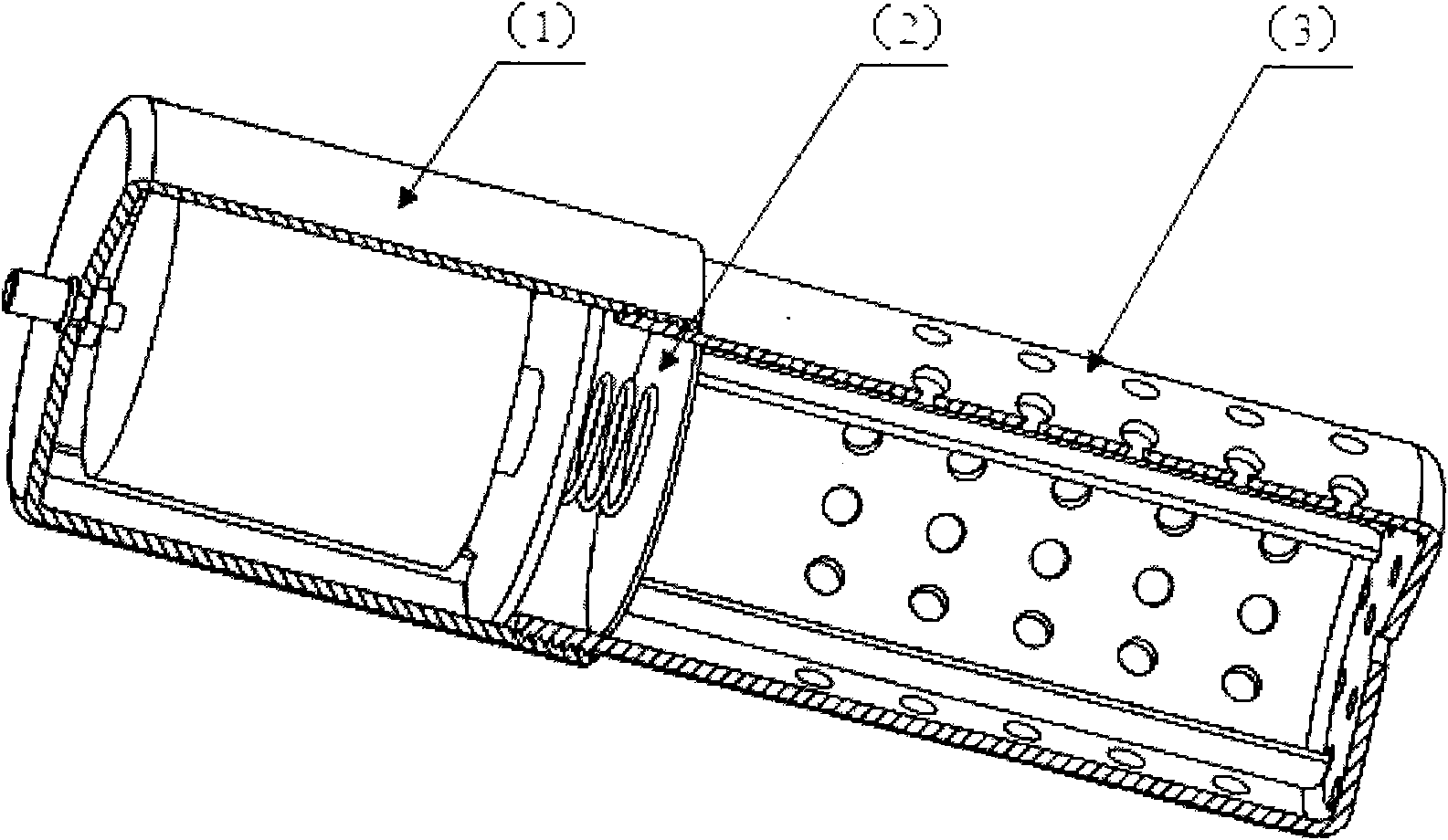
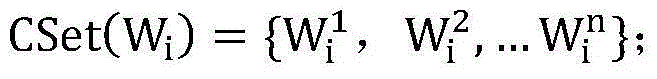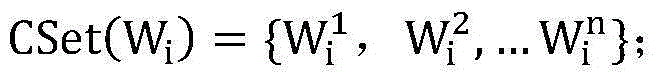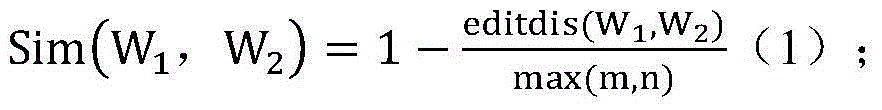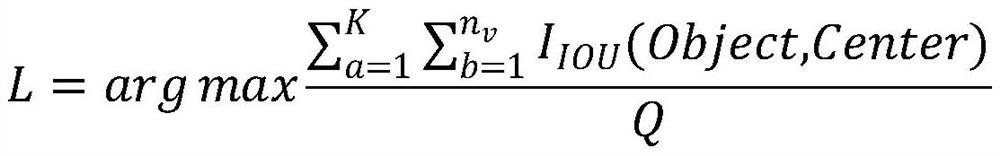Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
182results about How to "Meet the actual application needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
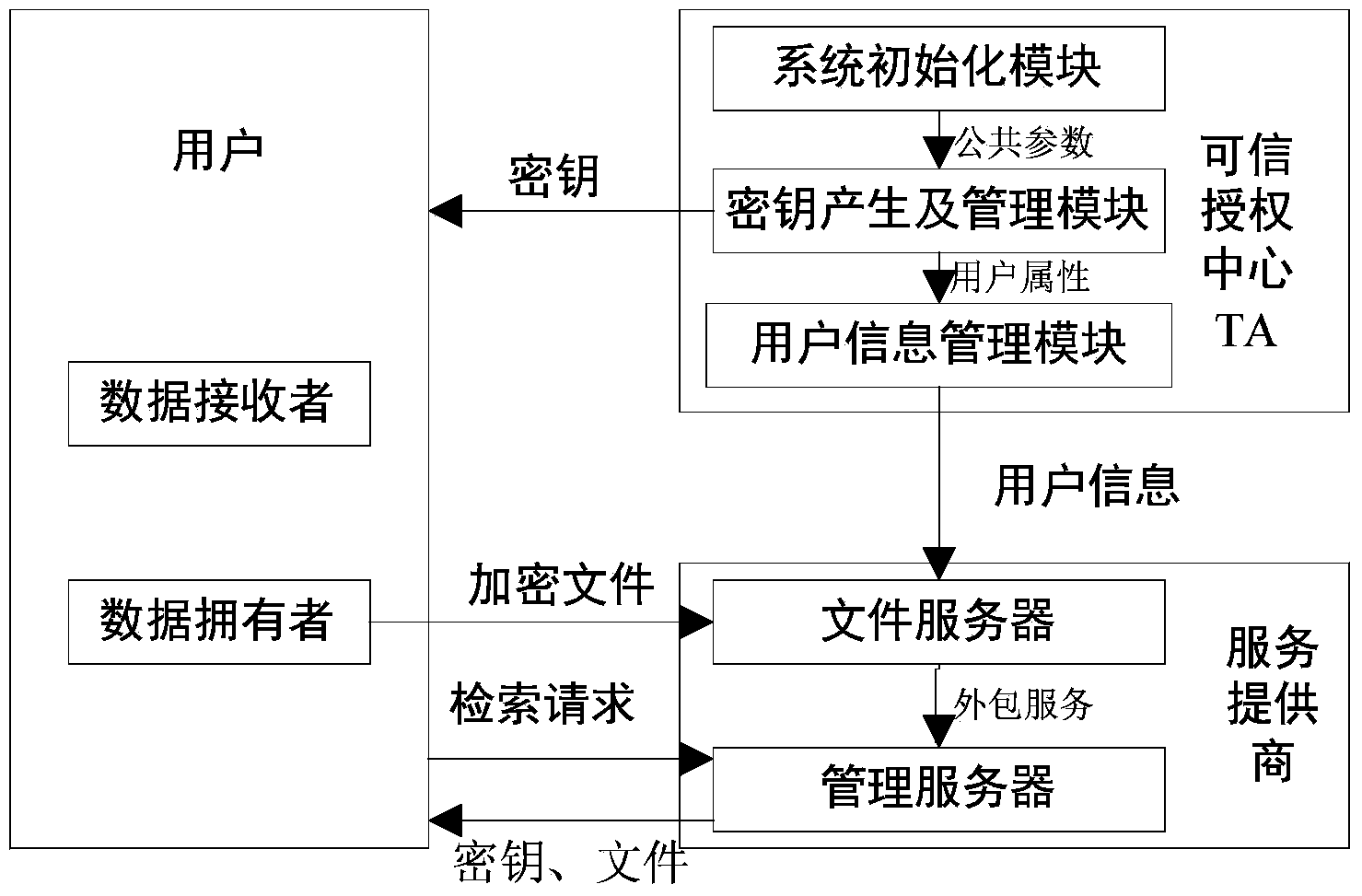
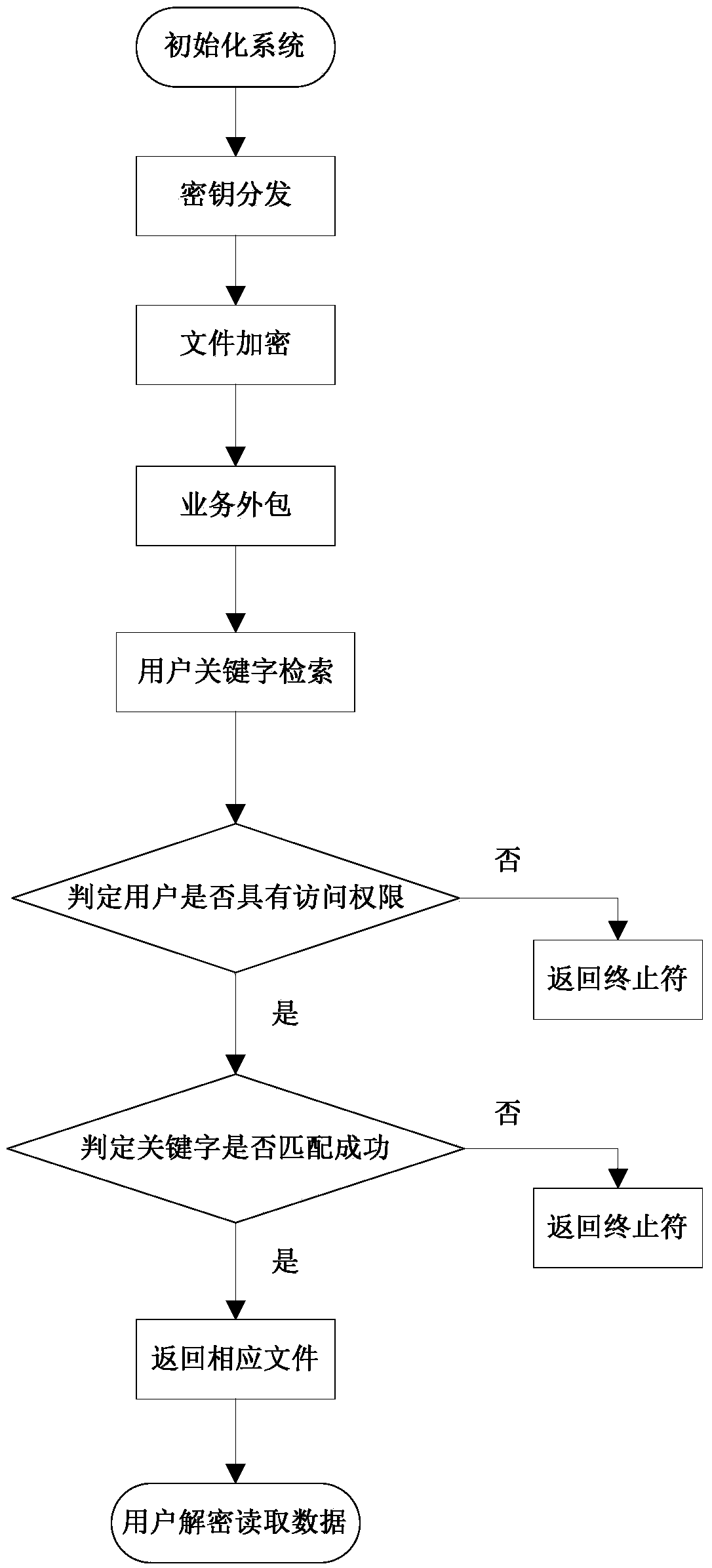
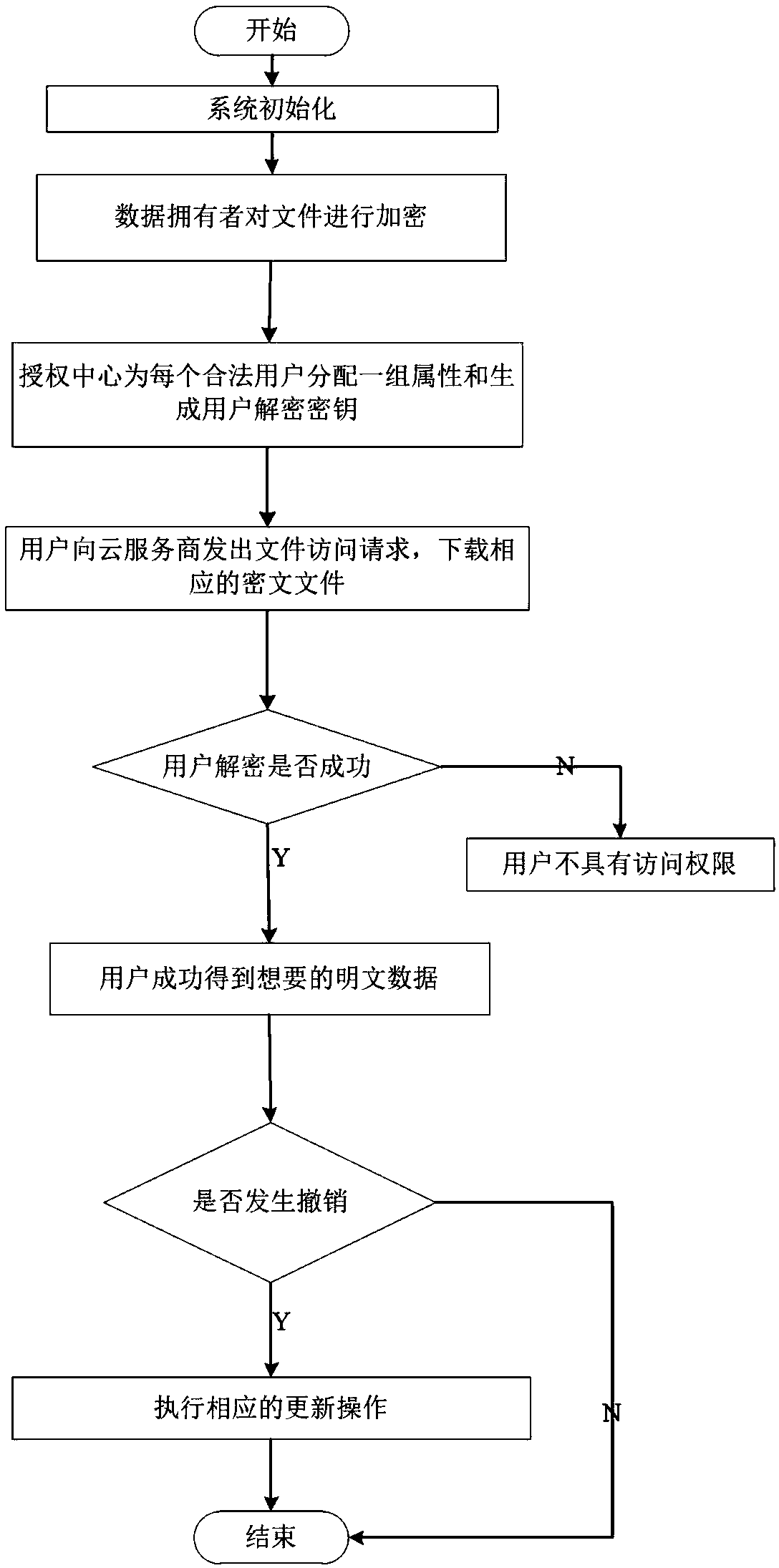
Multi-user supported searchable encryption system and method
InactiveCN103731432AMeet the actual application needsImprove securityKey distribution for secure communicationSpecial data processing applicationsData providerService provision
The invention discloses a multi-user supported searchable encryption system and method and accordingly the problem that specific encrypted files cannot be searched accurately in the prior art is mainly solved. The multi-user supported searchable encryption system comprises a credible authorization center TA, service providers and users; the credible authorization center TA is formed by a system initialization module, a secret key generation and management module and a user information management module; the service providers comprise a file server and a management server; the users comprise data providers and data receivers. The multi-user supported searchable encryption method comprises the steps of system initialization, secret key distribution, file encryption, business outsourcing, file retrieval, user decryption and user logout and adding. According to the multi-user supported searchable encryption system and method, the file retrieval time of the users is shortened due to the establishment of a key word index on files, the storage and computational overhead of the users is reduced due to the accurate file retrieval, the file retrieval is accurate, meanwhile the forward and backward security of the files is ensured, and meanwhile the multi-user simultaneous decryption is supported.
Owner:西安电子科技大学昆山创新研究院 +1
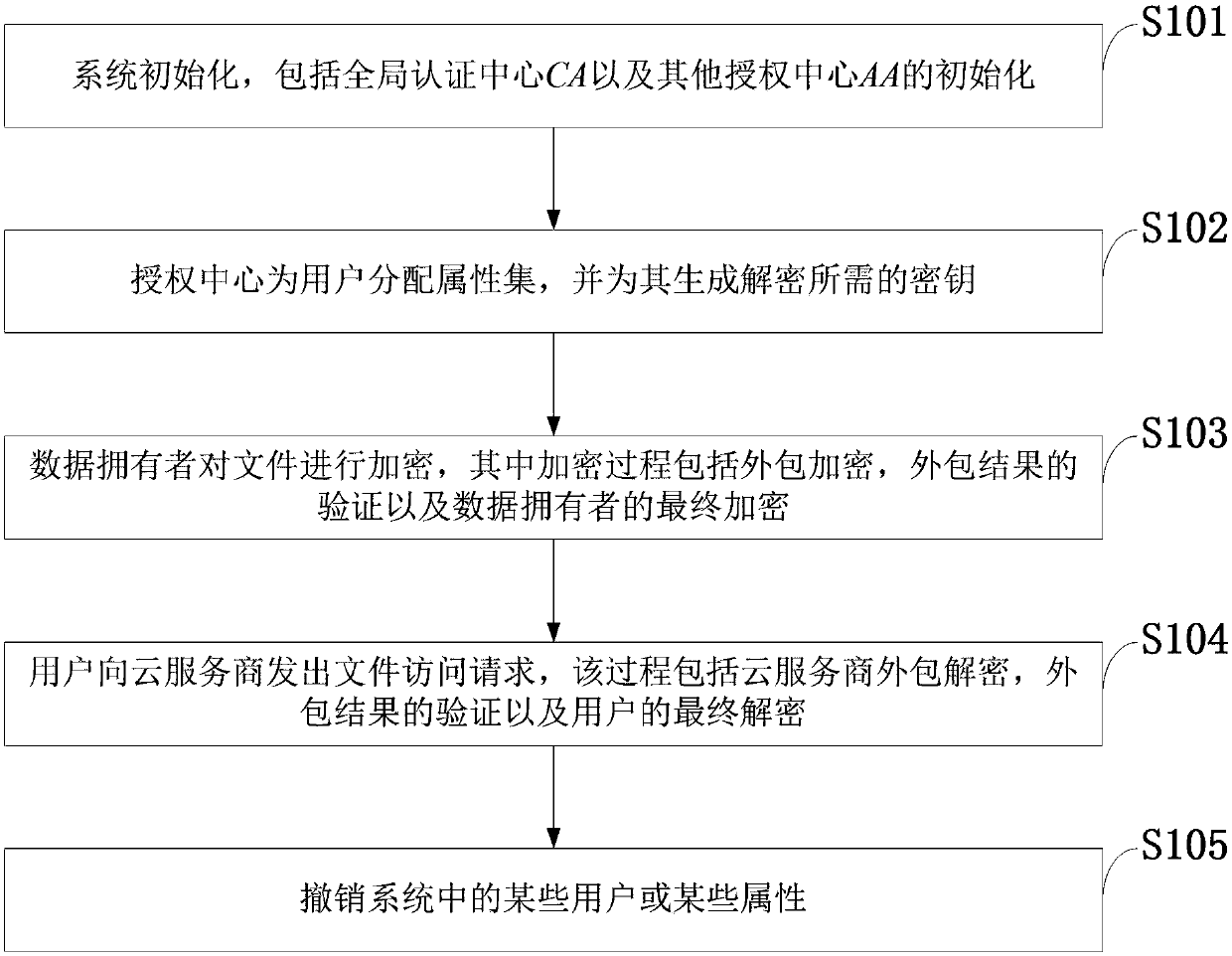
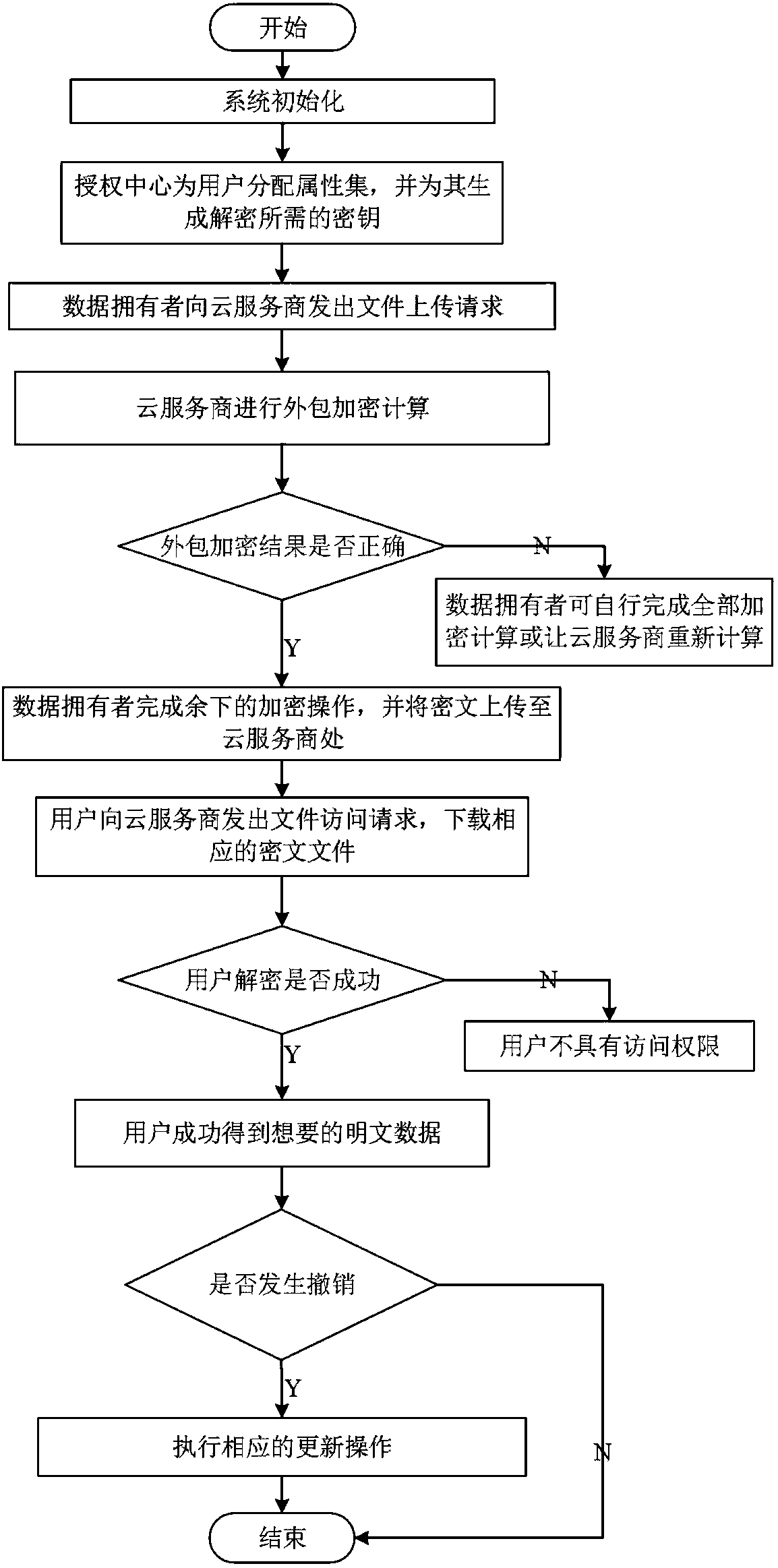
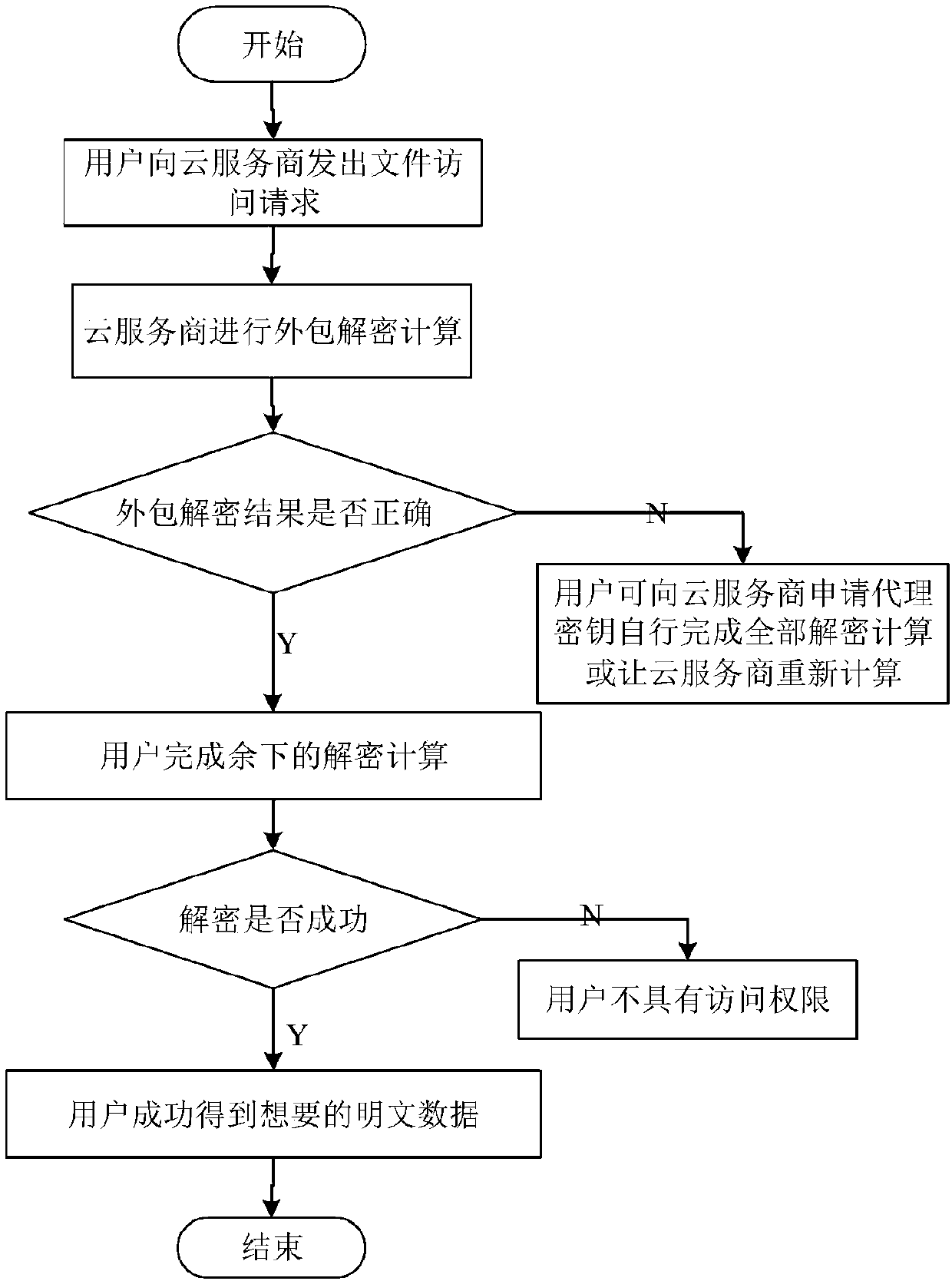
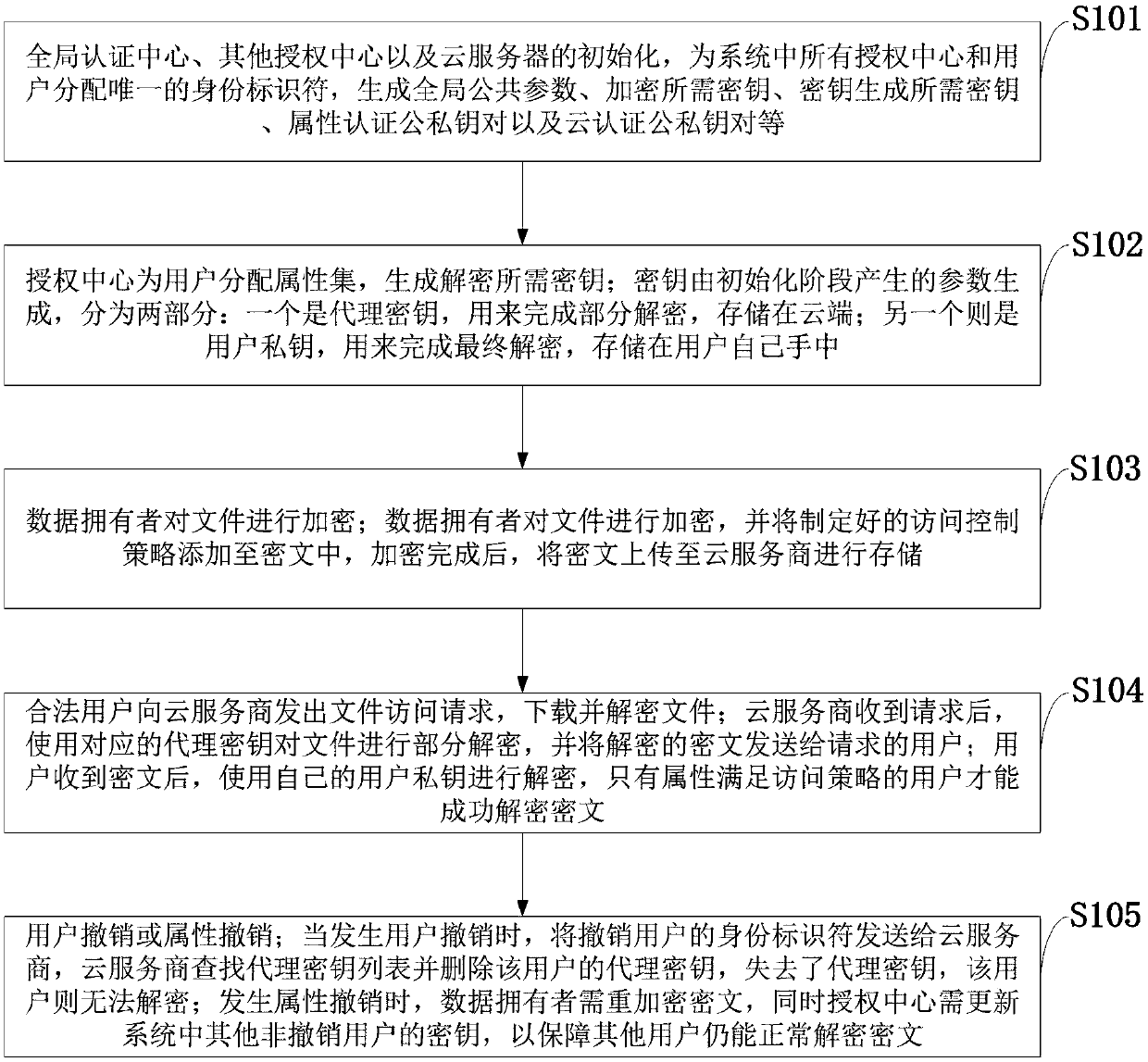
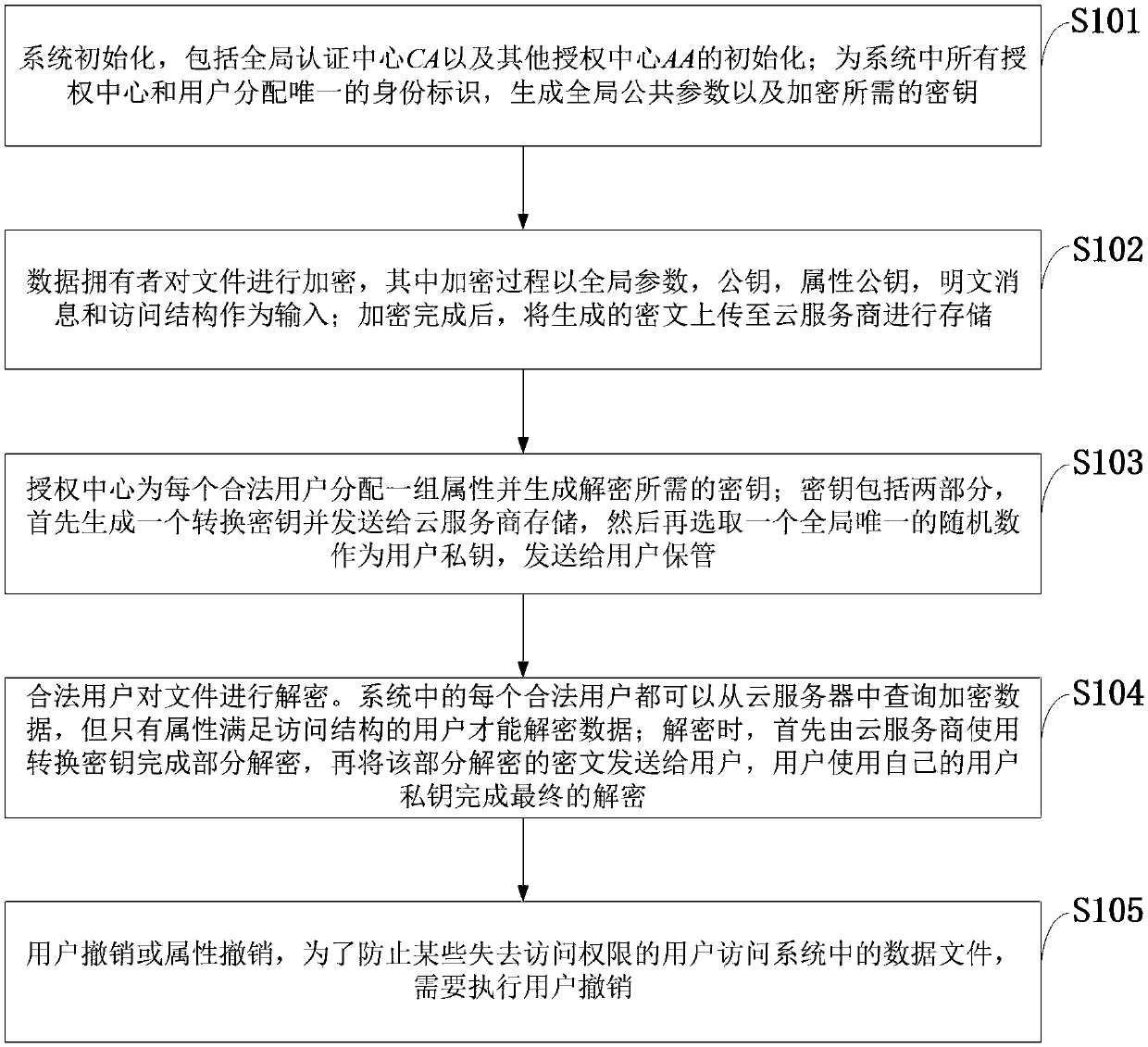
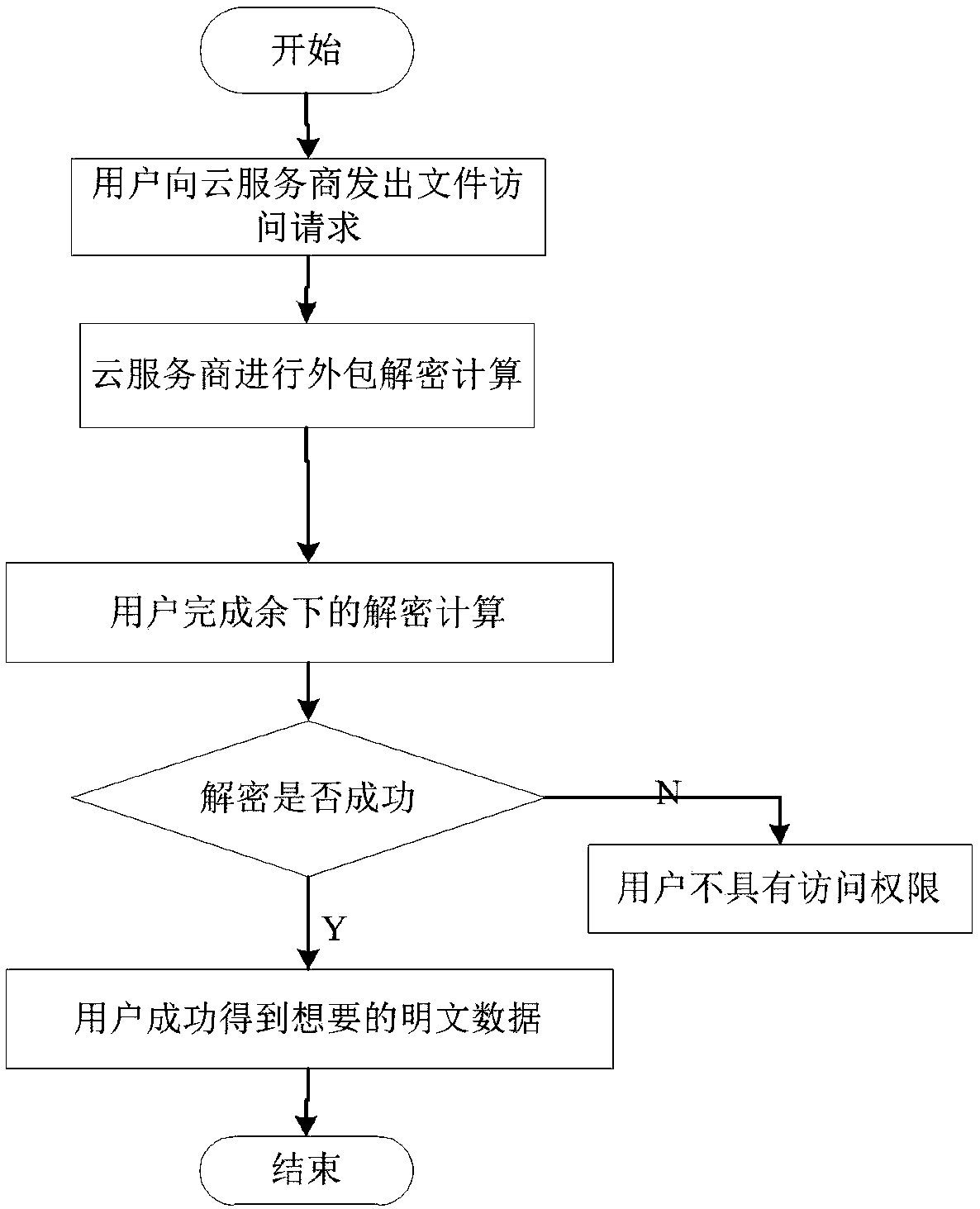
Cancellation-supported outsourcing verifiable multi-authorization center access control method, and cloud server
ActiveCN108390876ARich domainImprove efficiencyKey distribution for secure communicationUser PrivilegeCloud storage
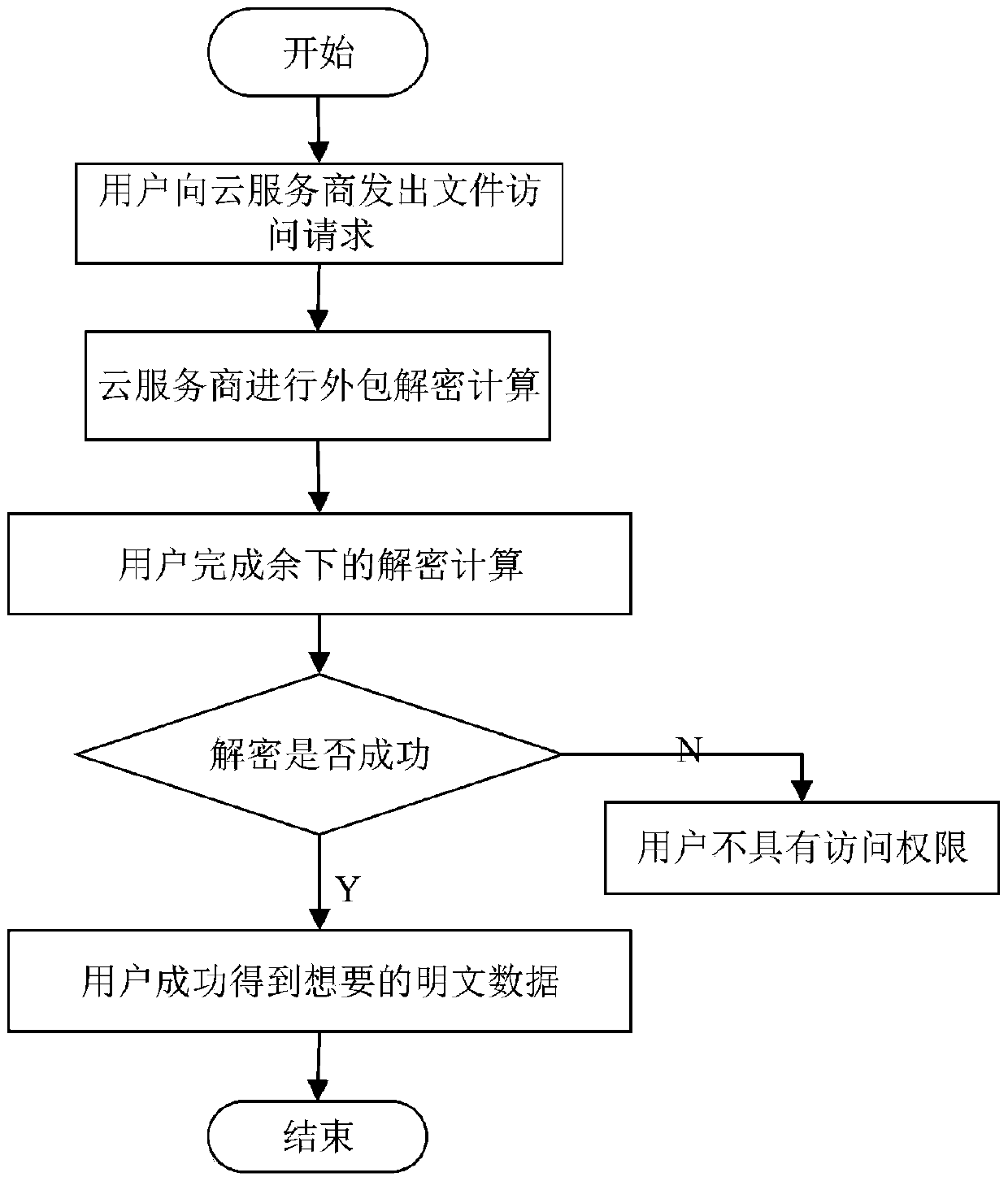
The invention belongs to the technical field characterized by a protocol, and discloses a cancellation-supported outsourcing verifiable multi-authorization center access control method, and a cloud server. The method comprises the following steps: system initialization, including the initialization of a global authentication center and other authorization centers; allocating an attribute set for auser by the authorization centers, and generating a secret key needed by decryption for the user; encrypting a file by a data owner, wherein the encryption process comprises outsourcing encryption, the verification of an outsourcing result and the final encryption of the data owner; issuing a file access request to a cloud service provider by the user, wherein the process includes cloud service provider outsourcing decryption, the verification of the outsourcing result, and the final decryption of the user; and cancelling some users or some attributes in a system. The cancellation-supported outsourcing verifiable multi-authorization center access control method provided by the invention has the advantages of being high in system access efficiency, low in computation overhead, capable of supporting dynamic user authority management and the like, and can be used for guaranteeing the privacy data safety of the user in cloud storage, reducing the computation overhead of the user and dynamically managing the authority of the user in the system.
Owner:XIDIAN UNIV
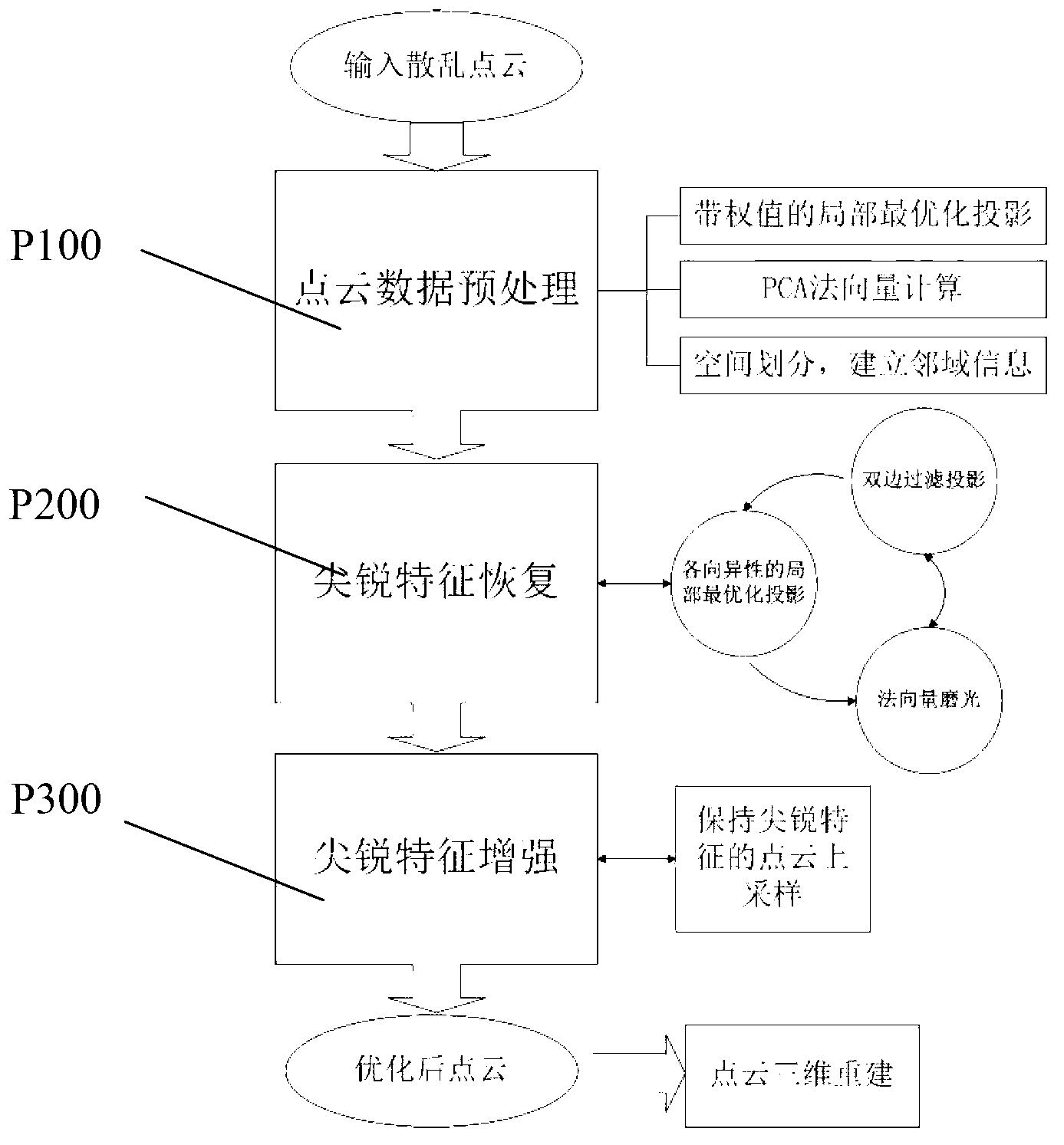
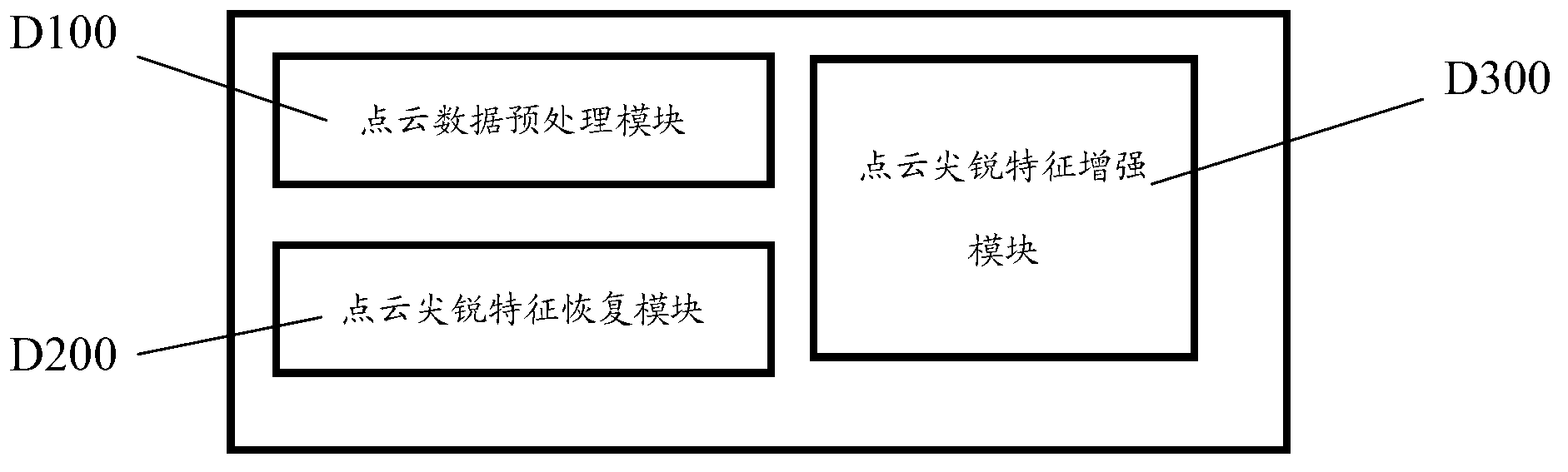
Device and method for point cloud optimization
InactiveCN103065354AEasy to adjustMeet the actual application needsImage enhancement3D modellingPoint cloudAutomation
A method for point cloud optimization includes point cloud data preprocessing steps, point cloud sharp feature recovering steps and point cloud sharp feature enhancing steps, wherein the point cloud data preprocessing steps include large-scale random scanning point cloud simplifying, noise reducing, exterior point removing, homogenization, normal vector calculating and space structure division preprocessing, the point cloud sharp feature recovering steps include further projection and normal vector calculating and point cloud sharp feature recovering, and the point cloud sharp feature enhancing steps include point cloud sharp feature up-sampling and point cloud sharp feature enhancing. By enhancing sharp features of random scanning point cloud, a three-dimensional model finally achieved is up to the requirement of practical application. Meanwhile, optimized point cloud is more concise and neat, so that the existing art can be more suitable for adjusting parameters and capable of improving efficiency. In other words, under the condition that existing point cloud three-dimensional reconstruction processes are not changed, by optimizing raw materials of point cloud, degree of automation, production efficiency and quality of products are improved.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
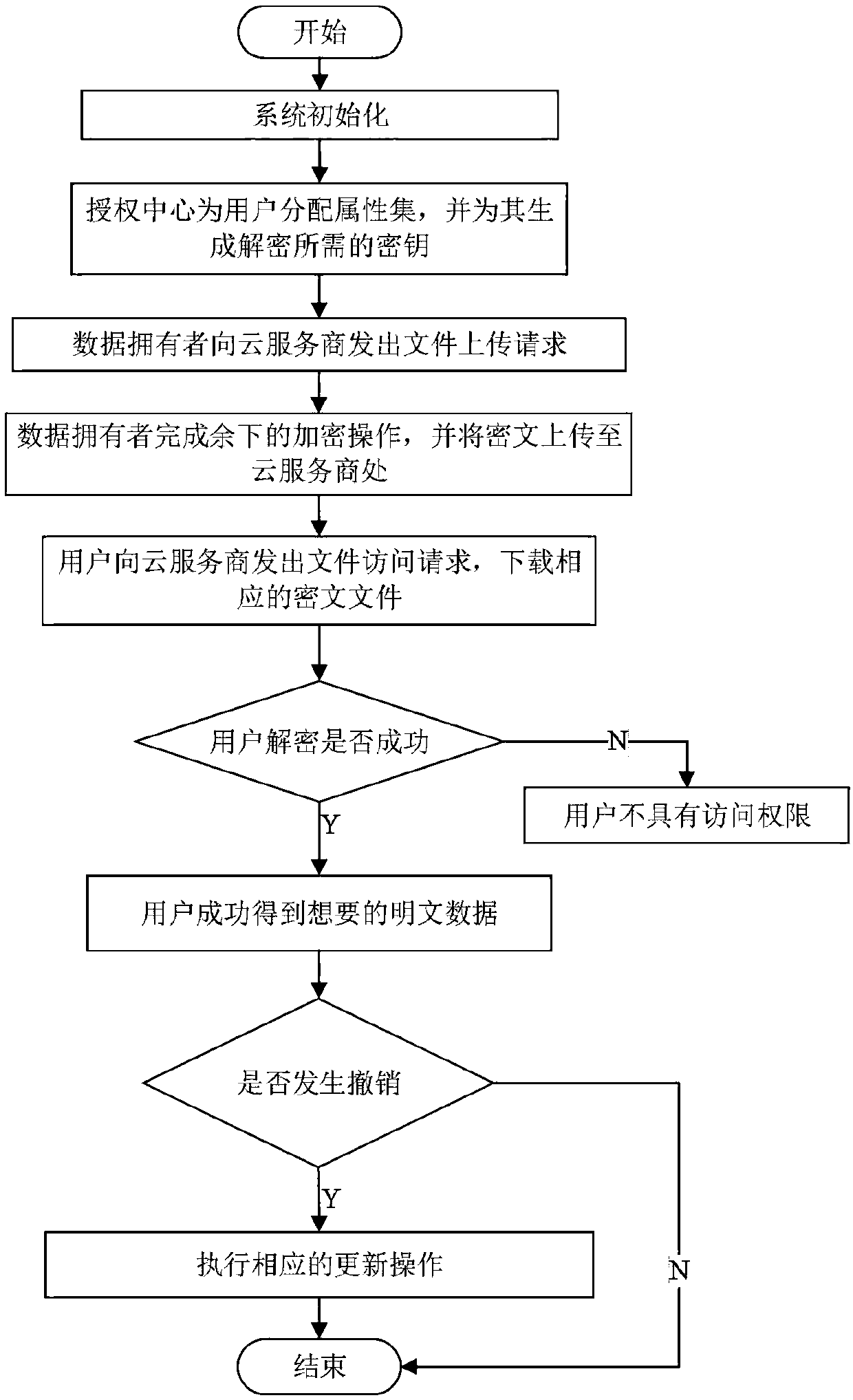
Agent-based revocable multi-authorization center access control method and cloud storage system
ActiveCN108810004ARich domainAvoid Collusion AttacksKey distribution for secure communicationUser PrivilegeData information
The invention belongs to the technical field of wireless communication networks, and discloses an agent-based revocable multi-authorization center access control method and a cloud storage system. Themethod comprises the steps that system initialization is conducted, wherein initialization of a global authentication center CA and other authorization centers AA and initialization of a cloud serverare included; the authorization centers AA allocate attribute sets to users and generate keys needed for decryption for the users; a data owner encrypts a file; the users send file access requests toa cloud service provider, wherein the process comprises outsourcing decryption of the cloud service provider and final decryption of the users; and some users or some attributes in the system are revoked. The method has the advantages of being high in system efficiency, supporting dynamic user permission management and the like and can be used for ensuring the privacy data security of the users in the data information system, reducing the computing overhead of the users and dynamically managing the permissions of the users in the system.
Owner:XIDIAN UNIV
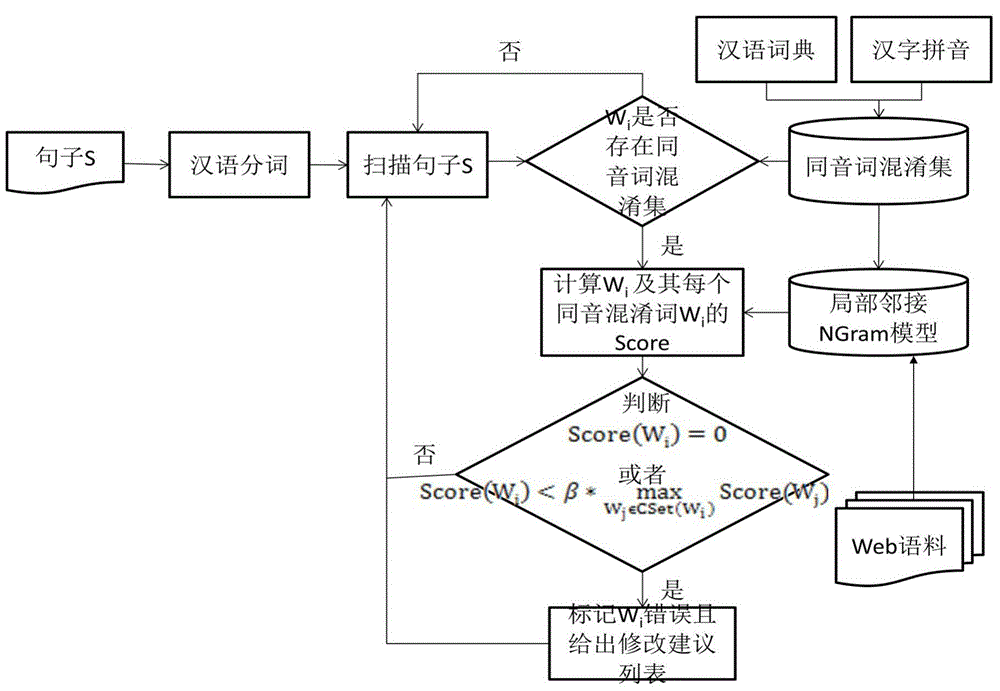
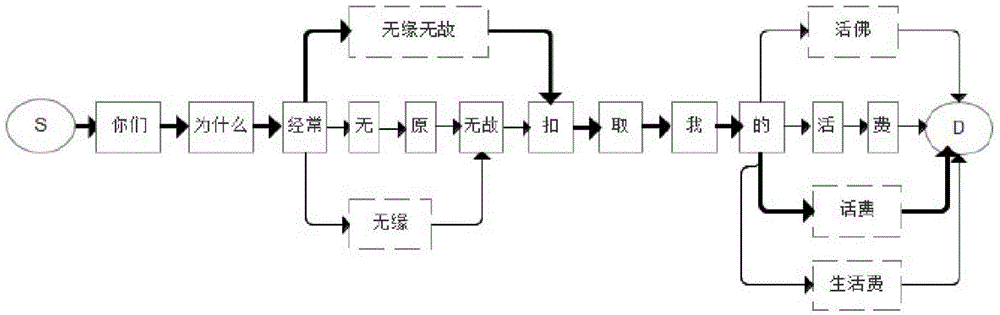
Chinese homonym error auto-proofreading method
ActiveCN105045778AQuick responseMeet the actual application needsSpecial data processing applicationsProbability estimationAlgorithm
The present invention discloses a Chinese homonym error auto-proofreading method. The method comprises: first, generating a confusion set of Chinese homonyms; through large-scale Web corpus training, collecting statistics on a left-adjacent binary model, a right-adjacent binary model, and an adjacent ternary model; obtaining a local adjacent NGram model by using the confusion set of Chinese homonyms and a probability estimation algorithm; by using a weighted combination method and by calculating a sentence context support degree of a word in a sentence and a sentence context support degree of a homonym in a homonym confusion set corresponding to the word, determining whether a homonym error exists; marking the homonym error and providing a correction suggestion list, so as to implement Chinese homonym auto-proofreading. The Chinese homonym error auto-proofreading method provided by the present invention is quick in system response and high in efficiency and accuracy, and meets precision requirements of actual applications.
Owner:JIANGSU UNIV OF SCI & TECH
Fuzzy word segmentation based non-multi-character word error automatic proofreading method
ActiveCN104991889AQuick responseMeet the actual application needsSpecial data processing applicationsChinese wordWord graph
The invention discloses a fuzzy word segmentation based non-multi-character word error automatic proofreading method. According to the method, accurate segmentation is carried out based on a correct word dictionary and a wrong character word dictionary to generate a word graph; then the similarity of Chinese word strings is calculated by utilizing a fuzzy matching algorithm, accurately segmented disperse strings are subjected to fuzzy matching, and a fuzzy matching result is added into the word graph to form a fuzzy word graph; and finally a shortest path of the fuzzy word graph is calculated by utilizing a binary model of words in combination with similarity, so that automatic proofreading of Chinese non-multi-character word errors is realized. According to the fuzzy word segmentation based non-multi-character word error automatic proofreading method provided by the invention, the system response is quick, the precision meets actual application demands, and the effectiveness and the accuracy are high.
Owner:南方电网互联网服务有限公司
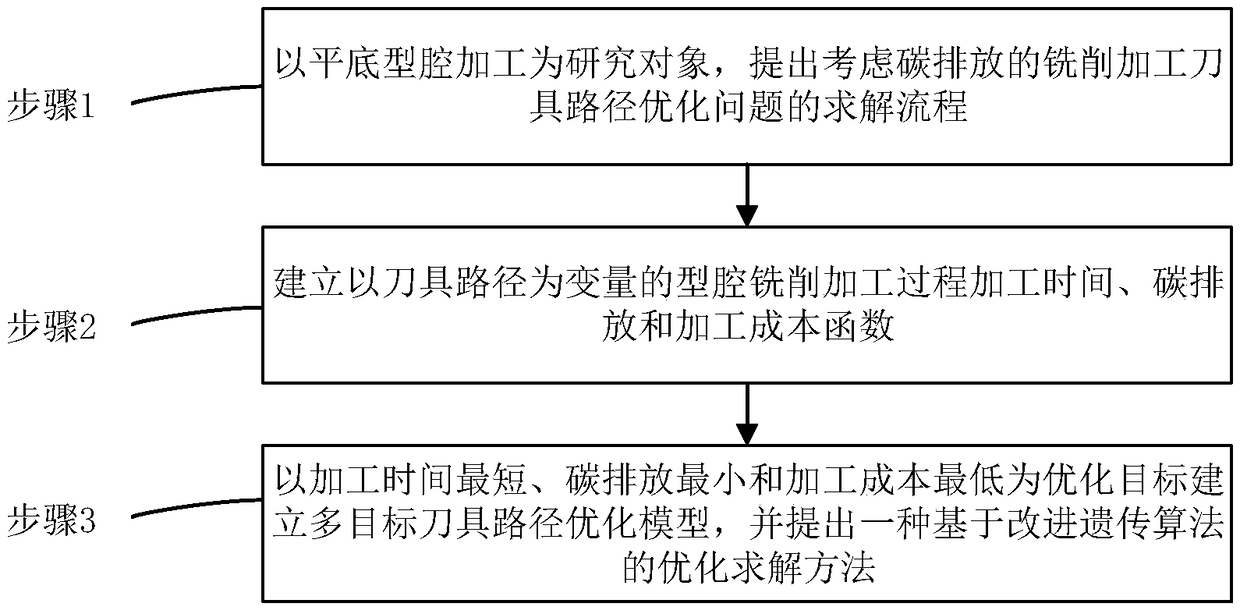
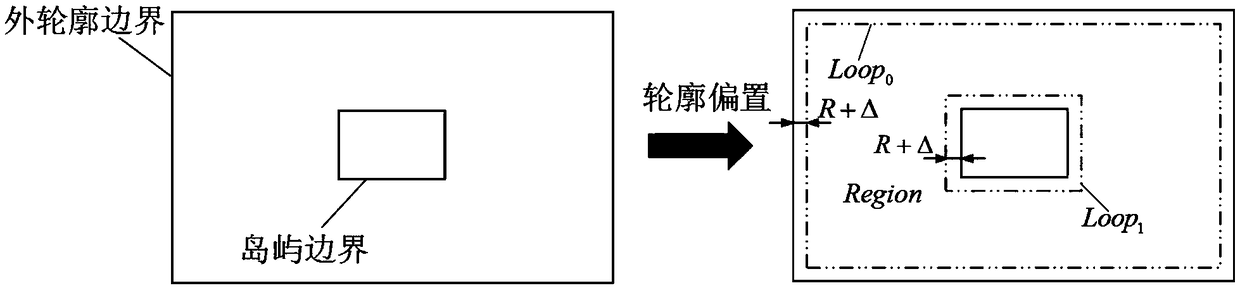
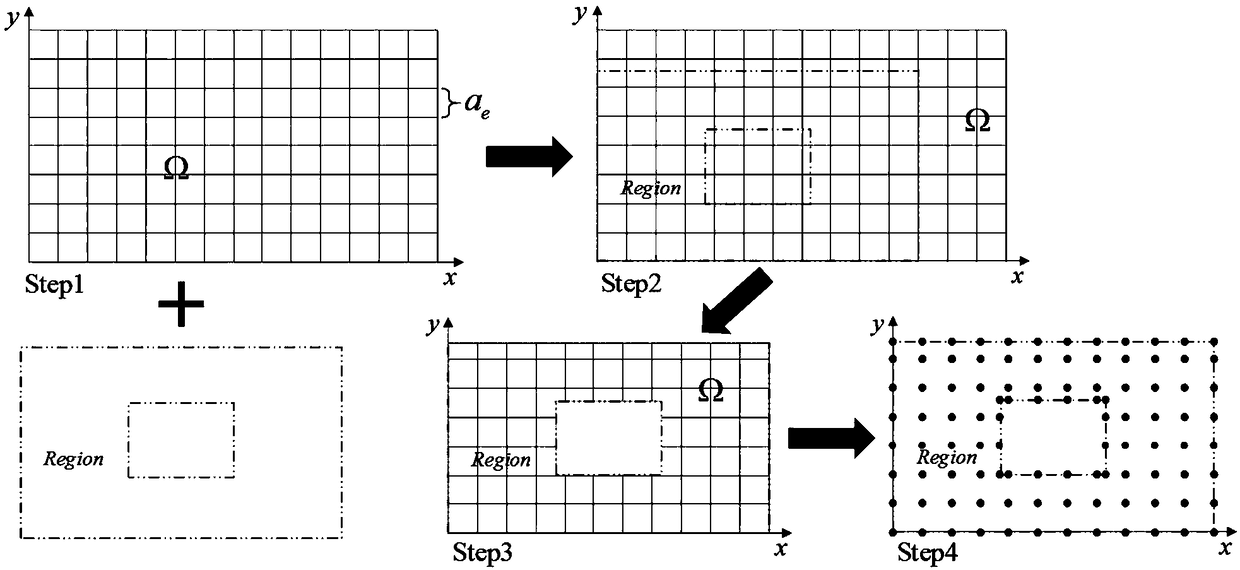
Milling tool path optimization method for low carbon
ActiveCN109240202AGuaranteed surface qualityEmission reductionNumerical controlLocal optimumResearch Object
The invention discloses a milling tool path optimization method for low carbon. The milling tool path optimization method comprises the steps of firstly, building solving process of milling tool pathoptimization problem considering carbon emission by taking flat cavity processing as a research object; secondly, building processing time, carbon emission and a processing cost function of cavity milling process taking a tool path as a variable; and finally, building a multi-target tool path optimization model taking shortest processing time, minimum carbon emission and lowest processing as optimization targets, and optimizing the multi-target tool path optimization model by an improved genetic algorithm-based optimization solution method. The method comprehensively considers the targets of the processing time, the carbon emission and the processing cost, the actual application demand of an enterprise is satisfied, the tool path optimization solving process is simple and effective and iseasy to implement, the population convergence speed is rapid during path optimization solving by the proposed improved genetic algorithm, and the algorithm can be effectively prevented from being sunken to local optimal solution.
Owner:XI AN JIAOTONG UNIV
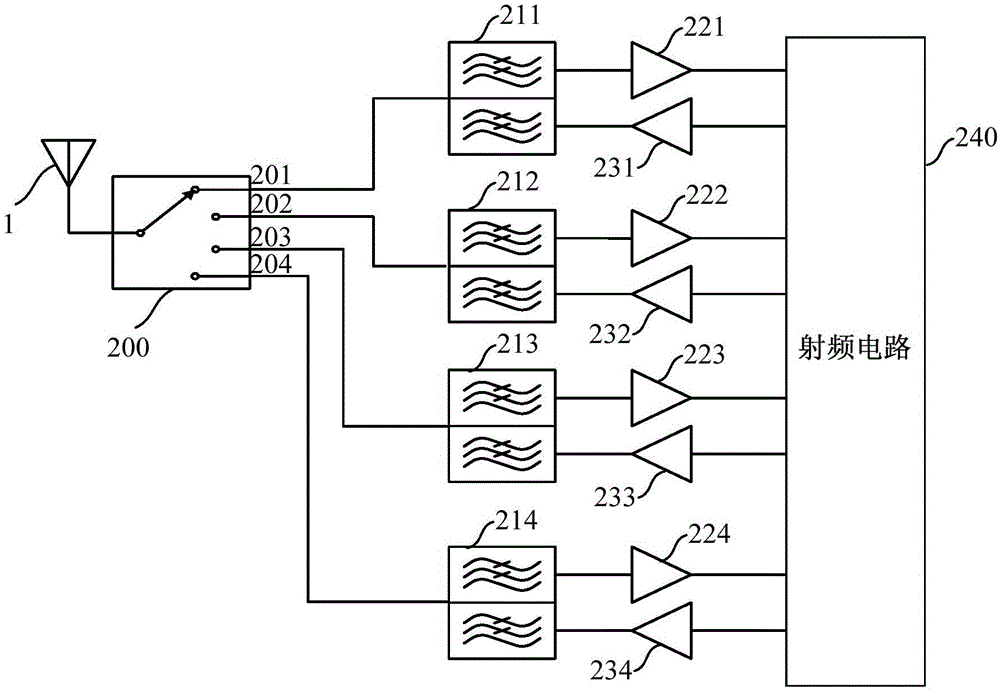
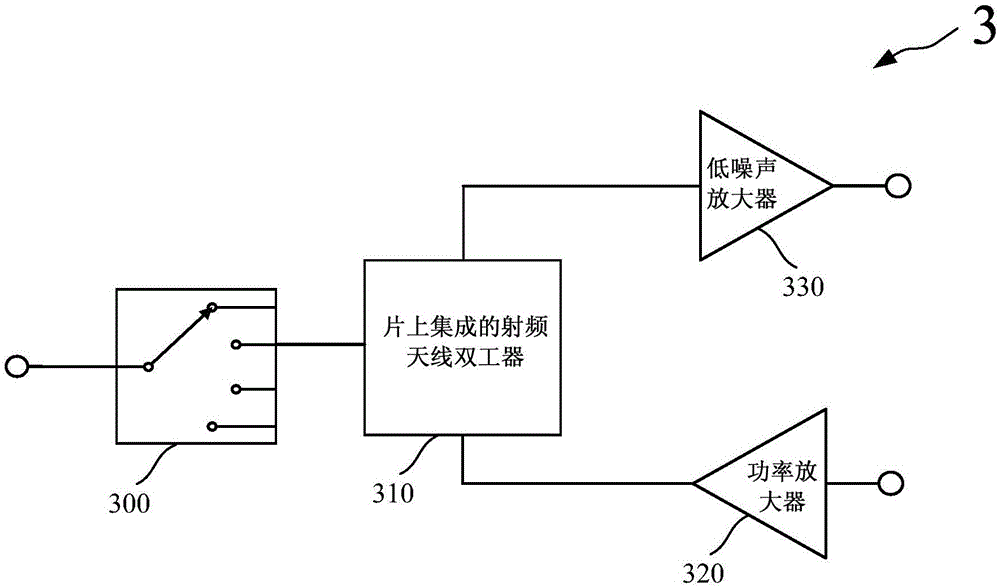
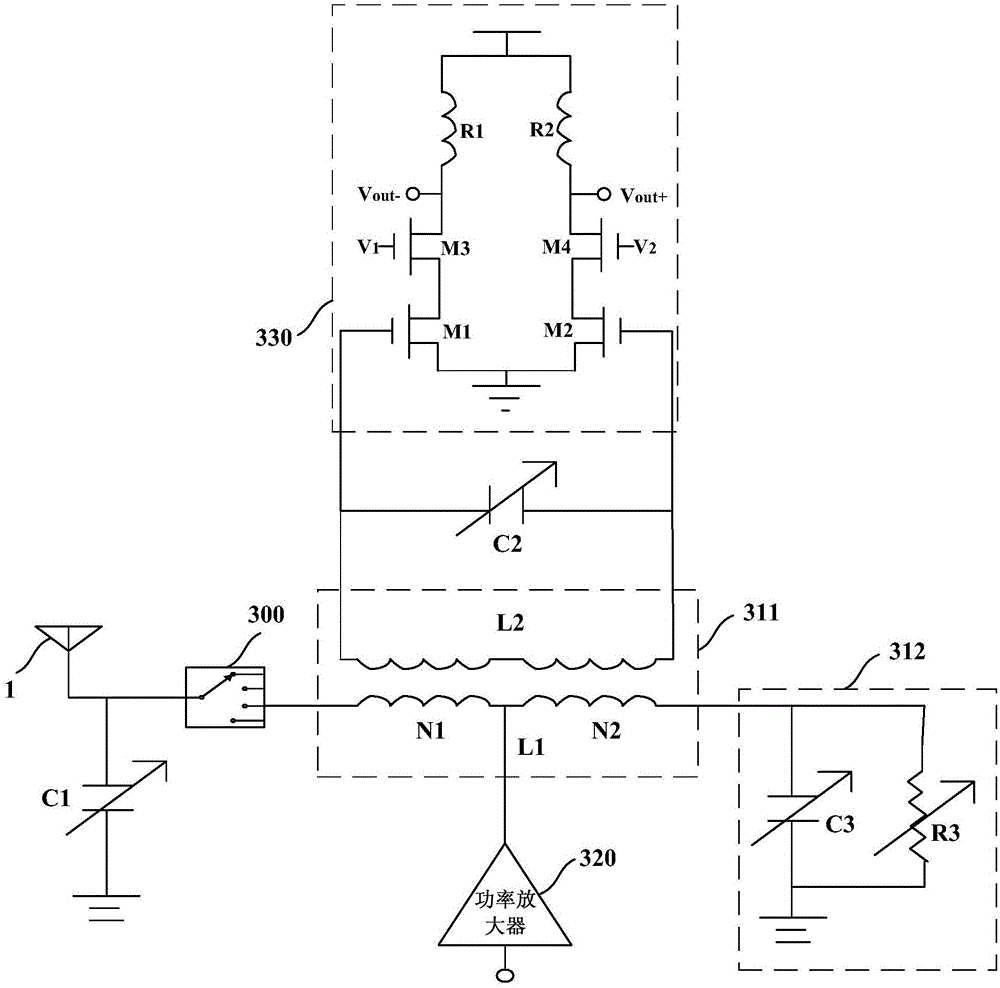
Communication radio frequency front-end module and communication radio frequency front-end communication method
The invention provides a communication radio frequency front-end module and a communication radio frequency front-end communication method. The communication radio frequency front-end module comprises an antenna switch for switching transmission links, a diplexer for supporting multi-band frequency signal transmission, a power amplifier for transmitting output signals of a transmitter to the diplexer, and a low-noise amplifier for transmitting input signals to receiver. By regulating an impedance balance network, the communication radio frequency front-end module is arranged to a corresponding frequency range; the antenna receives signals of the corresponding frequency range, and the signals are transmitted to the low-noise amplifier by the diplexer in a differential mode signal form; the transmitter sends signals which are amplified by the power amplifier and then transmitted to the diplexer and then the antenna, at the same time, the diplexer transmits output signals to the low-noise amplifier in a common mode signal form, and the low-noise amplifier eliminates the common mode signals to achieve the isolation effect. The number of devices required by the radio frequency front end is effectively reduced, and requirements for supporting multiple communication radio frequency ranges, achieving small noise coefficients and according with practical application are met.
Owner:宁波隔空智能科技有限公司
Revocable data sharing method based on fog calculation
ActiveCN108833393ARich domainSatisfy Computational OverheadKey distribution for secure communicationPublic key for secure communicationRevocationRights management
The invention belongs to the field of information retrieval and the technical field of its database structure, and discloses a revocable data sharing method based on fog calculation. When a user revocation occurs, it is not necessary to update the keys of other unrevoked users and re-encrypt the ciphertext, only the conversion key of the revoked user needs to be deleted; after the conversion key is deleted, the cloud server cannot perform partial decryption operations for the revoked user, thereby realizing the user's revocation. When an attribute revocation occurs, the keys of all affected users in the system needs to be updated and the ciphertext is re-encrypted to ensure that other users may still decrypt the ciphertext as usual. The invention realizes the data access control in the data network system, has the advantages such as high system access efficiency, low computational cost, and support for dynamic user rights management, and may be used for protecting the privacy data of the user in the data network, reducing the calculation cost of the user, and dynamically managing the authority of the user in the system.
Owner:XIDIAN UNIV
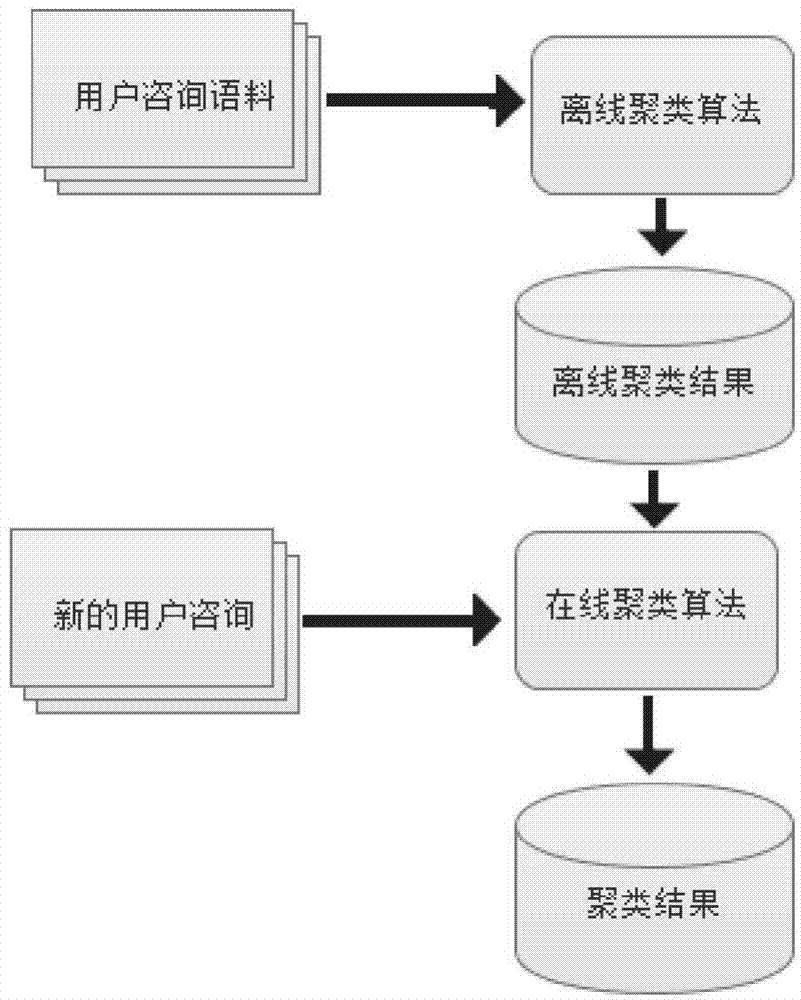
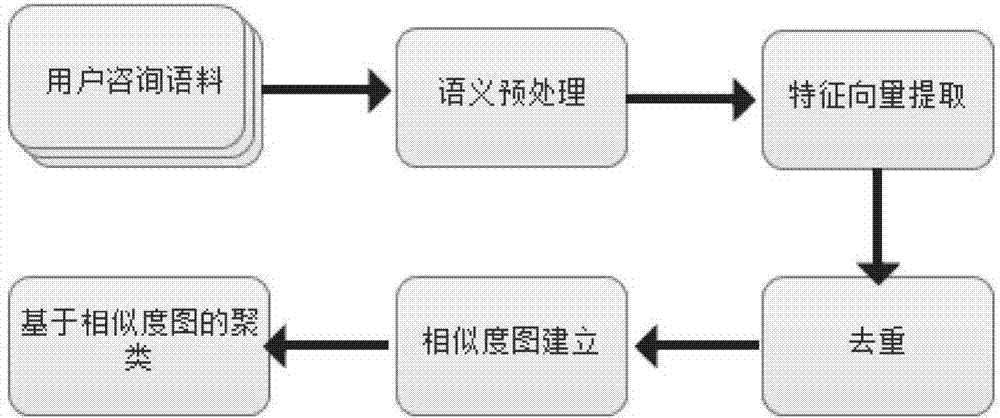
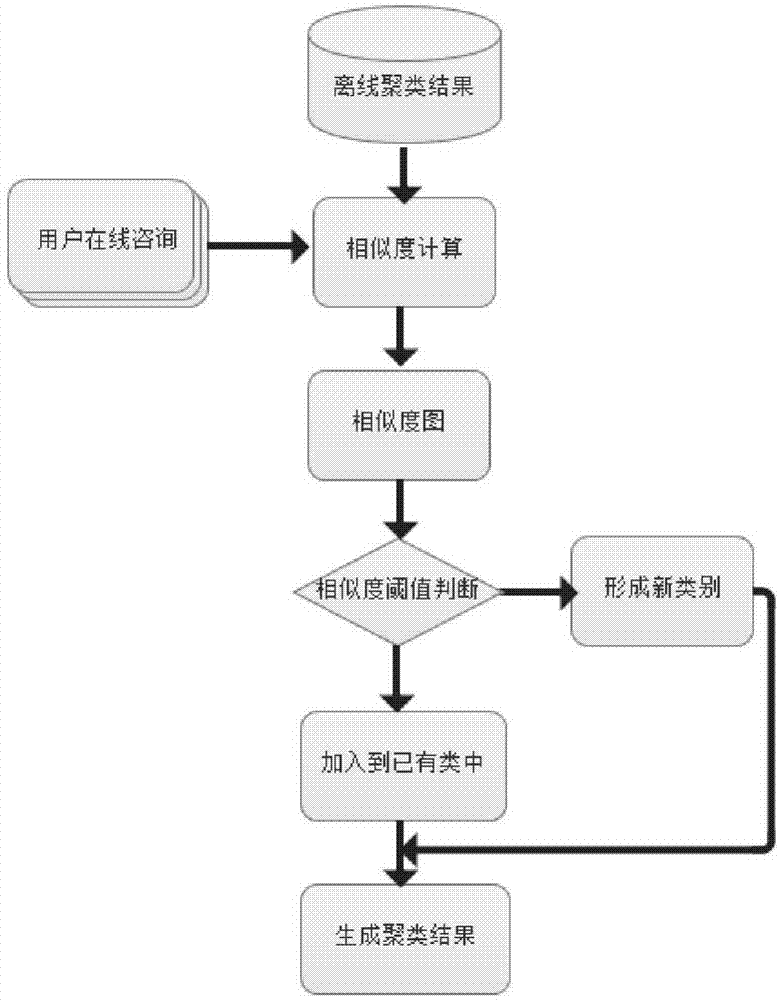
Rapid incremental clustering method for domain question-answering system consultations
ActiveCN104778256AReduce complexityQuick responseSpecial data processing applicationsCluster algorithmPart of speech
The invention discloses a rapid incremental clustering method for domain question-answering system consultations. The method comprises the following steps of performing semantic pretreatment on user consultations by utilizing a semantic irrelevancy dictionary and a word class dictionary through combination of consultation history offline clustering algorithm and consultation repeat removal on the basis of a clustering frame combined with offline clustering and online clustering, so that semantic normalization is realized; furthermore, calculating and constructing a similarity degree pattern on the basis of the similarity degree of multiple characteristics; performing offline clustering on consultation history of a user on the basis of the similarity degree pattern; and furthermore, performing online clustering on the consultations of the user by utilizing the offline clustering result as a clustering characteristic, and combining the offline clustering result with the online clustering result, so as to generate a clustering result. The clustering method provided by the invention is rapid in system response, is capable of achieving the accuracy conforming to the practical application demand, and is high in effectiveness and accuracy.
Owner:南方电网互联网服务有限公司
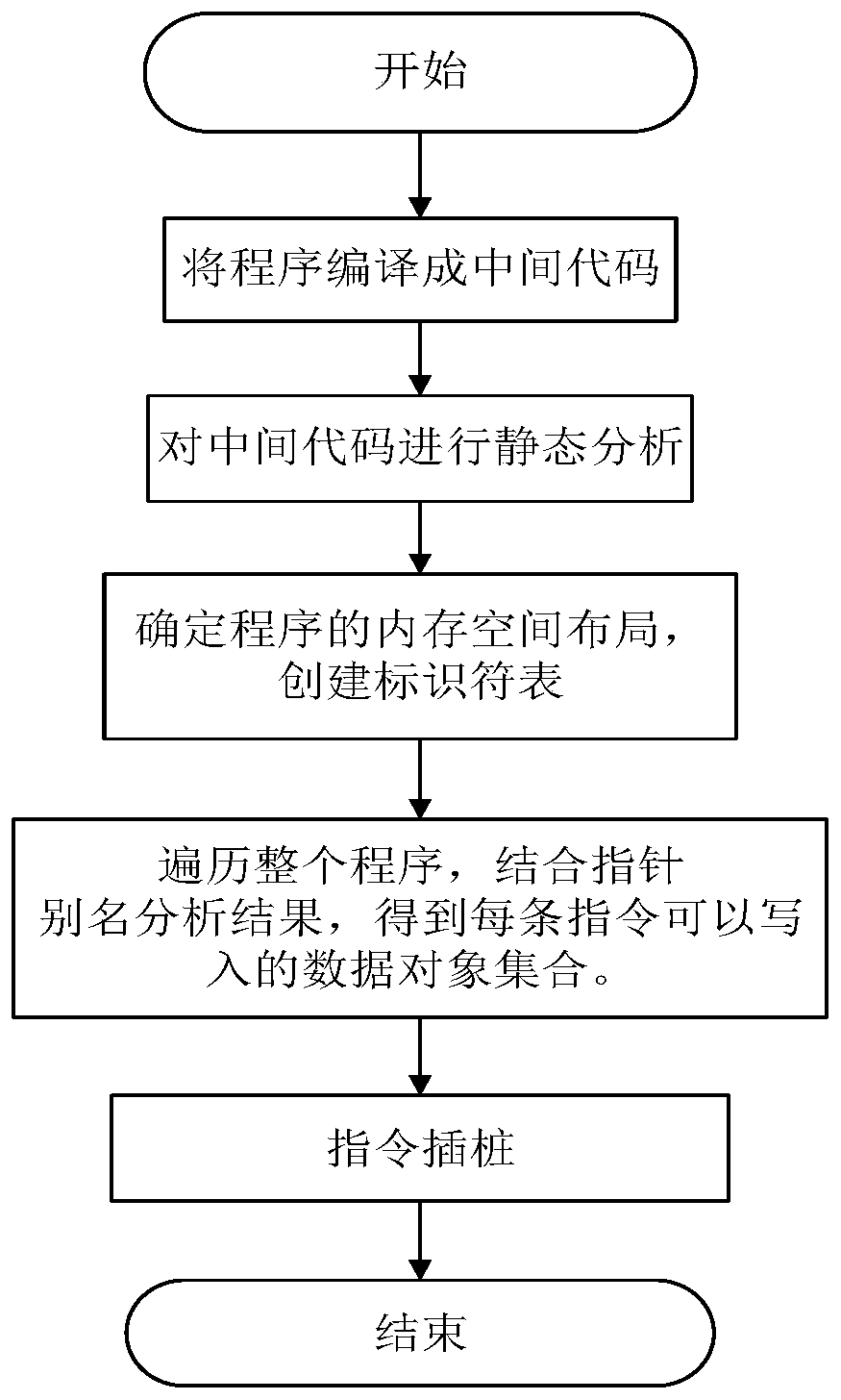
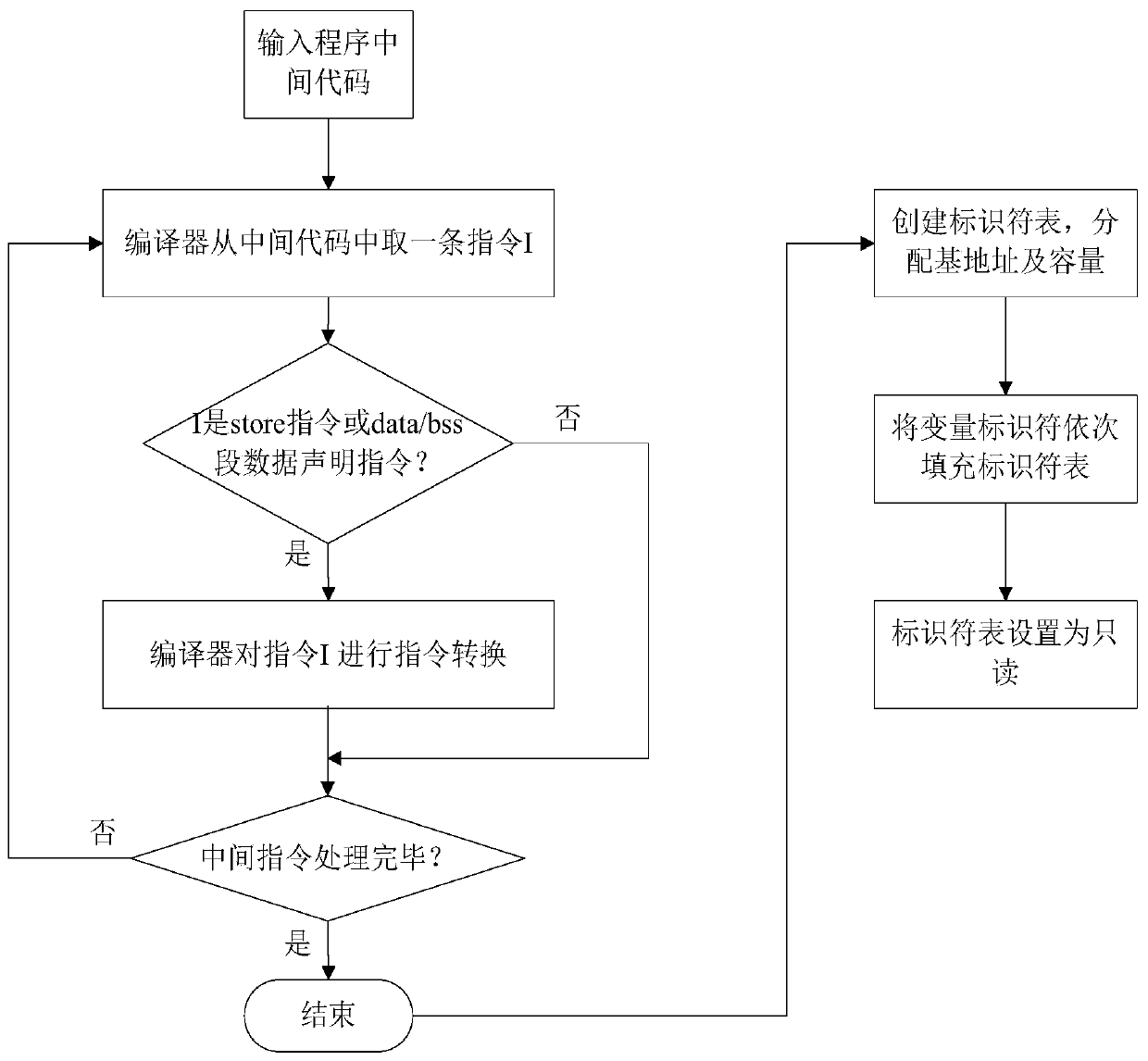
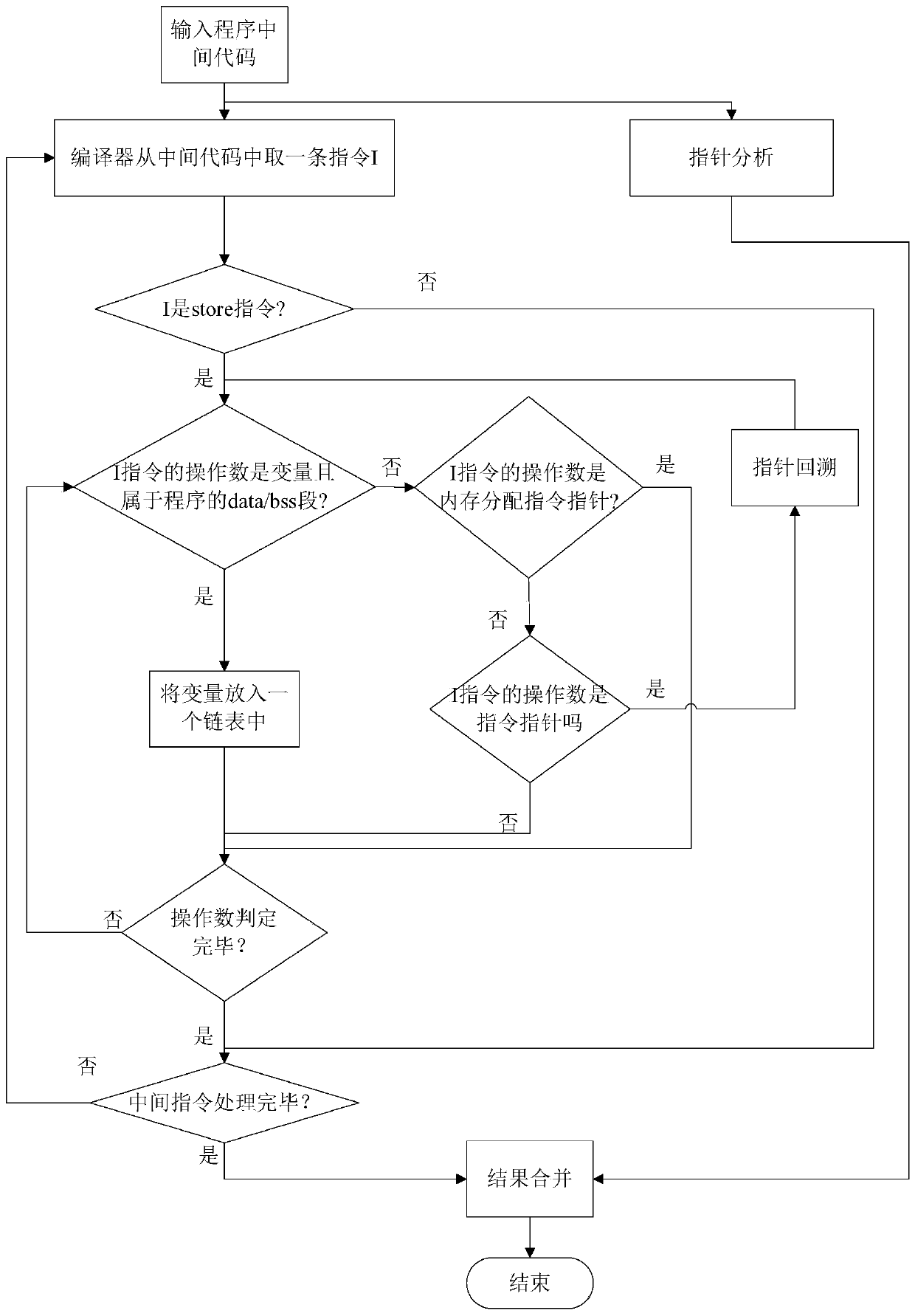
program non-control data attack protection method based on an LLVM compiler
ActiveCN109918903AWill not affect the running processImprove accuracyPlatform integrity maintainanceCode compilationAttackSoftware engineering
The invention provides a program non-control data attack protection method based on an LLVM compiler, and the method comprises the steps: compiling a program source code into an intermediate code fora 64-bit application program which is widely applied at present, carrying out the static analysis of the intermediate code, obtaining a directivity analysis result, and obtaining non-control data which needs to be protected; meanwhile, carrying out instruction instrumentation on the basis of the intermediate code, so that non-control data of the program are prevented from being maliciously tampered. According to the method, the defects of an original static analysis method are overcome, the analysis accuracy is improved, and the security threat caused by malicious tampering of program non-control data by an attacker is solved by utilizing relatively low space and time complexity.
Owner:陕西数图行信息科技有限公司
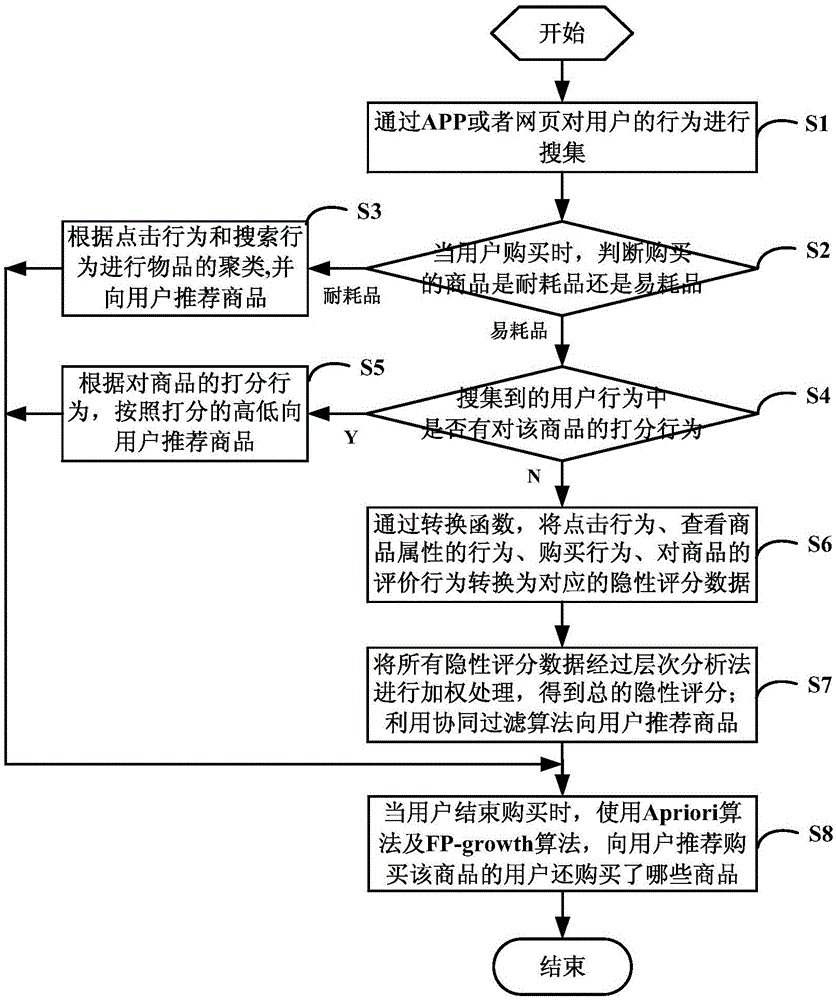
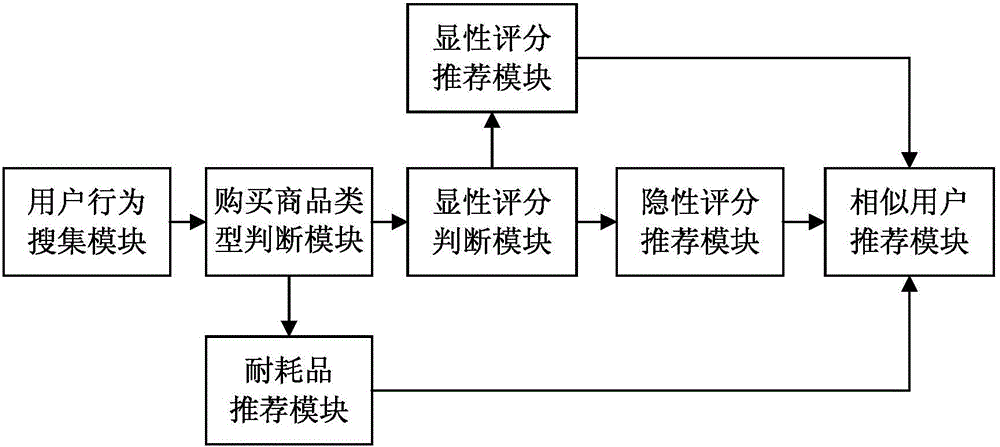
Commodity recommending method and system based on user behaviors
InactiveCN106600372AImprove experienceImprove accuracyBuying/selling/leasing transactionsSpecial data processing applicationsWeb pageEvaluation data
The invention discloses a commodity recommending method and system based on user behaviors, which relate to commodity recommending technology field. The method comprises the following steps: searching and collecting the user behaviors through an APP or a page; when the user purchases a commodity, determining whether the commodity is an endurable commodity or a consumable commodity; if the commodity is an endurable one, then clustering the items according to the clicking behaviors and the searching behaviors and recommending to the user the commodity; if the commodity is a consumable commodity, determining whether there is any scoring behavior for the commodity; if there is any, according to the scoring behavior, recommending to the user the commodity; if there is no such scoring behavior, transmitting the clicking behavior, the commodity attribute inquiring behavior, the purchase behavior and the commodity evaluating behavior into corresponding hidden score evaluation data; subjecting all the hidden score evaluation data to a layer analyzing method for weighted process so as to obtain a total hidden score; and based on the total hidden score, using a collaborative filtering algorithm to recommend the commodity to the user. According to the invention, not only high recommending efficiency can be achieved; but also the actual application requirement can be met, therefore, bringing excellent user experience to the user.
Owner:WUHAN FIBERHOME INFORMATION INTEGRATION TECH CO LTD
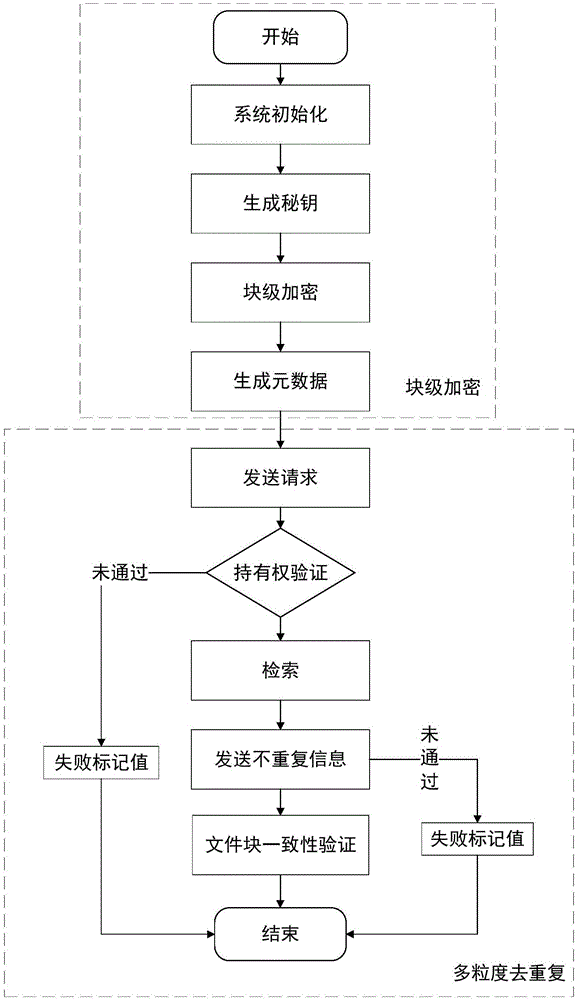
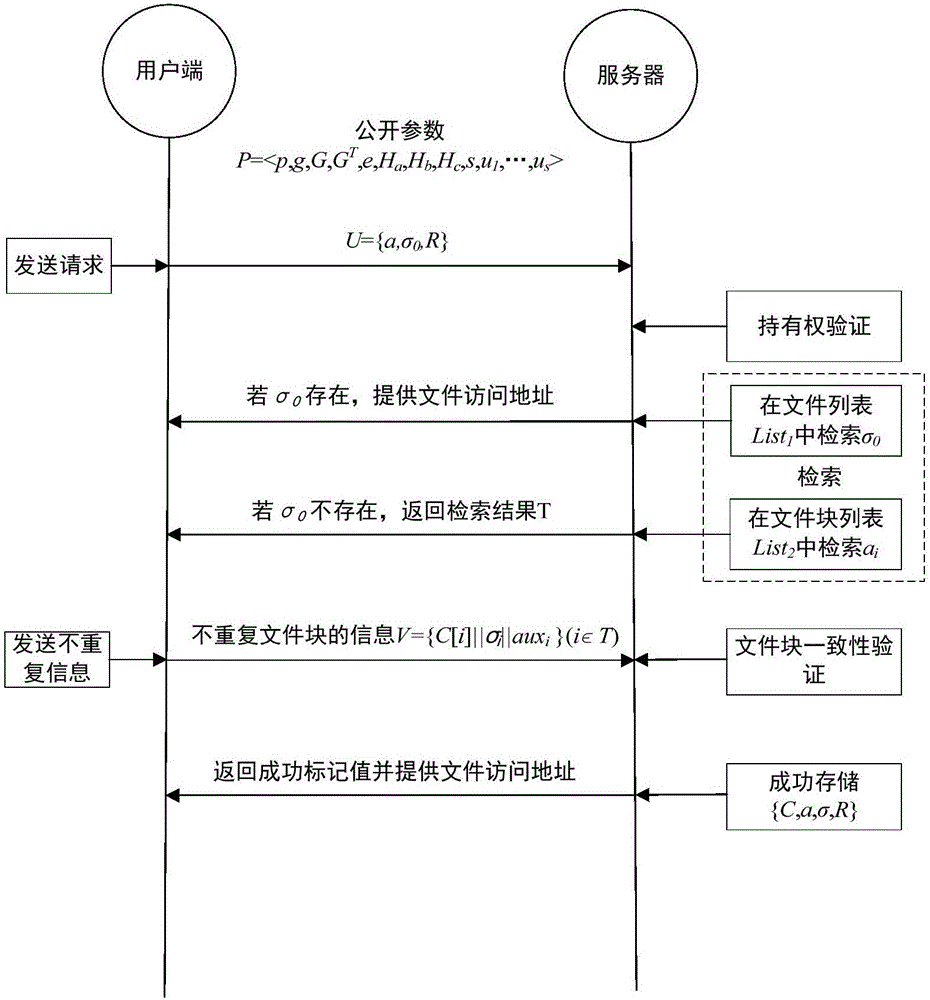
Block level encryption method in cloud storage and multi-granularity deduplication method
ActiveCN106603561ADe-duplicationReduce overheadDigital data protectionTransmissionGranularityCloud storage
The invention discloses a block level encryption method in cloud storage and a multi-granularity deduplication method, belonging to the technical field of network security. The block level encryption method comprises the steps that a system public parameter is set, a user end calculates a key and encryptes a file, and metadata is calculated; and the user end selects a part of metadata as a deduplication request and sends the request to a server, the server verifies the file ownership of a user according to the request and retrieves a file in a storage list, if the file exists, access is provided directly, otherwise the server asks the user end to upload non-repeat information, the server carries out consistency verification on received data, and the server allows the user end to access the file if the verification is passed. The method is suitable for the cloud storage with security and efficiency of data and aims to safely and reliably carry out deduplication on the user data, and the data storage efficiency is high.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
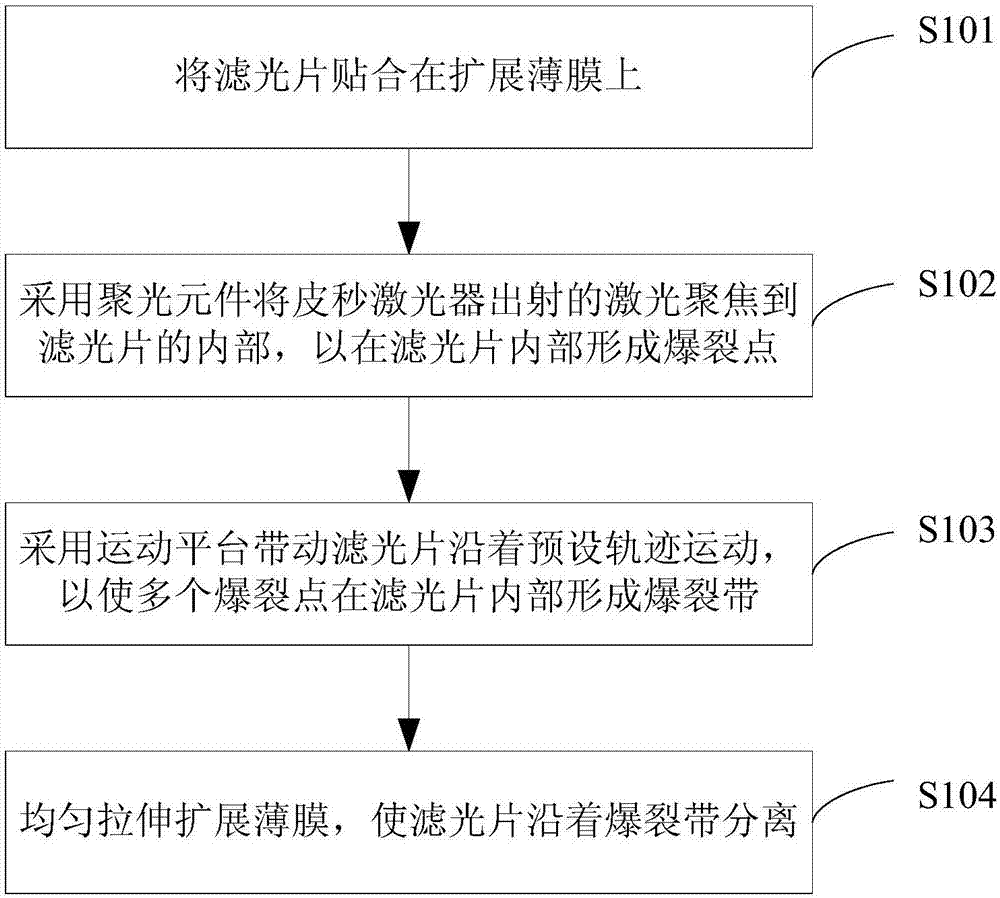
Method and system for performing laser cutting on light filter plate
ActiveCN107030400AUniform fracture surfaceReduce lossWelding/soldering/cutting articlesLaser beam welding apparatusOptoelectronicsLaser cutting
The invention provides a method and a system for performing laser cutting on a light filter plate. The method comprises the following steps of: adhering the light filter plate on a spreading film; focusing laser emitted by a picoseconds laser unit inside the light filter plate by a light focusing element to form bursting points inside the light filter plate; and driving the light filter plate to move along a preset path through a motion platform, and forming a bursting zone inside the light filter plate by the bursting points; uniformly stretching and spreading the film, and separating the light filter plate along the bursting zone. According to the method provided by the invention, focused laser spots are relatively small, and therefore, the width of the formed bursting zone, namely a cutting channel is relatively small, loss of materials can be reduced, and the strip yield is increased; and moreover, the distance from the bursting zone to the first surface and the distance from the bursting zone to the second surface are greater than or equal to a first preset value, and therefore, an antireflection film on the surface is not damaged; besides, the film uniformly stretches and spreads, so that the bursting zone inside the light filter plate spreads towards upper and lower surfaces to realize plate splitting and separating, and therefore, the fracture surface of the light filter plate is uniform without taper.
Owner:东莞市盛雄激光先进装备股份有限公司
A management method and system of a portrait label
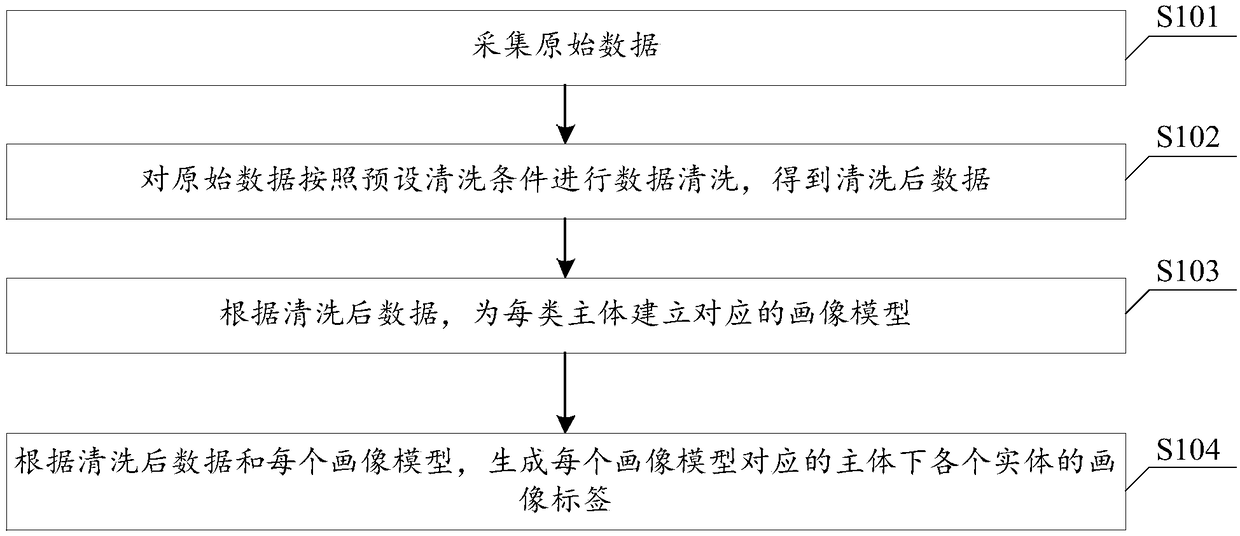
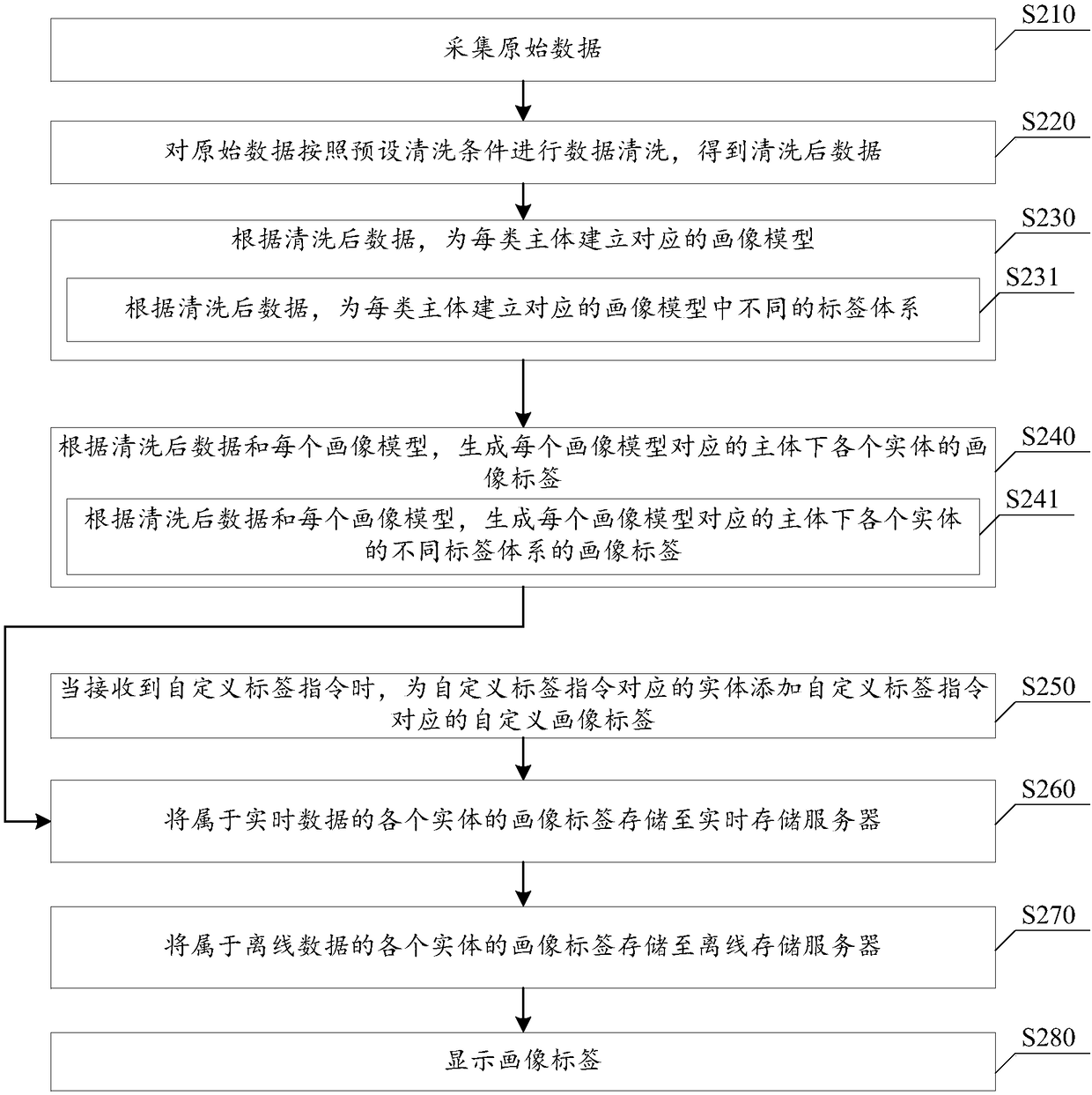
InactiveCN109003027AUpdate reasonableIncrease update frequencyLogisticsSpecial data processing applicationsOriginal dataData mining
The invention discloses a management method and system of a portrait label. The method comprises the steps of: collecting original data which include service data, behavior data and backflow data; carrying out data cleaning on the original data according to a preset cleaning condition to obtain the cleaned data; according to the cleaned data, establishing the corresponding portrait model for eachtype of subject; according to the cleaned data and the portrait model, generating a portrait tag of each entity corresponding to each portrait model is generated. The invention provides the functionsof screening and visual analysis of the portrait label, and the use effect data of the label can be returned to the system, so as to help the operation and maintenance personnel of the system to reasonably update, add and delete the label, and improve the accuracy of the label and the use efficiency of the label.
Owner:JIANGSU MANYUN SOFTWARE TECH CO LTD
Autonomous underwater vehicle field source searching method and system based on gradient estimation
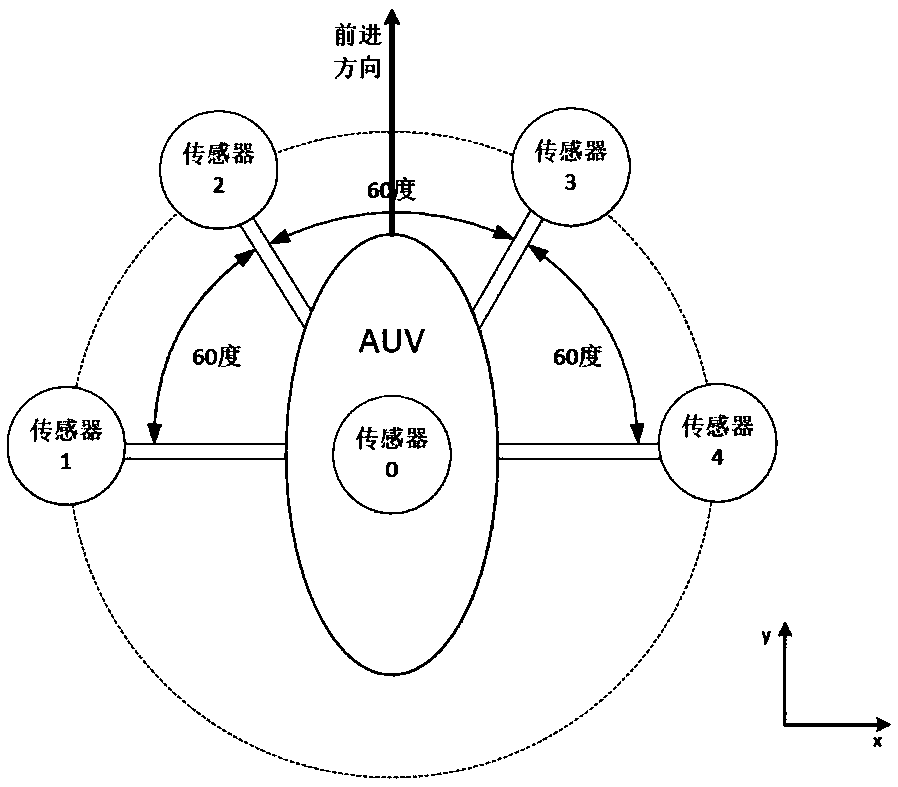
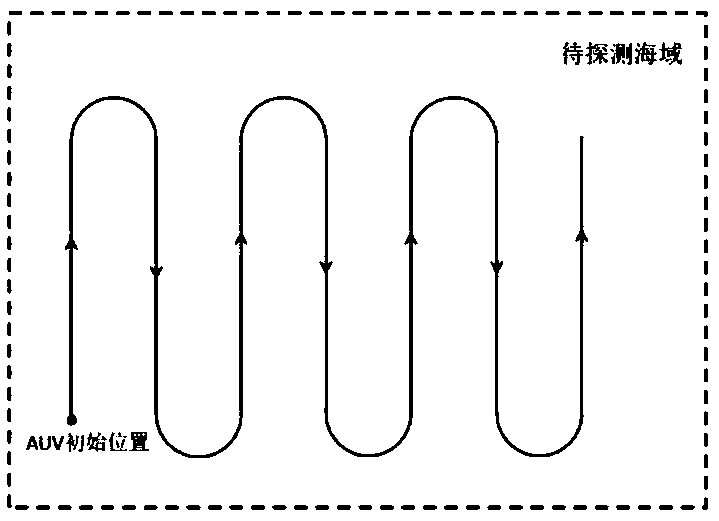
InactiveCN108664039AFormation controlLow costInternal combustion piston enginesTarget-seeking controlSimulationGradient estimation
The invention provides an autonomous underwater vehicle (AUV) field source searching method and system based on gradient estimation, and belongs to the field of control engineering and optimization. The method comprises the steps of constructing an AUV field source searching optimization model, determining the model of the AUV according to the searching task of the field source, installing a plurality of identical sensors; the AUV starting the field source searching from an initial position, and if the current position signal field intensity is larger than a preset field intensity threshold value, performing field source gradient estimation at the current moment, and determining whether the AUV reaches a field source position or not according to the gradient estimation result; and if the AUV does not reach the position of the field source, carrying out motion control on the AUV by utilizing the gradient estimation, the AUV moving to a new current position according to the control inputat the current moment, and repeating the process until the position of the field source is reached. According to the method and system, field source searching is carried out through gradient estimation for the first time, and an AUV still approaches the position of the field source at a preset posture and a height under the condition that the gradient is not accurate in the optimization problem.
Owner:TSINGHUA UNIV
Corner self-servo passive and supple hydraulic robot joint
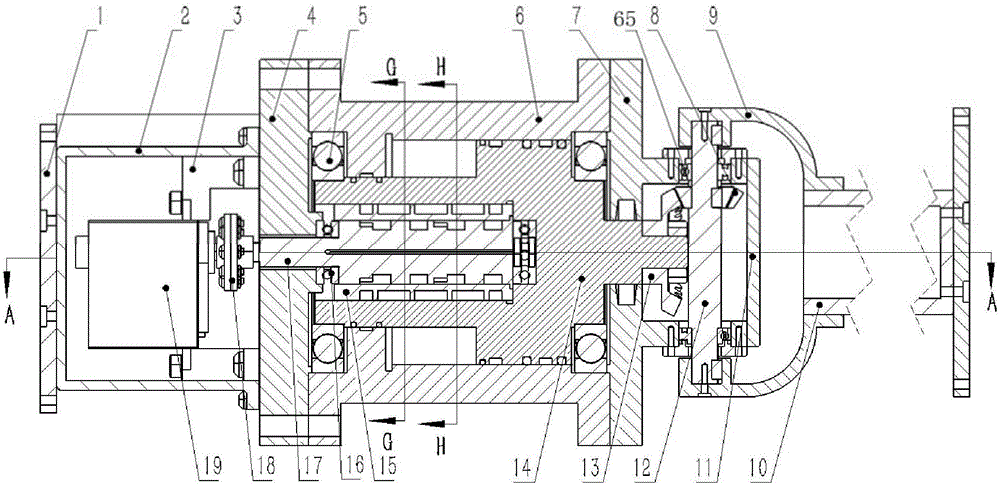
ActiveCN106737827AEasy to fixEasy to assembleProgramme-controlled manipulatorJointsBall bearingDrive shaft
The invention provides a corner self-servo passive and supple hydraulic robot joint. According to the technical scheme of the corner self-servo passive and supple hydraulic robot joint, a valve body (14) is concentrically installed in a cylindrical cavity (32) of a cylinder body; the left end and the right end of the valve body (14) are concentrically provided with two deep groove ball bearings (5); a driving bevel gear (13) is concentrically installed on the shaft shoulder of an output shaft at the right end of the valve body (14); a driven shaft (12) is installed on a right end cover (7); a driven bevel gear (8) is concentrically installed on the driven shaft (12); two connecting rods (9) are fixedly and symmetrically installed at the two ends of the driven shaft (12) through screws; and a driven arm (10) is installed between the other ends of the two connecting rods (9). The corner self-servo passive and supple hydraulic robot joint has the beneficial effects that a fixing stop block can be fixed easily and assembled easily, the output torque of the joint is large, the force borne by the valve body is in balance, displacement is not prone to occurrence, the dynamic characteristic is good, the joint flexibility is good, the response speed is high, and the control precision is high.
Owner:WUHAN UNIV OF SCI & TECH
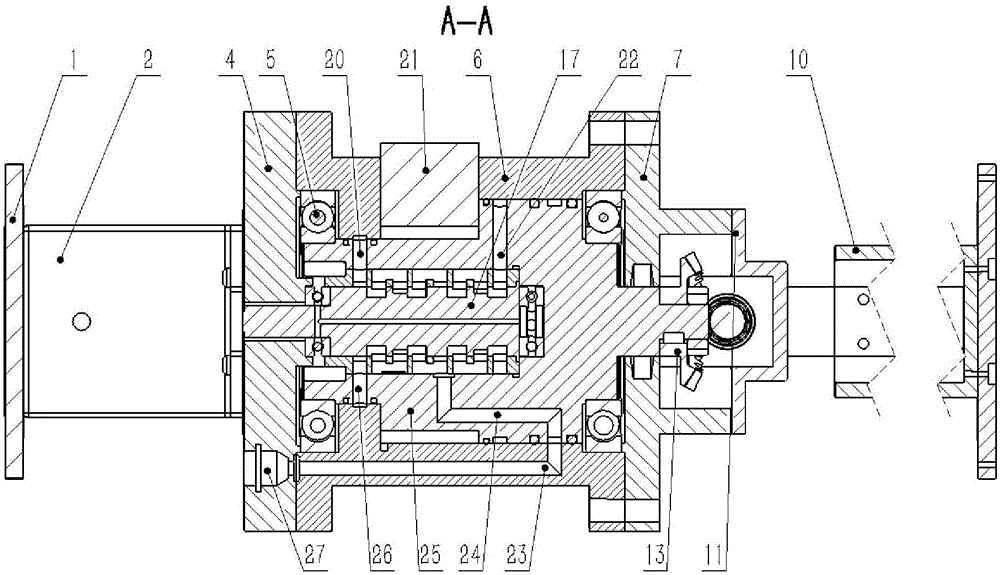
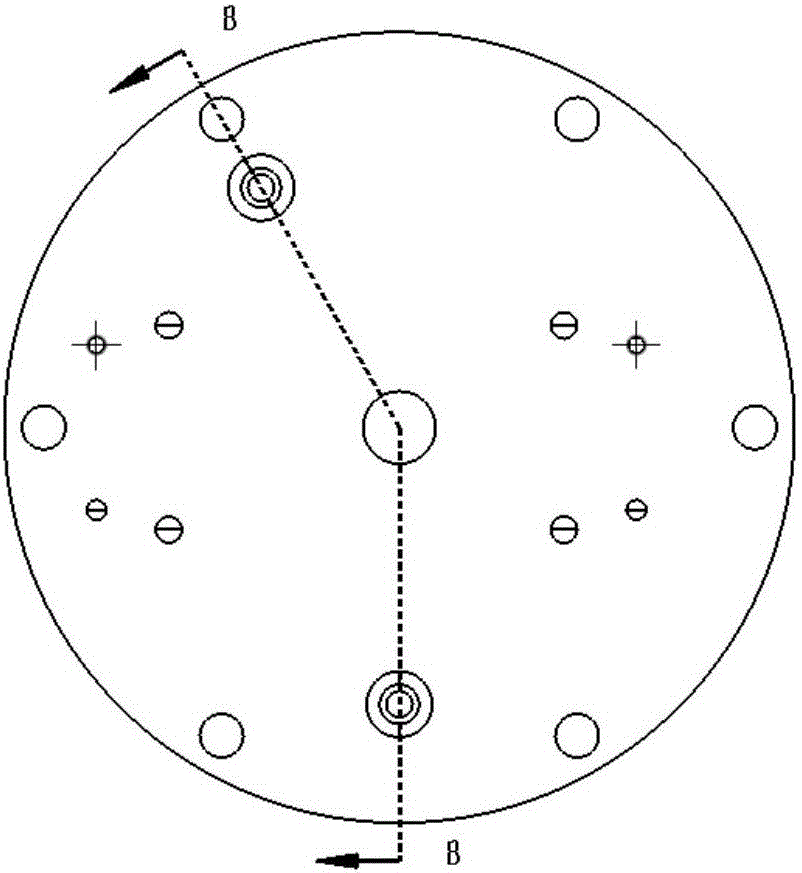
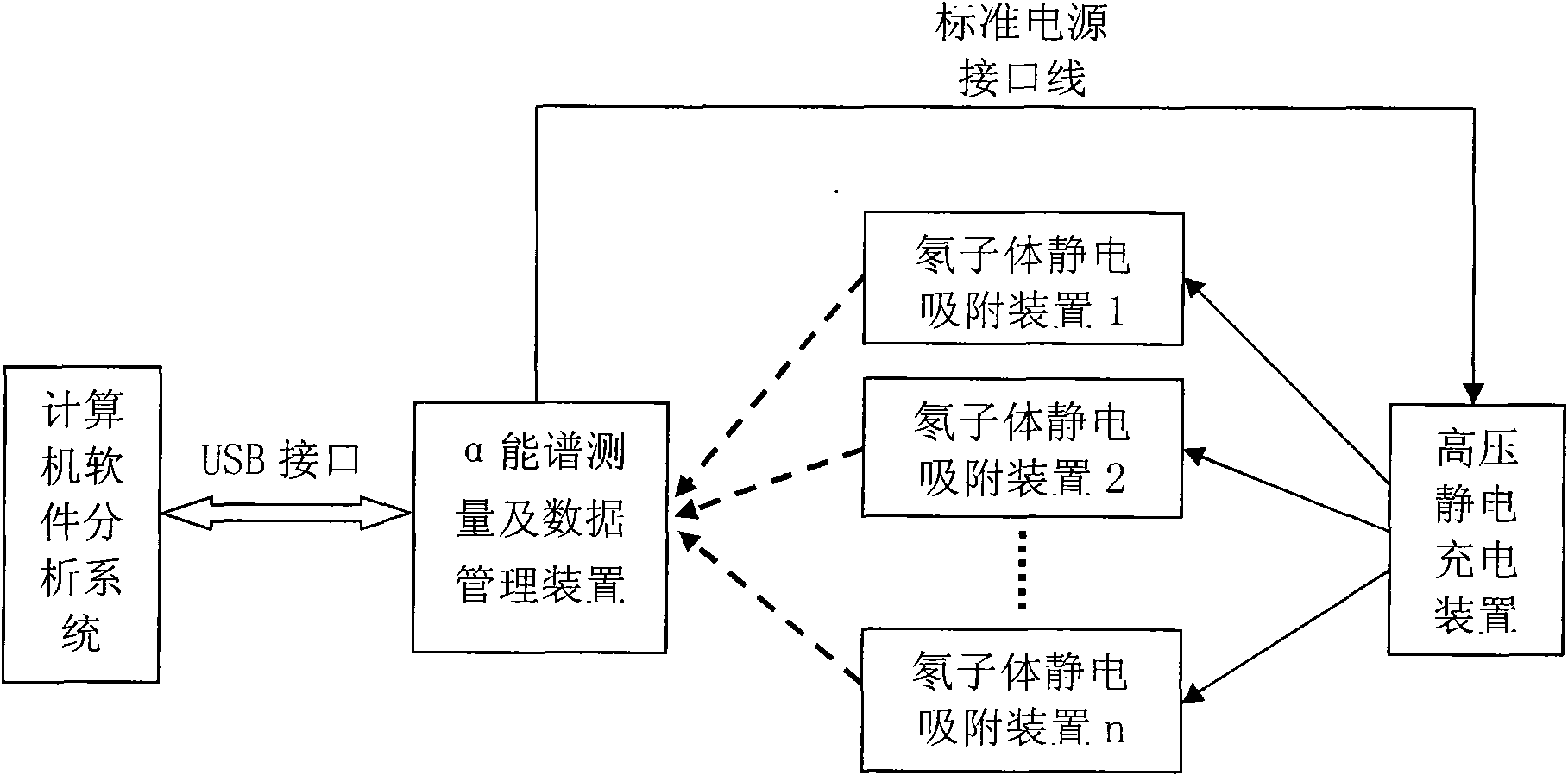
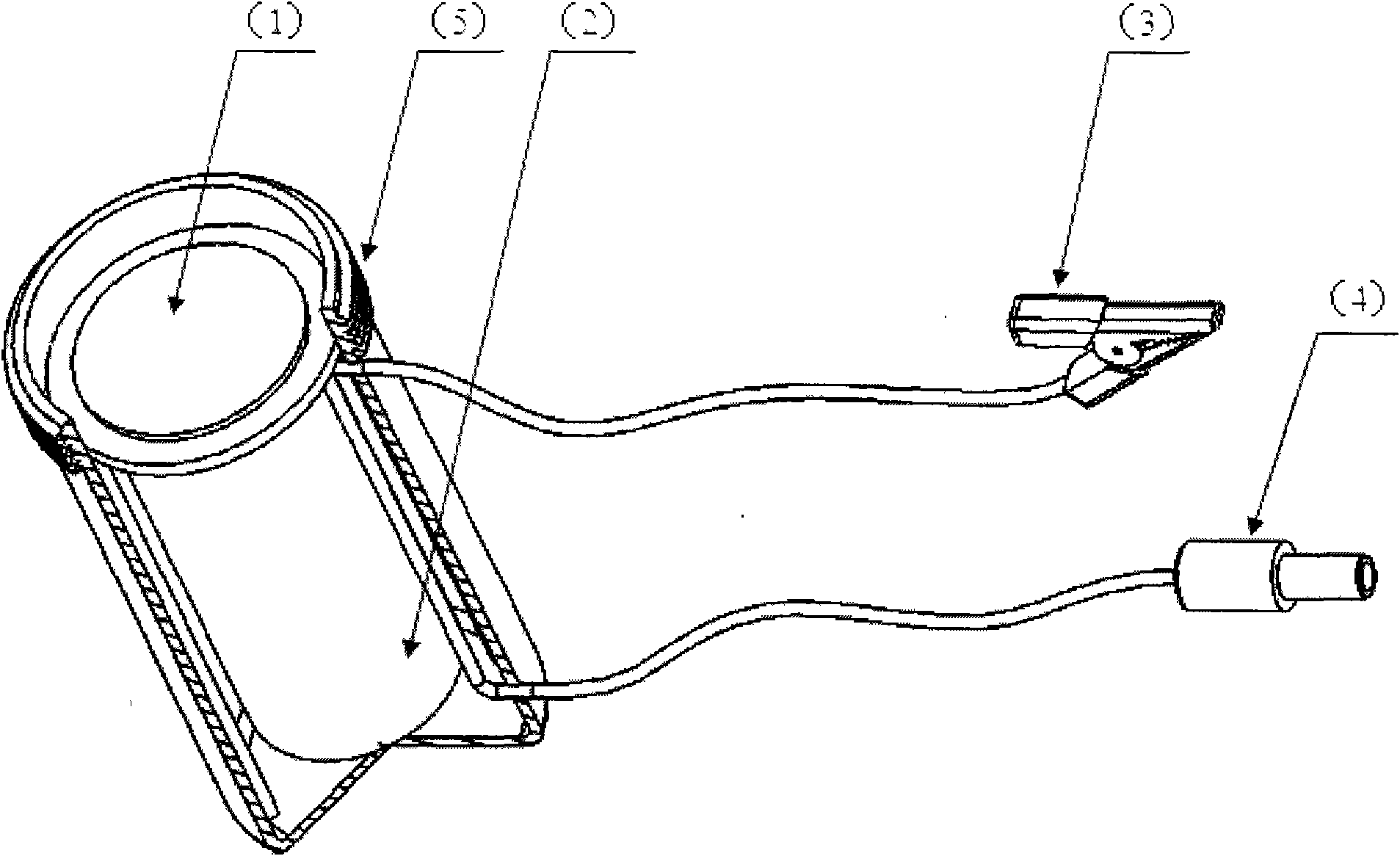
Alpha energy spectrum measuring method of radon in soil based on static diffusion and electrostatic adsorption principle of radon in soil
InactiveCN101620274AEliminate pollutionRealize measurementX-ray spectral distribution measurementNuclear radiation detectionHigh pressureHigh voltage
The invention discloses an alpha energy spectrum measuring method of radon in soil based on a static diffusion and electrostatic adsorption principle of the radon in soil, which comprises the following steps: (A) during measuring, burying a radon daughter electrostatic adsorption device in soil for a period of time, and then taking the radon daughter electrostatic adsorption device out and using an alpha energy spectrum measuring device to measure adsorbed radon daughters; (B) using a high-voltage electrostatic charging device to charge the radon daughter electrostatic adsorption device so as to enable the radon daughter electrostatic adsorption device to have high-voltage static electricity; (C) using an alpha energy spectrum measuring and data managing device to measure the alpha energy spectrum information of the adsorbed radon daughters of the radon daughter electrostatic adsorption device and concentratively managing the data; and (D) using a computer software analysis system to detailedly analyze the measuring data. The method can overcome the defects of the prior measuring method of the radon in soil, solve the problems of low soil radon measurement efficiency, precision, accuracy and reliability, and the like, indirectly measure the radon in soil by measuring nuclides of the radon daughters in soil, overcome the influences of thoron and meet the urgent requirement on the measurement of the radon the soil of the geological survey field and the environmental evaluation field at present.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
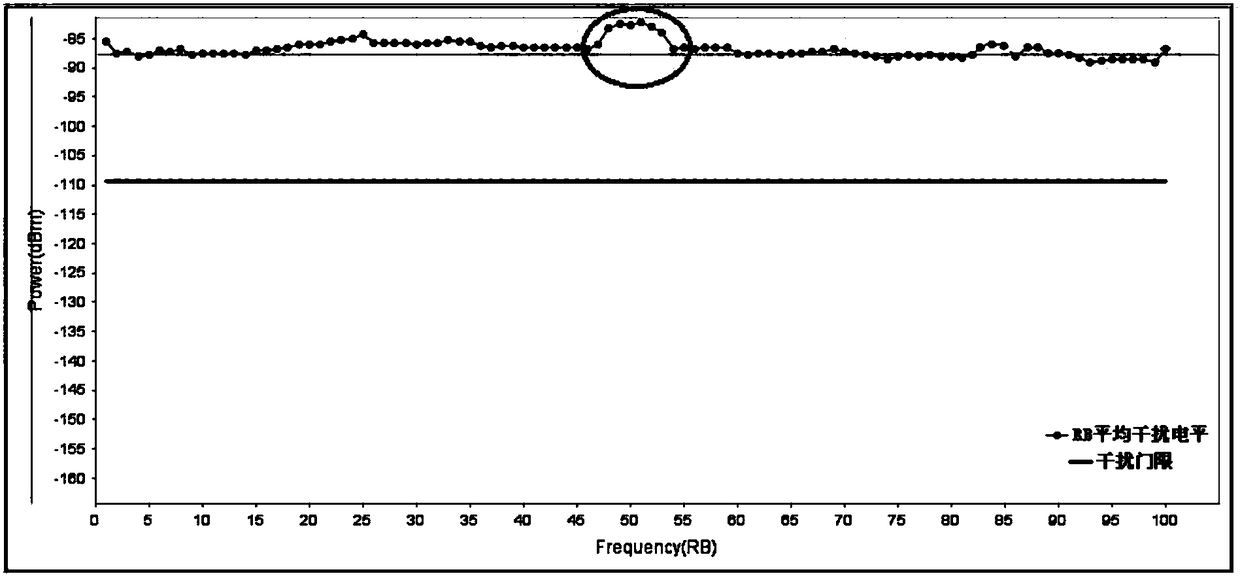
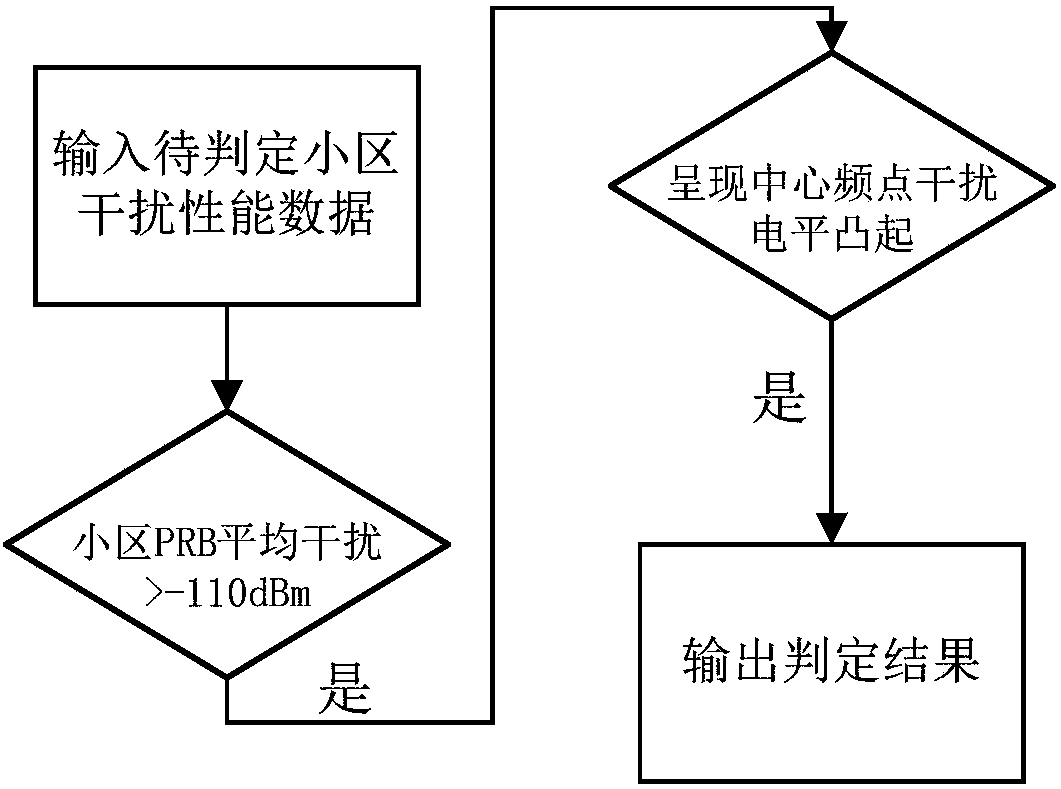
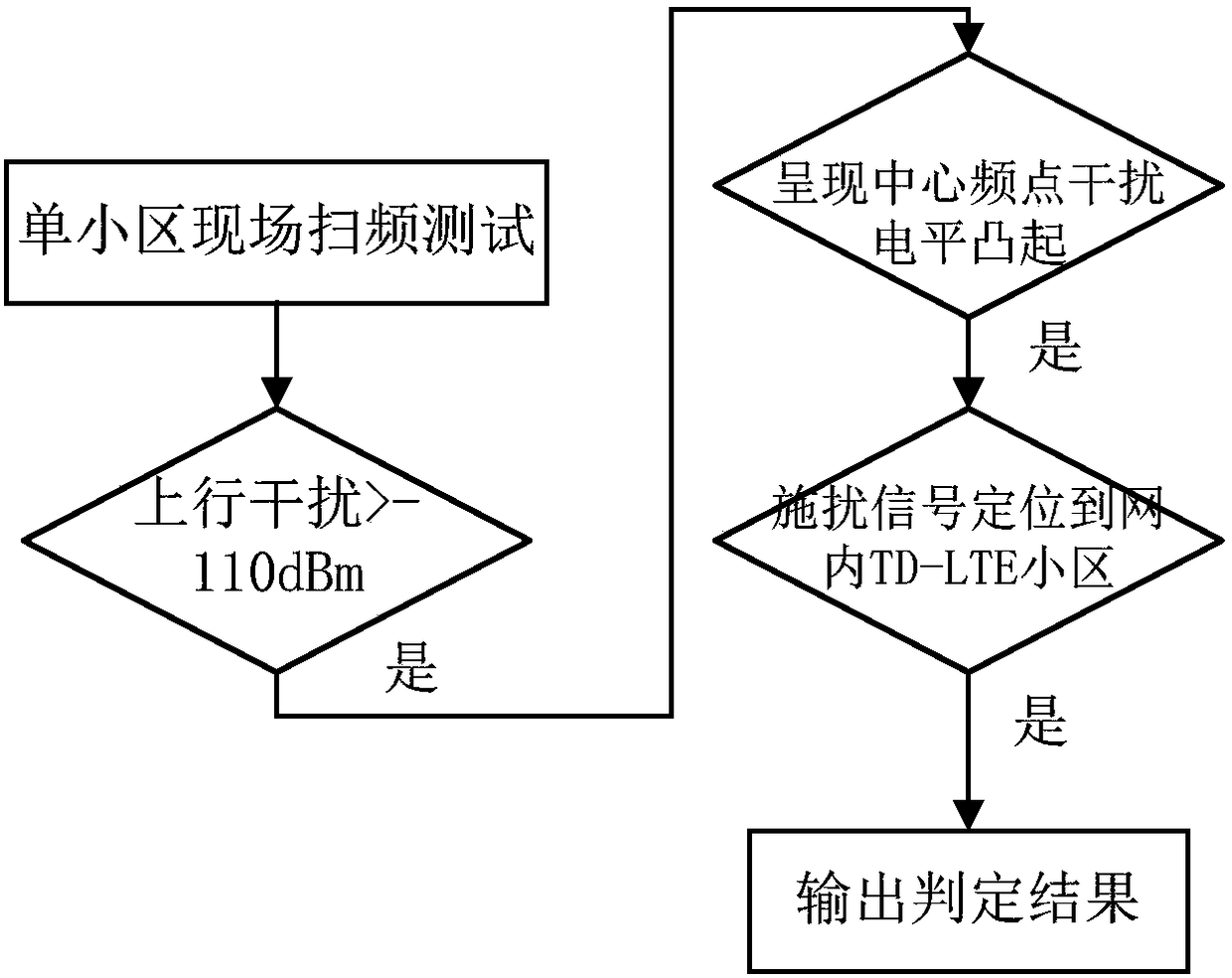
Method and system for positioning TD-LTE network atmospheric waveguide interference
ActiveCN108289302AReduce consumptionAchieve positioningWireless communicationGeolocationNetwork management
The embodiment of the invention discloses a method and system for positioning TD-LTE network atmospheric waveguide interference and belongs to the technical field of wireless network optimization. According to the method, cell performance interference data is taken as basic data, and starting from atmospheric waveguide cell performance, geographic positions and time characteristics, big data mining and analysis are carried out deeply, so LTE cells interfered by the atmospheric waveguide interference are positioned accurately. Compared with the prior art, the method and the system provided by the invention have the advantages that judgment conditions are relatively sufficient, misjudgment of lifting interference such as interference unit interference can be effectively avoided, and the judgment efficiency and accurately are relatively high. According to the method and the system, the atmospheric waveguide interference judgment is carried out based on background network management performance and engineering parameter data, the cost is low, the timeliness is high, the efficiency is high, and the method and the system are very applicable to daily judgment of the atmospheric waveguideinterference.
Owner:HANDAN BRANCH OF CHINA MOBILE GRP HEBEI COMPANYLIMITED +1
Switching method of multipoint-multiuser oriented cooperation transmission
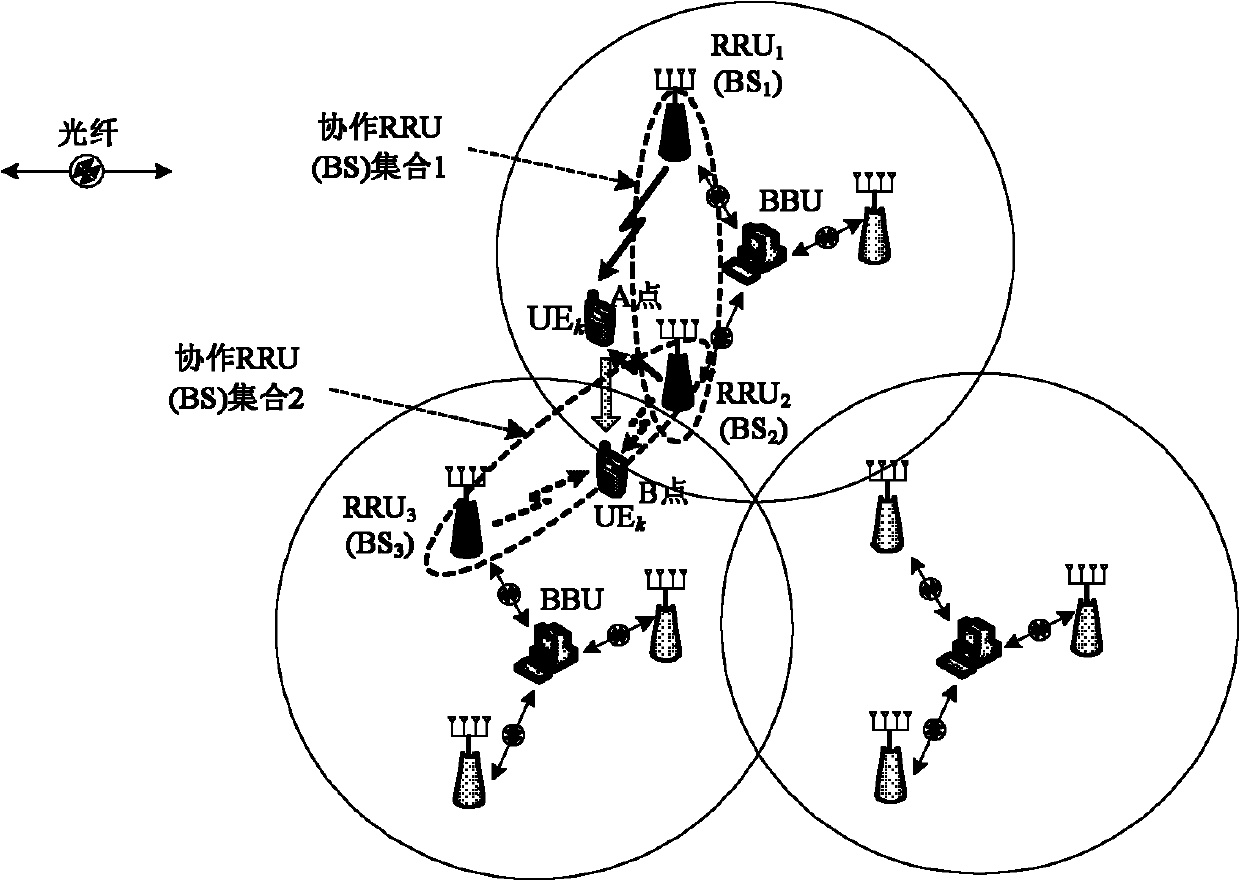
InactiveCN102186215AReduce Feedback OverheadReduce complexityWireless communicationError prevention/detection by diversity receptionUser needsSoft switching
The invention discloses a switching method of multipoint-multiuser oriented cooperation transmission, mainly solving the problem that the existing switching technology does not support multiple cooperation transmission points and multiple cooperation users to participate in switching simultaneously. The switching method comprises the steps of: firstly establishing 'cooperation point / users' combined space backup of the users according to the requirements on time-frequency synchronous constraint and average 'F-norm' of channel matrixes, and dynamically monitoring the 'quality' of all combinations in a backup set; and when users need to be switched, judging whether the combinations meeting the requirements on synchronous errors, Doppler residual frequency difference and the average 'F-norm' of the channels exist in the backup set by a baseband processing unit, if so, carrying out cooperation wave-beam soft switching for the users, and if not, carrying out cooperation wave-beam hard switching. The switching method has the advantages that cooperation resources are distributed for switching users in a self-adaptive manner and the computing complexity of a user side is reduced, and is used for cooperation resource switching under the environment of multipoint-multiuser cooperation communication.
Owner:XIDIAN UNIV
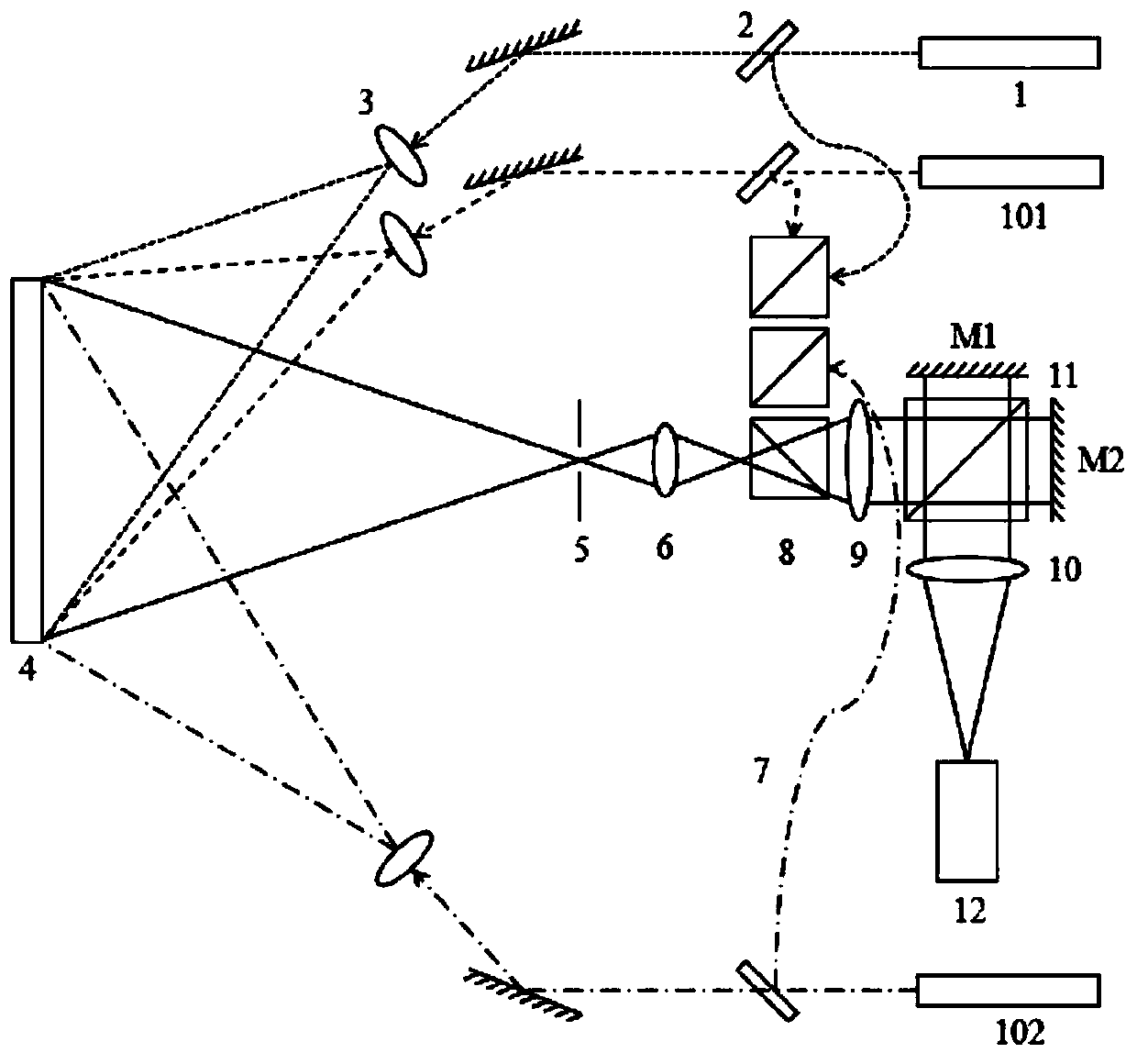
Speckle interference-based synchronous deformation and strain measurement system and method
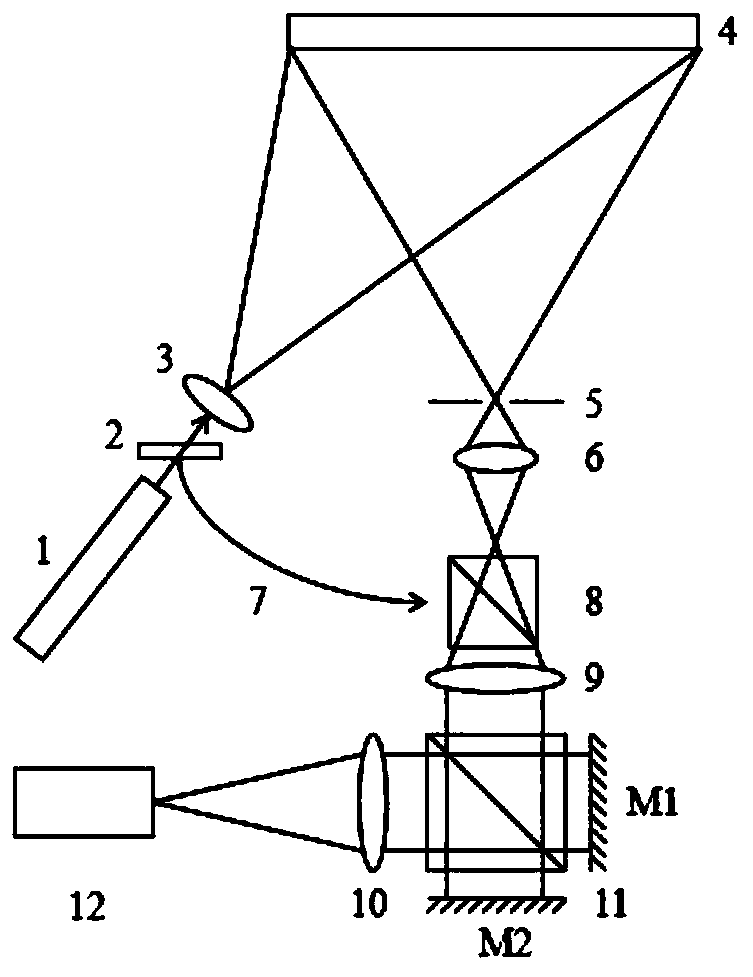
ActiveCN110118537AIncrease the areaImprove measurement efficiencyUsing optical meansBeam splitterFull field
The invention provides a speckle interference-based synchronous deformation and strain measurement system and method, and relates to the technical field of optical test. The system is characterized bycomprising a laser and a beam splitter; the laser light emitted by the laser is divided into transmitted light and reflected light by the beam splitter; the transmitted light is expanded by the beamexpander and then irradiated to a measured object to form diffuse reflected light; the reflected light passes through an optical fiber and a beam splitter prism in sequence to enter an optical path asreference light; the diffuse reflected light passes through a diaphragm, an imaging lens, the beam splitter prism and a Michelson shearing device in sequence to obtain two beams of object light having shear amounts; the reference light introduced by the optical fiber passes through the Michelson shearing device to obtain two beams of reference light having shear amounts; the two beams of object light having the shear amounts and two beams of reference light having the shear amounts interfere each other on the target surface of a CCD camera so as to form a speckle interference diagram. The system can perform synchronous dynamic detection of speckle and shear on the tested objects, and is a non-destructive, full-field and high-precision measurement system.
Owner:HEFEI UNIV OF TECH
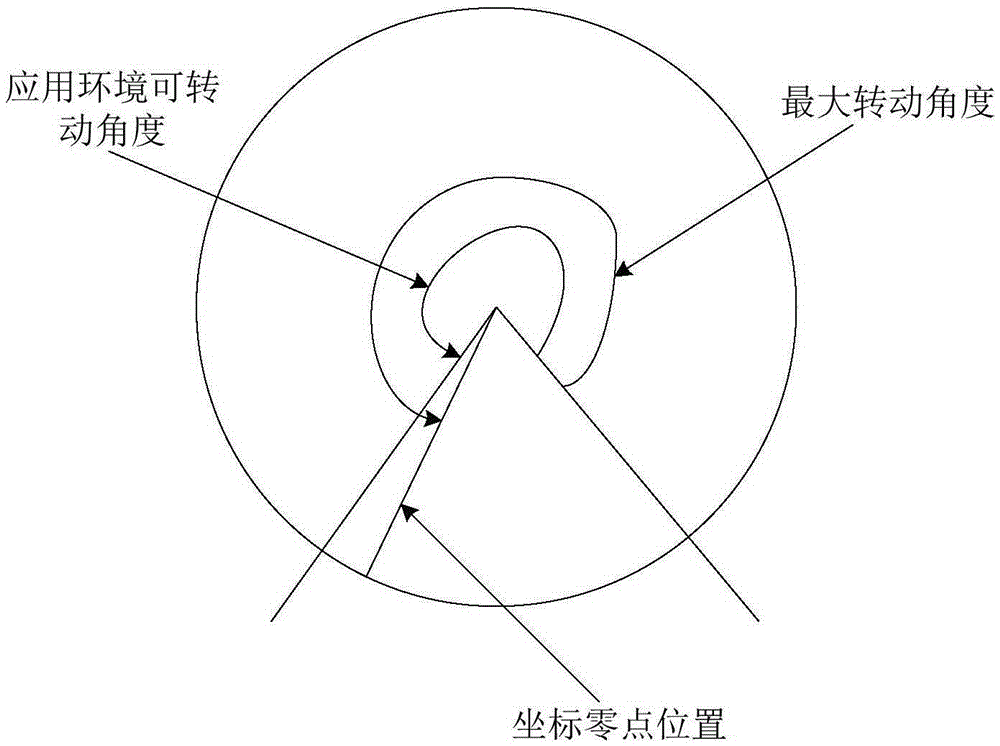
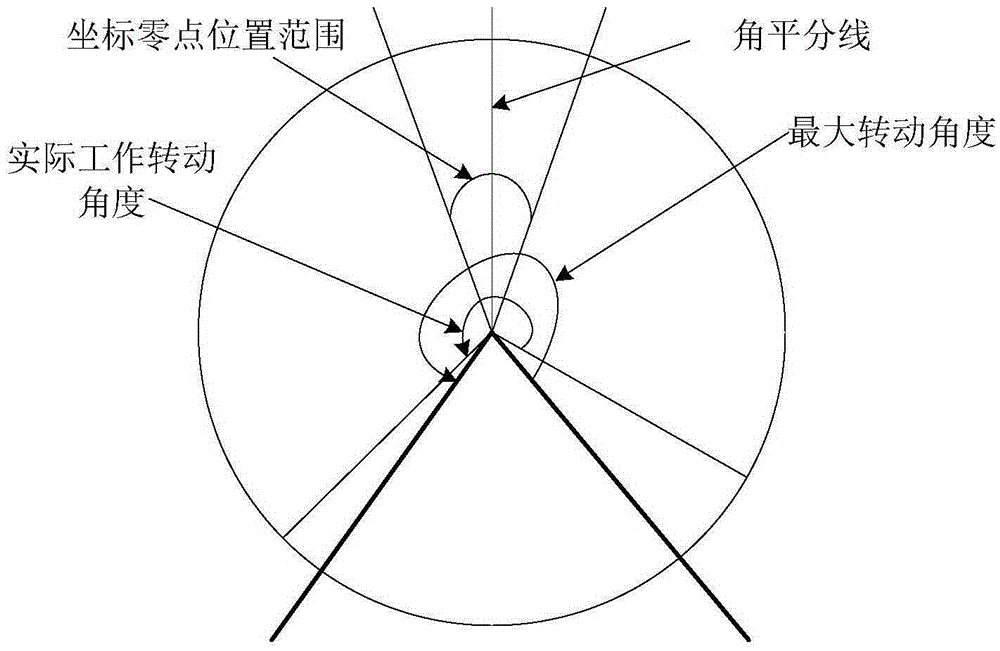
Anti-interference camera and anti-interference method thereof
InactiveCN105391946AAvoid exceptionAvoid damageTelevision system detailsColor television detailsElectricityComputer science
The invention discloses an anti-interference camera and an anti-interference method thereof. According to the anti-interference method, a coordinate zero point position is positioned in a set range at two sides of an angular bisector of a maximal rotational angle of a cradle head, the position, corresponding to the coordinate zero point position, on a rotary structure is a zero point mark position, a signal device is arranged on the rotary structure according to the zero point mark position, and the coordinate zero point position is detected according to the signal device. The anti-interference camera comprises the rotary structure and a detection module and a setting module for setting the coordinate zero point position, the position, corresponding to the coordinate zero point position, on the rotary structure is the zero point mark position, and the signal device is arranged on the rotary structure according to the zero point mark position; the detection module is used for detecting the coordinate zero point position according to the signal device. The anti-interference camera and the anti-interference method thereof can realize fast powering zero point self inspection, and effectively prevents environment interference.
Owner:ZHEJIANG UNIVIEW TECH CO LTD
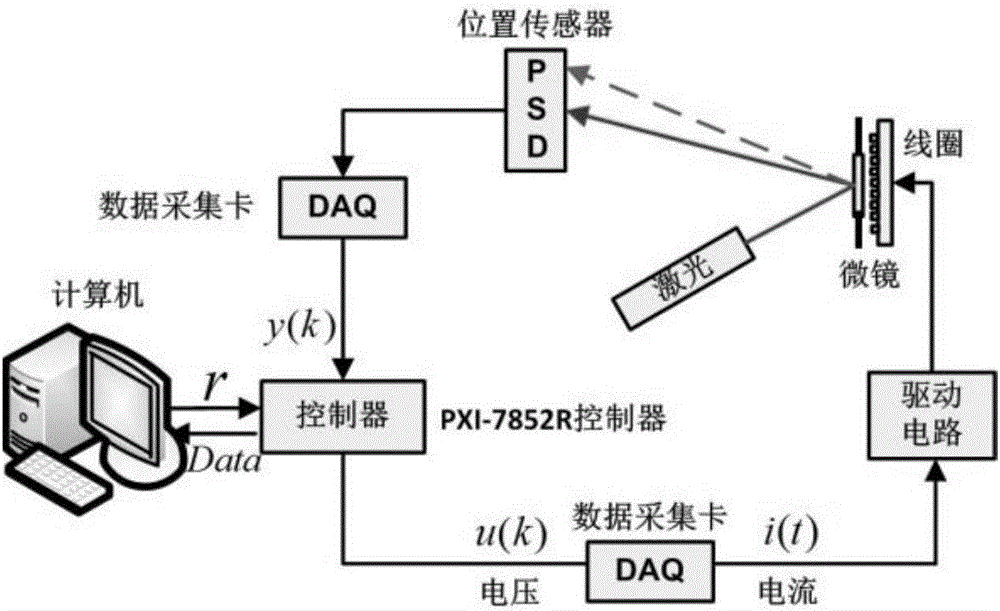
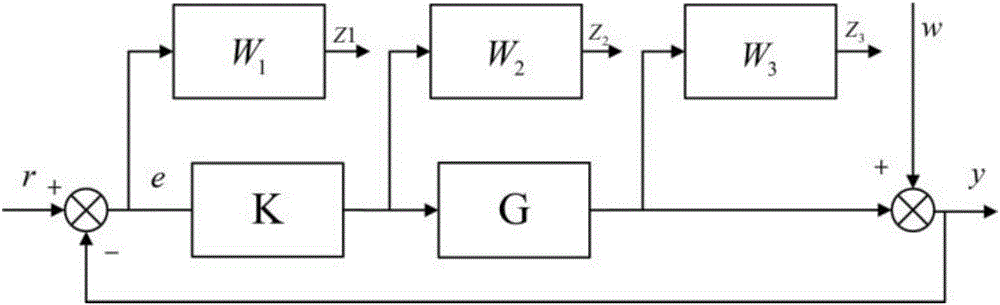
Electromagnetically-driven micro mirror H-infinity control method and H-infinity control system
InactiveCN106647252AImprove dynamic robust performanceReduce power consumptionAdaptive controlLabview softwareA-weighting
The invention discloses an electromagnetically-driven micro mirror H-infinity control method and an H-infinity control system, which are applied to an electromagnetically driven micro mirror platform composed of an NI PXI controller and LabVIEW software and other hardware equipment. The control method comprises the following steps: S1, selecting an optimization model; S2, selecting a weighting function; S3, regulating the parameters of the weighting function; S4, solving an H-infinity controller; S5, analyzing the performance of a closed-loop system; and S6, discretizing the H-infinity controller through a Z transformation method. The electromagnetically-driven micro mirror H-infinity control method is disclosed in view of the shortcomings of the existing electromagnetically driven micro mirror PID control method. On the basis of ensuring good dynamic and static characteristics of the micro mirror system, the method improves the un-modeled dynamic robust performance of the system, reduces the power consumption of the controller, and restrains the output noise. The method achieves a good control effect, and is more in line with the requirements of practical application.
Owner:SOUTH CHINA UNIV OF TECH
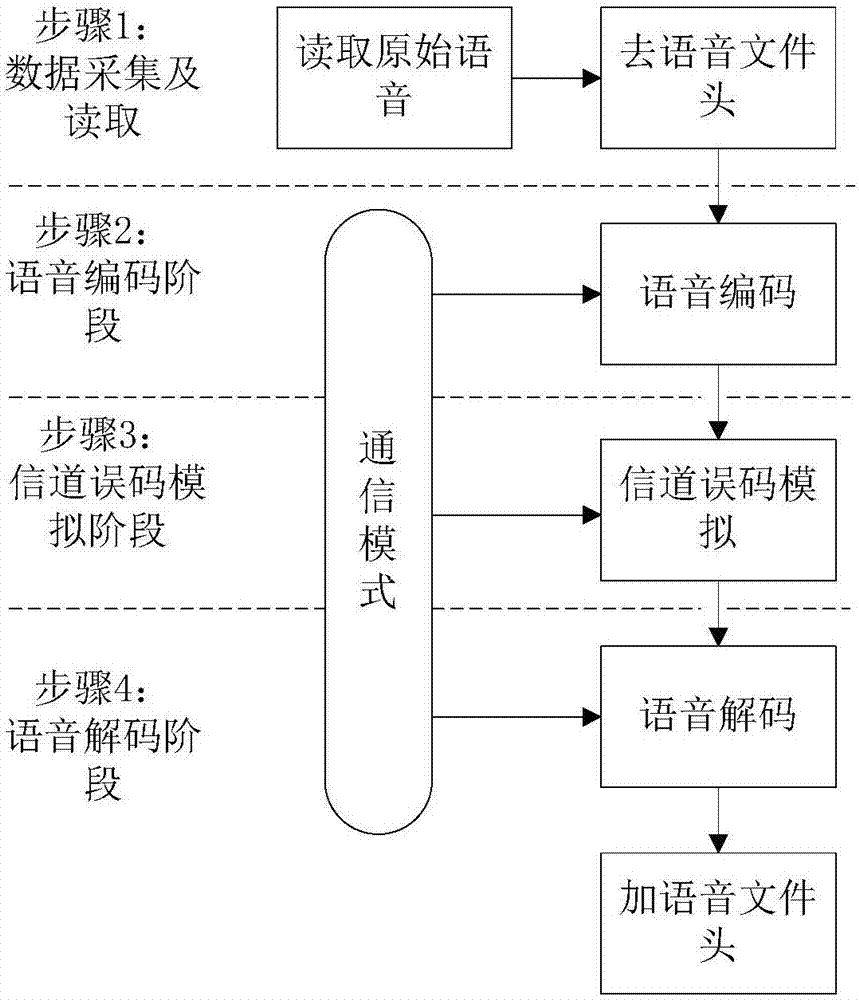
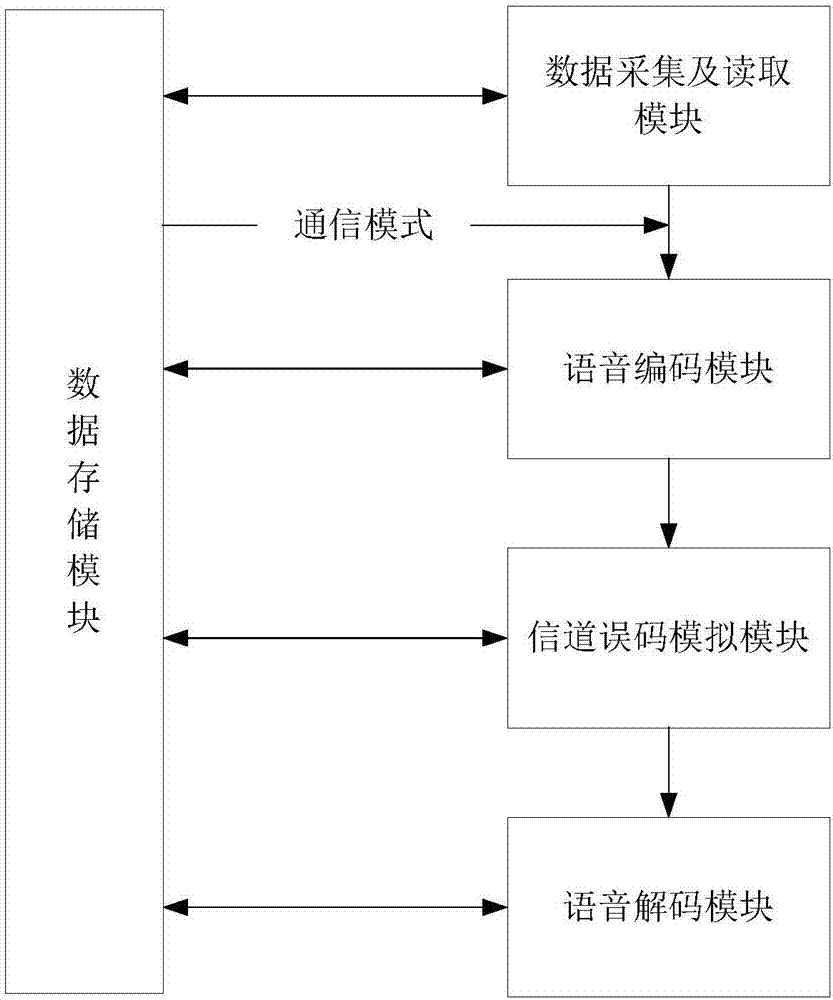
Voiceprint-recognition-based channel matching method and device
The invention, which belongs to the fields of voice recognition and voice communication, provides a voiceprint-recognition-based channel matching method and device. According to the method, voice data are collected; according to a needed simulated communication mode, voice coding is carried out on the voice data to obtain compressed voice data; error code processing is carried out on the compressed voice data according to an error code rate of channel simulation in a corresponding communication mode to obtain channel simulation voice data; and then voice decoding is carried out on the voice data to obtain voices in a corresponding communication mode. In addition, the device is composed of a voice acquisition and reading module, a voice coding module, a channel error code simulation module, a voice decoding module and a data storage module. Therefore, fixed-phone, VOIP, WeChat-phone, QQ-phone, 2G, 3G, 4G and other voice communication processes can be simulated to obtain training voices having the same channel conditions as the testing voice, so that the channel mismatch problem is solved. The voiceprint-recognition-based channel matching method and device are suitable for meeting the voiceprint recognition application need.
Owner:TSINGHUA UNIV
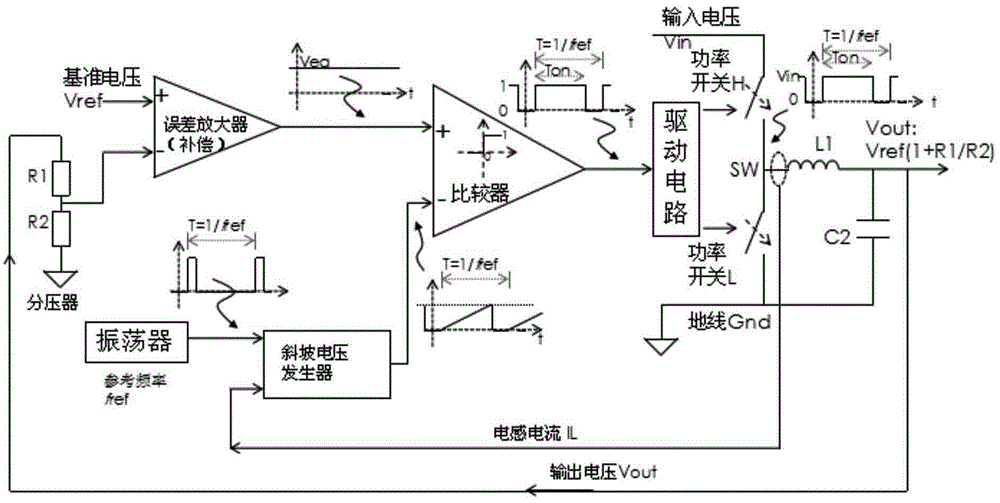
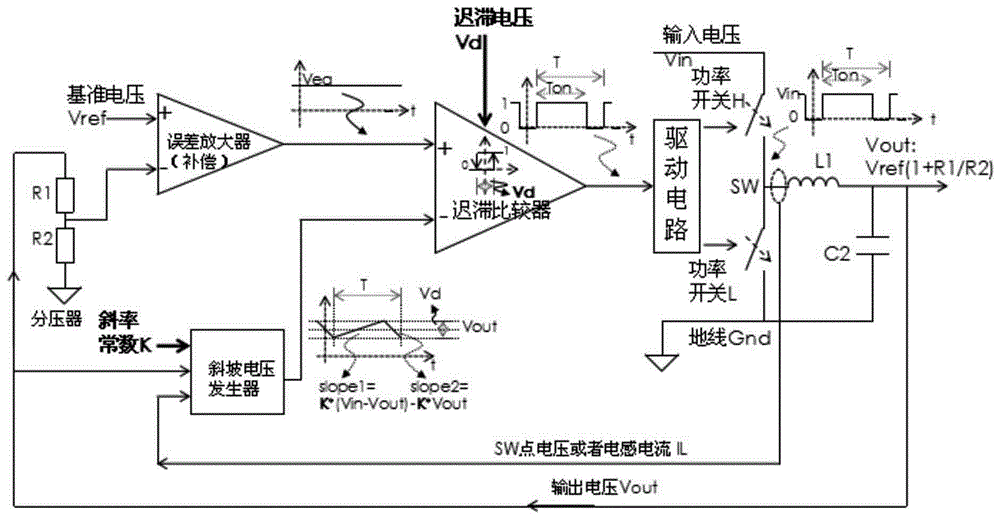
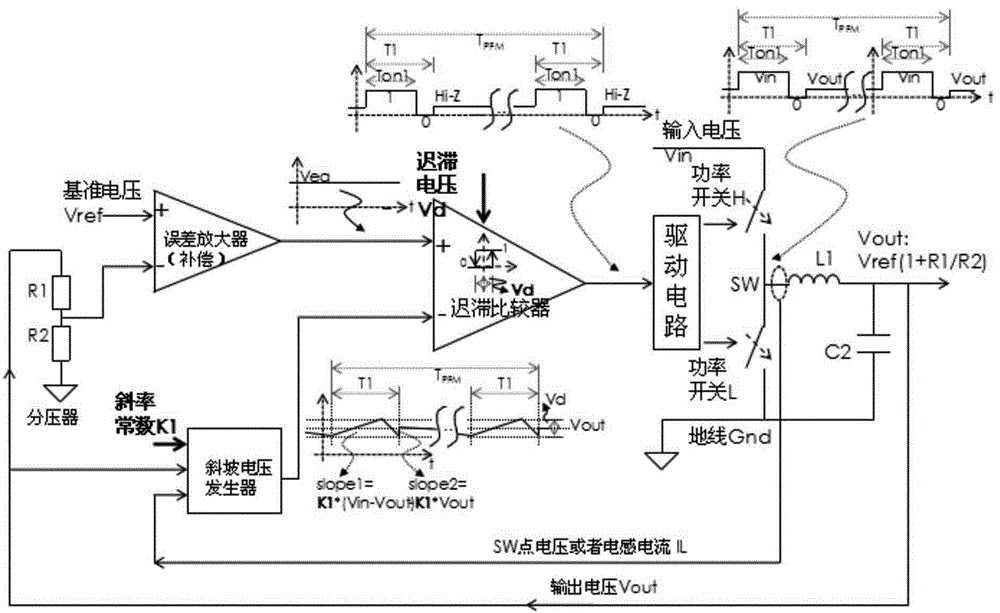
Control method of hysteresis controller in PWM and PFM modes
ActiveCN105958820AOutput Ripple GuaranteedMeet the actual application needsDc-dc conversionElectric variable regulationVoltageHysteresis
The present invention relates to a control method of a hysteresis controller in PWM and PFM modes. According to the method, the maintenance of a fixed working frequency in a PWM working mode is needed, and an output voltage ripple similar to PWM is maintained in a PFM working mode. In the PWM working mode, a frequency follower is used to monitor the difference between a reference oscillator and a PWM working frequency, an error is used to do a corresponding parameter change, and thus the PWM working frequency is driven to be fixed to a reference frequency. In the PFM working mode, through recording the actual numerical value needed by a system in the PWM mode in real time and storing the actual numerical value by using a memory unit, after the system is switched to the PFM mode, and the actual numerical value is directly called and used by a control loop. According to the method, when the system is in the PWM and PFM working modes, a determined working frequency and a determined output ripple can be ensured so as to ensure that the system conforms to the requirement of practical application.
Owner:HALO MICROELECTRONICS CO LTD
Single chip working method of wireless charging receiving end for directly charging battery
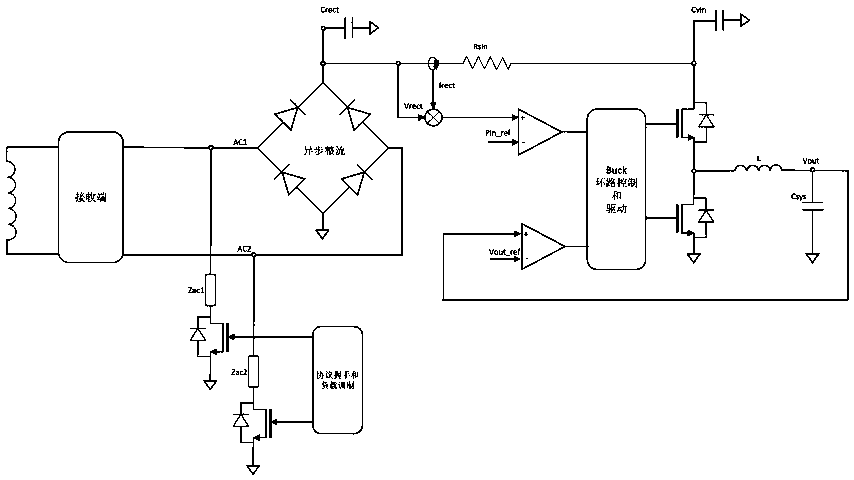
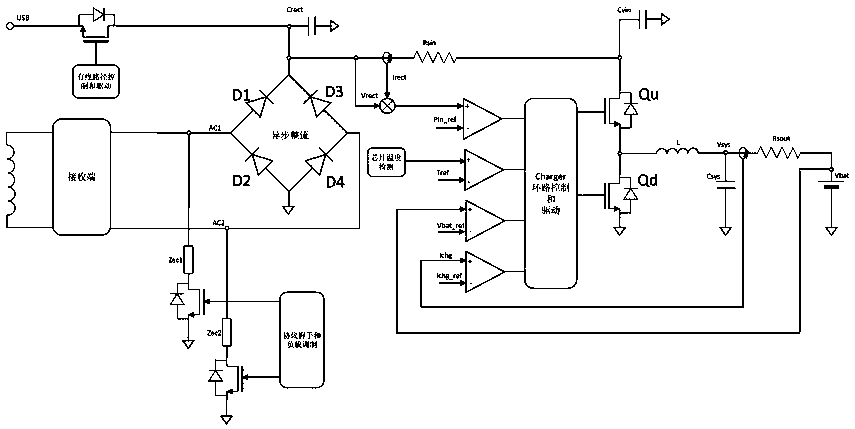
InactiveCN108183559AReduce areaLow costCharging managementDc-dc conversionElectrical batteryFast charging
The invention provides a single chip working method of a wireless charging receiving end for directly charging a battery. According to the scheme, the single chip simultaneously realizes wireless communication and quick charging and the scheme has higher charging efficiency, less peripheral components and smaller circuit board design. DC power supply recovery of the wireless receiving end is completed on the chip by using the mode of the AC rectifier. The power supply is utilized for the subsequent circuit to directly charge the battery connected with the output end, wherein the input power, the output current and the output voltage are correspondingly regulated by using the subsequent circuit in the charging process. The basic framework of wireless charging is realized through the singlechip so as to acquire smaller circuit area, lower cost and higher charging efficiency and ensure that the system meets the requirements of actual application.
Owner:HALO MICROELECTRONICS CO LTD
Face detection method based on clustering analysis and model compression
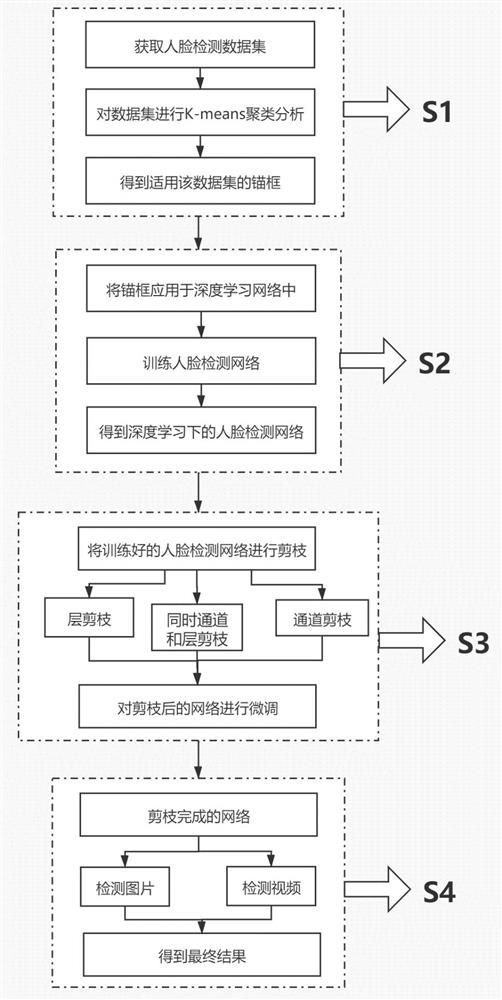
PendingCN112132005AHigh precisionMatch the quantityCharacter and pattern recognitionNeural architecturesPattern recognitionFace detection
The invention relates to a face detection method based on clustering analysis and model compression. The method comprises the steps: firstly obtaining a face detection data set, carrying out K-means clustering analysis of the face data set, carrying out analysis of the number and a size of anchor frames and an application degree of the data set, and finally generating a detection anchor frame mostsuitable for the data set; applying the generated detection anchor frame to a deep learning network, and training a face detection network; finally, after layer pruning or channel pruning is performed on the trained face detection network, carrying out fine adjustment on the network, and acquiring a lighter-weight network; and detecting the image and the video by using the network to obtain a final result. The method has advantages of high detection accuracy and a high detection rate, and can be applied to human face attendance, access control systems, traffic identity approval and other scenes.
Owner:FUZHOU UNIV
Voice processing model training method and device and voice processing method and device
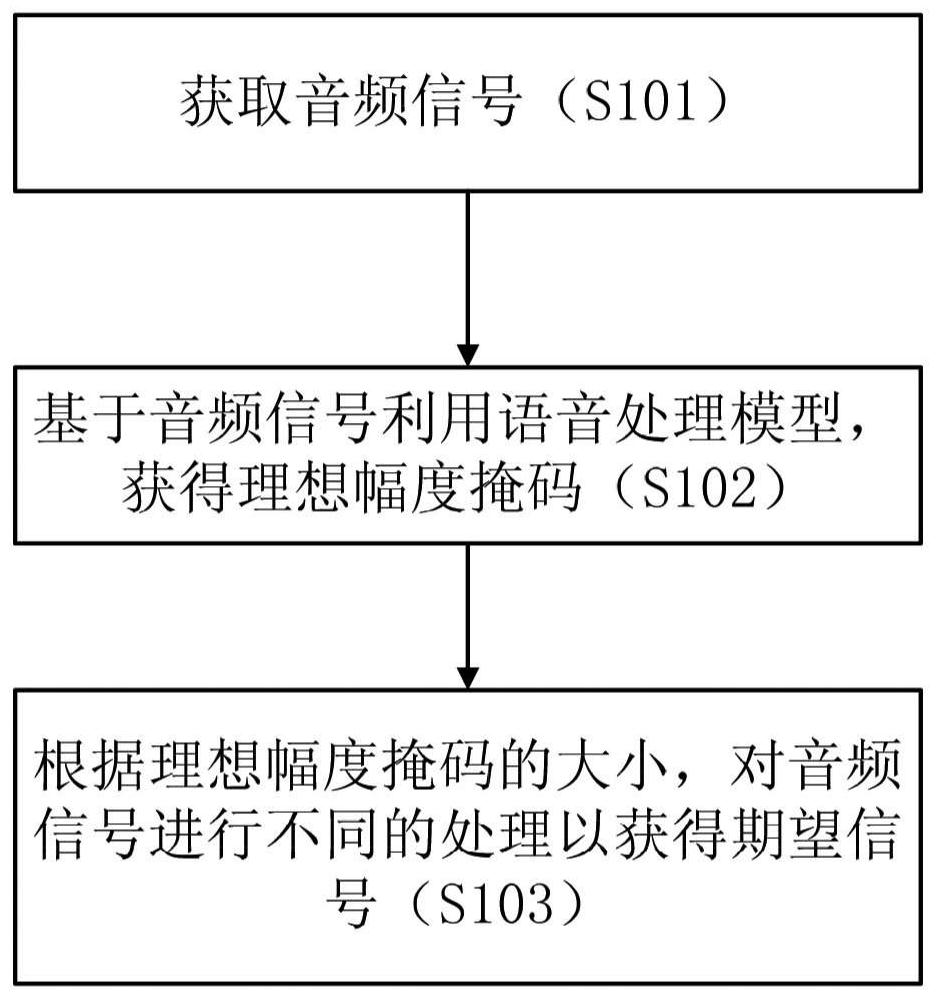
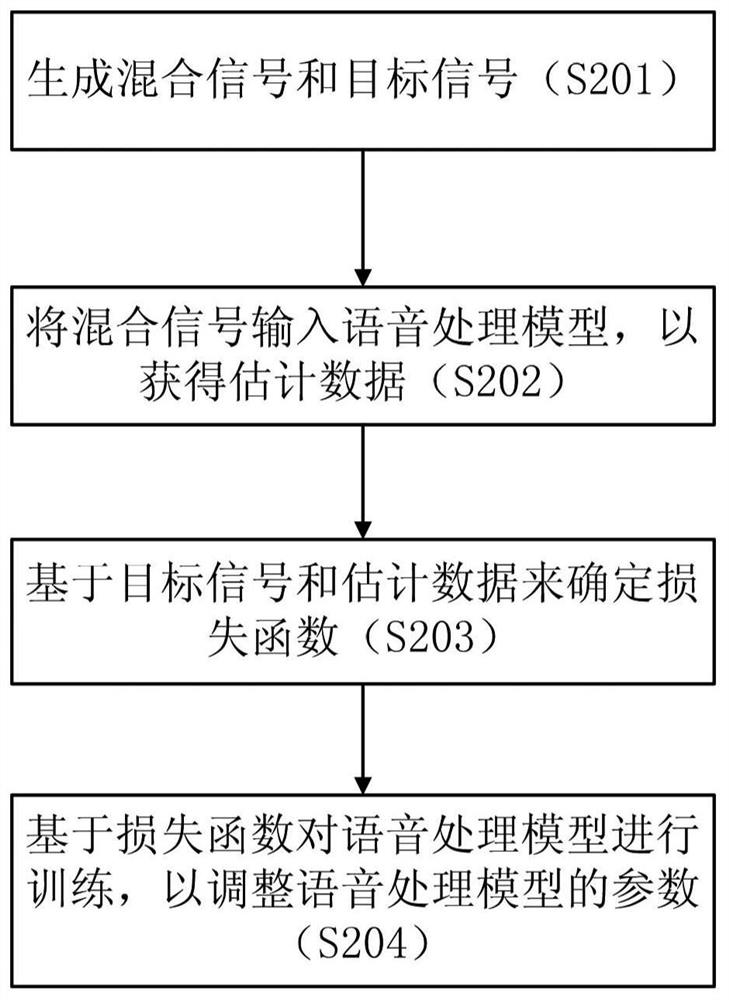
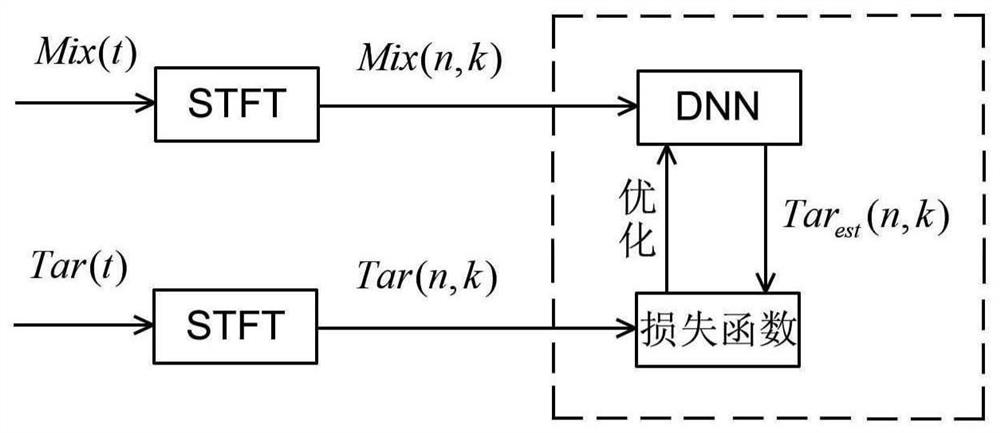
PendingCN112309426AMeet the actual application needsSpeech analysisNeural architecturesTarget signalSpeech sound
The invention provides a voice processing model training method and device and a voice processing method and device. The training method comprises the following steps: generating a mixed signal and atarget signal based on at least one of a voice signal, a noise signal and a specific signal; inputting the mixed signal into a voice processing model to obtain estimated data; determining a loss function based on the target signal and the estimation data; and training the voice processing model based on the loss function so as to adjust parameters of the voice processing model.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
Wireless low-jitter transmission method for high-precision digital asynchronous pulse
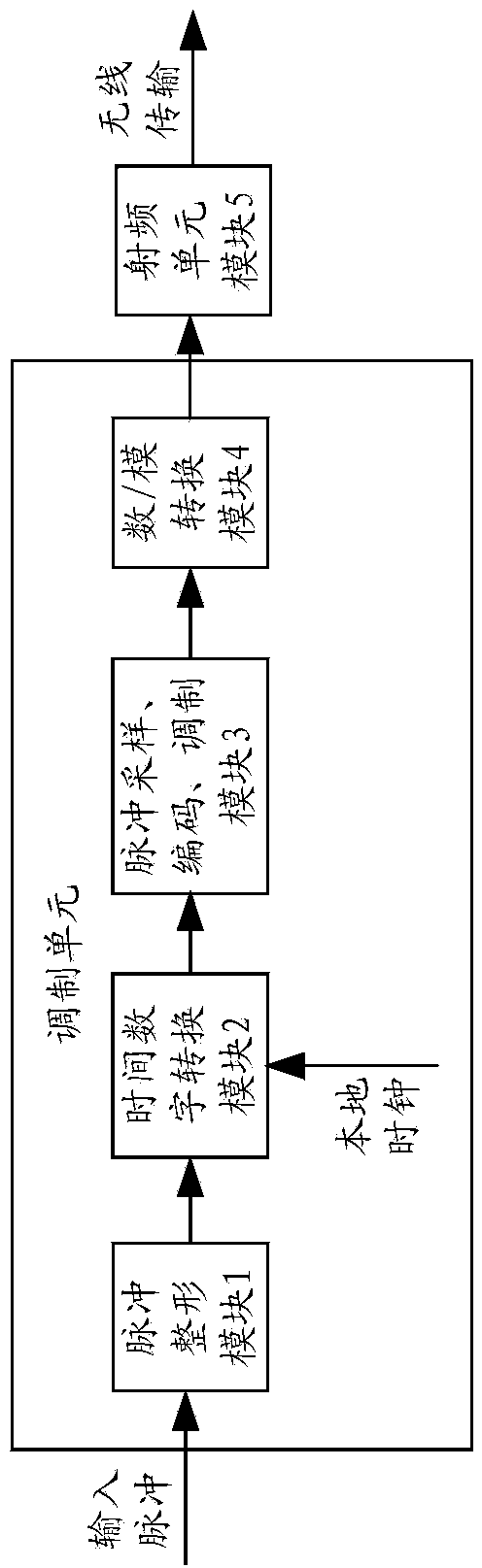
ActiveCN103905015AImprove processing precisionMeet the actual application needsPulse manipulationLow jitterEngineering
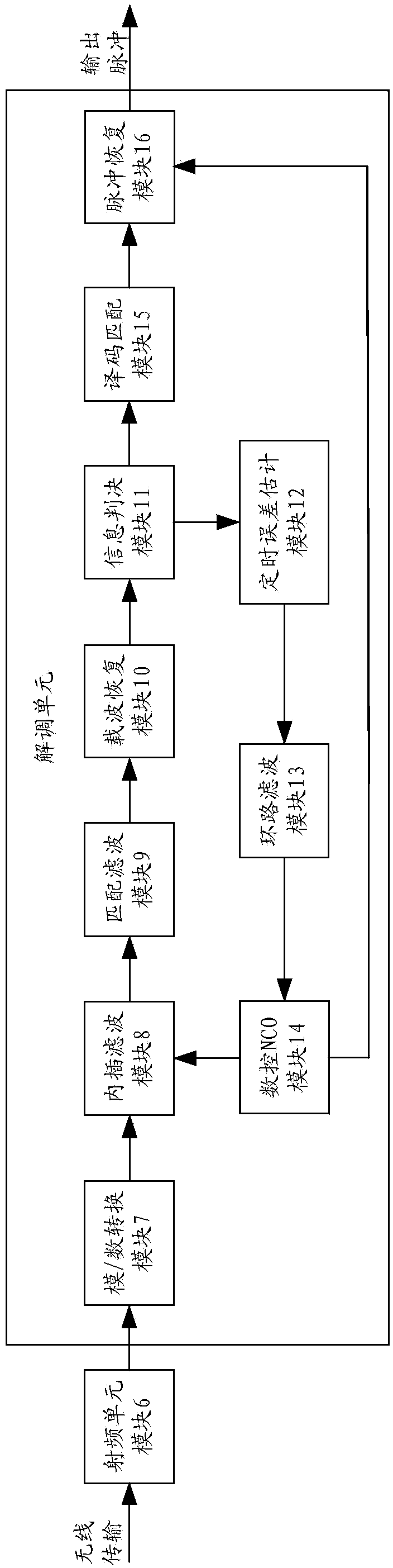
The invention relates to a wireless low-jitter transmission method for a high-precision digital asynchronous pulse in the field of pulse wireless transmission and communication, and the wireless low-jitter transmission method is particularly suitable for wireless low-jitter transmission of a radar pulse. Pulse shaping is carried out on a transmitting terminal, a time-digital conversion module is used for converting the time difference between an asynchronous pulse signal obtained after pulse shaping and a rising edge or a falling edge of a local clock into a digital signal, and the steps of digital sampling, encoding, modulation and the like are conducted on the digital signal; on a receiving terminal, a timing error estimation module, a loop smoothing module, an NCO module, an interpolation and filtering module and the like are used for improving the precision of the local clock, output pulse phase position errors are reduced on the premise that the bandwidth is not sacrificed, and finally a high-precision low-jitter pulse signal is output. According to the wireless low-jitter transmission method, a full-digital processing method is adopted, and the high-precision asynchronous low-jitter pulse transmission effect can be realized without local clock synchronization. Main circuit components are obtained through FPGAs or ASICs, so that the design difficulty and the modulation difficulty are low.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
Preparation method for cuprous oxide coated molding carbon material
InactiveCN108400346AEasy to prepareStable film forming effectFinal product manufactureCell electrodesIonHeavy metals
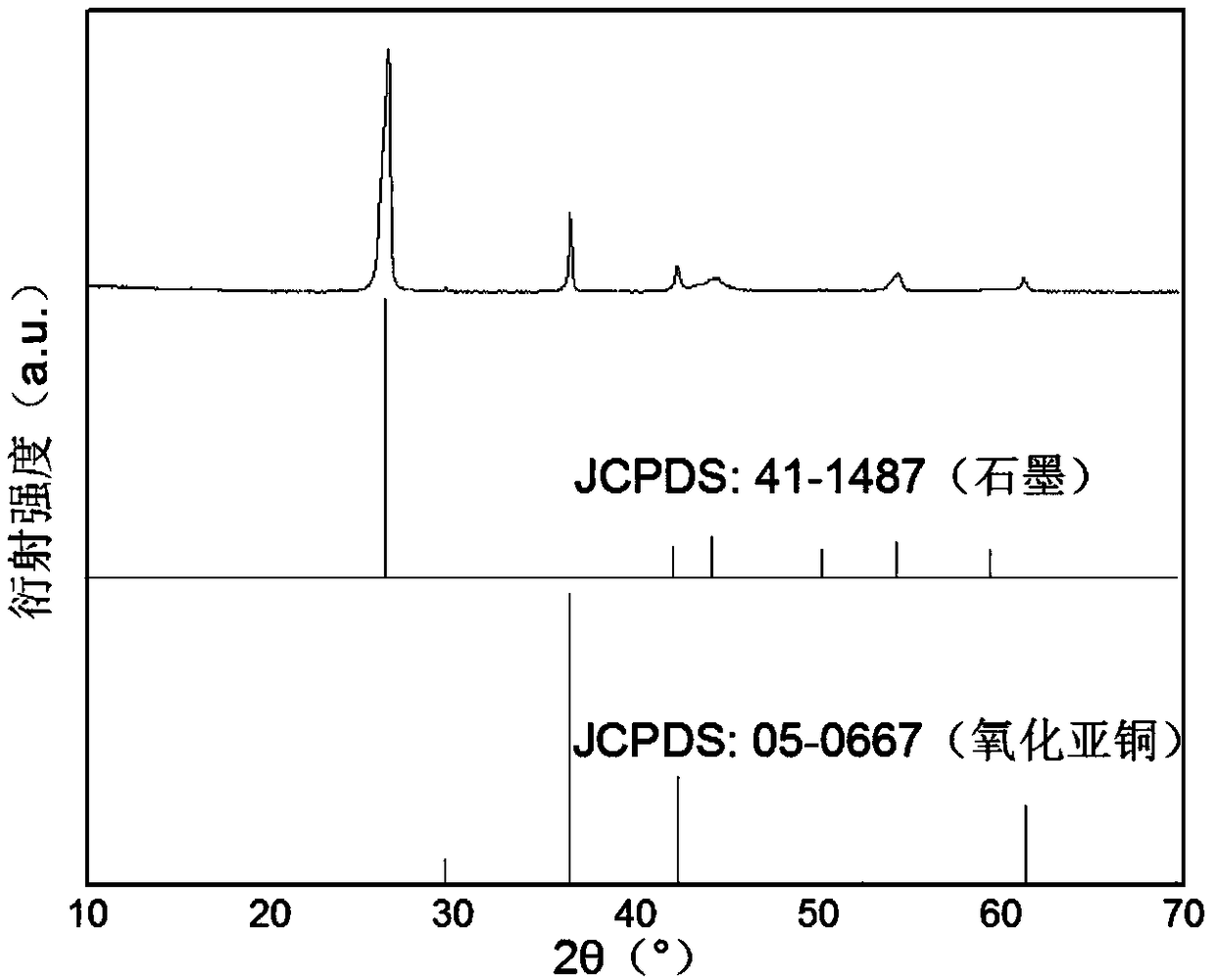
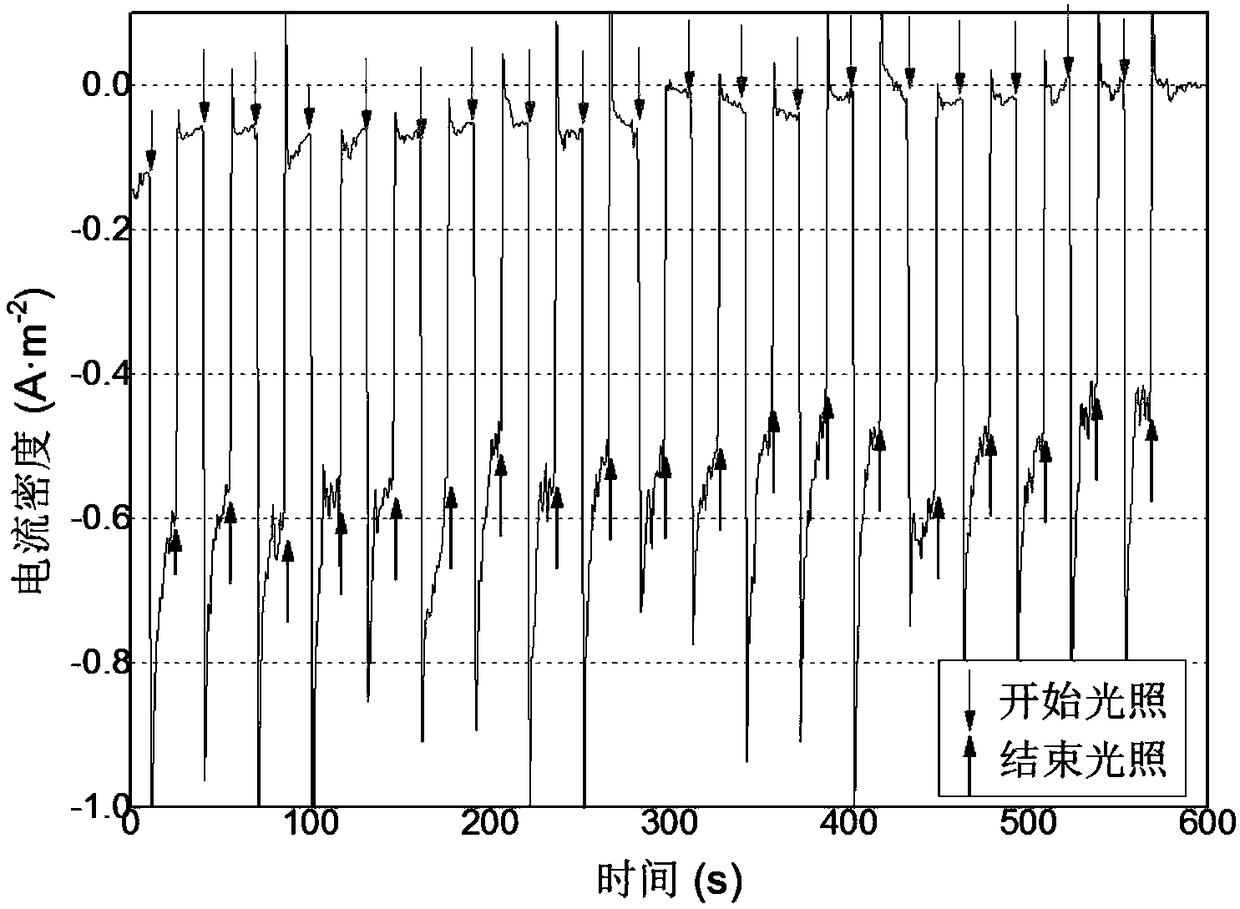
The invention relates to the field of new energy and sewage treatment, and aims at providing a preparation method of a cuprous oxide coated molding carbon material. The method comprises the followingsteps of grinding and cleaning a molding carbon material, and soaking in mixed solution of copper nitrate and a stabilizer; carrying out electric reduction treatment; washing with deionized water, andsoaking in the deionized water at room temperature; and carrying out vacuum drying under a dark condition to obtain the cuprous oxide coated molding carbon material. According to the method, the molding carbon material is used as a cuprous oxide substrate material for the first time and more conforms to the actual application requirements; a prepared product has remarkable photoelectric responseunder the visible light irradiation; the thickness of a cuprous oxide thin film can be adjusted by regulating the current density and the electrodeposition time; the preparation method is simple, thefilm forming effect is stable, and mass production is facilitated. The method is carried out at low temperature, the current density is small, the current utilization rate is high, and the energy costis low. The used electrolyte is low in heavy metal content and easy to treat.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com