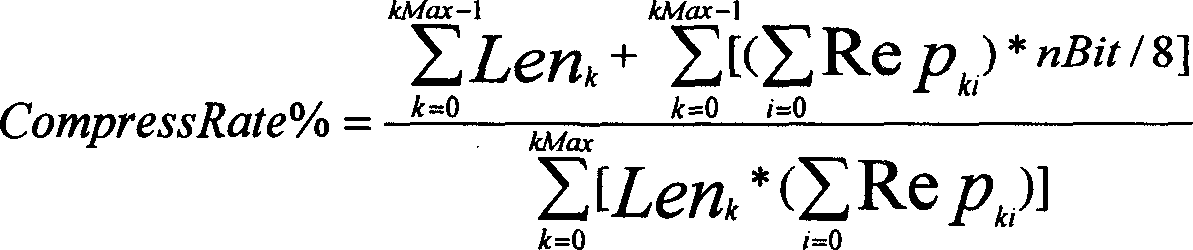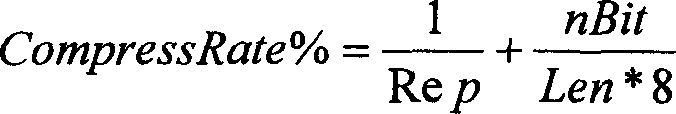Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39 results about "Substitute character" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A substitute character (␚) is a control character that is used in the place of a character that is recognized to be invalid or erroneous, or that cannot be represented on a given device. It is also used as an escape sequence in some programming languages.
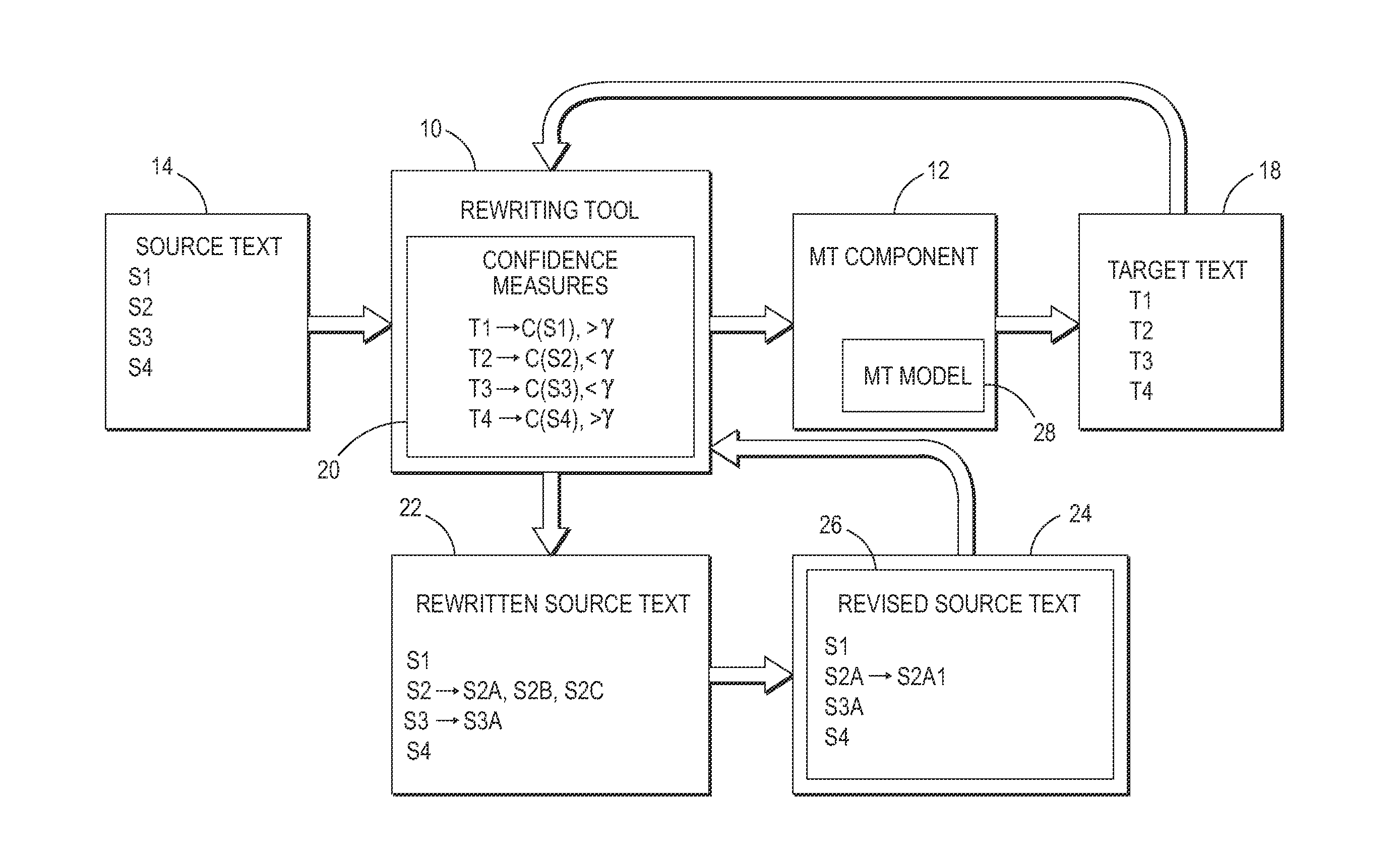
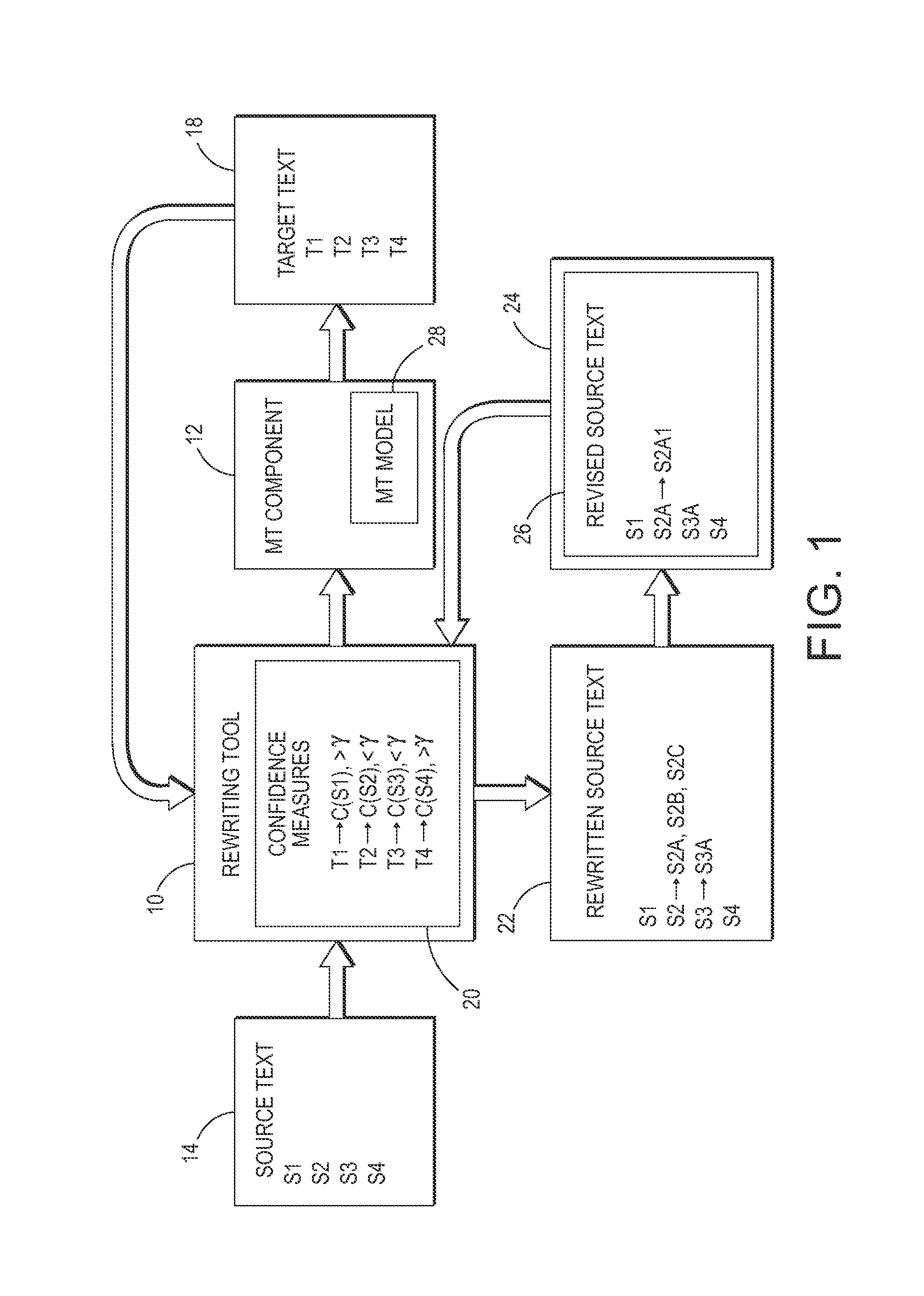
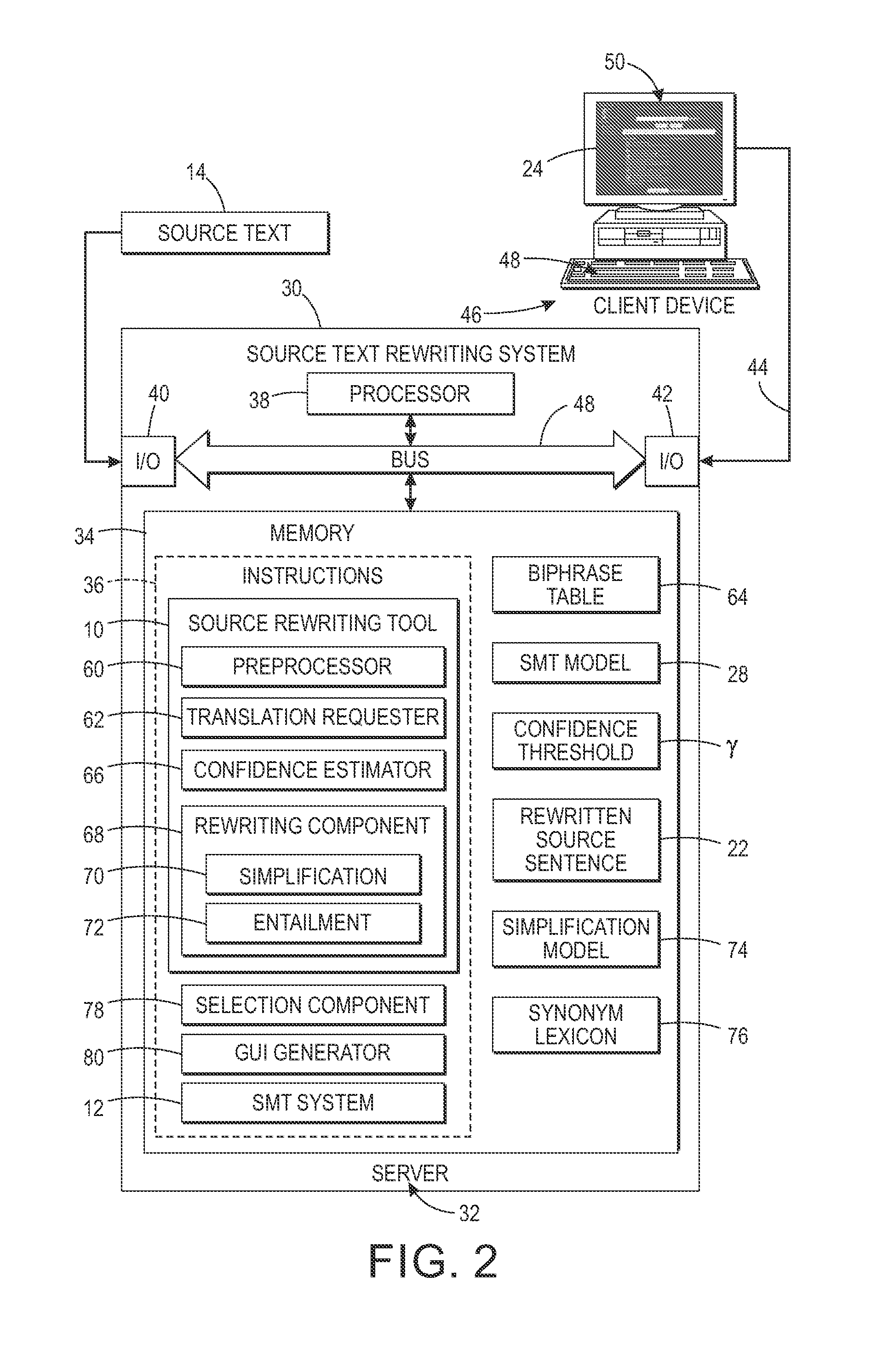
Confidence-driven rewriting of source texts for improved translation
InactiveUS20140358519A1Natural language translationSpecial data processing applicationsGraphicsGraphical user interface
A method for rewriting source text includes receiving source text including a source text string in a first natural language. The source text string is translated with a machine translation system to generate a first target text string in a second natural language. A translation confidence for the source text string is computed, based on the first target text string. At least one alternative text string is generated, where possible, in the first natural language by automatically rewriting the source string. Each alternative string is translated to generate a second target text string in the second natural language. A translation confidence is computed for the alternative text string based on the second target string. Based on the computed translation confidences, one of the alternative text strings may be selected as a candidate replacement for the source text string and may be proposed to a user on a graphical user interface.
Owner:XEROX CORP
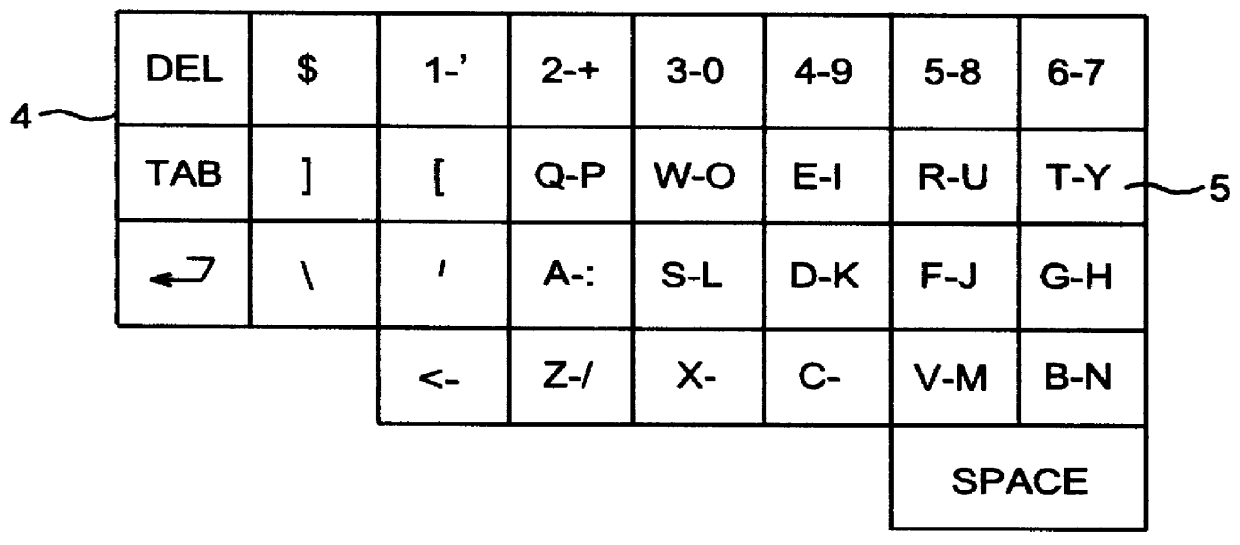
Keyboard for touch typing using only one hand
InactiveUS6102594AEasy to useEasy to learnElectronic switchingOther printing apparatusTypingComputer science
Keyboard for one-handed touch typing derived from a normal Sholes keyboard, where each character-key is assigned two characters (for instance T / Y), thereby reducing the number of keys to approximately half the number of keys on a normal Sholes keyboard. The choice between the two alternative characters of a specific key is based on the mode of depression of that particular key, and hence no separate key for choise between the two alternatives is needed. The characteristics of the keyboard can either be set once and for all or can be particularly adapted to the specific user of the keyboard, such as for instance to the user's writing speed.
Owner:TELEFON AB LM ERICSSON (PUBL)
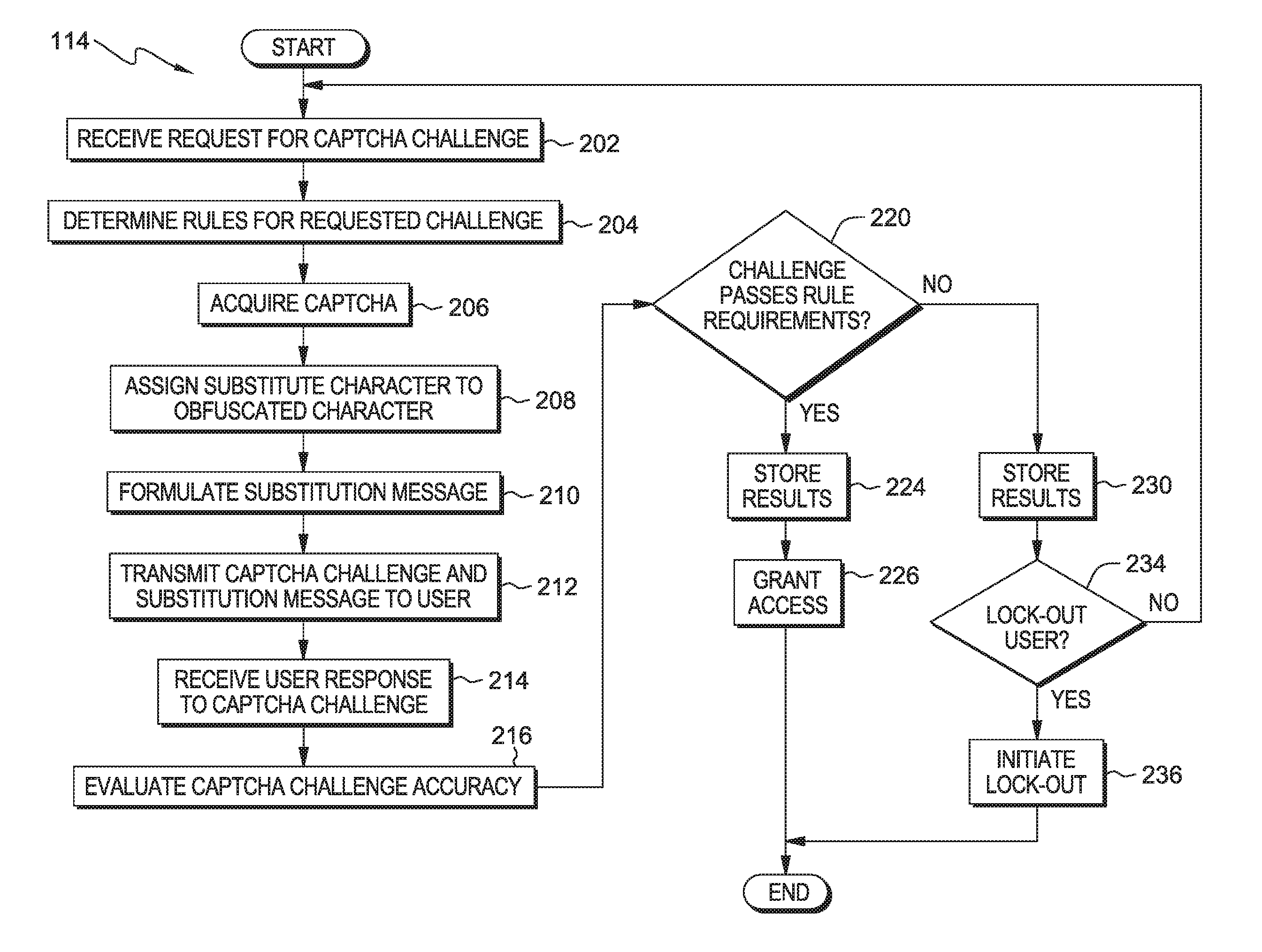
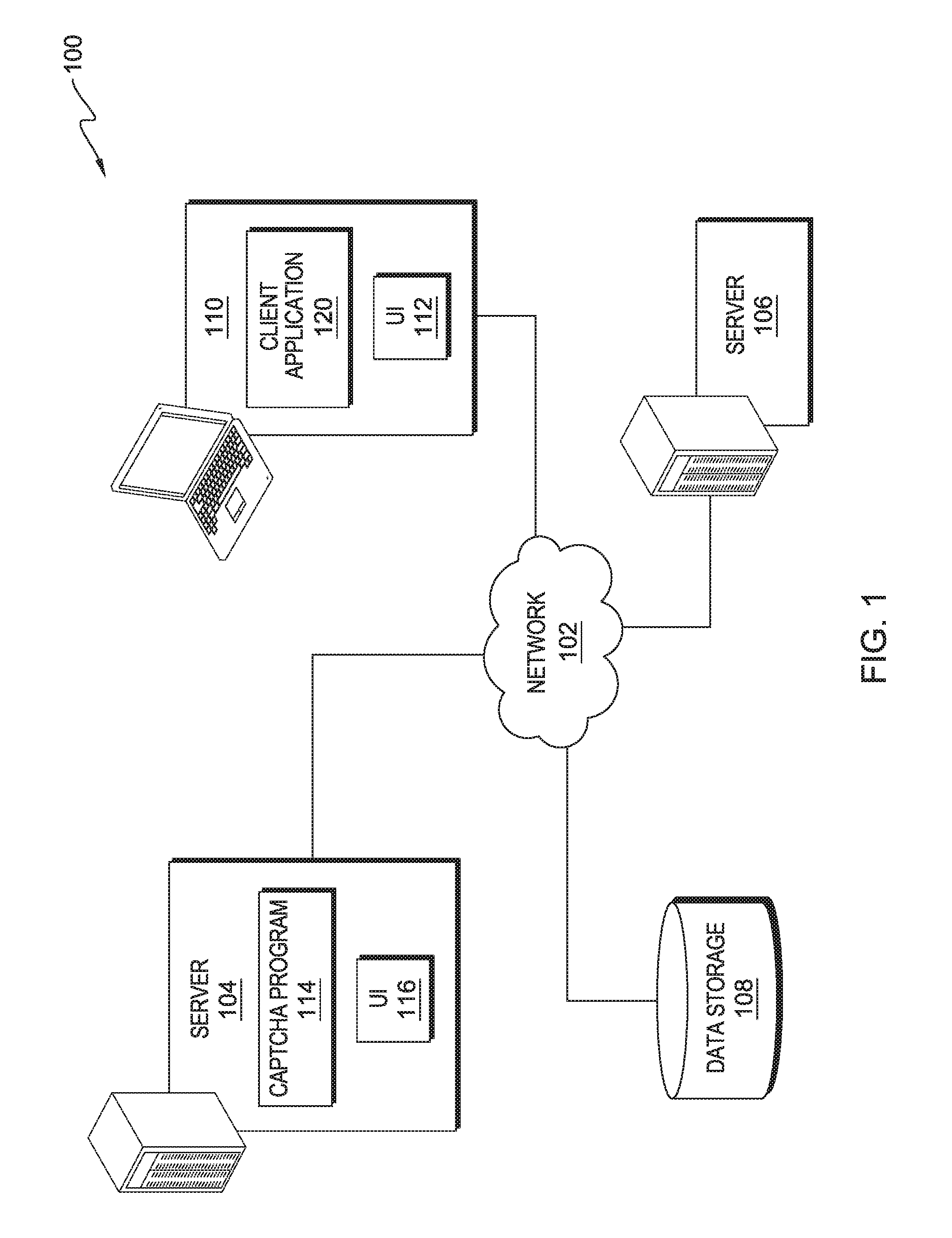
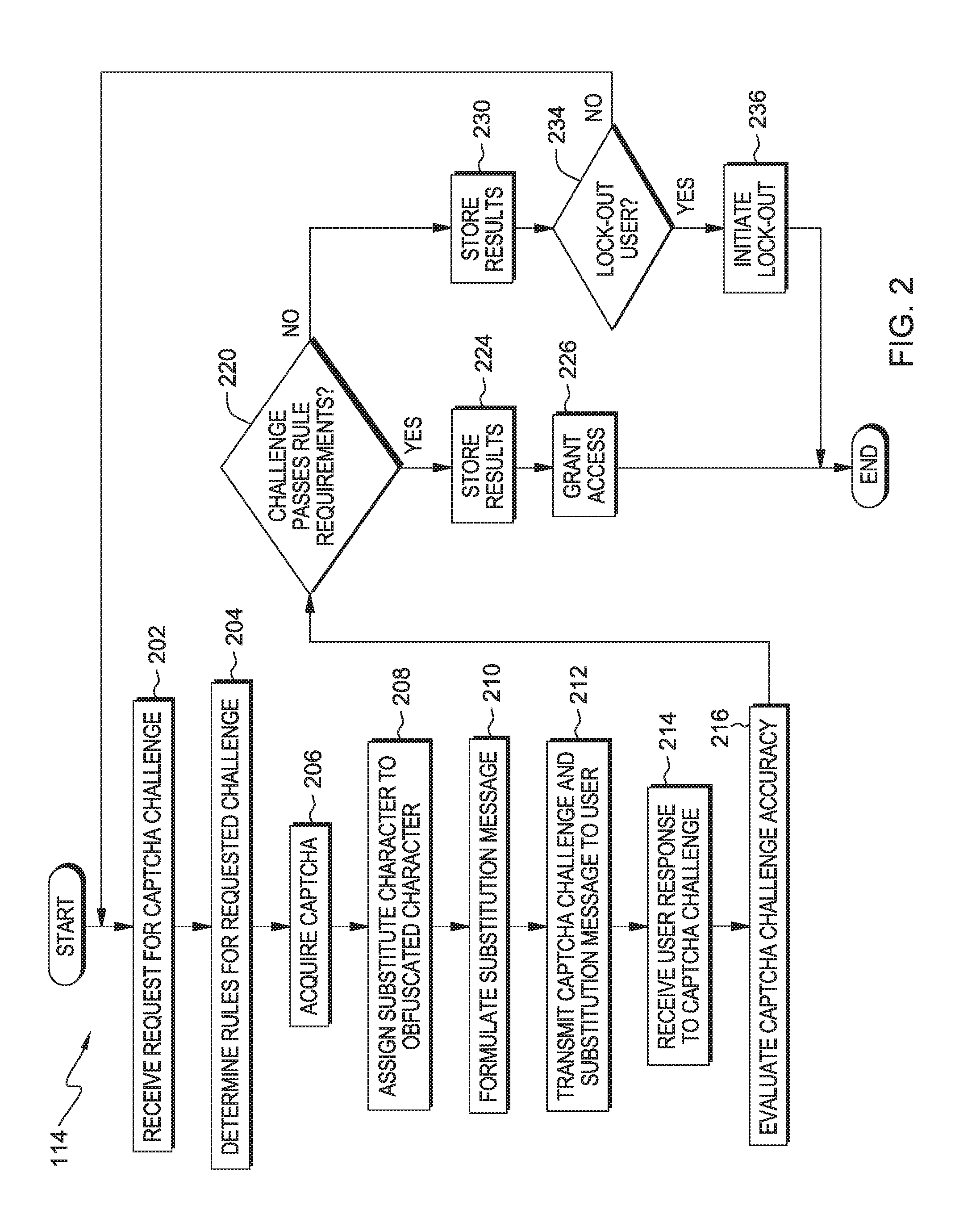
Captcha challenge incorporating obfuscated characters
InactiveUS20150365401A1Digital data processing detailsMultiple digital computer combinationsAlgorithmSoftware engineering
A method for determining if a user of a computer system is a human. A processor receives an indication that a computer security program is needed and acquires at least one image depicting a first string of characters including at least a first and second set of one or more characters. A processor assigns a substitute character to be used as input for each of the second set of one or more characters. A processor presents the at least one image and an indication of the substitute character and when to use the substitute character to the user. A processor receives a second string of characters from the user. A processor determines whether the second string of characters substantially matches the first string of characters based on the substitute character assigned to each of the second set of one or more characters and determines whether the user is a human.
Owner:KYNDRYL INC
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
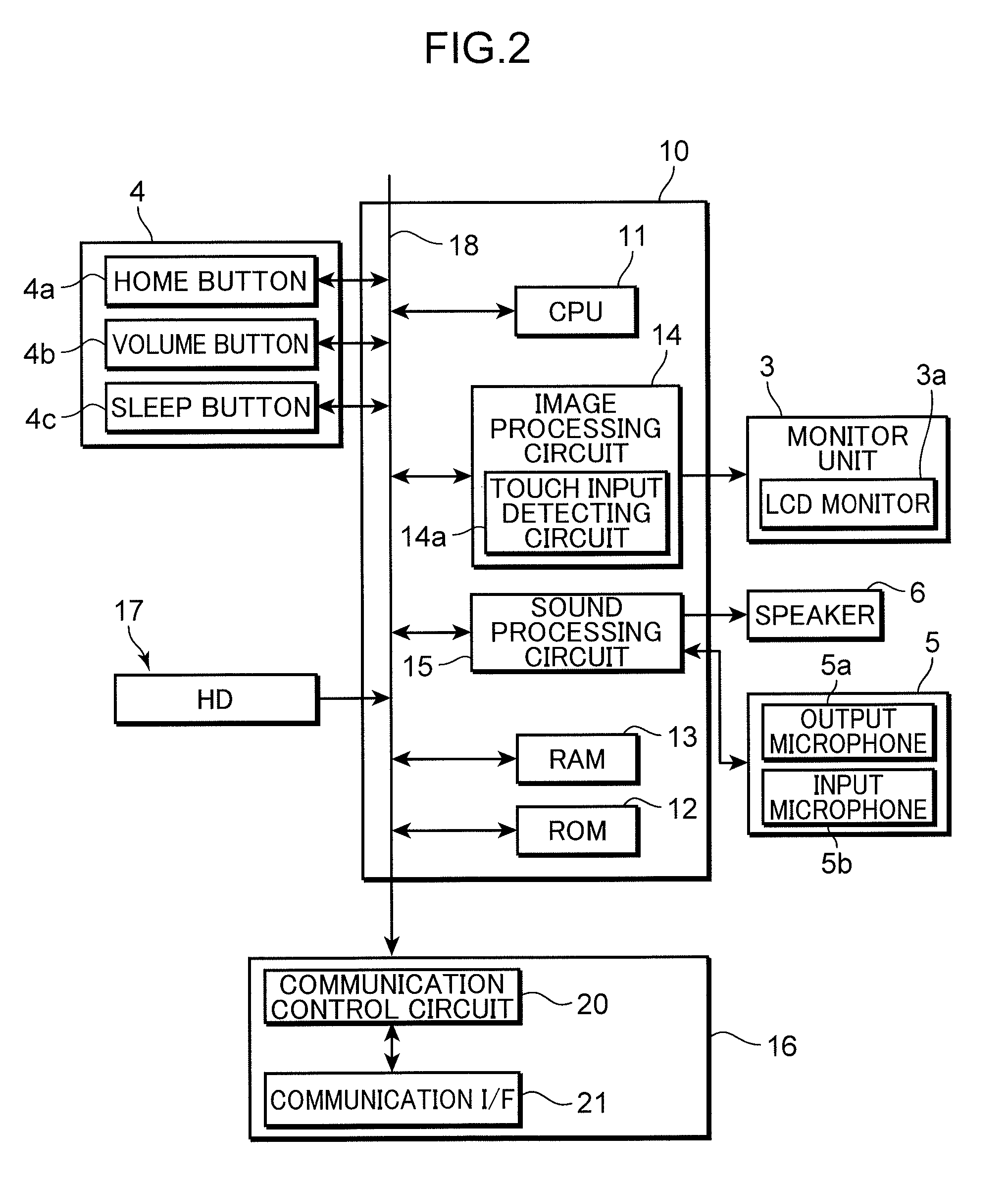
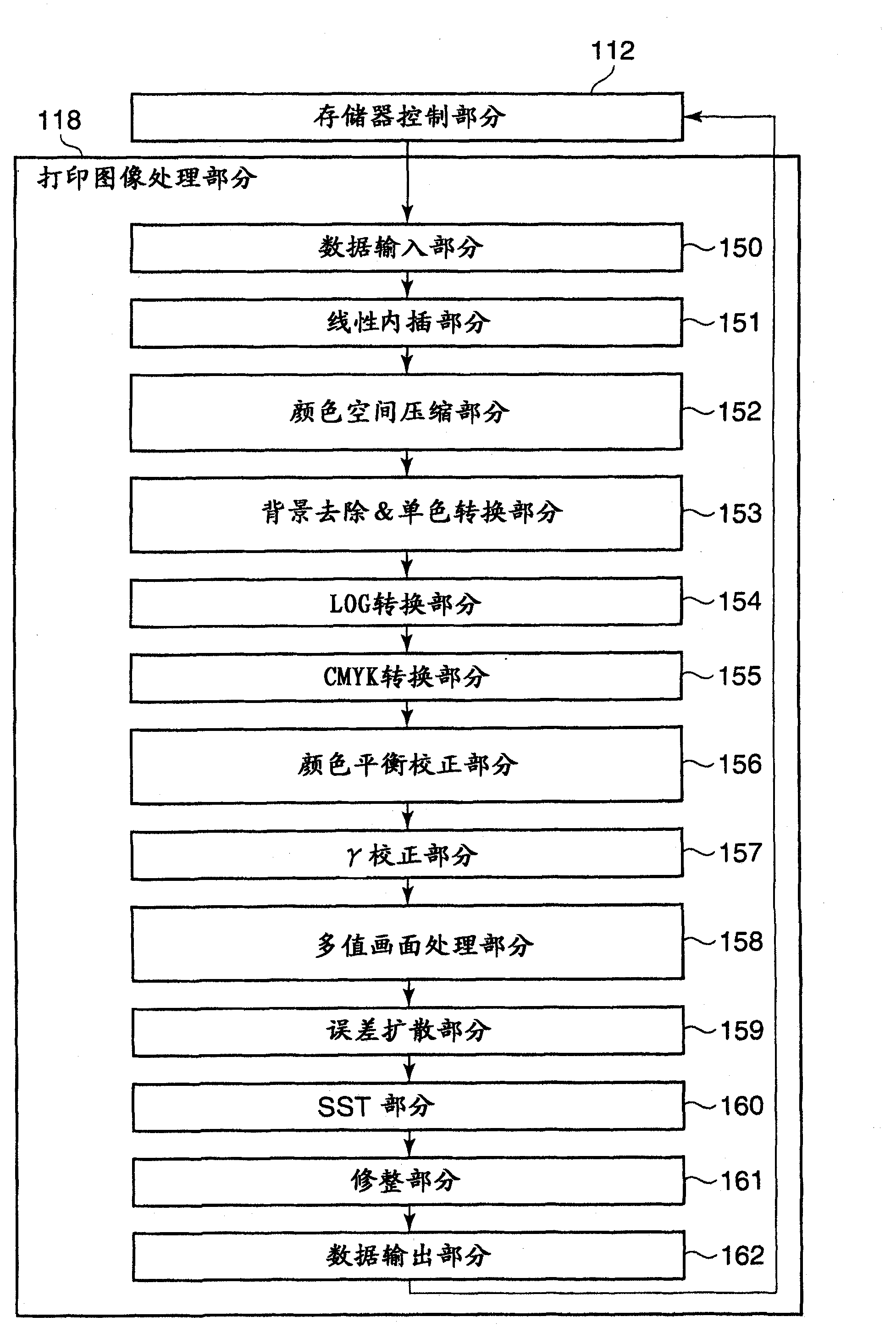
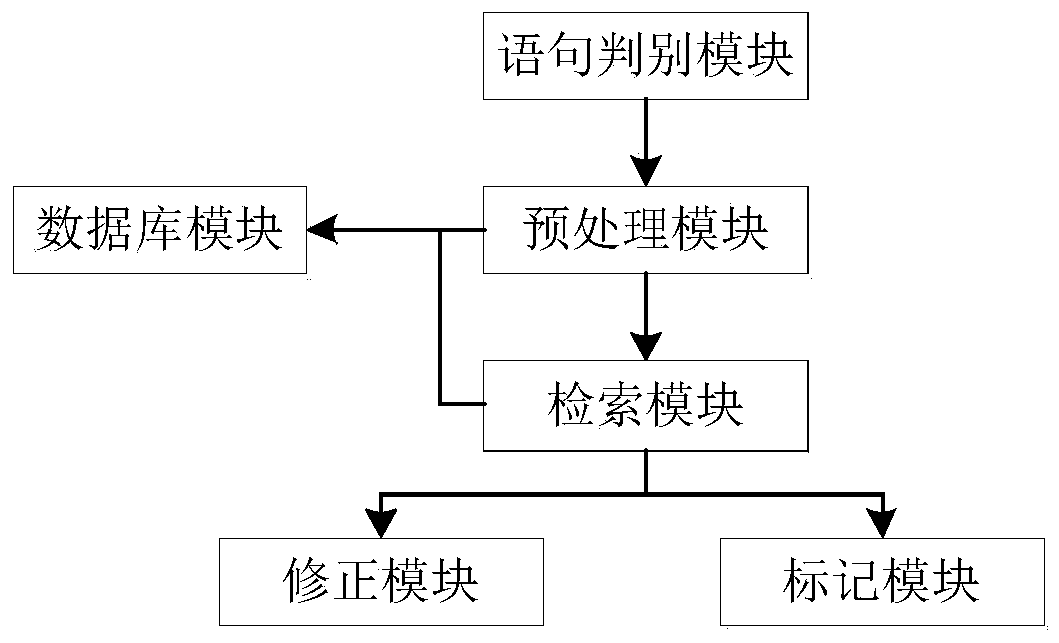
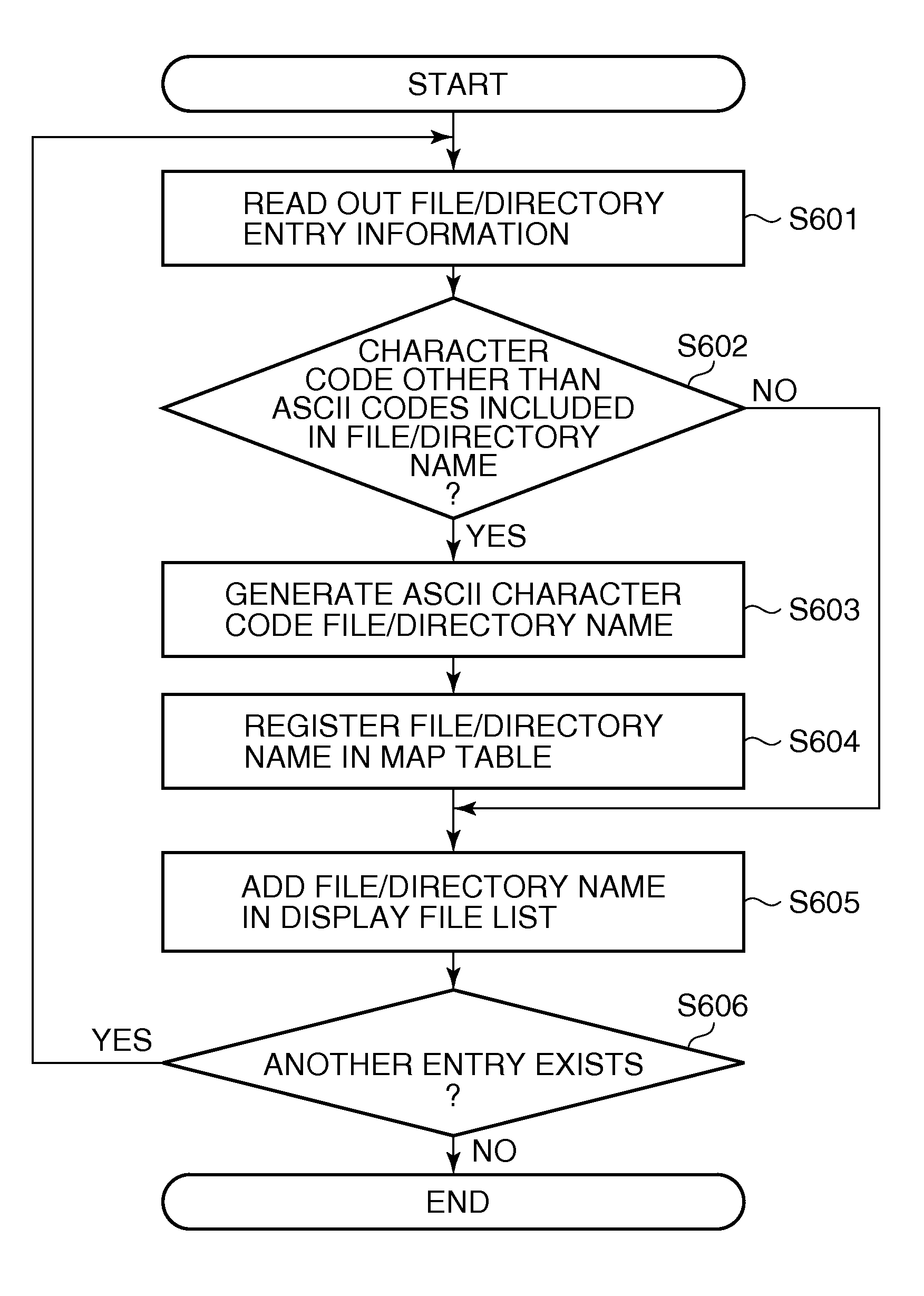
Information processing apparatus, method of controlling the same, and storage medium
InactiveUS20110125768A1Reliably access files associatedDigital data information retrievalDigital data processing detailsMass storageInformation processing
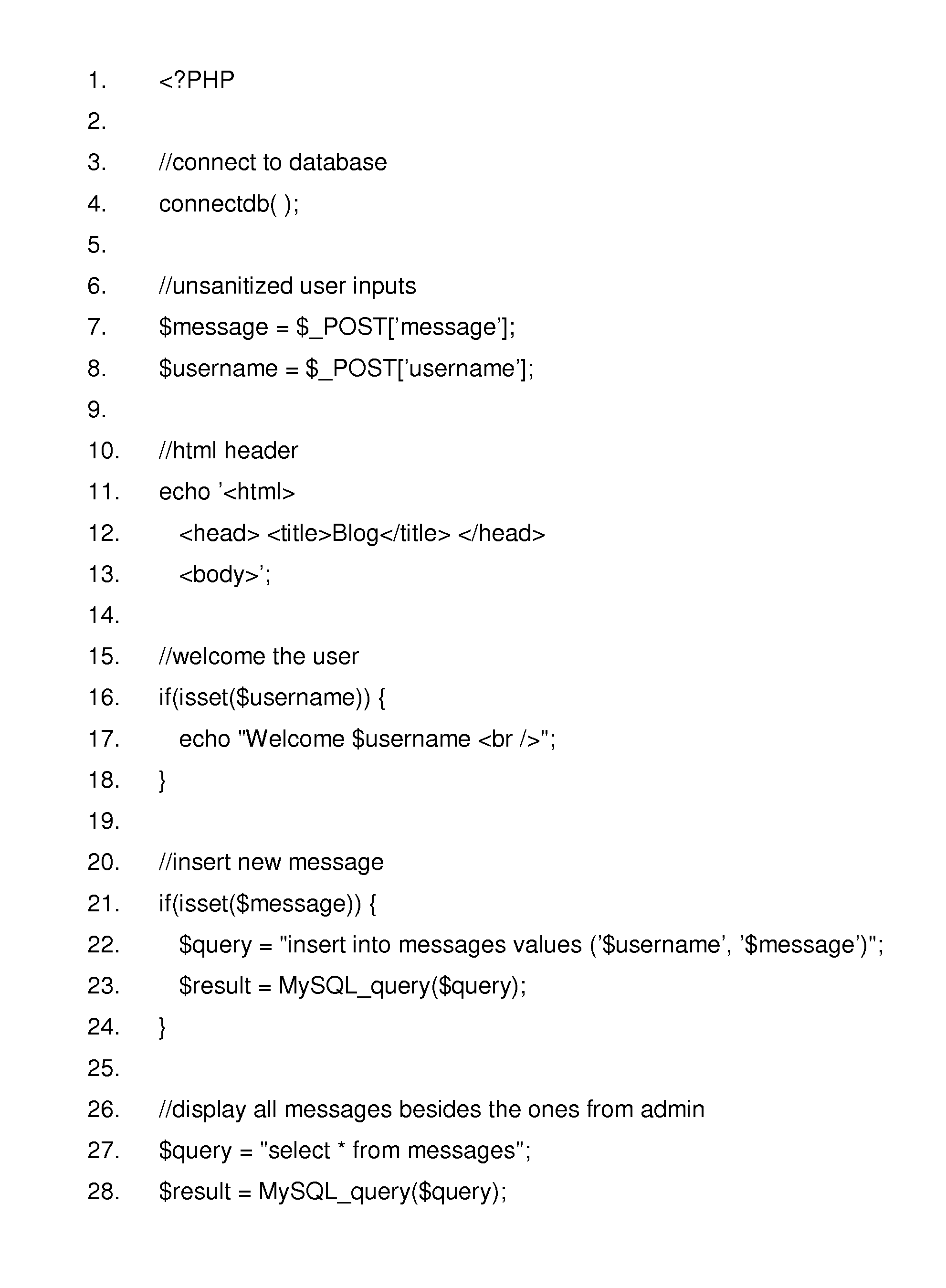
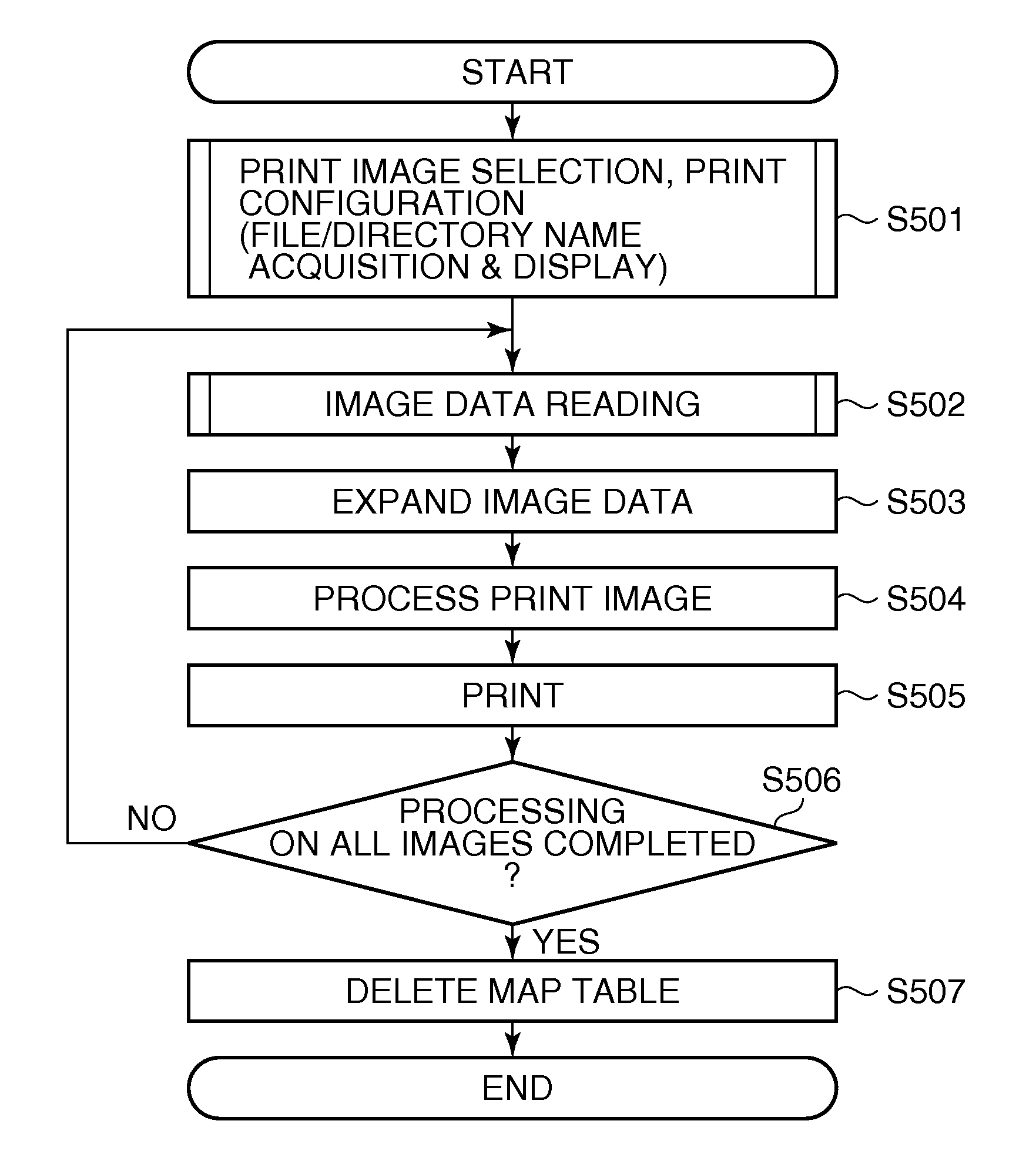
An information processing apparatus capable of reliably accessing files associated with file identification information generated based on more character code systems, without necessitating a large-capacity memory. When the information processing apparatus (MFP) acquires file identification information, a CPU of the MFP determines whether or not the MFP is capable of performing processing based on a predetermined character code system used for describing the identification information. When the MFP is not capable of performing processing based on the character code system, the CPU converts the identification information described in the predetermined character code system into substitute character codes processable thereby. Then, the CPU registers the substitute character codes and the original character codes before the conversion in a map table in association with each other. When the processing on the file is completed, the CPU deletes the substitute character codes and the original character codes from the map table.
Owner:CANON KK
System and methods for vehicle identification number validation
A method and apparatus is used to of validate a vehicle identification number (VIN). At least a first VIN having a plurality of characters in a plurality of positions is received. At least a first character in a first position of the first VIN to inspected to determine if the first character is included in a first set of valid characters. The first character is identified as being in error when the first character is not in the first set of valid characters. The first character is replaced with a substitute character.
Owner:FDI CONSULTING
Data input panel character conversion
ActiveUS20050099408A1Access to such functionalityInput/output for user-computer interactionDigital data processing detailsData inputSubstitute character
An in-place data input panel provides a user with access to a list of alternate characters to which displayed characters may be converted. The data input panel provides an indicator, such as an indicator bar, corresponding to segmentation of the characters. A user can change the segmentation of the characters by expanding or contracting the segmentation bar. Also, the user can access a drop-down menu listing alternate character choices corresponding to the characters in the segment indicated by the segmentation bar.
Owner:MICROSOFT TECH LICENSING LLC
Distribution contents forming method, contents distributing method and apparatus, and code converting method
InactiveUS20080028101A1Good effectSmall sizeSpecial service provision for substationCode conversionAlgorithmEngineering
Owner:SONY CORP
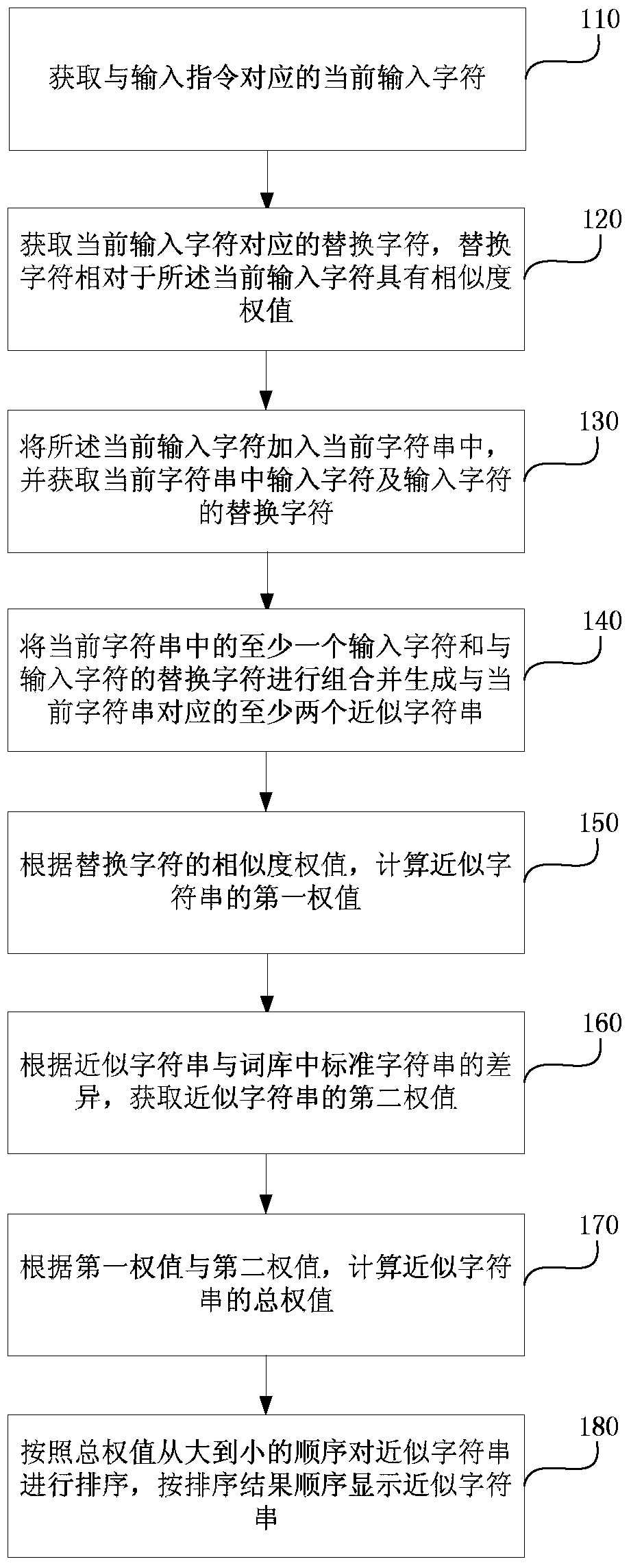
Character string input method and device
ActiveCN103699233AImprove input efficiencySolve the problem that the correct input cannot be effectively promptedInput/output processes for data processingKey pressingAlgorithm
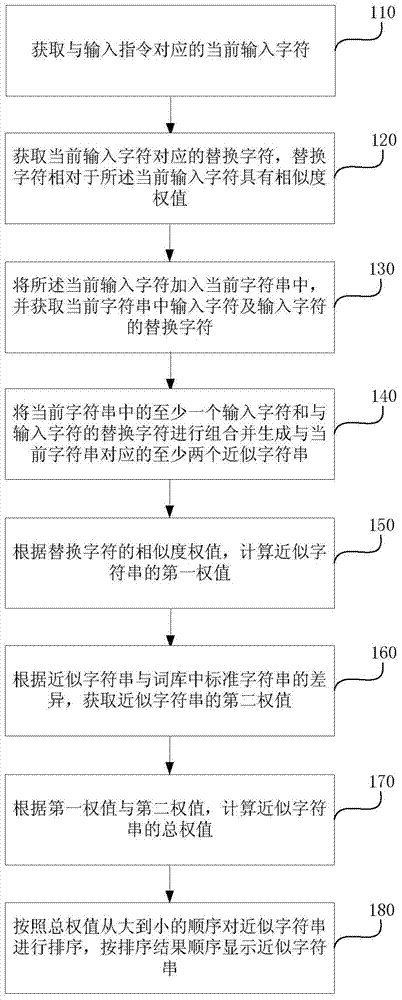
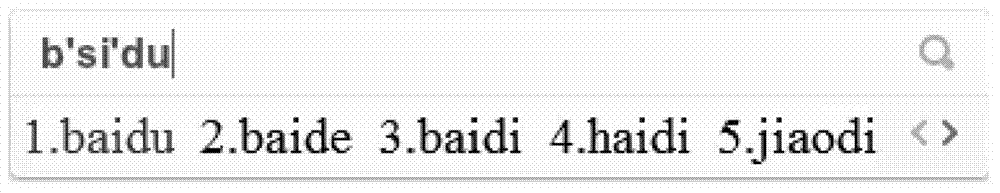
The invention discloses a character string input method and a character string input device. The method comprises the following steps of: acquiring an input character corresponding to an input instruct; acquiring a substitute character corresponding to the input character; adding the input character into a current character string; acquiring the input character and the substitute character of the input character in the current character string; generating an approximate character string corresponding to the current character string; calculating a first weight value of the approximate character string; acquiring a second weight value of the approximate character string according to difference between the approximate character string and a standard character string in a word database; calculating a total weight value of the approximate character string; sequencing the approximate character string; and displaying the approximate character string according to a sequence result. According to the method and device, correct input character string can be still acquired from selectable character string options even due to clicking or contacting other keys around an expected key by mistake during character string input at a client.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
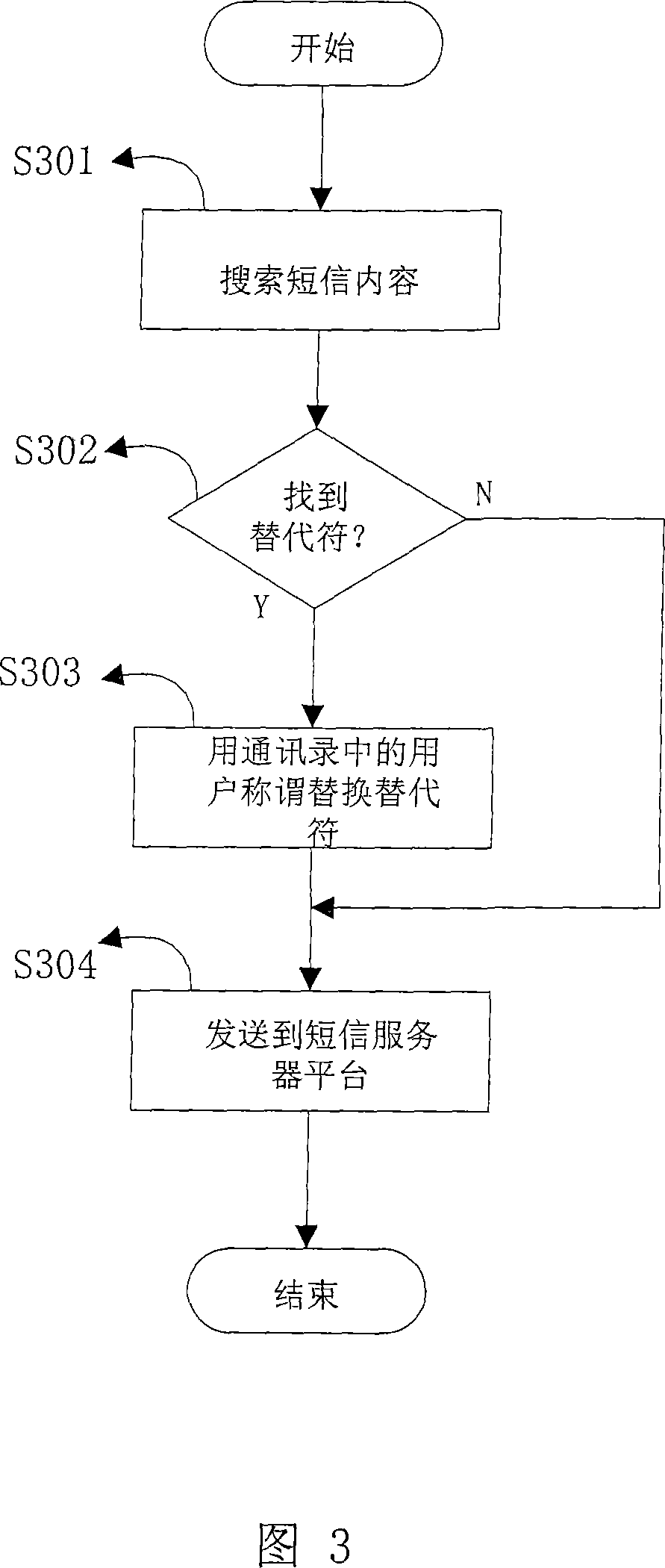
A method and system for adding names of target users in SMS group
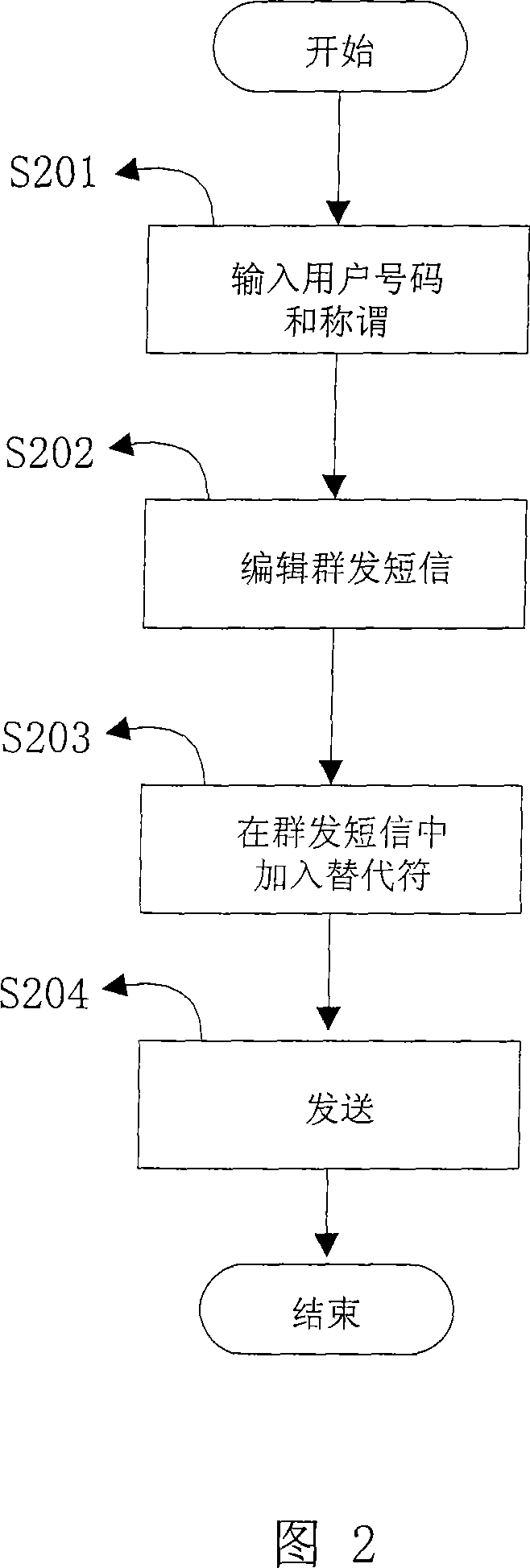
InactiveCN101127945ARadio/inductive link selection arrangementsMessaging/mailboxes/announcementsMobile Telephone NumberPersonalization
The utility model relates to a way and a system to add appellations of target users when mass-sending messages, which is to add individual appellations of target users automatically when mass-sending messages by use of the function module of mass-sending messages. Firstly, the mobile numbers and the appellations of target users are added to the communication list provided with the message send-receive terminal device by the user; then when compiling a mass-sending message, substitute characters required as an uniform regulation of the system are inputted in the positions where individual appellations of target users are to be presented; after the mass-sending message is well compiled, select mobile phone numbers for different target users from the communication list provided with the message send-receive terminal device and mass-send the message. Meanwhile the message mass-sending function module of the message send-receive terminal device receives the order of sending out the message; if substitute characters are detected, the substitute characters will be replaced with appellation of target users in the communication list corresponding to the phone mobile numbers of the target users; and then the message is sent out.
Owner:黄家昌 +1
Chinese language input system based on graphic form
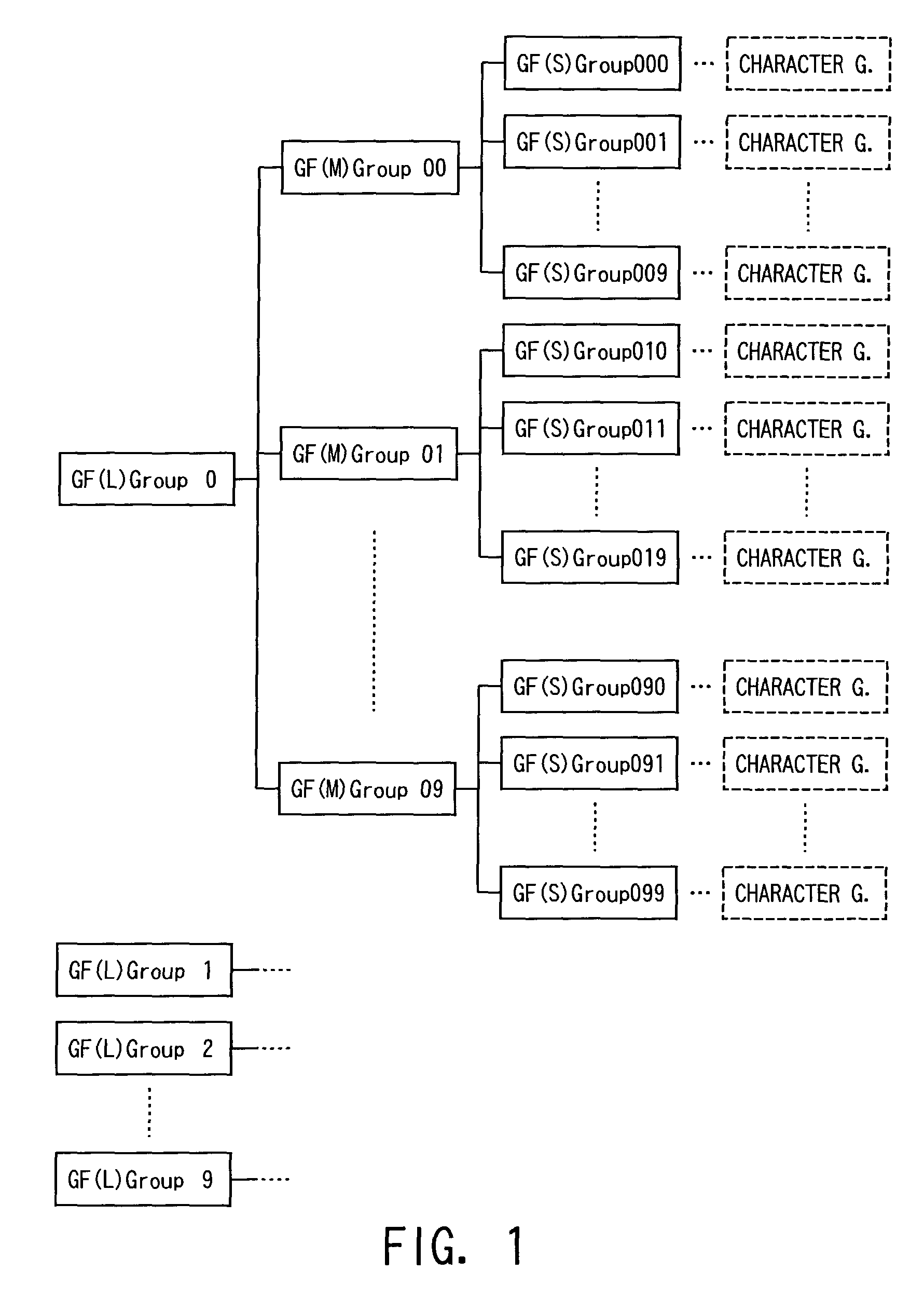
InactiveUS7058900B2Efficient inputCharacter and pattern recognitionSpecial data processing applicationsGraphicsChinese characters
Every Chinese character belongs to a small graphic form group which is created with respect to the radical of the character instead of character components. Every small graphic form group is incorporated into higher-level groups, i.e. medium graphic form groups, in turn every medium graphic form group is incorporated into higher-level groups, i.e. large graphic form groups. Input guidance is provided according to this hierarchy concerning graphic form. More specifically, the large groups are presented and one of them is selected by the first keystroke, the medium groups are presented and one of them is selected by the second keystroke, and the small groups are presented and one of them to which the desired character for input belongs is selected by the third keystroke. In this fashion, three keystrokes to a numeric keypad efficiently narrows down the alternative characters for conversion.
Owner:FUJITSU LTD
Data input panel character conversion
InactiveUS7406662B2Input/output for user-computer interactionDigital data processing detailsPattern recognitionData input
An in-place data input panel provides a user with access to a list of alternate characters to which displayed characters may be converted. The data input panel provides an indicator, such as an indicator bar, corresponding to segmentation of the characters. A user can change the segmentation of the characters by expanding or contracting the segmentation bar. Also, the user can access a drop-down menu listing alternate character choices corresponding to the characters in the segment indicated by the segmentation bar.
Owner:MICROSOFT TECH LICENSING LLC
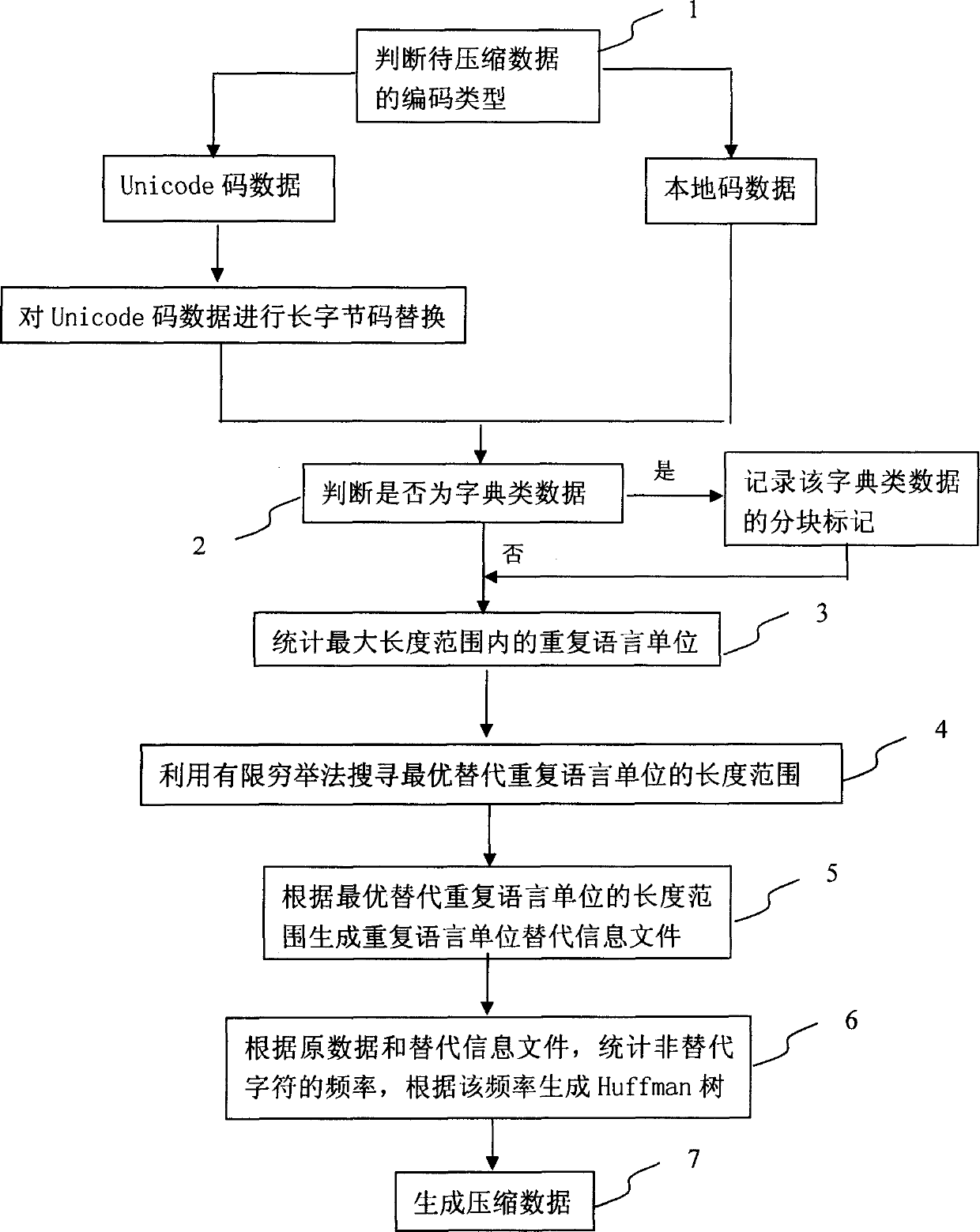
Data compression method by finite exhaustive optimization
InactiveCN1737791AIncrease the compression ratioGuaranteed adaptabilityCode conversionSpecial data processing applicationsData compressionHuman language
Owner:WUDI SCI & TECH (XIAN) CO LTD
Analysing character strings
InactiveUS20120141031A1Accurate readingRead easily, accurately, and quicklyReadingCharacter and pattern recognitionAlgorithmSubstitute character
A method for analyzing a character string, the method including: analyzing a character string to determine one of more characters of the character string; determining from a dictionary source, an alternative character string to the analyzed character string; comparing the analyzed character string with the alternative character string to determine a weighting factor for each of the characters of the analyzed character string relative to the positional arrangement of the characters in the alternative character string; and for each determined weighting factor, generating for each of the characters in the analyzed character string a corresponding character of a particular size as determined by the weighting factor.
Owner:IBM CORP
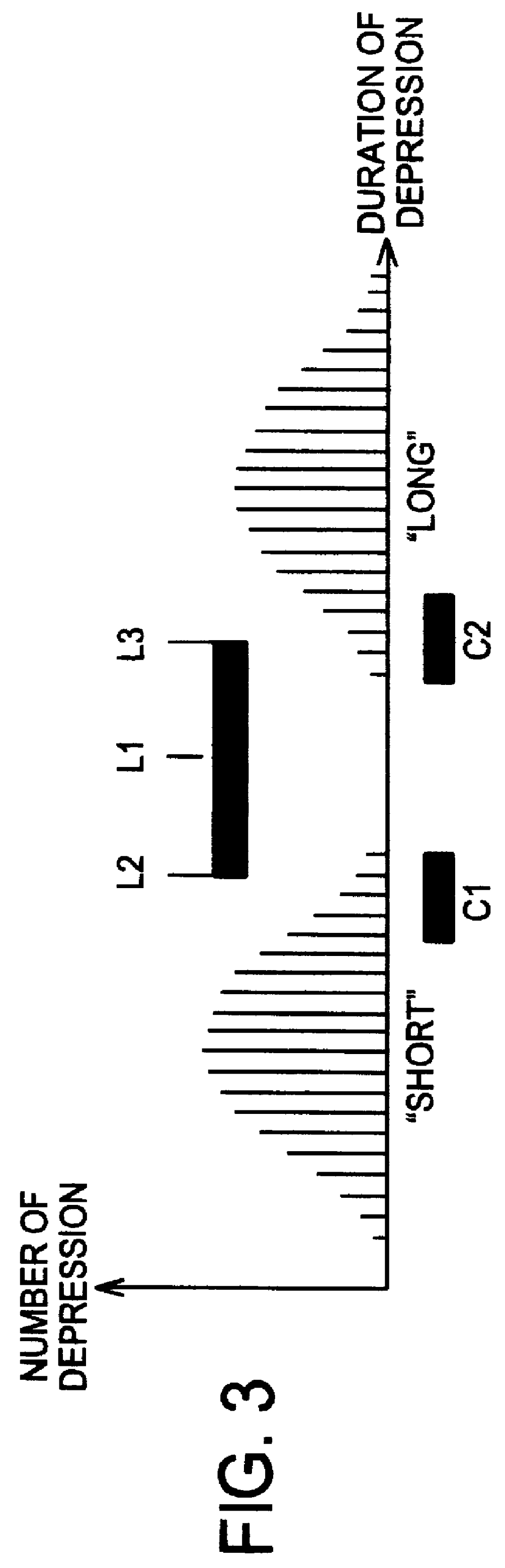
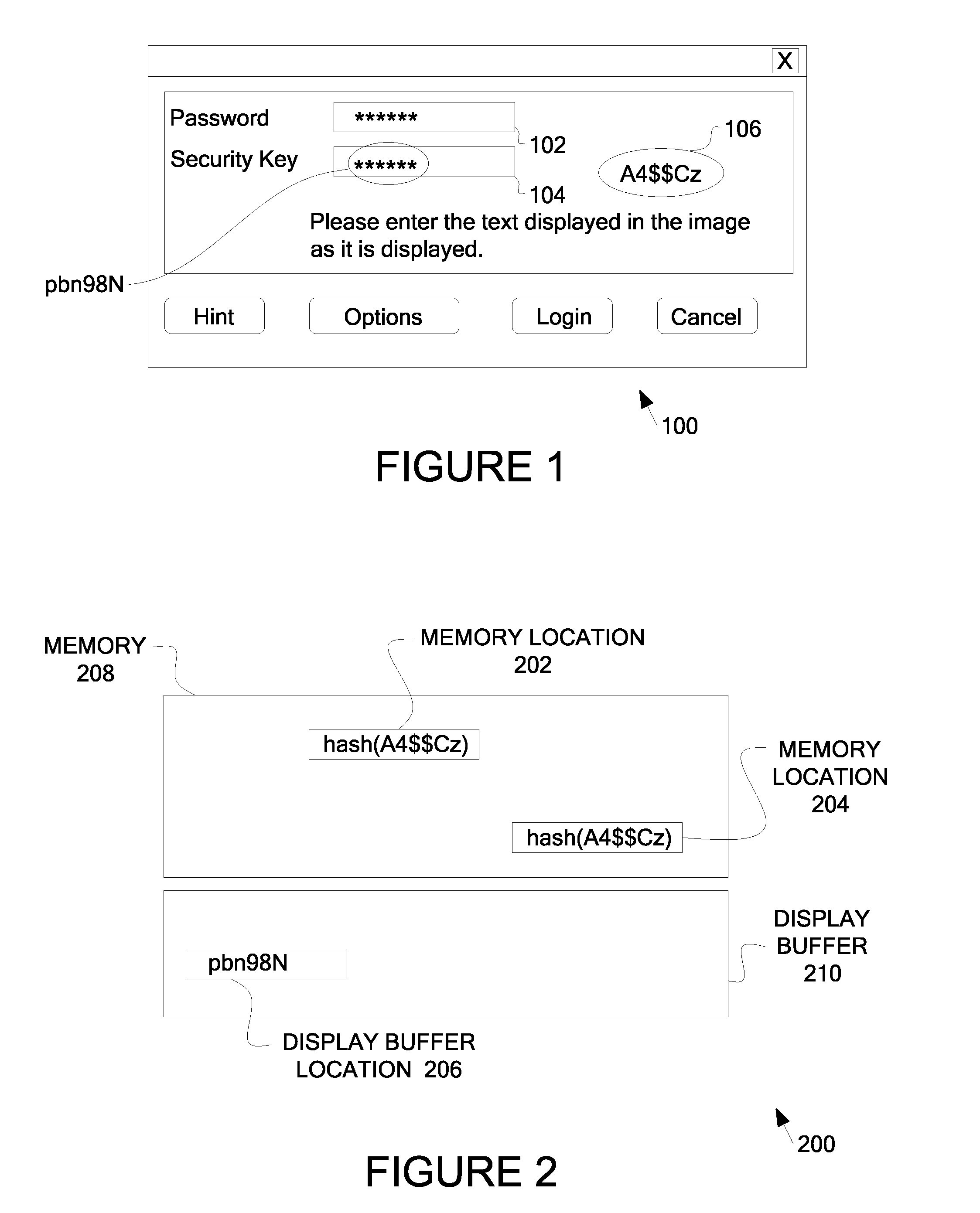
System and Method of Generating and Providing a Set of Randomly Selected Substitute Characters in Place of a User Entered Key Phrase
InactiveUS20090044284A1Digital data processing detailsAnalogue secracy/subscription systemsUser inputNumber generator
Systems and methods of generating and providing a set of randomly selected substitute characters in place of a user entered key phrase are described here. One embodiment includes receiving a key phrase input by a user to gain access to secured data, and, in response to receiving the user entered key phrase, randomly selecting a set of substitute characters and providing the set of substitute characters in place of the key phrase entered by the user. In one embodiment, the randomly selecting comprises using a random number generator to select from a substitute character from a pre-generated set of substitute characters for each character, number, or text of the user entered key phrase. In one embodiment, the providing the set of substitute characters further comprises providing the randomly selected set of substitute characters in a display buffer as the user entered key phrase.
Owner:MCM PORTFOLIO LLC
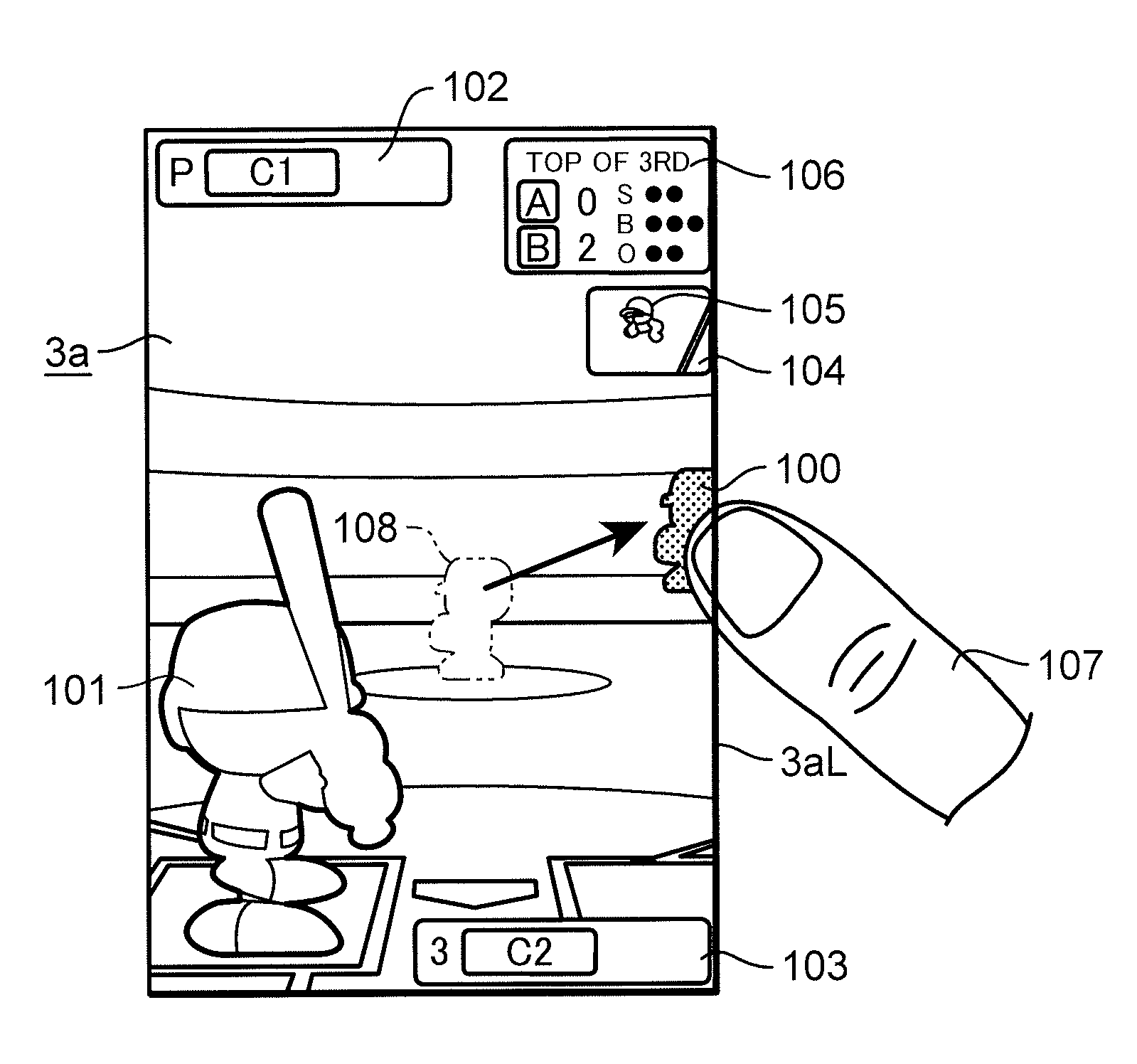
Game device which recognizes and replaces a substitution object participating in a competition game in a virtual space
ActiveUS9089776B2Easy to operateAvoid flowVideo gamesSpecial data processing applicationsVirtual spaceHuman–computer interaction
A game device including: a substituted-for character recognizing unit which recognizes a character to become a substitution object by bringing a finger 107 into contact with the character; a substituted-for character determination unit which determines the recognized character to be a substituted-for character by causing the recognized character to be moved to a substituted-for character determination region (an edge of a monitor 3a); and a candidate character list display unit which displays a candidate character list 109 on an image display unit based on the determination of the substituted-for character, wherein after determining a character who enters the game by bringing the finger 107 into contact with a character on the candidate list, the entering character is displayed on the image display unit in place of the substituted-for character.
Owner:KONAMI DIGITAL ENTERTAINMENT CO LTD
Captcha challenge incorporating obfuscated characters
InactiveUS20160103983A1Digital data processing detailsAnalogue secracy/subscription systemsAlgorithmSoftware engineering
A method for determining if a user of a computer system is a human. A processor receives an indication that a computer security program is needed and acquires at least one image depicting a first string of characters including at least a first and second set of one or more characters. A processor assigns a substitute character to be used as input for each of the second set of one or more characters. A processor presents the at least one image and an indication of the substitute character and when to use the substitute character to the user. A processor receives a second string of characters from the user. A processor determines whether the second string of characters substantially matches the first string of characters based on the substitute character assigned to each of the second set of one or more characters and determines whether the user is a human.
Owner:KYNDRYL INC
Free typesetting printing method
InactiveCN105511820AReduce in quantityRealize free typesetting printingDigital output to print unitsContent formatEquipment use
Owner:BOOMHOPE INFORMATION TECH CO LTD
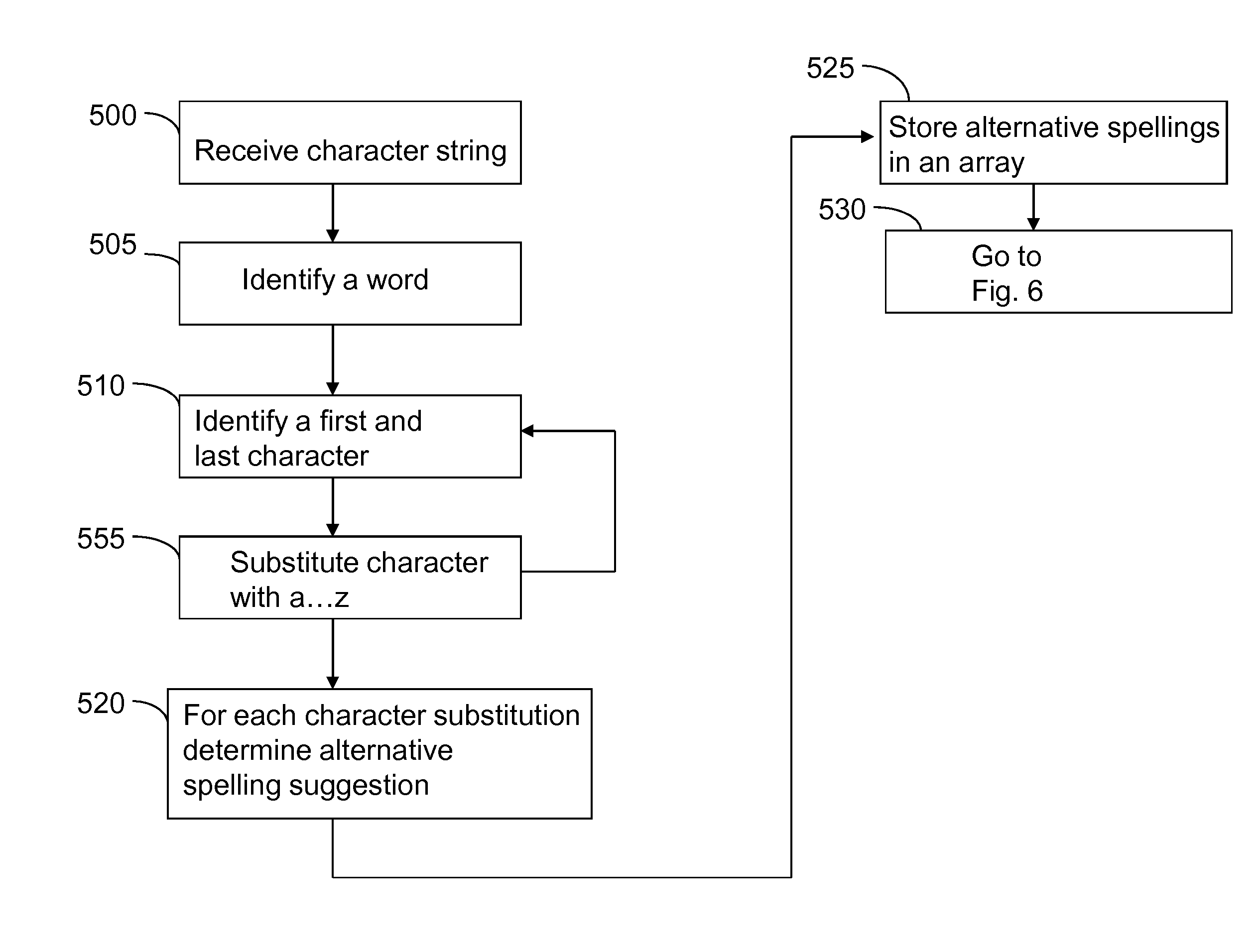
Determining an alternative character string
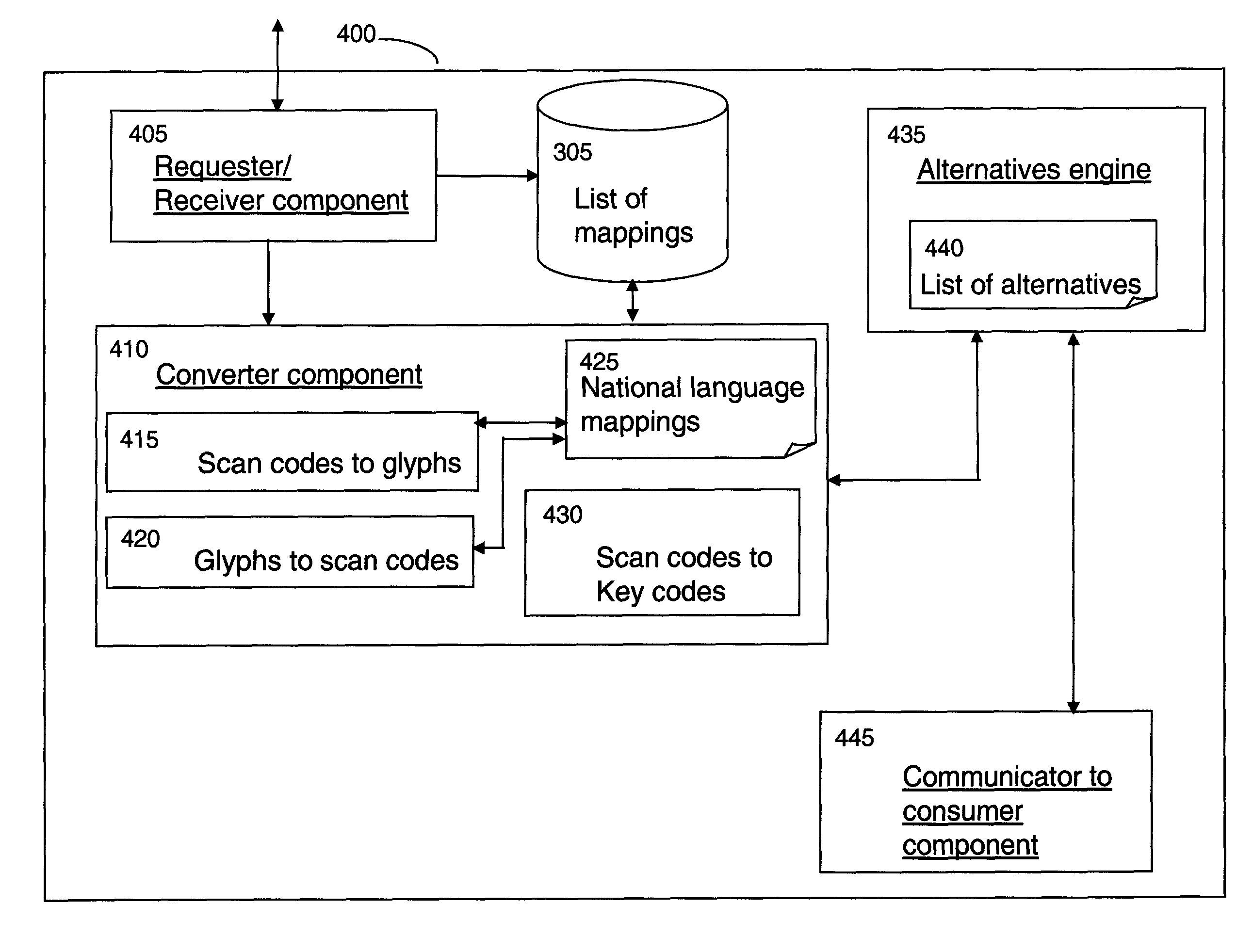
ActiveUS8232901B2Electric signal transmission systemsNatural language data processingGlyphSubstitute character
Method and apparatus for determining an alternative character string, in response to an invalid character string being received by a consumer application, wherein the invalid character string is derived from the selection of a series of keyboard keys in combination with a modifier key and wherein each key is associated with at least one glyph. An embodiment includes: a converter component for converting each glyph of the invalid character string into a first format; a converter component for parsing each of the converted first formats into a second format; an alternatives engine for determining from each of the second formats a third format which can be derived from a combination of a selection of the key and an alternative modifier key; and a converter component for converting each of the determined third formats into their associated glyphs for compiling into a list of alternative character strings.
Owner:INT BUSINESS MASCH CORP
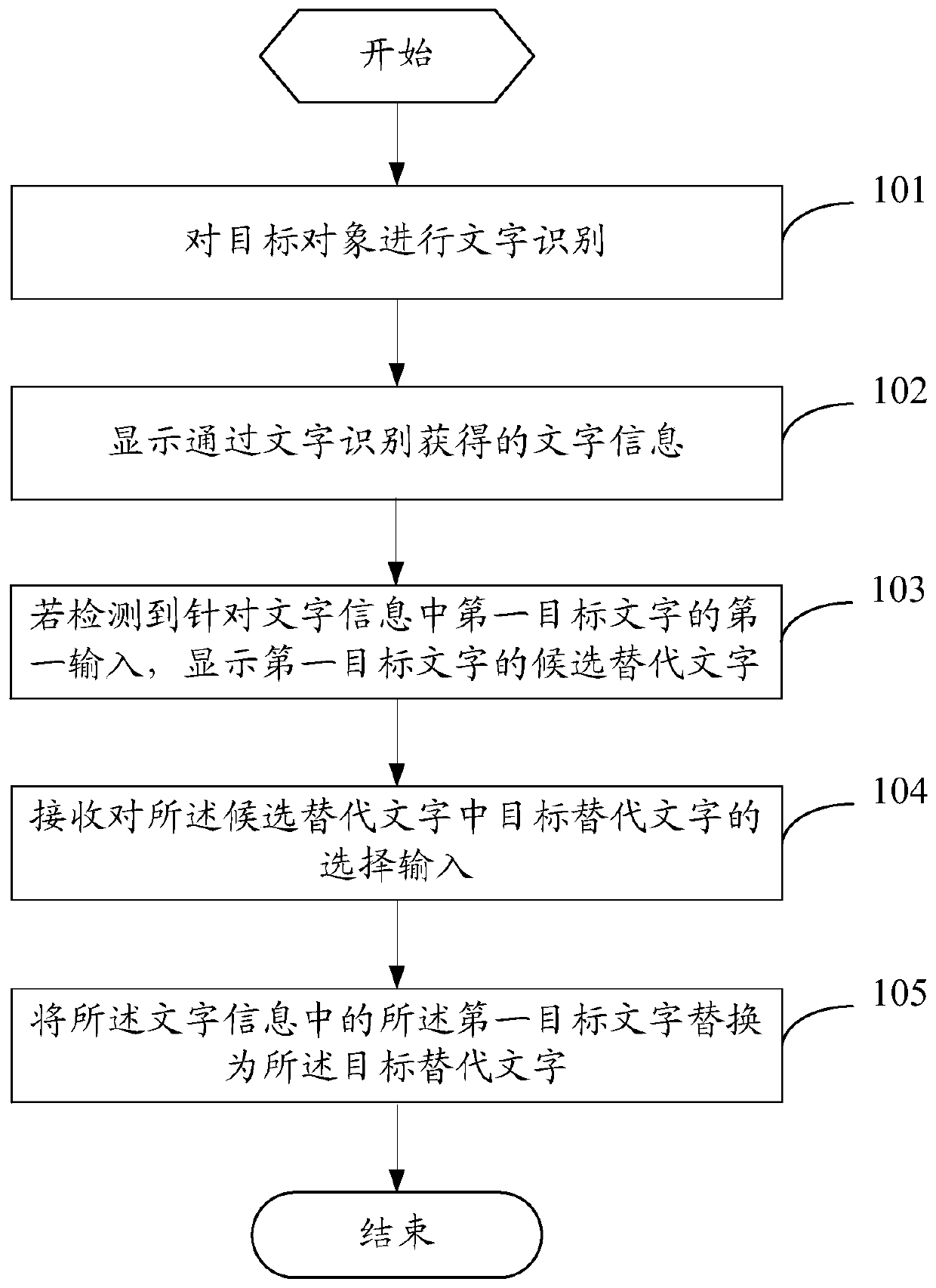
Character processing method and terminal
InactiveCN110008884ASimplify modification operationsImprove modification efficiencyCharacter and pattern recognitionNatural language data processingComputer terminalSubstitute character
The invention provides a character processing method and a terminal. The method comprises the following steps: carrying out character recognition on a target object; displaying the character information obtained through character recognition; if a first input for a first target character in the character information is detected, displaying a candidate substitute character of the first target character; receiving selection input of a target substitution character in the candidate substitution characters; and replacing the first target character in the character information with the target replacement character. Thus, the first target character in the character information can be directly modified, the modification operation on the first target character can be simplified, and the modification efficiency is improved.
Owner:VIVO MOBILE COMM CO LTD
Distribution contents forming method, contents distributing method and apparatus, and code converting method
InactiveUS7653752B2Good effectSmall sizeSpecial service provision for substationCode conversionAlgorithmEngineering
Owner:SONY CORP
Computer product, searching apparatus, and searching method
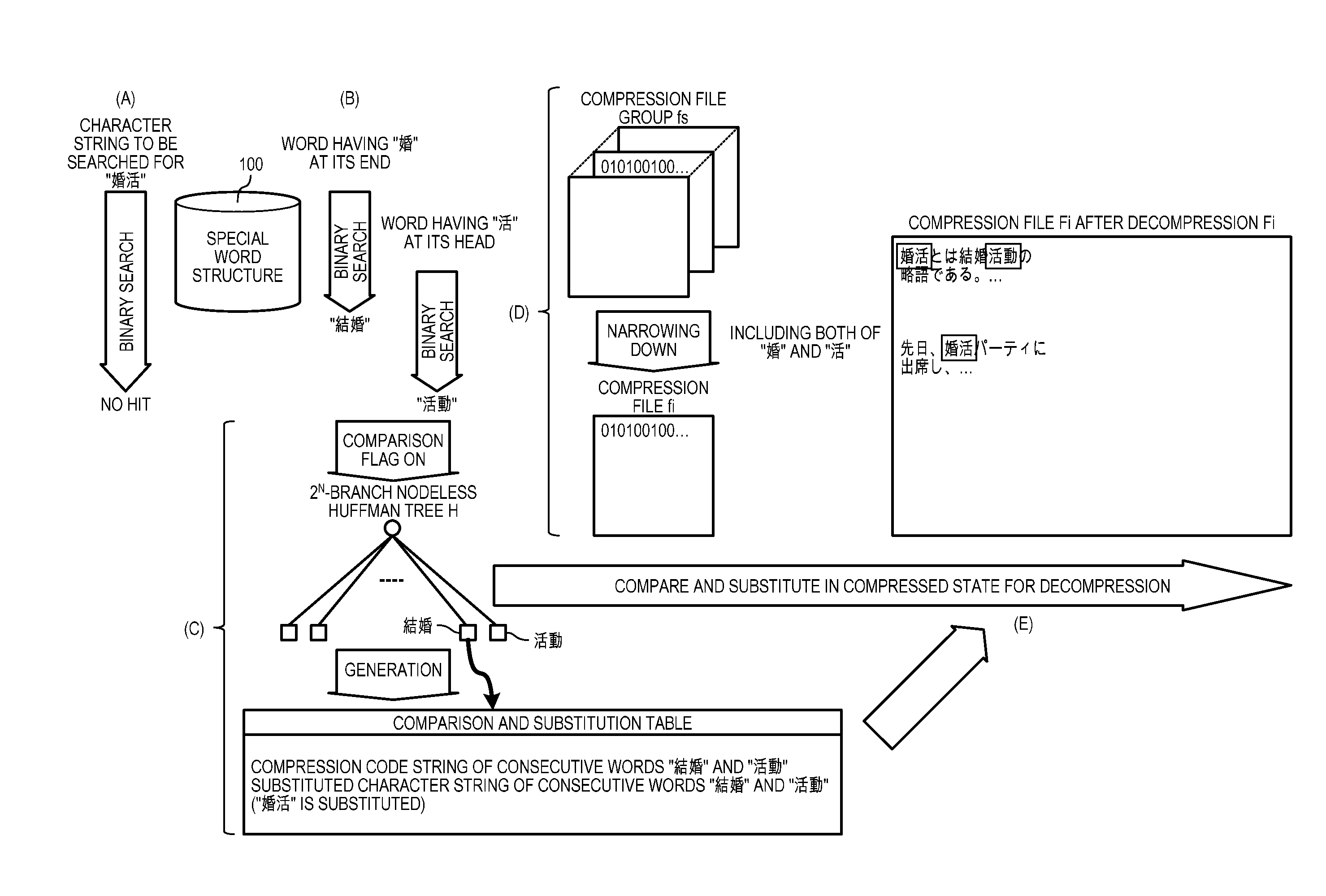
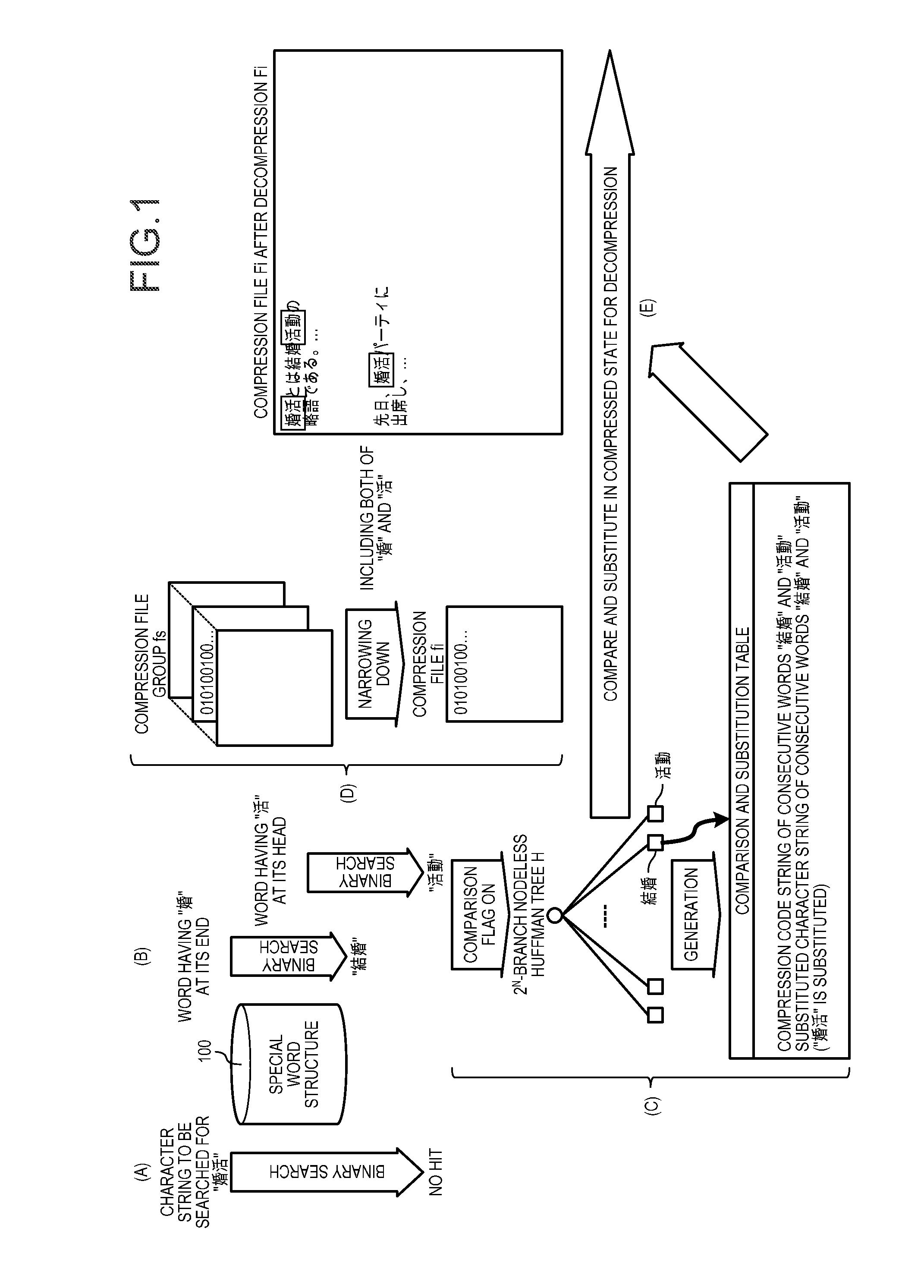
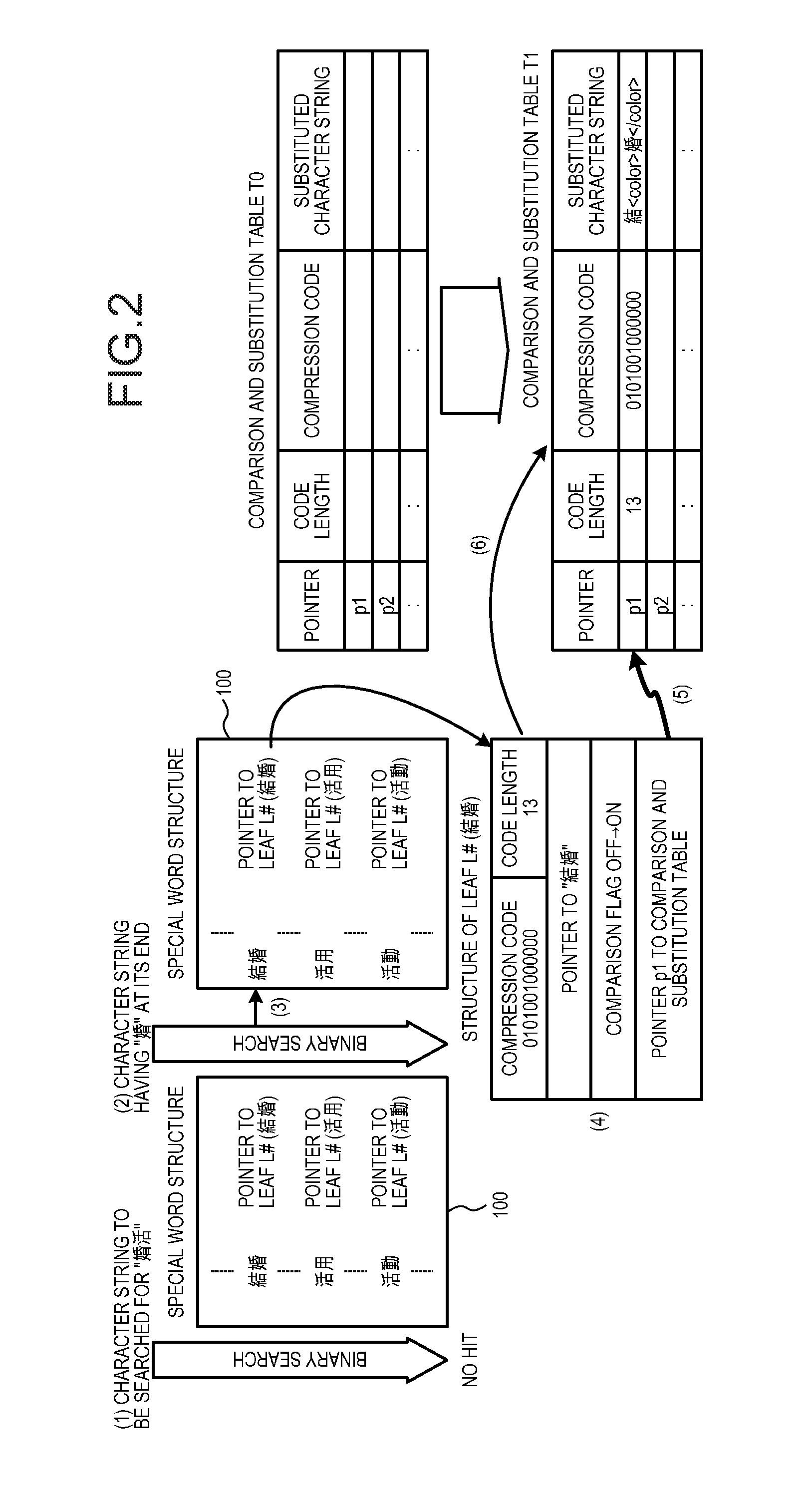
ActiveUS20130346443A1Digital data information retrievalDigital data processing detailsTheoretical computer scienceObject file
A compression file formed by compressing an object file is compared in a compressed state with a compression code string that matches with a compression character string of a character string to be searched for. The compression code string acquiring no match as the result of the comparison is decompressed as it is. On the other hand, the compression code string acquiring match is substituted with a substituted character string in a comparison and substitution table generated in advance.
Owner:FUJITSU LTD
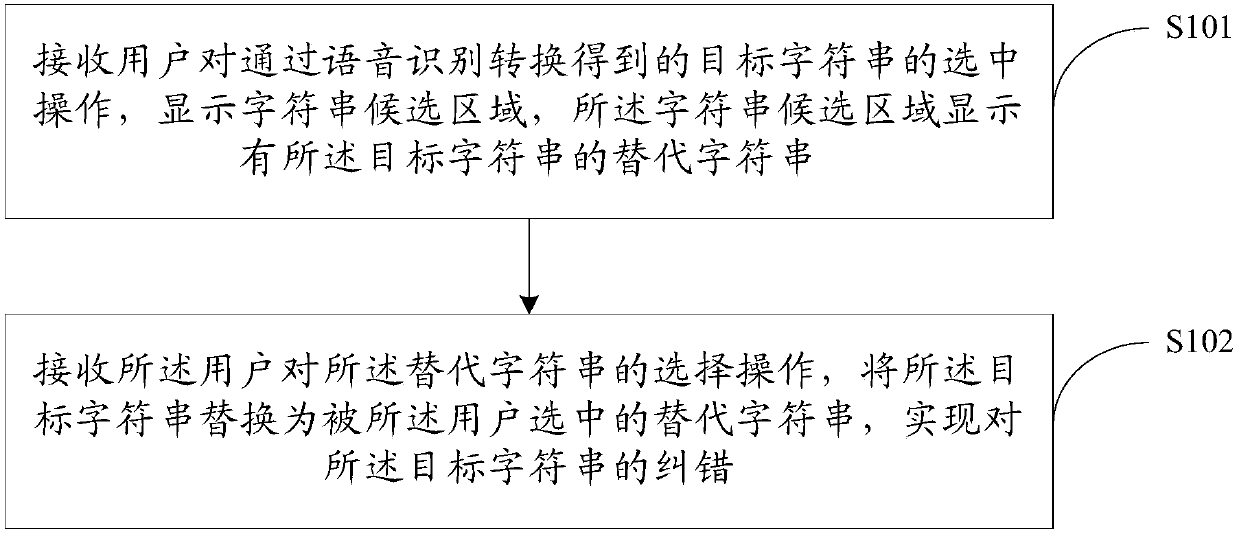
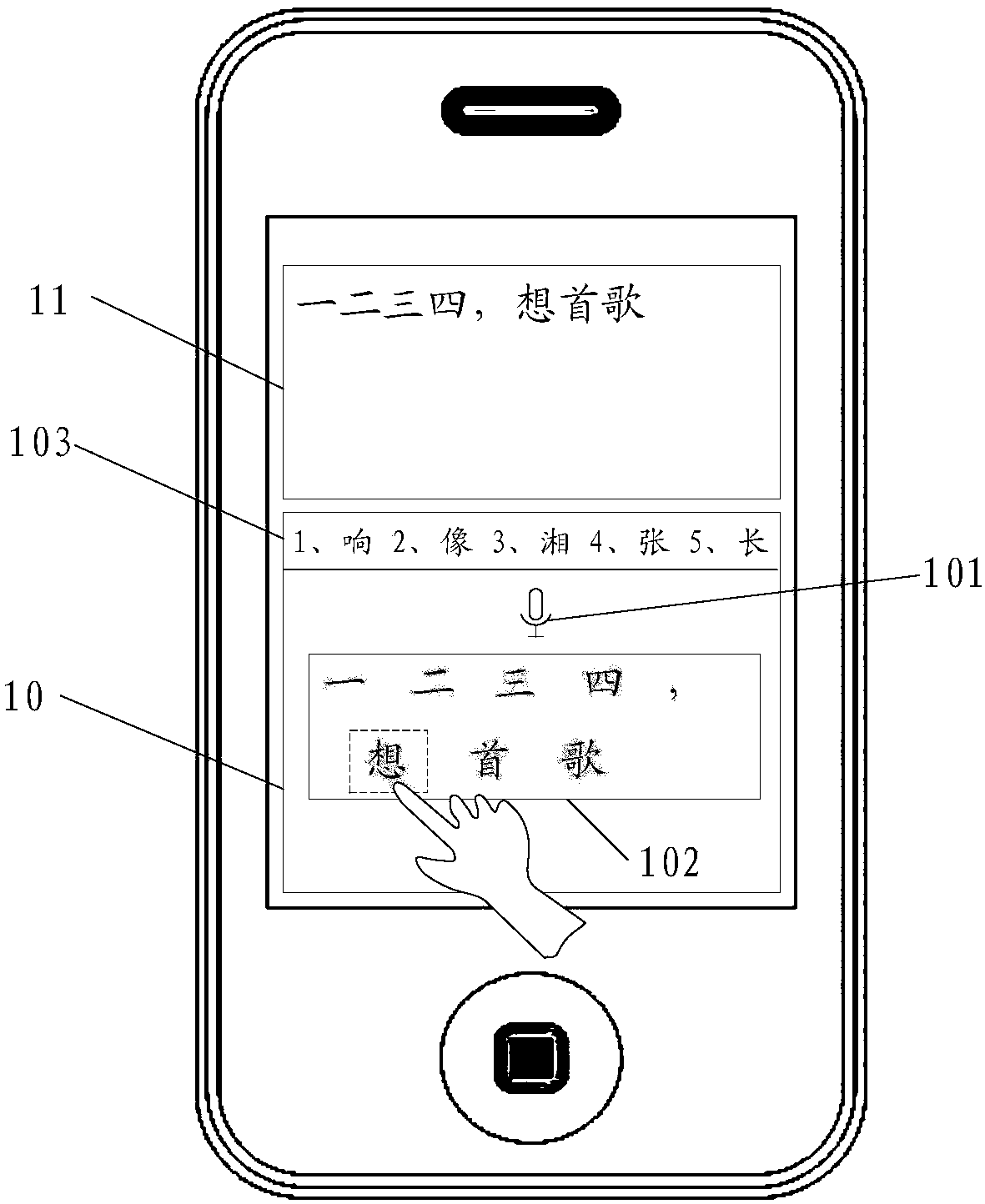
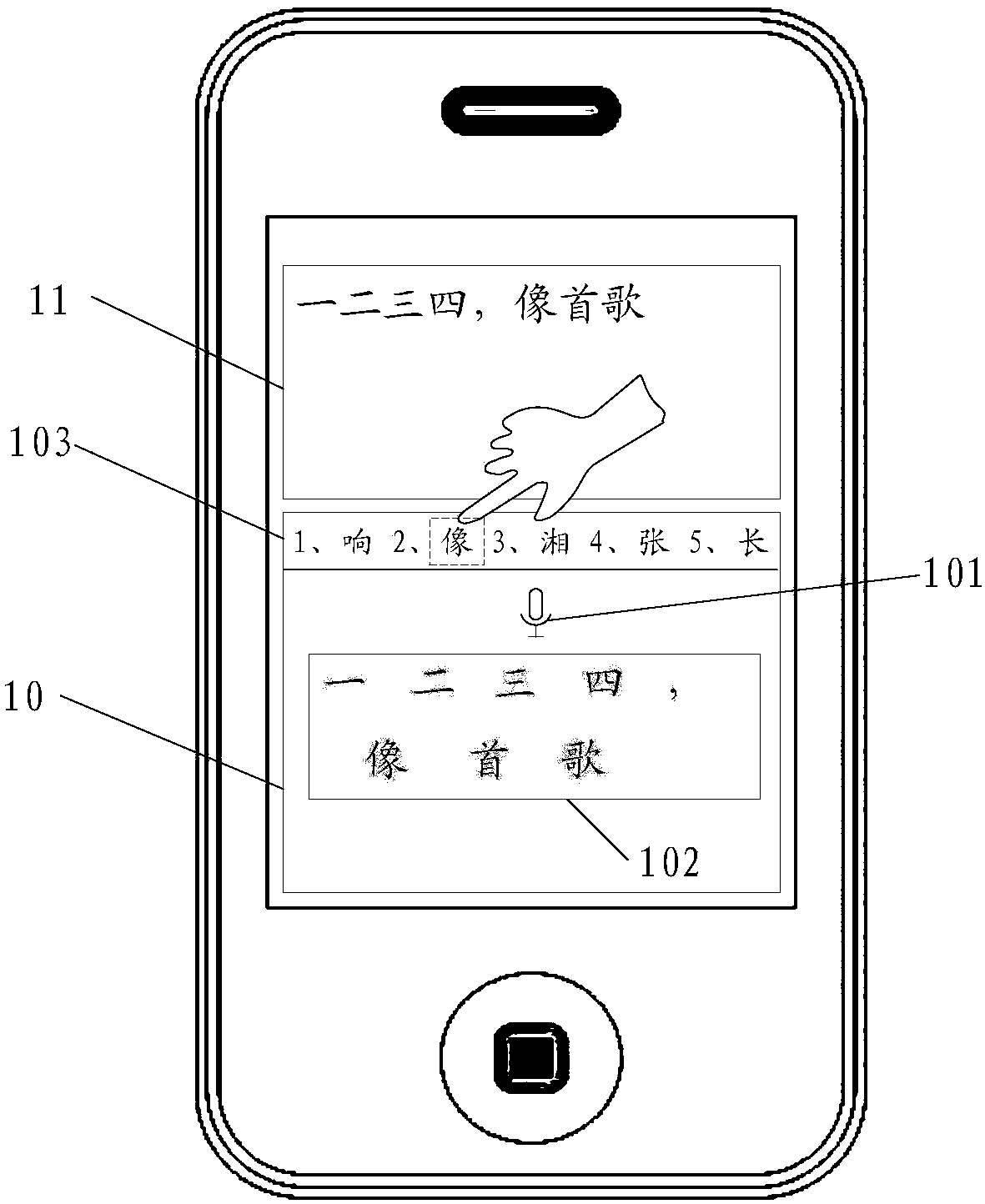
Character string error correction method and device
PendingCN109740142AImprove experienceImprove error correction efficiencySpecial data processing applicationsInput/output processes for data processingSubstitute characterCorrection method
The embodiment of the invention discloses a character string error correction method and device. Error correction efficiency and user experience of a character string are improved. The method comprises the steps that a selection operation of a user on a target character string obtained through speech recognition conversion is received, a character string candidate area is displayed, and a replacement character string of the target character string is displayed in the character string candidate area; and receiving a selection operation of the user on the alternative character string, and replacing the target character string with the alternative character string selected by the user to realize error correction of the target character string.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Analysing character strings
InactiveUS8805095B2Read easily, accurately, and quicklyMore legibleReadingCharacter and pattern recognitionAlgorithmSubstitute character
A method for analyzing a character string, the method including: analyzing a character string to determine one of more characters of the character string; determining from a dictionary source, an alternative character string to the analyzed character string; comparing the analyzed character string with the alternative character string to determine a weighting factor for each of the characters of the analyzed character string relative to the positional arrangement of the characters in the alternative character string; and for each determined weighting factor, generating for each of the characters in the analyzed character string a corresponding character of a particular size as determined by the weighting factor.
Owner:INT BUSINESS MASCH CORP
Information processing apparatus, method of controlling the same, and storage medium
InactiveCN102077178AEasy accessDigital data information retrievalNatural language data processingMass storageInformation processing
An information processing apparatus capable of reliably accessing files associated with file identification information generated based on more character code systems, without necessitating a large-capacity memory. When the information processing apparatus (MFP) acquires file identification information, a CPU of the MFP determines whether or not the MFP is capable of performing processing based on a predetermined character code system used for describing the identification information. When the MFP is not capable of performing processing based on the character code system, the CPU converts the identification information described in the predetermined character code system into substitute character codes processable thereby. Then, the CPU registers the substitute character codes and the original character codes before the conversion in a map table in association with each other. When the processing on the file is completed, the CPU deletes the substitute character codes and the original character codes from the map table.
Owner:CANON KK
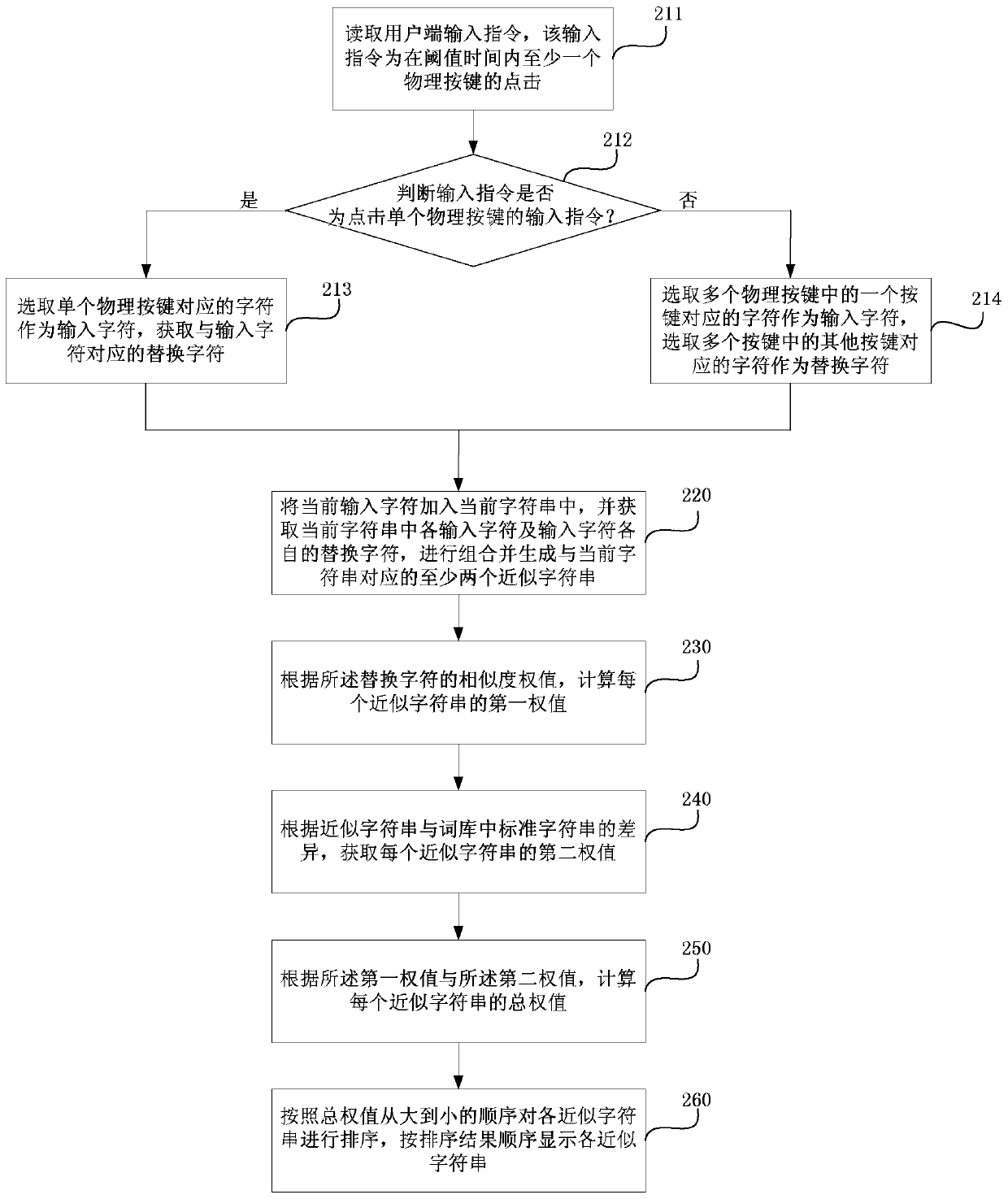
Character string input method and input device
ActiveCN103699233BImprove input efficiencySolve the problem that the correct input cannot be effectively promptedInput/output processes for data processingAlgorithmTheoretical computer science
The invention discloses a character string input method and a character string input device. The method comprises the following steps of: acquiring an input character corresponding to an input instruct; acquiring a substitute character corresponding to the input character; adding the input character into a current character string; acquiring the input character and the substitute character of the input character in the current character string; generating an approximate character string corresponding to the current character string; calculating a first weight value of the approximate character string; acquiring a second weight value of the approximate character string according to difference between the approximate character string and a standard character string in a word database; calculating a total weight value of the approximate character string; sequencing the approximate character string; and displaying the approximate character string according to a sequence result. According to the method and device, correct input character string can be still acquired from selectable character string options even due to clicking or contacting other keys around an expected key by mistake during character string input at a client.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Mode for preventing personal information for being lost and stolen
InactiveCN105512987AAvoid Personal Information QuestionsRemove real concernsData processing applicationsInternet privacyData management
The invention discloses a mode for preventing personal information for being lost and stolen. The mode employs an authentication module for personal information matching through authorization and authentication, employs a substitute character which is autonomously set according to a rule, starts with the authentication of a personal name, is used for daily signature and work of persons, customs clearance and preserve basis, and forms a release link of the personal true identity with retained information and data. A functional department obtains or gathers the personal true information according to the duty and authority through a data management and control center or a related department, thereby achieving an effect of preventing the personal information from being leaked, improving the office efficiency, enlarging the application range, and improving the building of a social safety protection network.
Owner:叶春林
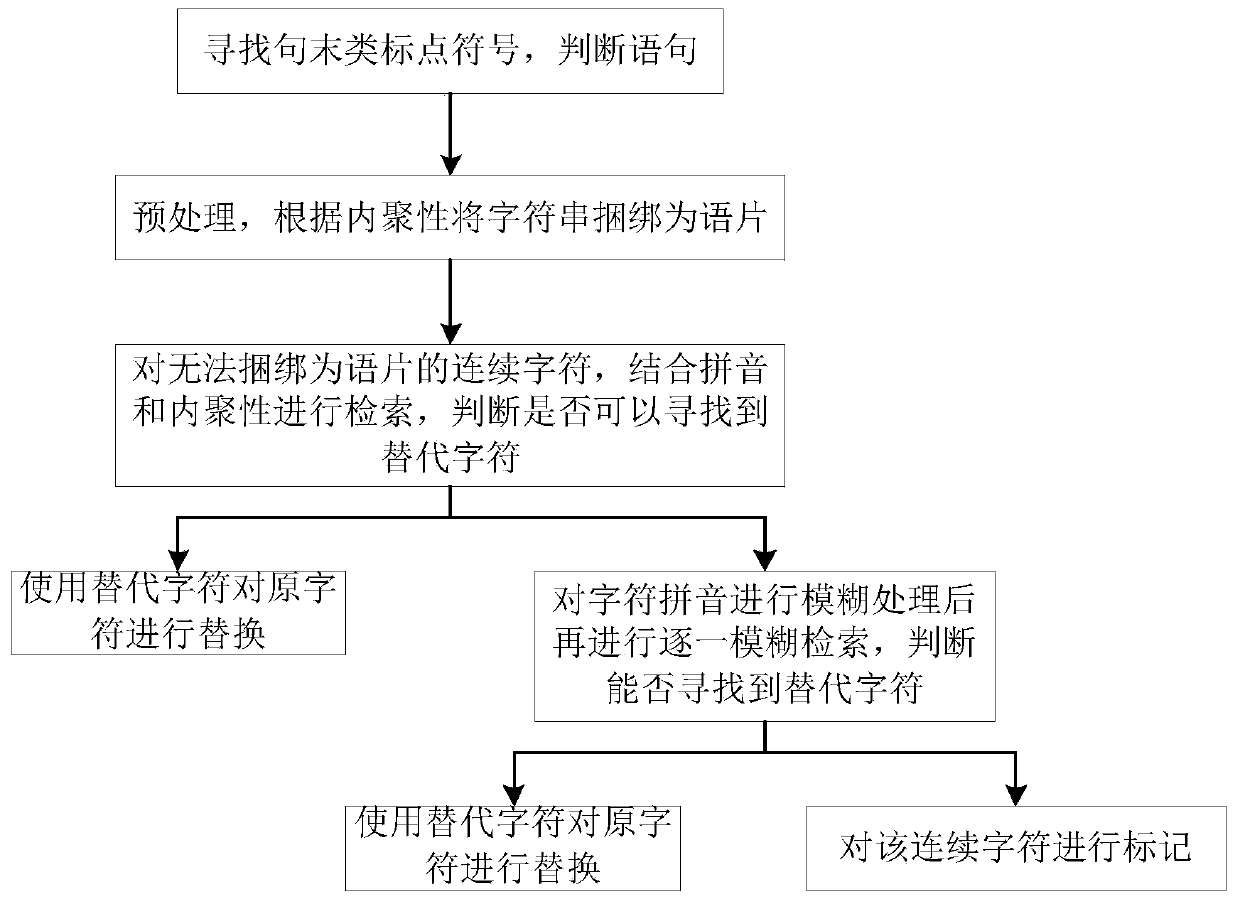
Online character error correction method and system
ActiveCN110457695AEffective error correctionDigital data information retrievalSpecial data processing applicationsCharacter recognitionSubstitute character
The invention discloses an online character error correction method and system. The online character error correction method is characterized in that characters input by a user are recognized as sentences, and the character string is bound into a speech slice according to cohesiveness among characters in the statement, so as to identify whether two or more continuous characters in the statement cannot be bundled into a speech slice or not, so that the possibility of wrongly written characters is high; as in the process of typing the characters by the user, wrongly written characters caused bypinyin input selection errors often occur, the alternative characters with the same pinyin are retrieved to replace wrongly written characters in the original characters; and due to the fact that in the character typing process of the user, wrongly written characters caused by a single pinyin typing error often occur, fuzzy processing and fuzzy retrieval are carried out on any bit in pinyin of allthe characters, and replacement characters are searched for to replace the wrongly written characters, and online character error correction can be effectively carried out on the characters typed bythe user.
Owner:安徽火蓝数据有限公司
Information processing apparatus, method of controlling the same, and storage medium
InactiveUS9405760B2Reliably access files associatedDigital data information retrievalDigital data processing detailsInformation processingMass storage
An information processing apparatus capable of reliably accessing files associated with file identification information generated based on more character code systems, without necessitating a large-capacity memory. When the information processing apparatus (MFP) acquires file identification information, a CPU of the MFP determines whether or not the MFP is capable of performing processing based on a predetermined character code system used for describing the identification information. When the MFP is not capable of performing processing based on the character code system, the CPU converts the identification information described in the predetermined character code system into substitute character codes processable thereby. Then, the CPU registers the substitute character codes and the original character codes before the conversion in a map table in association with each other. When the processing on the file is completed, the CPU deletes the substitute character codes and the original character codes from the map table.
Owner:CANON KK
Code data processing method and device and electronic equipment
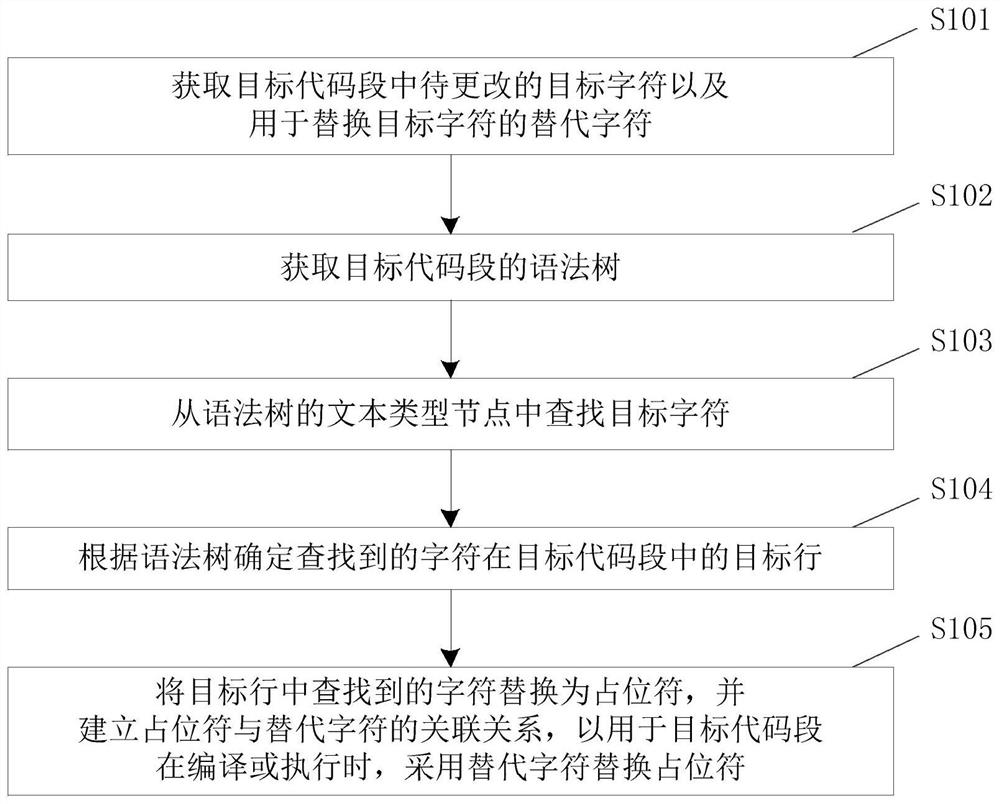
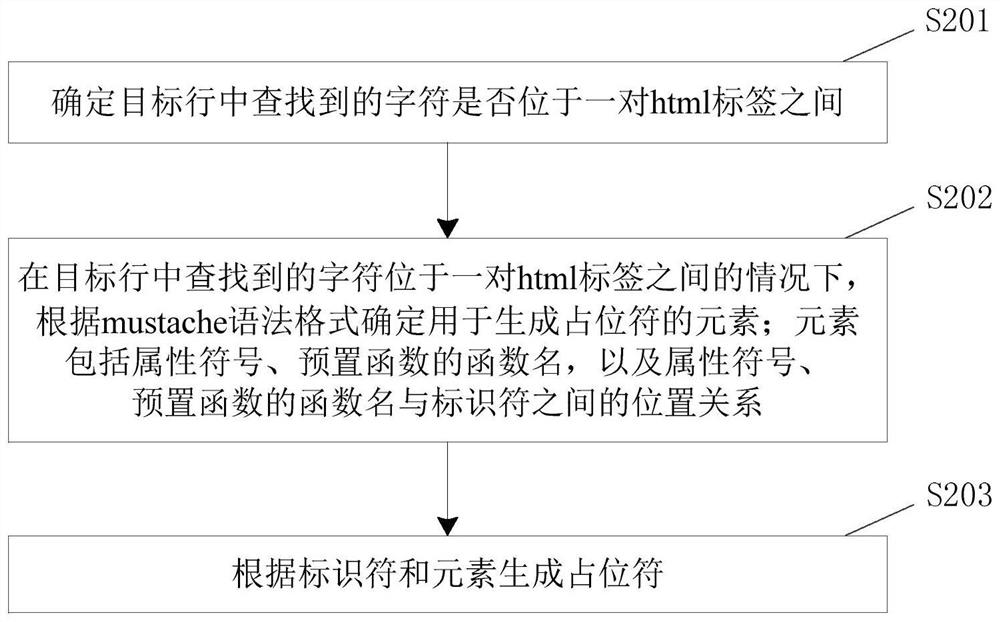
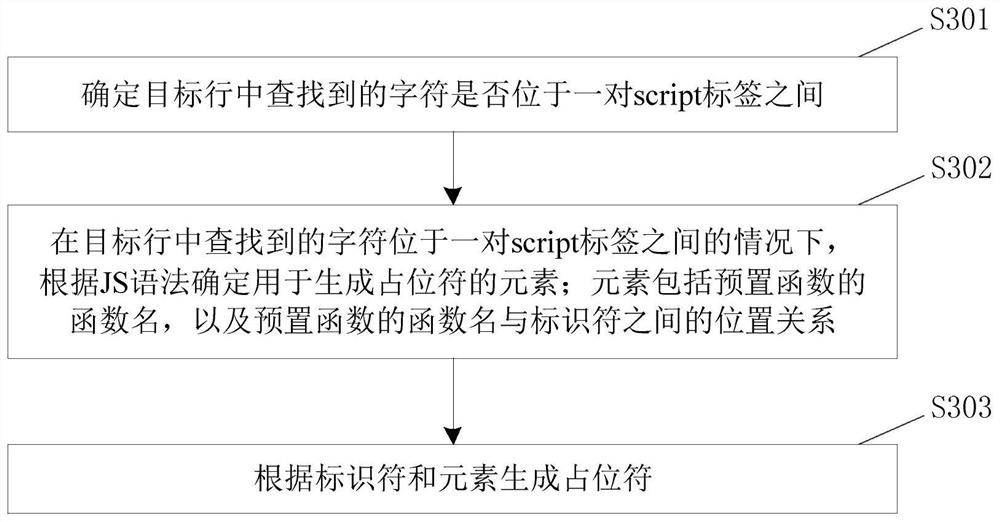
PendingCN113961192ANo abnormal problemsAccurate identificationCode compilationObject codeTarget line
The invention discloses a code data processing method and device and electronic equipment, and relates to the technical field of automatic coding. The method comprises the steps of obtaining a to-be-changed target character in a target code segment and a replacement character used for replacing the target character; obtaining a syntax tree of the target code segment; searching a target character from a text type node of the syntax tree; determining a target row of the searched character in the target code segment according to the syntax tree; and replacing the character found in the target line with a placeholder, and establishing an association relationship between the placeholder and the replacement character so as to replace the placeholder with the replacement character when the target code segment is compiled or executed. According to the scheme, the problem that existing character replacement is low in replacement accuracy and replacement efficiency is solved, and the technical effect of effectively improving the character replacement accuracy and replacement efficiency is achieved.
Owner:CHINA CONSTRUCTION BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com