Method for realizing dependable SSH based on dependable computing
A trusted computing and trusted technology, applied in key distribution, to achieve the effect of preventing replay attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
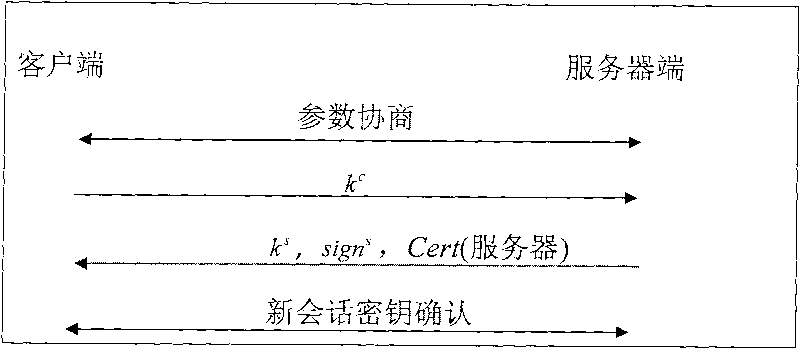
[0018] The method provided by the invention assumes that both the server and the client are equipped with trusted security chips in terms of hardware, and the BIOS of the server and the client supports TPM; and in terms of software, it assumes that the server and the client are installed with a measurement module and a trusted operating system. The measurement module determines the entity to be measured, the measurement time and the method of safely maintaining the measurement result. Its main functions include calculating the measurement value of those measured entities, recording the measurement event to the measurement storage log and recording the measurement value into the TPM specified PCR. The method of recording the measurement value into the PCR is: new PCR value=hash(original PCR value||measurement value). The metric storage log includes at least: the information of the entity being metric, the metric value and the metric time.
[0019] Combine below image 3 A det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com