Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
190results about How to "Avoid security breaches" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
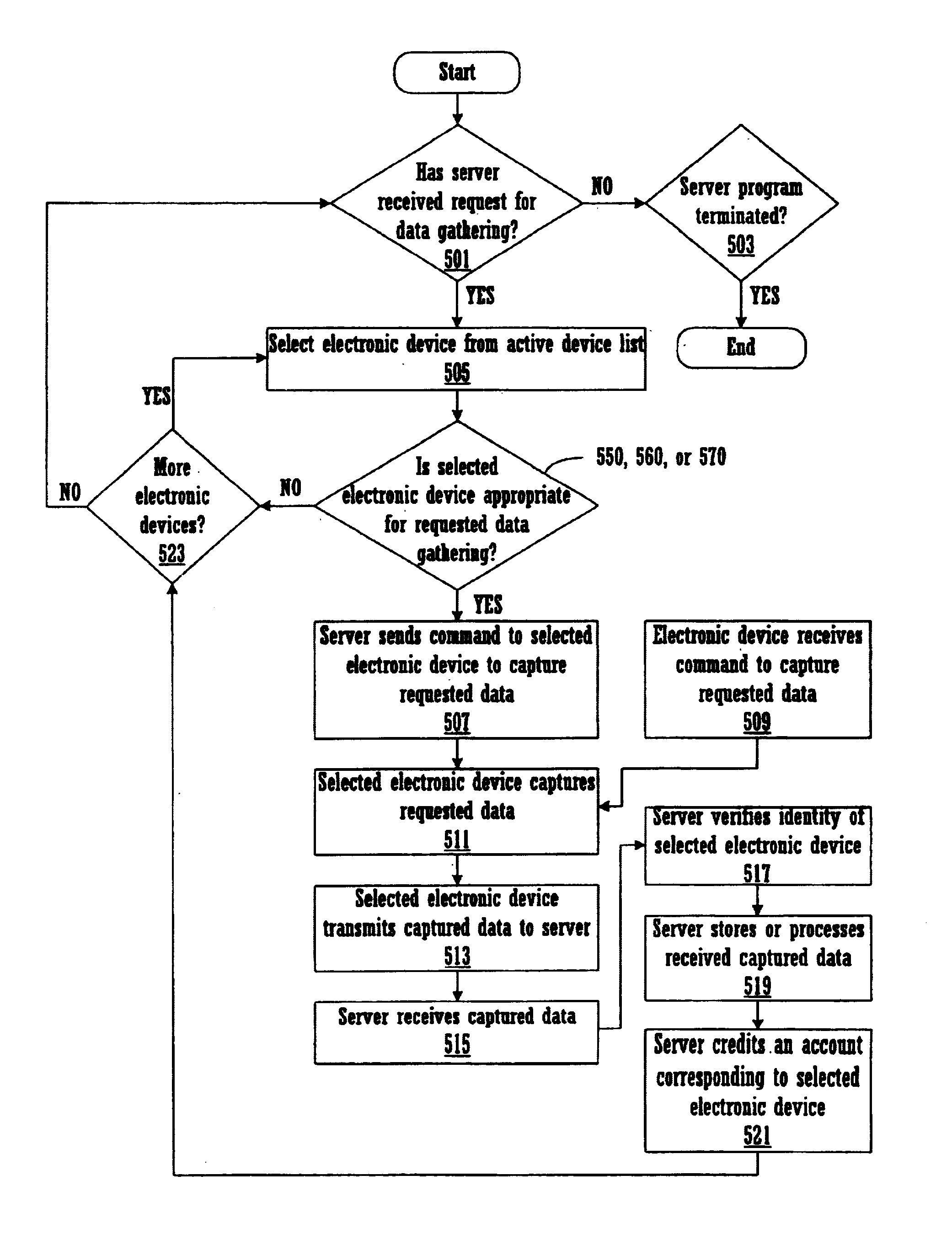
Method and apparatus for wirelessly networked distributed resource usage for data gathering
InactiveUS7194512B1Avoid security breachesServices signallingMultiple digital computer combinationsUser inputComputerized system
A method and system for gathering, collecting, and supplying geographically distributed data. In one embodiment, geographically distributed data is gathered in a server-commanded mode, such that the user of an electronic device need not participate in the capturing or transmitting of the data. In another embodiment, a server initiates requests the user of an electronic device to input data and the data then transmitted to the server. In another embodiment, a user initiates the capture of data with an electronic device and the electronic device transmits the data to a computer server. In another embodiment, the gathering of geographically distributed data is accomplished by the user of an electronic device instructing his electronic device to automatically collect input data and the data is then transmitted to a computer server. In embodiments of the present invention, the electronic device is a palm-sized computer system.
Owner:QUALCOMM INC
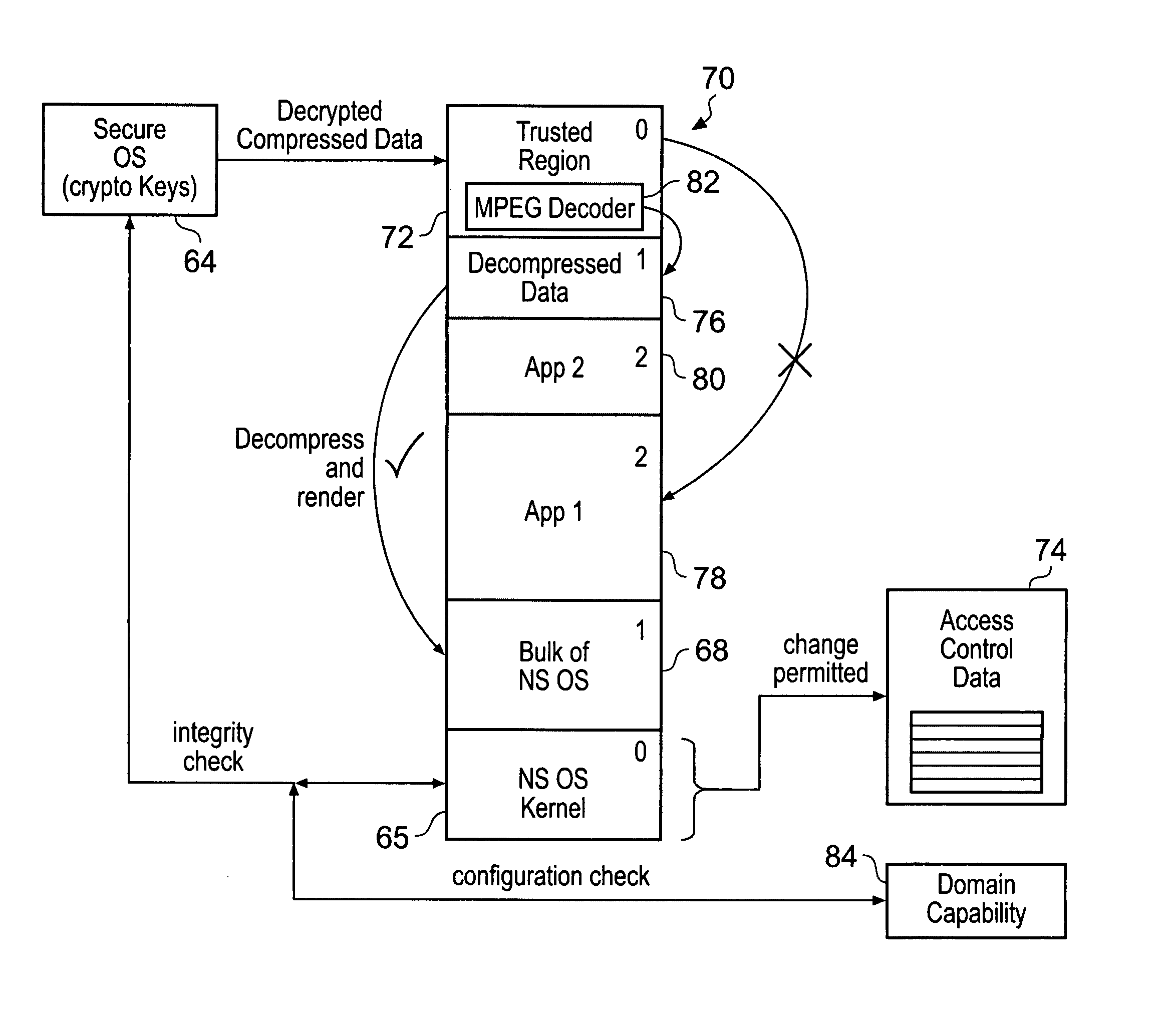
Memory domain based security control with data processing systems
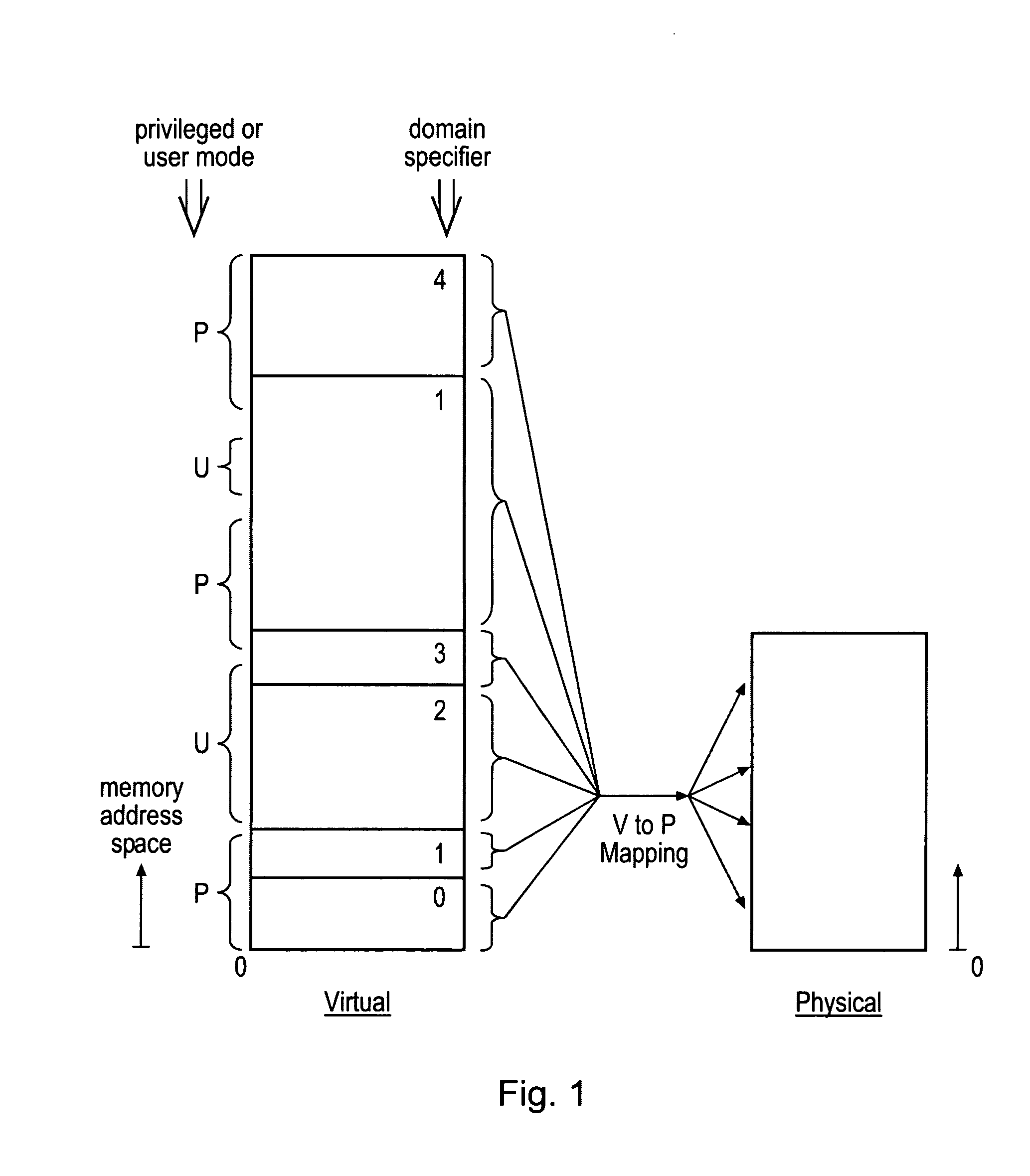
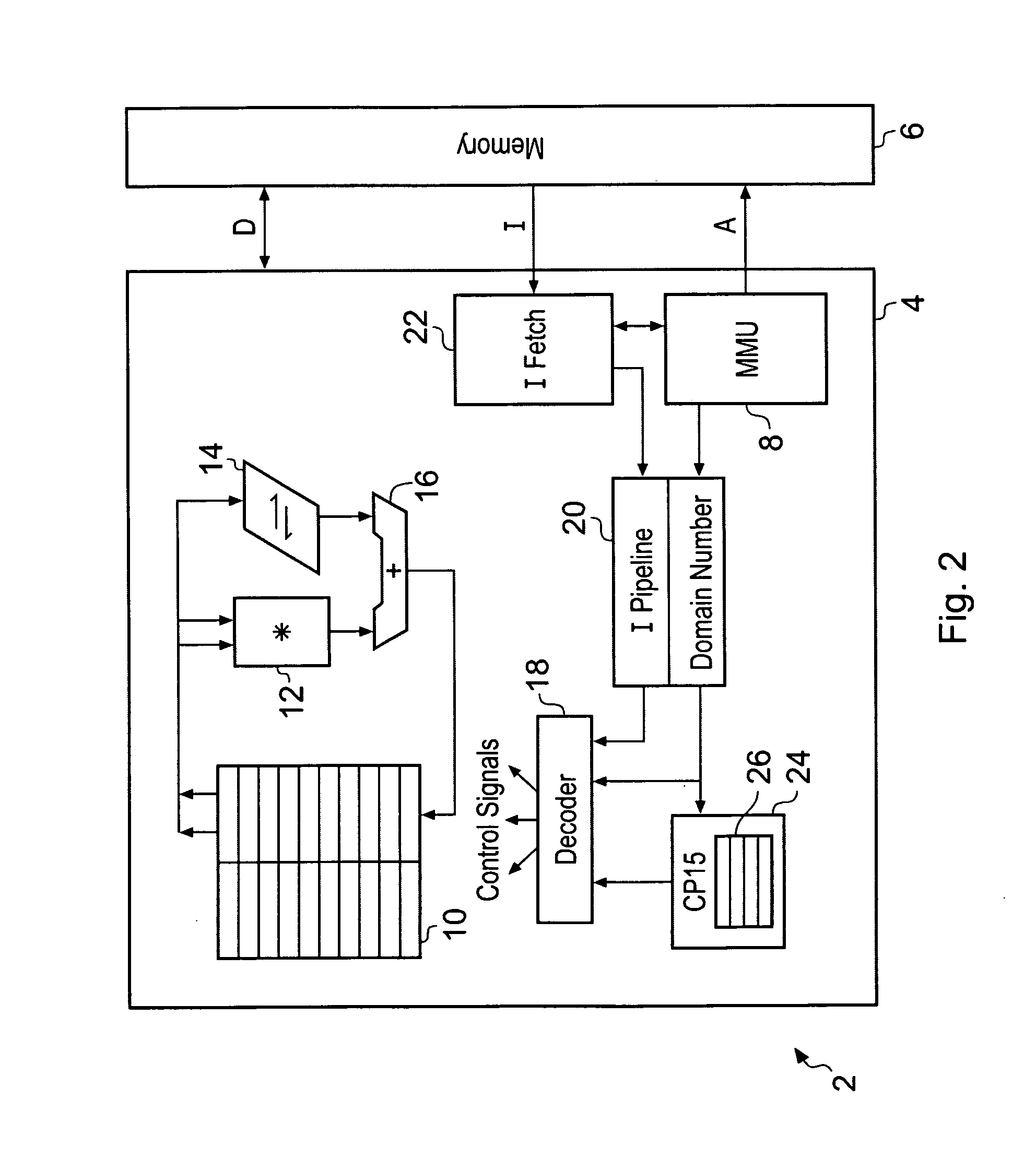
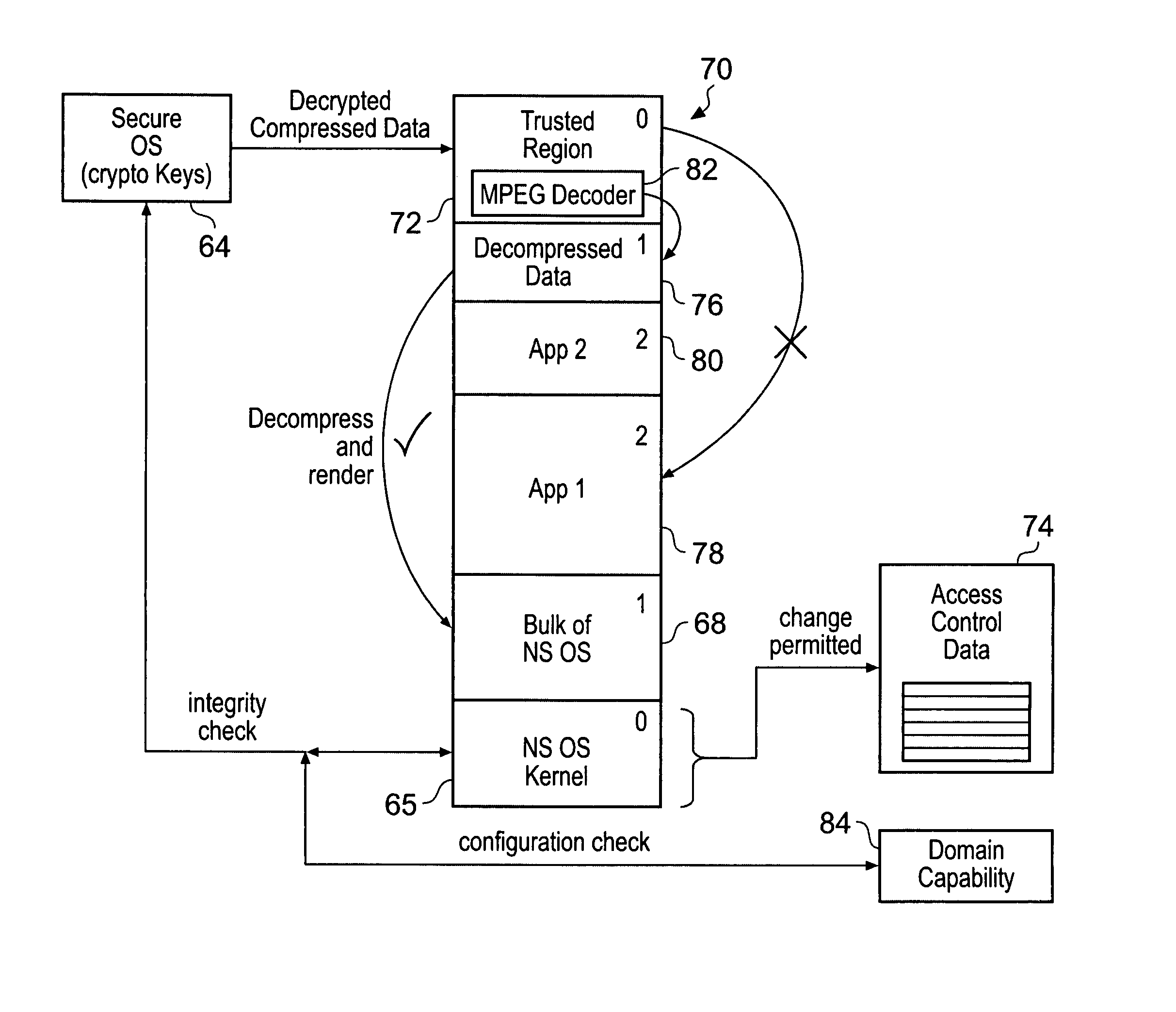
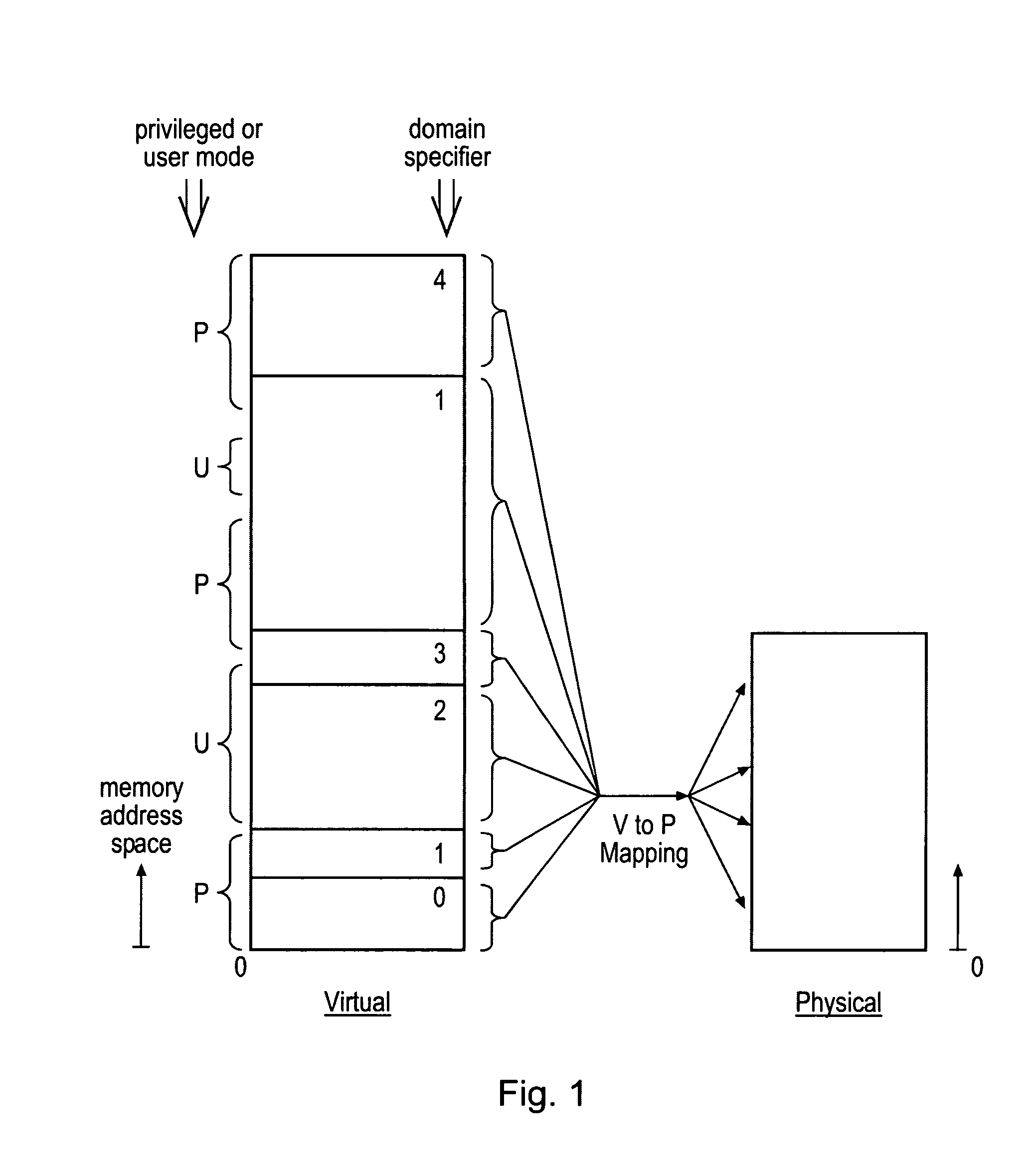
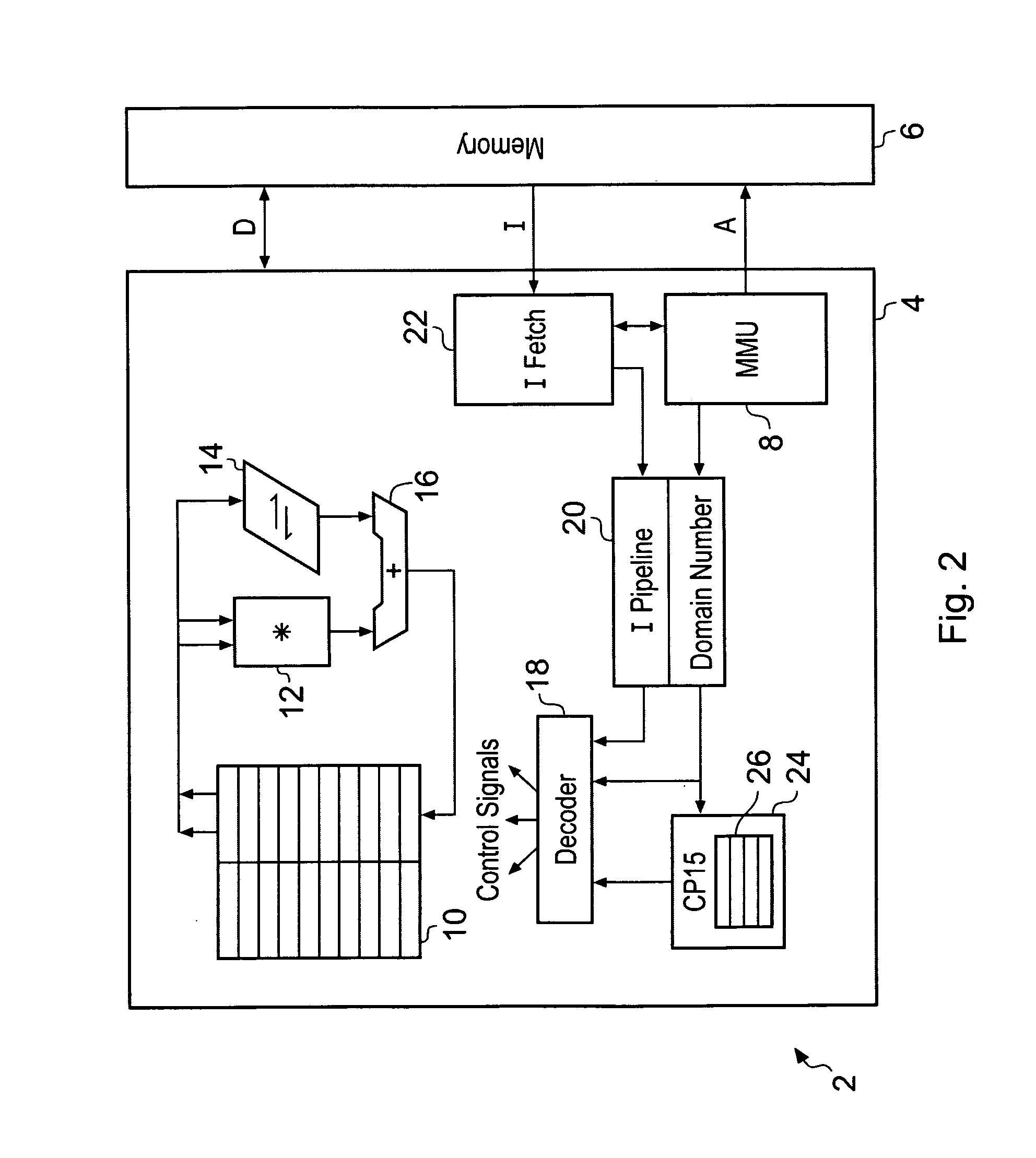
ActiveUS20080250217A1Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
Identity authentication system with biological characteristic recognition function and authentication method thereof
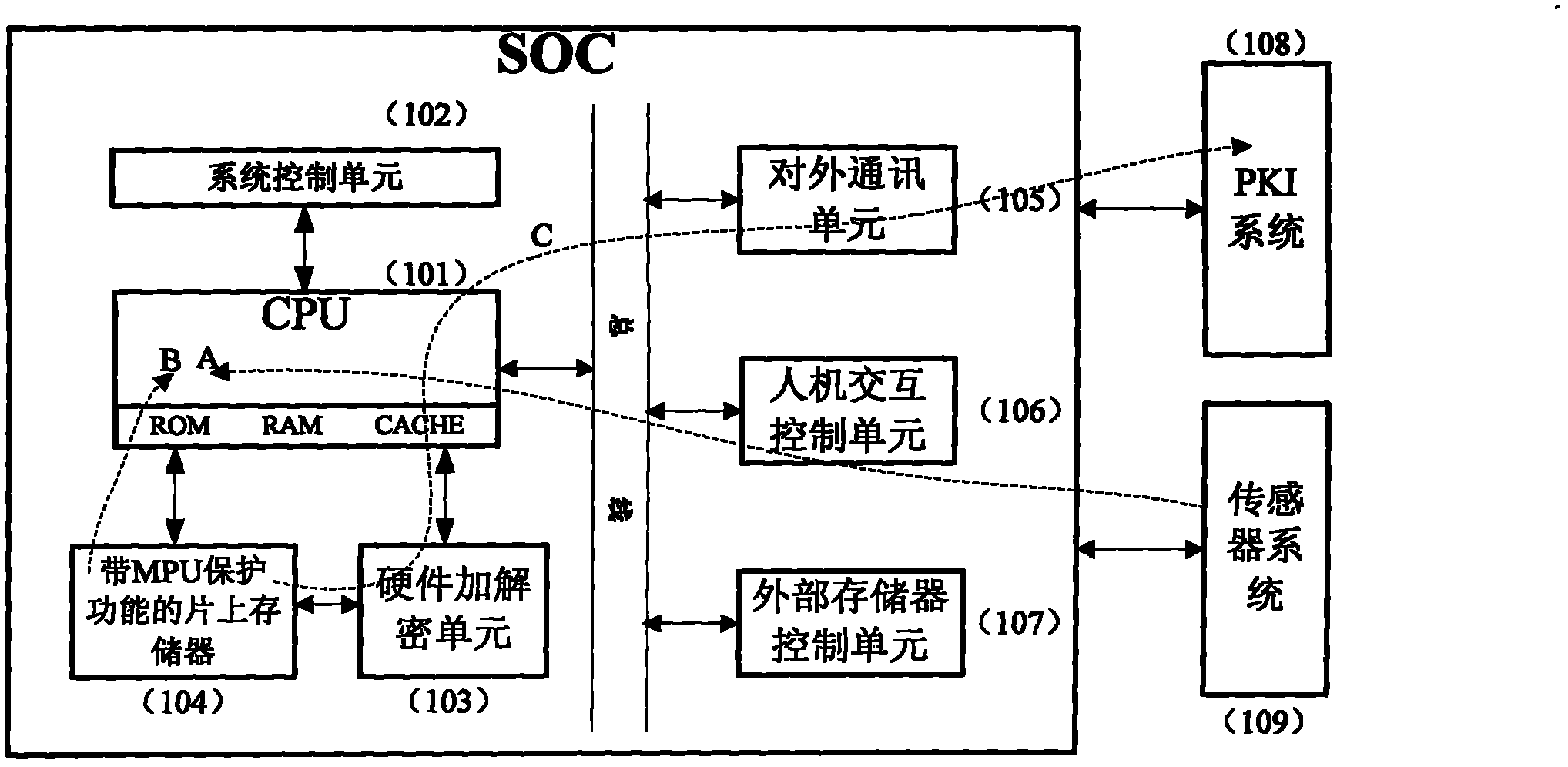
InactiveCN101986597AConfirm the solutionAvoid security breachesUser identity/authority verificationCharacter and pattern recognitionExternal storageComputer terminal
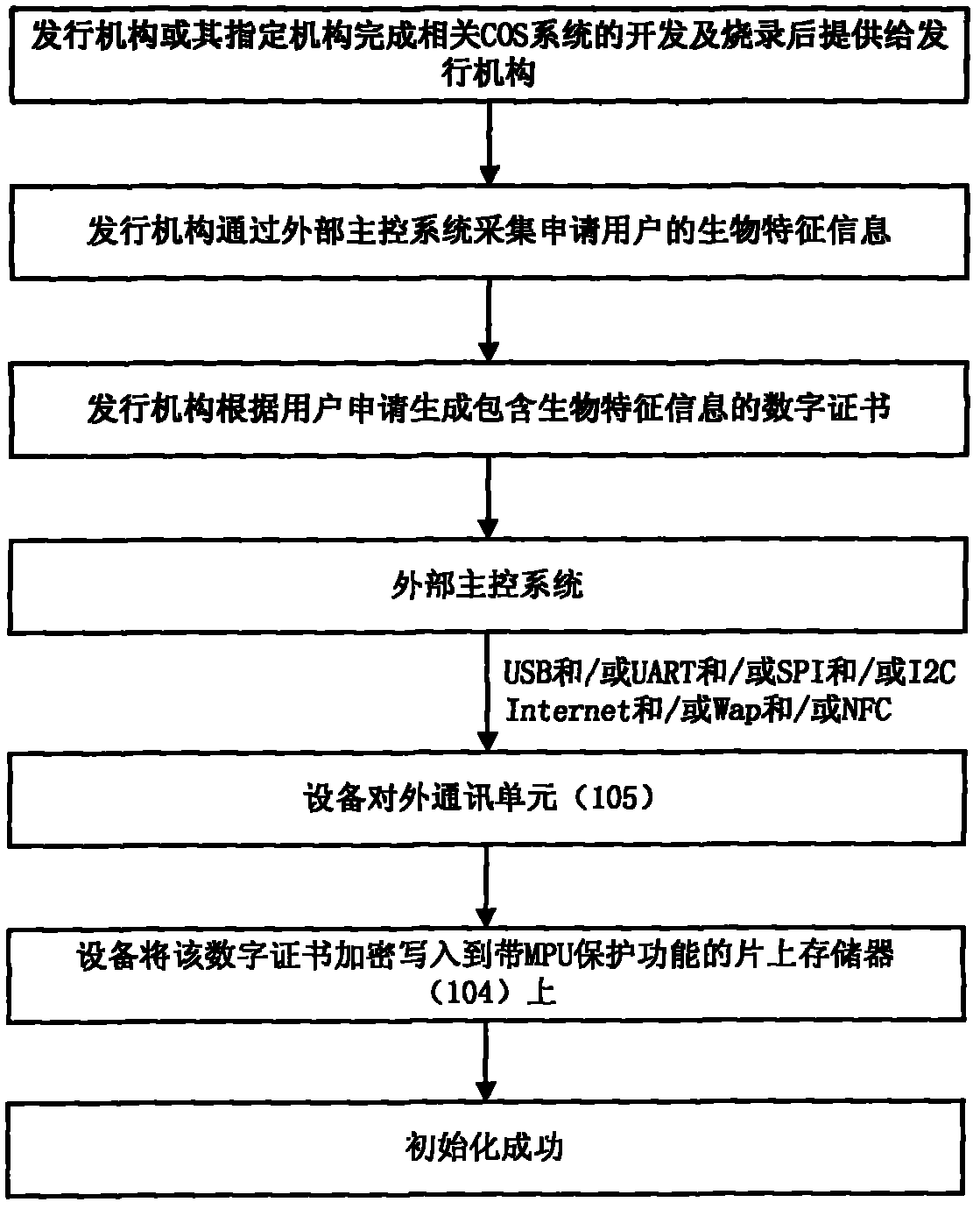
The invention relates to an identity authentication system with biological characteristic recognition function and an authentication method thereof. The system comprises a CPU main control unit (MCU), a system control unit, a hardware encryption and decryption unit, an on-chip memory with MPU protection function, an external communication unit, a man-machine interaction control unit, an external memory control unit, a PKI system and a sensor system, wherein the on-chip memory is used for realizing secure storage and access of such data as personal information, data, procedures, keys, system parameters, etc. The invention has the following beneficial effects: 1. solving the problem of security holes of pins of existing security products, radically solving the problem of authentication of personal identity and having high security; 2. guaranteeing the personal information of the user not to be cracked by logic attacks, side frequency attacks, physical attacks and other means through the hardware; 3. guaranteeing the personal information of the user to be securely stored and not to be cracked by splitting and photographing the chips and other means through the hardware; and 4. effectively avoiding the leak that the transaction information is tampered when the transaction information is sent to the personal identity authentication terminal.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
System and method for providing connection orientation based access authentication
ActiveUS6981143B2Avoid security breachesOvercome vulnerabilityUser identity/authority verificationUnauthorized memory use protectionComputer usersAuthentication
The present invention is embodied in a system and method for providing access authentication of users attempting to gain access to a network based on connection orientation parameters to prevent security breaches of the network. In general, after a connection is requested to gain access to a networked computer, all router addresses through which the request went is gathered and compared to a well-known set of firewall router addresses (for example, of known companies) to determine the validity of the request. If one of the gathered addresses match the well-known set of firewall address, the request is deemed to have come from the other side of the firewall and the connection is denied. As such, in an intranet networking environment that uses a firewall, the present invention will provide computer users of the intranet protection from unauthorized access by others that do not have access past the firewall.
Owner:TREND MICRO INC
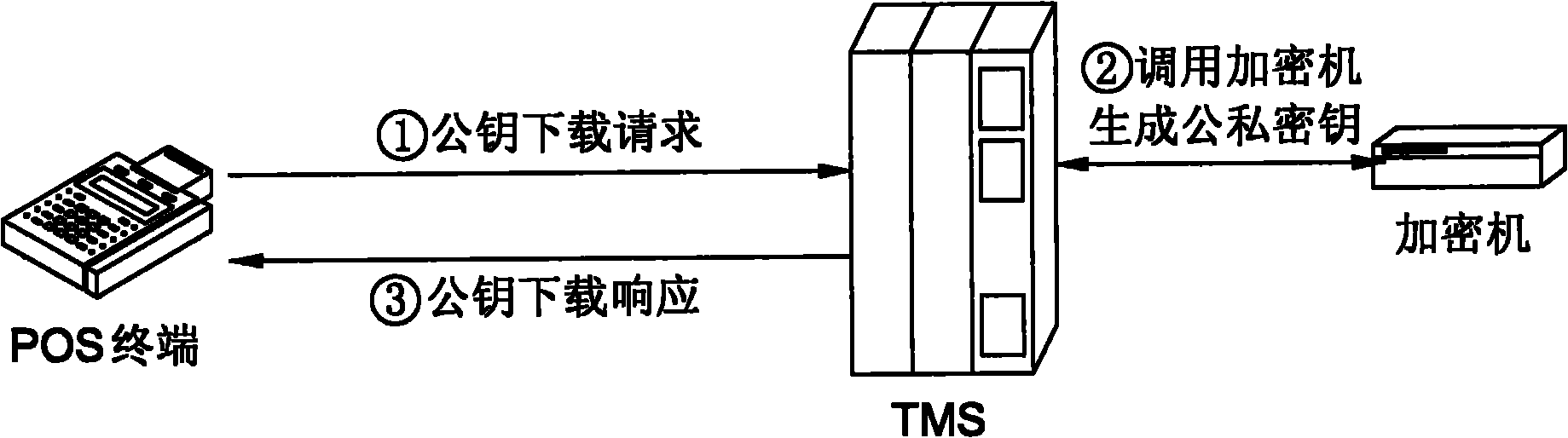
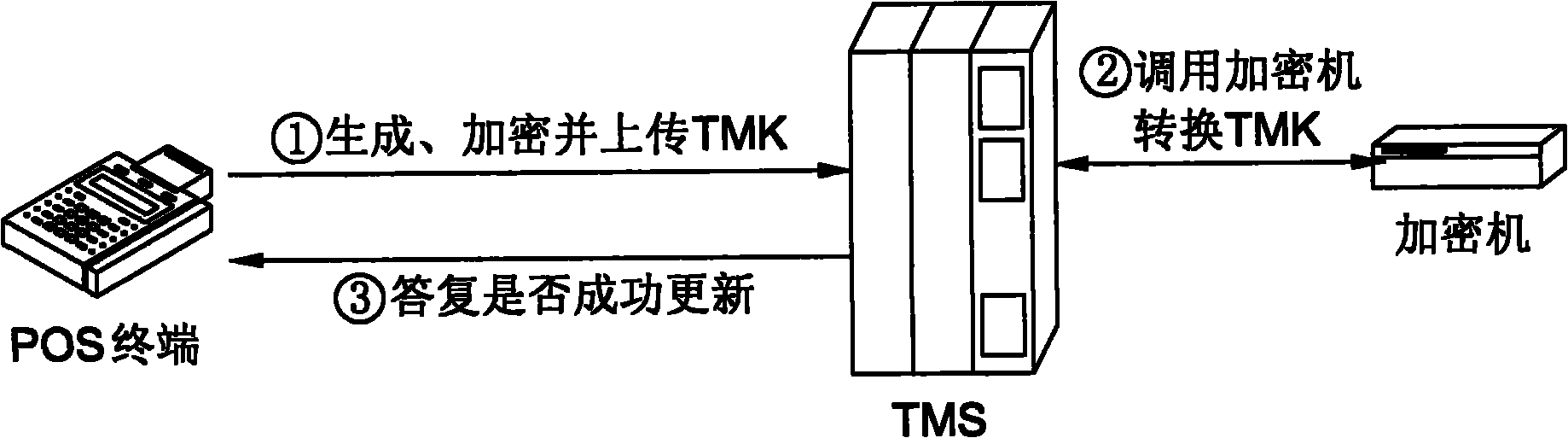
Method for safely downloading master key automatically in bank card payment system and system thereof
ActiveCN101930644AAvoid security breachesImprove securityCash registersTransmissionPlaintextCiphertext
The invention discloses a method for safely automatically downloading a terminal master key TMK in a bank card payment system and a system thereof. The bank card payment system comprises a point of sales (POS) terminal, a terminal management system (TMS), a password keyboard and a hardware security machine. The method comprises that: the TMS calls the security machine to generate a pair of public and private keys; the POS terminal calls the password keyboard to randomly generate the terminal master key TMK, and encrypts the TMK by using the public key of the TMS and uploads the encrypted TMK to the TMS; and the TMS calls the security machine and decrypts the TMK by using the private key and stores the decrypted TMK. The TMK is randomly generated, the transmission process is closed, a TMK plaintext cannot appear outside safe storage equipment and is encrypted by the public key in the transmission process, and a TMK ciphertext can only be decrypted in the security machine of the TMS, so that the method and the system have high safety.
Owner:CHINA UNIONPAY
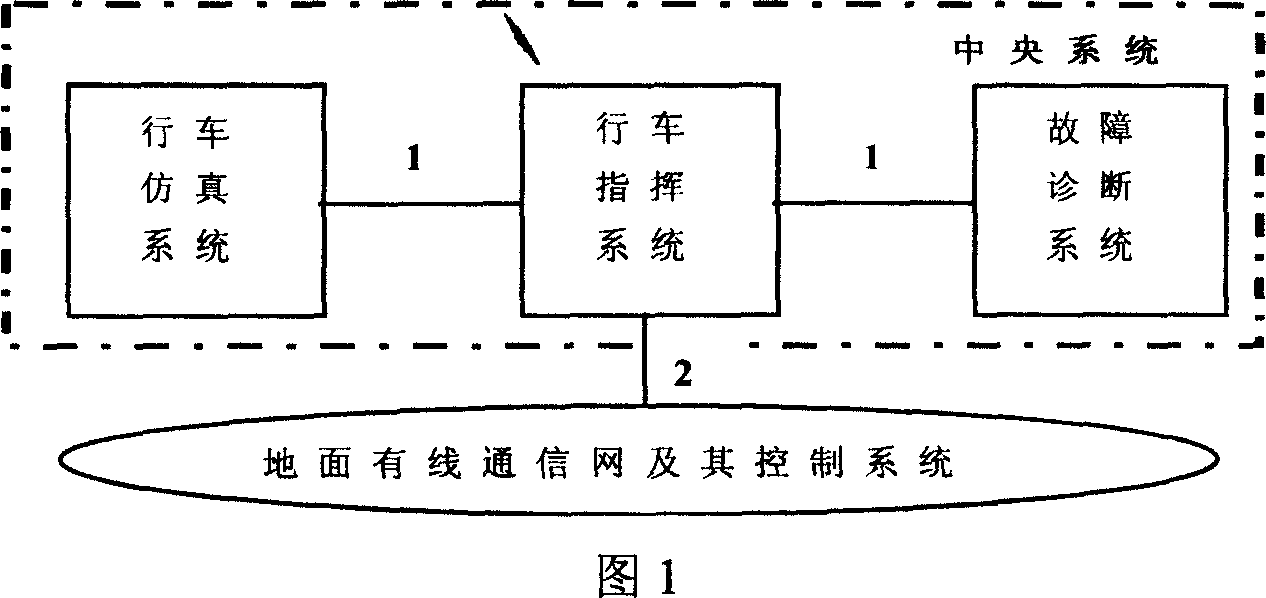
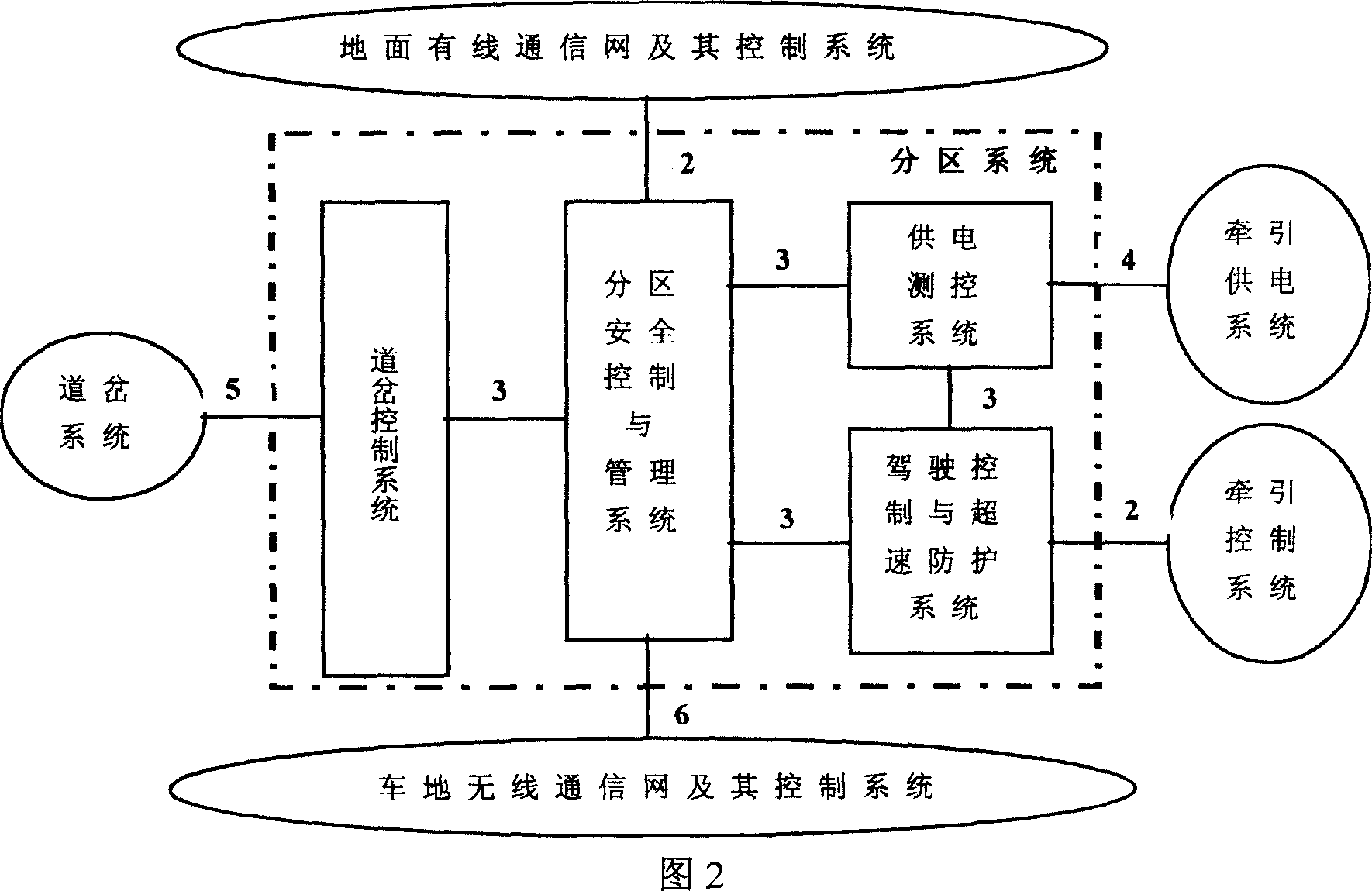
High speed magnetic suspension train travel control system
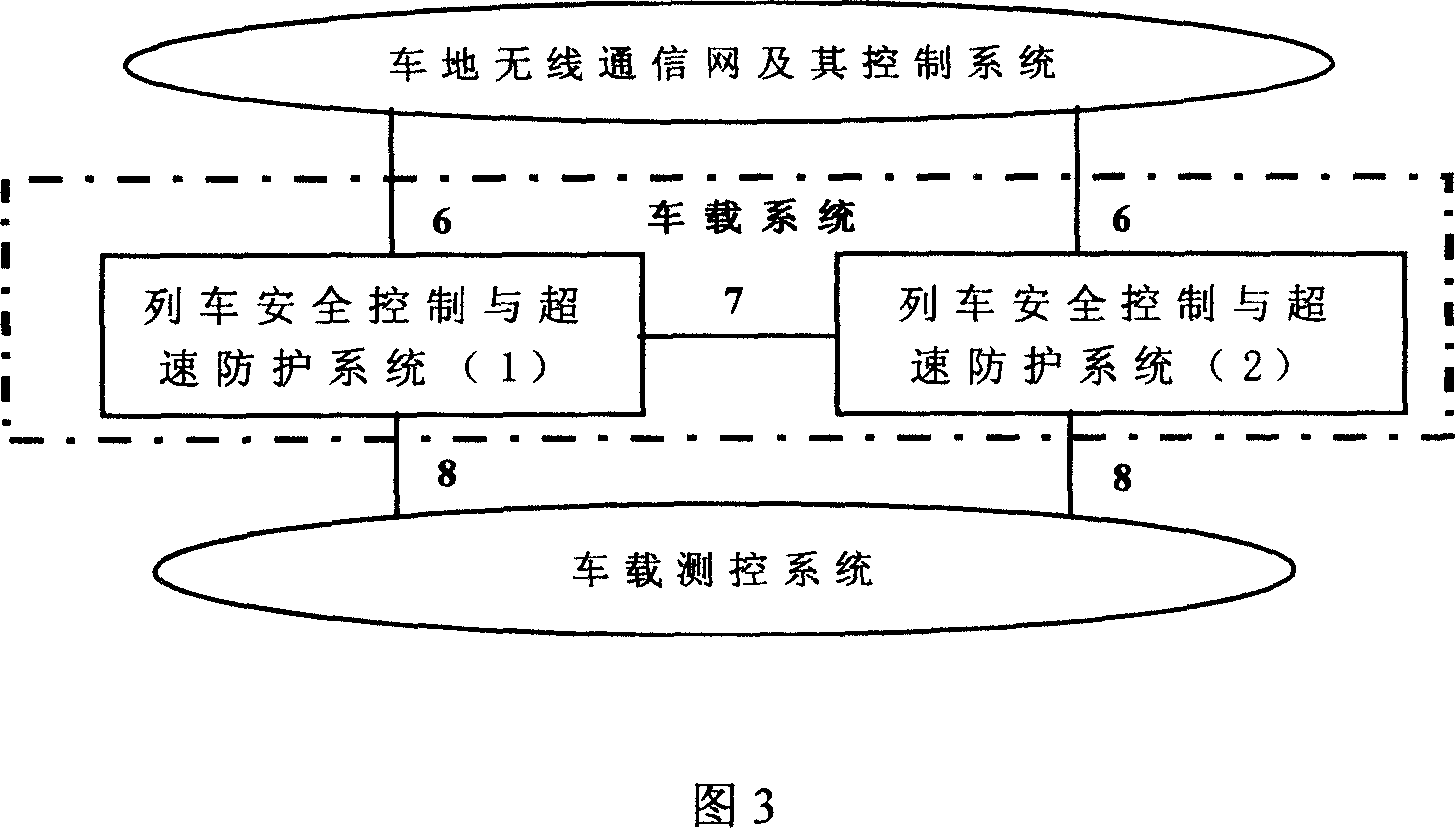
The high speed magnetic suspension train operation control system includes central system in the control center, divisional systems in the stations and transformer stations beside rail, and vehicular systems on trains. The central system includes control system, fault diagnosing system and operation simulating system with safety computer system to raise the safety and the efficiency magnetic suspension train system. The divisional system consists of divisional safety control and managing system, drive control and speed limiting system, switch control system and powering and measuring system, and has modular safety computer. The vehicular system has two independent safety control and speed limiting systems for raised reliability. All the systems are connected via radio or wired communication network.
Owner:BEIJING JIAOTONG UNIV
Miniature iris recognition module adopting active visual feedback
ActiveCN101369311ALow costAvoid security breachesCharacter and pattern recognitionProcess functionDisk controller
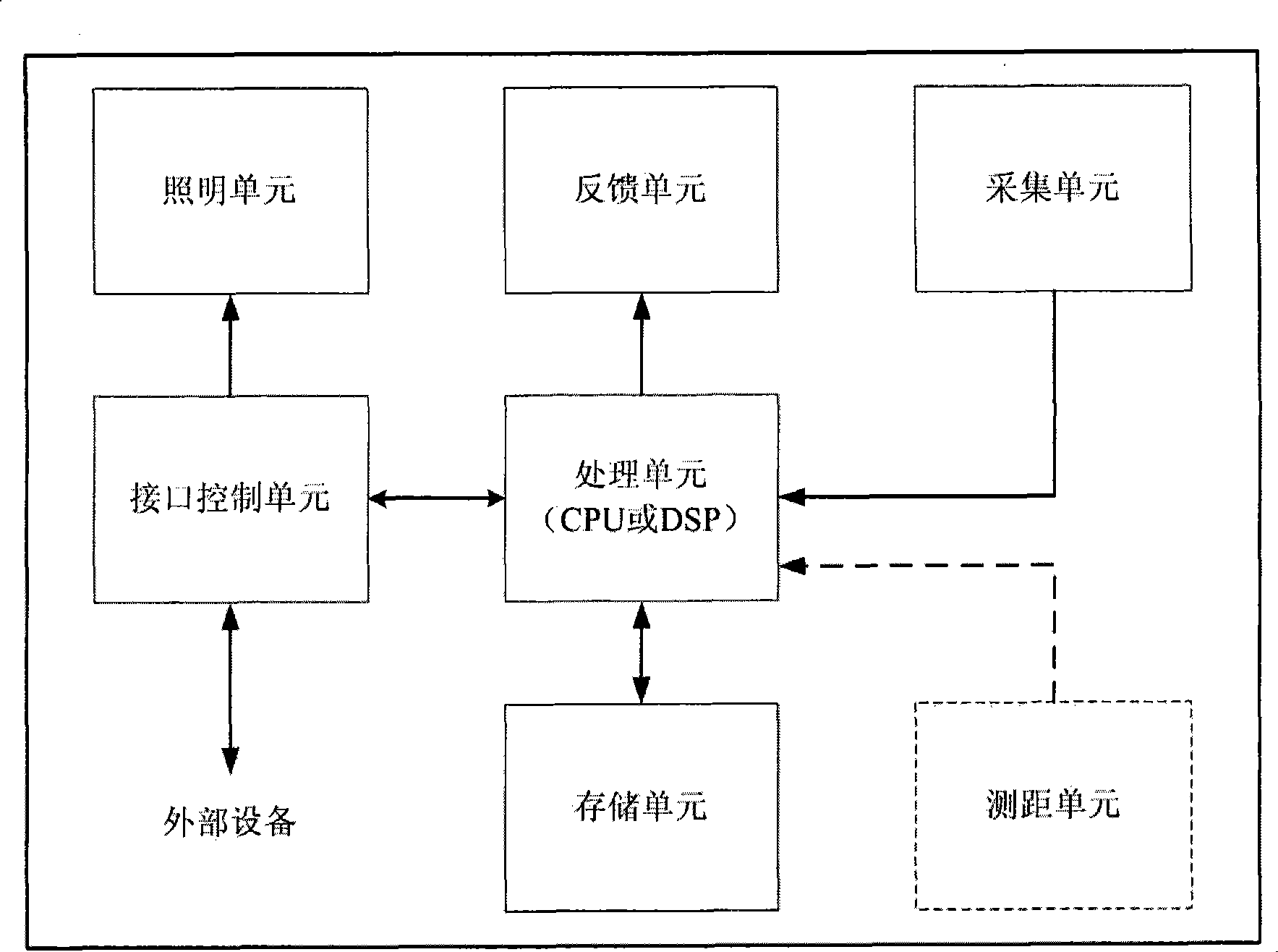
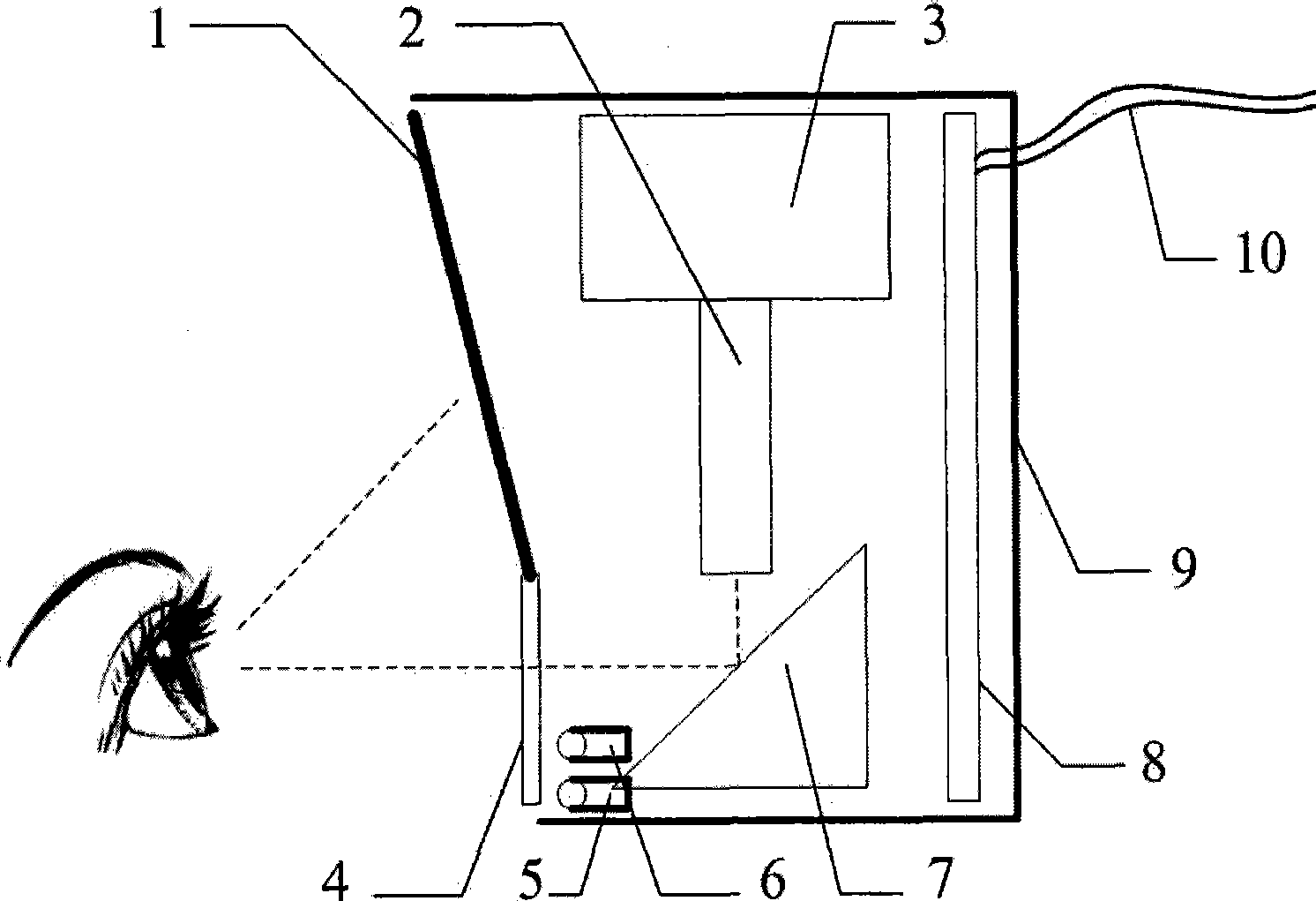
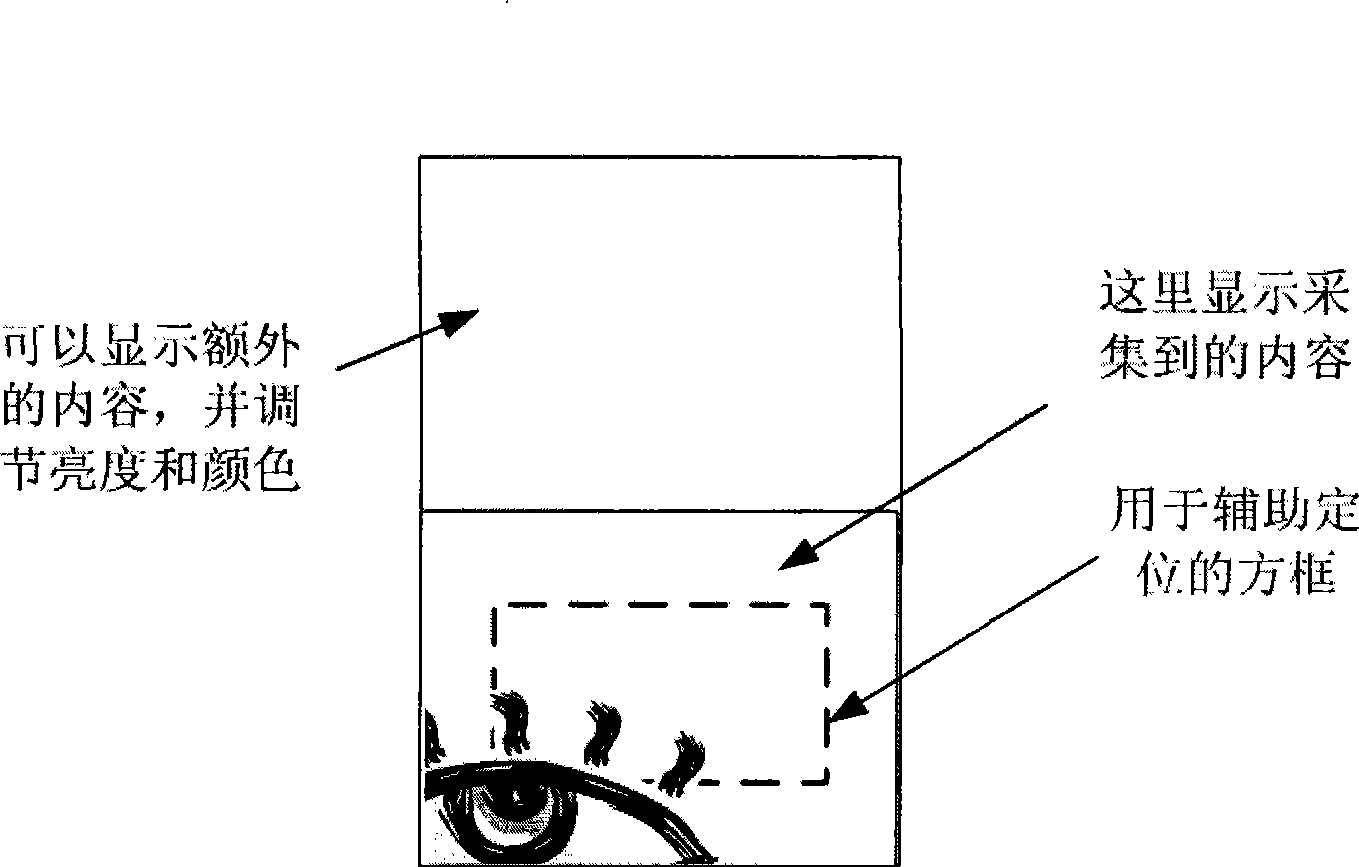
Provided is a miniaturization iris identification module adopting active vision feedback, which independently completes collection of eye iris images and process function, and can be used as a miniaturization module with independent iris identification function embedded into and connected to other devices, e.g. a safe box (a safe case), a lock, a finance safety-deposit box, a fire-arm storage box, a bag storage cabinet, a ATM, a POS, a work attendance machine, a gate inhibition controller, a channel controller, a lift controller, a radio set, a copier, a electrograph, a telephone, a printer, a mouse, a computer, a household electrical appliance, a cable TV remoter, a toy, a digital camera, a moving device, a car, a motor, a motor-assisted bicycle and the like, thereby upgrading to a product with iris identification and authentication function.
Owner:BEIJING IRISKING
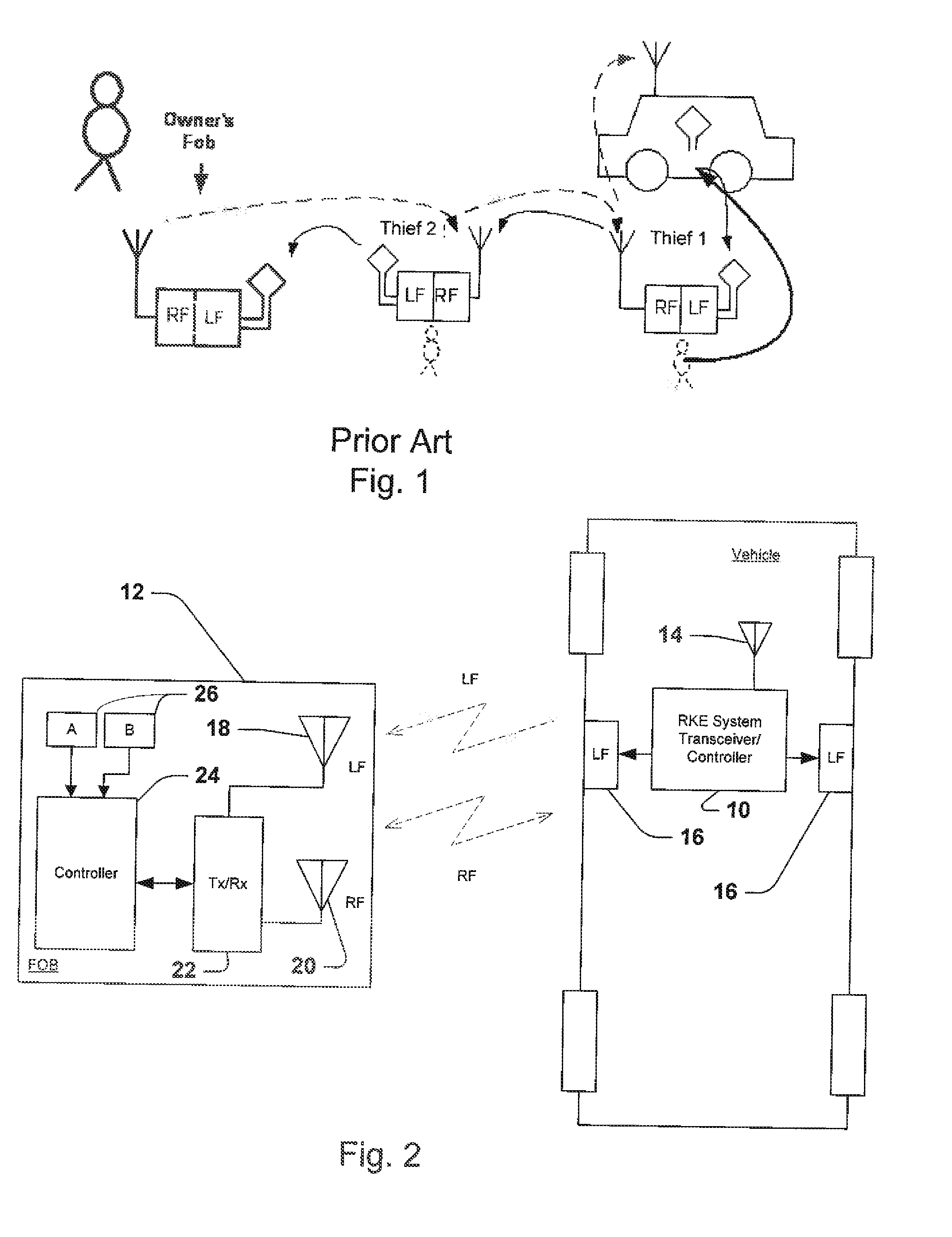
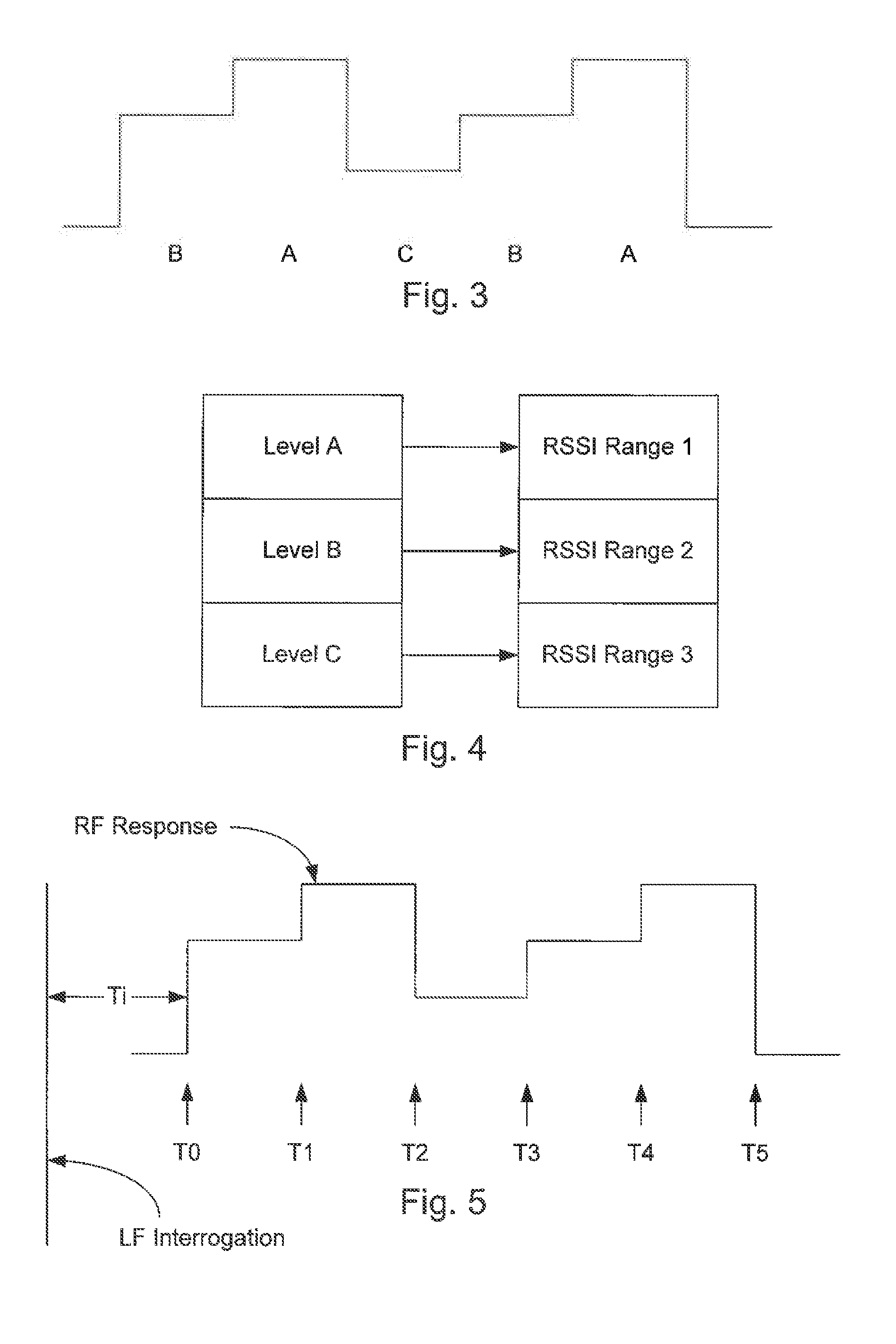
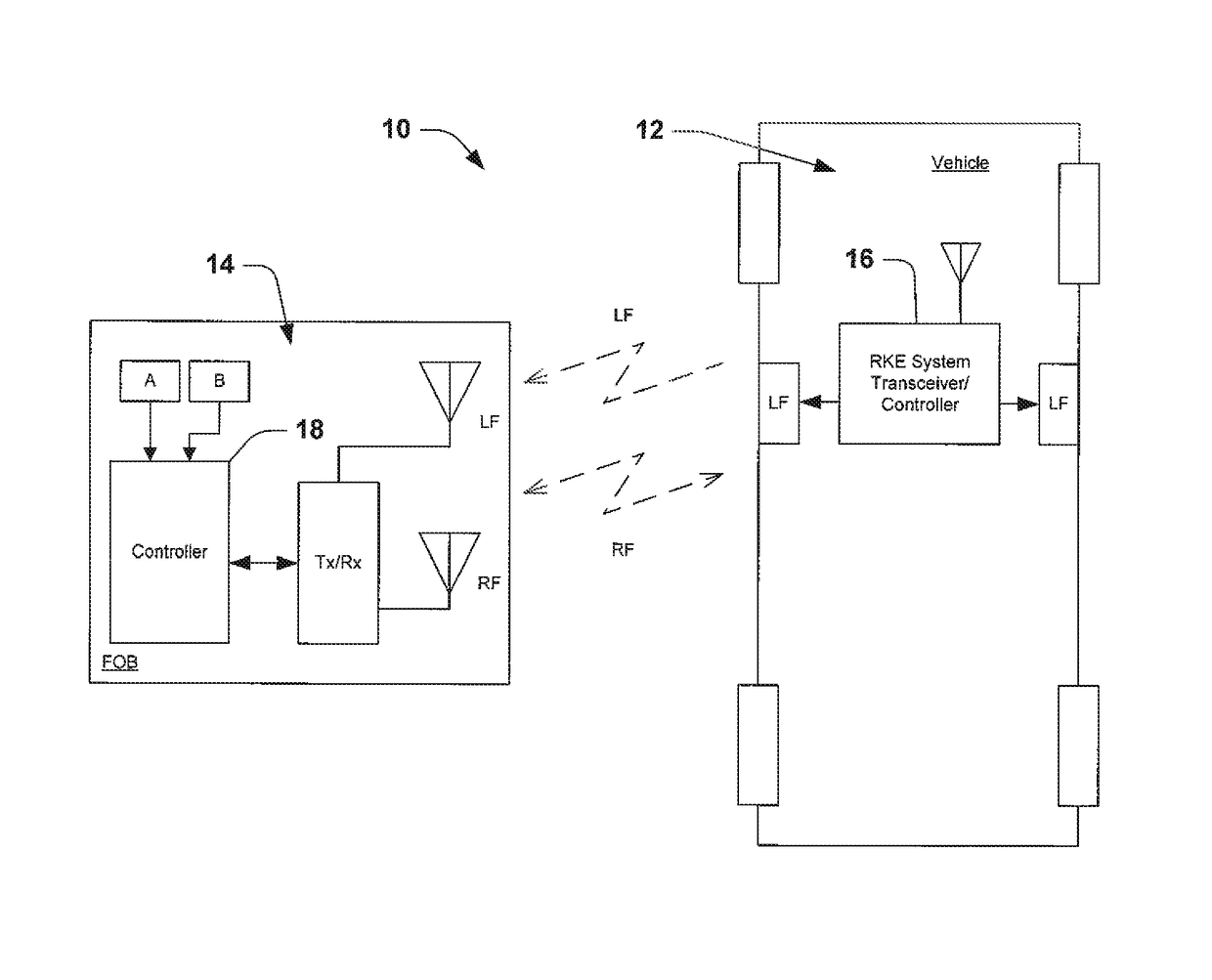
Passive remote keyless entry system with level-based Anti-theft feature
ActiveUS20150022332A1Avoid security breachesAnti-theft devicesIndividual entry/exit registersAnalog signalEngineering
Method for preventing security breaches via the two-thief method of attack of passive remote keyless entry systems for vehicles. The method involves the transmission of a signal between a fob and the vehicle, where the level of the signal changes in a particular pattern. At the receiving side, anomalies in the pattern of the received signal (e.g., levels, timing) are detected and used to detect attempts to mimic the signal.
Owner:TRW AUTOMOTIVE US LLC
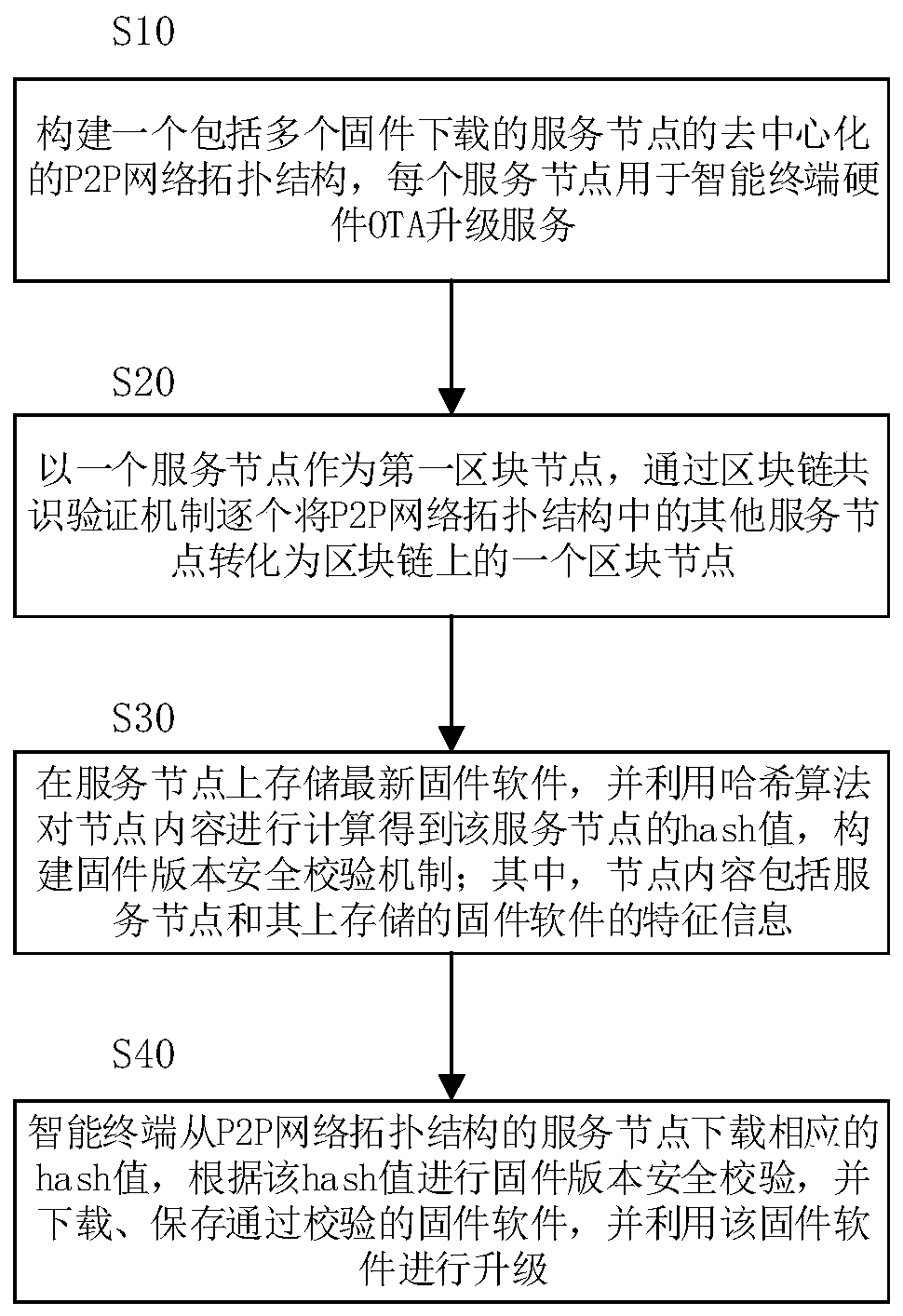
System and method for realizing OTA upgrade of embedded hardware based on block chain
ActiveCN109889589AUpgrade does not affectImprove upgrade reliabilityUser identity/authority verificationData switching networksComputer networkFirmware version
The invention discloses a system and a method for realizing OTA upgrade of embedded hardware based on a block chain. The method comprises the following steps: constructing a P2P network topological structure comprising a plurality of service nodes downloaded by firmware; taking one service node as a first block node, and converting other service nodes in the P2P network into one block node on theblock chain one by one through a block chain consensus verification mechanism; storing the latest firmware software on the service node, and calculating the node content by using a Hash algorithm to obtain a Hash value of the service node; wherein the node content comprises feature information of the service node and firmware software stored on the service node; and the intelligent terminal downloads the corresponding hash value from the service node of the P2P network, carries out firmware version security verification according to the hash value, downloads and stores the verified firmware software, and upgrades the firmware software. The safe and credible P2P network topological structure is established by using the block chain technology, and the OTA upgrading reliability and safety ofthe intelligent terminal are improved.
Owner:IGRS ENG LAB
Memory domain based security control with data processing systems
ActiveUS7966466B2Improve securityLimited abilityDigital computer detailsUnauthorized memory use protectionMemory addressOperational system
Access to memory address space is controlled by memory access control circuitry using access control data. The ability to change the access control data is controlled by domain control circuitry. Whether or not an instruction stored within a particular domain, being a set of memory addresses, is able to modify the access control data is dependent upon the domain concerned. Thus, the ability to change access control data can be restricted to instructions stored within particular defined locations within the memory address space thereby enhancing security. This capability allows systems to be provided in which call forwarding to an operating system can be enforced via call forwarding code and where trusted regions of the memory address space can be established into which a secure operating system may write data with increased confidence that that data will only be accessible by trusted software executing under control of a non-secure operating system.
Owner:ARM LTD
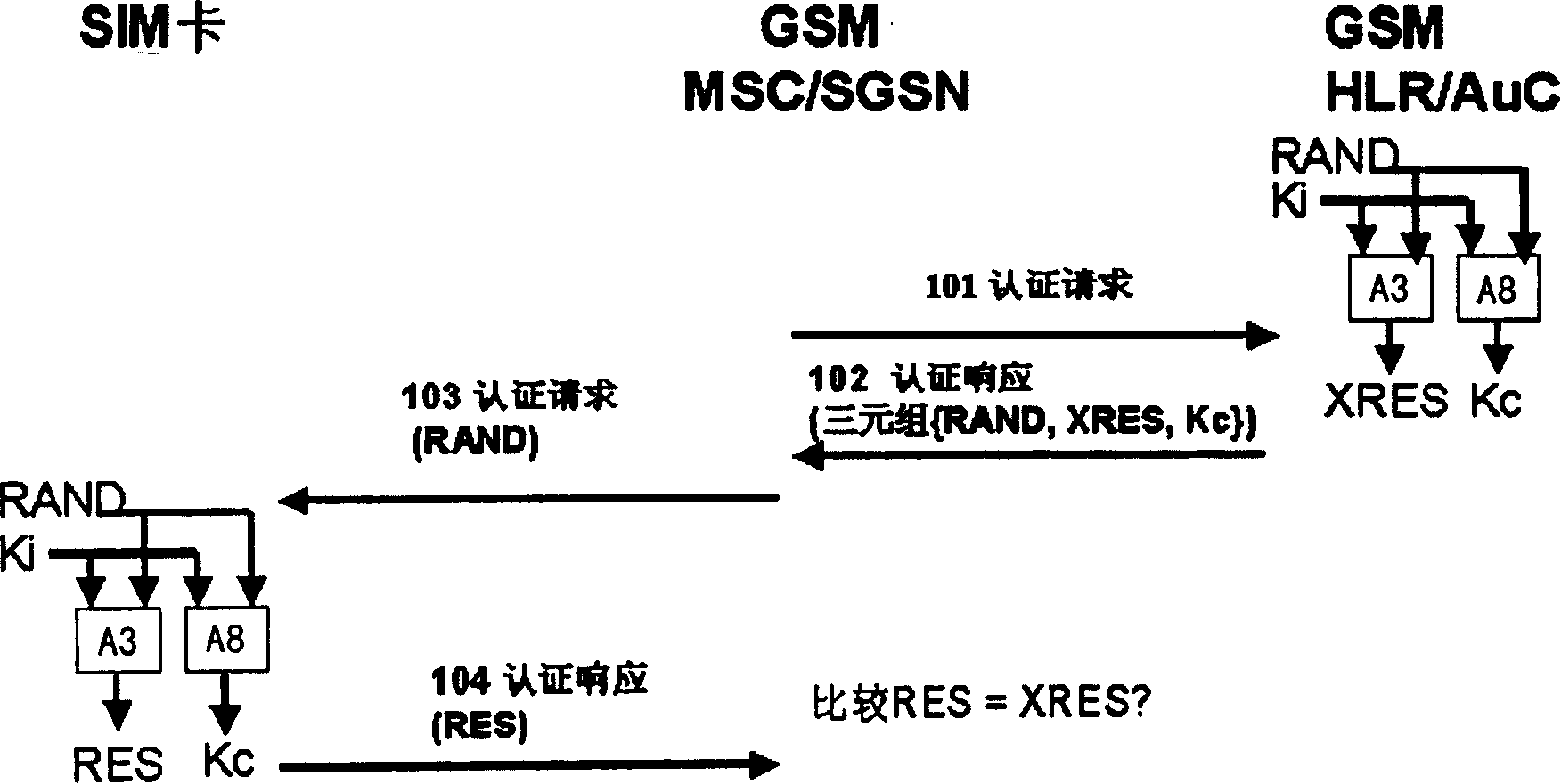
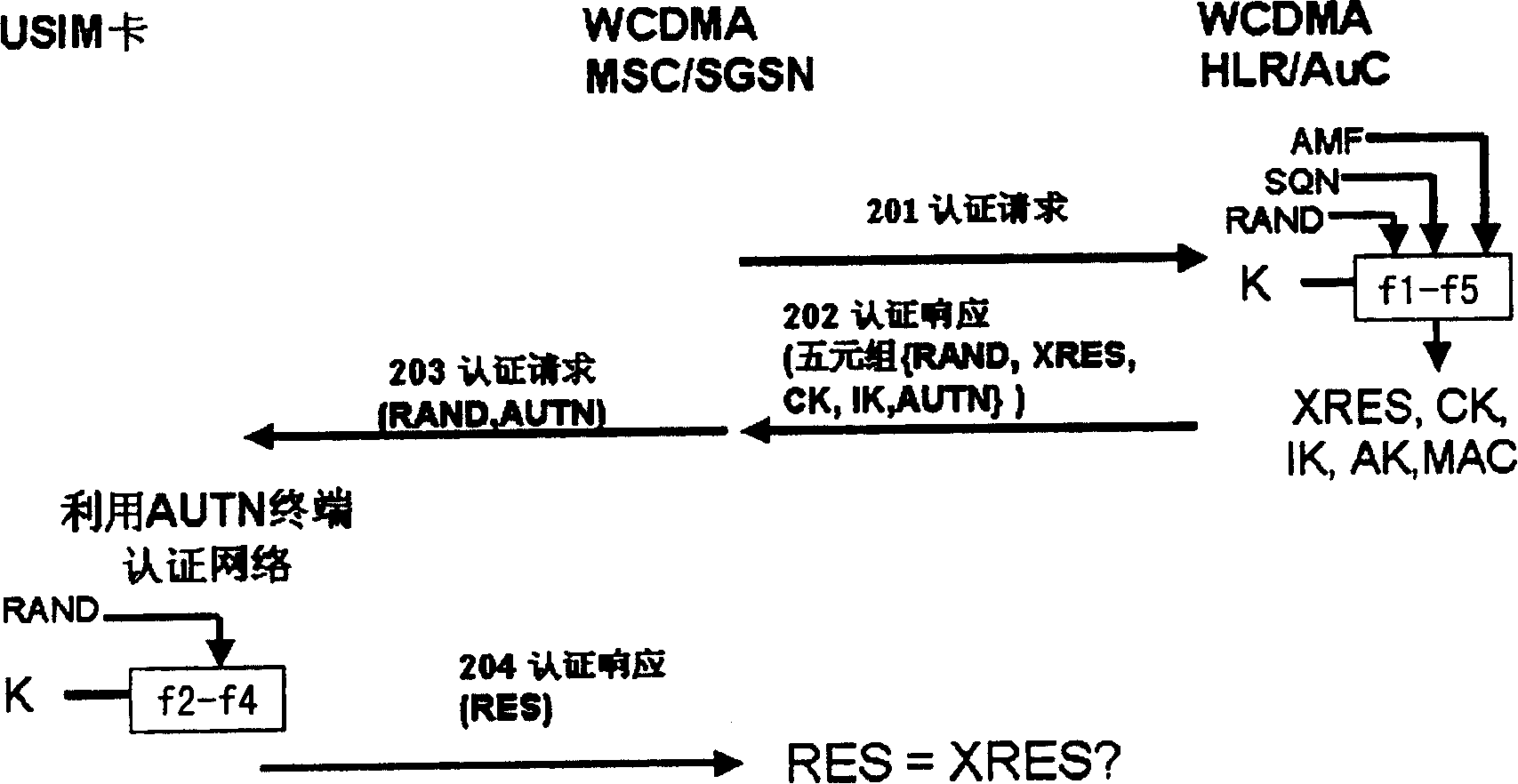
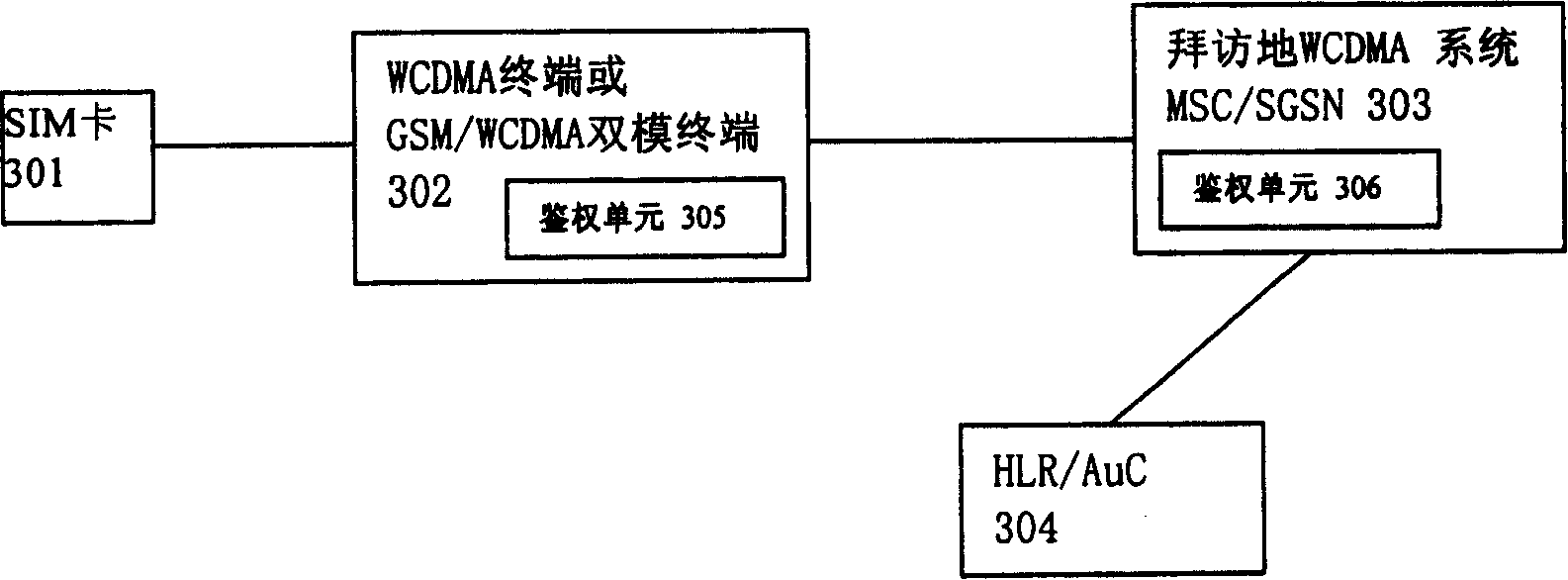
System and method for authenticating network for terminal when SIM card use UMTS terminal and UMTS system
InactiveCN101163003AAvoid security breachesUser identity/authority verificationRadio/inductive link selection arrangementsGSMAuthentication
The invention relates to a device, which realizes a terminal authentication network when a SIM card uses a WCDMA or GSM / WCDMA terminal and a WCDMA network. The device includes a SIM card, the terminal of an authentication unit and the network entity of the authentication unit, wherein, the SIM card is used to generate a temporary key Kc, the terminal of the authentication unit is used to calculate the parameters of the terminal authentication network and compare the parameters with the corresponding parameters sent by a network, and the network entity of the authentication unit is used to calculate the parameters of the terminal authentication network of the network side, which are then sent to the terminal. The invention provides a method and the device, which can be conveniently realized and applied and realize the terminal authentication network when the SIM card of 2G uses the WCDMA or GSM / WCDMA terminal and the WCDMA network, so a bidirectional authentication mechanism is provided to make up for the security vulnerability of being attacked by counterfeit base stations, thus enhancing the security mechanism under the widely existing situations.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
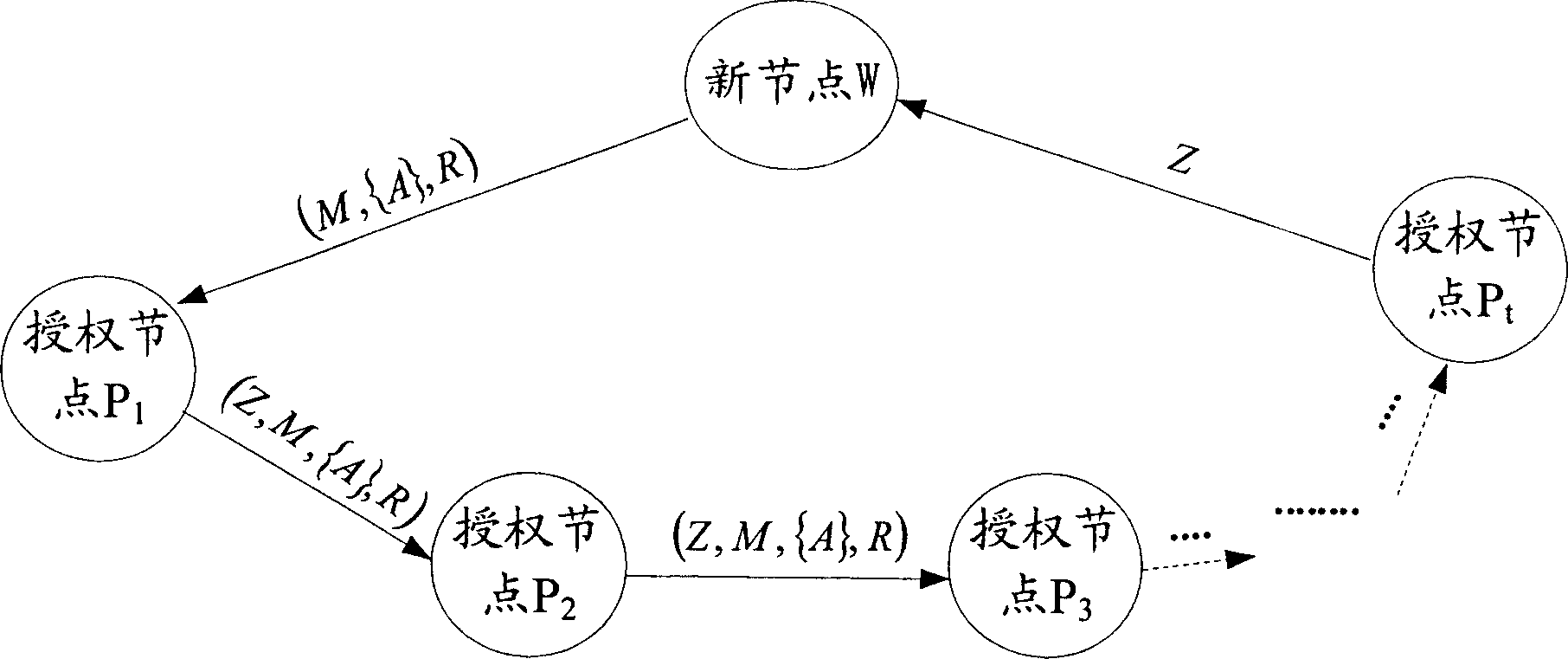
Distributed identity-card signature method
ActiveCN1897518AAvoid security breachesAchieve reuseKey distribution for secure communicationUser identity/authority verificationAuthorizationGroup signature
The method comprises: new node initiates an identification letter issuing request to all authorization node; after receiving the responses for agreeing to participate in issuing identification letter from at least t authorization nodes, the new node selects t authorization nodes from them; the selected authorization nodes use a hop-by-hop signature approach to incorporate with the new node to generate the group signature and to generate identification letter.
Owner:HUAWEI TECH CO LTD +1
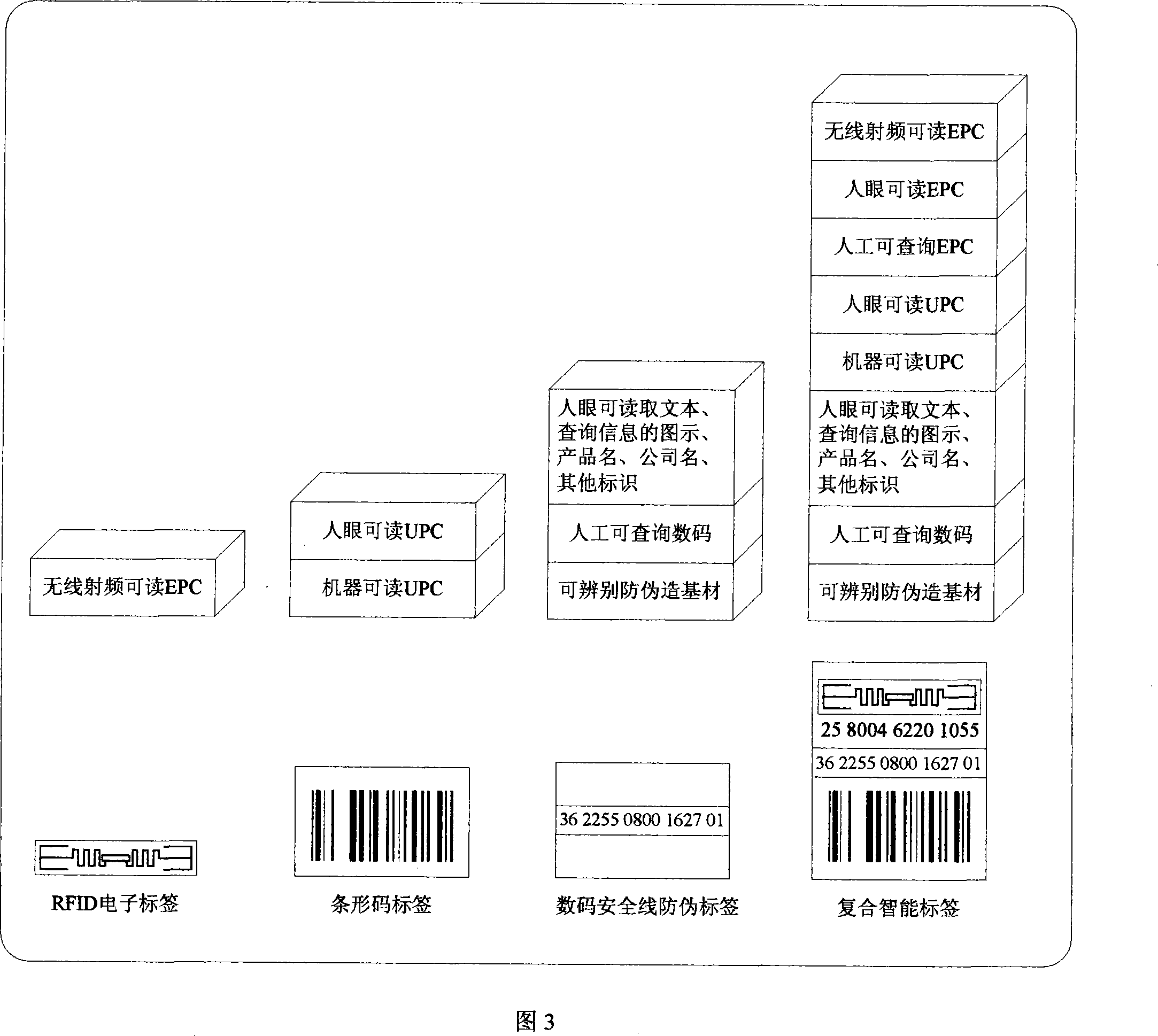
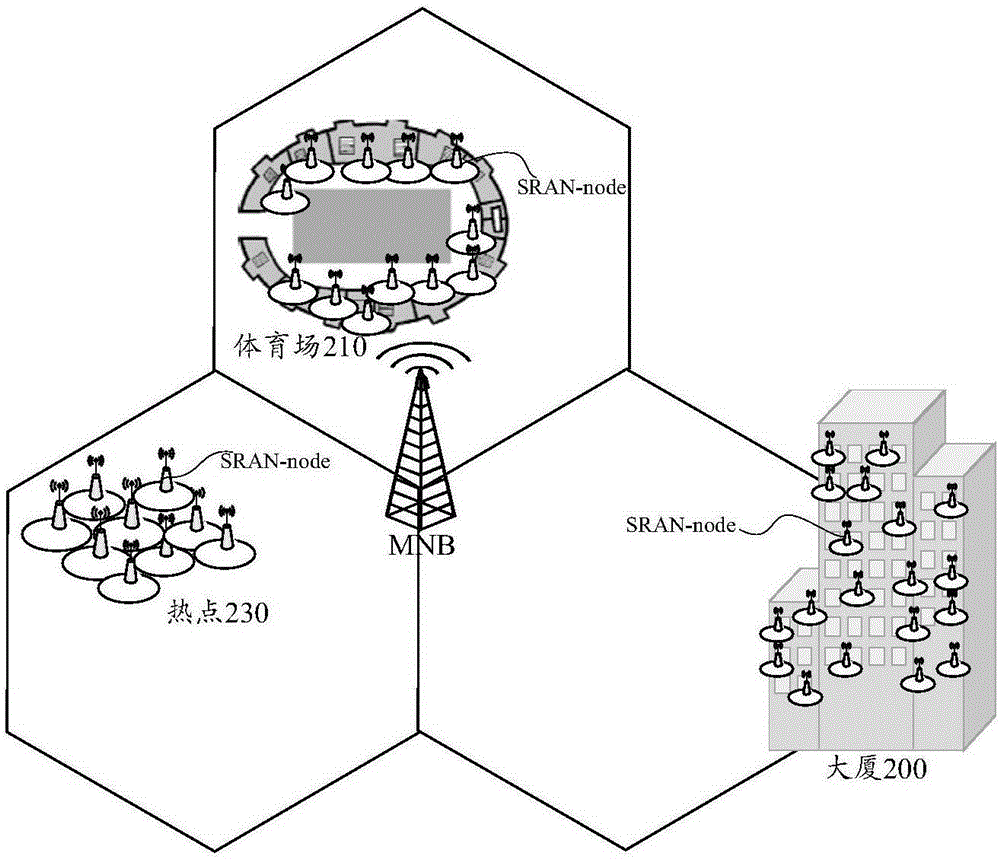
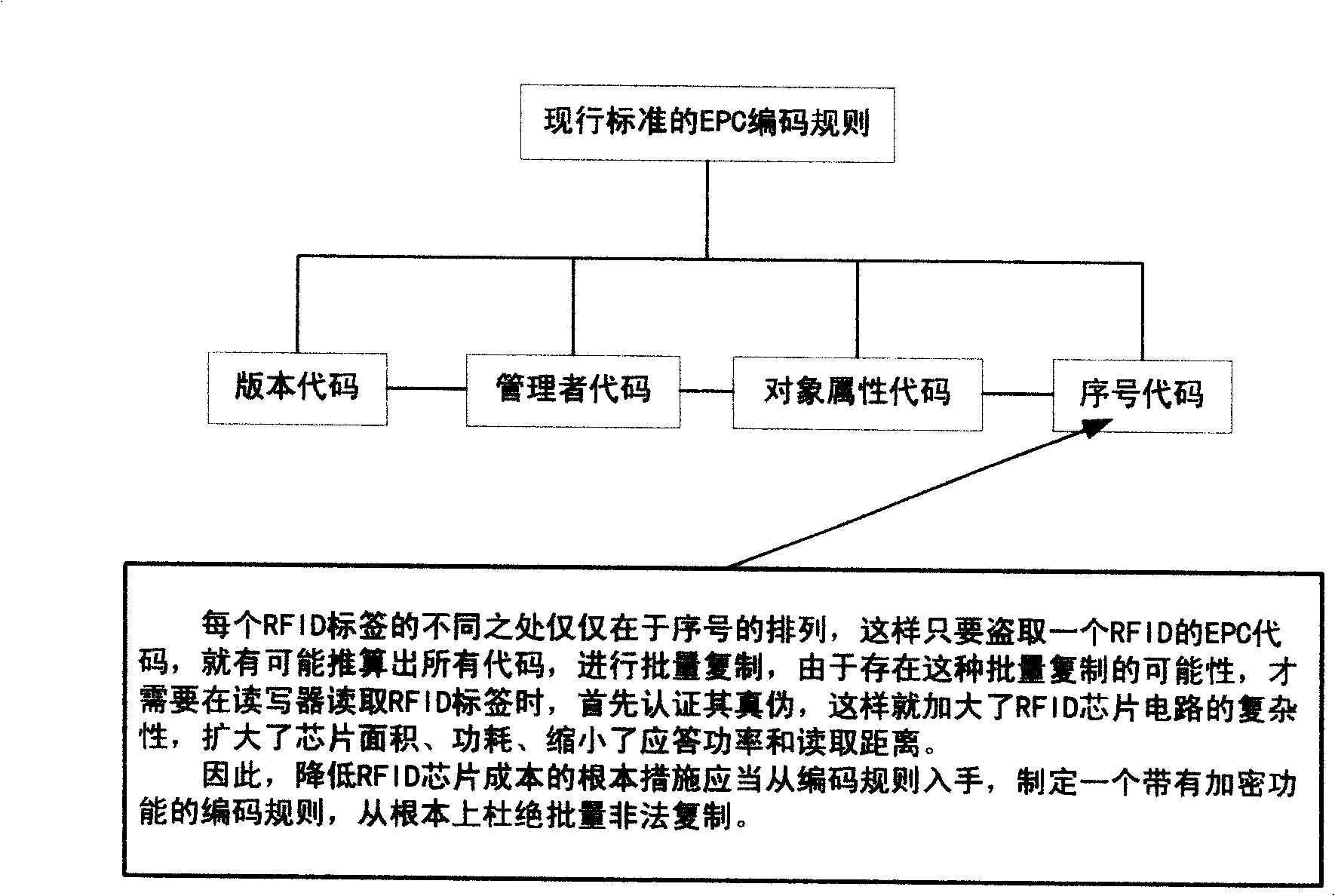
A coding and preparation method for the multiple cross-validation of RFID compounding labels and its system
InactiveCN101216897AImprove securityAvoid security breachesDigitally marking record carriersPaper/cardboard articlesPlaintextThe Internet
The invention relates to a method for encoding and manufacturing a multi-interactive authentication RFID compound intelligent tag, as well as a system thereof. An EPC product electronic code which is provided with a time code and is randomly corresponding to a sequence code is prepared as a storage code of a non-chip RFID, a surface acoustic wave RFID or a powder RFID chip; the code is converted to a plaintext code via encryption and is printed on a tag for covering; the plaintext code is converted to a bar code and printed on the tag; a digital safe line production tag is used to carry out the pre-chopping treatment of the tag, so as to prevent the transfer; numbers on the safe line are identified by photography; EPC codes, passwords, bar codes and the safe line digital codes are stored correspondingly; a tag anti-counterfeit system, a bar code scanning system and a radio frequency identification system are all connected with the Internet of Things; thus the same product information and logistics path information can be accessed through the EPC Internet of Things regardless of using radio frequency identification, man-made identification or machine identification. The invention can greatly reduce the tag cost, improve the safety, and expand the information redundancy and the application adaptability.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
Embedding and extracting method for audio zero water mark based on vector quantization of coefficient of mixed domain
InactiveCN101290772AAvoid security breachesSpeech analysisRecord information storageCarrier signalInformation security
An audio zero watermark embedding and extraction method is based on mixed domain coefficient vector quantization in an audio processing method in the information security technical field. The watermark embedding part of the method is as follows: segmenting processing of an original audio signal is carried out; discrete wavelet transformation of each segment of audio frequency is carried out to extract a wavelet approximate component; discrete cosine transform and vector quantization of the obtained wavelet approximate component are carried out; a polarity vector is constructed according to the statistic characteristics of an index value after vector quantization; and through carrying out XOR operation of the polarity vector and a to-be-embedded original watermark signal, a watermark is embedded in a detection cipher key. The watermark extraction part of the method is as follows: firstly, a polarity vector is obtained from a to-be-measured audio signal through adopting a method identical to that of the watermark embedding part; then, XOR operation of the polarity vector and a watermark detection cipher key is carried out to obtain an extracted watermark signal. The audio zero watermark embedding and extraction method shows stronger robustness to various normal audio signal processing operations and malicious attacks, and also omits the trouble of reconstructing an audio carrier signal.
Owner:上海交通大学无锡研究院
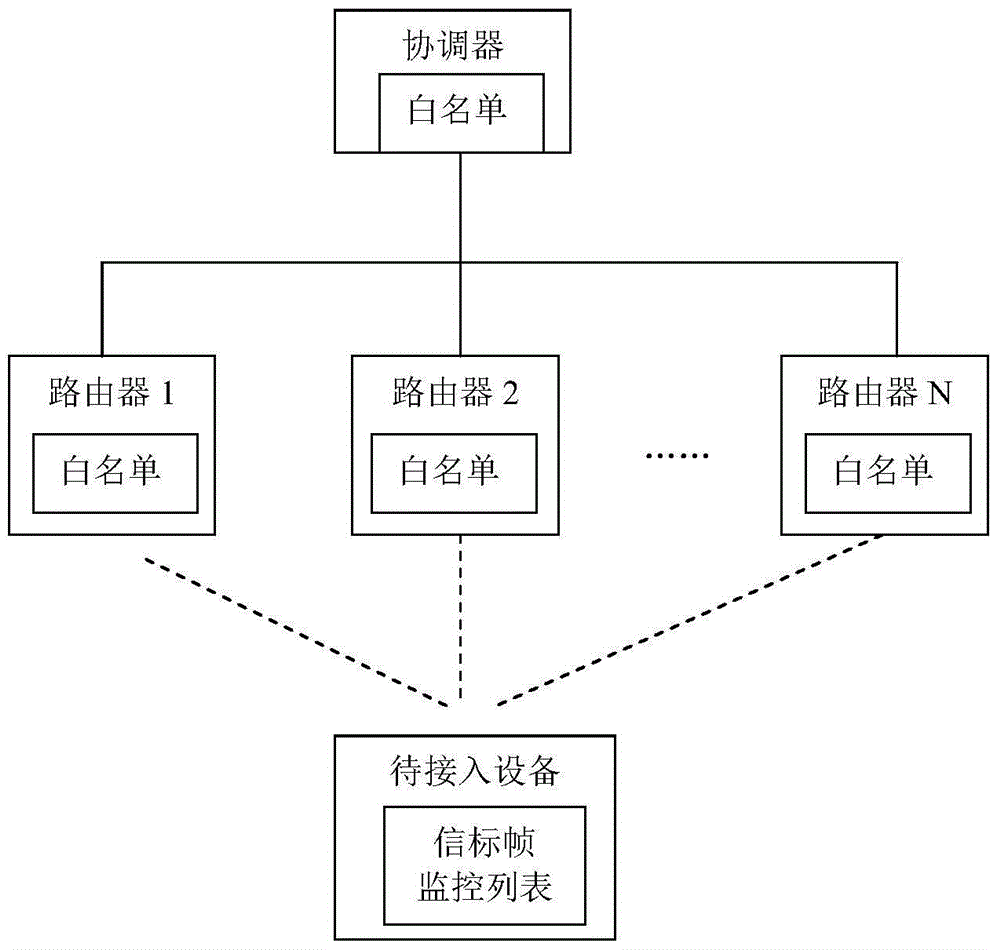
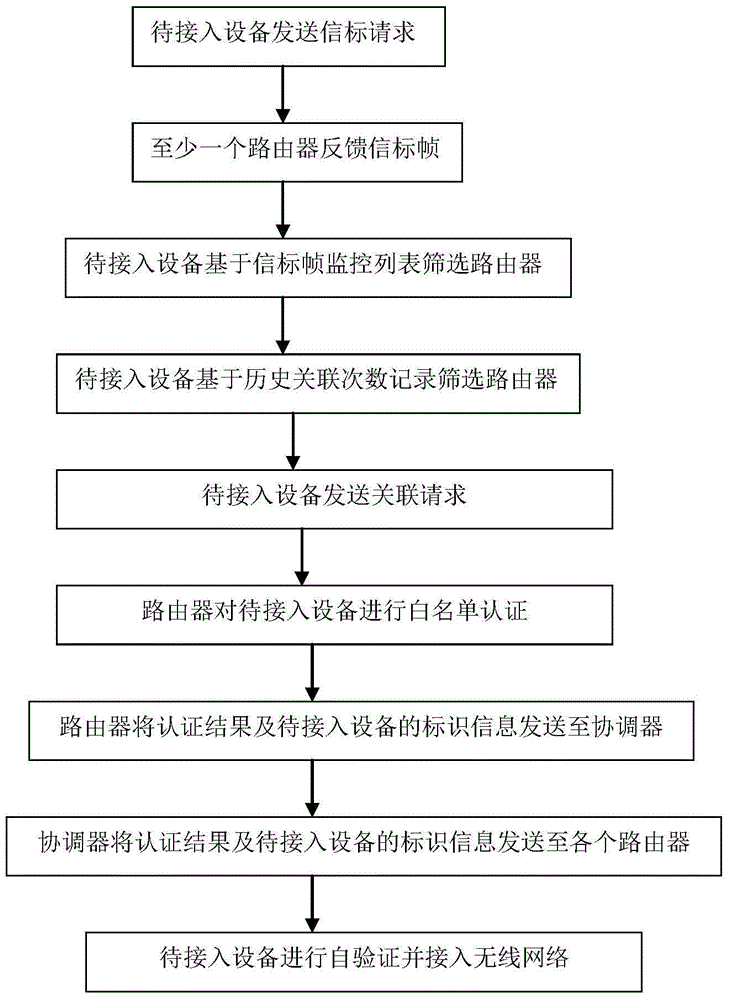
Wireless network system and wireless network access method
ActiveCN105072613AImprove securityIncrease success rateAssess restrictionTransmissionAccess methodWireless mesh network
The invention relates to a wireless network system and a wireless network access method. The wireless network system comprises a coordinator and at least one router; the router is selected by equipment to be accessed based on a beacon frame monitoring list, and the router is provided with a white list for authenticating the equipment to be accessed; the coordinator is used for transmitting an authentication result of the white list and identification information of the equipment to be accessed to each router so as to accept / reject a re-connecting request of the equipment to be accessed. Through beacon frame buffer screening for the router, the wireless network system and the wireless network access method of the invention not only could filter ineffective or malicious equipment to be accessed, but also could select to obtain the most effective equipment to be accessed according to historical linkage times, thereby improving the safety performance of the wireless network.
Owner:CHENGDU CENTURY PHOTOSYNTHESIS TECH
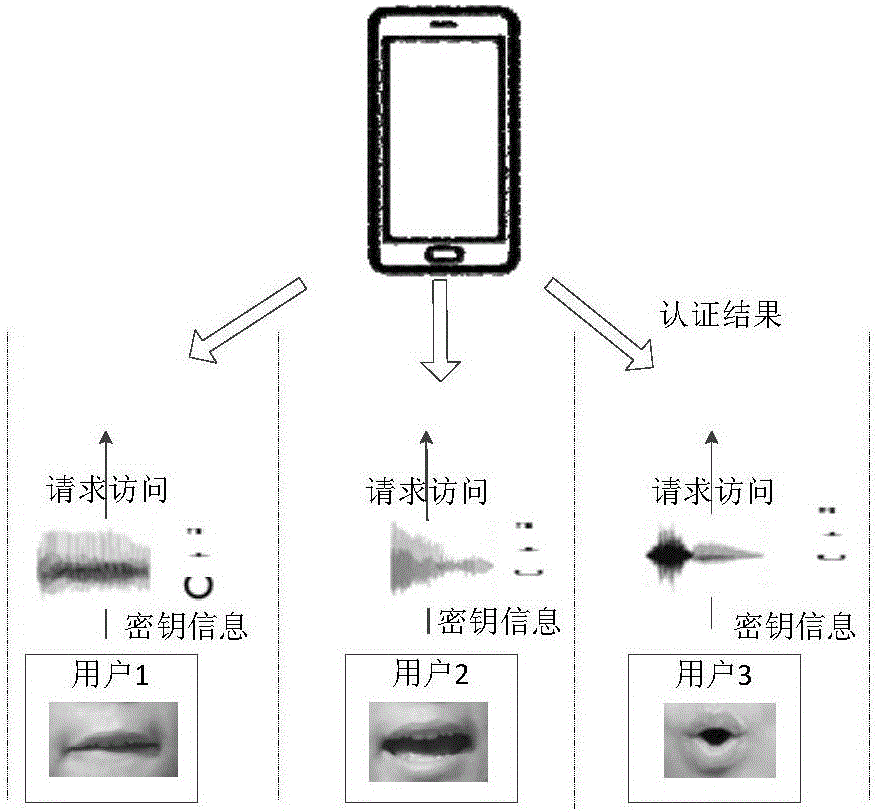
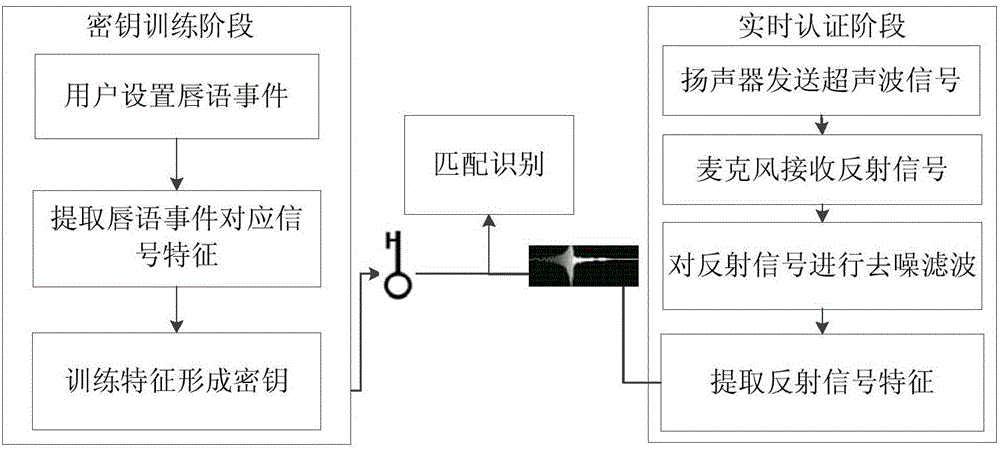
Identity authentication method based on ultrasonic lip-reading recognition
ActiveCN106778179AAvoid security breachesLower deployment costsDigital data authenticationFrequency spectrumFeature extraction
An identity authentication method based on ultrasonic lip-reading recognition comprises the steps of (1) transmitting, by a signal transmitting source, an ultrasonic signal, and receiving, by a signal receiving source, a reflected signal from the mouth; (2) extracting lip-reading characteristics from the reflected signal acquired which include spectral characteristics corresponding to a lip-reading event and dynamic lip outline characteristics of a user; (3) recognizing and authenticating the user according to the lip-reading characteristics extracted in step (2). The identity authentication method has the advantages that identity authentication characteristic parameters are acquired through ultrasonic sensing capacity without extra hardware customization, the deployment cost is low, and the applicable range of ultrasonic technology in mobile terminals is widened; the security vulnerabilities in the existing techniques such as facial recognition and fingerprint recognition are solved by taking advantage of differences between behavior habits of users expressing a same lip-reading event in conjunction with biological characteristics, and efficient identity authentication can be achieved.
Owner:NANJING UNIV
Method And System For Operating A Primary PC From A Remote Pseudo-mobile PC
InactiveUS20110113121A1Safe storageAvoid the needStatic indicating devicesMultiple digital computer combinationsMain processing unitTransceiver
The method and system allows a remote user to virtually access and use software in his / her primary processing unit from remotely located mobile input / output device which can comprise a display, keyboard, mouse, and a transceiver. The only function of the mobile input / output device is to send input signals to the remotely located primary processing unit where they are processed and transmitted back to the mobile input / output device for display and use by the user. Input sent from the mobile input / output device to the primary processing unit is in the form of raw, unprocessed electronic signals. The mobile input / output device uses computing power of the primary processing unit; the CPU, applications, files and services of the primary processing unit to process the electronic signals. The mobile input / output device needs only very limited power, and does not require its own software and associated hardware to duplicate data processing or storage functions.
Owner:SARKAR AMIT
Method, apparatus, and computer-readable recording medium for authenticating a user
InactiveCN104169933AAvoid security breachesIncrease success rateDigital data authenticationTransmissionPattern recognitionUser authentication
Provided are a method, apparatus, and computer-readable recording medium for authenticating a user. The user authentication method includes obtaining an image including a face and a face movement by driving a camera to extract feature information on a facial image and a movement pattern from the obtained image, and comparing the extracted feature information on the facial image with feature information on a facial image registered in a storage and, when the extracted feature information matches the registered feature information, comparing the extracted movement pattern with a movement pattern registered in the storage and, when the extracted movement pattern matches the registered movement pattern, unlocking a device.
Owner:INTEL CORP
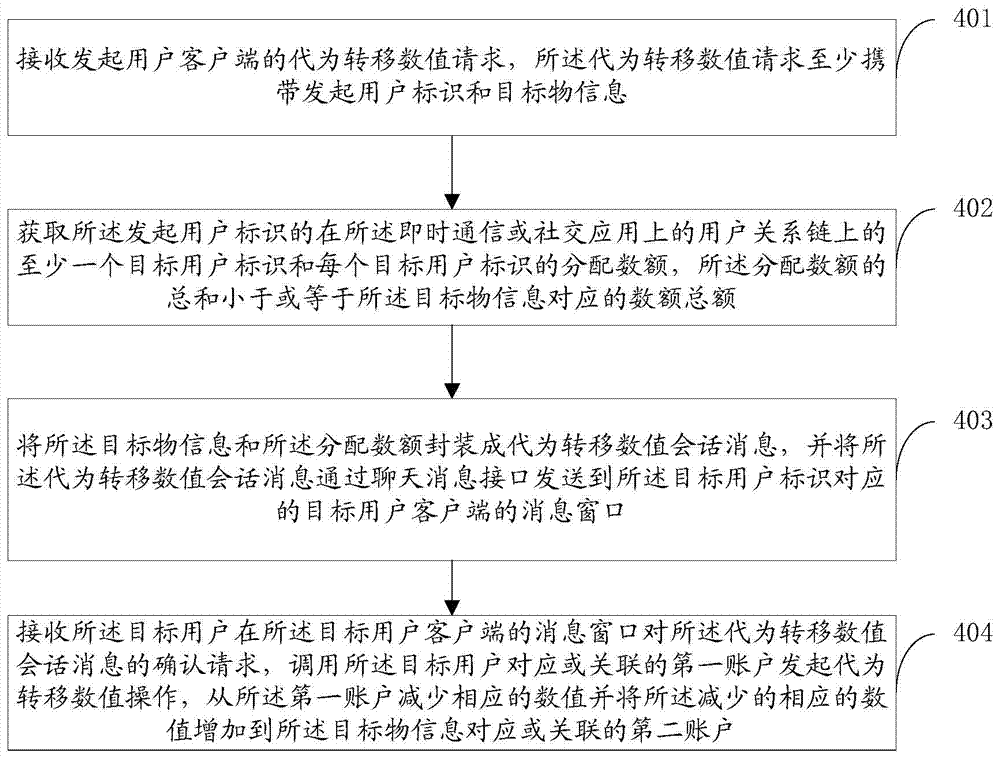
Data processing method and device based on instant messaging or social applications
ActiveCN104753907ANot easy to tamper withImprove securityData switching networksProtocols using social networksData AppliedInstant messaging
Adata processing methodis implemented in a system including a processor. The system receives a request for transferring amount from an initiating user client, where the request includes an initiating user identification and target information. The system obtainsa target user identification and an allotted amount of the target user identification based on the received request, wherein the allotted amount is smaller than or equal to a total amount corresponding to the target information. The systemencapsulates the target information and the allotted amount in a dialog message, and sending the dialog message to a message window of a target user client corresponding to the target user identification. The systemreceives a confirmation request from the target user for confirming the dialog message on the message window of the target user client, then subtracts a corresponding amount from a first account and adds the corresponding amount to a second account.
Owner:TENCENT TECH (SHENZHEN) CO LTD
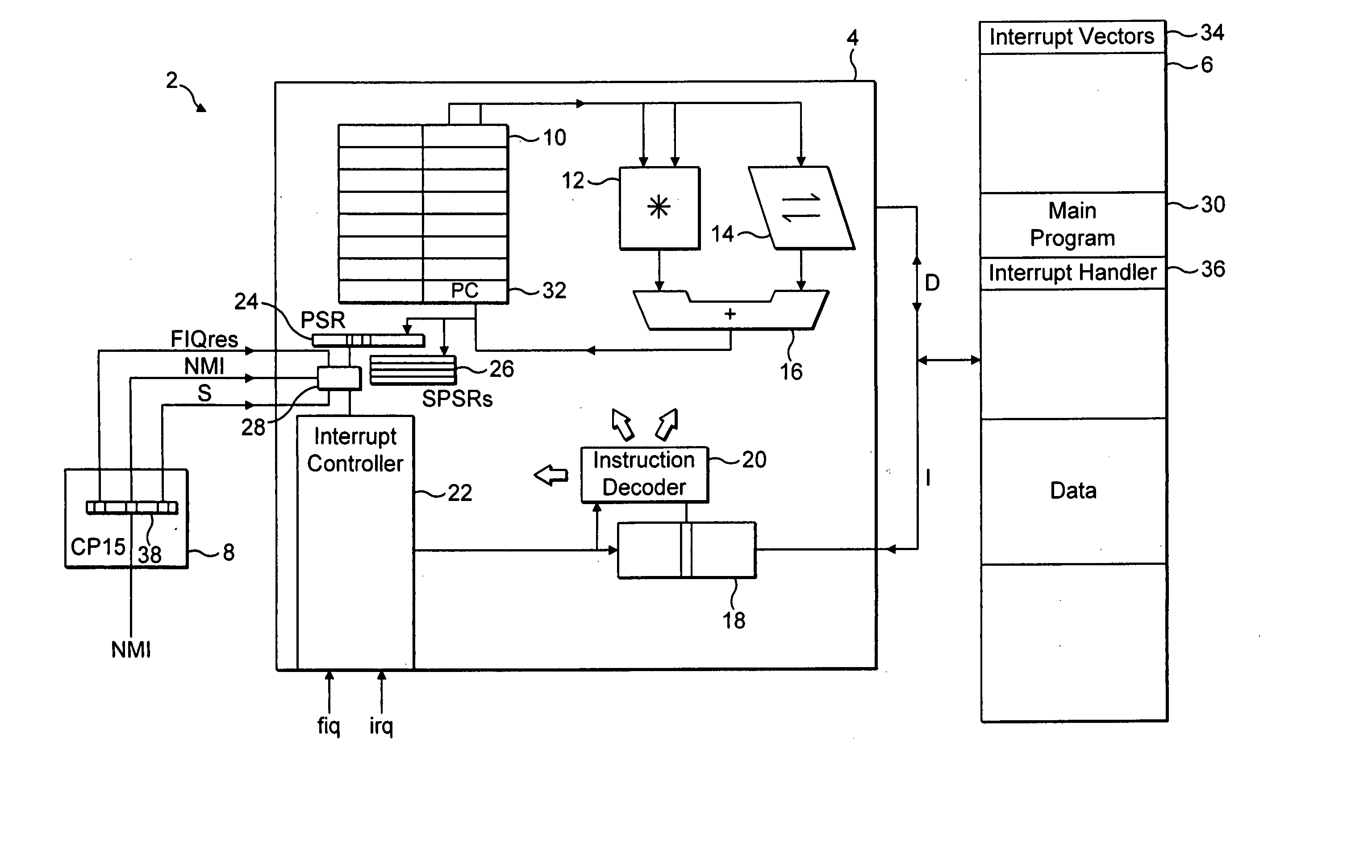
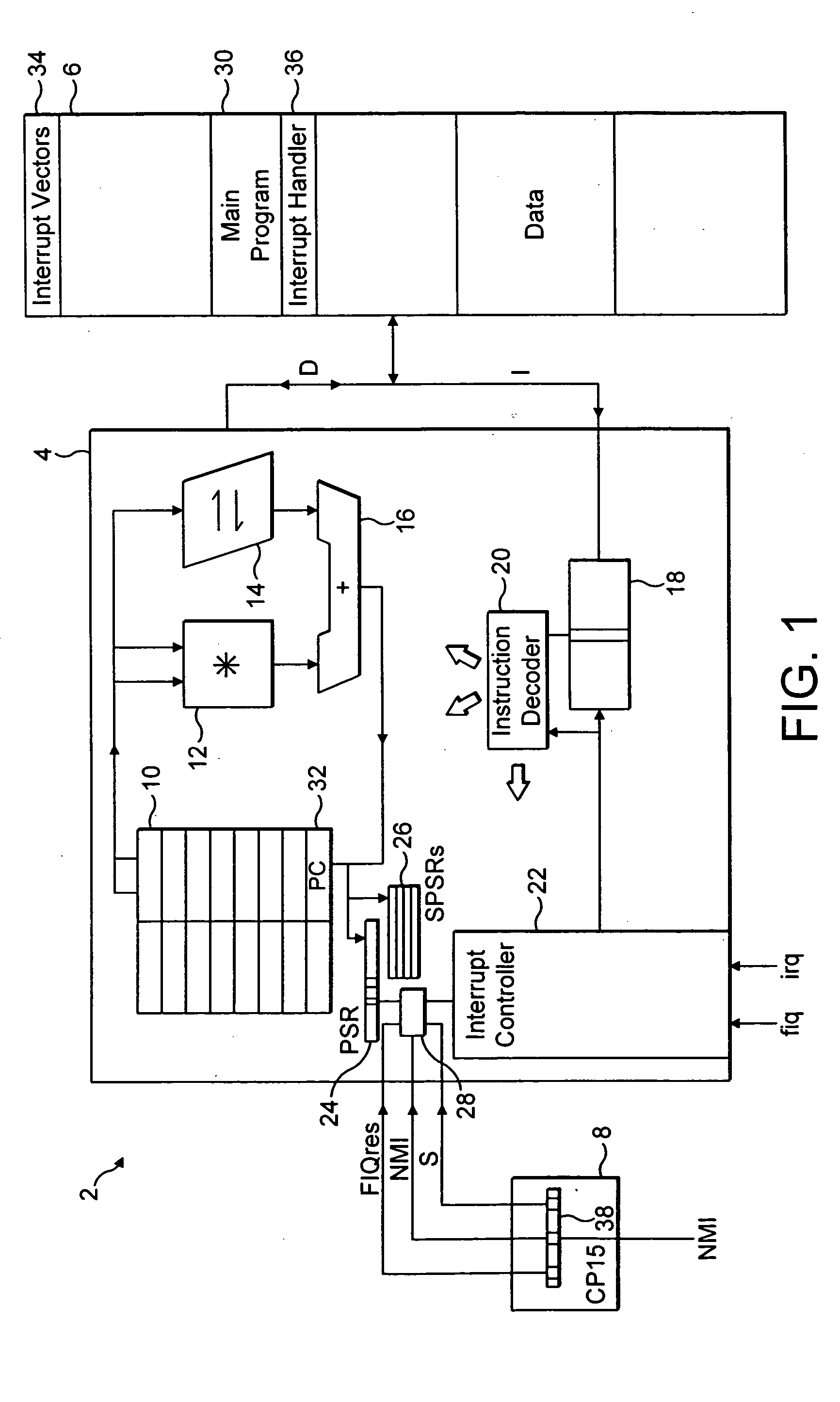
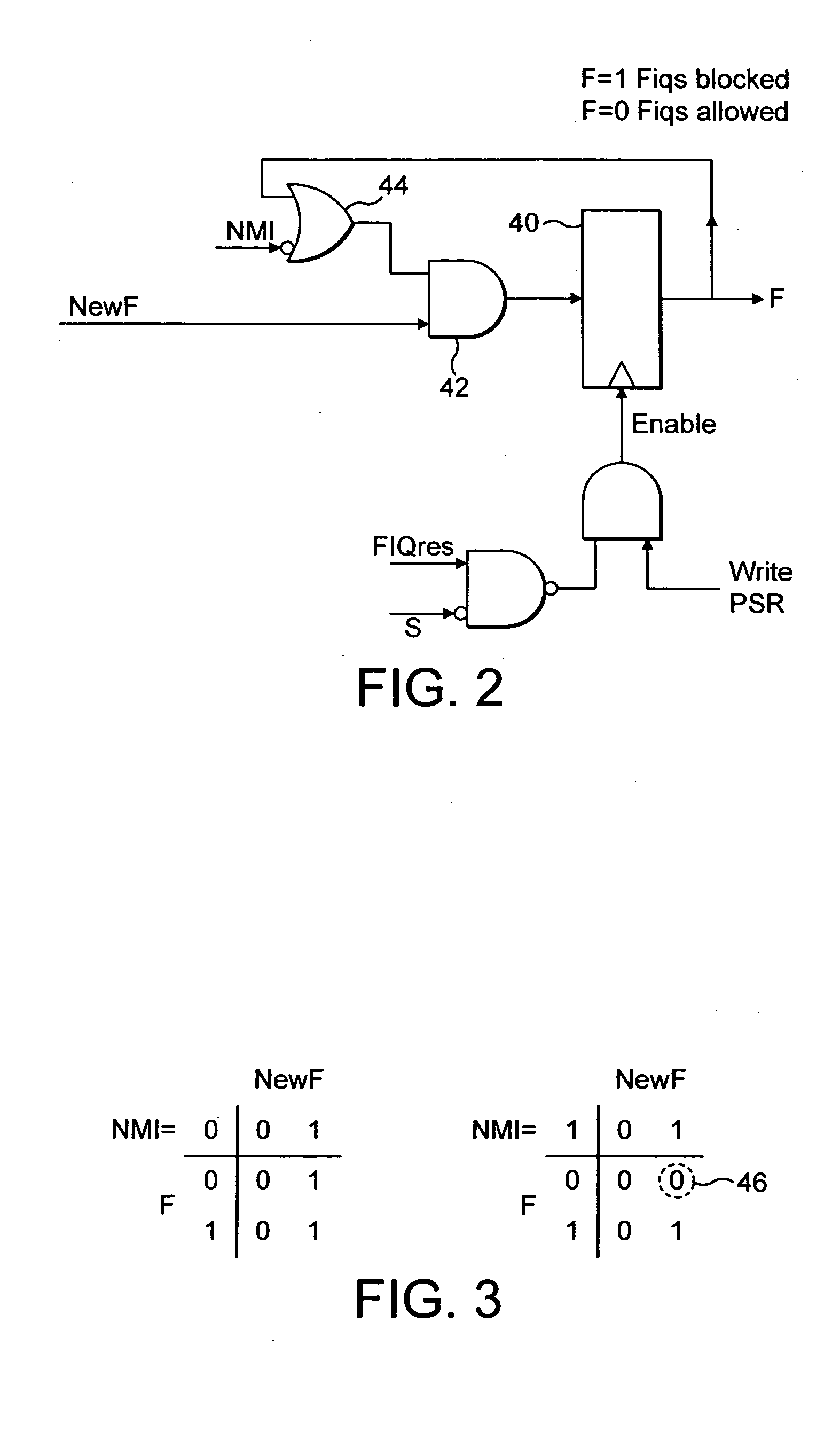
Interrupt masking control
ActiveUS20050138257A1Avoid security breachesProgram initiation/switchingMemory systemsControl signalEmbedded system
A processor core 4 is provided with an interrupt controller 22 which serves to set an interrupt mask bit F and a hardware control when an interrupt fiq occurs. A masking control signal NMI serves to either allow or prevent the software clearing of the interrupt mask bit F.
Owner:ARM LTD
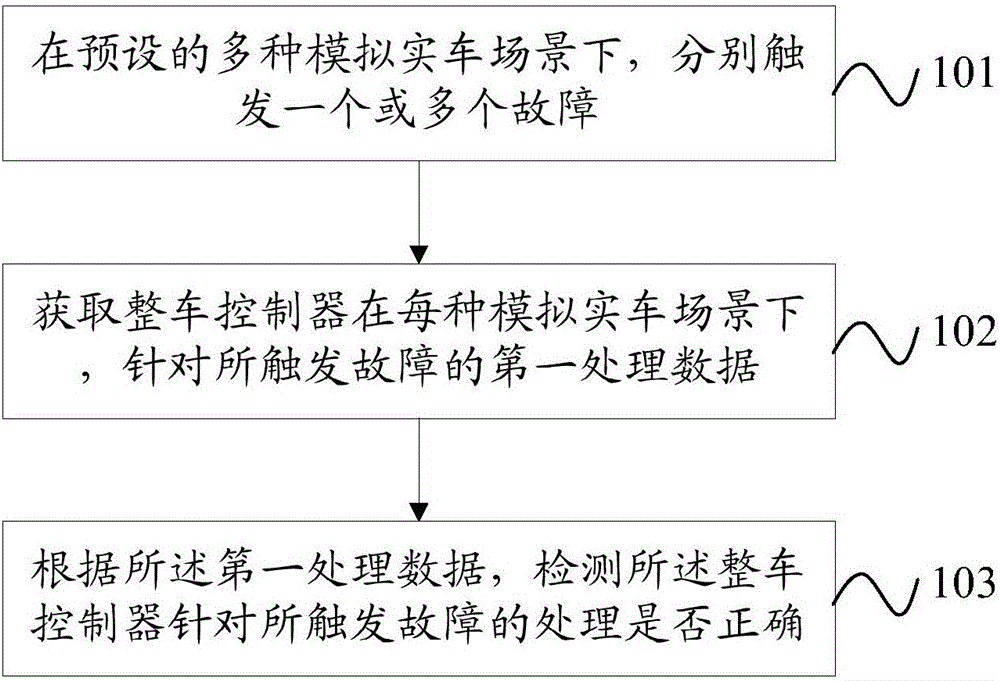
Method and device for testing failure processing of vehicle control unit
ActiveCN106155042AImprove satisfactionAvoid security breachesProgramme controlElectric testing/monitoringEngineeringMultiple failure
The invention provides a method and a device for testing the failure processing of a vehicle control unit, relating to the technical field of automobile testing. According to the method and the device, the problem of incomplete testing cover degree of relevant tests of the vehicle control unit in the prior art is solved. The method comprises the following steps: respectively triggering one or more faults in multiple preset simulated real vehicle scenes; acquiring first processing data aiming at a trigger failure of the vehicle control unit in each simulated real vehicle scene; and detecting whether the processing, aiming at the trigger failure, of the vehicle control unit is correct according to the first processing data. According to the scheme, multiple failures can be simultaneously triggered, and the comprehensive testing of multiple simulated real vehicle scenes is realized, so that the testing cover degree is increased, the real vehicle testing risk is reduced, the product quality is guaranteed, and the satisfaction degree of a consumer is increased.
Owner:BEIJING ELECTRIC VEHICLE
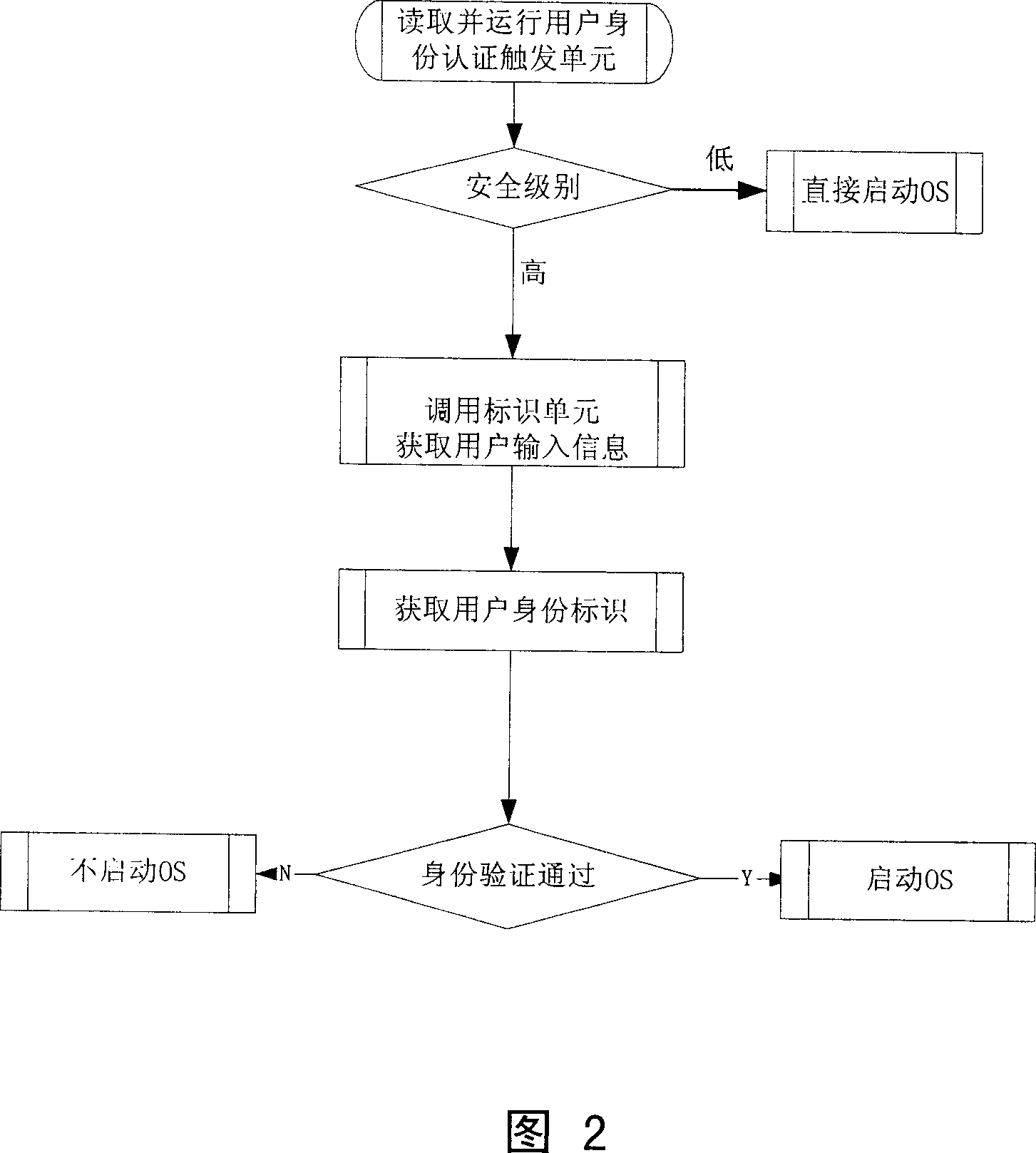
Computer system of bottom identity identification and method therefor
InactiveCN1936761AFix security issuesAvoid security breachesDigital data processing detailsSecuring communicationOperational systemManagement unit
A computer system and method for the bottom identity authentication, it contains the trigger unit for the identity authentication of the users of EFI (21), The identification unit of the identity of the users of EFI (22), the certification unit of the identity of the users of EFI (23), and the management unit of the safety for the EFI. The trigger unit for the identity authentication of the users of EFI (21) will be started after the users has started the computer system and finished the initialization of the platform. It will judge the safe grade of the computer system and enter directly the start of the operation system or execute the next step according to the safe grade assigned. It will remind the users to execute the identity authentication, and the users must input information. And then the identification unit of the identity of the users of EFI (22) will be started to obtain the identification information of the users. The certification unit of the identity of the users of EFI (23) will be activated to verify the legitimacy of the identity information of the user. The operation system will be started if the users is legitimate, otherwise, the operation of the user will be refused and not to start the operation system. The method is easy and useful, and has some advantages, such as the supporting function and the applicability of it are very strong.
Owner:LENOVO (BEIJING) CO LTD
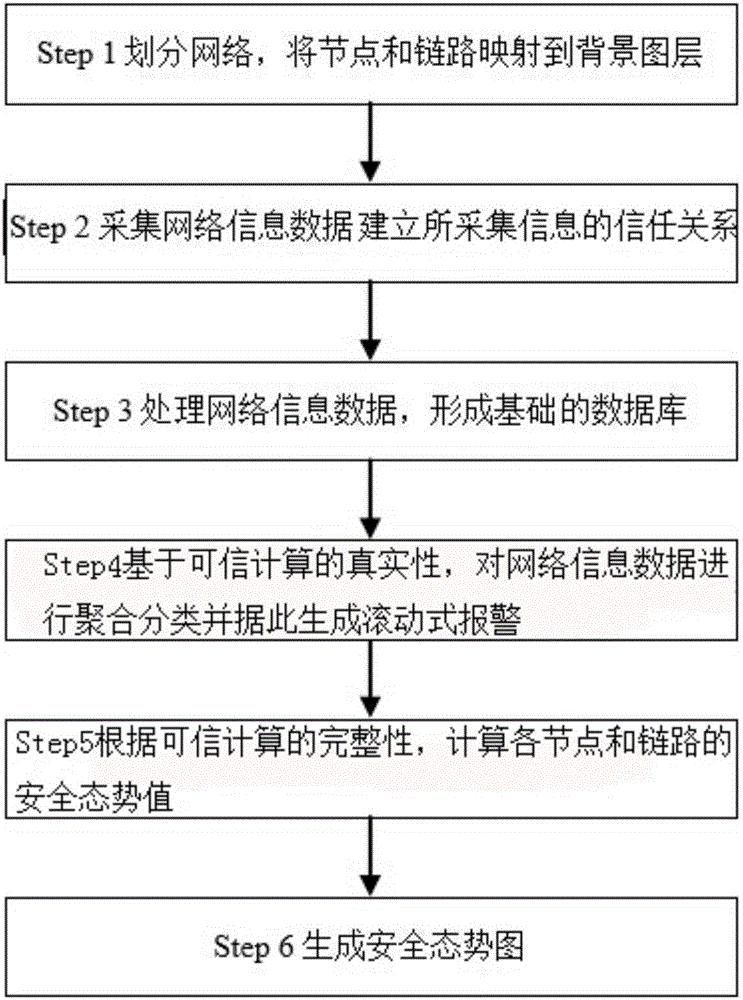
Method for generating big data security posture map based on trusted computing
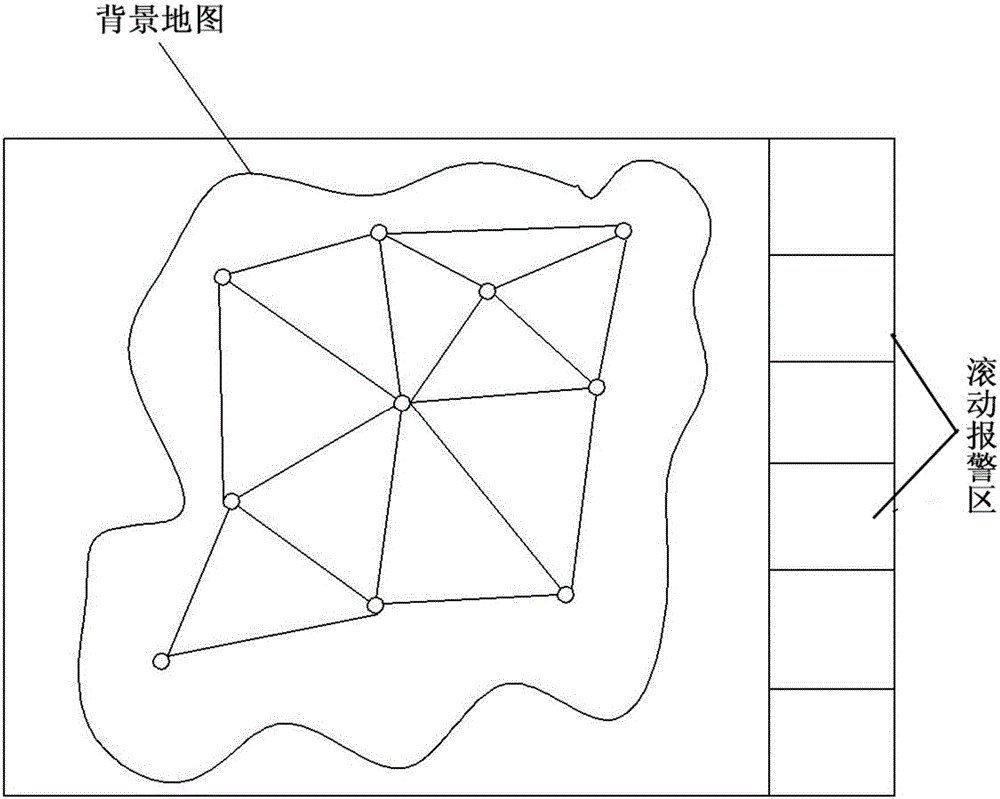
ActiveCN106209856AEnsure comprehensivenessDiversity guaranteedTransmissionSecurity bugBig data security
The invention provides a method for generating a big data security posture map based on trusted computing. The method for generating a trusted security posture map based on a geographical map, security data acquisition and the like, the credibility of information data acquisition of a trusted network is guaranteed, and alarm information is filtered and aggregated based on an algorithm for degree of nearness; events which cannot affect the security are removed from the normal alarm, so that the security hole is avoided while the disturbance to a monitor is reduced; the authenticity of trusted security behaviors of the posture map is higher; an overall map generation trusted environment from trusted data acquisition to merging and filtering to alarm generation and posture map generation is constructed, so that the trusted security, the integrity and the authenticity of the security posture map are guaranteed, the credibility of the posture map is guaranteed, and a trusted access and display mechanism is constructed on the basis of characteristics with a protection function, authentication and integrity measurement and the like.
Owner:重庆市大夔文化传播有限公司
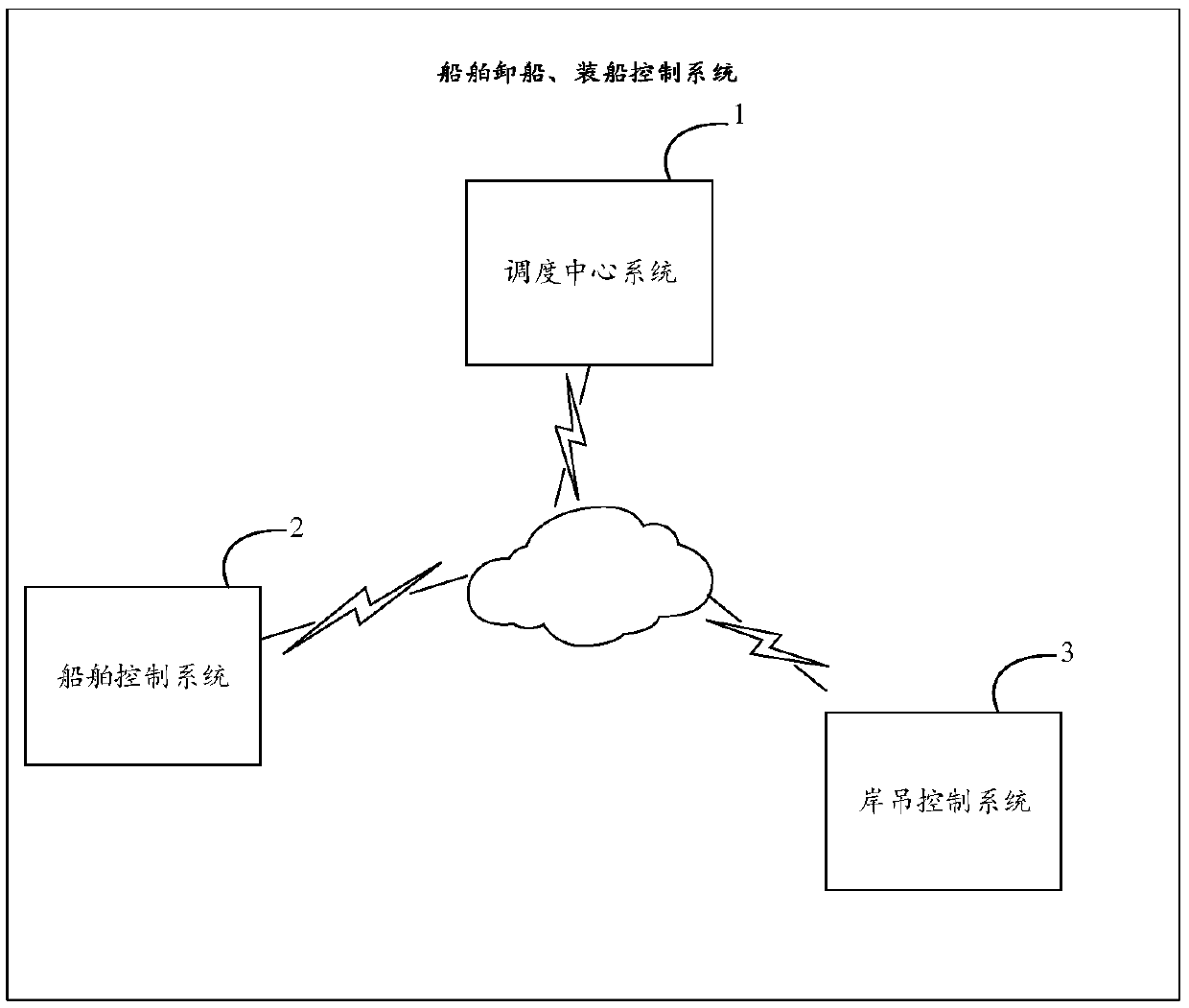
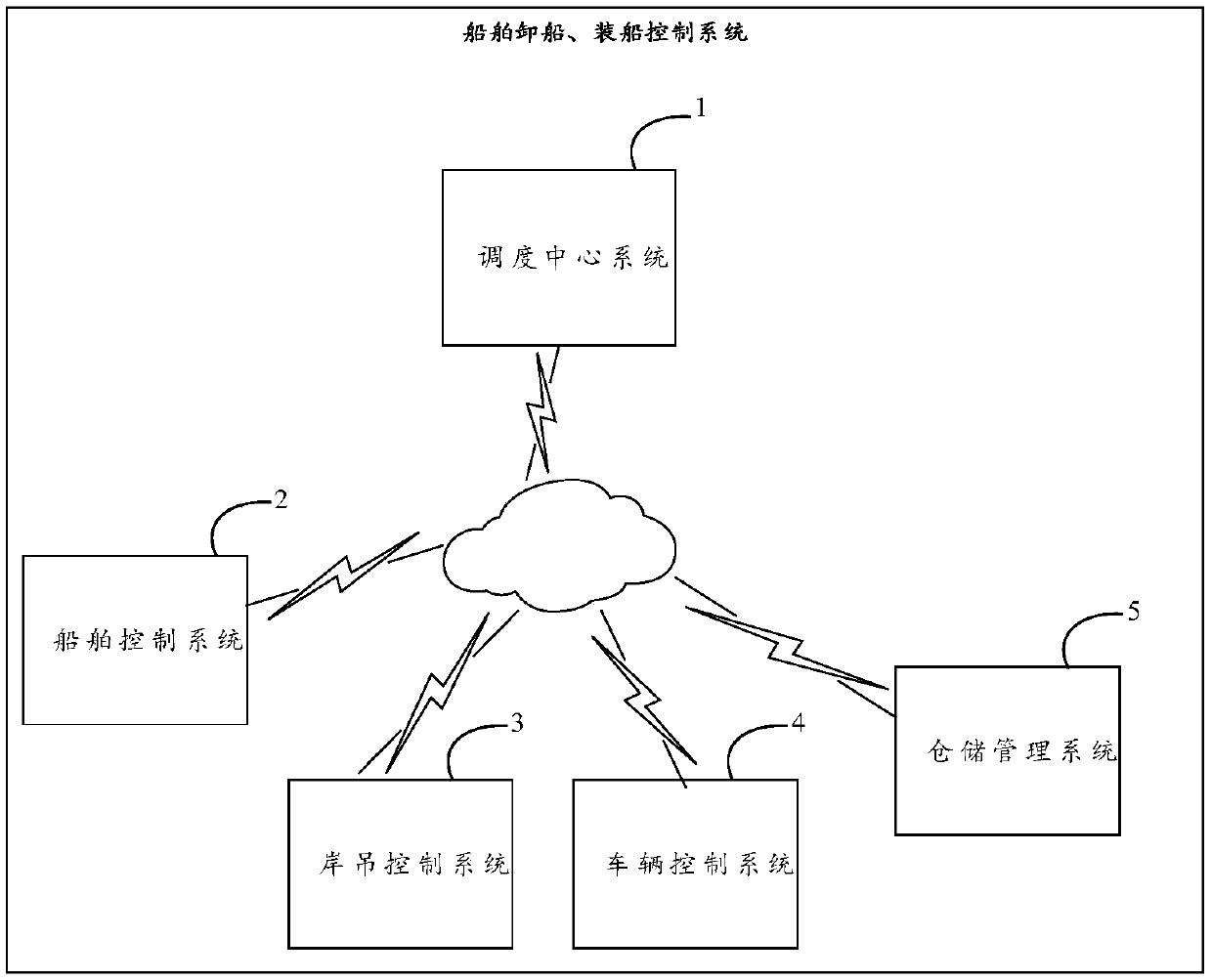
Ship unloading and loading control system and related system and device
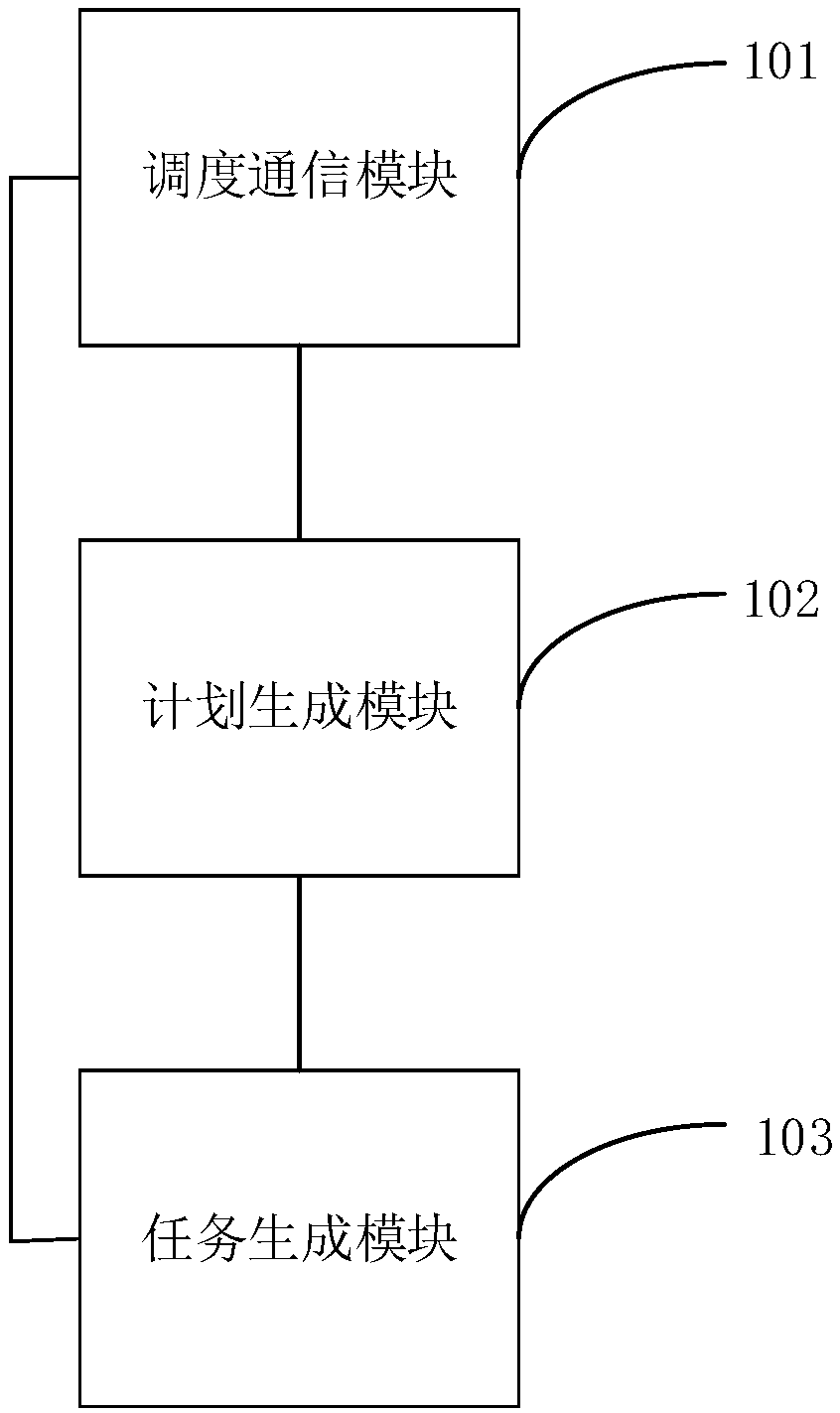
PendingCN109685435AReduce human resource investmentReduce labor cost investmentSteering initiationsOffice automationShoreCrane Equipment
The invention discloses a shipping unloading and loading control system and related systems and devices, which can achieve full automation of ship loading and unloading; The ship unloading control system comprises the dispatching center system generates a ship unloading plan according to the ship information of the target ship, the container information and the shore crane equipment information, generates a ship unloading task and a ship berthing task according to the ship unloading plan, and sends the ship berthing task and the ship unloading task to a ship control system of the target ship and a shore crane control system of the target shore crane equipment respectively; The ship control system sends ship information and container information to the dispatching center system, controls atarget ship to run to an operation area corresponding to the target shore crane equipment according to the received ship berthing task, and sends a ship in-place notification message to a shore cranecontrol system of the target shore crane equipment; And when the shore crane control system receives the ship in-place notification message from the ship control system, the shore crane control systemcontrols the target shore crane equipment to load the container on the target ship to the vehicle according to the ship unloading task.
Owner:BEIJING TUSEN ZHITU TECH CO LTD
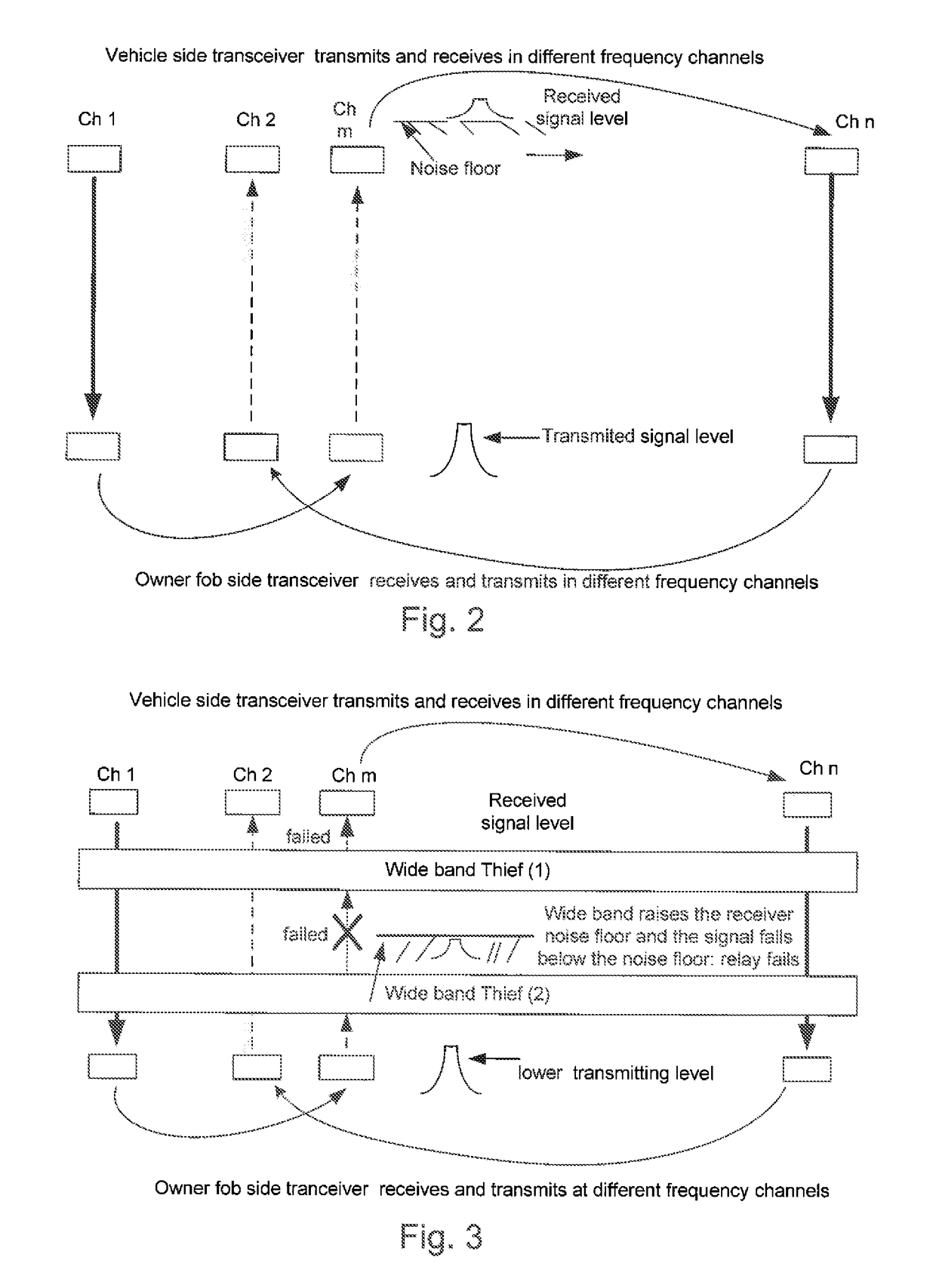
Anti-theft remote keyless entry system using frequency hopping with amplitude level control
InactiveUS20170320465A1Avoid security breachesAnti-theft devicesIndividual entry/exit registersEngineeringVIT signals
A method for defeating a two-thief attack on a passive RKE system by using frequency hopping. Radio frequency signals are transmitted between a fob and a vehicle. The transmitted signals hop between at least two radio frequency transmitting channels in a particular pseudo-random pattern known to the vehicle. At the vehicle, the transmitted signals are received in a process that is sequentially adjusted to take account of the known characteristics of each portion of the known pattern. Anomalies in the pattern of the received signals are detected and, if the anomalies exceed permissible limits, access to said vehicle is blocked.
Owner:TRW AUTOMOTIVE US LLC
Method for realizing access layer security, user equipment, and small radio access network node
ActiveCN106375989AEasy to moveEnsure safetyAssess restrictionNetwork topologiesData transmissionRadio access
The invention discloses a method for realizing access layer security, user equipment, and a small radio access network node. The method comprises: end-to-end user plane access layer security between user equipment (UE) and a gateway node is executed; and when a micro-communication path exists at the UE, end-to-end control plane access layer security between the UE and an initial access node is executed; and or when a micro-communication path and a macro-communication path exist at the UE, end-to-end control plane access layer security between the UE and a macro eNB in the macro-communication path is executed. The micro-communication path is a communication path in which the UE is connected to a small radio access network node by a radio access link and then is connected to a core network and the macro-communication path is a communication path in which the UE is connected to the macro eNB by a radio access link and then is connected to a core network. Because the user plane security is only executed in an end-to-end mode between the UE and the gateway, the user plane security is guaranteed well; and the control plane security is only executed in an end-to-end mode between the UE and the initial access node or the macro eNB, so that the time delay of the control plane security operation is reduced on the premise that the control plane security is guaranteed. Meanwhile, the mobility performance of the UE is improved; and continuity of user plane data transmission of the UE is guaranteed.
Owner:ZTE CORP
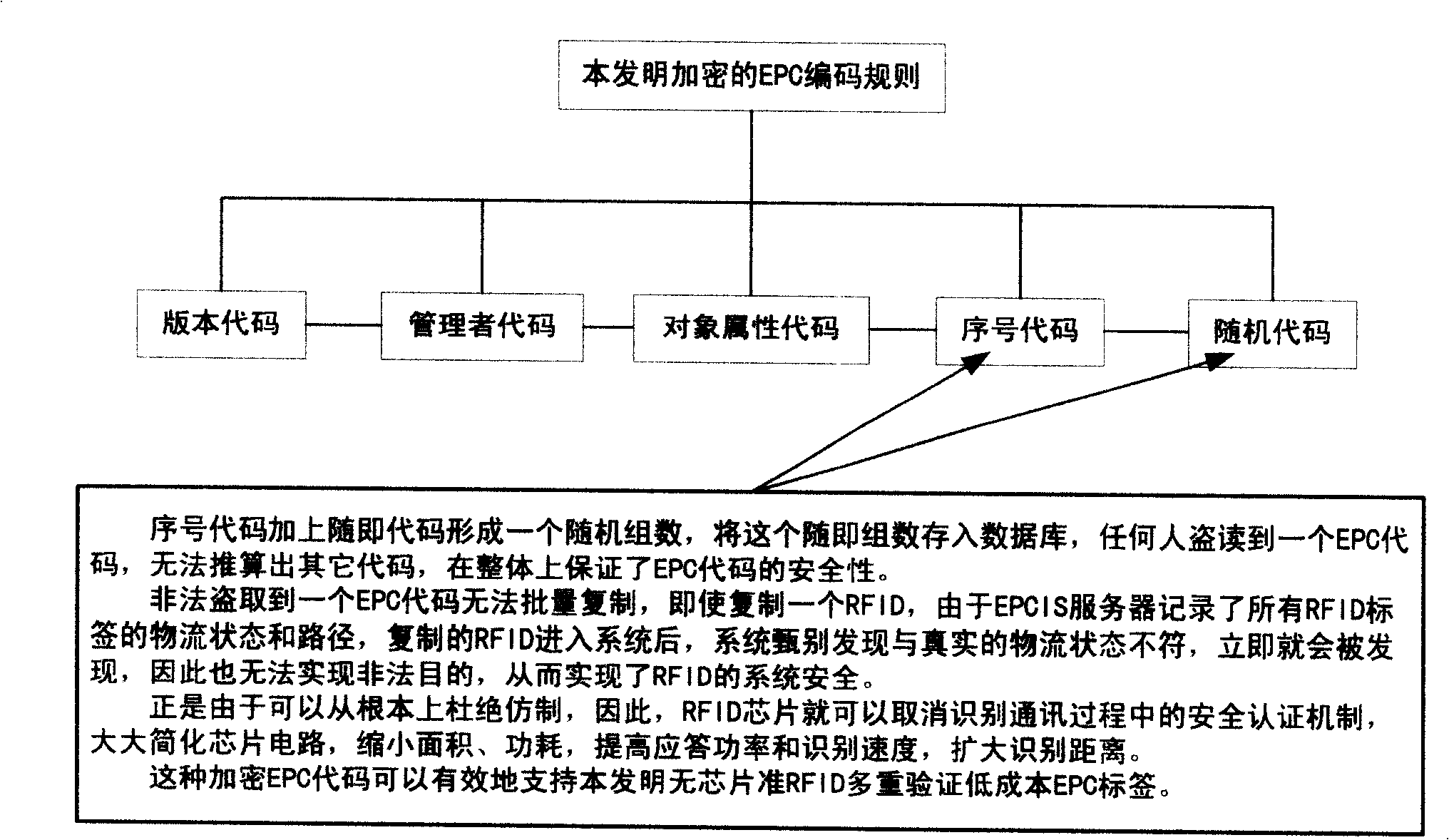
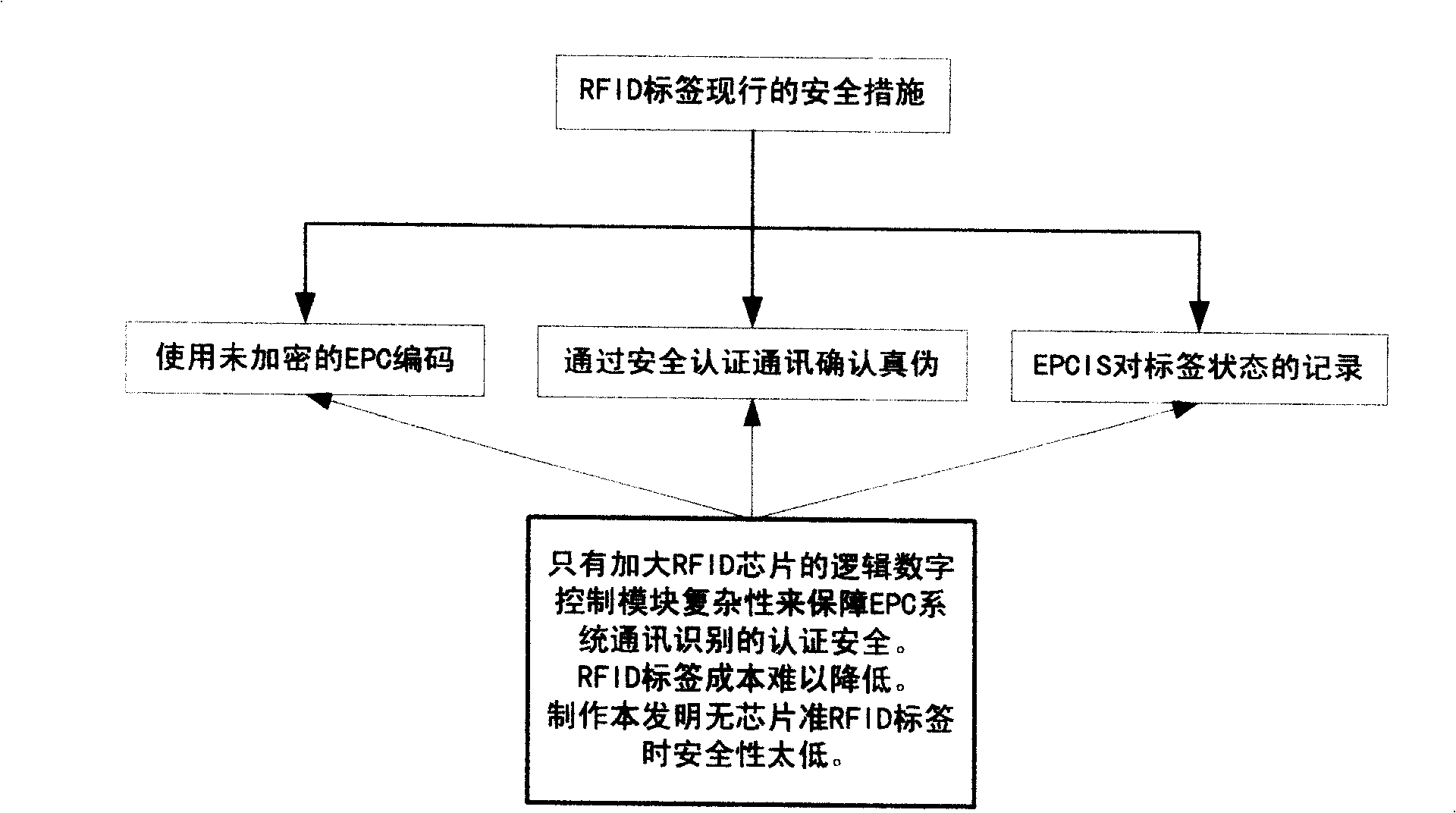
Chip-free quasi RFID multiple verification low cost encrypted EPC composite label and system
InactiveCN101286203AImprove securityAvoid security breachesCo-operative working arrangementsRecord carriers used with machinesPlaintextLogistics management
The invention relates to a chipless quasi-RFID multi-verification low-cost encrypted EPC compound label coding method, a manufacturing method and a structure, as well as a computer management system. An EPC product electronic code which is provided with a random encryption code and is randomly corresponding to a sequence code is compiled, a plain-text password which is converted by encryption is printed on a label for covering, the plain-text password is then converted to a bar code to be printed on the label, a digital safety line is used for producing the label, the label is carried out the pre-chopping treatment to prevent the transfer, digits on the safety line are shot and identified, the random encryption EPC code, the plain-text password, the bar code and the digits of the safety line are stored correspondingly, a label anti-counterfeiting inquiry system and a bar code scanning system are both connected with an EPC network, the same product information and the logistics path information can be obtained by the EPC network regardless of artificial recognition and machine identification. The label cost is greatly reduced, the safety is improved, the information redundancy and the application adaptability are expanded, and the seamless connection is updated to RFID labels with other recording forms.
Owner:SICHUAN ZHENGDAOTIANHE INFORMATION TECH
Software service interface calling method and system with high security levels
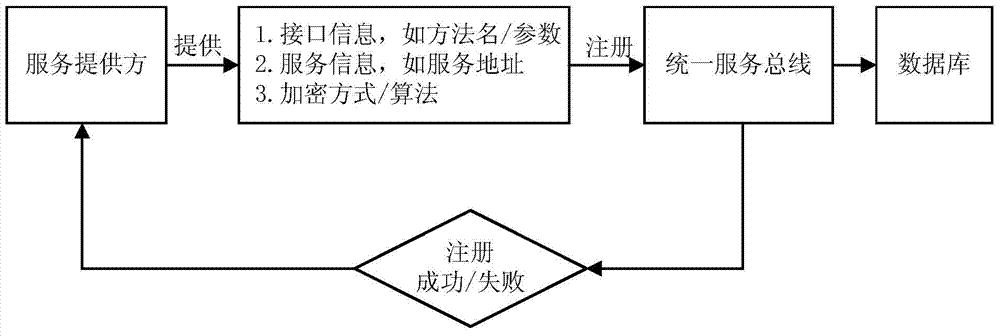
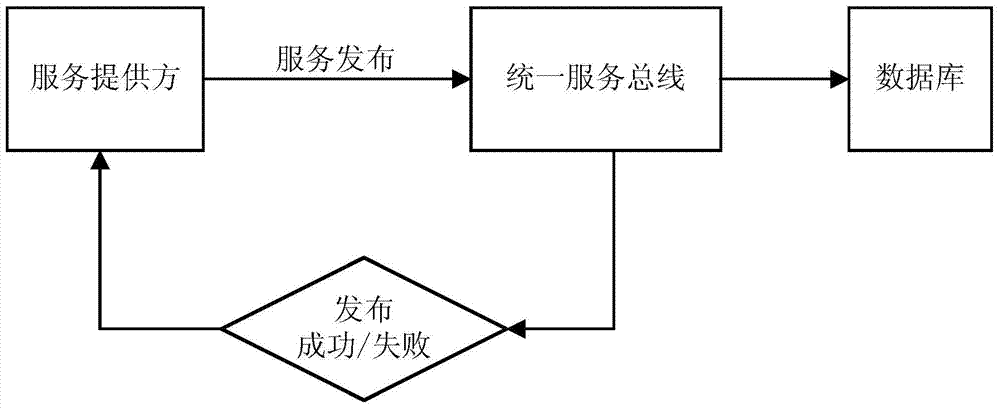
ActiveCN104506486AEnsure safetyAvoid security breachesTransmissionInformation transmissionInformation transfer
The invention relates to a software service interface calling method and system with high security levels. The scheme mainly comprises service management, service publication and service calling. The security and reliability of information transmission can be ensured in the following forms: an interface is implemented through a file transmission layer, and one-way transmission and asynchronous response are adopted; bidirectional secondary encryption is performed in a file transmission process, and the security of data can be ensured, so that security holes caused by the cracking of the key of one side are avoided; links of each application and service are isolated effectively through a service scheduling center, and all calling is performed through a service bus; and a tracing basis is laid through an auditing function. The software service interface calling method and system are suitable for the high-security software manufacturing industry, and can support software service interfaces among different platforms or different development languages.
Owner:RUN TECH CO LTD BEIJING
Data transfer method, device and system
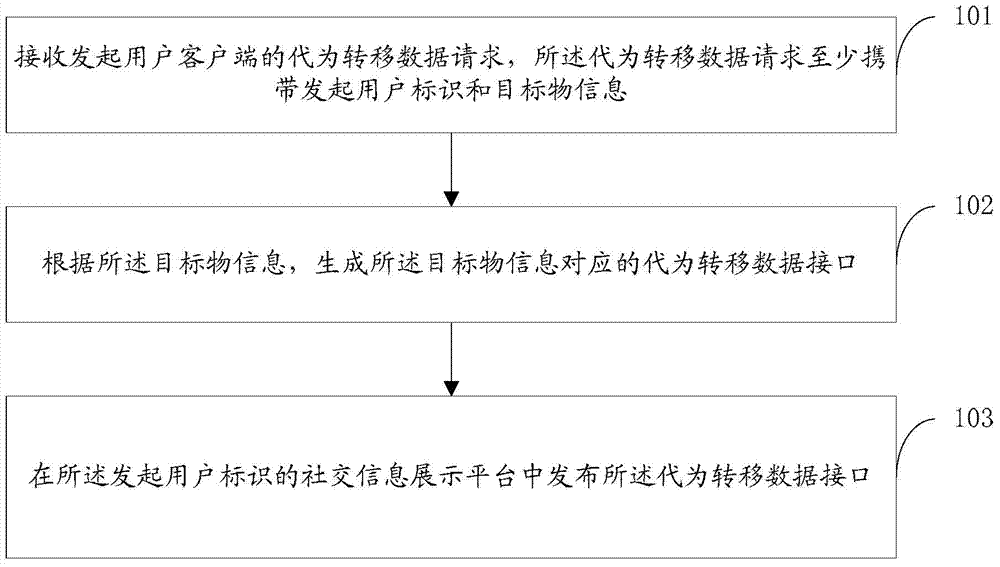
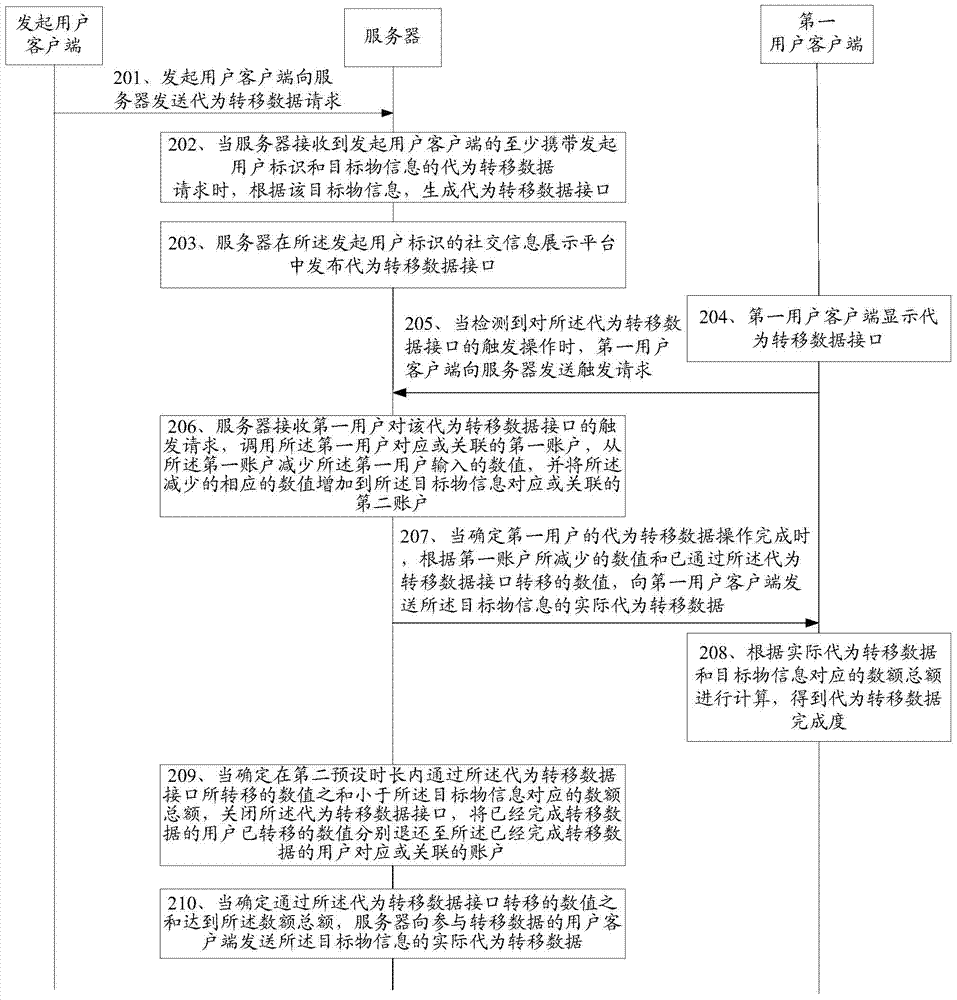
ActiveCN104753906AImprove securityIncrease flexibilityData switching networksProtocols using social networksClient-sideDatabase
In a method, device and system for transferring data, a request is received by a server from an initiating user client for transferring data, where the request includes the initiating user identification and information about a target for which the data is transferred. A data transfer interface that corresponds to the target is created by the server and published on a social information display platform that corresponds to the initiating user identification. When a trigger operation is detected in the data transfer interface from one or more user clients, a trigger request is sent to the server to transfer data from the one or more user's accounts to an account associated with the target information. The method, device and system improve the security of the data transfer process.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Handshake negotiation method and system in safe grade
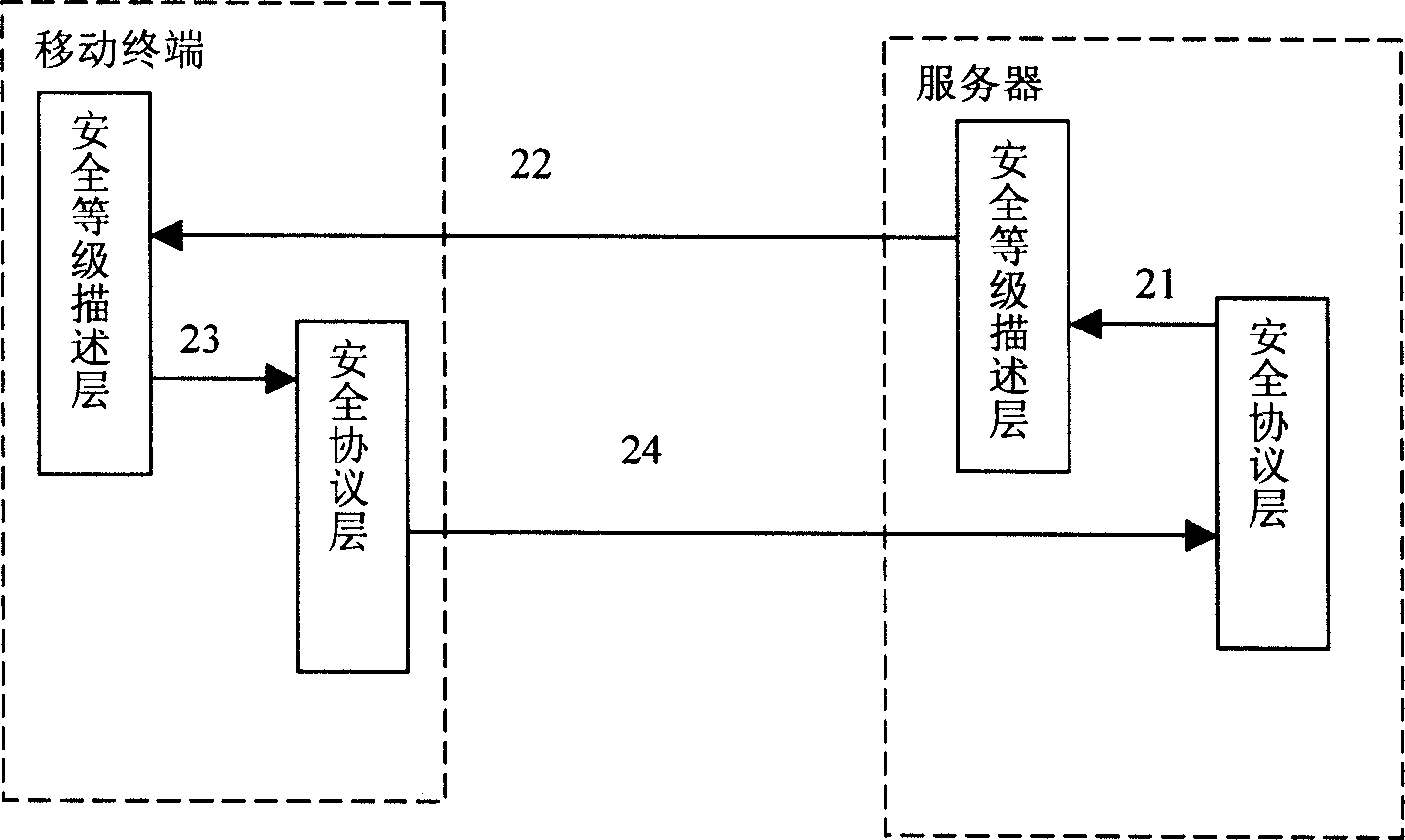
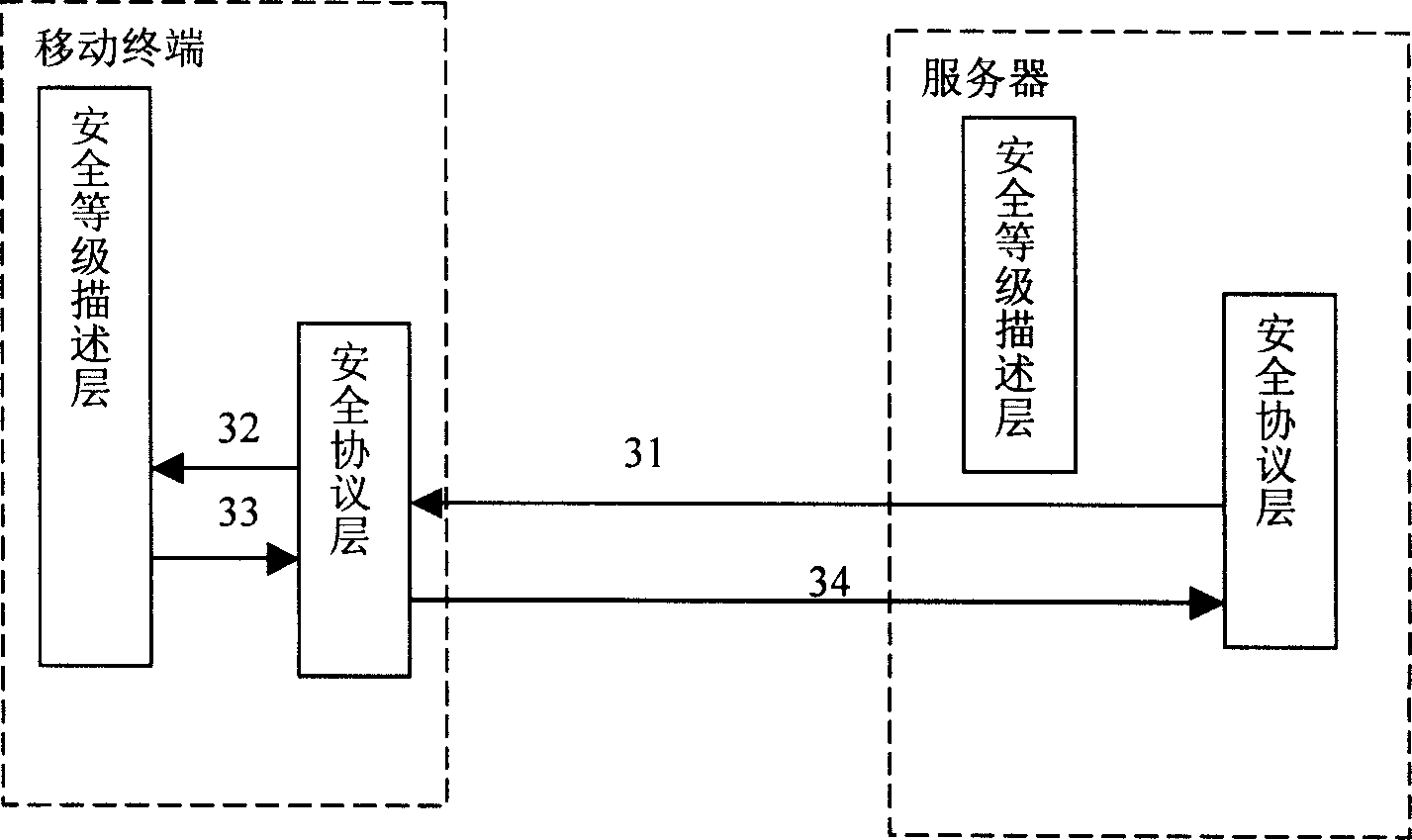
InactiveCN1728632AOptimizationEasy to useSecuring communicationProtocol for Carrying Authentication for Network AccessSecurity level
Security level description layer and security protocol layer are setup at mobile terminal and server. Dividing capabilities of security safeguards into different levels, the security level description layer converts parameters of security protocol from security protocol layer to security levels, and receives information of security level sent from security level description layer of opposite end, as well as converts security level to be sent to security protocol layer to parameters of security protocol. Security protocol layer stores needed parameters of security protocol, and receives parameters of security protocol sent from security protocol layer of opposite end. The invention uses original handshake signaling of security protocol fully to carry out information of level description so as to avoid potential safety loophole if additional signaling for describing security level is added. Advantages are: easy of configuring and using security technique and convenience for charging.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com