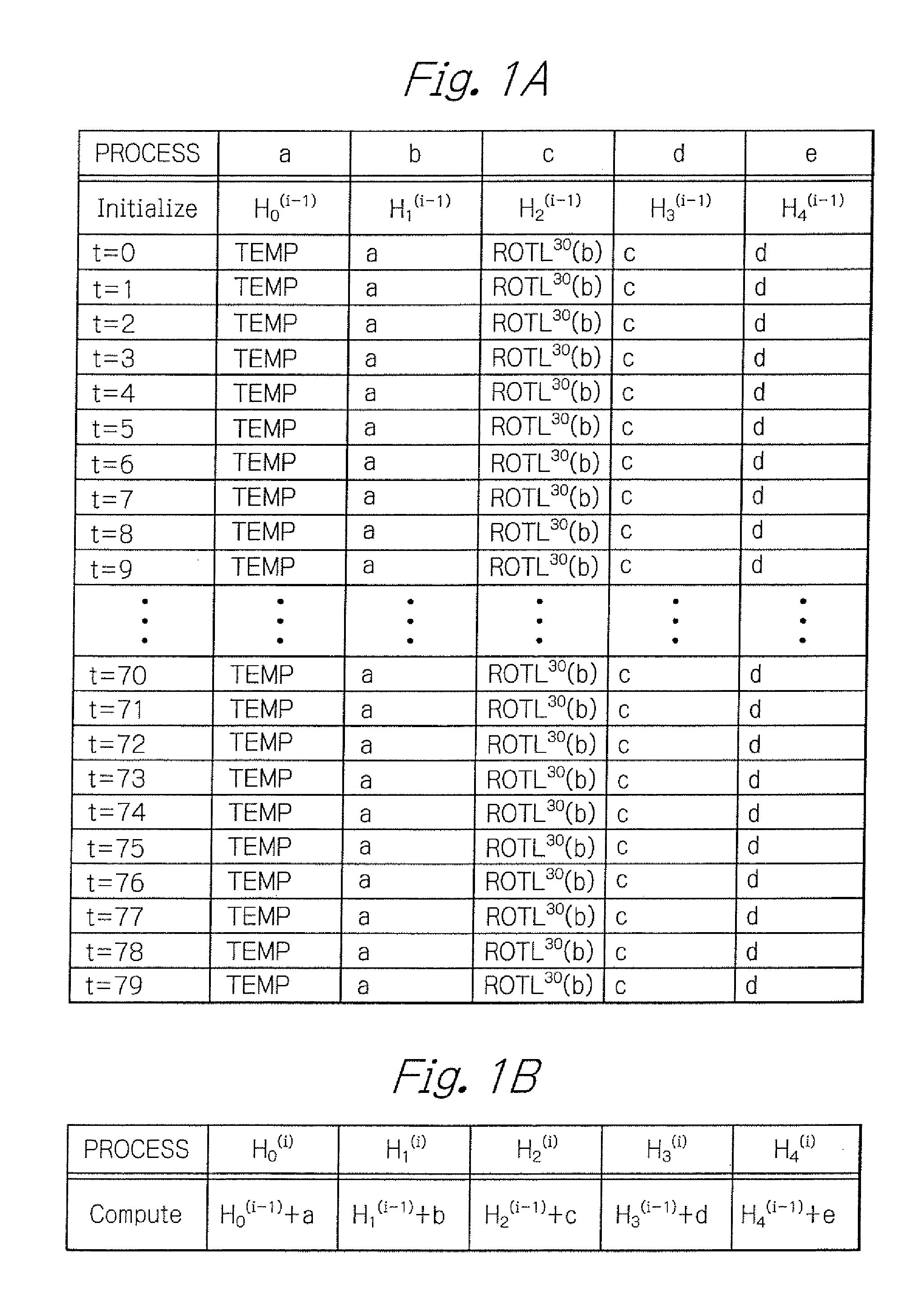
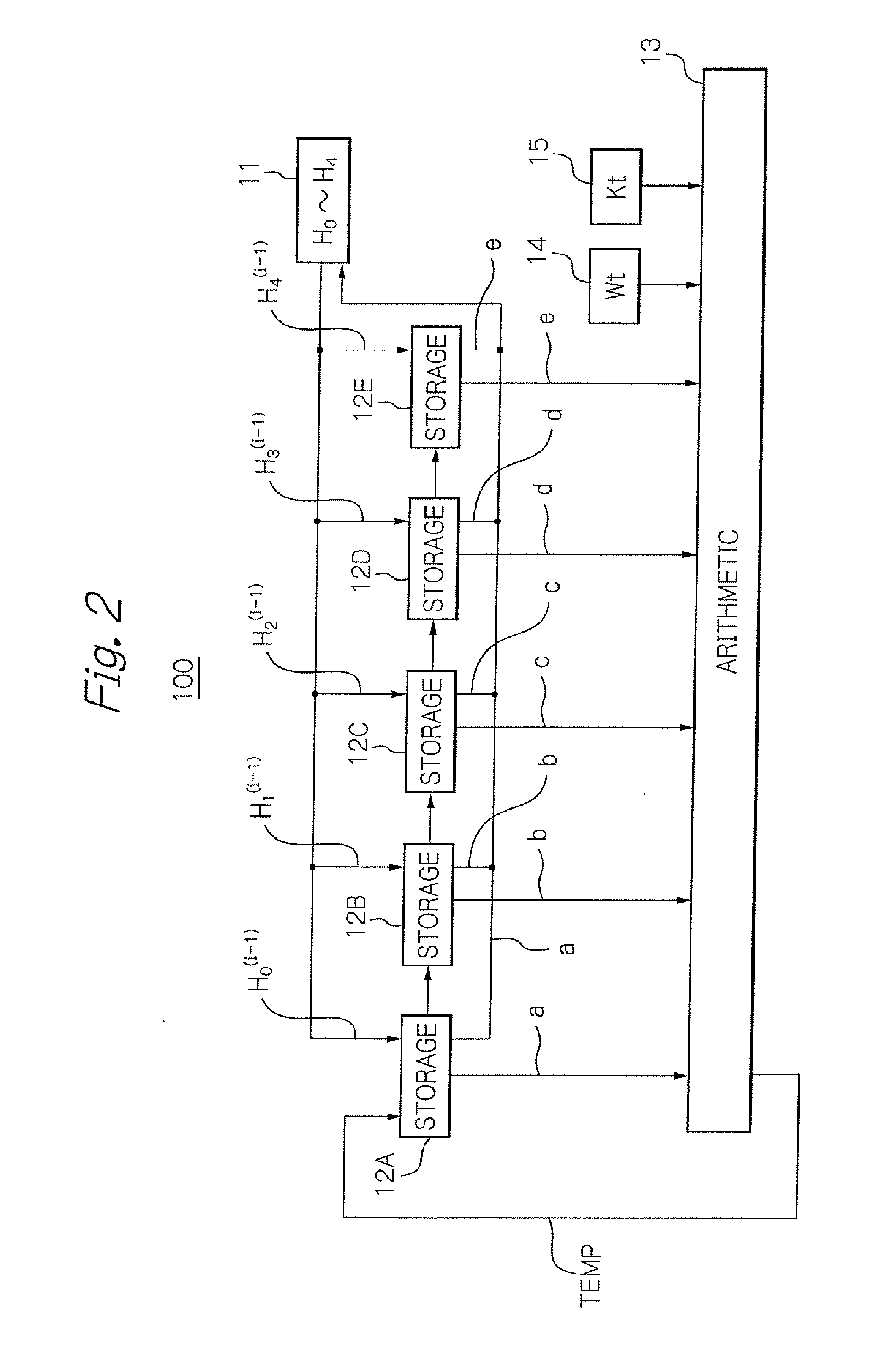
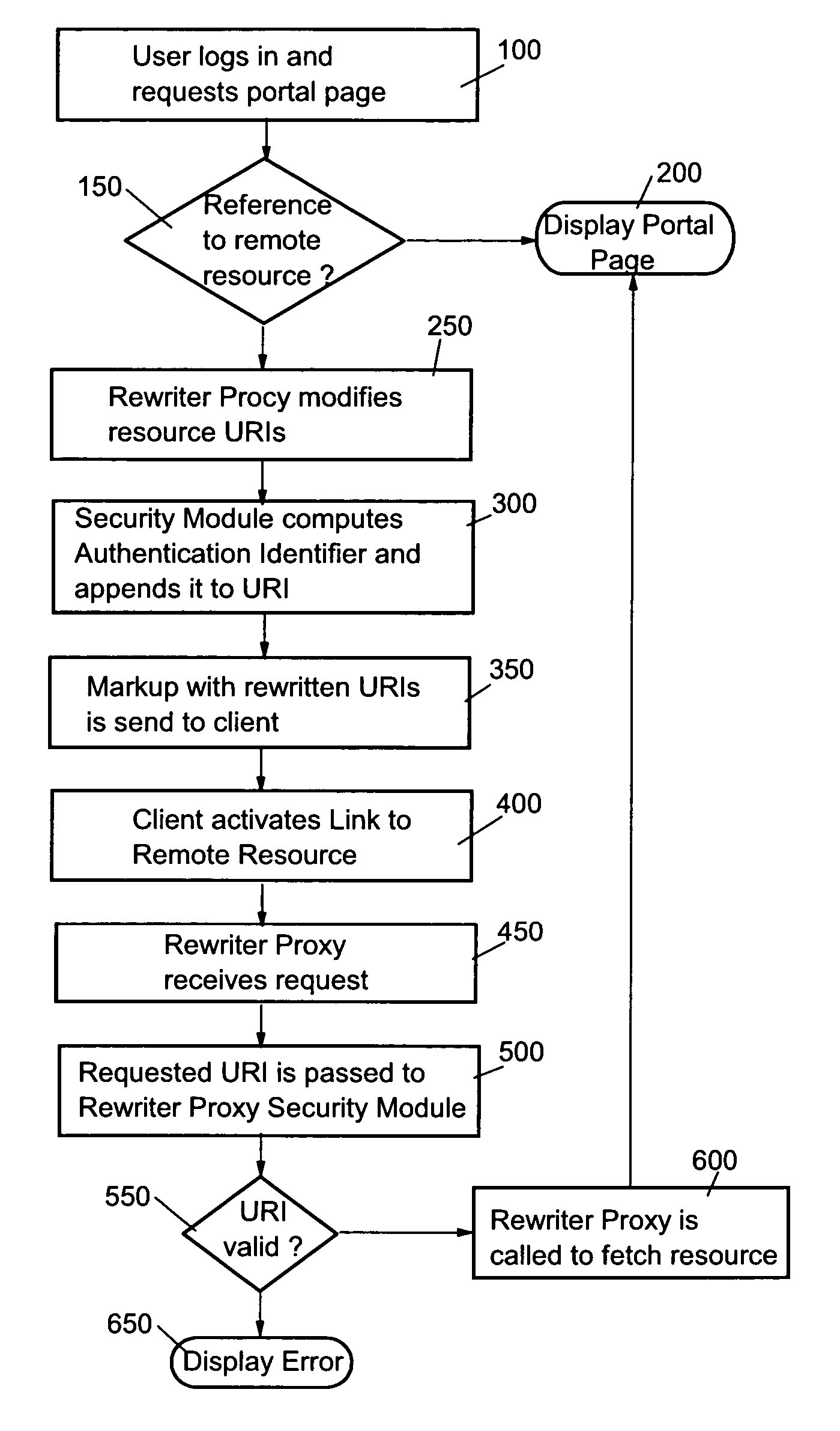
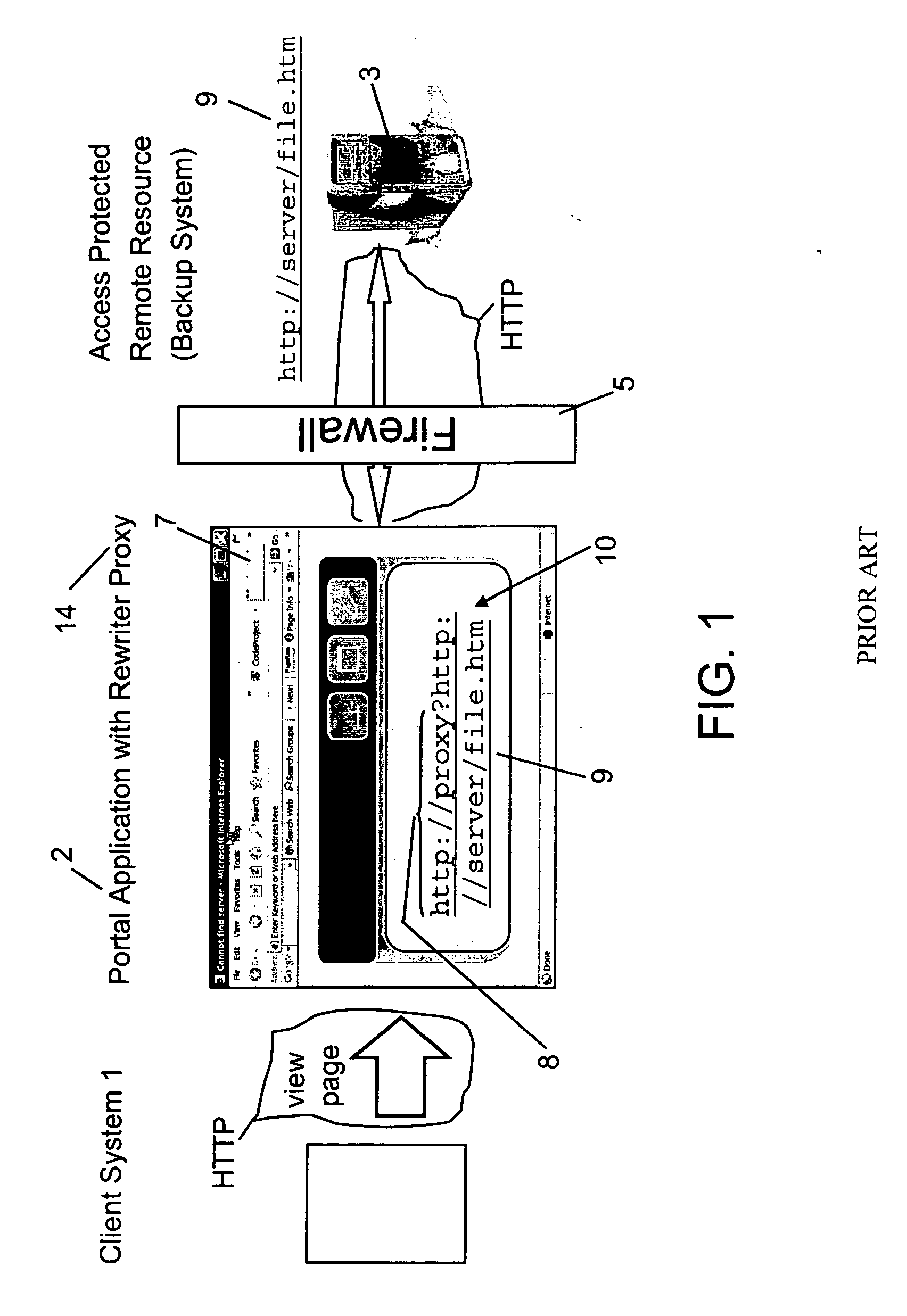
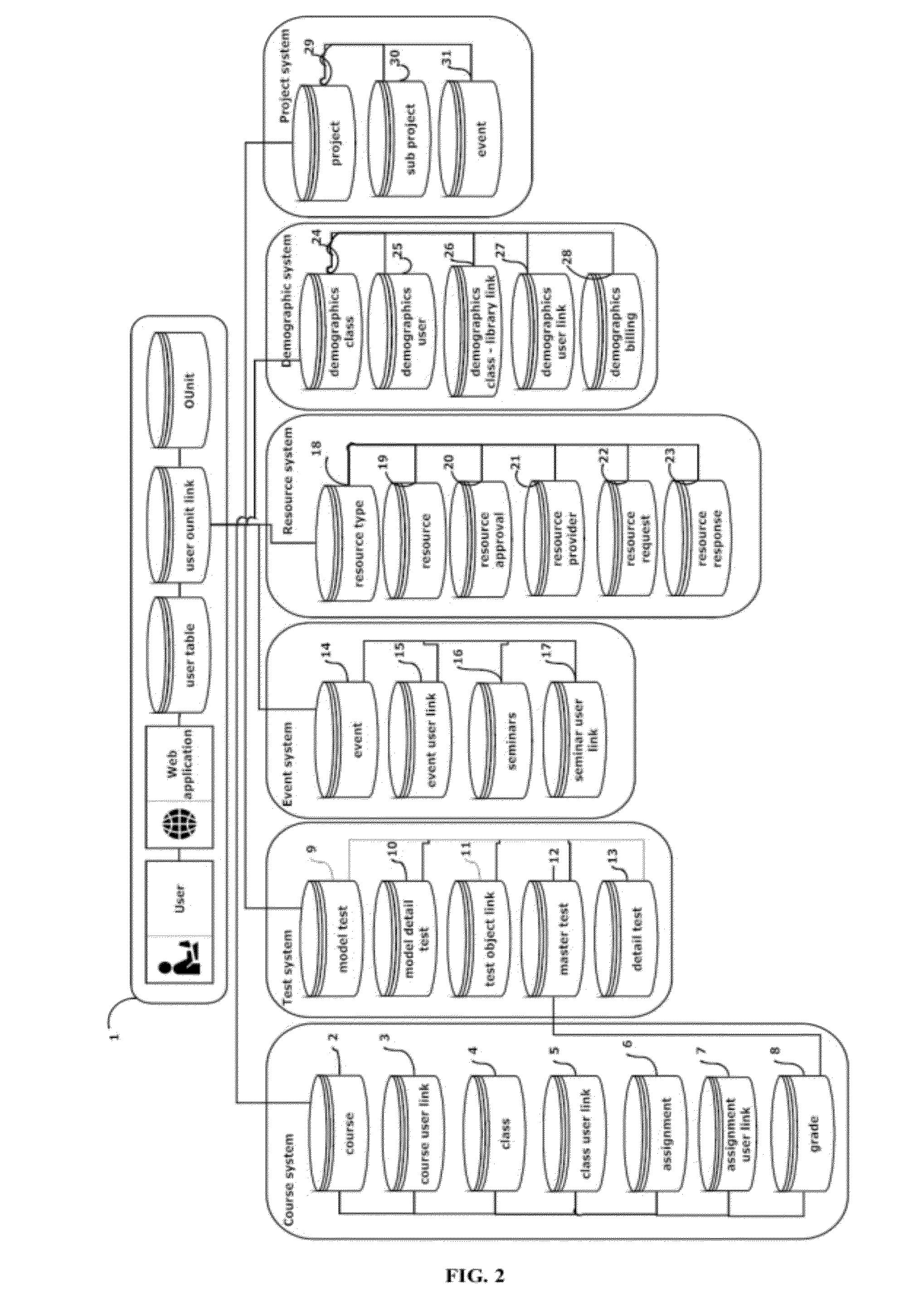
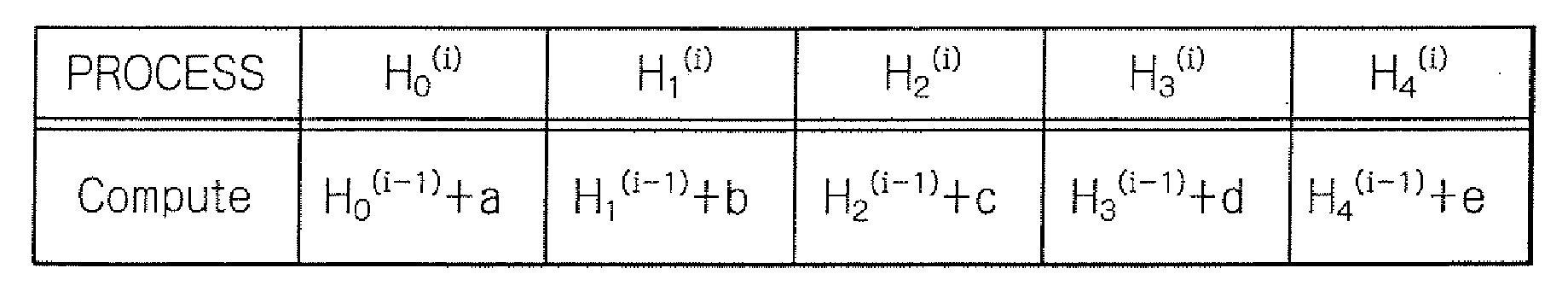Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
179 results about "Secure Hash Algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
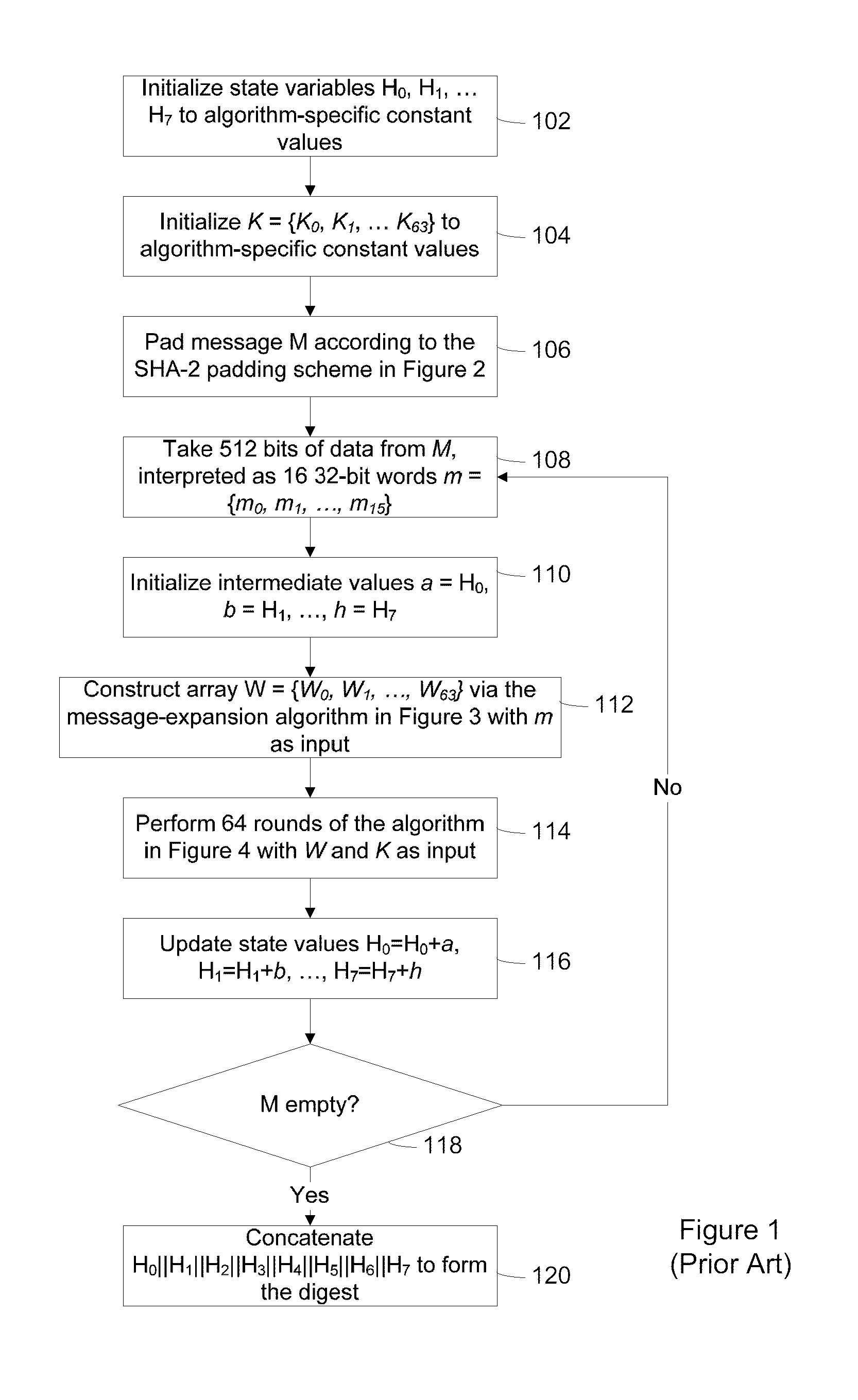
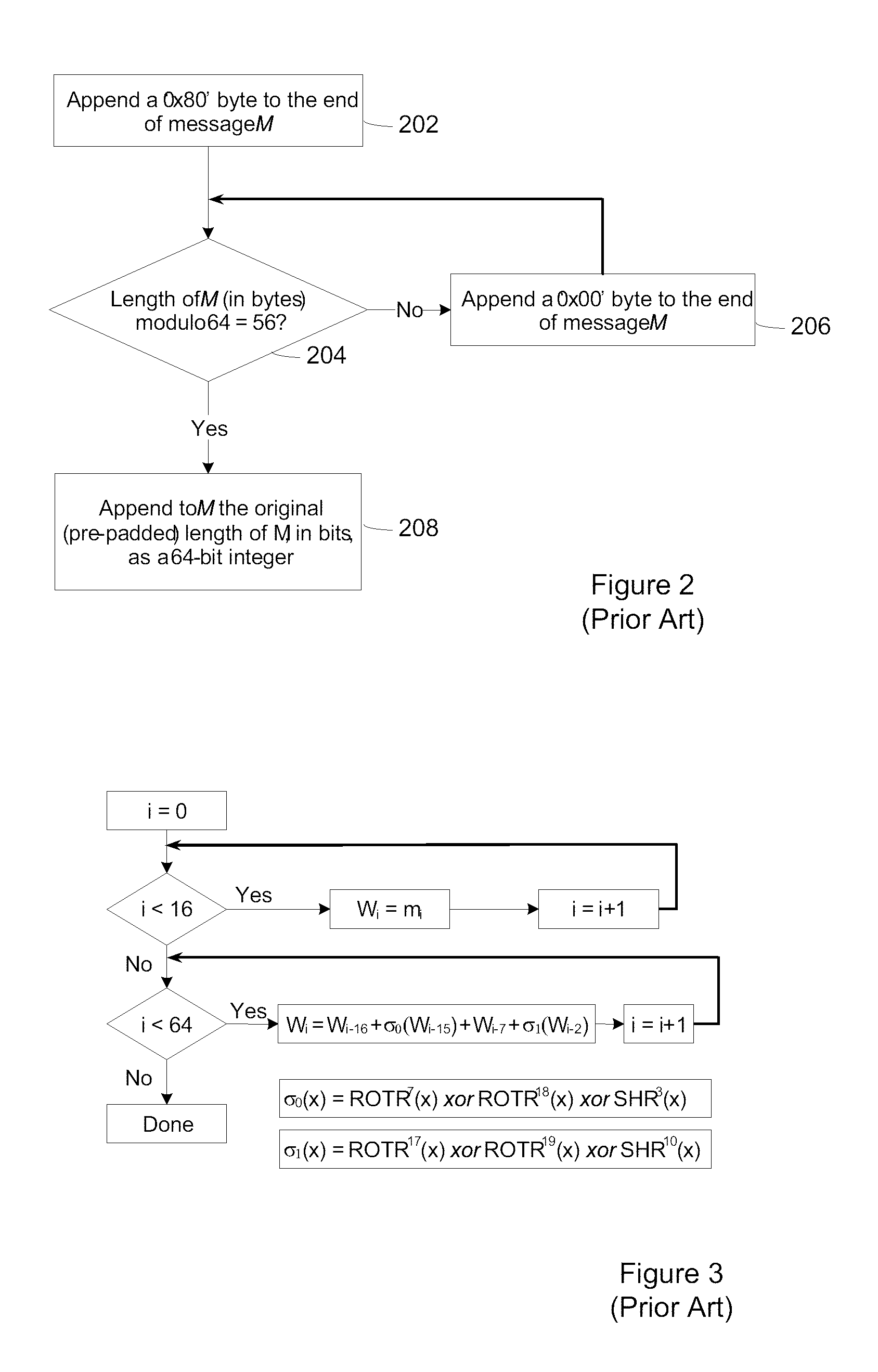
The Secure Hash Algorithm is a family of cryptographic hash functions published by the National Institute of Standards and Technology as a U.S. Federal Information Processing Standard, including: SHA-0: A retronym applied to the original version of the 160-bit hash function published in 1993 under the name "SHA". It was withdrawn shortly after publication due to an undisclosed "significant flaw" and replaced by the slightly revised version SHA-1. SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010. SHA-2: A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size; SHA-256 uses 32-bit words where SHA-512 uses 64-bit words. There are also truncated versions of each standard, known as SHA-224 and SHA-384. These were also designed by the NSA. SHA-3: A hash function formerly called Keccak, chosen in 2012 after a public competition among non-NSA designers.
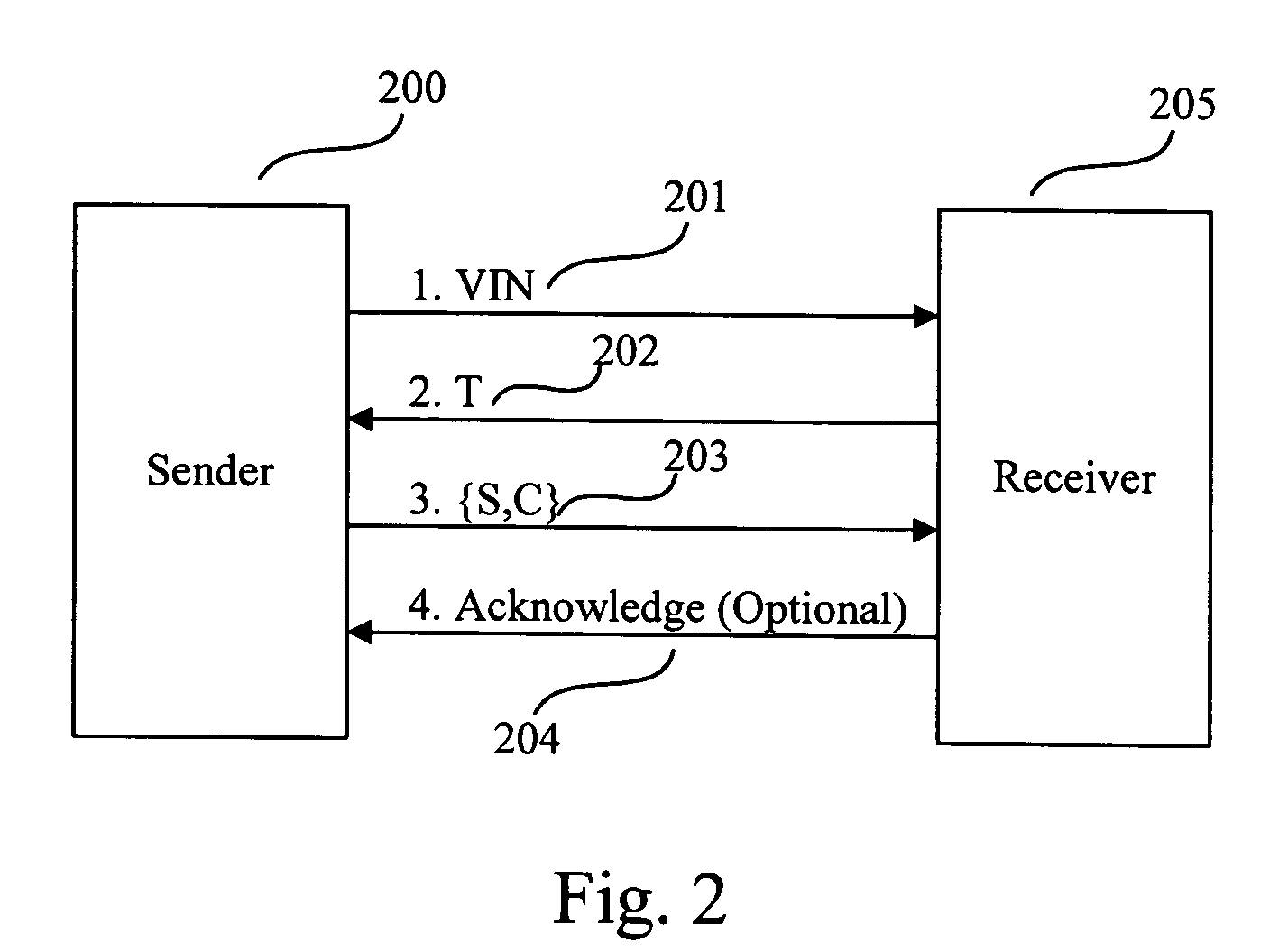
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
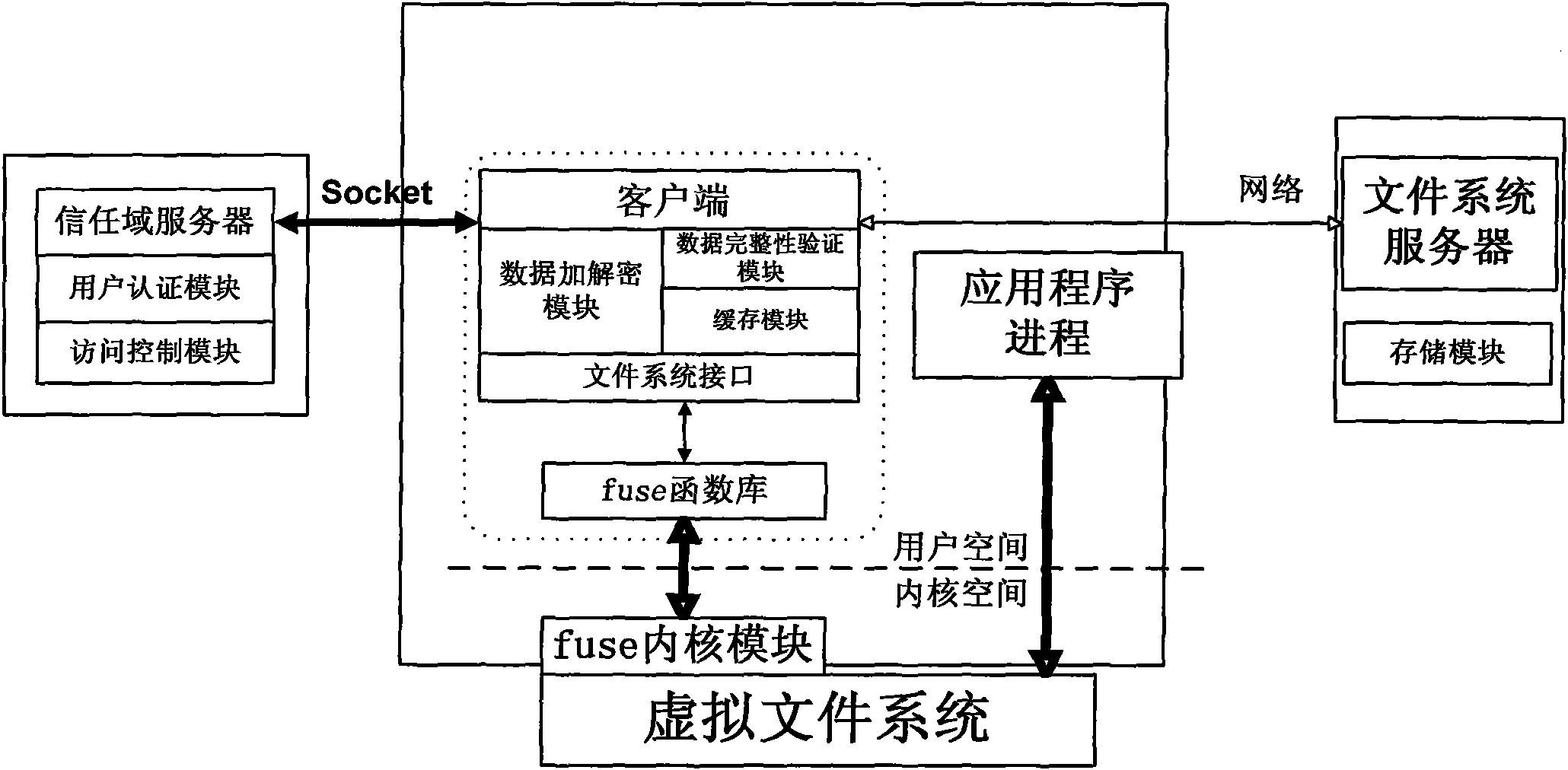
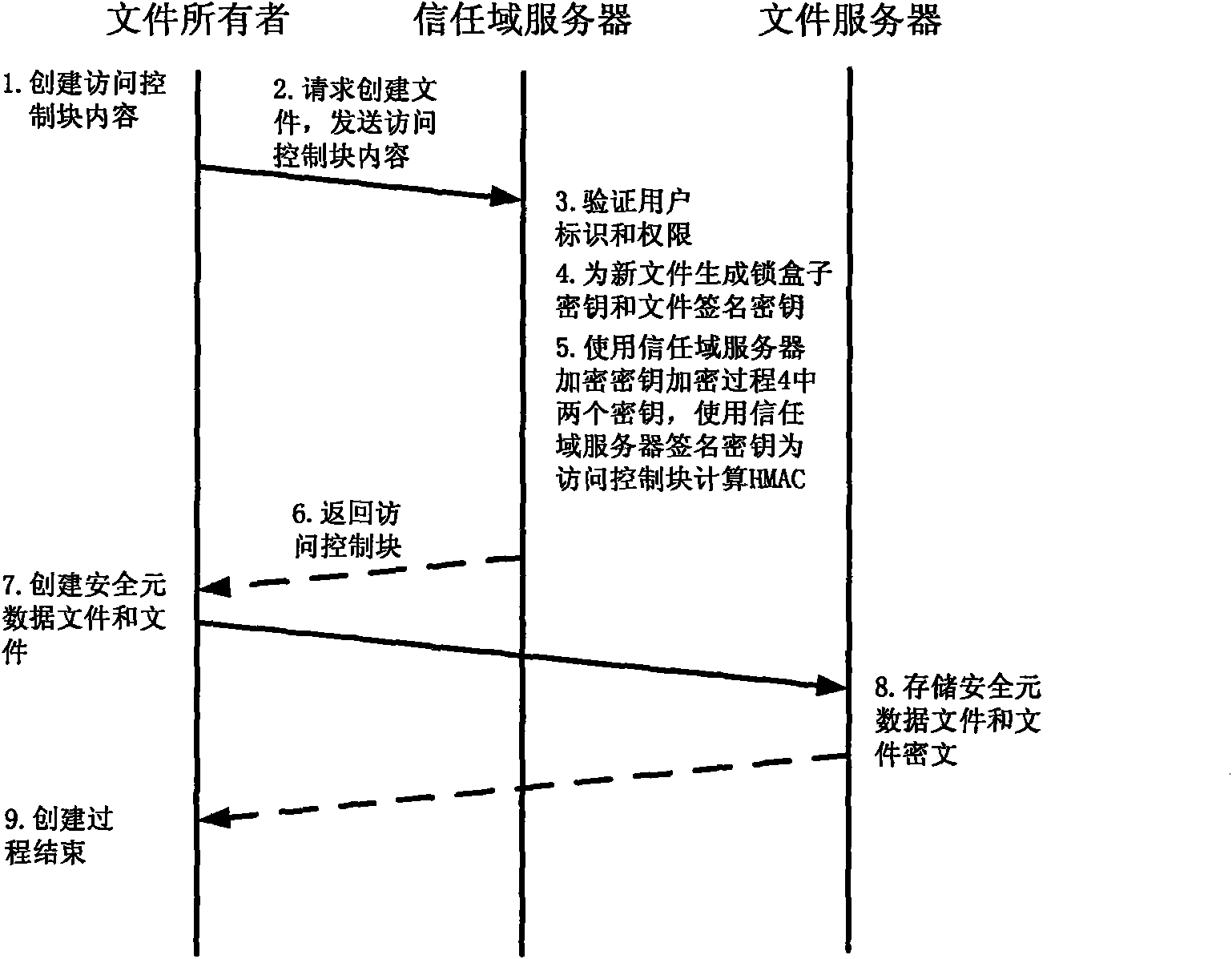
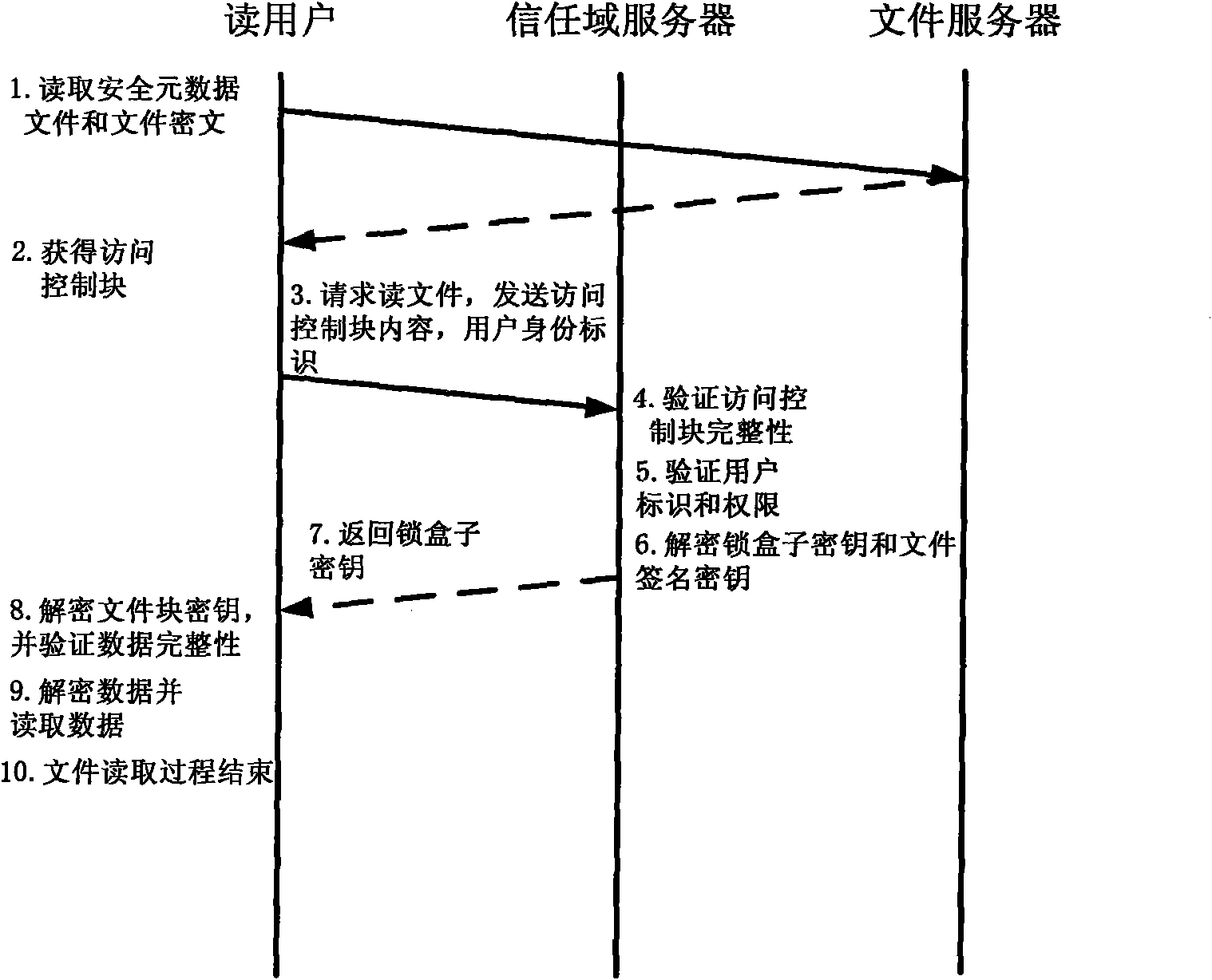
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
Method and a circuit for sha operation with power saved
InactiveUS20080107259A1Reduce power consumptionPublic key for secure communicationUser identity/authority verificationData segmentComputer science
A Secure Hash Algorithm (SHA) operation circuit includes plural storages for storing the variables of the SHA calculation, a permutation section for permuting the output signals of the storages, and an arithmetic unit for calculating a temporary value by the use of the output signals of the storages and a data segment successively extracted from input data from which the hash value is to be obtained. When each data segment is processed, some of the storages are supplied with no clock signal and thereby maintain the values stored therein without change. The SHA operation circuit is thus capable of saving power.
Owner:LAPIS SEMICON CO LTD
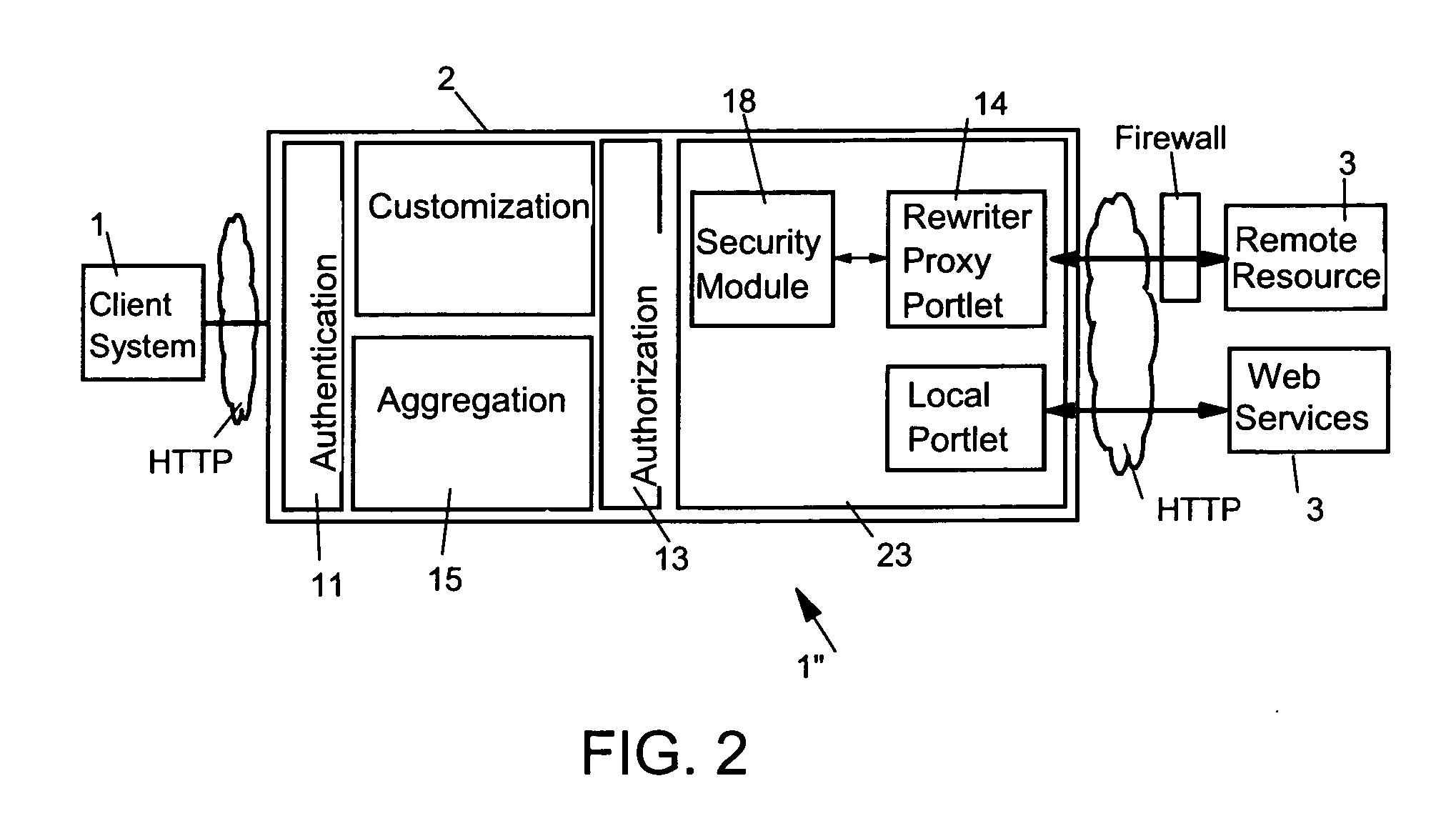
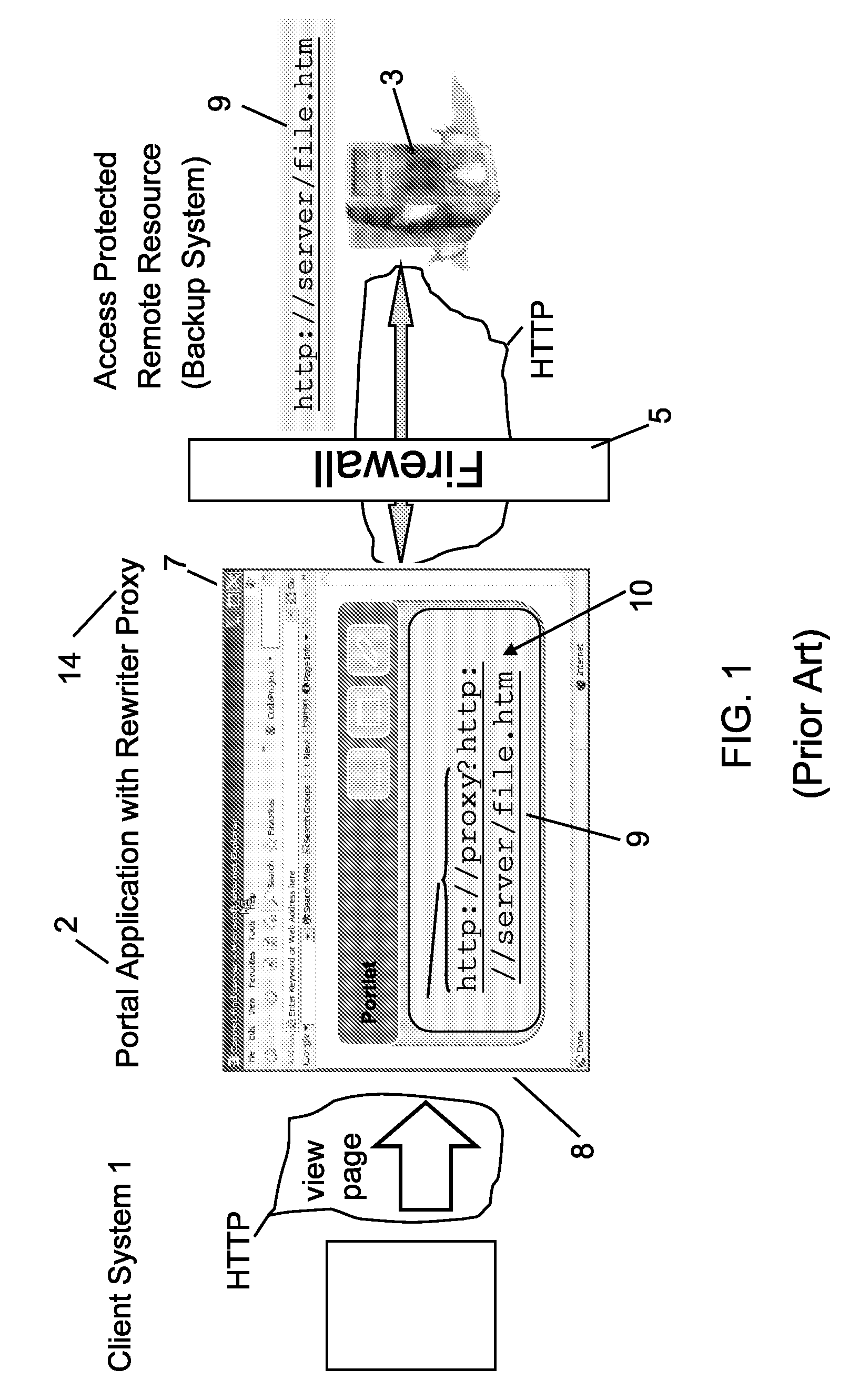
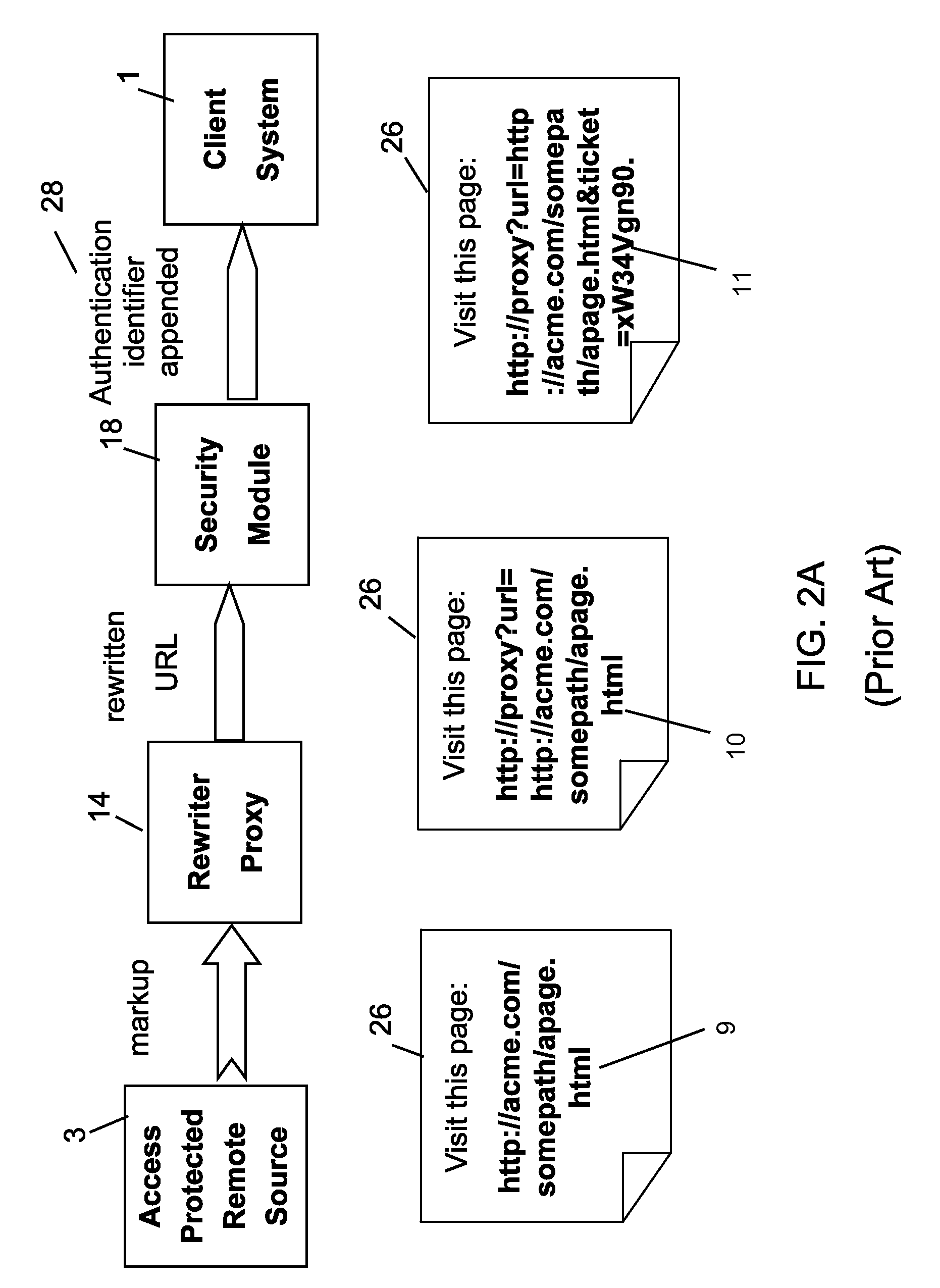
Controlling access of a client system to an access protected remote resource
InactiveUS20050198332A1Digital data processing detailsMultiple digital computer combinationsWeb applicationClient-side
The present invention provides a security module for Web application, especially a portal application, using a rewriter proxy. The security module ensures that the rewritten URIs are appended by an authentication identifier for determining whether the rewritten URI has not been changed. Preferably, the authentication identifier can be generated by applying a secure hash algorithm and / or secret key to the original URIs of the remote resource or the entire rewritten URIs. When a client activates those URIs, a request is sent to the rewriter proxy. Before a connection to the access protected remote resource is established, the security module validates whether the URIs contained in the user client request have been changed by the user.
Owner:IBM CORP
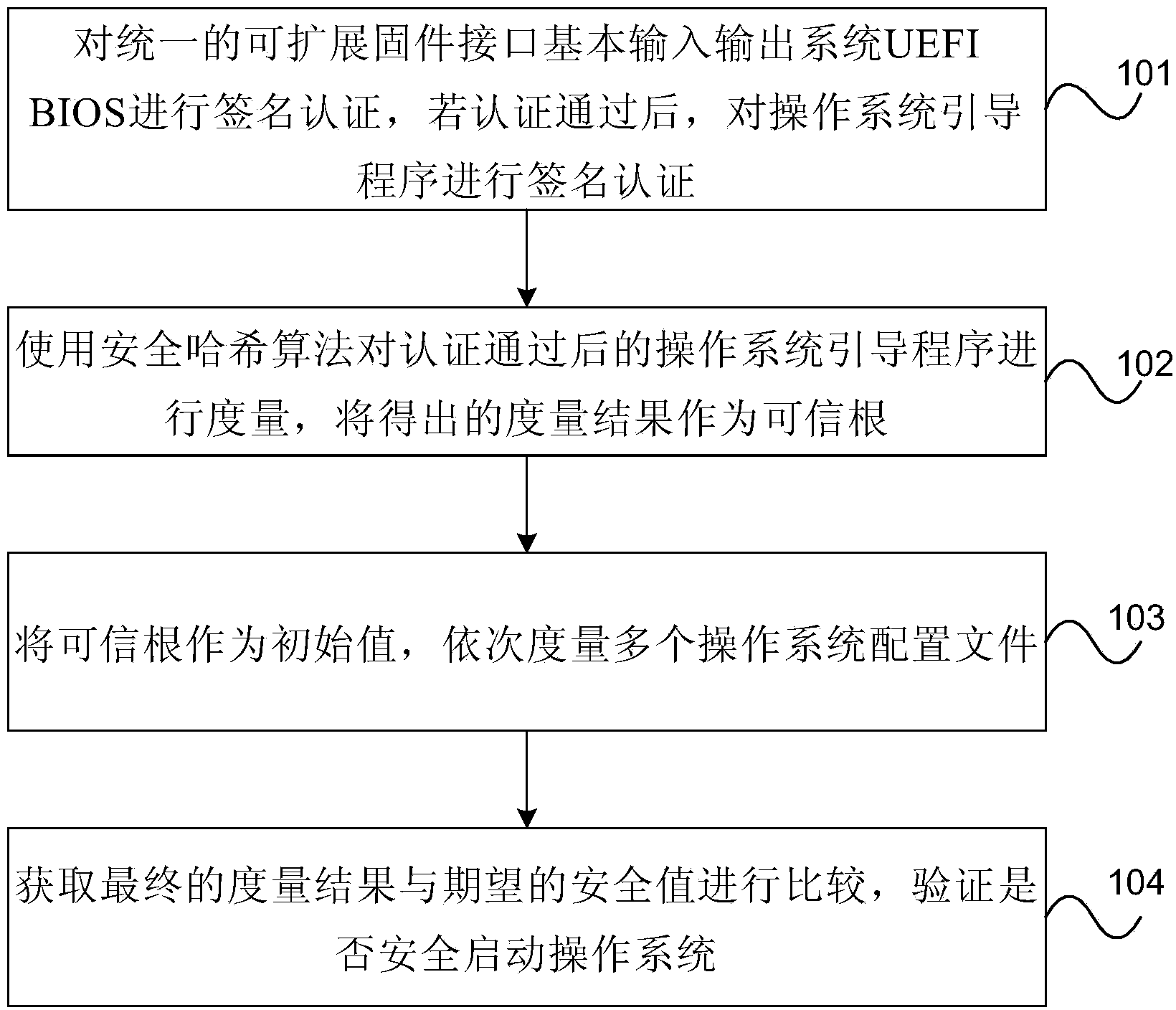
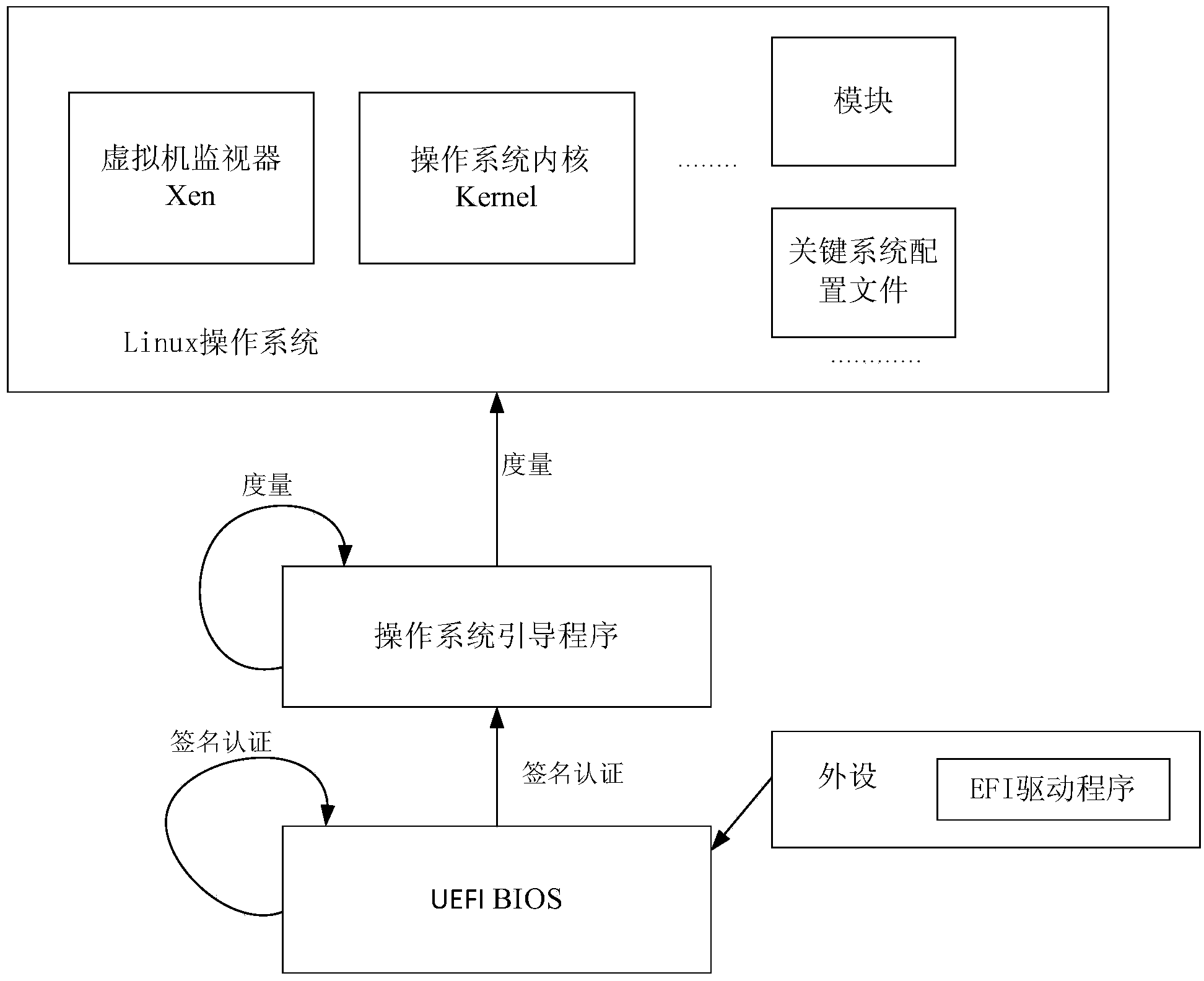
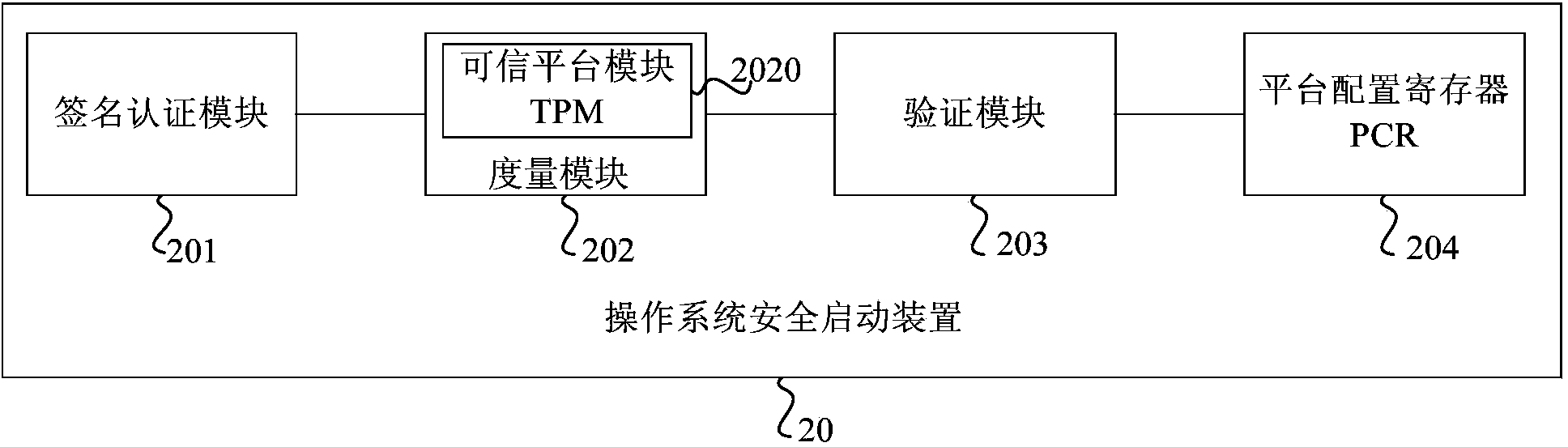
OS secure startup method and device
InactiveCN103927490AAchieving verification securityDigital data authenticationPlatform integrity maintainanceOperational systemDigital signature
The embodiment of the invention provides an OS secure startup method and device. The method includes the steps that signature verification is conducted on the UEFI BIOS, and signature verification is conducted on guidance programs of an OS if the UEFI BIOS passes the signature verification; the guidance programs, passing the signature verification, of the OS are measured through a secure hash algorithm, and the obtained measurement result serves as a trust root; the trust root serves as an initial value, and multiple configuration files of the OS are sequentially measured; the obtained final measurement result is compared with an expected secure value, and whether the OS is safely started or not is verified. By means of the OS secure startup method and device, security is verified through the method that the guidance programs of the OS pass the digital signature verification, the guidance programs, measured to be secure, of the OS generate the trust root, the OS is measured level by level according to the trust root, a trusted chain extends to the OS from the BIOS, and the problem that in the prior art, security of programs started after the Boot Loader can not be ensured is solved.
Owner:HUAWEI TECH CO LTD
Password protecting method and device
ActiveCN106656476AEnsure safetyReduce the risk of being leakedKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionPassword
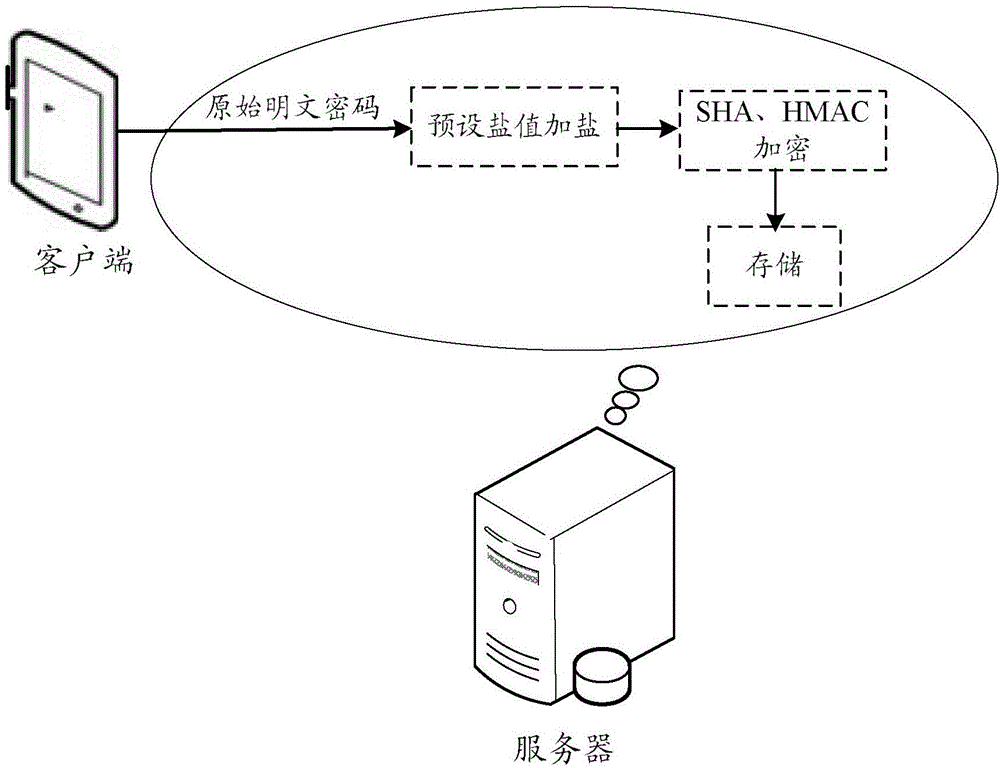
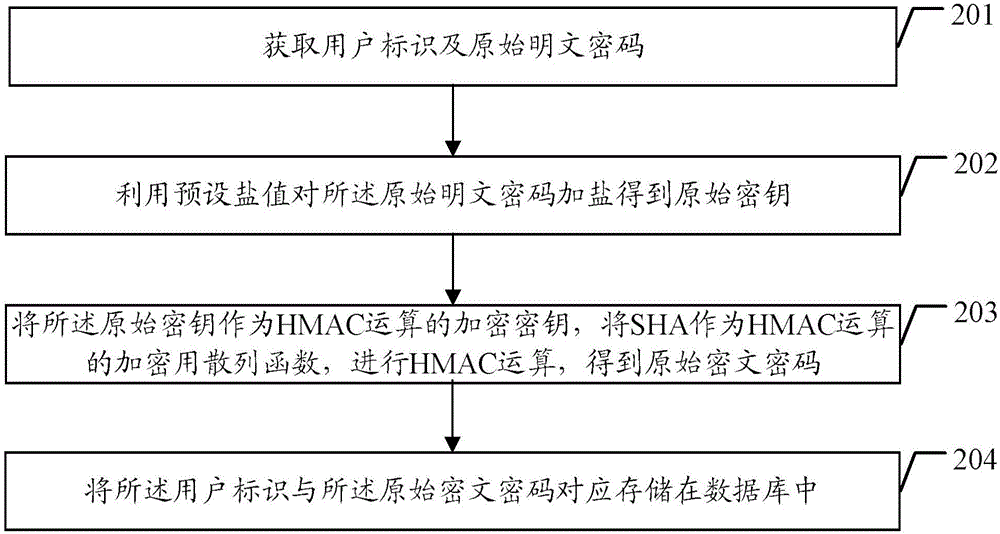
The embodiment of the present invention discloses a password protecting method and device, wherein, the password protecting method comprises: obtaining user identification and an original clear text password; adding salts to the original clear text password with a preset salt value to obtain an original key; using the original key as an encryption key of Hash-based message authentication code HMAC operation; using a secure Hash algorithm SHA as an encryption hash function of the HMAC operation to carry out the HMAC operation to obtain an original cryptograph password; and storing the user identification and the original cryptograph password correspondingly in a database. The embodiment of the present invention is able to assure the password security, and reduce the risk of password disclosing.
Owner:TENCENT TECH (SHENZHEN) CO LTD
System and method for secure encryption
ActiveUS20060034453A1Improve securityLower requirementPublic key for secure communicationUser identity/authority verificationSecure Hash AlgorithmCipher
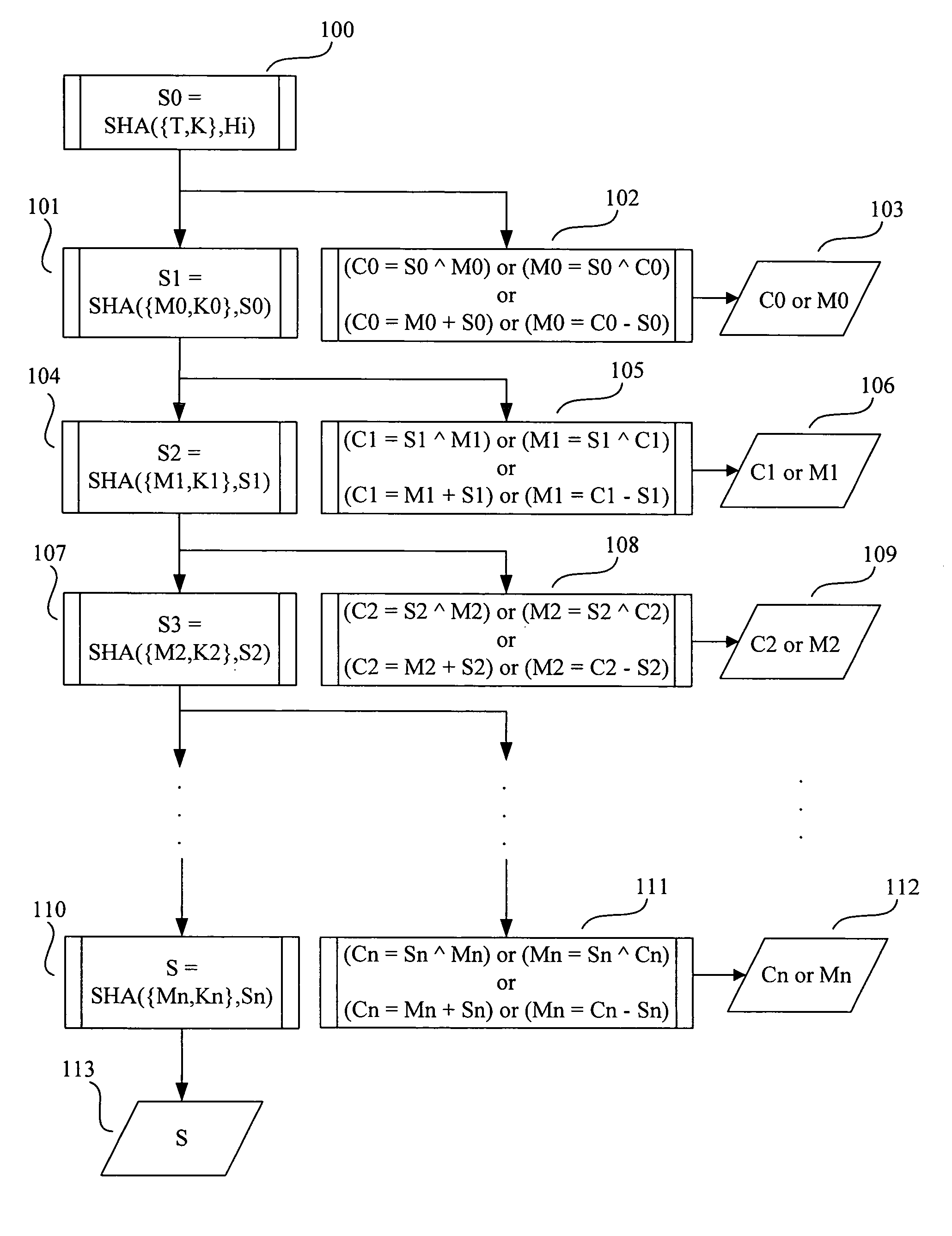
A method for encrypting a message containing a plurality of message segments is described. First, a key is input into a SHA function to generate a first hash value. Then, a first message segment is encrypted into a first cipher segment by use of a part of the first hash value. Next, the first message segment and the first hash value are input into the SHA function to generate a second hash value. Following that, the second message segment is encrypted into a second cipher segment by use of a part of the second hash value. Subsequently, next message segment is repeatedly encrypted and input into the SHA function to generate a next cipher segment and a next hash value, respectively, until the last message segment is encrypted and the last hash value is generated.
Owner:YEN FU LIU
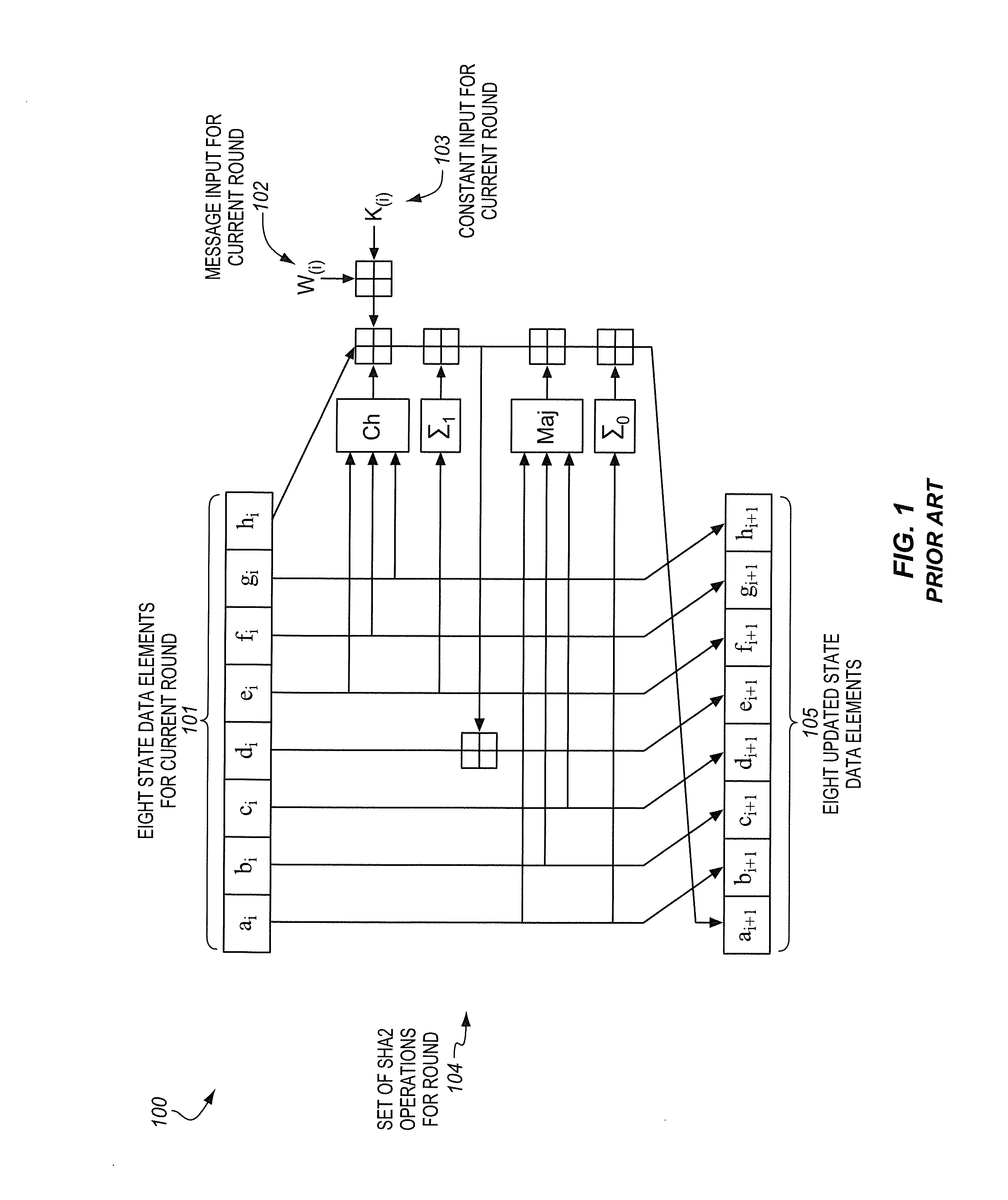
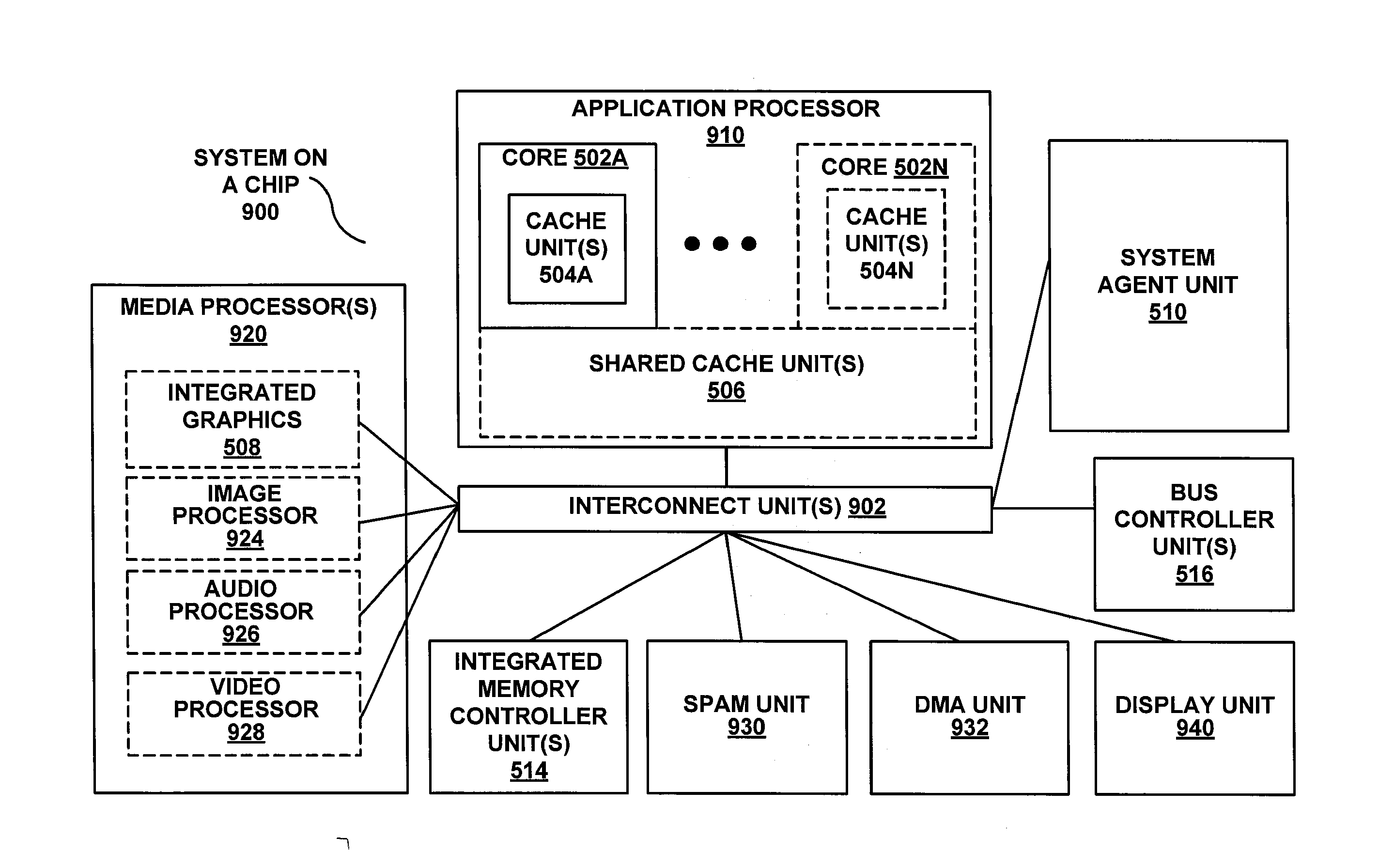
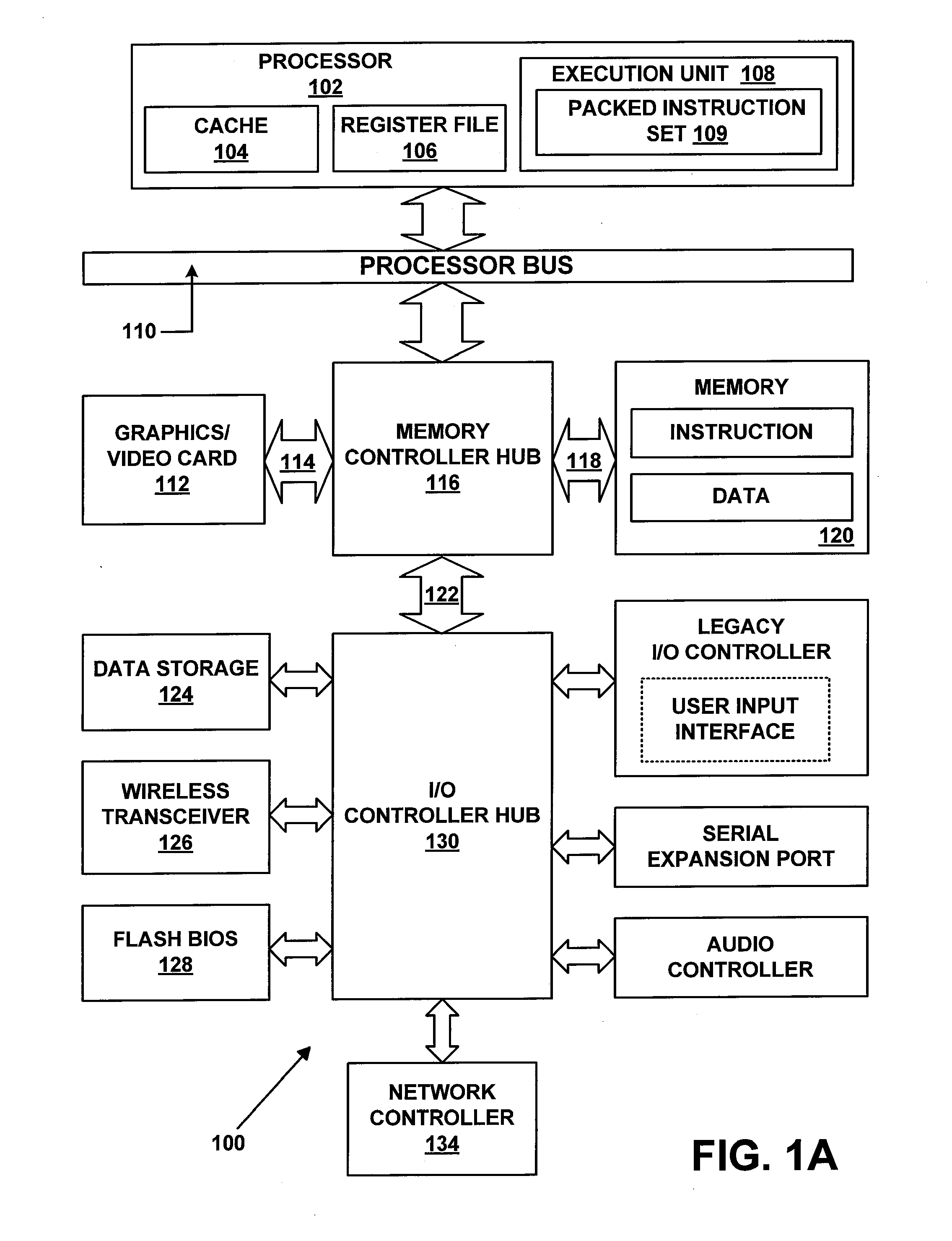
Method and apparatus to process sha-2 secure hashing algorithm
ActiveUS20140195782A1Memory architecture accessing/allocationSingle instruction multiple data multiprocessorsPosition dependentOperand
A processor includes an instruction decoder to receive a first instruction to process a secure hash algorithm 2 (SHA-2) hash algorithm, the first instruction having a first operand associated with a first storage location to store a SHA-2 state and a second operand associated with a second storage location to store a plurality of messages and round constants. The processor further includes an execution unit coupled to the instruction decoder to perform one or more iterations of the SHA-2 hash algorithm on the SHA-2 state specified by the first operand and the plurality of messages and round constants specified by the second operand, in response to the first instruction.
Owner:INTEL CORP
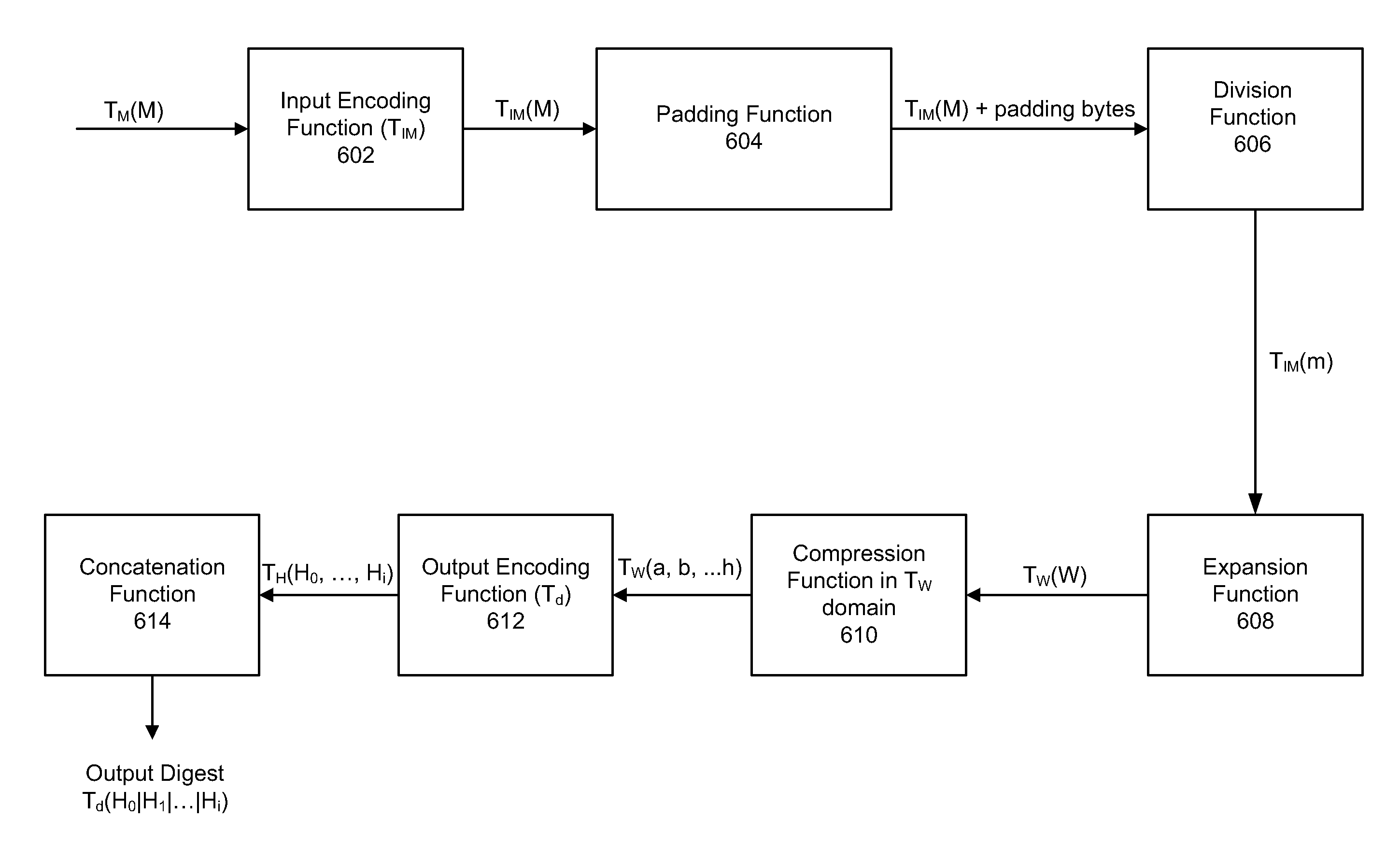
Method and System for Protecting Execution of Cryptographic Hash Functions
ActiveUS20140019771A1Digital data processing detailsUnauthorized memory use protectionComputer hardwareCryptographic hash function
A method of protecting the execution of a cryptographic hash function, such as SHA-256, in a computing environment where inputs, outputs and intermediate values can be observed. The method consists of encoding input messages so that hash function inputs are placed in a transformed domain, and then applying a transformed cryptographic hash function to produce an encoded output digest; the transformed cryptographic hash function implements the cryptographic hash function in the transformed domain.
Owner:IRDETO ACCESS
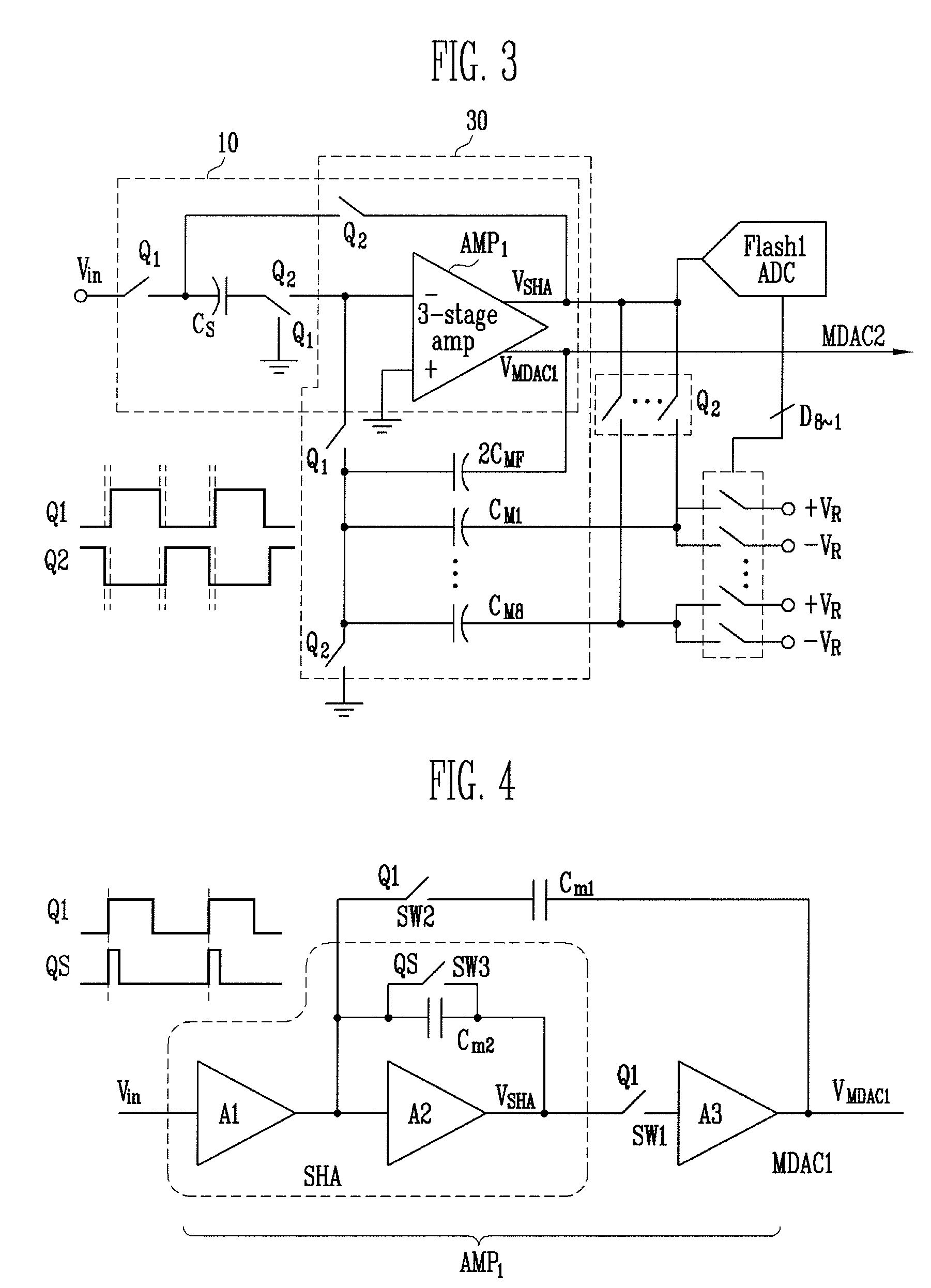
ADC first stage combining both sample-hold and ADC first stage analog-to-digital conversion functions
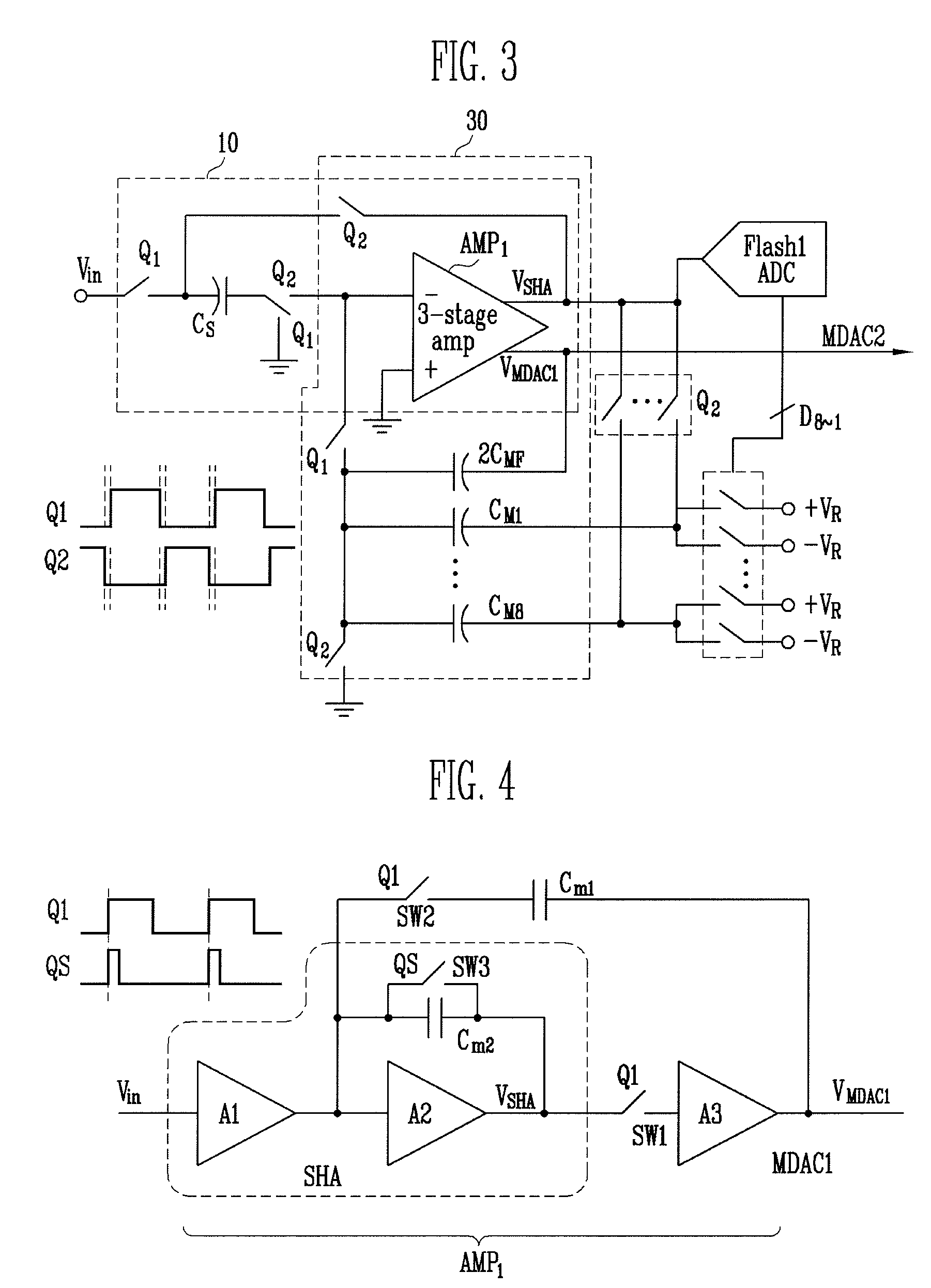
ActiveUS8604962B1Analogue/digital conversionElectric signal transmission systemsCapacitanceEngineering
A first stage circuit for a pipeline ADC first stage combines the functions of an input sample-and-hold-plus-amplifier (SHA) stage, and the functions of the first analog-to-digital conversion stage of an ADC, including a multiplying DAC (MDAC), stage-flash ADC (SFADC) comparators, and residue opamp (RAMP). The ADC first stage is duplicated, inputs and outputs are connected, and an autozero circuit using a switched-capacitor filter feedback loop controls the RAMP bias circuitry to reduce 1 / f noise and DC offsets. The sampling capacitors may be connected to the ADC input for one full sample clock time period and are disconnected from the analog input period before connecting the sampling capacitors to an amplifier voltage output or voltage reference, thereby sampling the input and allowing sufficient time for the SFADC comparators to resolve and control the MDAC capacitor settings with a low metastability error rate.
Owner:LEWYN CONSULTING
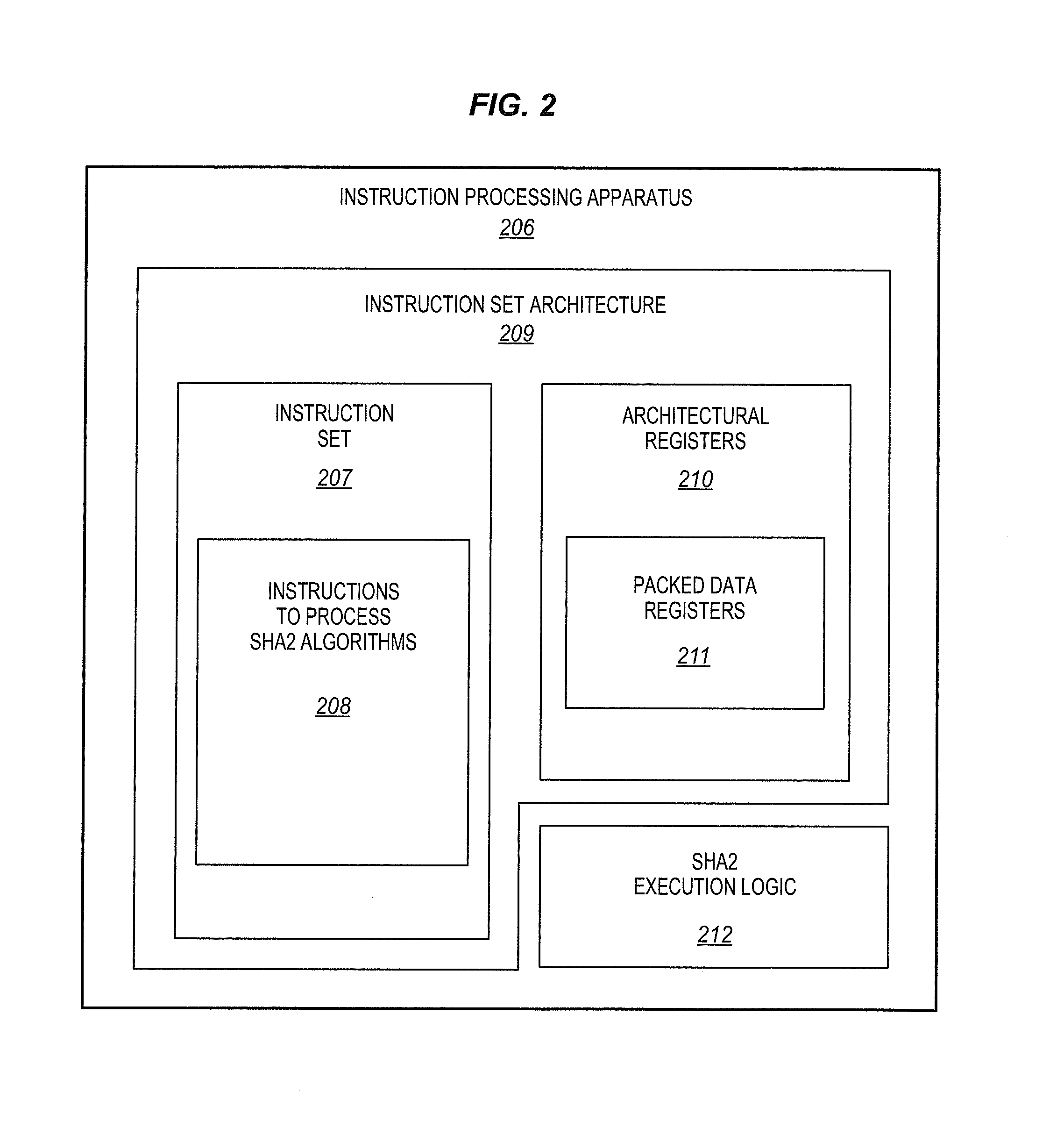
Instructions processors, methods, and systems to process secure hash algorithms
ActiveUS20140185793A1Instruction analysisDigital data protectionComputer hardwareSecure Hash Algorithm
A method of an aspect includes receiving an instruction. The instruction indicates a first source of a first packed data including state data elements ai, bi, ei, and fi for a current round (i) of a secure hash algorithm 2 (SHA2) hash algorithm. The instruction indicates a second source of a second packed data. The first packed data has a width in bits that is less than a combined width in bits of eight state data elements ai, bi, ci, di, ei, fi, gi, hi of the SHA2 hash algorithm. The method also includes storing a result in a destination indicated by the instruction in response to the instruction. The result includes updated state data elements ai+, bi+, ei+, and fi+ that have been updated from the corresponding state data elements ai, bi, ei, and fi by at least one round of the SHA2 hash algorithm.
Owner:INTEL CORP
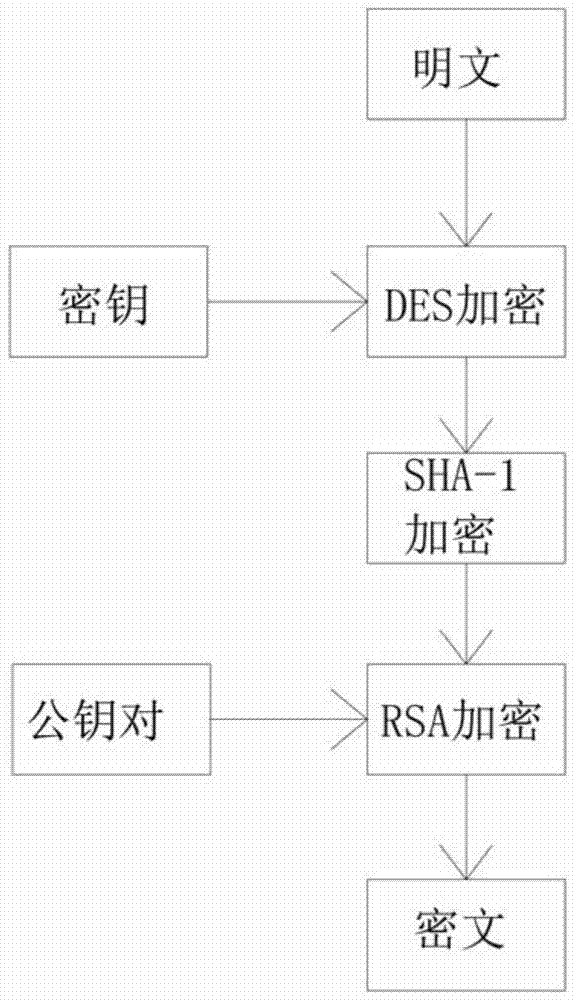
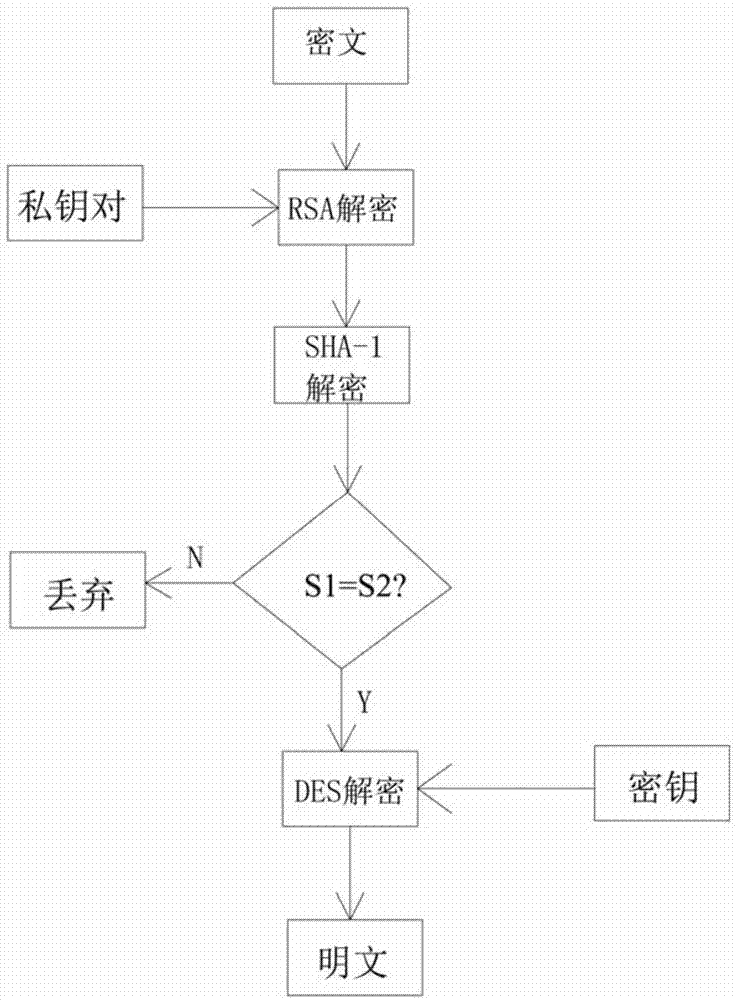
Communication data encryption and decryption method based on DES (Data Encryption Standard), RSA and SHA-1 (Secure Hash Algorithm) encryption algorithms
ActiveCN103684794AImprove securityAvoid harmPublic key for secure communicationUser identity/authority verificationDigital signatureCiphertext
The invention discloses a communication data encryption and decryption method based on DES (Data Encryption Standard), RSA and SHA-1 (Secure Hash Algorithm-) encryption algorithms. The communication data encryption and decryption method based on DES, RSA and SHA-1 encryption algorithms comprises the following steps: 1, generating data to be encrypted for sending; 2, encrypting the data to be sent for the first time, namely performing block DES encryption; 3, performing SHA-1 encryption algorithm to the data which has been encrypted for the first time to generate abstract content; 4, encrypting the data encrypted by SHA-1 and the abstract by a RSA encryption public key received by a receiving end; 5, sending cryptograph; 6, receiving the cryptograph by the receiving end and decrypting the cryptograph by an own private key for the first time; 7, authenticating the received data; 8, performing DES decryption to the data which has been authenticated, and reading the data content. The communication data encryption and decryption method based on DES, RSA and SHA-1 encryption algorithms utilizes different characteristics of the three encryption algorithms, and respectively encrypts a message to be sent by DES, RSA and SHA-1 encryption algorithms, so that the encrypted message for communication is much safer, and a digital signature is achieved for ensuring that the received message is the original message sent by a sending end without tampering.
Owner:SOUTH CHINA UNIV OF TECH
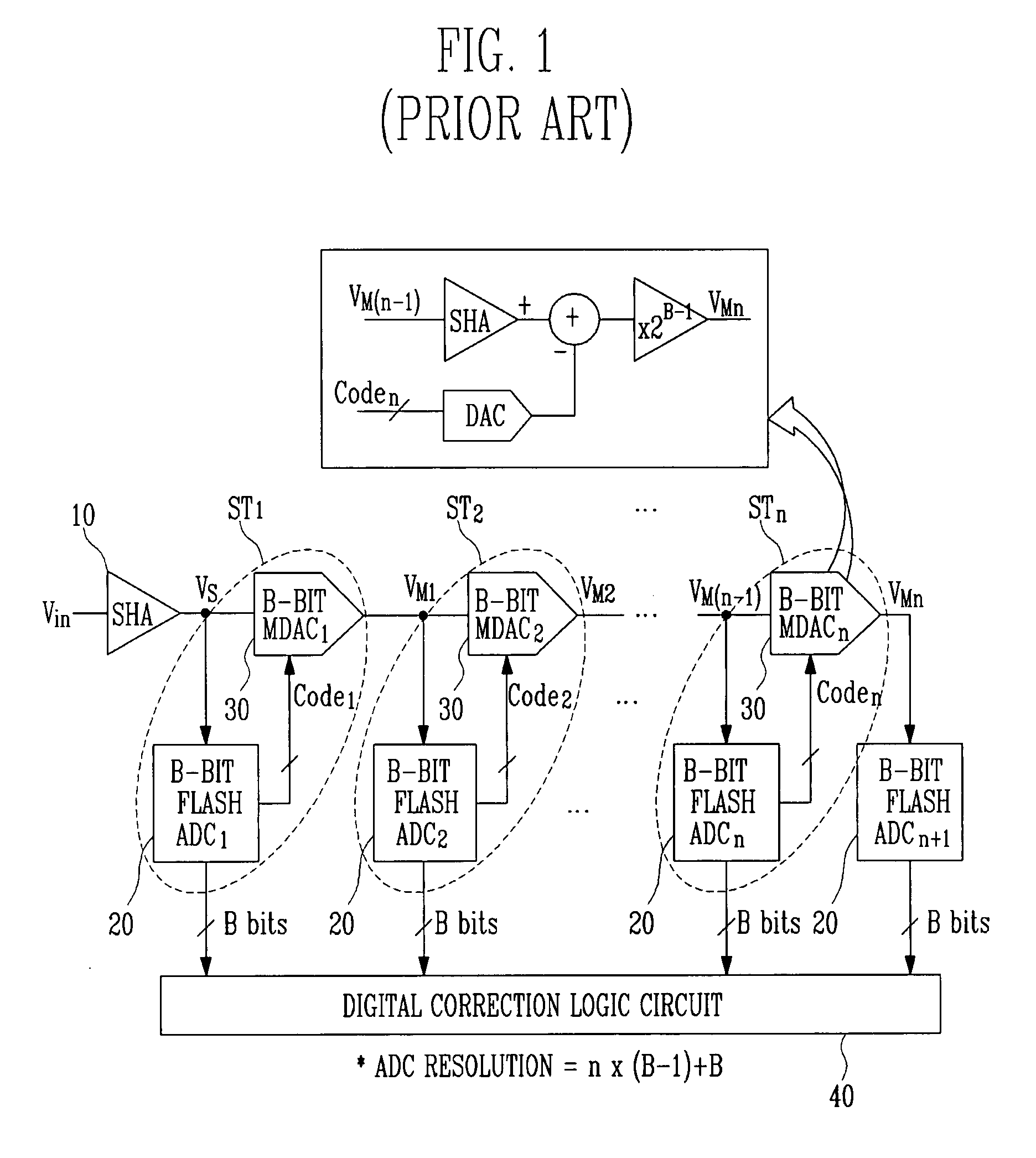
Multi-bit pipeline analog-to-digital converter capable of altering operating mode
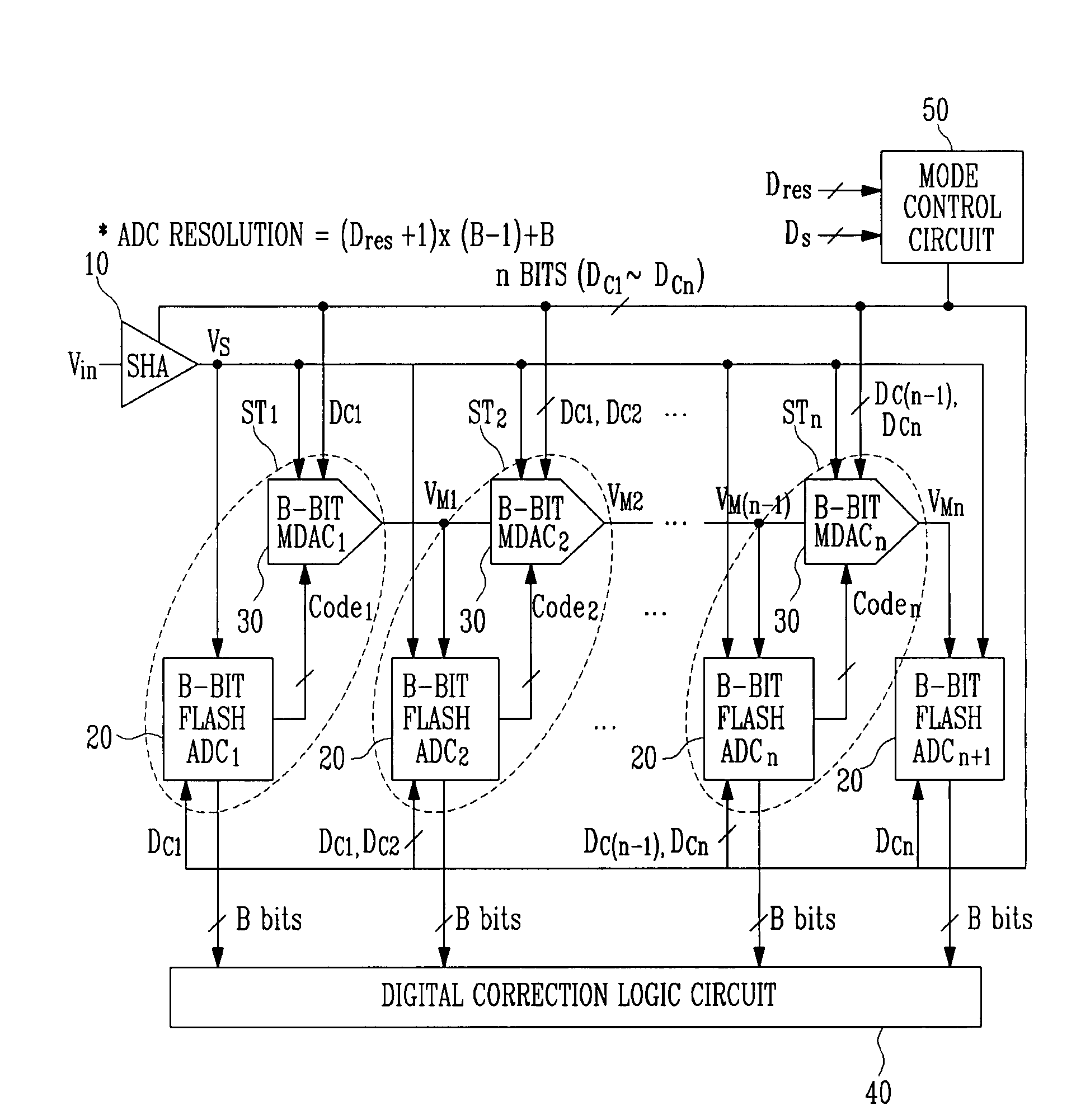
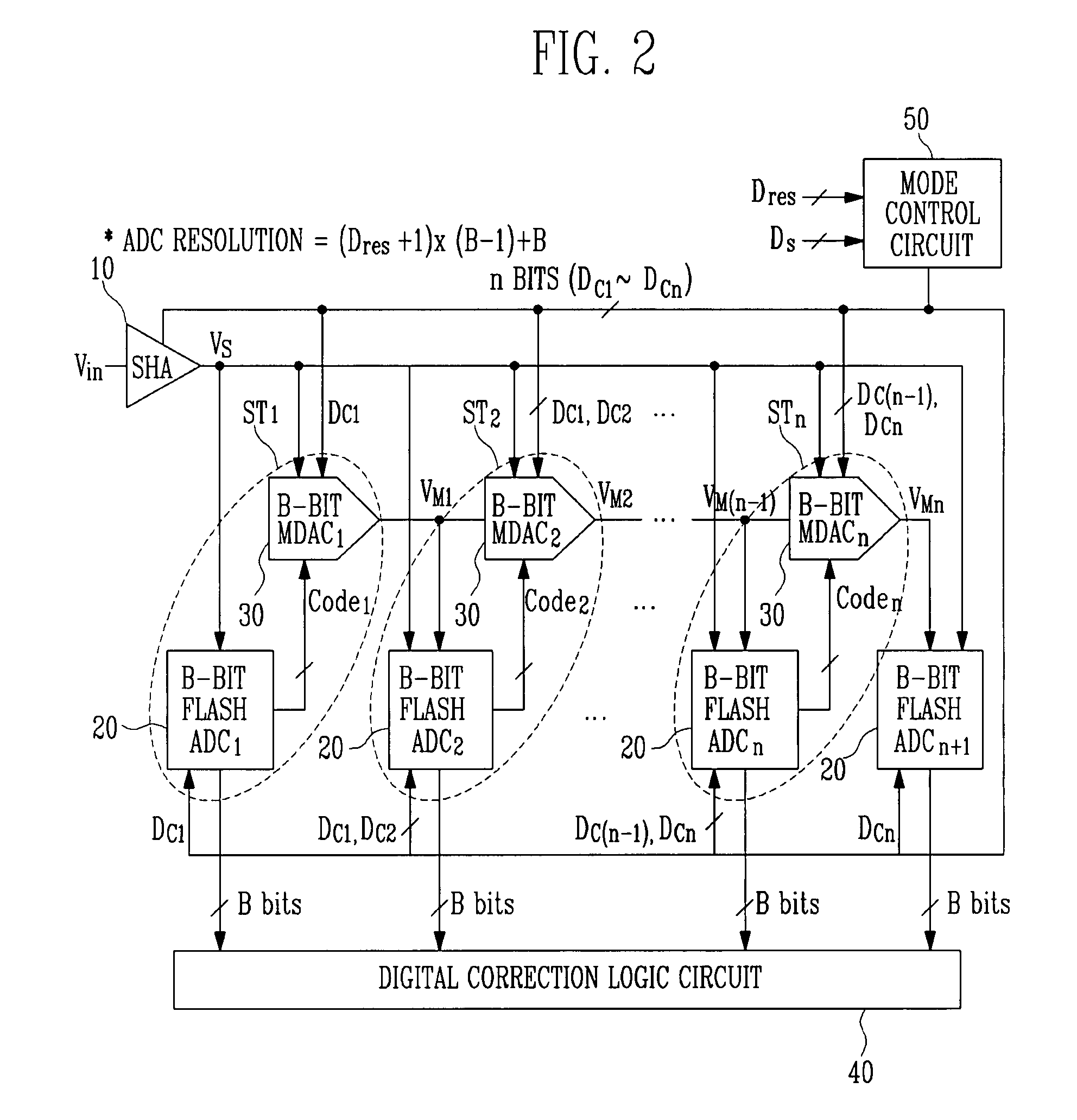
InactiveUS20080129567A1Minimize power consumptionPower saving provisionsElectric signal transmission systemsControl signalMode control
Provided is a multi-bit pipeline analog-to-digital converter (ADC) capable of altering an operating mode. The ADC includes: a sample-and-hold amplifier (SHA) for sampling and holding an input analog voltage; an n+1 number of B-bit flash ADCs for receiving an analog signal and converting the analog signal into a digital signal to output the digital signal; an n number of B-bit multiplying digital-to-analog converters (MDACs) for converting a difference between the digital signal output from the B-bit flash ADC and the front-stage output signal into an analog signal to output the analog signal to the next stage; and a mode control circuit for generating n-bit control signals to control the B-bit flash ADC and the B-bit MDAC according to required resolution and operating frequency. In the multi-bit pipeline ADC, an operating mode is altered by controlling the number of stages in a pipeline and a signal path according to required resolution and operating frequency, so that power consumption can be minimized under the corresponding operating condition and signals can be processed in a variety of ways.
Owner:ELECTRONICS & TELECOMM RES INST
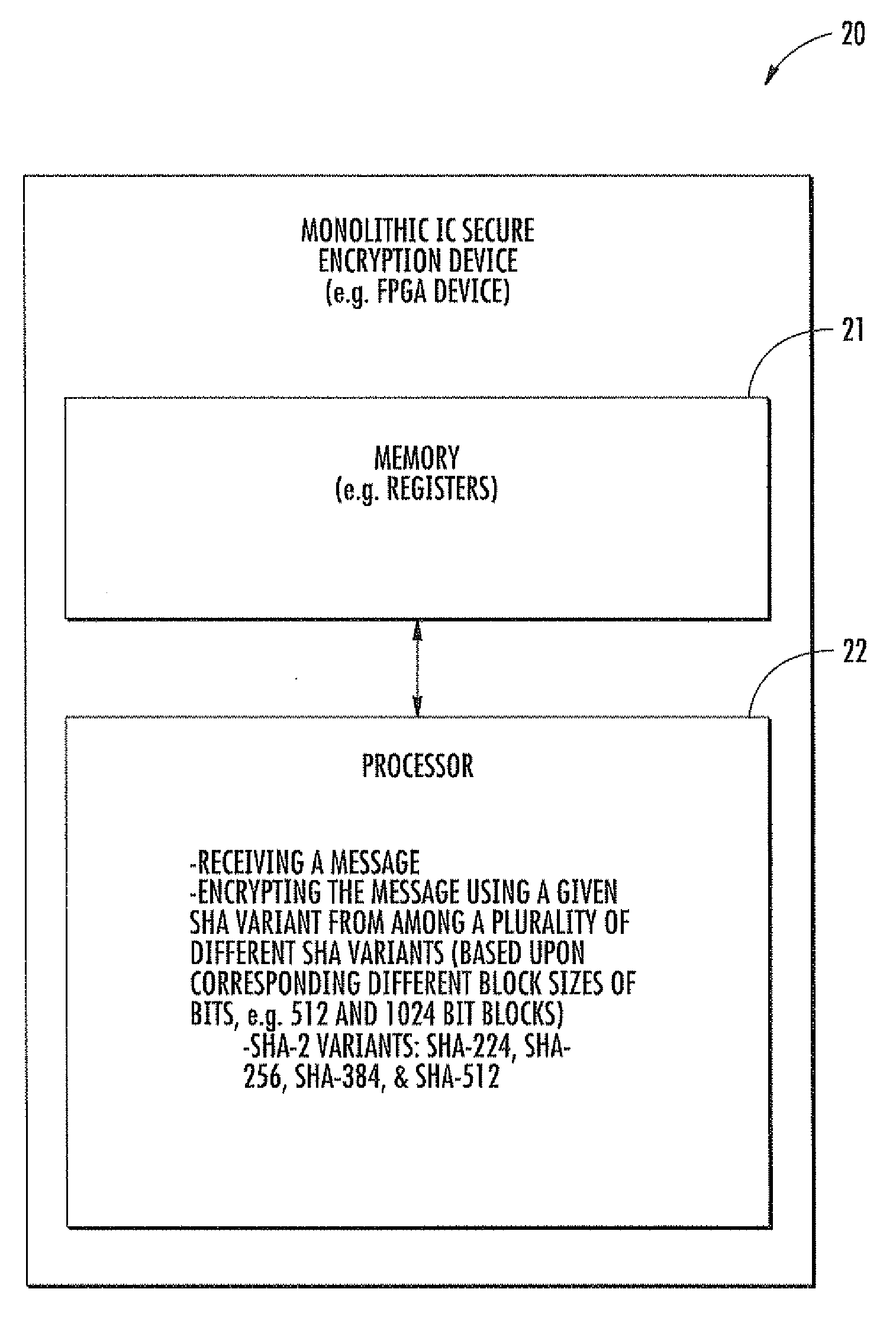
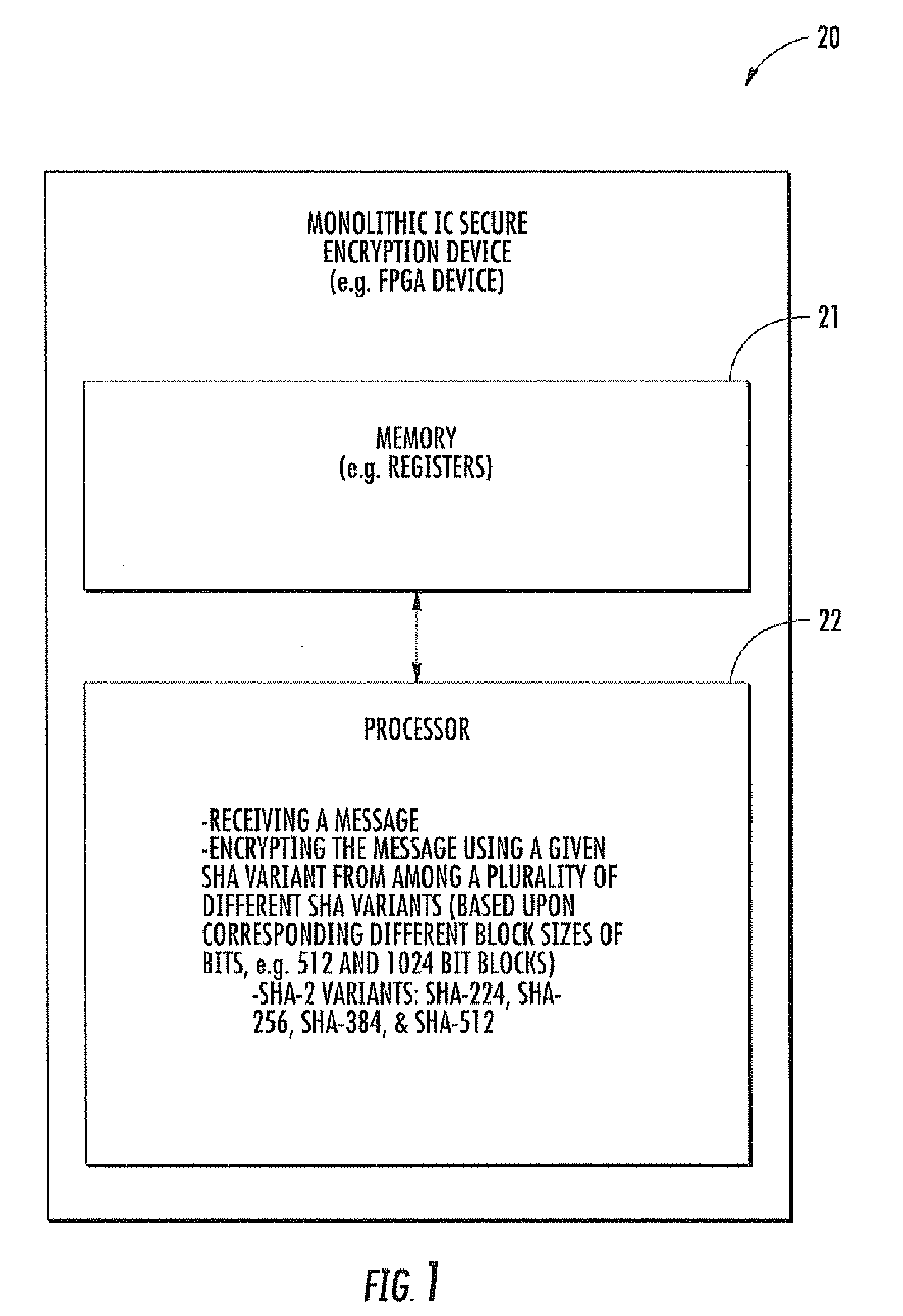
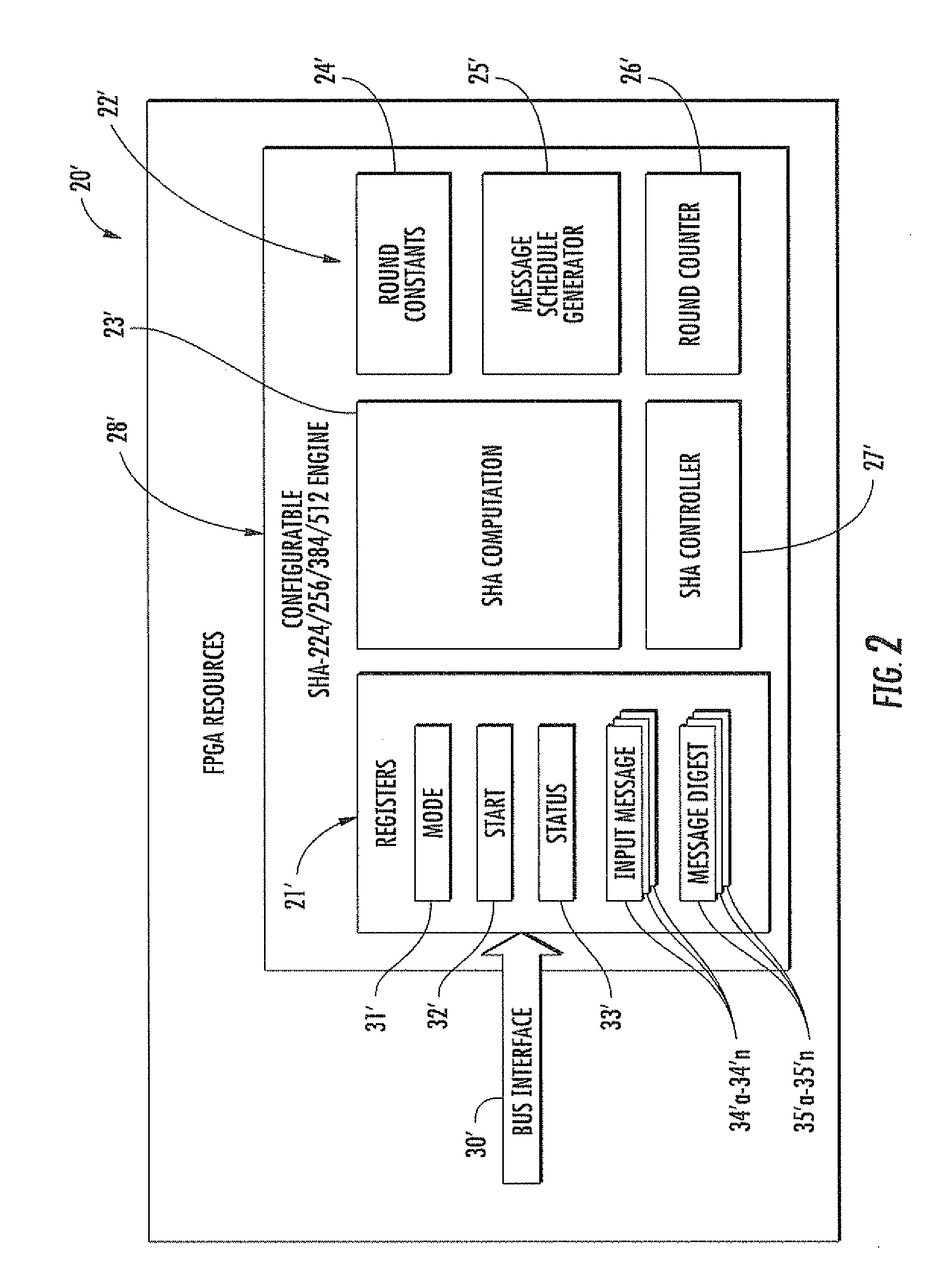
Secure hashing device using multiple different sha variants and related methods
ActiveUS20100278331A1Improve abilitiesInternal/peripheral component protectionSecret communicationComputer hardwareIntegrated circuit
A monolithic integrated circuit (IC) secure hashing device may include a memory, and a processor integrated with the memory. The processor may be configured to receive a message, and to process the message using a given secure hash algorithm (SHA) variant from among different SHA variants. The different SHA variants may be based upon corresponding different block sizes of bits.
Owner:HARRIS GLOBAL COMM INC
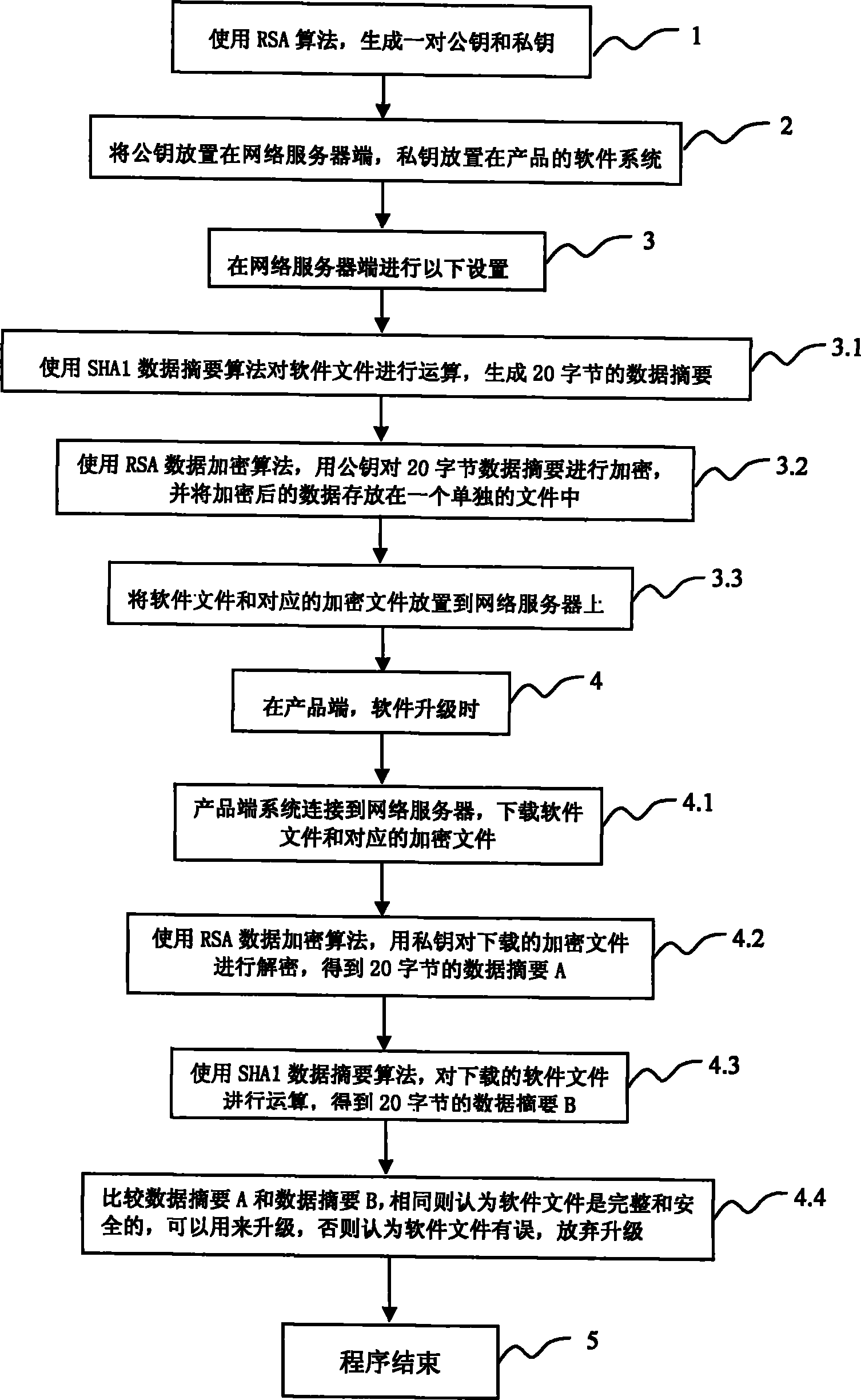
Method for upgrading software on line
InactiveCN102082784AAvoid upgradePublic key for secure communicationProgram loading/initiatingSoftware systemNetwork service
The invention discloses a method for upgrading software on line. The method comprises the following steps of: encrypting software to be upgraded by using asymmetry of a radio supervisory adapter (RSA) encryption algorithm to generate a public key and a private key which form a pair; and placing the public key at a network server end and the private key in a software system of a product, wherein the public key is used for encryption and the private key is used for decryption. Two prime numbers are multiplied by an RSA, and the product is publically used as an encryption key and is resolved into factors during decryption; but the two prime numbers can be more easily multiplied and the product can be extremely difficultly dissolved into the factors. The encryption and the decryption at the network server end and a product end are set by an RSA data encryption algorithm and a secure hash algorithm (SHA) 1 data digest algorithm respectively; the software can be downloaded and upgraded after settings are compared to be consistent; associated verification and encryption mechanisms are established at the two ends, namely the network server end and the product software system end; thus the integrity of the software is correctly identified, the wrong or tampered software is prevented from being upgraded into the product, and the software at the product end is securely upgraded.
Owner:广东欧加控股有限公司
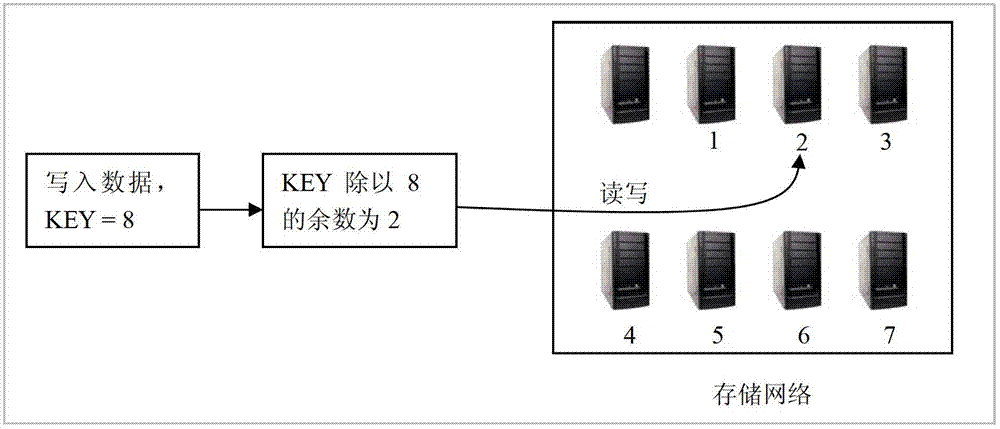
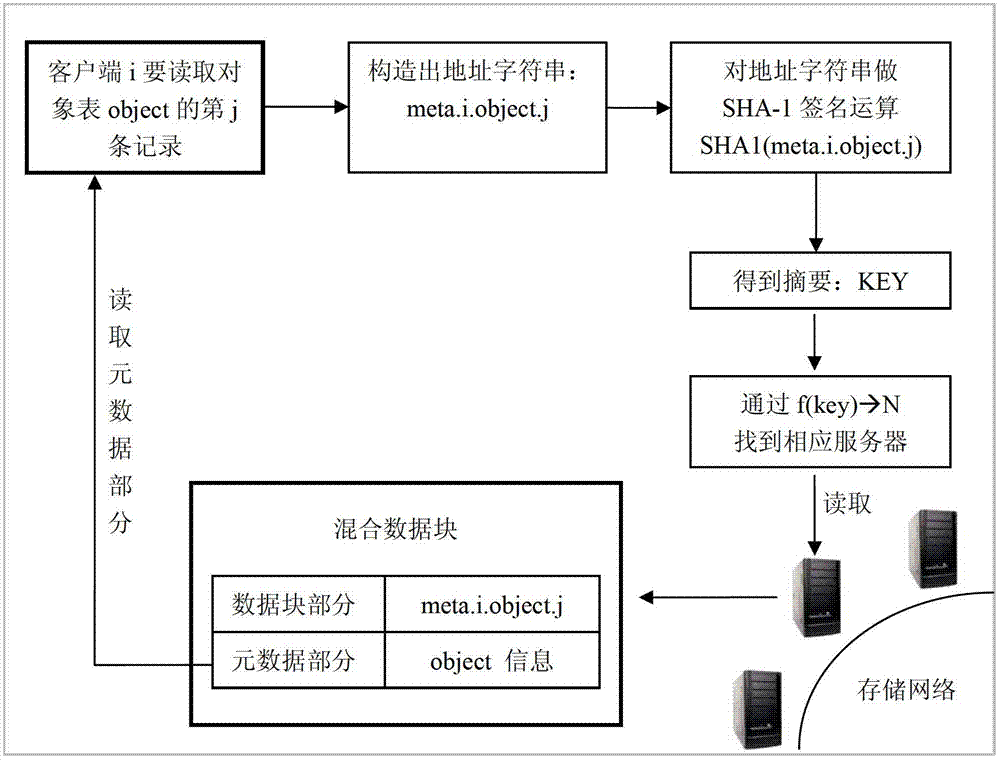
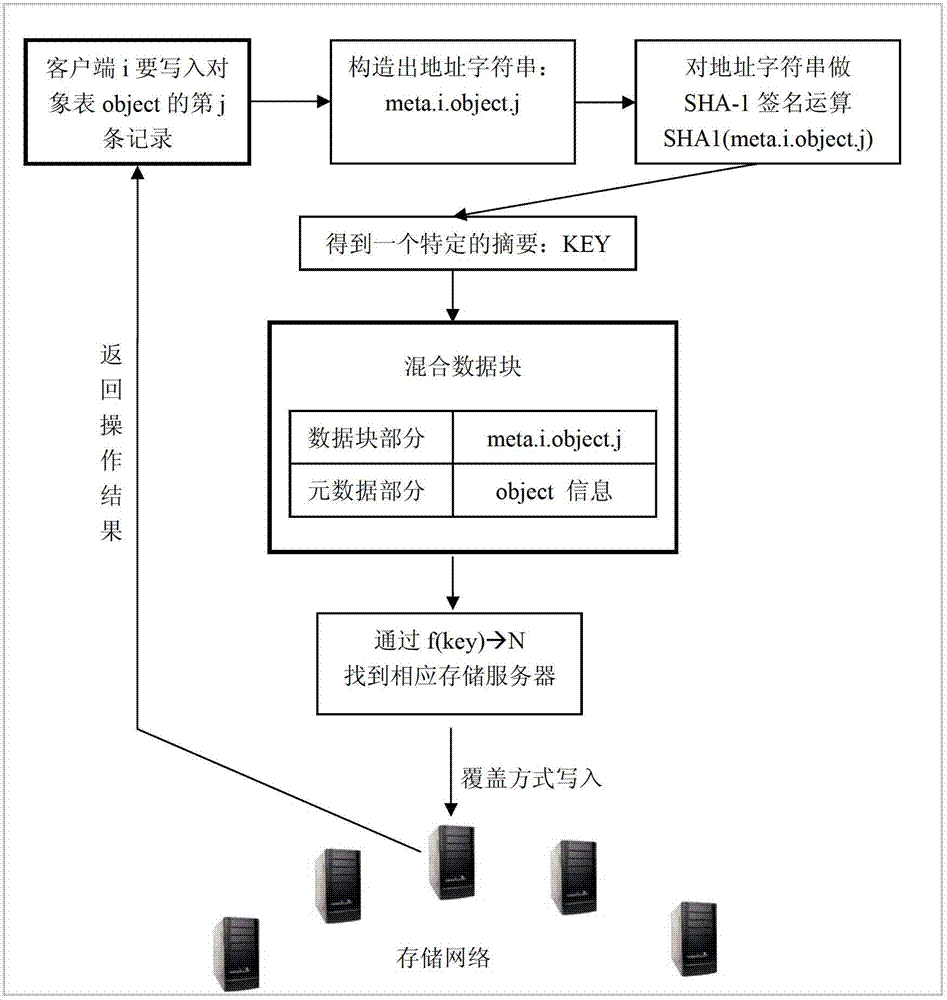
Metadata distributed storage method applicable to cloud storage system
ActiveCN102821138AReduce risk of damageSame redundancyTransmissionSpecial data processing applicationsExtensibilityCloud storage system
The invention provides a metadata distributed storage method applicable to a cloud storage system. The method comprises the following steps: carrying out signature operation on a data block through an SHA-1 (secure hash algorithm-1); carrying out distributed storage on the calculated data block; and carrying out mixed storage on the data block and metadata through a mapping method. With the adoption of the metadata distributed storage method applicable to the cloud storage system disclosed by the invention, the problem that the traditional metadata storage needs a special metadata server is solved, and the storage of the metadata and the storage of block data can be directly merged, so that the safety and expandability of the metadata are improved, and the problem that a whole storage network cannot be used by single point failure of the metadata is avoided.
Owner:广州鼎鼎信息科技有限公司
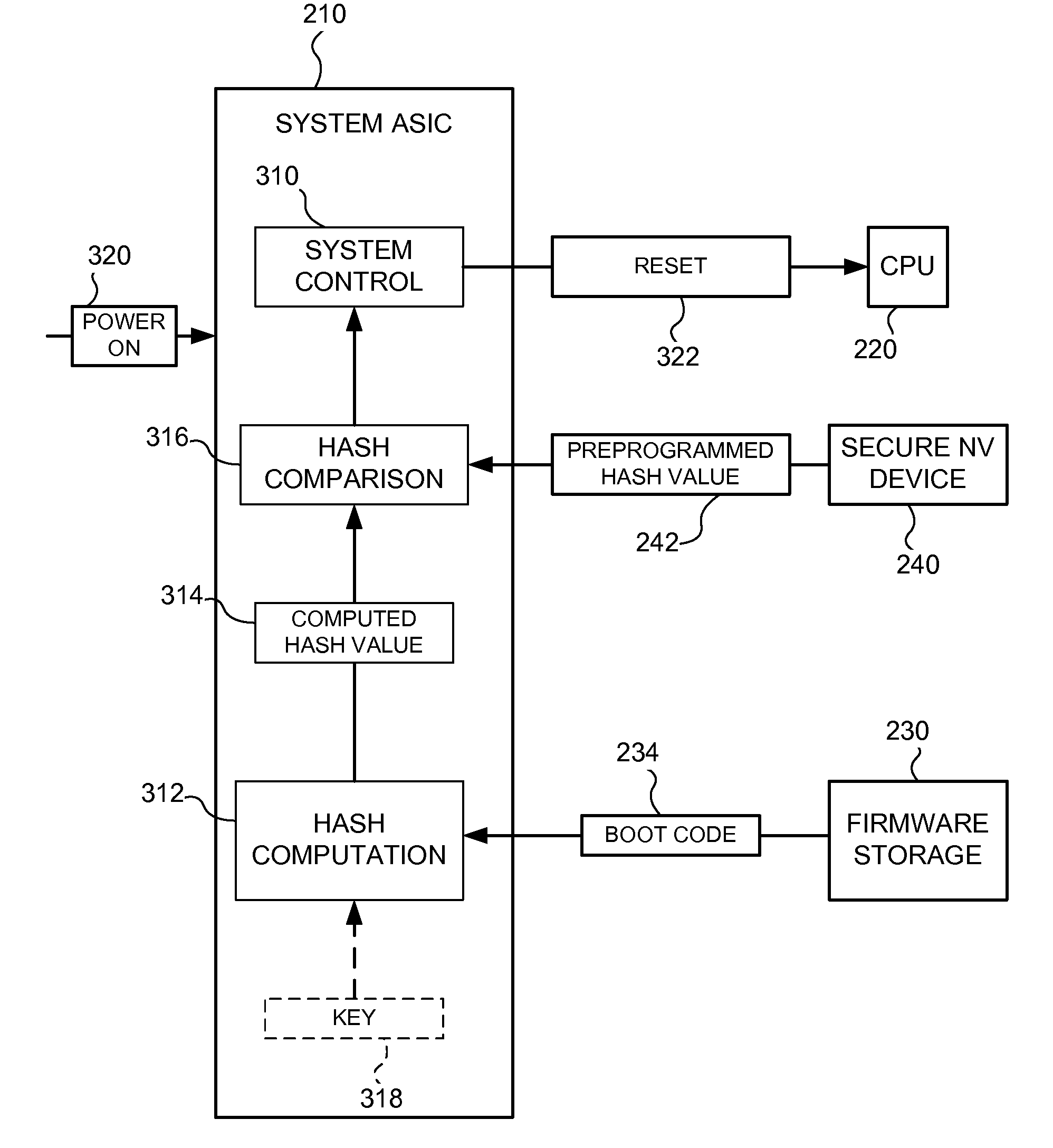
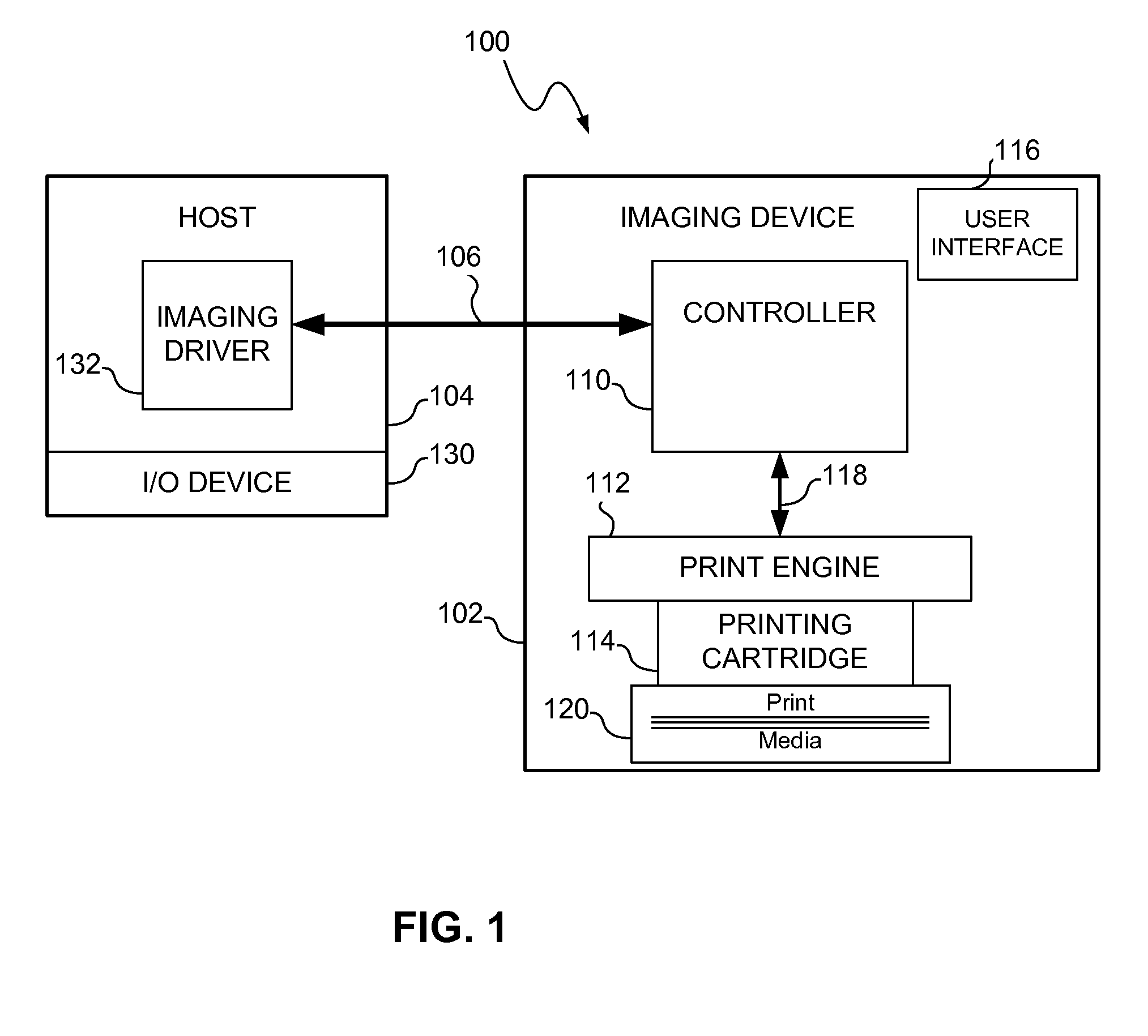
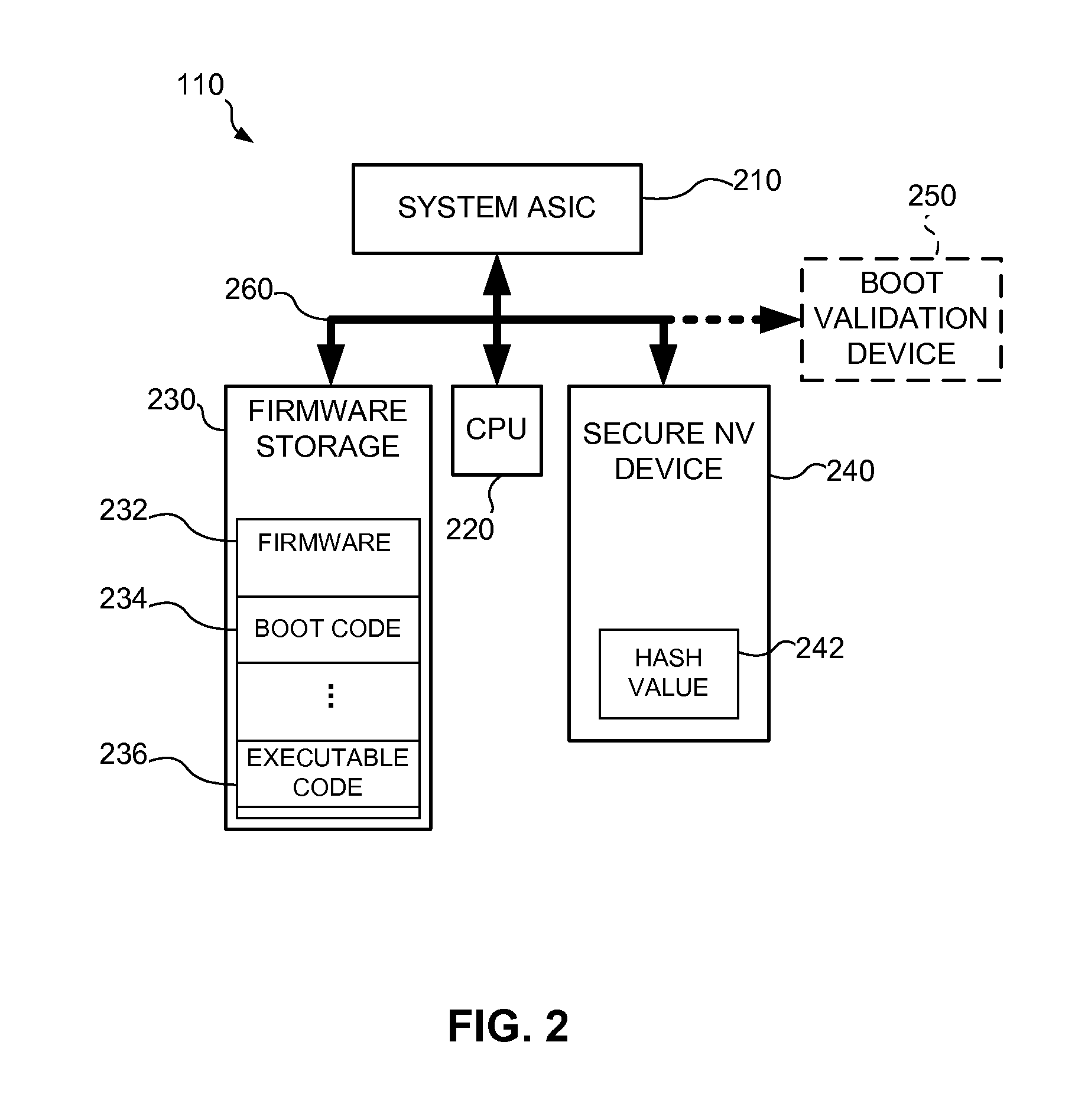
Boot Validation in Imaging Devices
InactiveUS20080313453A1Preventing executionDigital computer detailsComputer security arrangementsComputerized systemImaging equipment
A boot validation system and method may be used in a computer system to validate boot code before allowing the computer system to execute the boot code. In particular, a secure hash algorithm may be used to compute a hash value of the boot code and the computed hash value may be compared to a preprogrammed hash value stored in a secure non-volatile device. If the hash values match the boot code may be validated and the system may then be allowed to execute the boot code. Once the boot code is validated, the boot code may be executed to validate other code (e.g., firmware) in the computer system. In an exemplary embodiment, the boot validation system and method may be used in an imaging device, such as a printer.
Owner:LEXMARK INT INC
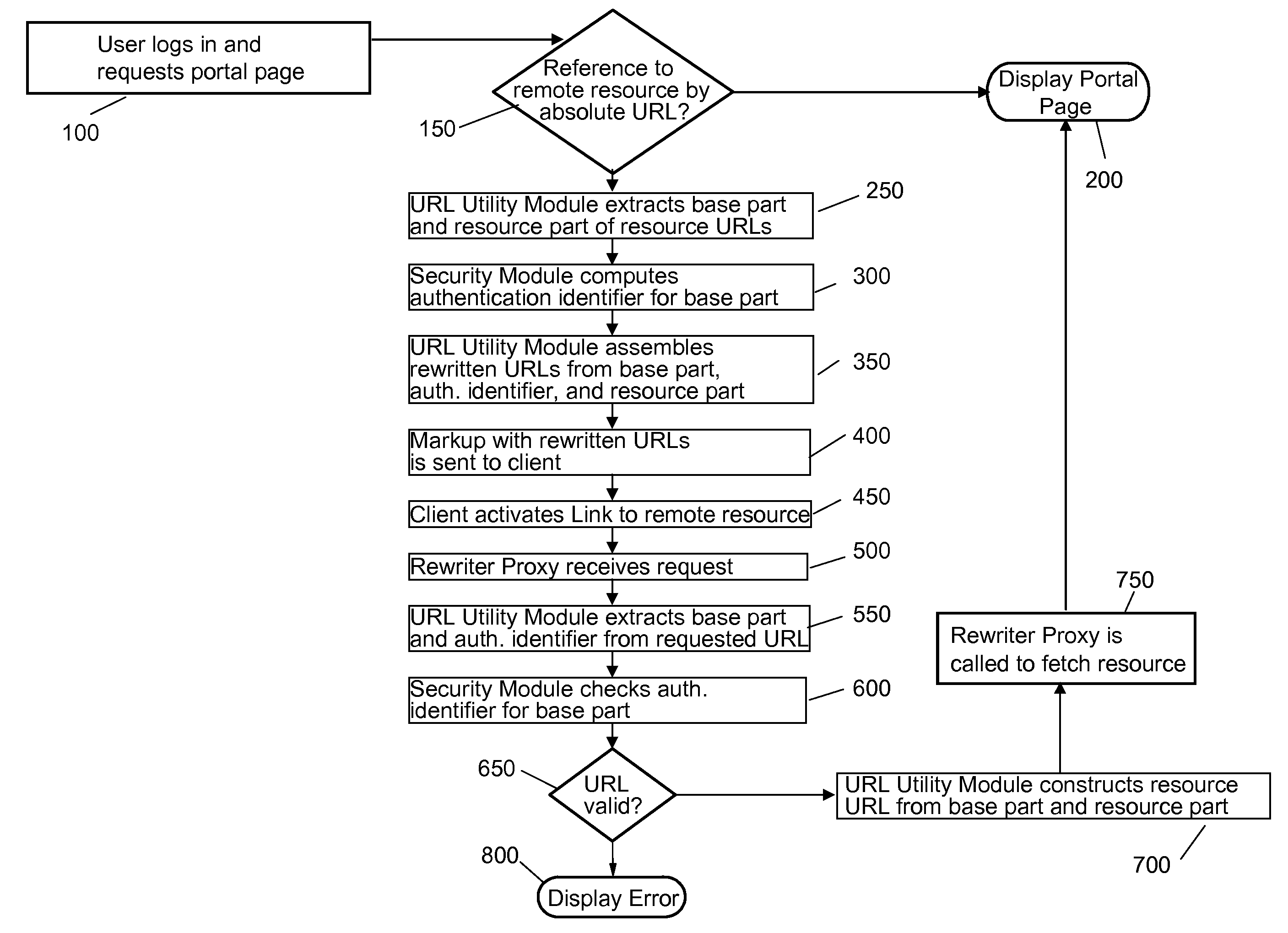
Controlling access of a client system to access protected remote resources supporting relative URLs
InactiveUS8365271B2Digital data processing detailsMultiple digital computer combinationsWeb applicationClient-side
A client system is controlled for accessing protected remote resources via a Web Application using a rewriter proxy that supports relative URLs. In one configuration, the Web application can be a Portal application. A URL utility module can be provided for a rewriter proxy that splits an absolute URL into a base part (the URL string up to the resource) and the resource part. A security module computes an authentication identifier for the base part. This can occur by applying a secure hash algorithm and / or secret key. The URL utility module then constructs the rewritten URL by concatenating the URL encoded base part, the authentication identifier, and the resource part as separate path elements.
Owner:INT BUSINESS MASCH CORP
Method for recogniting seal by digital watermark
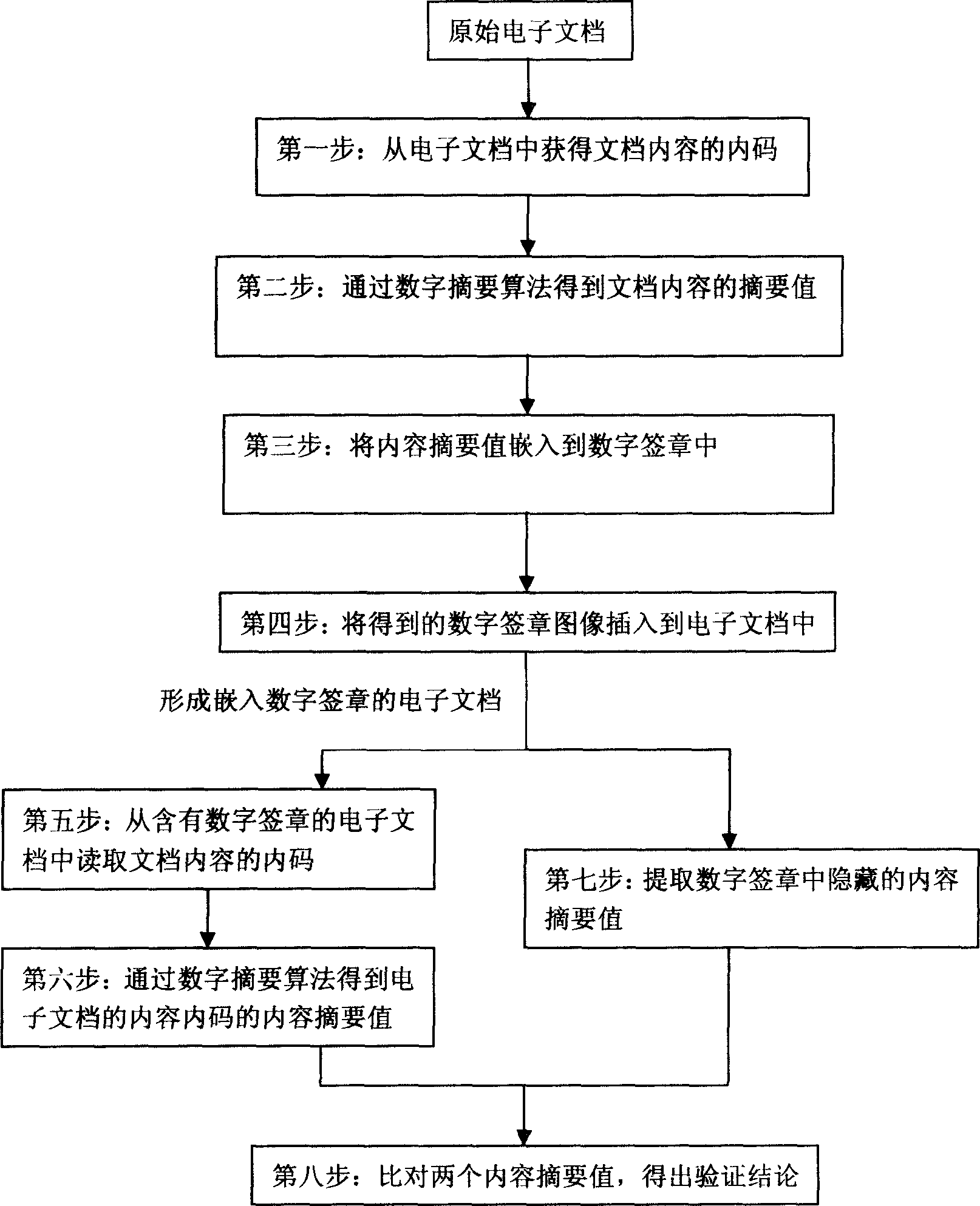
InactiveCN1758585AUniqueness guaranteedInfluence extractionSecuring communicationGraphicsImage extraction
A certification and seal method of digital watermark includes inserting process as calculating out file control abstract value by using digital abstract algorithm of SHA, SHA ¿C 1, MD5 and CRC16 / 32, embedding said abstract value in digital certification seal image and inserting it in electronic file; verifying process as calculating out file content abstract value by using relevant digital abstract algorithm, picking up hidden file content abstract from digital seal image in file and comparing two abstract values for obtaining verification result.
Owner:北京华旗数码影像技术研究院有限责任公司 +1
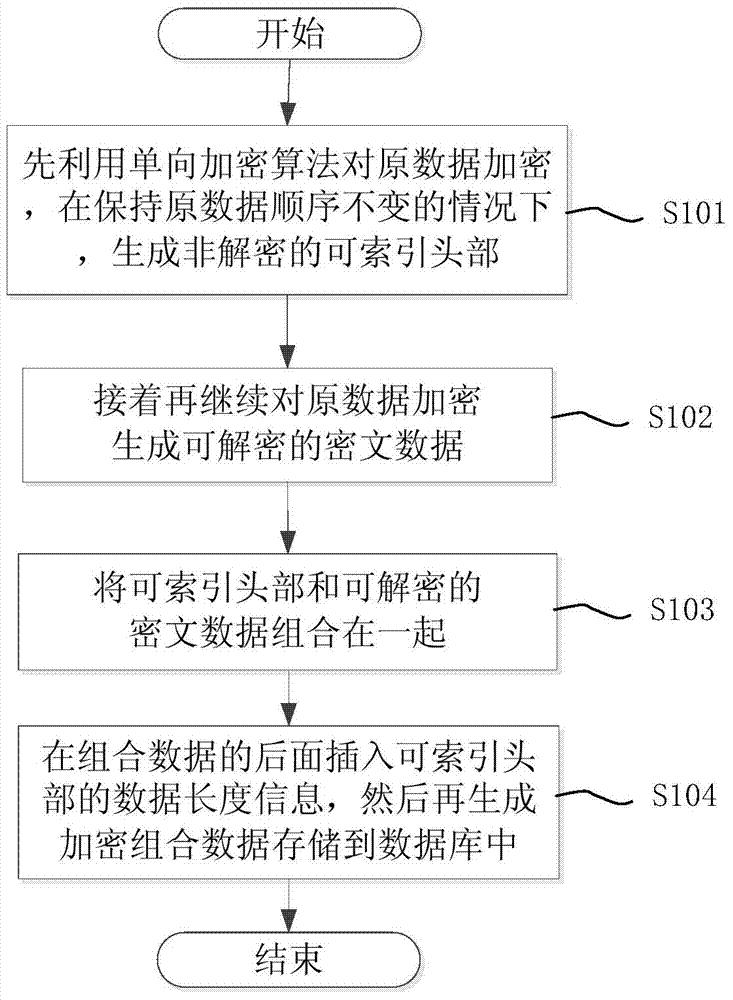
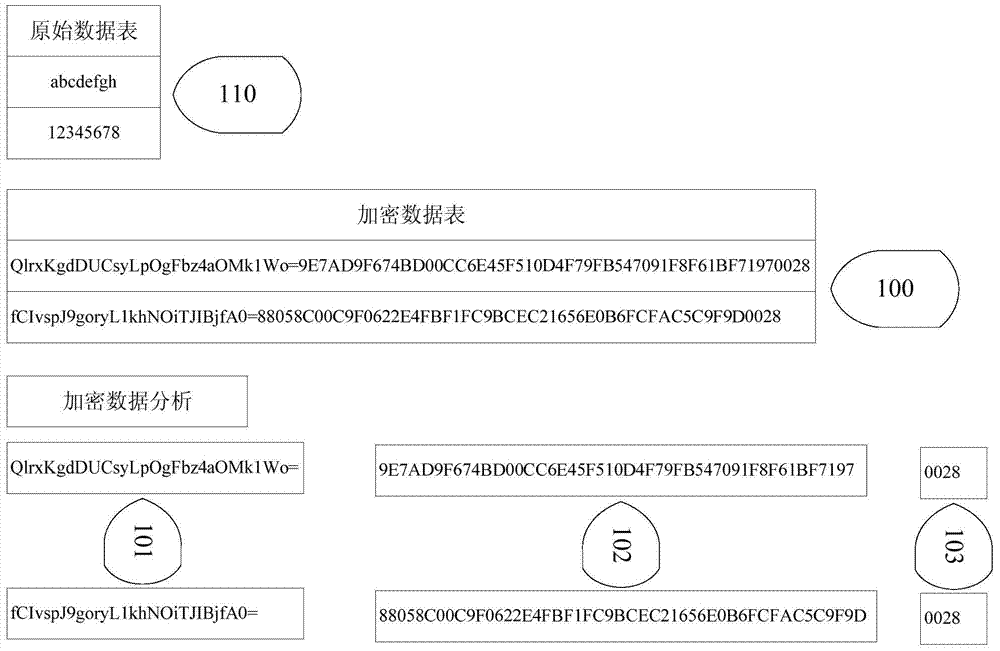
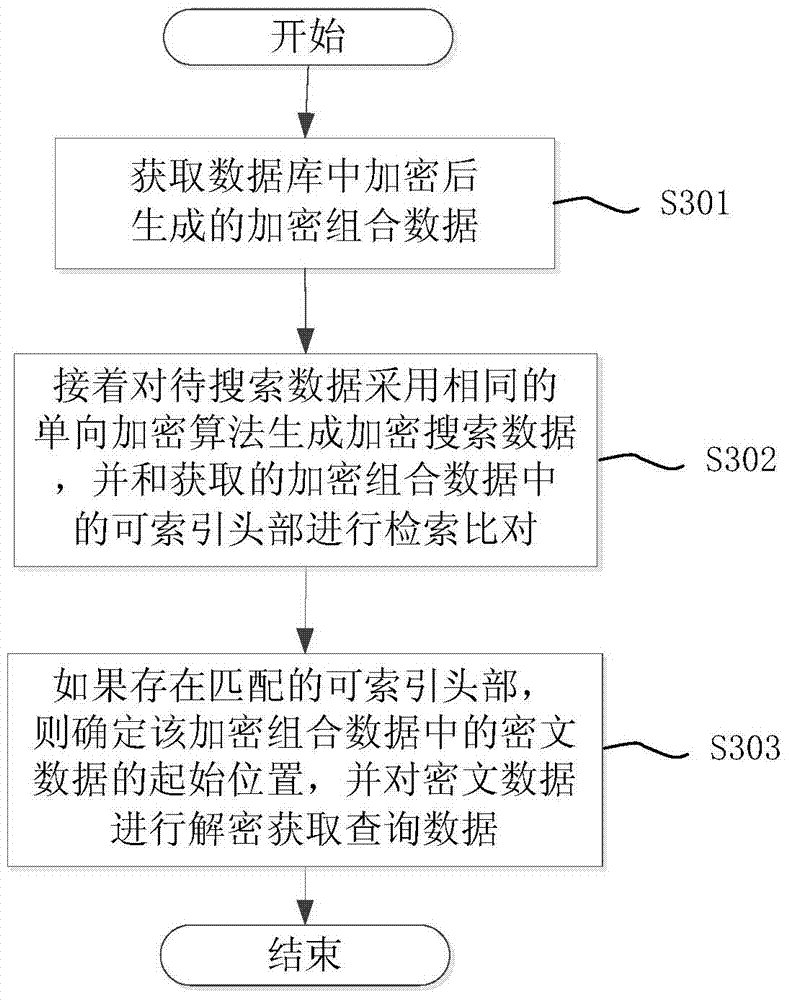
Data encryption and retrieval method for database
ActiveCN103927357AGuaranteed correctnessEnsure safetyDigital data protectionSpecial data processing applicationsFull table scanCiphertext
The invention discloses a data encryption and retrieval method for a database. The method includes the steps: a) encrypting raw data by means of a one-way encryption algorithm to generate a non-decipherable indexable head under the condition of keeping sequence of the raw data unchanged; b) continuing to encrypt the raw data to generate decipherable ciphertext data; c) combining the indexable head and the decipherable ciphertext data to generate encryption combined data, and storing the encryption combined data in the database, wherein the one-way encryption algorithm in the step a) refers to MD5 (message-digest algorithm 5), SHA (secure hash algorithm) or HMAC (hash message authentication code); the encryption algorithm in the step b) refers to the symmetric key encryption algorithm. The data encryption and retrieval method for the database has the advantages that since the indexable head and the decipherable ciphertext data are combined for encrypted storage of all of the raw data by means of cipertext, and the indexable head are used for quick retrieval of the encrypted data, full table scanning is avoided while accuracy in data decryption and security in data retrieval are guaranteed.
Owner:上海新炬网络技术有限公司
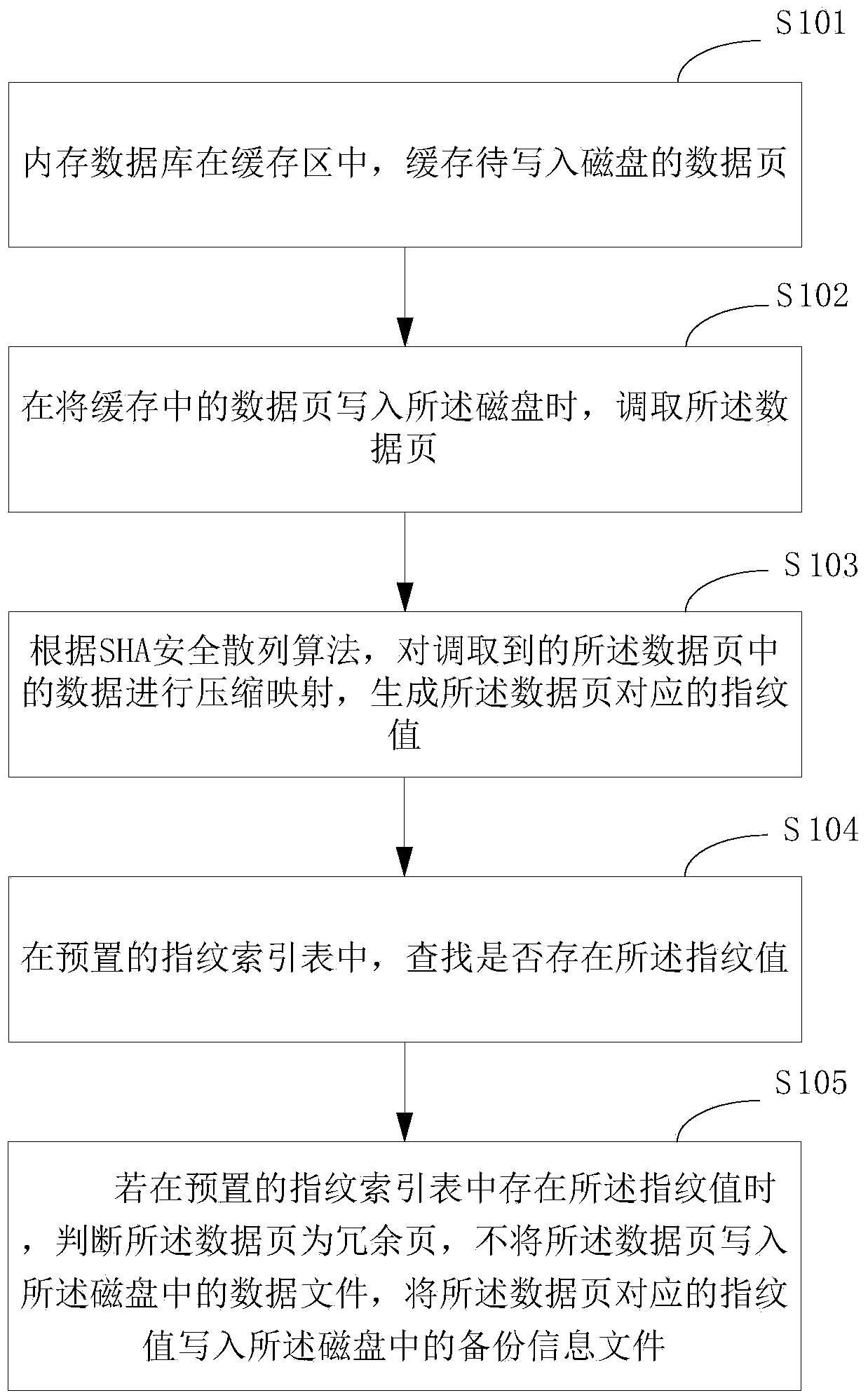
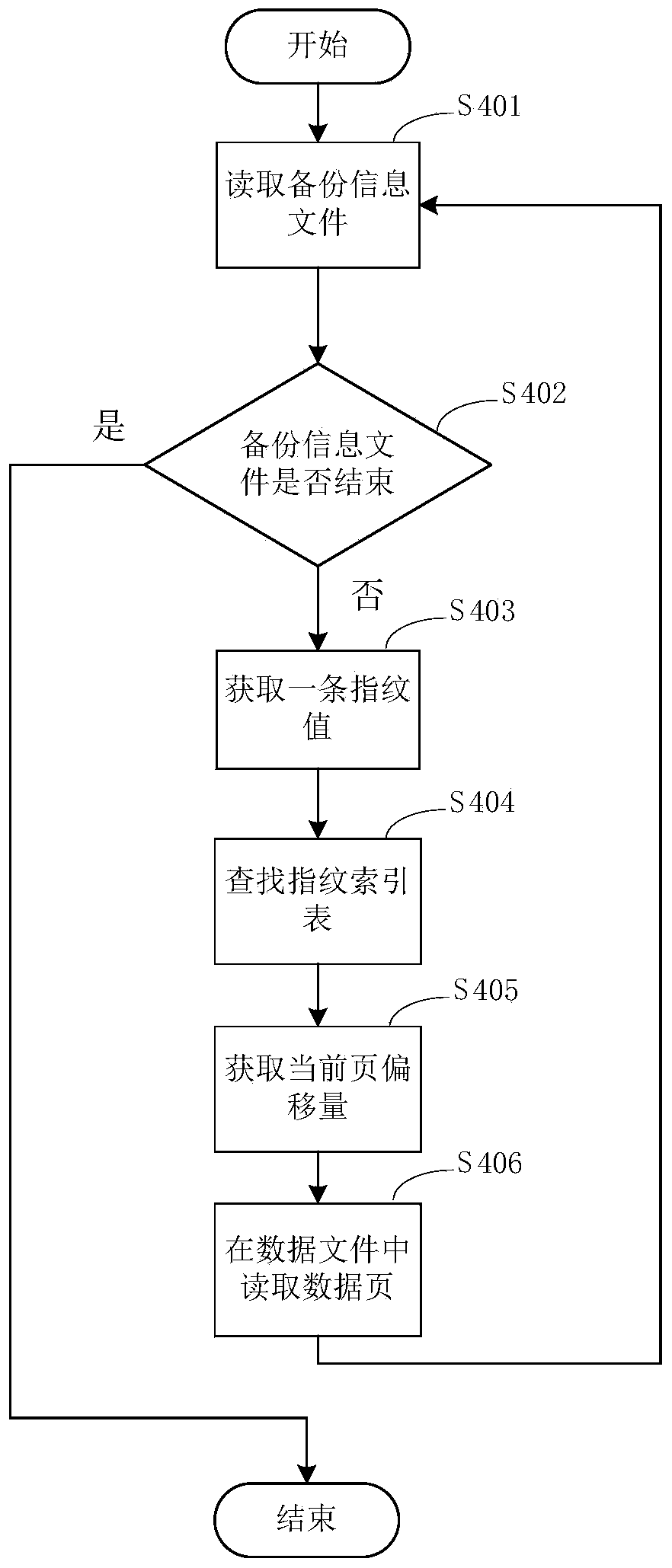
Method and device for deleting duplicated data and system
ActiveCN104077380ASave storage spaceImprove efficiencySpecial data processing applicationsIn-memory databaseExternal storage
The invention is suitable for the technical field of databases, and provides a method and a device for deleting duplicated data and a system. The method comprises the following steps: caching a data page to be written into an external storage by using a main memory database in a cache region; when the data page in a cache is written into the external storage, calling the data page; performing compressed mapping on the data in the called data page according to an SHA (Secure Hash Algorithm) to generate a fingerprint value corresponding to the data page; finding out whether the fingerprint value exists in a preset fingerprint index table or not; if the fingerprint value exists in the preset fingerprint index table, judging that the data page is a redundant page, not writing the data page into a data file in the external storage, and writing the fingerprint value corresponding to the data page into a backup information file in the external storage. The method, the device and the system have the beneficial effects that on one aspect, the storage space of the external storage is saved; on the other aspect, the backup efficiency of current data in the main memory database is increased.
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY
Speed up secure hash algorithm (SHA) using single instruction multiple data (SIMD) architectures
A processing apparatus comprises logic to, according to a selected secure hash algorithm (SHA) algorithm, generate hash values by preparing message schedules for a plurality of message blocks in parallel using single instruction multiple date (SIMD) instructions and performing compression in serial, and logic to generate a message digest conforming to the secure hash algorithm (SHA) algorithm.
Owner:TAHOE RES LTD
Speed up secure hash algorithm (SHA) using single instruction multiple data (SIMD) architectures
ActiveUS20130332742A1Unauthorized memory use protectionHardware monitoringSecure Hash AlgorithmMessage broker
A processing apparatus may comprise logic to preprocess a message according to a selected secure hash algorithm (SHA) algorithm to generate a plurality of message blocks, logic to generate hash values by preparing message schedules in parallel using single instruction multiple data (SIMD) instructions for the plurality of message blocks and to perform compression in serial for the plurality of message blocks, and logic to generate a message digest conforming to the selected SHA algorithm.
Owner:TAHOE RES LTD
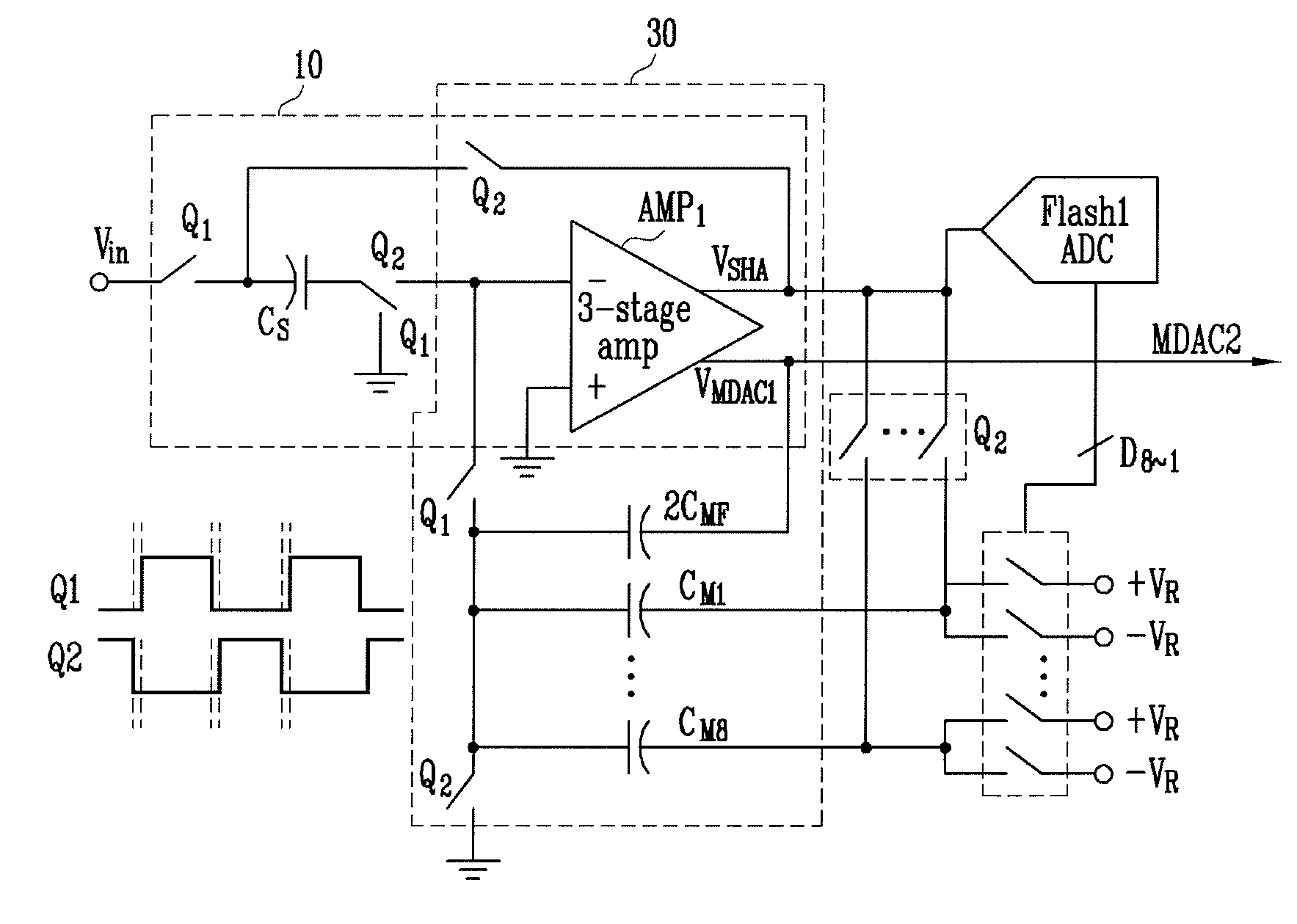
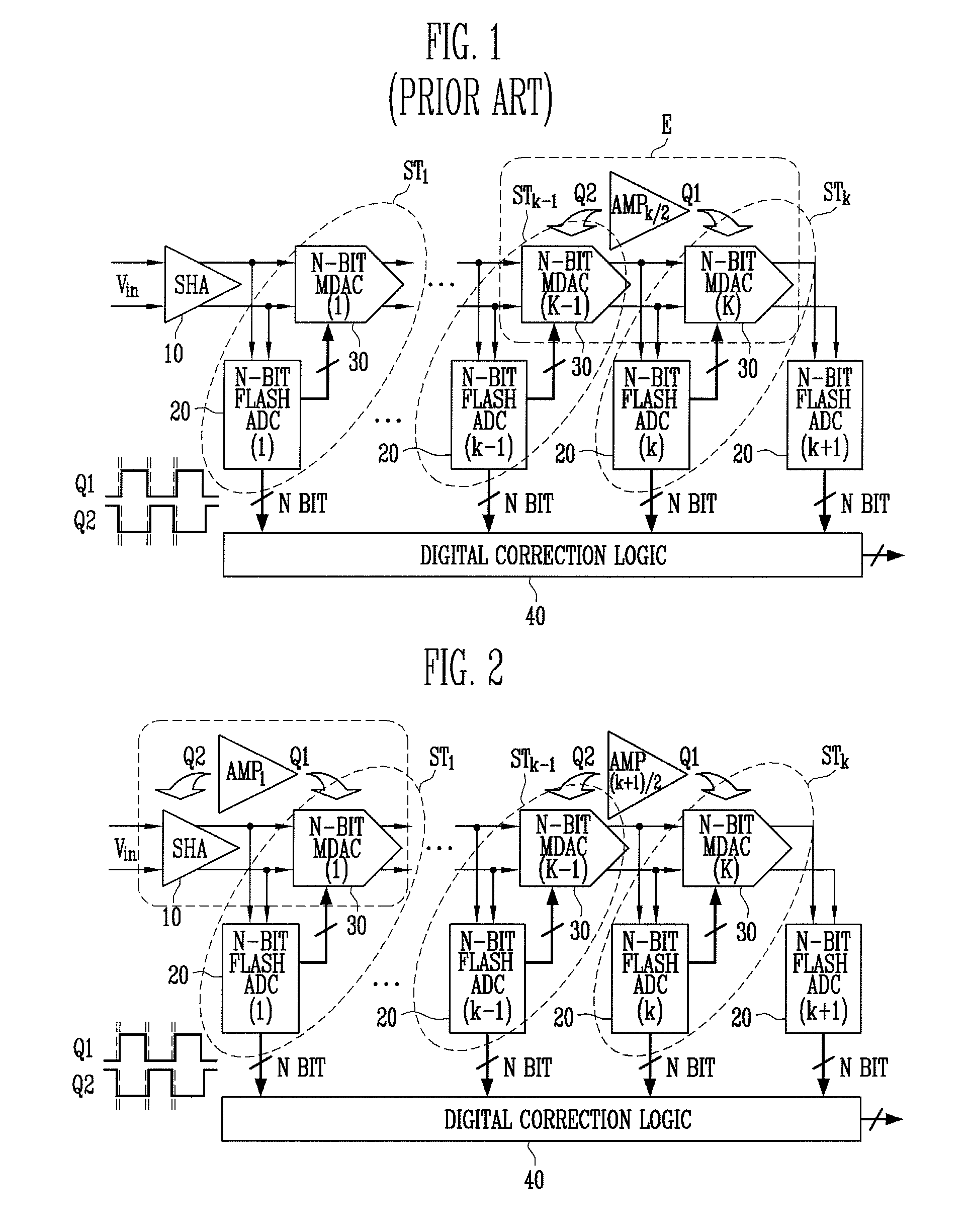
Multi-bit pipeline analog-to-digital converter having shared amplifier structure
ActiveUS7397409B2Reduce consumptionSmall sizeElectric signal transmission systemsAnalogue-digital convertersDigital down converterEngineering
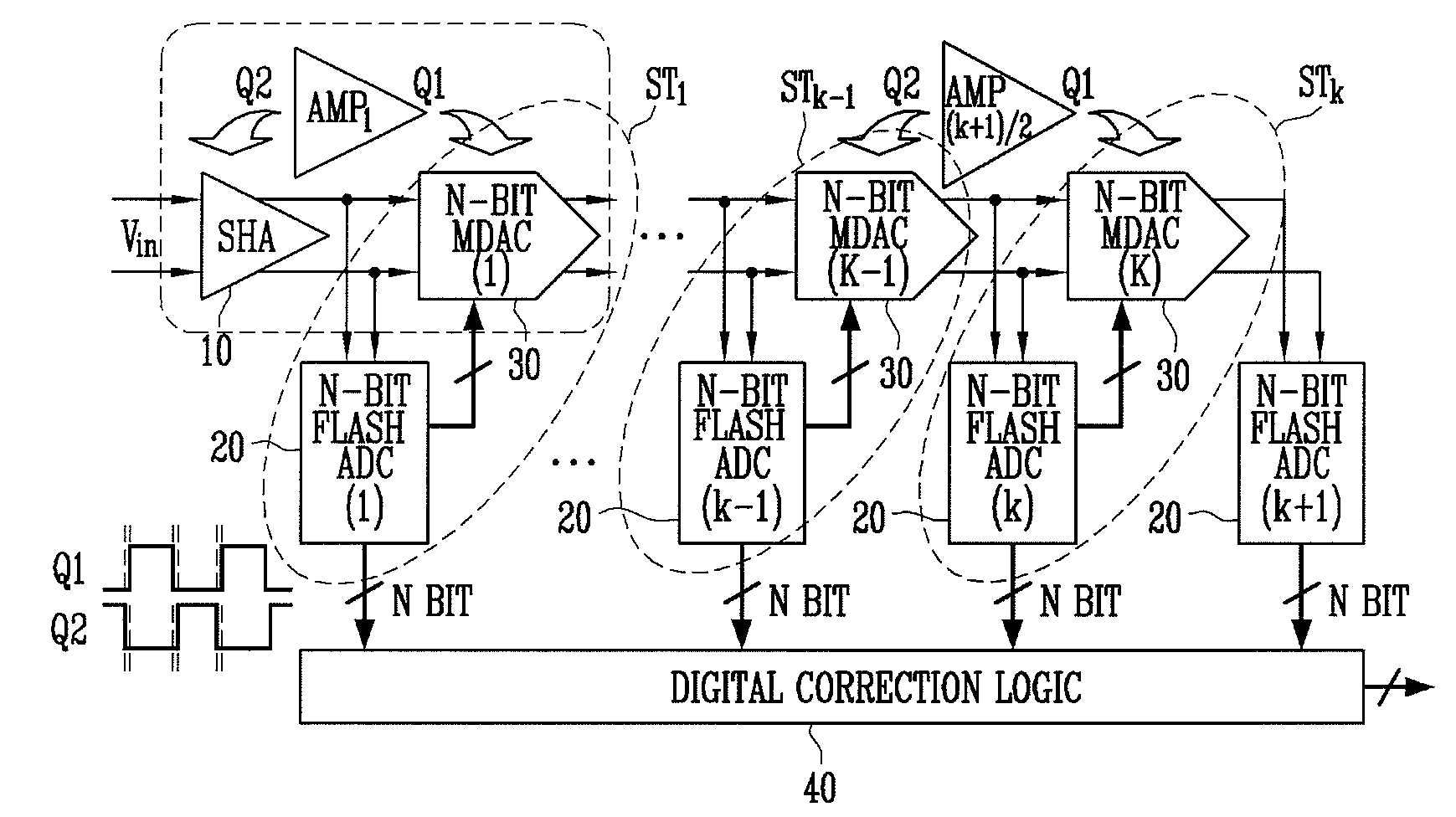
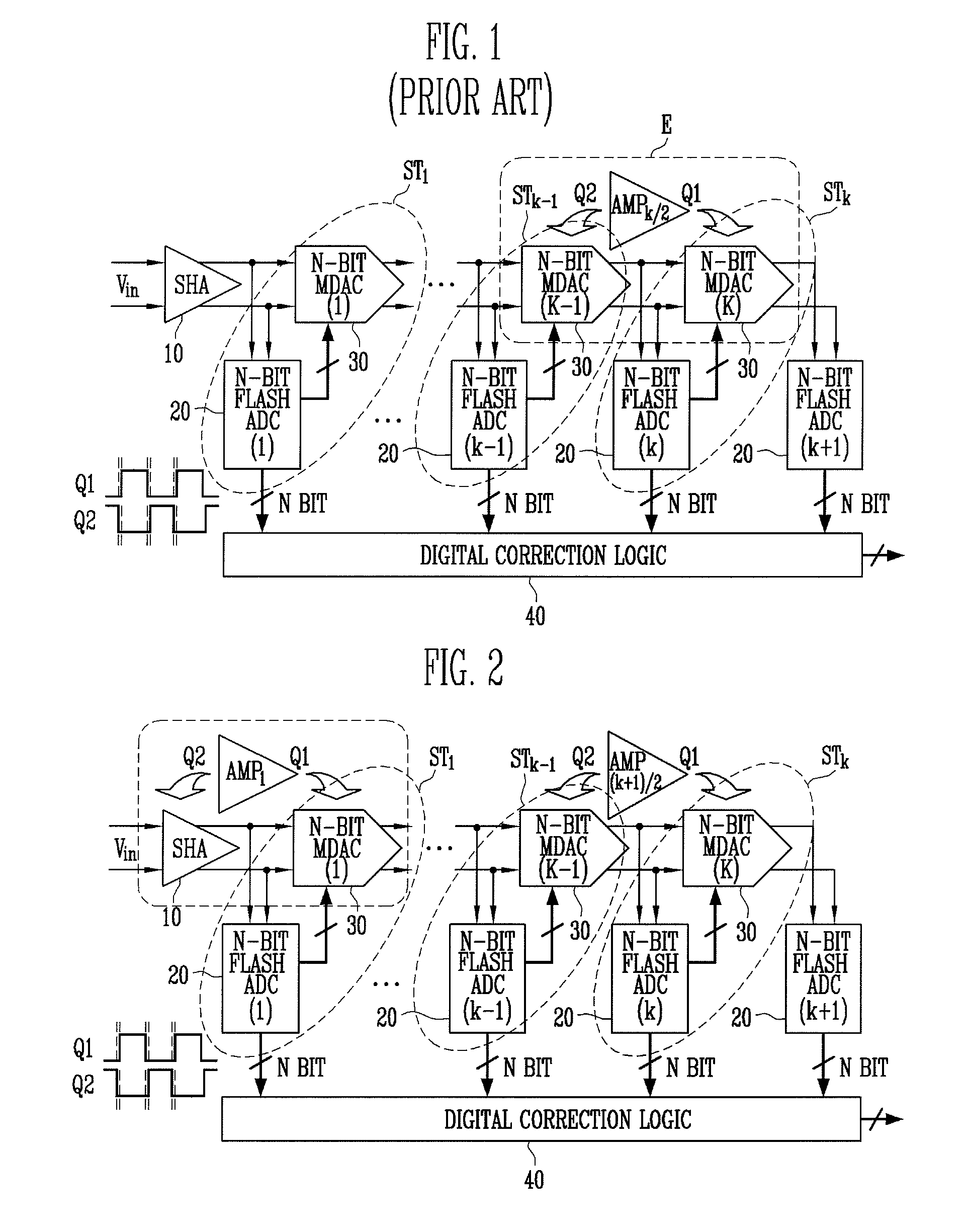
A multi-bit pipeline analog-to-digital converter (ADC) having a shared amplifier structure includes: a sample-and-hold amplifier (SHA) for sampling and holding an input analog voltage and removing a sampling error of the input voltage; N-bit flash ADCs of first to K-th stages receiving analog signals, converting them into digital signals and outputting the digital signals; N-bit multiplying digital-to-analog converters (MDACs) of first to K-th stages converting differences between the digital signals output from the N-bit flash ADCs and output signals of preceding stages back into analog signals and outputting the analog signals; and a three-stage amplifier connected to an output of the N-bit MDAC of the first stage at a first clock and an output of the SHA at a second clock, wherein intergers N>= and K>=2. An amplifier can be shared between an SHA and an MDAC of a first stage, thereby reducing power consumption and chip size.In the multi-bit pipeline ADC, an amplifier can be shared between an SHA consuming much power and an MDAC of a first stage, so that power consumption and chip size can be reduced.
Owner:ELECTRONICS & TELECOMM RES INST
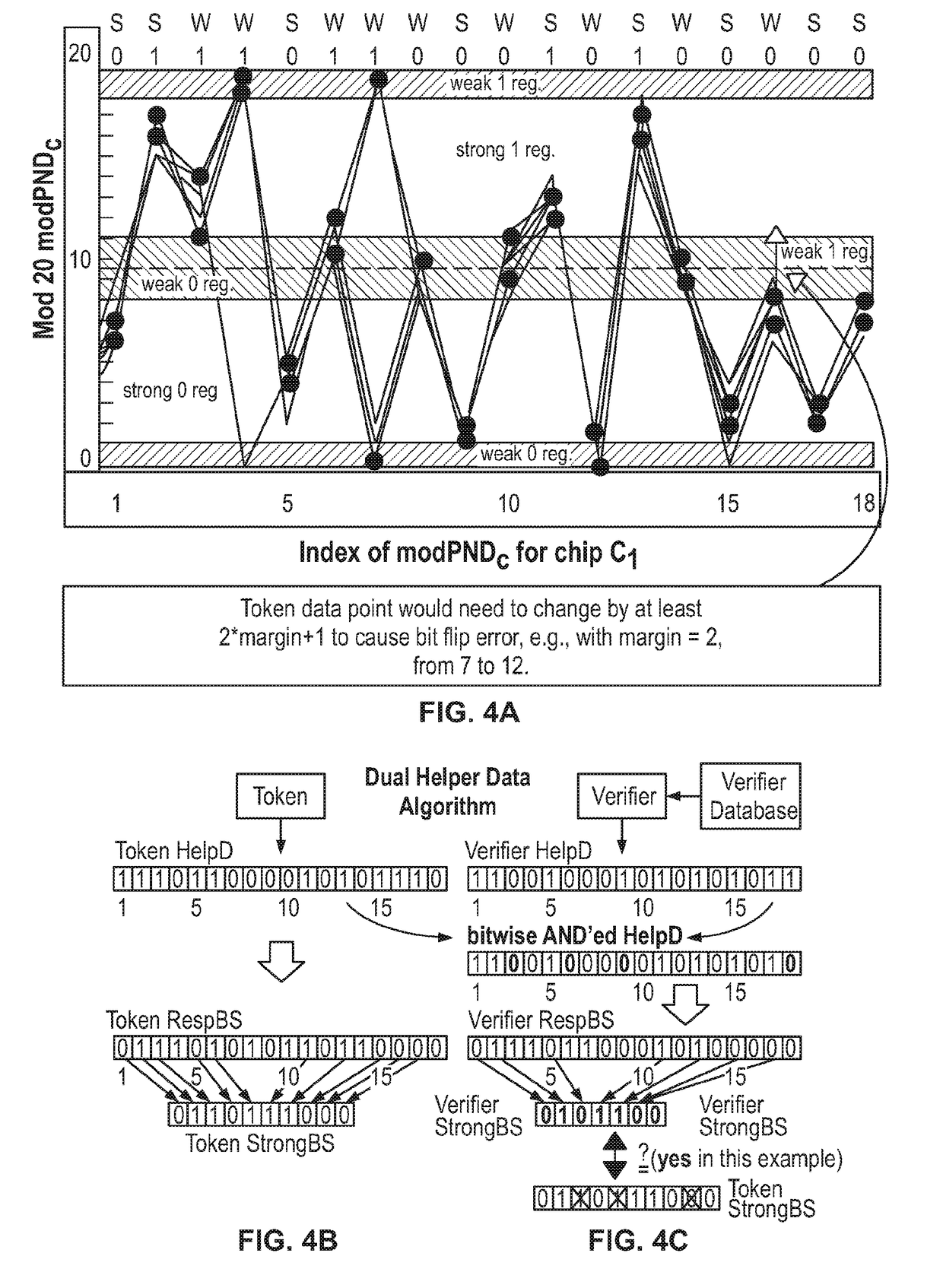
A privacy-preserving, mutual puf-based authentication protocol
ActiveUS20190026457A1Improve reliabilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareDigitization
An authentication protocol using a Hardware-Embedded Delay PUF (“HELP”), which derives randomness from within-die path delay variations that occur along the paths within a hardware implementation of a cryptographic primitive, for example, the Advanced Encryption Standard (“AES”) algorithm or Secure Hash Algorithm 3 (“SHA-3”). The digitized timing values which represent the path delays are stored in a database on a secure server (verifier) as an alternative to storing PUF response bitstrings thereby enabling the development of an efficient authentication protocol that provides both privacy and mutual authentication.
Owner:STC UNM
System for scaling a system of related windows-based servers of all types operating in a cloud system, including file management and presentation, in a completely secured and encrypted system
The described embodiment of the system includes business methods and software and hardware that creates a cloud based Windows operating system server system that provides education and collaboration tools and system s to general education providers, business entities, and medical professionals and patients, and provides a system of real time delivery of services and information to users. The system uses SSL, AES, RC6, SHA, and UDP VPN over SSL, along with HMAC style logins to provide end-to-end security from within and external to the cloud. It provides online collaboration including live video streaming, email, SMS and live chat. It provides file handling for the conversion of paper medical records into electronic versions.
Owner:LOVE THOMAS +1
Data interaction method and data interaction device based on CHAP protocol
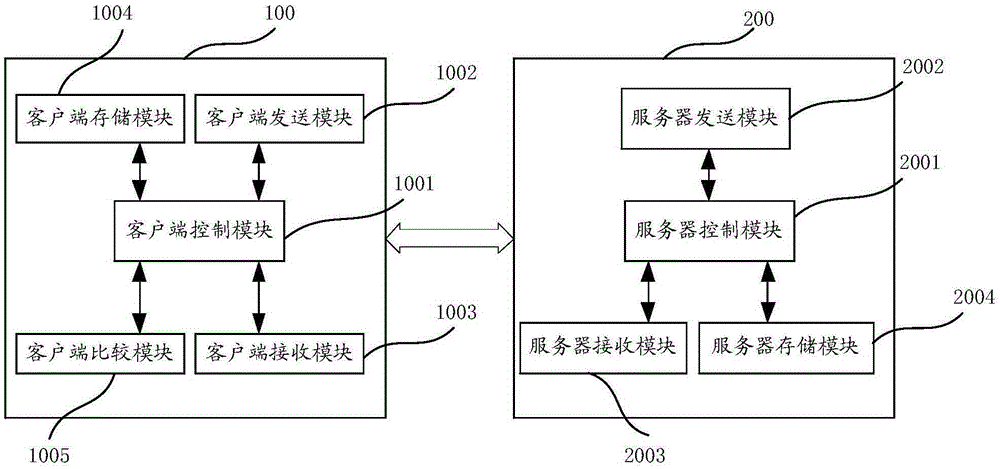
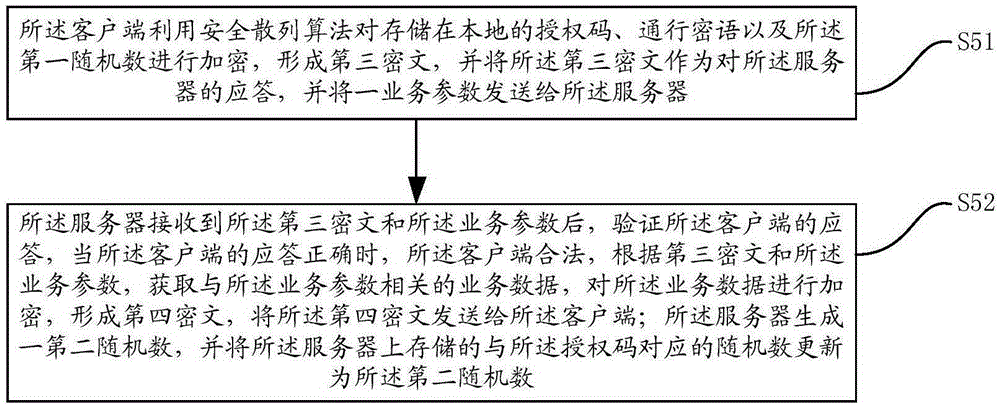
ActiveCN105282168AAchieve legitimacyImplement authenticationUser identity/authority verificationInteraction deviceClient-side
The invention provides a data interaction method and a data interaction device based on the CHAP protocol. The data interaction device based on the CHAP protocol comprises a client and a server. The client and the server carry out data interaction after identity authentication succeeds. The legitimacy of the client and the server is verified using a first random number, an asymmetric encryption algorithm and a secure hash algorithm, and therefore, identity authentication between the client and the server is realized, and attack from the middleman is avoided. Data transmission is carried out between the client and the server after identity authentication succeeds, so that the safety and reliability of data transmission between the client and the server are ensured, and replay attack is avoided.
Owner:SHENGQU INFORMATION TECH SHANGHAI
Image compressed encryption method based on compressed sensing and Chua's circuit
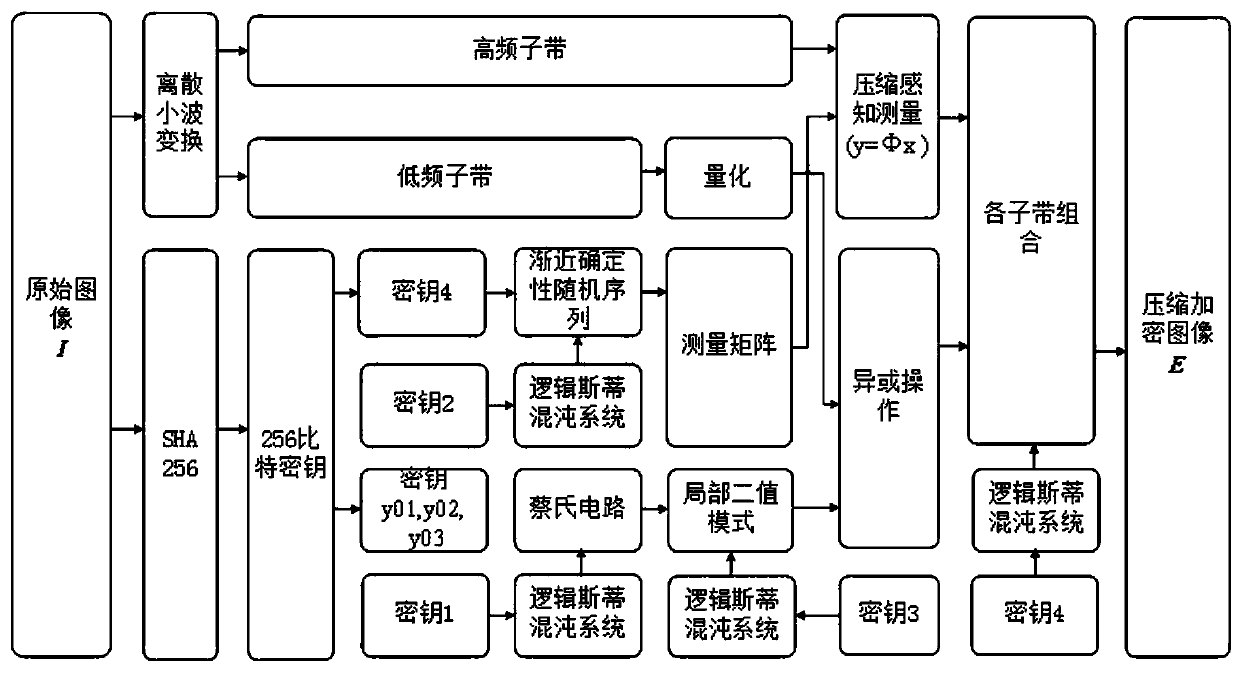
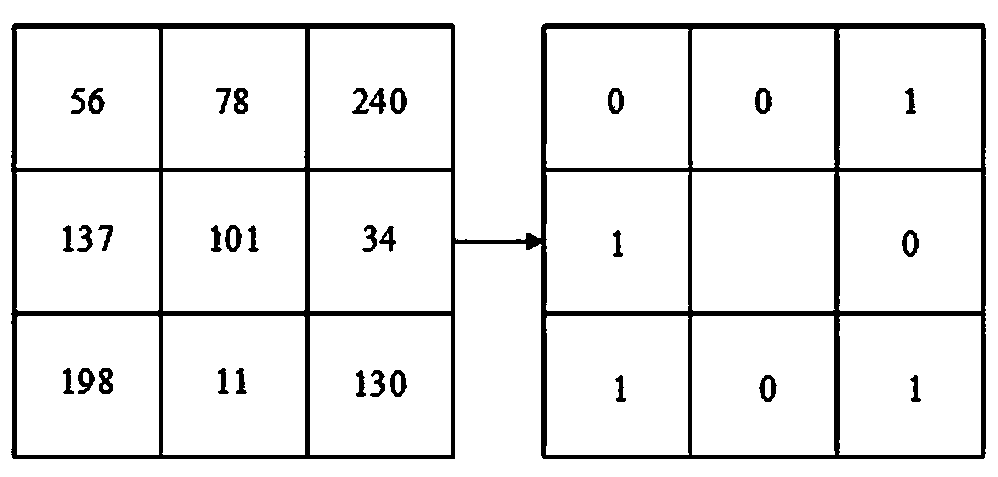
InactiveCN108235029AResistance to Differential AttacksRandomDigital video signal modificationPattern recognitionImage compression
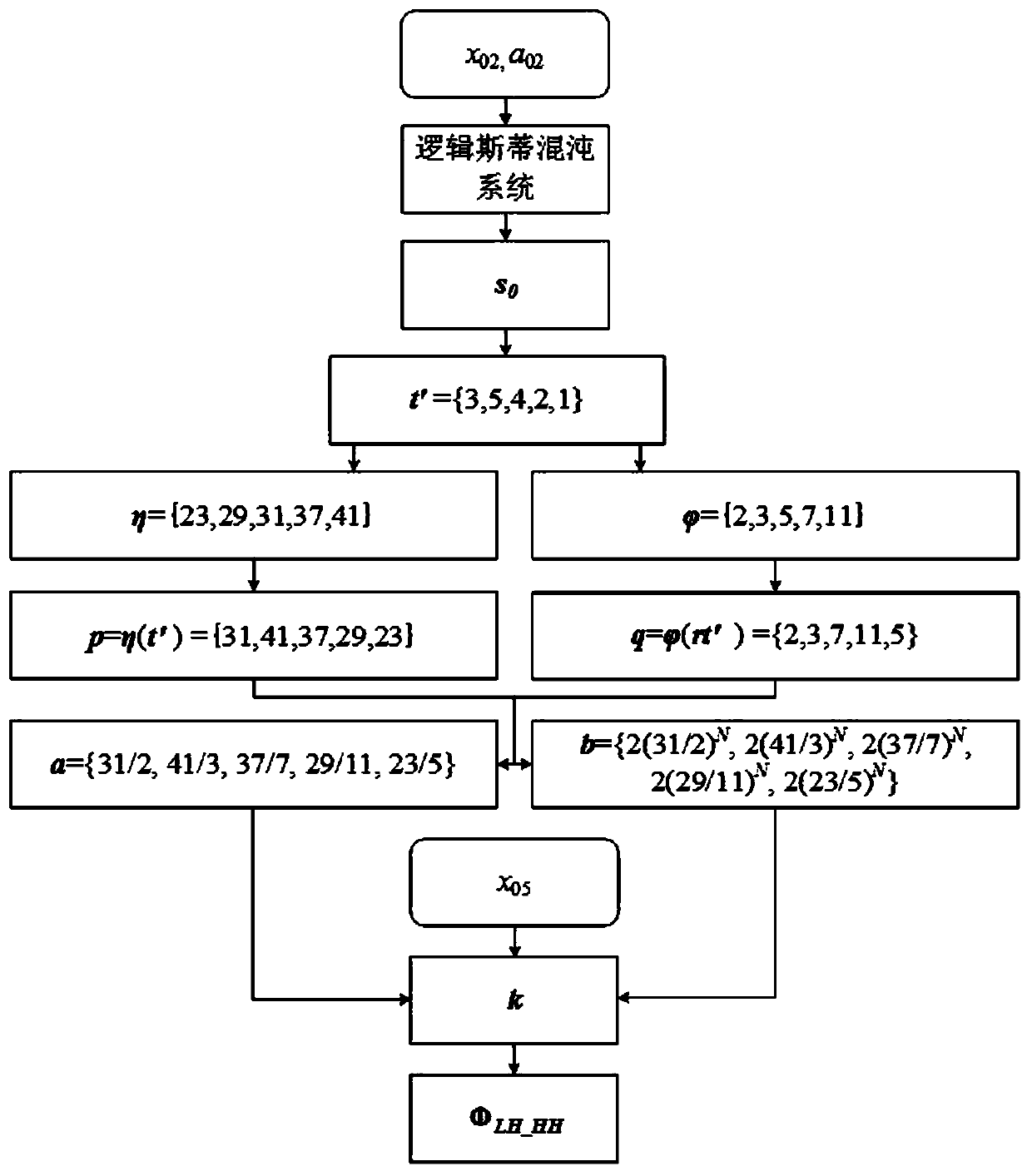
The invention discloses an image compressed encryption method based on compressed sensing and a Chua's circuit. The method comprises the following steps of 1, generating a key related to plaintext according to an original image by using SHA-256; 2, performing iteration on initial values x02 and a02 to generate a chaos sequence t' and t'', and generating measurement matrixes FORMULA and FORMULA through performing iteration on t' and t''; 3, measuring sub-bands LH, HH and HL by different compression ratios; 4, quantizing to acquire an integer sequence z, and forming a matrix z'; 5, acquiring a diffusion matrix f'; 6, acquiring a matrix LL', and performing an XOR operation on the diffusion matrix f'; and 7, combining four sub-bands such as LL, LH, HL and HH, and scrambling the chaos sequencegenerated by x04 and a04 to acquire a final compressed encryption image E. According to the method the data transmission quantity can be reduced, the robustness of the image can also be enhanced, thesecurity is high, and particularly, the method is good in performance when being used for resisting shearing attacks and noise attacks.
Owner:GUANGXI NORMAL UNIV
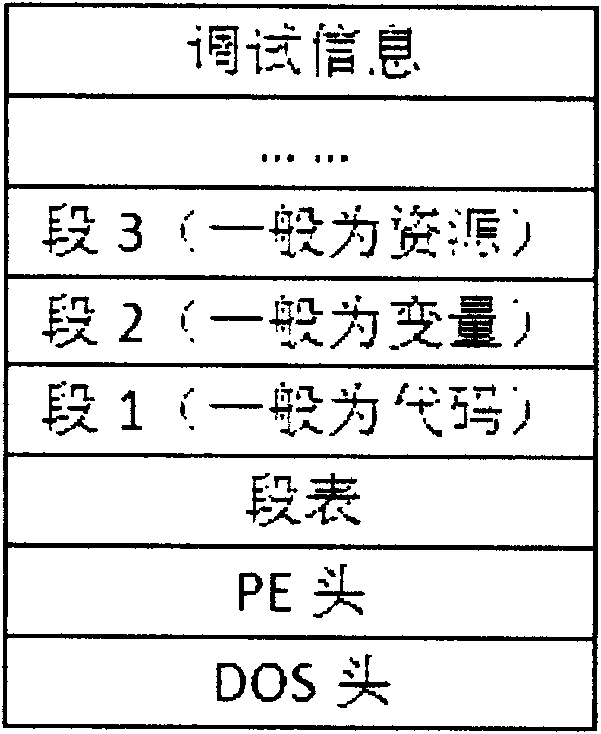
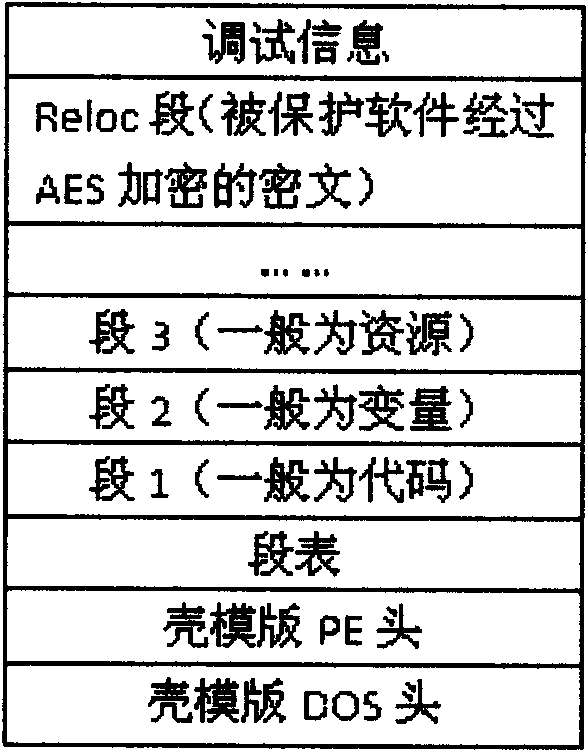
PE loader-based software packing protection method
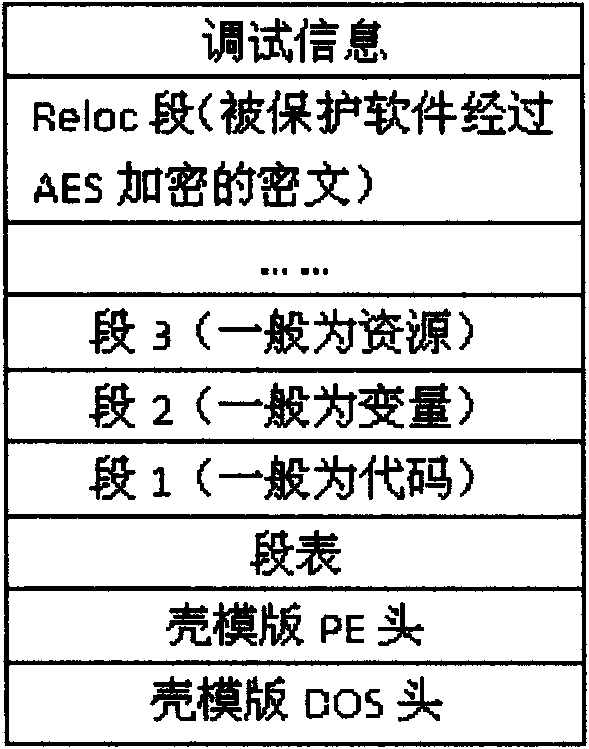
InactiveCN101964040APrevent disassembly crackingPrevent illegal tamperingPlatform integrity maintainanceData ingestionInternal memory
The invention relates to a PE loader-based software packing protection method. The method comprises the following steps of: mapping a shell template into an internal memory, repositioning the base address of the shell template by simulating a PE loader of Windows and calculating a relative virtual address (RVA) of a segment where the entry point of the shell template is positioned and the size of the segment, wherein the calculated RVA value of the segment and the size value of the segment are taken as parameters and a hash value calculated by a secure hash algorithm (SHA) is taken as a key of an advanced encryption standard (AES) encryption algorithm; mapping protected software into the internal memory and encrypting the protected software by the AES encryption algorithm by using calculated key; adding encrypted data into a Reloc segment of the shell template; processing a special resource in the software to be protected and extracting additional data of the special resource, attaching the special resource and the additional data to the end of a shell template file respectively and modifying a corresponding data item related to the special resource in the PE structure of the shell template; and repeating the modified shell template from the internal memory to a disc so as to obtain protected software. The method remarkably enhances the safety of the software.
Owner:XIAN UNIV OF TECH
Multi-bit pipeline analog-to-digital converter having shared amplifier structure
ActiveUS20080068237A1Reduce consumptionSmall sizeElectric signal transmission systemsAnalogue-digital convertersDigital down converterEngineering
Provided is a multi-bit pipeline analog-to-digital converter (ADC) having a shared amplifier structure. The multi-bit pipeline ADC includes: a sample-and-hold amplifier (SHA) for sampling and holding an input analog voltage and removing a sampling error of the input voltage; N-bit flash ADCs of first to K-th stages receiving analog signals, converting them into digital signals and outputting the digital signals; N-bit multiplying digital-to-analog converters (MDACs) of first to K-th stages converting differences between the digital signals output from the N-bit flash ADCs and output signals of preceding stages back into analog signals and outputting the analog signals; and a three-stage amplifier connected with an output of the N-bit MDAC of the first stage at a first clock and an output of the SHA at a second clock, wherein N is an integer greater than or equal to 1 and K is an integer greater than or equal to 2.In the multi-bit pipeline ADC, an amplifier can be shared between an SHA consuming much power and an MDAC of a first stage, so that power consumption and chip size can be reduced.
Owner:ELECTRONICS & TELECOMM RES INST
Method and system for partial matching query of encrypted field in database
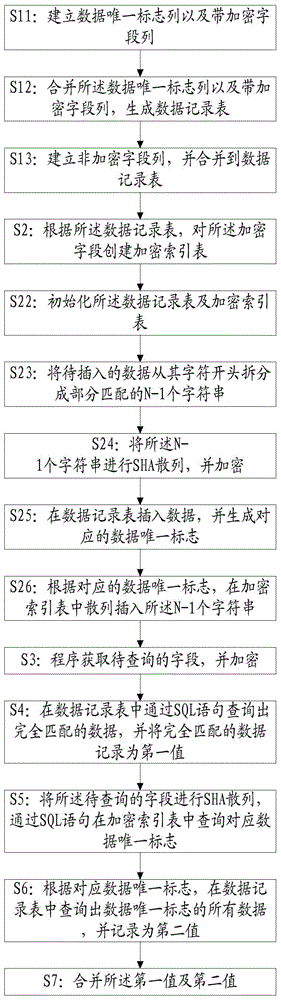
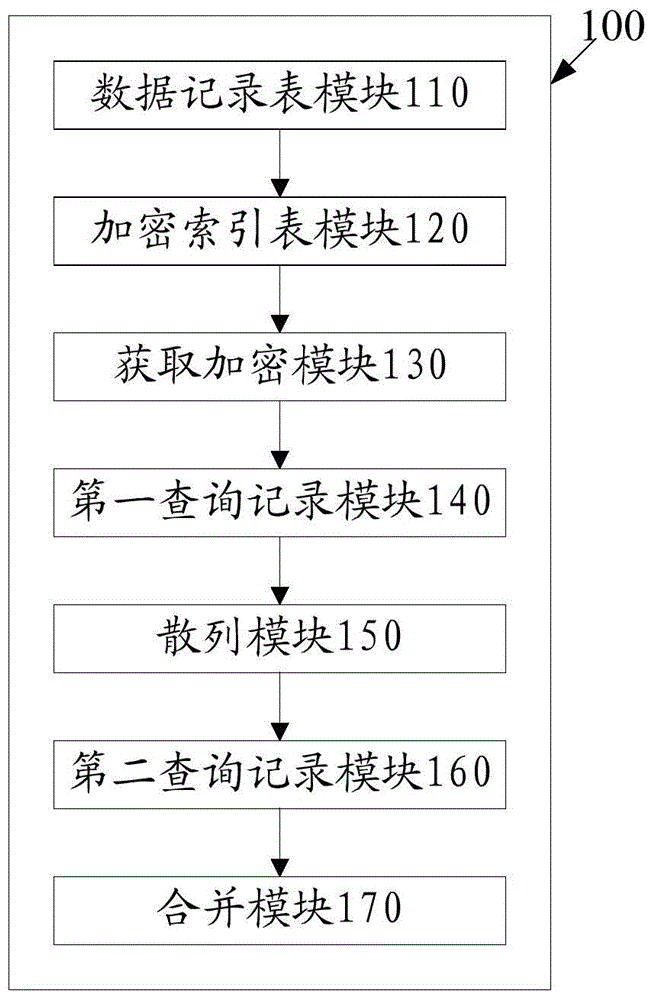
ActiveCN105138585AEasy to operateImprove efficiencySpecial data processing applicationsUsabilityDatabase encryption
The invention discloses a method and a system for partial matching query of an encrypted field in a database. The method comprises the following steps: creating a data record table; creating an encrypted index table for the encrypted field according to the data record table; obtaining and encrypting a to-be-queried field by program; querying completely matched data from the data record table through a structured query language (SQL) sentence, and recording the completely matched data as first values; carrying out secure hash algorithm (SHA) hashing on the to-be-queried field, and querying a corresponding unique data identifier from the encrypted index table through the SQL sentence; and querying all data with the unique data identifier in the data record table according to the corresponding unique data identifier, and recording the data as second values; and merging the first values with the second values. In the manner, an encryption scheme can be used only by partial matching query of the field under the condition of ensuring the performance, so that the safety and the usability of the system are improved.
Owner:FUJIAN TQ DIGITAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com