Password protecting method and device
A password protection and password technology, applied in the field of information security, can solve the problems of user security risks, inability to guarantee password security, password leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
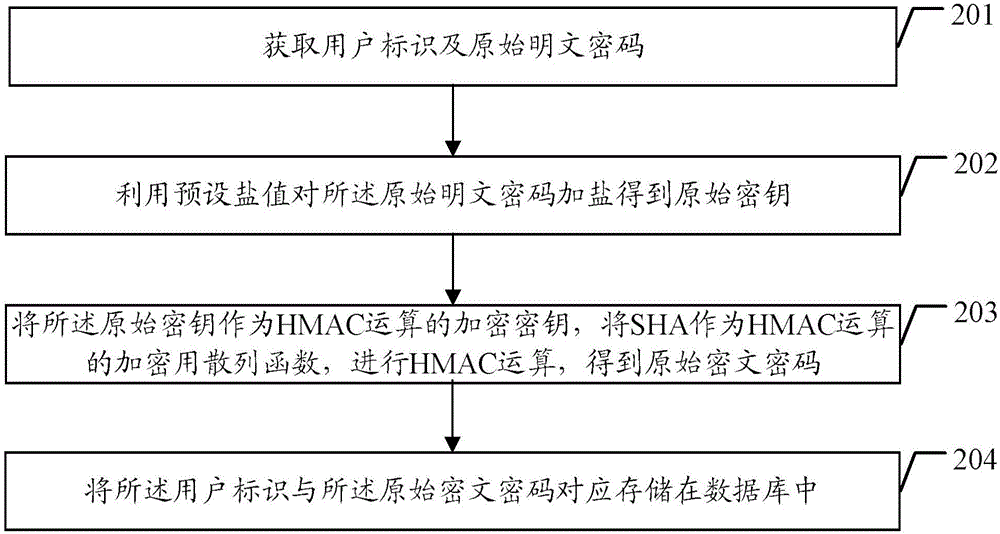
[0028] Such as figure 2 As shown, the method of the present embodiment includes the following steps:
[0029] Step 201, obtaining the user ID and the original plaintext password;
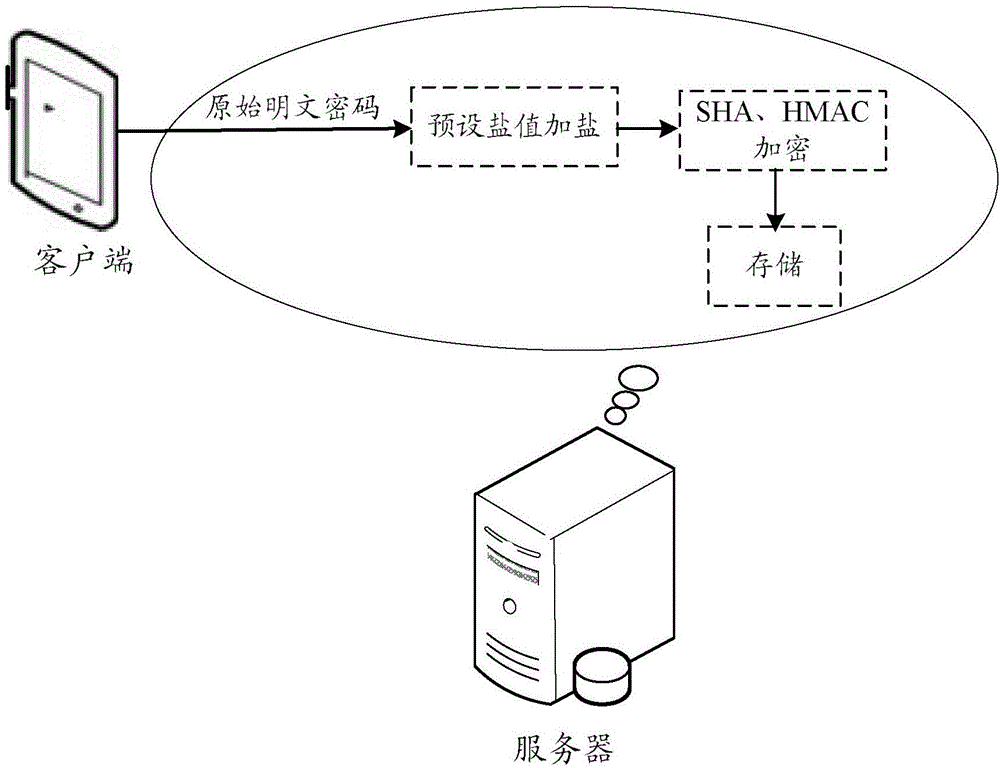
[0030] In specific implementation, when the client registers, the server can obtain the user ID and original plaintext password from the client. The user ID can also be called a user name, registered account number, etc., and the original plaintext password is the registration password provided by the client during registration.
[0031] The client can directly carry the user ID and the original plaintext password in the registration request, and the server can directly obtain the user ID and the original plaintext password from the registration request. However, in this way, the password will be transmitted between the client and the server in plain text, which is easily intercepted by a third party, resulting in password disclosure. Therefore, in this embodiment, the client can also encrypt the...
Embodiment 2
[0051] The method described in Embodiment 1 will be further described in detail in this embodiment with an example. The description process of this embodiment will be divided into two stages, namely, the registration stage and the verification stage. The following describes the process of the registration phase first, such as Figure 3a As shown, the registration phase includes the following steps:
[0052] Step 301, receiving the registration request sent by the client, the registration request includes the user ID and the first ciphertext, and the first ciphertext is obtained by encrypting the original plaintext password by the client using a preset encryption algorithm;
[0053] The user ID can also be called a user name, a registered account number, etc., and the original plaintext password is the registration password provided by the client during registration.
[0054] Specifically, the client can first encrypt the original plaintext password with the RSA public key, an...
Embodiment 3
[0089] In order to better implement the above method, the embodiment of the present invention also provides a password protection device, such as Figure 5 As shown, the password protection device of this embodiment includes: an acquisition unit 501, a salt addition unit 502, a first encryption unit 503 and a storage unit 504, as follows:
[0090] (1) acquisition unit 501;
[0091] The acquiring unit 501 is configured to acquire the user ID and the original plaintext password.
[0092] In a specific implementation, the obtaining unit 501 can obtain the user ID and the original plaintext password from the client when the client registers. The user ID can also be called a user name, a registered account number, etc., and the original plaintext password is the registration password provided by the client during registration. .
[0093] The device in this embodiment may also include a receiving unit, the client may directly carry the user ID and the original plaintext password i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com