Data transmission method, device and system thereof
A data transmission method and a technology for disclosing parameters, which are applied in the field of devices and systems, and data transmission methods, can solve the problems of limited ability to resist man-in-the-middle attacks, do not support identity authentication of neighbor nodes, and cannot resist impersonation attacks, etc., to avoid counterfeiting attacks, Avoid node spoofing attacks and ensure the effect of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
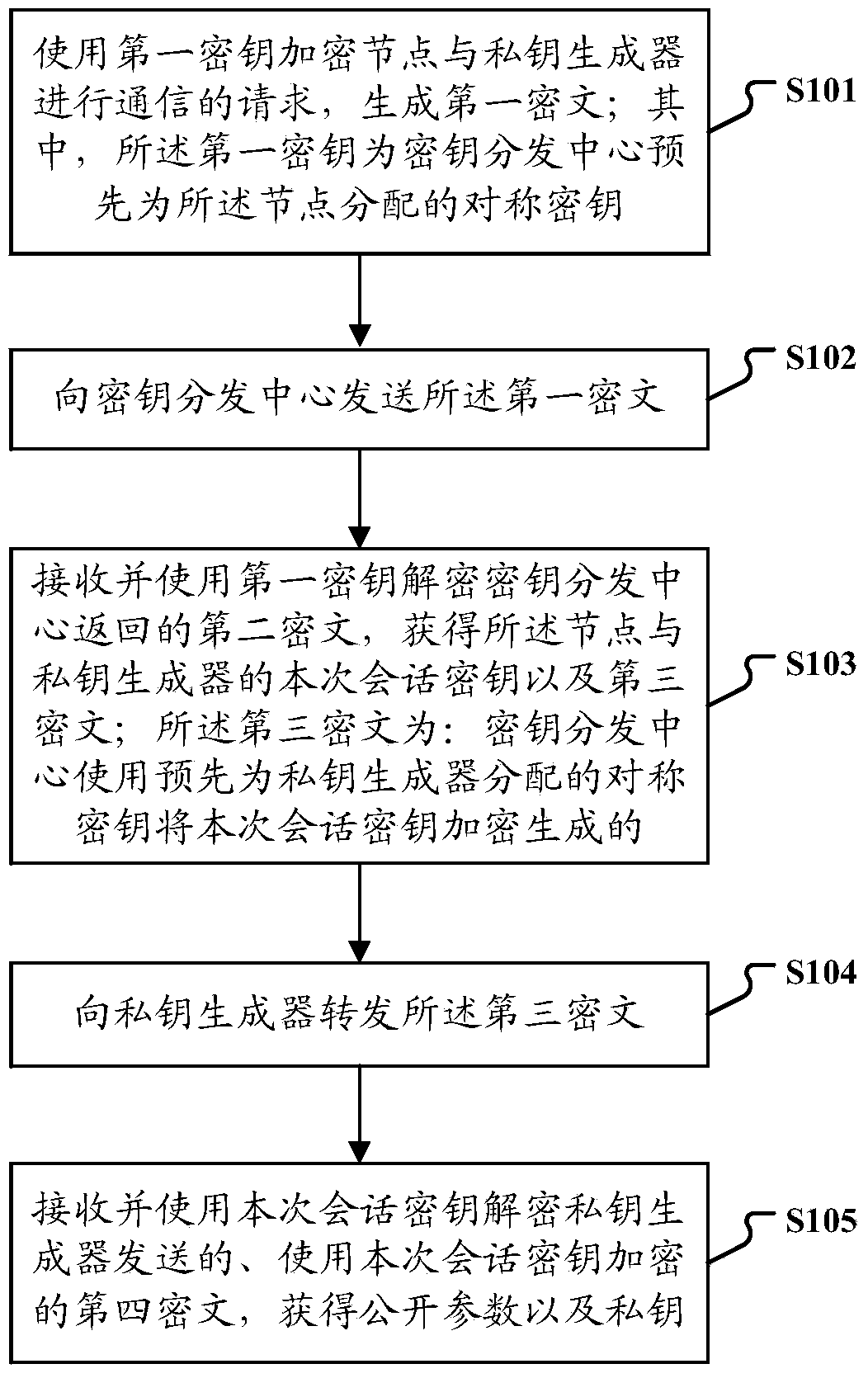
[0083] Such as figure 1 As shown, a data transmission method for a node proposed by an embodiment of the present invention includes the following steps:
[0084] Step S101: use the first key to encrypt the request of the node to communicate with the private key generator, and generate a first ciphertext; wherein, the first key is a symmetric key previously assigned to the node by the key distribution center;
[0085] Step S102: sending the first ciphertext to the key distribution center;
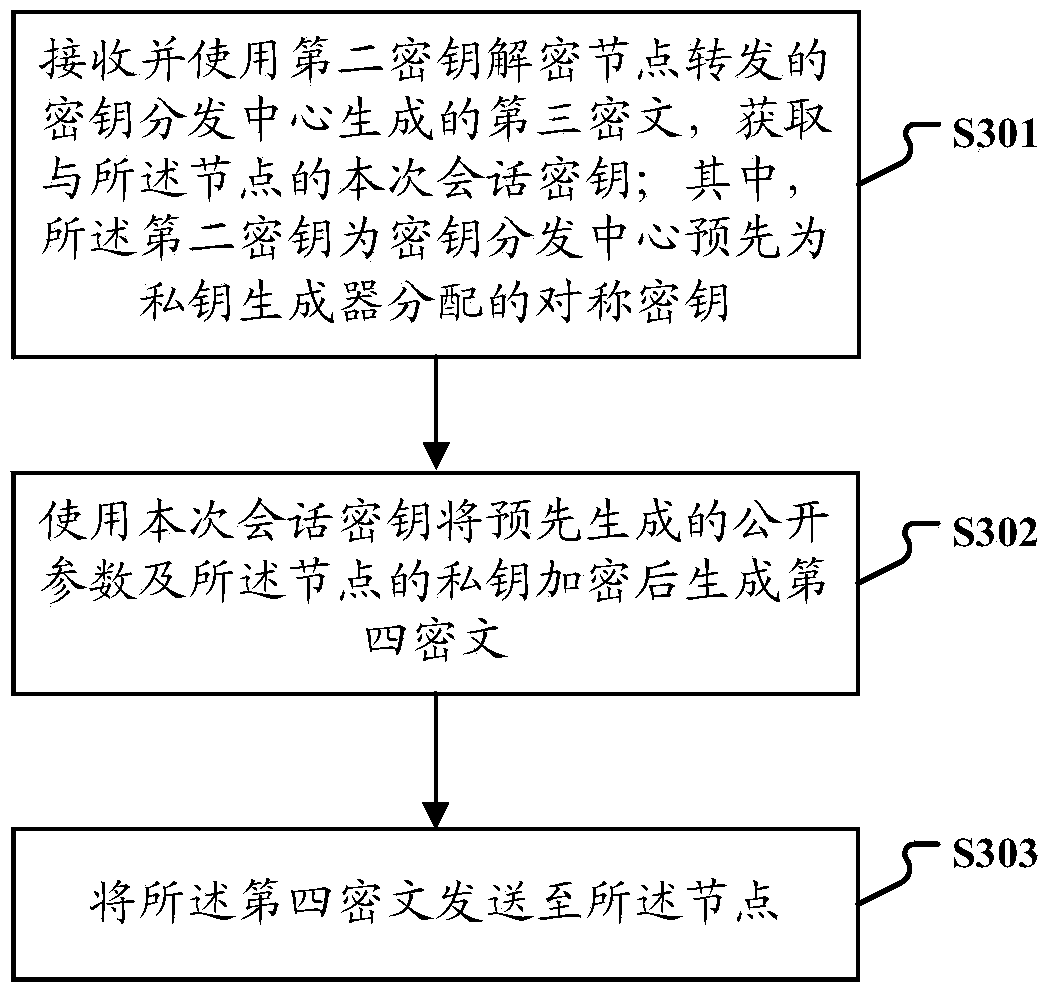
[0086] Step S103: Receive and use the first key to decrypt the second ciphertext returned by the key distribution center, and obtain the current session key between the node and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com