Android intelligent terminal security authentication method
A security authentication, smart terminal technology, applied in the field of Android smart terminal security authentication, can solve the problems of unpopularity, inconvenient user operation, forgery, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The present invention will be described in further detail below in conjunction with the accompanying drawings.
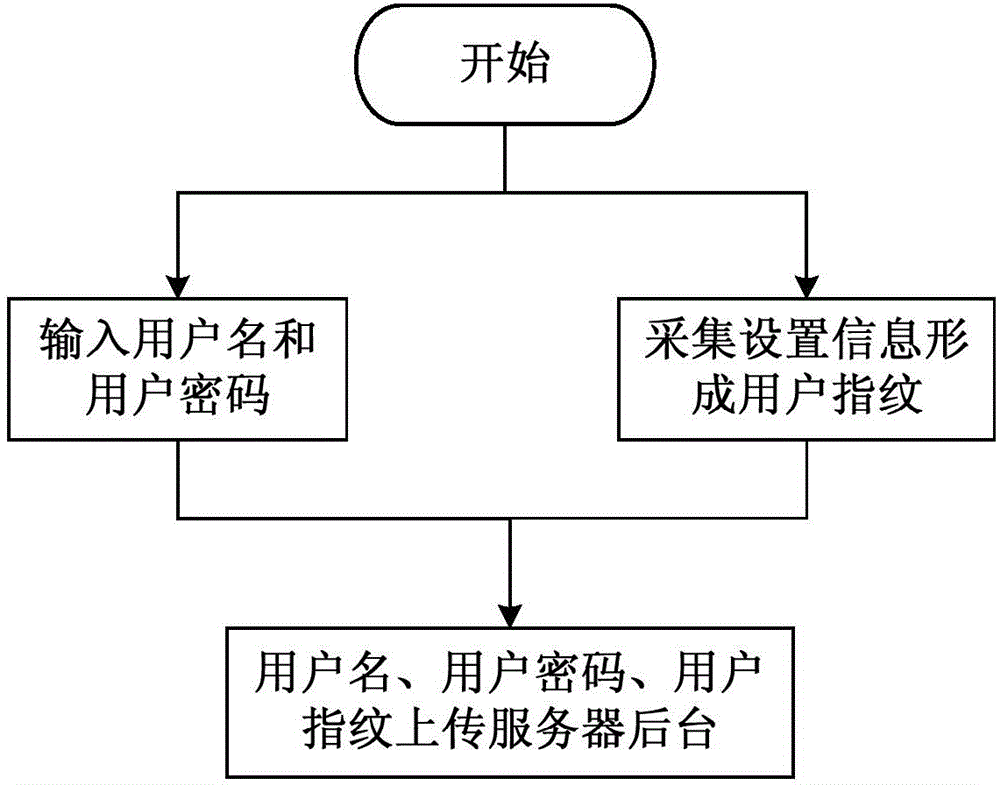
[0060] The present invention provides a kind of Android intelligent terminal security authentication method, described method comprises the following steps:
[0061] Step 1: Obtain setting information and form user fingerprints;
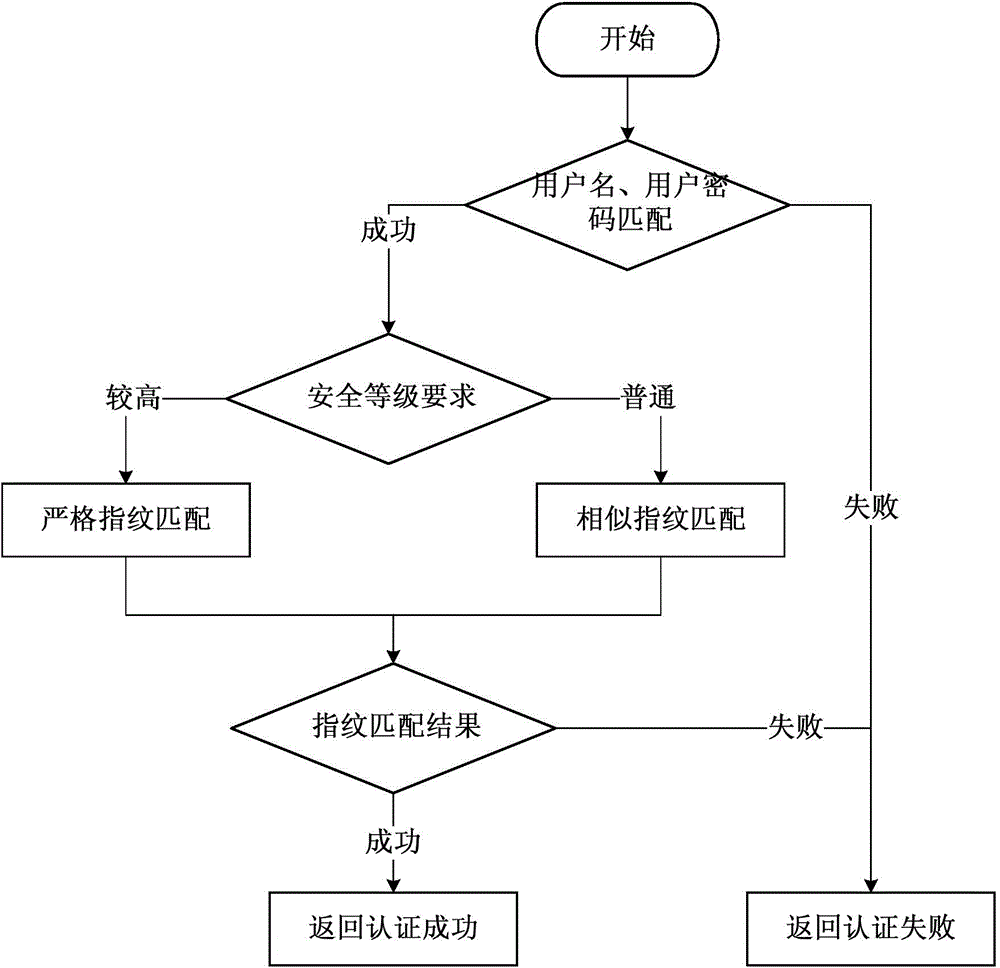
[0062] Step 2: Match and authenticate the user's fingerprint;
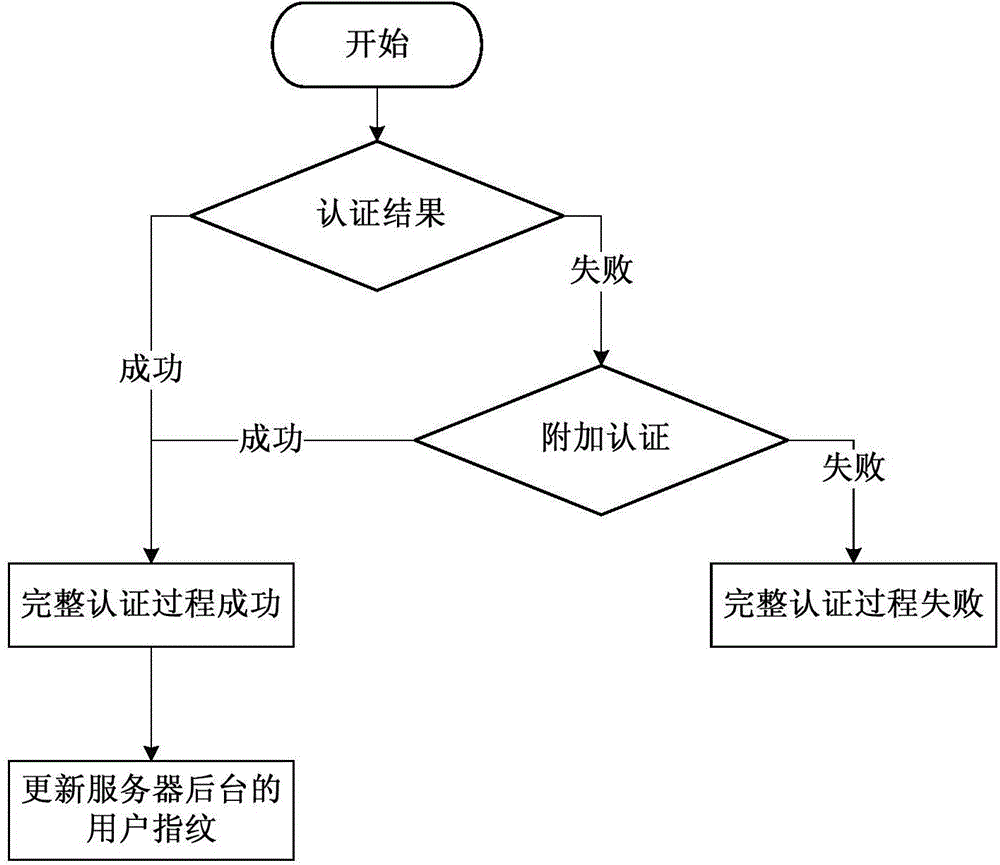
[0063] Step 3: Update the fingerprint reserved in the background of the server and record the update information.
[0064] In the step 1, (such as figure 1 ) through the API interface to obtain the setting information, and combine the obtained setting information to form a dictionary form of key-value pairs as the user fingerprint.
[0065] The setting information includes a list of optional ring tones, phone ring tones, SMS tones, notification tones, user wallpapers, user input methods, lock screen patterns, and the hour system; specifically:
[0066] (1) The data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com