Identification method and system for junk mail
A spam and identification method technology, applied in the field of communication, can solve problems such as performance degradation, and achieve the effect of stable identification performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the purpose, technical solution, and advantages of the present invention clearer, the specific implementation examples of a service function authorization method and system involved in the present invention will be further described in detail below with reference to the accompanying drawings.
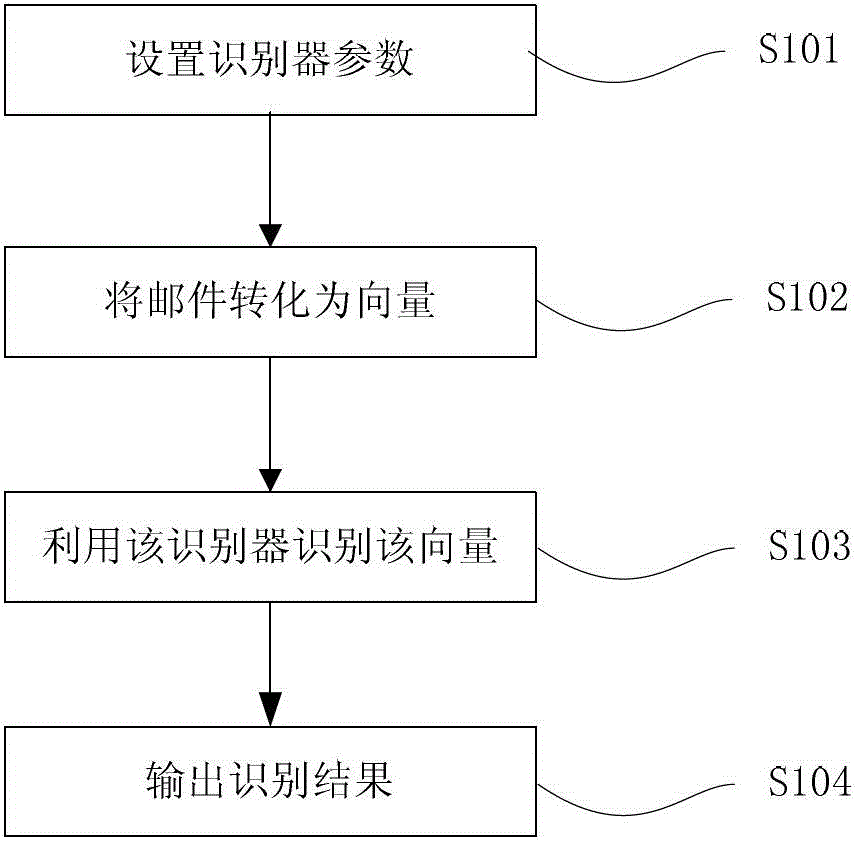
[0042] refer to figure 1 , the method flowchart of a preferred embodiment of the present invention,
[0043] Step S101, setting recognizer parameters,
[0044] Step S102, converting the email into a vector,
[0045] Step S103, using the identifier to identify the mail,
[0046] Step S104, outputting the recognition result.
[0047] In the present invention, a mail document is expressed as a vector x=[f 1 ,..., f d ]. First collect all the words that appear in the mail database and compile them into a general dictionary. Then sort by the frequency of a specific word in spam, select d + words into the representation dictionary; similarly, sort according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com