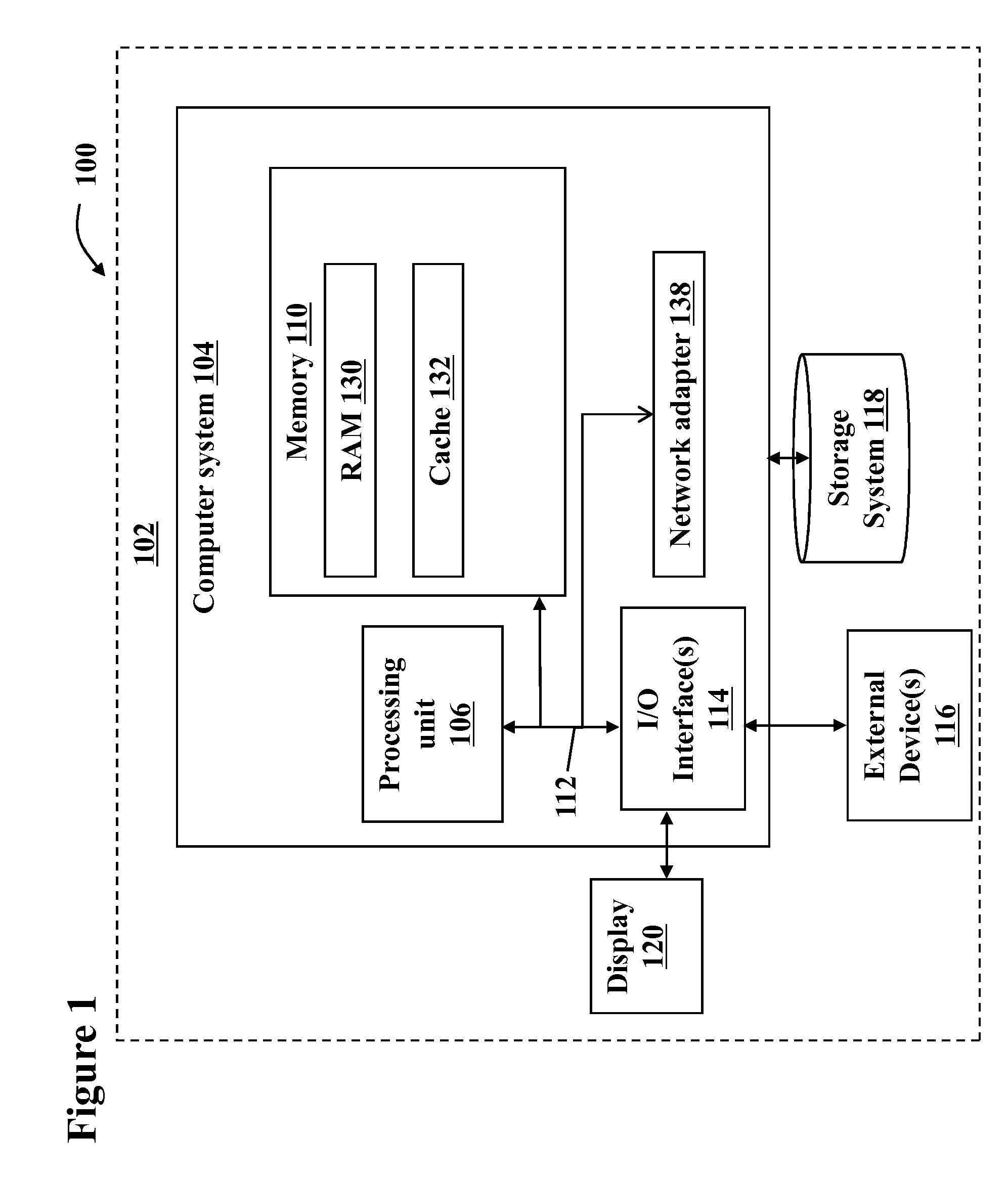
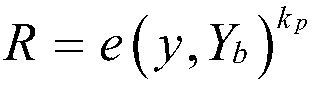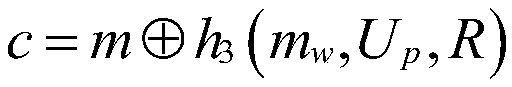Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
36 results about "Surrogate key" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
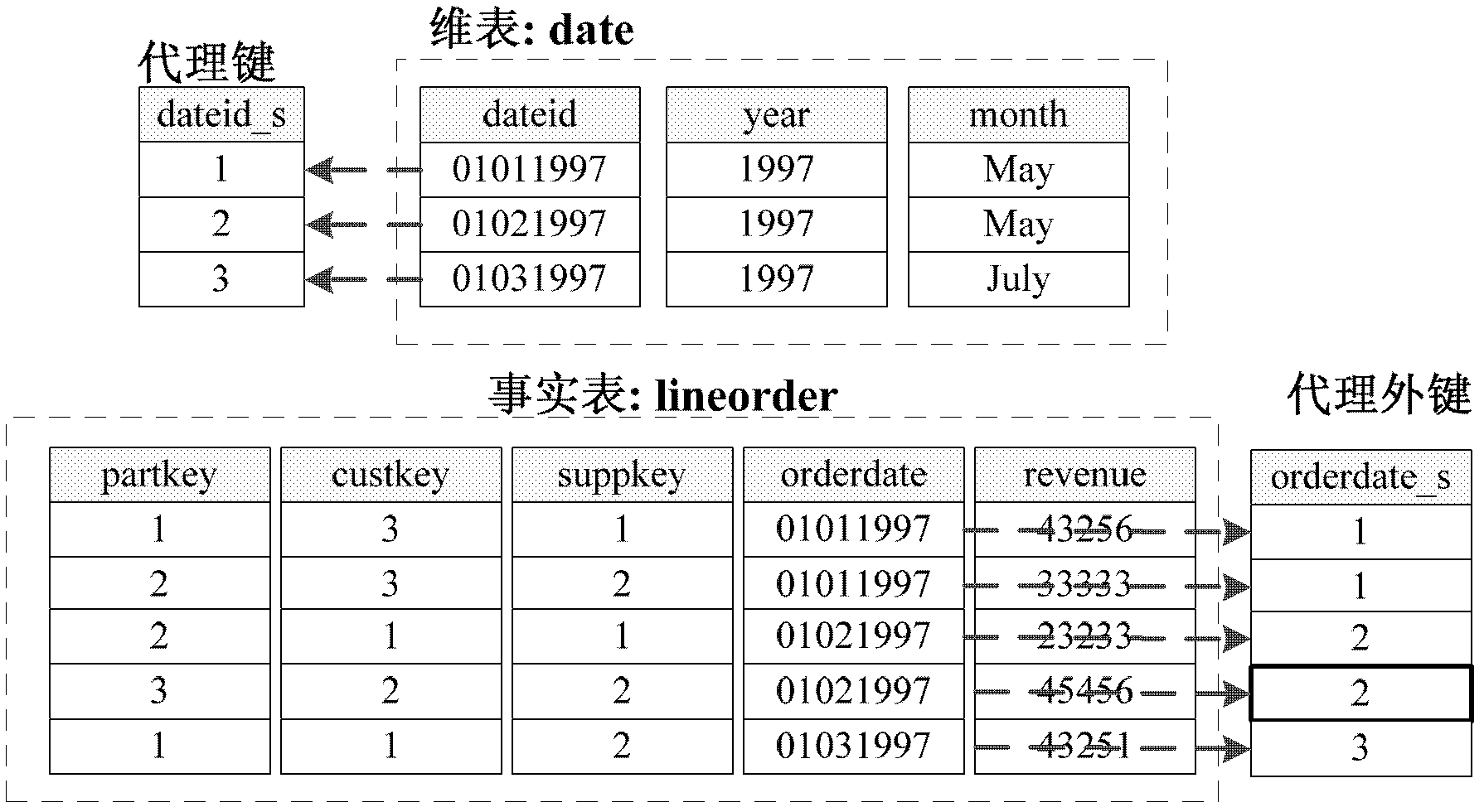
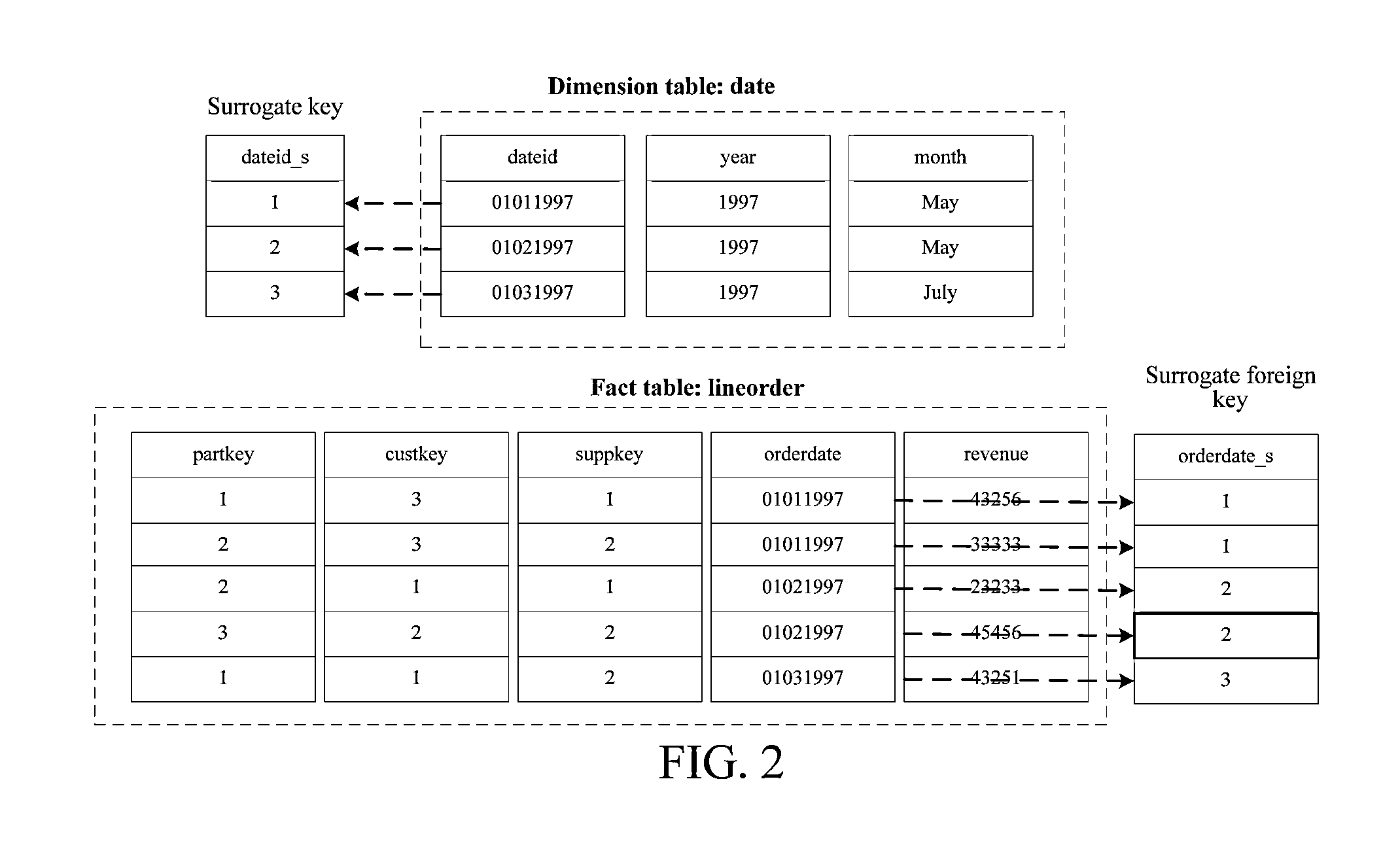
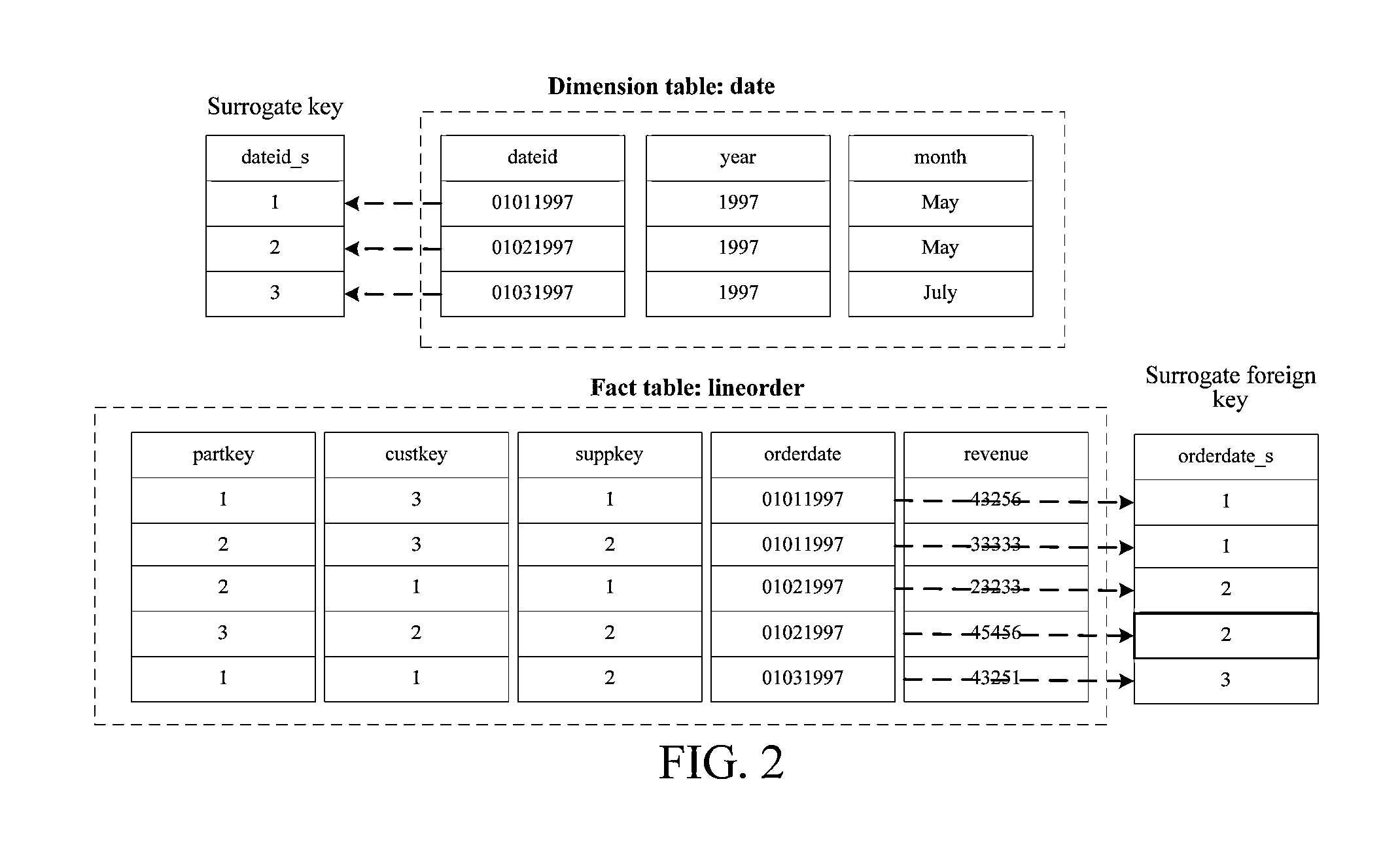
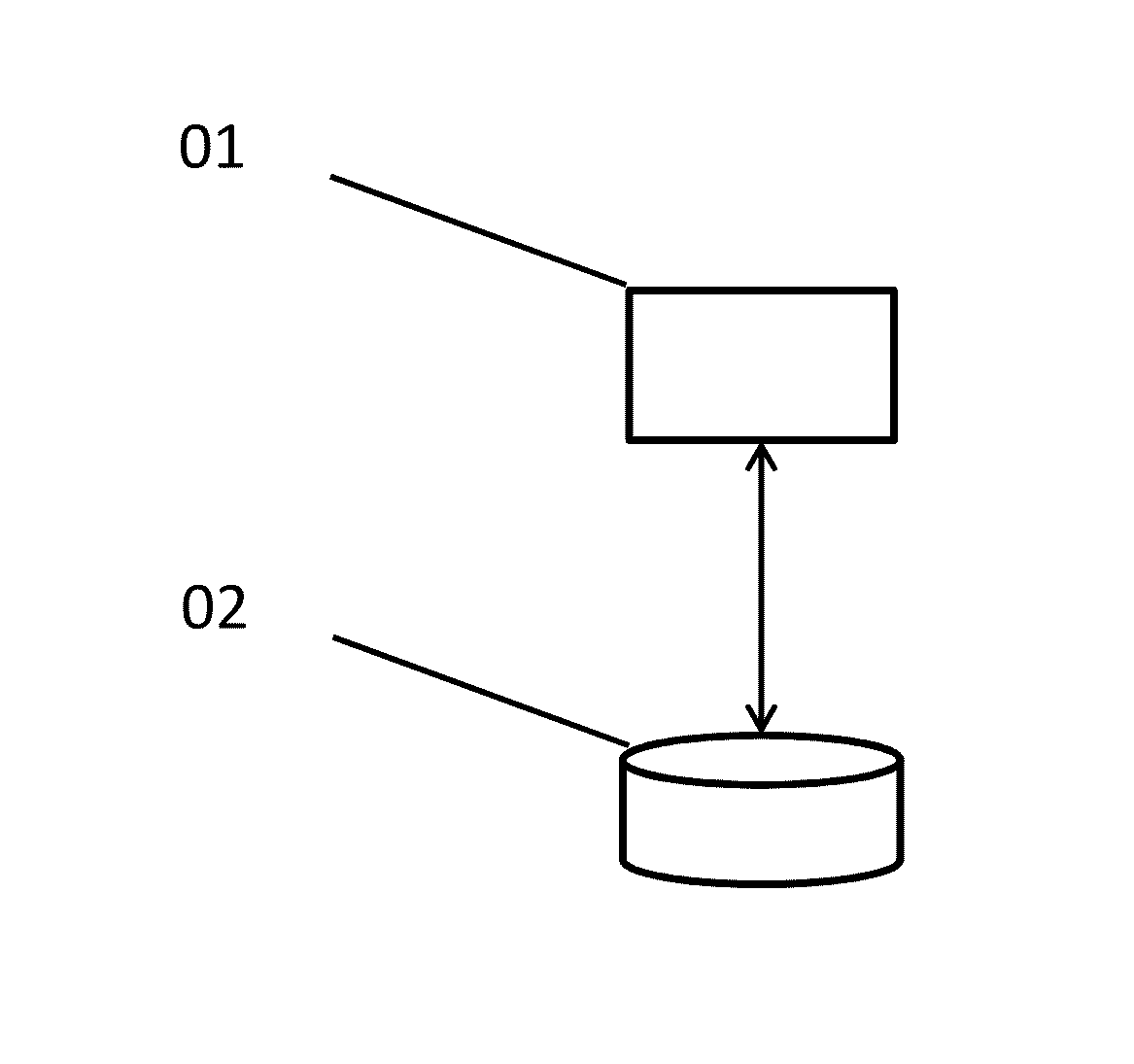
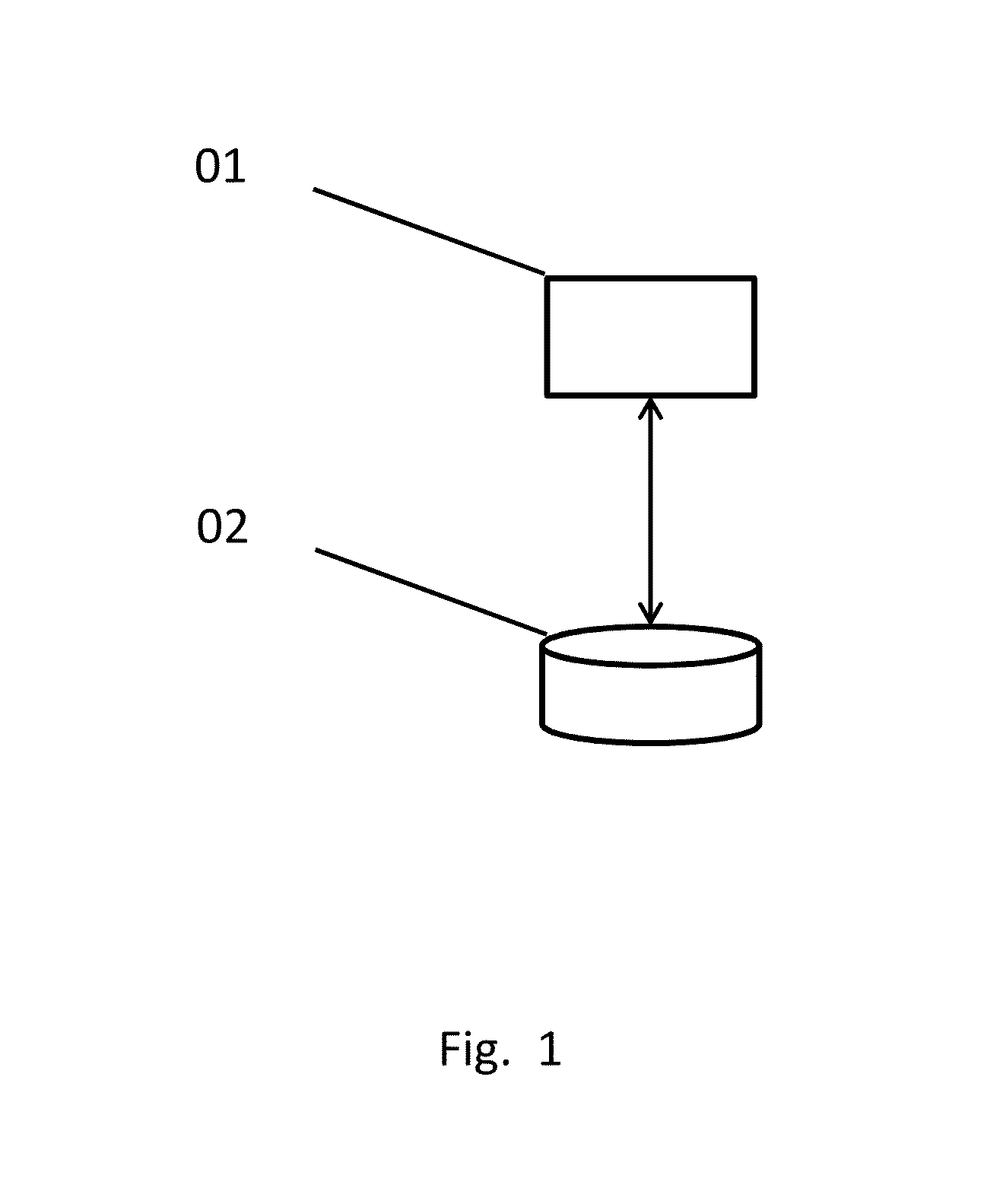
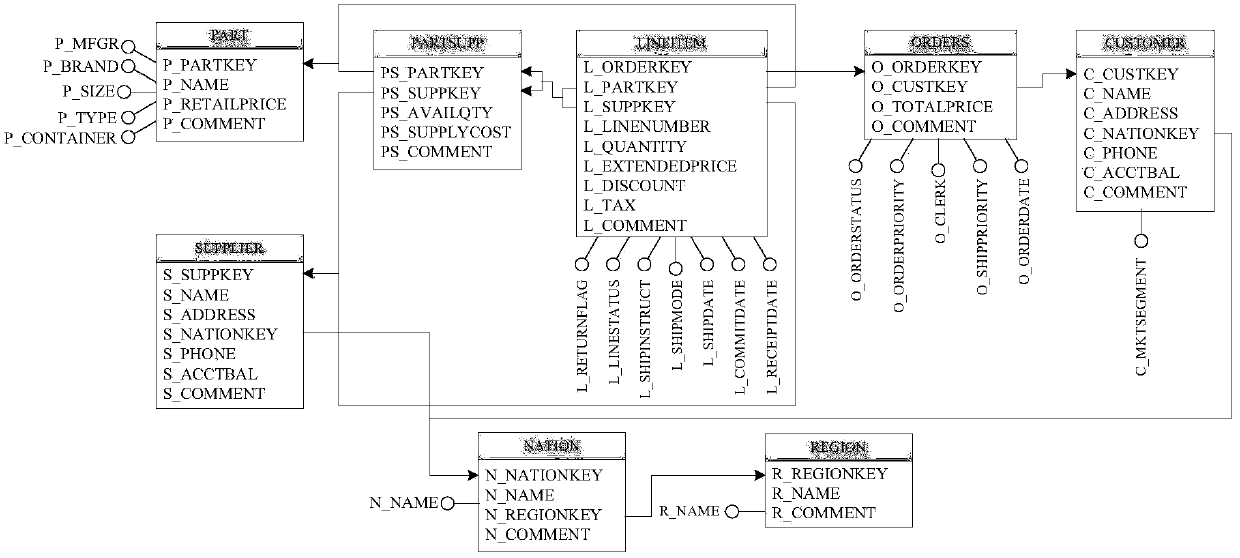
A surrogate key (or synthetic key, entity identifier, system-generated key, database sequence number, factless key, technical key, or arbitrary unique identifier) in a database is a unique identifier for either an entity in the modeled world or an object in the database. The surrogate key is not derived from application data, unlike a natural (or business) key which is derived from application data.
Multi-dimensional OLAP (On Line Analytical Processing) inquiry processing method facing column storage data warehouse
ActiveCN102663116AReduce complexityImprove performanceSpecial data processing applicationsSurrogate keyGroup operation
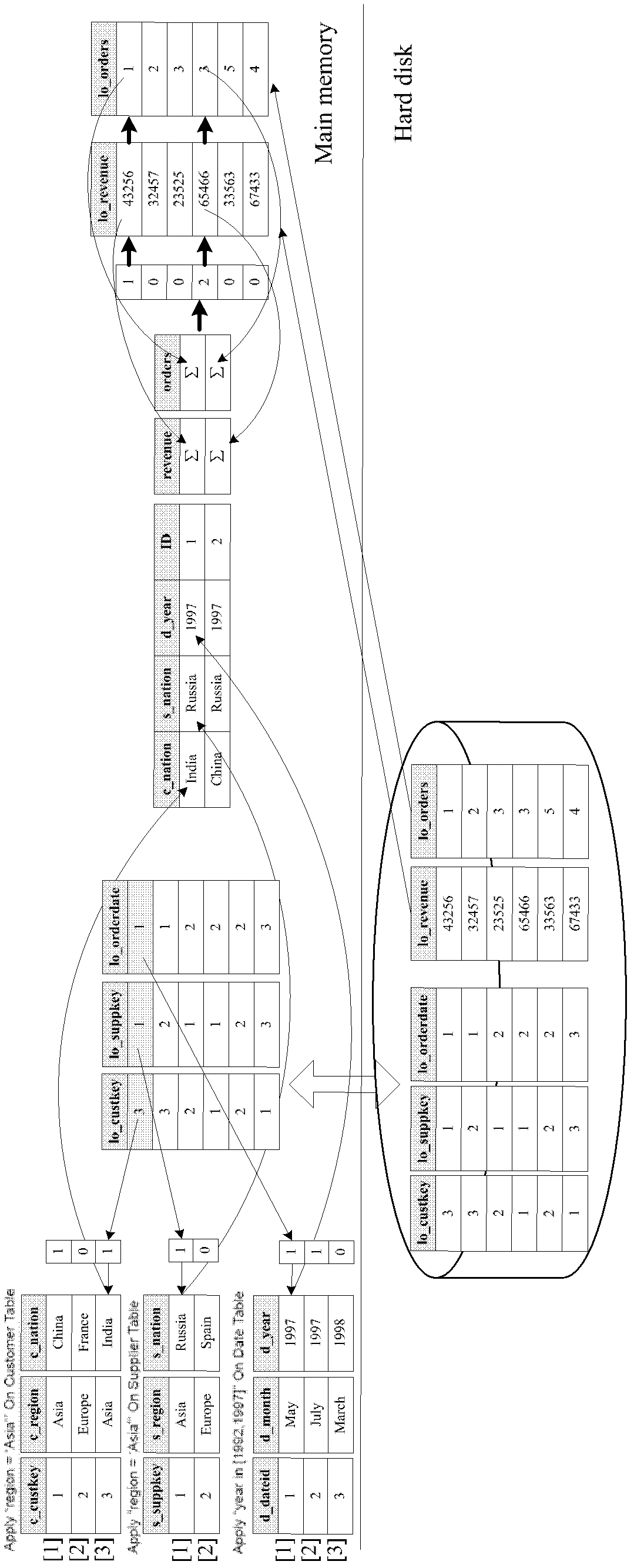
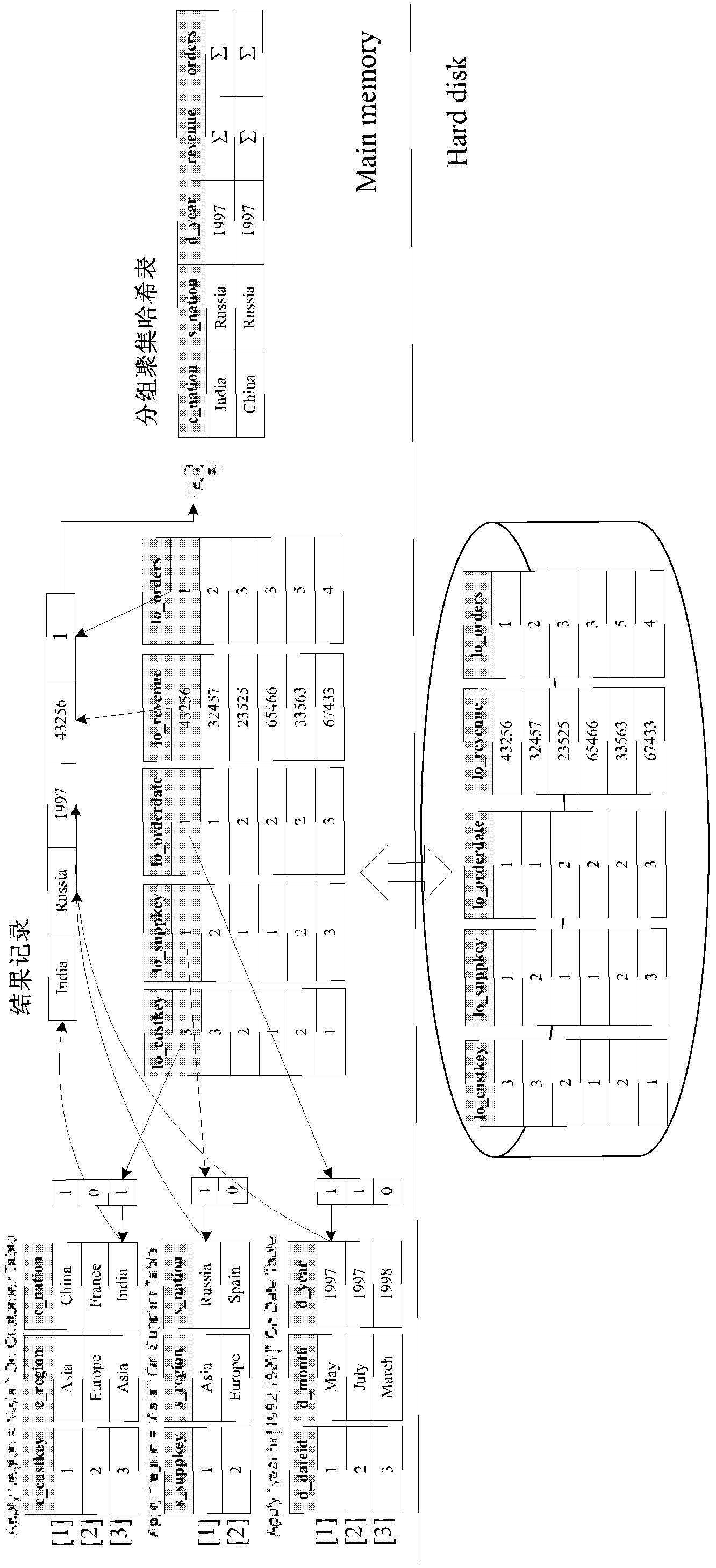
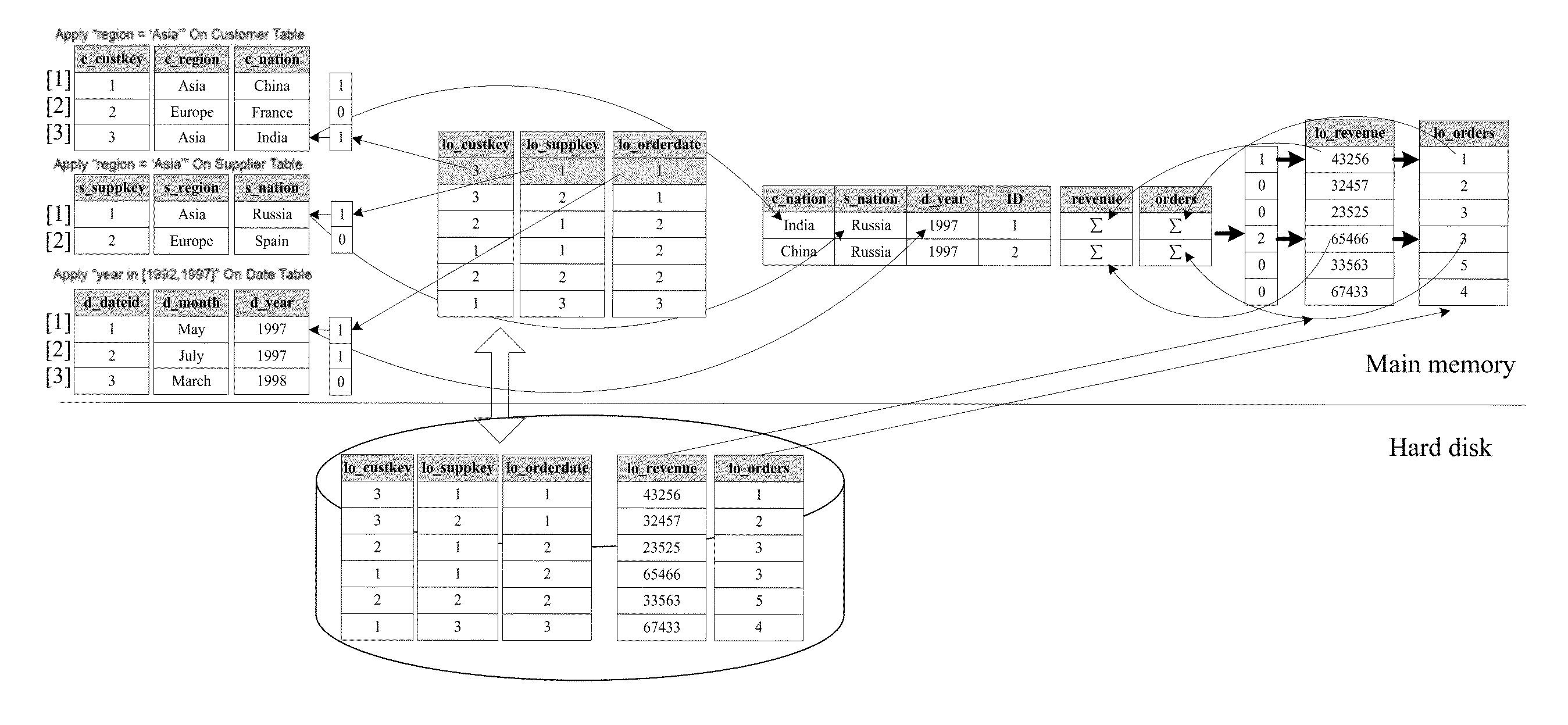
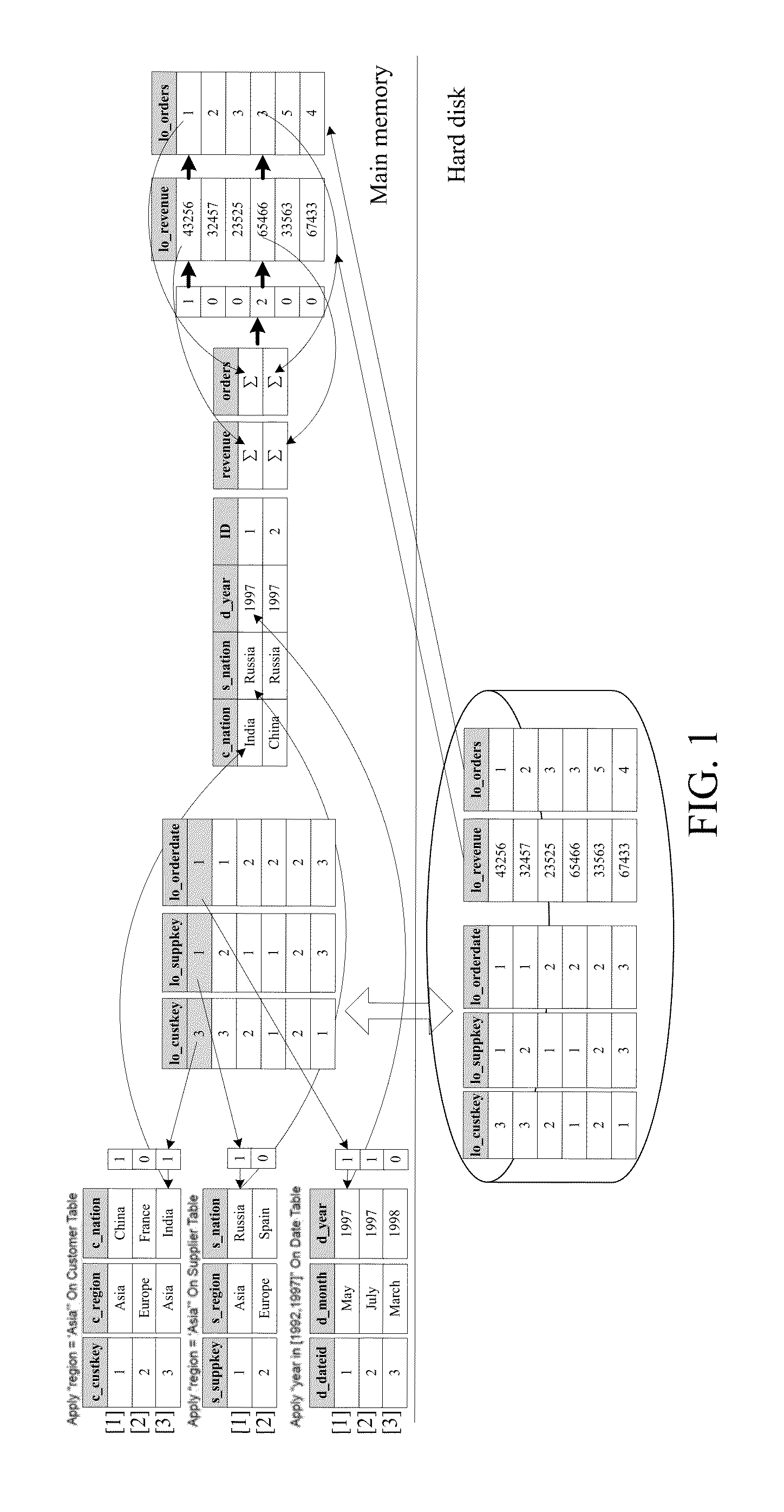
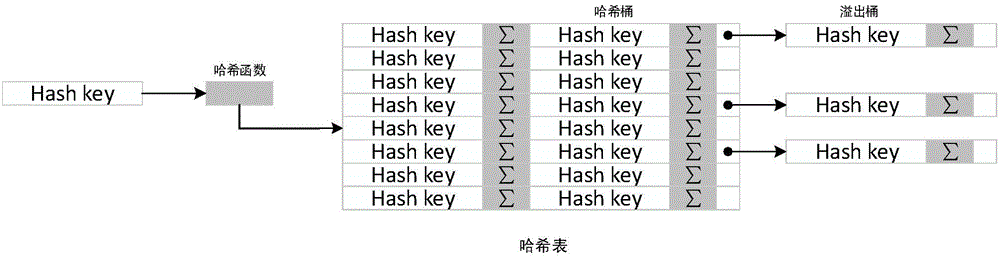
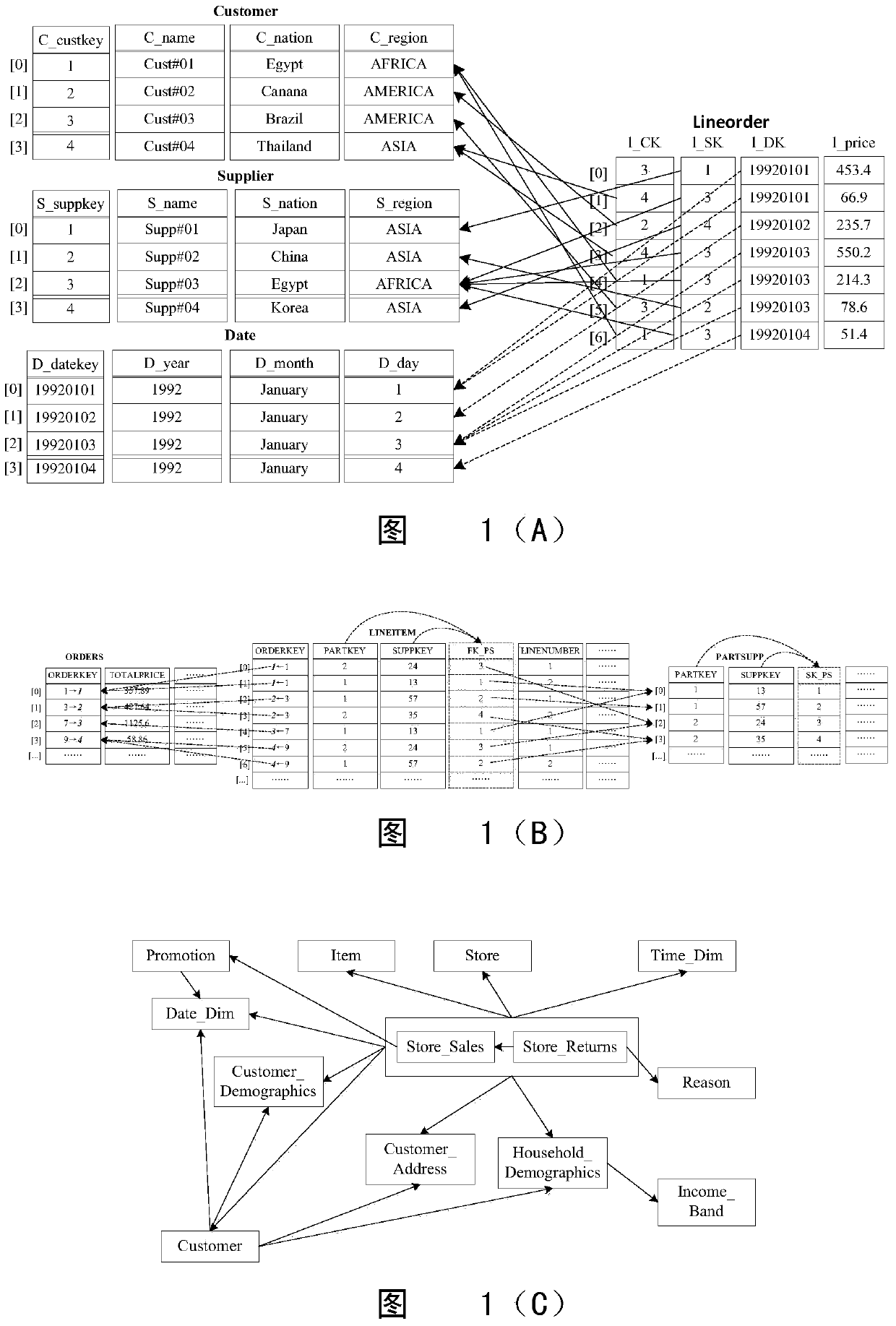
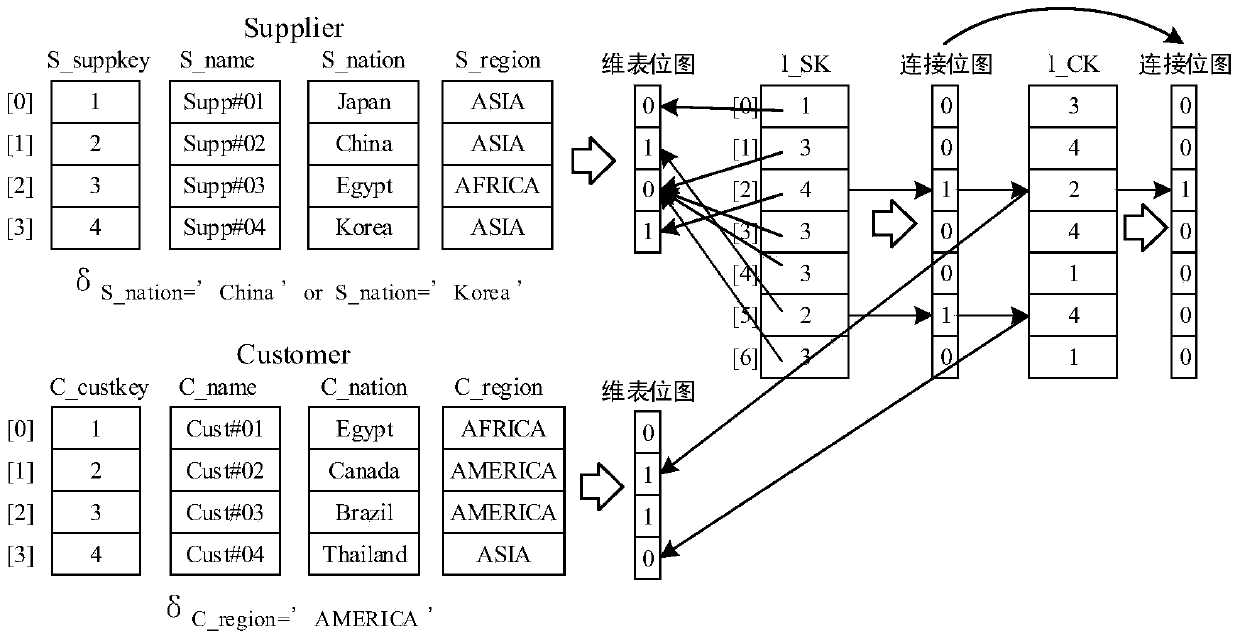
The invention discloses a multi-dimensional OLAP (On Line Analytical Processing) inquiry processing method facing a column storage data warehouse. In the multi-dimensional OLAP inquiry processing method, the OLAP inquiry is decomposed into a bitmap filtering operation, a grouping operation and an aggregation operation. In the bitmap filtering operation, firstly, the predication is executed on a dimension table and a predicate vector bitmap is generated; and a connection operation is converted into a direct dimension table record access operation by surrogate key address mapping so as to implement access according to the positions. In the grouping operation, the pre-generation of grouping units is carried out on fact table records which meet the filtering conditions according to grouping attributes in an SQL (Structured Query Language) command and increasing IDs (identity) are distributed. In the aggregation operation, the grouping aggregation calculation which is carried out according to a grouping item of a grouping filtering vector of a fact table is implemented by carrying out column scanning on the metric attribute of the fact table for once. According to the invention, all OLAP processing tasks can be completed only by carrying out column scanning on the fact table for once, so that the cost of repeatedly scanning is avoided.
Owner:RENMIN UNIVERSITY OF CHINA
Multi-Dimensional OLAP Query Processing Method Oriented to Column Store Data Warehouse
ActiveUS20130275365A1Improve I/O performanceReduce complexityDigital data processing detailsMulti-dimensional databasesOne passSurrogate key
A multi-dimensional OLAP query processing method oriented to a column store data warehouse is described. With this method, an OLAP query is divided into a bitmap filtering operation, a group-by operation and an aggregate operation. In the bitmap filtering operation, a predicate is first executed on a dimension table to generate a predicate vector bitmap, and a join operation is converted, through address mapping of a surrogate key, into a direct dimension table tuple access operation; in the group-by operation, a fact table tuple satisfying a filtering condition is pre-generated into a group-by unit according to a group-by attribute in an SQL command and is allocated with an increasing ID; and in the aggregate operation, group-by aggregate calculation is performed according to a group item of a fact table filtering group-by vector through one-pass column scan on a fact table measure attribute.
Owner:RENMIN UNIVERSITY OF CHINA
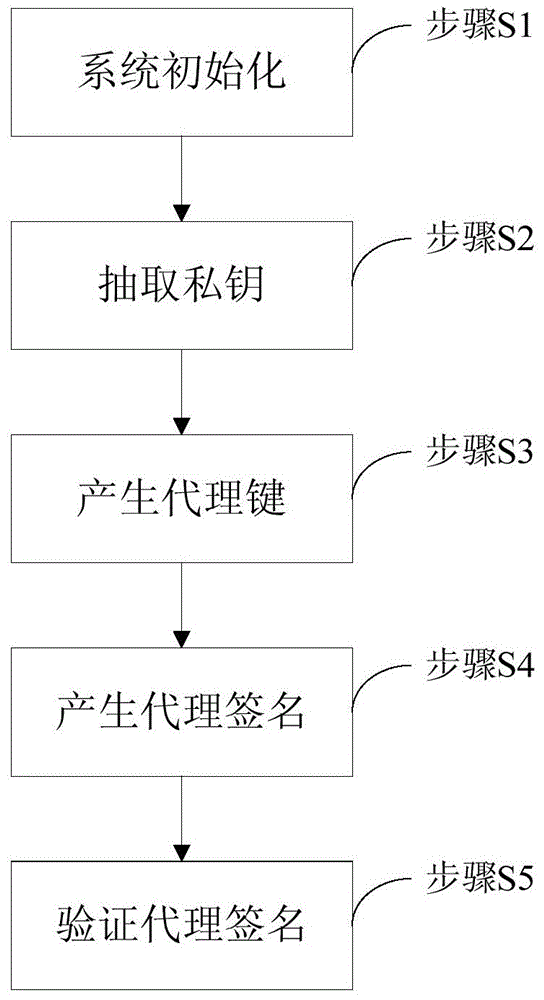
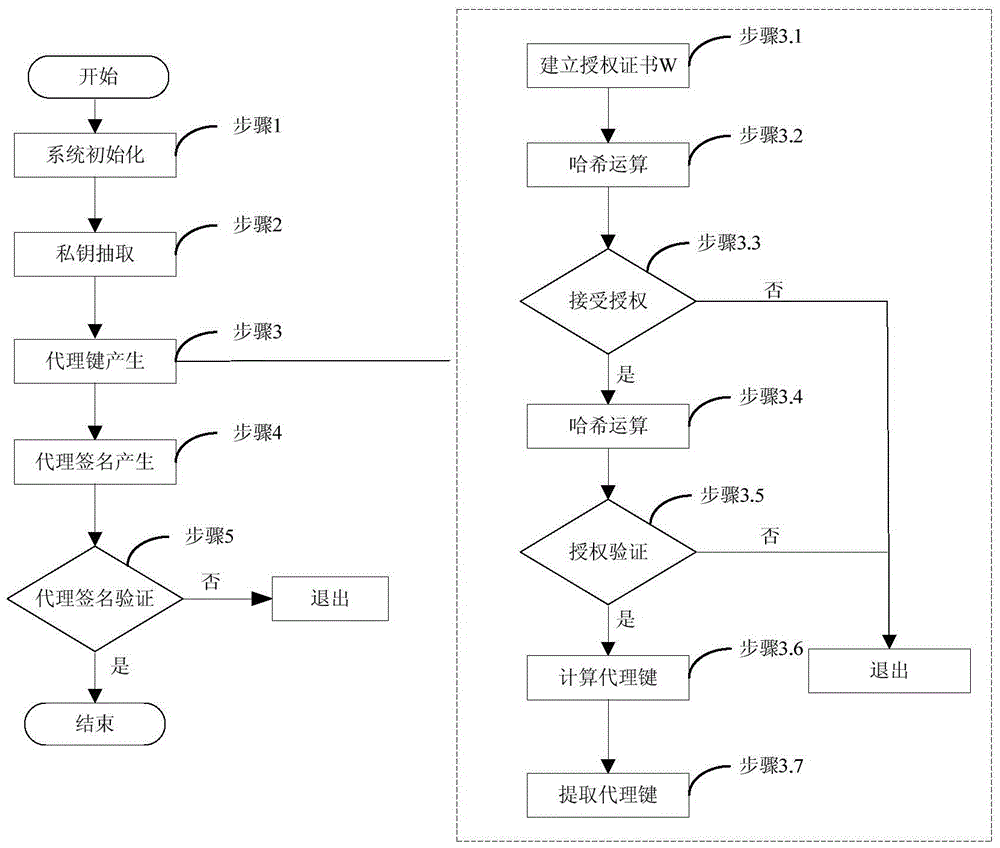
Method and system for agent signature
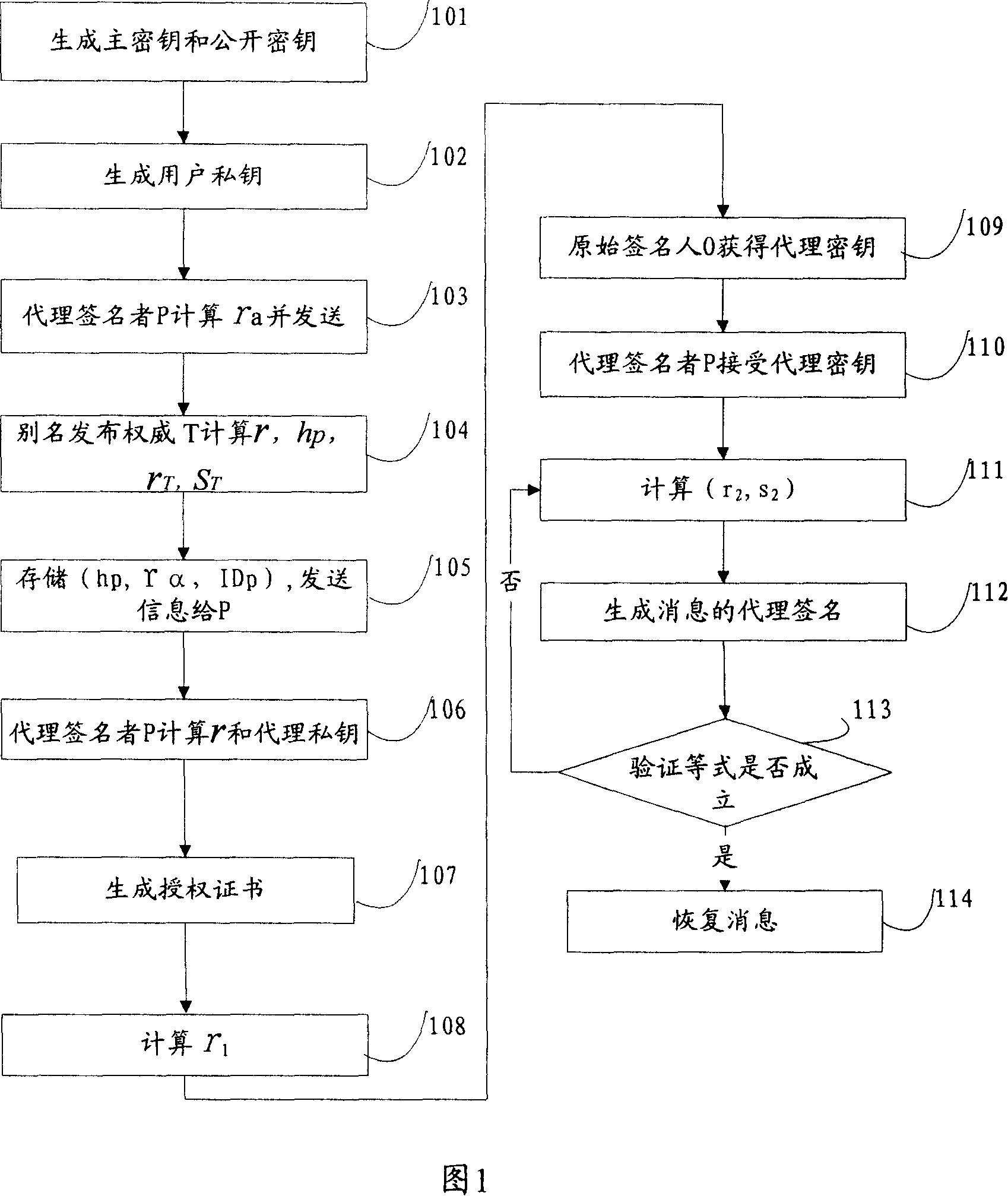
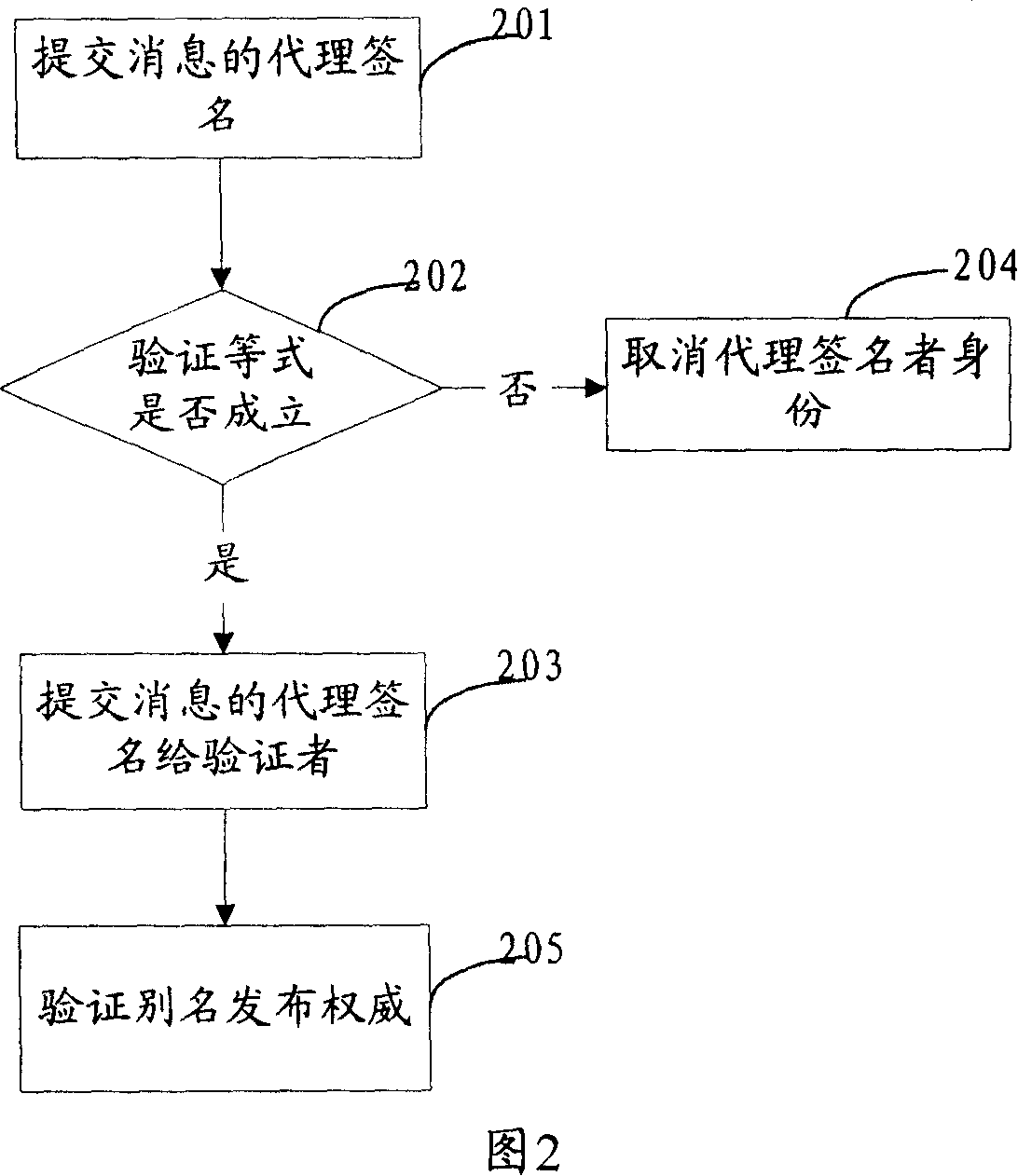
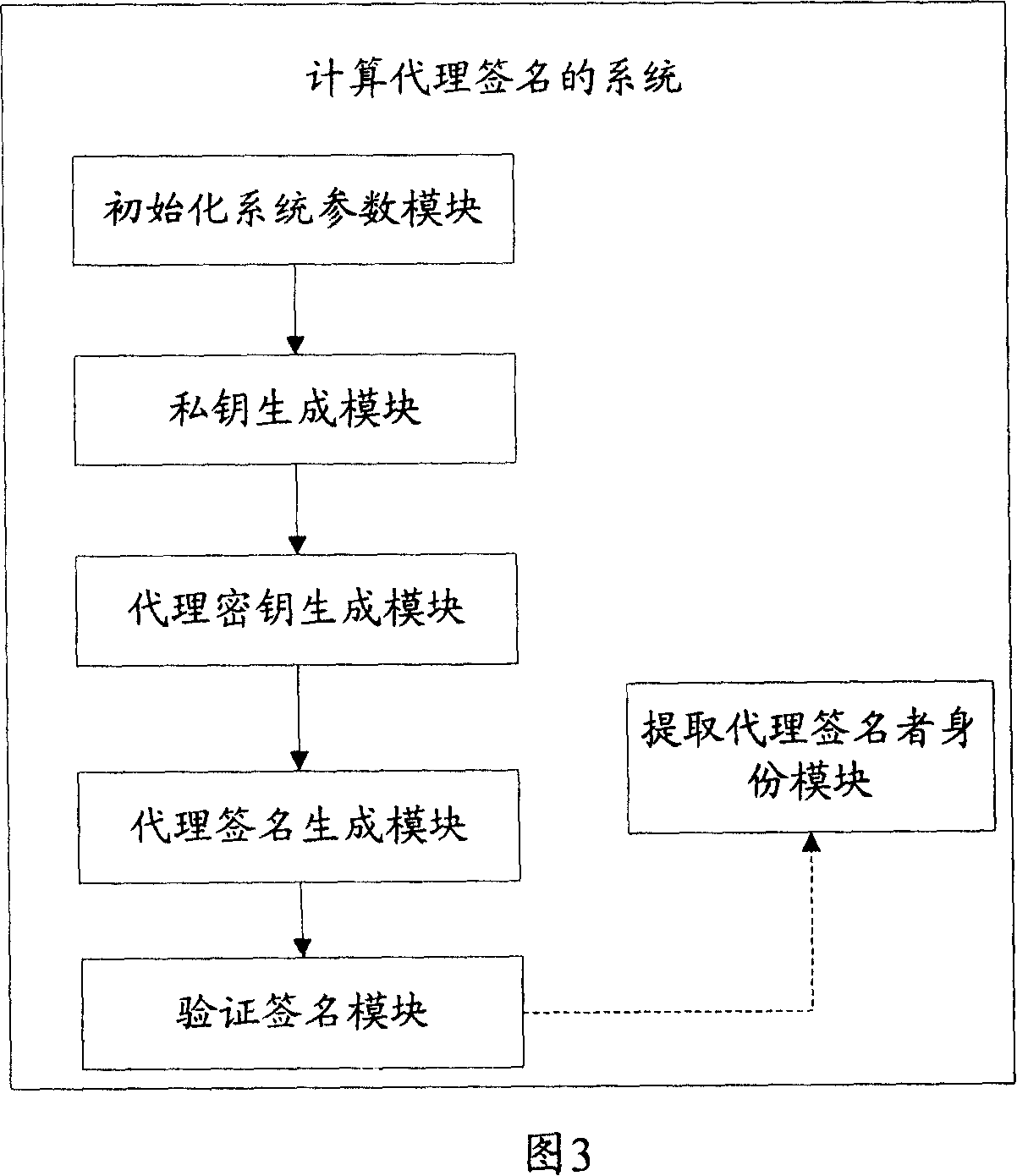
InactiveCN101051901ASatisfy non-repudiationUser identity/authority verificationCommerceSurrogate keyOperability
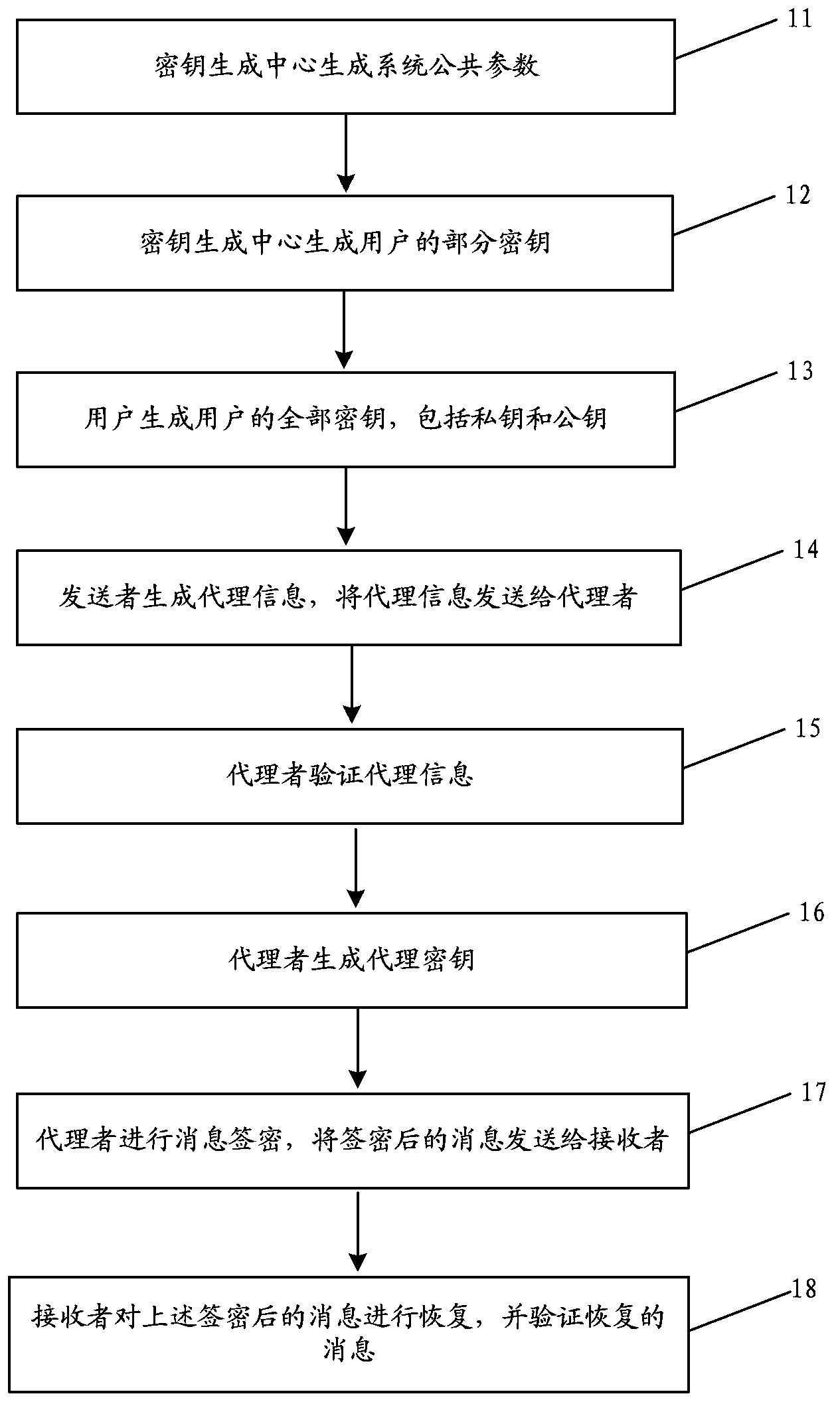
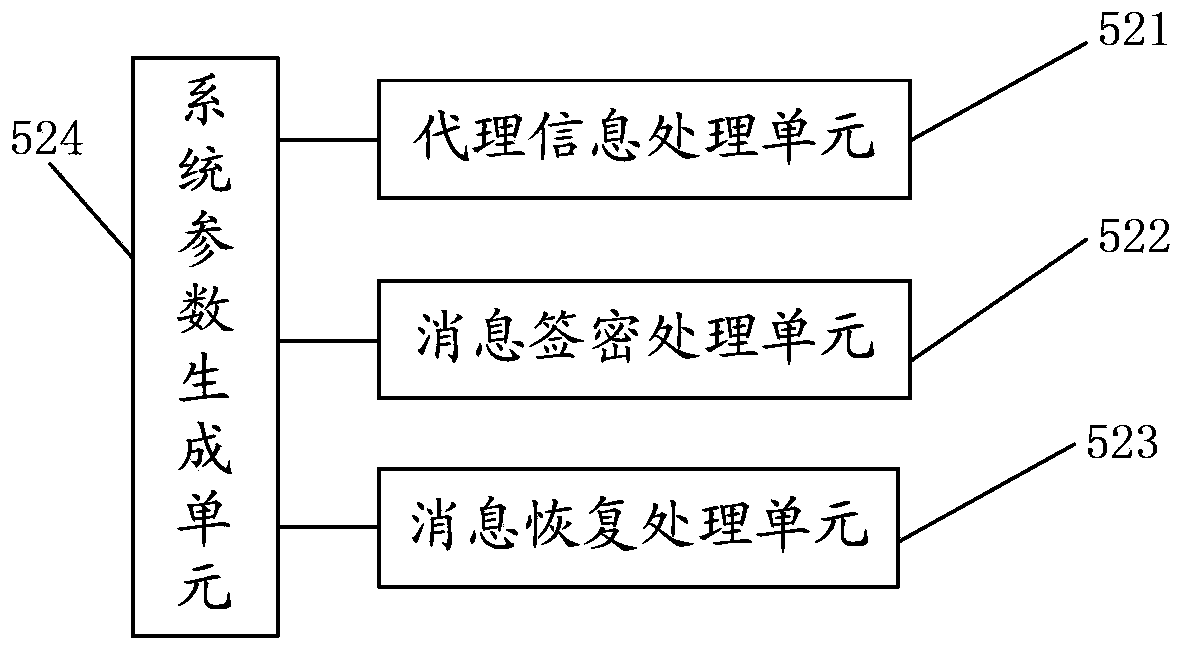
The invention solves issues that disadvantages of poor operability and difficulty for implementing undeniable characteristic of server exist in current technique. The disclosed method for proxy signature includes steps: initializing system parameters; based on system parameters to generate private key of proxy signer; original signer generates proxy key of proxy signer; proxy signer generates proxy signature for message; validating proxy signature. The invention also discloses a system of proxy signature. The system includes module for initializing system parameters, private key generation module, proxy key generation module, proxy signature generation module, module for validating signature, and module for picking up Id of proxy signer. The invention satisfies undeniable characteristic of server, protects proxy signer, and the security is based on RSA.
Owner:SHANGHAI JIAO TONG UNIV +1
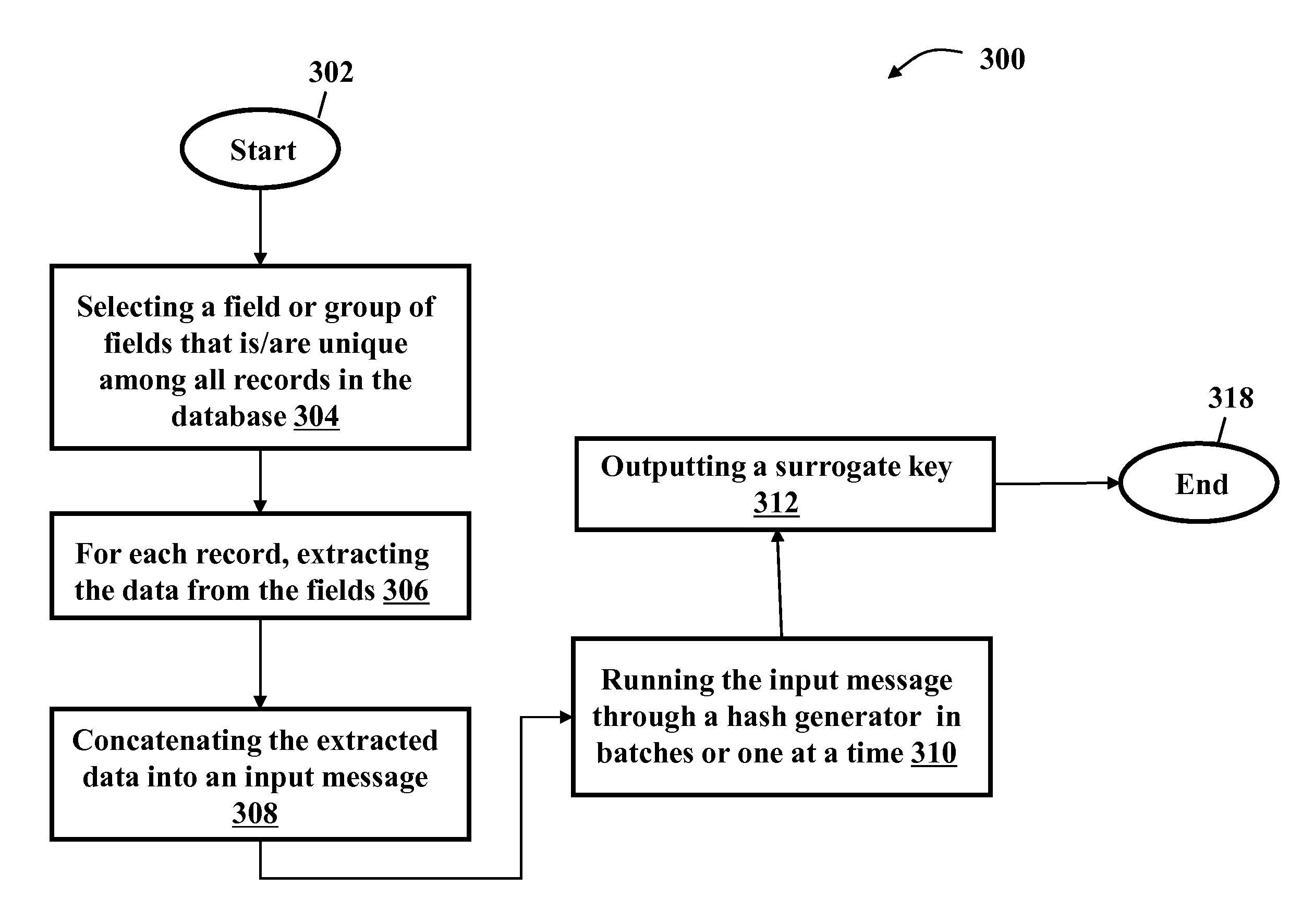
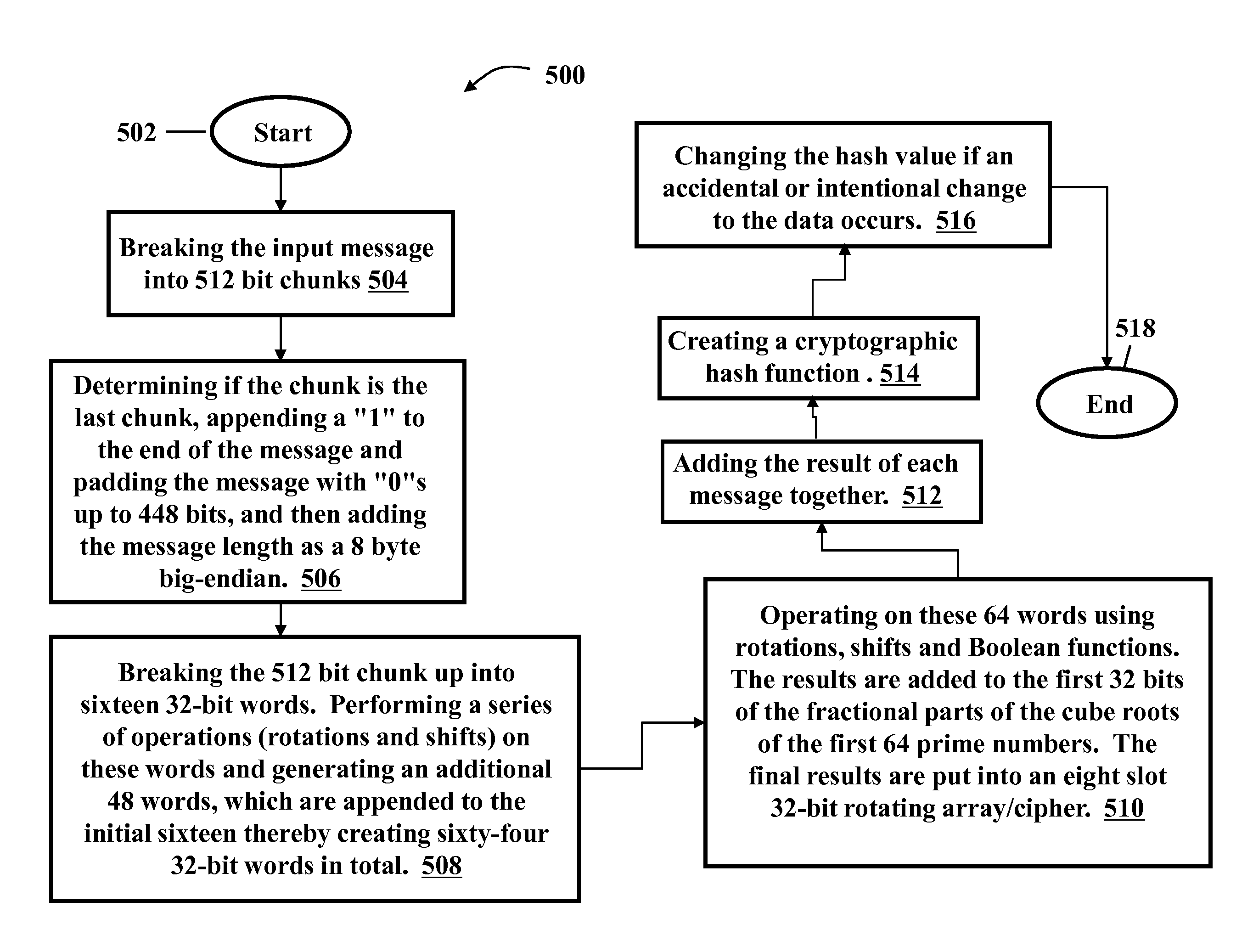
Surrogate key generation using cryptographic hashing
InactiveUS20110123021A1Validating data qualityReduce data redundancyDigital data information retrievalEncryption apparatus with shift registers/memoriesComputer hardwareSurrogate key
The present invention relates to a method or system of generating a surrogate key using cryptographic hashing. One embodiment of the method of the present invention may have steps such as selecting a field or group of fields that is or are unique among all records in the database, for each record, extracting the data from the fields, concatenating the extracted data into an input message, running the input message through a hash generator, either in batches or one at a time, for testing purposes perhaps, and outputting a surrogate key.
Owner:IBM CORP
Incremental data capturing and extraction method based on timestamps and logs
ActiveCN102915336AImprove extraction efficiencyRelieve pressureSpecial data processing applicationsSurrogate keyTimestamp
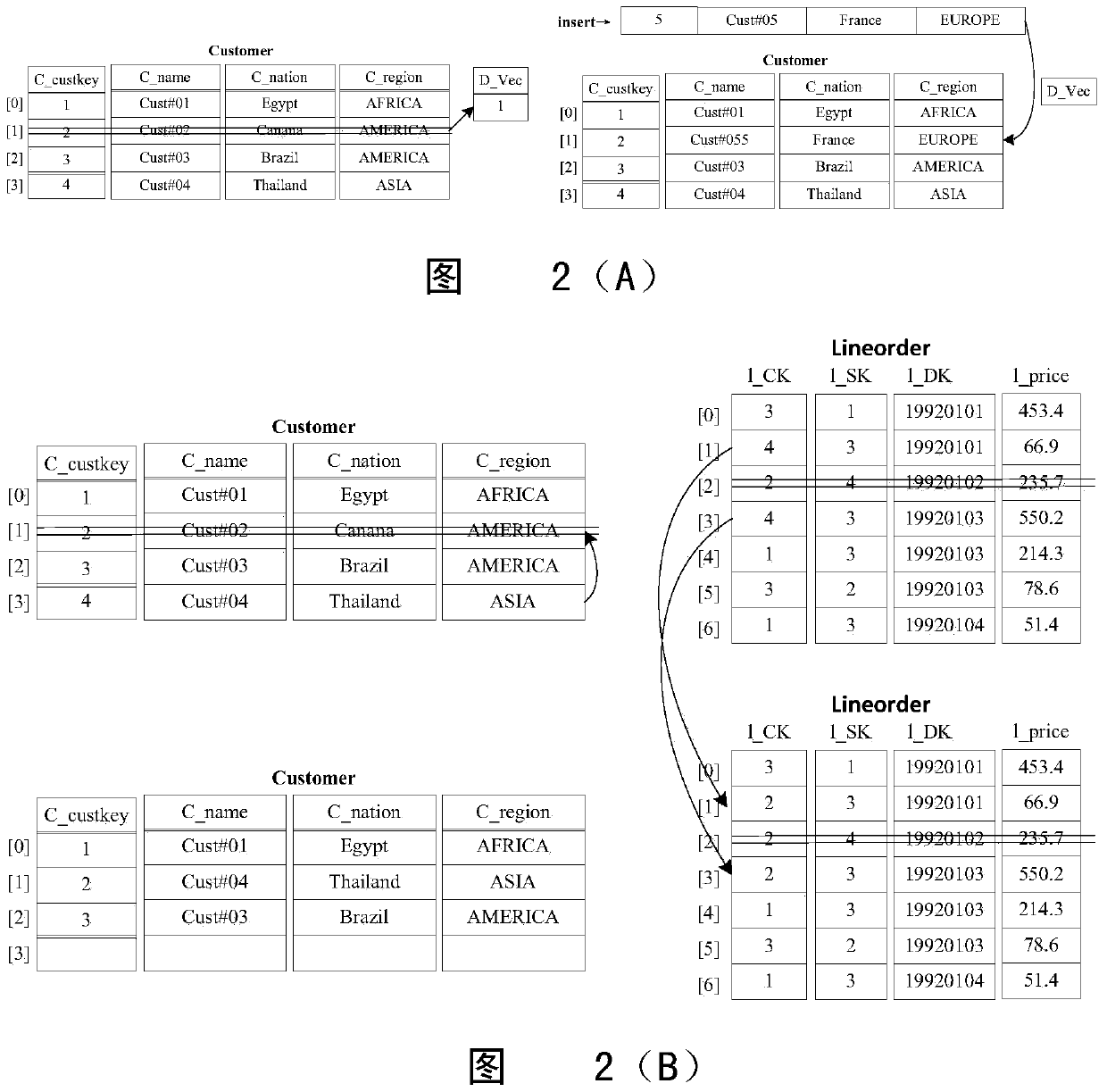
The invention discloses an incremental data capturing and extraction method based on timestamps and logs. The incremental data capturing and extraction method comprises the following steps: step 1, adding an auto increment surrogate key field and a timestamp field for each sheet which is required to incrementally extract data in a service system; step 2, using a timestamp way when data in data sheets are added or revised; and step 3, using a log recording way when the data in the data sheets are deleted. By the incremental data capturing and extraction method, a service database and a data warehouse can be heterogeneous; the service database and the data warehouse are allowed to be in communication status only if being extracted, and are not necessary to be in the communication status all the time; only the added or the revised data which are not extracted last time are extracted each time, only the undeleted data which are not processed last time are processed, so that service data volume is small; by the incremental data capturing and extraction method, extraction efficiency is remarkably increased, pressure to the service database when extracted is relieved, and technical complexity of the extraction is reduced.
Owner:BEIJING JINHER SOFTWARE
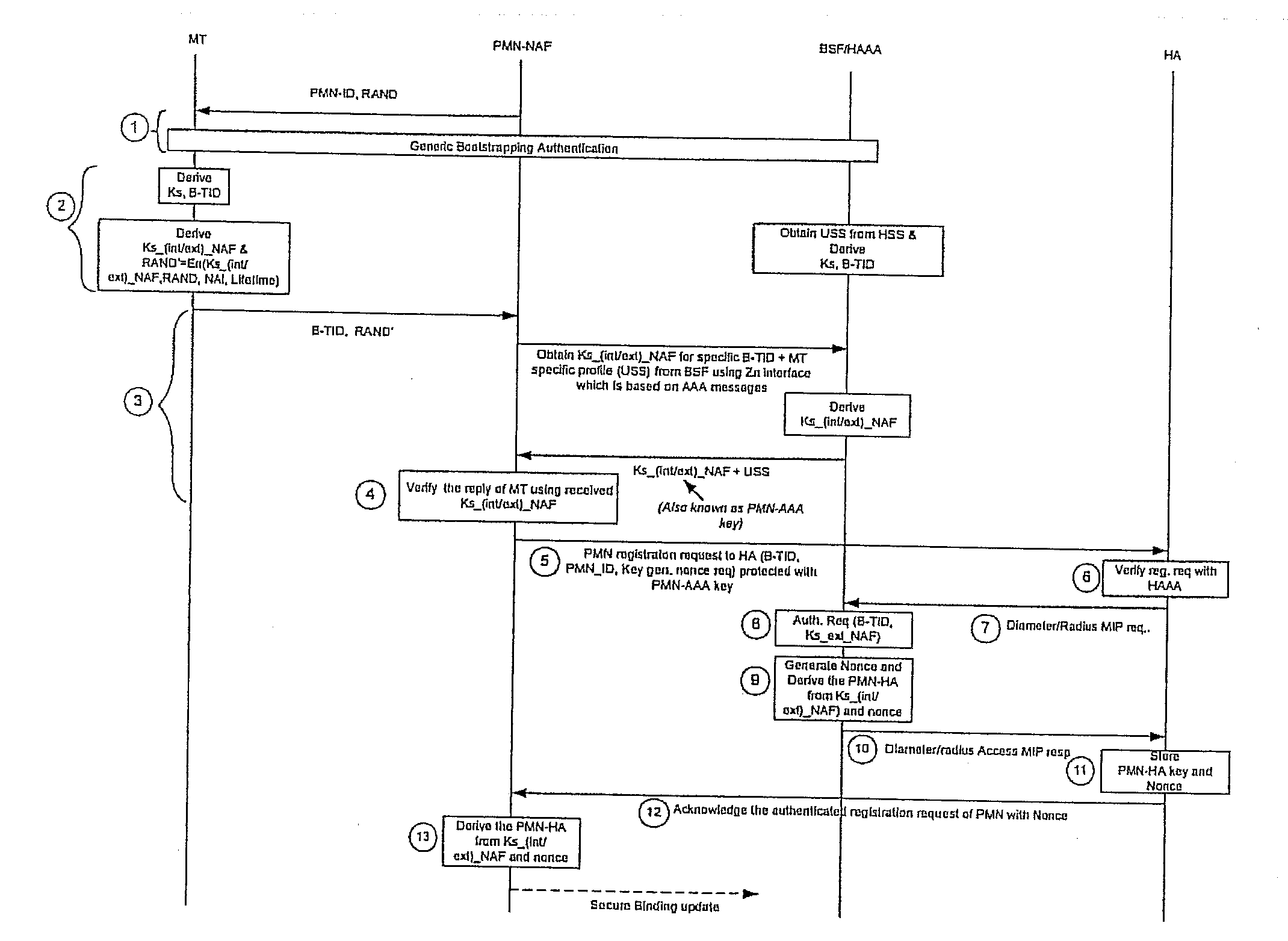
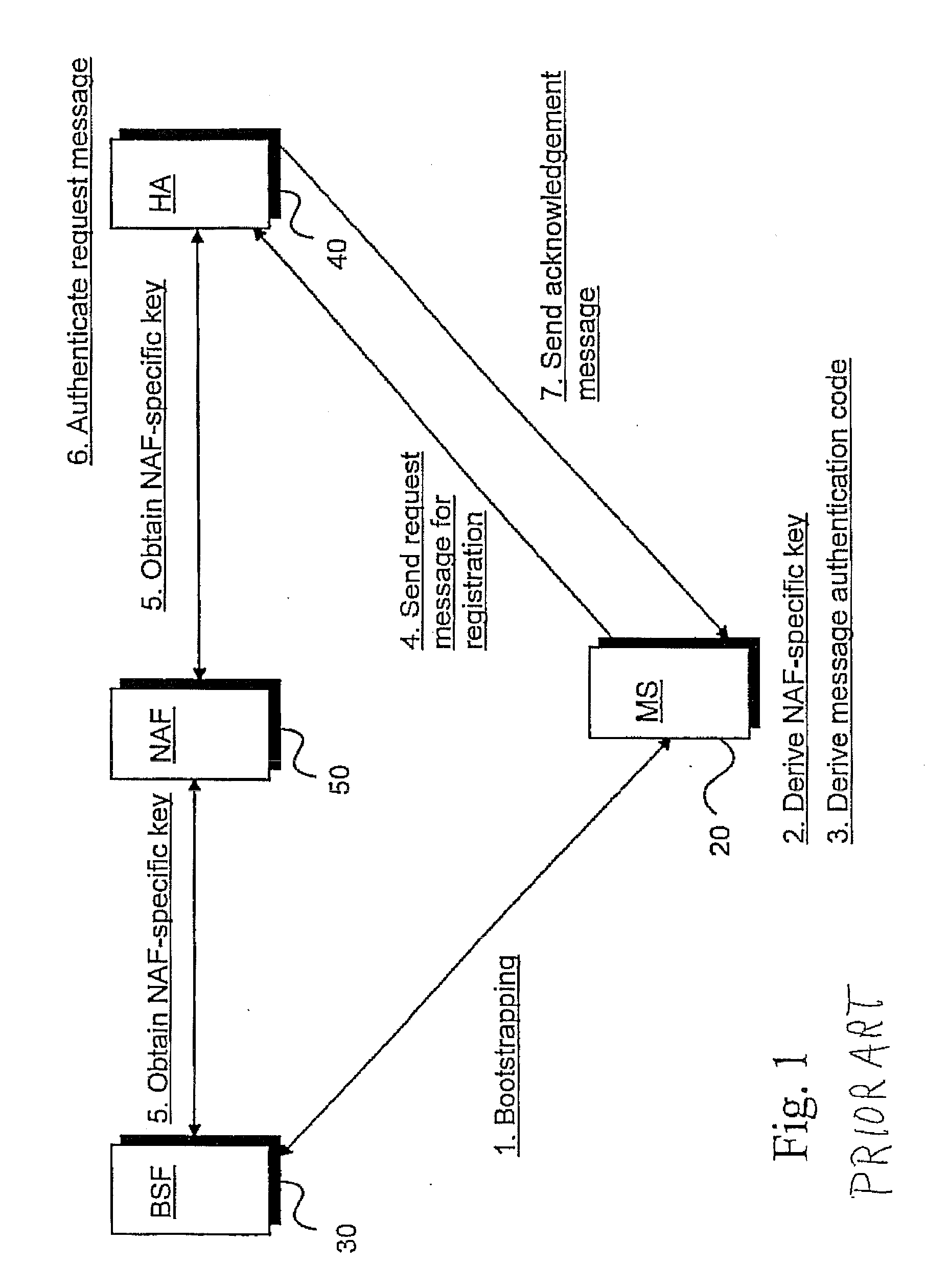
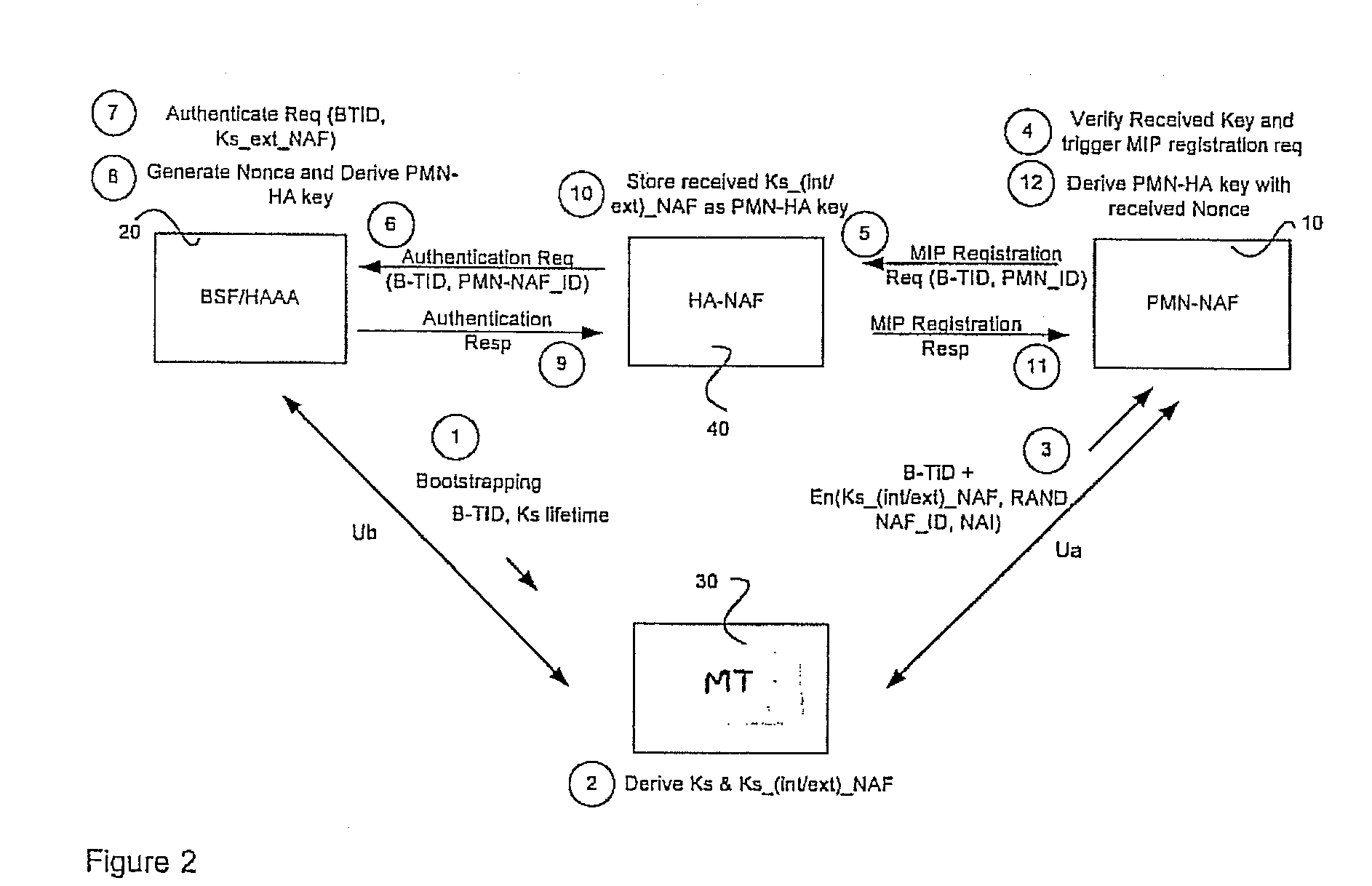
Using gaa to derive and distribute proxy mobile node home agent keys
InactiveUS20090138955A1Digital data processing detailsUser identity/authority verificationSurrogate keyMessage authentication code
A Generic Authentication Architecture bootstrapping procedure is performed between a mobile terminal and a bootstrapping server function resulting in the mobile terminal and the bootstrapping server function each acquiring at least a bootstrapping transaction Identifier associated with the mobile terminal and a corresponding shared key. The mobile terminal derives a network application function specific key based on at least the acquired shared key and an identifier of said network application function. The bootstrapping transaction identifier and the network application function specific key are sent from the mobile terminal to the proxy mobile node. A request message for Mobile Internet Protocol registration is sent from the proxy mobile node to a home agent on behalf of the mobile terminal, the request message including the bootstrapping transaction identifier and an identifier of the proxy mobile node. The registration message is verified in the home agent with the use of a network application function specific key obtained from the bootstrapping server function or a network application function. The request message for Mobile Internet Protocol registration is authenticated with the proxy mobile node acting on behalf of the mobile terminal by verifying the message authentication code with the obtained network application function specific key.
Owner:WSOU INVESTMENTS LLC
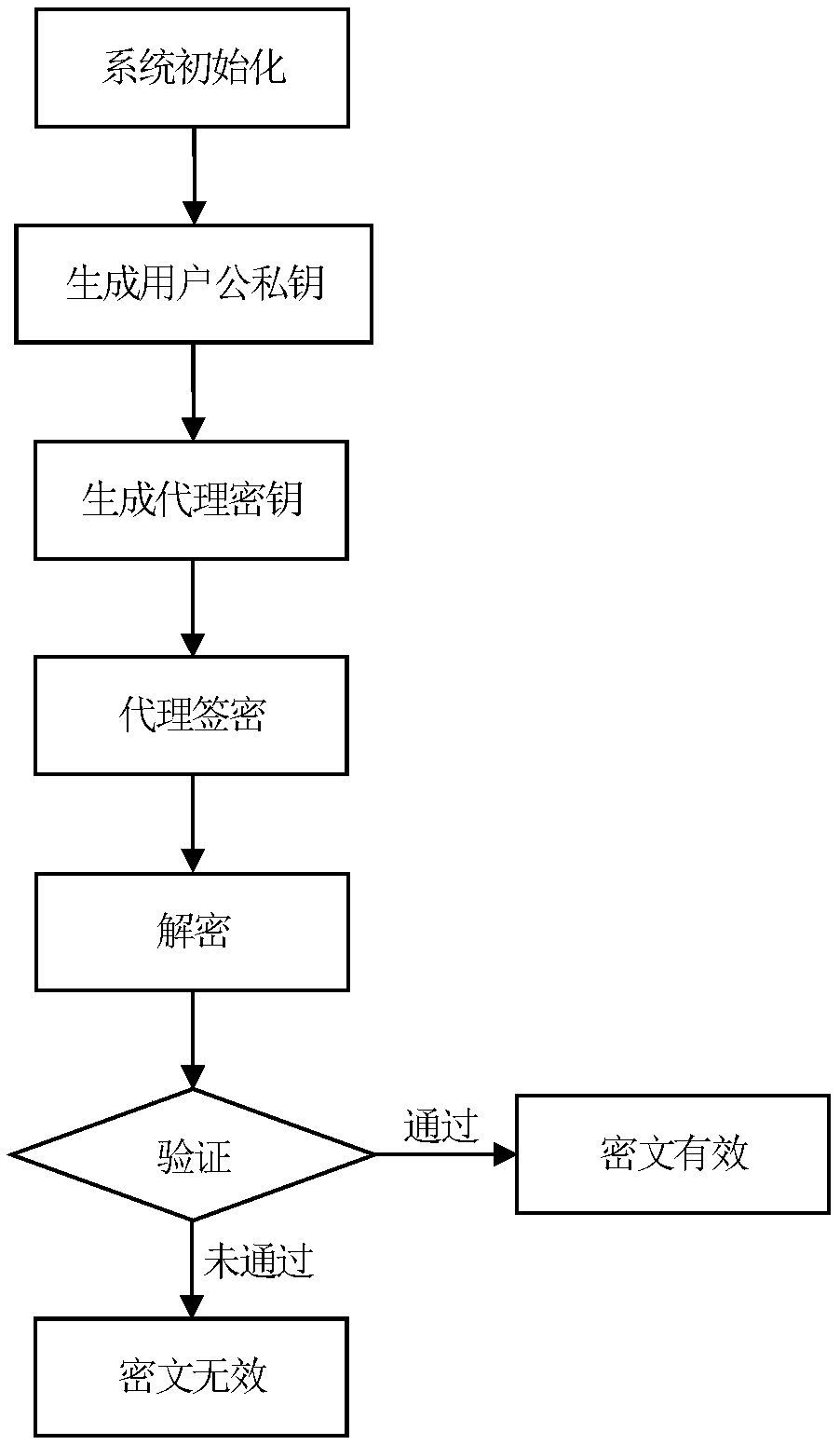
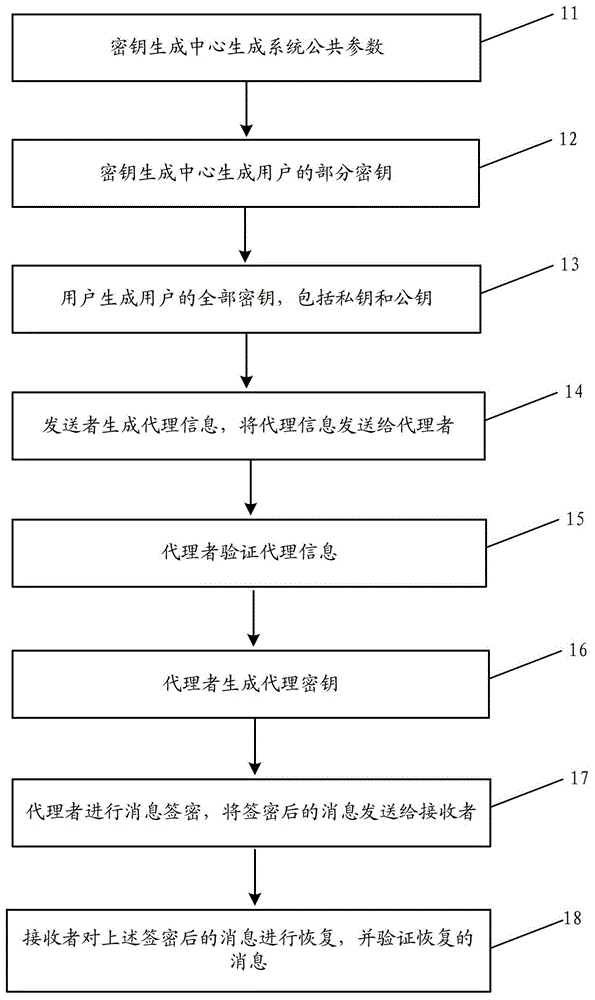
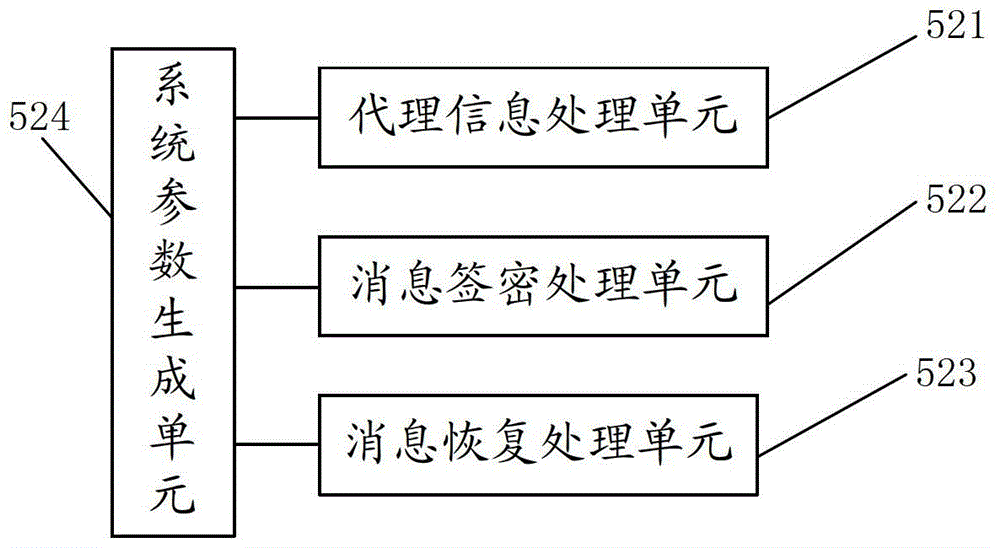
Method and system for certificateless and pairing-free identity-based proxy signcryption
ActiveCN103905189ATroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSurrogate keySigncryption
The embodiment of the invention provides a method and a system for certificateless and pairing-free identity-based proxy signcryption. The method mainly comprises the following steps: a sender generates a private key and a public key thereof according to common parameters of the system and identity information parameters of the sender, generates proxy information based on the private key and the public key thereof, and sends the proxy information to a proxy; after the proxy information passes verification of the proxy, the proxy generates a proxy key, performs signcryption on a message needing to be sent based on the proxy key and the common parameters of the system to obtain a signcrypted message and an intermediate parameter, and sends the signcrypted message and the intermediate parameter to a receiver; and the receiver recovers the signcrypted message with the use of the intermediate parameter and the common parameters of the system to obtain a recovered message, and verifies the recovered message. The certificateless and pairing-free identity-based proxy signcryption scheme provided by the embodiment of the invention has both signature and encryption characteristics and has the feature of proxy. A key generation center only generates part of keys of a user, no certificate is needed, and the problem of key escrow is solved.
Owner:AEROSPACE INFORMATION
Multi-dimensional OLAP query processing method oriented to column store data warehouse
ActiveUS8660985B2Improve I/O performanceReduce complexityDigital data processing detailsMulti-dimensional databasesOne passSurrogate key
A multi-dimensional OLAP query processing method oriented to a column store data warehouse is described. With this method, an OLAP query is divided into a bitmap filtering operation, a group-by operation and an aggregate operation. In the bitmap filtering operation, a predicate is first executed on a dimension table to generate a predicate vector bitmap, and a join operation is converted, through address mapping of a surrogate key, into a direct dimension table tuple access operation; in the group-by operation, a fact table tuple satisfying a filtering condition is pre-generated into a group-by unit according to a group-by attribute in an SQL command and is allocated with an increasing ID; and in the aggregate operation, group-by aggregate calculation is performed according to a group item of a fact table filtering group-by vector through one-pass column scan on a fact table measure attribute.
Owner:RENMIN UNIVERSITY OF CHINA
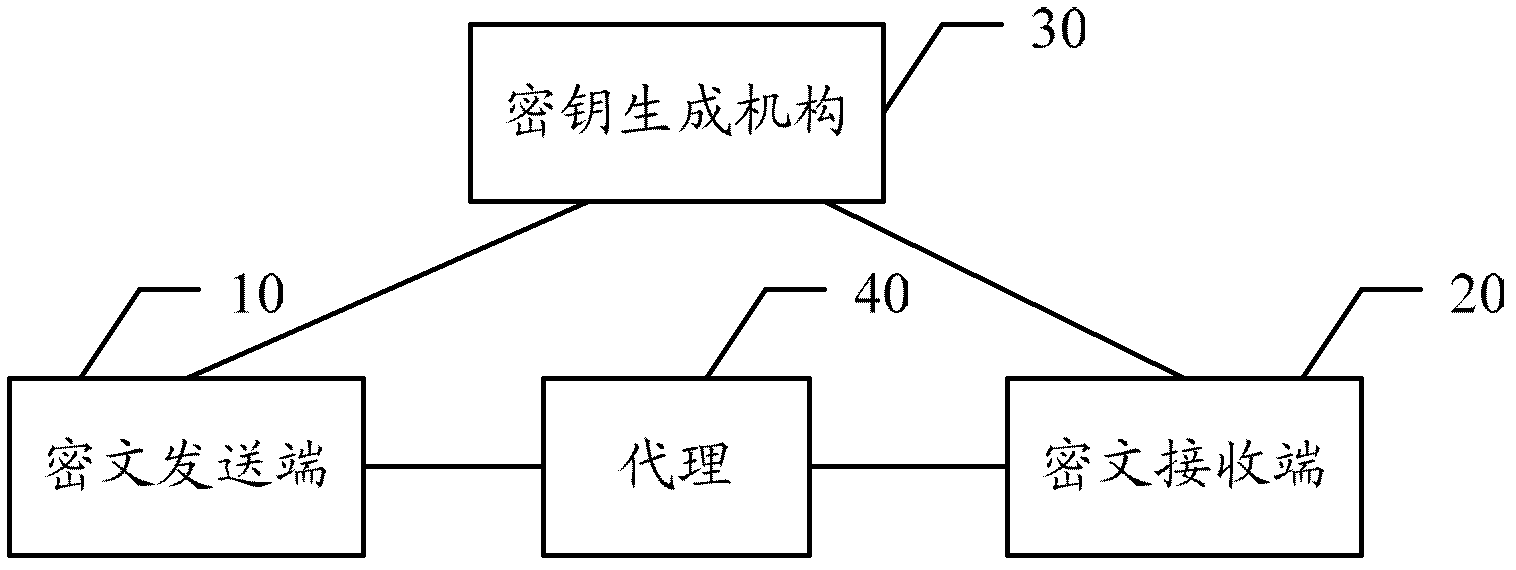
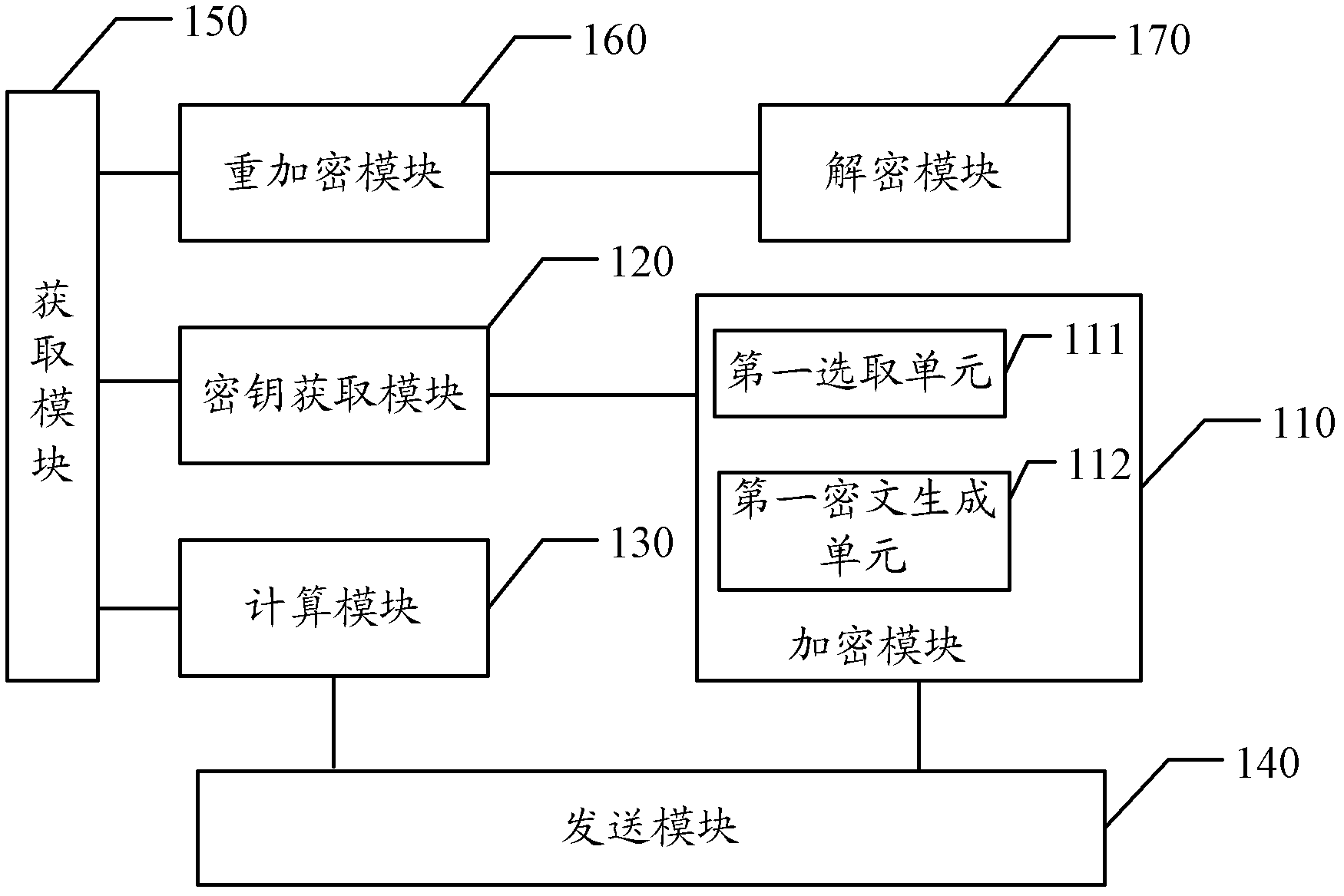
Method, device and system for processing cipher text
InactiveCN102404121AReduce usageImprove scalabilityKey distribution for secure communicationPublic key for secure communicationExtensibilitySurrogate key
The embodiment of the invention discloses a method, a device and a system for processing cipher text. The method comprises the following steps: selecting the random secret value by a cipher text transmitting terminal; calculating the key of the terminal according to the partial keys obtained by the terminal and the random secret value; calculating the proxy key according to the keys of the terminal and public keys published by a cipher text receiving terminal, wherein the public keys published by the cipher text receiving terminal are obtained through calculating by the cipher text receiving terminal according to the selected random secret value and public parameters of the system; and transmitting the proxy key so that the cipher text receiving terminal obtains the cipher text after being switched according to the cipher text transmitted to the cipher text transmitting terminal by the proxy key, and decrypts. After adopting the embodiment of the invention, the shortcoming of the cipher text re-encryption technology on collusion can be effectively prevented, and the safety of the information can be ensured. Simultaneously because of the realization of the invention, public key infrastructures (PKI) can be saved, and extensibility is better.
Owner:HUAWEI TECH CO LTD
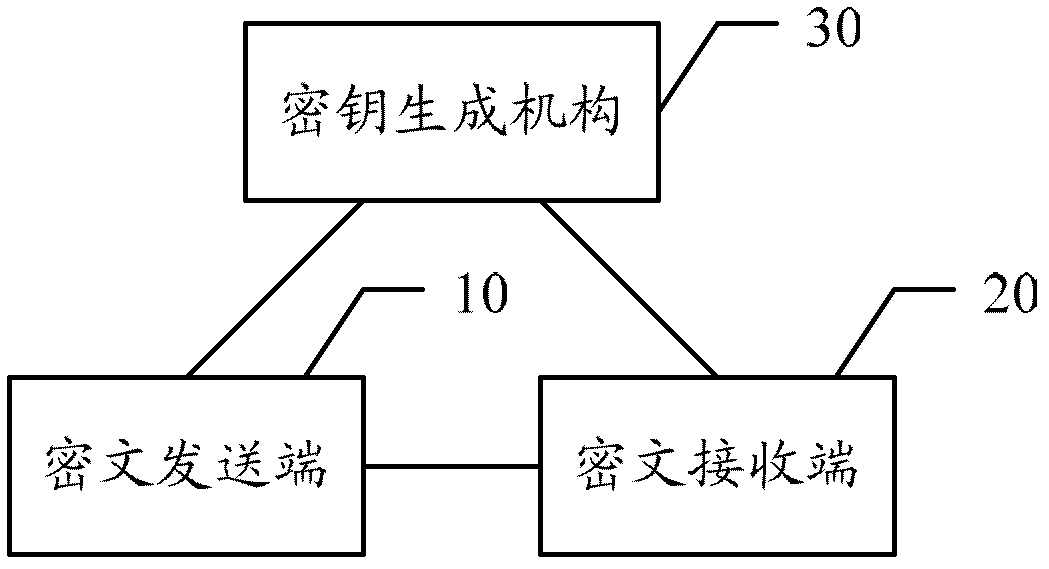
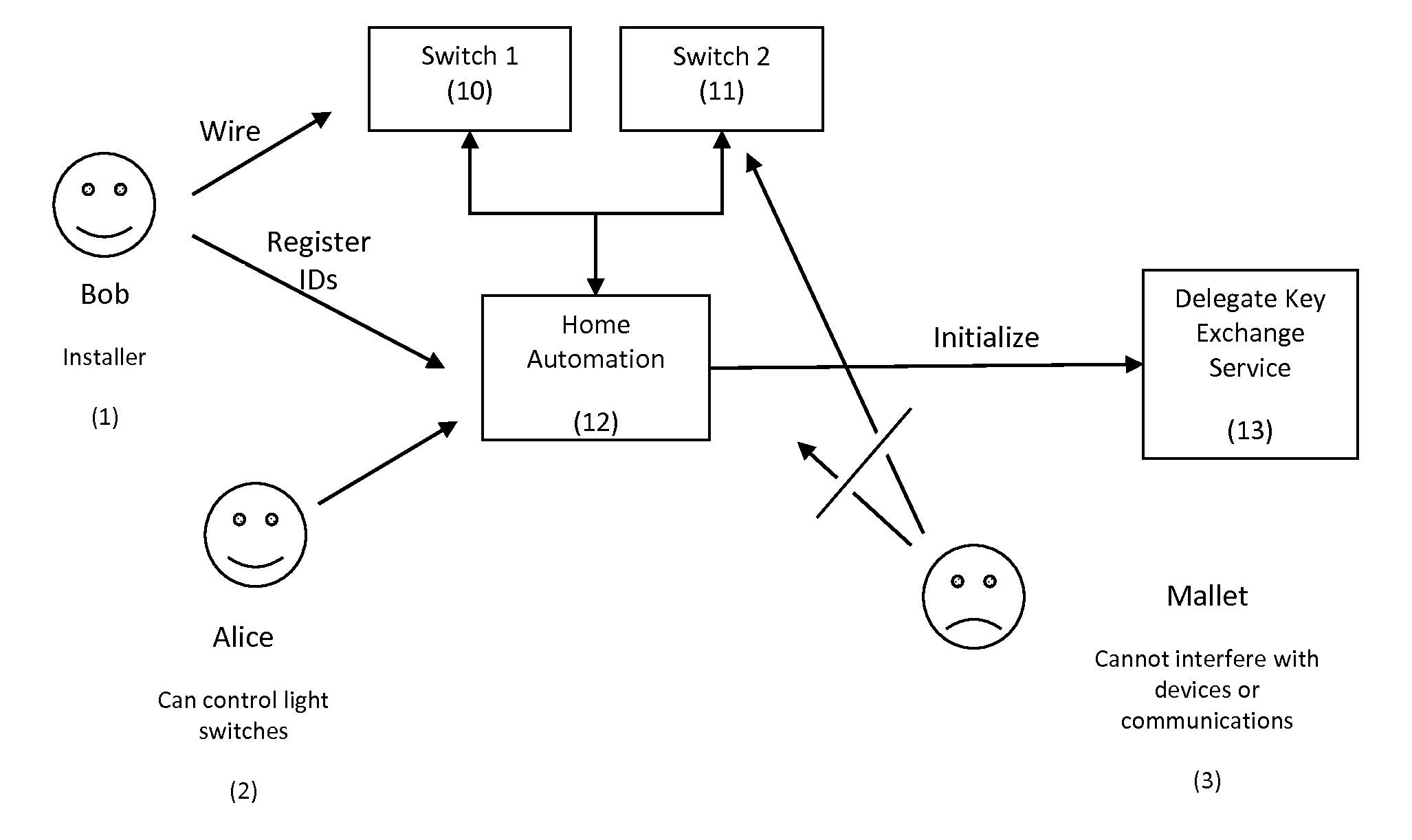
Delegated Key Exchange System and Method of Operation
A cryptographic key exchange protocol that enables a device that does not have the capability to perform public key operations to securely establish a shared key with a host device without any information disclosing the key being revealed to the delegate key service.
Owner:HALLAM BAKER PHILLIP MARTIN
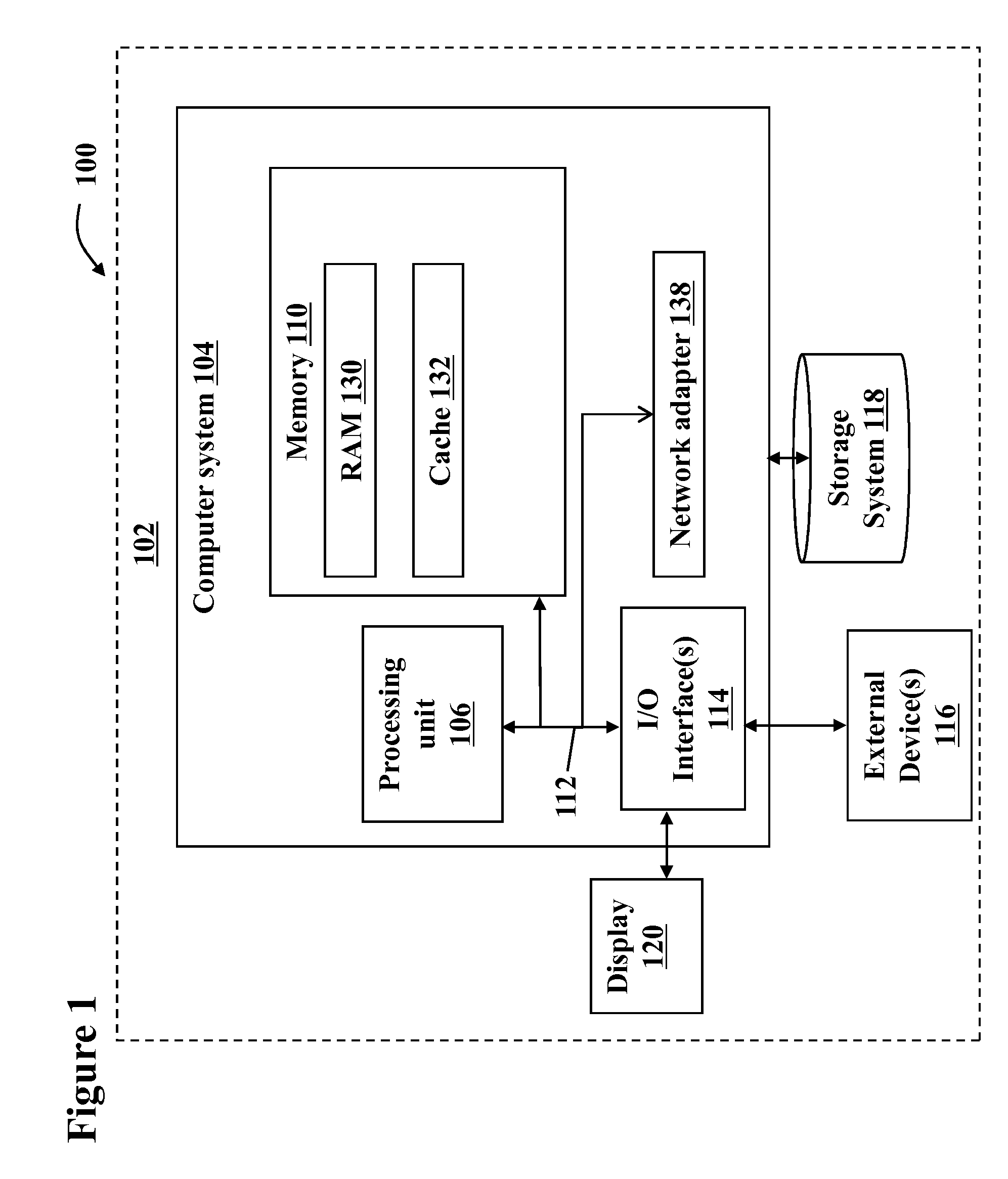
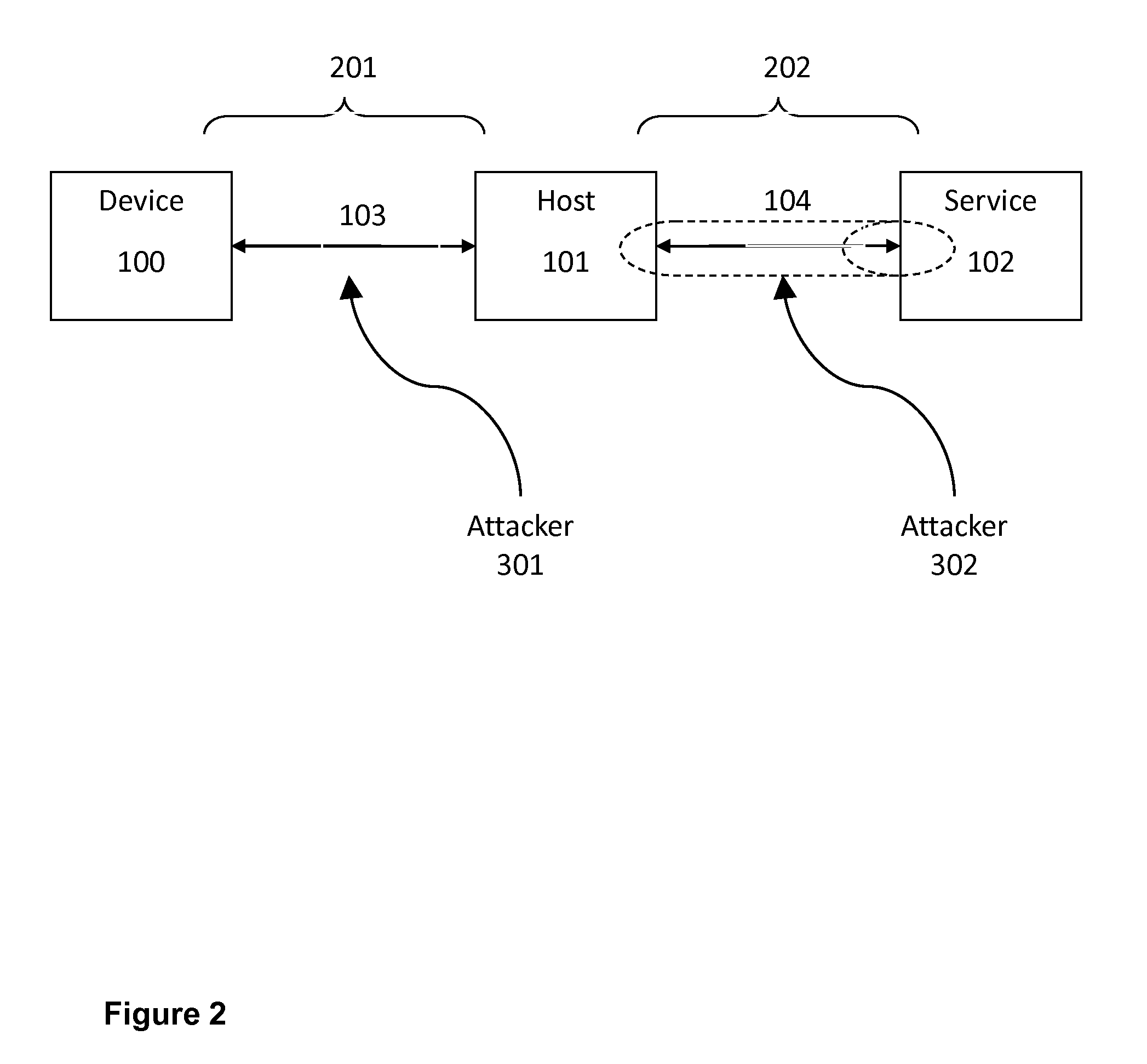
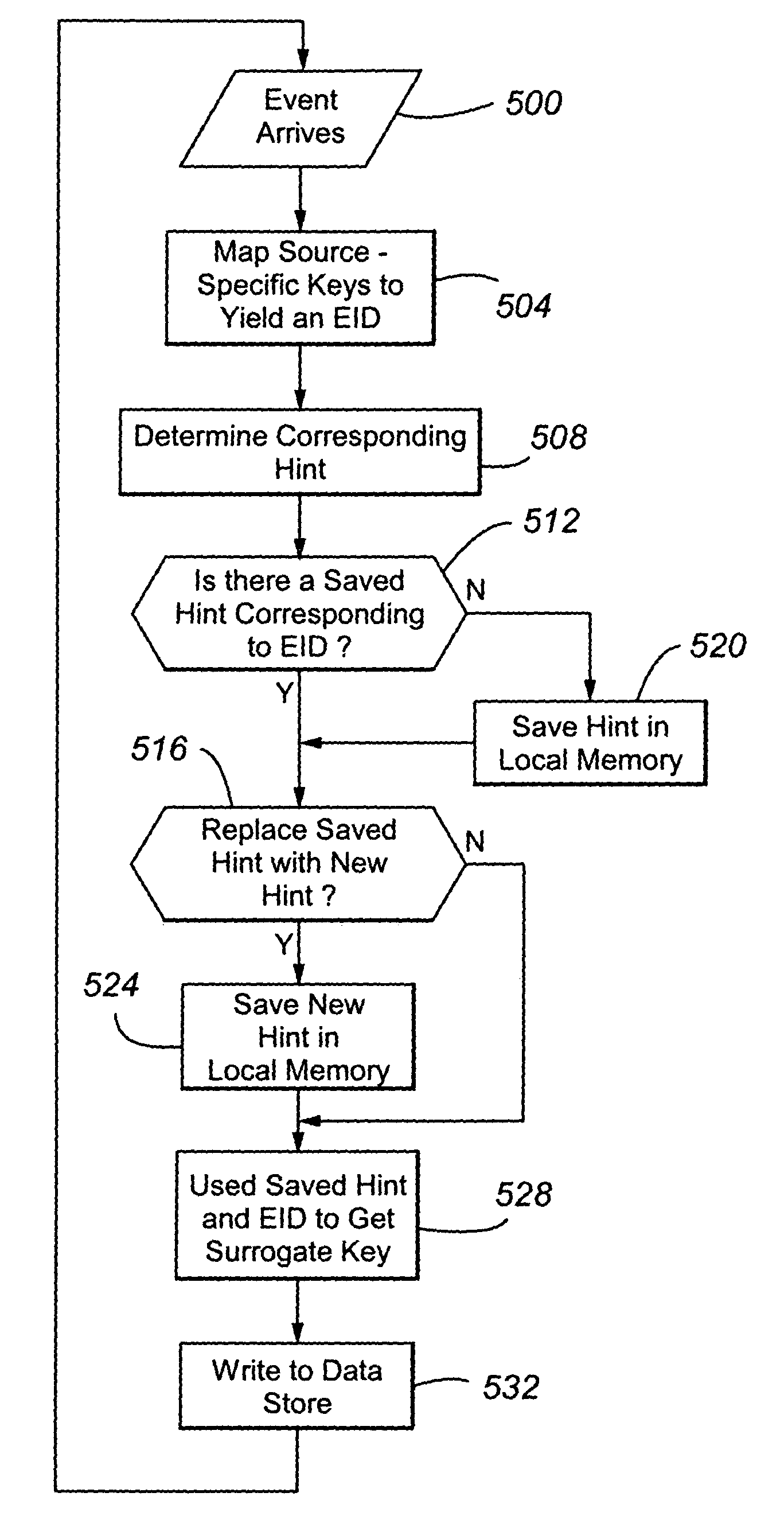
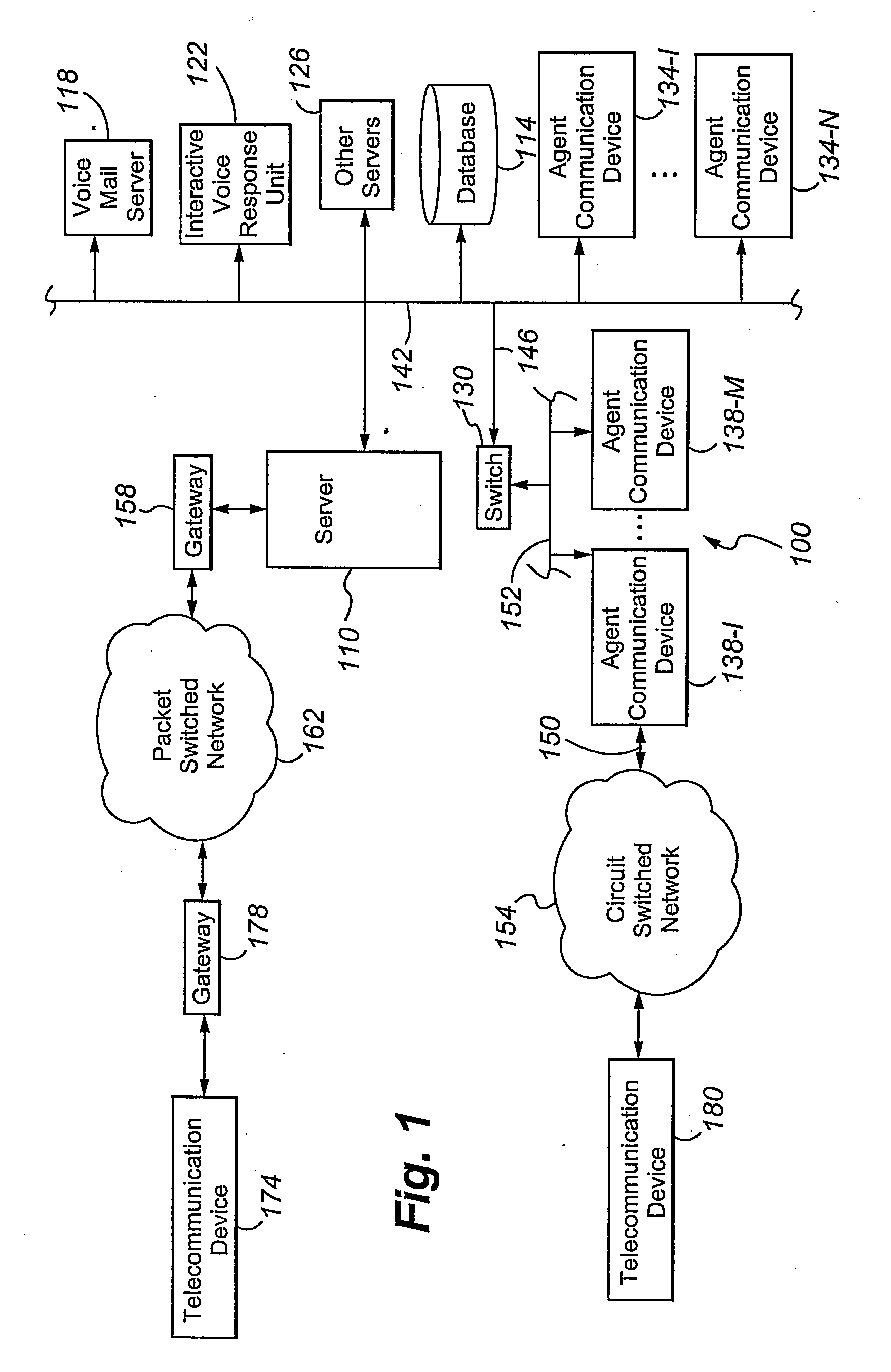
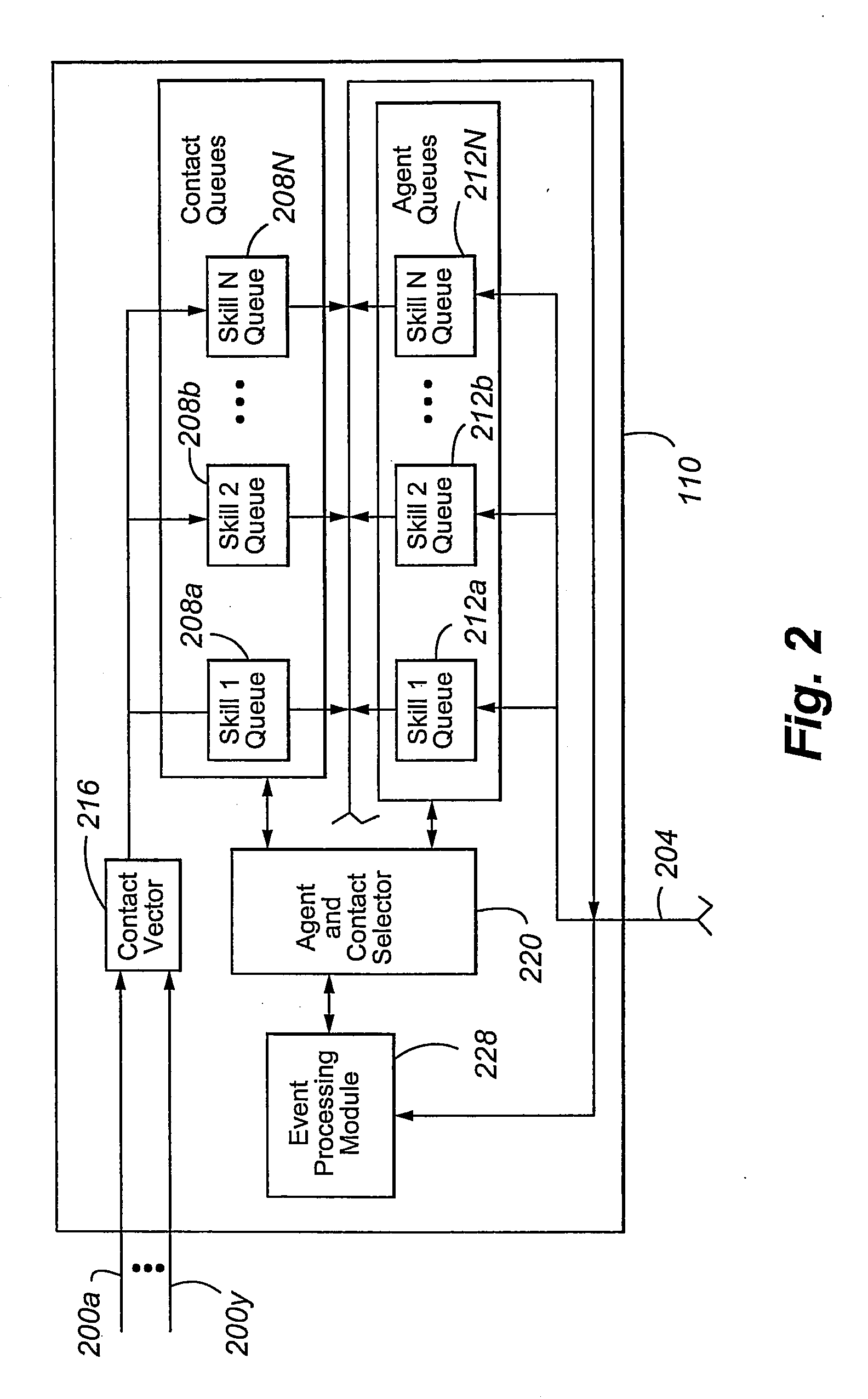
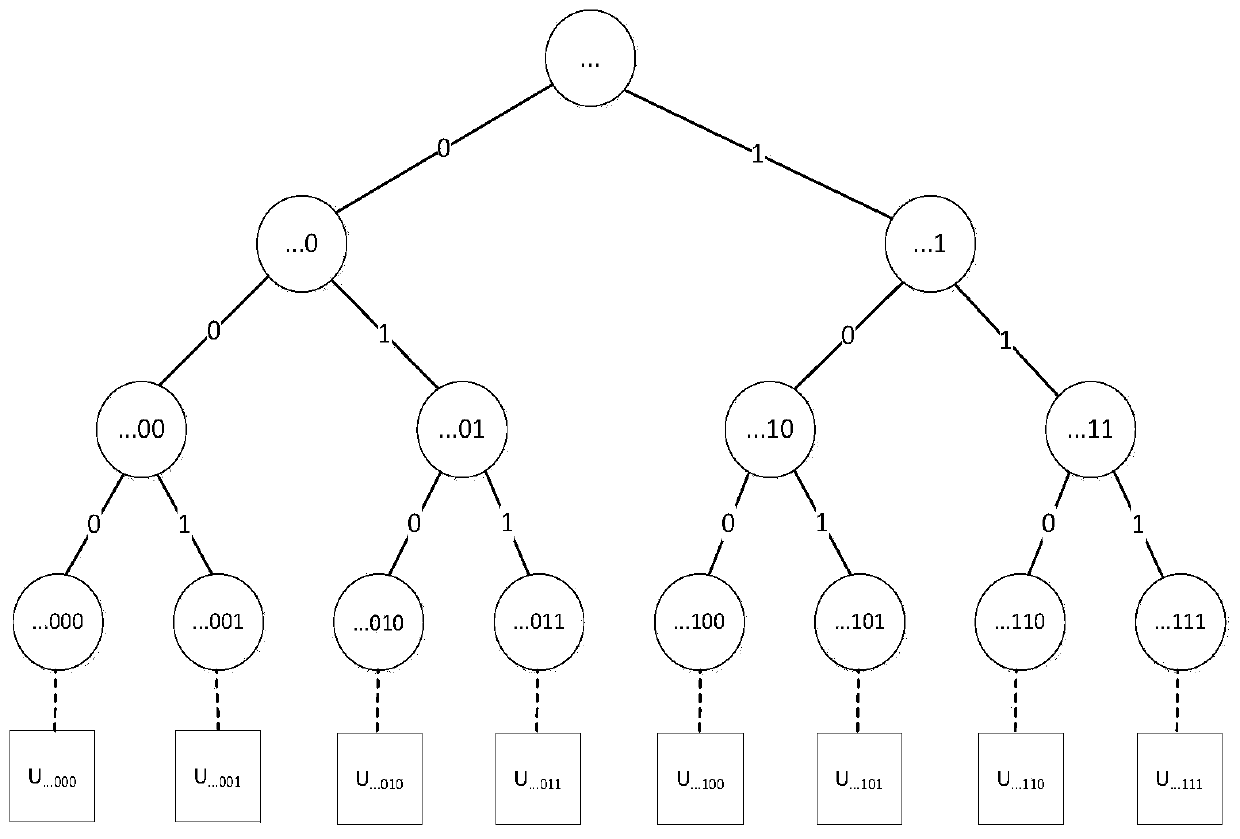
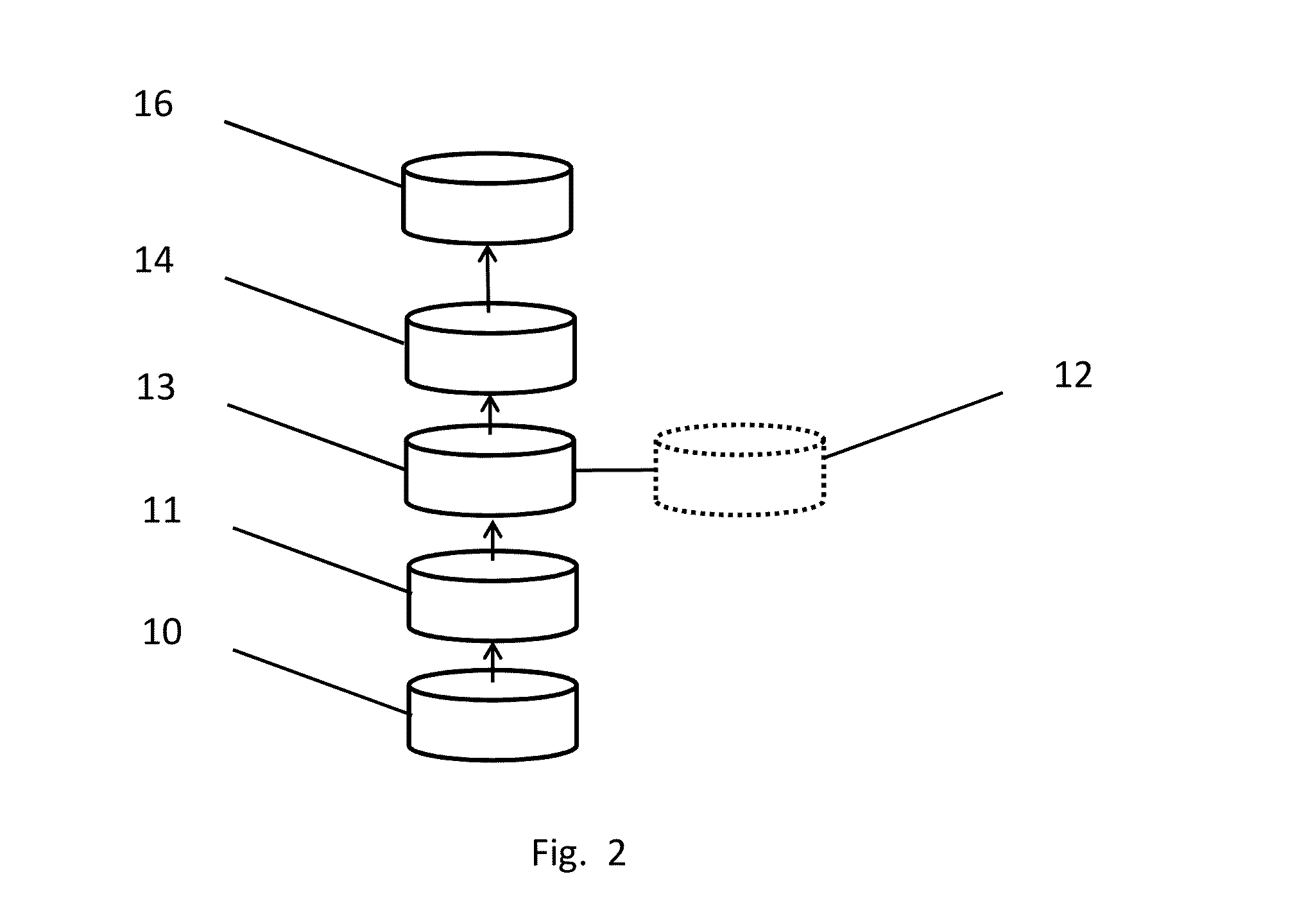
Deferred control of surrogate key generation in a distributed processing architecture
An event reporting system includes a computational component 228 operable (a) to receive notification of a change to an attribute of an entity, the entity, prior to the change, being associated with a first surrogate key, and (b) to defer the use of a second surrogate key for the entity until a selected time. The second surrogate key was generated to reflect the change.
Owner:AVAYA INC
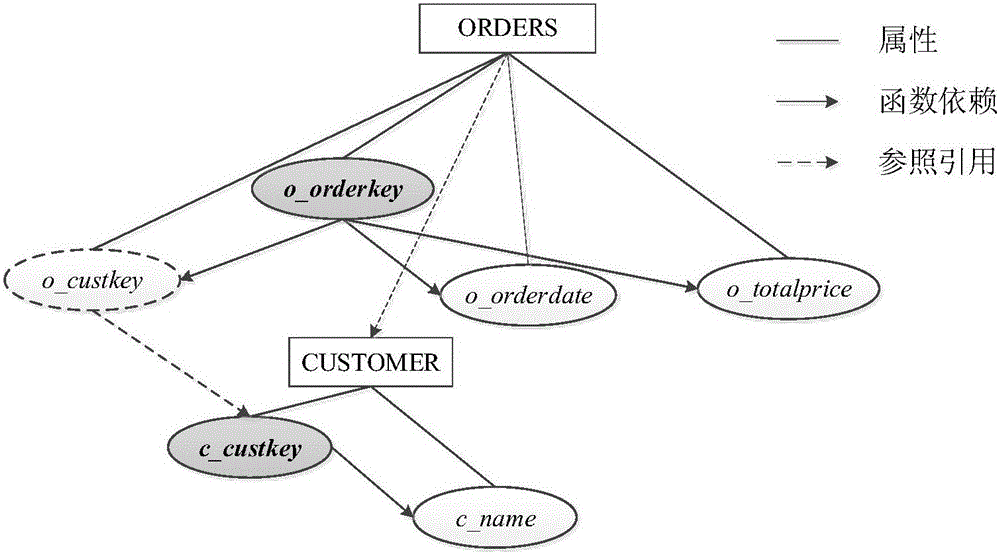
OLAP grouping aggregation method based on function dependency relationship
ActiveCN105930388AReduce the cost of group computingReduce computational costMulti-dimensional databasesSpecial data processing applicationsSurrogate keyData mining
The invention relates to an OLAP grouping aggregation method based on a function dependency relationship. The method comprises following steps: a function dependency tree structure among grouping attributes is defined, and the function dependency relationship between the grouping attributes and attributes among tables is defined; the grouping attribute of the GROUP BY clause is detected according to the grouping attribute function dependency tree; a query grouping attribute is divided into two subgroups which are formed by function dependency key attributes and other grouping attributes respectively; mode resolution is performed on a dimension table according to the function dependency relationship, wherein the dimension table adopts surrogate key mechanism and memory column storage mechanism; under the mechanisms of dimension table mode resolution and surrogate key index, grouping aggregation calculation further converts the subgroup attributes into function dependency attributes; after the grouping aggregation calculation is completed, the function dependency attributes are directly mapped to a memory offset address of related dimension table records according to function dependency attribute values to complete the operation of extracting other related grouping attributes. By means of the method, the size of grouping attributes can be reduced, and the Hash grouping calculating efficiency is increased.
Owner:RENMIN UNIVERSITY OF CHINA
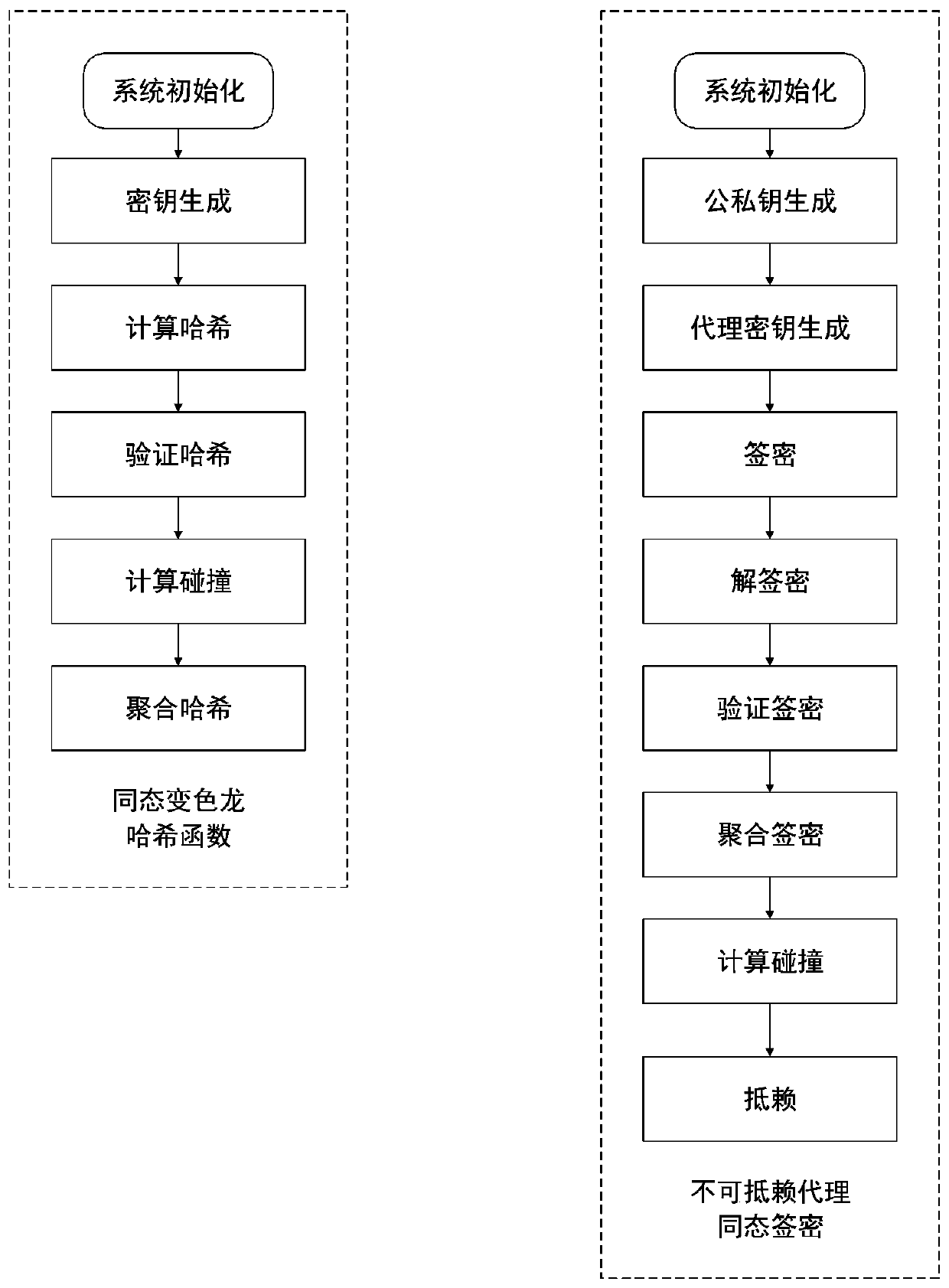
Hash calculation method and signcryption method based on homomorphic chameleon Hash function
ActiveCN110086599AComputationally efficientFunctionalKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionSurrogate key
The invention discloses a Hash calculation method and a signcryption method based on a homomorphic chameleon Hash function. According to the provided homomorphic chameleon hash function, a chameleon hash value result adopts a logarithm form, a signcryption result based on the hash in the signcryption method is also a logarithm form, so that the homomorphic property is achieved, the homomorphic aggregation can be conducted in hash calculation, hash is more efficiently calculated, and the homomorphic chameleon hash function has both the homomorphic state and the key leakage prevention characteristics. The signcryption method is realized on the basis of the homomorphic chameleon hash function, the homomorphic aggregation signcryption ensures the homomorphism, the system public parameters generated by the system initialization are used together by the chameleon hash function and the signcryption, and two password schemes share one set of system parameters, so that multiple function effectscan be realized under one set of shared system parameters, and multiple functions are supported under the same framework. Secondly, the proxy key generation and proxy re-signature steps realize the proxy re-signature, and the non-repudiation is realized through a repudiation step.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Method and equipment for generating inextensible unidirectional proxy re-encryption key, and method and system for executing inextensible unidirectional proxy re-encryption
InactiveCN102111269APublic key for secure communicationUser identity/authority verificationSurrogate keyProxy re-encryption
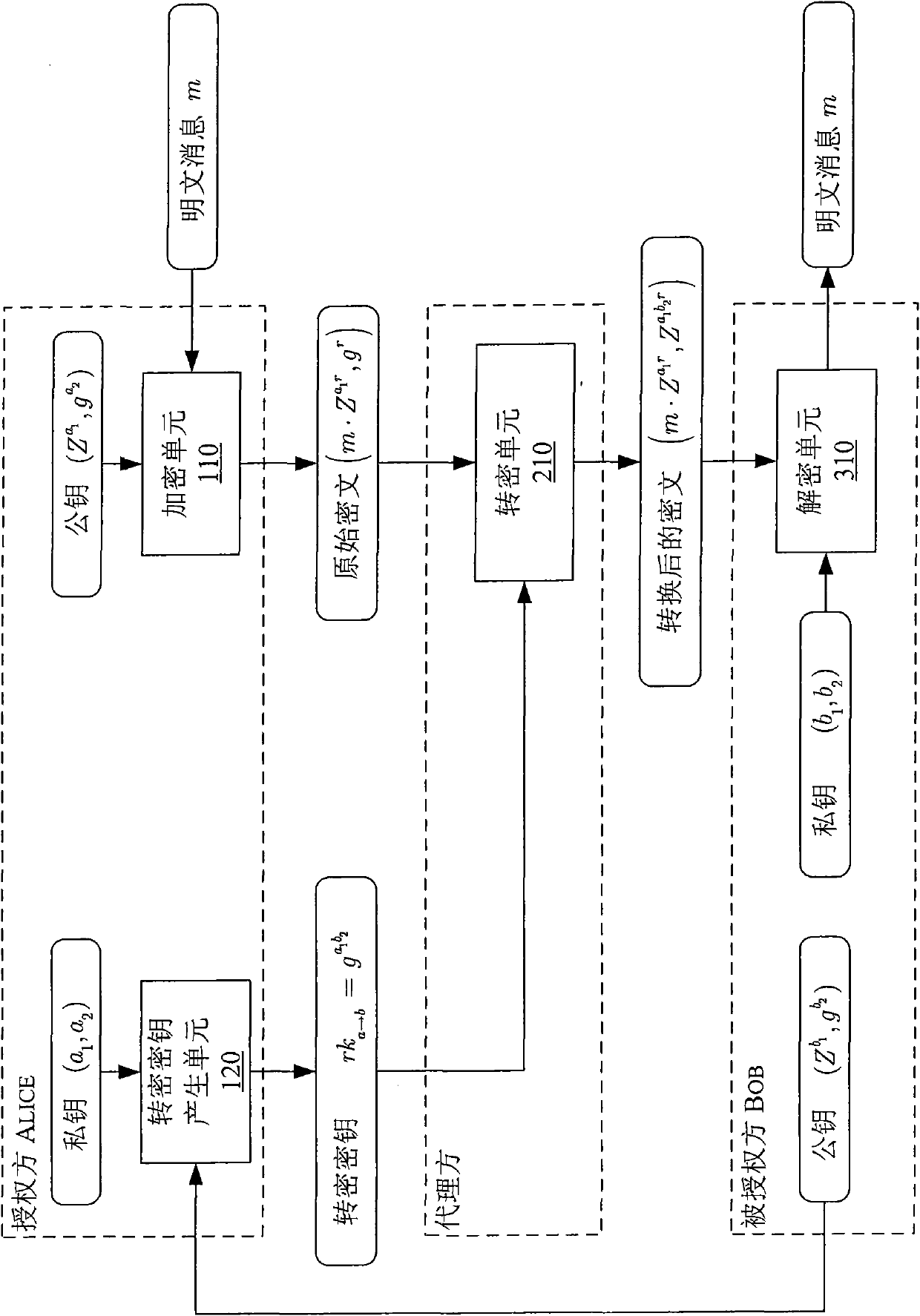
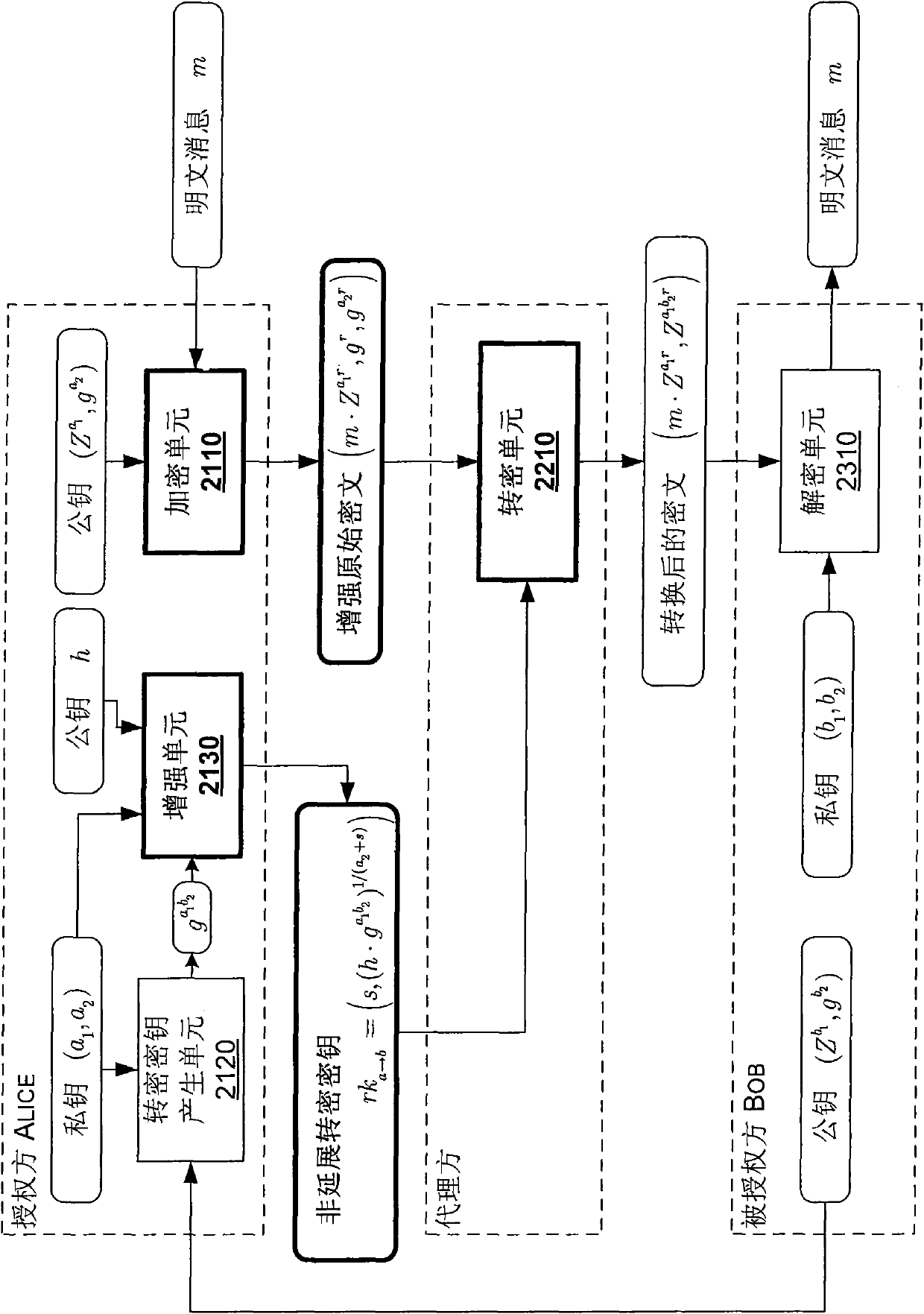
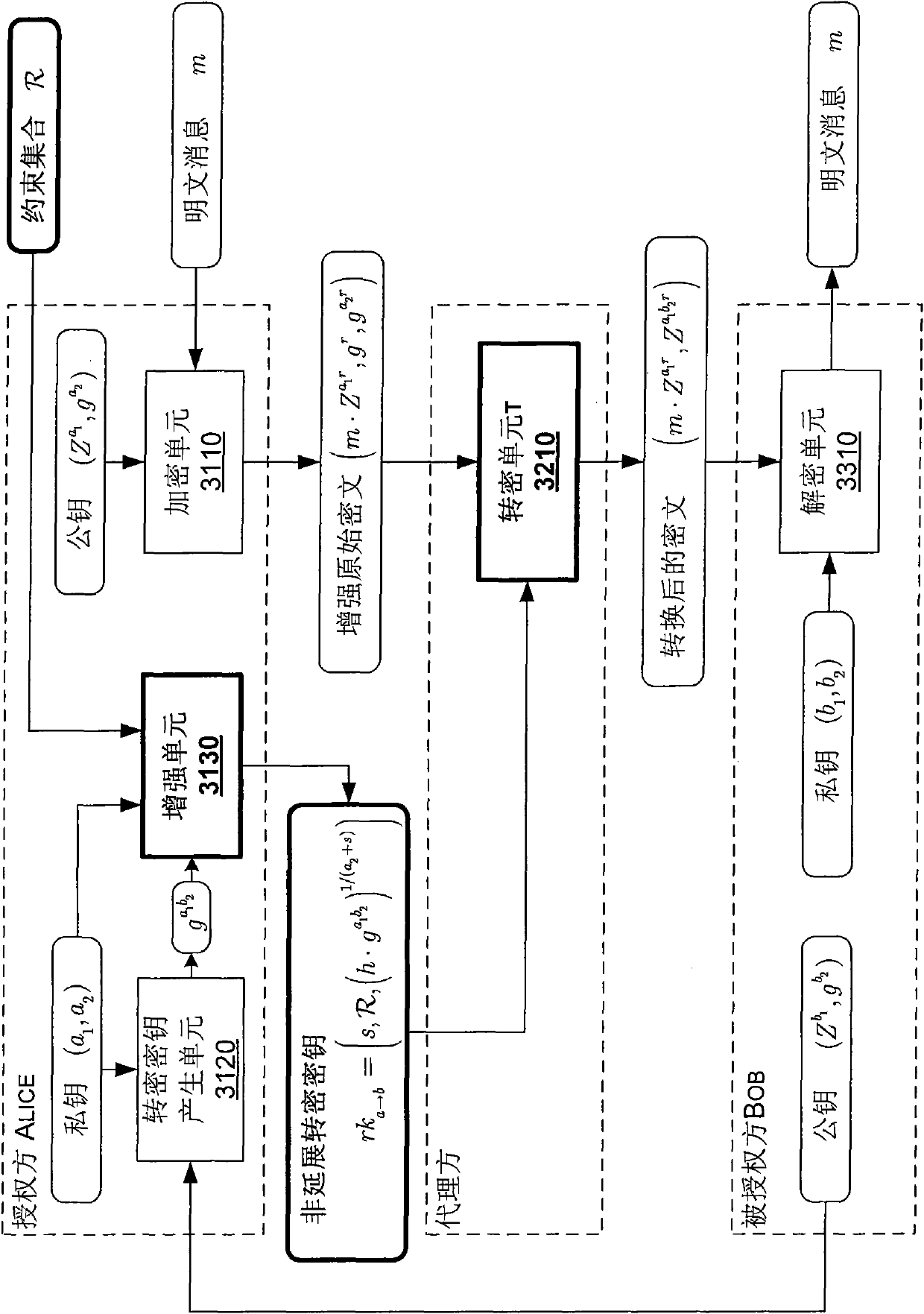
The invention discloses equipment for generating an inextensible unidirectional proxy re-encryption key. The equipment comprises a re-encryption key generating unit and a strengthening unit, wherein the re-encryption key generating unit is used for acquiring a private key pair (a1, a2) of an authoring part and a public key of an authorized part and generating a unidirectional proxy key according to one private key a1 in the private key pair of the authorizing part and the public key of the authorized part; and the strengthening unit is used for selecting an adjusting factor s, acquiring the public key h of the authorizing part, and generating the inextensible unidirectional proxy re-encryption key rka-b by introducing the selected adjusting factor s, the public key h of the authorizing part and the other private key a2 in the private key pair of the authorized part according to the generated unidirectional proxy re-encryption key. In addition, the invention also discloses a method for generating the inextensible unidirectional proxy re-encryption key, and a method and a system for executing inextensible unidirectional proxy re-encryption.
Owner:NEC (CHINA) CO LTD
Deferred control of surrogate key generation in a distributed processing architecture
InactiveUS20100235371A1Digital data processing detailsMulti-dimensional databasesSurrogate keyDatabase
An event reporting system includes a computational component 228 operable (a) to receive notification of a change to an attribute of an entity, the entity, prior to the change, being associated with a first surrogate key, and (b) to defer the use of a second surrogate key for the entity until a selected time. The second surrogate key was generated to reflect the change.
Owner:AVAYA INC
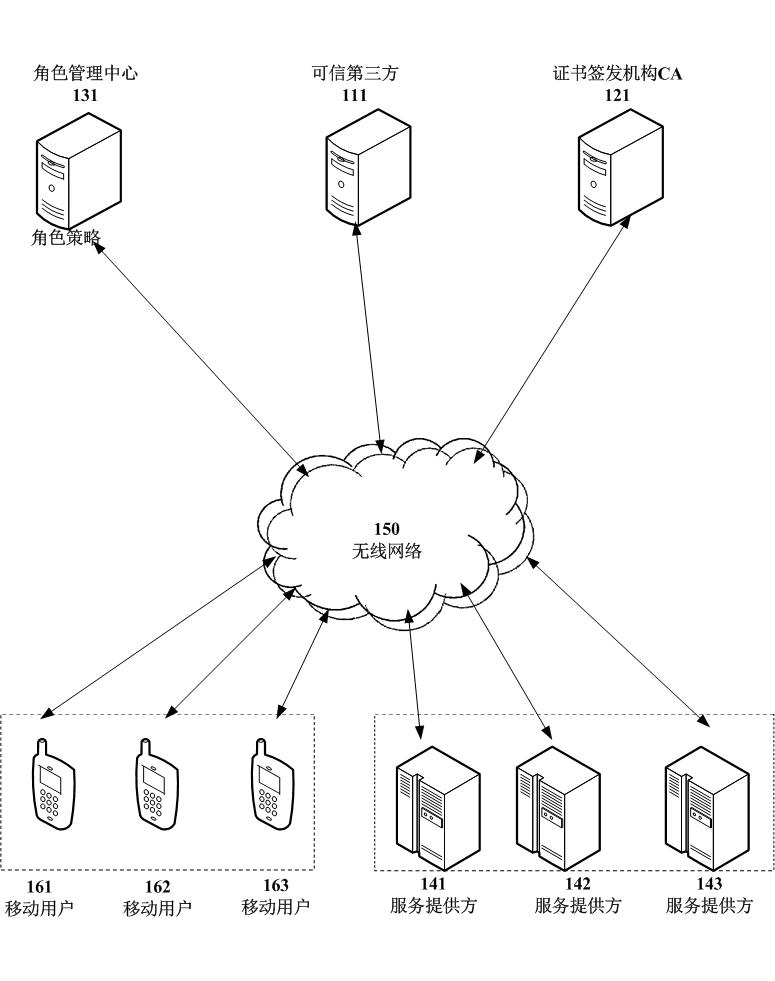
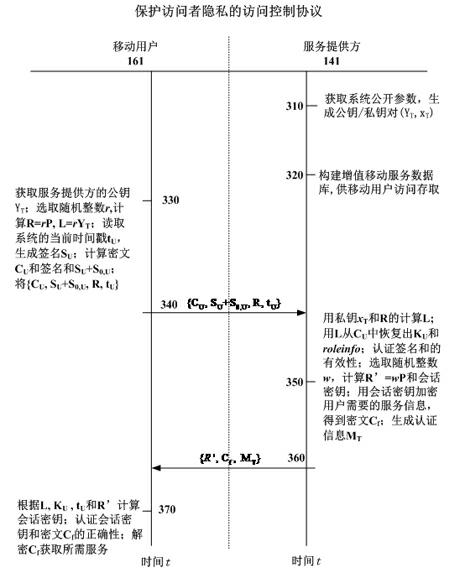
Access control method for protecting access privacy of user in mobile value-added service system
InactiveCN102665205AProtection precisionSuitable for development requirementsPublic key for secure communicationSecurity arrangementSurrogate keyRole management
The invention relates to the technical field of mobile value-added services, in particular to an access control method for protecting access privacy of a user in a mobile value-added service system. The method comprises system initialization, role-based authorization, certification and secret key consultation, tracking of the user and revocation of a user role. A role management center is required to implement honestly the authorization of the agent key and the opening of the anonymity, in particular, the role management center can not forge request information of the mobile user and protects interest of the user, and besides, a service provider does not know personal preferences of legal users to the mobile value-added service, so that the requirement of the system is reduced, the legitimate interests of users are safeguarded, the privacy right of users is protected and the method is suitable for development requirements of existing value added services.
Owner:JINAN UNIVERSITY
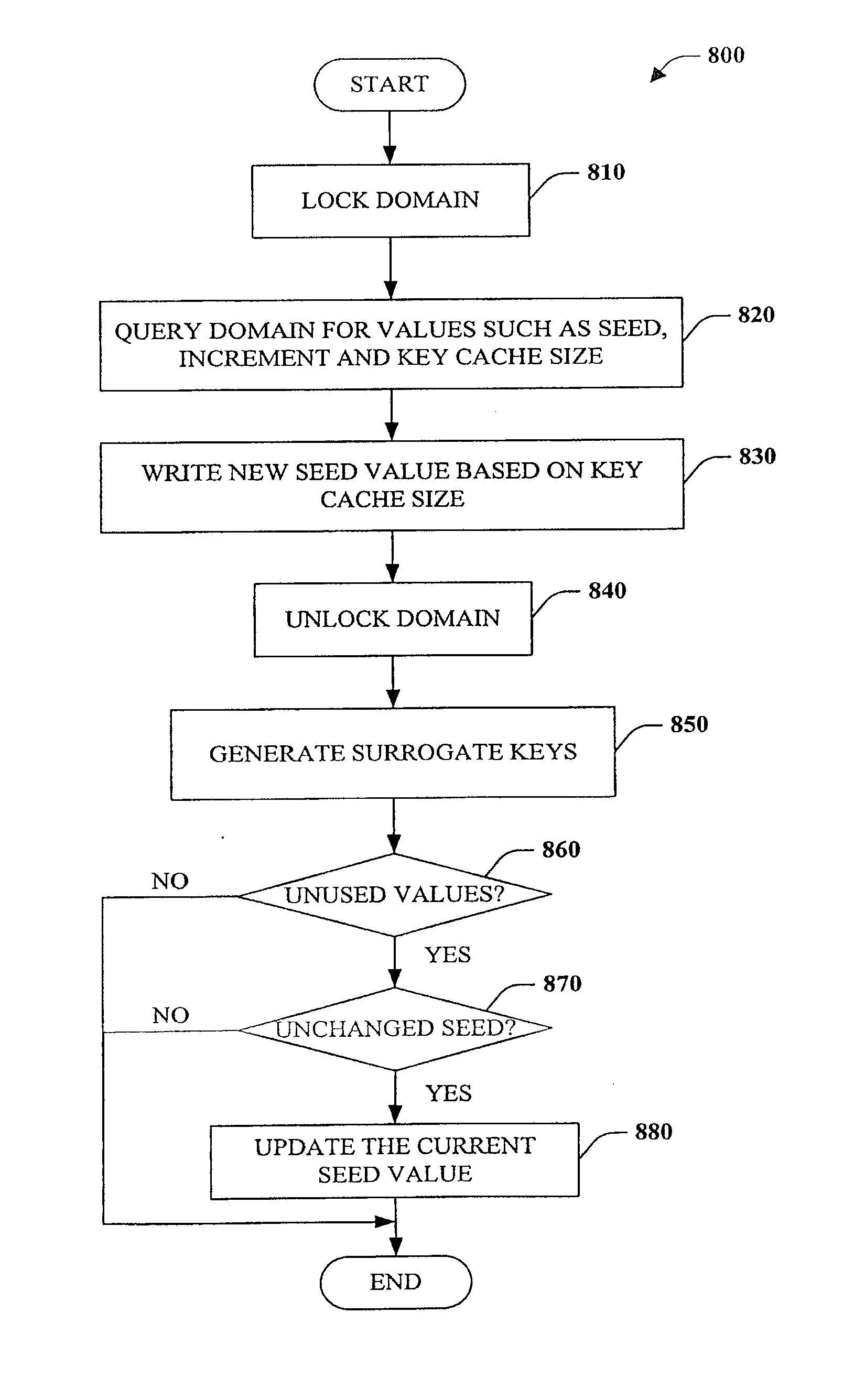
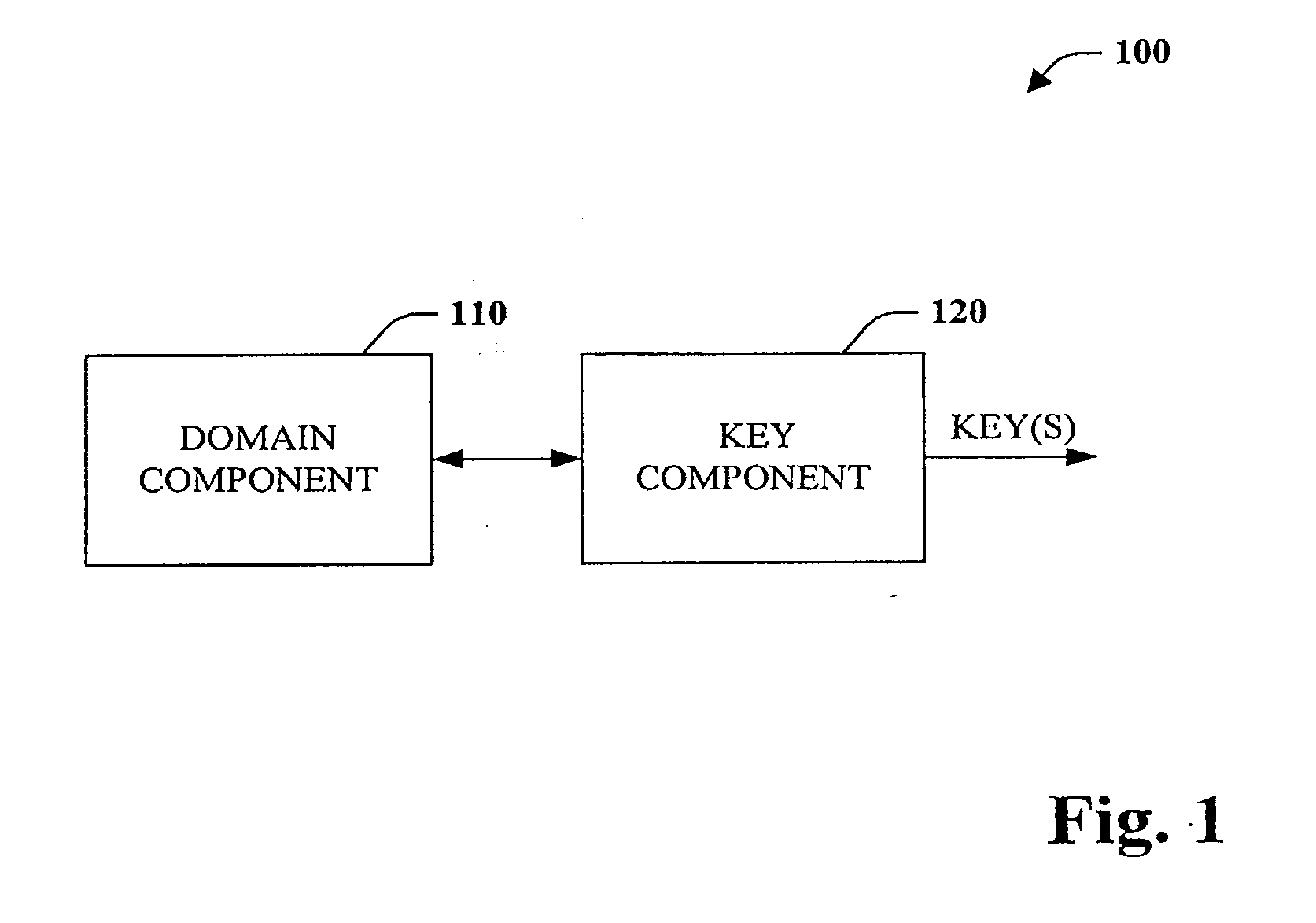
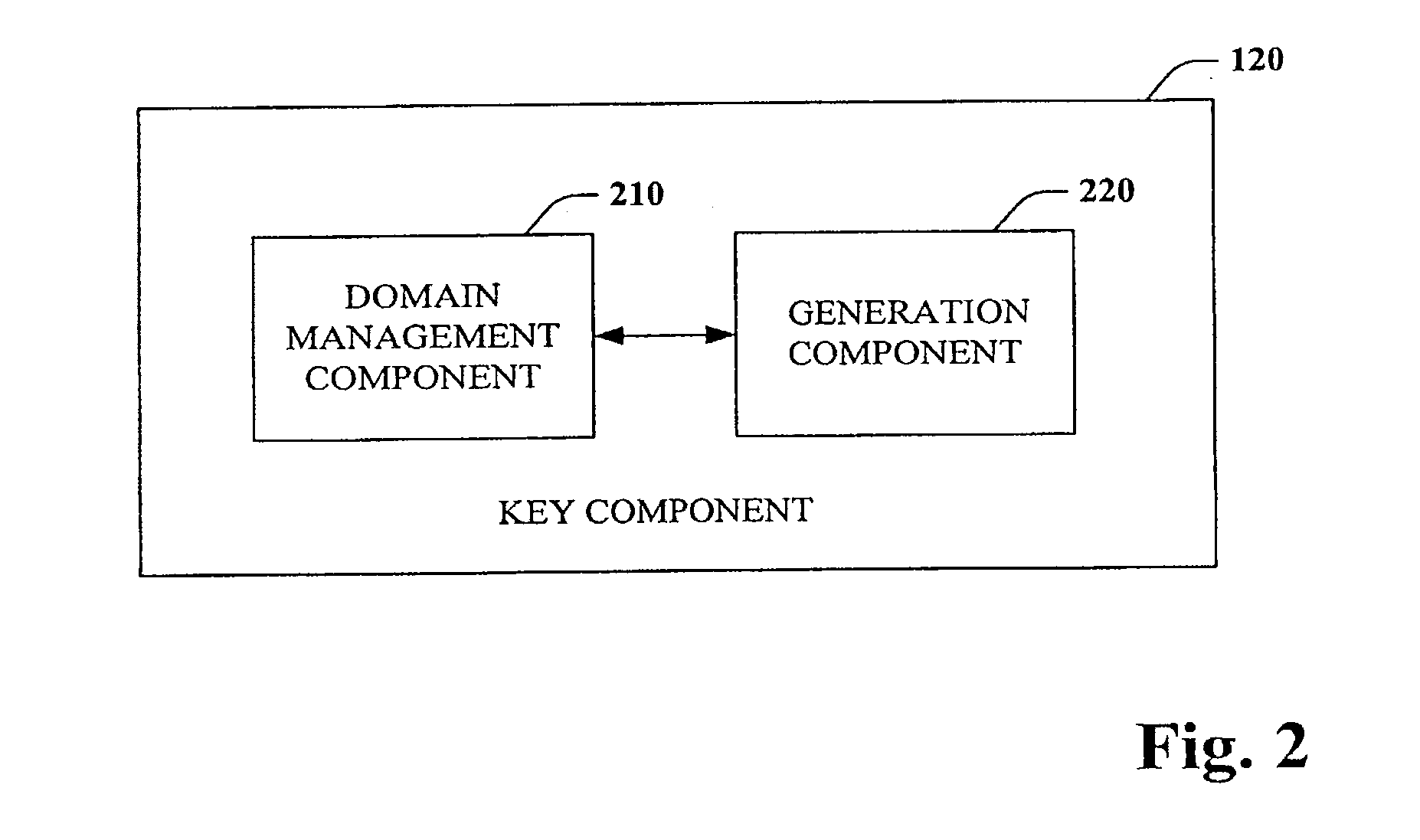
Surrogate key generation and utilization
InactiveUS20100332463A1Reduce the burden onAbility to provideDigital data processing detailsRelational databasesSurrogate keyData warehouse
The subject disclosure pertains to databases as well as generation and utilization of keys. A desired or default number of values can be requested from a domain and allocated for use. These values can be utilized to generate surrogate keys. Subsequently or concurrently, the keys can be employed with respect to operations such as single pass loading of databases and / or data warehouses. Any unused keys can be returned and made available for use by other users or processes. Furthermore, the key generation functionality can be provided outside a database thereby relieving a database system of this burden.
Owner:MICROSOFT TECH LICENSING LLC
Methodology supported business intelligence (BI) software and system
InactiveUS20140136472A1Extensive reusabilityDigital data processing detailsHierarchical databasesSurrogate keyOriginal data
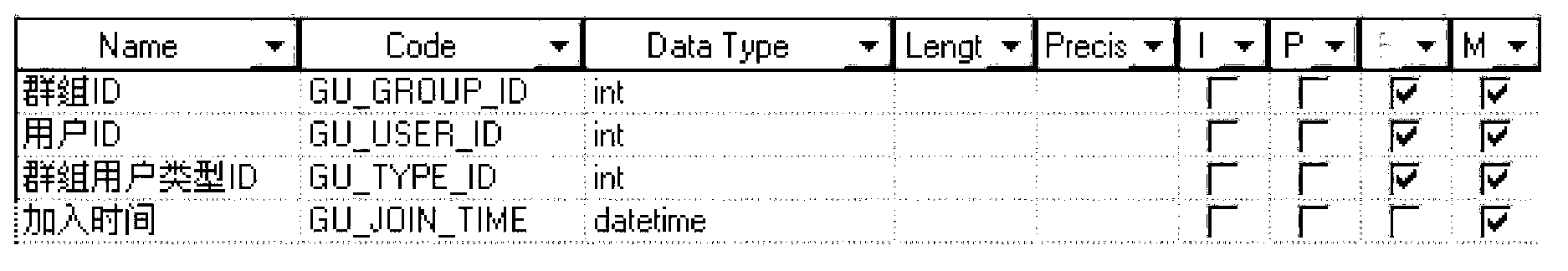
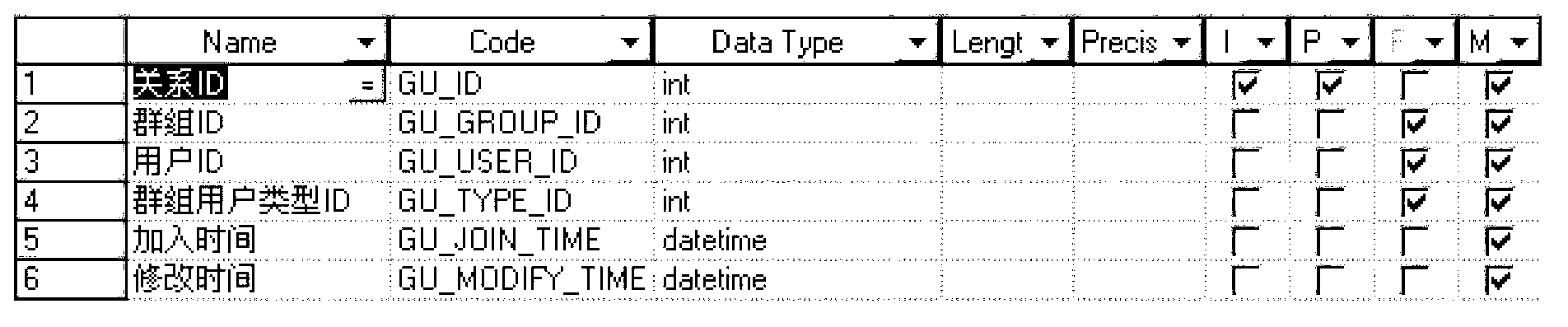
The invention provides idealized and reusable data source interfaces. The process of idealizing includes reengineering of the original data model using a surrogate key based model. The technique emphasizes readability and performance of the resulting operational data store.The invention provides a unique method for handling changes that allows all types of changes to be automatically implemented in the operational data store by table conversion.Further the invention provides Inline materialization that supports a continuous data flow dependency chain. The continuous dependency chain is used to provide automated documentation as well as dynamic paralleled transformation process.Finally master data integration is provided as a benefit of architecture and the inbuilt surrogate key based data model. The feature implements integrations by specification rather than by programming.
Owner:BI BUILDERS
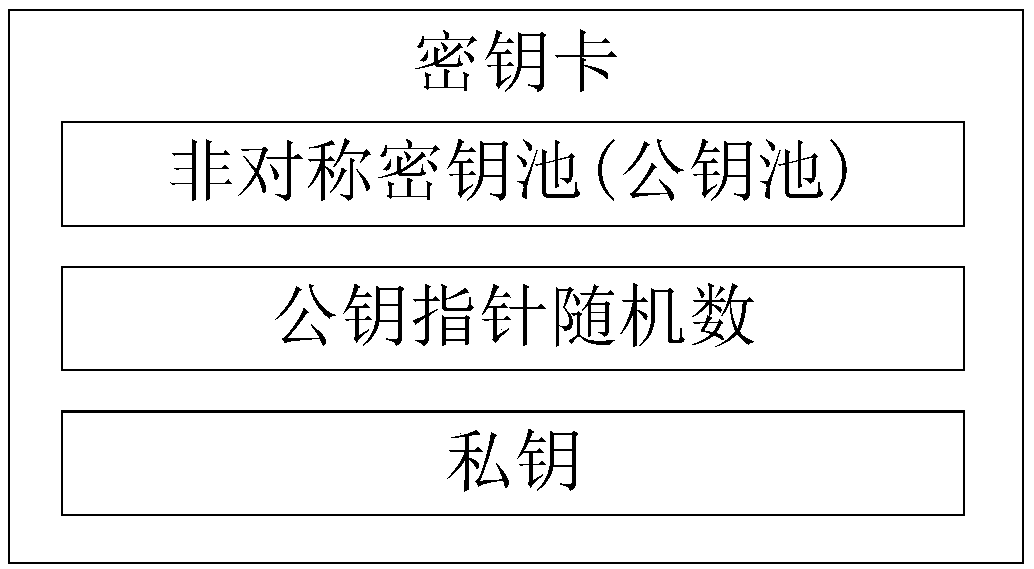
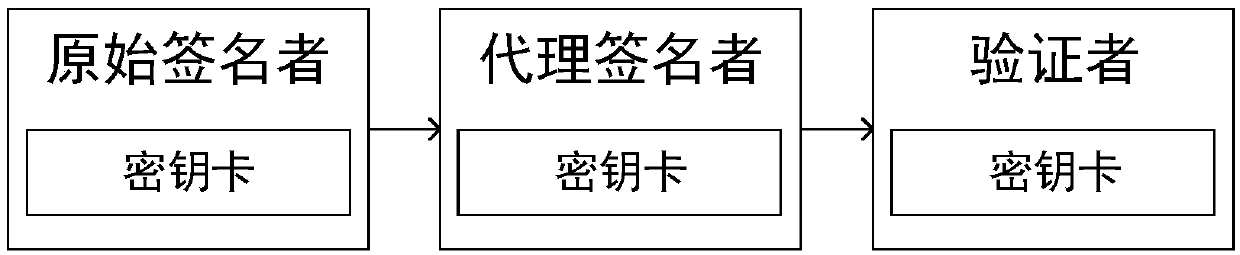
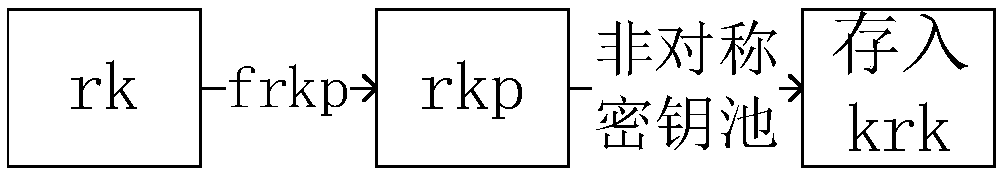
Anti-quantum computing proxy digital signature method and signature system based on asymmetric key pool, and computer equipment
ActiveCN109560926AAvoid crackingReduce the possibilityKey distribution for secure communicationPublic key for secure communicationSurrogate keyQuantum computer
The invention relates to an anti-quantum computing proxy digital signature method and an anti-quantum computing proxy digital signature system based on an asymmetric key pool, and computer equipment.The anti-quantum computing proxy digital method comprises the steps that: an original signature party uses a signature private key of the original signature party to generate a proxy key, and transmits an original text to be signed, the proxy key and a public key pointer random number corresponding to a signature public key of the original signature party to a proxy signature party; the proxy signature party obtains the signature public key of the original signature party from a secret key card of the proxy signature party according to the public key pointer random number, and utilizing the signature public key to verify the proxy key; performing signature operation on the original text by utilizing the proxy key to generate a file signature by the proxy signature party after the verification passes, and transmitting the original text, the file signature and the public key pointer random number to a verification party; and the verification party obtains a signature public key of the original signature party from a secret key card of the verification party according to the public key pointer random number, and verifies file the signature by utilizing the signature public key.
Owner:RUBAN QUANTUM TECH CO LTD
Universally composable identity proxy signcryption method
ActiveCN109286485AOvercoming problems such as computational costsTo achieve the effect of confidentiality and authenticationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputation complexitySurrogate key
The invention relates to a universally composable identity proxy signcryption method. The method includes the steps of system initialization, public and private key generation, proxy key generation, proxy signcryption, decryption, and verification. According to the universally composable identity proxy signcryption method, the public key of a user is determined according to the identity information of the user; and the private key of the user is generated through a private key generator. With the universally composable identity proxy signcryption method adopted, the problem of calculation costs for certificate generation, storage, distribution, revocation and verification of traditional public key infrastructure can be solved; with no secure channels required, confidentiality and authentication can be realized. The method of the invention has the advantages of universal composite security, low computational complexity, and the like, and is suitable for technical fields such as mobile agents and electronic conferences.
Owner:XIAN UNIV OF POSTS & TELECOMM +1
General surrogate key generation method for identity-based proxy cryptography method
InactiveCN105721430ASimple structureSmall amount of calculationUser identity/authority verificationHash functionSurrogate key
Provided is a general surrogate key generation method for an identity-based proxy cryptography method. The general surrogate key generation method can be applied to any known identity-based cryptography method. The general surrogate key generation method directly adopts a certificate of authorization as a surrogate public key. A Hash function is adopted to encrypt middle parameters. Various efficient identity-based proxy cryptography methods which are established by using the method of the invention can be widely applied to electronic commerce, mobile agents, distributed networks, etc., and greatly enhance the running efficiency and safety.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
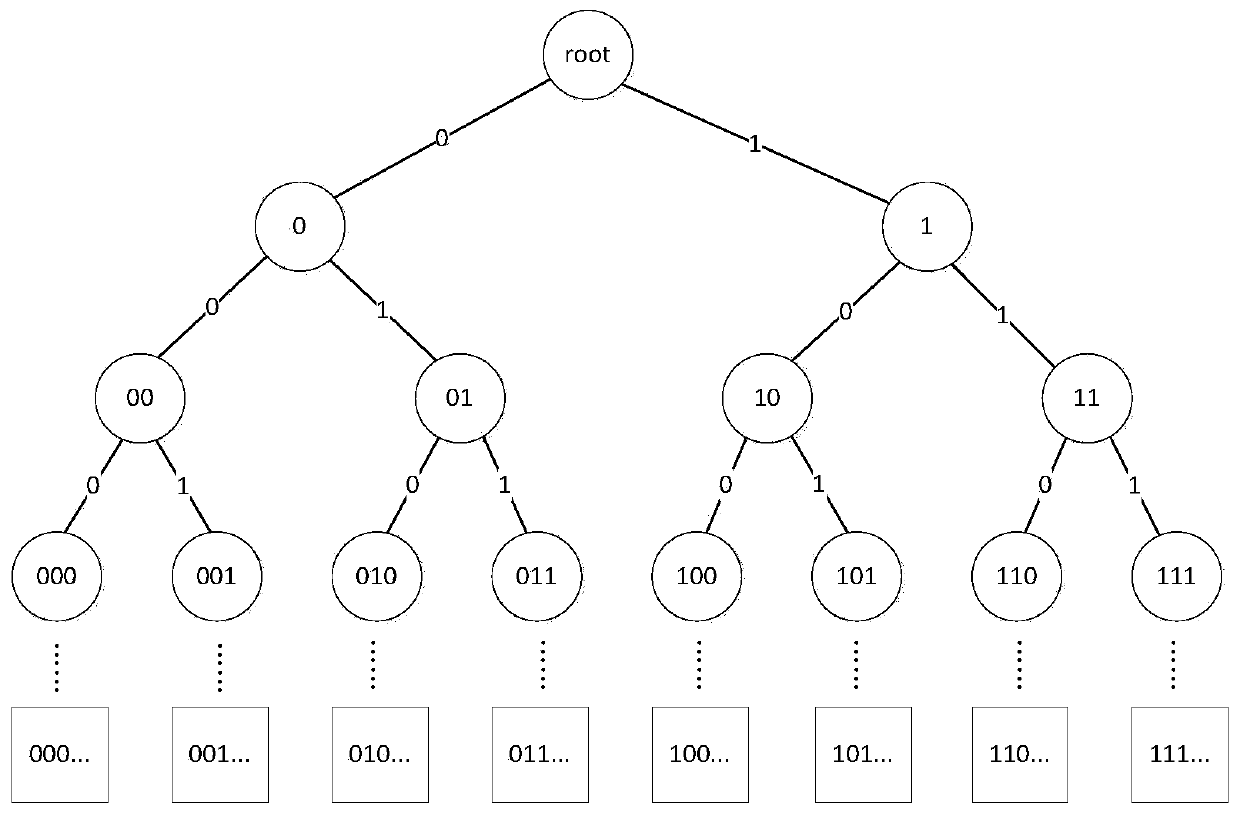
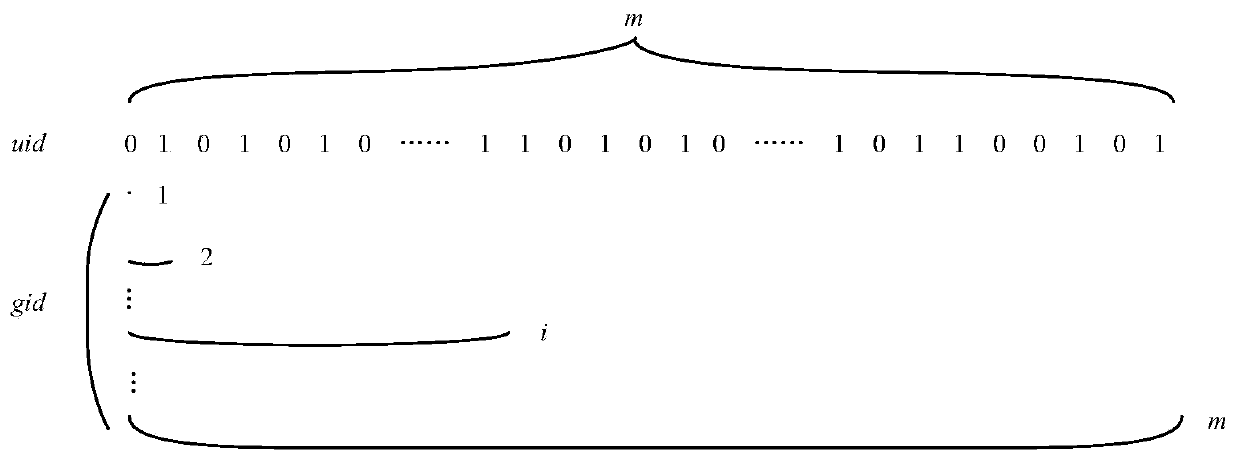
Attribute revocation method
ActiveCN110098926AReduce allocationEnsure safetyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesSurrogate keyConfidentiality
The invention discloses an attribute revocation method. A tree-shaped user space organization mode is used to define that the user identity identification code is a character string consisting of 0\ 1characters; the identity identification codes of all users have the same length m; the user identity space is a global I composed of all possible user identity identification codes; the size of the domain is 2m; groups are divided according to attribute use conditions; the users are randomly divided into irrelevant groups; the minimum coverage mechanism is introduced, a reduced user group is organized by using a minimum coverage group mechanism; the group identification code representing one user group is stored in the revoked user group, a combination mechanism is introduced, the adjacent groups are combined into one group when no user enters the user group with the revoked authority, and the proxy key of the user and the interpolation factor of the reduced user group are updated to complete attribute revocation. According to the method, collusion attacks can be resisted, and the confidentiality of the data and the forward and backward security of the data are ensured.
Owner:XI AN JIAOTONG UNIV
A query optimization method based on join index in data warehouse
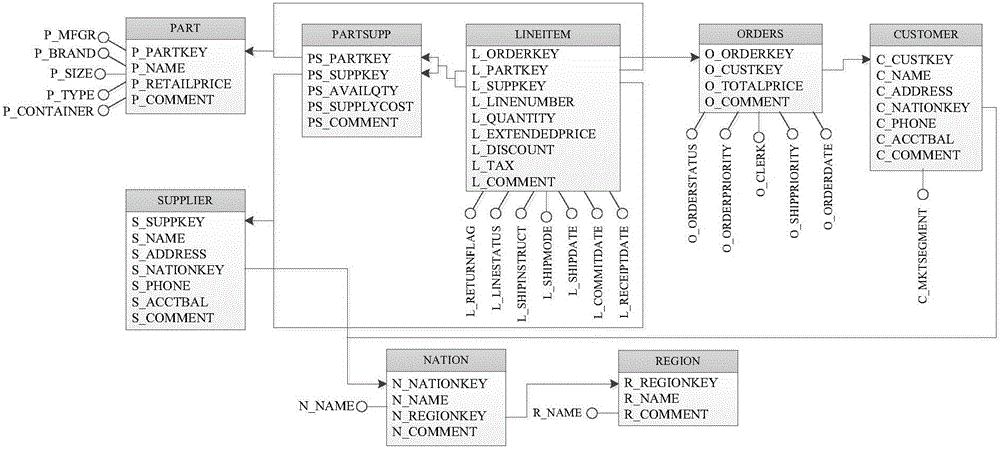
ActiveCN104866608BReduce storage overheadReduce maintenance costsMulti-dimensional databasesSpecial data processing applicationsMemory addressSurrogate key
The invention relates to a query optimization method based on a connection index in a data warehouse. The steps are: creating a connection index of a fact table foreign key based on a dimension table proxy key; creating a connection index update strategy; when there is a predicate condition on the dimension table, through the connection After the index directly accesses the dimension table records, it needs to judge the predicate, and refer to the bitmap connection index to generate the connection bitmap index through dynamic bitmap connection index calculation; when the selection rate on the dimension table is very low, the dimension table bitmap is further compressed to improve the dimensionality. The cache level of the table bitmap calculation; the calculation method of the reference bitmap connection index based on the coprocessor memory calculation is adopted, and only the array and the bitmap data structure are used to calculate the simple memory address access. The invention can effectively improve the computing performance of the bitmap index, and can be combined with high-performance coprocessors such as GPU and Xeon PhiTM to accelerate the computing performance of the index, and can be widely used in the field of data warehouses.
Owner:RENMIN UNIVERSITY OF CHINA
Methodology supported business intelligence (BI) software and system
InactiveUS20150006469A1Extensive reusabilityDigital data processing detailsCommerceSurrogate keyDocumentation procedure
The disclosed device provides idealized and reusable data source interfaces. The process of idealizing includes reengineering of an original data model using a surrogate key based model. The technique emphasizes readability and performance of the resulting operational data store. In, addition, the disclosed device provides a unique method for handling changes which allows for all types of changes to be automatically implemented in the operational data store by table conversion. Further the disclosed device provides inline materialization which supports a continuous data flow dependency chain. A continuous dependency chain is used to provide automated documentation as well as a dynamic paralleled transformation process.
Owner:BI BUILDERS
Surrogate key generation using cryptographic hashing
InactiveUS8369523B2Validating data qualityReduce data redundancyDigital data information retrievalEncryption apparatus with shift registers/memoriesSurrogate keySecret code
The present invention relates to a method or system of generating a surrogate key using cryptographic hashing. One embodiment of the method of the present invention may have steps such as selecting a field or group of fields that is or are unique among all records in the database, for each record, extracting the data from the fields, concatenating the extracted data into an input message, running the input message through a hash generator, either in batches or one at a time, for testing purposes perhaps, and outputting a surrogate key.
Owner:INT BUSINESS MASCH CORP
Certificateless and pairless identity-based proxy signcryption method and system
ActiveCN103905189BTroubleshoot hosting issuesPublic key for secure communicationUser identity/authority verificationSurrogate keySigncryption
Owner:AEROSPACE INFORMATION
Atomic index storage method based on bitmap summary model
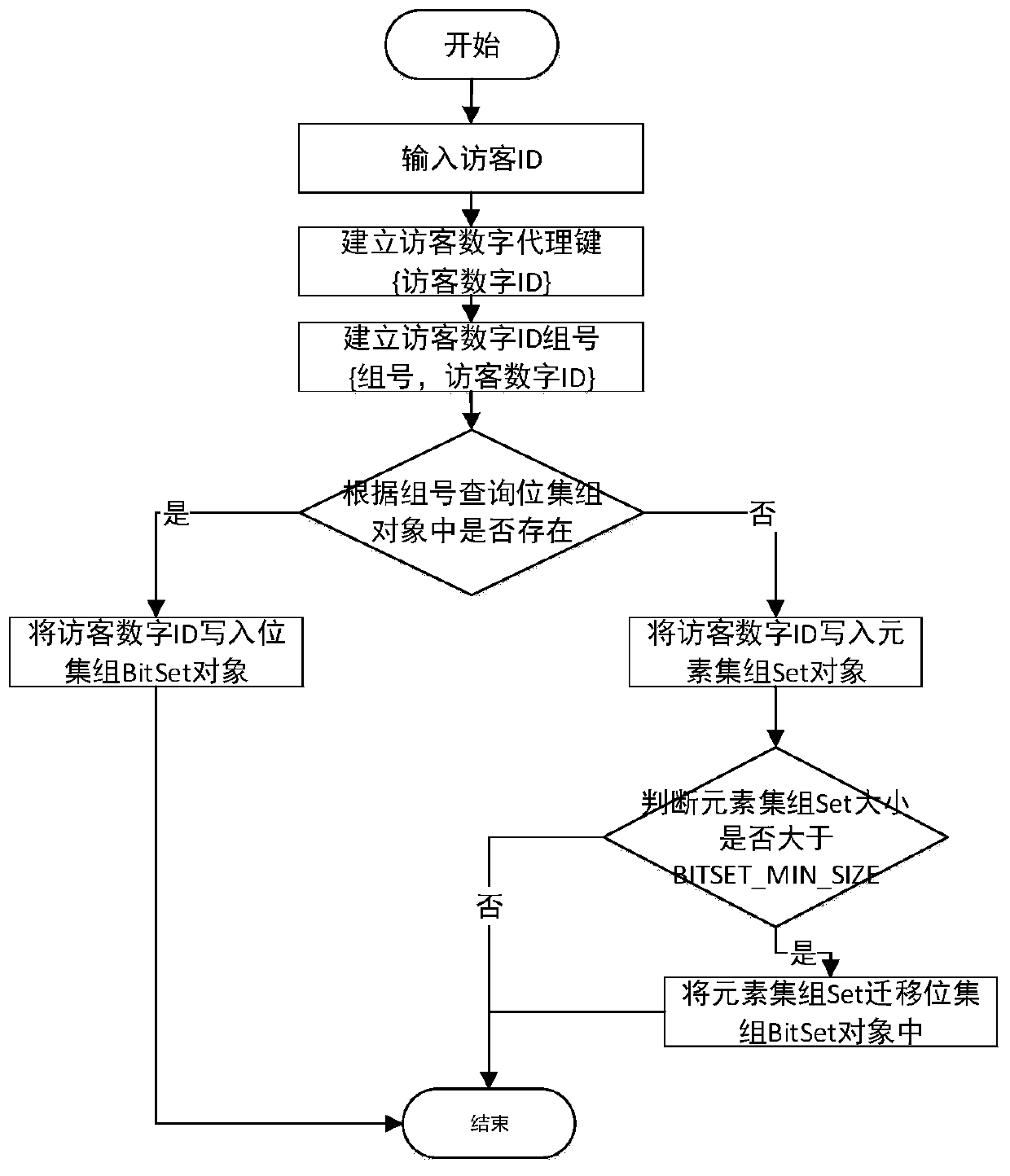
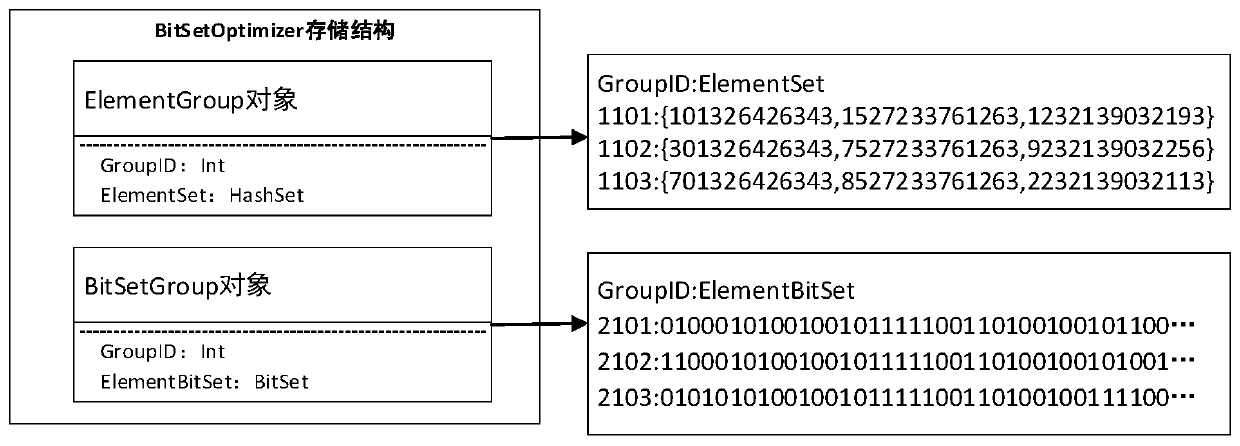
ActiveCN111221816AReduce meshReduce storage sizeSpecial data processing applicationsDatabase indexingCode moduleSurrogate key
The invention discloses an atomic index storage method and system based on a bitmap summary model, and the method comprises the steps that a bitmap optimizer carries out grouping storage of proxy keydigital indexes of atomic indexes, and comprises an element group object and a bit set group object; a digital coding module performs digital coding on the atomic indexes to be stored to generate proxy key digital indexes and corresponding group numbers of the atomic indexes; and a matching storage module respectively matches the atomic indexes to be stored with the bit set group object and the element group object of the bitmap optimizer, and stores proxy key digital indexes of the atomic indexes. The number of data entries and the storage size can be reduced, and the aggregation query efficiency is improved.
Owner:SUNING CLOUD COMPUTING CO LTD
Methodology supported business intelligence (BI) software and system
InactiveUS20160259831A1Extensive reusabilityBuying/selling/leasing transactionsHierarchical databasesSurrogate keyDocumentation procedure
The disclosed device provides idealized and reusable data source interfaces. The process of idealizing includes reengineering of an original data model using a surrogate key based model. The technique emphasizes readability and performance of the resulting operational data store. In, addition, the disclosed device provides a unique method for handling changes which allows for all types of changes to be automatically implemented in the operational data store by table conversion. Further the disclosed device provides inline materialization which supports a continuous data flow dependency chain. A continuous dependency chain is used to provide automated documentation as well as a dynamic paralleled transformation process.
Owner:BI BUILDERS
Method, device and system for processing cipher text
InactiveCN102404121BReduce usageImprove scalabilityPublic key for secure communicationUser identity/authority verificationExtensibilitySurrogate key
Embodiments of the present invention disclose a ciphertext processing method, apparatus, and system. The method includes: selecting, by a ciphertext sending end, a random secret value; calculating a private key of a local end according to a partial private key acquired by the local end and the random secret value; calculating a proxy key according to the private key of the local end and a public key publicized by a ciphertext receiving end, where the public key publicized by the ciphertext receiving end is calculated by the ciphertext receiving end according to a random secret value selected by the ciphertext receiving end and a system public parameter; and sending the proxy key, so that the ciphertext receiving end acquires a ciphertext obtained after a re-encryption operation is performed, according to the proxy key, on a ciphertext sent by the ciphertext sending end, and performs decryption. Existing defects of a ciphertext re-encrypting technology in a collusion aspect can be effectively avoided by adopting the embodiments of the present invention, thereby better ensuring information security, and meanwhile, implementation of the present invention avoids using a public key infrastructure (PKI), thereby having better extensibility.
Owner:HUAWEI TECH CO LTD
A Grouping Aggregation Method of Olap Based on Functional Dependency
ActiveCN105930388BReduce the cost of group computingReduce computational costMulti-dimensional databasesSpecial data processing applicationsSurrogate keyData mining
The invention relates to an OLAP grouping aggregation method based on a function dependency relationship. The method comprises following steps: a function dependency tree structure among grouping attributes is defined, and the function dependency relationship between the grouping attributes and attributes among tables is defined; the grouping attribute of the GROUP BY clause is detected according to the grouping attribute function dependency tree; a query grouping attribute is divided into two subgroups which are formed by function dependency key attributes and other grouping attributes respectively; mode resolution is performed on a dimension table according to the function dependency relationship, wherein the dimension table adopts surrogate key mechanism and memory column storage mechanism; under the mechanisms of dimension table mode resolution and surrogate key index, grouping aggregation calculation further converts the subgroup attributes into function dependency attributes; after the grouping aggregation calculation is completed, the function dependency attributes are directly mapped to a memory offset address of related dimension table records according to function dependency attribute values to complete the operation of extracting other related grouping attributes. By means of the method, the size of grouping attributes can be reduced, and the Hash grouping calculating efficiency is increased.
Owner:RENMIN UNIVERSITY OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com