Method for realizing access layer security, user equipment, and small radio access network node
An access layer security and wireless access technology, applied in security devices, access restrictions, wireless communication, etc., can solve problems such as no specific implementation technical solutions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0130] In order to make the purpose, technical solution and advantages of the present invention more clear, the embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined arbitrarily with each other.
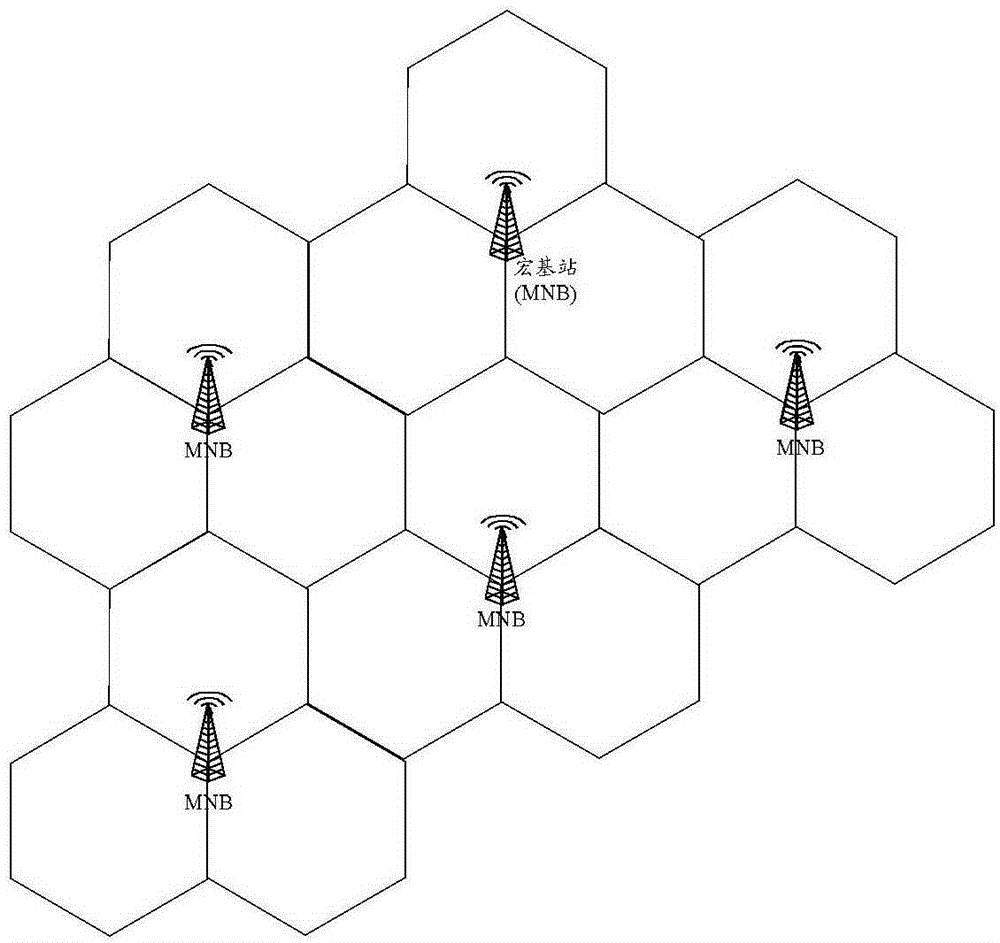
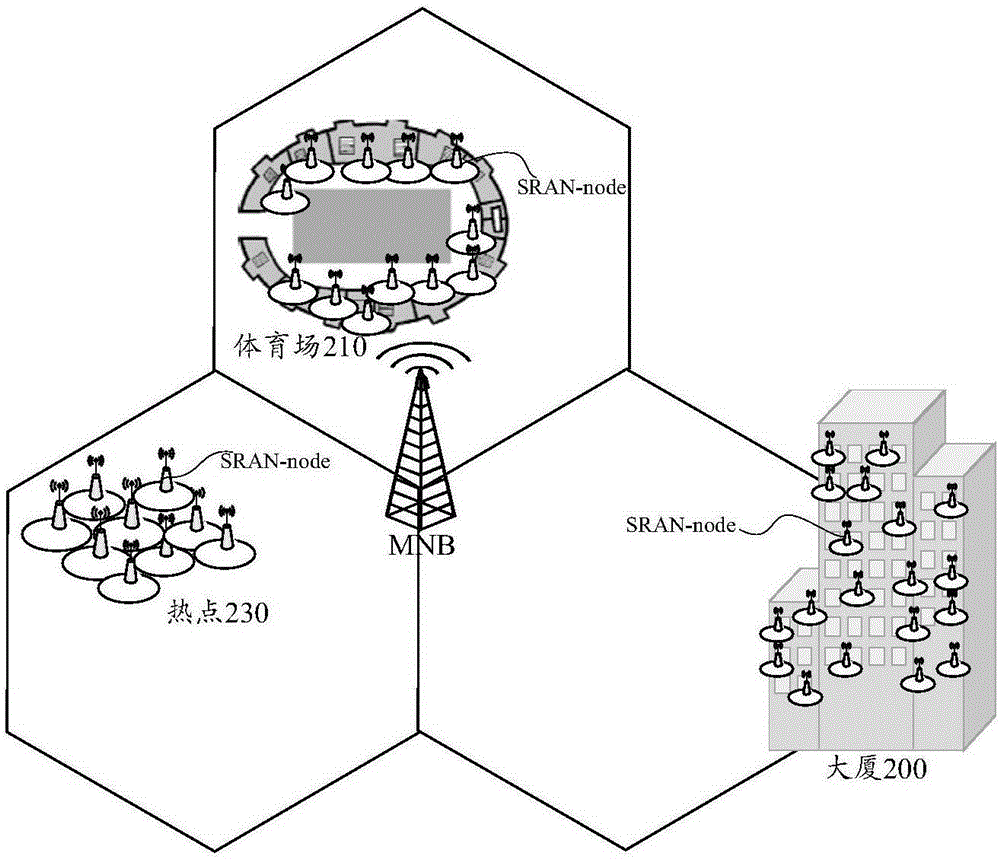
[0131] In order to meet the expectation of a thousand-fold increase in business volume in the next 10 years, UDN will be widely deployed to bear a large amount of business traffic. UDN can be deployed in indoor or outdoor hotspot areas or any areas with large traffic demands. image 3It is a schematic diagram of ultra-dense network deployment in a certain area in the future, taking into account the infrastructure constraints of the actual deployment network, such as the limited number of wired network ports in the area shown, and the realization of flexibility without increas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com