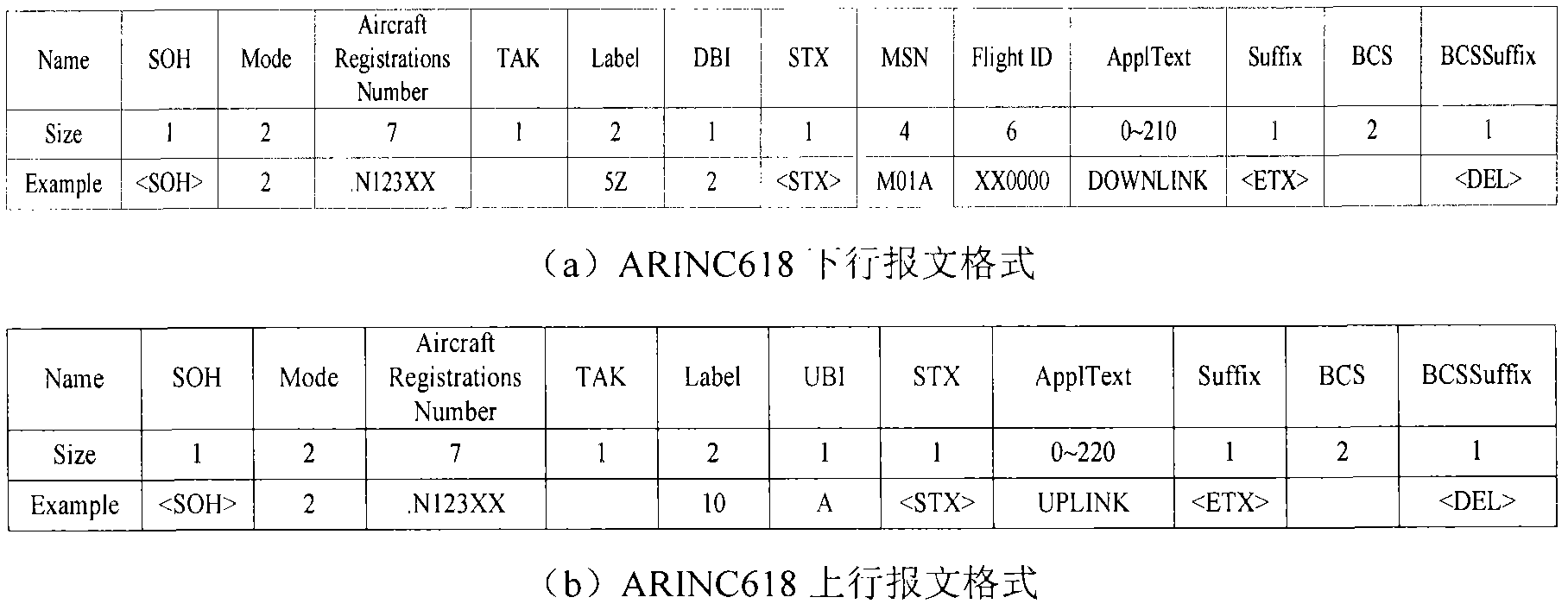
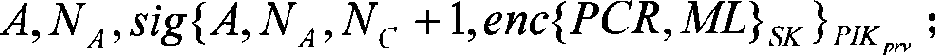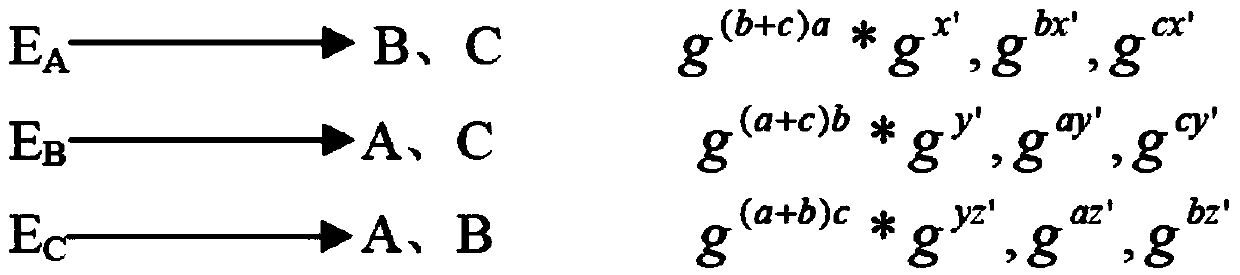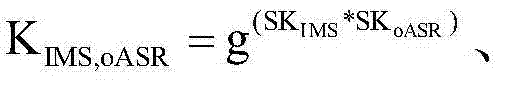Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52 results about "Impersonation attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Impersonation attacks are emails that attempt to impersonate a trusted individual or company in an attempt to gain access to corporate finances or data.
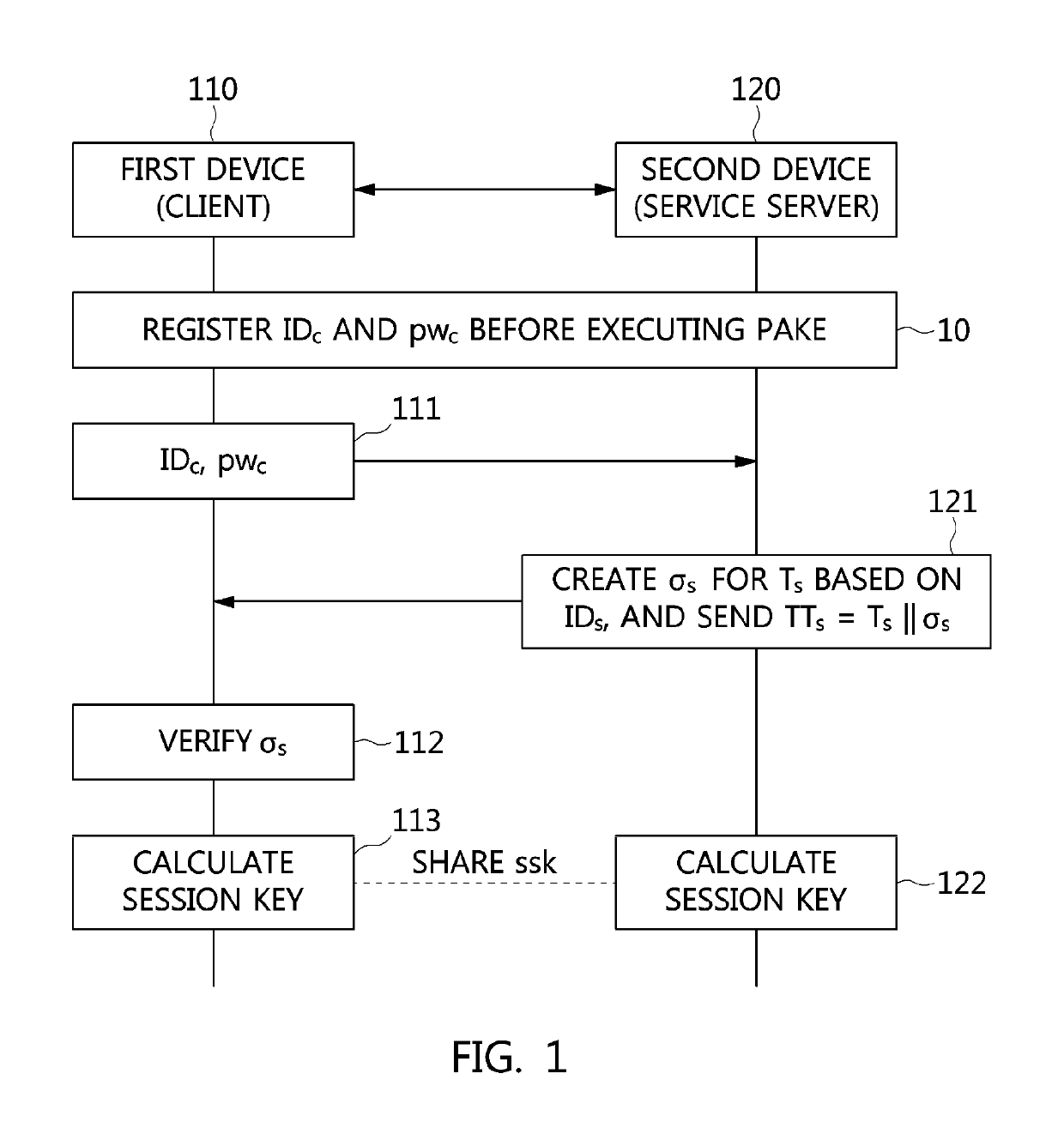
Remote proving method in trusted computation environment
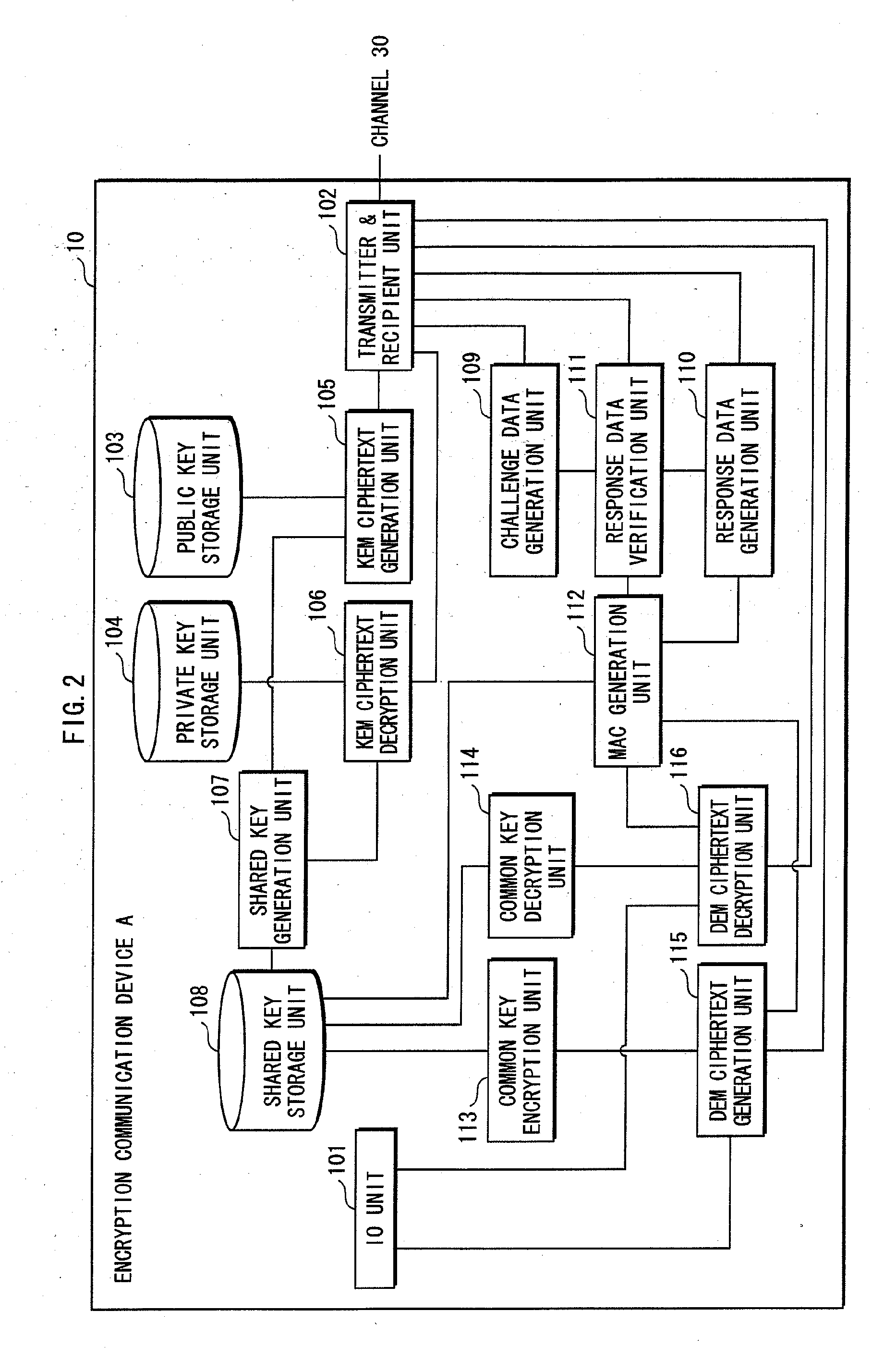
InactiveCN101477602AGuarantee authenticityGuaranteed privacyInternal/peripheral component protectionTransmissionMan-in-the-middle attackDigital signature
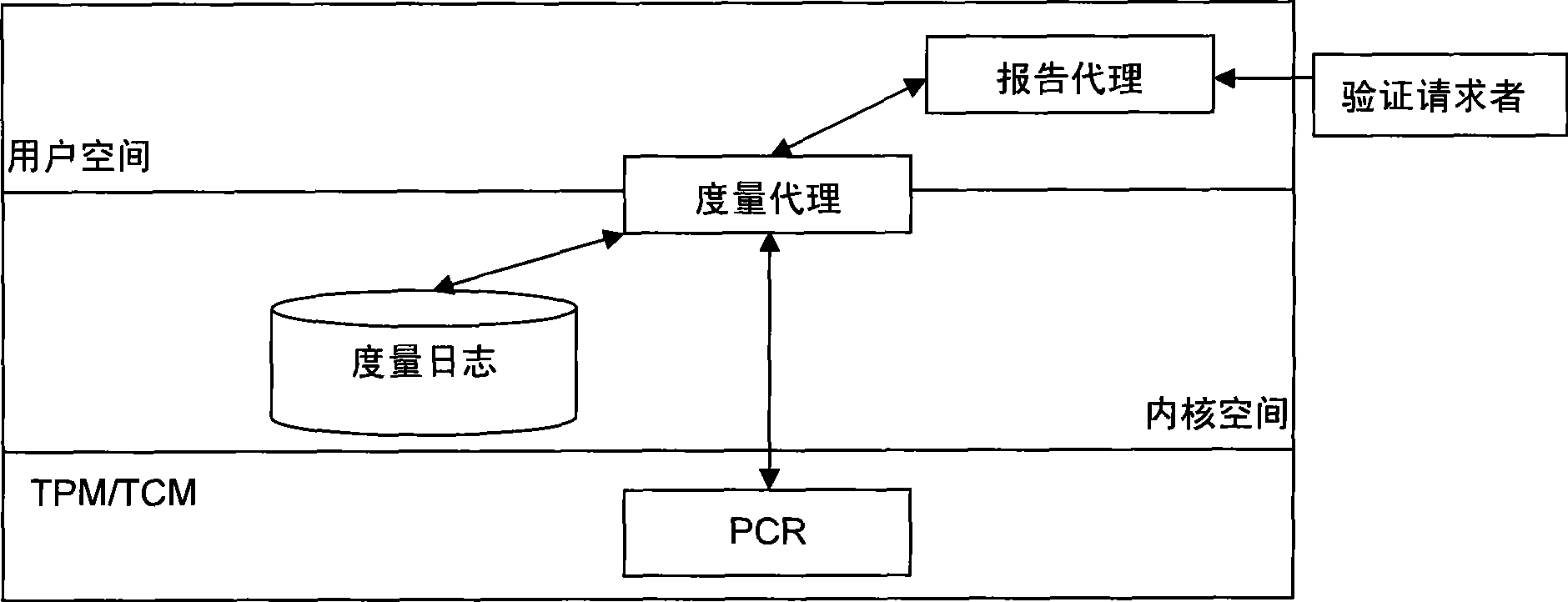
The invention provides a method for remote attestation in a trusted computing environment. The method is characterized in that secure session key is adopted for encrypting the metric value and the metric log of trusted platform to be verified, and signs for encryption result data. The method is based on a security chip TPM / TCM; the adopted remote attestation framework comprises three parts: an integrity measuring mechanism, a reporting mechanism and a validation mechanism, which are achieved by an integrity measuring agency, a report agency and a verification requestor, wherein, the measuring agency, the report agency and the verification requestor are installed in the trusted platform to be verified. The method ensures that the authenticity of the integrity measuring value and the measuring log and the privacy of the platform are kept; the replay attack, impersonation attack and man-in-the-middle attack are effectively prevented; the method is used for proving to the verification requestor that the running environment of the platform is credible, or used for self-test of the platform running environment; the method can be used for not only proving to the requestor that the platform running environment is credible, but also the self-test of the platform running environment; and the method is more suitable for a fair and open network environment.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
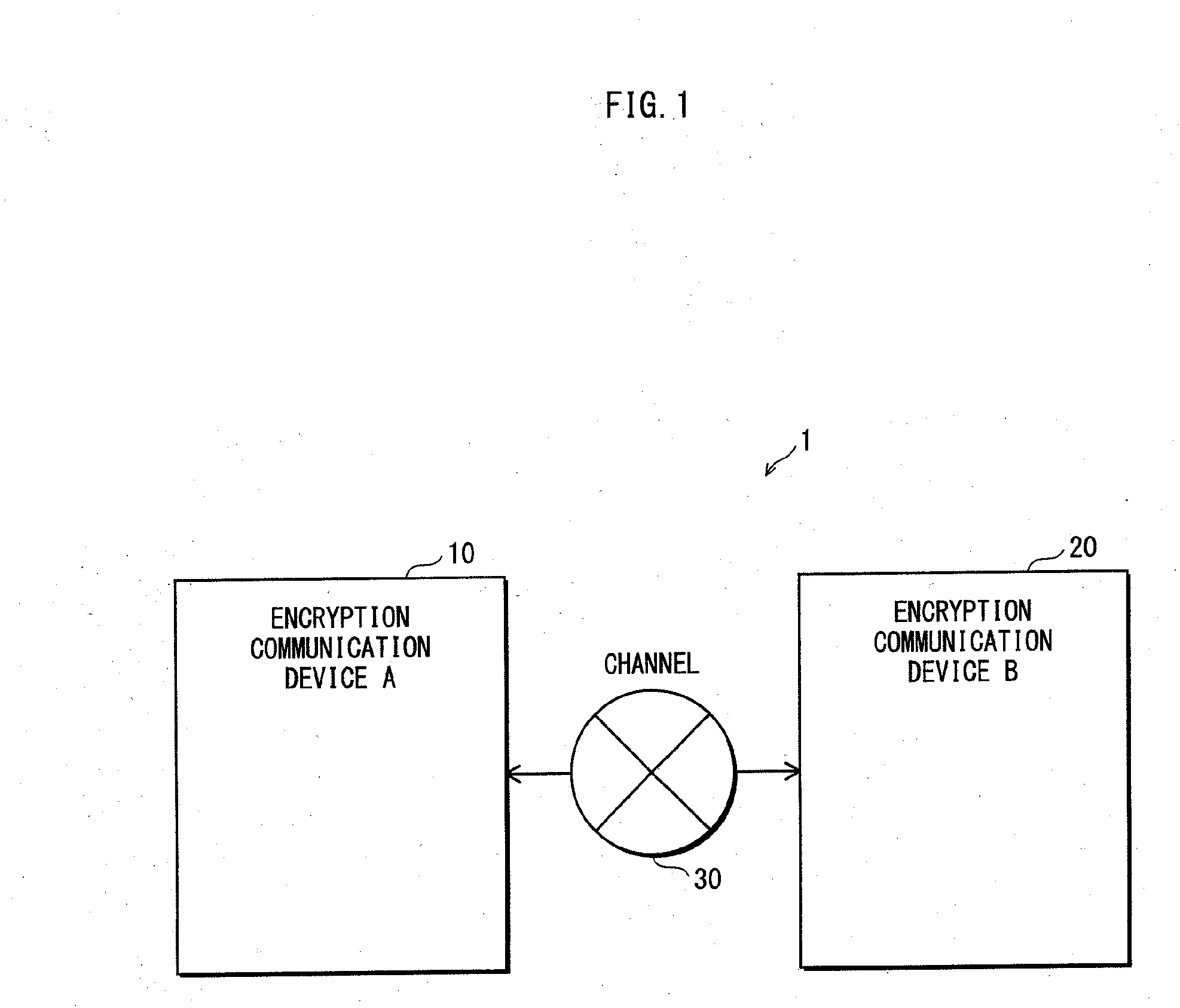
Communication device and communication system
InactiveUS20090100264A1Avoid attackVerify validityKey distribution for secure communicationUser identity/authority verificationComputer hardwareThird party
A communication device is secure against an impersonation attack as well. The communication device secretly communicates, with an external device, target data with use of a key shared with the external device. Without being known to a third party, the communication device generates a key shared with the external device using a scheme of which security is proved. Validity of the external device is determined by authentication with use of a key dependent function that is shared with the external device and is dependent on the shared key. If the external device is determined to be valid, for secretly communicating the target data, verification data for verifying validity of the target data is generated from the target data with use of the key dependent function.
Owner:PANASONIC CORP
Repeating data deleting system and method applicable to cloud storage
The invention discloses a repeating data deleting system and method applicable to cloud storage. The repeating data deleting system is based on strategies, a security agent and a random storage mechanism are adopted, a storage service is separated from a security service, the space utilization rate of cloud storage is improved, bandwidth occupation of redundant data is reduced, and security of user data and privacies is improved at the same time. The system is mainly composed of a client, the security agent and the cloud storage, wherein the security agent is the most secure core and is mainly used for ensuring the security of the user data and privacies. The repeating data deleting system and method applicable to cloud storage have the advantages of being high in security, system efficiency, bandwidth utilization rate and the like, and can resist replay attack, impersonation attack and security threats brought by partially trusted cloud storage providers.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for resisting simulated main customer attack in cognitive radio
InactiveCN101420758AAvoid interferenceHigh precisionConnection managementSecurity arrangementFrequency spectrumComputer science
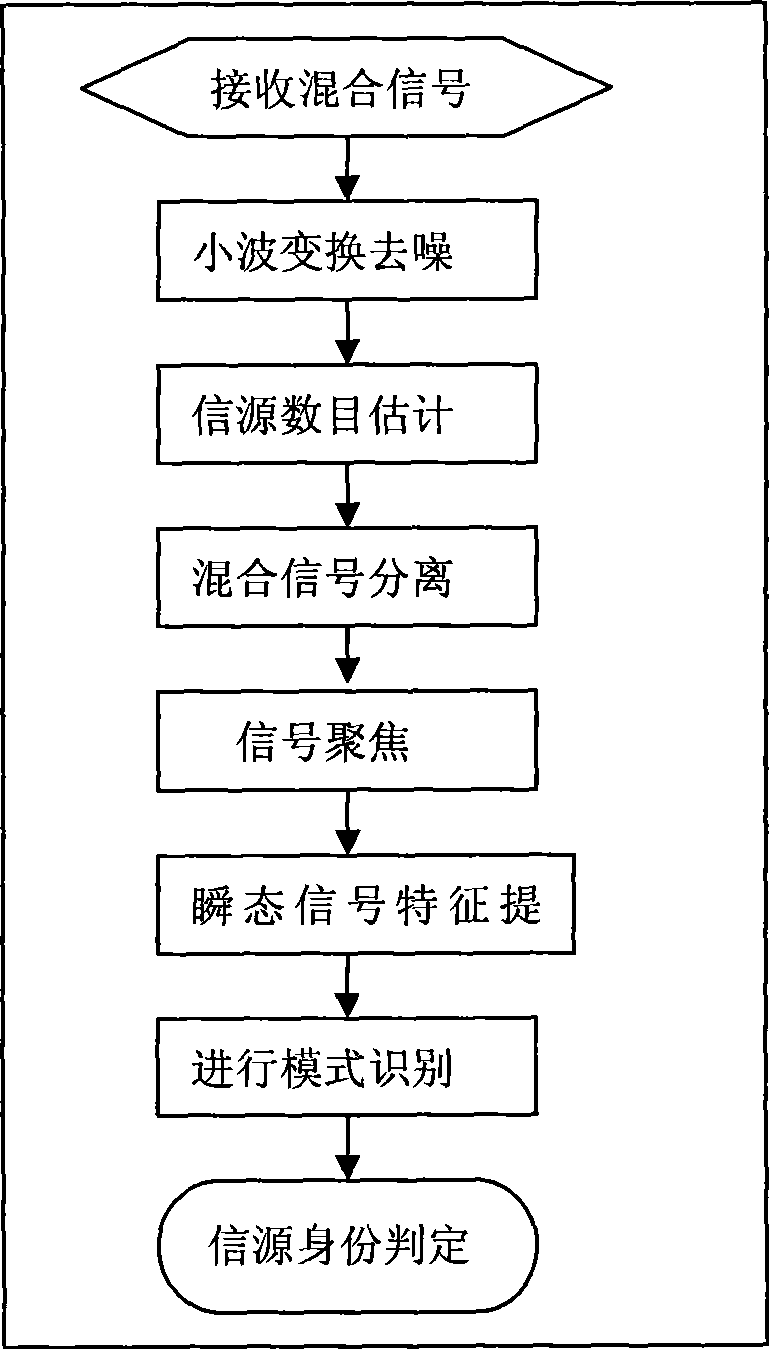
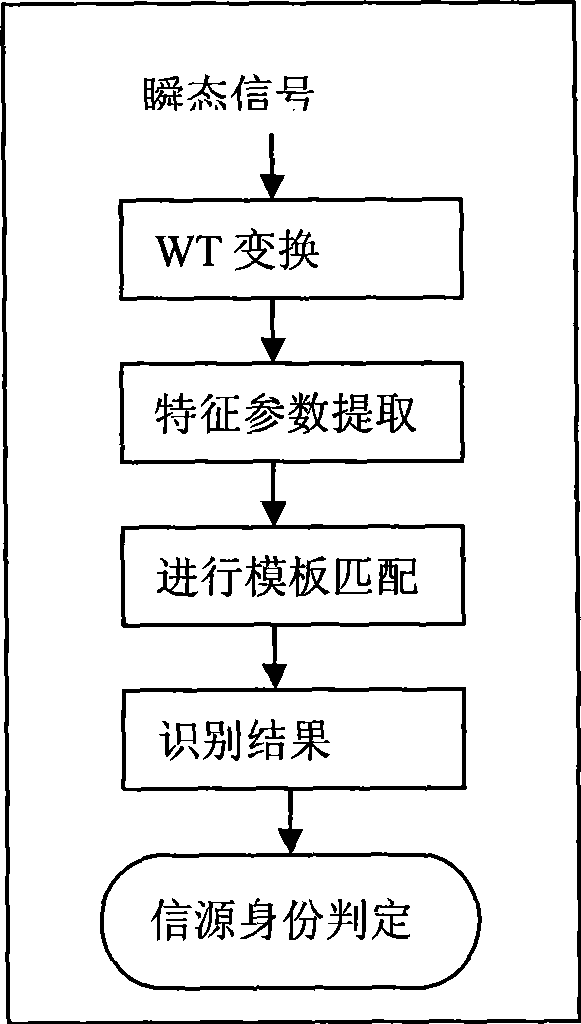
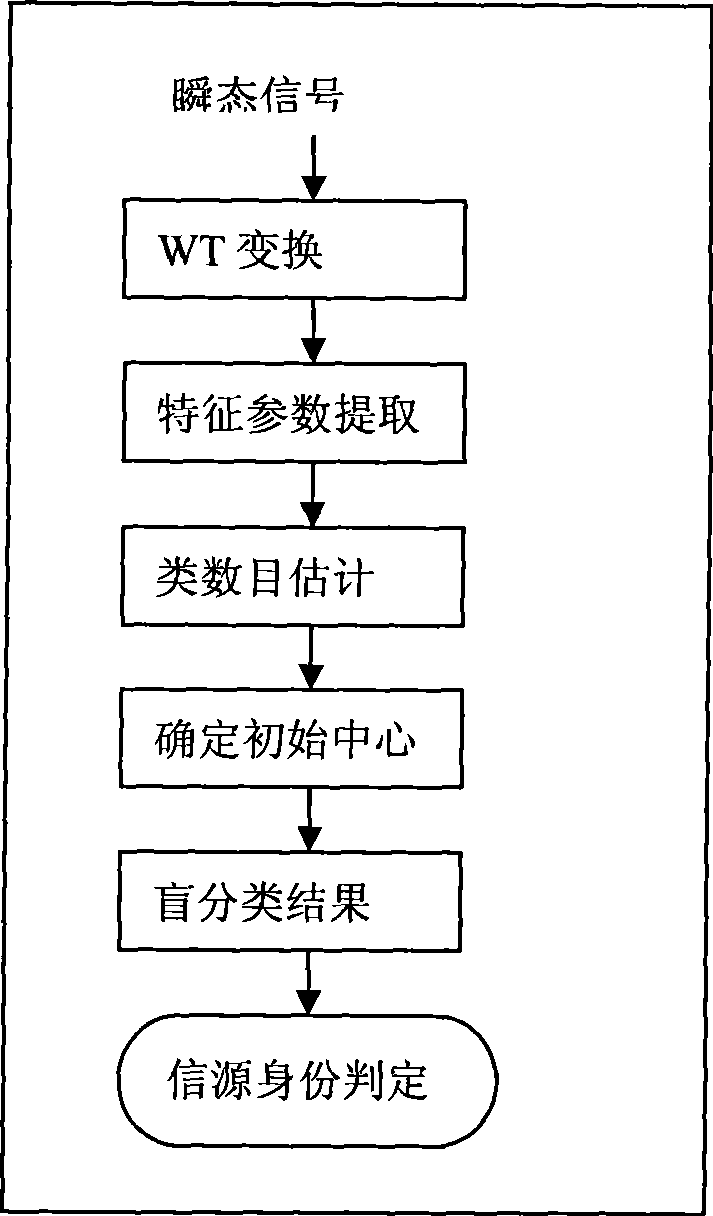
A method for resisting primary user impersonation attacks in cognitive radio belongs to the technical field of radio communication, particularly relates to sensing and processing of the signals in the cognitive radio system and identification of a signal source. The method comprises the following steps: reducing noise of a composite signal which is received during a spectrum sensing process, estimating number of the signal sources in the composite signal, and reconstructing various signals by a Capon beamformer; separating the signals of different radios, focusing the signals of different radios to separate out a transient signal and a modulation signal, analyzing the transient signal by wavelet transformation; extracting characteristic parameters and realizing identification of the signal source. The method for resisting the primary user impersonation attacks helps realize effective identification of the signal source and effectively resist the primary user impersonation attacks; and the method has a wide application scope, does not change a working mode of the existing primary user network, and satisfies operation requirements of FCC for a cognitive network.
Owner:UNIV OF SCI & TECH BEIJING
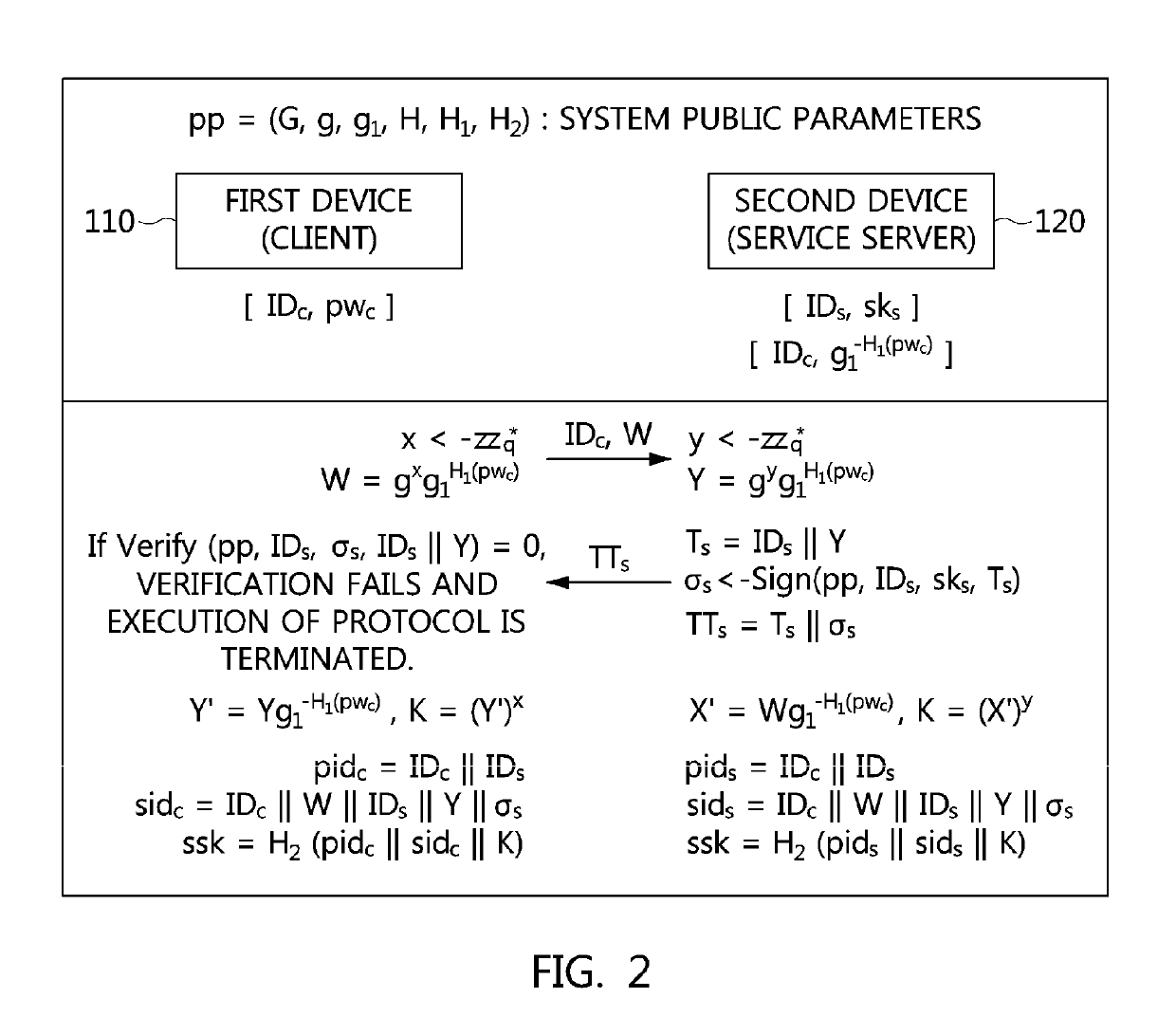
Method and apparatus for authenticated key exchange using password and identity-based signature
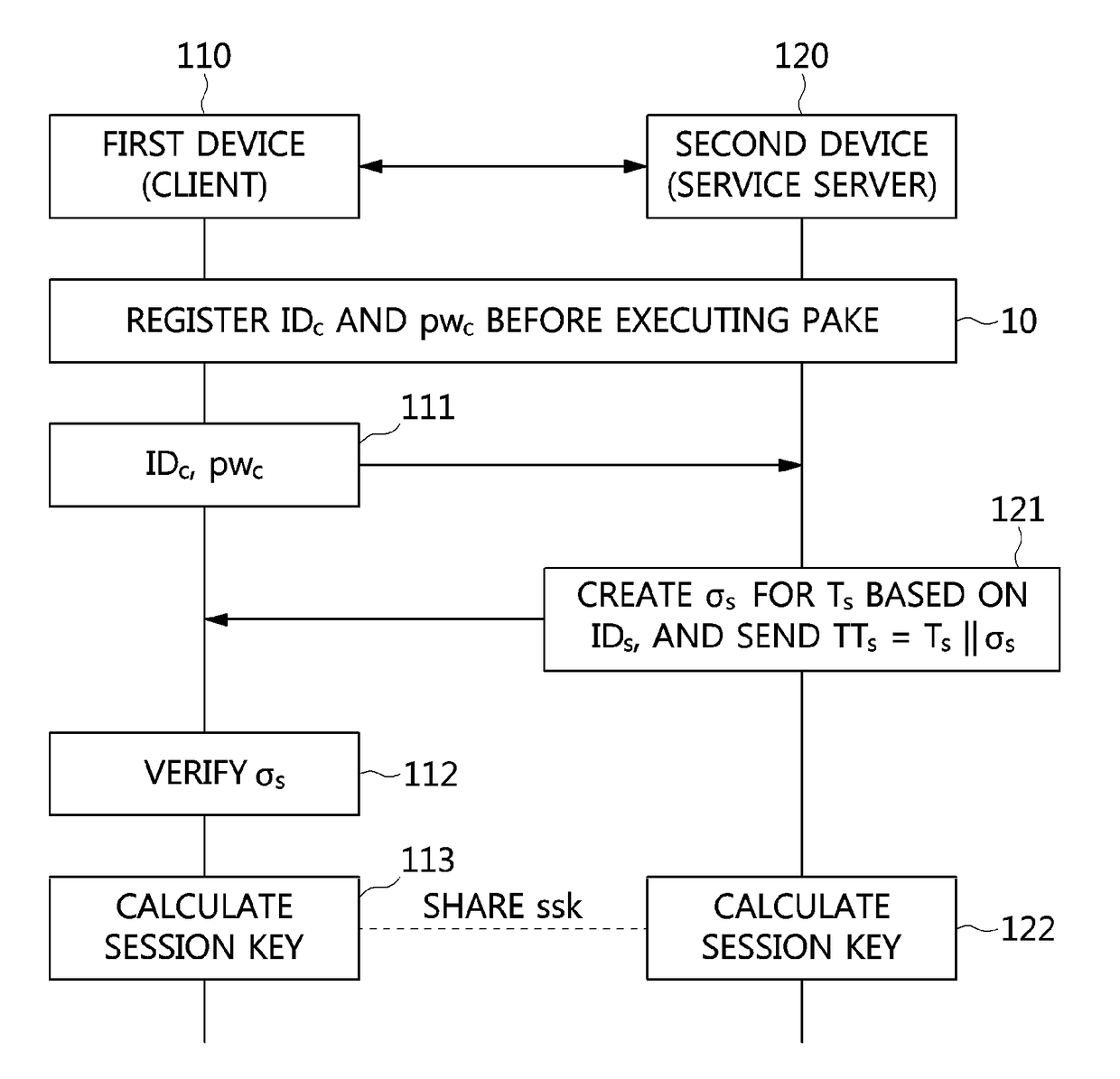
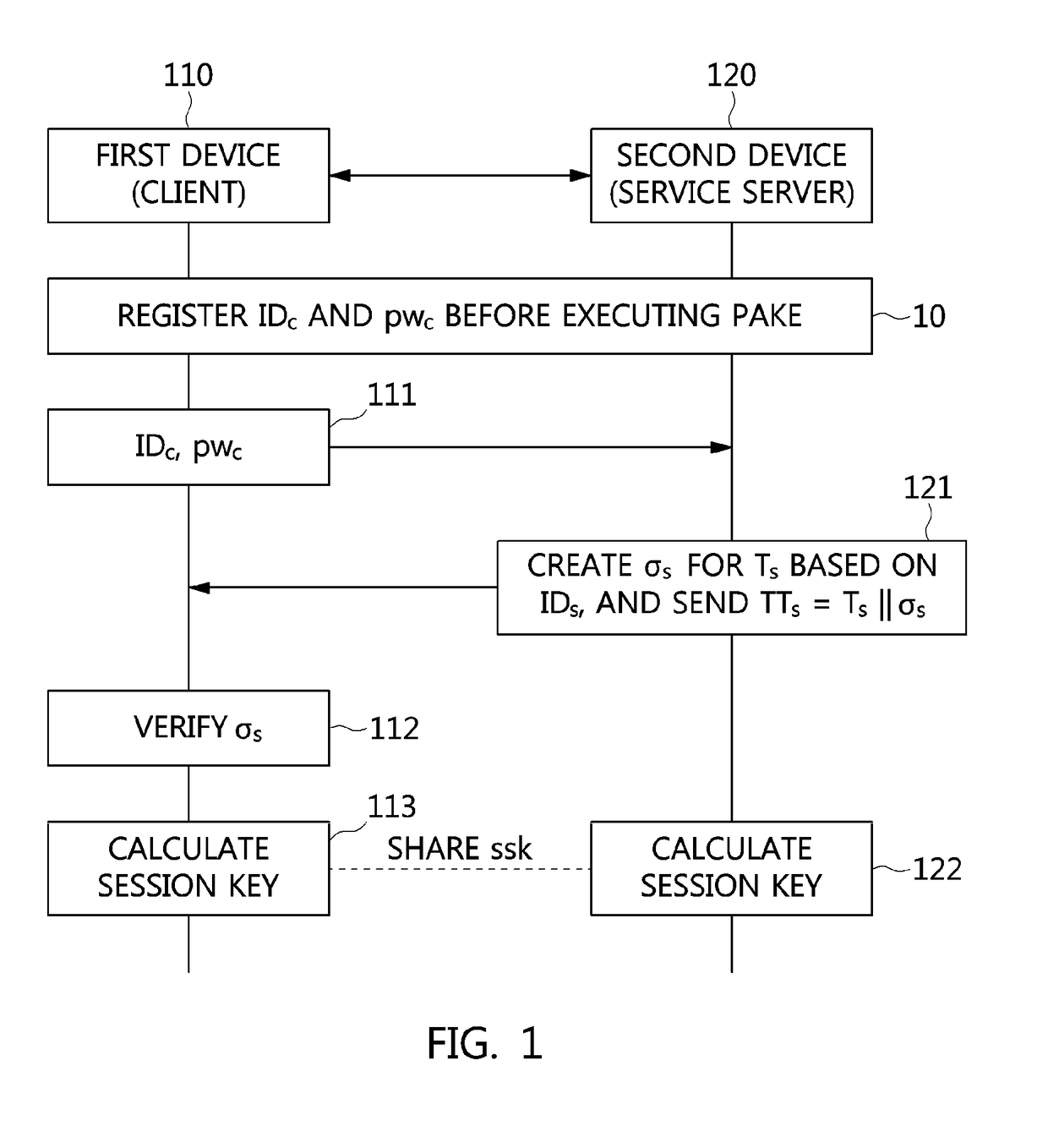
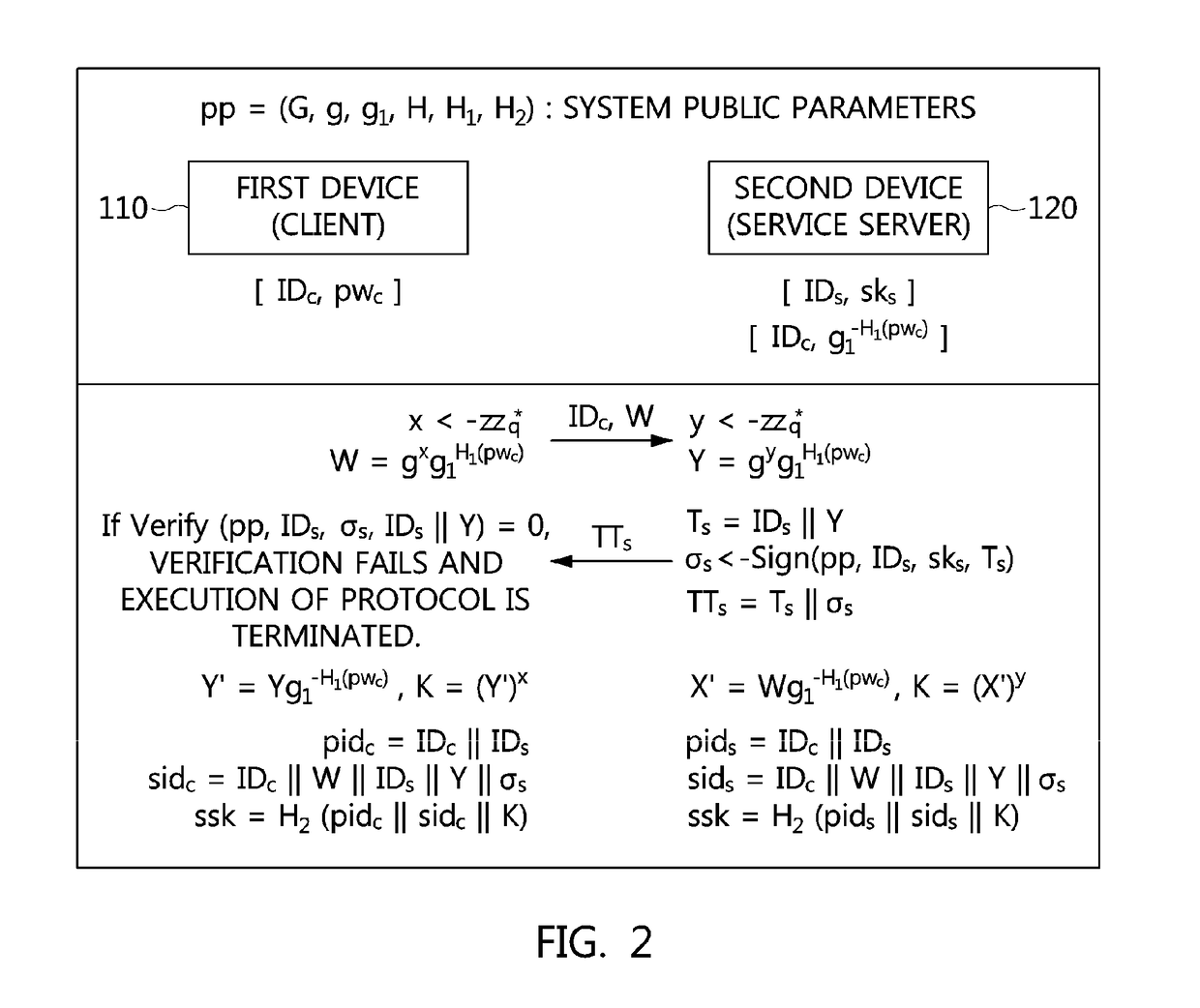
ActiveUS20170339118A1Authentication is convenientEasy to useMultiple keys/algorithms usagePublic key for secure communicationPasswordImpersonation attack
Disclosed herein are an apparatus and method for authenticated key exchange using a password and an identity-based signature, by which robustness is provided in order to prevent a server impersonation attack when a password is exposed, and by which a client may be provided with convenient authentication using an ID and a password.
Owner:ELECTRONICS & TELECOMM RES INST
IBAKA (Identity Based Authentication and Key Agreement) method
InactiveCN102624528AAnti-disclosure and masquerade attackResists man-in-the-middle attacksKey distribution for secure communicationPublic key for secure communicationProtocol for Carrying Authentication for Network AccessImpersonation attack
The invention discloses an IBAKA (Identity Based Authentication and Key Agreement) method. The method comprises the following steps that: a user at a sending terminal generates first authentication data for authenticating the identity of the user at the sending terminal and sends the first authentication data to a user at a receiving terminal; the user at the receiving terminal carries out legality authentication on the identity of the user at the sending terminal according to the received first authentication data; if authenticating that the identity of the user at the sending terminal is legal, the user at the receiving terminal generates second authentication data which does not contain key information of the user at the sending terminal, sends the second authentication data to the user at the sending terminal and generates a conversation key of the receiving terminal; the user at the sending terminal carries out legality authentication on the identity of the user at the receiving terminal according to the received second authentication data; and if the identity of the user at the receiving terminal is authenticated to be legal by a sensing terminal, the user at the sending terminal generates a conversation key of the sending terminal. The method disclosed by the invention can be used for solving the problem that a risk of denial of service attack, key leakage impersonation attack or temporal key leakage attack exists in an IBAKA protocol.
Owner:NO 61 INST OF GENERAL STAFF
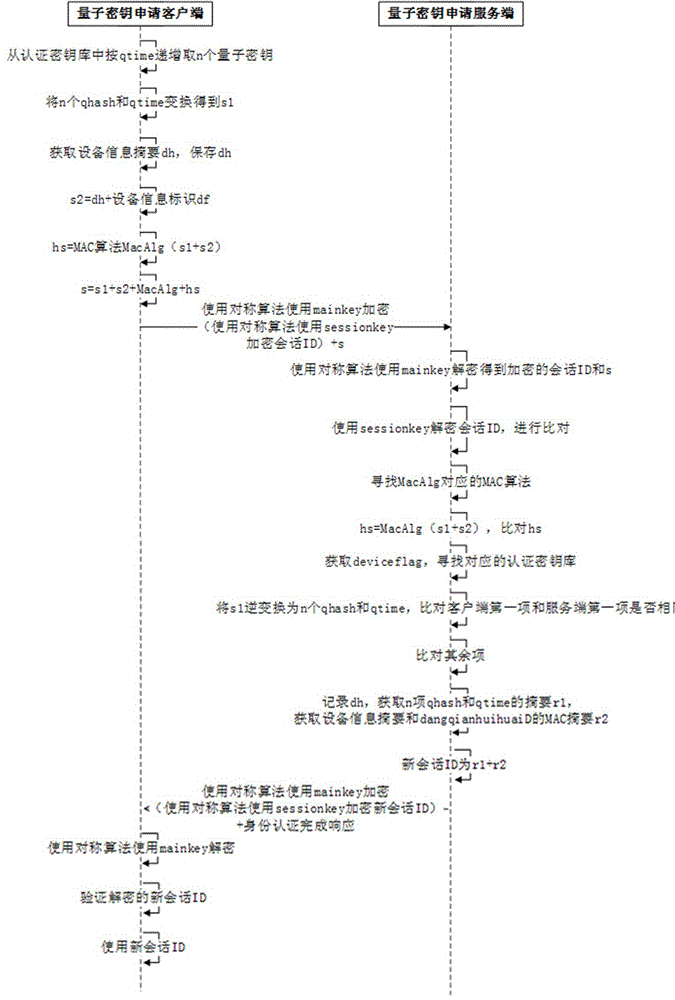
Identity authentication method during quantum secret key application process
ActiveCN105763563AEnsure safetySecurity updateKey distribution for secure communicationInformation transmissionVia device
The invention discloses an identity authentication method during a quantum secret key application process. The identity authentication method includes the steps: a quantum network deployment phase, a preparation initial phase, a secret key preparation phase, an identity authentication phase and a secret key application phase. During an abstract extraction process, as the identity authentication method uses a quantum secret key and the quantum secret key is provided with true randomness, the difficulty for performing reverse operation on the abstract can be further reduced and the safety for information transmission can be improved; and at the same time, after accomplishment of one time of session identity authentication, only a device for identity authentication is allowed to apply for a secret key, so that the safety is further improved through verification of the device information, and during the process, a session ID is in continuous changing state and depends on a plurality of factors, so that a large amount of impersonation attack can be timely eliminated through verification of the session ID. For the identity authentication method during a quantum secret key application process, the secret key is applied to the quantum secret key application process to verify the legal identity between two parties for communication, so that verification of the legal identity of the opposite side between the two parties for communication can be realized and the required data for verification has absolute safety during the transmission process in the network.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Physical unclonability-based RFID lightweight class authentication method
InactiveCN104112106ALow costTaking into account the costSensing record carriersComputer hardwareImpersonation attack
The invention discloses a physical unclonability-based RFID lightweight class authentication method, uses a PUF, a linear feedback shift register (LFSR), and XOR operation to perform processing, a label has small hardware requirements, cost is relatively low, the operation amount is small, and the method is resistant to various attacks including replay attack, impersonation attack, message stop attack, synchronization attack, wiretapping attack, physical attack, and label cloning, thereby effectively realizing forward security, and protecting privacy of a user. At the same time, through bidirectional authentication between a label and a reader, balance between efficiency and security is realized, hardware cost is well given consideration to, and thus the method is suitable for use of lowcost labels, and has relatively large practicability.
Owner:GUANGZHOU ZHONGCHANG KANGDA INFORMATION TECH +1
Method for realizing dependable SSH based on dependable computing
InactiveCN101741842AAvoid security threatsProtection against replay attacksKey distribution for secure communicationUser identity/authority verificationKey exchangeMan-in-the-middle attack
The invention provides a method for realizing dependable SSH based on dependable computing. The method integrates remote authentication of the dependable computing with key exchange of an SSH protocol so as to closely combine platform status information verification with session key negotiation; and the method enhances the security of data at a communication end point on the premise that safe transmission of the data is ensured. The method requires that both a server and a client are provided with dependable security chips; and the platform status can be measured by a measurement module and a dependable operating system. The method can not only effectively prevent the security threat that the communication with an unknown end point by using a security channel may undergo various attacks in the SSH protocol, but also effectively protect against replay attack, impersonation attack and man-in-the-middle attack.
Owner:BEIJING JIAOTONG UNIV
Low-complexity identity authentication method based on intelligent card and under multiserver environment
InactiveCN103346887AAvoid loss attackPrevent impersonation attacksUser identity/authority verificationDigital data authenticationSmart cardImpersonation attack
The invention discloses a low-complexity identity authentication method based on an intelligent card and under a multiserver environment. The low-complexity identity authentication method comprises the steps of registering, logging and authentication, wherein the registering further comprises the steps that registering information of a user is converted by a registration center and the intelligent card and then is stored in the intelligent card; the logging further comprises the steps that the intelligent card carries out local legitimacy verification on the identity of the user, and if the identity of the user is legitimate, a random number is generated, and first verification data are generated and sent to a server; the authentication further comprises the steps that the server carries out the legitimacy verification on the identity of the user, and if the identity of the user is legitimate, second verification data are generated and sent to the intelligent card; the intelligent card carries out the legitimacy verification on the identity of the server, and if the identity of the server is legitimate, third verification data are generated and sent to the server; the server carries out secondary verification on the identity of the user, and if the identity of the user is legitimate, the server and the intelligent card generate the same session key. The low-complexity identity authentication method avoids intelligent card losing attacks and impersonation attacks.
Owner:SHANDONG UNIV OF SCI & TECH
Automobile remote-control key-free door control identity authentication method
InactiveCN101866534APrevent Intercept Scanning AttacksPrevent replay attacksTransmission systemsMultiple keys/algorithms usagePlaintextRemote control
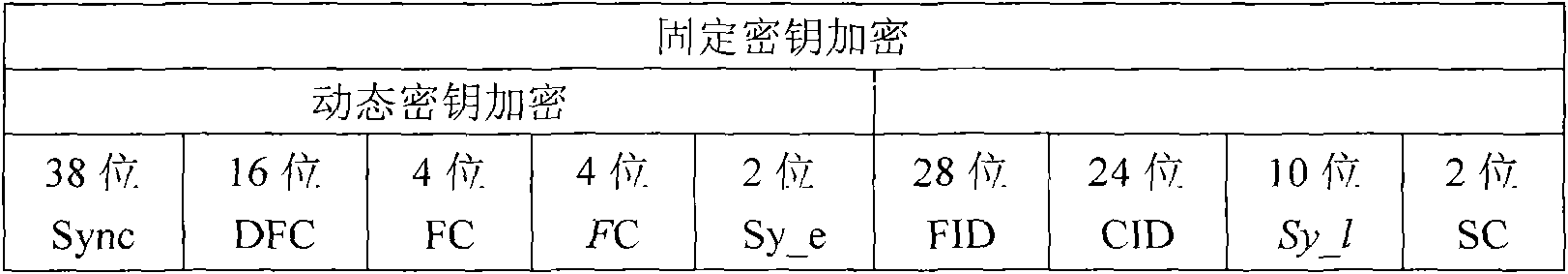
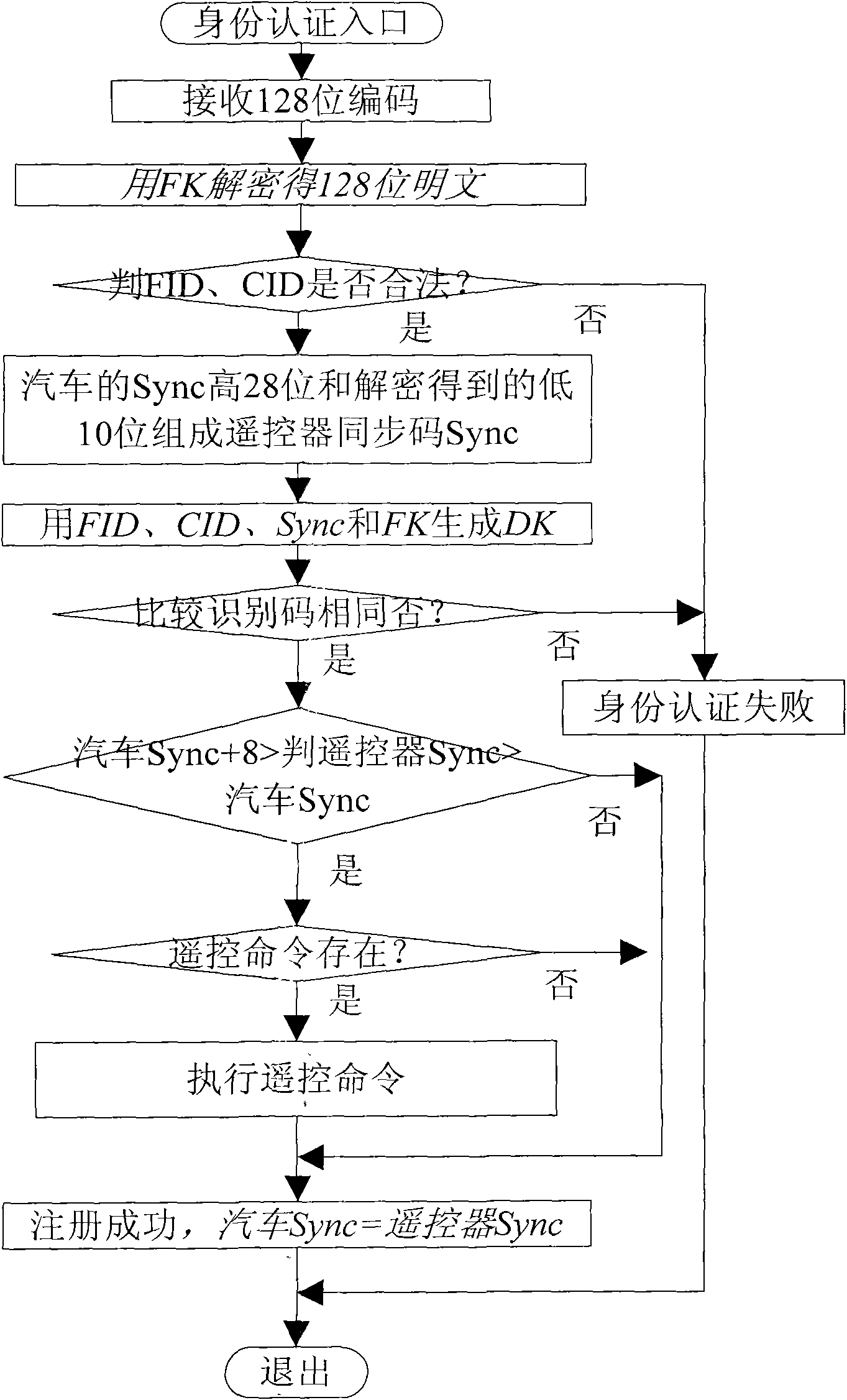
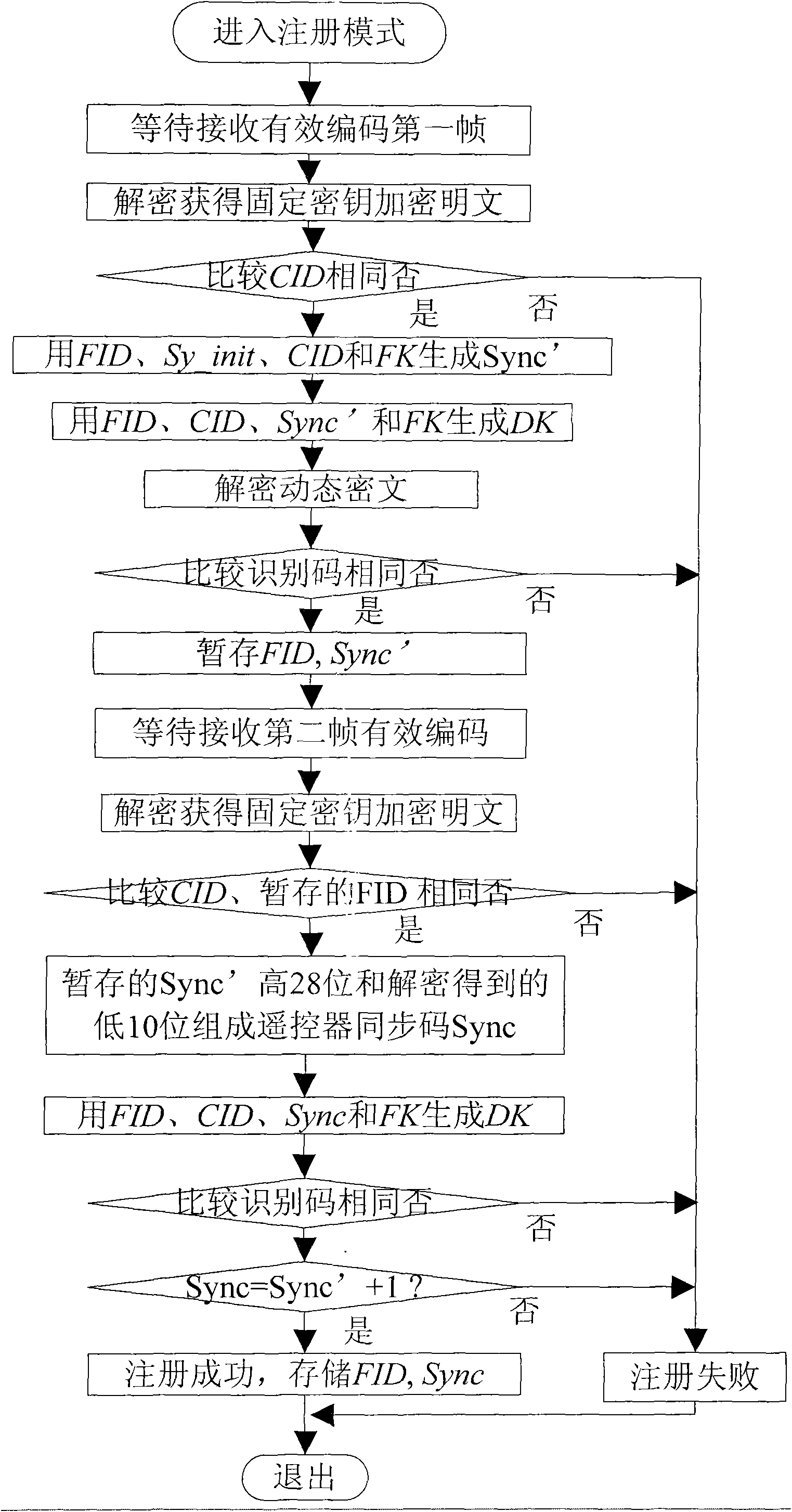
The invention discloses an automobile remote-control key-free door control identity authentication method. In the invention, an automobile ID, a remote controller ID and a 38-bit synchronous code are used for generating a 128-bit plain text; the 128-bit plain text is composed of two parts, the front 64 bits are a plain text, and the rear 64 bits are a plain text; a 64-bit ciphertext is subject toAES encryption by using a 128-bit dynamic key; the 128-bit plain text is subject to AES encryption by using a fixed key to obtain a 128-bit ciphertext; the 128-bit ciphertext is transmitted to an automobile decoder; the automobile decoder decodes the received 128-bit ciphertext into the 64-bit ciphertext and the 64-bit plain text; a received automobile CID and a received remote controller FID arecompared with an automobile CID' and anremote controller FID' which are stored by the automobile, thereby completing a first authentication; and the dynamic key is used for decryption and compares identity codes to complete a second authentication. The invention protects the data transmission by AES encryption of the fixed key and the dynamic key, and can carry out authentication twice by only carrying out communication once in the whole authentication process. The invention can effectively resist strong attacks, and deny service attacks, impersonation attacks and other common attacks.
Owner:CENT SOUTH UNIV
Physical layer authentication method based on multi-carrier transmission
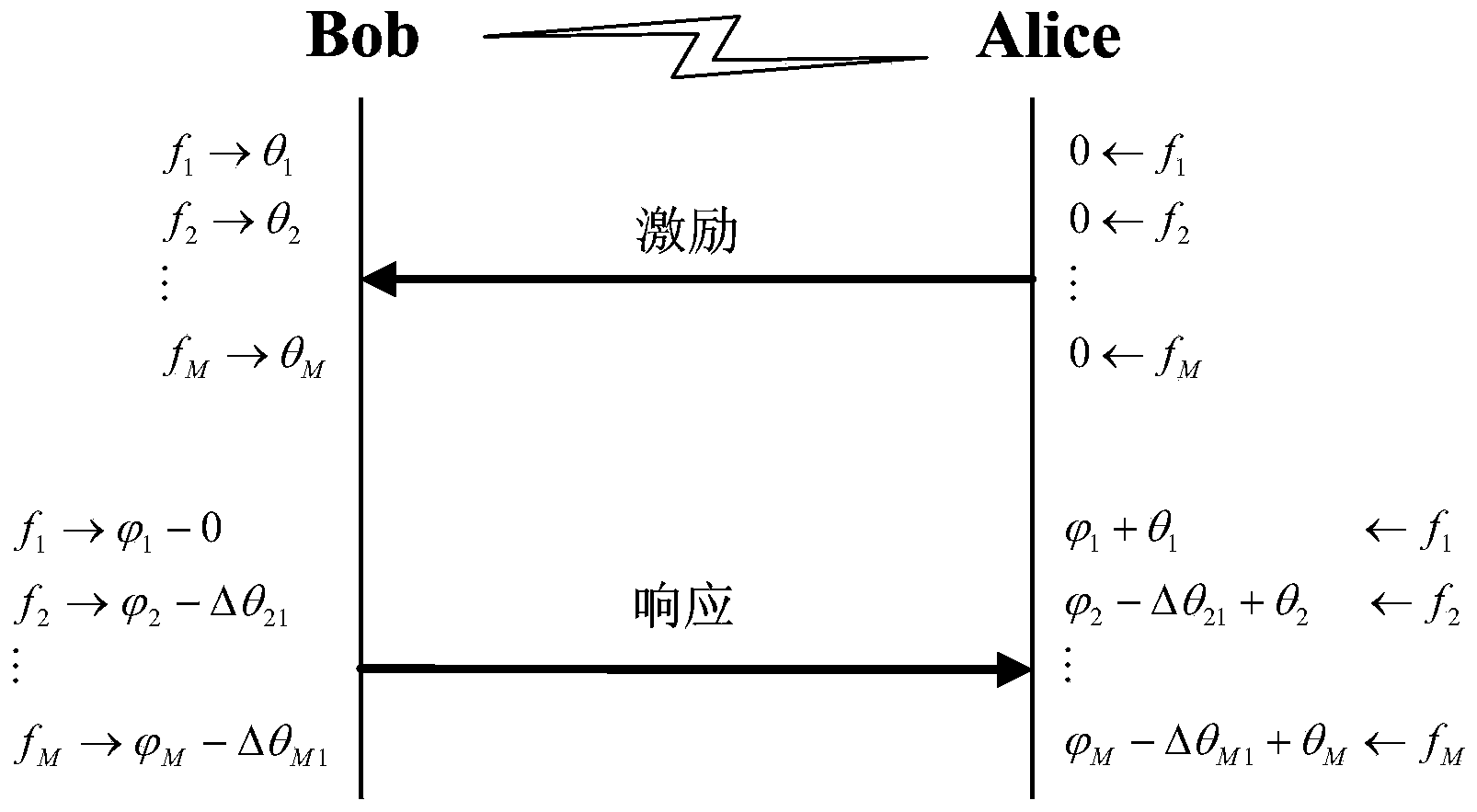
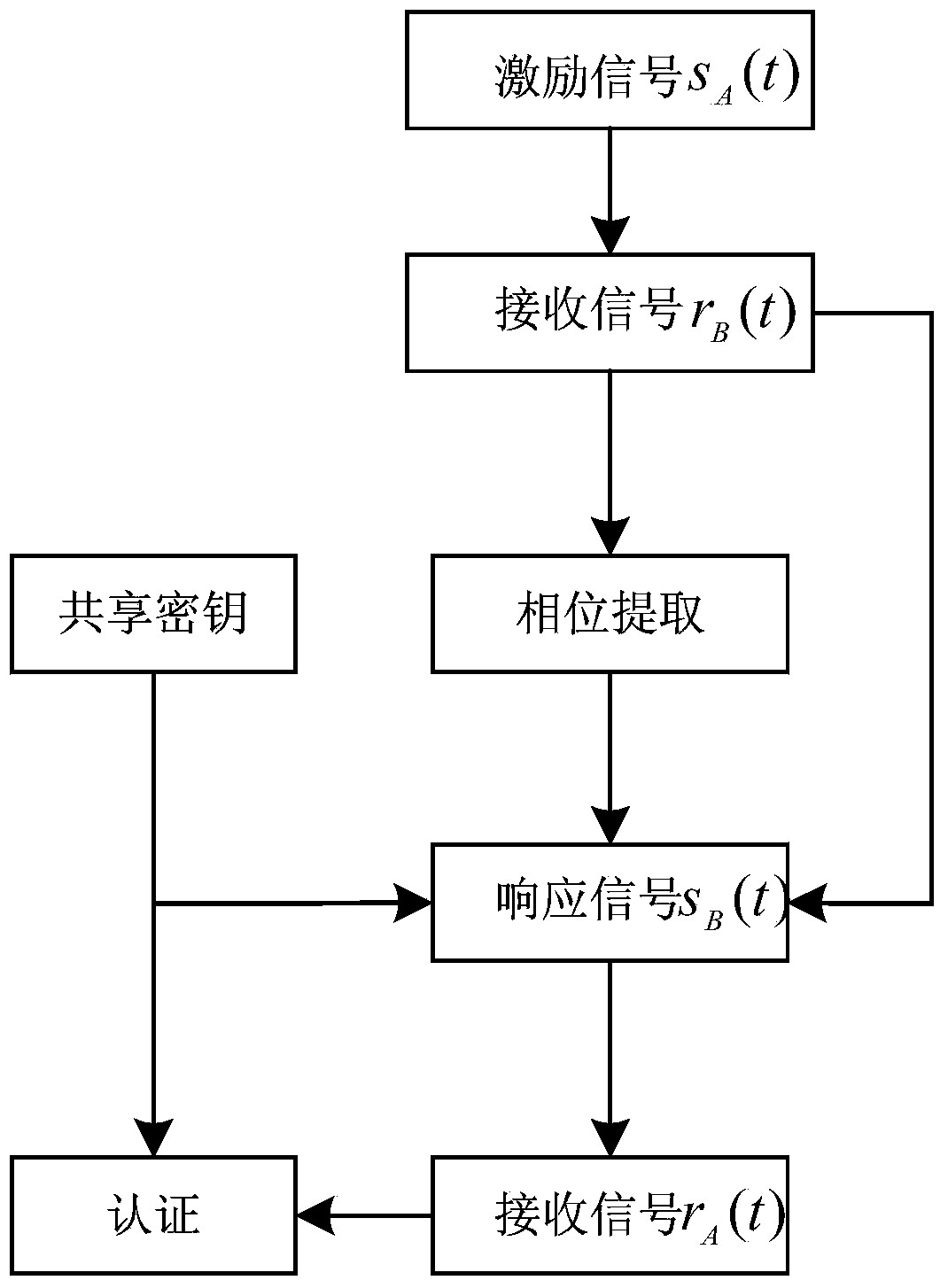
ActiveCN104168562AGood authentication performanceImprove securityWireless network protocolsTransmission path multiple useComputer hardwarePhase response
The invention discloses a physical layer authentication method based on multi-carrier transmission. According to the method, based on the multi-carrier transmission, channels are regarded as a set of M fading sub-channels, and the reciprocity and randomness of phase responses of the sub-channels are used for performing on identity authentication on both parties of communication. The method includes the implementation steps that Alice transmits an excitation signal to Bob, the phase difference of the multi-carrier channels is measured after Bob receives the excitation signal, then Bob transmits a signal where a shared secrete key is packaged to Alice, and Alice authenticates whether the signal is from Bob or not according to the received signal and the shared secrete key. According to the authentication process of the method, the characteristics of the phase responses of the channels are used, and kinds of spoofing attacks such as the interference attack, the replay attach, impersonation attack are effectively resisted.
Owner:青岛联众芯云科技有限公司
ZigBee security network with public key cryptography system NTRU (number theory research unit)
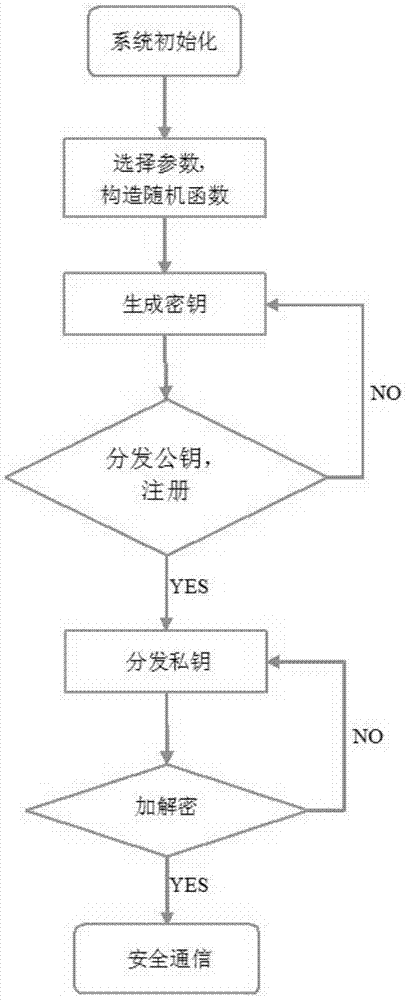
InactiveCN104333860AImprove securityReduce occupancyNetwork topologiesSecurity arrangementExtensibilitySecret code
The invention discloses a ZigBee security network with a public key cryptography system NTRU (number theory research unit). The ZigBee security network includes the steps: selecting system parameters meeting NTRU building conditions in system initialization according to the public key cryptography system NTRU, and constructing a random function; generating keys; distributing the keys and performing the encryption and decryption process. The ZigBee security network has the advantages that security of a ZigBee wireless communication process is improved, encryption and decryption speed is high, communication efficiency is improved, energy consumption is low, fewer storage resources are occupied, the storage load of the system is not increased, the ZigBee security network has fine expandability, the anti-attack capability of the system is improved, impersonation attack and replay attack can be effectively resisted, low cost of the system is ensured, and broad market requirements can be met.
Owner:成都卫士通信息产业股份有限公司
Quantum identity authentication method, computer, computer program and readable storage medium
InactiveCN108092770AResist attackWon't leakKey distribution for secure communicationBell stateComputer hardware
The invention belongs to the technical field of quantum communications, and discloses a quantum identity authentication method, a computer, a computer program and a readable storage medium. The methodcomprises the steps that binary identity strings of both sides are used for preparing two groups of particle sequences according to specified rules; Alice sends a first particle used for preparing aBell-state particle sequence to Bob, and Bob sends a second particle used for preparing the Bell-state particle sequence to Alice; Bell-based measurement is conducted on particles in the two sides, and the measurement results are subjected to binary representation. In the identity authentication process, no unitary transformation is needed in the Bell-state transmission process, and information transmission can be achieved simply by executing Bell-state measurement and a bitwise exclusive OR operation. In practical application, achievement of the protocol is achieved by only depending on Bell-state accurate preparation and Bell-state reliable measurement, and the protocol can resist impersonation attack.
Owner:CHENGDU UNIV OF INFORMATION TECH
Authentication method based on public key encryption system
ActiveCN108400867AVerify freshnessDefense against replay attacksKey distribution for secure communicationUser identity/authority verificationImpersonation attackKey distribution center
Owner:中国科学院沈阳计算技术研究所有限公司
Human living body detection method and device based on human brain intelligence and man-machine interaction
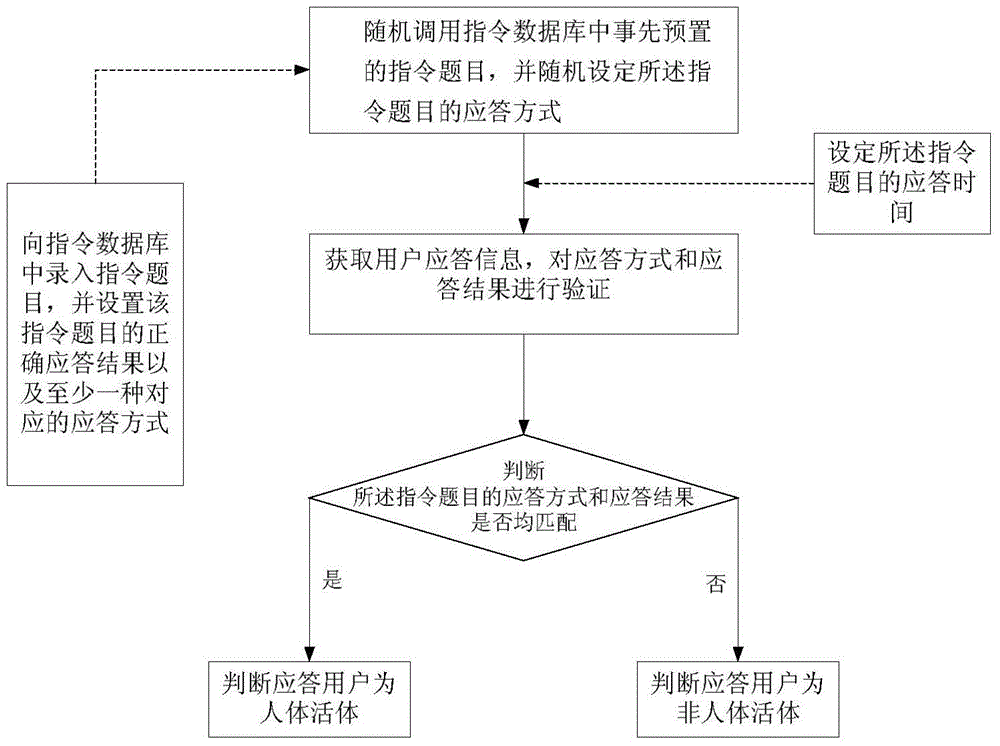
InactiveCN104965589APrevent Fraud AttacksLow costInput/output for user-computer interactionGraph readingHuman bodyHuman–robot interaction
The invention discloses a human living body detection method based on human brain intelligence and man-machine interaction. The human living body detection method comprises the following steps: randomly transferring an instruction subject which is pre-configured in an instruction database in advance, and randomly setting a response mode; acquiring user response information and verifying the response mode and a response result; and if the response mode and the response result of the instruction subject are matched successfully, judging that a response user is a human living body. According to the method, the subject is appointed randomly to enable the user to answer in regulated time by the randomly-appointed response mode, and the transmitted instruction subject can be answered through the brain thinking of the user, so that an impostor can not adopt manners such as pure voice and / or video synthesis or editing and the like to cheat a human living body detection system. According to the human living body detection method, lawless persons can be effectively prevented from carrying out impersonation attacks through various means, so that the human living body detection system becomes more effective and reliable.
Owner:GUANGDONG MICROPATTERN SOFTWARE CO LTD
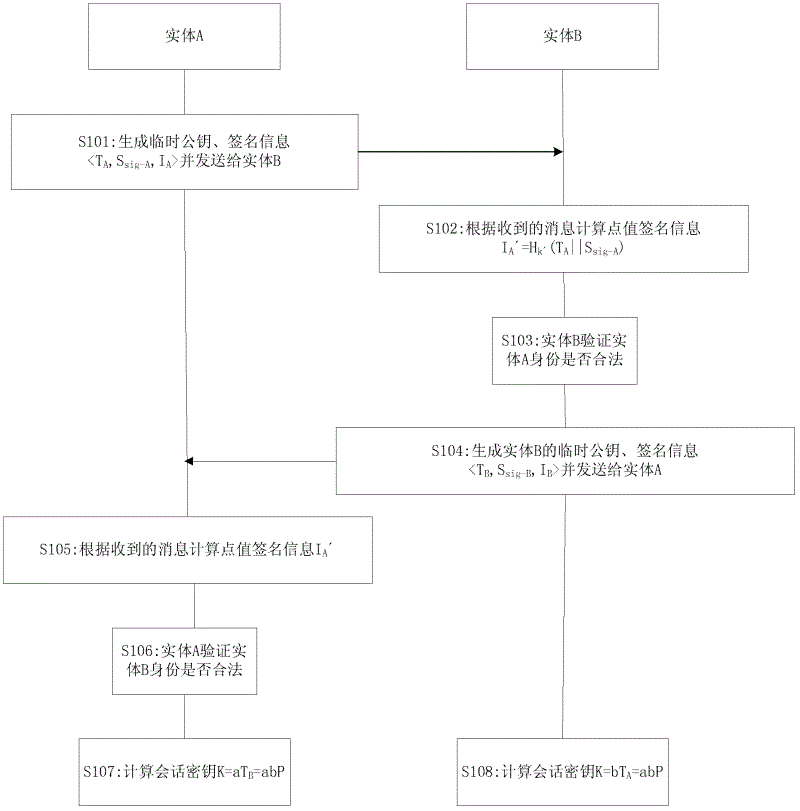
Three-party authentication key agreement protocol generating method based on certificates
InactiveCN103634104AImprove computing efficiencyImprove securityKey distribution for secure communicationComputer hardwareMan-in-the-middle attack
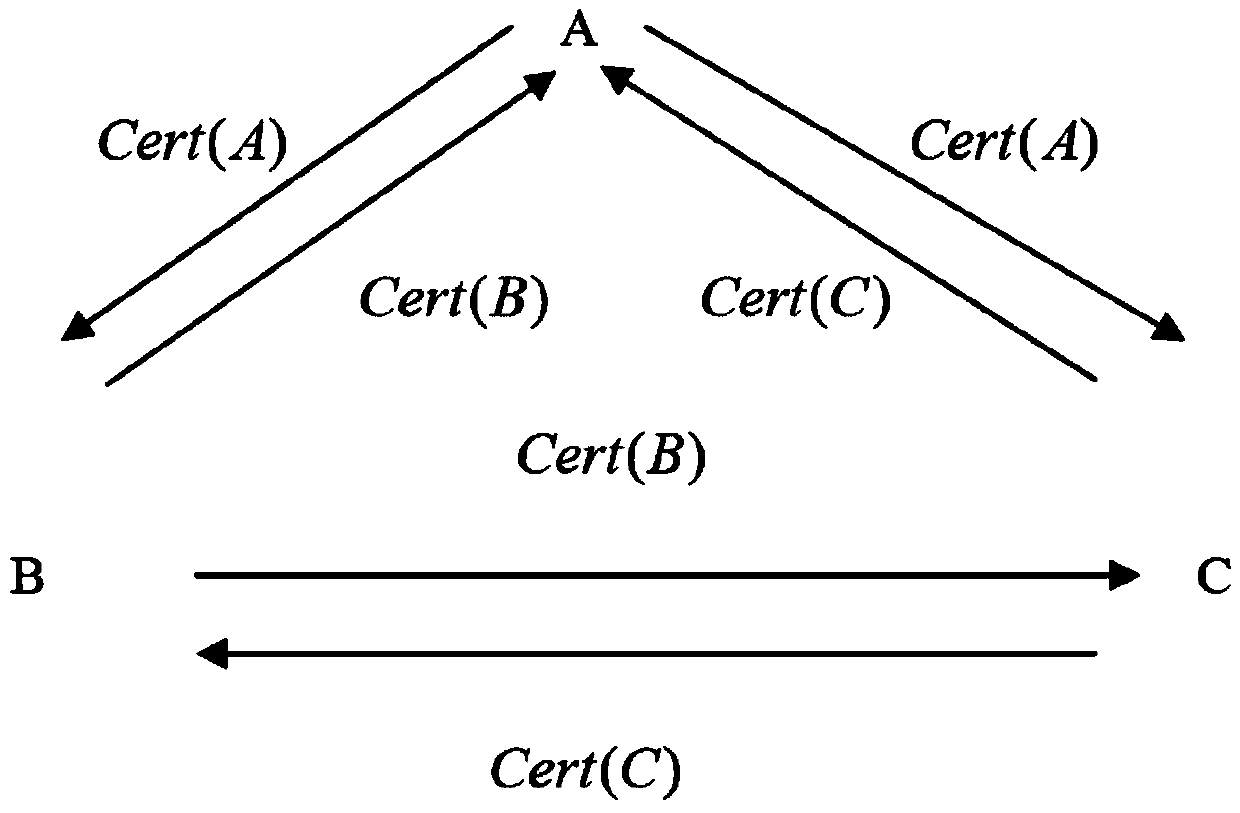
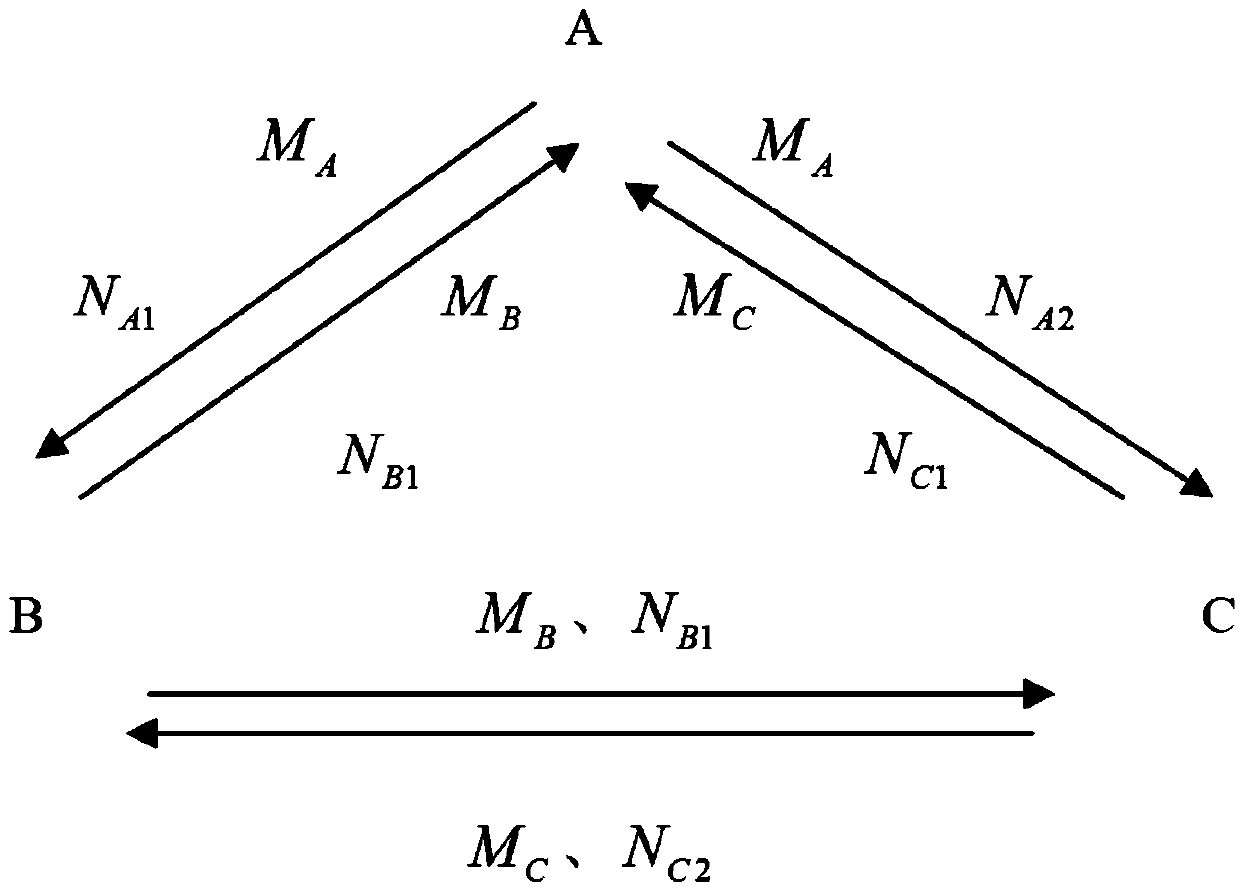
The invention relates to a three-party authentication key agreement protocol generating method based on certificates. The method is applied to a wireless network system and comprises the steps: (1) three communication parties A, B and C respectively send respective certificate to other two parties; (2) after the communication party A receives the certificates sent by the communication parties B and C, x is randomly selected as a temporary private key, the formulas that MA=(g*g<c>)*g<x> , NA1=(g)<x> and NA2=(g<c>)<x> are calculated, then the communication party A sends MA and NA1 to the communication party B, and sends MA and NA2 to the communication party C, and the processing modes of the communication parties B and C are identical with that of the communication party A; (3) after the communication party A receives the messages sent by the communication party B and the communication party C, calculation and verification are performed, if the formula is false, a protocol is stopped from operating; if the formula is successful, a session key is calculated; the modes of calculating the session keys of the communication party B and the communication party C are identical with that of the communication party A; (4) an agreement is completed. According to the three-party authentication key agreement protocol generating method based on the certificates, modular and exponent arithmetic and a hash function are used, the operation efficiency is higher, and the agreement can resist the man-in-the-middle attack, the unknown secret key sharing attack and the secret key reveal impersonation attack, so that the safety is high.
Owner:CHANGZHOU UNIV
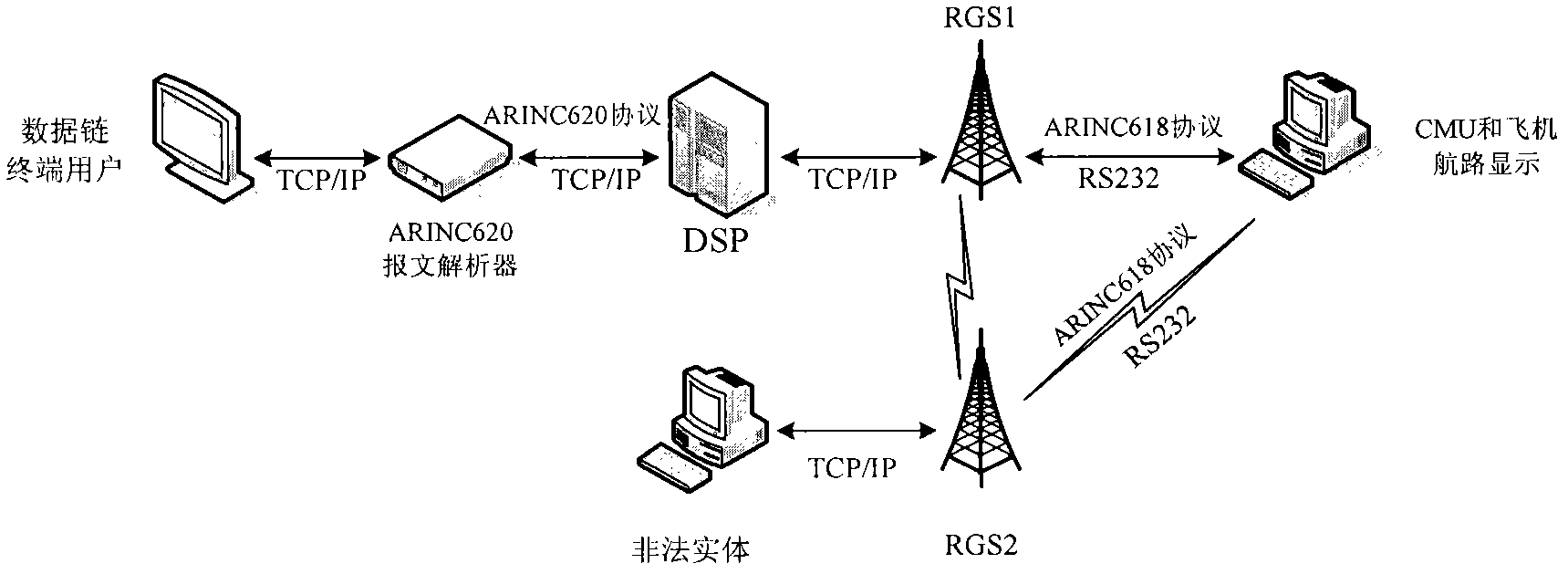
Entity impersonation attack penetration testing method aiming at aircraft communication addressing and reporting system (ACARS) data chain
InactiveCN103139165AImprove protectionSolve the problem of entity camouflageData switching networksPlaintextImpersonation attack
An aircraft communication addressing and reporting system (ACARS) data chain belongs to a wireless network, and compared with a wired network, the ACARS data chain is easily attacked. ACARS information is completely transmitted in a plaintext mode, and safety is insufficient. The invention provides a safety penetration testing method of the ACARS data chain. Entity impersonation attack is imitated mainly according to security holes existing in the ACARS data chain. In an ACARS system, an entity is easily disguised as a digital signal processor (DSP) terminal, space communication is destroyed, and normal operation of the ACARS system is blocked, and major accidents such as an aircraft crash are even caused. According to the safety penetration testing method of the ACARS data chain, a computer is disguised as a DSP through simple assembly, and sends an illegal control message to an aircraft in the air, a skyborne terminal can not detect legality of the illegal control message, and thus the illegal control message is responded. According to the technical scheme, safety loopholes of the ACARS data chain can be found out, and the safety penetration testing method of the ACARS data chain plays an active part in protection of safety of the ACARS data chain.
Owner:CIVIL AVIATION UNIV OF CHINA
Intra-domain mapping updating authenticating method in identity and position separation network
InactiveCN104270756AGuaranteed confidentialityTransmissionSecurity arrangementMan-in-the-middle attackComputer network
The invention discloses an intra-domain mapping updating authenticating method in an identity and position separation network, and relates to the technical field of communication route or path selection. The method comprises the following steps: (1) constructing an intra-domain mapping updating authenticating model in the identity and position separation network; (2) performing registering; (3) carrying out an intra-domain mapping updating authenticating process in the identity and position separation network. According to the method, replay attack, man-in-the-middle attack, impersonation attack and the like can be effectively resisted, and the confidentiality of a mapping updating message is effectively guaranteed.
Owner:SHIJIAZHUANG TIEDAO UNIV
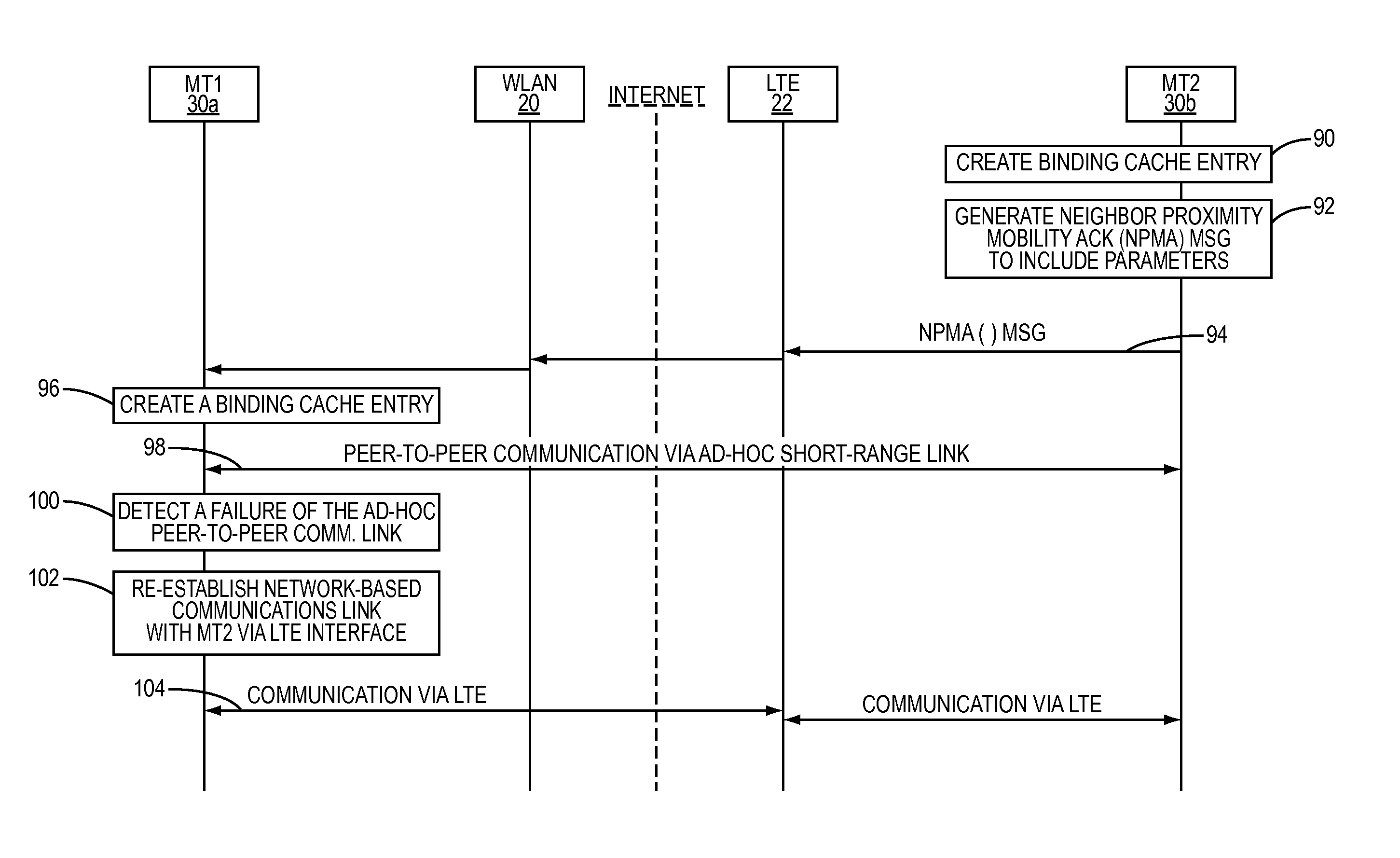
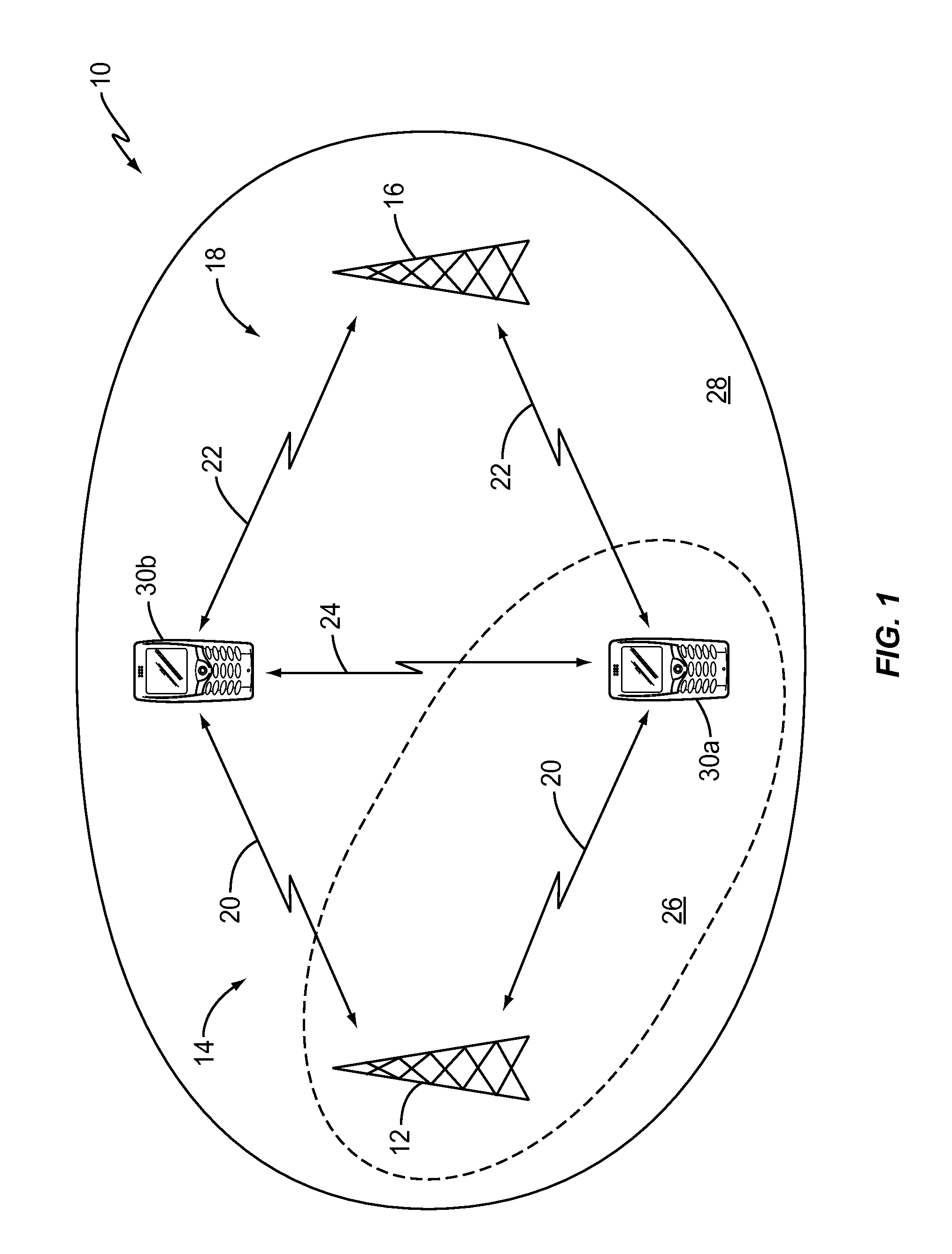
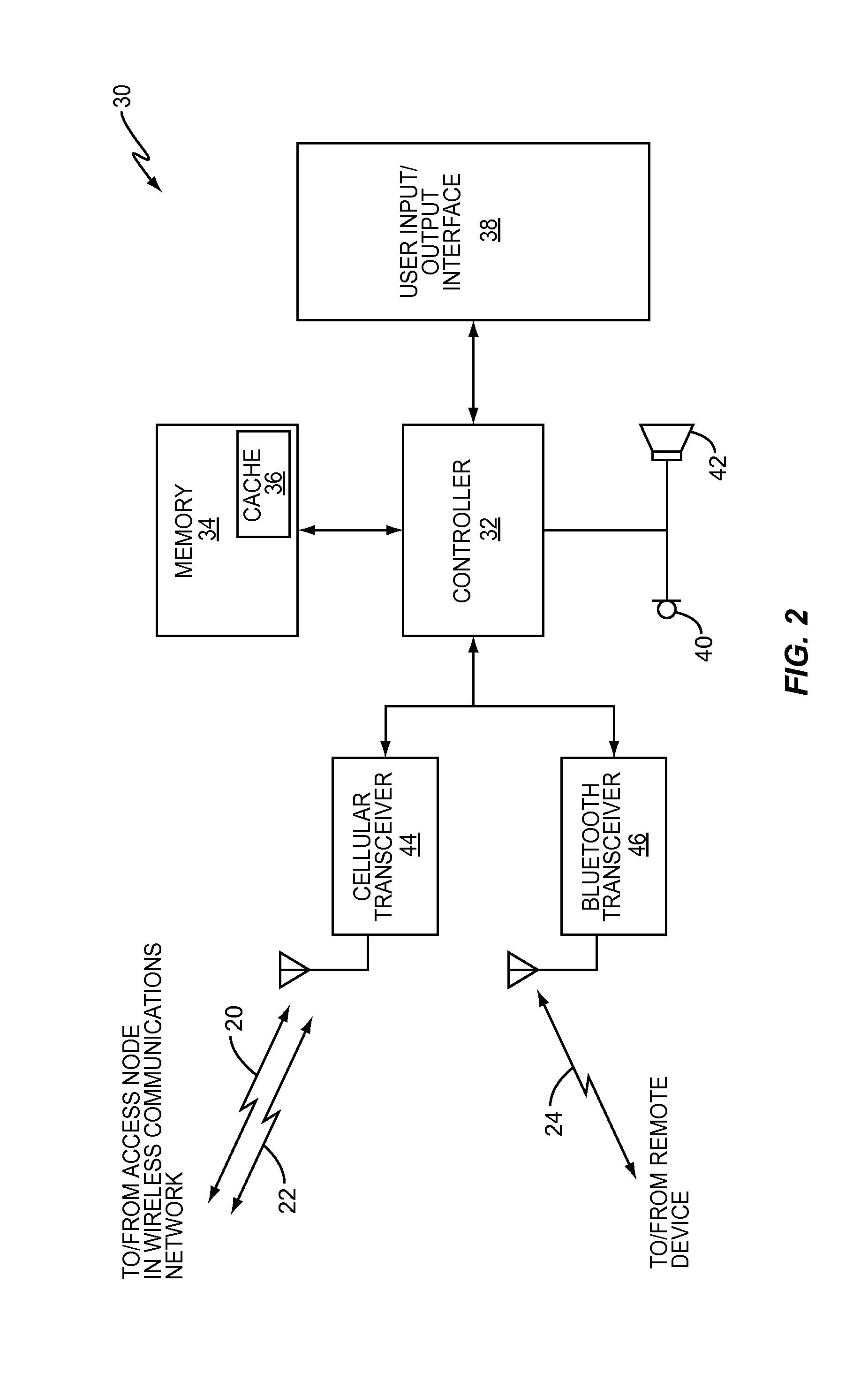
Enabling IPv6 mobility with sensing features for AD-HOC networks derived from long term evolution networks
InactiveUS8385269B2Avoid the build processNetwork topologiesTime-division multiplexThird partyTelecommunications
A wireless communication device includes a plurality of different wireless interfaces to facilitate communications with a remote device over a corresponding plurality of networks. The device can switch between the different interfaces to migrate an on-going communications session from one that requires the infrastructure of a fixed wireless communication network to one that does not require the infrastructure of a fixed wireless communication network. Switching between the various interfaces allows the migration to occur while protecting the device against malicious third-party impersonation attacks.
Owner:TELEFON AB LM ERICSSON (PUBL)
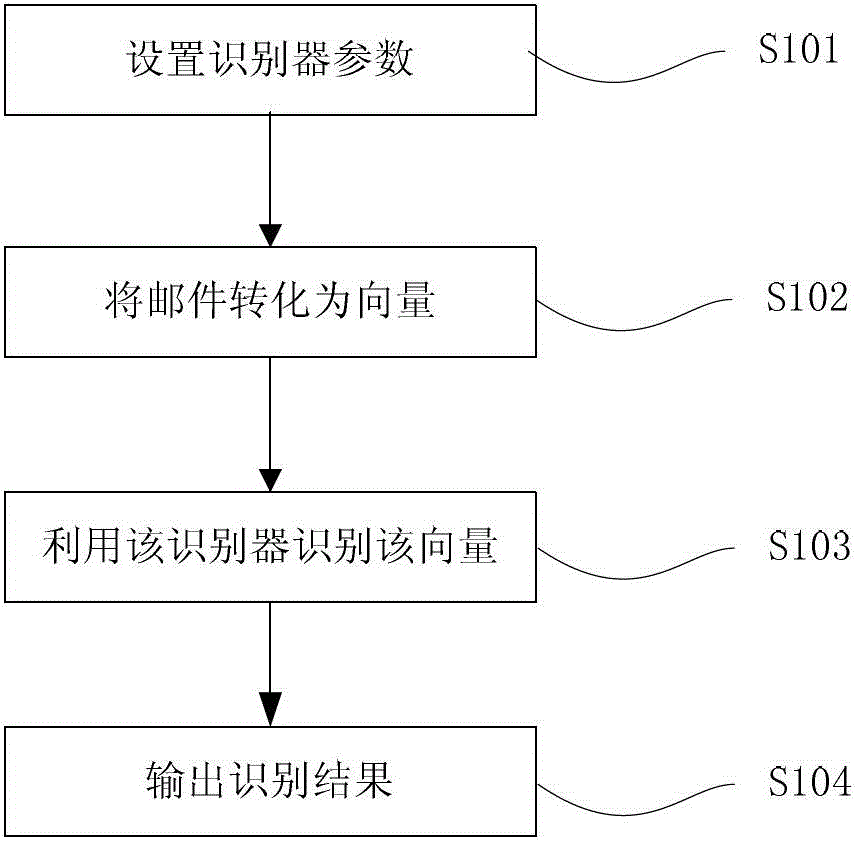
Identification method and system for junk mail
ActiveCN102984176ARealize intelligent identificationRecognition stabilityData switching networksRecognition algorithmData mining
The invention discloses an identification method and a system for a junk mail. The identification method and the system overcome a deficiency that in the prior art, when more keywords are modified in the junk mail, the performance of a standard identification algorithm such as a support vector machine algorithm is degraded more rapidly. The method comprises the steps of setting parameters of an identifier, converting the mail into a vector, identifying the mail with the identifier, and outputting an identification result. The method and the system can realize intelligent identification of the junk mail resisting impersonation attacks, and achieve a technological effect of more stable identification performance.
Owner:CHONGQING UNIV
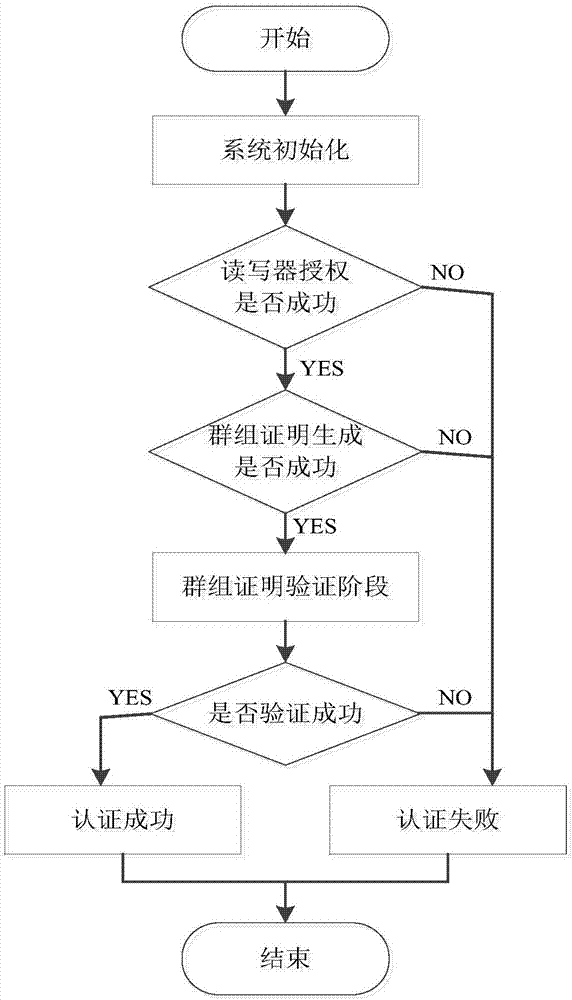
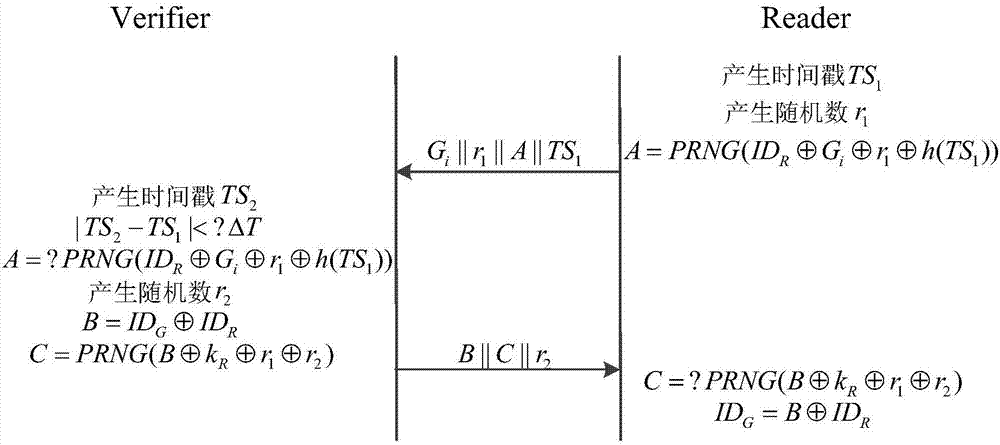
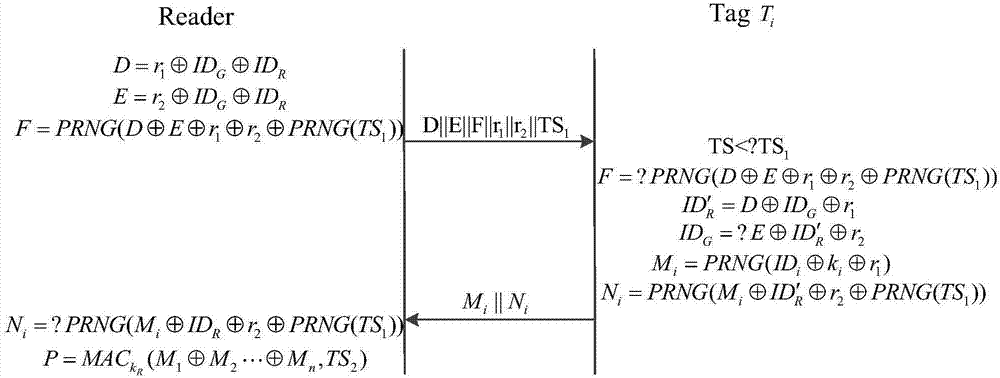
Method for verifying RFID label group
The invention discloses a method for verifying an RFID label group, wherein the method relates to the technical field of Internet-of-things safe communication. An entity of the method comprises a verifier, reader-writer and multiple labels. In each group proving and authentication process, the reader-writer firstly acquires authorization and then broadcasts a message to a label in an anonymous packaging manner; and after label receives the message, the label verifies validity of the reader-writer and transmits the sensitive message to the reader-writer in a ciphertext manner. After the reader-writer receives the message of the group label, the reader-writer generates a group identification and transmits to the verifier for verification by the verifier. In the verification process, exchange and transmission between the entities are realized through the encrypted message. The method comprises the steps of authorization, challenge, response, calculation, matching, etc. According to the method, by means of group identity identification sharing technology, not only is expandability problem settled, but also independence of a label reading sequence is realized. Playback attack, impersonation attack and the like are resisted through a time sequence manner. Furthermore the message is transmitted between the entities in the ciphertext manner, thereby improving privacy protection for the sensitive message.
Owner:JIANGNAN UNIV
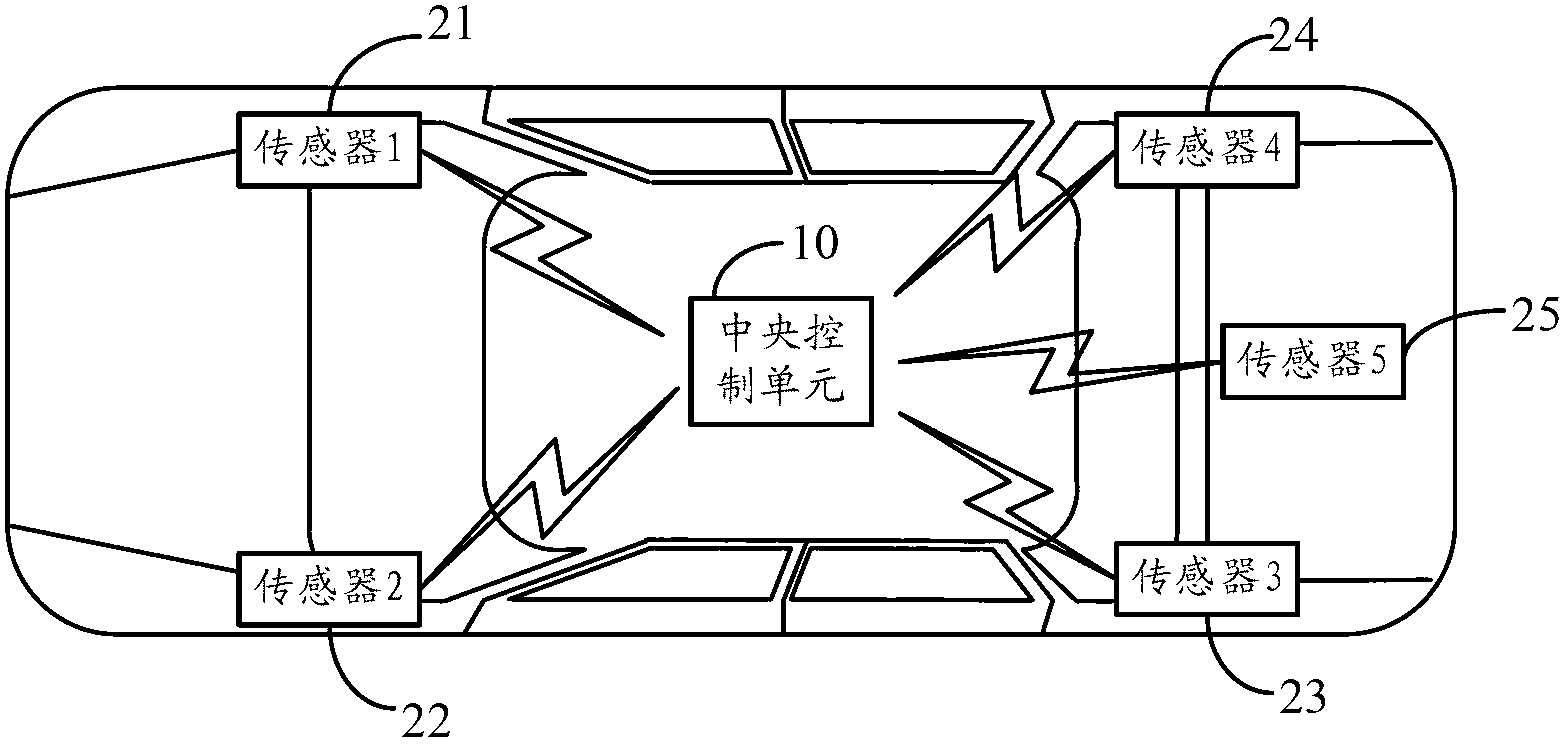
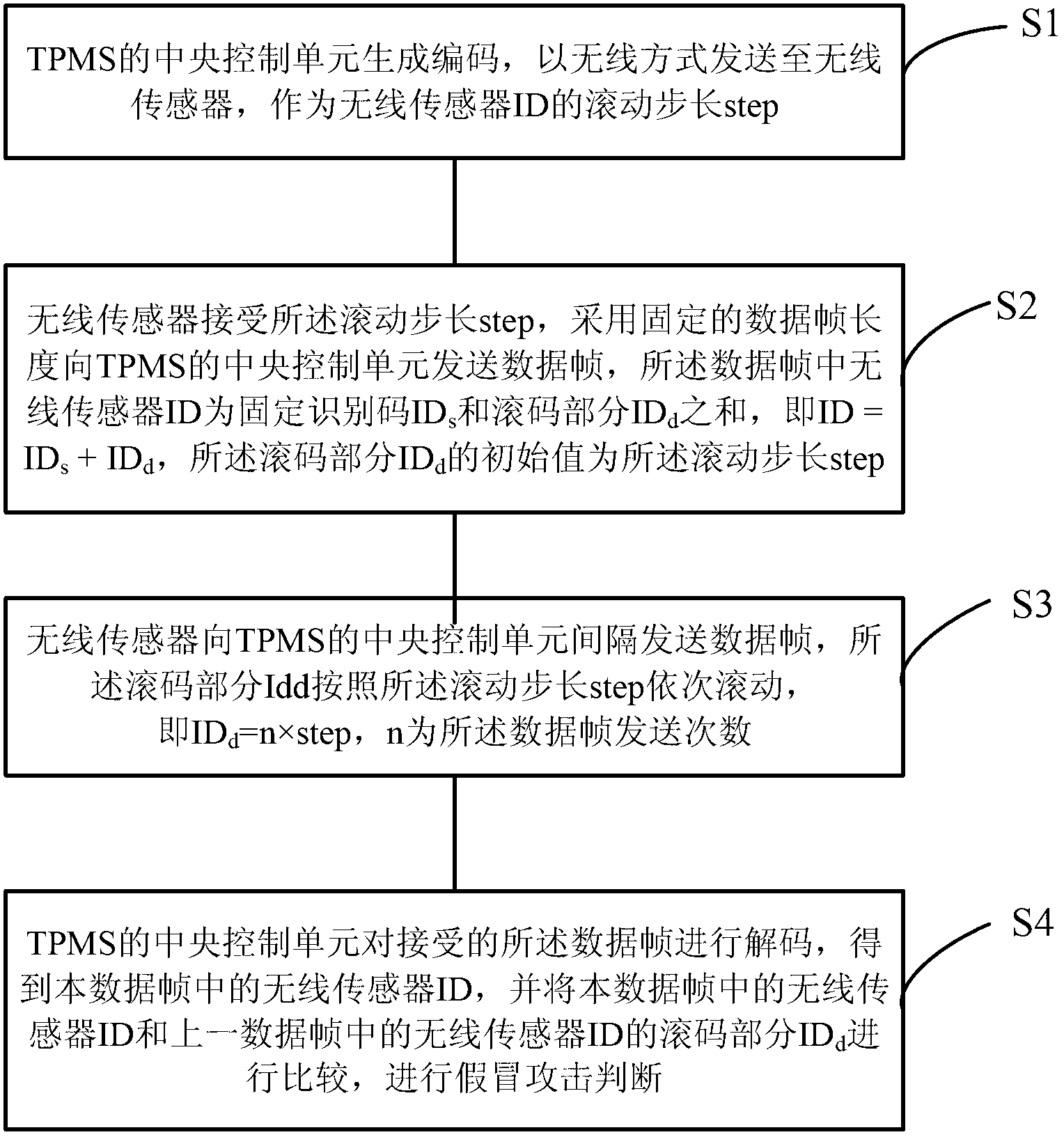
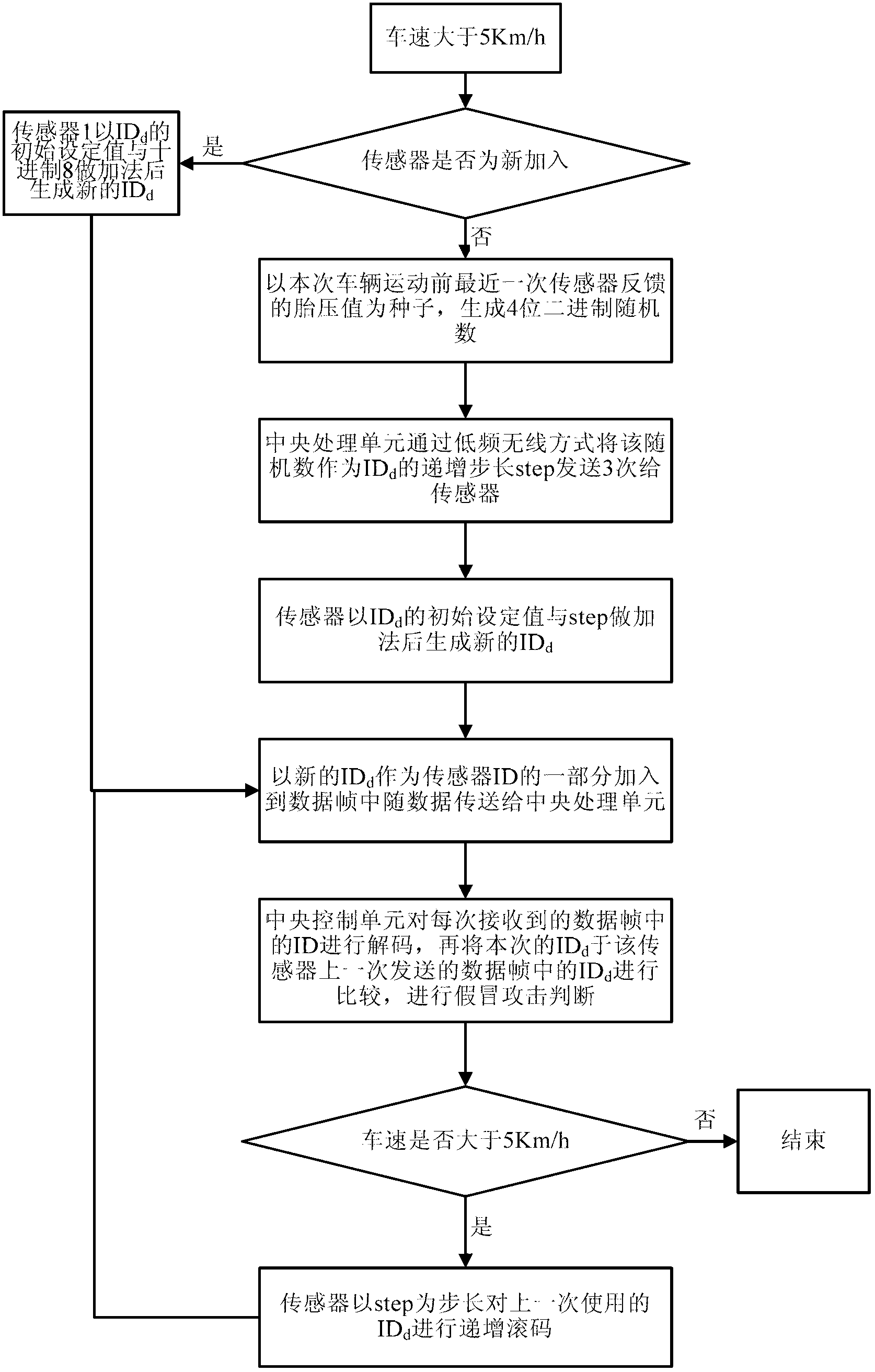
Tire pressure monitoring method and system based on wireless sensor
InactiveCN102700368AResist impersonation attacksImprove reliabilityTyre measurementsLine sensorTire-pressure monitoring system
The invention provides a tire pressure monitoring method and system based on a wireless sensor, wherein the tire pressure monitoring method comprises the following steps of: generating a code by a central control unit of the TPMS (Tire Pressure Monitoring System), and sending the code into the wireless sensor in a wireless way; receiving a rolling step by the wireless sensor, and sending a data frame to the central control unit of the TPMS by adopting a fixed data frame length; sending the data frame to the central control unit of the TPMS by the wireless sensor; decoding the data frame received by the central control unit of the TPMS to obtain the wireless sensor ID in the data frame, and judging an impersonation attack. The static ID in the data frame sent by the sensor of the TPMS is changed to be changeable in a dynamic rolling code way under the condition that the hardware cost is not increased, and the rolling step is a random number generated by taking the former tire pressure data as a seed, so that the impersonation attack of external malicious equipment to the TPMS is effectively resisted, and the reliability in the operation of the TPMS is improved.
Owner:JIANGSU UNIV
Mapping updating authentication method among credible regions in separation mechanism networks
ActiveCN103139218AIntegrity guaranteedGuaranteed credibilityUser identity/authority verificationConfidentialityTrusted Computing
The invention discloses a mapping updating authentication method among credible regions in separation mechanism networks, and belongs to the technical field of computer safety. By means of credible computing technology, the mapping updating authentication method not only can verify the identity of a mapping server, but also guarantees integrity of a mapping server platform and credibility of the identity of the platform, and effectively guarantees safety during mapping updating processes. The mapping updating authentication method comprehensively utilizes dependable computing, encryption, signature and other information security technology, guarantees the integrity of the mapping server platform, the credibility of the identity of the mapping server platform, and confidentiality of a mapping relation, and can effectively prevent replay attack, forgery attack and impersonation attack.
Owner:SHIJIAZHUANG TIEDAO UNIV
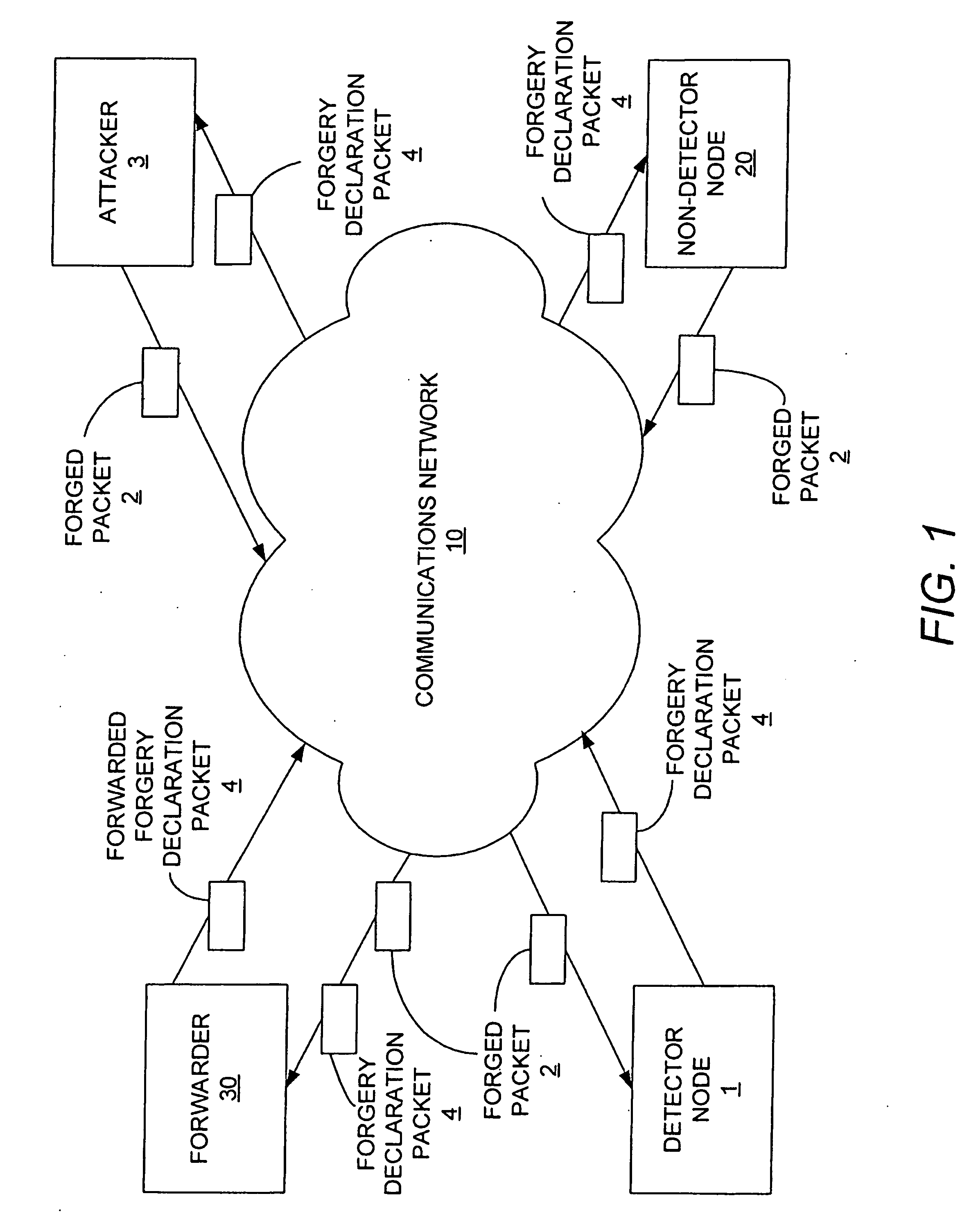
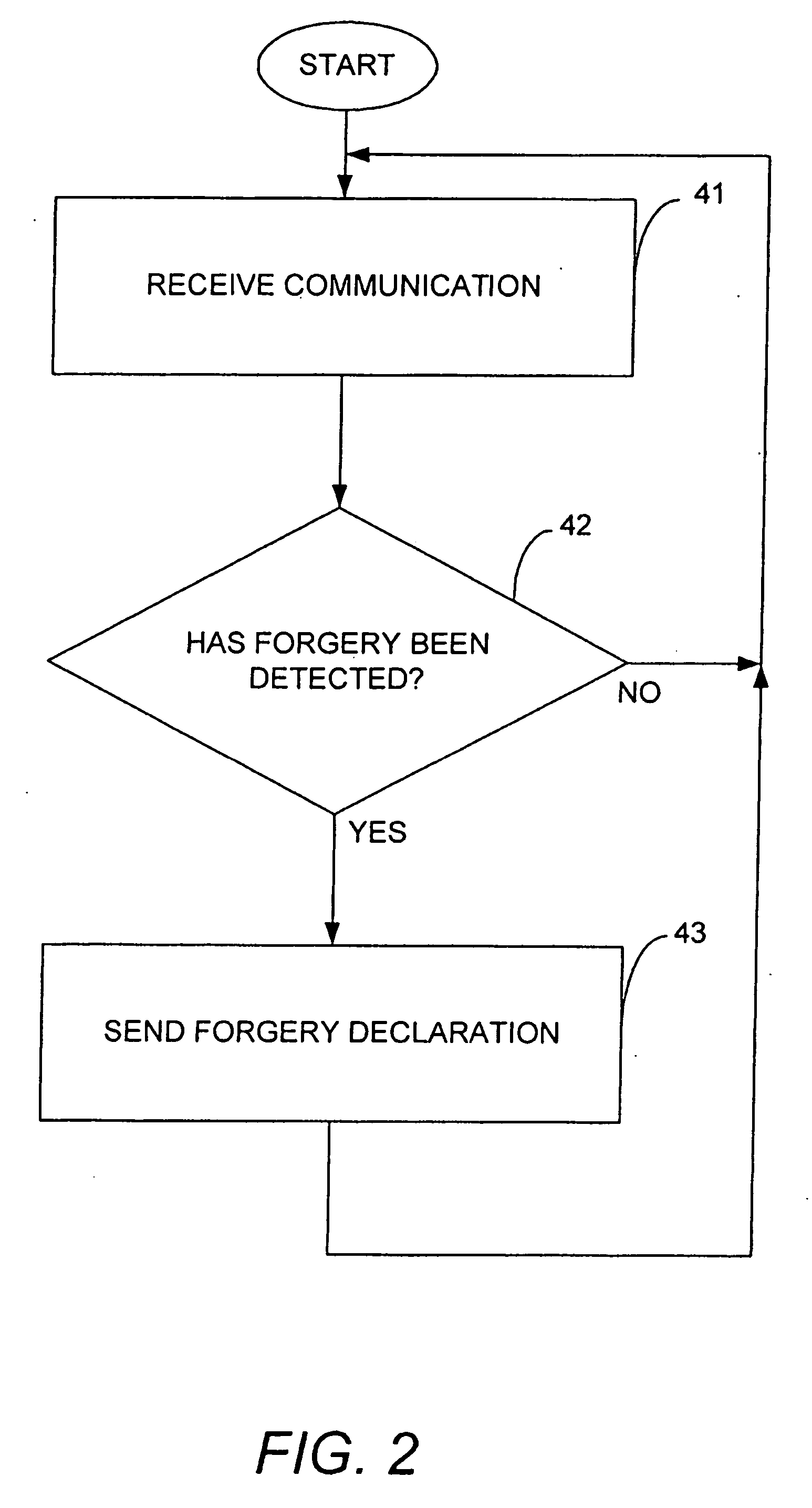
Methods, apparatuses and computer programs for protecting networks against attacks that use forged messages
Methods, apparatuses and computer programs for protecting a network against forged messages, or impersonation attacks, which do not require the use cryptography. One or more nodes on the network are configured to detect a forged message and to output an indication that a forged message has been detected. Nodes that receive an indication that a forged message has been detected may then take certain actions, such as, for example, discontinuing use of the protocol associated with the forged message for a period of time.
Owner:GENERAL INSTR CORP
Data connection method, system and device
The invention provides a data connection method. The method comprises the following steps: an authentication access gateway acquires a data connection message sent by terminal equipment and then judges whether the terminal equipment is successfully authenticated; the authentication access gateway correspondingly processes the data connection message according to the judgment result, and then sends the processed data connection message to an authorization control gateway; and the authorization control gateway judges whether sending the data connection message to a server according to an authorization policy corresponding to the terminal equipment. According to the above scheme, through the complete separation of authentication and authorization, a more effective and secure network access control and authorization method is provided, and meanwhile, impersonation attacks of IP addresses can be effectively prevented.
Owner:BEIJING LEADSEC TECH +1
Automatic repeat-request system for providing absolute safety and authentication in wireless networks
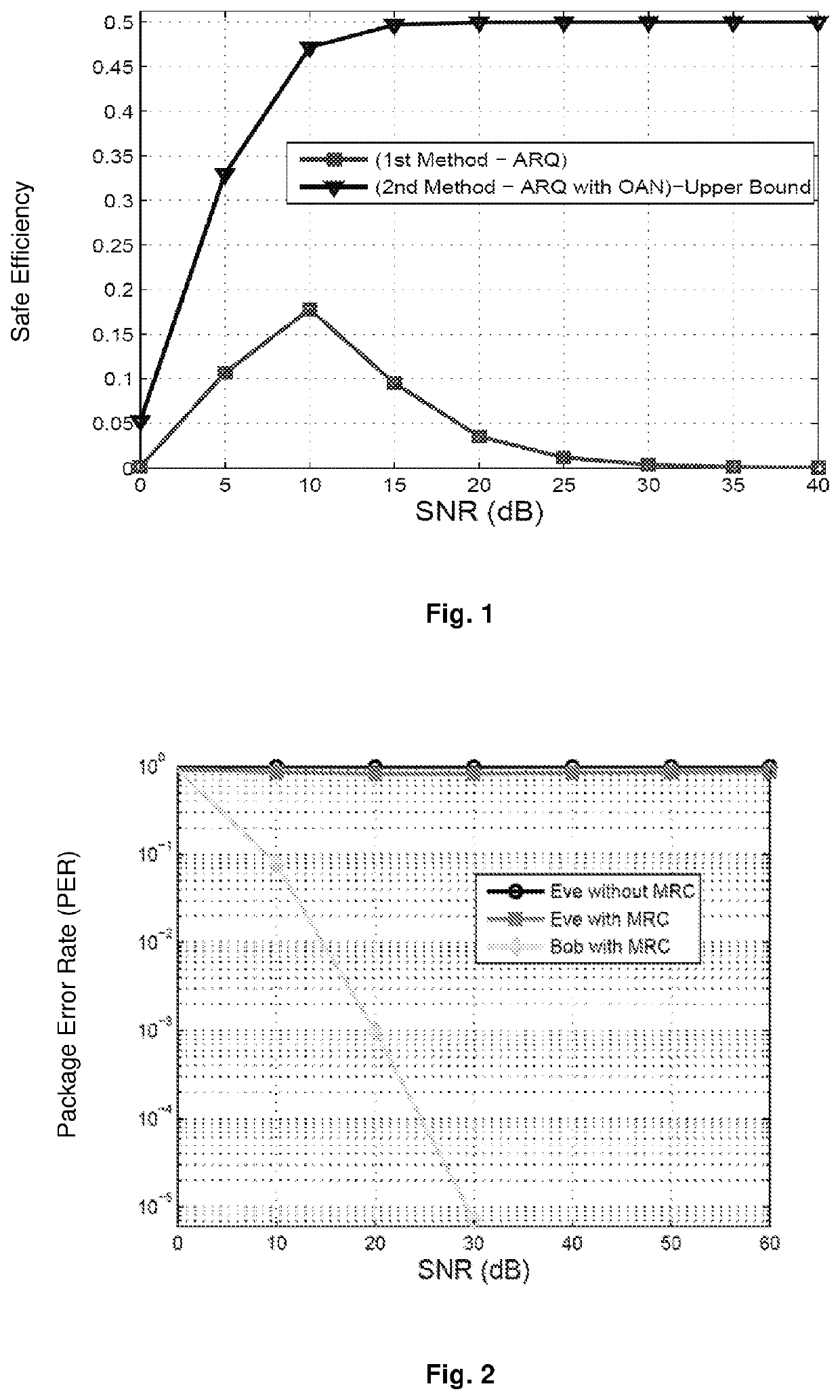
ActiveUS20210203433A1Significant comprehensive benefitsImprove operating conditionsError prevention/detection by using return channelKey distribution for secure communicationData packCommunications system
A system and method for providing confidentiality against eavesdropping and authentication against impersonation attacks for advanced wireless communication systems are disclosed. The method exploits ARQ as a MAC layer mechanism and artificial noise as a physical layer mechanism with maximal ratio combining to achieve secrecy. An artificial noise, not requiring class space in the channel, is designed and added to the data package based on the QoS requirements and channel condition between legitimate parties. Basically, a special AN, which does not require null-space in the channel, is designed based on the QoS requirements and the channel condition between the legitimate parties and injected to the data packet. If the same packet is requested by the legitimate receiver (Bob), an AN cancelling signal is designed and added to the next packet. Then, an AN-free packet is obtained by using MRC process at Bob, while deteriorating the eavesdropper's performance
Owner:T C ISTANBUL MEDIPOL UNIVERSITESI
Data transmission method, device and system thereof
ActiveCN104283667AAvoid Phishing AttacksGuaranteed distribution of public parametersData switching by path configurationSecuring communicationCiphertextKey generator
The invention discloses a data transmission method, a device and a system thereof, wherein the data transmission method for a node comprises the steps of: generating a first cryptograph through a communication request of a first secret key encryption node and a private key generator, wherein the first secret key is a symmetrical secret key which is distributed by a secret key distribution center to the node; transmitting the first cryptograph to the secret key distribution center; receiving and using the first secret key for decrypting a second cryptograph which returns from the secret key distribution center, obtaining the secret key of a session at this time and a third cryptograph; forwarding the third cryptograph to the private key generator; and receiving and using the secret key of the session at this time for decrypting a fourth cryptograph which is transmitted by the private key generator and is encrypted by the secret key at this time, and obtaining a public parameter and the private key. According to the data transmission method, the node uses the secret key distribution center for communicating with the private key generator through one-time session keys which are distributed according to different symmetrical keys as nodes, thereby effectively preventing impersonation attacks to the node, and simultaneously ensuring high safety in distributing a public parameter and a private key of the node by a private key server.
Owner:CHINA MOBILE GRP HEILONGJIANG CO LTD
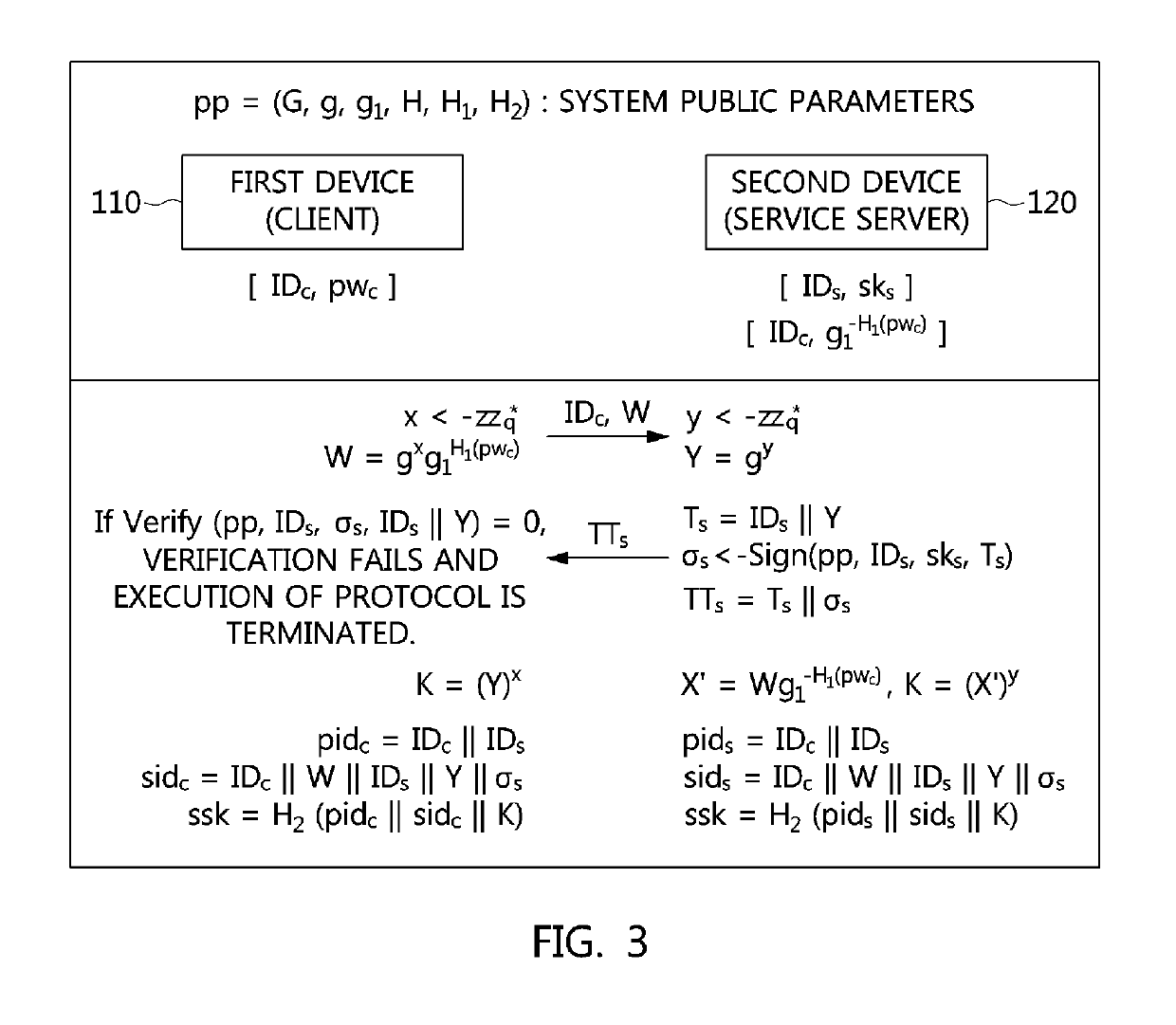
Method and apparatus for authenticated key exchange using password and identity-based signature
ActiveUS10263969B2Authentication is convenientEasy to useMultiple keys/algorithms usagePublic key for secure communicationPasswordImpersonation attack
Disclosed herein are an apparatus and method for authenticated key exchange using a password and an identity-based signature, by which robustness is provided in order to prevent a server impersonation attack when a password is exposed, and by which a client may be provided with convenient authentication using an ID and a password.
Owner:ELECTRONICS & TELECOMM RES INST
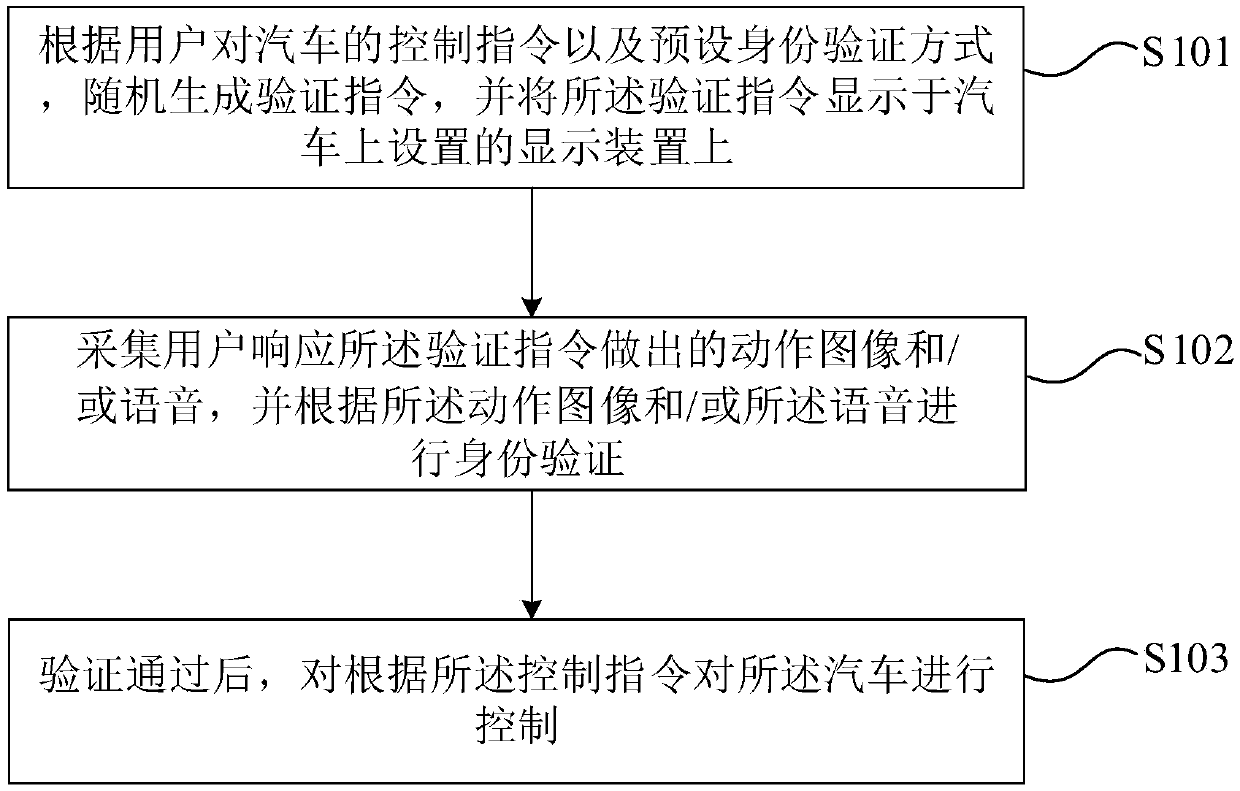
Vehicle control method, device and equipment and storage medium
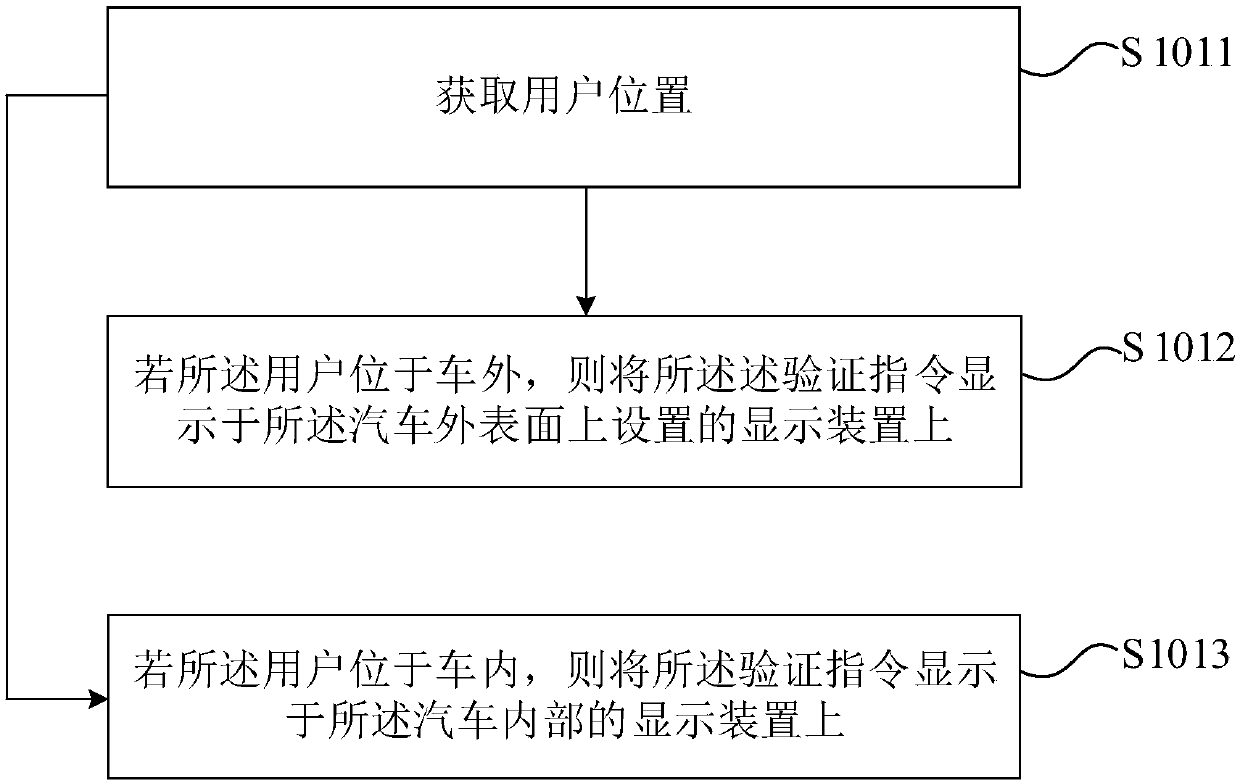
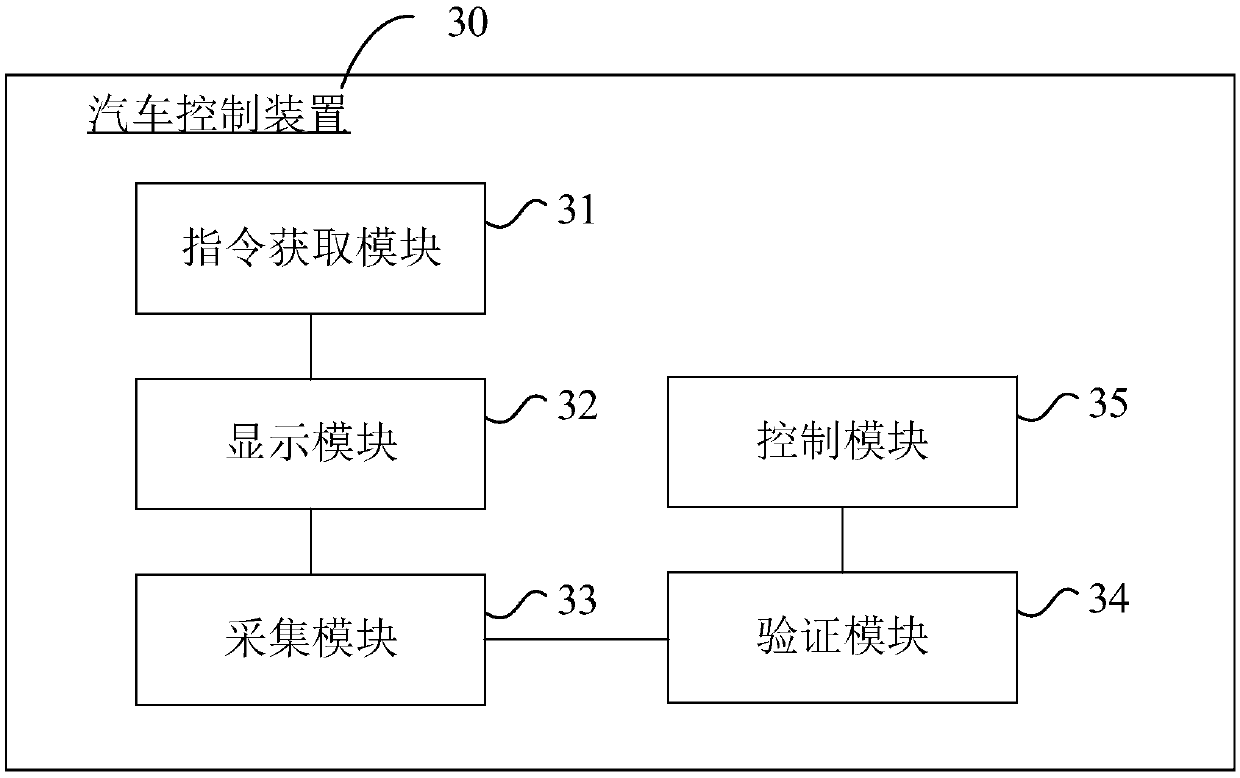
ActiveCN109624925AImprove reliabilityImprove securityAnti-theft devicesDisplay deviceImpersonation attack
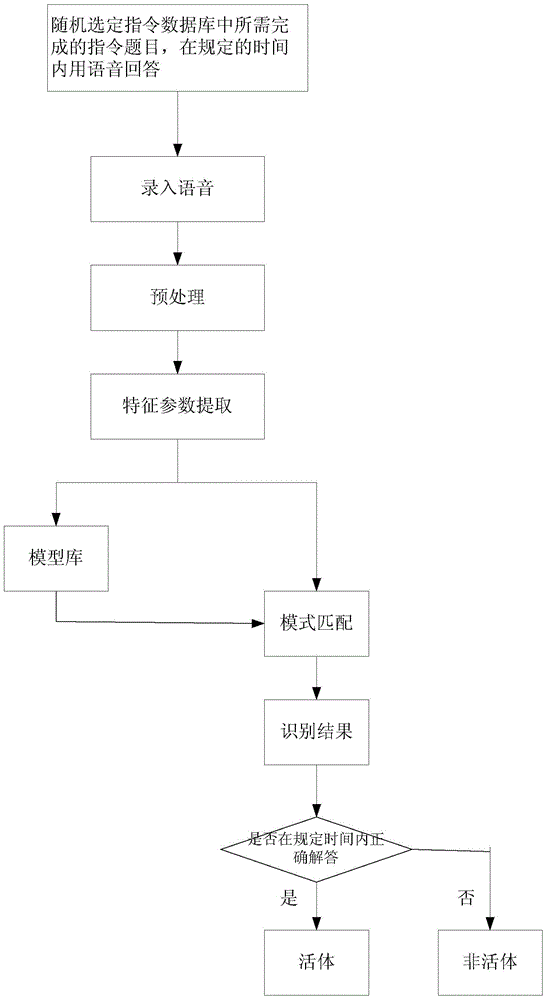
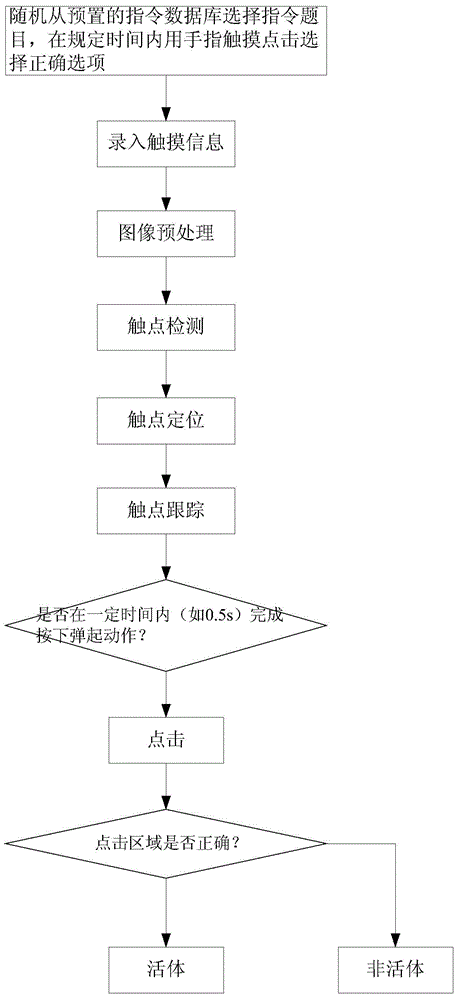
The invention provides a vehicle control method, device and equipment and a storage medium. According to the method, according to a control instruction of a user on a vehicle and a preset identity verification mode, a verification instruction is randomly generated and displayed on a display device arranged on the vehicle; then motion images and / or voice generated by the user in response to the verification instruction are collected, and identity verification is conducted according to the motion images and / or voice; after verification is successful, the vehicle is controlled according to the control instruction. By means of the vehicle control method, by randomly generating the verification instruction, the impersonation attack precaution capability in the identity verification process of the vehicle control process is improved, and the reliability and safety of identity verification are improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com