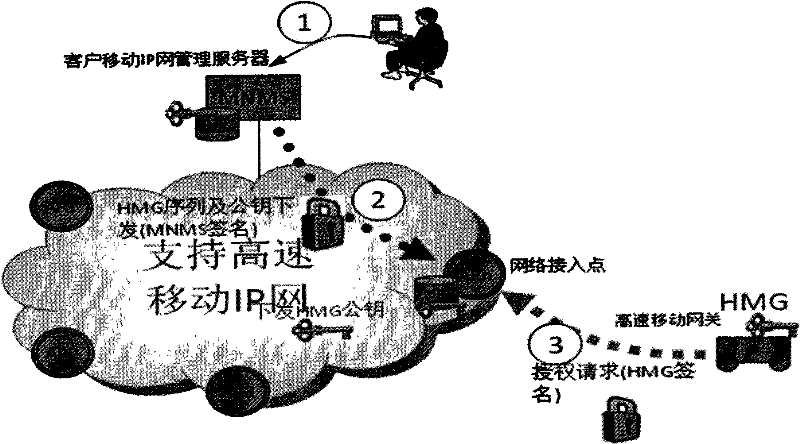
Security certification method, system and equipment for internet access
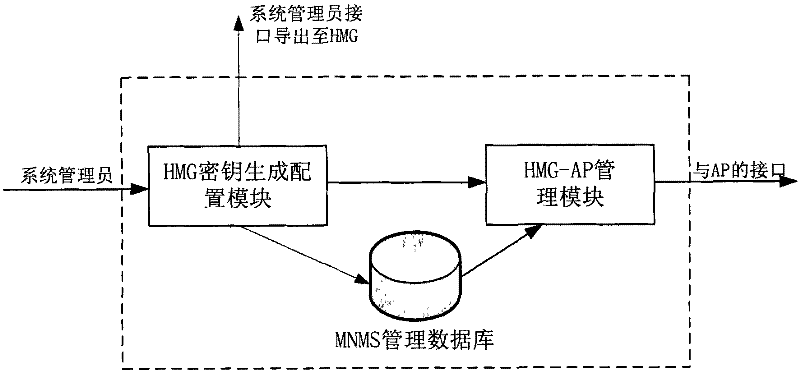
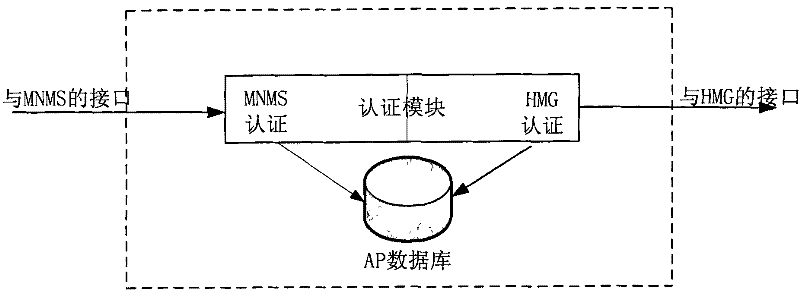
ActiveCN102546523AEasy accessMove quicklyUser identity/authority verificationInternet accessNetwork management
The invention discloses a security certification method, a system and equipment for internet access, which is applied in high-speed traffic tools. The security certification method comprises the following steps: a MNMS (mobile-customer IP network management server) generates a public key and a private key for each HMG (high-speed mobile gate); the public key is issued to an AP (access point); each private key is issued to the corresponding HMG; the MNMS generates a first signature for related information of the HMG by using the private key and the AP, and issues the generated first signature and the related information of the AP for the HMG to the corresponding AP; the AP carries out certification on the first signature in the issued information by using the public key, if the certification is passed, the related information in the information is extracted for storage, and a broadcast notice is sent to a coverage range; the HMG judges whether the AP is legally accessed, if so, the HMG utilizes the private key and the AP to generate a second signature for the related information of the HMG, and sends a certification request containing the second signature and the HMG identification to the broadcast AP; and the AP carries out certification on the second signature in the certification request by using the public key.
Owner:CHINA TELECOM CORP LTD
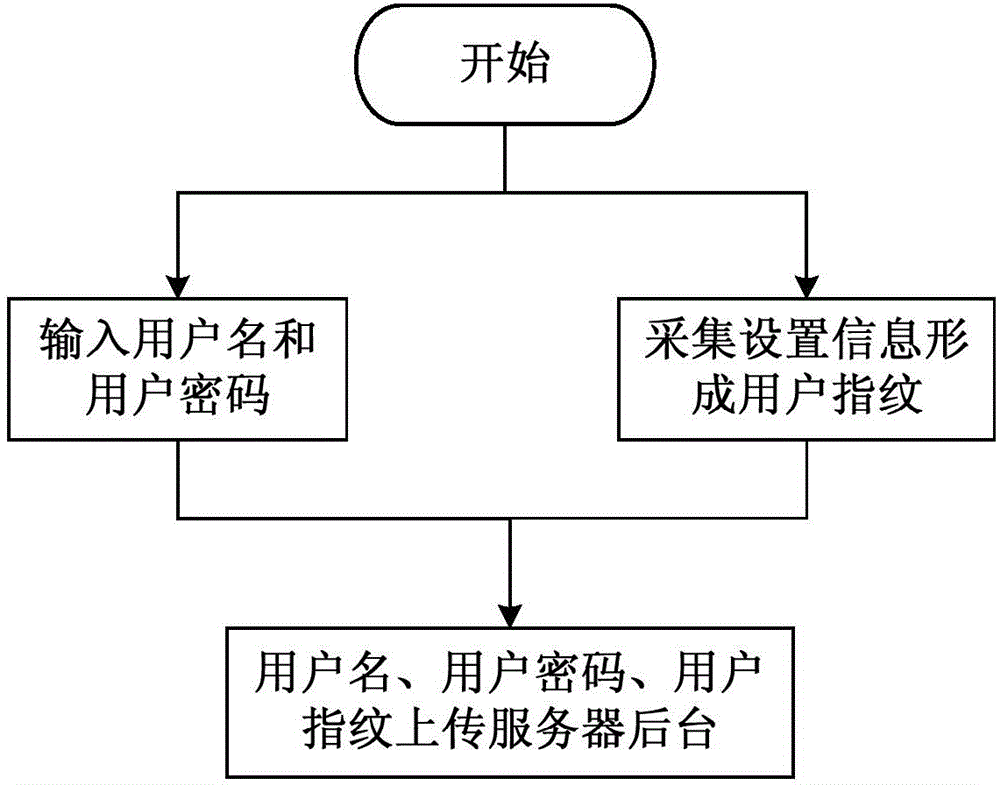
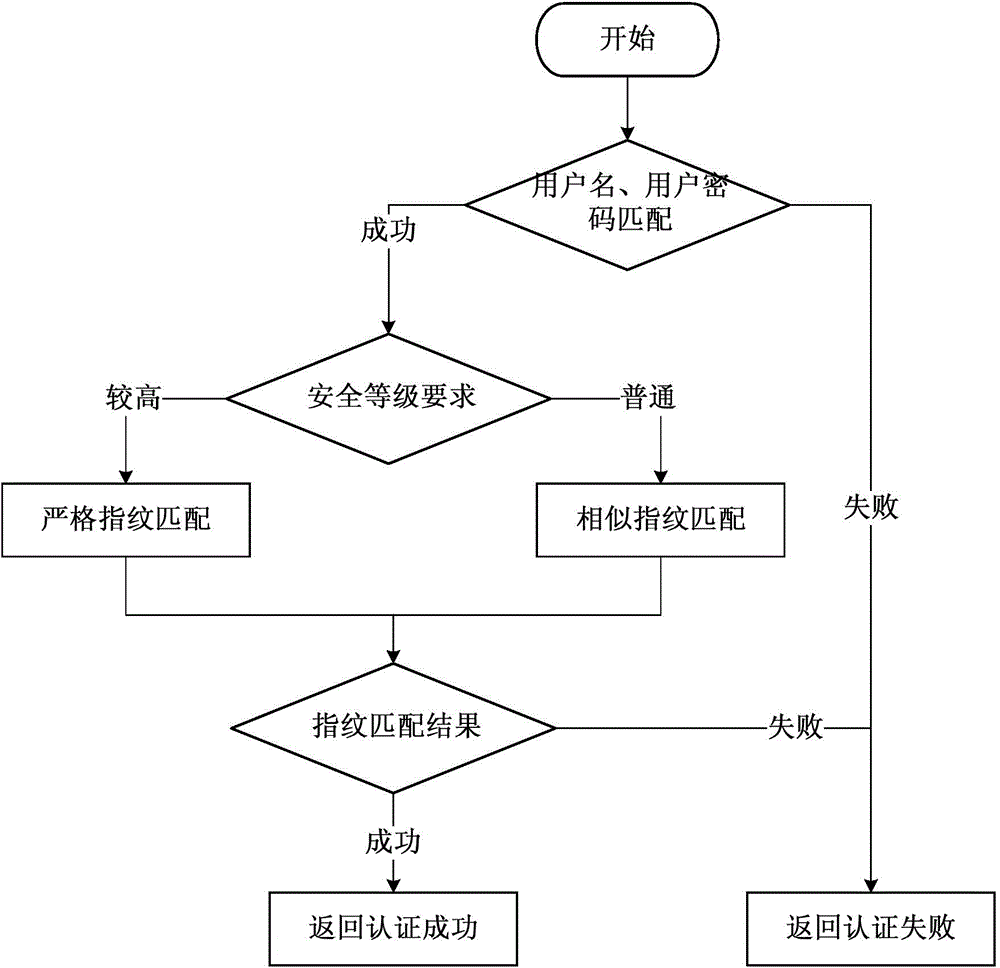
Android intelligent terminal security authentication method
ActiveCN104994105APreference is closely relatedEasy to identifySubstation equipmentTransmissionFingerprintSecurity authentication
The invention provides an Android intelligent terminal security authentication method. The method comprises following steps of acquiring setting information, and forming user fingerprint; performing matching authentication on the user fingerprint; and upgrading reserved fingerprint in a server background and recording upgrading information. According to the Android intelligent terminal security authentication method, on the basis of a user name password authentication manner, the setting information is acquired, the user fingerprint is formed, and different fingerprint matching strategies are made according to different security requirements, so that the whole security authentication is user-friendly.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +2
Outpatient and emergency transfusion management system based on RFID (Radio Frequency Identification Devices) technology
InactiveCN102903032ARealize managementNot easy to forgeSensing record carriersResourcesEngineeringTherapeutic treatment
The invention relates to an outpatient and emergency transfusion management system based on RFID (Radio Frequency Identification Device) technology, wherein a hospital information system and a digitalized transfusion chamber are seamlessly linked together by combining an outpatient and emergency transfusion management intellectualized system based on the RFID technology with a wireless network technology; and a discrete distribution management is updated to be a methodic digitalized management; Compared with the conventional transfusion mode, the outpatient and emergency transfusion management system has the advantages that by the reconfirmation on patients and transfusion medicines of the RFID radiofrequency non-contact function and the wireless transmission system of a therapy vehicle, the possible medical errors can be further reduced. A more reliable guarantee is provided for therapy and nursing for transfusion patients; and by the system integration integrating software functions and hardware functions such as identity authentication and therapeutic treatment and rescue, a more comprehensive management mode is provided for therapy for the transfusion patients in a hospital, and a solution scheme which is advanced in technology, safe, reliable and feasible is provided for transfusion management.
Owner:SHANGHAI PUDONG NEW AREA PEOPLES HOSPITAL
Safety online detecting system facing to terminal computers
ActiveCN102663298AAvoid defects that require on-site inspectionAvoid pitfalls of on-site inspectionPlatform integrity maintainanceNetwork onComputer security
A security online detecting system facing to terminal computers performs a centralized detection on all the terminal computers in network on a center computer on line. The system comprises a online detecting tool, a packaging module and the center computer, the online detecting tool is packed as CAB form and stored in the center computer by the packaging module, and the CAB is embedded into the IE browser by the center computer, the CAB is downloaded from the center computer to the terminal computer through the IE browser and automounted, a user can input a project command which expected to be detected and input information corresponding to the detected project by the IE browser on the center computer, the received project command and the input information corresponding to the detected project are send to a security detecting unit by a unified data interface module of every terminal computer, and the security detecting unit starts strategy security online detecting or patch security online detecting or hardware resource information security online detecting or software security online detecting according to the project command, and then the detecting results are displayed by a display module.
Owner:BEIJING INST OF SPACECRAFT SYST ENG +1
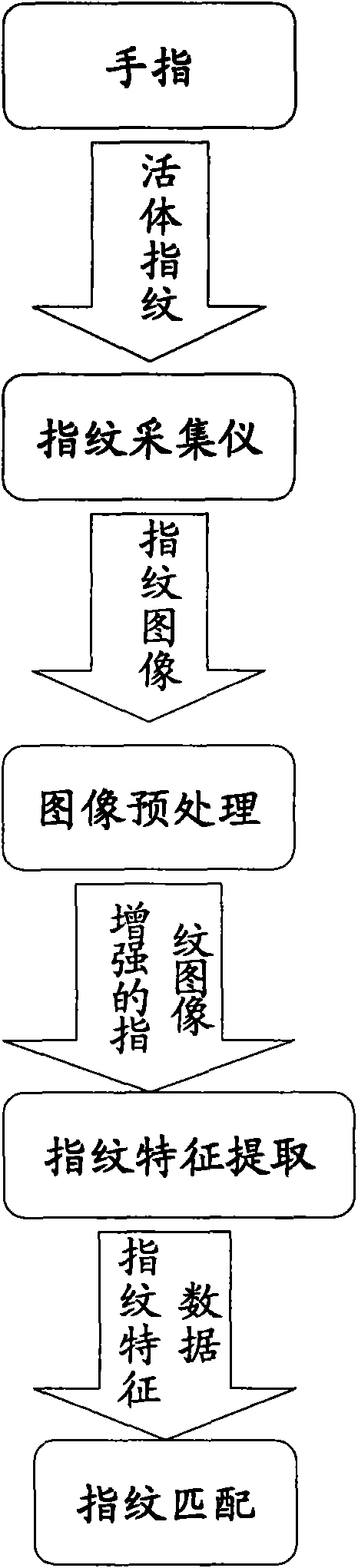
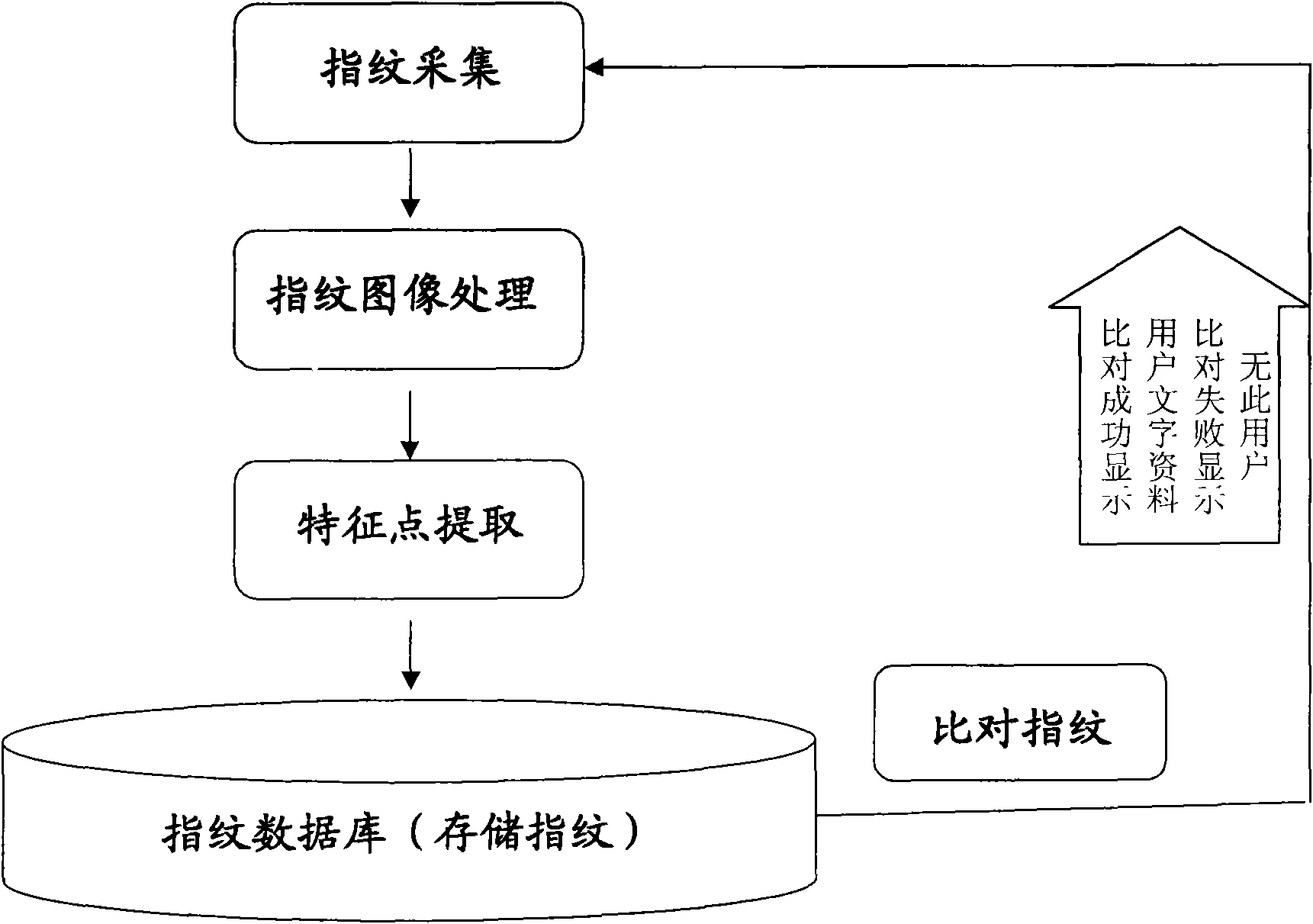
Application process of fingerprint identification technology on POS machine, imprinter and cash dispenser
InactiveCN101556713ANot easy to forgetNot easy to loseCharacter and pattern recognitionSpecial data processing applicationsCredit cardPattern recognition
An application process of fingerprint identification technology on a POS machine, an imprinter and a cash dispenser mainly comprises fingerprinting, fingerprint image preprocessing, characteristic point extraction, characteristic point storage, integrates the characteristics of individual fingerprints into the information of the individual data of a credit card so as to bind with the information of the individual data. The fingerprint comparison comprises fingerprint collection, fingerprint image preprocessing, and characteristic point extraction, carries out feather matching on the extracted characteristic points and the stored characteristic points, and finally outputs and shows the comparison results. The invention has the advantages that the fingerprint identification technology is applied to the POS machine, the imprinter and the cash dispenser, has two major functions of fingerprint registration and fingerprint comparison, the individual fingerprint identification technology and the image conversion technology are used for realizing the transmission process of the image data and ensuring the non-losing and non-damaging of the characteristic information of the fingerprint; the implicative information is more obvious, is difficult to be forgotten or lost, forged or stolen, and carried about, is safe, convenient and fast in utilization.
Owner:FUSHUN JINDAO TECH
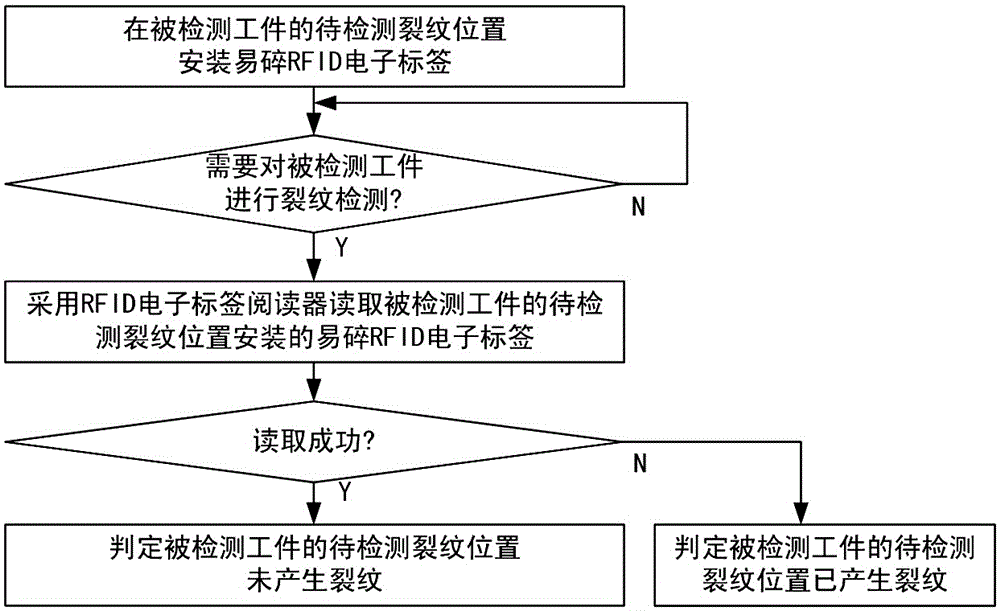
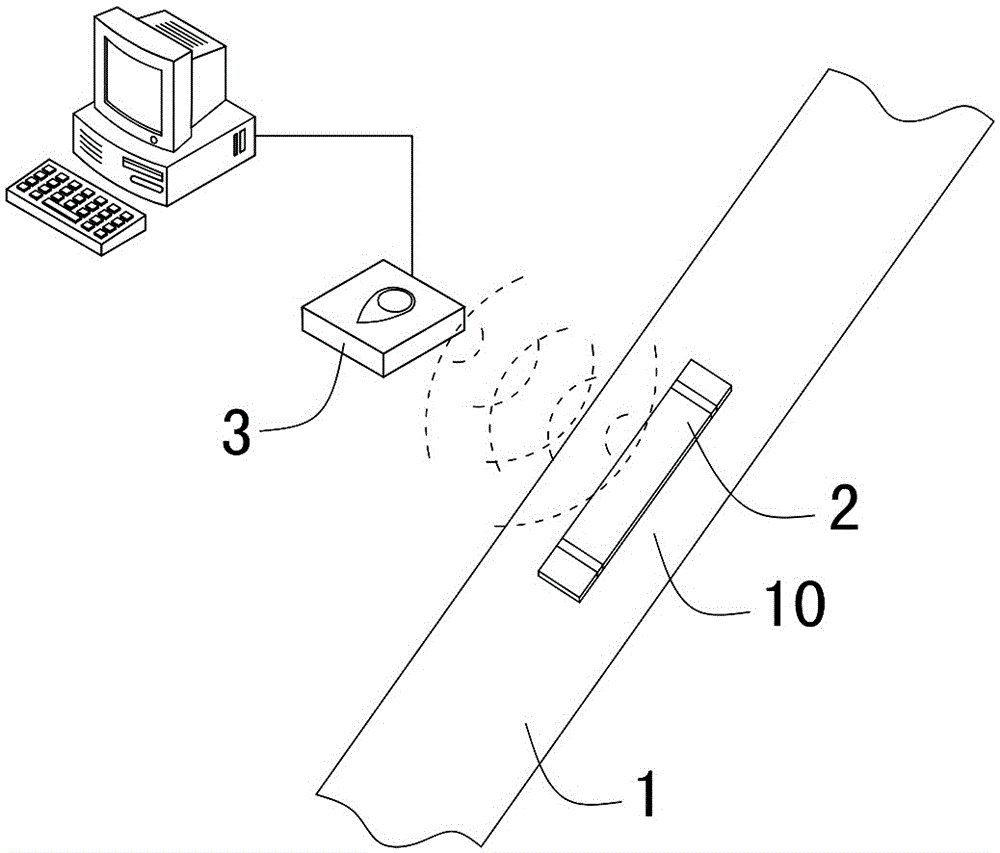
Work-piece crack detection method based on an RFID (Radio Frequency Identification Device)
InactiveCN105139045AQuick checkFast recognitionCo-operative working arrangementsTelecommunicationsElectronic tagging
The invention discloses a work-piece crack detection method based on an RFID (Radio Frequency Identification Device). The work-piece crack detection method comprises the following steps: installing a fragile RFID electronic tag at a crack position to be detected of a detected work-piece in advance, so that the fragile RFID electronic tag is respectively connected and fixed with two sides of the crack position to be detected on the detected work-piece; and reading the installed fragile RFID electronic tag at the crack position to be detected on the detected work-piece by adopting an RFID electronic tag reader in need of detecting the crack of the detected work-piece, if reading successfully, judging that the crack is not generated at the crack position to be detected on the detected work-piece, and if not, judging that the crack is generated at the crack position to be detected. According to the invention, a work-piece is unnecessary to take down from equipment; and the work-piece crack detection method has the advantages of being rapid in identification speed, wide in identification range, easy to operate and control, simple, practical, small in equipment volume, flexible in shape, convenient in data format updating, good in safety and wide in application range and is capable of realizing penetrability and non-barrier detection.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
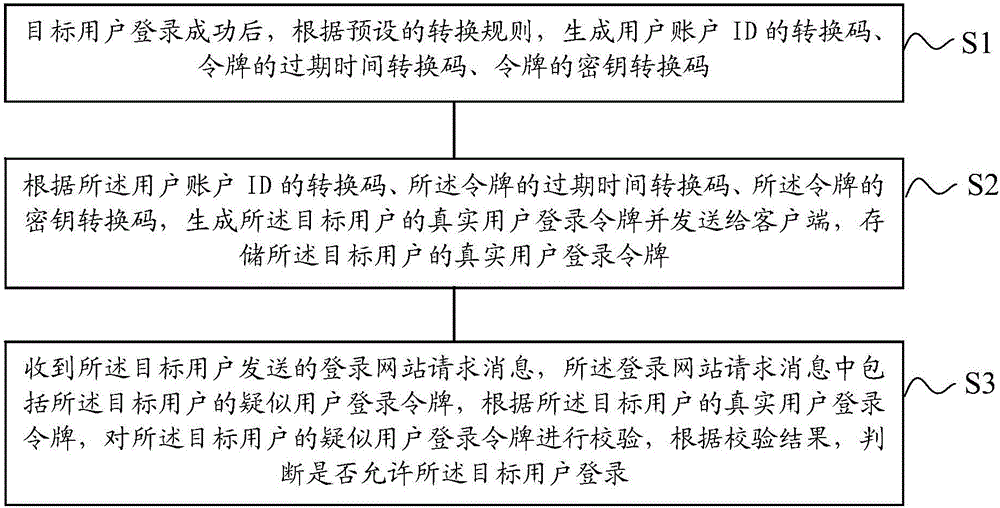
User account logging-in method, device and system
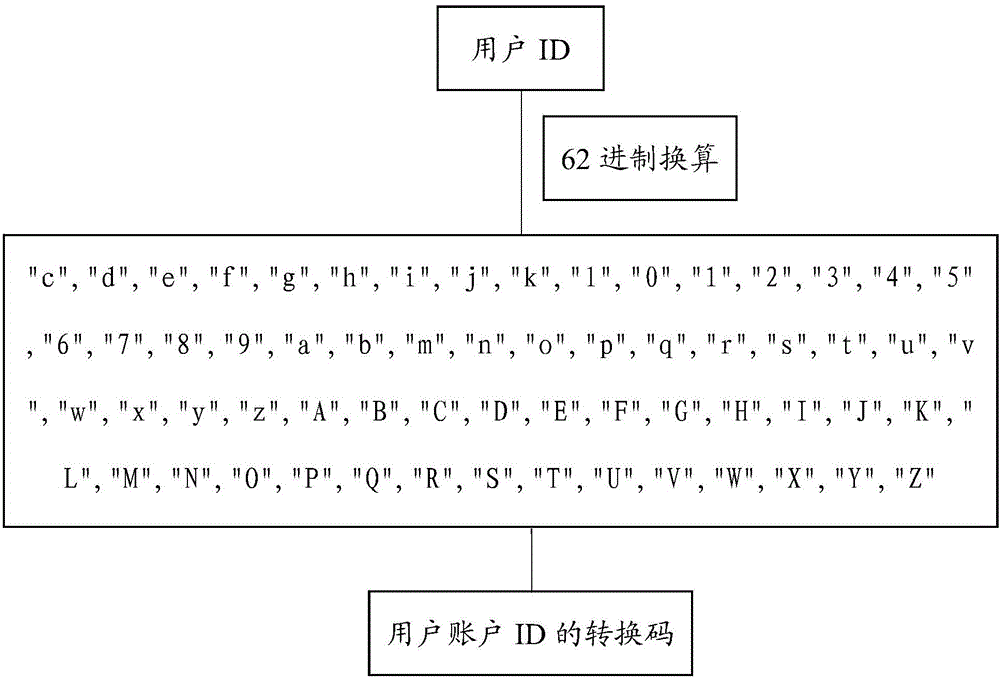
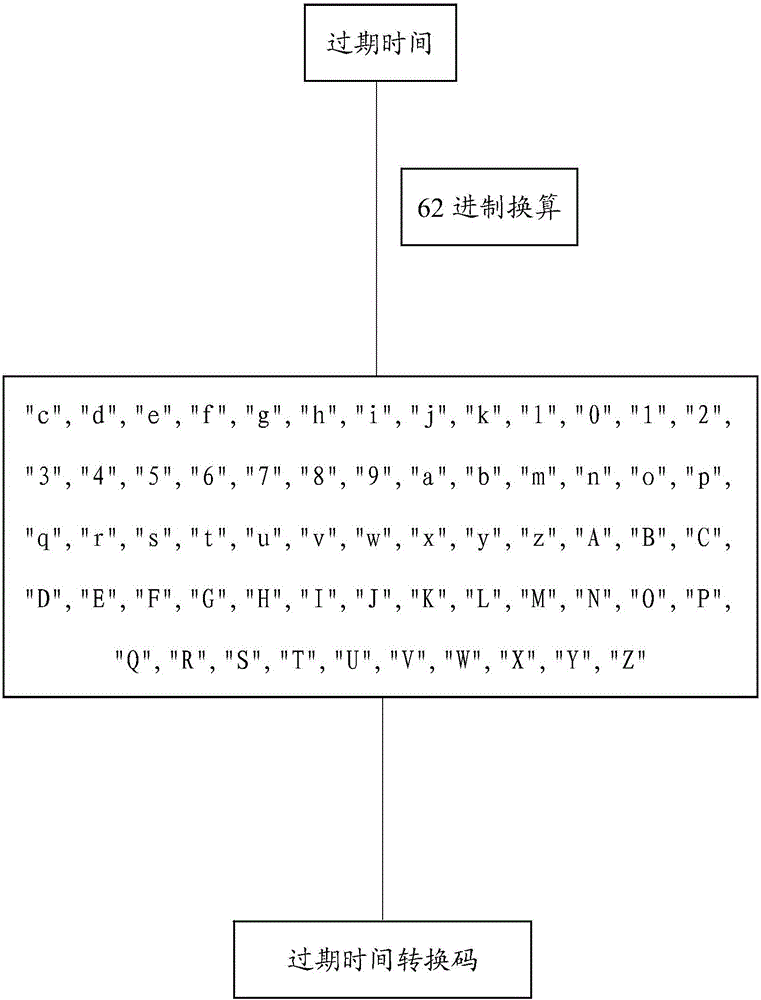
InactiveCN106101103AImprove securityIncrease randomnessKey distribution for secure communicationUser identity/authority verificationExpiration TimeClient-side
The embodiment of the invention discloses a user account logging-in method, device and system, and relates to the technical field of website logging-in. The method comprises the steps of: after a target user successfully logs in, according to a preset conversion rule, generating a conversion code of a user account ID (Identity), an expiration time conversion code of a token and a secret key conversion code of the token; according to the conversion code of the user account ID, the expiration time conversion code of the token and the secret key conversion code of the token, generating a real user logging-in token of the target user and sending the real user logging-in token to a client; and receiving a logging-in website request message sent by the target user, verifying a suspected user logging-in token of the target user according to the real user logging-in token of the target user, and according to a verification result, judging whether to allow the target user to log in. According to the user account logging-in method, device and system disclosed by the embodiment of the invention, safety of the user logging-in token and a user account can be improved.
Owner:LETV HLDG BEIJING CO LTD +1
Two-dimension code anti-counterfeiting method
InactiveCN104240093ATo achieve the purpose of anti-counterfeitingSimple methodCo-operative working arrangementsCommerceProgramming languageMobile phone
The invention discloses a two-dimension code anti-counterfeiting method. In particular, a unique two-dimension code is arranged for each commodity, special character strings or numeric strings in the two-dimension codes correspond to an IMEI number of a mobile phone for checking whether the unique two-dimension codes are bound with other mobile phones or not, the authenticity of the commodities can be further checked, and the anti-counterfeiting aim is achieved. The two-dimension code anti-counterfeiting method is simple, effective and not prone to counterfeiting.
Owner:成都鹰瑞科技有限公司
Admittance identity authentication system based on image identification
InactiveCN104240347APrevent Identity InquiryImprove recognition efficiencyIndividual entry/exit registersInternet privacyConfidentiality
The invention discloses an admittance identity authentication system based on image identification. According to the system, an acquisition terminal acquires character information and image information, so as to generate acquired data; a server stores the acquired data in corresponding region classification databases according to regional attributions of the acquired data; an authentication terminal acquires data to be authenticated from the regional attributions; the server compares the data to be authenticated with the acquired data, judges whether the regional attributions are matched with the region classification databases, where the corresponding acquired data are located, or not, generates authentication information according to matching results and sends the authentication information to the authentication terminal, the authentication terminal judges whether authentication permissions can be obtained or not, and then, whether the data to be authenticated pass through the admittance authentication of the regional attributions or not is acquired. The system has the advantages that the anti-counterfeiting performance is good, forgery and theft are difficult, convenience is brought for the arrangement of various types of field services, the admittance efficiency is increased, the staff setting is simplified, then, the effect of getting twice the result with half the effort is achieved, the identity check and authentication among different regional attributions can be prevented, and thus, the confidentiality of identity authentication is improved.
Owner:福建省智慧物联网研究院有限责任公司
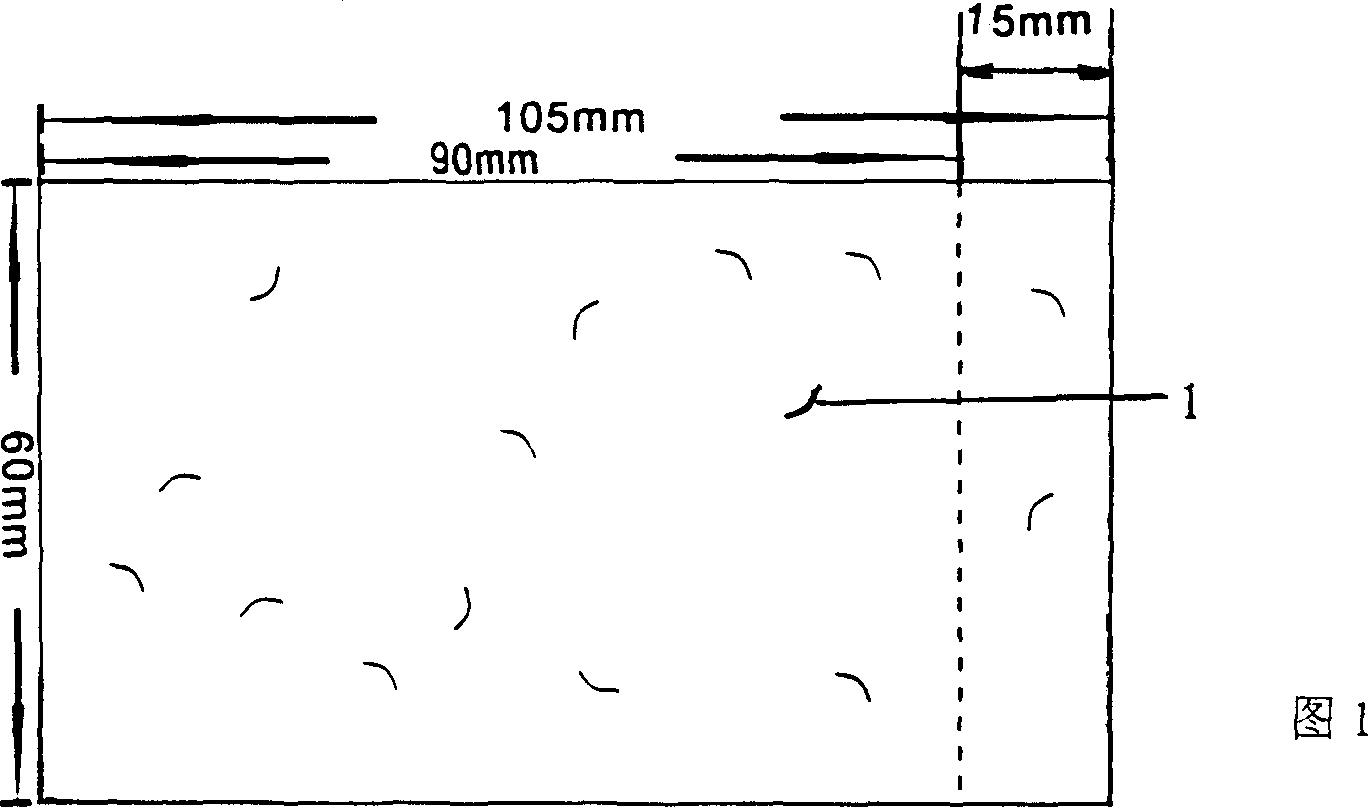
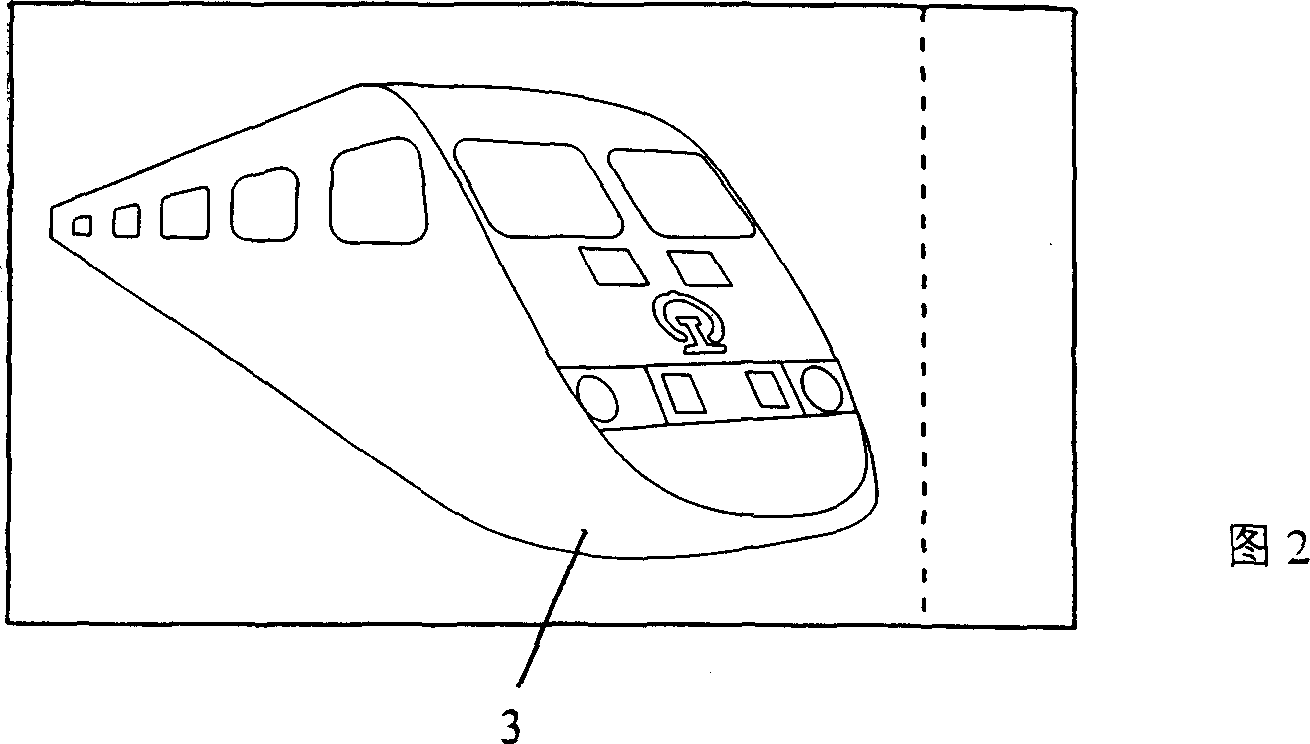
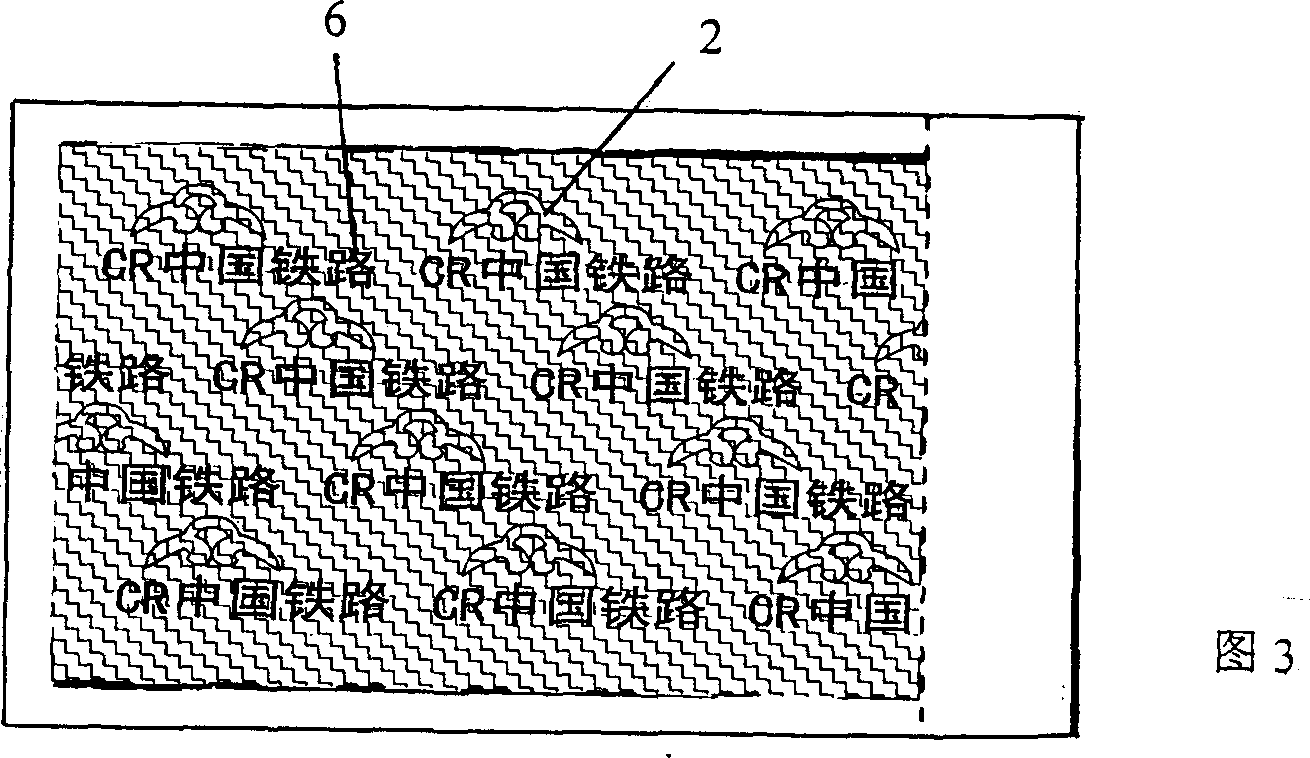
Method for making anti-fake train ticket of real name system and its anti-fake train ticket of real name system
InactiveCN1944075ANot easy to forgeEasy to installOther printing matterLight effect designsCard readerComputer science
The present invention is anti-fake train ticket of real name system and its making process. The ticket is printed with plate possessing color cloud pattern and optical anti-fake characters. It is printed in a train ticket selling computer system with ID card reader, and after the ID card information is read out, the ticket information, the passenger name, ID card bar code and the selling information are printed. In the railway station, corresponding ticket validating device is set. The ticket has six kinds of anti-fake technology adopted and is safe, reliable, hard to forge and easy to validate.
Owner:李雪平
Specific personnel behavior supervision system and method based on blockchain and smart contract
ActiveCN109194710AHas a supervisory functionImprove securityTransmissionComputer terminalEngineering
The present invention relates to a specific personnel behavior supervision system and method based on a blockchain and smart contract which is designed aiming at the problems that the data is prone totampering, counterfeiting and hostile attack risks and an intelligent terminal is lack in range, pressure bearing and electric quantity monitoring in the current similar method. The user terminal ofthe system is an intelligent terminal worn on a special person, the special person position information and the device operation state information of the carrying intelligent terminal are uploaded into a blockchain, and the behavior criterion smart contract codes are written in the blockchain to perform specification for the special person's behaviors; when the special person is out of the activity range set by a manager, or is out of the pressure range of the intelligent terminal, the device electric quantity is lower than the safety electric quantity range and the charging is not performed,a contract execution sub module automatically operate the smart contract codes and emits alarm to prompt the manager to the illegal behaviors of the person such as out of the activity range or viciousdamaging of the device and not charging deliberately.
Owner:广州华创物联科技股份有限公司
Process for producing antibacterial food packaging bag having anti-counterfeiting function
InactiveCN108910289AWith bactericidal functionHigh removal rateFlexible coversWrappersFiberComposite film
The invention discloses a process for producing an antibacterial food packaging bag having an anti-counterfeiting function. The process comprises the following steps of preparation of an antibacterialfilm: weighing raw material soybean fiber, potassium permanganate powder, nano silica powder, paraffin, polyethylene resin, polyhydroxyalkanoate, gelatin and plasticizer, melting and evenly mixing the paraffin, the polyethylene resin, the polyhydroxyalkanoate and the gelatin, and standing to make a mixed material; evenly mixing the soybean fiber, the potassium permanganate powder, the nano silicapowder and the plasticizer to obtain a mixture; adding the mixture into the mixed material, and performing melt blending to obtain a blended material; performing hot pressing on the blended material;performing cold press molding after hot pressing, and obtaining the antibacterial film. The preparation of the antibacterial packaging bag includes performing printing on a reverse side of the antibacterial film; performing spray printing of an anti-counterfeiting code on the reverse side; and compositing a PE film below the well printed antibacterial film, to form a composite film; curing the composite film; performing spray printing of an anti-counterfeiting image layer on the front of the composite film, and after code spraying, performing slitting to manufacture an independent packaging bag. According to the process, the antibacterial food packaging bag can kill various harmful bacteria and have a bacteriostasis effect and strong anti-counterfeiting performances.
Owner:益阳市鸿利来彩印包装有限公司
Perspective information anti-fake print and its verifying tool and verifying method and anti-fake stamp
InactiveCN1588430AImprove concealmentSimple structureCharacter and pattern recognitionValidation methodsComputer engineering
Owner:DONGGUAN HUIFENG COMML CO LTD
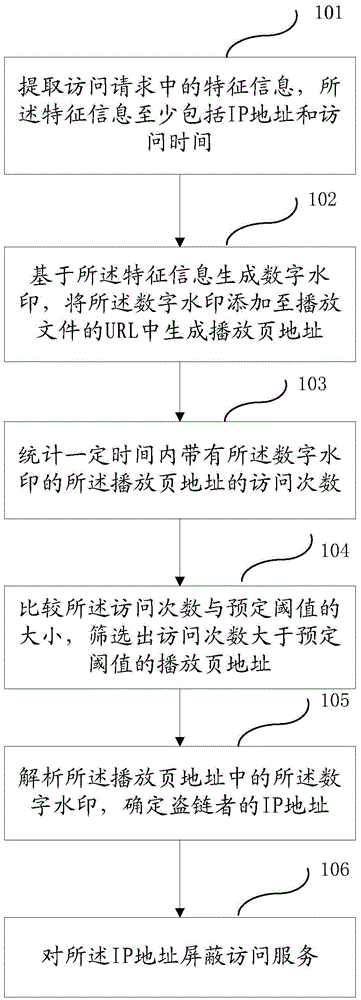
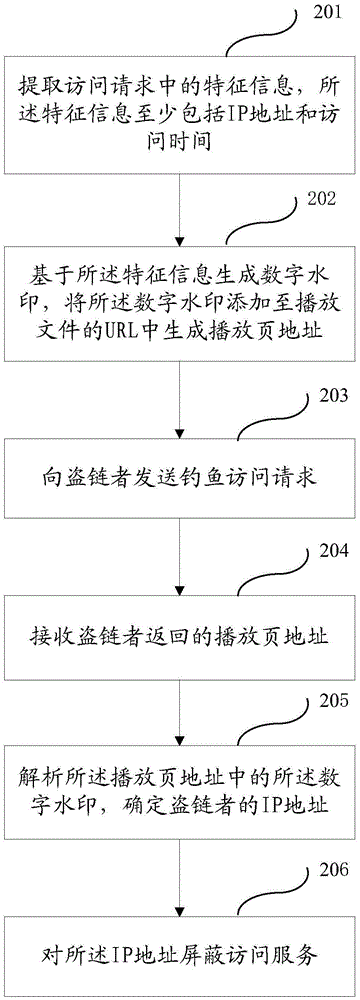
Anti-hotlinking method and system
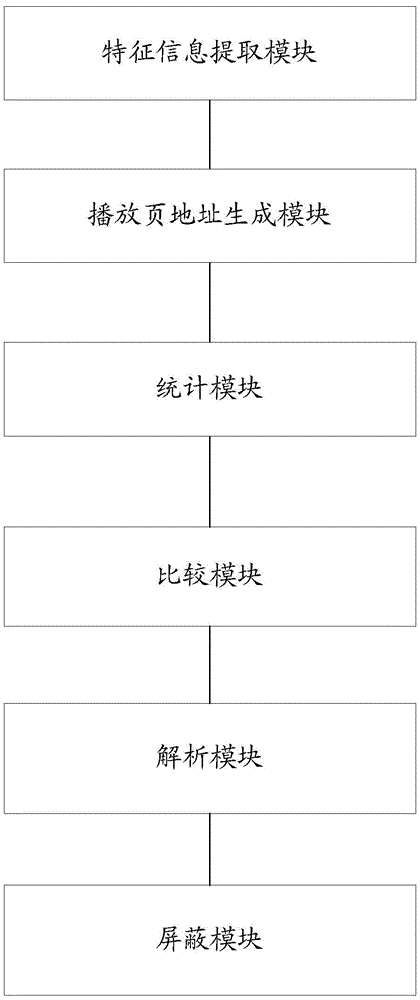
The invention provides an anti-hotlinking method. The method comprises the steps that feature information in an access request is extracted, wherein the feature information at least comprises an IP address and access time; based on the feature information, a digital watermark is generated, and the digital watermark is added to URL of a play file to generate a play page address; the number of access times of the playback page address with the digital watermark within a certain period of time is counted; the number of access times is compared with a predetermined threshold value, and the play page address the selected, wherein the number of access times of the play page address is greater than the predetermined threshold value; the digital watermark in the play page address is parsed to determine the IP address of a hotlinking person; and the access service of the IP address is shielded. The invention further provides an anti-hotlinking system. Thorough hotlinking preventing is realized. The anti-hotlinking accuracy is improved.
Owner:LETV CLOUD COMPUTING CO LTD
Optical storage method utilizing light variation image
InactiveCN1385764AEasy to detectEasy to observeRecord information storage3D-image renderingGratingAlgorithm
There is an optical storage method taking advantage of light-changing graph, its characters lies in that it incldues steps as follows: (1) it changes stored information into graph, word or data list with given coding mode; (2) according to the characters of light-changing graph, it arranges the graph and word list in step (1) into light-changing graph and word. Hereinto, so called light-changing graph is made up of grating unit array, each grating unit is made of elaborate graph, word or data bit and the scale of grating unit is no more than 160 micron; (3) it storages the light-changing graph acquired from step (2) to recording material by light-changing graph copy-arrangement system. Technical scheme of the invention realizes high information-density light-changing's stored light-carving of the random digital graph and word.
Owner:湖北强大包装实业有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com