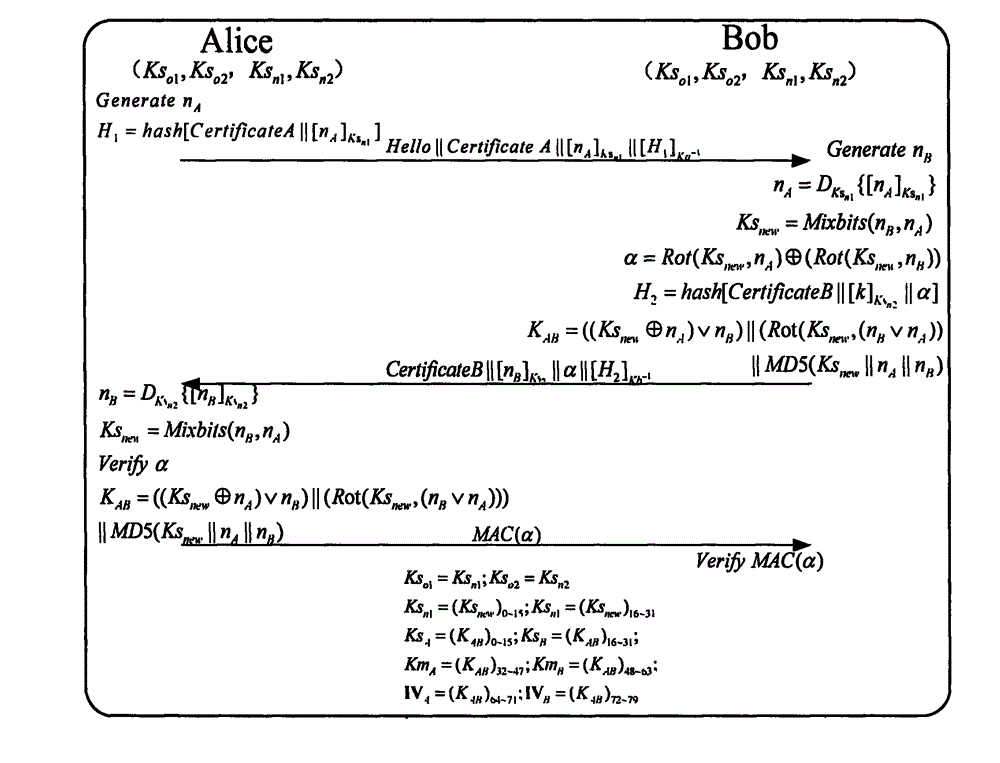
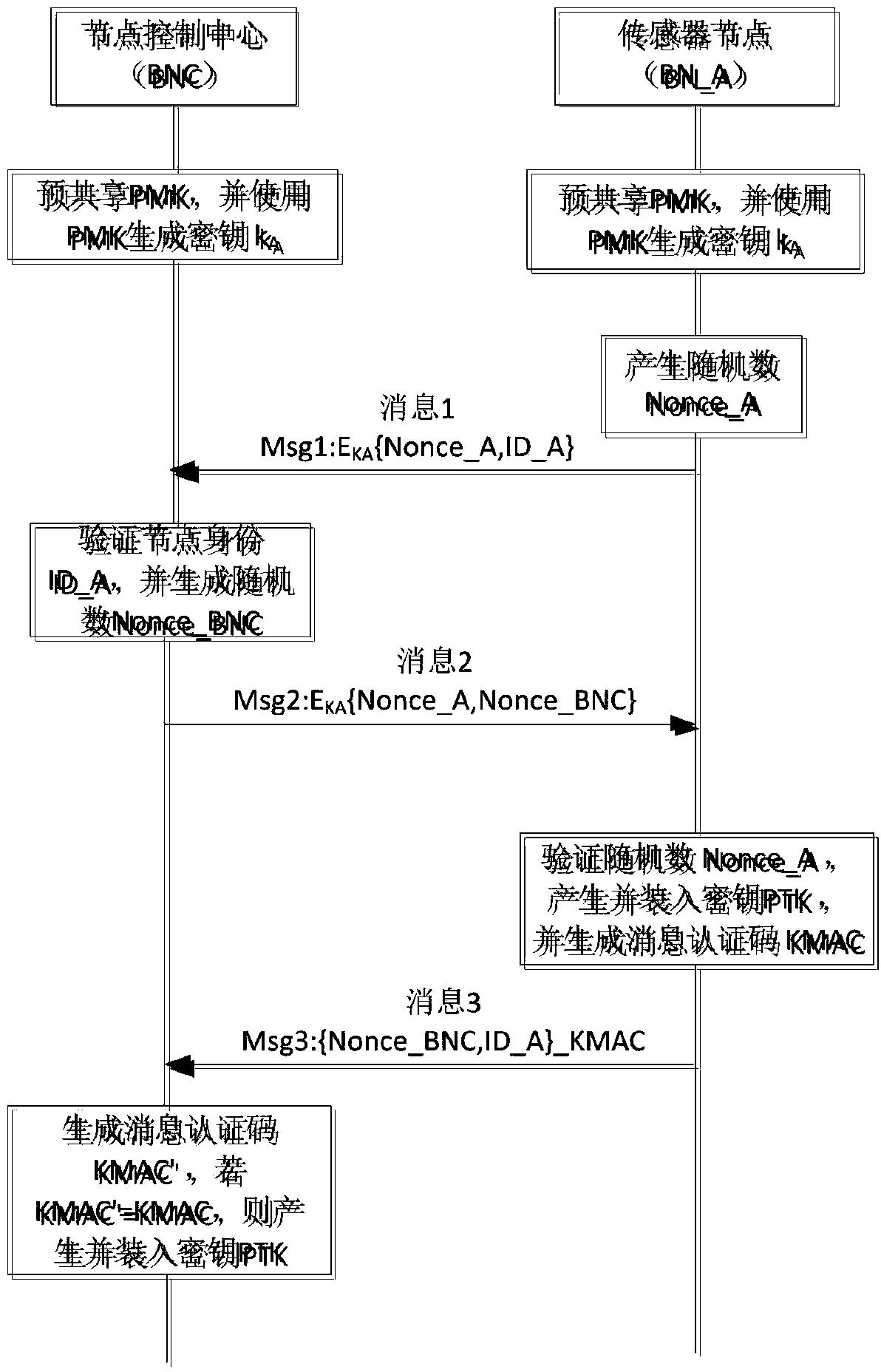
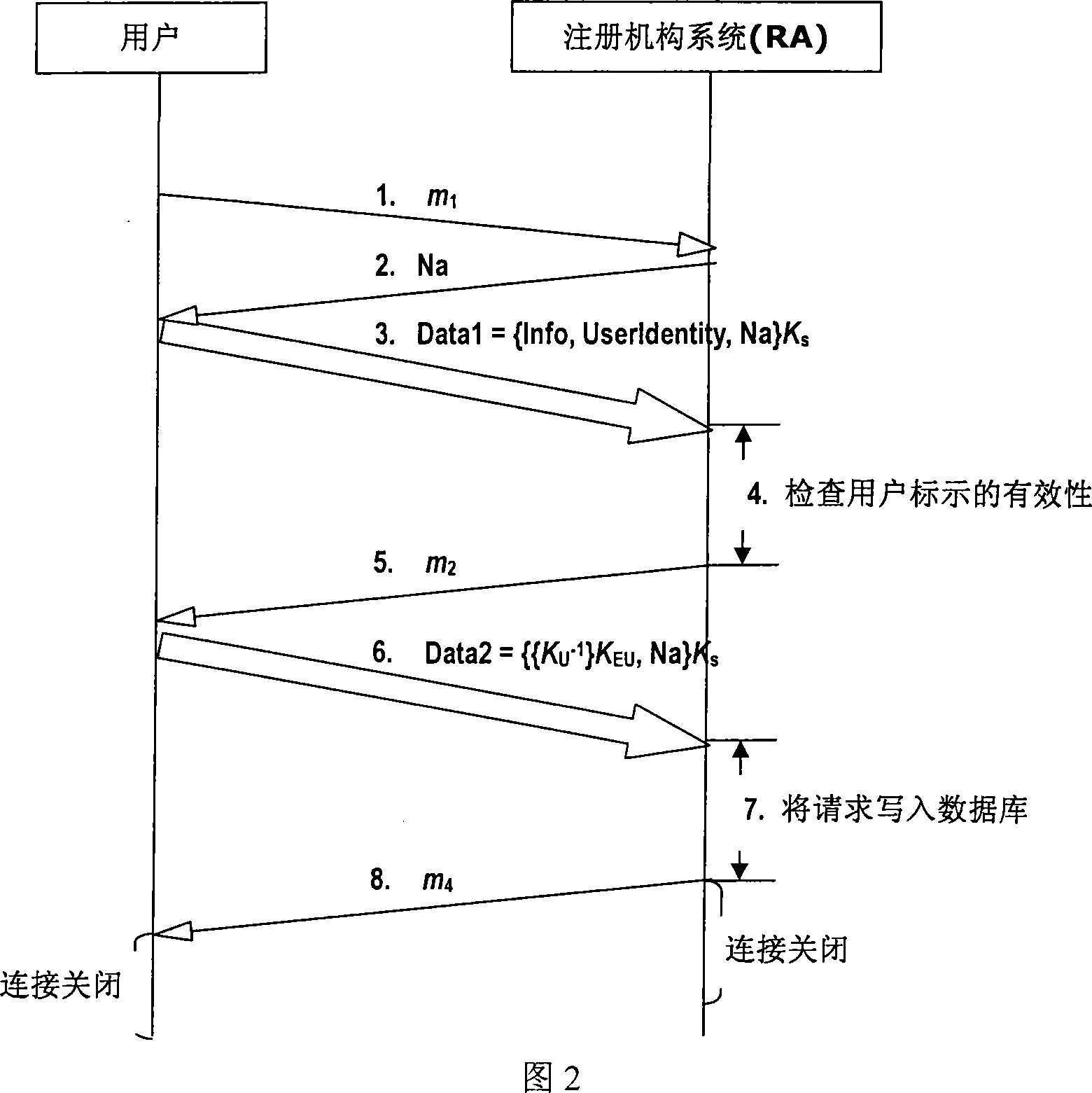
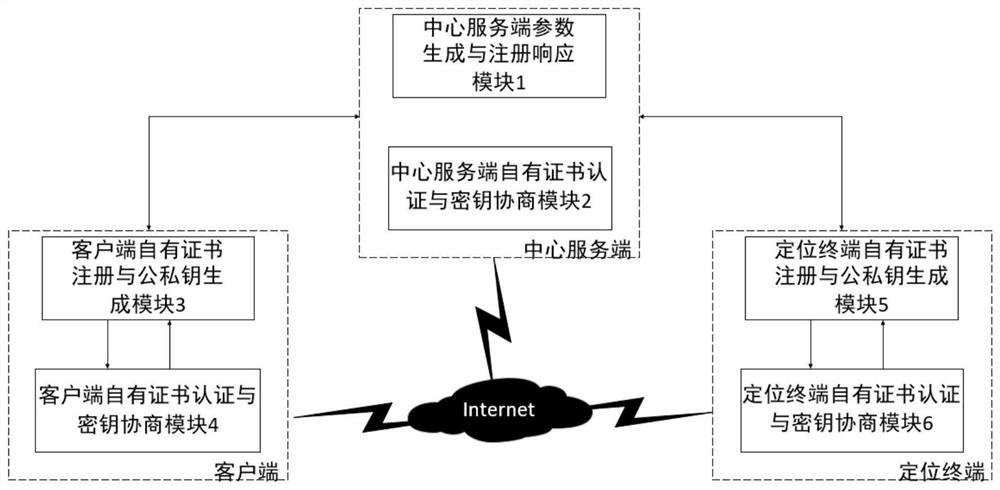
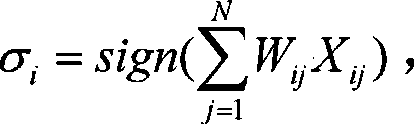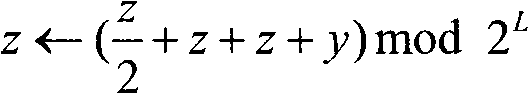Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
138results about How to "Defense against replay attacks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
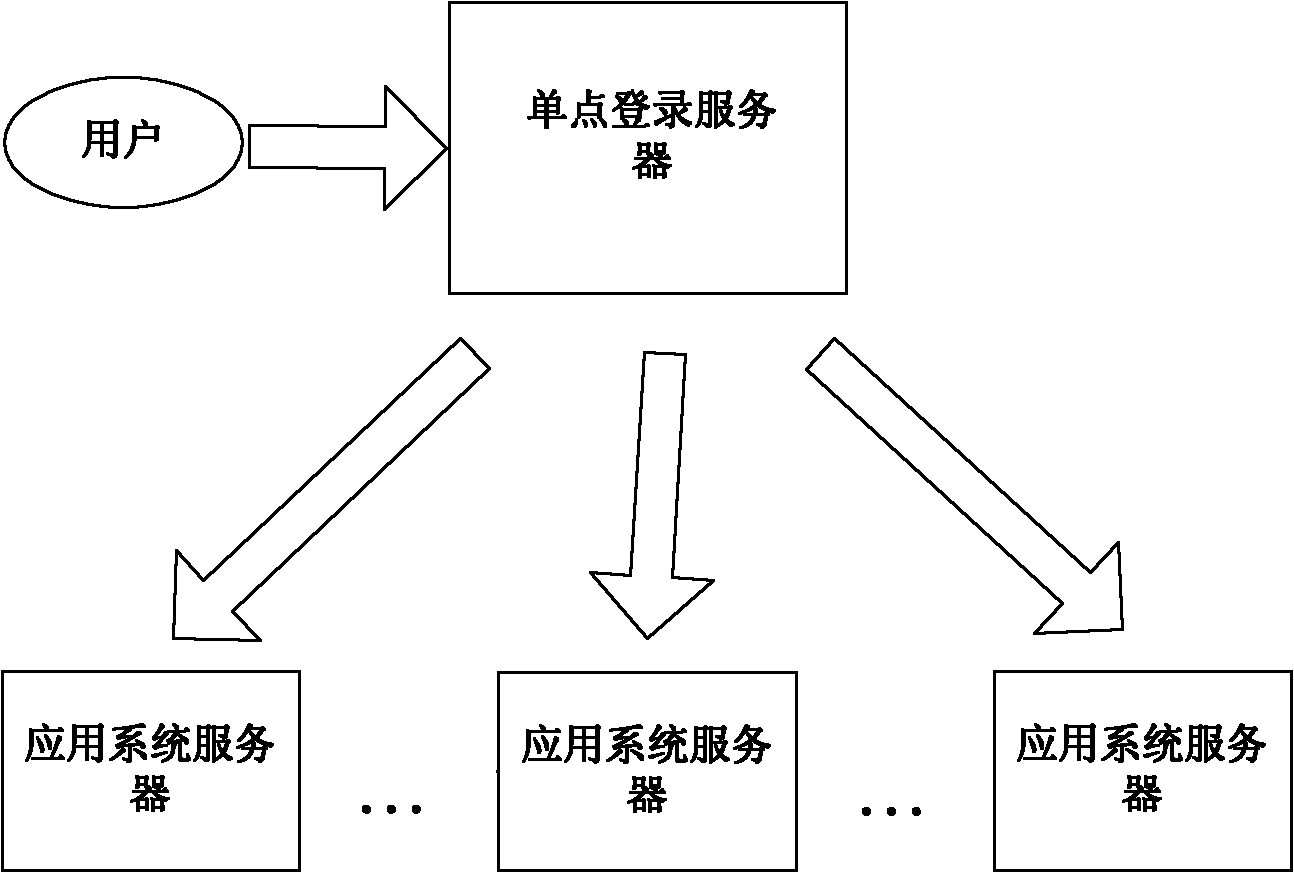
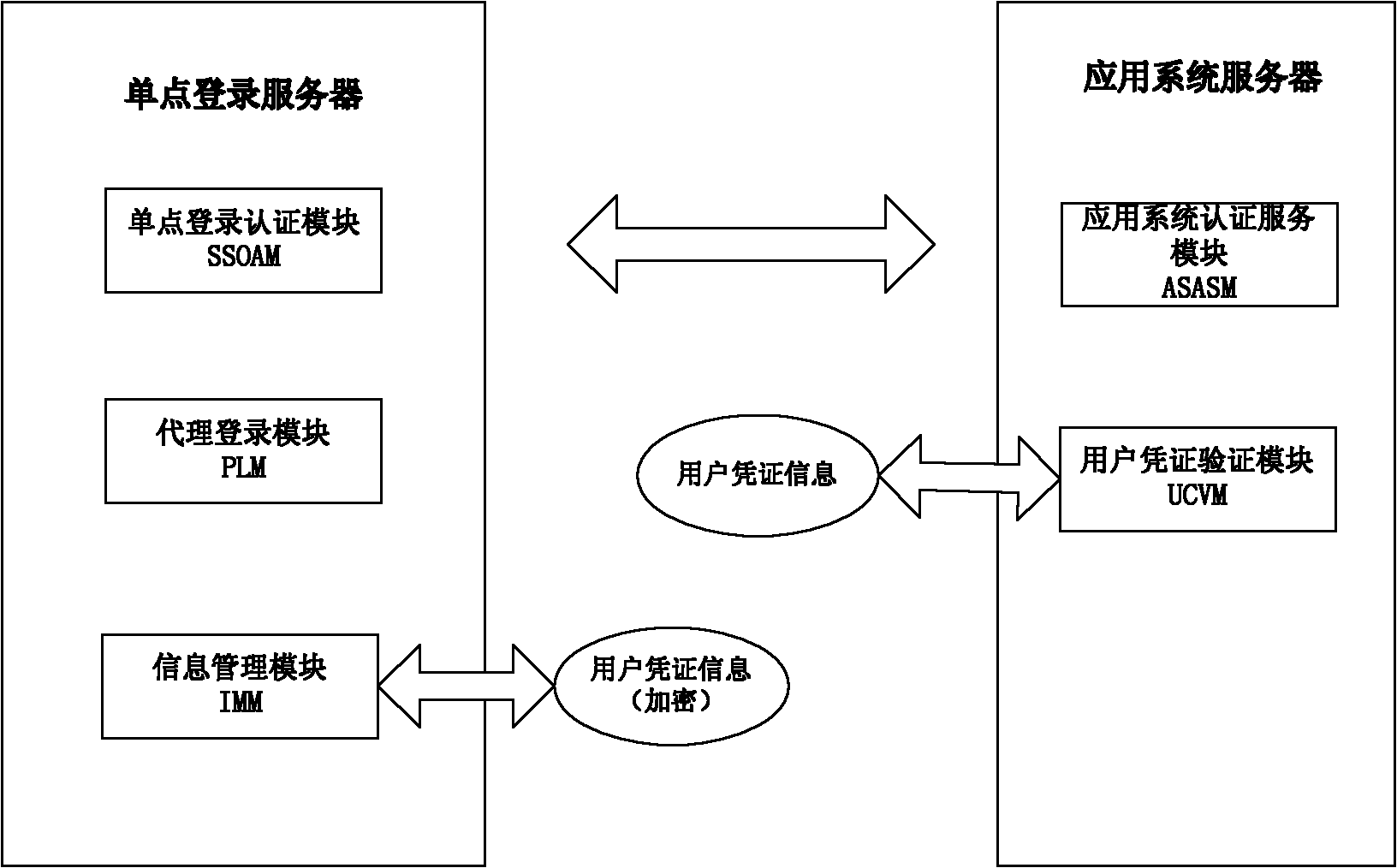
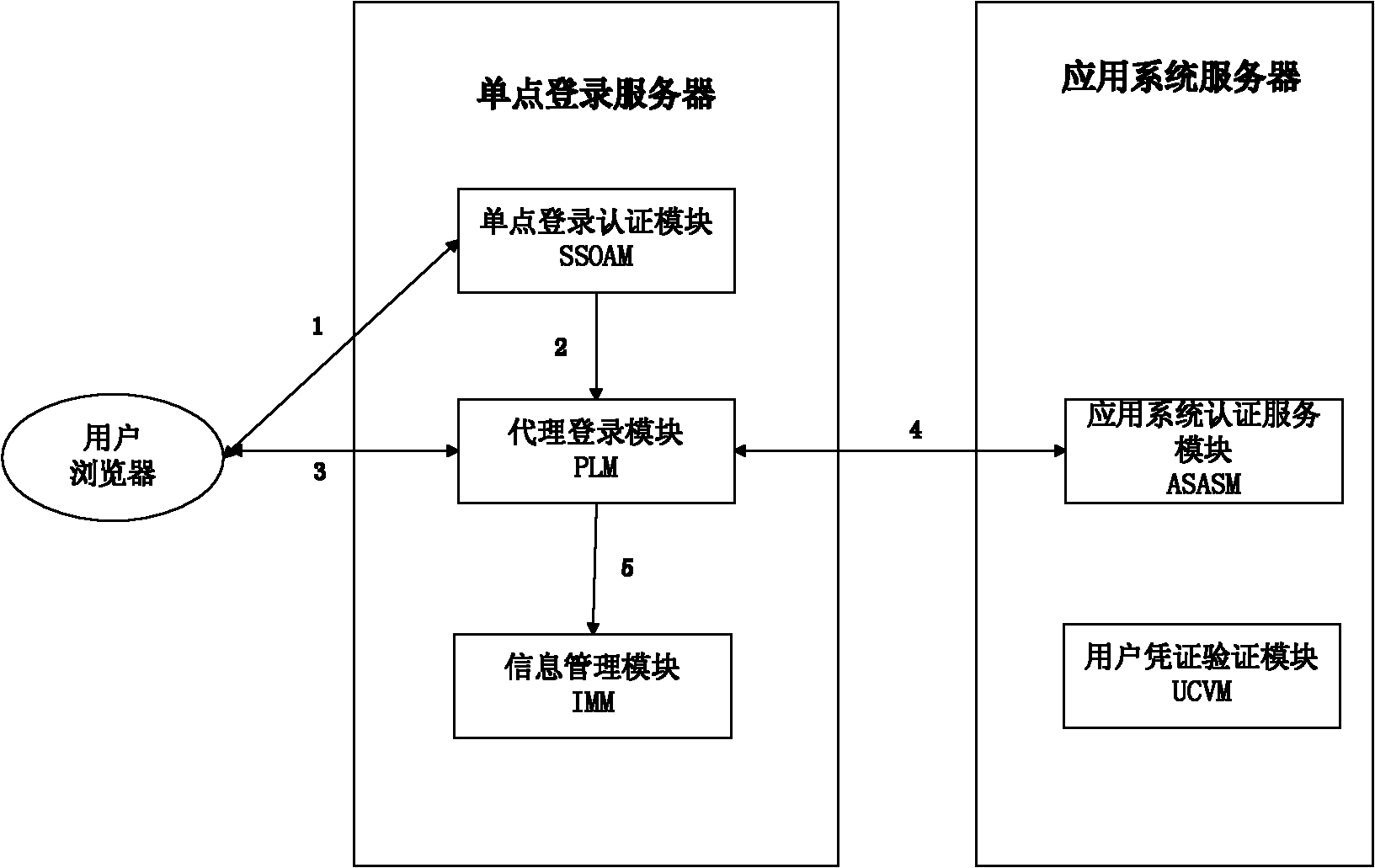
Agent-based single sign on (SSO) method and system
InactiveCN102111410AThe configuration cost is reasonableProtect personal privacyUser identity/authority verificationApplication serverCiphertext
The invention discloses an agent-based single sign on (SSO) method and system, belonging to the technical field of computer information. In the method, a user (U) registers and acquires a user certificate (C) in an application server (S); the U logs in an SSO server (L) and sends a certificate setting request; the L stores user identifications, application server identifications and ciphertext (C') in an associated manner; the U logs in the L and requests to access the S; the L is interacted with the S to acquire a token issued by the S and a signature (sig) of the S for the token; the L usesa self-private key to sign the token to acquire sig' and then searches the C' associated with the U identifications and the S identifications as well as sends the C', the token and the sig' to the U;the U uses a private key in the user C to decrypt c' so as to acquire C, and sends SSO server identifications, the C, the token and the sig' to the S; and the S verifies the token and the sig', if the token and the sig' pass the verification, the user C is continued to be verified; and if the user C passes the verification, the U is permitted to log in. The invention also discloses an SSO system corresponding to the SSO method.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
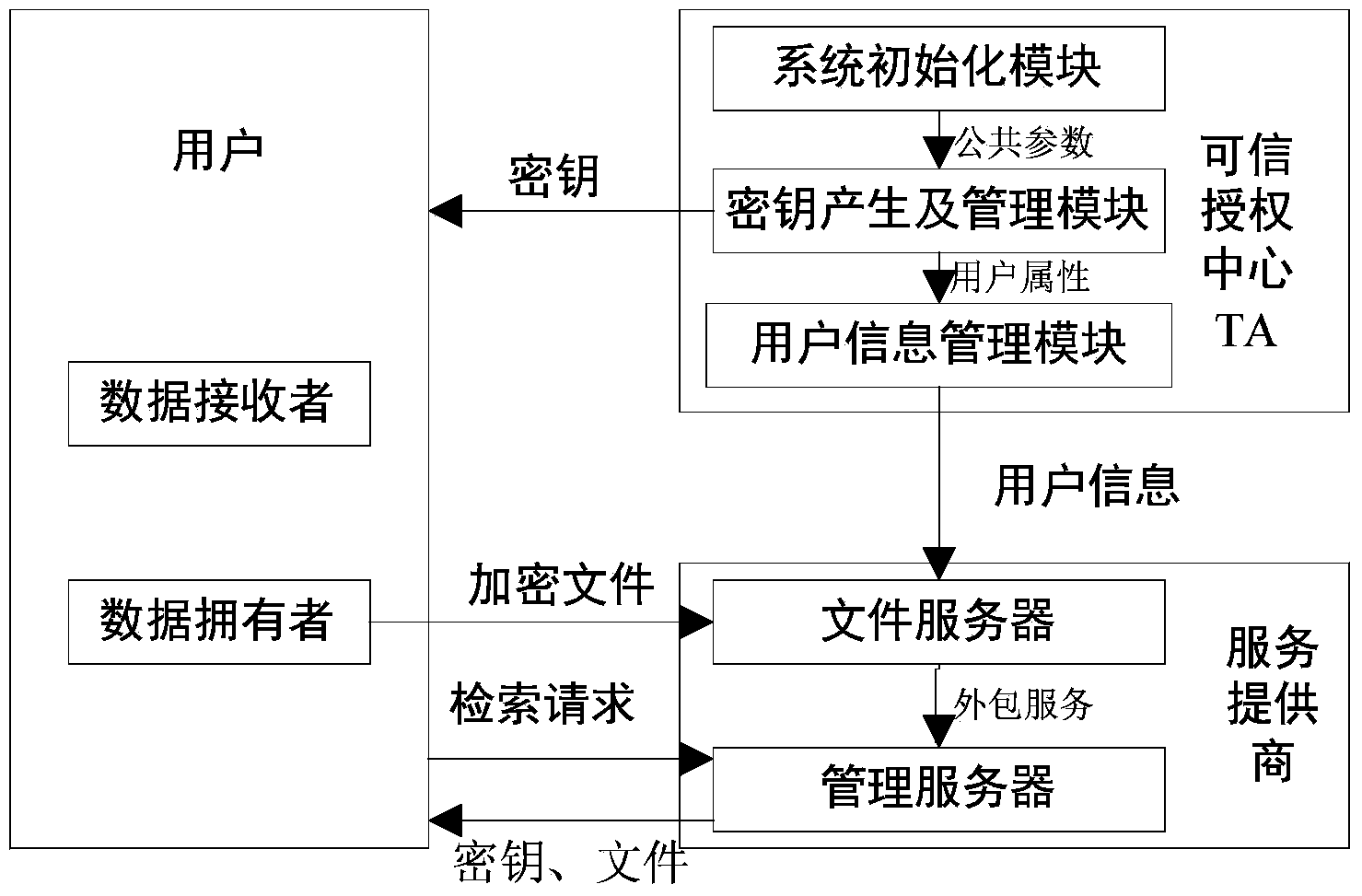
Multi-user supported searchable encryption system and method
InactiveCN103731432AMeet the actual application needsImprove securityKey distribution for secure communicationSpecial data processing applicationsData providerService provision
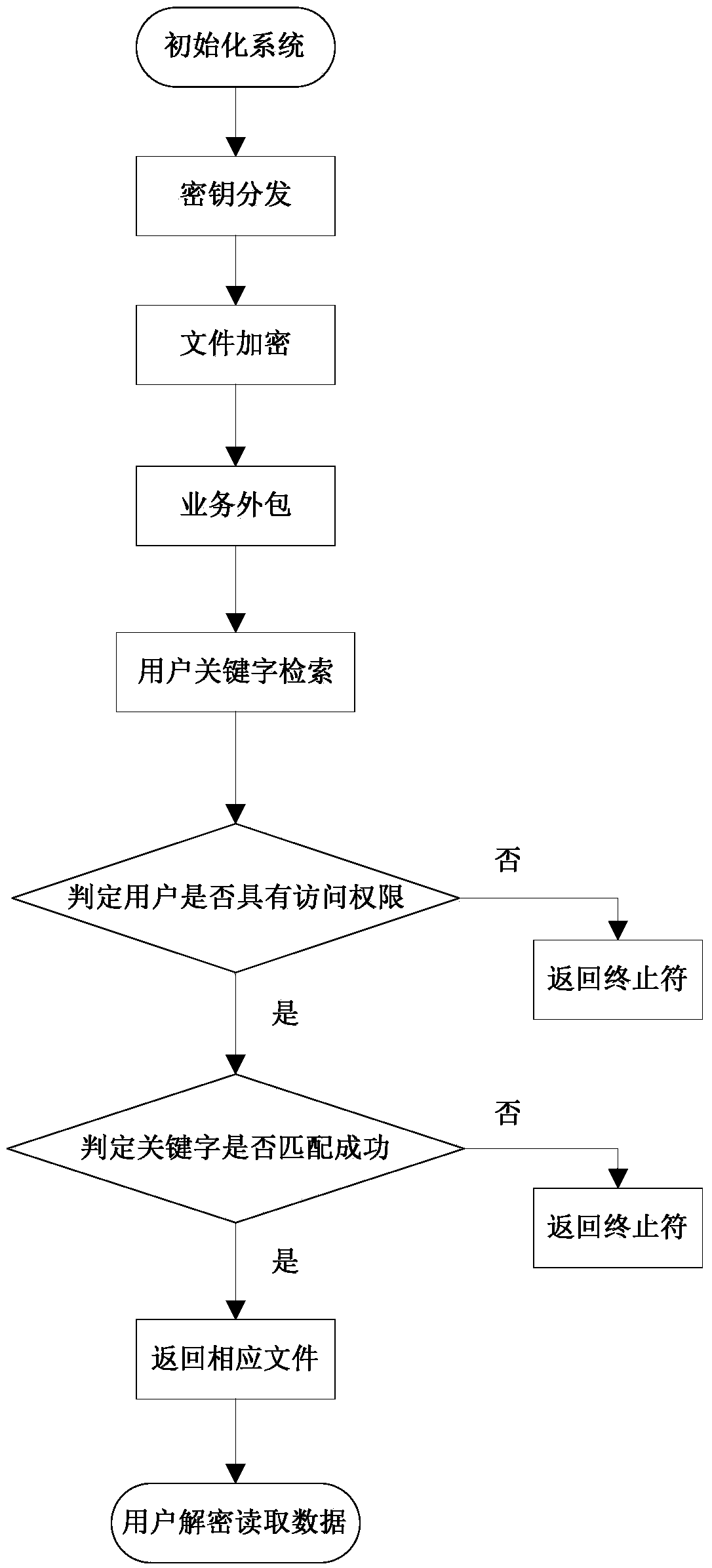
The invention discloses a multi-user supported searchable encryption system and method and accordingly the problem that specific encrypted files cannot be searched accurately in the prior art is mainly solved. The multi-user supported searchable encryption system comprises a credible authorization center TA, service providers and users; the credible authorization center TA is formed by a system initialization module, a secret key generation and management module and a user information management module; the service providers comprise a file server and a management server; the users comprise data providers and data receivers. The multi-user supported searchable encryption method comprises the steps of system initialization, secret key distribution, file encryption, business outsourcing, file retrieval, user decryption and user logout and adding. According to the multi-user supported searchable encryption system and method, the file retrieval time of the users is shortened due to the establishment of a key word index on files, the storage and computational overhead of the users is reduced due to the accurate file retrieval, the file retrieval is accurate, meanwhile the forward and backward security of the files is ensured, and meanwhile the multi-user simultaneous decryption is supported.
Owner:西安电子科技大学昆山创新研究院 +1
Secure certificateless hybrid signcryption method without pairing
InactiveCN105024994AResistant to Substitution AttacksImprove security levelPublic key for secure communicationPlaintextSigncryption
The invention discloses a secure certificateless hybrid signcryption method without pairing. The method is used for solving a technical problem of low efficiency of a conventional certificateless hybrid signcryption method. The method is characterized by a KGC is restricted by a user part public key in a stage of generating a part secret key by prescribing a fixed secret key generation sequence of a user so as to bind the user part public key when a signcryption user performs signcryption on a plaintext and guarantee enough resistance to public key replacing attack; before a user complete private key is generated, using a part private key bound with user identity information and a part public key to verify an equality in order that the user timely detects an invalid behavior of the active dishonest KGC, resists to malicious KGC attack, improves a system security level, and eliminates unnecessary computation consumption; in a unsigncryption stage, substituting scalar multiply operation on a elliptical curve to for expensive time-consuming bilinear pairings to complete message signcryption and unsigncryption processes, thereby improving computation efficiency.
Owner:东莞市三航军民融合创新研究院
Light-weight authentication key negotiation method based on implicit certificate
ActiveCN106411528ACalculation speedReduce the probability of collisionKey distribution for secure communicationPublic key for secure communicationClient-sideSecure channel
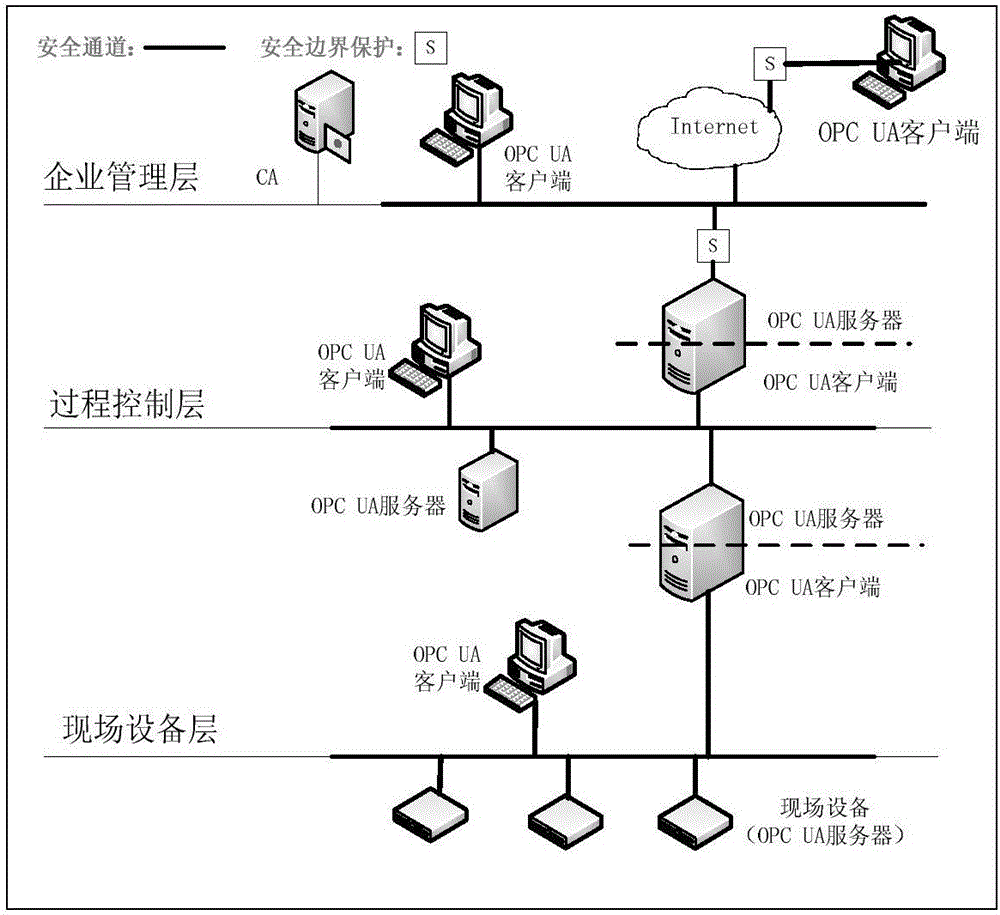
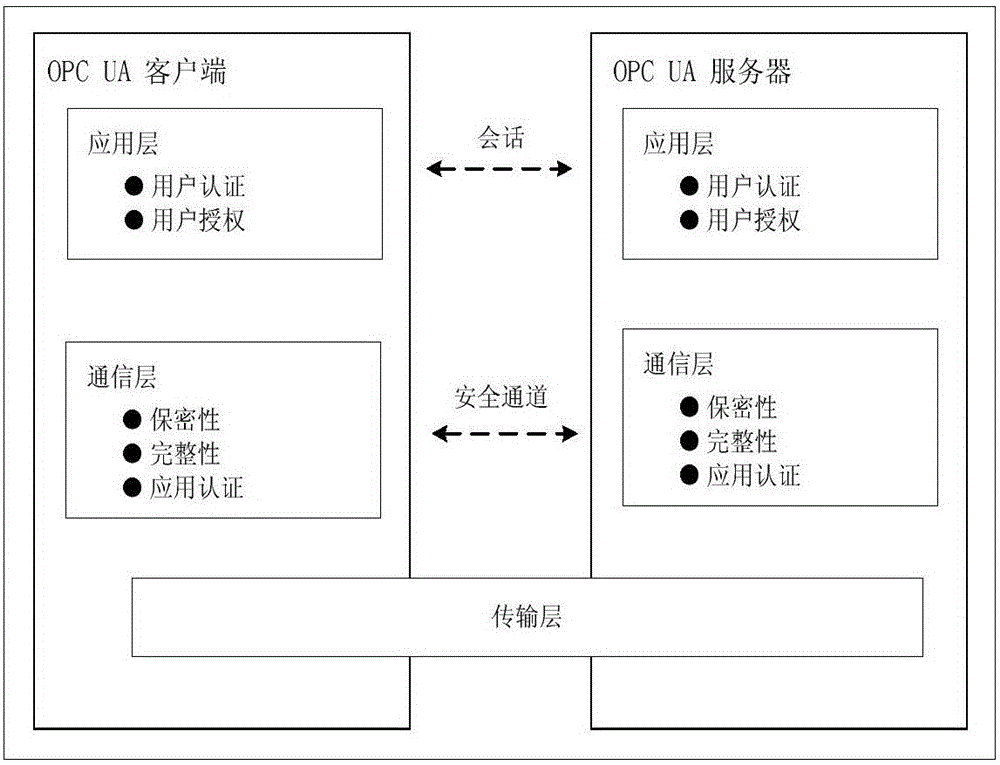
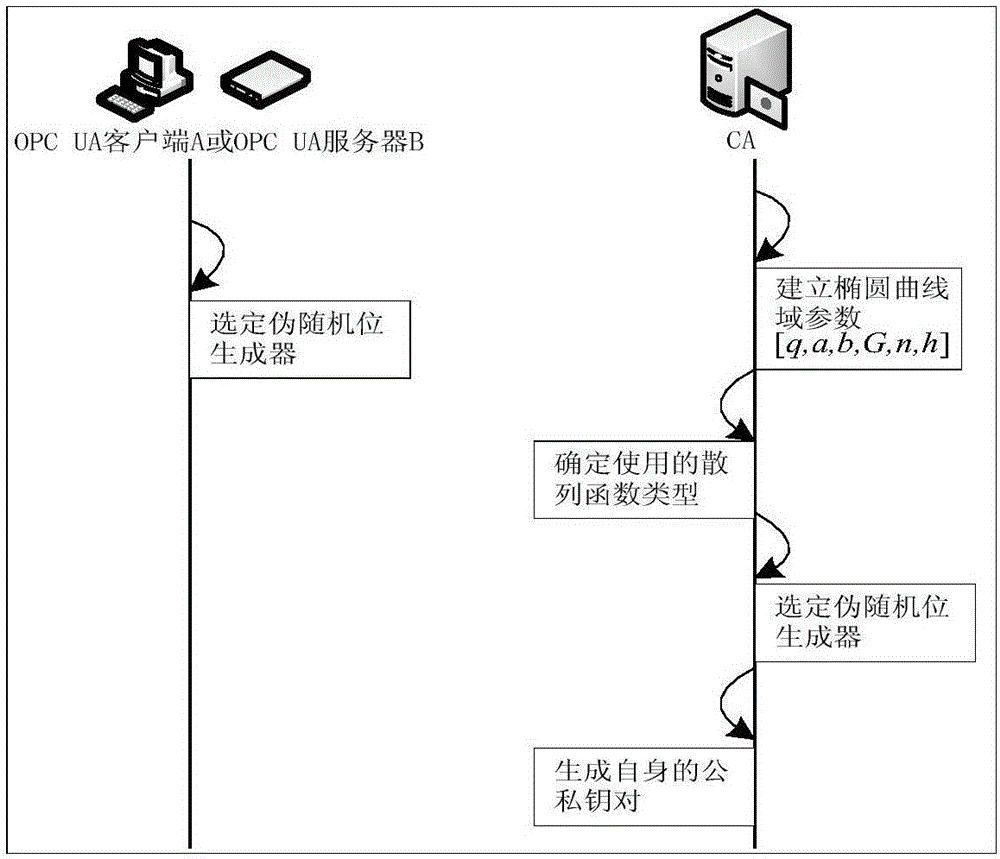
The invention relates to a light-weight authentication key negotiation method based on an implicit certificate, and belongs to the technical field of identity authentication. The method is used for establishing a secure channel between an OPC UA server and an OPC UA client and generating of a session key. Three entities, a credible certification authority (CA), the OPC UA client A and the OPC UA server B, are involved in an authentication key negotiation process. The OPC UA server B and the OPC UA client A acquire the own implicit certificates after the CA completes identity registration. Then the OPC UA server B and the OPC UA client A complete bidirectional authentication and key negotiation between the entities by using a light-weight algorithm. According to the method provided by the invention, the light-weight authentication key negotiation method based on the implicit certificate is provided aiming at the problem that an existing OPC UA security mechanism is not applicable to a resource-constrained communication environment. The method provided by the invention can be efficiently and safely applicable to an industrial network with a large amount of resource-constrained embedded OPC UA equipment.
Owner:KYLAND TECH CO LTD
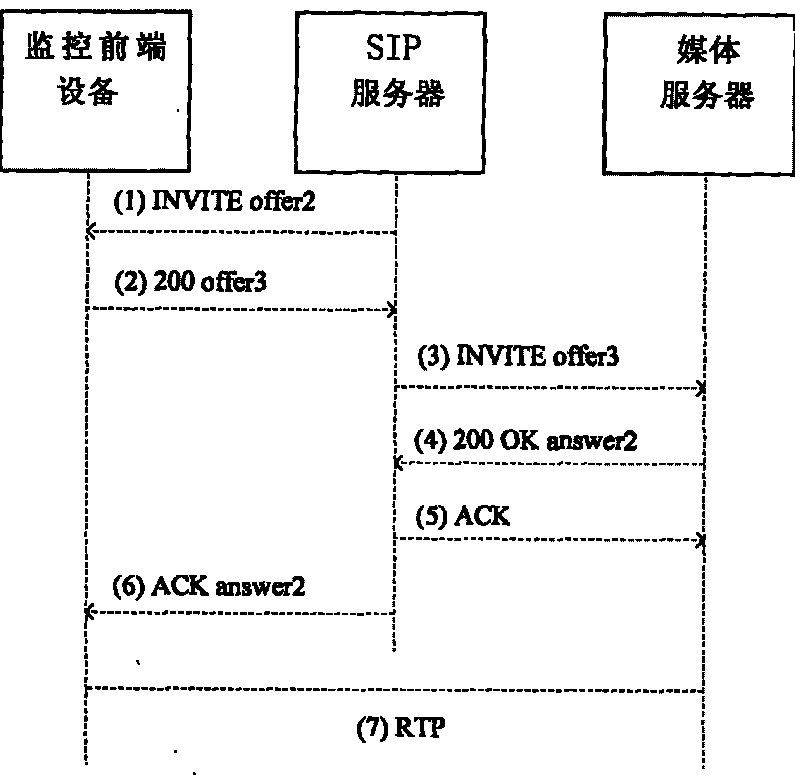
Method for distributing code stream encrypting and decrypting keys in SIP video monitoring system
ActiveCN101729854AEliminate security risksImprove securityKey distribution for secure communicationUser identity/authority verificationVideo monitoringMedia server
The invention discloses a method for distributing code stream encrypting and decrypting keys in an SIP video monitoring system. In the method, in a process for calling a 3 pcc between code stream encrypting monitoring front end equipment and code stream decrypting customer premise equipment, or a process of calling a 3 pcc between the code stream encrypting monitoring front end equipment and a media server and a 3 pcc between code stream decrypting customer premise equipment and the media server, seeda, seedb and seedc, which are obtained by the monitoring front end equipment, the media server and the customer premise equipment in an identity authentication process during registration, are used as keys shared with an SIP server and identifiers, the content of an SIP signaling message bodySDP is expanded to carry the encrypting and decrypting keys, and a symmetric algorithm or asymmetric algorithm is used to guarantee the safety of the transmission of the encrypting and decrypting keys. The method has the advantages of generating different keys at each time of broadcasting, greatly improving safety coefficient, resisting replay attack and eliminating the safety hazards of the storage of the keys at multiple places.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
Method for mutual authentication of user identities based on elliptic curve passwords
ActiveCN104639329AReduce verification timesReduce storage overheadPublic key for secure communicationUser identity/authority verificationInteraction timeMan-in-the-middle attack
The invention relates to a method for mutual authentication of user identities based on elliptic curve passwords. The characteristics of storage capability, calculation capability and limited bandwidth of an Ad Hoc network are considered, and a self-authentication public key system and the intractability of an elliptic curve discrete logarithm problem are utilized, so as to reduce the interaction times of the user identity authentication process, and accelerate the authentication speed. The method comprises the following steps of system initializing, user registering, and mutual authentication of the user identities. The method has the advantages that while the mutual authentication of the user identities is guaranteed, the function of session key negotiation is realized, the storage expense, communication expense and calculation expense are all less, the replay attack, man-in-the-middle attack, counterfeiting and tampering attack, and key disclosure counterfeiting attack can be resisted, a generated one-time session key has the advancing security and backward security, and the security is higher.
Owner:ZHEJIANG UNIV
Repeating data deleting system and method applicable to cloud storage
The invention discloses a repeating data deleting system and method applicable to cloud storage. The repeating data deleting system is based on strategies, a security agent and a random storage mechanism are adopted, a storage service is separated from a security service, the space utilization rate of cloud storage is improved, bandwidth occupation of redundant data is reduced, and security of user data and privacies is improved at the same time. The system is mainly composed of a client, the security agent and the cloud storage, wherein the security agent is the most secure core and is mainly used for ensuring the security of the user data and privacies. The repeating data deleting system and method applicable to cloud storage have the advantages of being high in security, system efficiency, bandwidth utilization rate and the like, and can resist replay attack, impersonation attack and security threats brought by partially trusted cloud storage providers.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for monitoring and analyzing own health status of wireless sensor network
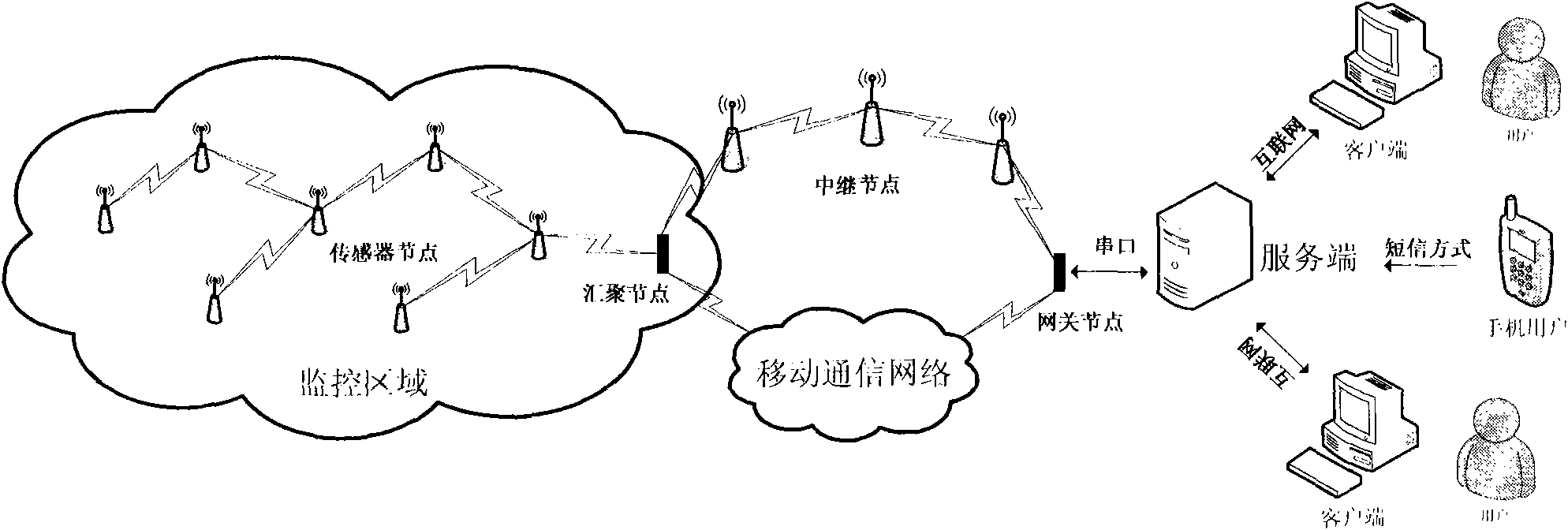
InactiveCN101808353AReduce threat levelDefense against replay attacksNetwork topologiesLine sensorWireless mesh network
The invention relates to a method for monitoring and analyzing the own health status of a wireless sensor network. The method comprises the steps: A, allocating 50 sensor nodes and 1 convergence node in a monitoring region; B, storing, and then transmitting to clients through the internet in a multicast mode; and C, analyzing the own health status of the wireless sensor network. In addition, commands can also be sent to each node through a server by using the clients and mobile telephones to adjust the status of the network. The invention has the advantage that the server can obtain various status information of the remotely-monitored region through a mobile communication network or trunk nodes, and simultaneously transmit the status information to multiple clients through the internet in the multicast mode after the analysis and storage processing, and therefore, users can observe the own health status information of the current wireless sensor network after the status information is visualized through the clients.
Owner:NANCHANG HANGKONG UNIVERSITY
Multi-factor identity authentication method and system
ActiveCN104660605AEasy to useDefense against replay attacksUser identity/authority verificationValidation methodsClient-side
The invention discloses a multi-factor identity authentication method and system. The multi-factor identity authentication method comprises a registration phase and an authentication phase, wherein in the registration phase, a current user is set as C, and registration is performed through a user login name and a login password; the authentication phase comprises bidirectional authentication and login association of a client and a server side: the server side verifies client information in combination of a random number and hardware fingerprint, the client verifies the server side through a public key returned by a server during registration, and the server side performs login association of current login and next login. The non-hardware multi-factor identity authentication method can meet the requirements for identity authentication and information safety, integrity and non-repudiation during login of the identity authentication system; hardware equipment is not required, and the method is convenient to implement.
Owner:BEIJING ANPRO INFORMATION TECH
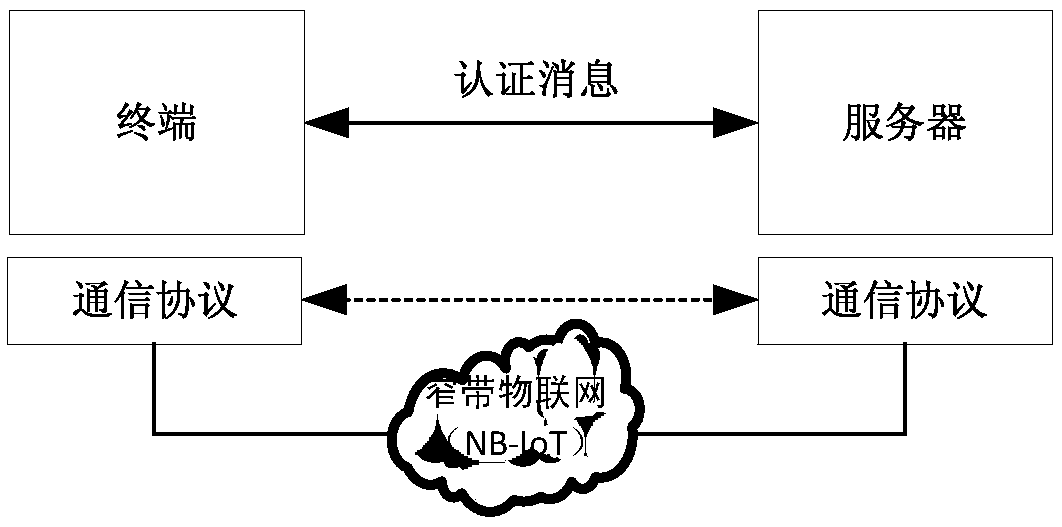
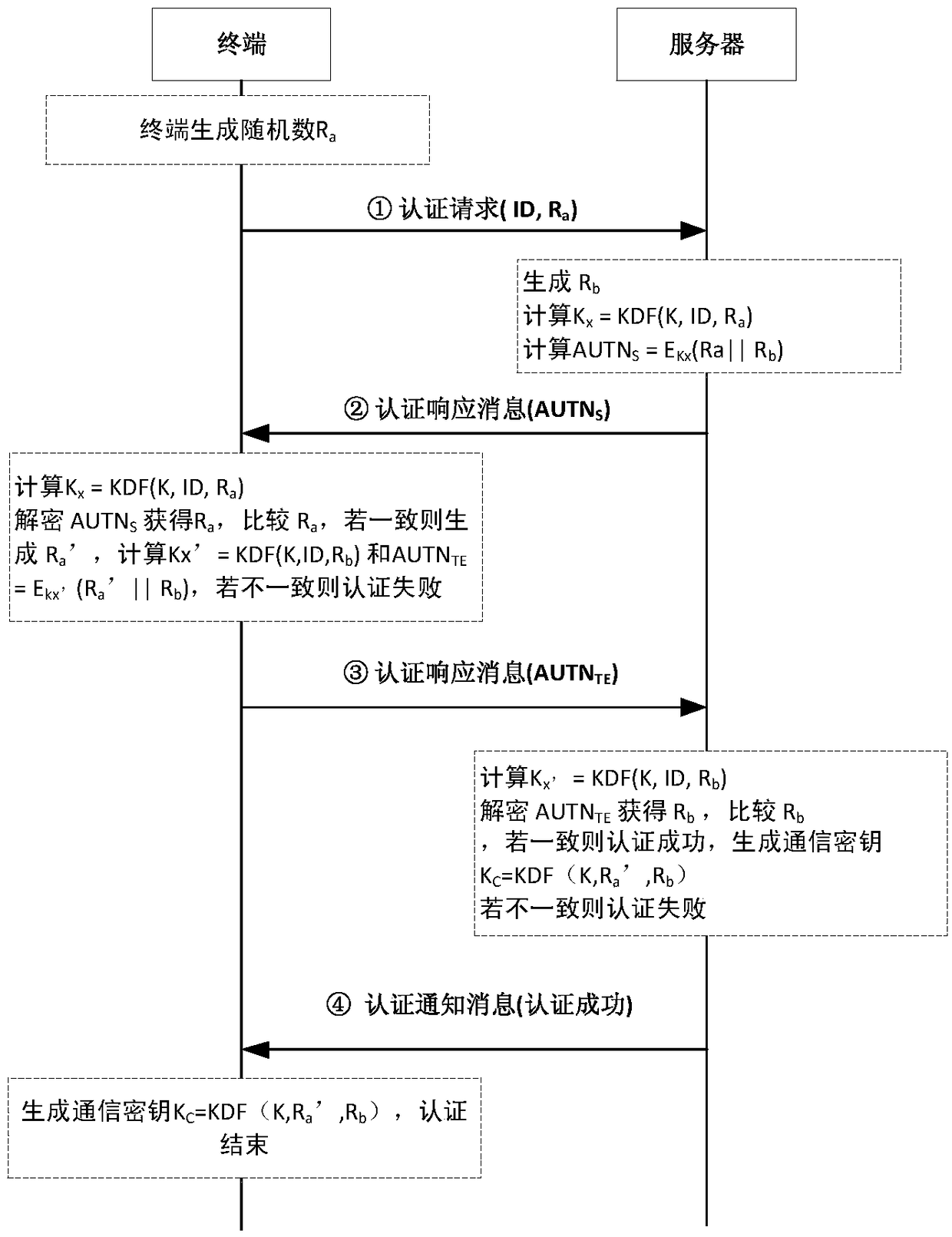
A lightweight secure authentication and key exchange method for narrowband Internet of things
ActiveCN108989318AAvoid risk of leakageReduce Interaction ComplexityTransmissionKey exchangeThe Internet
The invention discloses a lightweight security authentication and key exchange method for narrow-band internet of things. The communication main body comprises a terminal and a server. Before the communication is established, the root key is shared between the terminal and the server, and the two-way authentication is realized by adopting a challenge-response interaction mechanism based on a symmetric cryptosystem. The present invention mainly solves the problem of the two-way identity authentication and key exchange between the terminal and server in the Internet of Things application systembased on NB-IoT and other narrow-band Internet of Things connection technologies, can realize lightweight security authentication algorithm, protocol and key agreement mechanism, and meet the design requirements of low power consumption, low bandwidth consumption, low interaction frequency and high security.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
RFID (radio frequency identification device) authentication method and system based on PUFs (physical unclonable functions)
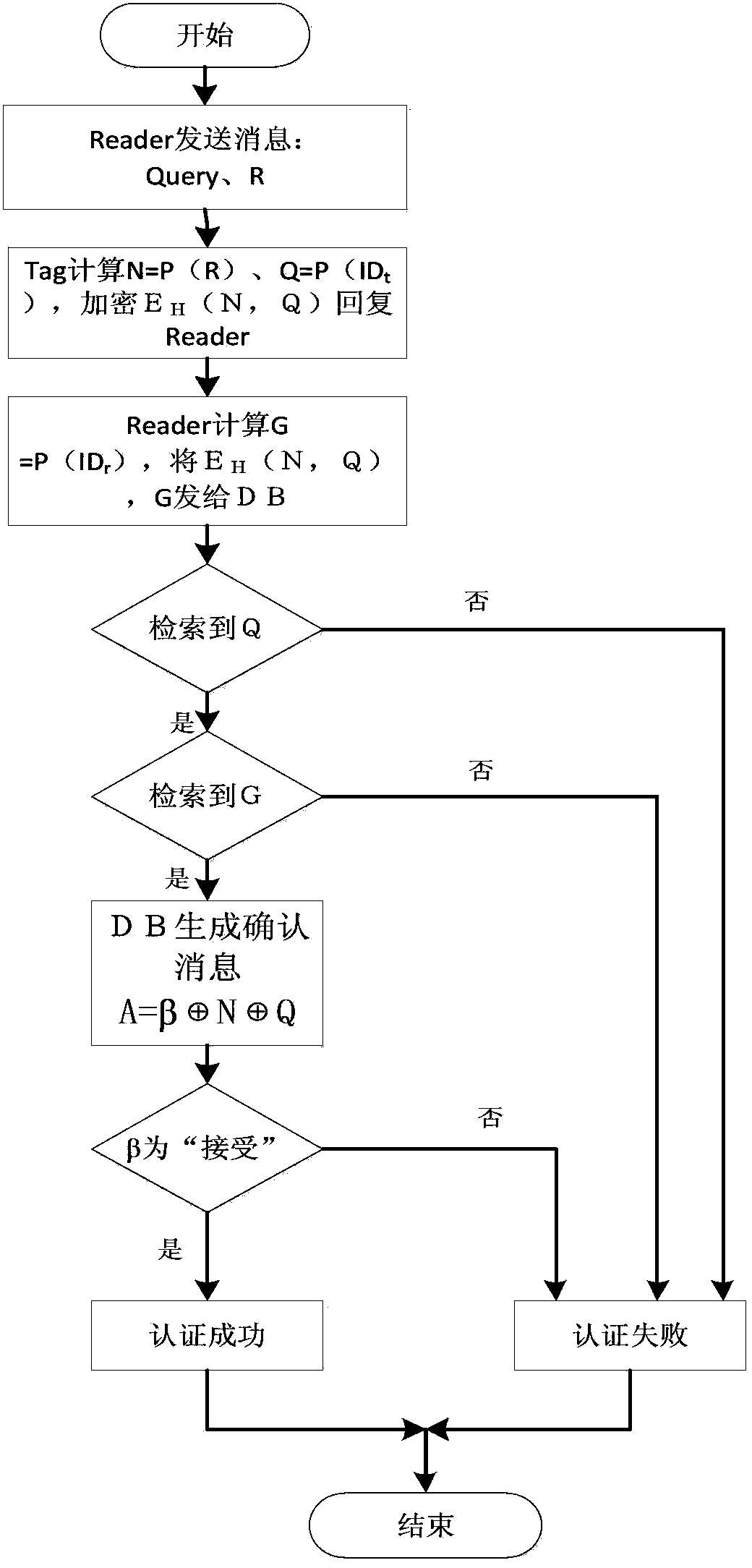
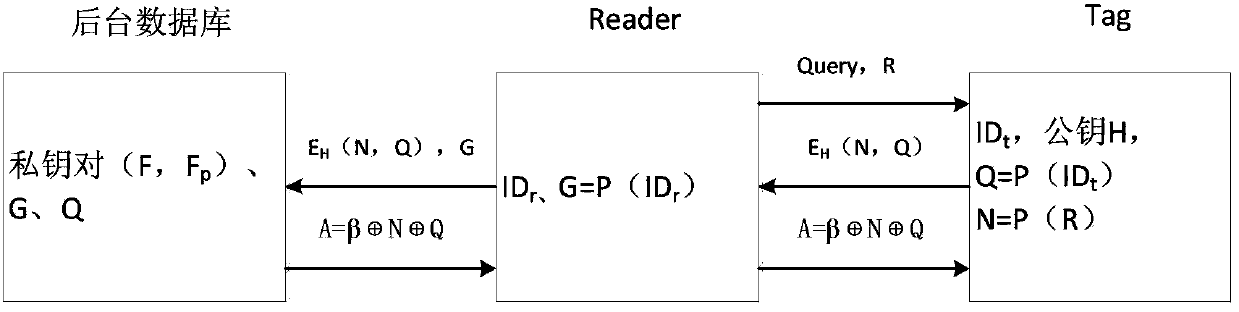
ActiveCN103391199ADefense against replay attacksResist impersonation attacksUser identity/authority verificationCo-operative working arrangementsRfid authenticationResource consumption
The invention discloses an RFID authentication method and system based on PUFs. The system comprises a backend database, a reader and a tag, wherein communication between the backend database and the reader can be realized by using a conventional network security technology, so that the communication between the backend database and the reader is safe; however, the communication between the reader and the tag is not realized through the conventional network security technology, so that the communication is not safe. The RFID authentication method has the advantages of high safety and authentication efficiency, little in resource consumption and the like, can resist typical attack techniques such as replay attacks, counterfeit attacks, track attacks, physical attacks and the like, has forward safety and backward safety, and realizes bidirectional authentication between the reader and the tag. A public key encryption method is used, so that the RFID authentication method has higher safety.
Owner:NANJING UNIV OF POSTS & TELECOMM
Physical unclonability-based RFID lightweight class authentication method
InactiveCN104112106ALow costTaking into account the costSensing record carriersComputer hardwareImpersonation attack
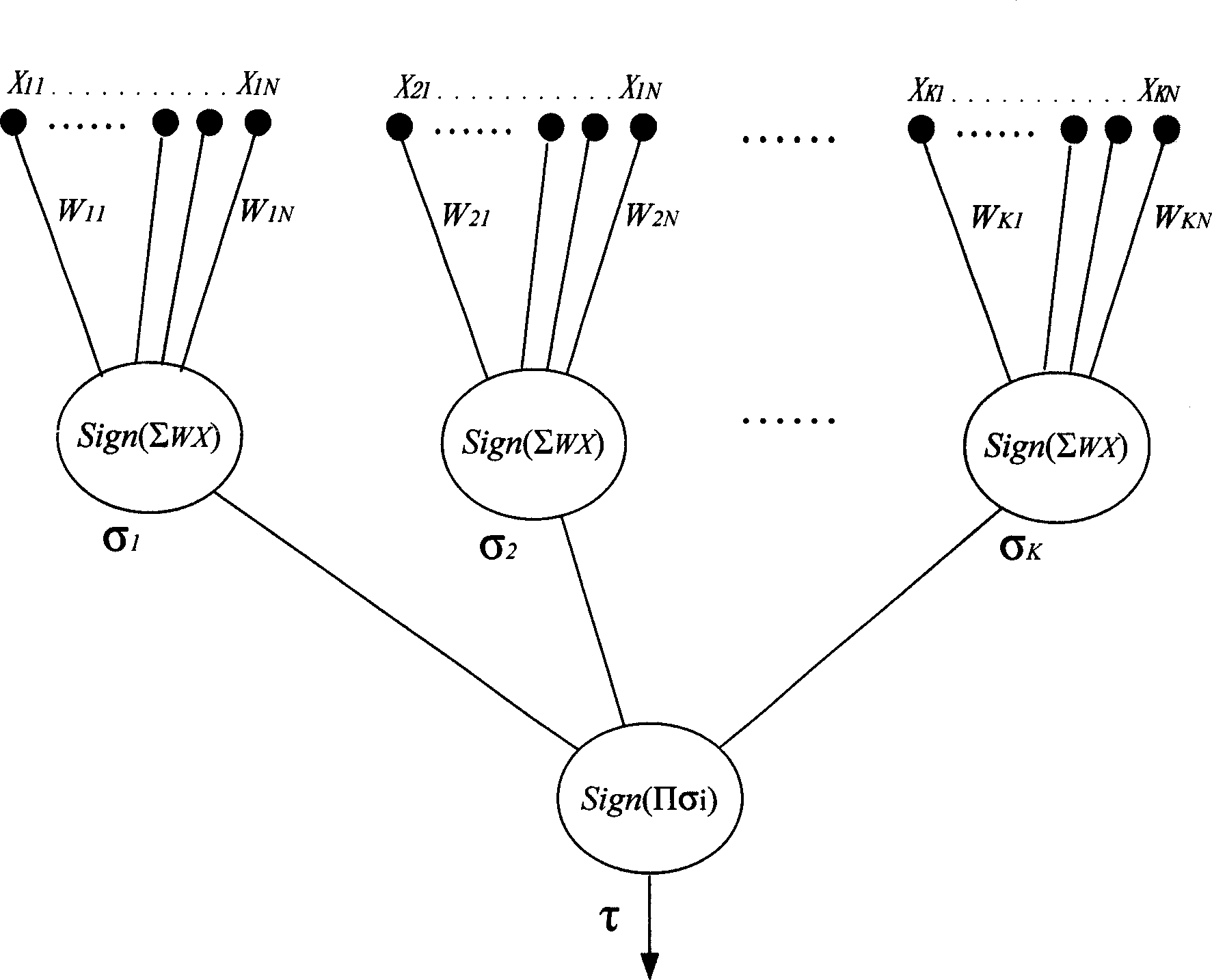
The invention discloses a physical unclonability-based RFID lightweight class authentication method, uses a PUF, a linear feedback shift register (LFSR), and XOR operation to perform processing, a label has small hardware requirements, cost is relatively low, the operation amount is small, and the method is resistant to various attacks including replay attack, impersonation attack, message stop attack, synchronization attack, wiretapping attack, physical attack, and label cloning, thereby effectively realizing forward security, and protecting privacy of a user. At the same time, through bidirectional authentication between a label and a reader, balance between efficiency and security is realized, hardware cost is well given consideration to, and thus the method is suitable for use of lowcost labels, and has relatively large practicability.
Owner:GUANGZHOU ZHONGCHANG KANGDA INFORMATION TECH +1
Safety authentication method of webpage and apparatus thereof
ActiveCN107295011AImprove securityDefense against replay attacksEncryption apparatus with shift registers/memoriesUser identity/authority verificationObjective informationPassword
The invention provides a safety authentication method of a webpage and an apparatus thereof. The method comprises the following steps of generating a random number according to a service request sent by a user terminal; sending the random number to the user terminal so that the user terminal carries out Hash encryption on the random number, a server address and a password input by a user, and acquiring target information; determining whether the target information and a user name input by the user accord with a service authentication condition; and if the target information and the user name input accord with the service authentication condition, passing authentication of the service request. In the safety authentication method of the webpage of the invention, when the hash encryption is performed, the hash encryption is performed on the random number, the server address and the password. Because of existence of the random number, encryption objects are different each time so that the target information acquired through encryption each time is also different. Therefore, the target information is safe in a transmission process, replay attacks can be effectively prevented, safety of webpage authentication is increased, and technical problems that traditional webpage authentication safety is poor and a hidden trouble of the replay attacks exists are alleviated.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method for preventing location cheating for iBeacon and authentication server, base station
ActiveCN104219244ADefense against replay attacksAvoid location spoofingTransmissionMajor and minorUser identifier
The invention discloses a method for preventing location cheating for iBeacon, and the method comprises the steps as follows: sending the current dynamic random number, Major initial value and Minor initial value to the iBeacon base station by the authentication server; receiving and analyzing the notice frame data broadcasted by iBeacon base station and obtained by the mobile phone APP and sending the data message, obtains the Major, Minor of mobile phone APP and user ID, having the OR operation on the obtained Major, Minor and the current dynamic random number to obtain the correlative value of the Major and Minor; judging whether the correlative value of the Major and the initial value and the correlative value of the Minor and the initial value is equal; if yes, the authentication server sends the permission and user ID to the server, the mobile phone APP can obtain the application service of the application server. According to the present invention implementation case, and there is no need to modify the iBeacon protocol standard, the replay attack can be safely and effectively resisted for preventing location cheating for iBeacon.
Owner:SHENZHEN POWER SUPPLY BUREAU
Dynamic password safe login method
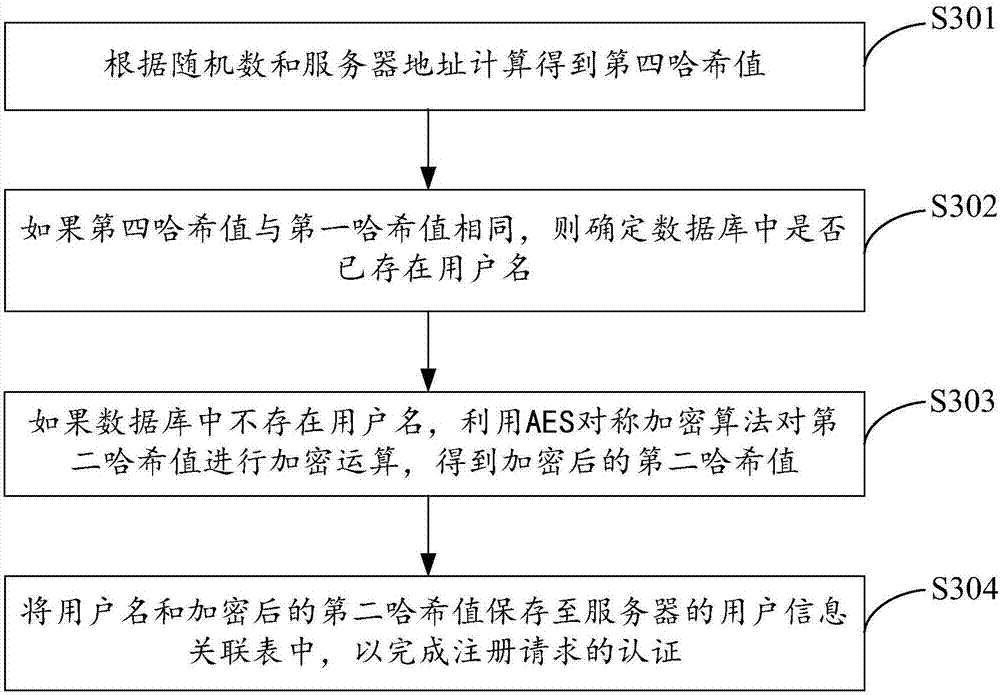
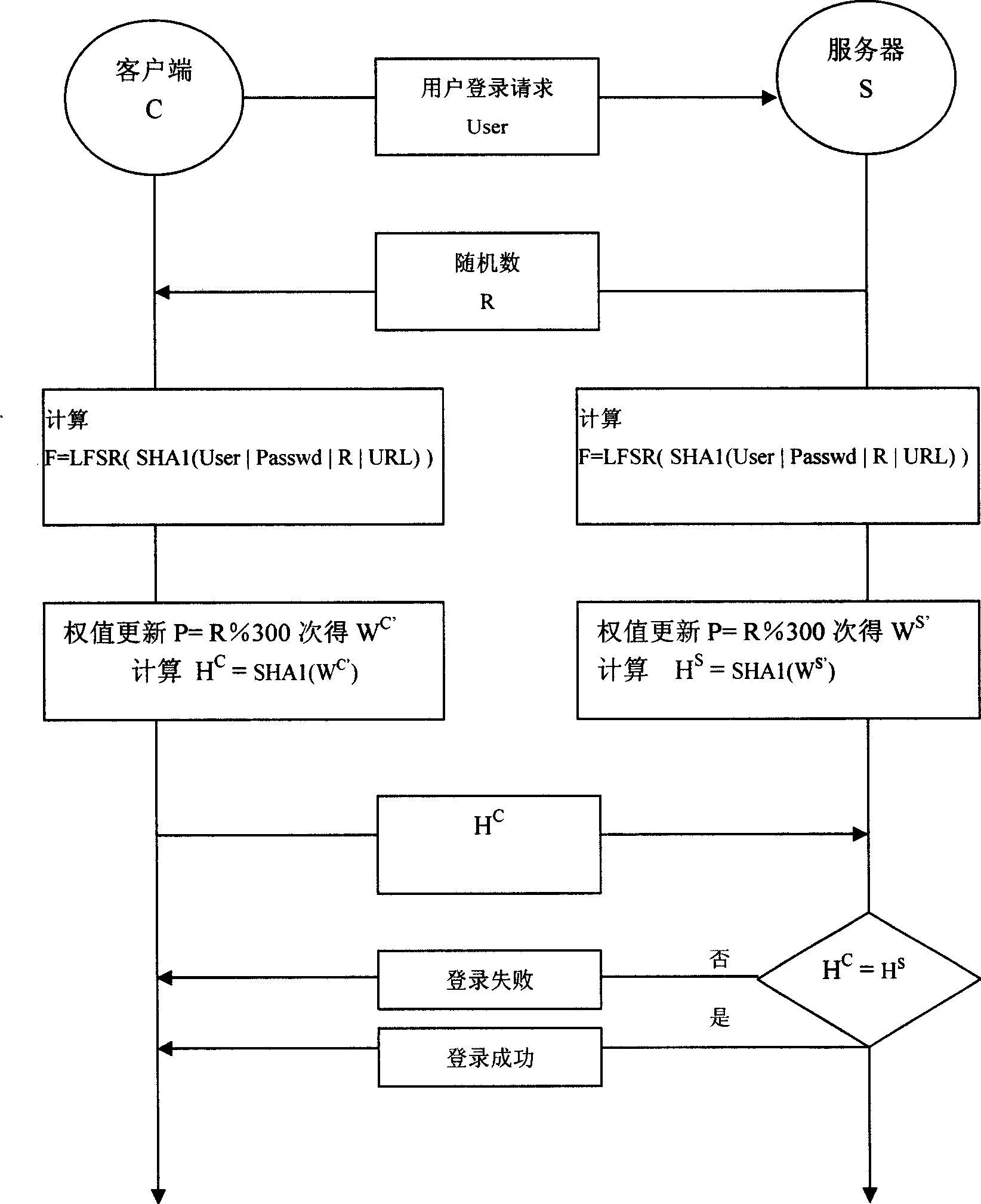
InactiveCN101459516AInnovative ideasGreat innovationUser identity/authority verificationPhysical realisationPasswordMapping algorithm
A dynamic password security login method is provided, which sets that a client and a server have weight synchronous models with the same parameters, and comprises the following steps: initiating a login request by the client, and sending a user name to the server, generating a random number by the server and returning to the client, obtaining that M=user 'Passwd' R, H=SHA1(M), F=LFSR (H) by respective calculations of the client and the server, obtaining the same weight WC=WS according to the mapping algorithm of a random number sequence F, leading the weight synchronous model to study P=%n order by the client according to the random number, wherein R is the random number, n is a preset value, sending the weight vector WC after updating P orders to the server after Hash algorithm SHA1(WC), and leading the weight synchronous model to study P orders by the server to obtain the weight vector WS after updating P orders, and calculating the Hash value SHA1 (WS) thereof, wherein the identification is success if the SHA1 (SC)=SHA1(WS), or is false. The dynamic password security login method has simple use, highly-effective security and low cost.
Owner:ZHEJIANG UNIV OF TECH
Lightweight authentication and key agreement protocol applicable to electric information acquisition
InactiveCN102882688AReduce the number of interactionsResistance to asynchronous attacksUser identity/authority verificationAttackKey-agreement protocol
The invention relates to a lightweight authentication and key agreement protocol applicable to electric information acquisition. An identify authentication stage is completed on the basis of communication of a digital certificate of an authentication center of a state grid cooperation of China and a shared key. In a key agreement stage, new and old parameter protection keys which are updated dynamically are utilized, and lightweight operators are utilized for computation, and the key agreement is completed by communication circulations only. In a key updating stage, a session key group and the new and old parameter protection keys are synchronized. During key agreement, parameters are protected alternatively by the new and old parameter protection keys so that nonsynchronous attack can be resisted effectively. The protocol can be analyzed by combination of BAN logic formal analysis and informal analysis methods, can be approved to have safety attributes such as two-way entity authentication, perfect forward security and the like when reaching first-level faith and second-level faith, resists to various attacks, and can complete identify authentication and key agreement in real time effectively on the premises of security guarantee and meet requirements of an electric information acquisition system to key application.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Phonetic telecommunication method for mobile self-organizing network
ActiveCN1585329AImprove reliabilityReduce broadcast stormsData switching by path configurationSecuring communicationNetwork connectionIp address
The method can remove the influence to the voice communication by changing address in mobile self-organized network. It includes following steps: at the stage of building network connection, through a handshake process the real current IP address in the goal node is obtained; a random number is shared by the both sides of communication to use in authentication and encryption in communication process; after completing connection and entering into calling, each side of communication must periodically transmit the message about encrypted address to another side for informing another side real IP address that is currently used by present side, with the method any change of address in current node will be informed another side in time.
Owner:PHICOMM (SHANGHAI) CO LTD
Wireless body area network security access method
ActiveCN104301888AEnable secure accessReduce communication delayShort range communication serviceSecurity arrangementHand shakesAccess method
The invention discloses a wireless body area network security access method. Two interaction modes, namely, the unicast mode and the multicast mode, are set; two launching modes are set, and in other words, a network coordinator launches hand shaking and sensor nodes launch hand shaking; thus, when a certain part is injured and the blood pressure suddenly rises or in other words, the measurement indexes of a certain or some sensor nodes exceed the corresponding index limitations, the corresponding sensor nodes actively launch the hand shaking process, the situations of patients are rapidly fed back to medical staff, and patients are helped in time. According to the method, dynamic negotiation of a user conversation key is achieved through enhanced four-step hand shaking, hand shaking information is reduced, all the information is encrypted, the unicast access mode and the multicast access mode are set, and the remote access problem is solved through a multi-hop method. The method has the advantages that the access efficiency of a large number of sensing nodes is high, security is high, and the energy consumption is low, and the method can be used for the access of the sensing nodes in a wireless body area network and the dynamic negotiation of the user conversation key.
Owner:XIDIAN UNIV
Digital certificate system applicable to the no/weak local storage client system
InactiveCN101035135AAchieve legal accessLocal storage is reliableUser identity/authority verificationRegistration authoritySimultaneity
Applying to no / weak local storage system client digital certificates system belong to a digital certificate system technology. Its features are: based on public key infrastructure architecture, containing certificates body system, a registered body system, certificate management systems, key management system, information dissemination and interface systems and procedures for client visit one or more of these components, adopted random number, salt and several rounds of iteration, etc to guarantee the security of the system and conducted by the client decryption key generation and processing operation means to achieve the system's scalability. The system without the help of key external storage devices solved the network computer systems deployed digital certificate system in the terminal when the entity's private key data storage needs of the local computer network and storage characteristics of contradictions. Thus in ensuring security and scalability simultaneity, the digital certificate system implementation complexity and costs are lower.
Owner:TSINGHUA UNIV
Three-party authenticated key agreement method for centralized mobile positioning system
ActiveCN111682938AShorten the lengthReduce operational complexityKey distribution for secure communicationPublic key for secure communicationMan-in-the-middle attackThird party
The invention discloses a three-party authenticated key agreement method for a centralized mobile positioning system, and the method comprises the steps: achieving the mutual authentication and key agreement among a communication entity client, a central server and a positioning terminal through the autonomous design of a self-owned certificate ECC three-party authenticated key agreement algorithm, and generating a safe session key; and by adopting an autonomously designed self-owned certificate registration algorithm, enabling the client, the central server and the positioning terminal to locally generate public and private key pairs and self-owned certificates. According to the method, participation of a key generation center and a certificate issuing mechanism is not needed, and the certificate management problem, the certificate authentication overhead problem and the third-party key trusteeship problem are solved; through adoption of an autonomously designed signature algorithm and an identity authentication algorithm, bidirectional authentication of a communication entity is realized, and man-in-the-middle attacks and replay attacks can be effectively resisted; according to the designed ECC three-party authenticated key agreement algorithm, a one-time pad effect is achieved by setting a security random number, and forward security is ensured.
Owner:SOUTHEAST UNIV +1
Method for generating and authenticating hidden video tags based on video characteristics and digital signatures
ActiveCN101977319ADefense against replay attacksImplement integrity verificationTelevision systemsTransmissionDigital signatureInformation security
The invention provides a method for generating and authenticating hidden video tags based on video characteristics and digital signatures, belonging to the technical field of information safety. In the method, a way for extracting and optimizing groups based on visual descriptors is used to generate video characteristics serving as one part of the tags, thereby realizing binding of the tags and the video, and effectively resisting conspiracy attack behaviors of attackers to authorized tags. The hidden tags constructed by the method have not only preferably robustness and safety, but also integrity and non-repudiation which are not endowed to the common video watermarks, as well as unique binding of the tags and the video and the like.
Owner:SHANGHAI JIAO TONG UNIV
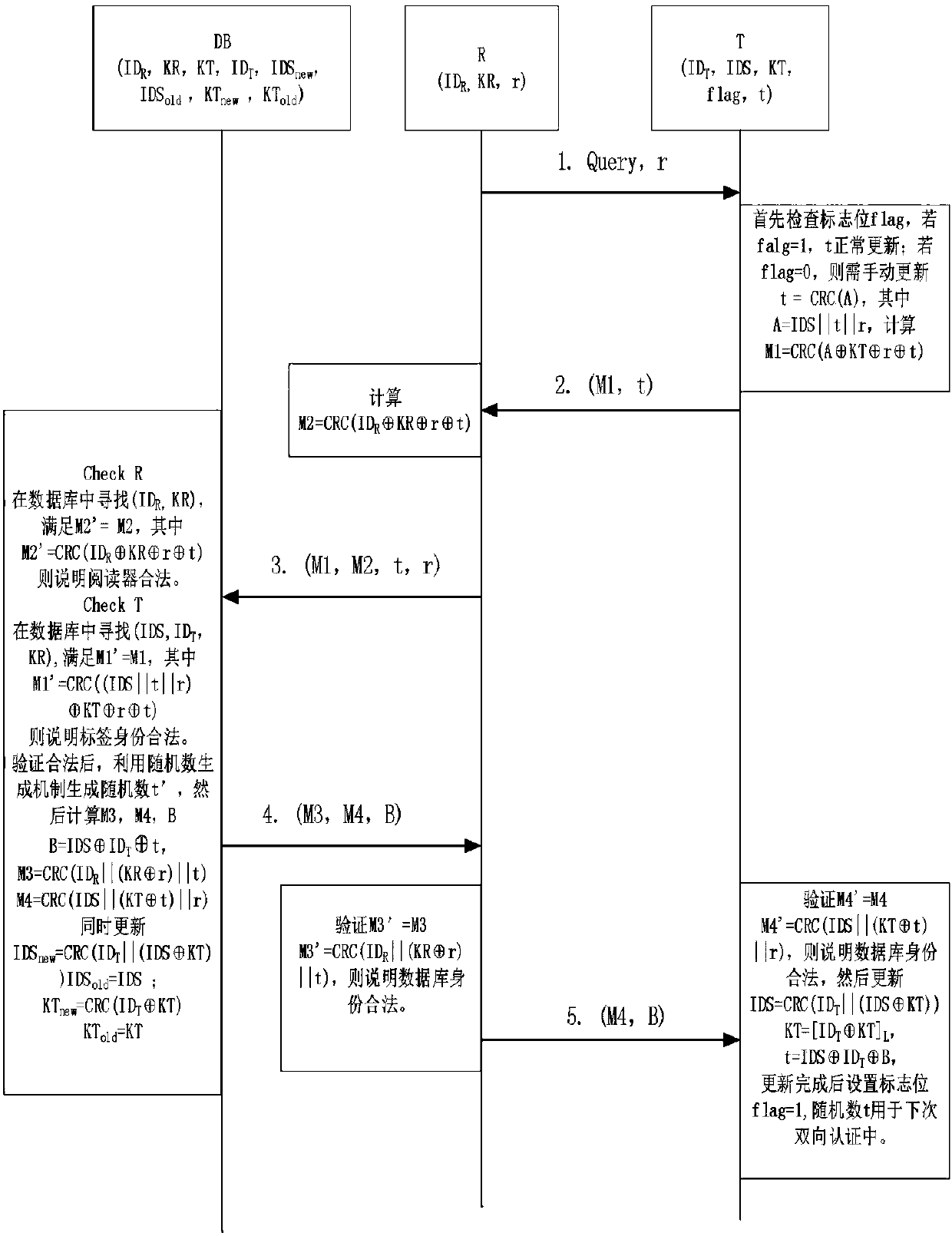
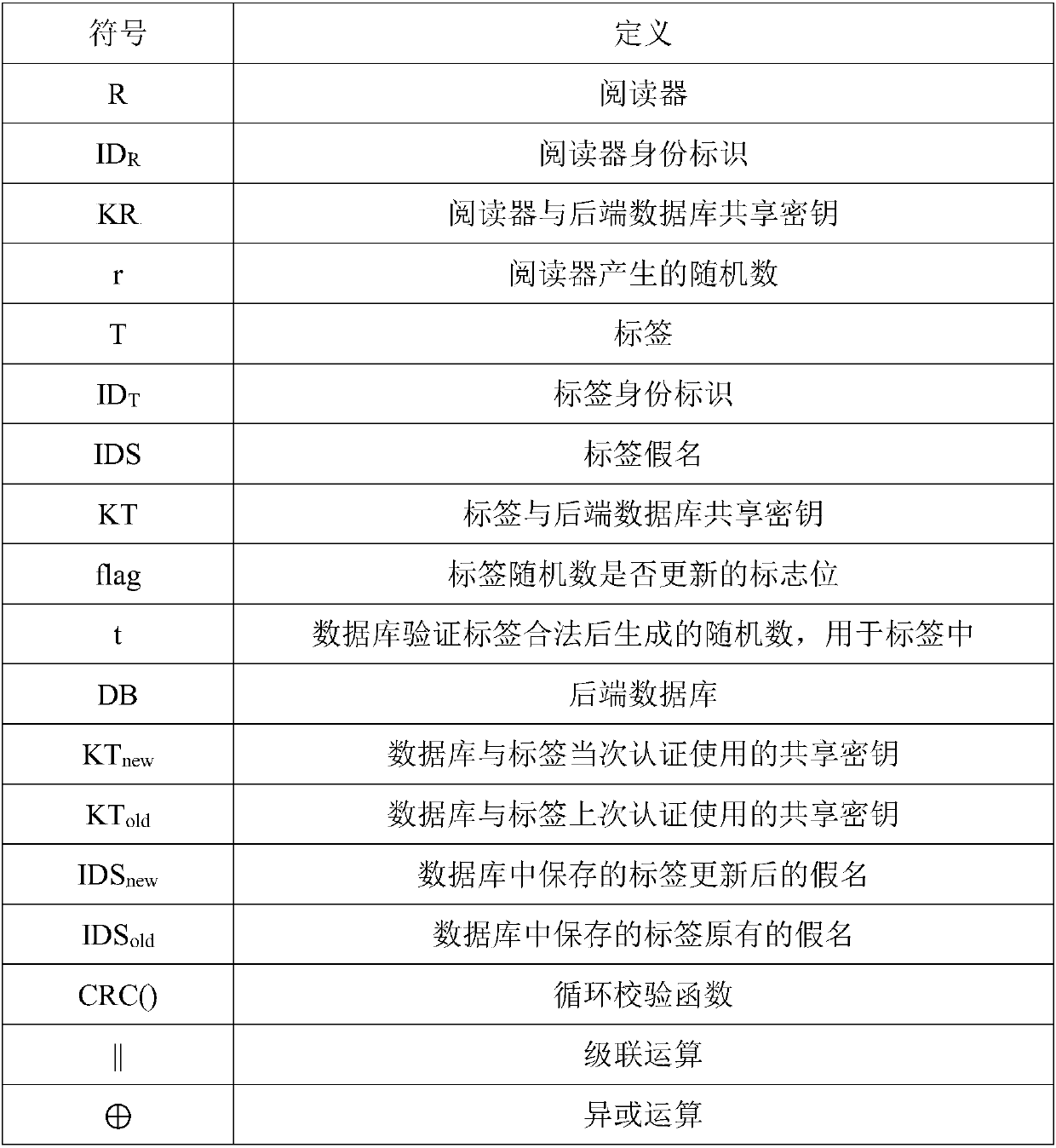
Bidirectional authentication method for ultra-lightweight mobile RFID system
ActiveCN108304902AReduce hardware costsSmall amount of calculationKey distribution for secure communicationCo-operative working arrangementsExclusive orSecure authentication
The invention relates to the technical field of communication, and particularly relates to the safety certification problem among a tag, a reader and a back-end database in a mobile RFID system. The method comprises the following steps: (1) the reader sends the request information to the tag; (2) the reader sends the tag response request information and the own information to the database; (3) thedatabase authenticates the reader and the tag; (4) the reader authenticates the database; (5) the tag authenticates the database. According to the invention, the protocol of the system adopts a cyclic checking function and a simple exclusive-or and cascade algorithm to encrypt the to-be-transmitted information. In this way, the anonymity of the tag and the bidirectional authentication of the system are realized. Meanwhile, the calculation amount of the database and the tag is effectively reduced. A tag random number is generated by a back-end database random number generation mechanism and then is forwarded to the tag or automatically updated through the cyclic checking function. Therefore, the hardware cost of the tag is reduced. According to the invention, a dynamic ID and a cyclic checking function mechanism are utilized, so that the system can resist various attacks.
Owner:XIDIAN UNIV
Wireless network lightweight class authentication key negotiation protocol based on digital certificate
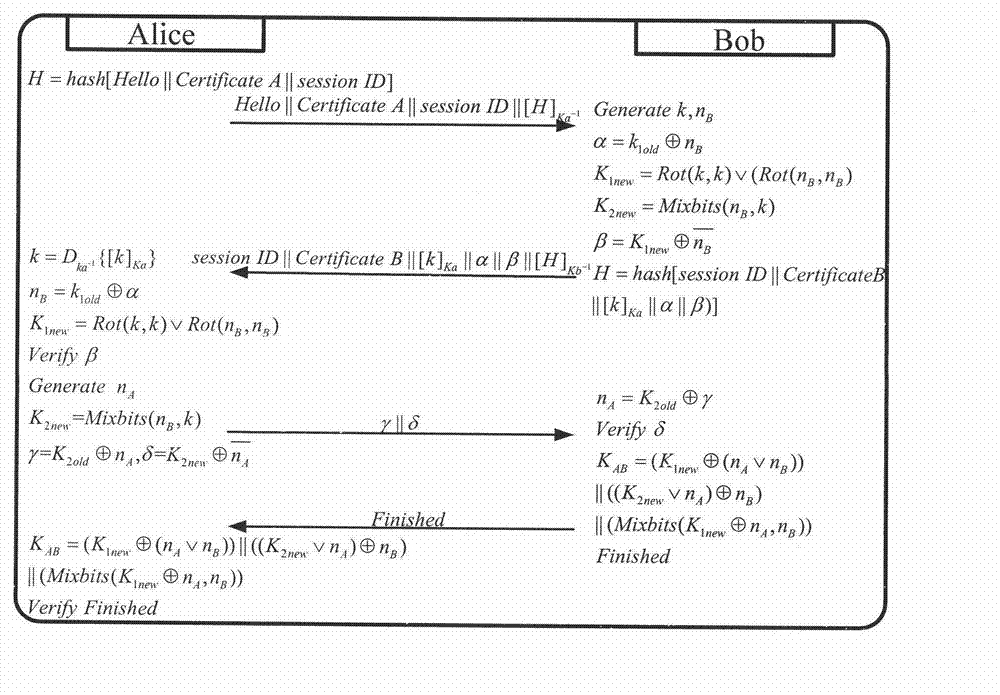
InactiveCN102833748AReduce the number of communicationsSmall amount of calculationSecurity arrangementKey-agreement protocolPassword
The invention relates to a wireless network lightweight class authentication key negotiation protocol based on a digital certificate. A user identity is subjected to dual authentication through a 'certificate private key and protection key' dual authentication system and a 'protection key' dynamic negotiation mechanism by sharing a dynamic protection key according to a public key password; a user proves the session holdness and the private key owning property by exchanging the certificate according to a private key signature, so that primary authentication is executed; and due to protection key sharing, secondary authentication is executed. Important parameters are protected by two parties through the protection key after the last session is finished; the correctness of the key is confirmed through a new protection key calculated at the session; during each communication, when the parameters are exchanged, the correctness can be checked. Negotiation for key groups and parameter exchange adopt simple bit computation; and the key updating is confirmed by Finished messages. According to the protocol, a dynamic ID is set to dynamically select whether the shared old parameters are used for calculating the key of the session; and safety and high efficiency are guaranteed, and the flexibility of the protocol is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Message processing method and system
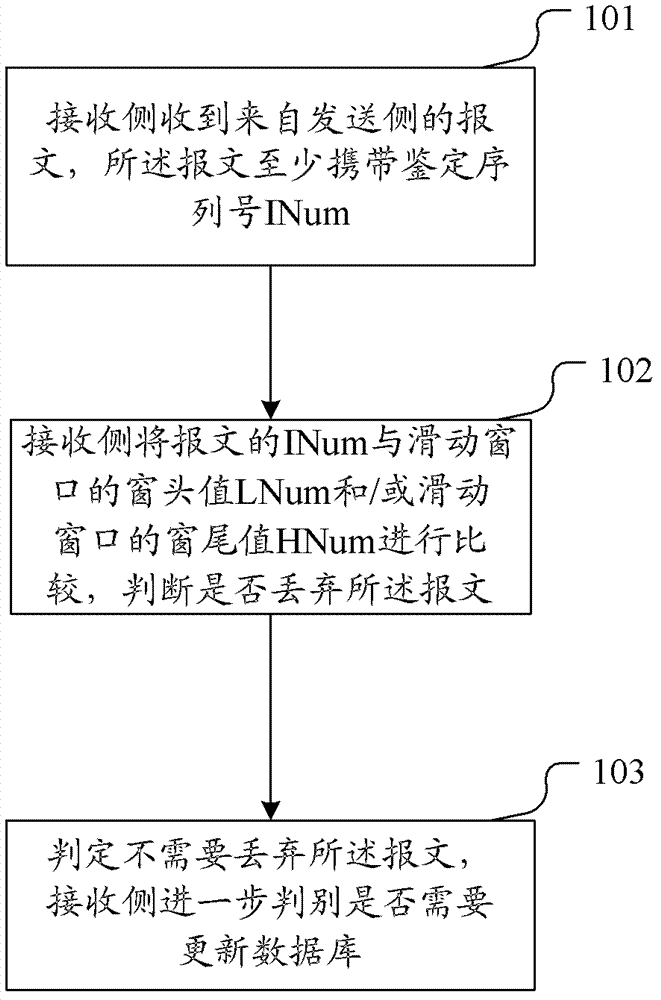
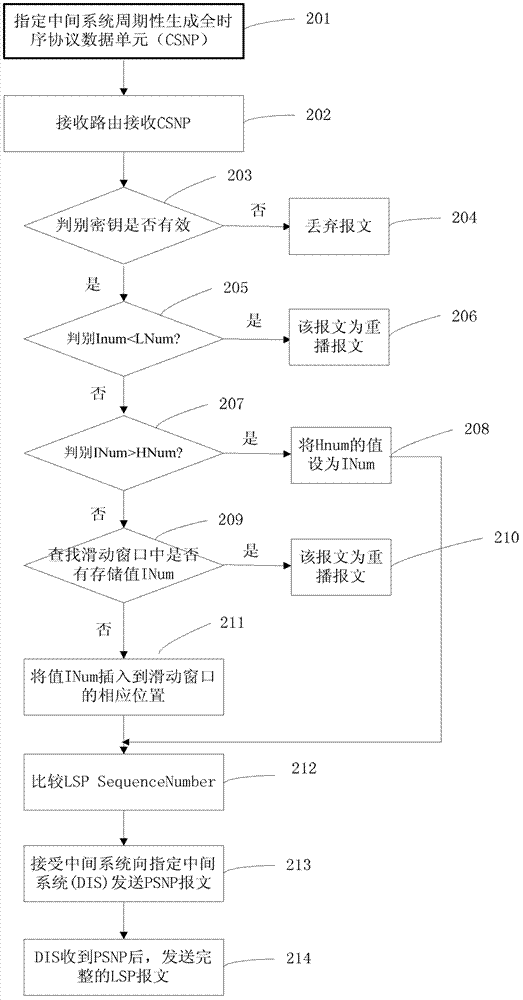
InactiveCN103095563AResistance to replay attacksGood processing effectData switching networksSlide windowTreatment system
The invention discloses a message processing method. The message processing method includes the following steps. A receiving side receives a message from a sending side. The message at least carries an identifying serial number INum. The INum of the message is compared with a window header value LNum and / or a window end value HNum of a sliding window by the receiving side and whether the message is supposed to be abandoned or not is judged. The invention correspondingly discloses a message processing system. With the message processing method and the message processing system, the sliding window slides based on the window header value (minimum value) and the size of the sliding window is not fixed so that replay attack can be effectively resisted, a good effect of processing a delayed message is achieved and safety and reliability of the system are enhanced.
Owner:ZTE CORP
Remote authentication protocol method based on password and intelligent card
ActiveCN104901809AEnhanced anonymityReach deliveryUser identity/authority verificationArray data structurePassword
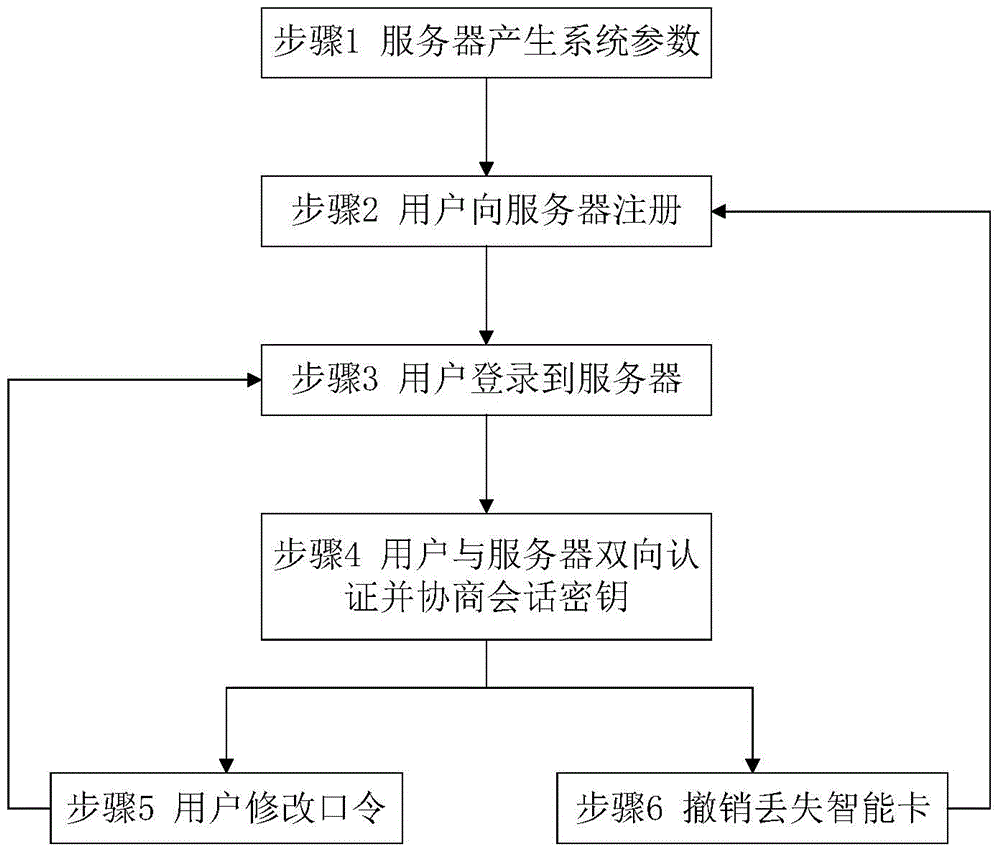
The invention provides a remote authentication protocol method based on password and an intelligent card, and belongs to the field of information safety. The protocol employs an optimized elliptical curve algorithm, a counting set and authentication codes are embedded, password can be modified, and the lost intelligent card can be canceled. The anonymity of a user is ensured, the method is safe and efficient, mutual authentication and negotiation of session key of the user are realized via twice interaction, and the method is suitable for remote authentication systems as e-cash, online education and remote medicine.
Owner:BEIHANG UNIV
Privacy protection-based crowd-sensing network truth value discovery method
ActiveCN109347829AGuaranteed privacyDefense against replay attacksEncryption apparatus with shift registers/memoriesUser identity/authority verificationSensing dataTruth value
The invention provides a privacy protection-based crowd-sensing network truth value discovery method, and belongs to the technical field of Internet of things crowd-sending. The privacy of a message is guaranteed by using an improved Paillier encryption algorithm during message transmission; the identity authentication of a user is guaranteed by using a one-way hash chain; and the high efficiencyof output is guaranteed by using a superlinear sequence. An identity authentication process can meet an authentication requirement of terminal equipment in a truth value discovery environment to resist an attack of an external attacker; a secure truth value discovery process can acquire real sensing data and guarantee the security and privacy protection of the whole system. Compared with a traditional method, the privacy protection-based crowd-sensing network truth value discovery method can protect the data and weight privacies of the user, greatly reduce the computation and bandwidth consumption of the terminal equipment and improve the efficiency and security of the whole system.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Multi-encryption based data transmission method
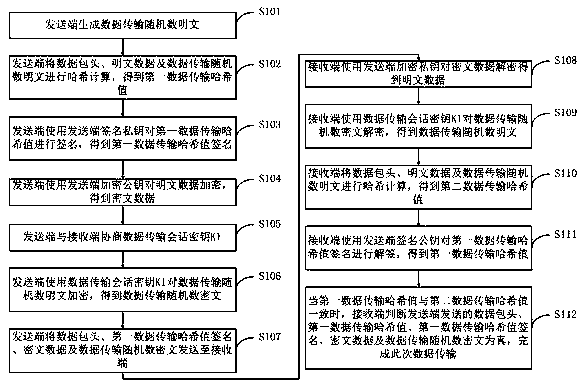
ActiveCN108683647AIntegrity guaranteedDefense against replay attacksUser identity/authority verificationData transmissionMultiple encryption
The present application discloses a multi-encryption based data transmission method. Compared with the prior art, the present application uses triple-hybrid encryption. When data is transmitted each time, plaintext data is encrypted by an asymmetric encryption method, and the data transmission random number plaintext is encrypted by a symmetric encryption method. A signature is added to the transmitted data. Once the signature is found to be inconsistent, it can be inferred that there is an illegal attacker, and random numbers generated each time are different from each other, and are doped inan encrypted message, so the attacker is difficult to determine the specific ciphertext length and a location of the specific encrypted message, and cracking and reuse cannot be achieved, thereby effectively resisting replay attacks and ensuring the confidentiality and authenticity of the data transmission. In addition, the present application also uses the hash value contrast method to ensure the integrity of the transmitted data.
Owner:CHONGQING JIAOTONG UNIVERSITY
Method and system for verifying source address
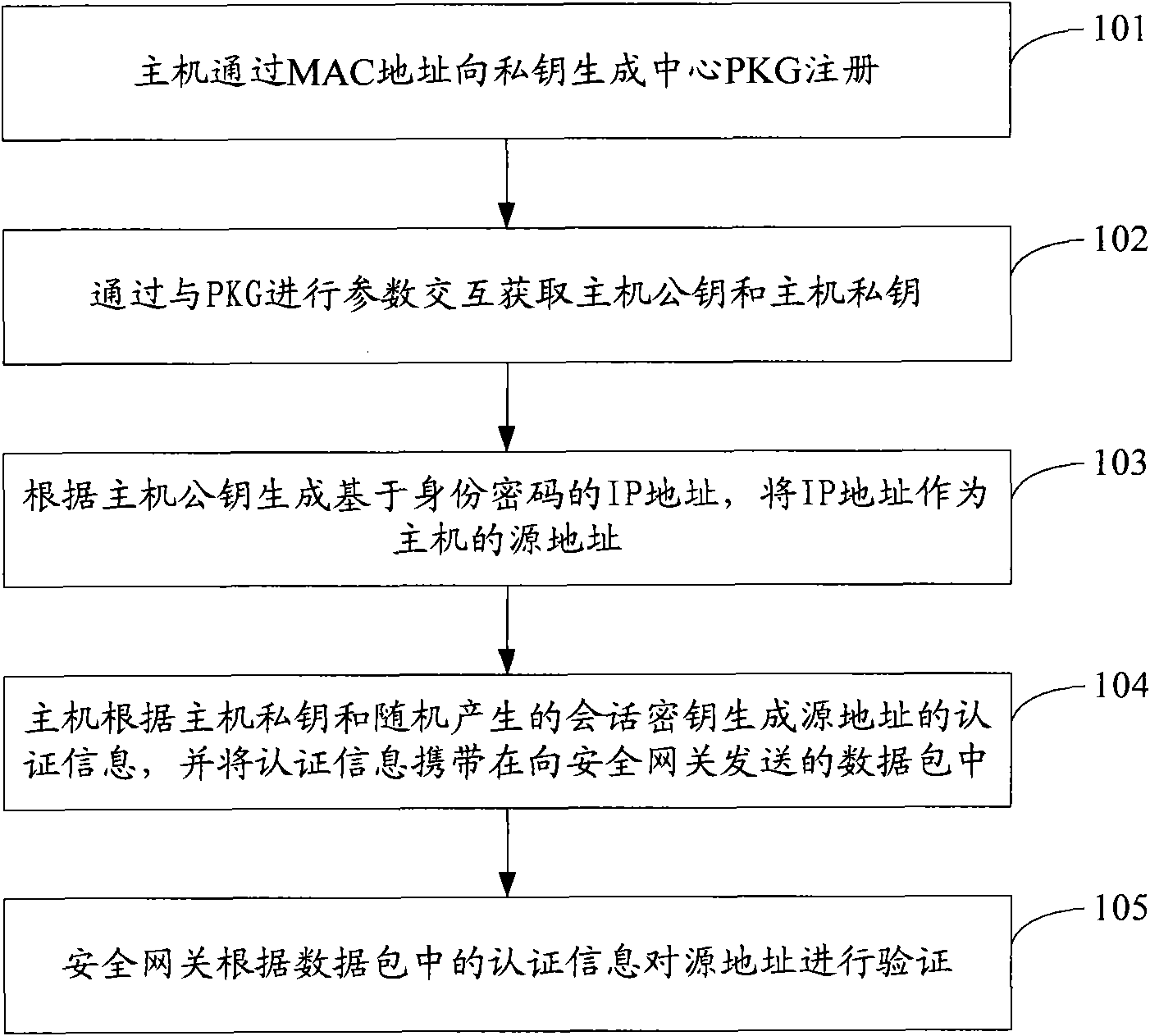
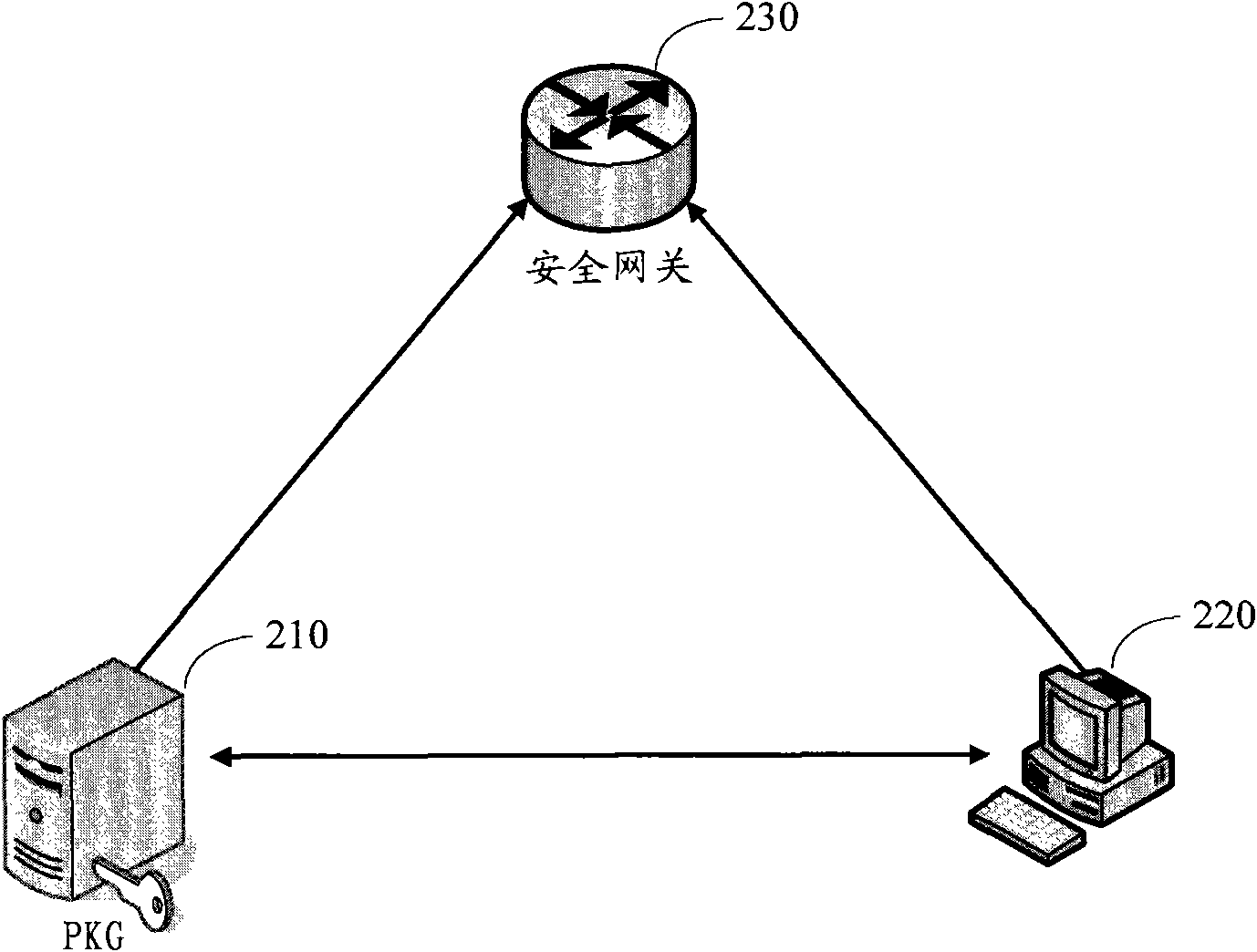
InactiveCN101938500AAvoid dependencePrevent tamperingUser identity/authority verificationData switching networksBase codeIp address
The embodiment of the invention discloses a method and a system for verifying a source address. The method comprises the following steps that: a host registers in a private key generation centre PKG through an MAC address; a host public key and a host private key are acquired by interacting parameters with the PKG; an identity code-based IP address is generated according to the host public key and the IP address serves as the source address of the host; the host generates the authentication information of the source address according to the host private key and a conversation key and carries the authentication information in a data packet sent to a security gateway; and the security gateway verifies the source address according to the authentication information in the data packet. In the embodiment of the invention, a code system access to a sub-network is established by adopting an identity-based code mechanism, so that the dependence on the PKI is avoided; and the authentication information of the source address is added into each data packet, so that the source address is prevented from being distorted. Through a stream authentication method, the verification security and verification efficiency of the source address are improved.
Owner:THE PLA INFORMATION ENG UNIV
Remote protocol authentication method based on biological features
ActiveCN104767624AEnhanced anonymityStable deliveryUser identity/authority verificationDigital data authenticationUser needsPassword
The invention provides a remote protocol authentication negotiation protocol method based on biological features and belongs to the field of information safety. An efficient elliptic curve coding system is adopted. The method comprises the following steps that (1) system initialization is carried out to generate elliptic curve data; (2) a user submits register information to a server through a safe channel, and the server conducts data processing and then stores the information into an intelligent card and sends the information to the user through the safe channel; (3) a user needs to calculate login information and sends the login information to the server; (4) the purpose of authentication and key negotiation between the user and the server can be achieved through two times of hand shaking, and a session key is generated; (5) the user can achieve the purposes of changing a password and the biological features through the operation of the intelligent card without the assistance of the server. By means of the design, the protocol is high in safety, all mentioned known attacks can be resisted, meanwhile, dynamic identity is adopted, the anonymity of the user is protected, and the calculation performance is also greatly improved. The method is suitable for online education, remote medical and other remote authentication systems.
Owner:BEIHANG UNIV
Internet-of things-oriented equipment anonymous identity authentication method and system
ActiveCN112953727AMake sure it hasn't been tampered withDefense against replay attacksKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessAnonymity
The invention belongs to the technical field of equipment identity authentication in an internet of things environment, and discloses an internet-of things-oriented equipment anonymous identity authentication method and system, the internet-of things-oriented equipment anonymous identity authentication method comprises the following steps: defining a communication model; selecting system parameters; initializing the system; registering equipment; calculating a private key and a temporary secret value; decrypting the ciphertext by using the temporary secret value; carrying out equipment authentication and key negotiation; and judging. The method has anonymity, and the real identity of the equipment and the relation between the equipment are not exposed in the interaction process; the method has the advantages of low power consumption, consideration of factors of limited processing and communication capabilities of sensor equipment, reduction of the calculation amount, the number of communication rounds and the storage overhead of a protocol, and adoption of elliptic curve point multiplication, hash function and XOR operation in other stages except for calculation of a temporary key by using bilinear mapping in an equipment registration stage; and the method has security, can successfully resist common Internet of Things attacks, and is well suitable for the Internet of Things terminal with limited resources.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com