RFID (radio frequency identification device) authentication method and system based on PUFs (physical unclonable functions)
An authentication method and reader technology, applied in the field of Internet of Things and information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The invention will be described in further detail below in conjunction with the accompanying drawings.
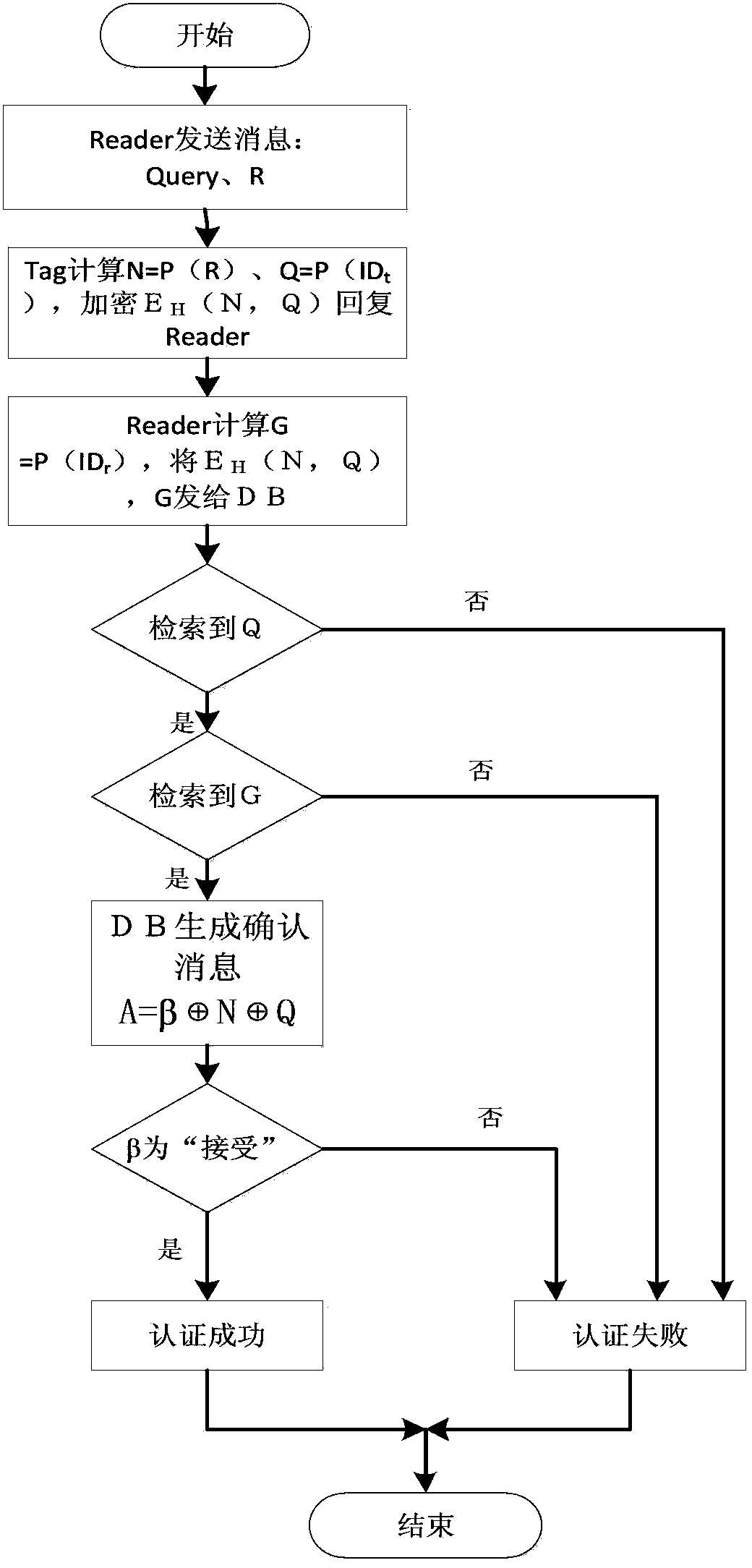
[0031] The authentication method of the present invention mainly has two stages, namely: initialization stage and authentication stage, and its specific implementation mode is:
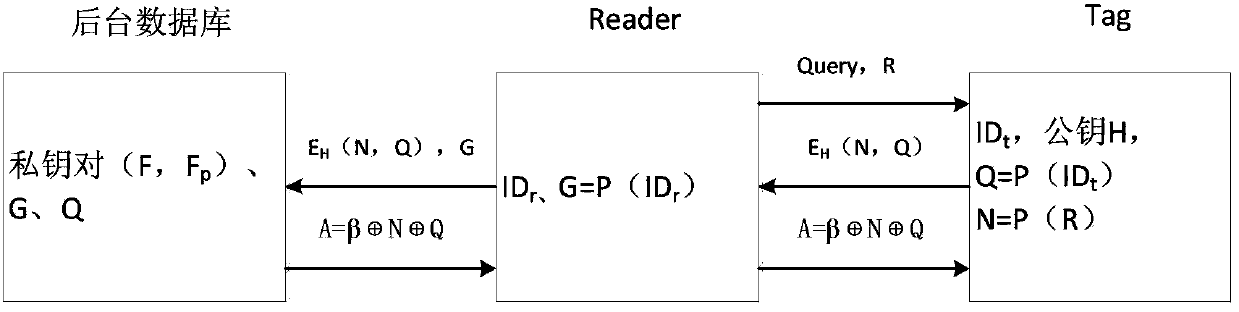
[0032] 1. Initialization stage: background database, reader and all tags are pre-installed with some information in a safe environment.
[0033] (1), the server calculates the public key H and the private key pair (F, F p ), then (ID t , H) as a record stored in the label, where ID t is the ID of the tag, and the reader IDr is stored in the reader.
[0034] (2), built-in PUF module in the reader and tag (expressed by P function), calculate G=P(ID r ), Q=P(ID t ) will G, Q, (F, F p ) into the background database.
[0035] 2. Authentication stage: To realize the authentication process of Reader and Tag, it is divided into the following five steps.
[0036] Step 1: Reader sends a reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com