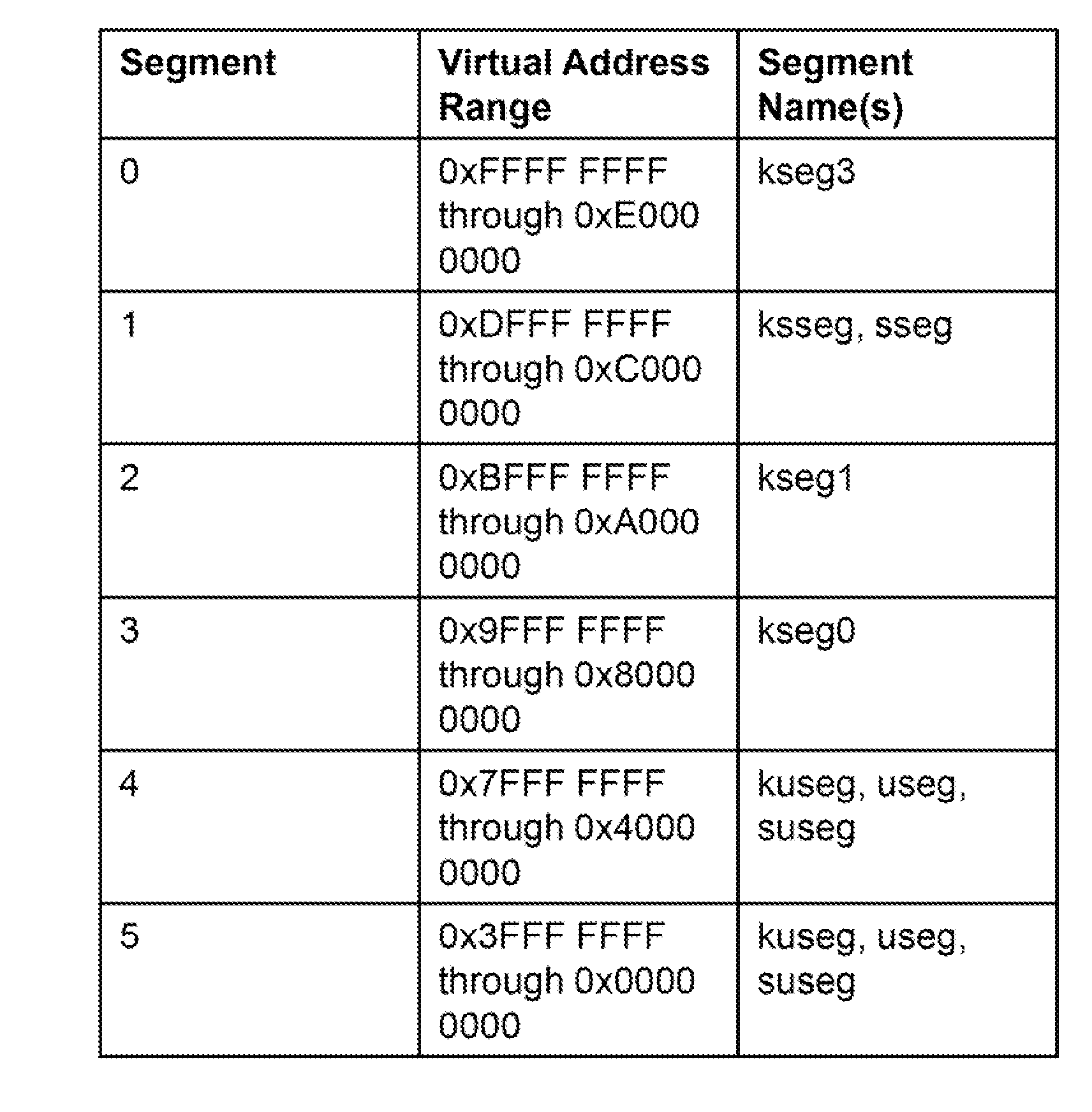
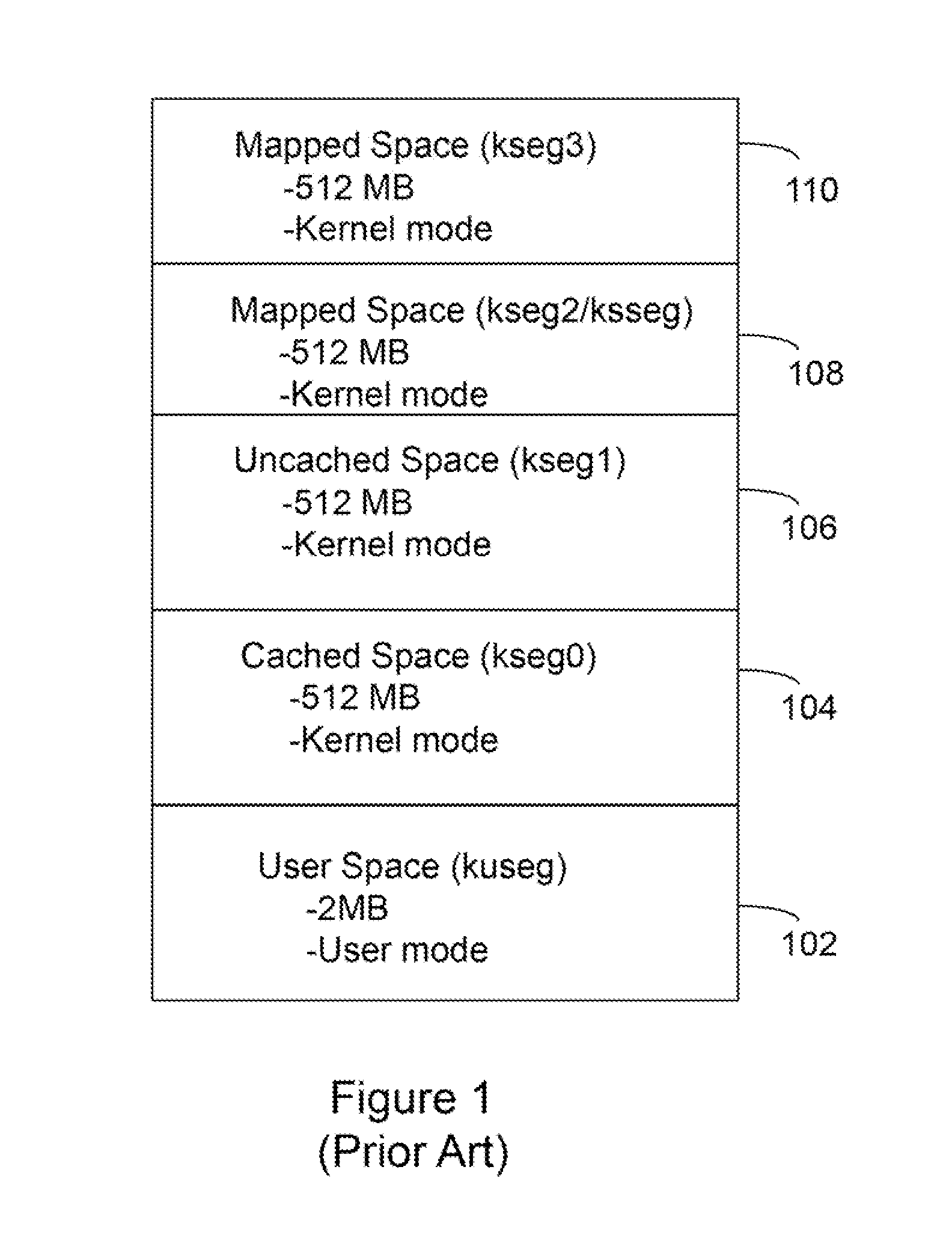
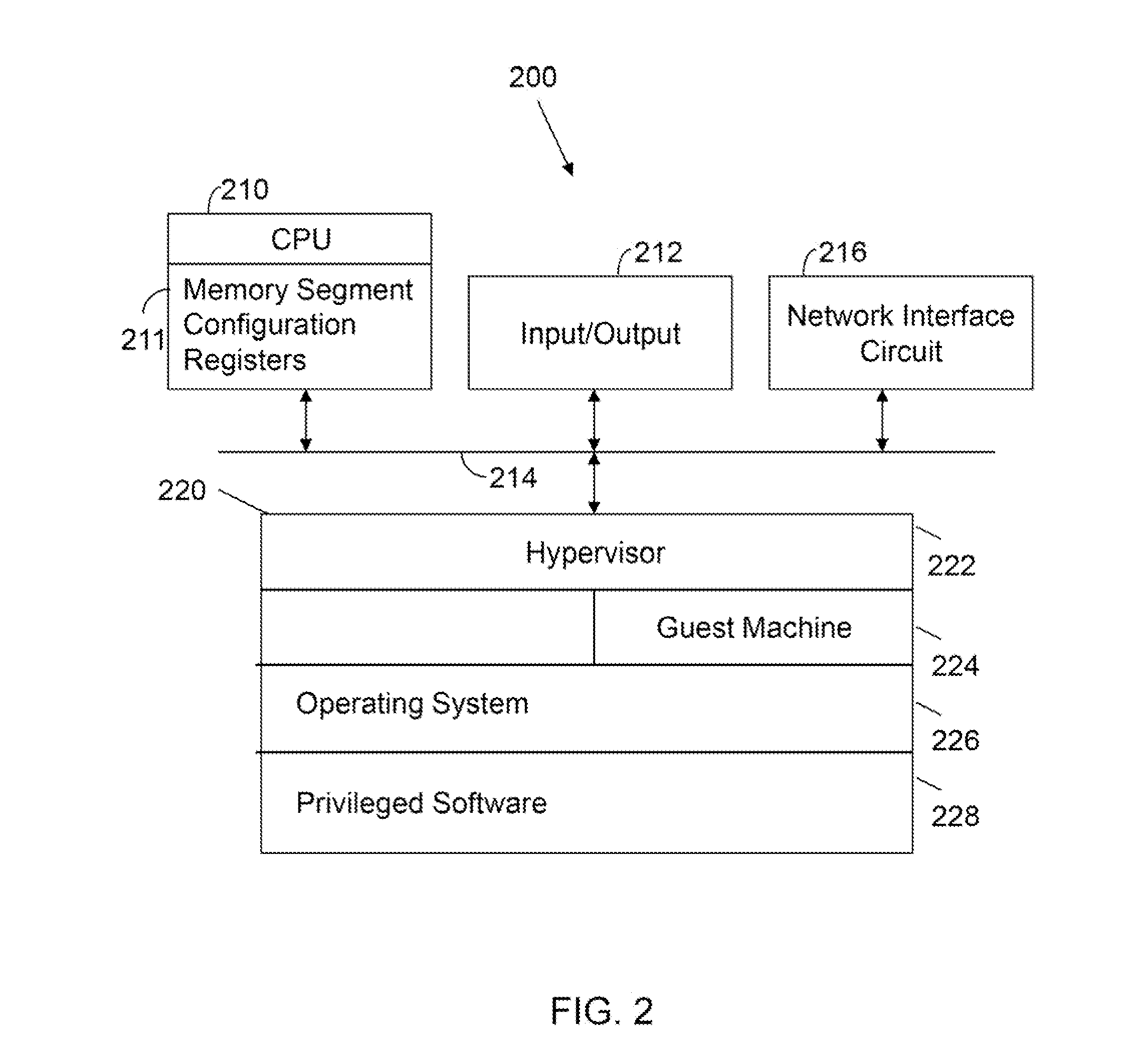
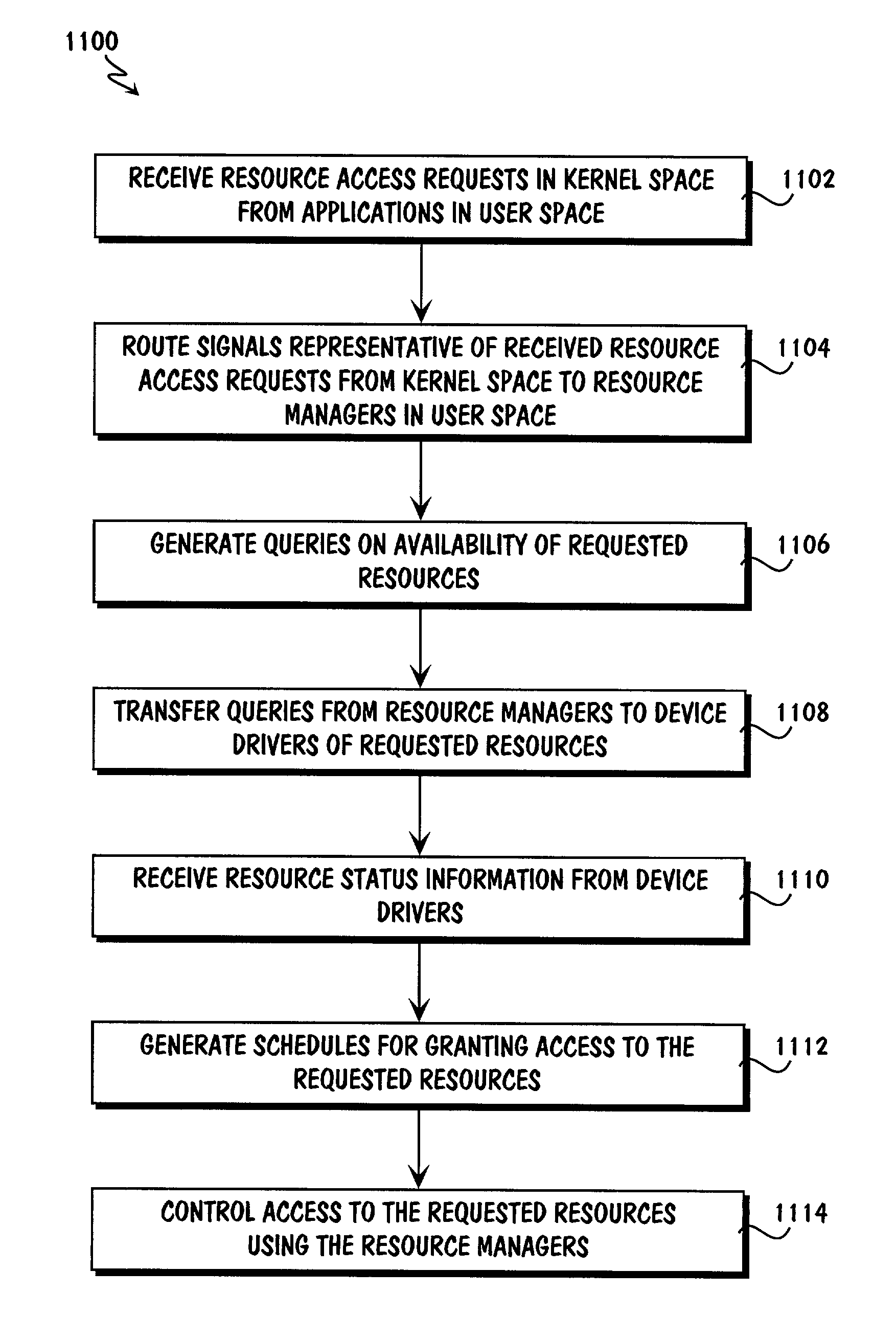
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
768 results about "User space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
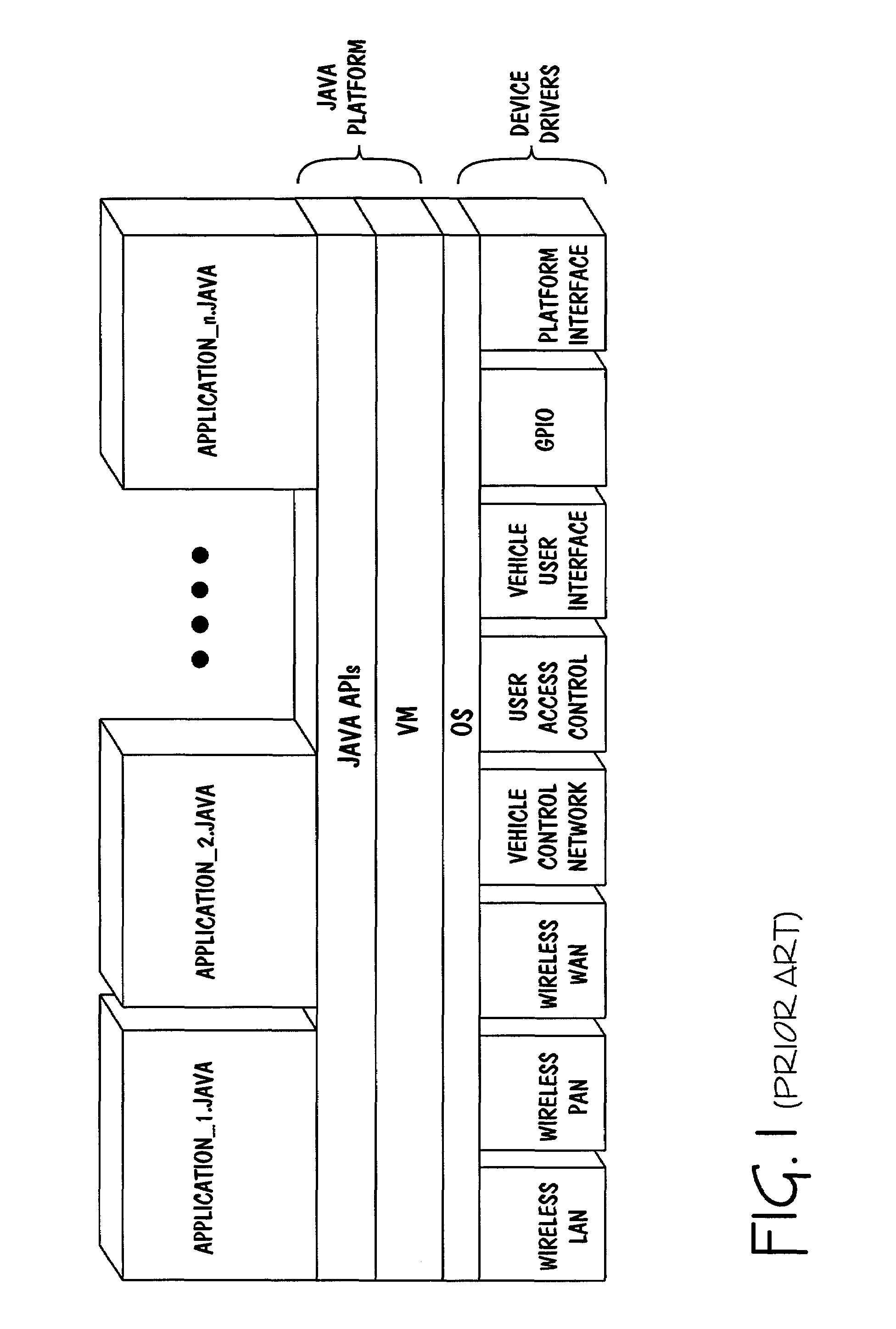
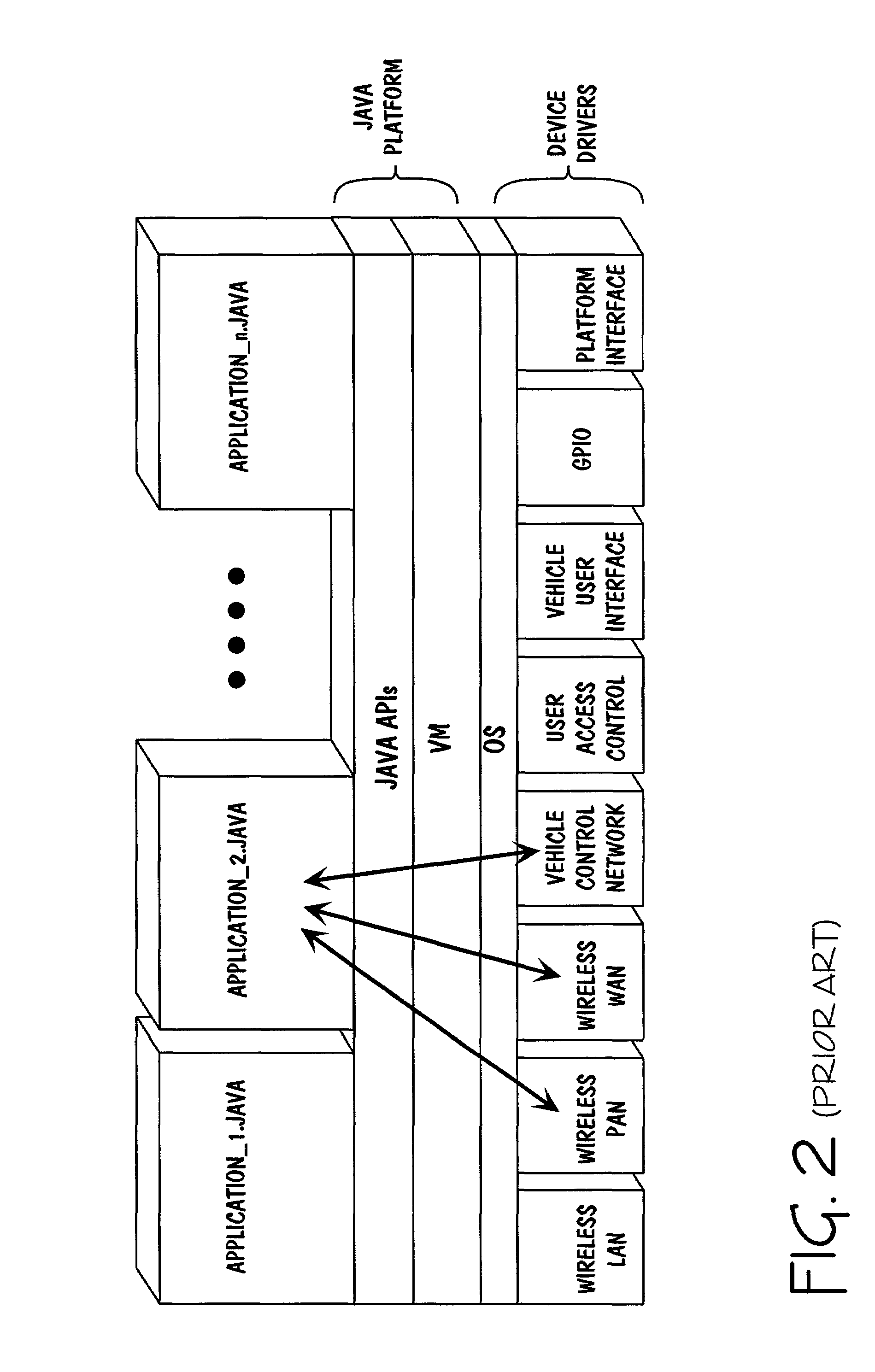
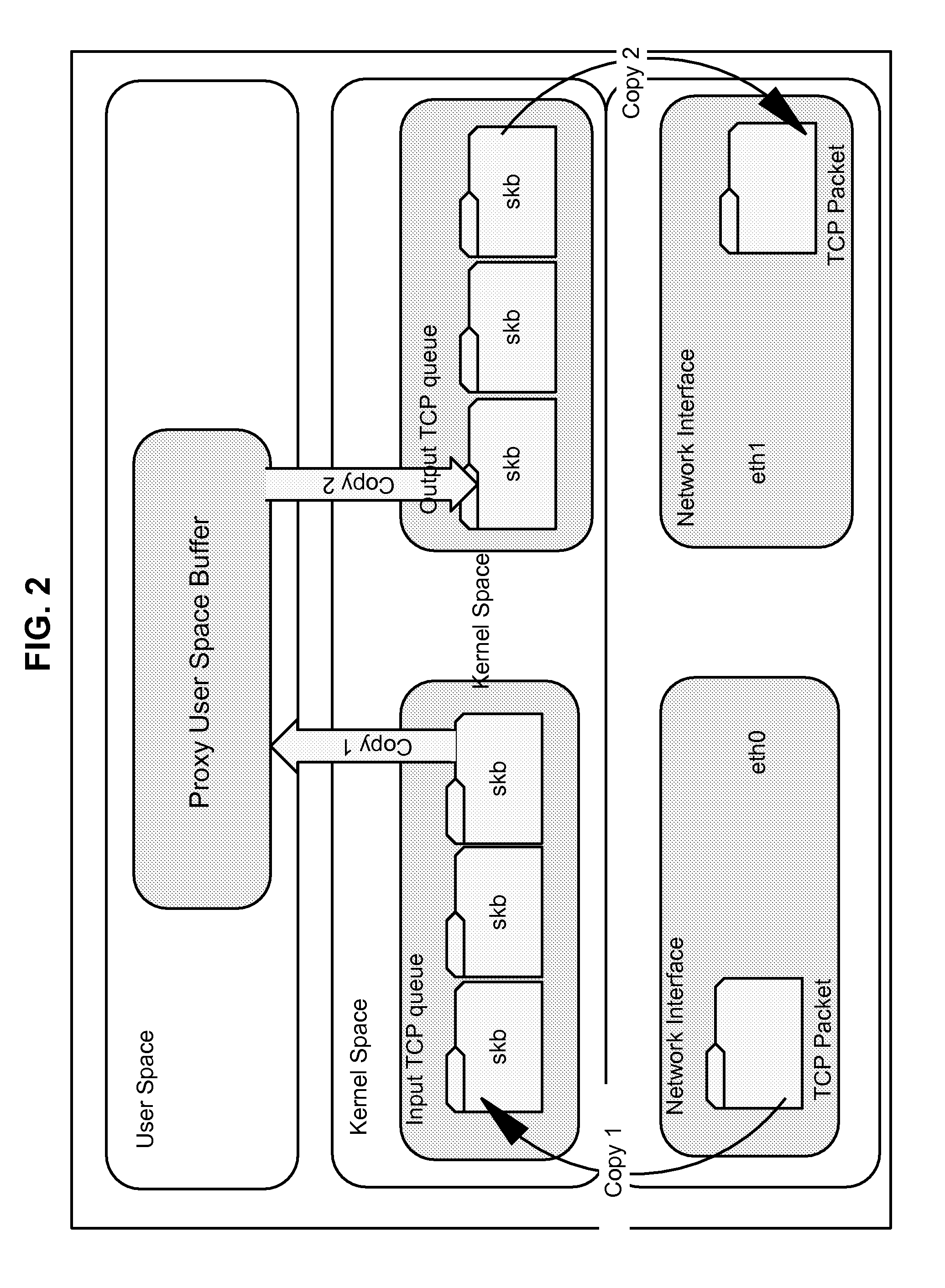
A modern computer operating system usually segregates virtual memory into kernel space and user space. Primarily, this separation serves to provide memory protection and hardware protection from malicious or errant software behaviour.
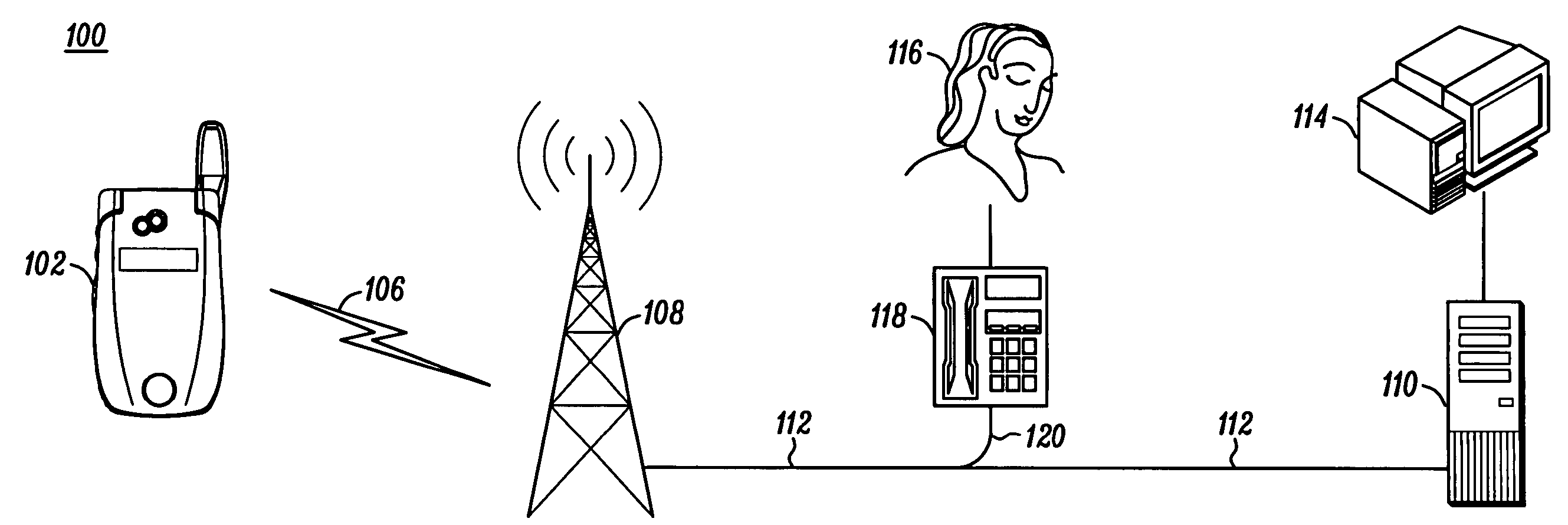
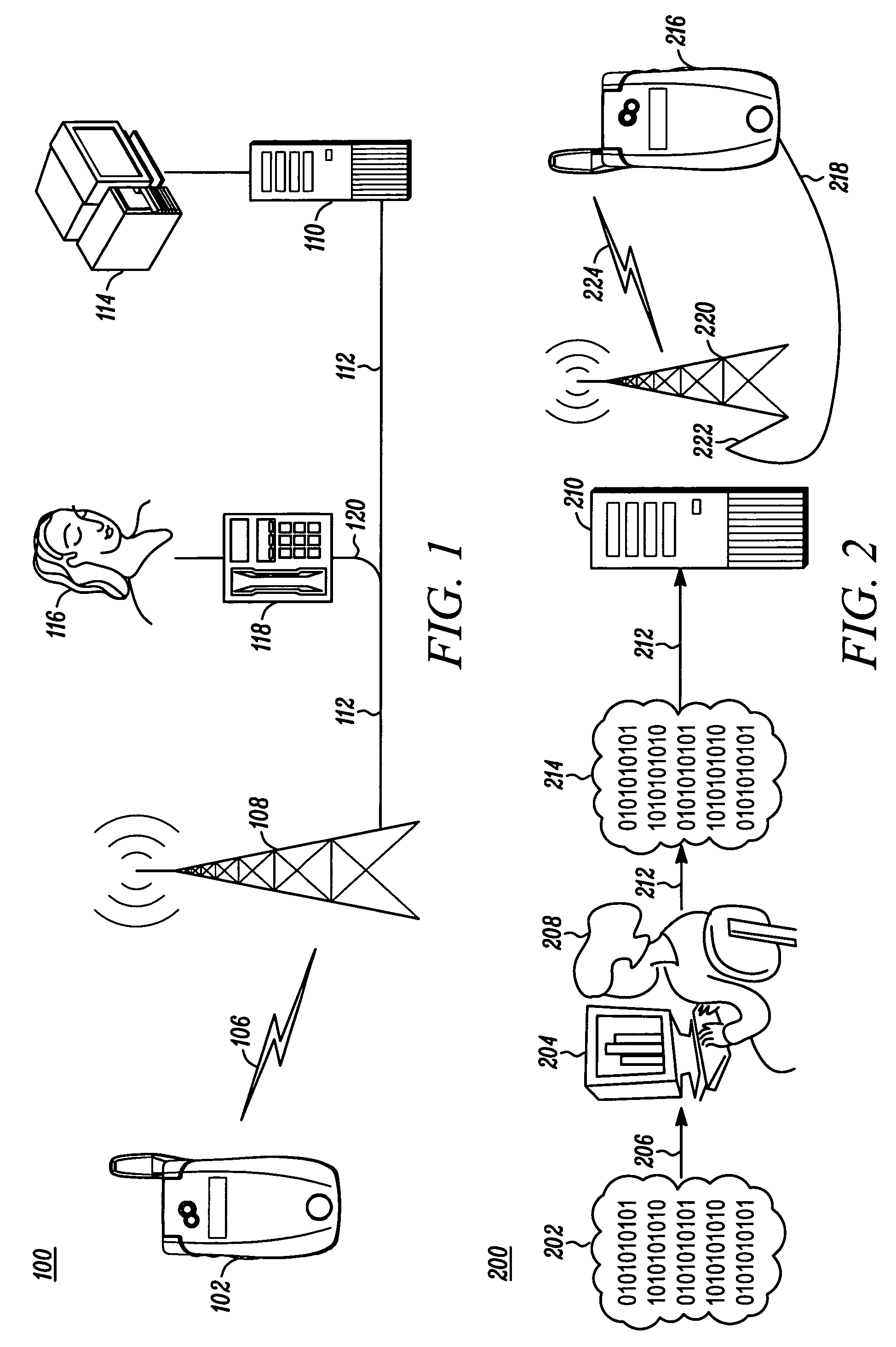
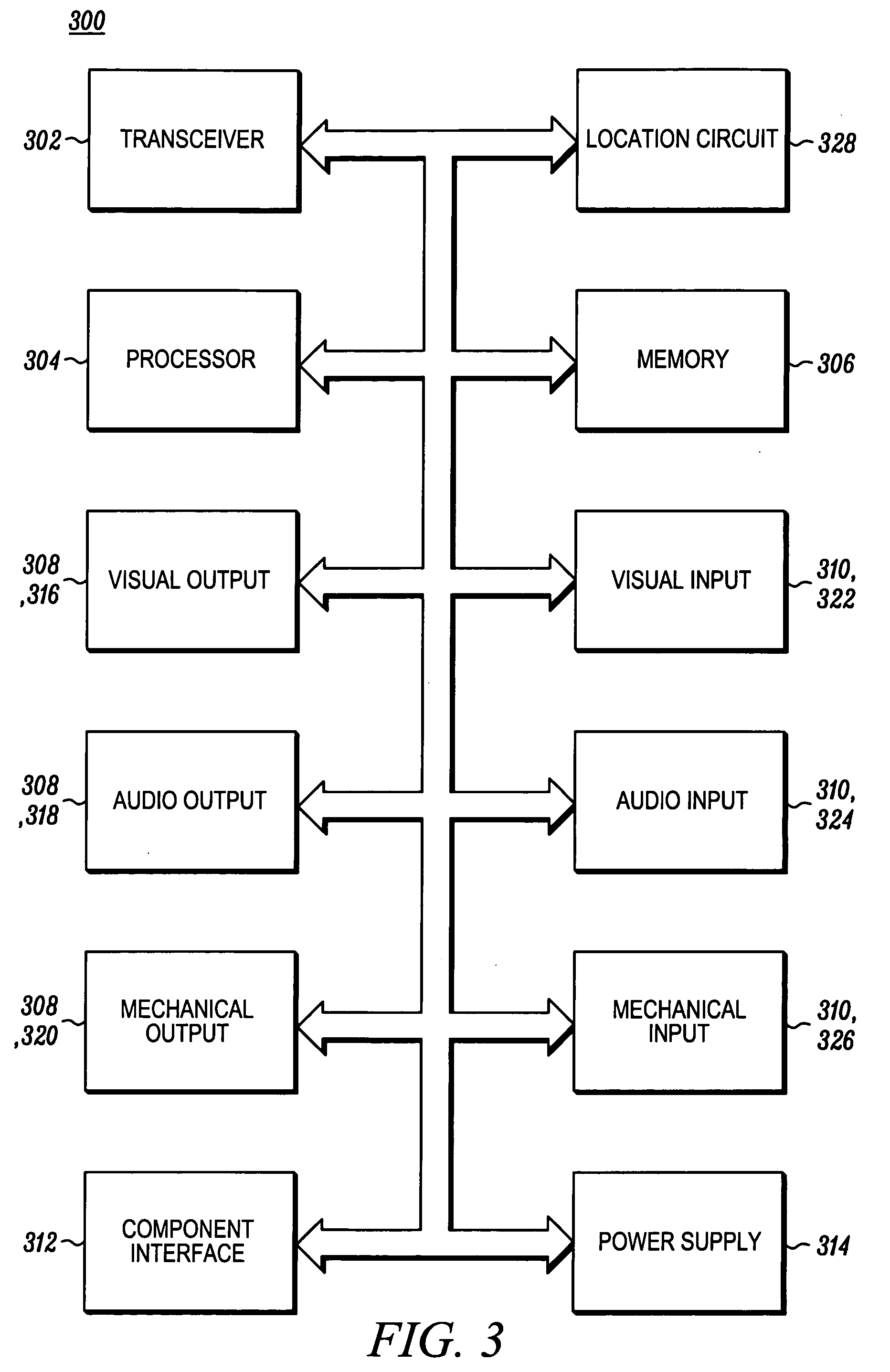
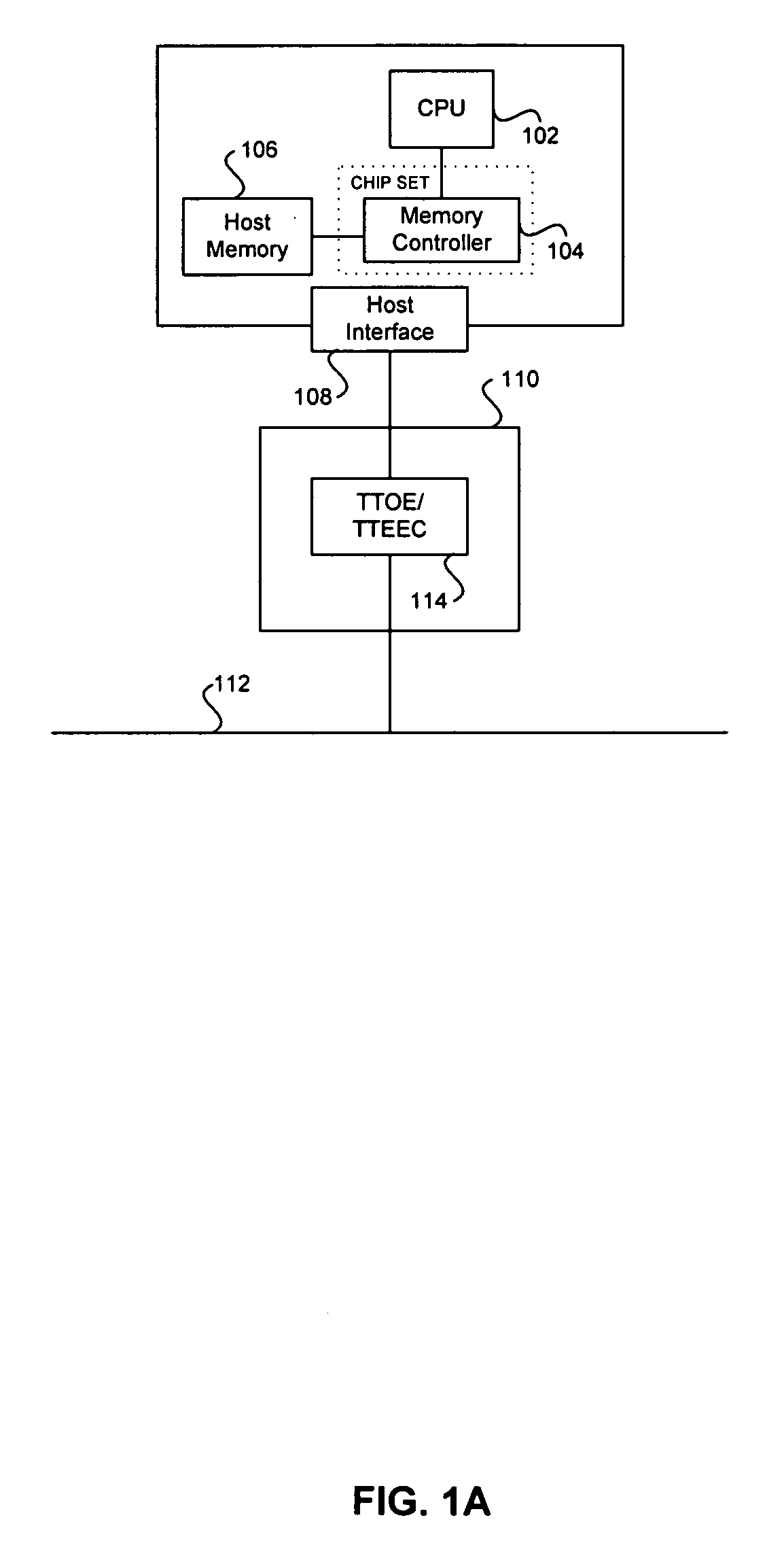
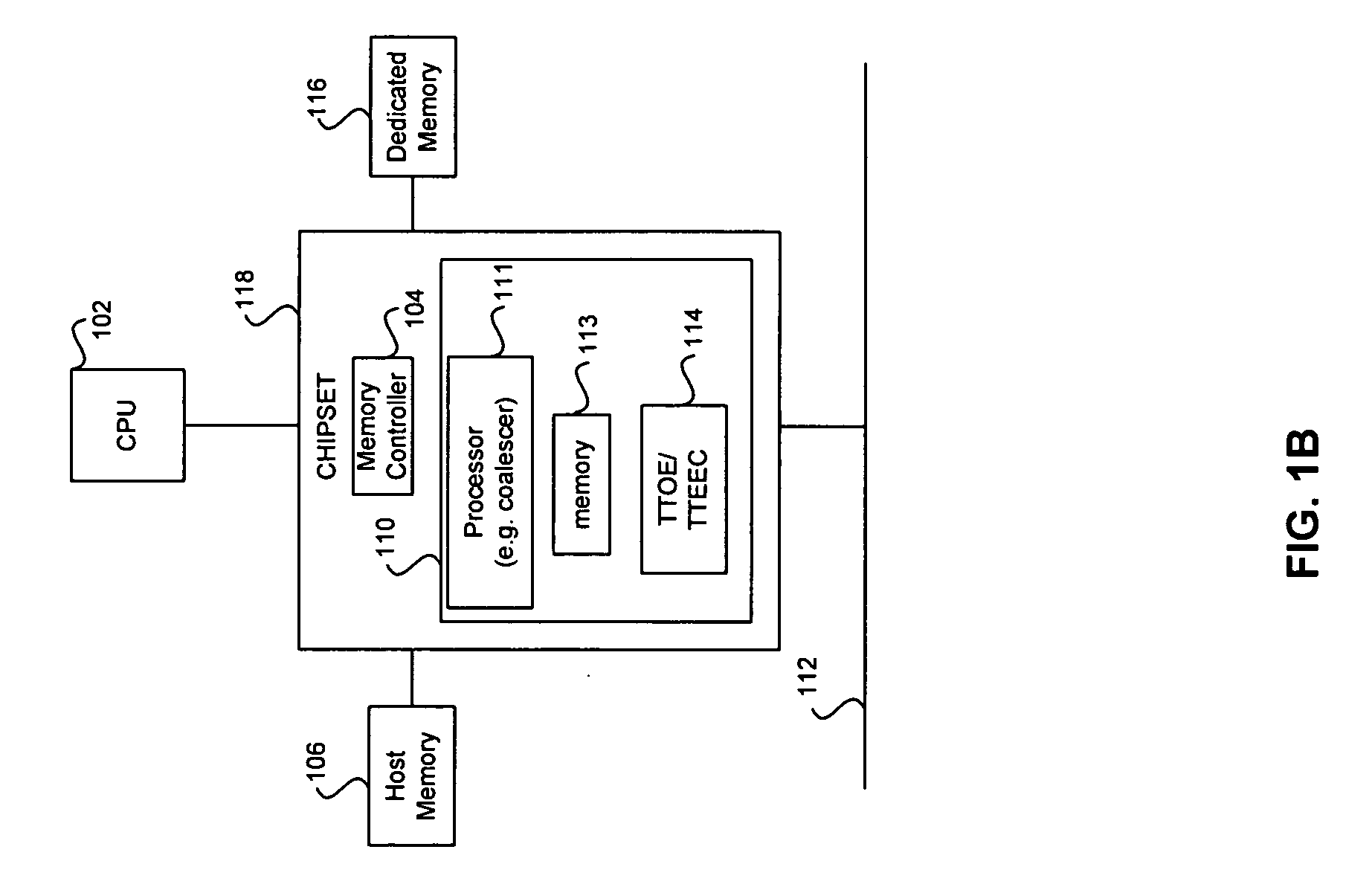
Processor with Kernel Mode Access to User Space Virtual Addresses
ActiveUS20130132702A1Enhanced kernel mode memory capacityIncrease memory capacityMemory adressing/allocation/relocationUnauthorized memory use protectionMemory addressParallel computing
A computer includes a memory and a processor connected to the memory. The processor includes memory segment configuration registers to store defined memory address segments and defined memory address segment attributes such that the processor operates in accordance with the defined memory address segments and defined memory address segment attributes to allow kernel mode access to user space virtual addresses for enhanced kernel mode memory capacity.
Owner:MIPS TECH INC
Open platform architecture for shared resource access management
An open platform architecture and methods for shared resource access management are provided. A redirection module in kernel space receives requests for access to resources from applications in user space. The redirection module routes signals representative of the received requests to a device driver interface in user space. Components of the device driver interface include resource management modules and device drivers that correspond to available resources. The resource management modules generate queries to the device drivers regarding availability of the requested resources. Upon receipt of resource status information from the device drivers, components of the device driver interface generate schedules for granting access to the requested resources. Further, the device driver interface components control access to the resources in accordance with the generated schedules including issuing responses to the requesting applications and the device drivers of the requested resources.
Owner:WI LAN INC
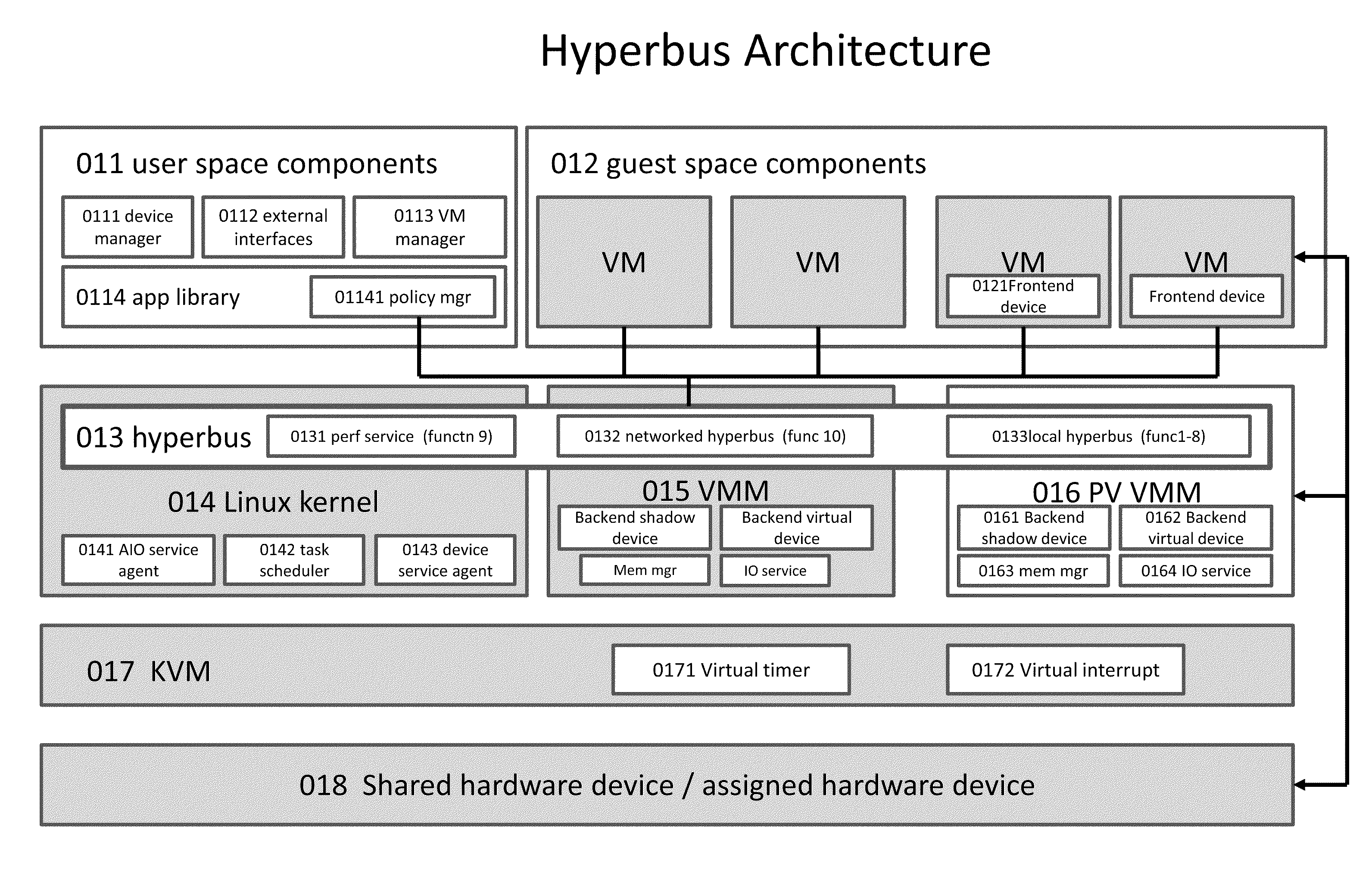
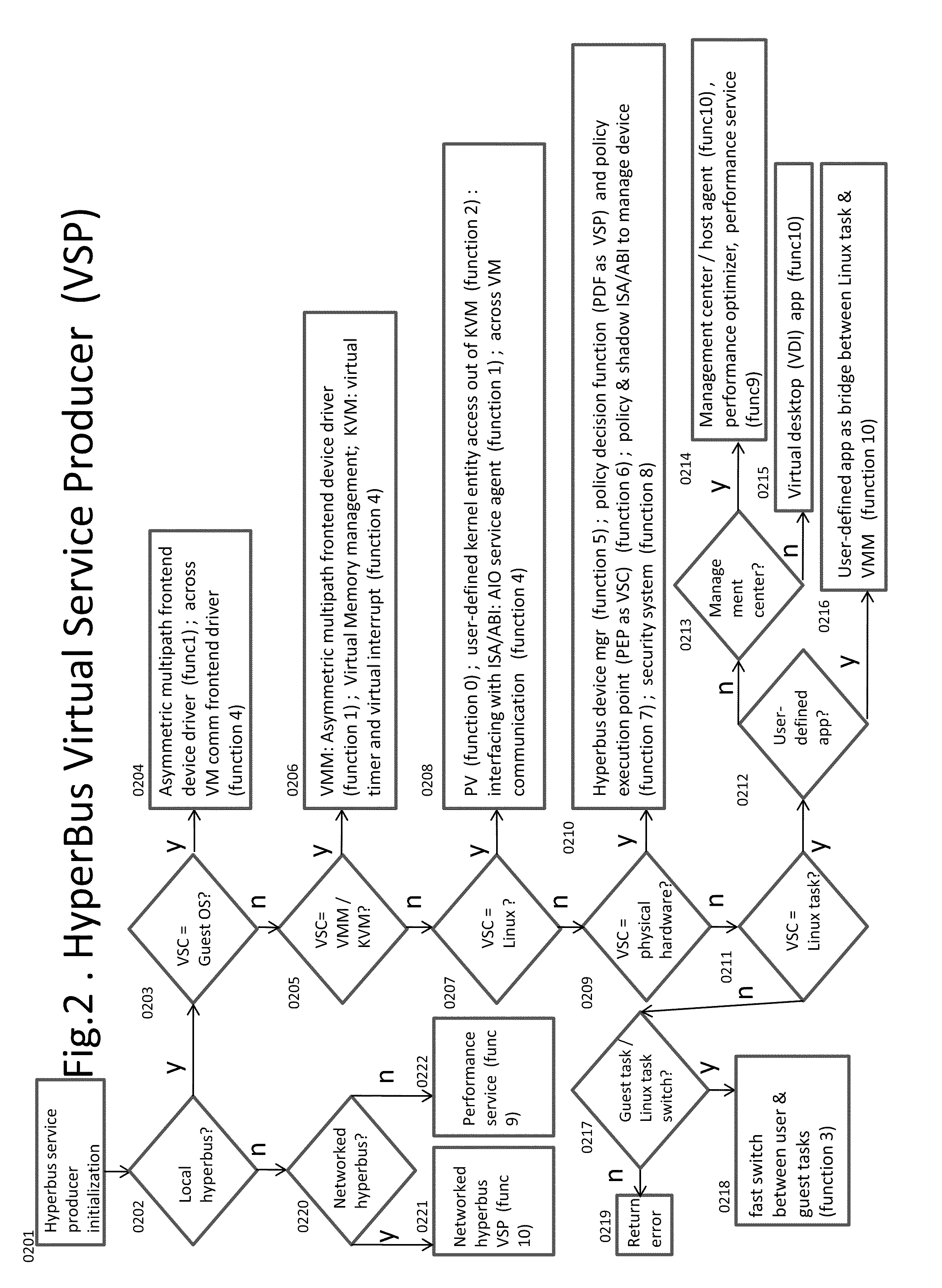
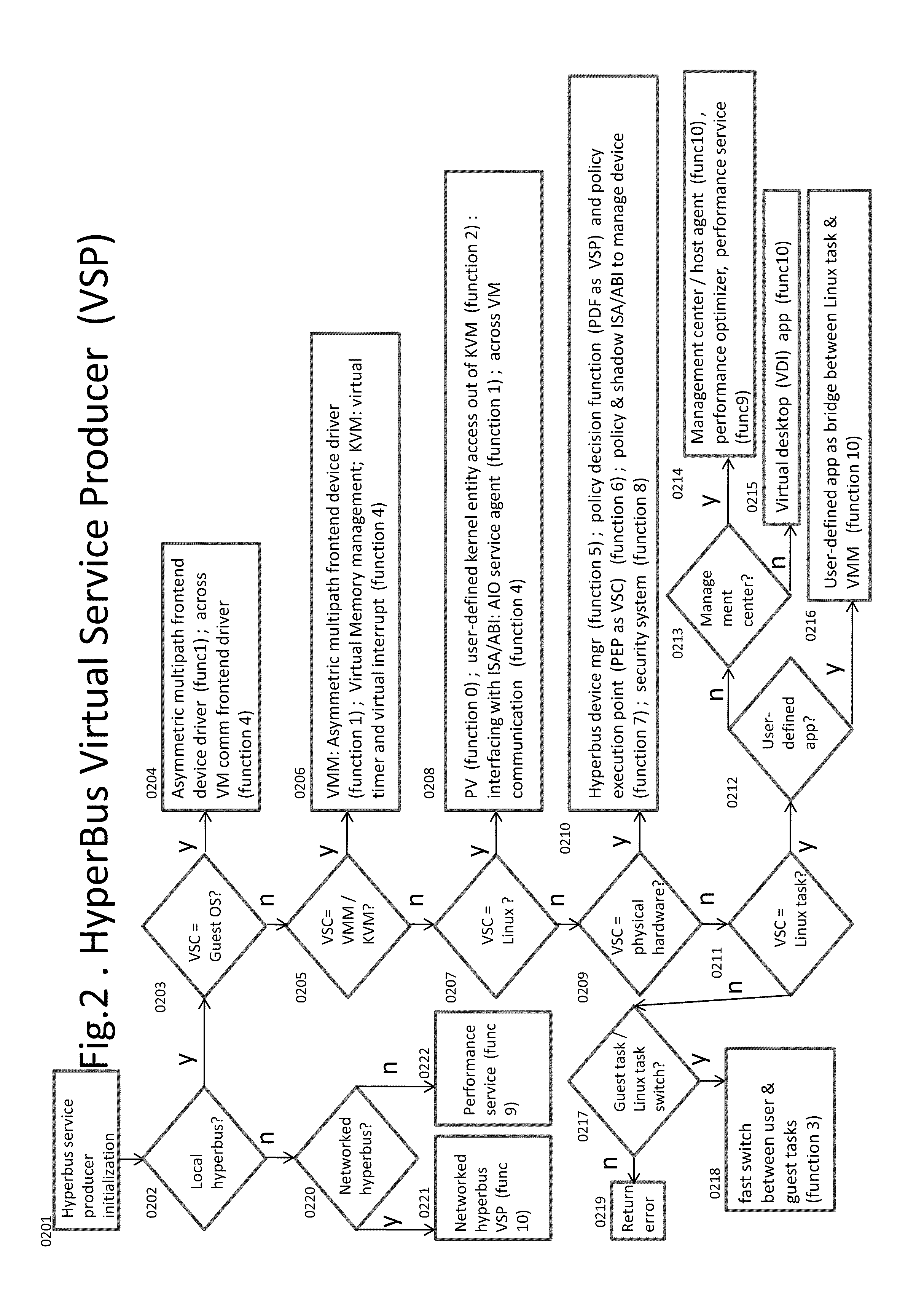
Kernel Bus System to Build Virtual Machine Monitor and the Performance Service Framework and Method Therefor
InactiveUS20110296411A1Fast deliveryImprove performanceSoftware simulation/interpretation/emulationMemory systemsVirtualizationSystem configuration
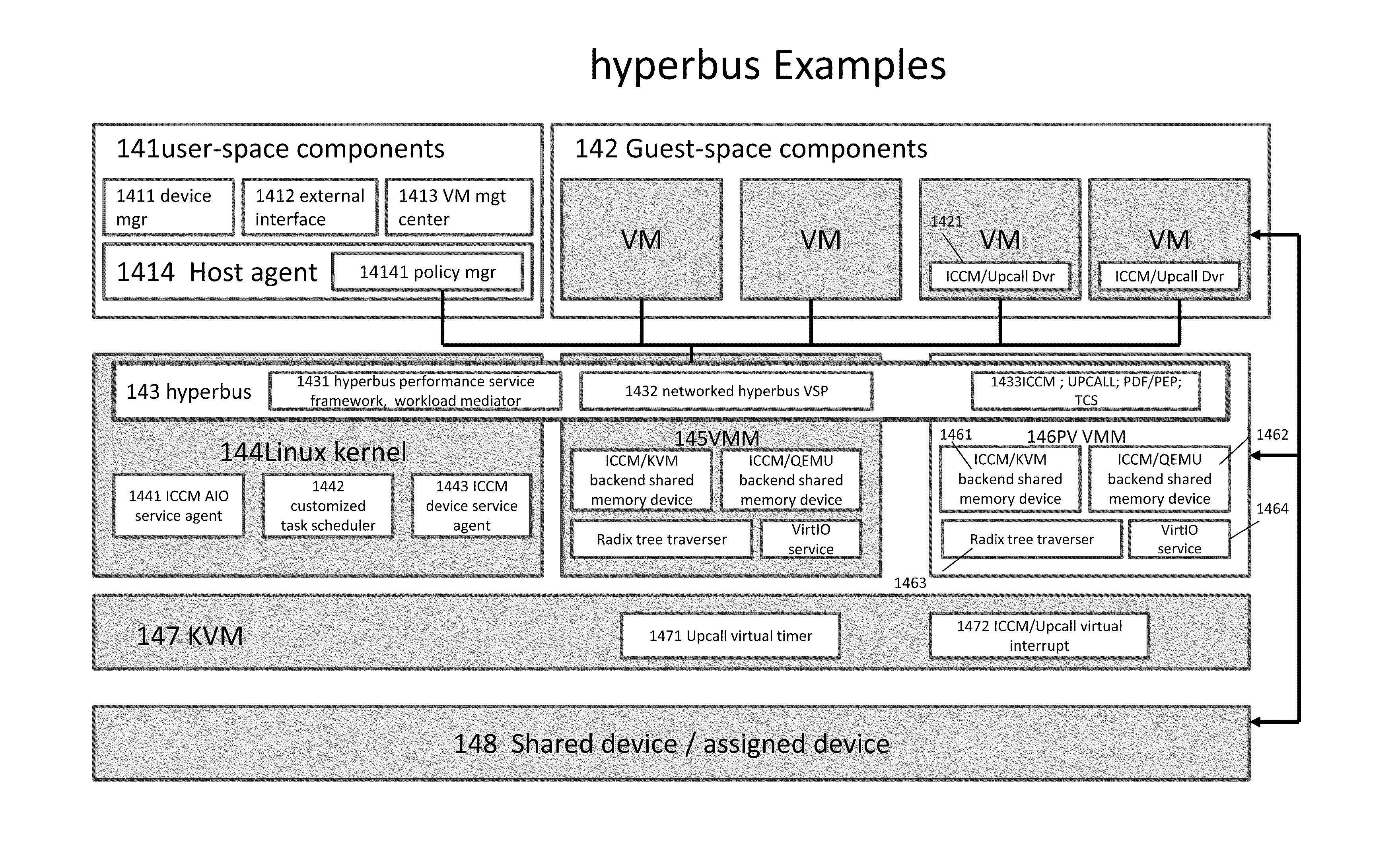
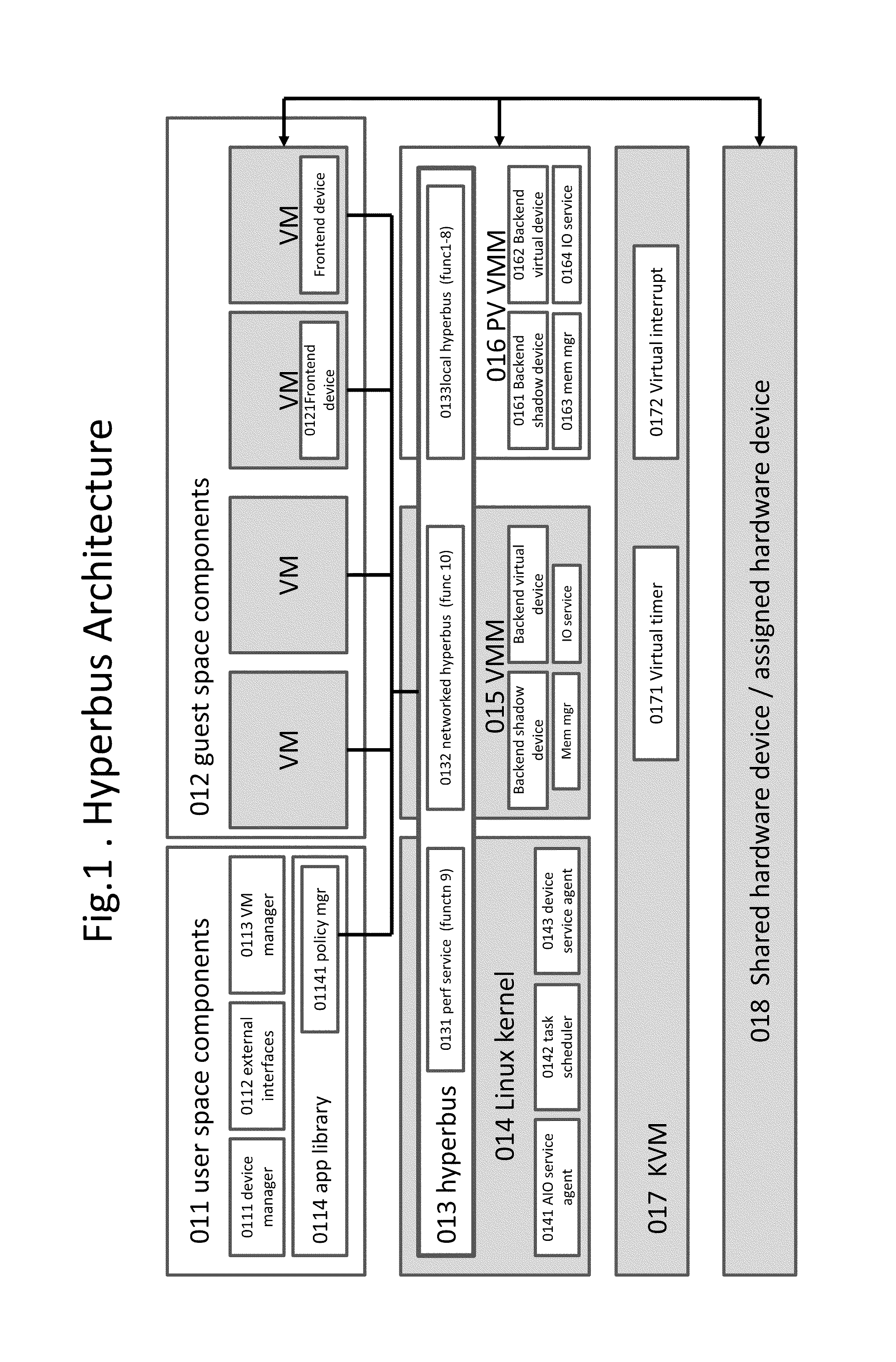
Some embodiments concern a kernel bus system for building at least one virtual machine monitor. The kernel bus system is based on kernel-based virtual machine. The kernel bus system is configured to run on a host computer. The host computer comprising one or more processors, one or more hardware devices, and memory. The kernel bus system can include: (a) a hyperbus; (b) one or more user space components; (c) one or more guest space components configured to interact with the one or more user space components via the hyperbus; (d) one or more VMM components having one or more frontend devices configure to perform I / O operations with the one or more hardware devices of the host computer using a zero-copy method or non-pass-thru method; (e) one or more para-virtualization components having (1) a virtual interrupt configured to use one or more processor instructions to swap the one or more processors of the host computer between a kernel space and a guest space; and (2) a virtual I / O driver configured to enable synchronous I / O signaling, asynchronous I / O signaling and payload delivery, and pass-through delivery independent an QEMU emulation; and (f) one or more KVM components. The hyperbus, the one or more user space components, the one or more guest space components, the one or more VMM components, the one or more para-virtualization components, and the one or more KVM components are configured to run on the one or more processors of the host computer. Other embodiments are disclosed.
Owner:TRANSOFT
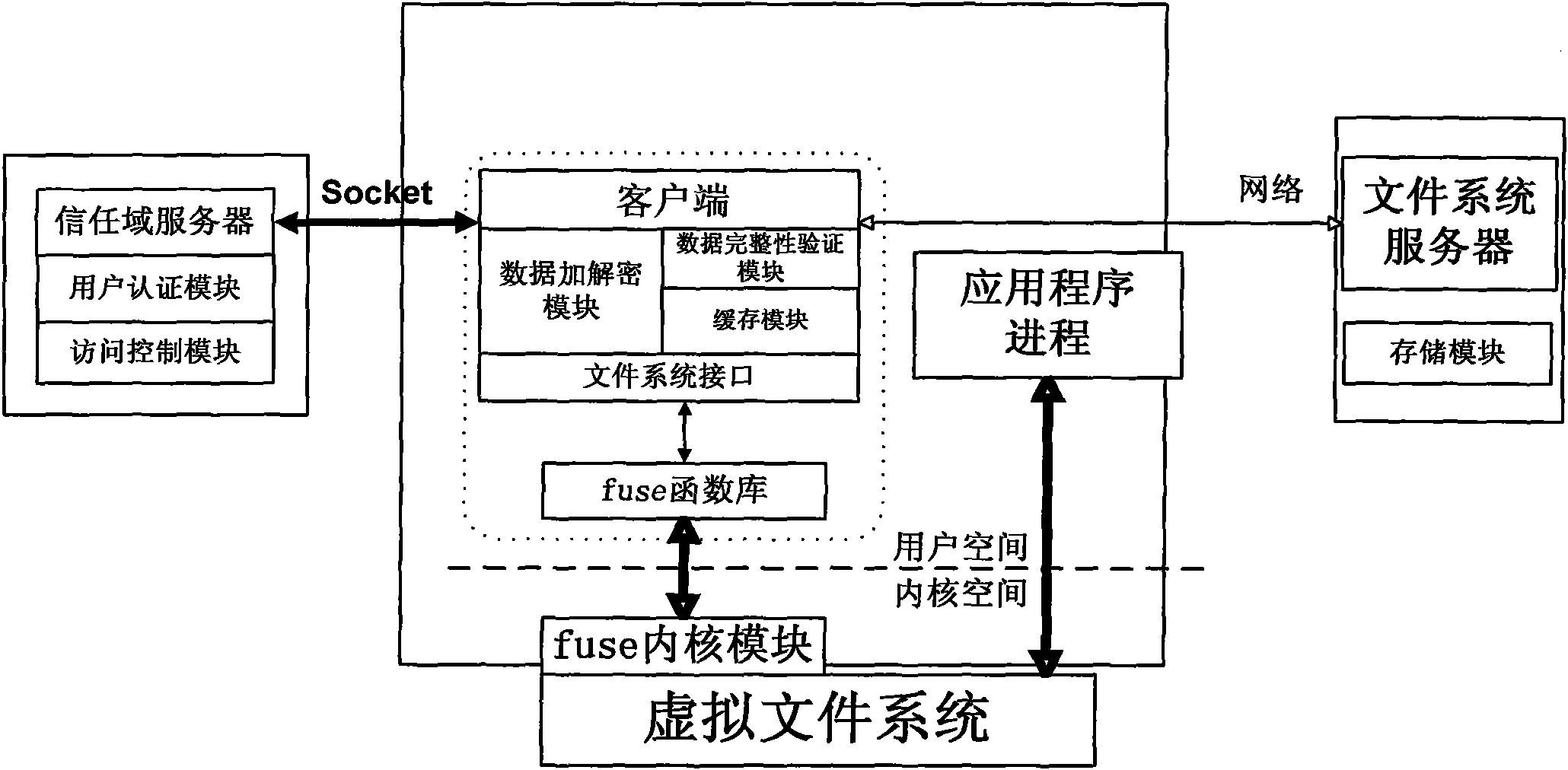
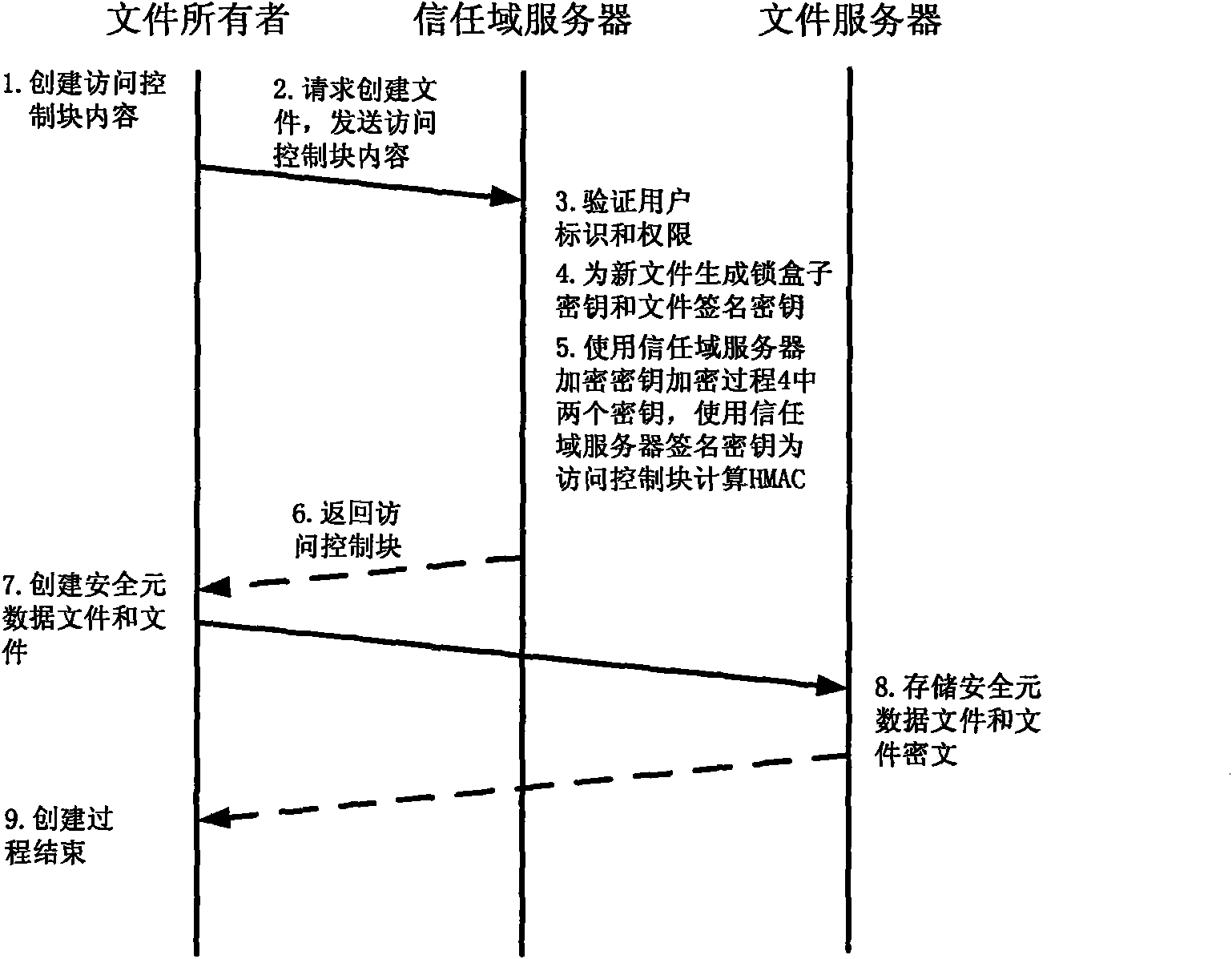
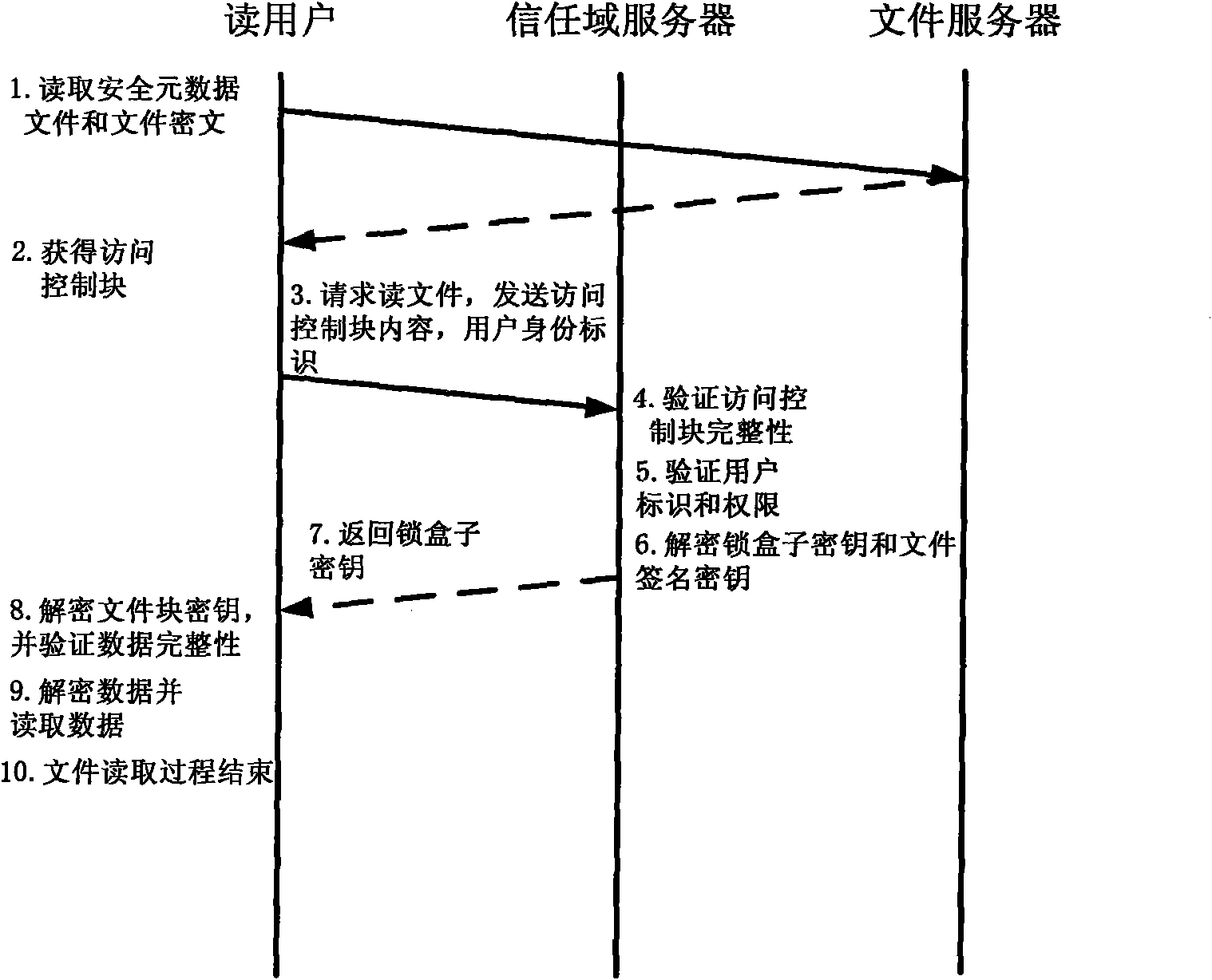
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
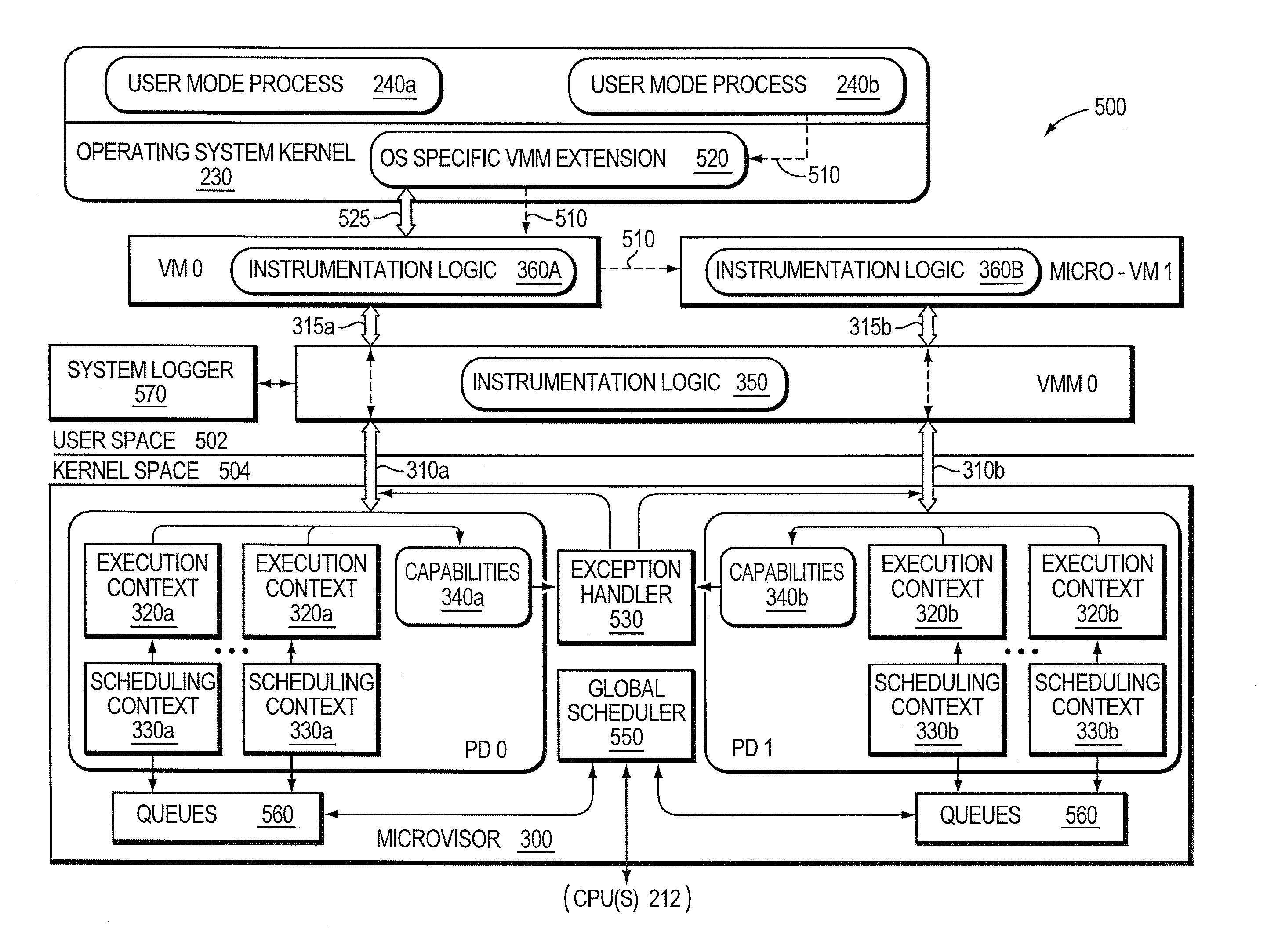
Micro-virtualization architecture for threat-aware microvisor deployment in a node of a network environment
ActiveUS9292686B2Digital data protectionPlatform integrity maintainanceVirtualizationOperational system
A micro-virtualization architecture deploys a threat-aware microvisor as a module of a virtualization system configured to facilitate real-time security analysis, including exploit detection and threat intelligence, of operating system processes executing in a memory of a node in a network environment. The micro-virtualization architecture organizes the memory as a user space and kernel space, wherein the microvisor executes in the kernel space of the architecture, while the operating system processes, an operating system kernel, a virtual machine monitor (VMM) and its spawned virtual machines (VMs) execute in the user space. Notably, the microvisor executes at the highest privilege level of a central processing unit of the node to virtualize access to kernel resources. The operating system kernel executes under control of the microvisor at a privilege level lower than a highest privilege level of the microvisor. The VMM and its spawned VMs execute at the highest privilege level of the microvisor.
Owner:MANDIANT +1
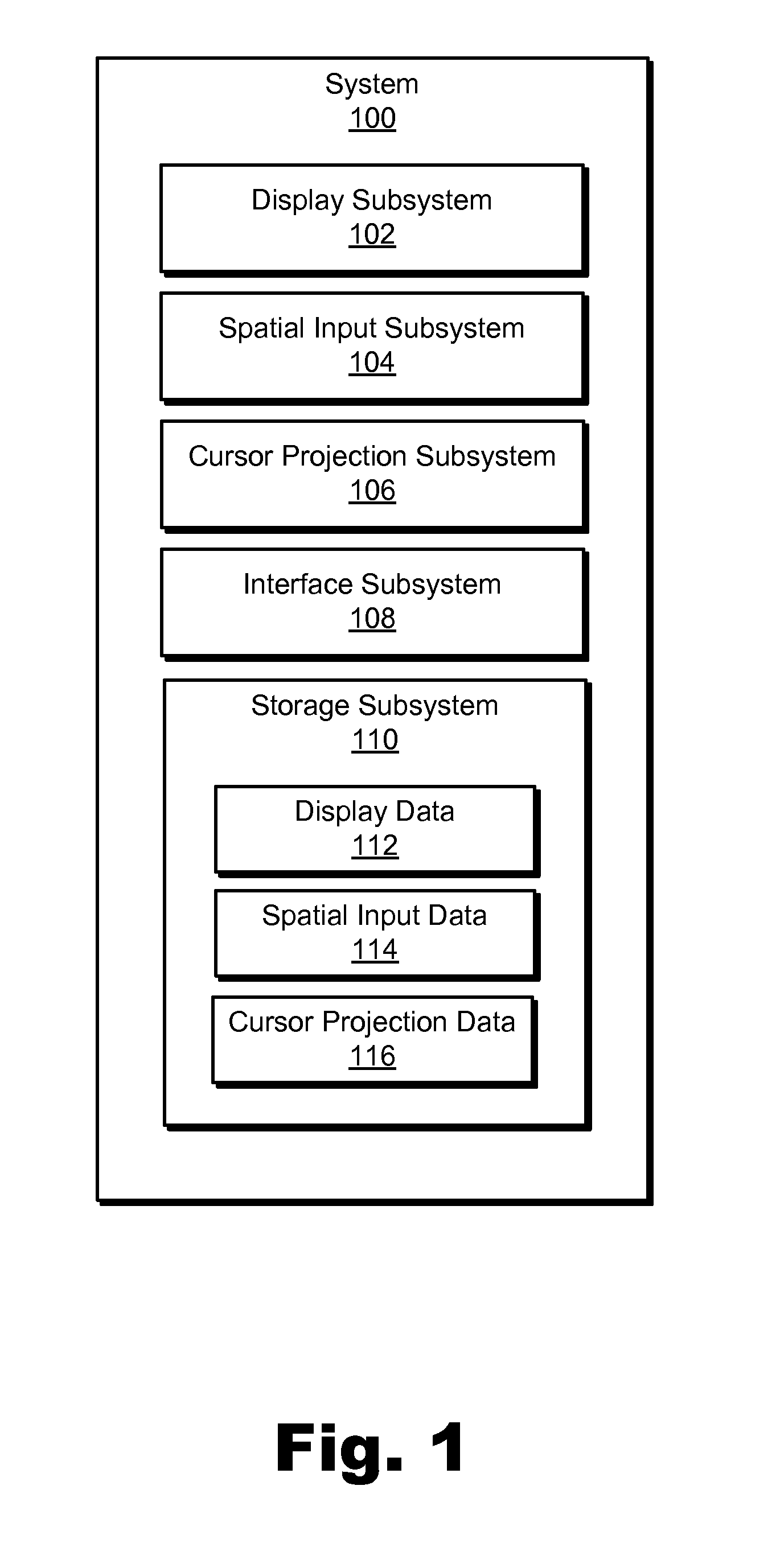
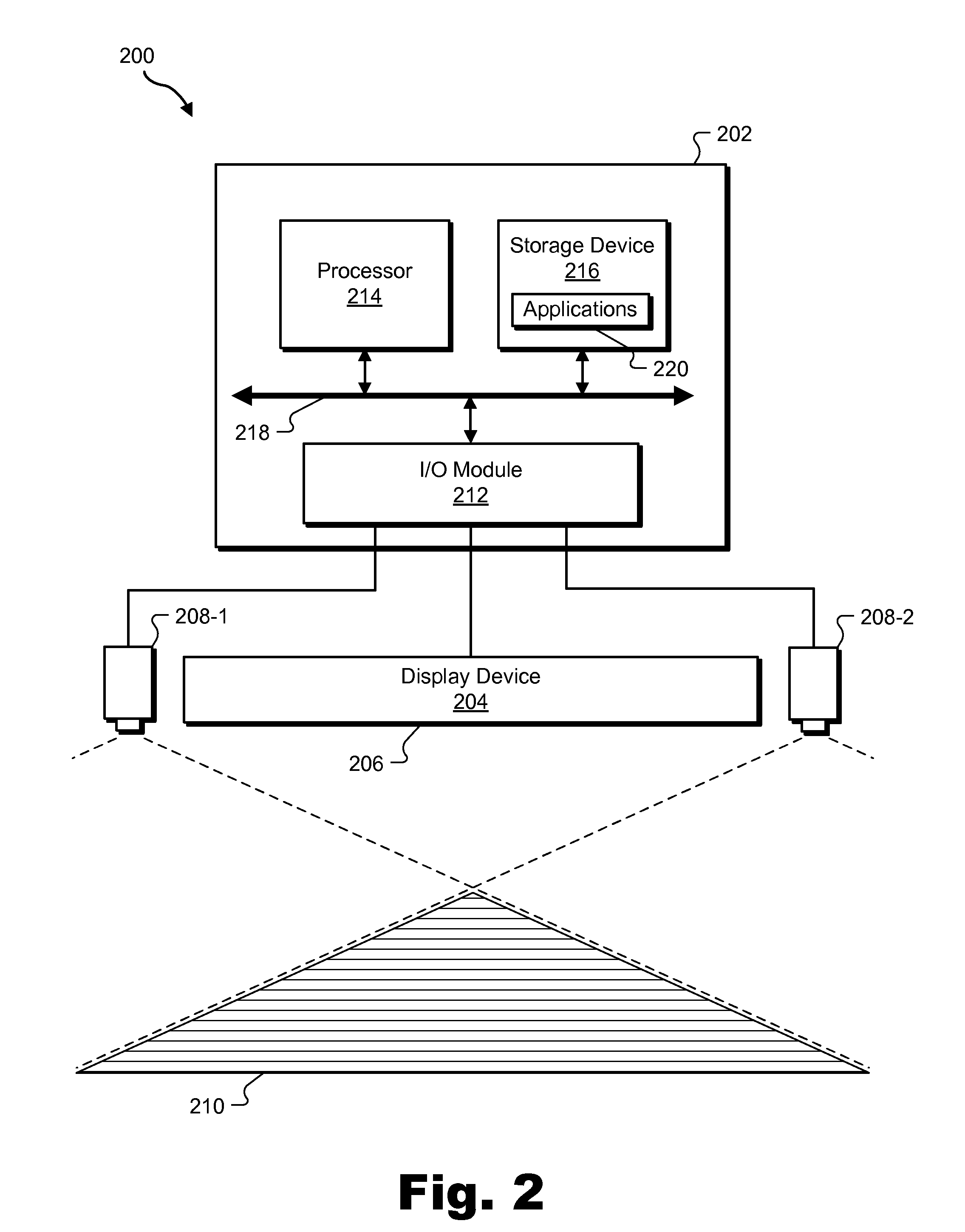
Spatial-input-based cursor projection systems and methods
ActiveUS20110267265A1Cathode-ray tube indicatorsInput/output processes for data processingPattern recognitionComputer graphics (images)
Exemplary spatial-input-based cursor projection systems and methods are disclosed herein. An exemplary method includes a cursor projection system detecting spatial input provided by a user within a physical user space associated with a display screen, determining that the spatial input is associated with a request for cursor projection, and mapping the spatial input to at least one cursor position on the display screen based on at least one of a plane projection heuristic and a vector projection heuristic. Corresponding systems and methods are also disclosed.
Owner:VERIZON PATENT & LICENSING INC
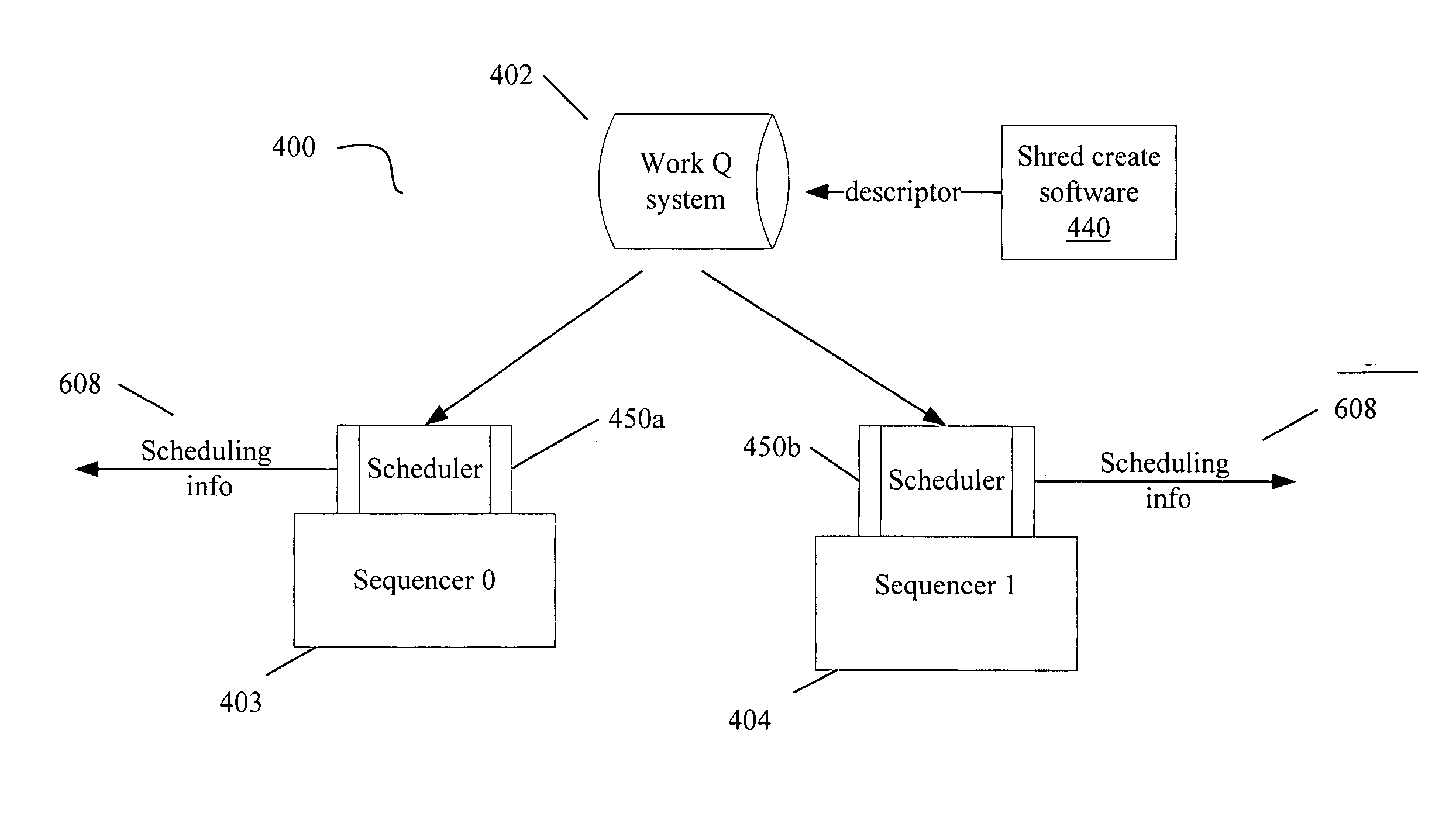
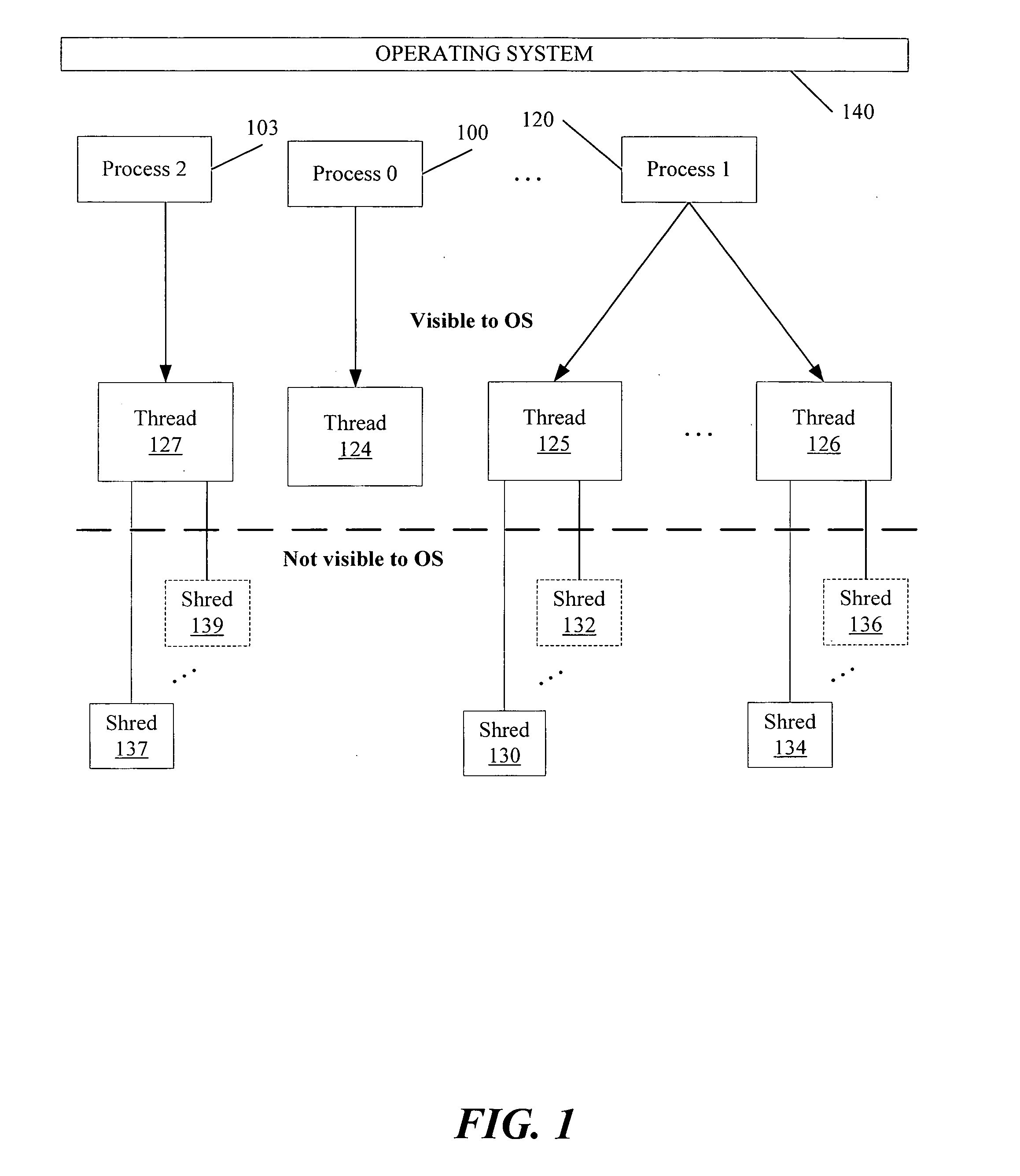
Scheduling optimizations for user-level threads
InactiveUS20070074217A1Multiprogramming arrangementsMemory systemsOperational systemThread scheduling
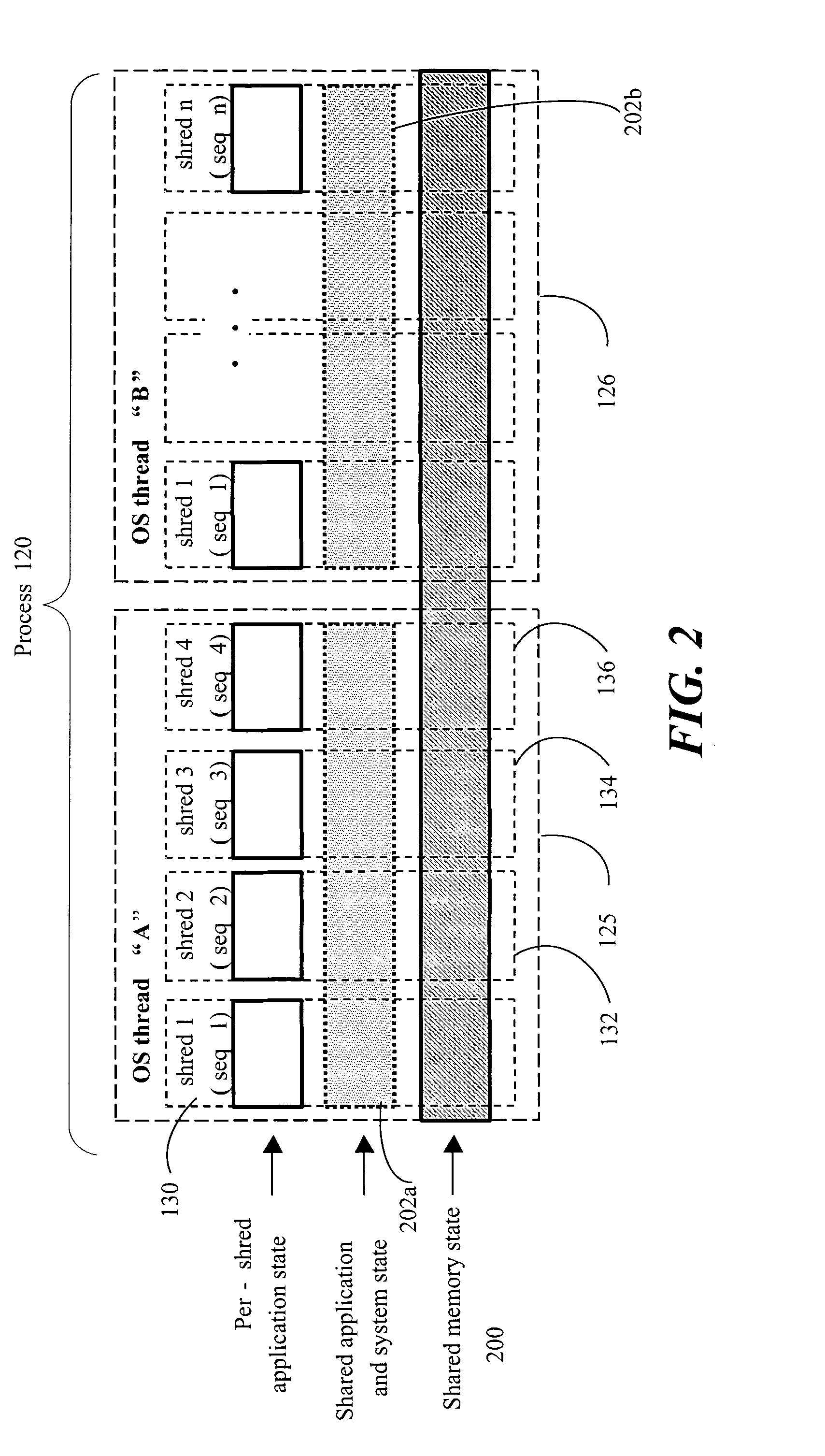
Method, apparatus and system embodiments to schedule user-level OS-independent “shreds” without intervention of an operating system. For at least one embodiment, the shred is scheduled for execution by a scheduler routine rather than the operating system. The scheduler routine resides in user space and may be part of a runtime library. The library may also include monitoring logic that monitors execution of a shredded program and provides scheduling hints, based on shred dependence information, to the scheduler. In addition, the scheduler may further optimize shred scheduling by taking into account information about a system's configuration of thread execution hardware. Other embodiments are also described and claimed.
Owner:INTEL CORP
Terminal services application virtualization for compatability
ActiveUS20100318992A1Improve baseline compatibilityLow costMultiple digital computer combinationsSoftware simulation/interpretation/emulationVirtualizationTerminal server
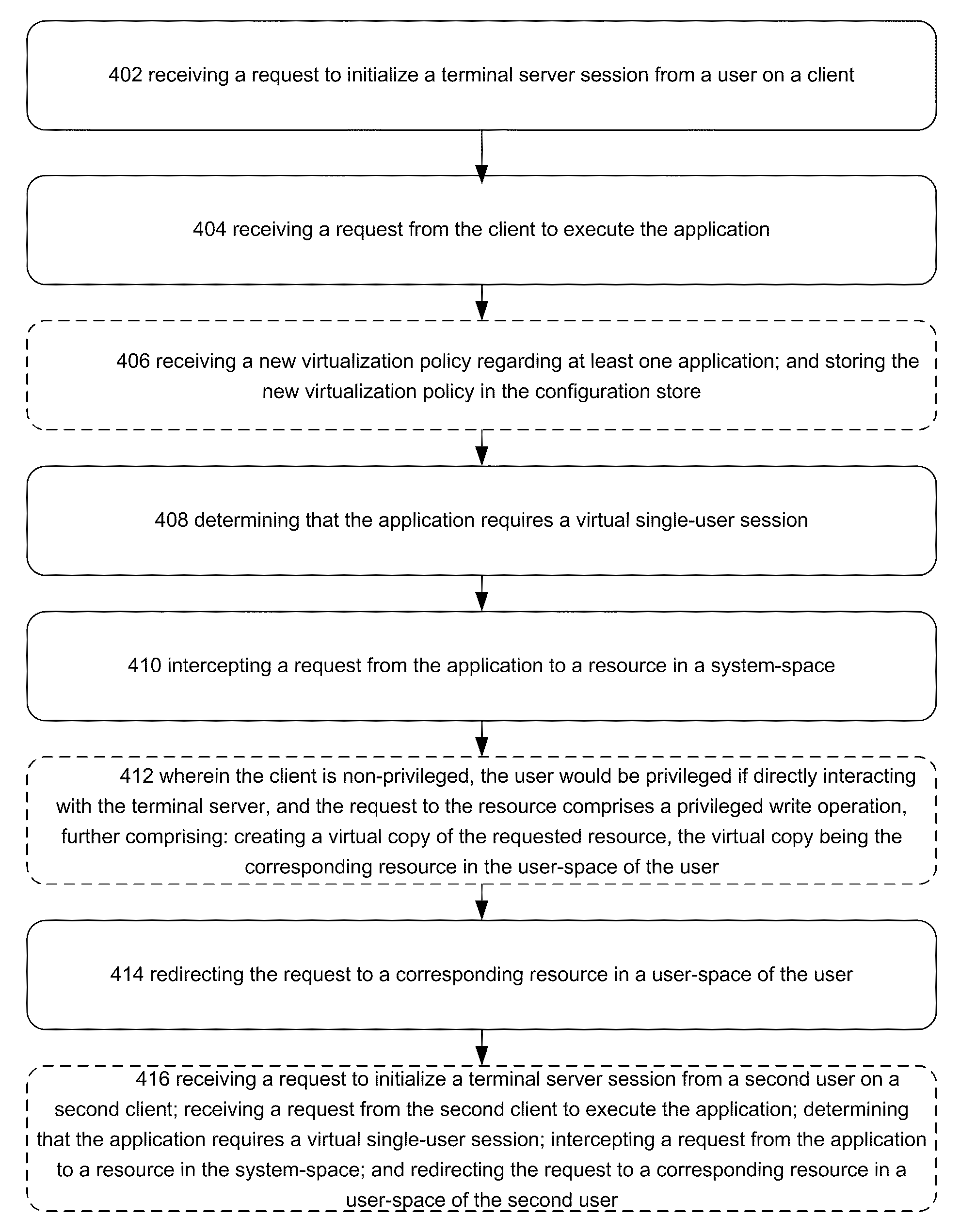
Systems, methods and computer-readable storage media are disclosed for providing a virtual single-user session to a client in a terminal server session. In an embodiment, requests to a resource in the system-space of a system made by an application are intercepted. A determination is made as to whether to virtualize the resource for the application. Where the resource is to be virtualized, a user-specific virtualized resource is created or maintained in user-space and provided to the application.
Owner:MICROSOFT TECH LICENSING LLC
Content filtering gateway realizing method based on network filter
InactiveCN101068229AEasy maintenanceNot easy to attackNetwork connectionsInternal memoryCommunications security
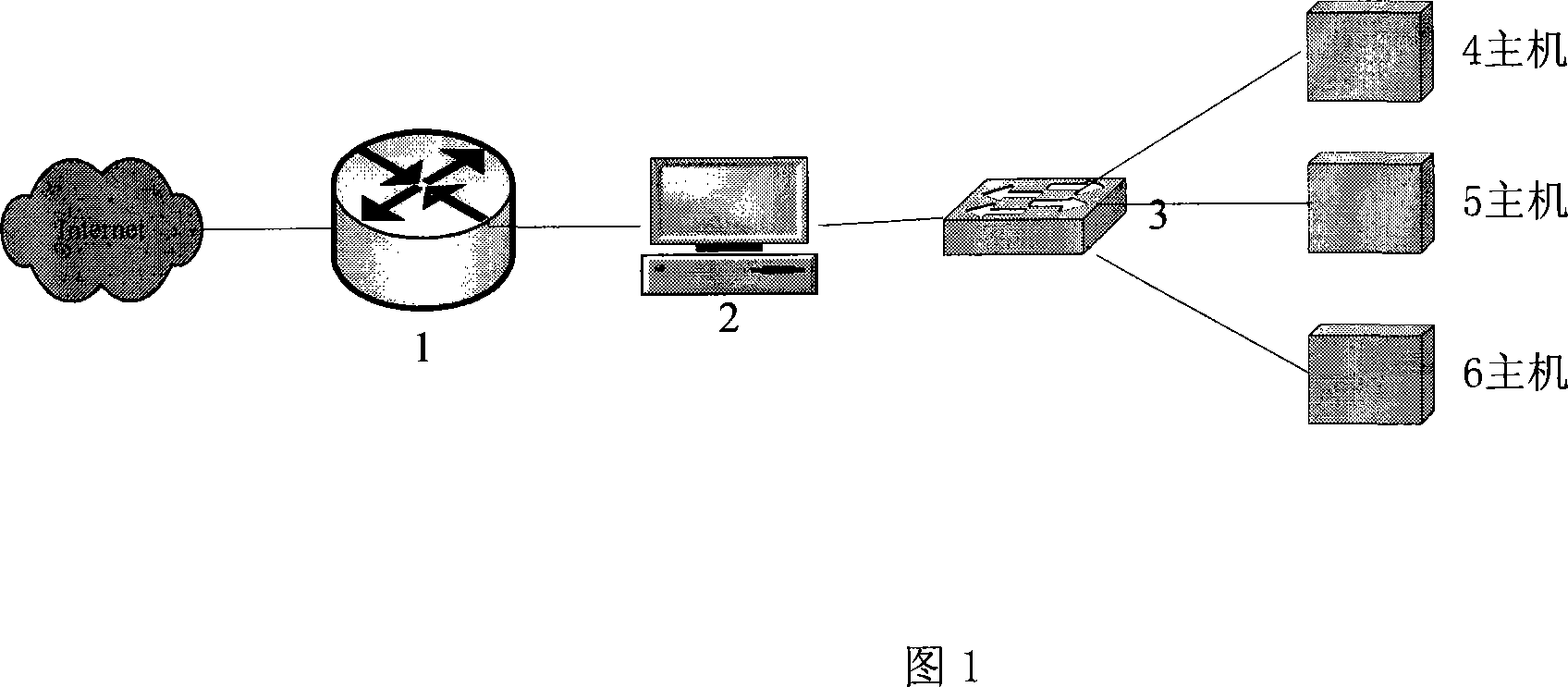
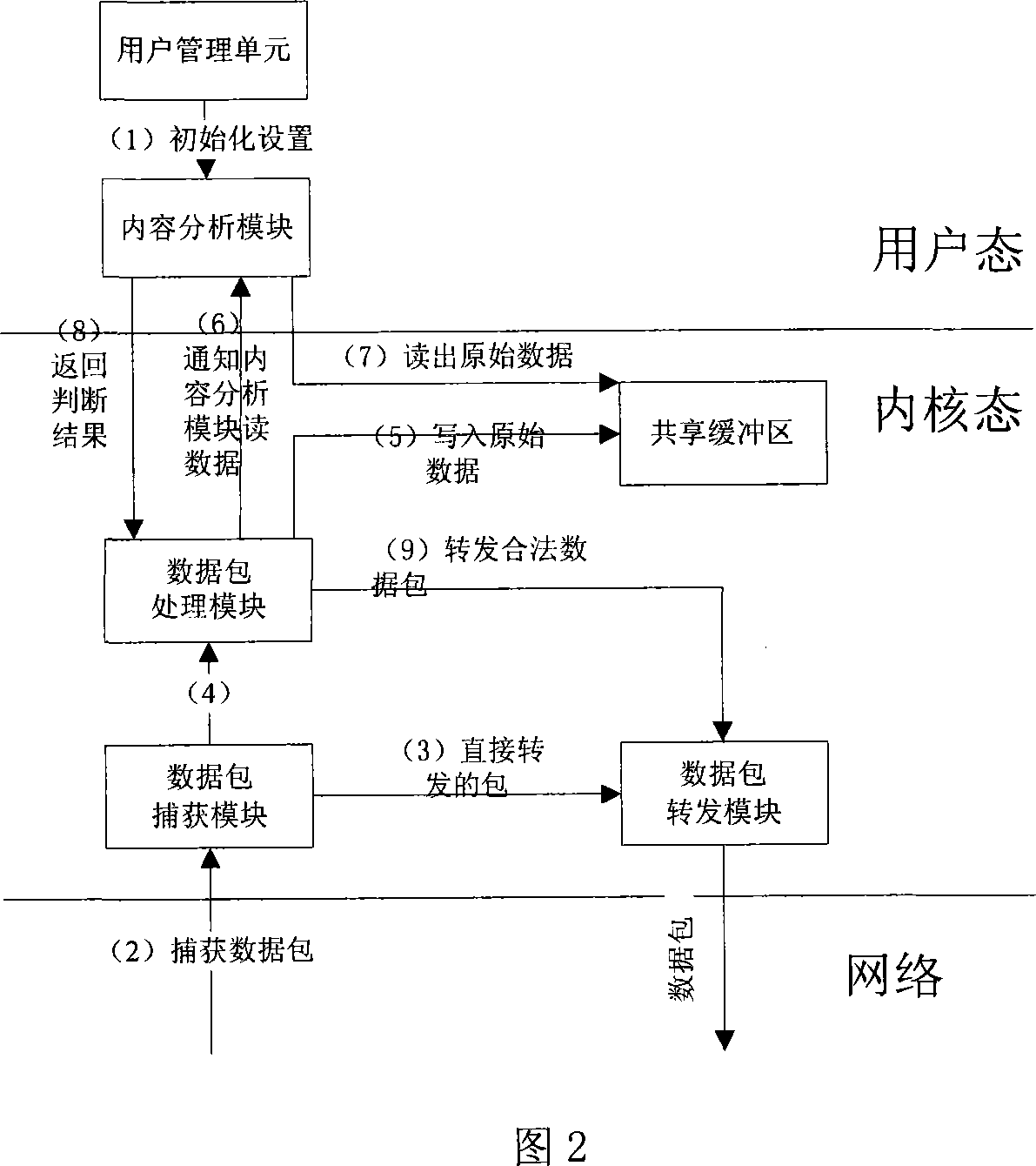
A method for realizing content filtering gateway based on network filter includes realizing network content analysis and real time monitor as well as realizing purpose of filtering application layer information at network layer based on Linux system platform, utilizing network filter Net-filter frame to carry out collection and filtering on data packet under kernel state for optimizing network path of data packet and for raising collection efficiency of data, furthermore using shared internal memory technique of user space and kernel space to submit session content from kernel state to content filtering module of user state.
Owner:BEIJING UNIV OF TECH
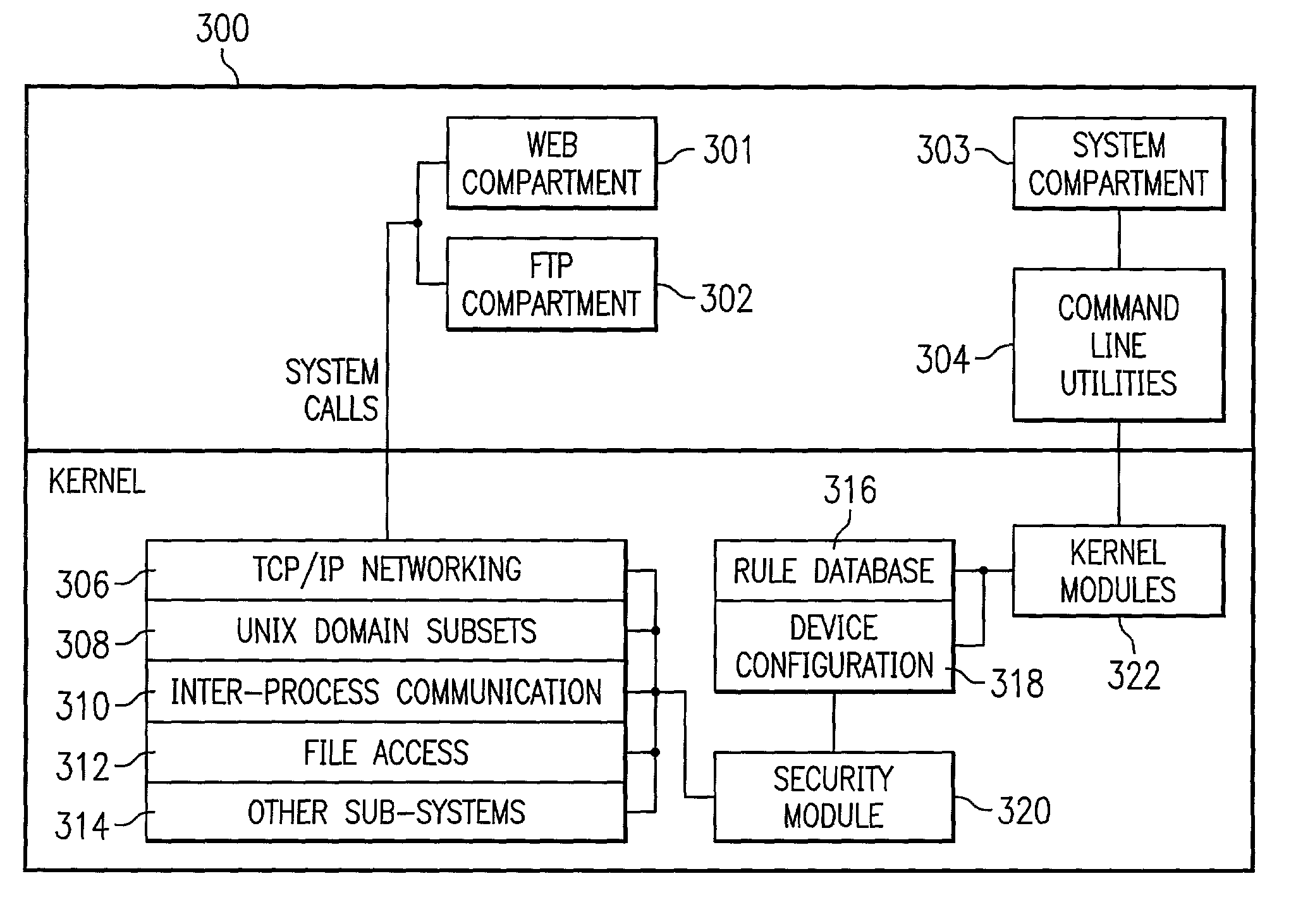
System and method for file system mandatory access control
InactiveUS7962950B2Digital data processing detailsAnalogue secracy/subscription systemsOperational systemFile system
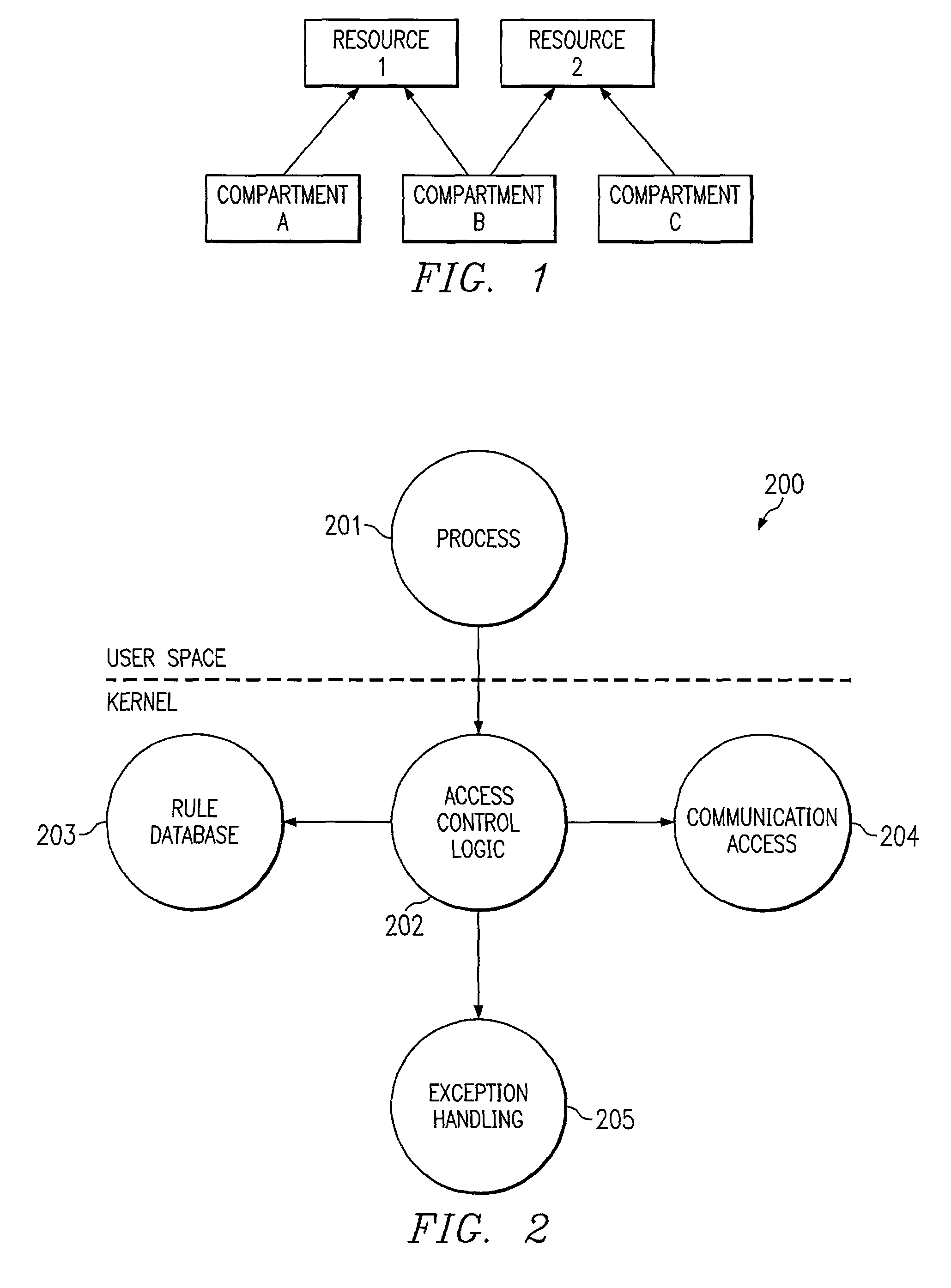
In one embodiment, the present invention is related to a computer system including compartments implemented on an operating system. A database contains access rules with the access rules defining which compartments are authorized to access particular file resources. A kernel module receives a system call to access a file from a user space application belonging to a compartment. A security module determines whether the user space application is authorized to access the file utilizing access rules stored in the database.
Owner:MICRO FOCUS LLC
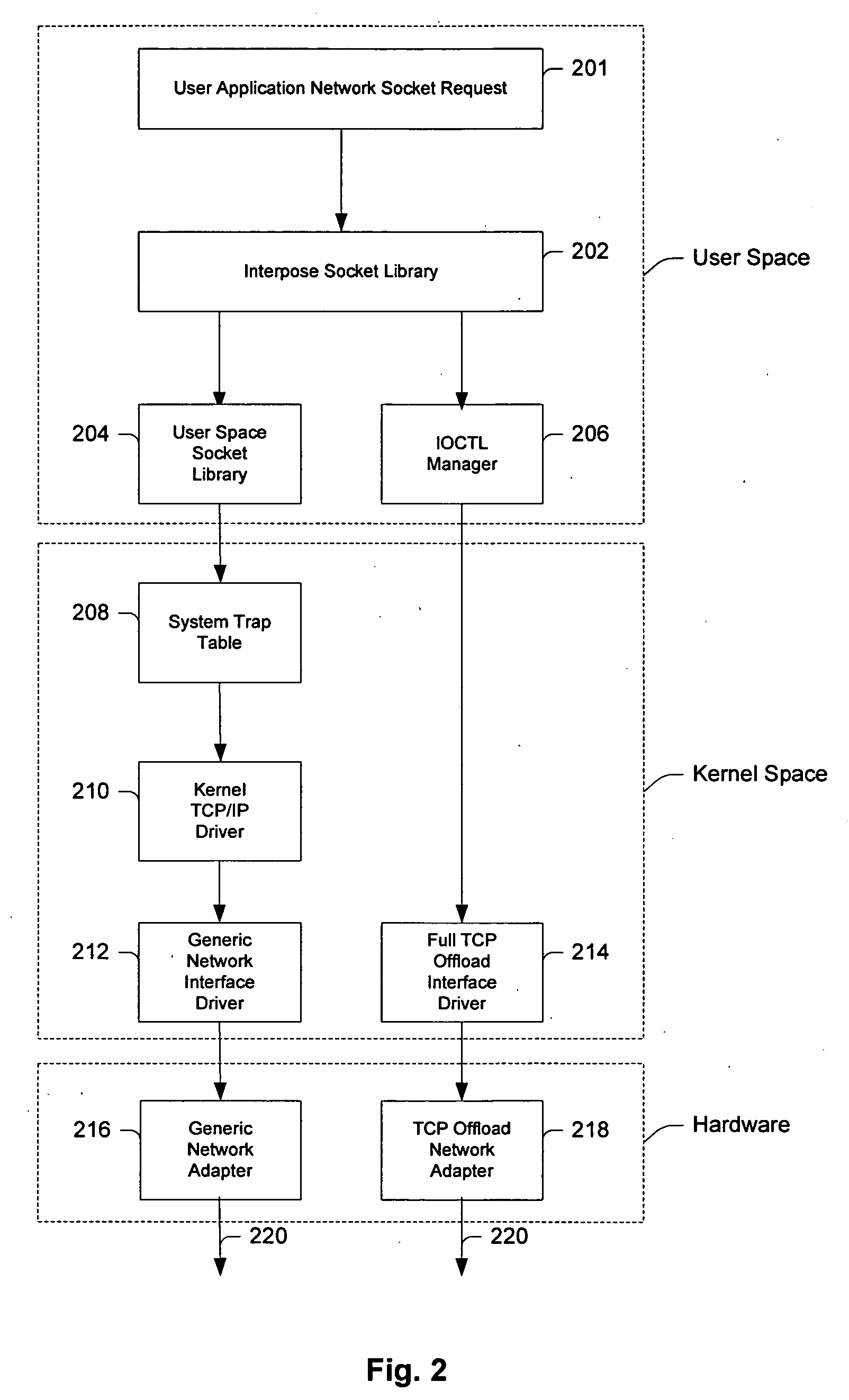
System and method for interfacing TCP offload engines using an interposed socket library
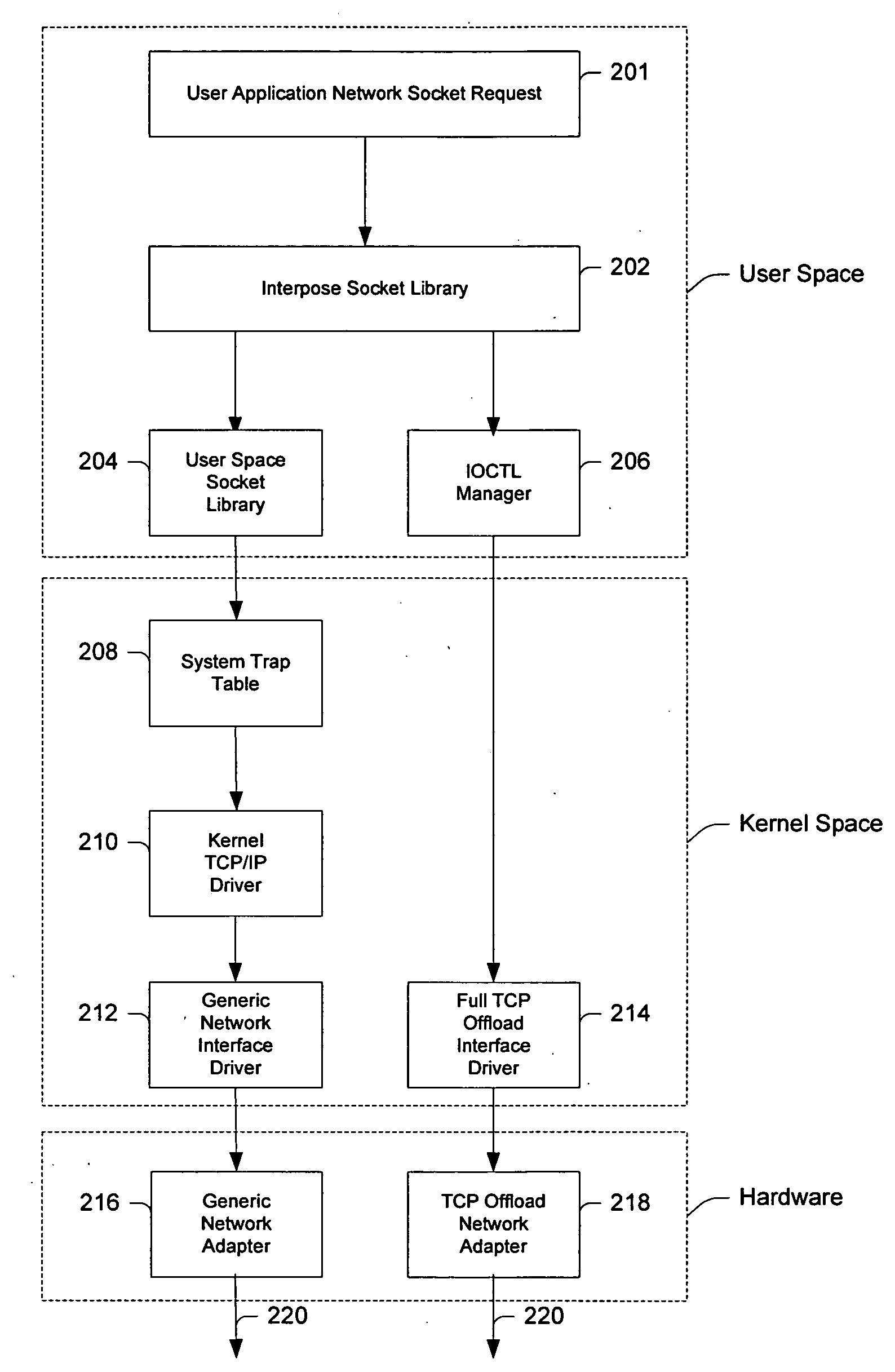
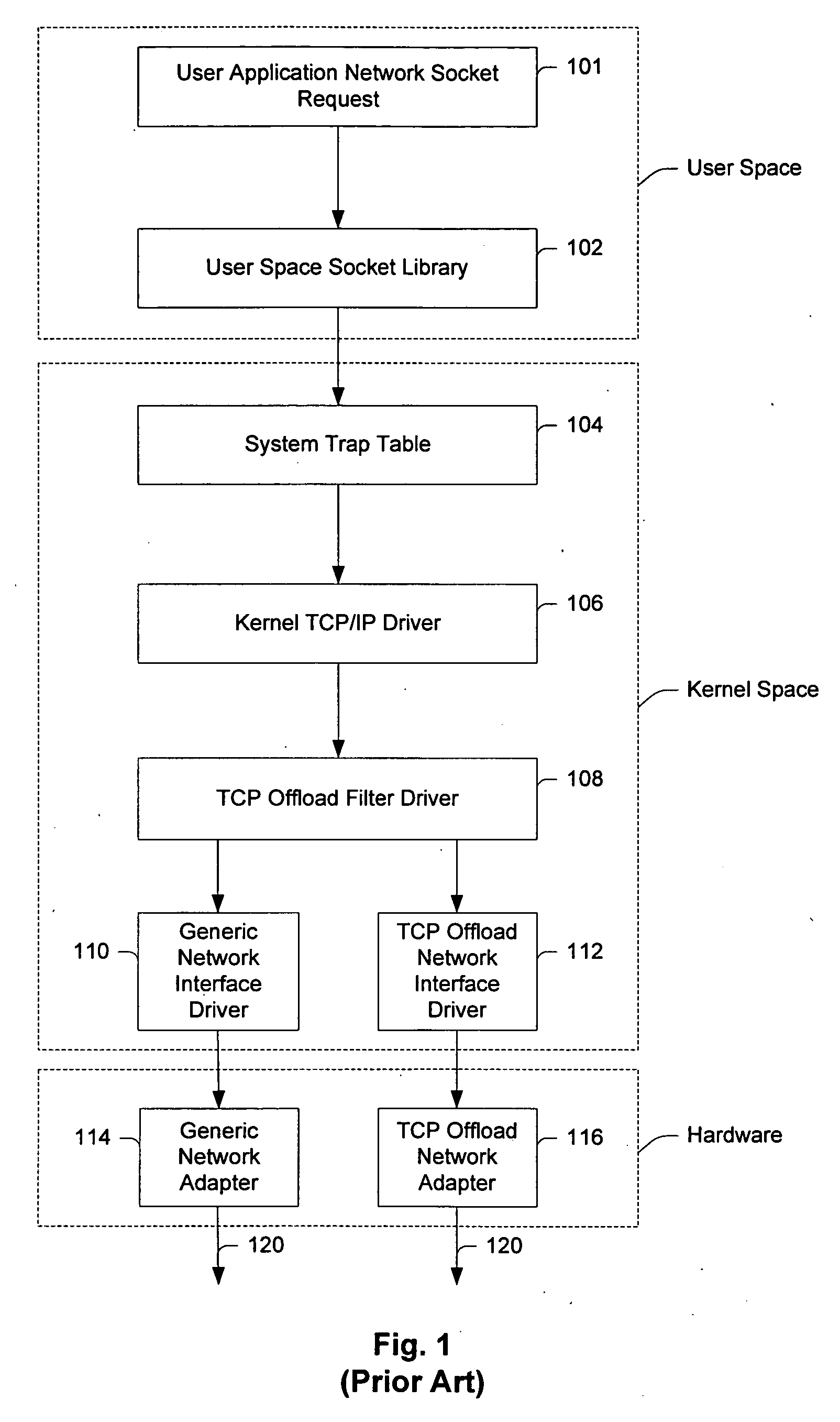
InactiveUS20050021680A1Improve system performanceReduce CPU utilizationMultiple digital computer combinationsProgram controlOperational systemNetwork socket
Owner:CENATA NETWORKS
Systems and Methods for Filtering File System Input and Output
InactiveUS20070110044A1Error preventionFrequency-division multiplex detailsOperational systemDistributed Computing Environment
Systems and methods for managing digital assets in a distributed computing environment are described. Meta-data for the digital assets is stored separately from the digital assets. Meta-data for some of the digital assets is copied and stored at a central location. Meta-data for the digital assets is generated by clients of the system. A method of filtering I / O requests of a computer system includes: receiving a plurality of I / O requests from a filter manager of the computer system, the filter manager executing in the system space of an operating system; applying a hierarchical rule set to at least a portion of the plurality of I / O requests by a mini-filter executing in the system space; and providing at least one of the plurality of I / O requests from the mini-filter to an agent executing in user space in response to the application of the hierarchical rule set by the mini-filter.
Owner:MICRO FOCUS LLC
Method and apparatus for providing digital rights management
InactiveUS20060129496A1Data processing applicationsProgram/content distribution protectionVirtual file systemOperational system
A method and wireless mobile device employs a virtual file system (706) and a digital rights management file system (708), at an operating system level, and a user space digital rights manager (712), at an application or user space level. The user space digital rights manager (712) is operative to manage digital rights associated with content that is stored in the digital rights management file system (708). For example, although an application may request content that has digital rights associated with it from the virtual file system (706), and the virtual file system (706) communicates with the digital rights management file system (708) at the operating system level, the DRM file system (708) redirects the calls to the user space digital rights manager (712) at the user space level which performs the digital rights operations.
Owner:MOTOROLA INC
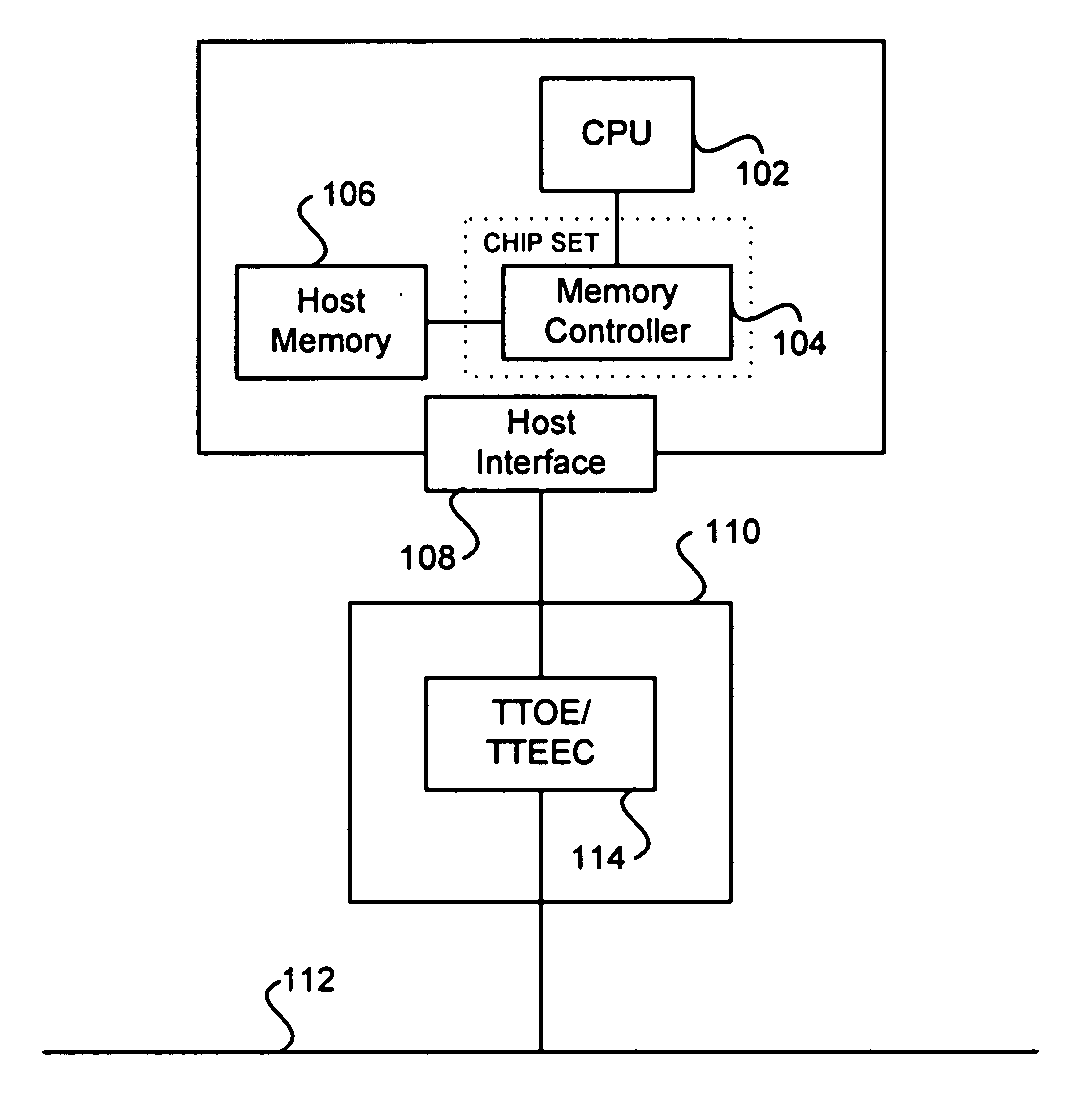
Method and system for transparent TCP offload (TTO) with a user space library
ActiveUS20070255802A1Error preventionFrequency-division multiplex detailsNetwork interfaceUser space
Certain aspects of a method and system for transparent TCP offload with a user space library are disclosed. Aspects of a method may include collecting TCP segments in a network interface card (NIC) without transferring state information to a host system. When an event occurs that terminates the collection of TCP segments, a single aggregated TCP segment based on the collected TCP segments may be generated. The aggregated TCP segment may be posted directly to a user space library, bypassing kernel processing of the aggregated TCP segment.
Owner:BROADCOM ISRAEL R&D
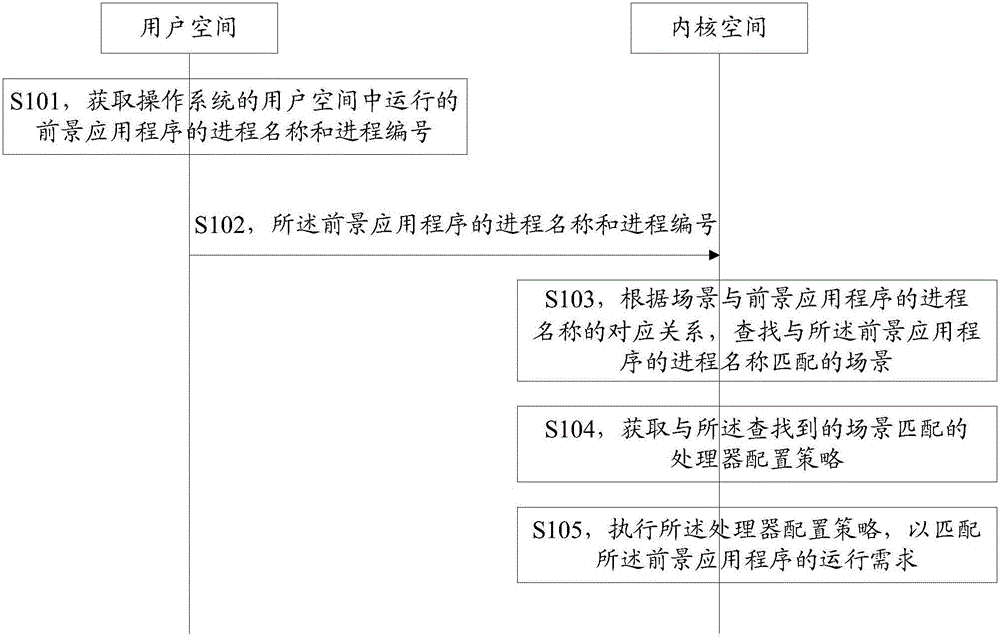
Foreground application program scene synchronization method, apparatus and system
ActiveCN106095592AImprove performanceReduce power consumptionResource allocationProgram synchronisationOperational systemScene matching
Embodiments of the invention disclose a foreground application program scene synchronization method, apparatus and system. By receiving a process name and a process number of a foreground application program running in the user space of the operating system, the kernel space of the operating system searches a scene matching the process name of the foreground application program according to the corresponding relationship between the scene and the process name of the foreground application program, a processor configuration policy that matches the searched scene is obtained, and the processor configuration policy is executed to match the operational requirements of the foreground application program, so that configuration of the processor can precisely match the operational requirements of the foreground application program, system performance is optimized, and power consumption is reduced.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
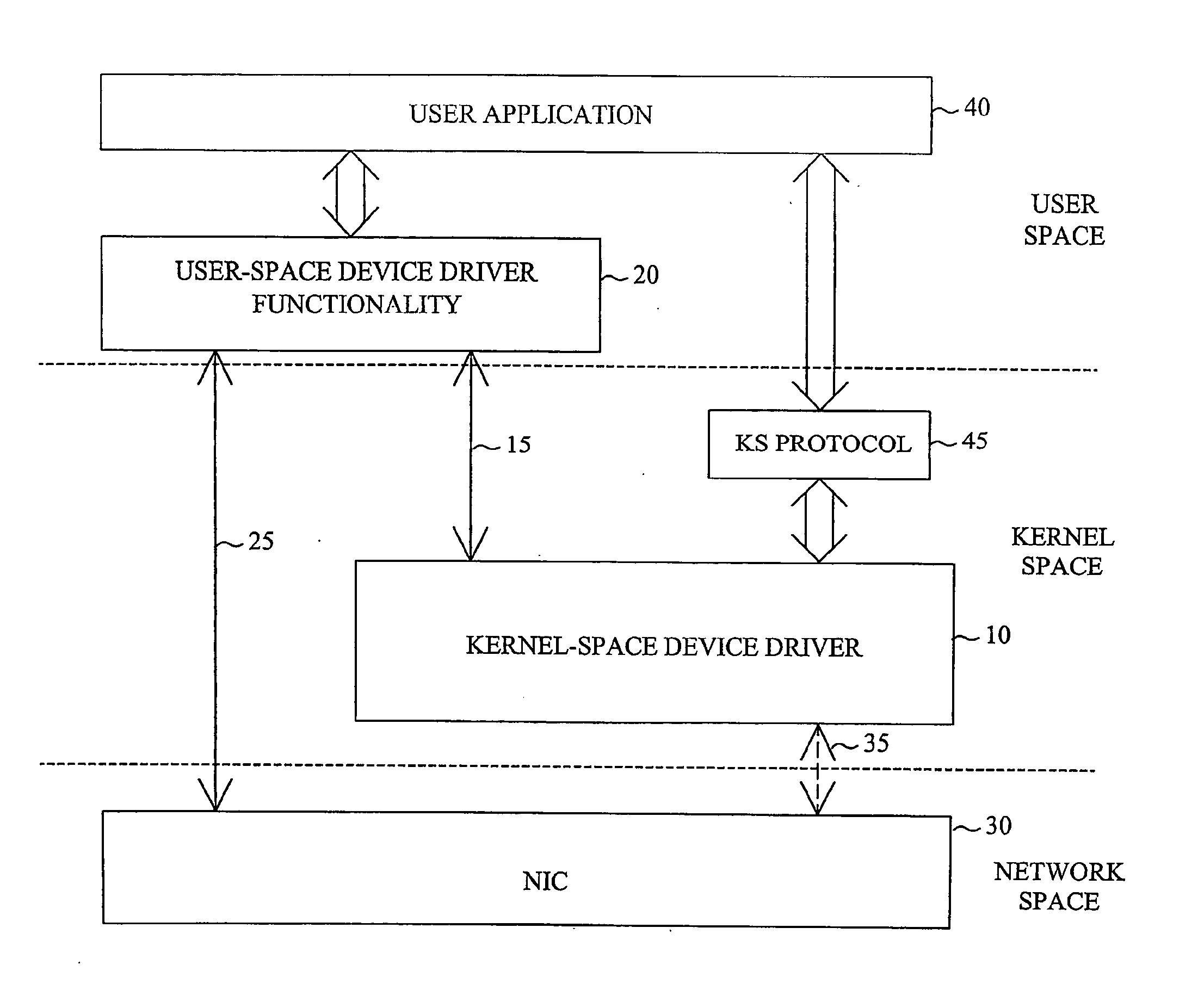
Network device driver architecture
InactiveUS20050210479A1Easy to adaptReduce in quantityMultiprogramming arrangementsTransmissionZero-copyCombined use
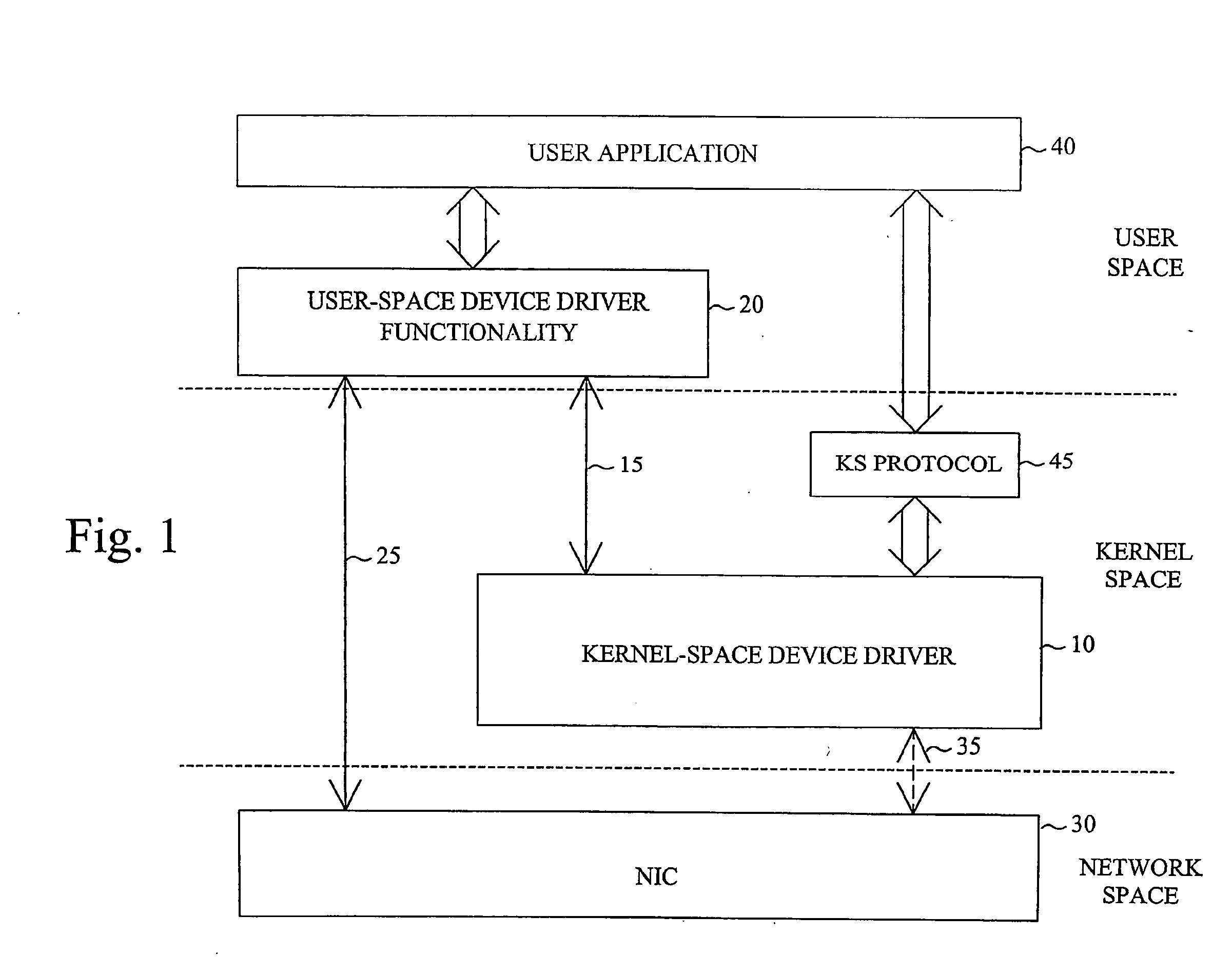
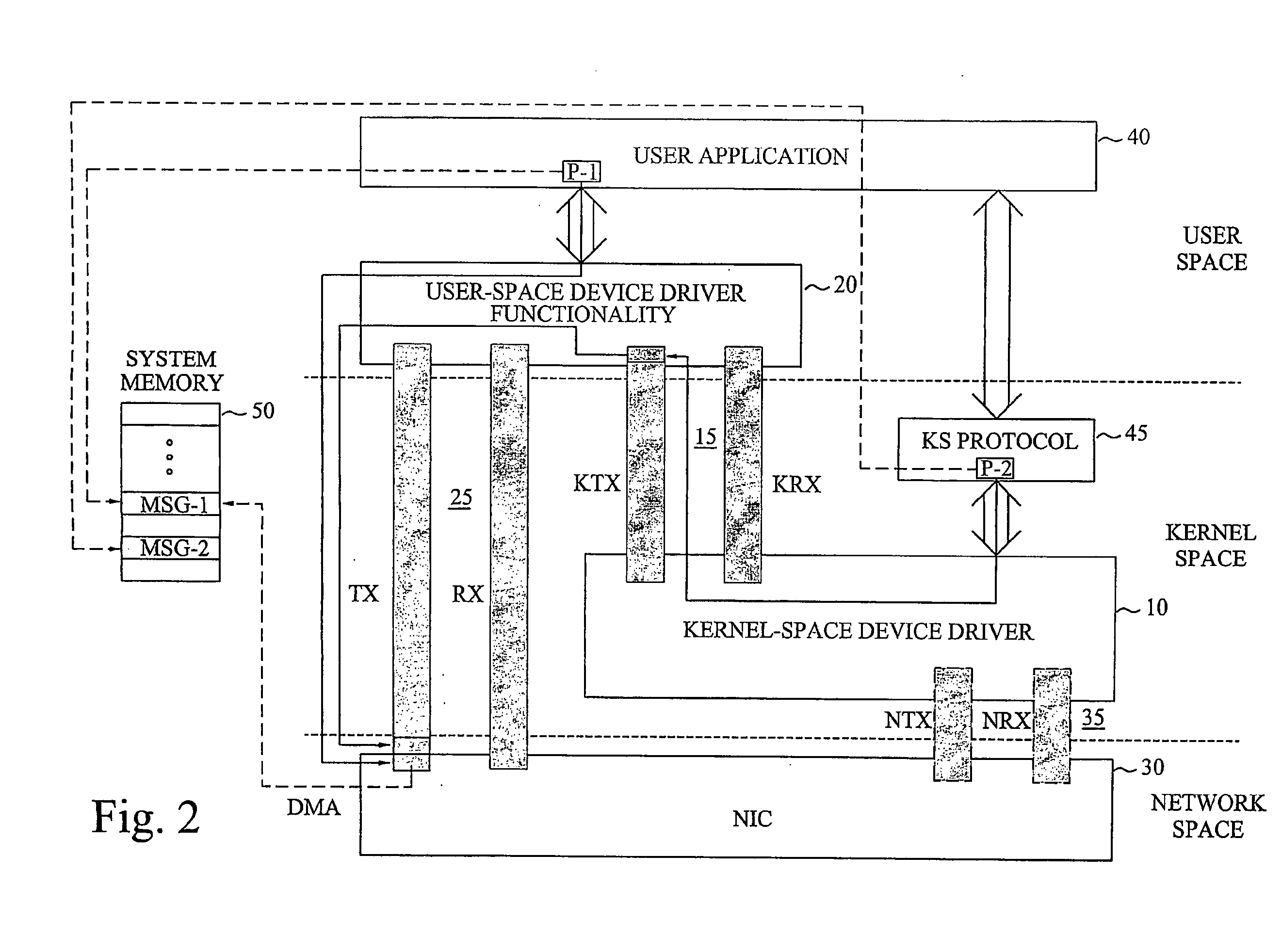
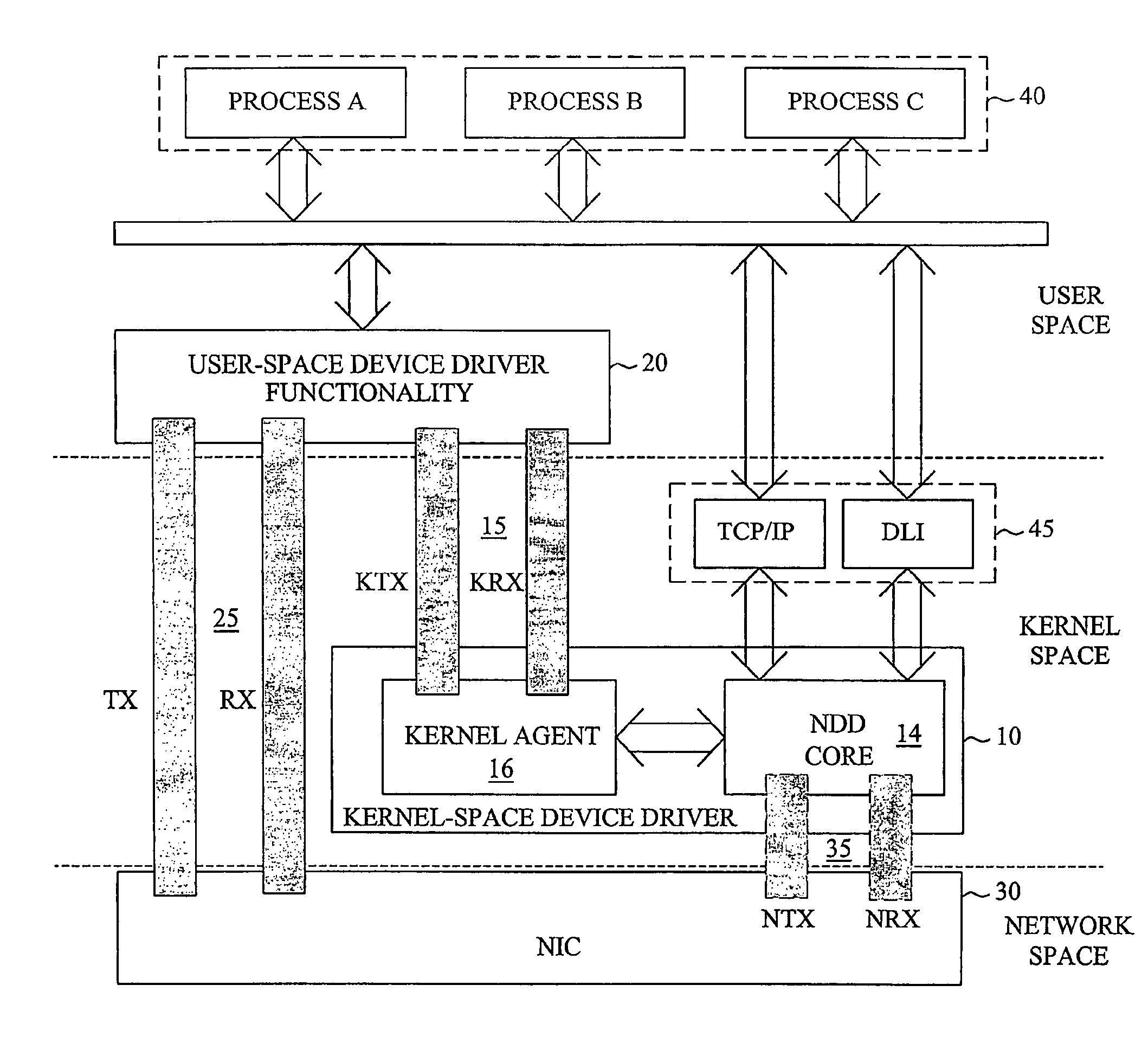
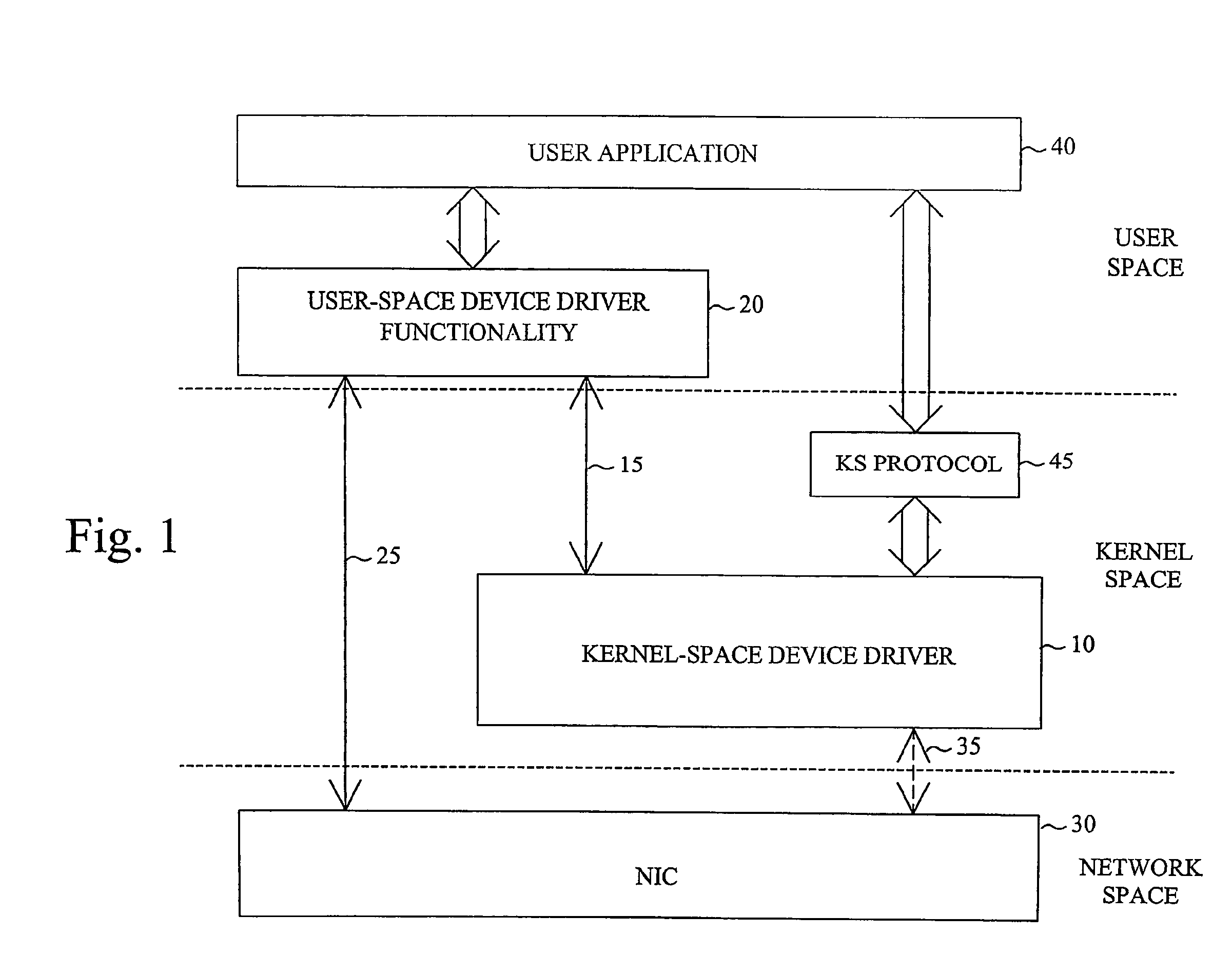
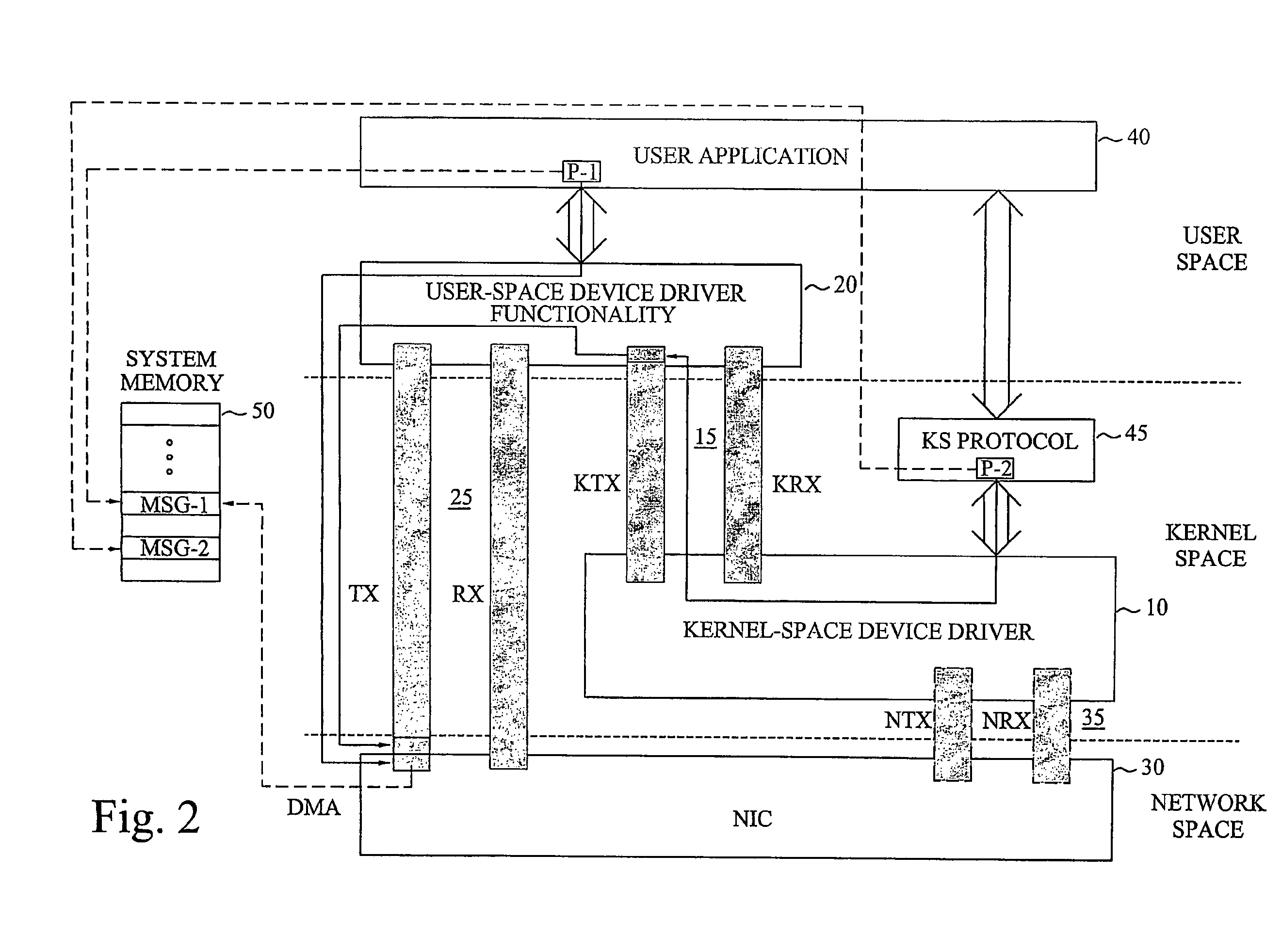
The invention proposes a network device driver architecture with functionality distributed between kernel space and user space. The overall network device driver comprises a kernel-space device driver (10) and user-space device driver functionality (20). The kernel-space device driver (10) is adapted for enabling access to the user-space device driver functionality (20) via a kernel-space-user-space interface (15). The user-space device driver functionality (20) is adapted for enabling direct access between user space and the NIC (30) via a user-space-NIC interface (25), and also adapted for interconnecting the kernel-space-user-space interface (15) and the user-space-NIC interface (25) to provide integrated kernel-space access and user-space access to the NIC (30). The user-space device driver functionality (20) provides direct, zero-copy user-space access to the NIC, whereas information to be transferred between kernel space and the NIC will be “tunneled” through user space by combined use of the kernel-space device driver (10), the user-space device driver functionality (20) and the two associated interfaces (15,25).
Owner:TELEFON AB LM ERICSSON (PUBL)
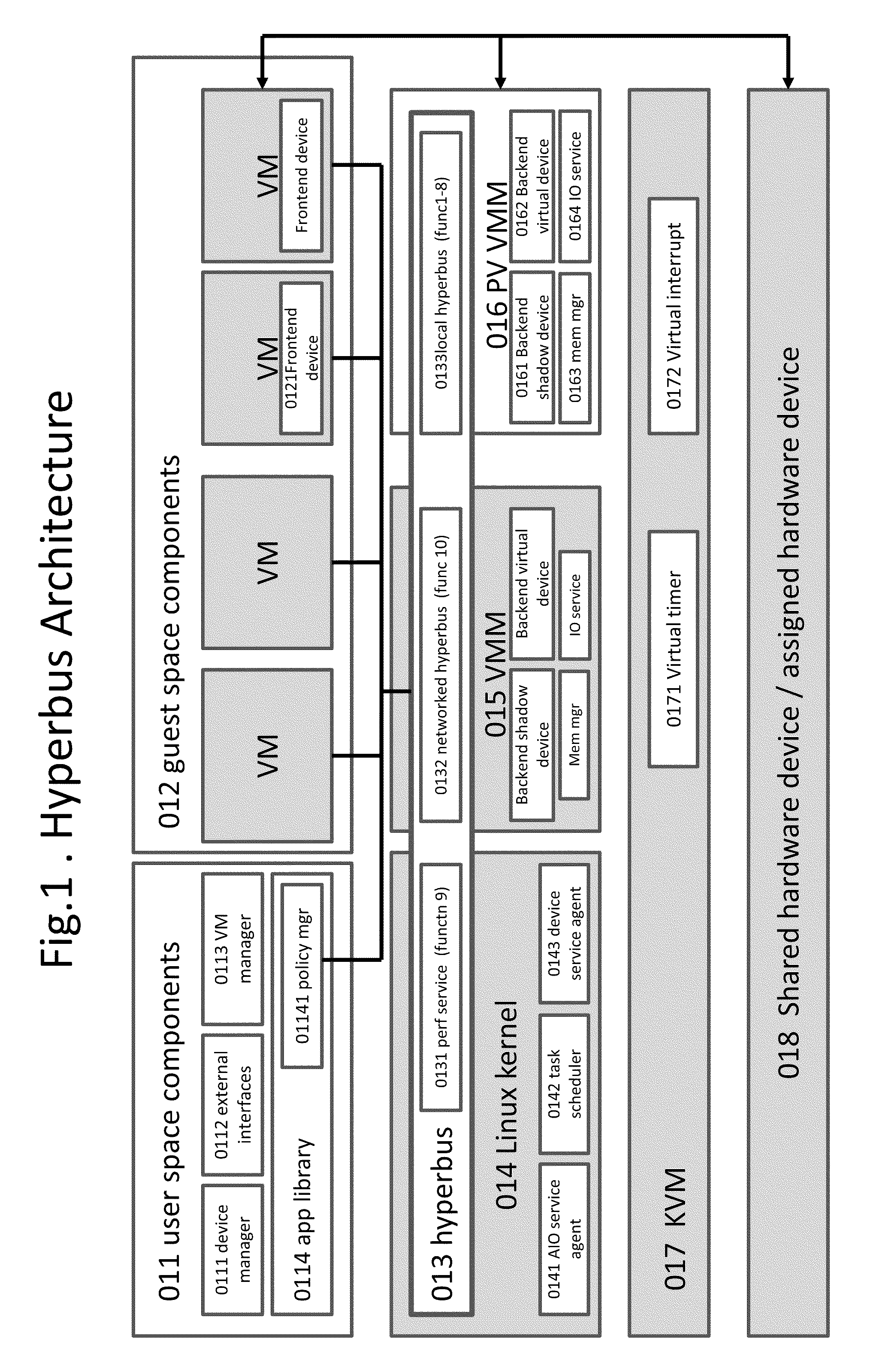
Kernel bus system with a hyberbus and method therefor
InactiveUS8832688B2Fast deliveryImprove performanceMultiprogramming arrangementsSoftware simulation/interpretation/emulationVirtualizationZero-copy
Some embodiments concern a kernel bus system for building at least one virtual machine monitor. The kernel bus system can include: (a) a hyperbus; (b) user space components; (c) guest space components configured to interact with the user space components via the hyperbus; (d) VMM components having frontend devices configure to perform I / O operations with the hardware devices of the host computer using a zero-copy method or non-pass-thru method; (e) para-virtualization components having (1) a virtual interrupt module configured to use processor instructions to swap the processors of the host computer between a kernel space and a guest space; and (2) a virtual I / O driver configured to enable synchronous I / O signaling, asynchronous I / O signaling and payload delivery, and pass-through delivery independent an QEMU emulation; and (f) KVM components. Other embodiments are disclosed.
Owner:TRANSOFT
Tabletop, mobile augmented reality system for personalization and cooperation, and interaction method using augmented reality
The present invention relates to a tabletop, mobile augmented reality system for personalization and cooperation and an interaction method using augmented reality. More particularly, the tabletop, mobile augmented reality system for personalization and cooperation according to the present invention adds a mobile interface for providing a personal user space to a table interface for providing a cooperative space for users such that information on a table can be brought to a personal mobile device and controlled directly or manipulated personally by a user, allows for fairness in the right to control the table, and permits users to share the result of personalization. The tabletop, mobile augmented reality system for personalization and cooperation according to the present invention includes a table interface for providing a cooperative space, which allows for interaction among users by enabling users to touch a specific piece of content of the image projected onto a table or via an object disposed on the specific piece of content. The invention further relates to a mobile interface for providing a personal space, which recognizes and traces said object to augment the image projected onto the table with three-dimensional content.
Owner:INTELLECTUAL DISCOVERY CO LTD
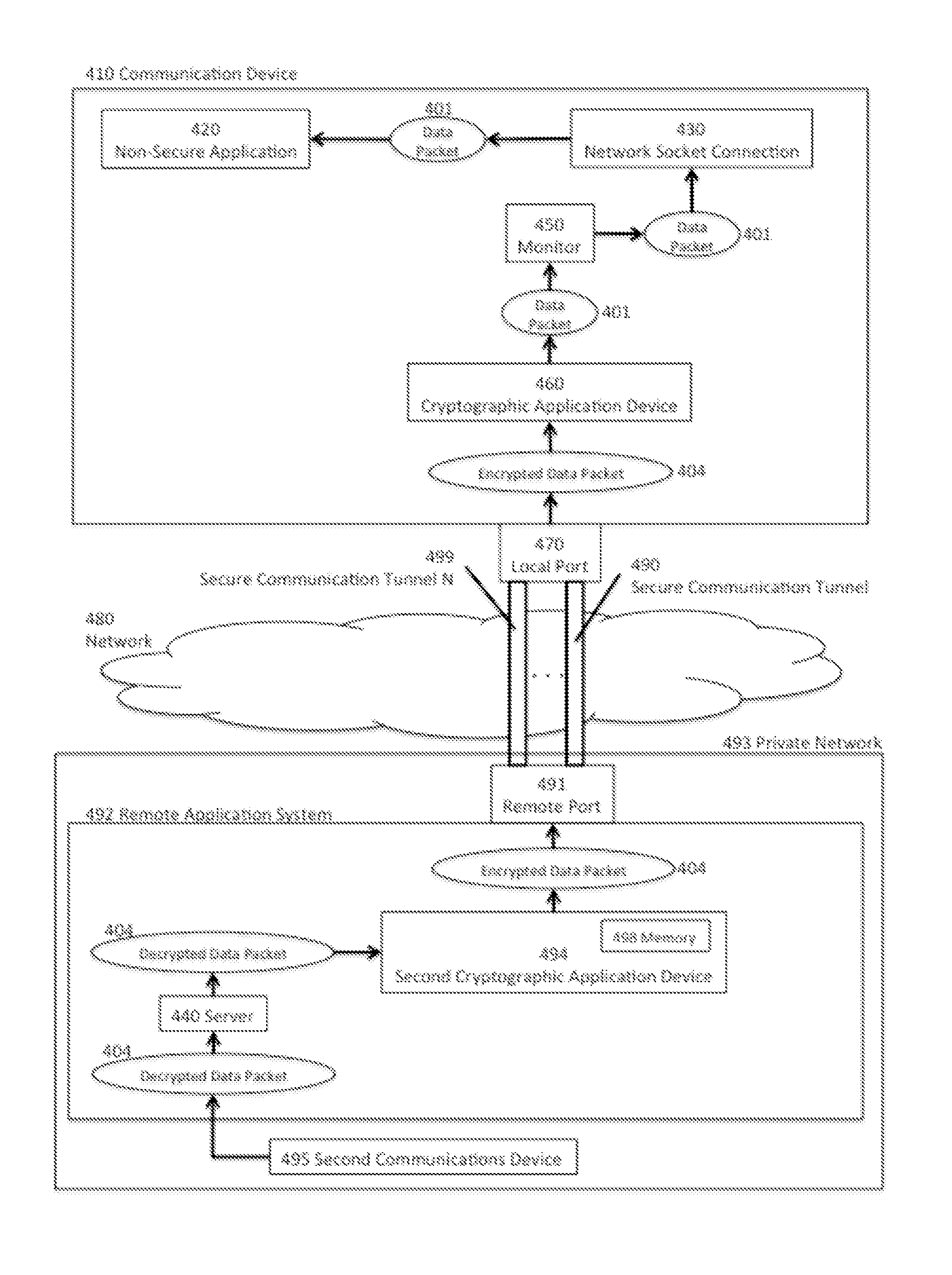
User-Space Enabled Virtual Private Network
This invention includes apparatus, systems, and methods to establish a virtual private network (“VPN”), or a secured network for authenticated and encrypted data transmission to prevent disclosure of private information to unauthorized parties. This invention provides secure and authenticated data transmission from a communication device to another device over any public or private network while using existing standard applications such as email, VoIP, internet browsers, ISR applications, video conferencing, telecommuting, inventory tracking and control, etc. without the need to secure or add encryption features into each specific application. This invention provides the opportunity to selectively secure one or more existing applications with configuration changes that can be made at the user-space level of the software stack and without need for higher level software stack access, such as root access.
Owner:SAIFE
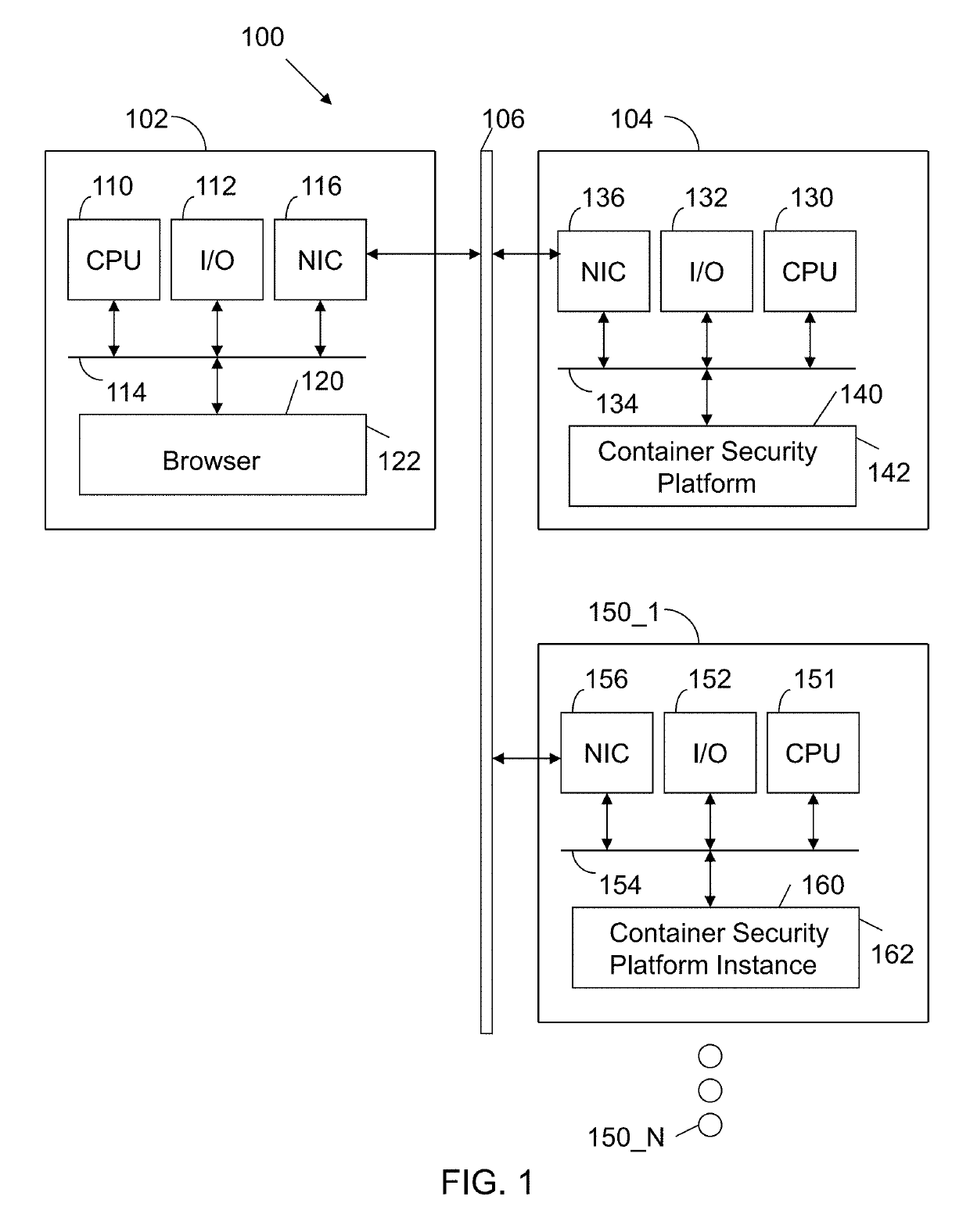
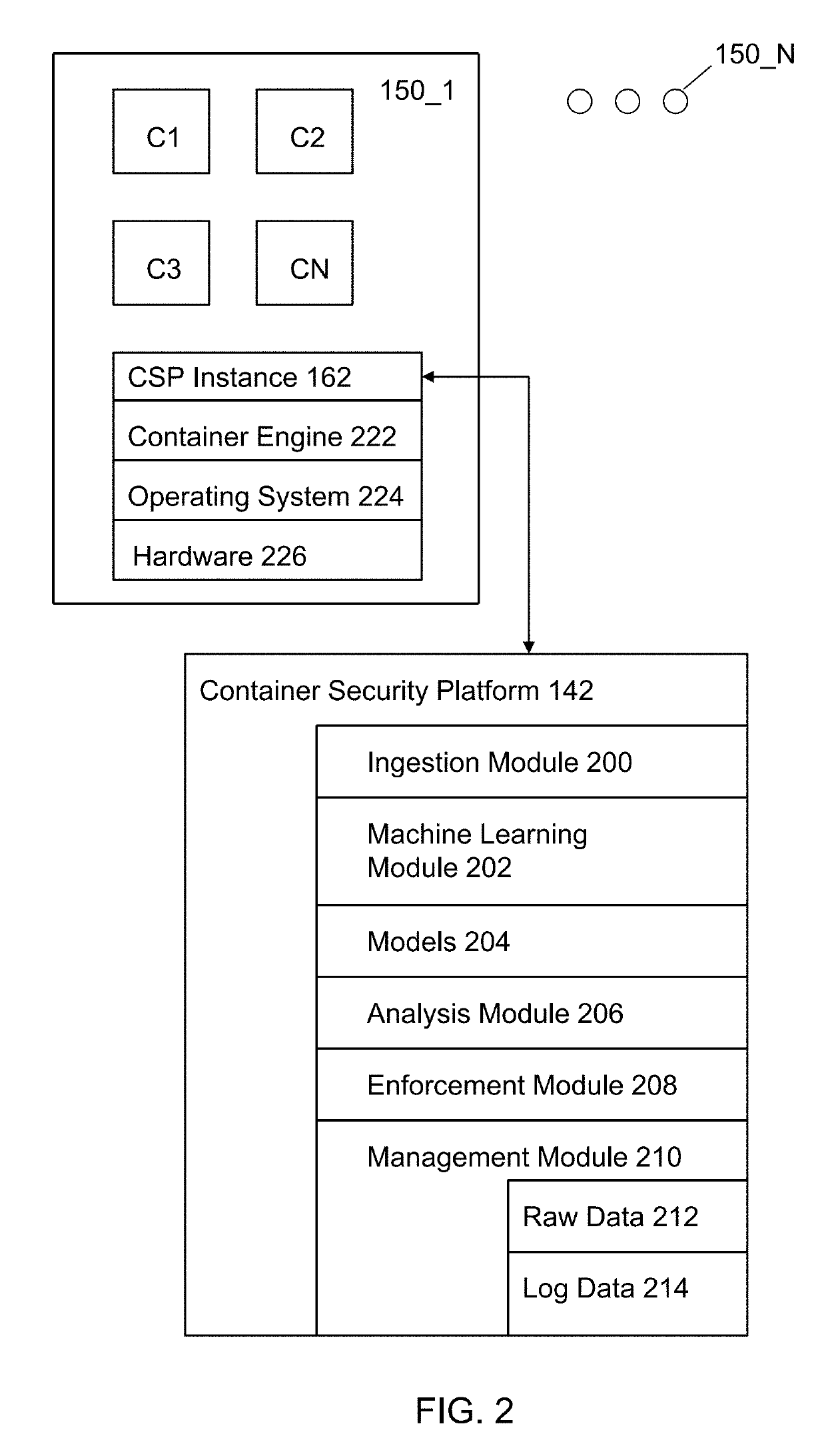
System and method for providing security in a distributed computation system utilizing containers
A server has a processor and a memory connected to the processor. The memory stores instructions executed by the processor to collect operating signals from machines, where each operating signal characterizes the state or a change in operational state of a designated application operating within a designated container, where the designated container is an isolated process in user space designated by an operating system kernel. The operating signals are compared to models that incorporate summarizations of data sets that represent observed benign operating signals and malicious operating signals for the designated application operating within the designated container. Risks associated with the operating signals are characterized.
Owner:RED HAT
Managing process state information in an operating system environment
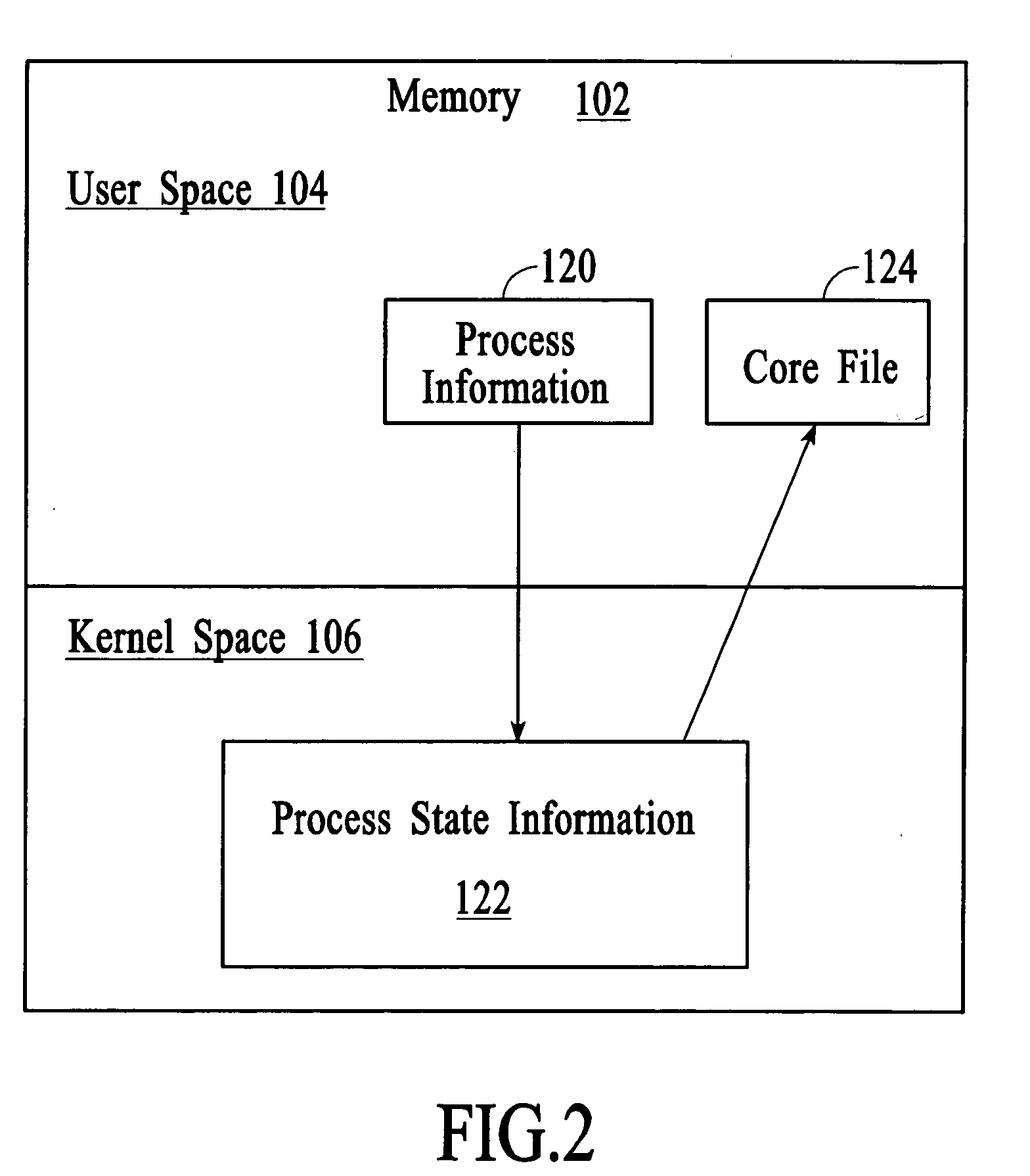
InactiveUS20050210077A1Excessively generatedNon-redundant fault processingProgram controlCore dumpOperational system
A technique for managing process state information involves pushing process state information from the kernel space to the user space in the event of an application crash and generating a core file at the user level instead of at the kernel level. Handling the process state information at the user level instead of at the kernel level provides more flexibility in the generation and management of a core file as compared to systems that use kernel code to generate and manage the core file. A core dump application at the user level can be programmed to forward the core file to another system that has permanent storage capacity available. Additionally, the core dump application can be programmed to compress the process state information and / or to extract only certain information from the process state information while generating the core file.
Owner:LUCENT TECH INC
Server load balancing system
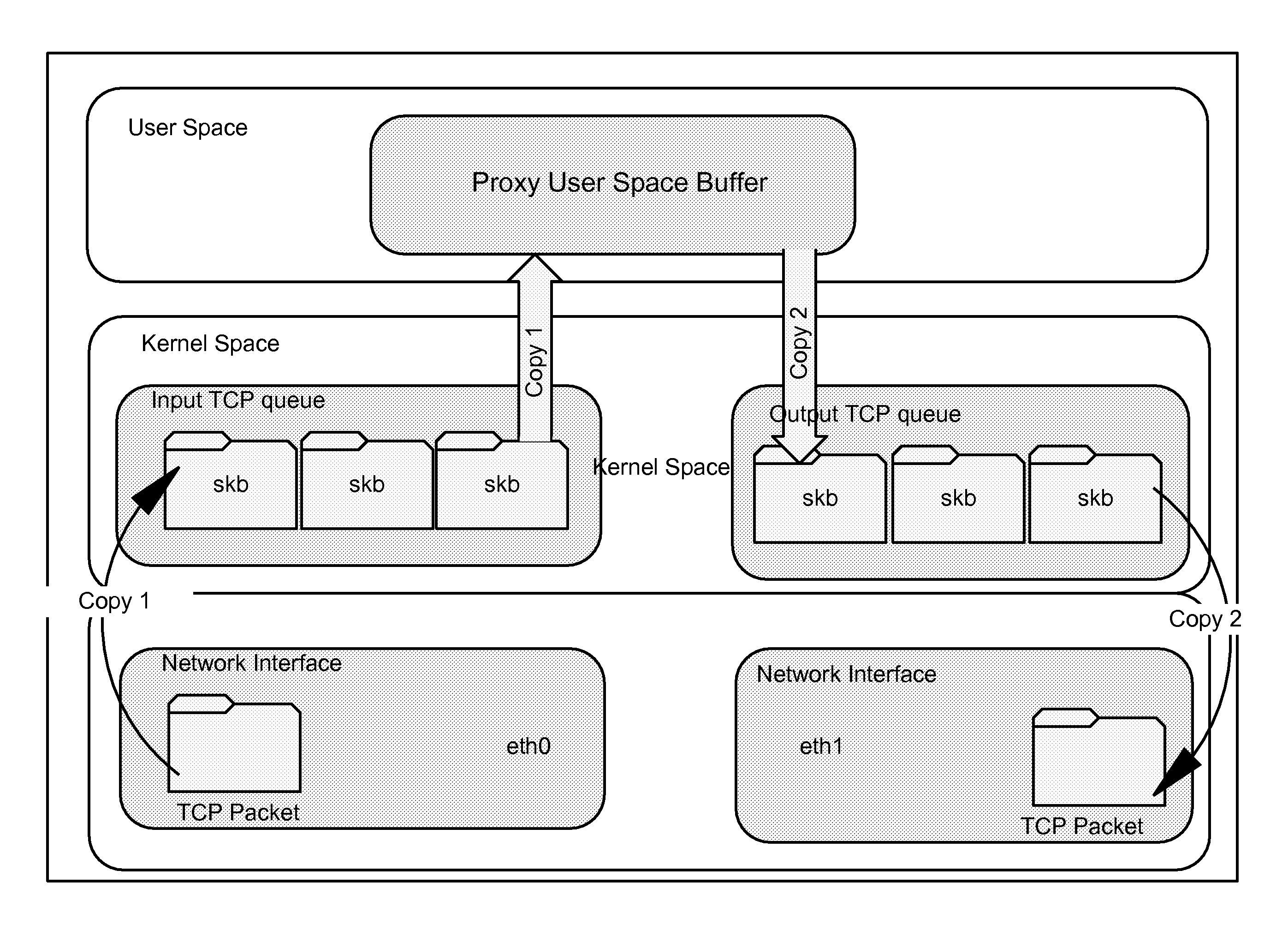
ActiveUS7475157B1Maximize efficiencyEliminate needMultiple digital computer combinationsTransmissionWeb serviceClient-side
A system for maximizing the efficiency of a load balancing server for an asymmetric web farm utilizes a TCP stack and data packets to send and receive client service requests. An internal buffer enables each web server in the web farm to balance their loading based on the contents of the client service request. Data switching between the address portion of the user space and the address portion of the kernel space within the load balancing server is eliminated.
Owner:CLOUDBLUE LLC
Intrusion detection system facing cloud calculating environment
InactiveCN102724176ASolve the large-scale dynamic number of usersEnsure application securityTransmissionCommunications securityService domain
According to the invention, a safety problem based on splitting and under large-scale shared virtual calculating environment is discussed. And the invention provides a safety framework based on a virtual machine and facing the virtual calculating environment and a large-scale distributed extensible intrusion detection system. The system provides resource access monitoring identity authentication inside and outside an ability service domain and an encrypted data transmission channel for a user, provides isolation and protection of a user space and a system space and finally guarantees application safety based on an ability server. By using the system of the invention, many safety problems under the ability server, such as, a large-scale dynamic user quantity, large-scale dynamic virtual resource objects, a calculating load of dynamic increase and reduction, user space isolation, user system isolation and protection, internal and external network attack prevention, equipment safety reuse and sharing, communication safety, uniform authentication, access control and the like, are solved.
Owner:BEIJING COMPUTING CENT
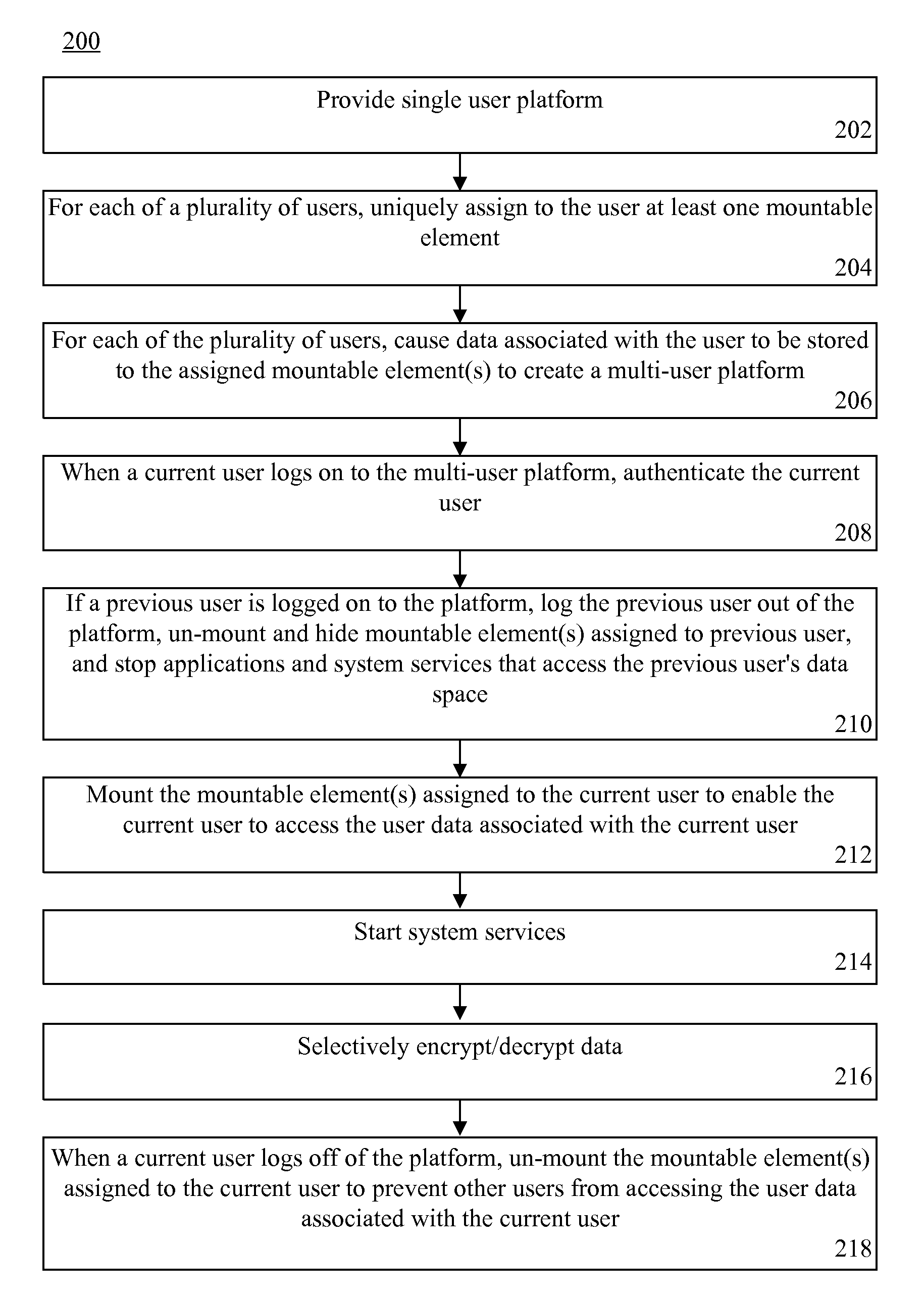
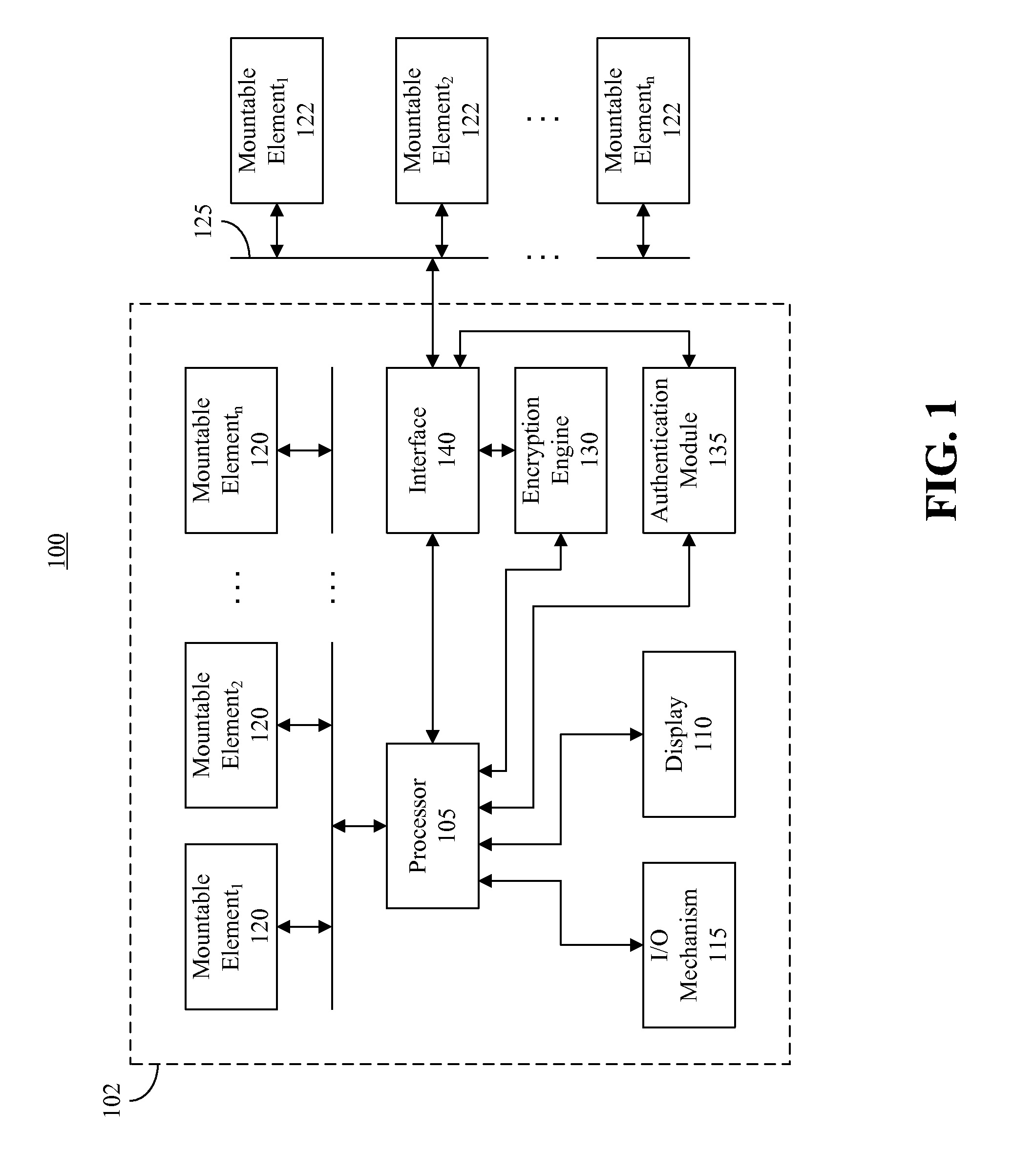
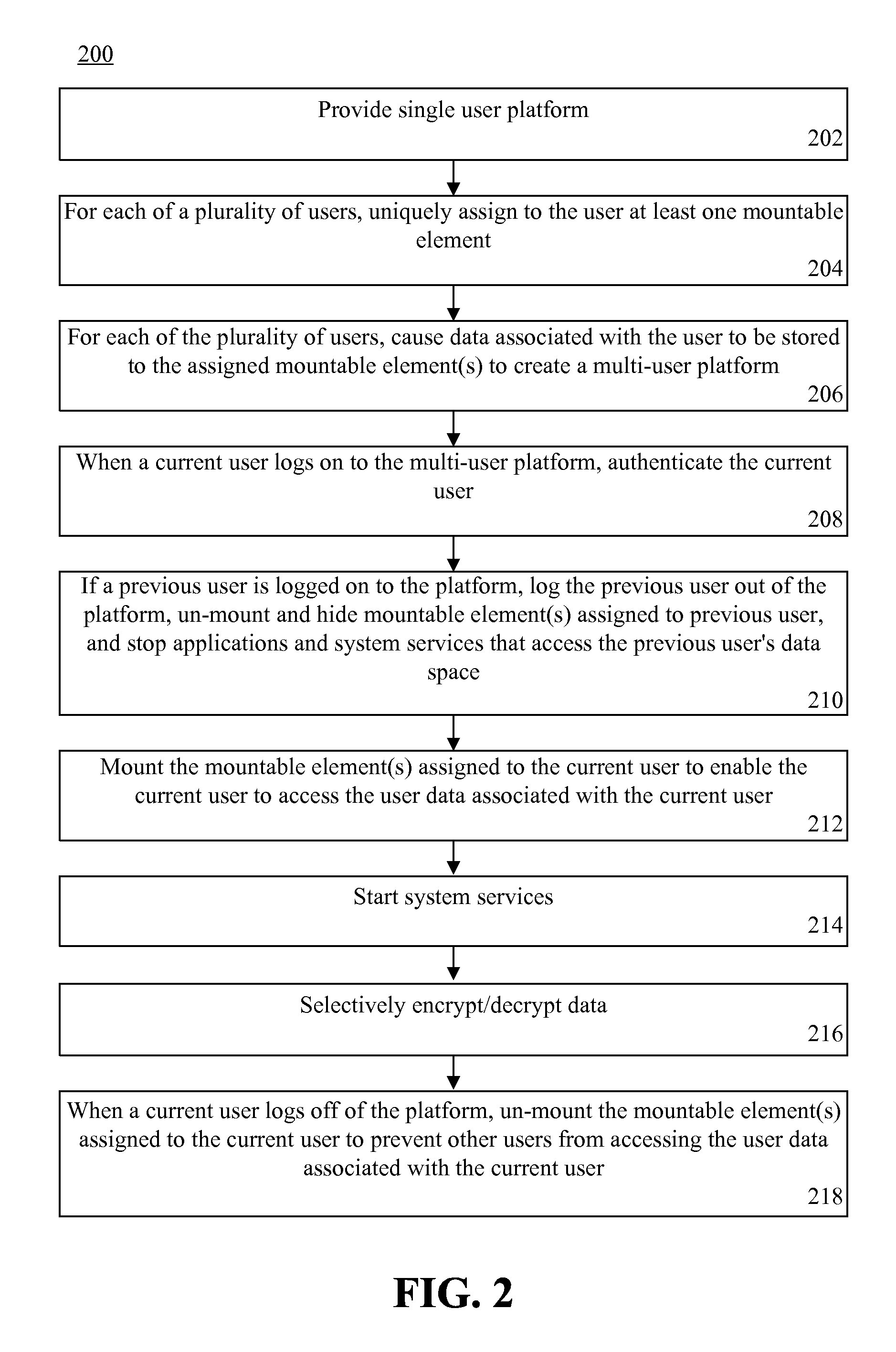
Creating distinct user spaces through mountable file systems
InactiveUS20120102564A1Digital data processing detailsUnauthorized memory use protectionFile systemComputer science
A method and a processing system for creating distinct user spaces. In a platform originally intended to be a single user platform, for each of a plurality of users, at least one mountable element can be uniquely assigned to the user and data associated with the user can be stored to the assigned mountable element to create a multi-user platform.
Owner:OPENPEAK LLC
Network device driver architecture
InactiveUS7451456B2Efficient and flexible accessEliminate bottlenecksDigital computer detailsMultiprogramming arrangementsZero-copyCombined use
The invention proposes a network device driver architecture with functionality distributed between kernel space and user space. The overall network device driver comprises a kernel-space device driver (10) and user-space device driver functionality (20). The kernel-space device driver (10) is adapted for enabling access to the user -space device driver functionality (20) via a kernel-space-user-space interface (15). The user-space device driver functionality (20) is adapted for enabling direct access between user space and the NIC (30) via a user-space-NIC interface (25), and also adapted for interconnecting the kernel-space-user-space interface (15) and the user-space-NIC interface (25) to provide integrated kernel -space access and user-space access to the NIC (30). The user-space device driver functionality (20) provides direct, zero-copy user-space access to the NIC, whereas information to be transferred between kernel space and the NIC will be “tunneled” through user space by combined use of the kernel-space device driver (10), the user-space device driver functionality (20) and the two associated interfaces (15,25).
Owner:TELEFON AB LM ERICSSON (PUBL)
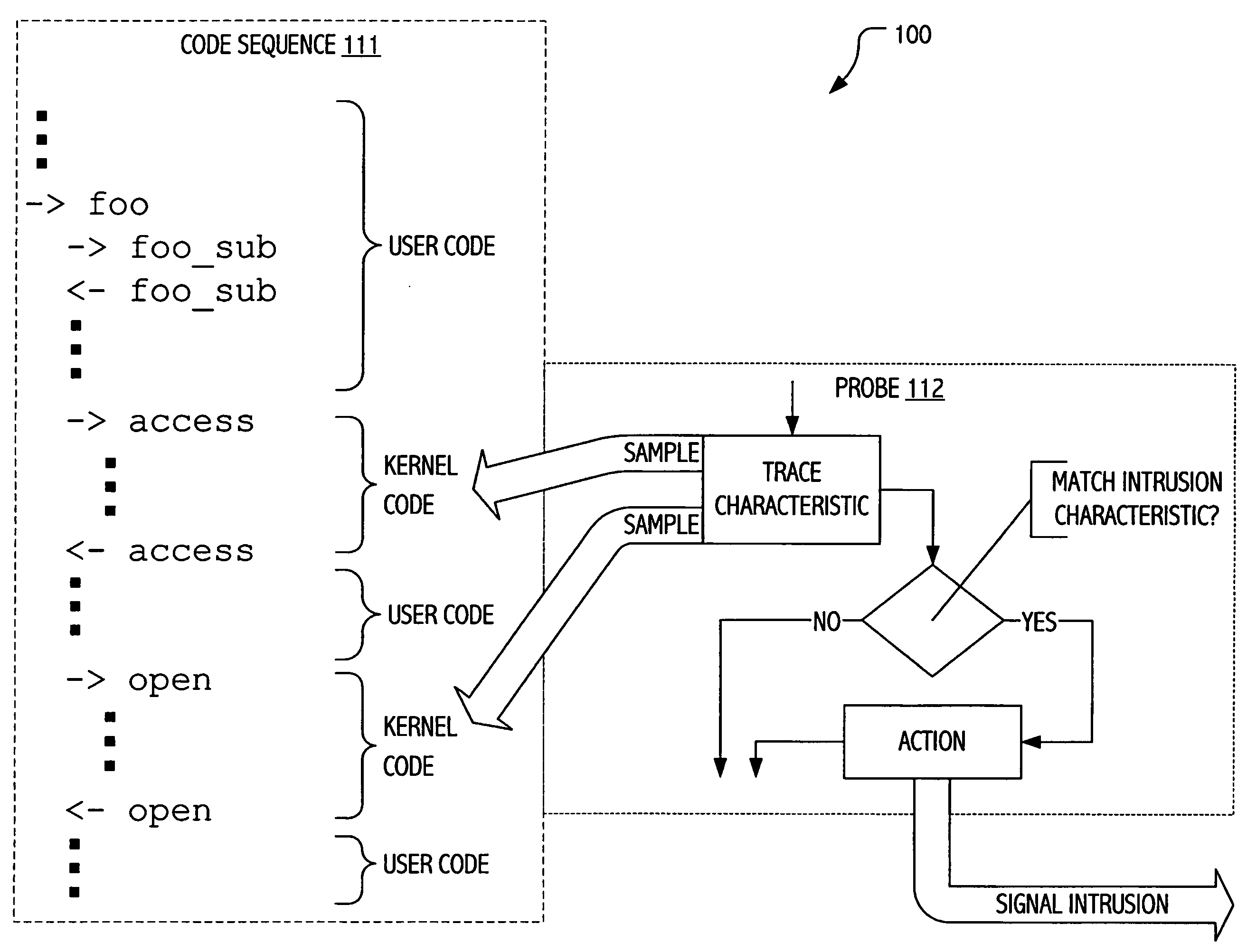
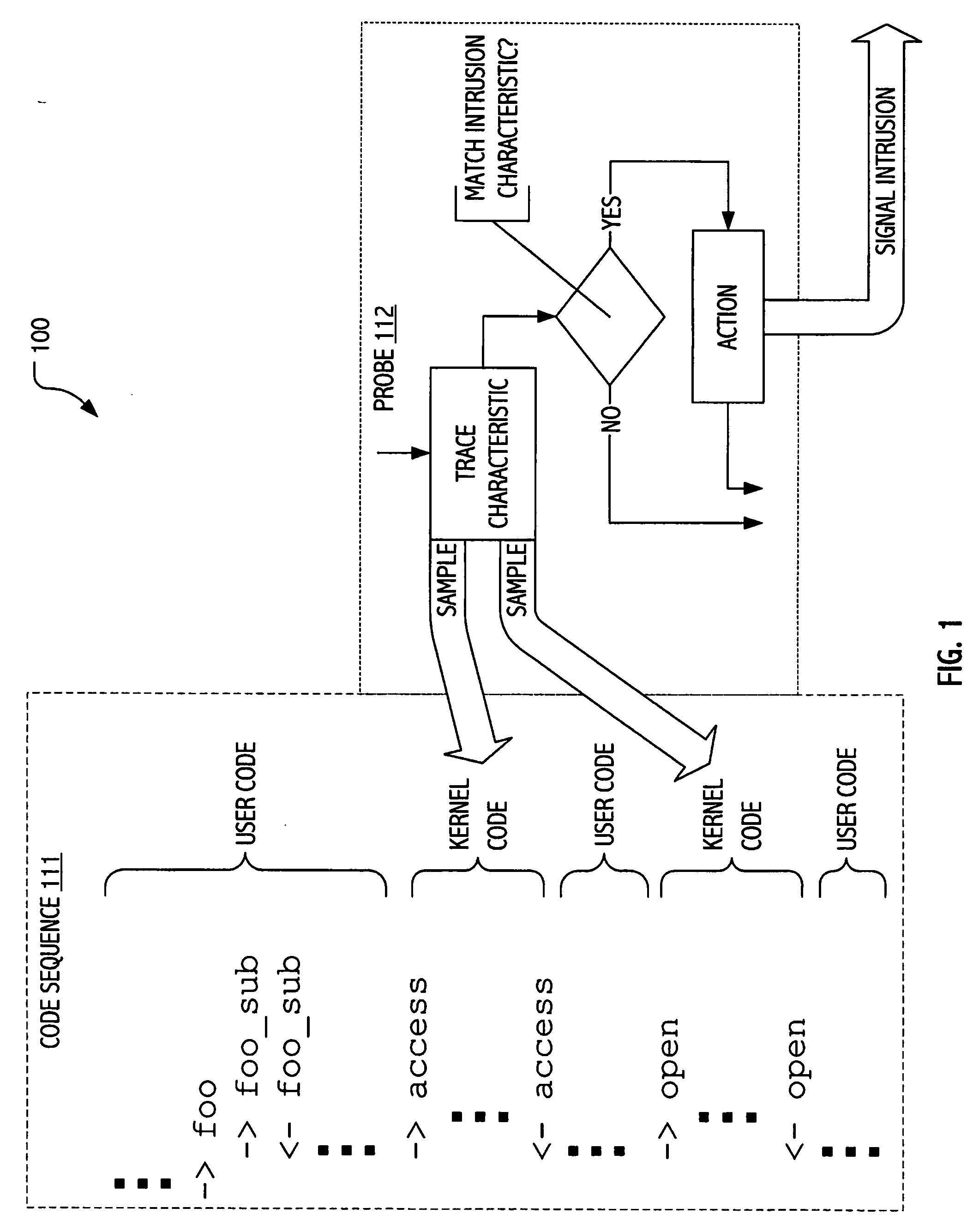
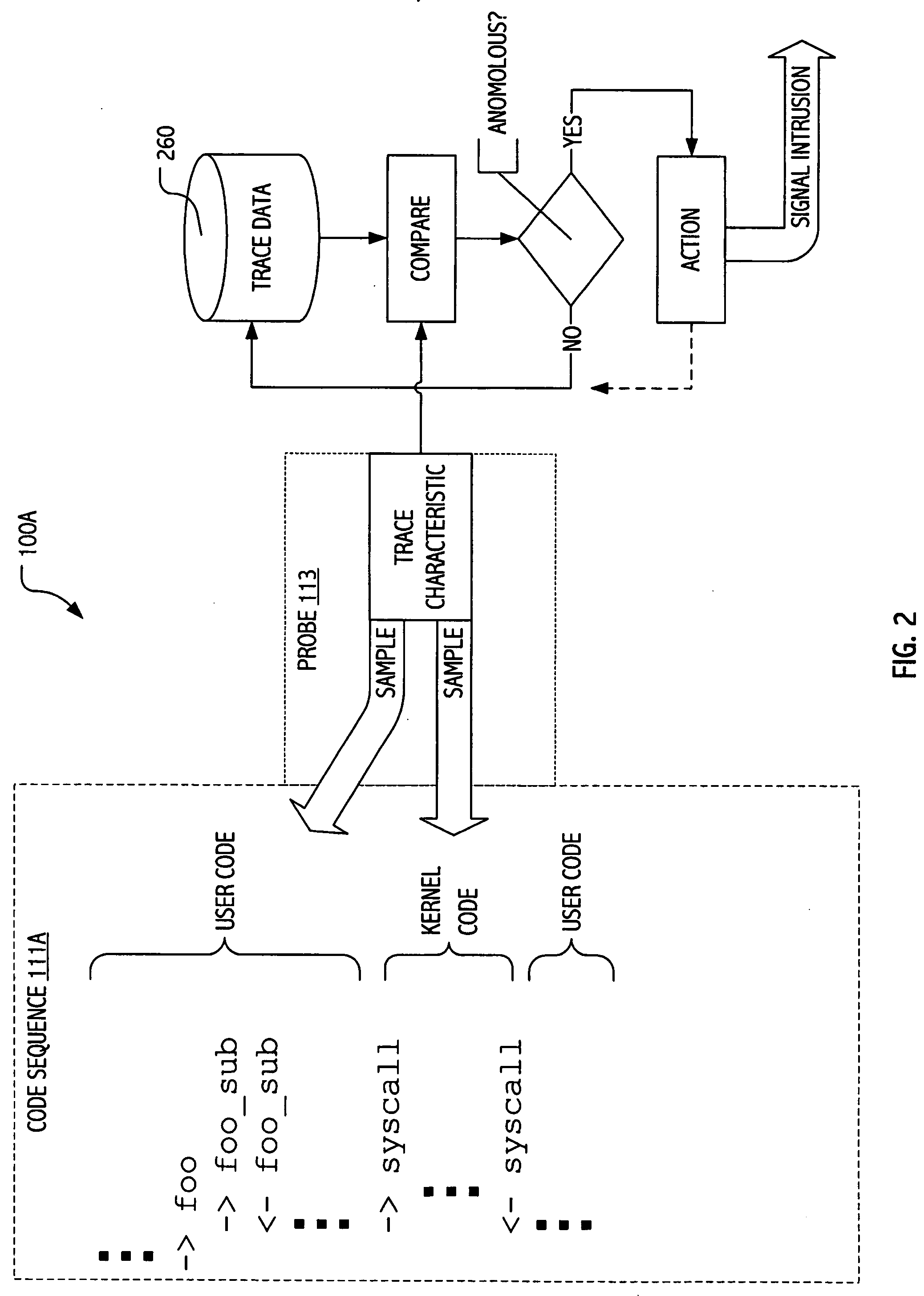
Intrusion detection using dynamic tracing
ActiveUS20070107058A1Reduce overheadPractical limitationMemory loss protectionError detection/correctionTime informationParallel computing
Techniques have been developed whereby dynamic kernel / user-level tracing may be employed to efficiently characterize runtime behavior of production code. Using dynamic tracing techniques, user space or kernel instruction sequences between system calls may be instrumented without access to source code. In some realizations, instrumentation may be interactively specified on a host system. In some realizations, instrumentation specifications may be supplied as functional definitions (e.g., as scripts and / or probe definitions) for installation on a host system. Using the developed techniques, data states, parameters passed and / or timing information may be sampled to provide more detailed insight into actual program behavior. In signature-oriented exploitations, more powerful intrusion signatures are possible. In anomaly-oriented exploitations, a more detailed “sense of self” may be developed to discriminate between normal and anomalous program behavior.
Owner:ORACLE INT CORP
Method for System Call Interception in User Space
InactiveUS20080250400A1Raise the level of performanceReduce performanceSpecific program execution arrangementsMemory systemsSystem callSignal processing
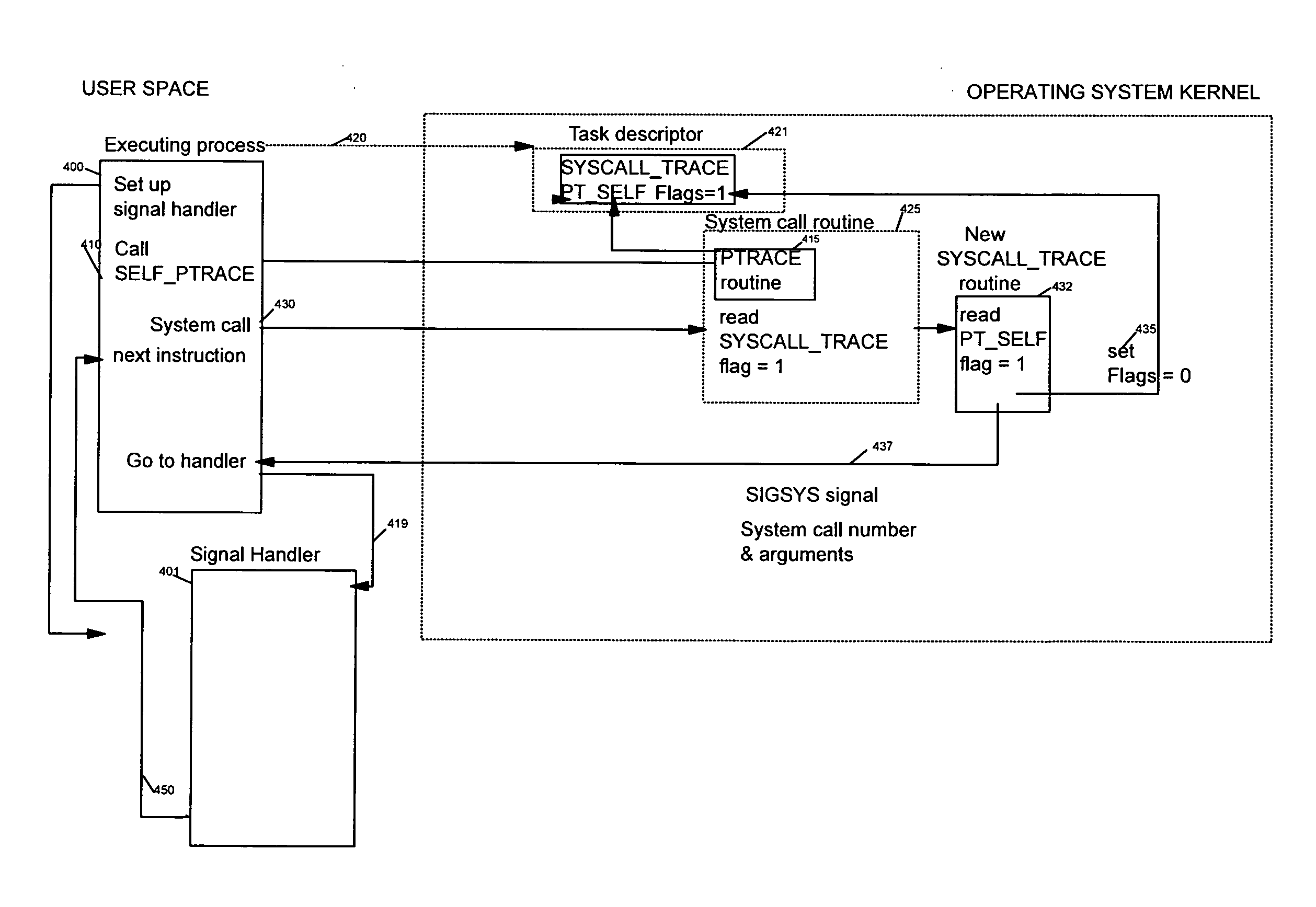
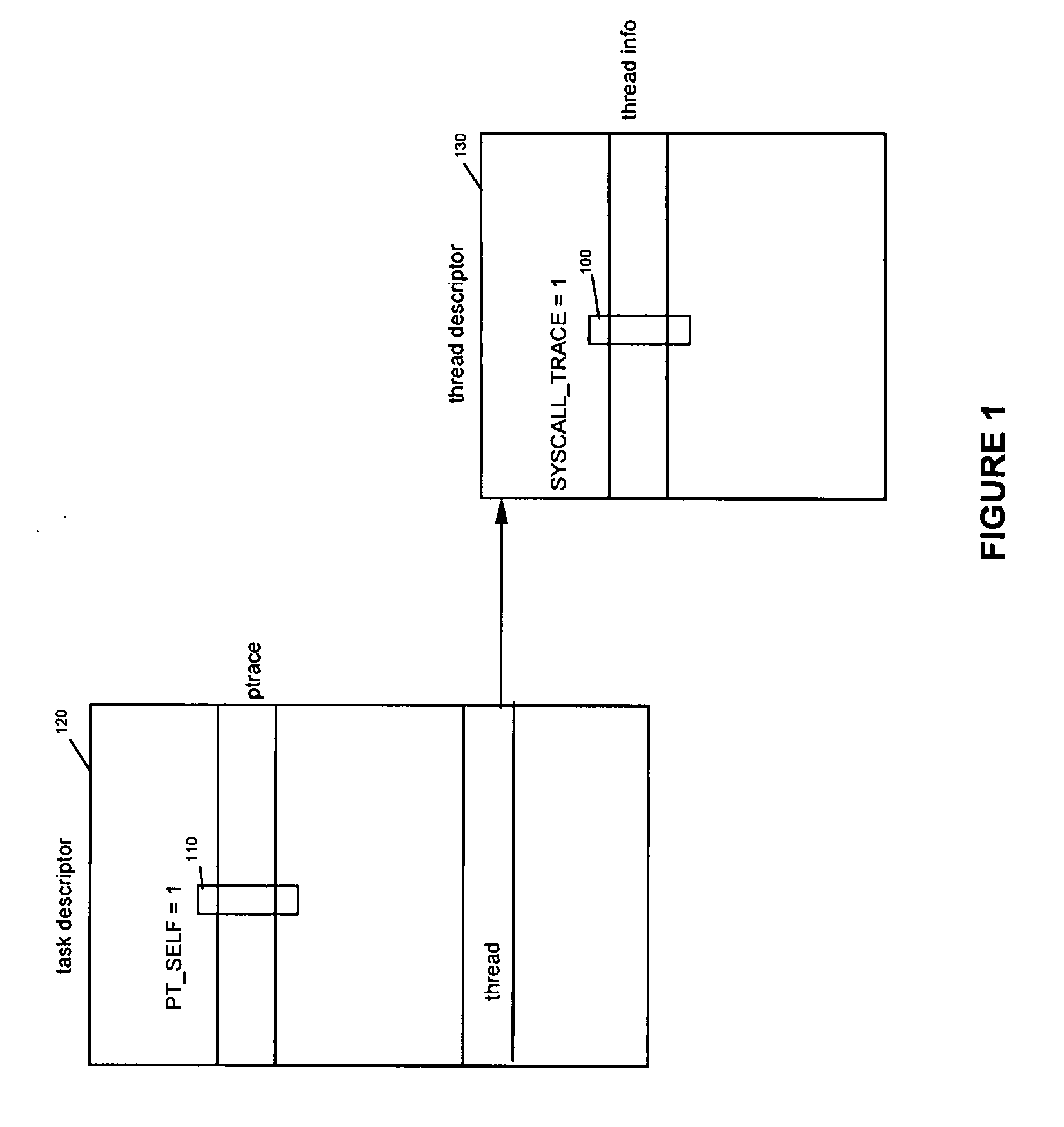
A method, and system for intercepting a system call performed by a process and for executing processing in relation with the intercepted system call from user space. The method comprises a first step for setting up, in the executing process, a signal handler performing processing in relation with an interception of a system call in the executing process upon reception of a specific signal. The executing process performs a ptrace system call with a new request, the self ptrace, which sets, in the task descriptor of the executing process, the system trace flag corresponding to the existing system trace ptrace request and set a new flag, the pt_self flag. When a system call is performed in the executing process, a new system call trace is executed testing if the pt_self flag is set. If the pt_self flag is set a specific signal is sent to the executing process itself and the handler which has been set up is executed in user space.
Owner:IBM CORP
Method and device for managing heterogeneous hybrid memory
ActiveCN104239225AFast data processingImpact of reduced data processing speedMemory adressing/allocation/relocationData processing systemBatch processing
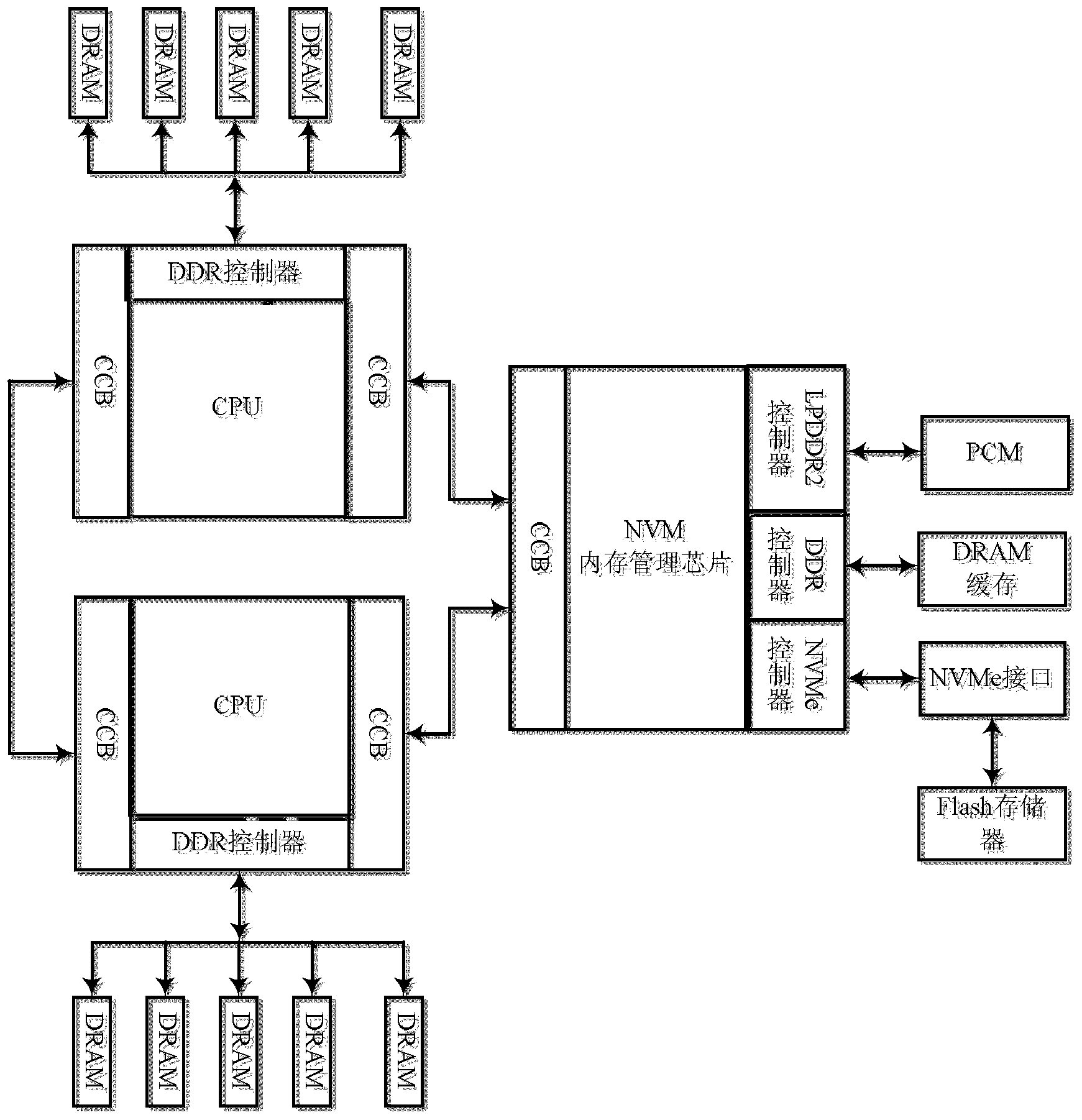
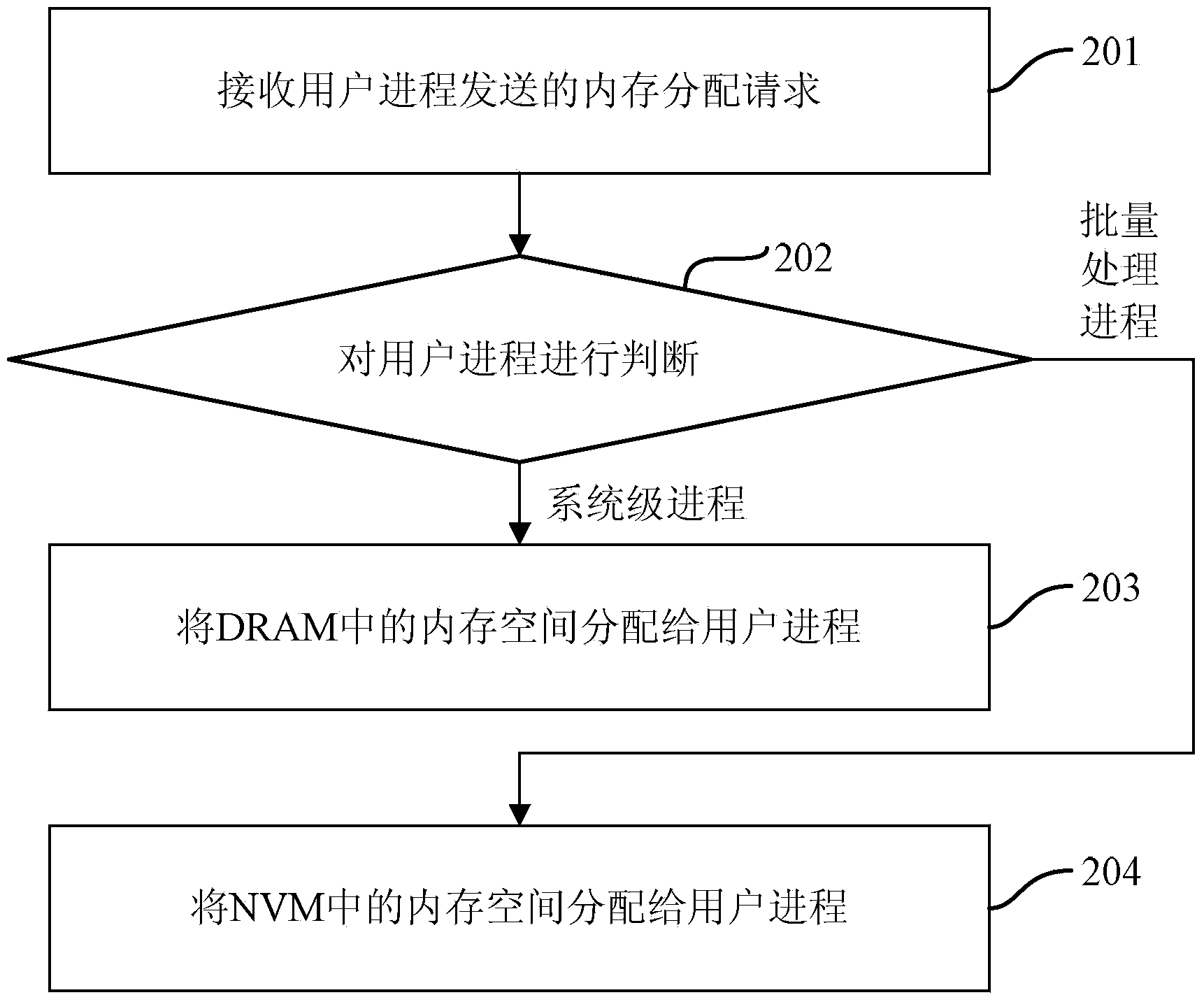
The invention discloses a method and a device for managing a heterogeneous hybrid memory. The heterogeneous hybrid memory comprises an NVM (Non-Volatile Memory) and a DRAM (Dynamic Random Access Memory). The method comprises the following steps: receiving a memory allocation request sent by a user process, and judging the user process; if the user process is a system-level process, allocating the memory space of the DRAM to the user space; if the user process is a batch processing process, allocating the memory space of the NVM to the user process. By virtue of the memory management mechanism, the system-level process is capable of performing data processing in the DRAM with relatively high access rate, the batch processing process is capable of performing data processing in the NVM, so that influence of the access speed difference between the DRAM and the NVM on the data processing speed is reduced, and the data processing speed of the user process and the overall processing performance of the system are enhanced.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
High-speed capturing method of bottom-layer data packet based on Linux
InactiveCN101841470AOvercome disadvantagesImprove acquisition efficiencyMemory adressing/allocation/relocationData switching networksOriginal dataGNU/Linux
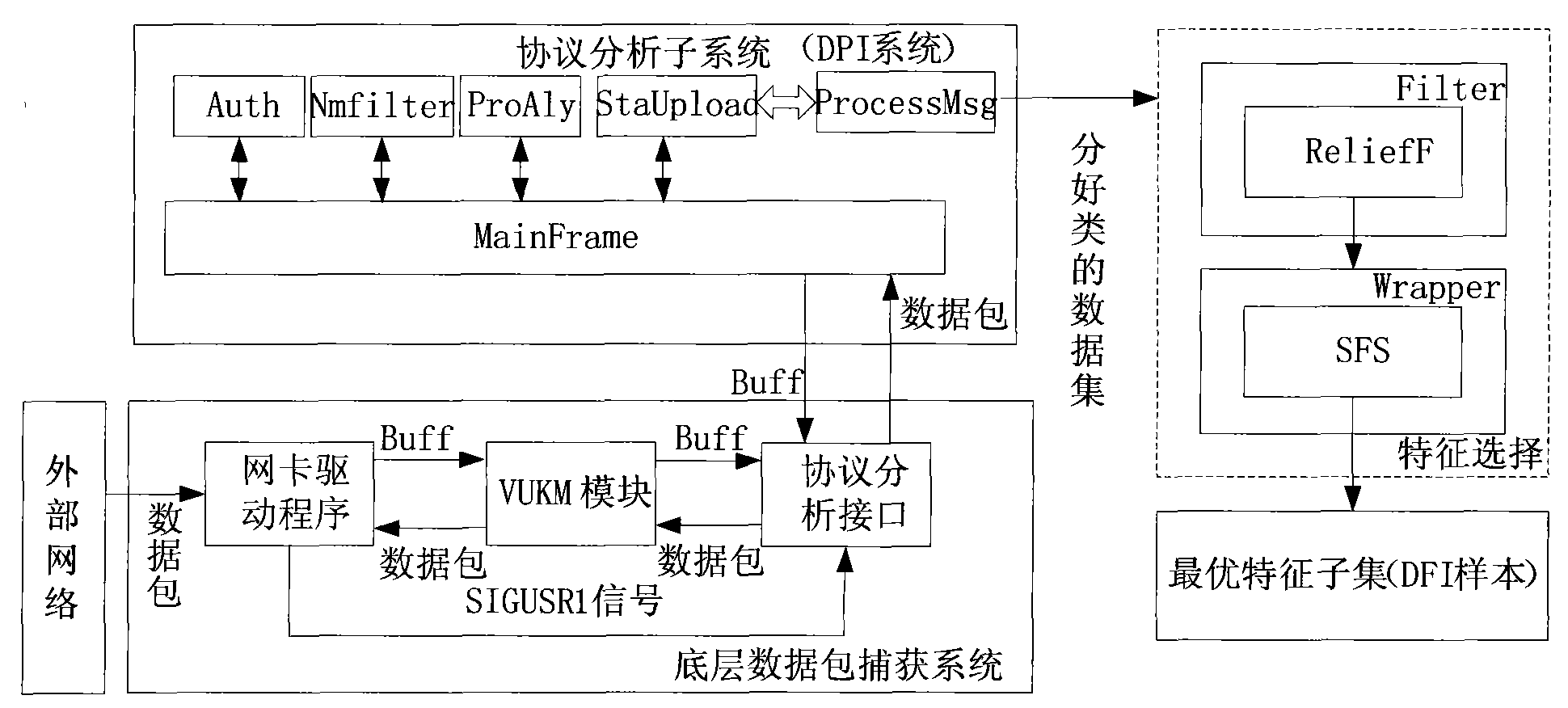
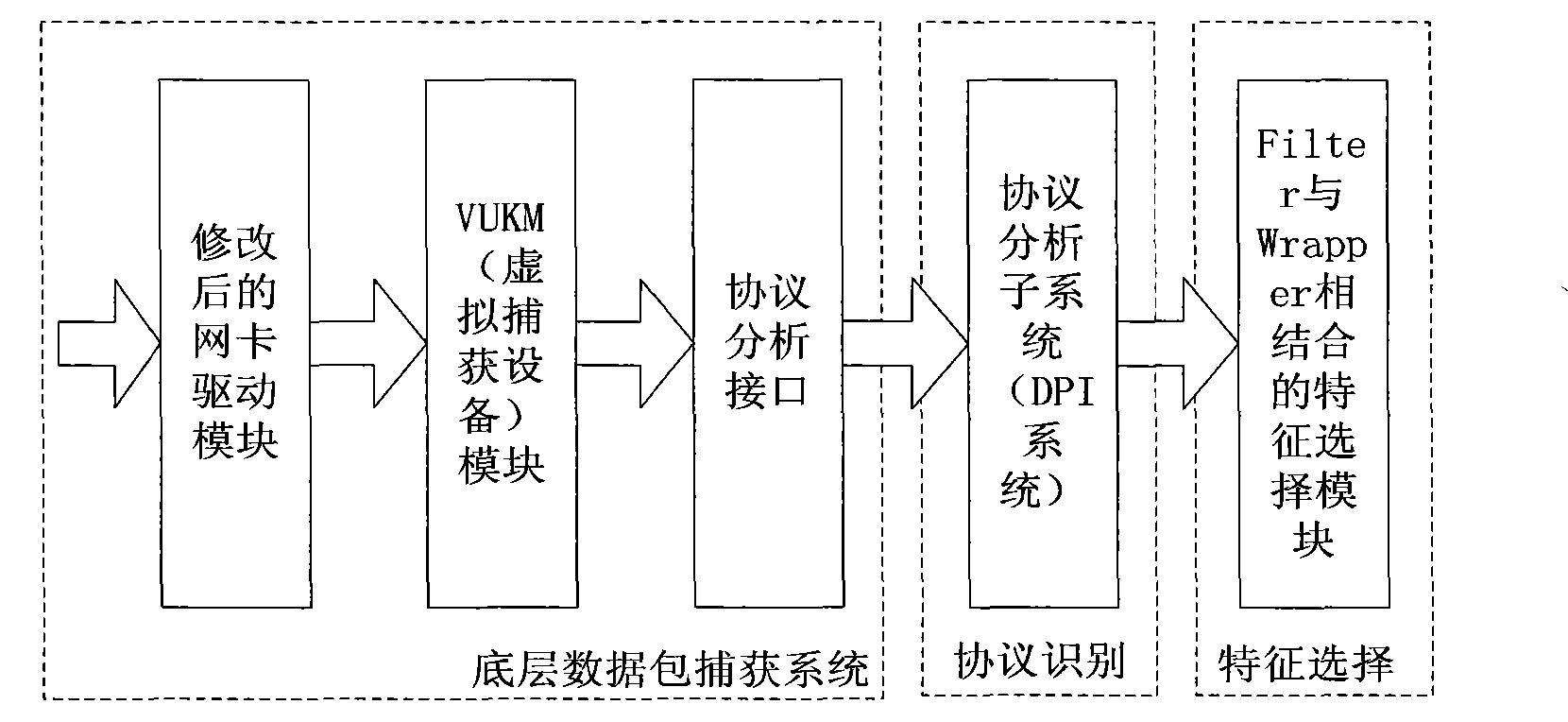
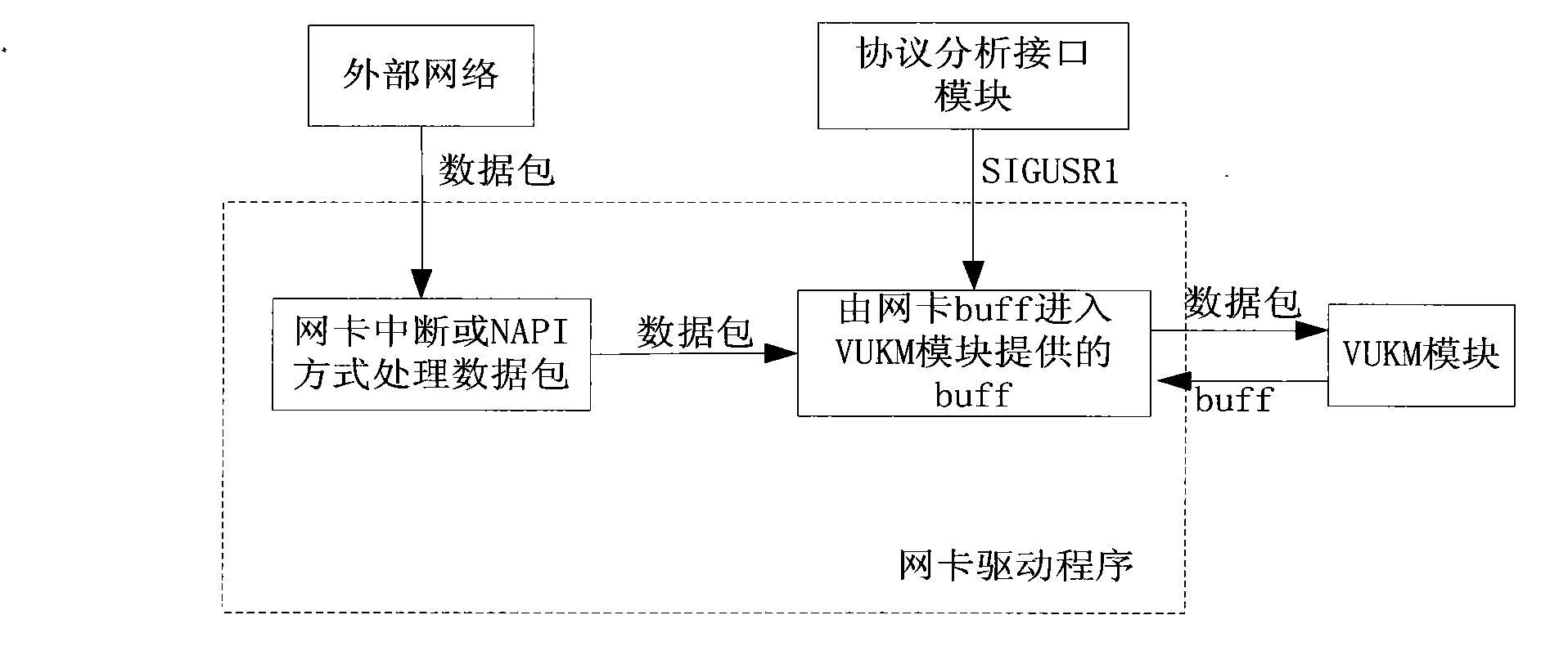
The invention provides a high-speed capturing method of a bottom-layer data packet based on Linux. By setting a virtual capturing equipment module (VUKM module) to modify a network card driver, the high-speed capturing method leads the data packet reaching to a network card to be capable of bypassing a kernel protocol to be directly passed to a subsequence module for processing so as to realize memory sharing of a user space and a kernel space; and the kernel space transmits the data packet to an upper-layer analysis processing interface module at a high speed, and provides a mechanism for leading an upper-layer application program and the network card to access the VUKM module in a conflict-free manner so as to make further processing to the captured data packet. The high-speed capturing method can acquire the original data packet by the network card at a high speed under the gigabit network environment, and can overcome the defect of the traditional data packet capturing technology, thus improving the acquisition efficiency.
Owner:SOUTHEAST UNIV
System and Method for WORM data storage
ActiveUS20080172563A1Digital data information retrievalEncryption apparatus with shift registers/memoriesVirtual file systemOperational system
A system and method for Write Once, Read Many (WORM) compliant storage is disclosed. A storage administrator in user space is employed as an interface between the kernel space WORM VFS and the user applications. The storage administrator accesses the WORM VFS through the operating system's Virtual File System. The WORM VFS comprises of three layers: a data encryption\compression layer, the WORM filesystem layer and a logical volume manager. The data encryption\compression layer preprocesses the data as it moves between from the user space and the WORM filesystem layer. The WORM filesystem layer stores the compressed and encrypted data on the physical disk drives in a specialized disk format. The logical volume manager manages the physical disk drives. A NVRAM journal aids in crash recovery.
Owner:STOKES TERRY LEE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com