Data connection method, system and device
A connection method and data technology, applied in the field of communication, can solve problems such as excessive time and resources, increased deployment work, lack of access authentication and filtering, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
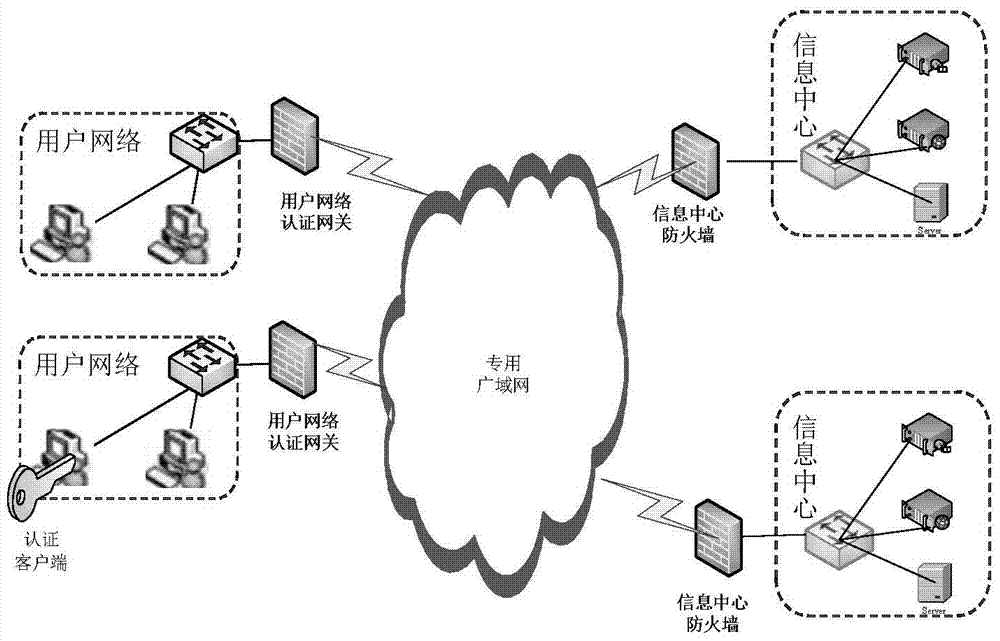
[0115] Such as Figure 5 As shown, this embodiment provides a data connection method, the method comprising:
[0116] Step S11: After the authentication access gateway obtains the data connection message sent by the terminal device, it judges whether the terminal device passes the authentication;
[0117] Step S12: The authentication access gateway performs corresponding processing on the data connection message according to the judgment result, and then sends the processed data connection message to the authorization control gateway;
[0118] Step S13: The authorization control gateway judges whether to send the data connection message to the server according to the authorization policy corresponding to the terminal device.
[0119] Optionally, also include:
[0120] Step S14: After the authentication access gateway receives the authentication information and identity sent by the authentication client on the terminal device, the authentication access gateway verifies the au...
Embodiment 2
[0142] The technical solution of the present invention is further described below.
[0143] 1. Certification process
[0144] 1. The user starts the authentication client, inserts the certificate or enters the account password, and the authentication client requests the authentication access gateway to establish a connection;
[0145] If the user inserts a certificate, submit the ID and certificate information to the authentication access gateway, and if the user enters the account password, submit the ID to the authentication access gateway. Usually the ID is a 4-byte or 8-byte integer.
[0146] 2. The authentication access gateway verifies the validity of the account password or certificate;
[0147] If the password is wrong or the certificate is invalid, the authentication will fail; if the password verification is passed or the certificate is valid, the authentication will pass, and at this time, the mapping relationship between the identity and the source address will b...
Embodiment 3
[0163] Such as Figure 7 As shown, this embodiment provides a data connection system, the system includes an authentication access gateway 11 and an authorization control gateway 12:
[0164] The authentication access gateway 11 is used to judge whether the terminal device has passed the authentication after obtaining the data connection message sent by the terminal device; it is also used to perform corresponding processing on the data connection message according to the judgment result Send the processed data connection message to the authorization control gateway;
[0165] The authorization control gateway 12 is configured to determine whether to send the data connection message to the server according to the authorization policy corresponding to the terminal device.
[0166] Optionally,
[0167] The authentication access gateway 11 is used to determine whether the terminal device is authenticated specifically refers to:
[0168] Comparing the source address of the data co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com