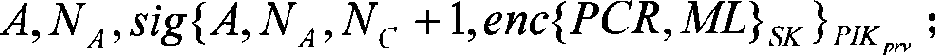Remote proving method in trusted computation environment
A remote certification and trusted computing technology, applied in computing, computer security devices, internal/peripheral computer component protection, etc., can solve the lack of replay attack, counterfeit attack man-in-the-middle attack prevention capabilities, lack of consistency and reliability in measurement and proof Issues such as scalability, inability to guarantee the authenticity of the integrity measurement value, platform privacy, etc., to achieve the effect of preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in detail below through specific embodiments and accompanying drawings.
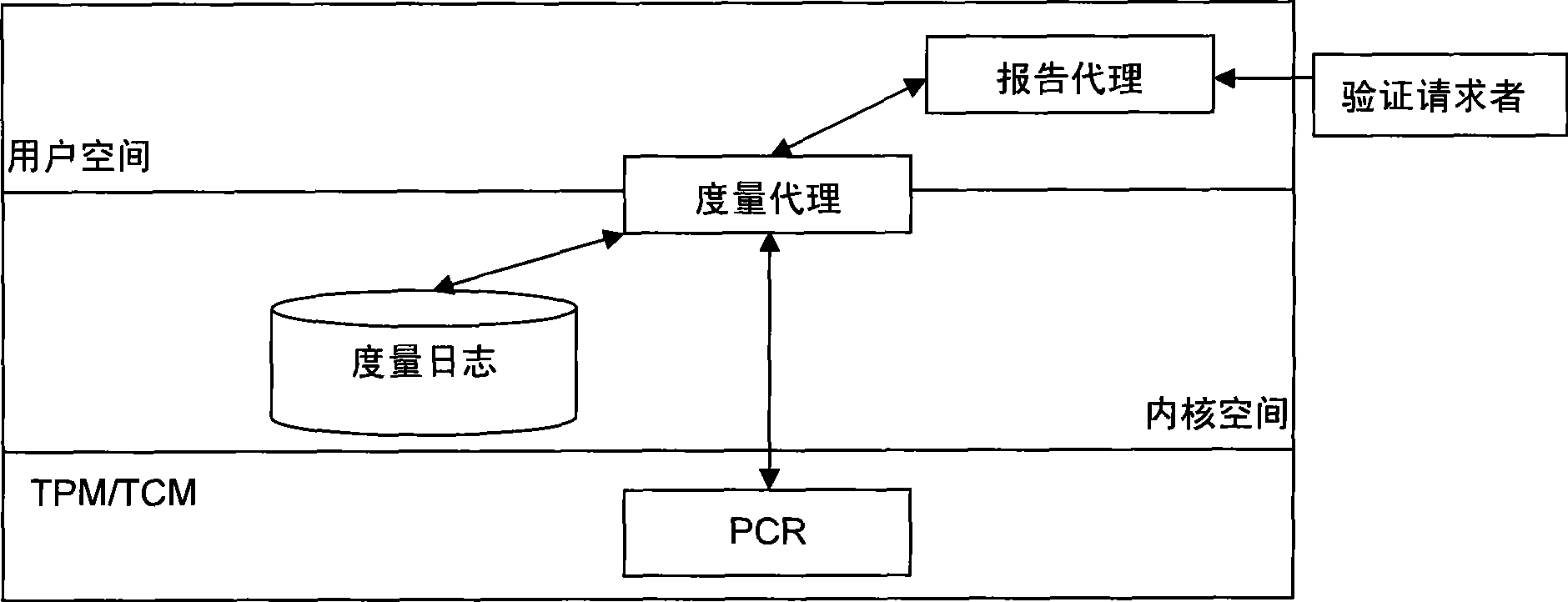
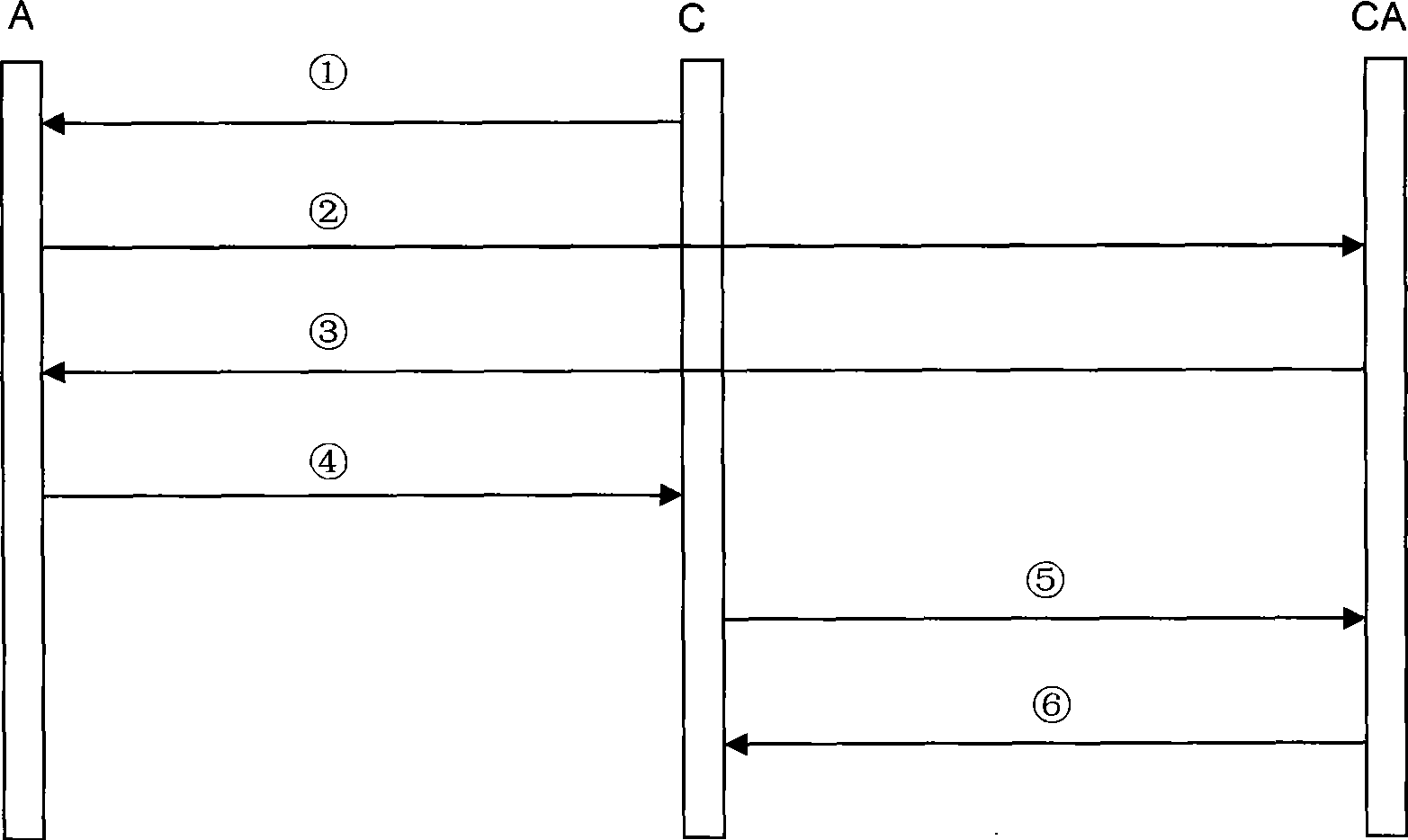
[0038] The present invention is a method for remote certification in a trusted computing environment. It uses a security chip TPM / TCM to generate a session encryption key by using the unanticipated time stamp generated by the verified trusted platform and the verification requester. The integrity measurement value and measurement log of the trusted platform are encrypted, and the identity, unpredictable time stamp, and encryption result are digitally signed to ensure the authenticity of the integrity measurement value and measurement log of the verified trusted platform and the privacy of the platform Through the measurement log, the verification requester reconstructs the integrity measurement process of the verified trusted platform, calculates and compares the integrity measurement value, and realizes the remote proof of the verified trusted platform.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com