Distributed identity-card signature method
A certificate issuance and distributed technology, applied in the field of distributed identity certificate issuance, can solve the problems of reducing the use efficiency of identity certificates, leaking confidential information of certificates, and invalidation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
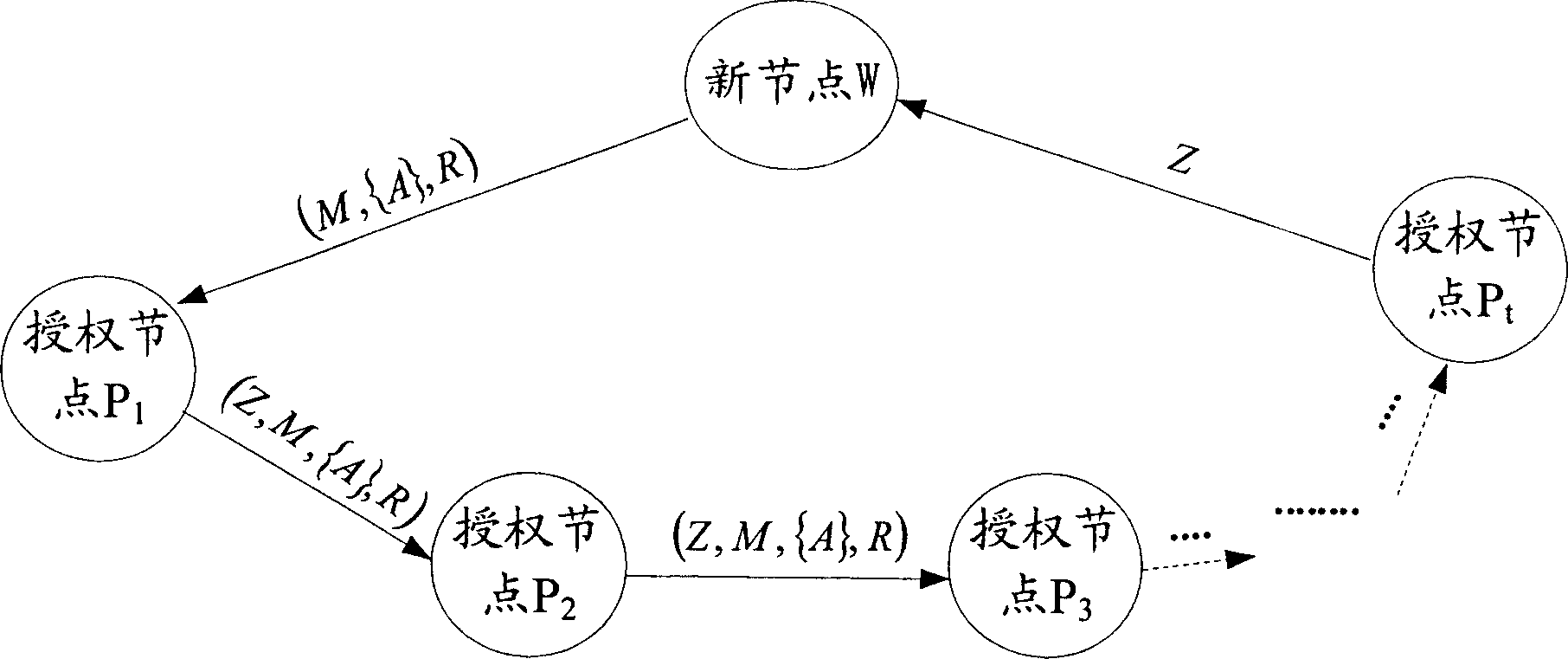
[0037]The process of the method proposed by the present invention is as follows: firstly, the network completes the network initialization in an offline state, determines the authorized node, and issues an identity certificate for the authorized node, and generates and distributes an identity certificate for issuing a new node and completes the identity authentication process at the same time The required parameters; after the initialization is completed, the new node initiates the identity certificate issuance process to the trust group, and the new node selects any t authorized nodes that agree to participate in the identity certificate issuance to form the identity certificate issuance group, and the authorization in the identity certificate issuance group Nodes generate group signatures in a hop-by-hop manner; finally, new nodes generate identity certificates based on the group signatures of the identity certificate issuing group, and then nodes in the network that have iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com