Method for resisting simulated main customer attack in cognitive radio
A cognitive radio, primary user technology, applied in wireless communication, electrical components, connection management, etc., can solve problems such as negative network impact
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
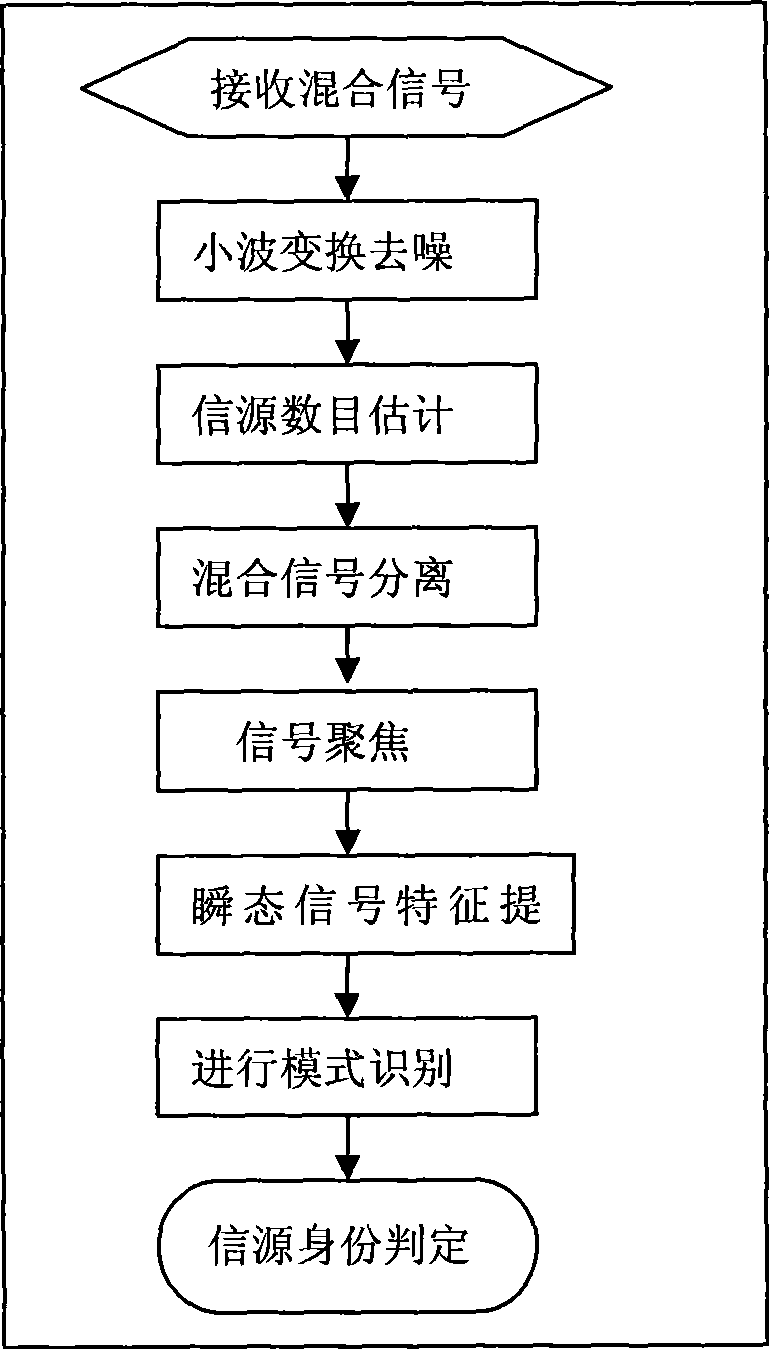
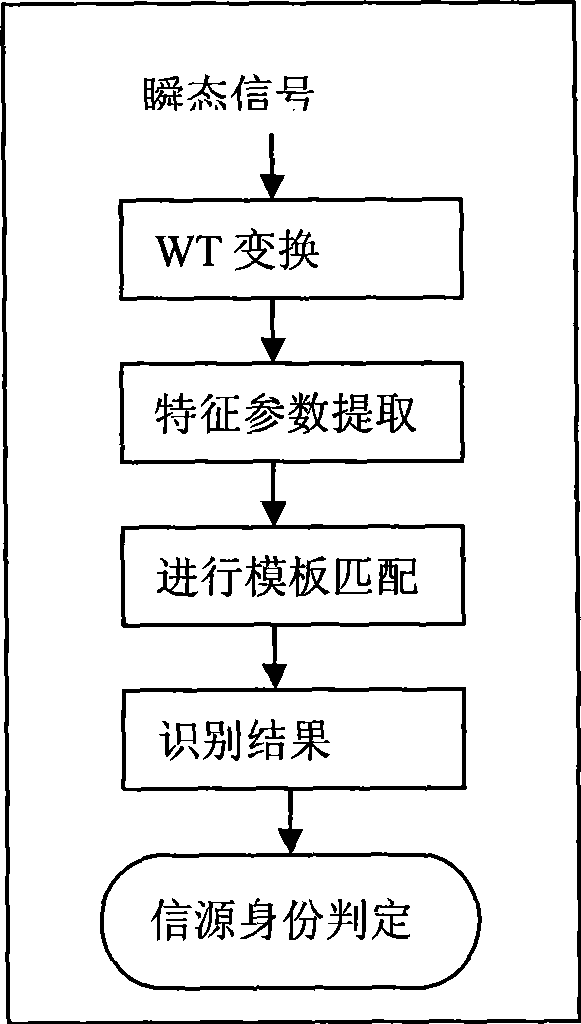
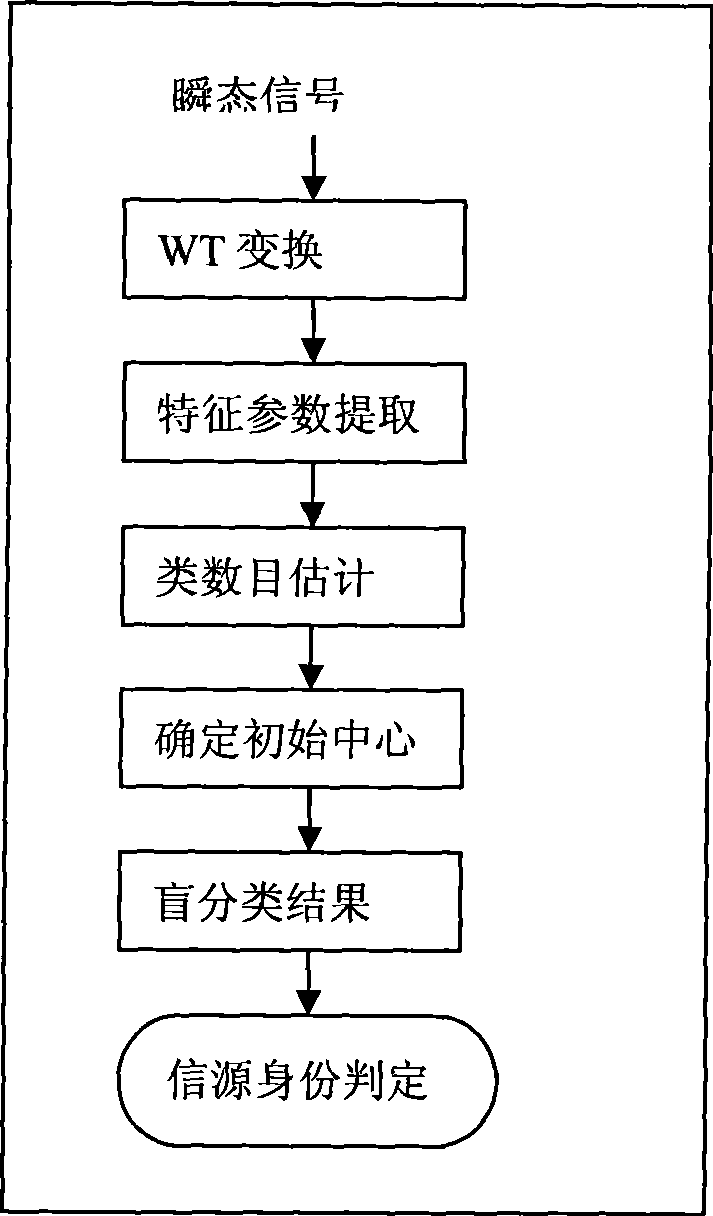
[0054] The realization of the present invention's anti-imitation master user attack, as attached figure 1 As shown, consider a cognitive radio system consisting of M primary users and N cognitive users, each cognitive user can perform spectrum sensing independently, and consider that cognitive user terminals can continuously sense the surrounding radio environment and receive Transient signals generated at the moment of power-on of each radio station. Cognitive users use an array antenna with the number of array elements p, and the number of mixed signals perceived by a cognitive user at a certain moment includes primary user signals and non-primary user signals is tentatively set to q (due to the uncertainty of the primary user q is a random number). The signal source identification method realized by the present invention is divided into the following steps:
[0055] Step 1: Perform noise reduction processing on the mixed signal received in the spectrum sensing process.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com