Authentication method based on public key encryption system
An authentication method and public key encryption technology, applied in the fields of network security and information security, can solve the problems of unreliability, increase the complexity of the protocol, and difficulty in time-stamp time synchronization, and achieve the effect of preventing impersonation and resisting replay attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be further described in detail below in conjunction with the examples.
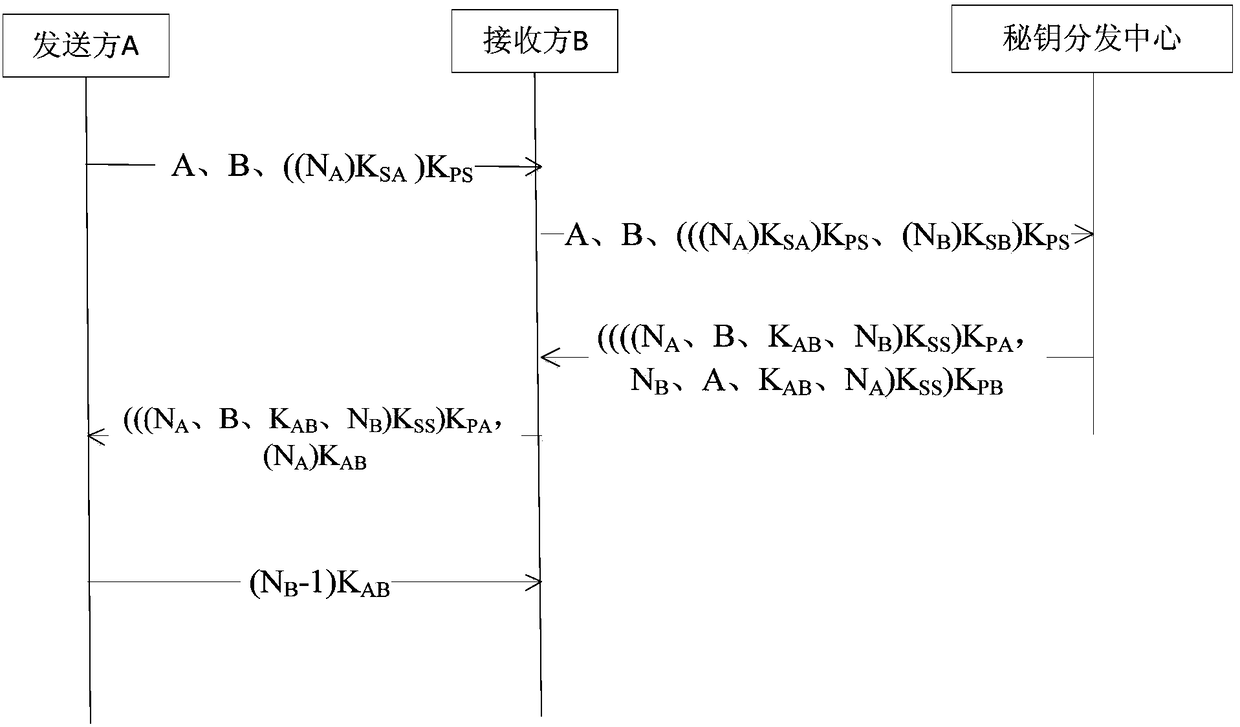
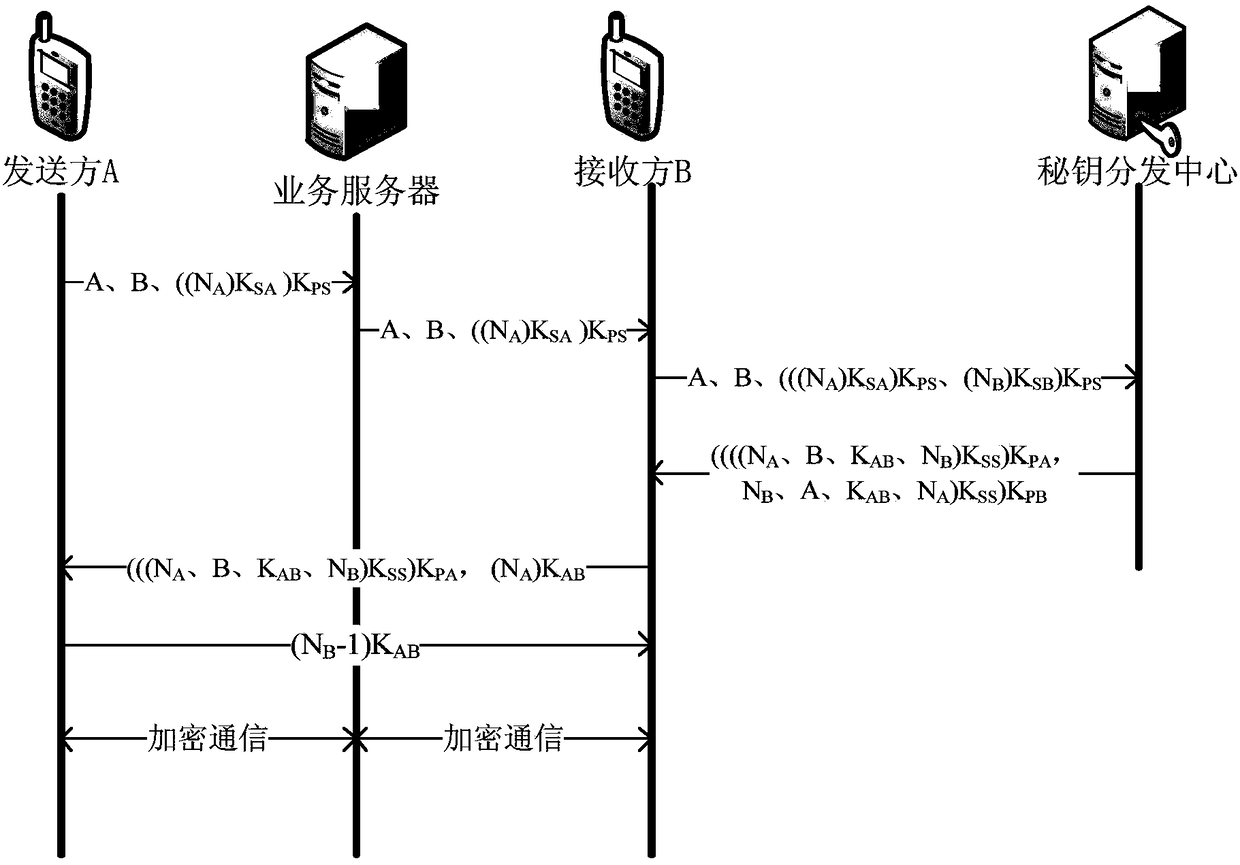
[0032] Such as figure 1 As shown, sender A and receiver B respectively represent client A and client B, an authentication method based on public key encryption system, including two functions of identity authentication and shared session key:
[0033] 1) The sender A and the receiver B send (local) random numbers N to the key distribution center respectively A , N B . The random number uses the private key K of sender A and receiver B respectively SA 、K SB Sign and use the public key K of the key distribution center PS Encryption, where the message sent by A is {A, B, ((N A )K SA )K PS}, the message sent by B is {A, B, (((N A )K SA )K PS , (N B )K SB )K PS} That is, A's message is forwarded by B.
[0034] 2) After receiving the message, the secret key distribution center uses its own private key K SS Decrypt the message and use the public key K of sender A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com