Access control method for protecting access privacy of user in mobile value-added service system
A value-added service and access control technology, applied in the direction of public keys, security devices, electrical components, etc. of secure communication, which can solve the problem of inability to provide lightweight management methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
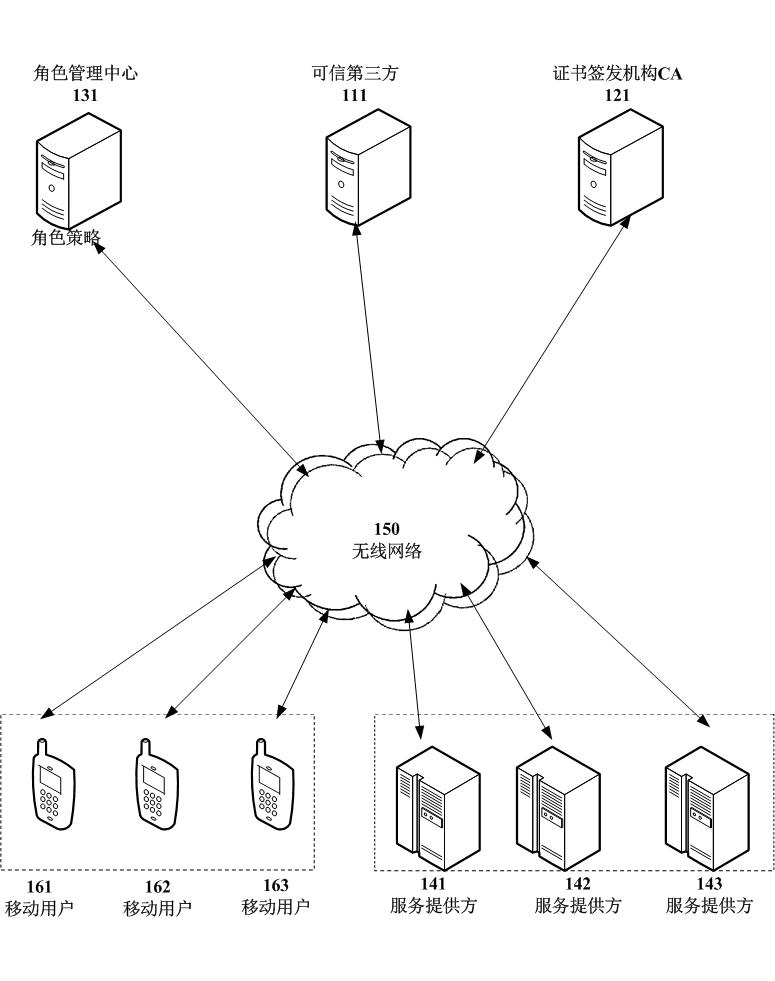
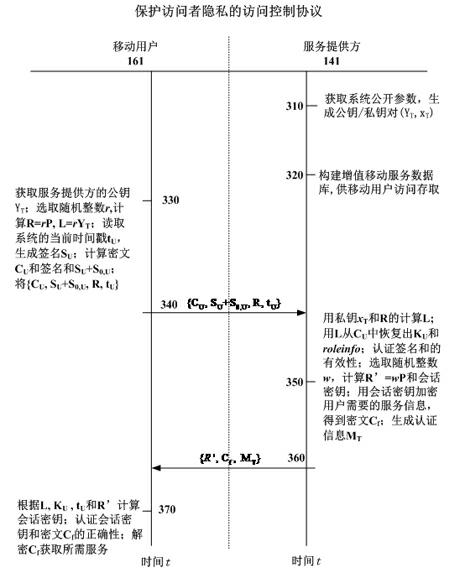
[0077] Such as figure 1 As shown, the system is composed of six types of entities: trusted third party 111 , certificate issuing authority server CA121 , role management center server 131 , service provider server 141 , wireless network 150 and mobile user equipment 161 . In a mobile value-added service environment in practical applications, in addition to multiple mobile user equipments 161, there may also be multiple service providers 141 and multiple role management centers 131. The trusted third party 111 is used to generate public parameters of the entire system. The certificate issuing authority server CA121 is used to generate public key / private key pairs of the role management central server 131, the service provider 141 and the mobile user equipment 161, and generate corresponding public key certificates. The role management center server 131 is used to perform proxy authorization on the proxy signature key of the mobile user. The authorization is based on the user r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com