Method and equipment for generating inextensible unidirectional proxy re-encryption key, and method and system for executing inextensible unidirectional proxy re-encryption
A non-extensible, one-way technology, used in transmission systems, public keys for secure communications, user identity/authority verification, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0091] In the following, the present invention will be described with reference to the accompanying drawings. In the following description, some specific embodiments are only for the purpose of description, and should not be construed as limiting the present invention in any way, but are only examples of the present invention. Conventional structures or constructions will be omitted when they may obscure the understanding of the present invention.
[0092] [Detailed scene description]
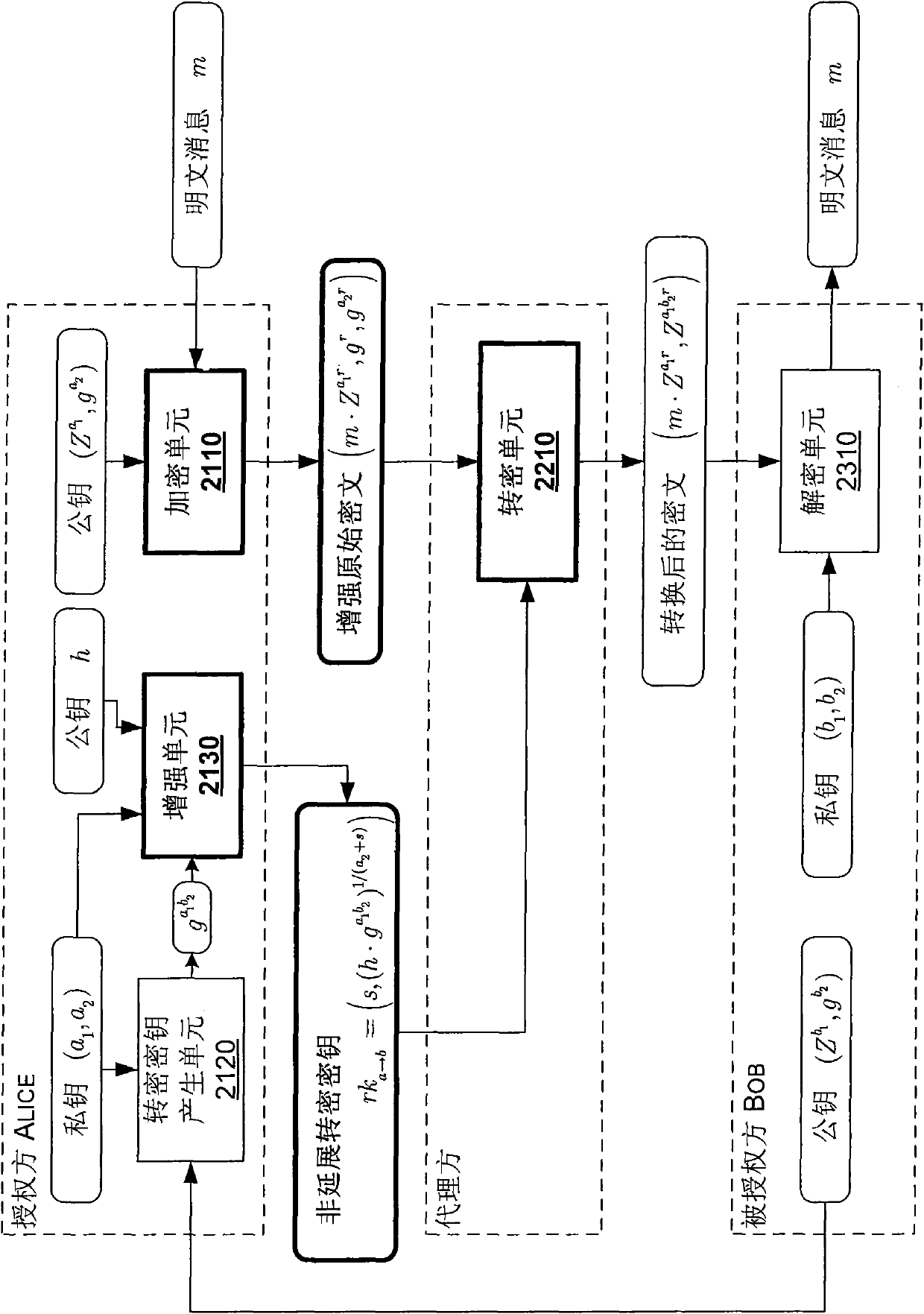
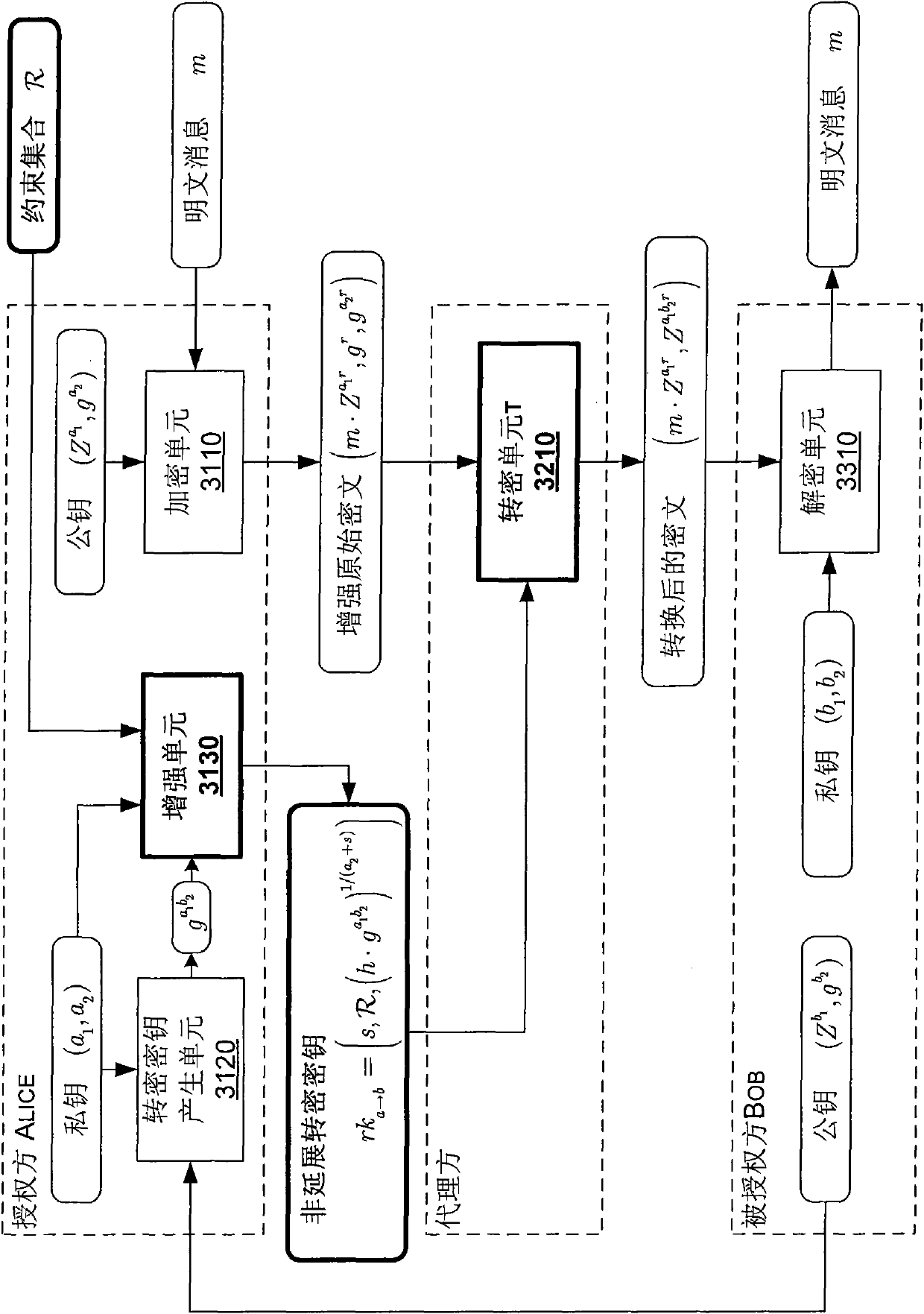
[0093] In the following, the non-extensible one-way proxy encryption (NRE) scheme according to the present invention is described in detail in comparison with references [4] and [5] which are regarded as the closest prior art of the present invention.
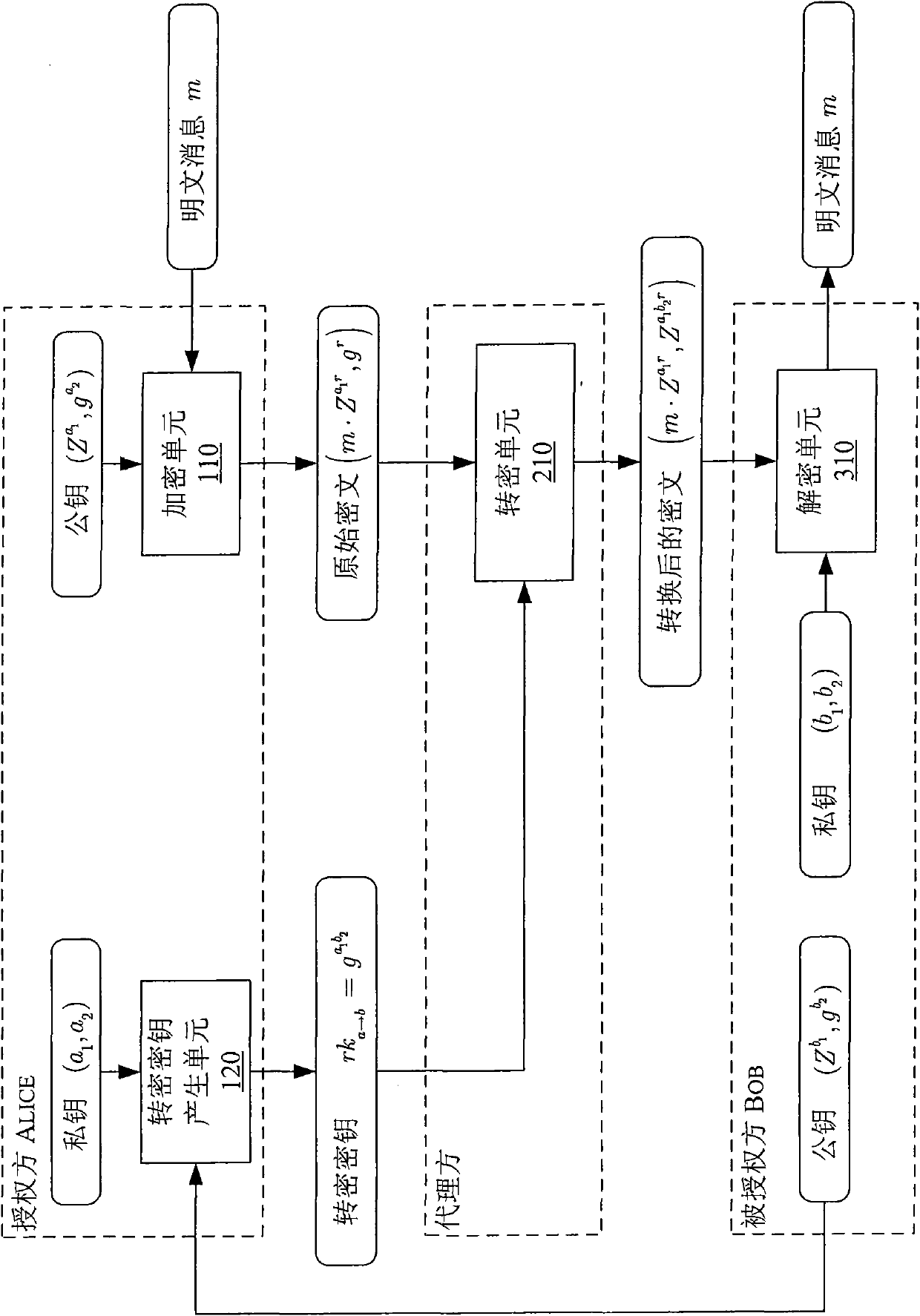
[0094] figure 1 is a schematic block diagram showing the various units operating in the Third Attempt of references [4] and [5]. refer to figure 1 , each unit of authorizing party Alice, agent and authorized party Bob is described as fol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com