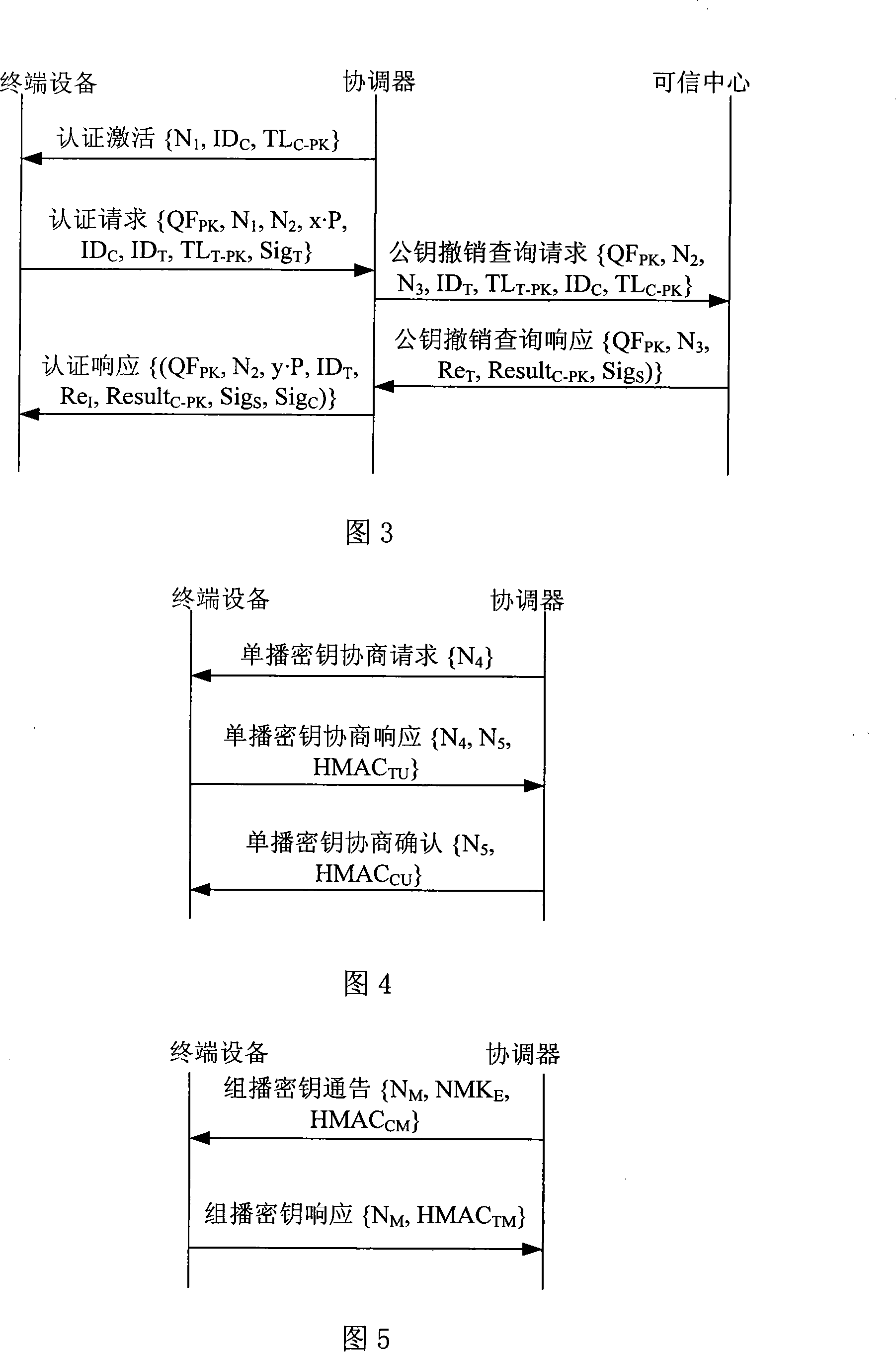
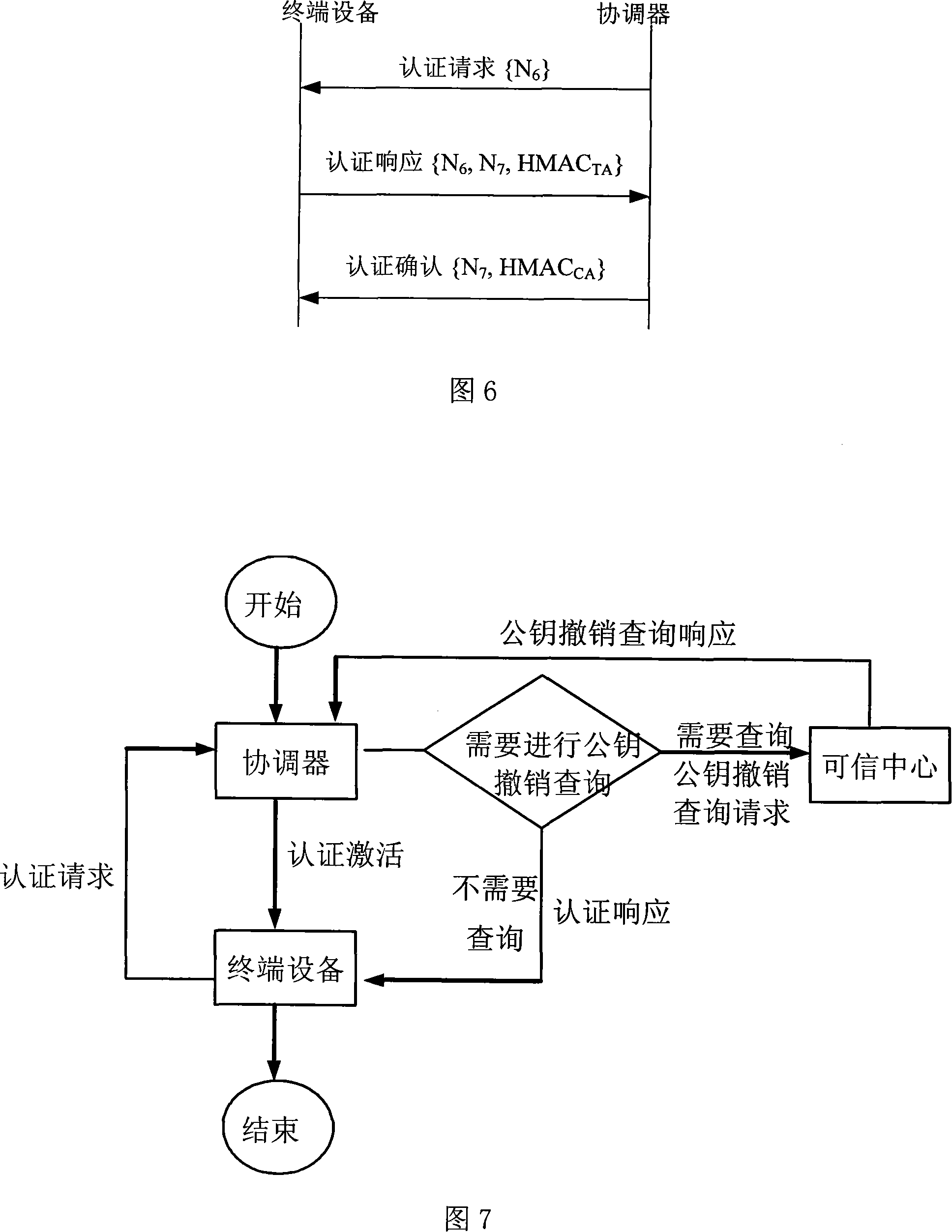
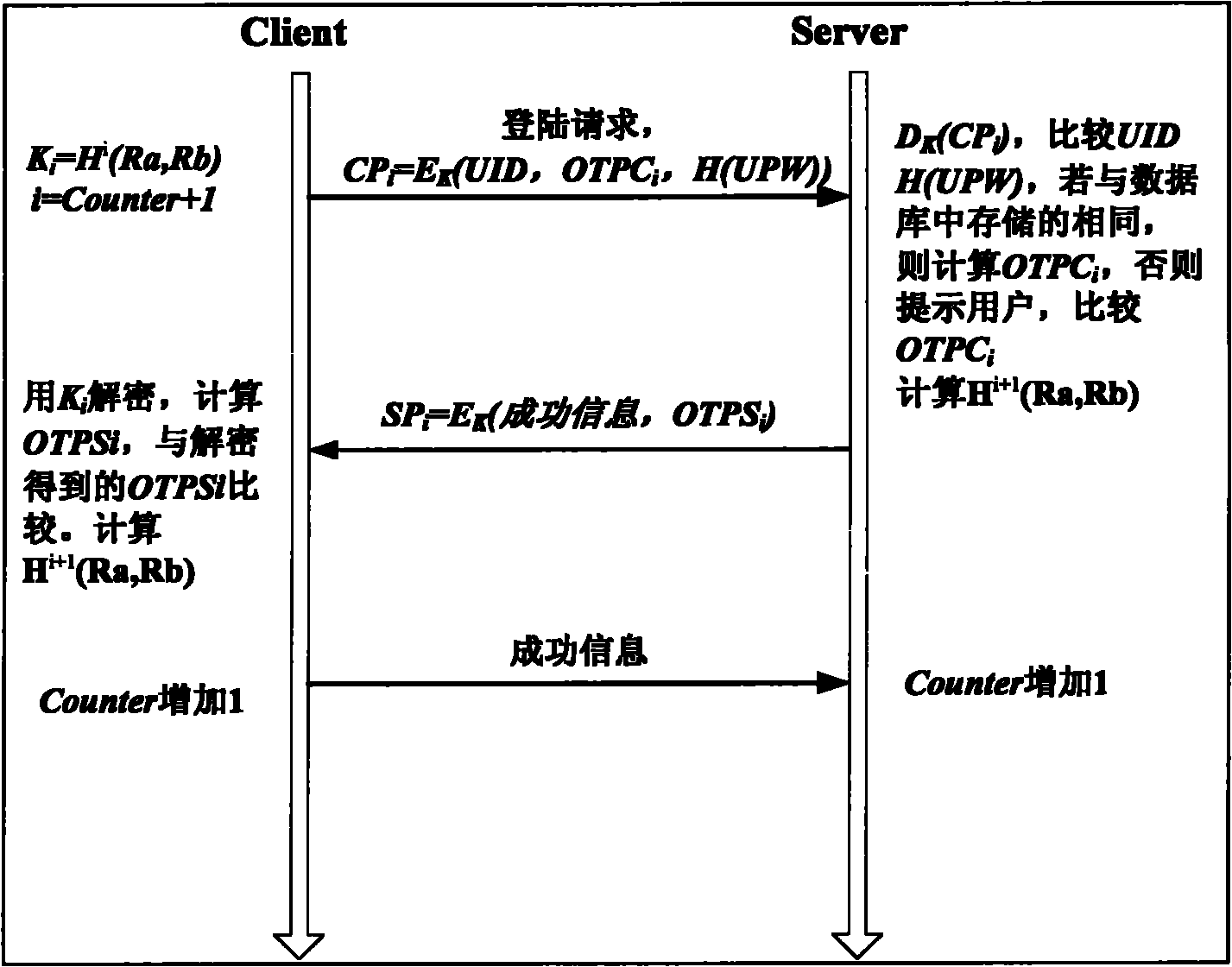
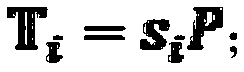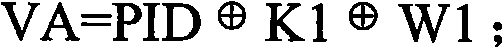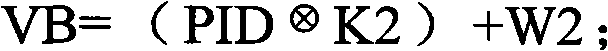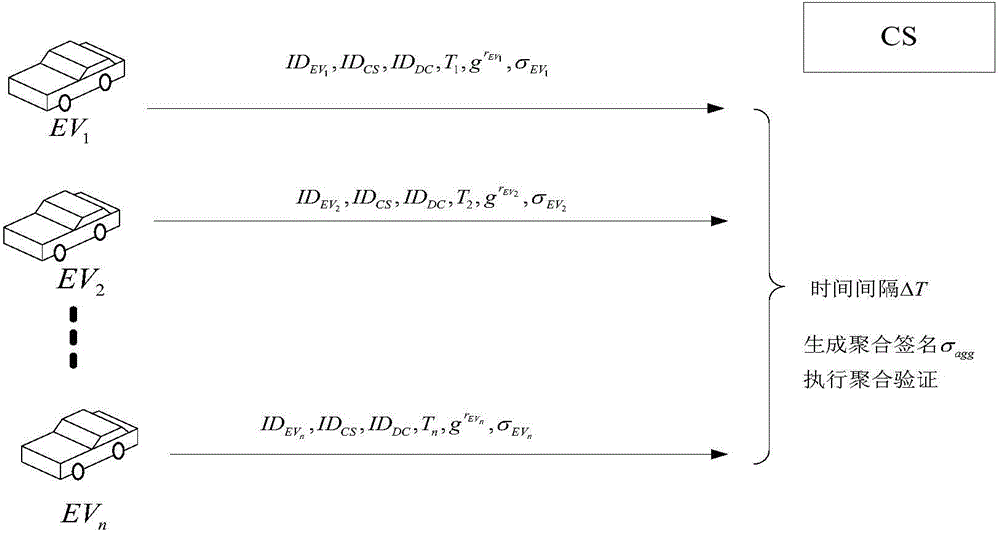Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
193results about How to "Implement two-way authentication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Identity authentication method, apparatus and system
ActiveCN106656481AImplement identity authenticationMaintain securityKey distribution for secure communicationComputer terminalEncryption
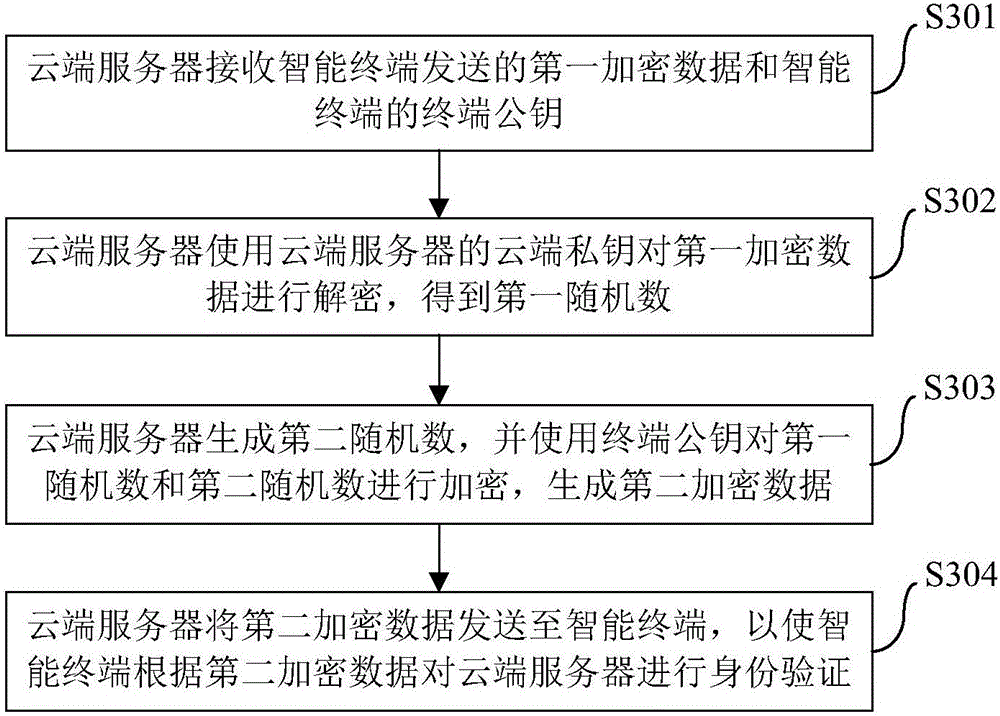
The invention brings forward an identity authentication method, apparatus and system. The identity authentication method comprises the following steps: an intelligent terminal generating a first randomized number and generating a terminal public key and terminal private key which form a pair; the intelligent terminal encrypting the first randomized number by use of a prestored cloud public key so as to obtain first encryption data; the intelligent terminal sending the first encryption data and the terminal public key to a cloud server; the intelligent terminal receiving second encryption data sent by the cloud server and decrypting the second encryption data by use of the terminal private key; and if a decryption result comprises the first randomized number, the intelligent terminal confirming that the cloud server succeeds in identity authentication. The identity authentication method simplifies operation steps, reduces operation resources, at the same time, maintains more secure data channels, promotes development of Internet of things and improves user experience.
Owner:MIDEA SMART TECH CO LTD +1
Identity-based unmanned aerial vehicle key management and networking authentication system and method
ActiveCN109218018AImprovements to computing inequalityImprove reliabilityKey distribution for secure communicationPublic key for secure communicationAuthentication serverAuthentication system
The invention belongs to the technical field of a device for verifying the identity or credentials of a system user, and discloses an identity-based unmanned aerial vehicle key management and networking authentication system and a method thereof. The ground authentication server is responsible for generating and distributing system parameters, identity information and keys required by the unmannedaerial vehicle for key management and network authentication. UAV authentication client is the main body of the system; Through mutual cooperation, the key pairs of UAV for network authentication canbe generated in a distributed manner, and the identity authentication and key agreement between UAV can be realized by using the key pairs. The invention improves the problem of unequal calculation of nodes in the key management of the UAV network existing in the prior art, enhances the reliability of the system, and realizes the key management of the UAV self-organization. The two-way authentication between UAV nodes ensures the credibility and authenticity of both sides of the communication. Using identity public key and bilinear pairing implementation, the computational overhead is less and the implementation efficiency is improved.
Owner:XIDIAN UNIV +1
Method and system for mutual authentication based on hash function
ActiveCN101662366ANo secure link requiredImplement two-way authenticationUser identity/authority verificationCo-operative working arrangementsMutual authenticationElectronic tagging
Owner:CHINA IWNCOMM
Authentication accessing method of wireless multi-hop network
InactiveCN101232378AImprove securityImprove performanceKey distribution for secure communicationPublic key for secure communicationAccess methodBeacon frame
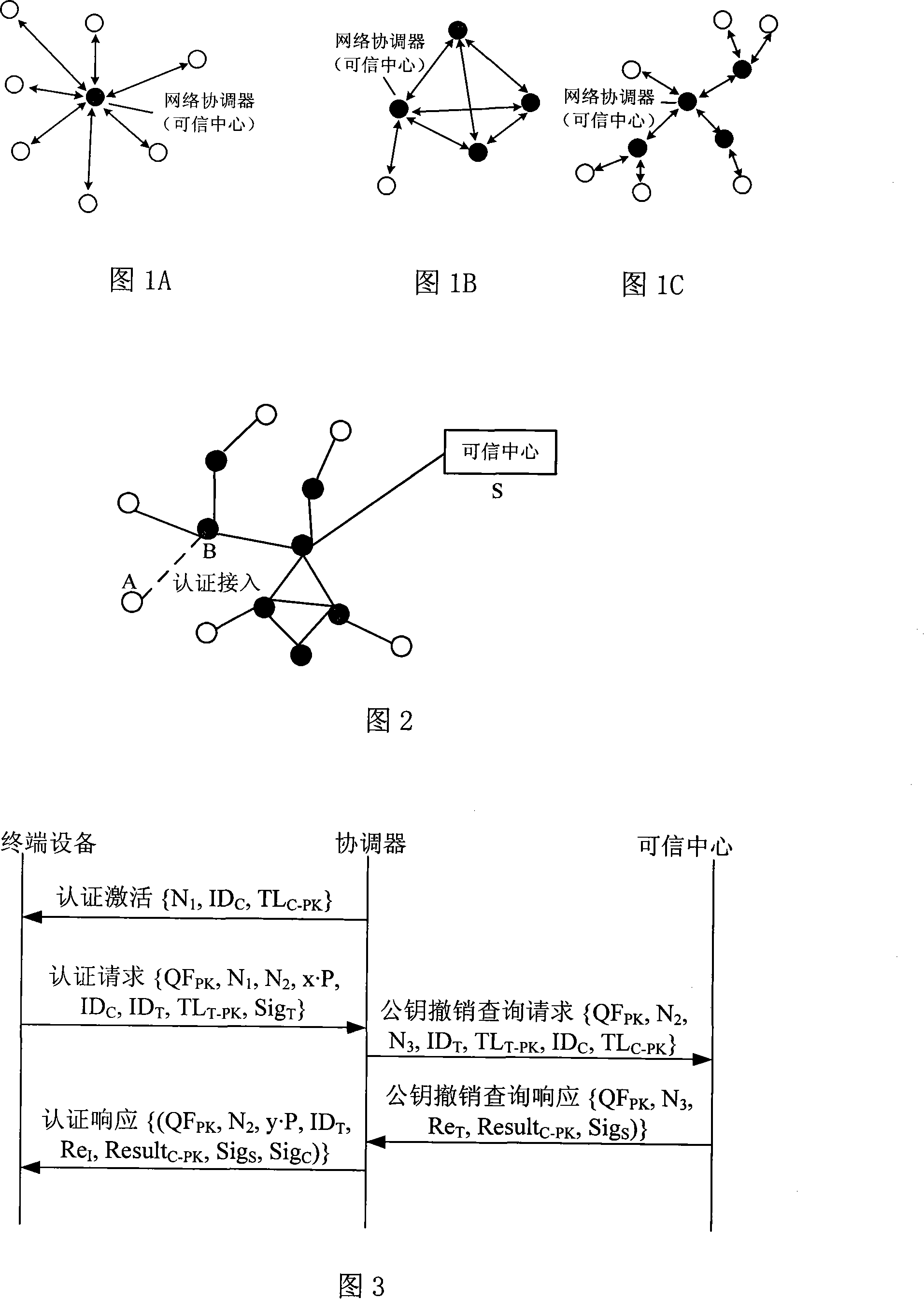
The invention relates to an authentication access method of a wireless multi-hop network. The invention is applicable to the safety application protocol of the WAPI framework method (TePA, the access control method which is based on the triple peer-to-peer identification) during the application on the specific network which includes a wireless LAN, a wireless MAN and a wireless PAN. A terminal equipment and a coordinator have the port control ability, the terminal equipment selects the authentication and key management suit and sends the connection request to command the coordinator after the broadcast beacon frame of the coordinator, the coordinator carries out the authentication together with the terminal equipment according to the selected authentication and key management suit by the terminal equipment, the connection response command is sent to the terminal equipment after the finish of the authentication; the terminal equipment and the coordinator carries out the control to the ports according to the authentication result, so as to realize the authentication access of the wireless multi-hop network. The invention solves the technical problem of the safety hidden trouble of the prior authentication method of the wireless multi-hop network.
Owner:CHINA IWNCOMM
Mobile commerce identity authentication method
InactiveCN101969446AEliminate inconvenienceMeet the inconvenienceUser identity/authority verificationInternet Authentication ServiceThird party
The invention provides a mobile commerce identity authentication method. In the method, key negotiation is realized by the most efficient elliptic curve-based public key cryptosystem in public key cryptosystems. An elliptic curve algorithm has the characteristics of low calculated amount and high safety, so the elliptic curve algorithm is used for generating a public key and a private key, and a public key cryptosystem without a third-party is realized and applied to the two-way authentication service of a client and a server.
Owner:BEIJING JIAOTONG UNIV
Single-point login method under point-to-point model
ActiveCN101286843AReduce the burden onImprove operational efficiencyPublic key for secure communicationUser identity/authority verificationService modeSecure channel
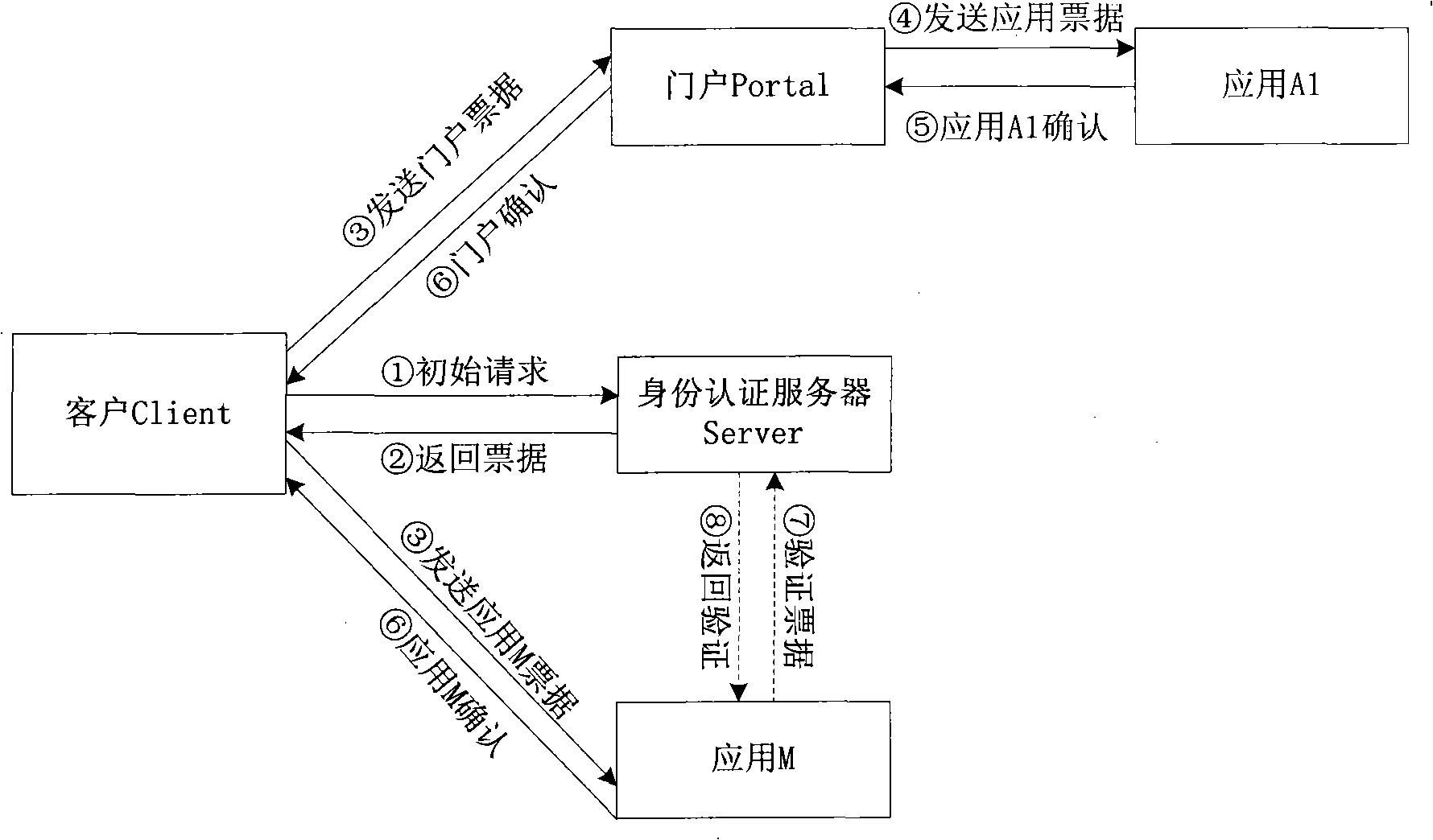
The invention relates to a single sign-on method in a point to point mode. Being different from the existing single sign-on method based on a customer server mode, the method manages the single sign-on life cycle of a customer by using valid period of certificate of the customer, and the customer can sign on for a plurality of times with single certification. The method completes the cross-certification of an application system and an identity certification server; the shared encryption key of communication parties is initialized, and a safe channel between the customer and the application system is established. Through the the identity certification server and the cross-certification of the application system, any application system can independently carry out identity certification, thus weakening the status of a central identity certification server, avoiding the defect of single-point failure in traditional customer / service mode and being characterized by low cost for system operation, high efficiency and good safety performance.
Owner:江西省电力信息通讯有限公司
Wireless multi-hop network authentication access method based on ID
InactiveCN101222772AImprove securityImprove performanceUser identity/authority verificationNetwork topologiesCommunications securityAccess method
The invention provides an access authentication method in ID based wireless multi-hop network, which is applicable to the security application protocol when WAPI frame method (TePA, an access control method based on triplet peer authentication) is applied on specific network including wireless local area network, wireless metropolitan area network and wireless personal area networks. The methods comprises the following steps that: a non-controlled port and a controlled port are defined; a coordinator transmits a beacon frame; a terminal equipment sends a command for connection request; the coordination conducts authentication with the terminal equipment; after the authentication is successful, the coordinator opens the controlled port and sends a connection response command; the terminal equipments receive the connection response commands and opens the controlled ports so as to get access to the network. The method of the invention solves the technical problem that the prior wireless multi-hop network has safety hidden danger in access authentication method and ensures the communication security between the terminal equipment and the coordinator.
Owner:CHINA IWNCOMM
Certificate-free remote anonymous authentication method based on third party in cloud application
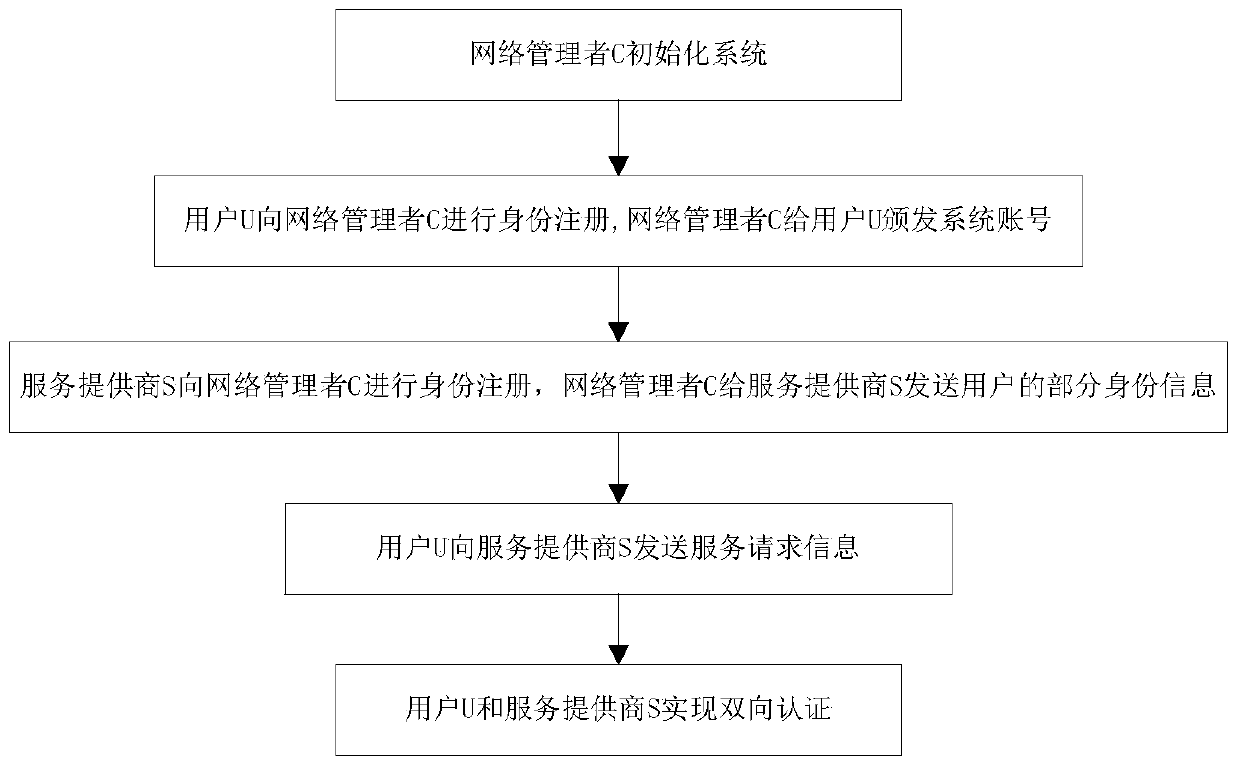
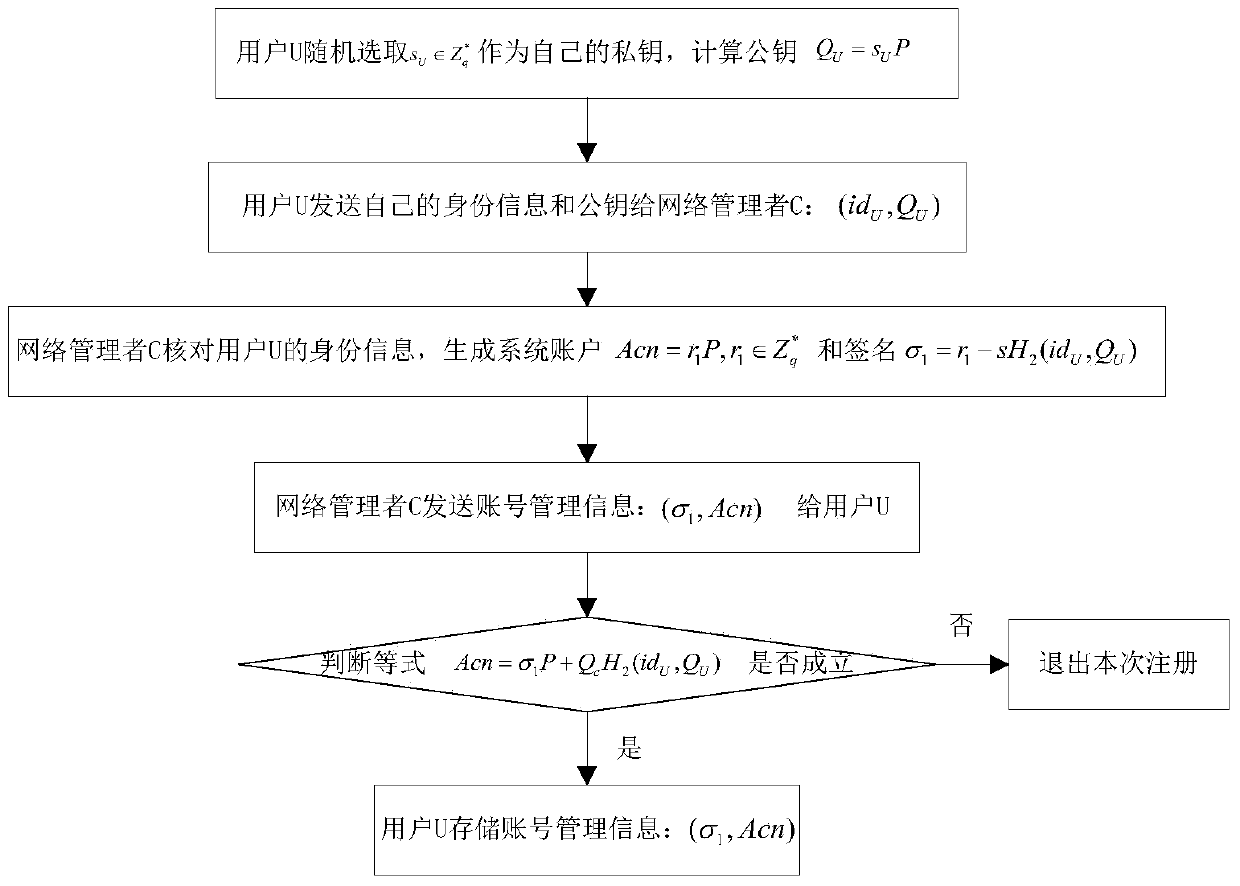
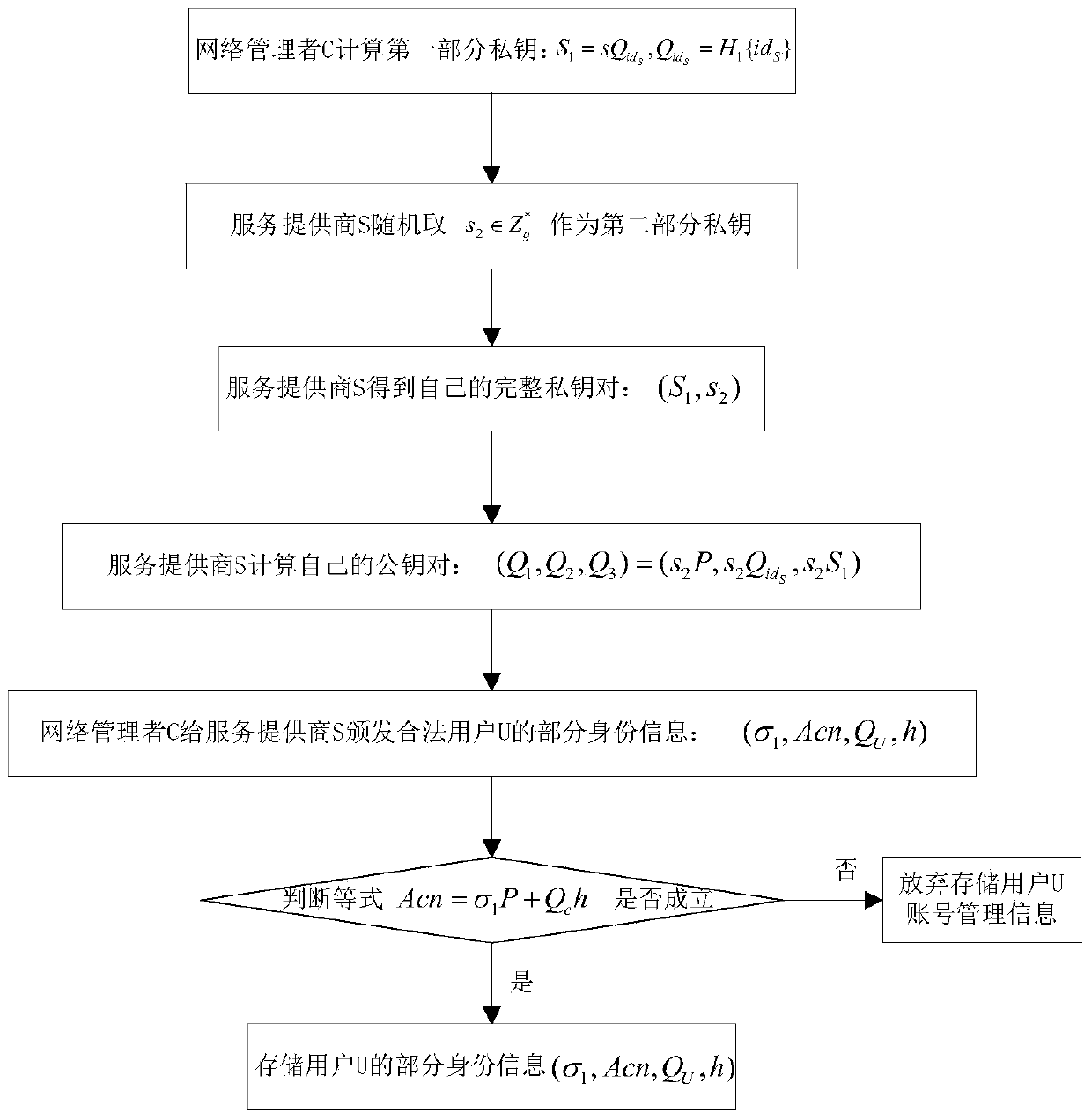
ActiveCN104052608AAchieve anonymityImprove securityUser identity/authority verificationData switching networksNetwork managementService provider
The invention discloses a certificate-free remote anonymous authentication method based on a third party in a cloud application, and the method mainly solves the problem that remote bidirectional authentication in the prior art is poor in safety. The method is achieved through the steps that (1) a network manager M initializes a system; (2) the network manager M conducts identity register on a user U, and issues a system account to the user U; (3) the network manager conducts identity register on a service provider S, and sends part of the identity information of the legitimate user U to the service provider S; (4) the user U sends a service request to the service provider S in an anonymous mode through the system account; (5) the service provider S and the user U conduct bidirectional authentication. According to the method, the requirement for a certificate is omitted, the defects of secret key trusteeship are omitted as well, safety in anonymous bidirectional authentication is improved, and the method can be used for identity authentication when a remote user in a wireless body area network conducts service request.
Owner:XIAN XIDIAN BLOCKCHAIN TECH CO LTD
Network camera identity authentication method based on TPCM
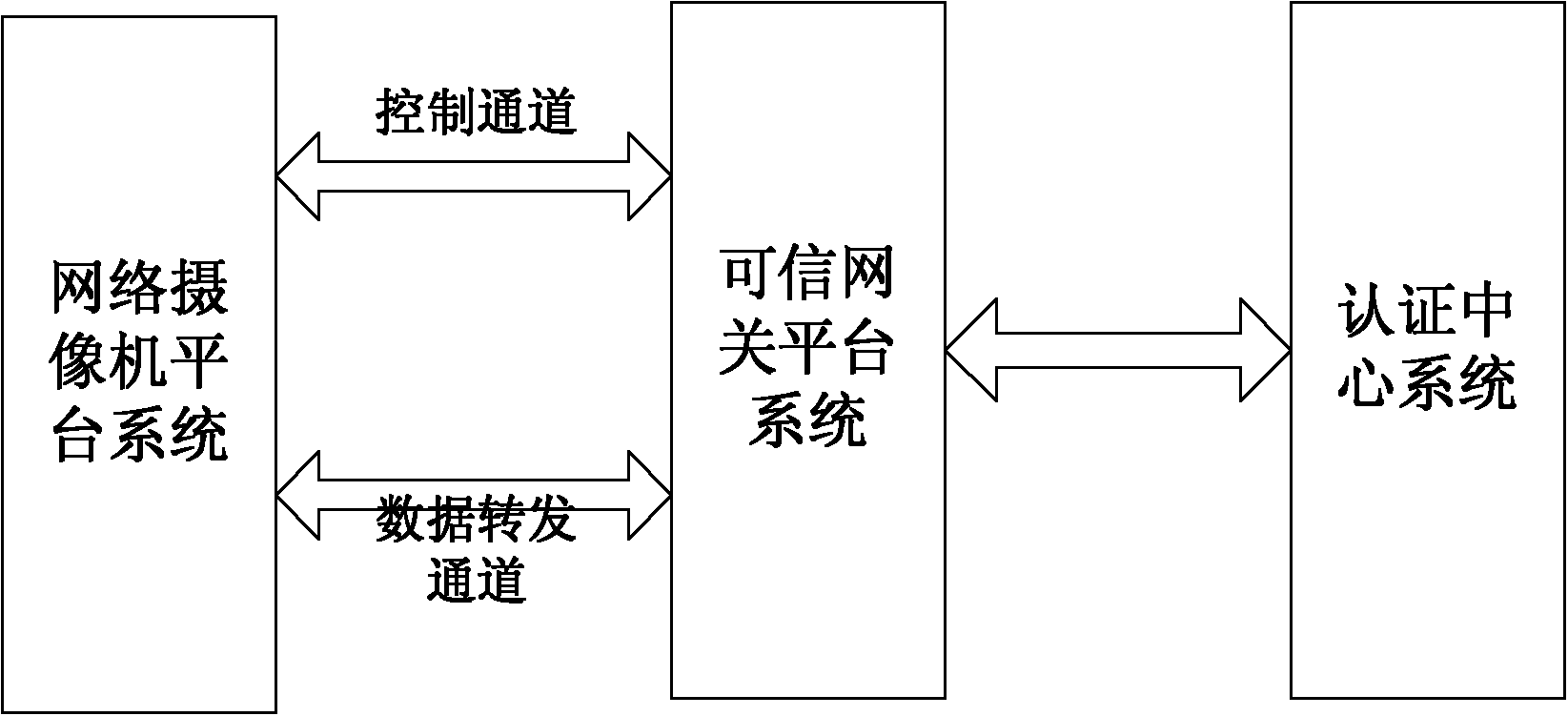
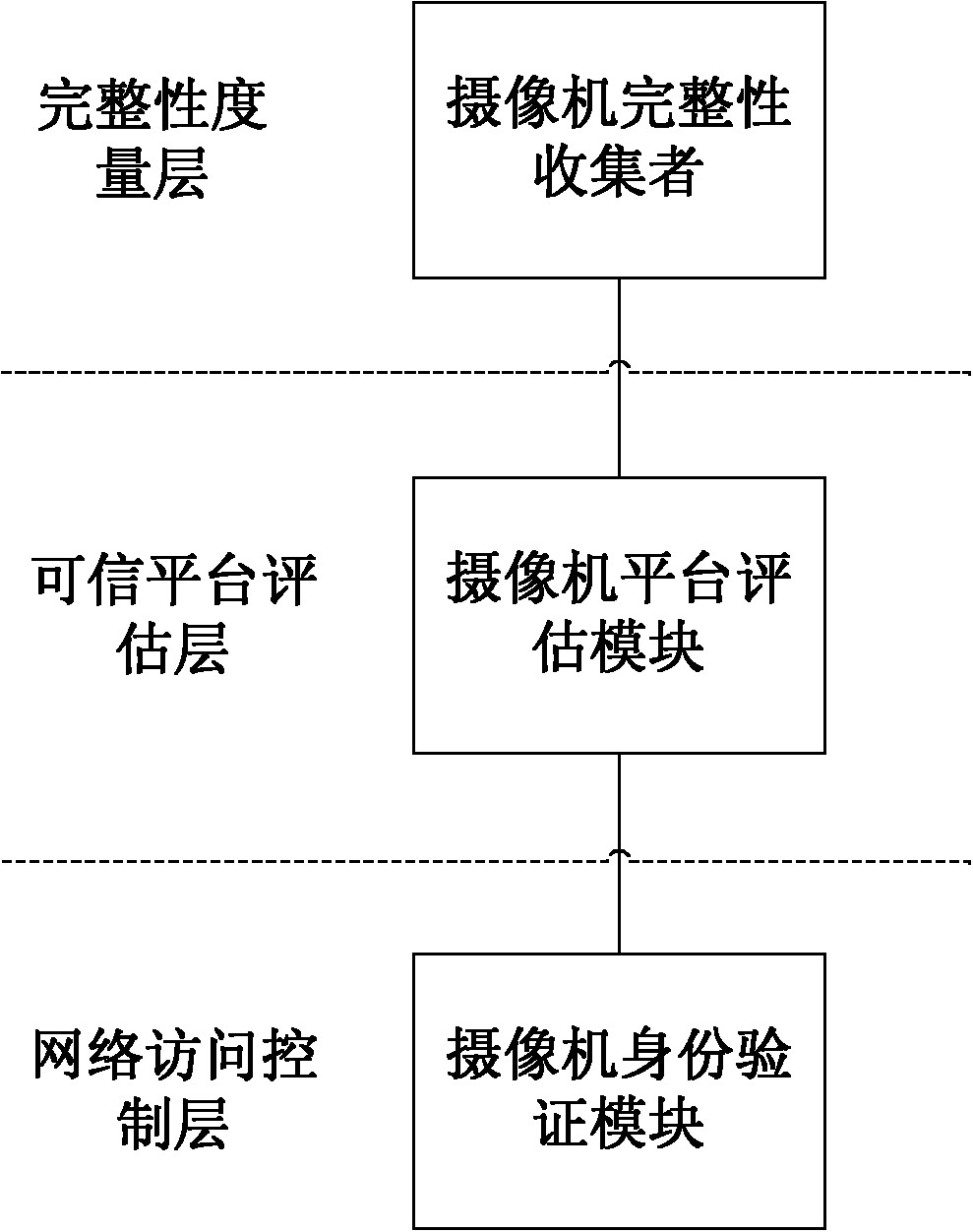
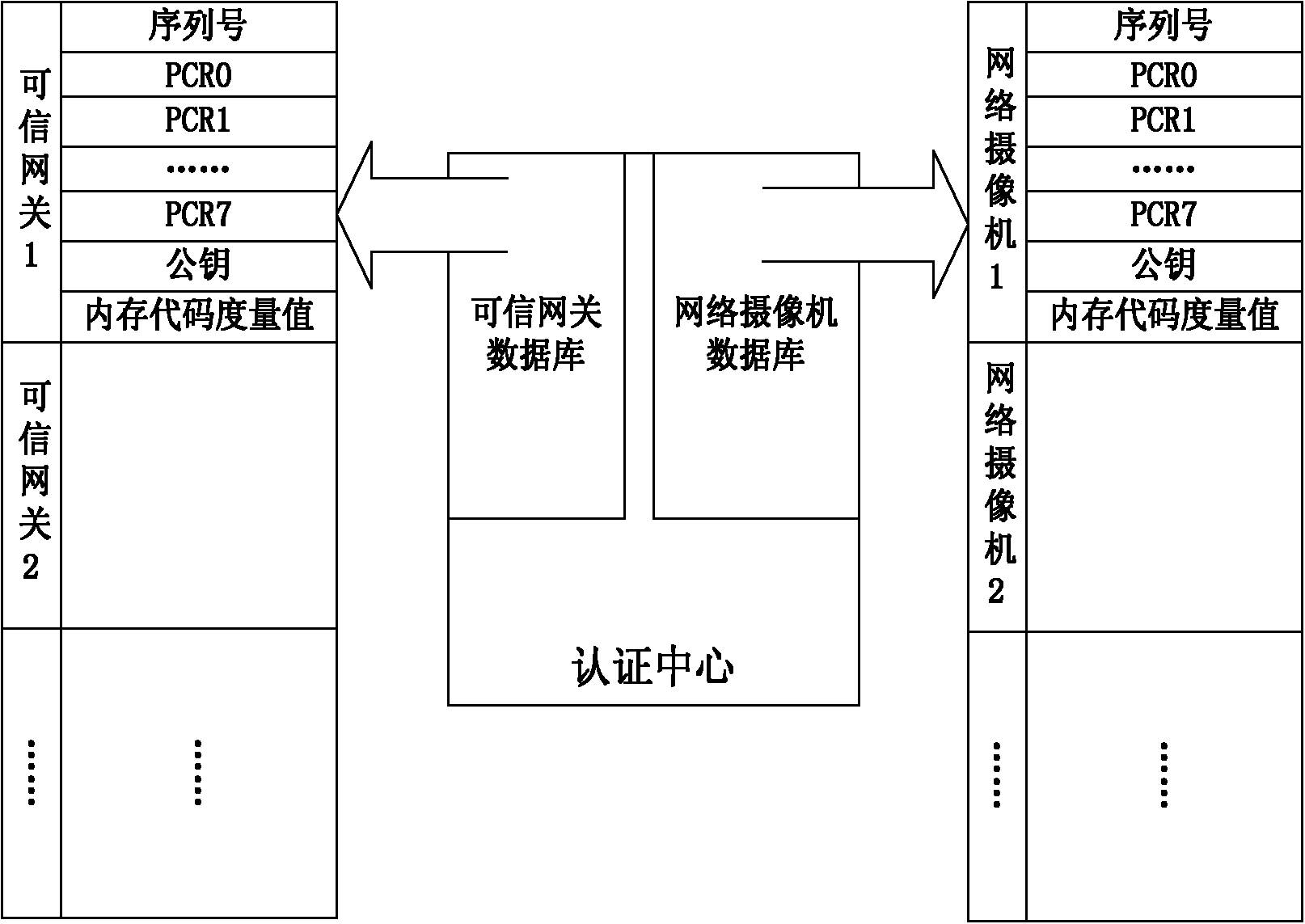
ActiveCN103888257AImplement identity authenticationReduced authenticationUser identity/authority verificationClosed circuit television systemsProcessor registerMemory code
The invention provides a network camera identity authentication method based on a TPCM. The method is characterized in that a network camera and a reliable gateway adopt a self-signing mode to generate a digital certificate which comprises a value of a platform configuration register and a measurement result of a memory code segment in operation. An authentication center verifies validity of the digital certificate and confirms identity of the verified party. Advantages are that a measurement value in the starting process of equipment is stored in the platform configuration register so that hardware of the network camera and the reliable gateway is ensured to be unchanged. Reliability of equipment identity is ensured from the aspect of software via measurement of the memory code segment. Besides, a signature secret key is generated by a TPCM chip and bound with the hardware platform state of the equipment so that the digital certificate is difficult to forge.
Owner:BEIJING UNIV OF TECH
RFID (radio frequency identification device) authentication method and system based on PUFs (physical unclonable functions)
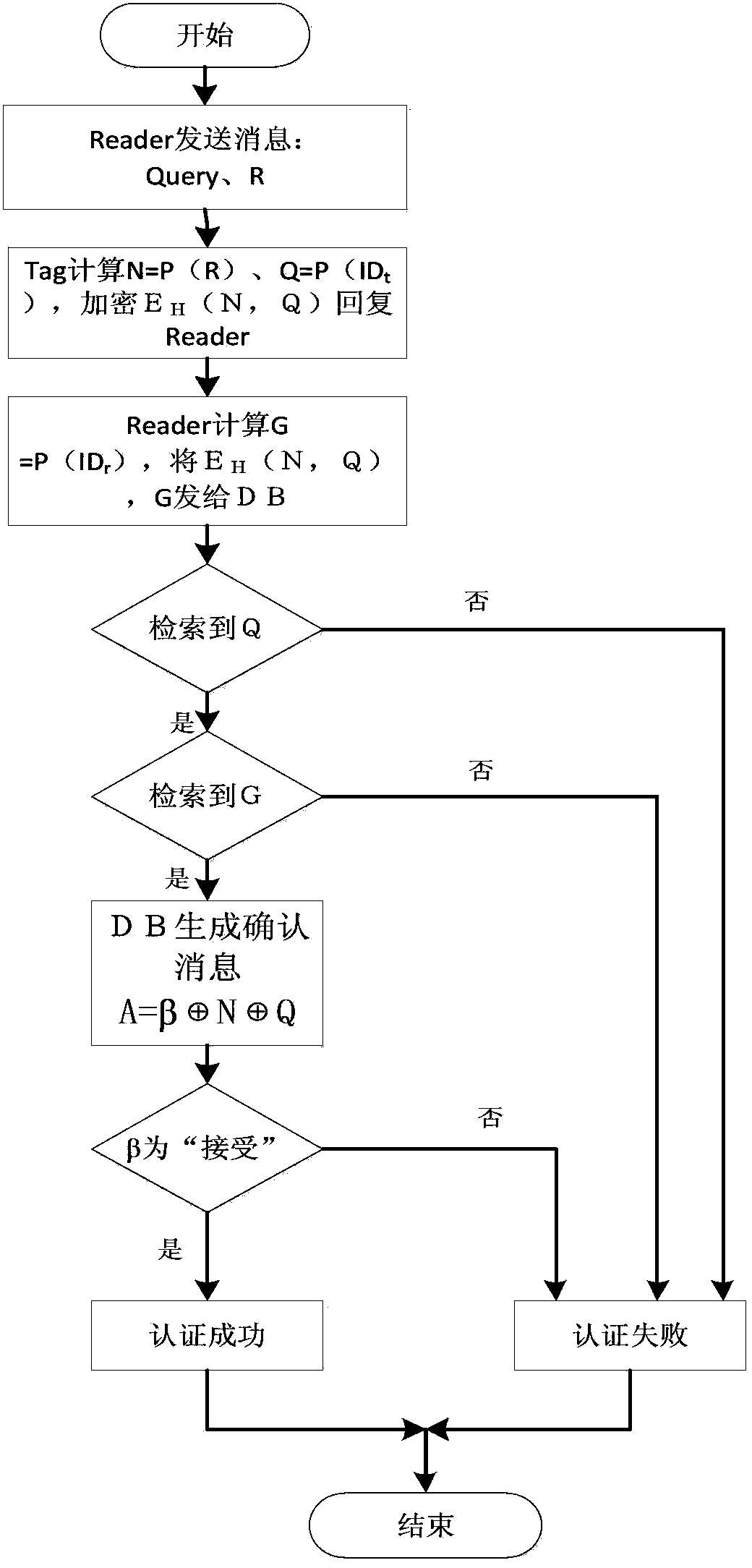
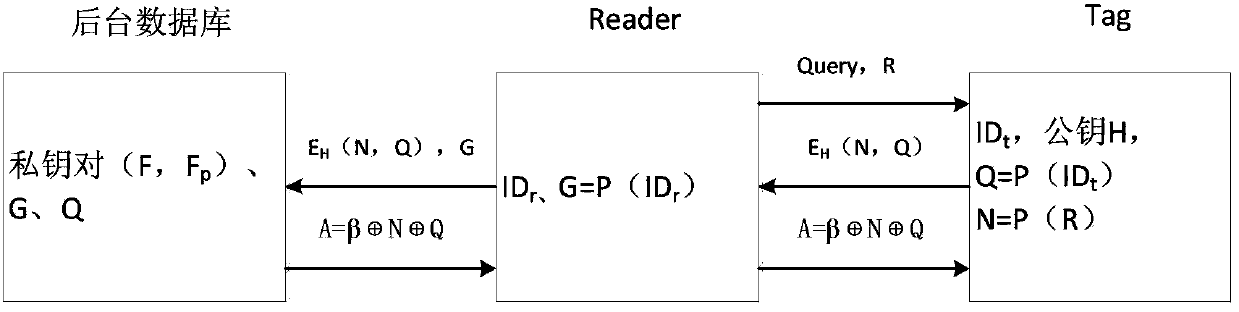
ActiveCN103391199ADefense against replay attacksResist impersonation attacksUser identity/authority verificationCo-operative working arrangementsRfid authenticationResource consumption
The invention discloses an RFID authentication method and system based on PUFs. The system comprises a backend database, a reader and a tag, wherein communication between the backend database and the reader can be realized by using a conventional network security technology, so that the communication between the backend database and the reader is safe; however, the communication between the reader and the tag is not realized through the conventional network security technology, so that the communication is not safe. The RFID authentication method has the advantages of high safety and authentication efficiency, little in resource consumption and the like, can resist typical attack techniques such as replay attacks, counterfeit attacks, track attacks, physical attacks and the like, has forward safety and backward safety, and realizes bidirectional authentication between the reader and the tag. A public key encryption method is used, so that the RFID authentication method has higher safety.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and equipment for performing safety communication between T_Box equipment and ECU equipment in internet of vehicles system
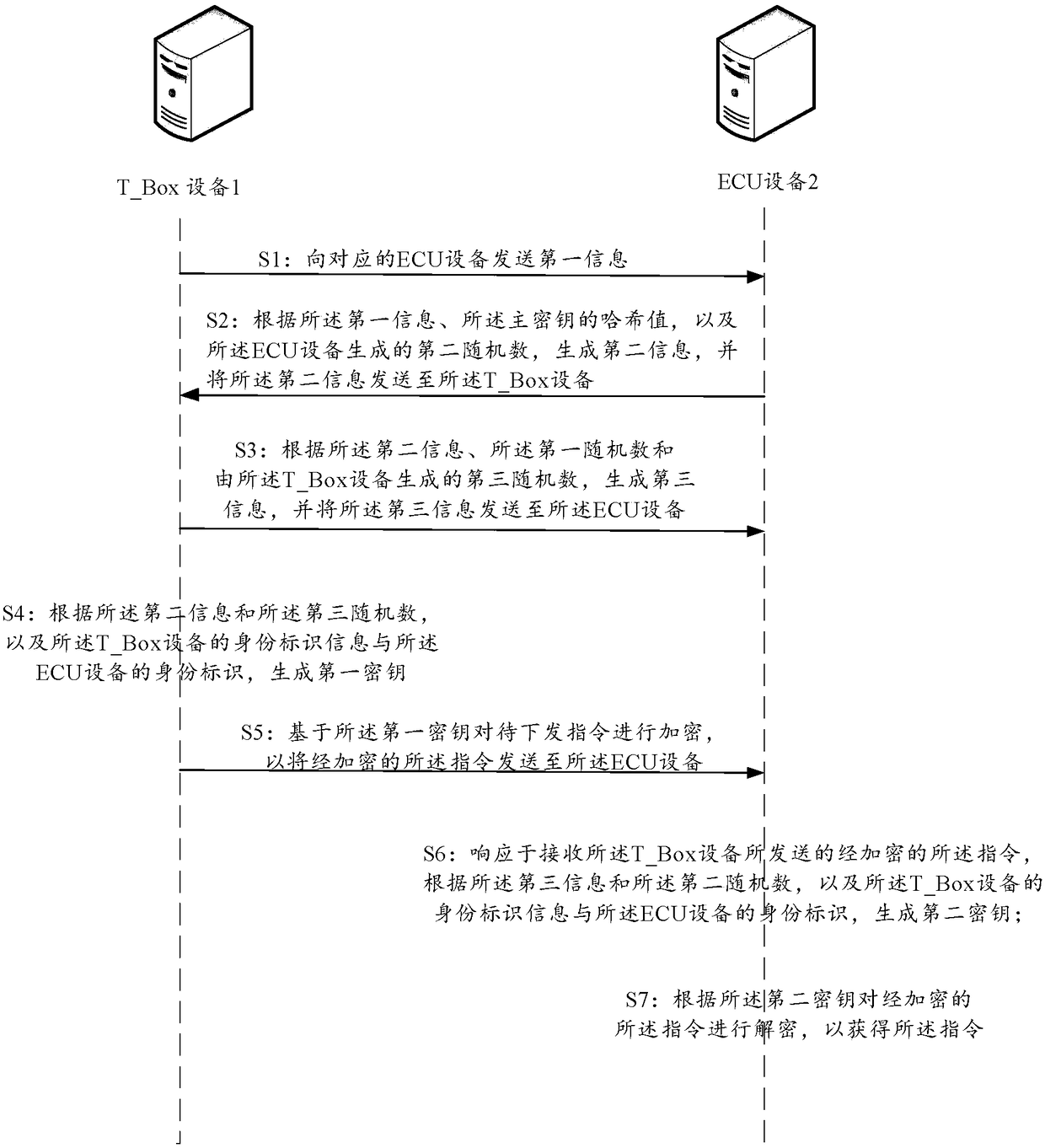
ActiveCN108347331AImplement two-way authenticationReduce illegal dataKey distribution for secure communicationDigital data protectionThe InternetEngineering
The invention aims at providing a method and equipment for performing safety communication between T_Box equipment and ECU equipment in an internet of vehicles system. The method specifically comprises the following steps: the T_Box equipment send first information to the corresponding ECU equipment; the ECU equipment generates second information according to the first information, a hash value ofthe main key and the second random number generated by the ECU equipment; the T_Box equipment generates third information according to the second information, the first random number and the third random number; the T-Box equipment generates the first key according to the second information and the third random number, and identity identifier information of the T_Box equipment and an identity identifier of the ECU equipment; the T_Box equipment encrypts a to-be-issued instruction based on the first key; the ECU equipment generates a second key according to the third information, the second random number, the identity identifier information of the T_Box equipment and the identity identifier of the ECU equipment; and the ECU equipment decrypts the encrypted instruction according to the second key so as to acquire the instruction. Compared with the prior art, the safety communication between the T_Box equipment and the ECU equipment is realized.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Method, device and system of verification of safety association between terminal equipment and user card
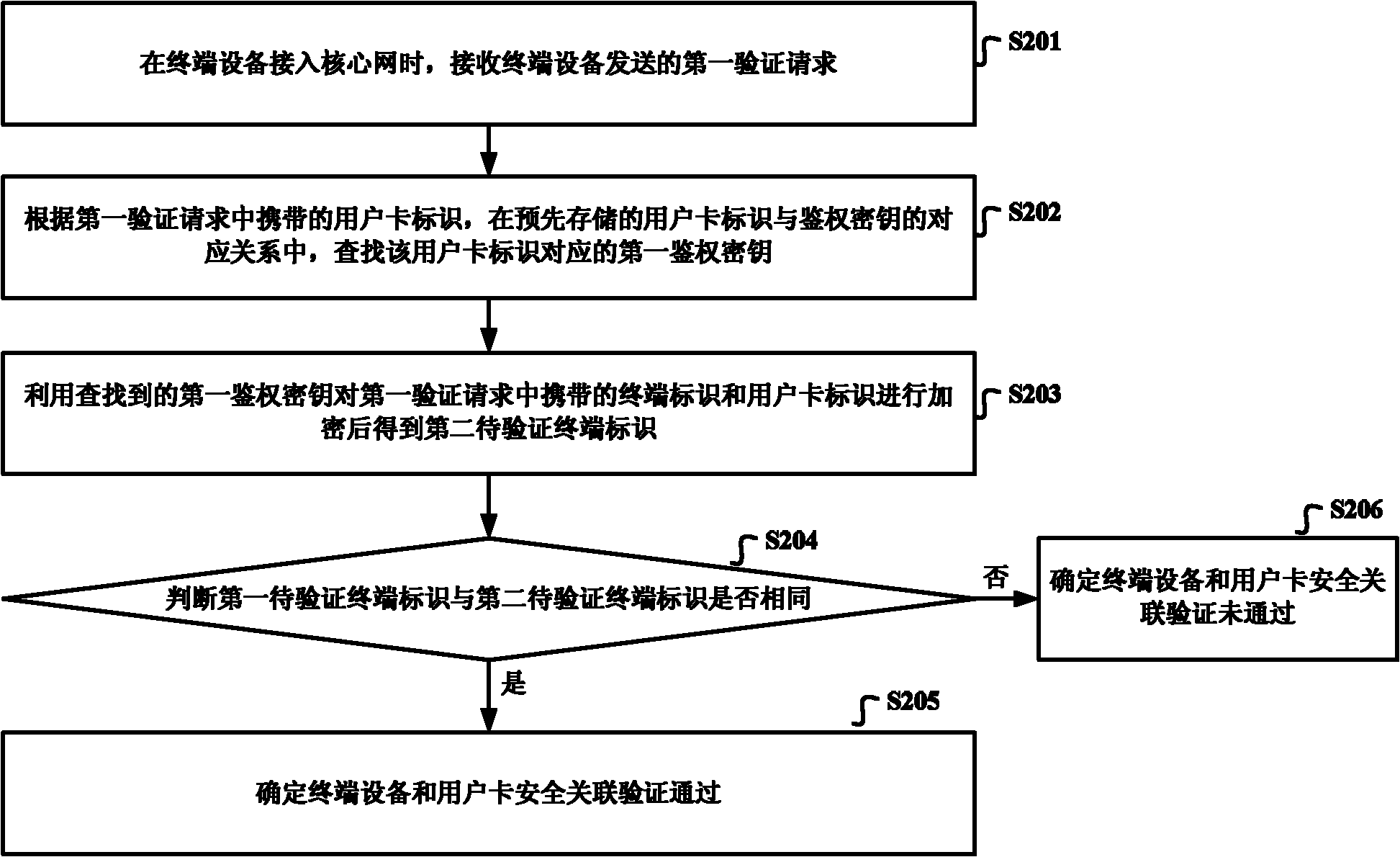
ActiveCN103108327AImplement two-way authenticationNo need for extensionsSecurity arrangementTerminal equipmentComputer terminal
The invention discloses a method, a device and a system of verification of safety association between terminal equipment and a user card. The method, the device and the system of the verification of the safety association between the terminal equipment and the user card are used for achieving two-way safety verification between the user card and the terminal equipment under the premise that functions of the user card are not expanded, wherein the method of the verification of the safety association between the terminal equipment and the user card comprises receiving a first verification request sent by the terminal equipment when the terminal equipment accesses a core network; searching for a first authentication key which corresponds to a user card identification in a corresponding relationship which is pre-stored between the user card identification and the first authentication key according to the user card identification carried by the verification request; carrying out encryption on a terminal identification and the user card identification carried in the verification request by using the first authentication key which is found, and obtaining a second to-be-verified terminal identification; confirming that the safety association verification between the terminal equipment and the user card passes when a first to-be-verified terminal identification and the second to-be-verified terminal identification are the same; and confirming that the safety association verification between the terminal equipment and the user card does not pass when the first to-be-verified terminal identification and the second to-be-verified terminal identification are not the same.
Owner:CHINA MOBILE COMM GRP CO LTD
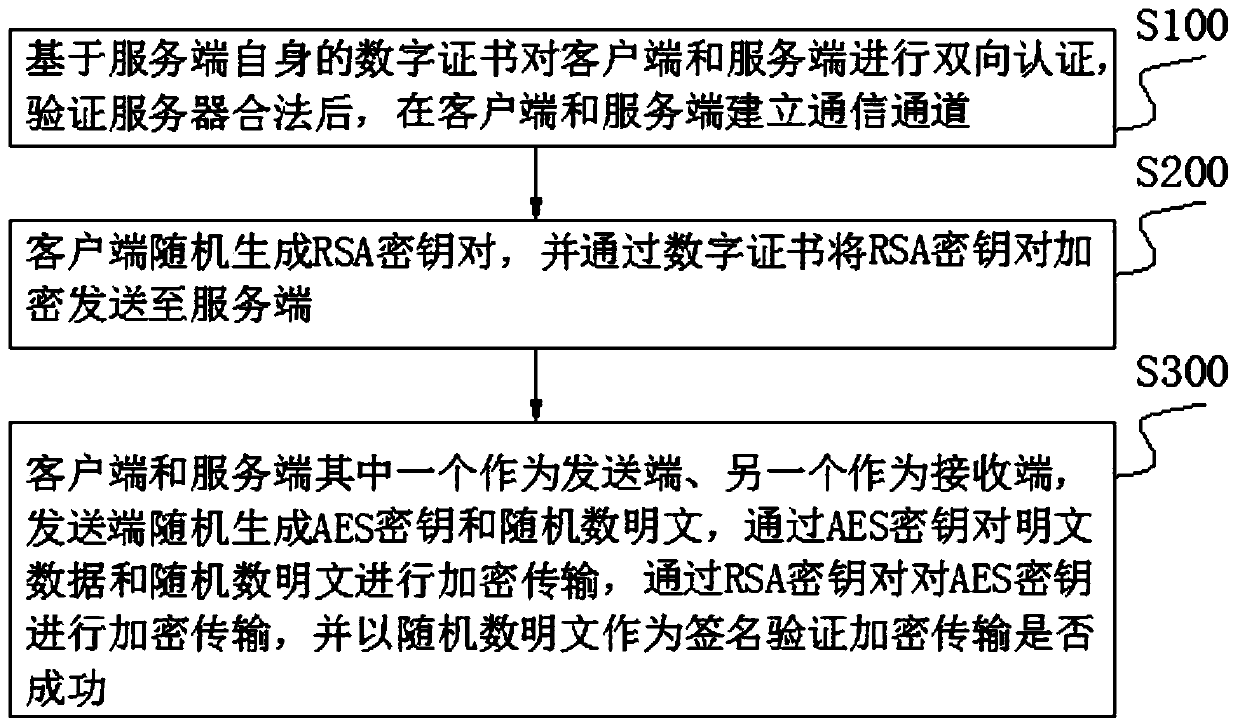
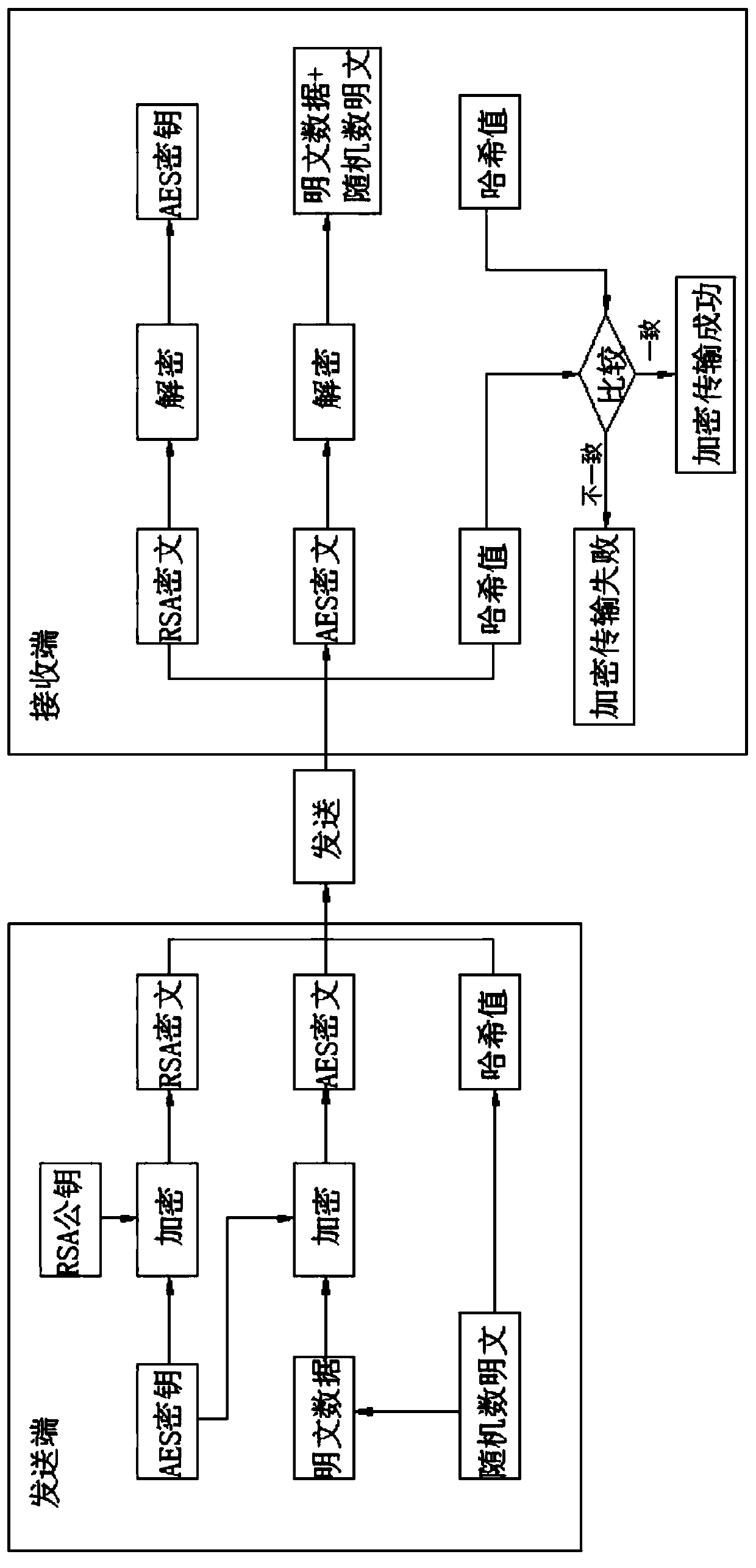
Data transmission method and system based on hybrid encryption algorithm
InactiveCN110535868AImplement two-way authenticationAvoid casual accessEncryption apparatus with shift registers/memoriesUser identity/authority verificationData transmissionPlaintext
The invention discloses a data transmission method and system based on a hybrid encryption algorithm, belongs to the field of encryption transmission, and aims to solve the technical problem of how torealize data transmission with high encryption speed and low encryption key management difficulty. The method comprises the following steps that bidirectional authentication is performed on a clientand a server based on a digital certificate of the server, and a communication channel between the client and the server is established after verifying that the server is legal; the client randomly generates an RSA key pair, and encrypts and sends the RSA key pair to the server through the digital certificate; one of the client and the server is used as a sending end, and the other one is used asa receiving end; the sending end randomly generates an AES secret key and a random number plaintext, carries out encryption transmission on plaintext data and the random number plaintext through the AES secret key, carries out encryption transmission on the AES secret key through an RSA secret key, and uses the random number plaintext as a signature to verify whether encryption transmission is successful or not. The system executes the data transmission method.
Owner:SHANDONG INSPUR COMML SYST CO LTD
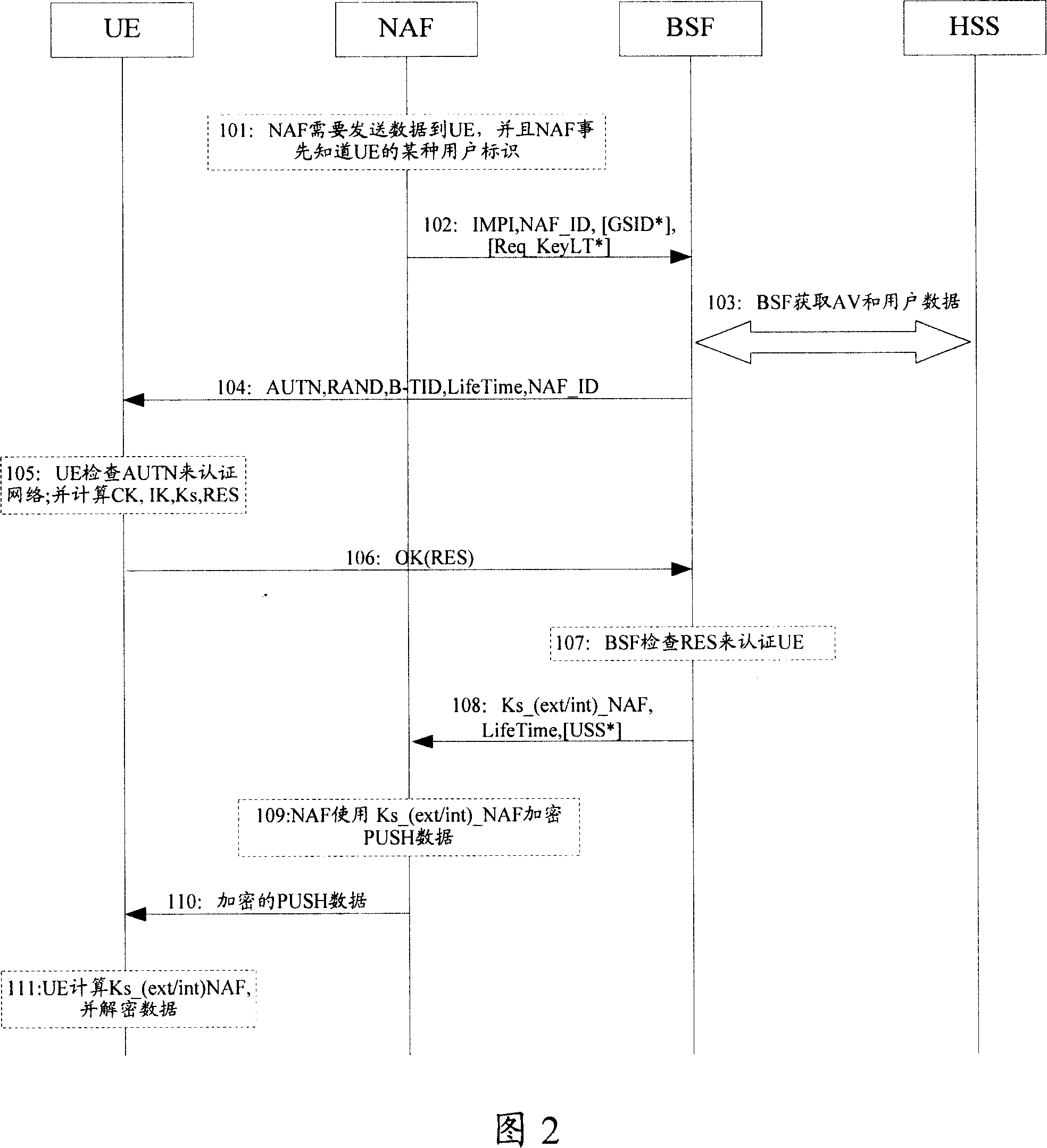
Universal guiding structure pushing method
InactiveCN101141792AAvoid demandMeet needsUser identity/authority verificationRadio/inductive link selection arrangementsComputer hardwareBusiness process
The invention discloses a GBA PUSH method. The method comprises: A. the NAF initiates the authentication request message to the BSF; B. the BSF transmits the PUSH information message used to establish the guiding communication process between the BSF and the UE, and transmits the authentication response message containing the derived cipher code and the derived cipher code validity term to the NAF; C. the NAF encode the PUSH data through the derived cipher code, and transmits to the UE through the PUSH service message; D. the UE decode the PUSH data received from NAF through the derived cipher code. The invention can solve the GBA PUSH service request initiated by the NAF to the UE, and can satisfy the demand of the OMA. In addition, the invention the GBA parameter which is generated during the GBA PUSH process is not limited in the process of the service which is actively initiated by the NAF at the network side, and the UE can also use the GBA parameter to protect the service request initiated actively by the UE.
Owner:HUAWEI TECH CO LTD
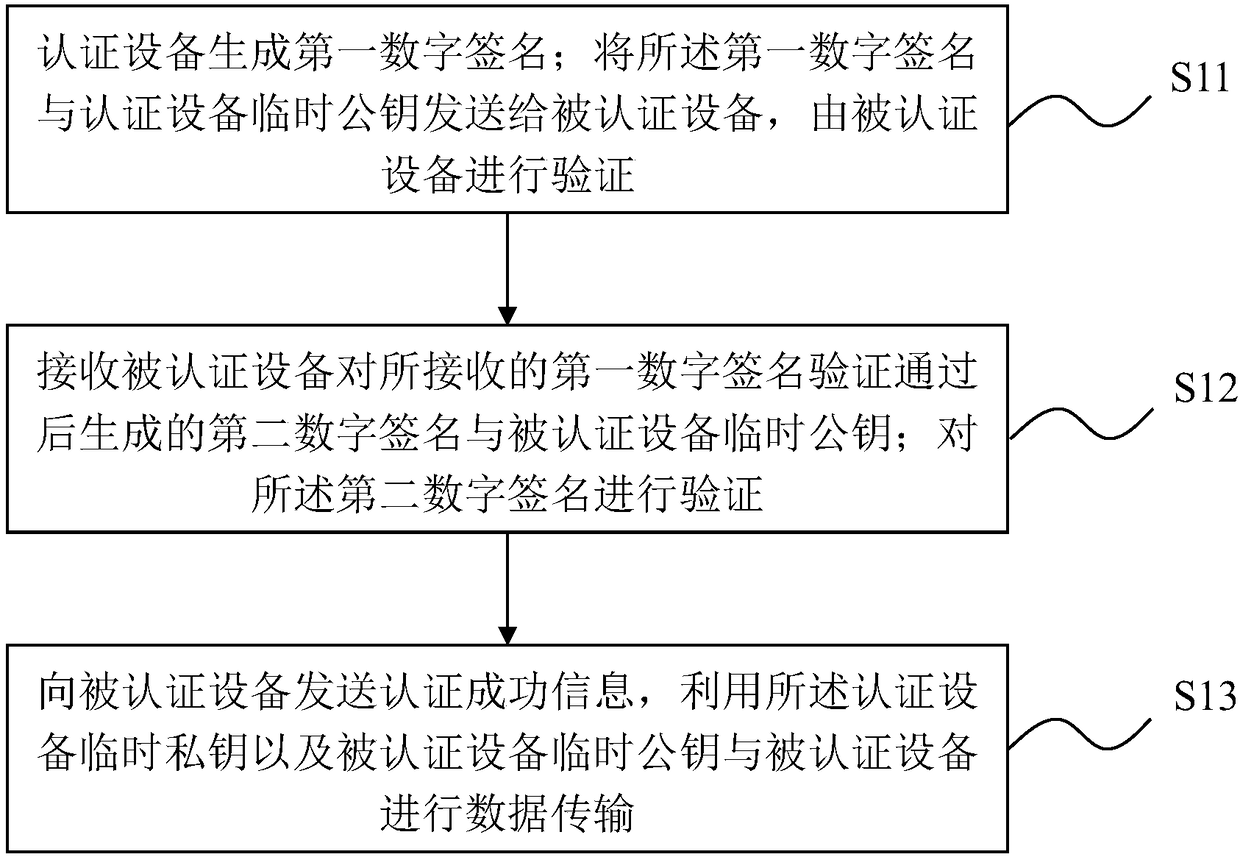
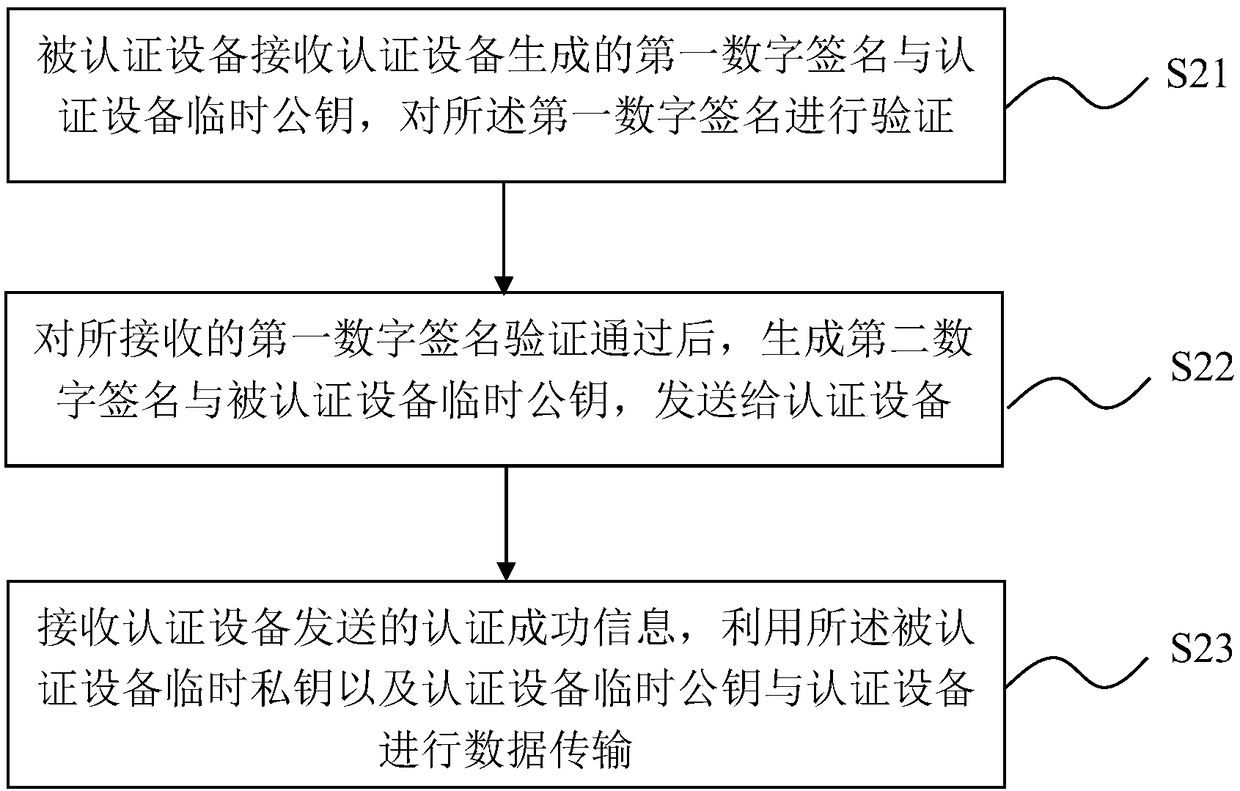
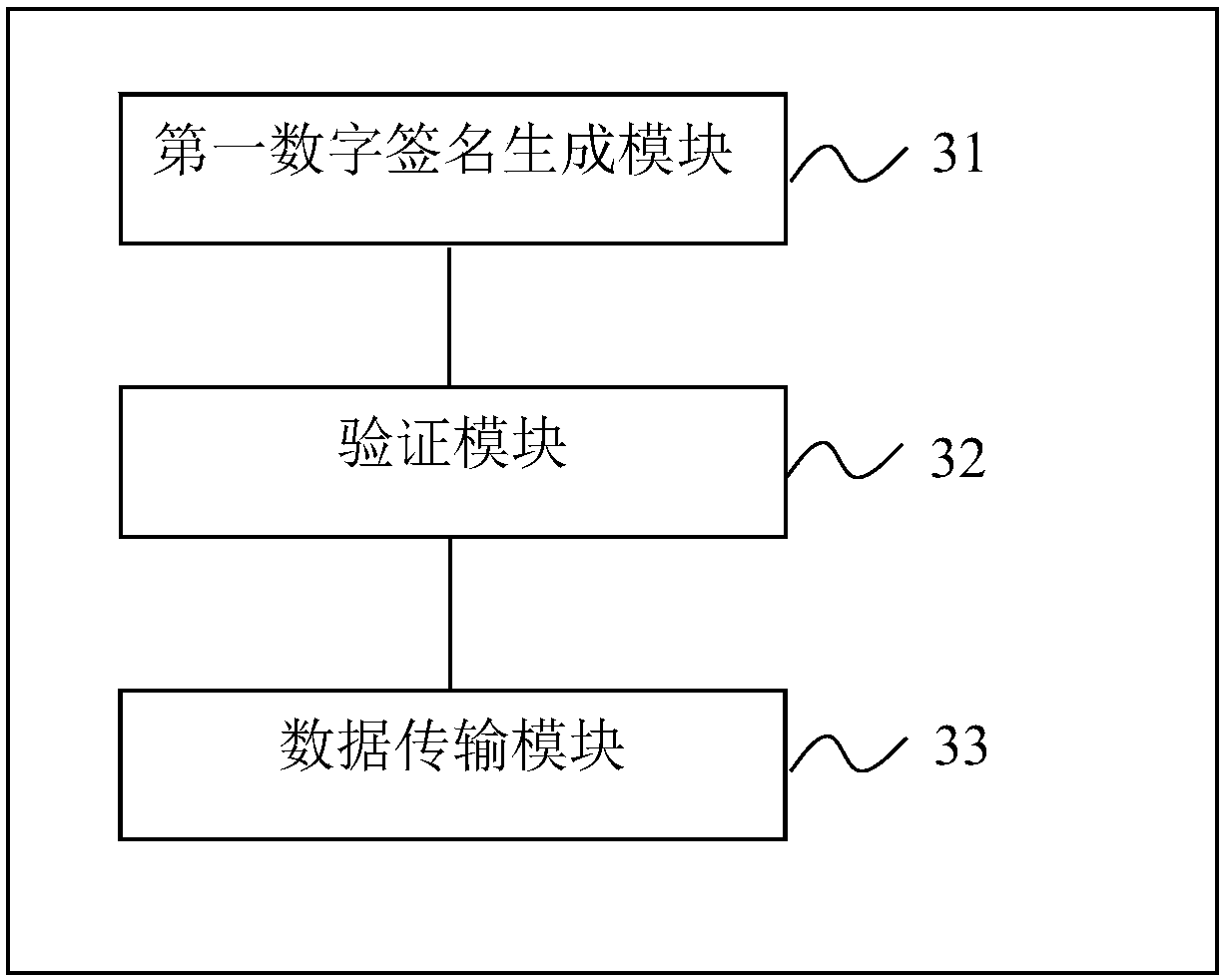
Two-way authentication method and system
ActiveCN108366069AImplement two-way authenticationImprove securityKey distribution for secure communicationUser identity/authority verificationDigital signatureData transmission
The invention relates to a two-way authentication method and system. The method comprises the following steps: forming, by an authentication device, a first digital signature of the key attribute information of an authenticated device; transmitting the first digital signature and a temporary public key of the authentication device to the authenticated device to be verified by the authenticated device; after the authenticated device verifies the received first digital signature, sending, by authenticated device, a second digital signature of the key attribute information of the authentication device and the temporary public key of the authenticated device to the authentication device to be verified by the authentication device; receiving and verifying, by the authentication device, the second digital signature; and sending, by the authenticated device, authentication success information, and performing encrypted data transmission by using the temporary public keys of the two parties. The authentication device and the authenticated device correctly the key attribute information of the opposite party and perform signature verification so as to achieve two-way authentication. The encrypted transmission of data interaction is realized, and the security of identity verification is further improved.
Owner:北京赛博兴安科技有限公司
WAPI-based wireless LAN operation method
InactiveCN1996840AImprove securityEnsure safetyUser identity/authority verificationNetwork topologiesAuthorizationWireless lan
This invention relates to one wireless local operation method based on WAPI, which comprises the following steps: 21, interface controller identifies the mobile terminal account information; 22, servo gives out mobile terminal authorization information according to the account information result to exchange mobile terminal and network data.
Owner:CHINA IWNCOMM +1
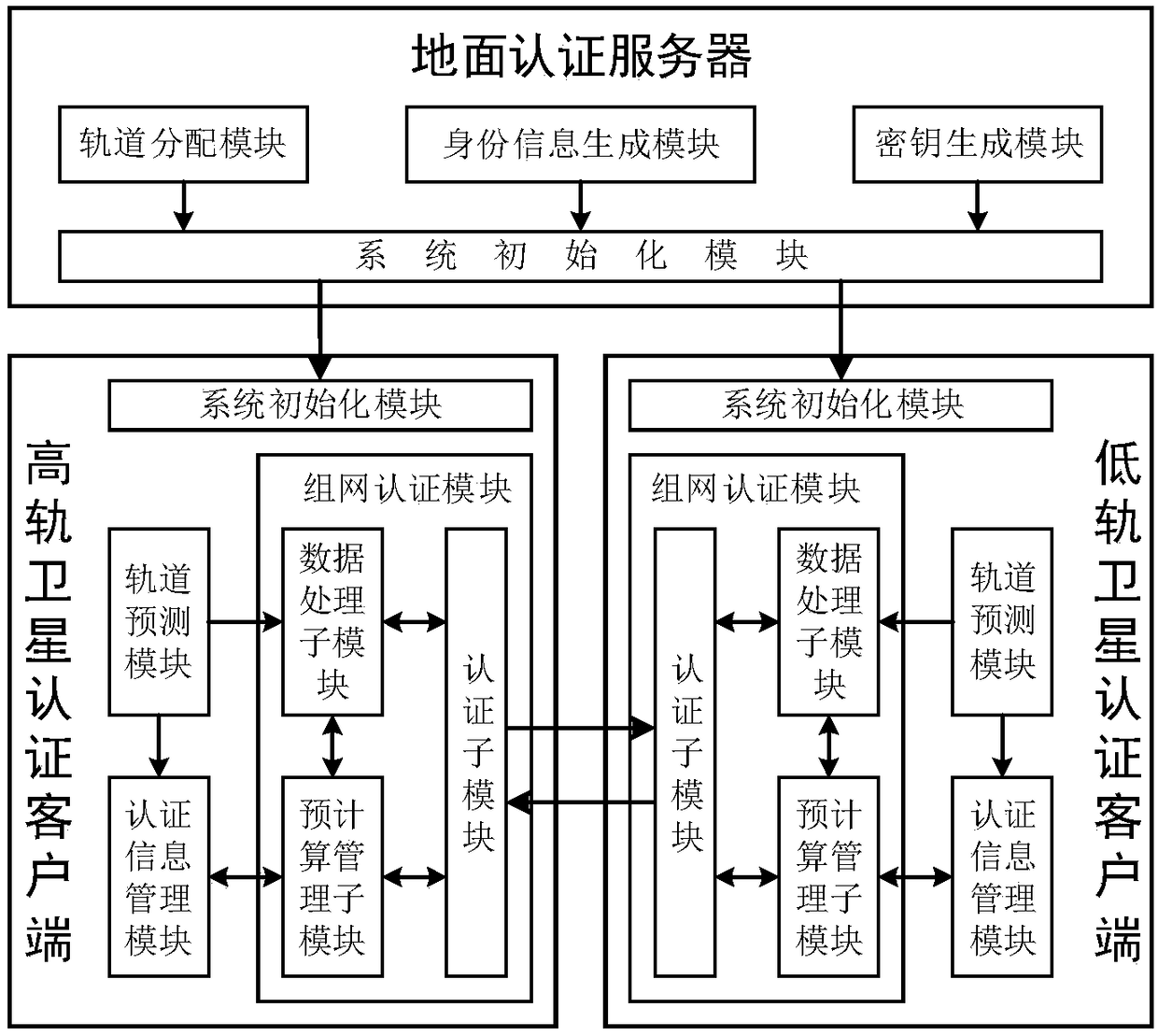
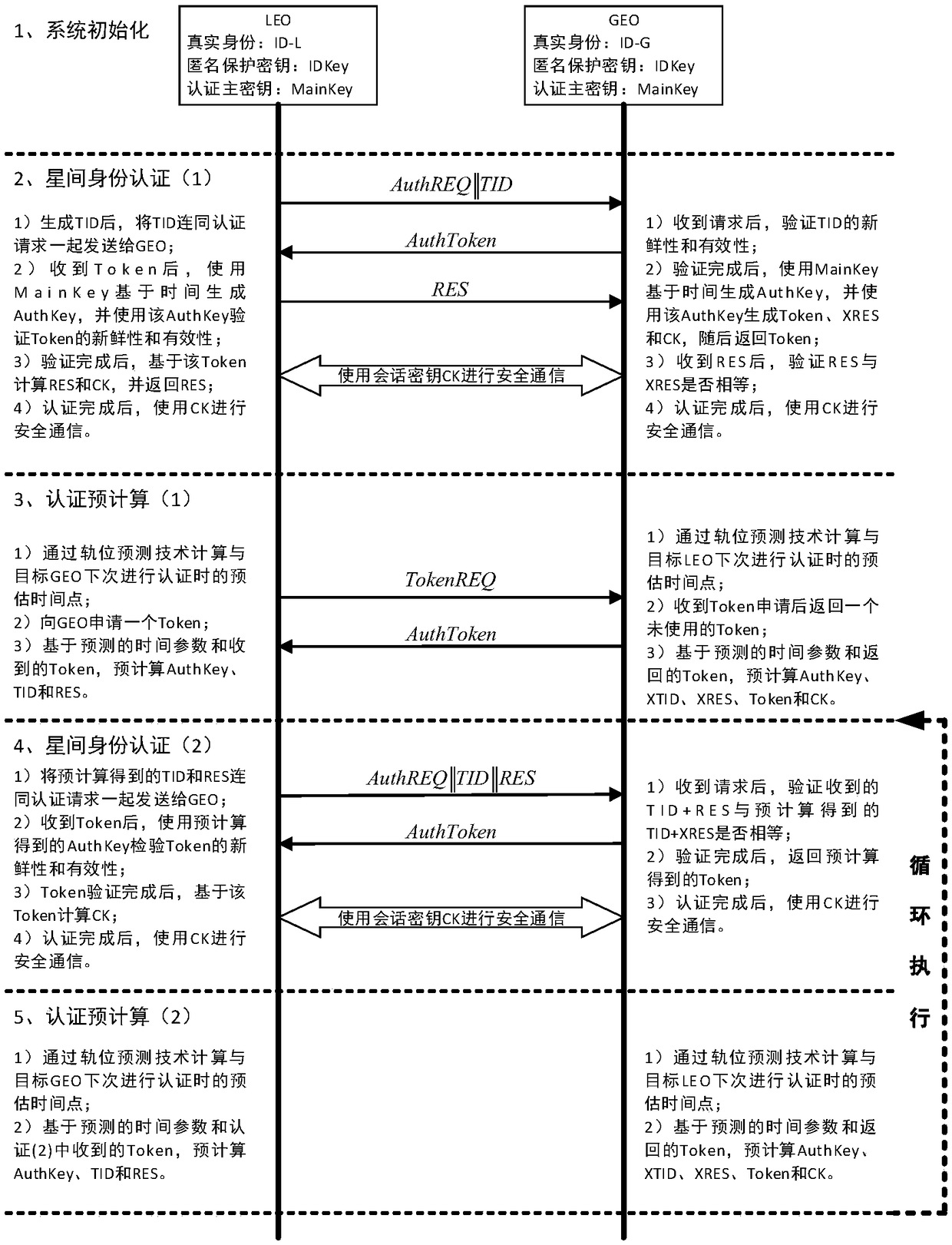
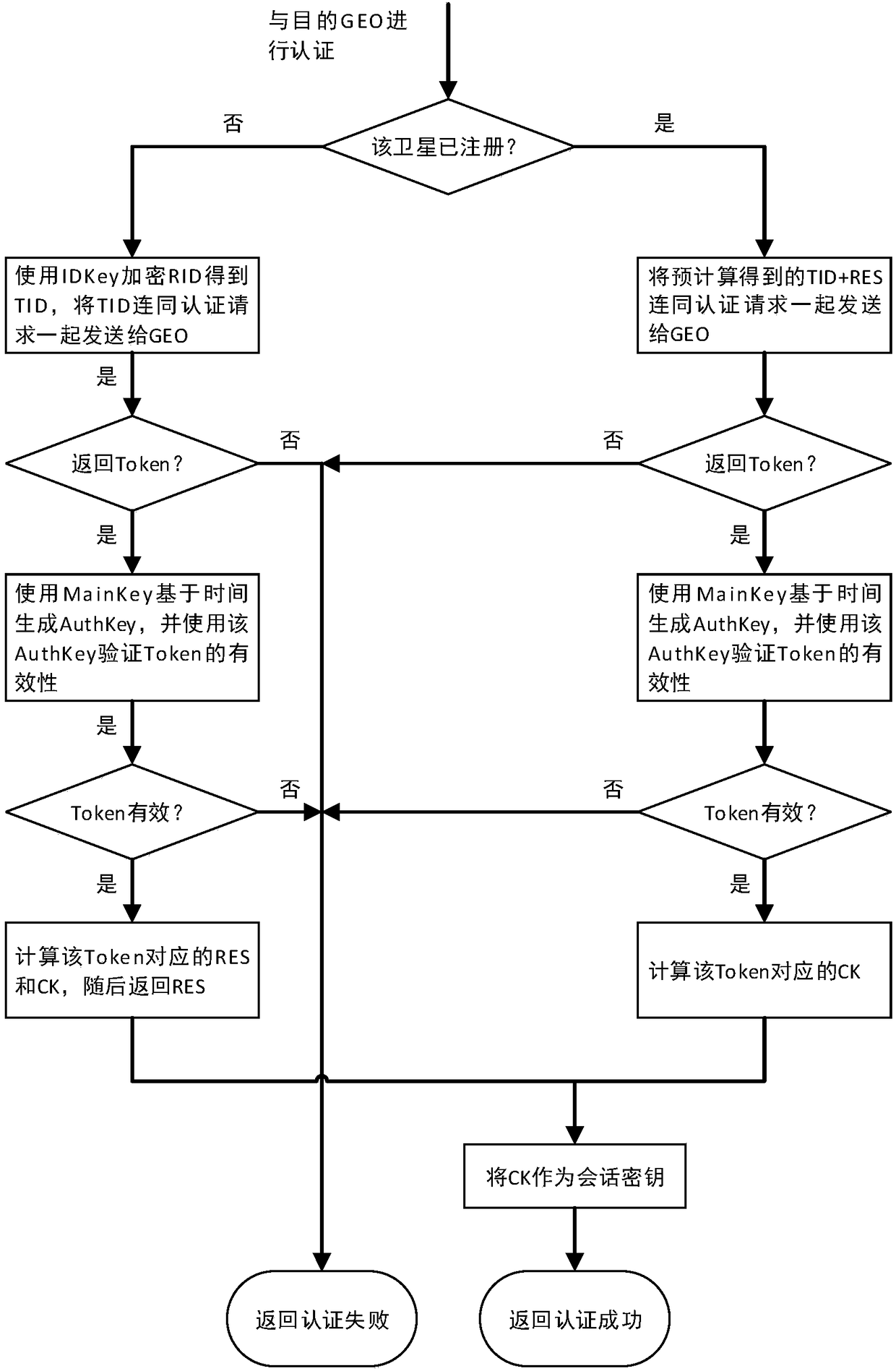
Inter-satellite networking authentication system and method suitable for double-layer satellite network
ActiveCN108566240AJudging freshnessImprove authentication efficiencyKey distribution for secure communicationUser identity/authority verificationPrecomputationAuthentication server
The invention belongs to the technical field of information safety, and discloses an inter-satellite networking authentication system and method suitable for a double-layer satellite network. The system comprises a ground authentication server, a high-orbit satellite authentication client and a low-orbit satellite authentication client, wherein the ground authentication server is used for completing initialization of a satellite authentication system, namely generating and distributing identity information, a secret key and track parameters which are needed for authentication between the satellites; the high-orbit satellite authentication client and the low-orbit satellite authentication client are main bodies of inter-satellite networking authentication, and the inter-satellite identity authentication and key negotiation are realized through the interaction of authentication parameters. An authentication precomputation mechanism is designed by utilizing the characteristics that a satellite network clock is highly synchronous and a node operation trajectory can be predicted, so that the authentication efficiency between the satellites is effectively improved. According to the system and the method, safe and efficient identity authentication and secret key negotiation of a high-orbit satellite and a low-orbit satellite in a networking stage can be realized, and the system and the method can be applied to networking authentication between the high-orbit satellite and the low-orbit satellite.
Owner:XIDIAN UNIV +1
Network authentication attack prediction method and system
InactiveCN110808836AAdd authentication signatureImplement two-way authenticationKey distribution for secure communicationUser identity/authority verificationTrusted authorityAttack
The invention provides a network authentication attack prediction method and system. The method comprises the following steps: establishing a security encryption channel between a controller and a switch, adding a trusted authority CA to authenticate and sign the controller and the switch, realizing bidirectional authentication between the controller and the switch, and performing key negotiationbetween the controller and the switch to realize targeted improvement of SDN network vulnerability; meanwhile, collecting data fragment copies; extracting available attack vectors; and analyzing whether the data fragments are abnormal or not and whether the plurality of abnormal data fragments are logically associated or not, thereby determining abnormal points, obtaining potential attack trajectories and security vulnerabilities of the network nodes, predicting whether the abnormal network nodes are improved in the future or not, and predicting whether other nodes similar to the network nodesare attacked or not.
Owner:武汉思普崚技术有限公司
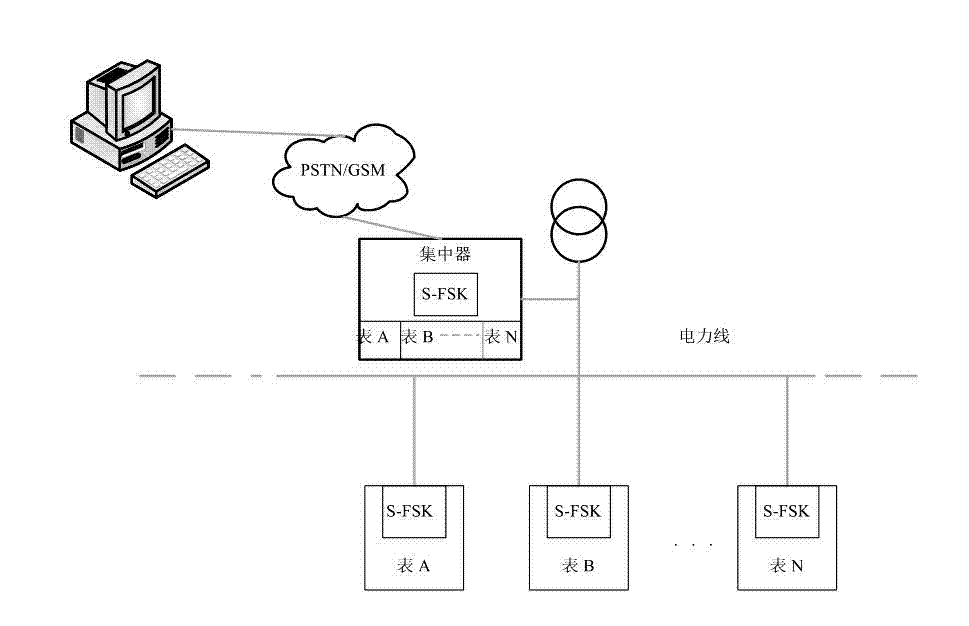
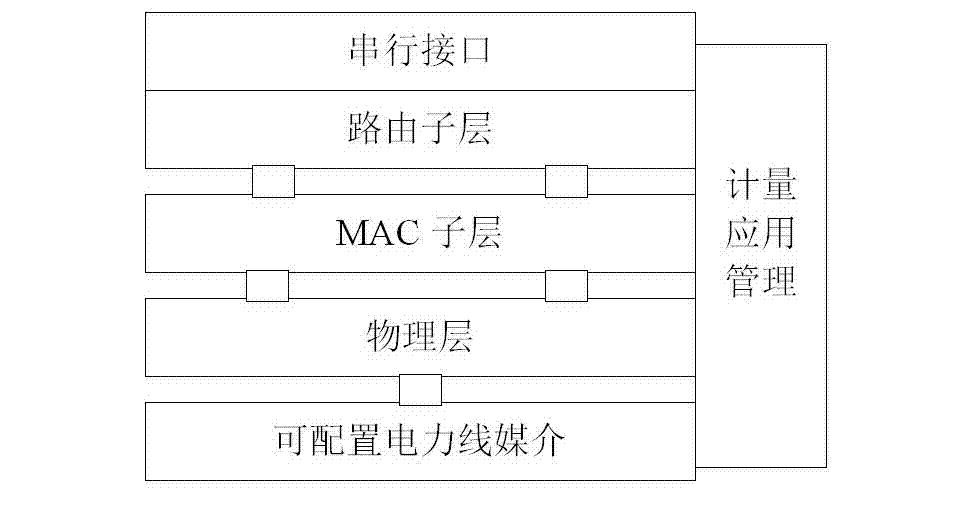
Network accessing method of automatic meter reading system
ActiveCN102832973ASolve the problem of unreliable joining the networkSolve the problem of not being able to automatically disengagePower distribution line transmissionUser identity/authority verificationElectricityAccess method
The invention discloses a network accessing method of an automatic meter reading system. The networking accessing method comprises the following steps of electrically starting and creating a network on an OFDM (Orthogonal Frequency Division Multiplexing) module at a concentrator side firstly, and then electrically adding the network on the OFDM module at an electric energy meter side. According to the network accessing method disclosed by the invention, the OFDM module adopts a mechanism of adding bidirectional authentication in the network, so the problem that an S-FSK power line carrier automatic meter reading system is unreliable in accessing the network is solved; a list file is maintained by a main module, so the problem that in the prior art, the list file work needs to be maintained in real time by a concentrator is solved; and meanwhile, the automatic separation can be carried out when an error network is added as the communication overtime time length is set, and thus the problem that in the prior art, the automatic separation cannot be carried out when an electric energy meter is added with the error network. Compared with the prior art, according to the network accessing method disclosed by the invention, several defects existing in the prior art are completely and effectively overcome, and the network accessing method of a power line carrier communication module with higher reliability is provided.
Owner:HUNAN UNIV +1
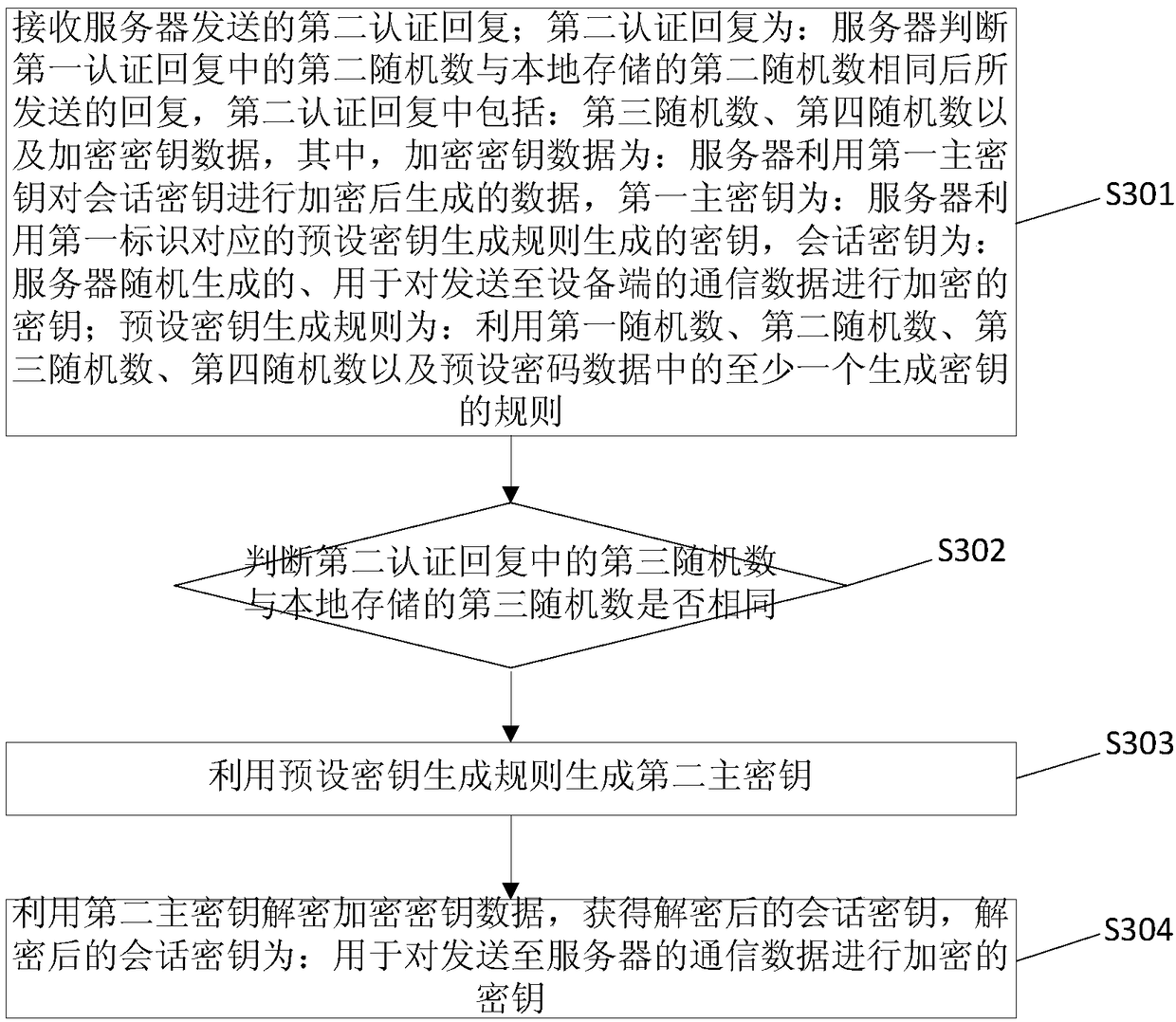
Authentication method and system
InactiveCN109391468AReduce manufacturing costImplement two-way authenticationKey distribution for secure communicationAuthentication
The embodiment of the invention provides an authentication method and system, and the method comprises the steps: enabling a device side to transmit a first authentication request to a server, whereinthe first authentication request comprises a first identification of the device side and a first random number, and the first random number is a character string which is generated by the device siderandomly; receiving a second authentication request sent by the server, wherein the second authentication request is a request sent by the server after the server performs the authentication of the device side based on the first identification and the authentication is passed, and comprises the first random number and a second random number, and the second random number is a character string generated by the server randomly; judging whether the first random number in the second authentication request is the same as a first random number stored locally or not: giving a first authentication reply to the server when the first random number in the second authentication request is the same as the first random number stored locally, so as to notify the server that the authentication is passed.According to the embodiment of the invention, the method reduces the requirements for the storage space of the device side to a certain degree, and reduces the production cost of the device side to acertain degree.
Owner:HANGZHOU EZVIZ NETWORK CO LTD
Mobile secure storage equipment with multiple data protection functions
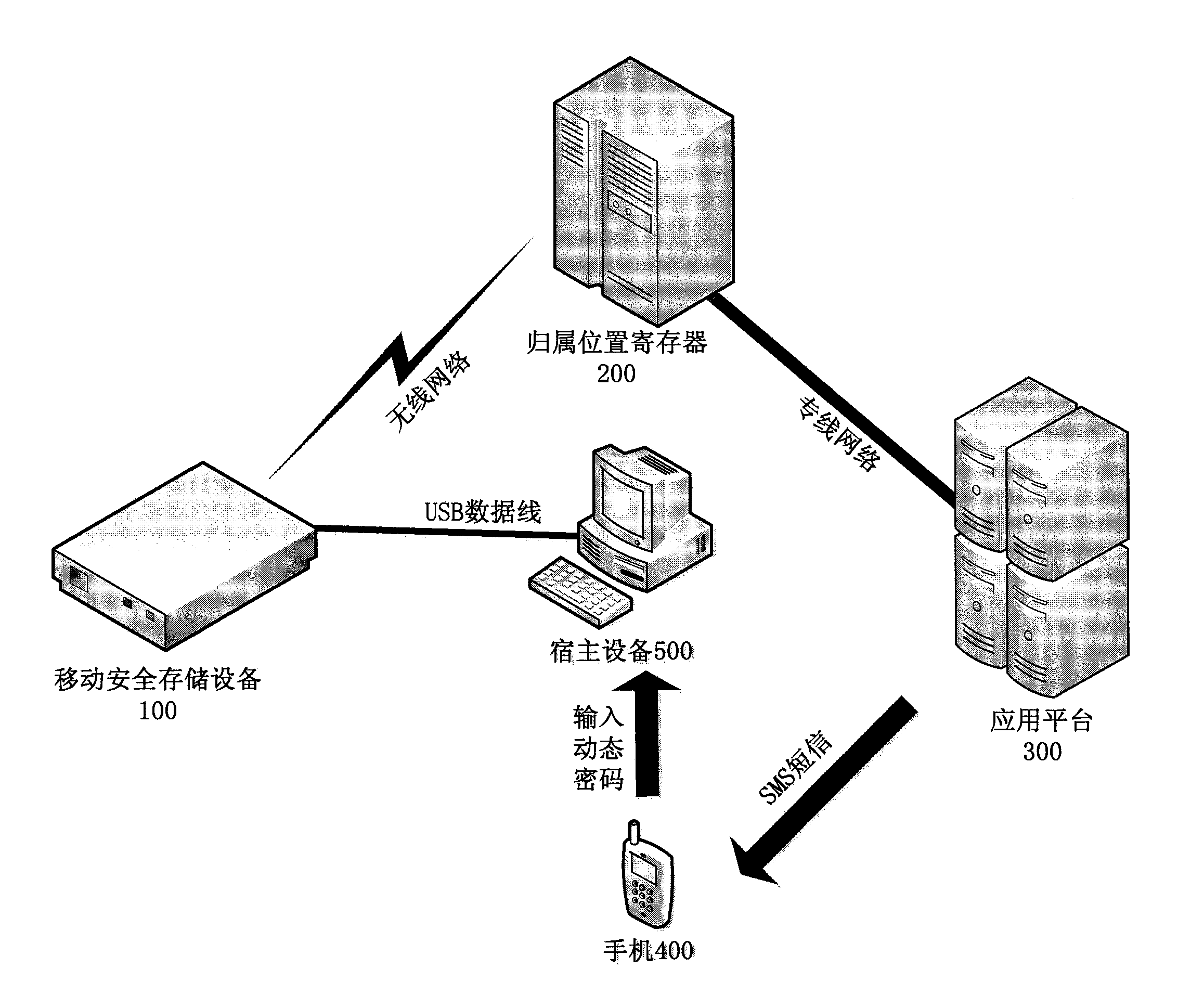
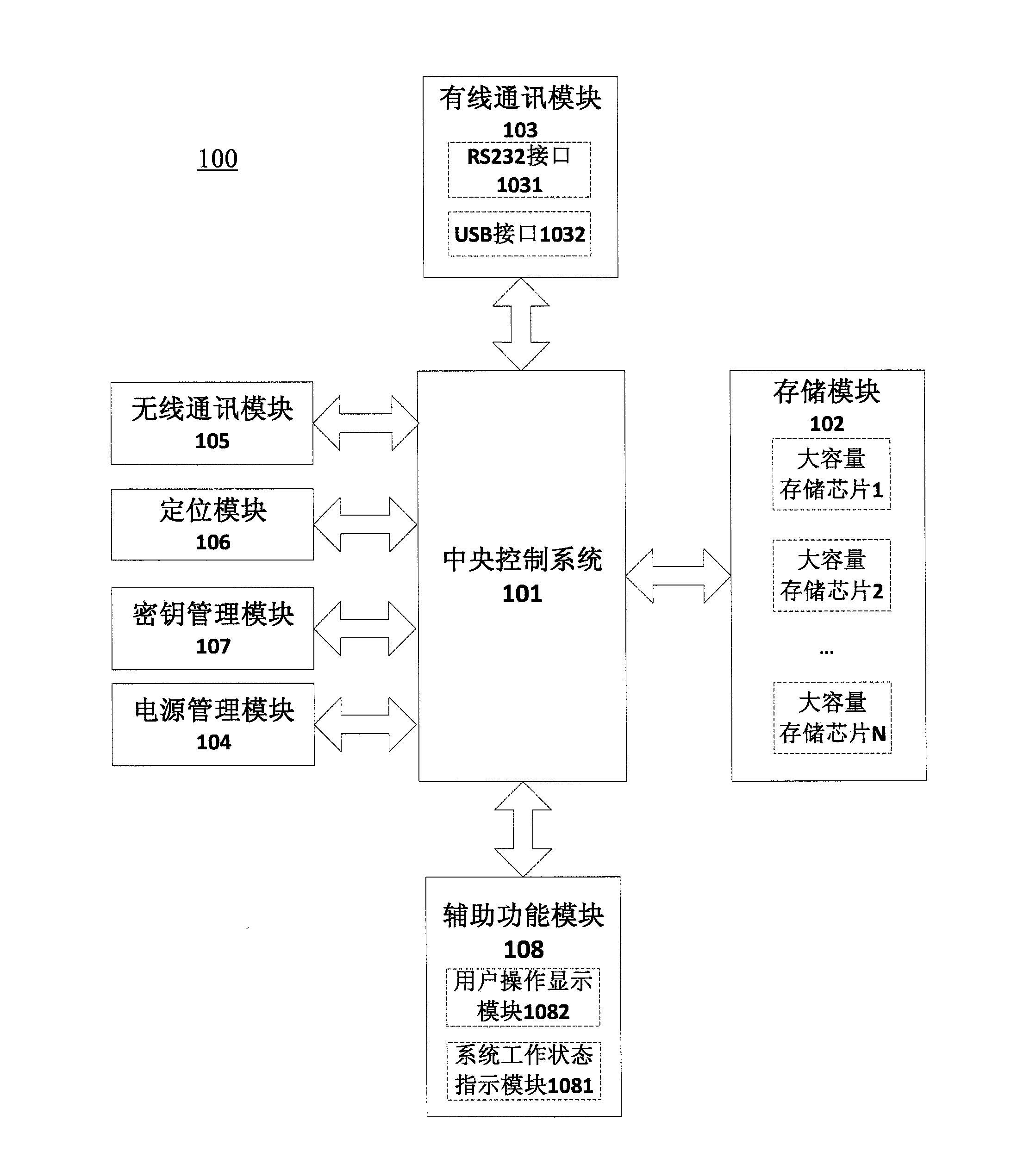
InactiveCN103853672ASafe and reliable authentication methodImprove securityMemory loss protectionUnauthorized memory use protectionOperational systemElectrical battery
The invention provides mobile secure storage equipment with multiple data protection functions. The mobile secure storage equipment comprises a storage module, a wired communication module, a wireless communication module, a key management module, a power management module and a central control system. Encrypted data are stored in the storage module; the wired communication module comprises an USB (universal serial bus) interface, and data can be exchanged between the wired communication module and host equipment; authentication data and business data can be transmitted between the wireless communication module and a home location register; the key management module is responsible for mutual authentication between the storage equipment and an application platform and encryption and decryption of data exchanged between the host equipment and the storage module; the power management module is responsible for charging internal batteries when the mobile secure storage equipment is externally connected and utilized via a USB, the various modules of the mobile secure storage equipment are powered by external power sources at the moment, and necessary working power is provided for the wireless communication module by the internal batteries when the mobile secure storage equipment is not externally connected and utilized via the USB; an operating system runs in the central control system, and the central control system manages the various modules of the mobile secure storage equipment in an integrated manner, schedules the various modules according to set working processes and manages communication of the various modules according to the set working processes. The mobile secure storage equipment has the advantages that various fused protection means are adopted, and accordingly the security of the mobile secure storage equipment can be improved.
Owner:SHANGHAI ZHONGYI COMM TECH ENG
Method, system and device for mutual authentication
InactiveCN101938741AImplement two-way authenticationConnection managementSecurity arrangementSubscriber identity moduleReplay attack
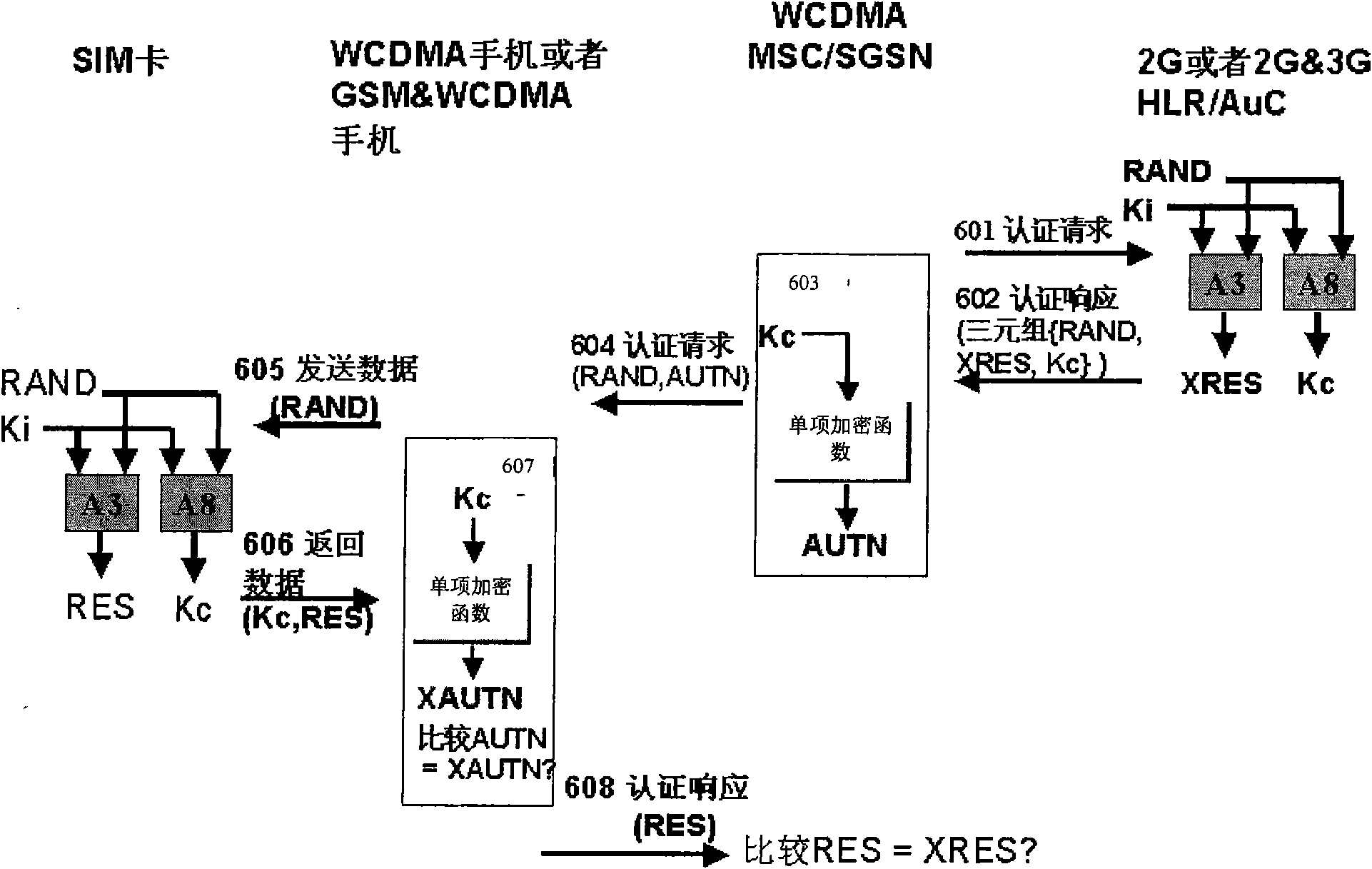
The invention provides a method, a system and a device for mutual authentication. The method comprises: a network entity obtains the new triplet vector of mobile equipment (ME); according to the triplet vector, the network entity generates an output parameter and sends the output parameter to the ME, wherein the output parameter is formed by encrypting random number RAND and authentication execution time CNR; the ME decrypts the output parameter and authenticates the network according to a decrypting result; meanwhile, the a subscriber identity module (SIM) card of the ME generates an RES and sends the generated RES to the network entity; and the network entity authenticates the ME according to the received RES. The invention can realize mutual authentication between ME and the network side and can judge that ME authenticates the network not to pass when suffering replay attack.
Owner:CHINA ACAD OF TELECOMM TECH
System and realization method for trusted authentication of user login in operating system
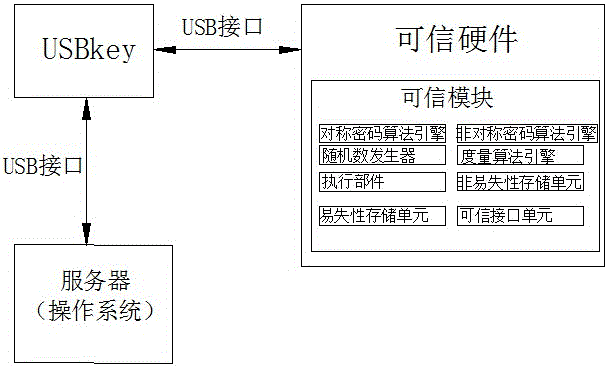
ActiveCN106127016AIdentity information protectionOvercome the defects of the login authentication methodDigital data protectionDigital data authenticationTrusted hardwareOperational system
The invention discloses a system and realization method for trusted authentication of user login in an operating system, pertaining to the computer security field. The technical problem to be solved is that a host of insecurity factors are caused by the method of utilizing simple passwords to verity users' identities by a traditional mainstream operation system. The adopted technical scheme is characterized in that the system comprises a USBkey and trusted hardware. The USBkey is connected with the trusted hardware through a USBkey interface and used for connecting with a server through the USBkey interface so that mutual authentication between the operation system and a user is achieved. The trusted hardware is used for storing information on users' identities and private information on related keys. The invention further comprises the operation system and the realization method for mutual authentication.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
Bidirectional authentication method and system based on symmetric encipherment algorithm
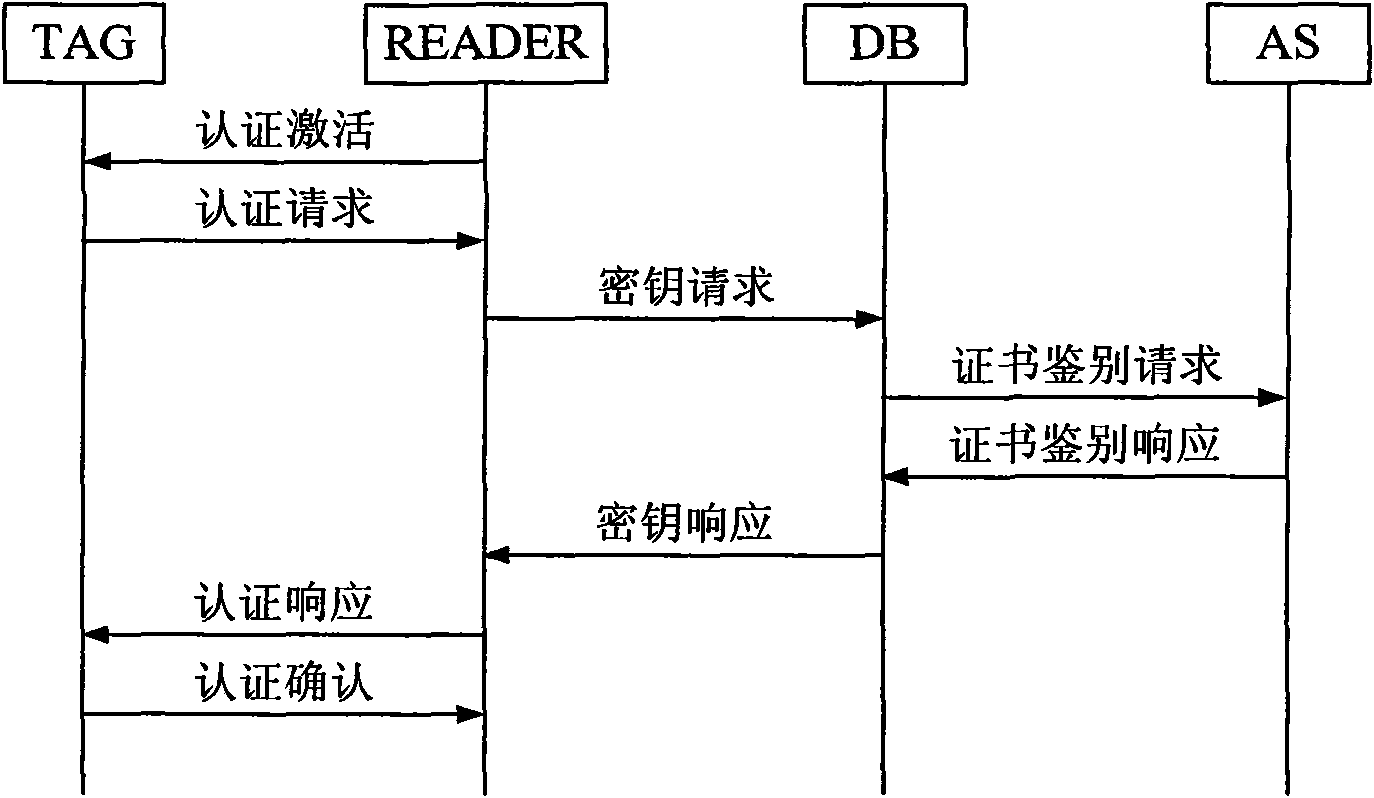
ActiveCN101645899AImplement two-way authenticationNo secure link requiredUser identity/authority verificationCo-operative working arrangementsElectronic taggingAuthentication server
The invention relates to a bidirectional authentication method and a system based on a symmetric encipherment algorithm. The method comprises: 1) a READER, a TAG and an electronic tag application system database (DB) corporately finish the collision process; 2) DB constructs and sends a certificate discrimination request grouping to an authentication server (AS); 3) sending a certificate discrimination response grouping to DB; 4) sending challenge information grouping to READER; 5) sending authentication request grouping to TAG; 8) sending the authentication response grouping to the READER; 7)sending certificate request grouping to DB; and 8) sending certificate response grouping to the READER. The invention can realize the bidirectional authentication method and the system based on the symmetric encipherment algorithm, which can perform bidirectional authentication and can reasonably utilize equipment performance without secure link between the database and the electronic tag.
Owner:CHINA IWNCOMM
Method, system and device for authenticating radio frequency tag
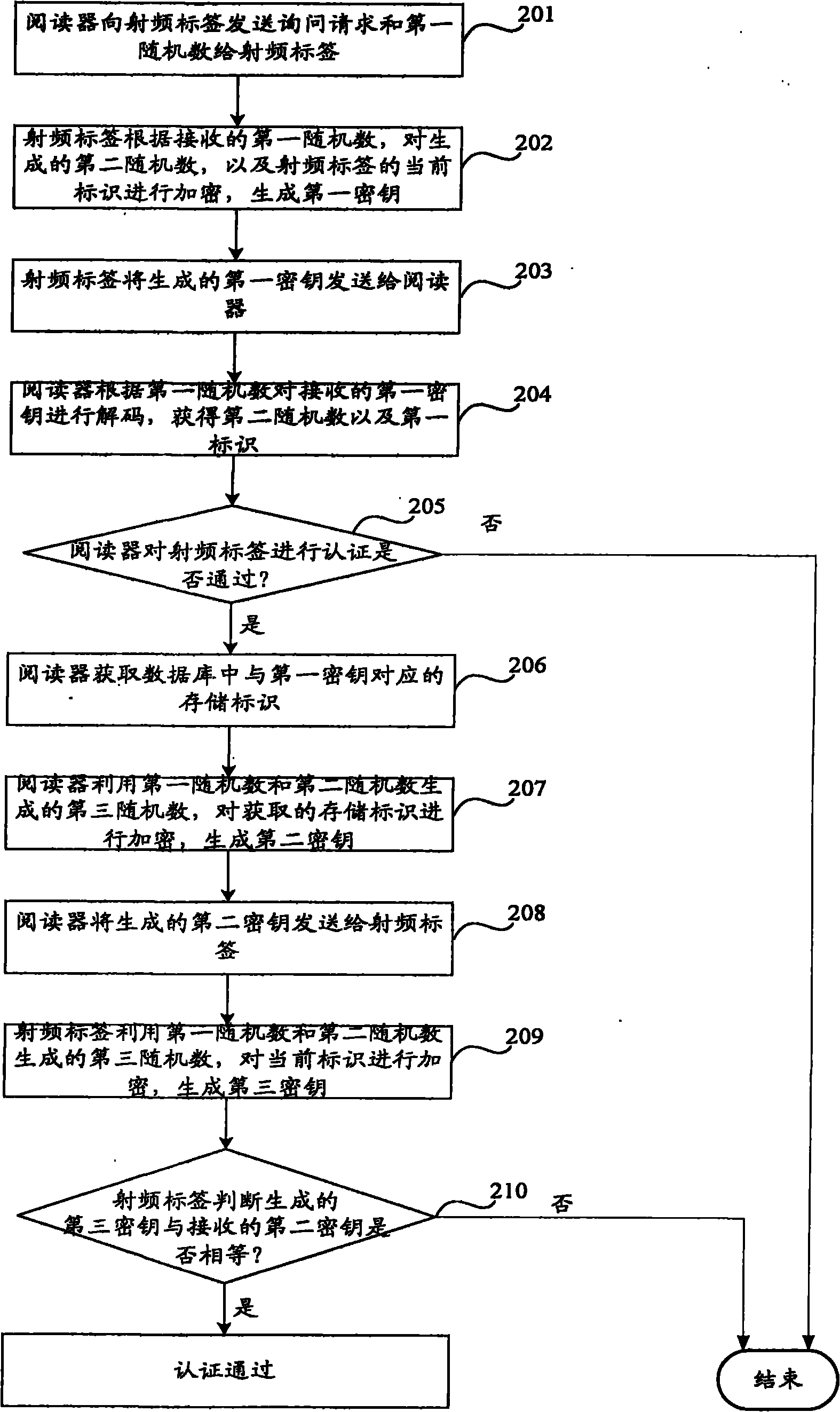
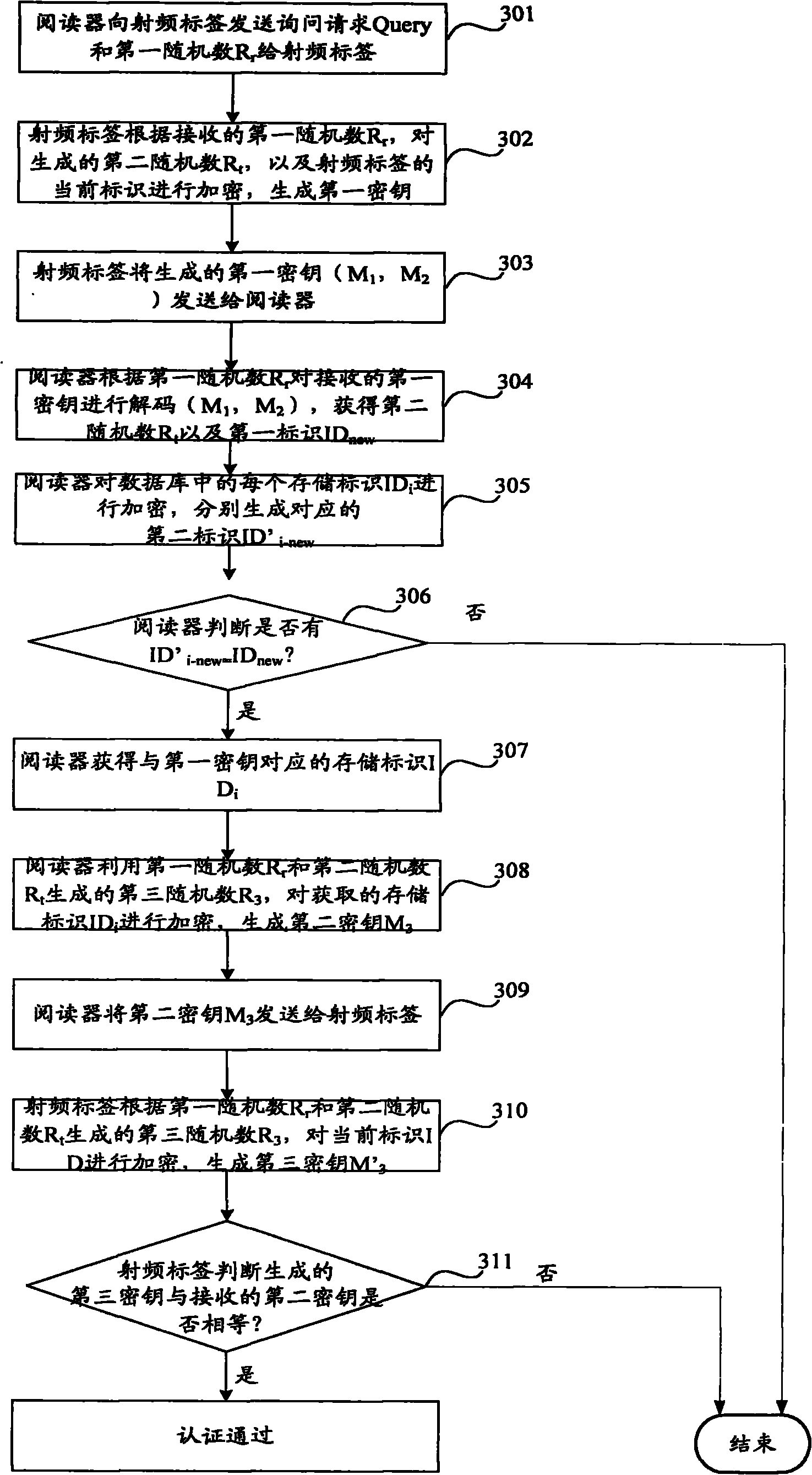
ActiveCN101980241AGuaranteed anonymityPrivacy protectionSensing record carriersRecord carriers used with machinesRadio frequencyRandom number generation
The invention discloses a method for authenticating a radio frequency tag. The method comprises the following steps that: the radio frequency tag receives a query request transmitted by a reader and a first random number generated by the reader; the radio frequency tag encrypts a generated second random number and a current identifier of the radio frequency tag according to the received first random number so as to generate a first key and transmit the first key to the reader; the radio frequency tag receives a second key returned by the reader, wherein the second key is generated by obtaining the second random number and a corresponding memory identifier by passing the authentication of the first key by the reader and encrypting the memory identifier by utilizing a third random number generated by the first random number and the second random number; and the radio frequency tag encrypts the current identifier by utilizing the third random number generated by the first random number and the second random number so as to generate a third key and confirms that the authentication of the reader is passed when the third key is equal to the received second key.
Owner:BEIJING WATCH DATA SYST
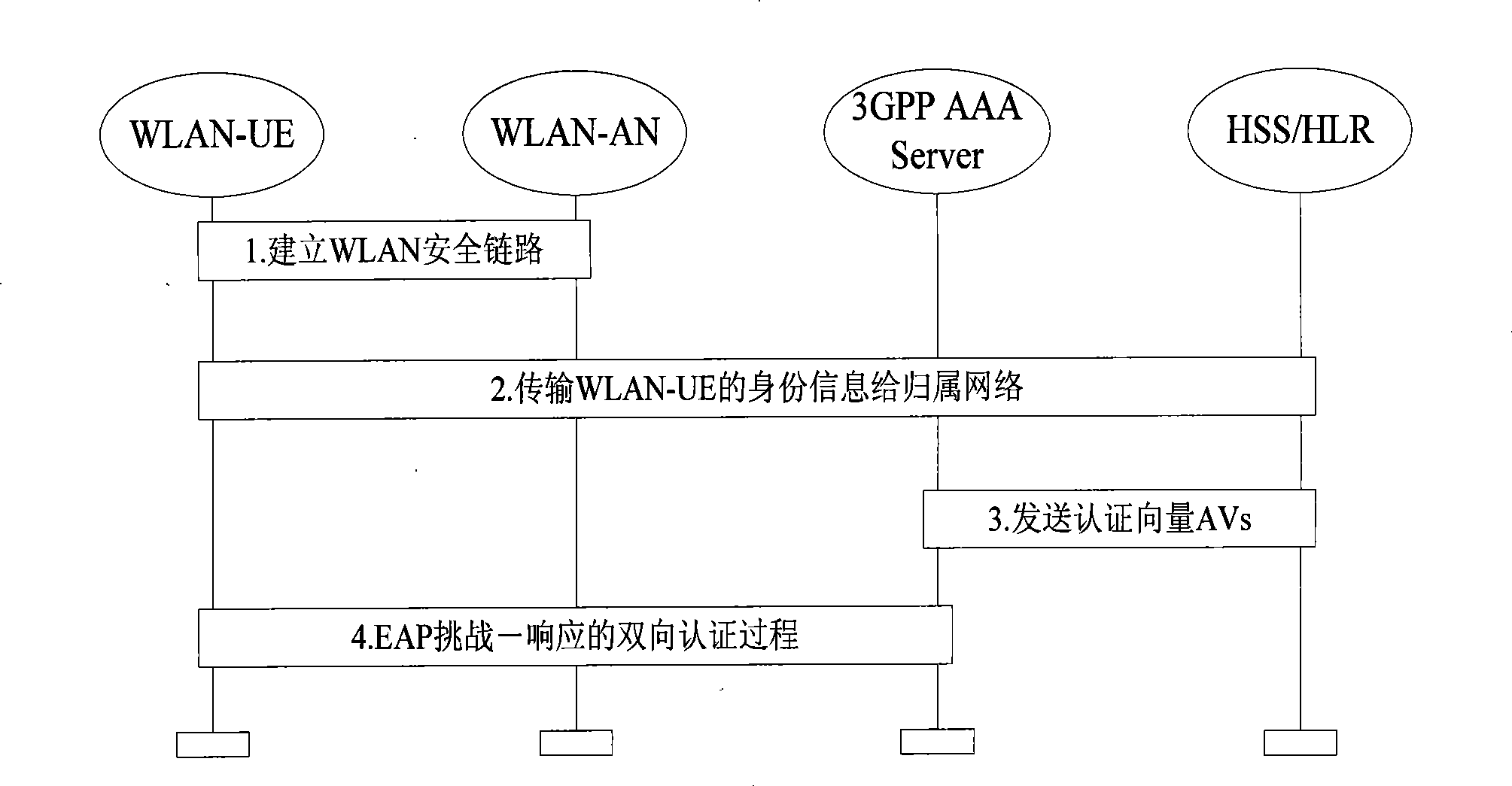
3G customer fast roaming authentication method based on wireless LAN
InactiveCN101420695AImplement two-way authenticationReduce delivery delayTransmissionSecurity arrangementAccess networkWireless mesh network
The invention provides a 3G user quick roaming authentication method based on a wireless local area network, belonging to the field of wireless communication. The method comprises the steps as follows: a user entity and a new access network establish a connection; the new access network gains the identity authentication information; subsequently, the old access network verifies the new access network and the identity of the user entity; finally, the new access network authenticates the user entity. The invention provides a quick roaming authentication method aiming at a 3G-WLAN Internet, leads the 3G mobile users to be quicker and safer to shift the roaming in access networks, and realizes the bidirectional authentication between the user entity and the 3G wireless access network at the same time; therefore the Re-direction attack behavior is withstood by the entity verification to the access network,; furthermore, the method effectively reduces the transmission delay of the message during the authentication process, improves the safety and efficiency of the access process of the 3G and heterogeneous internetworking network, and facilitates the mobile users to share smoother mobile services.
Owner:TIANJIN POLYTECHNIC UNIV +1
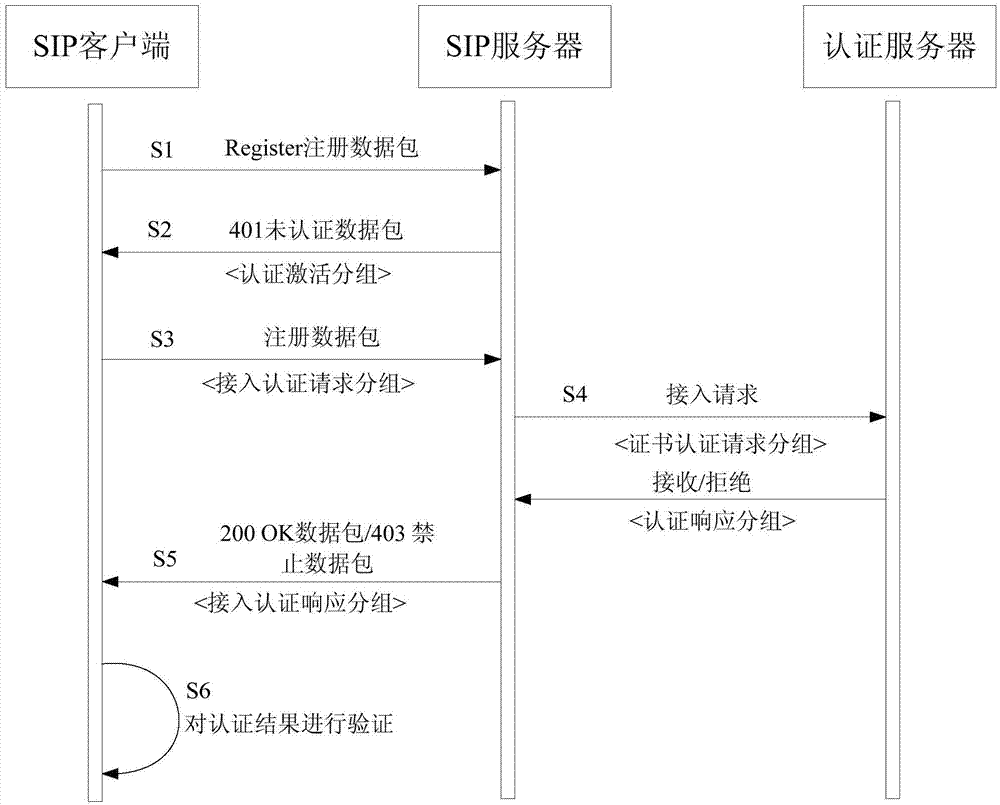
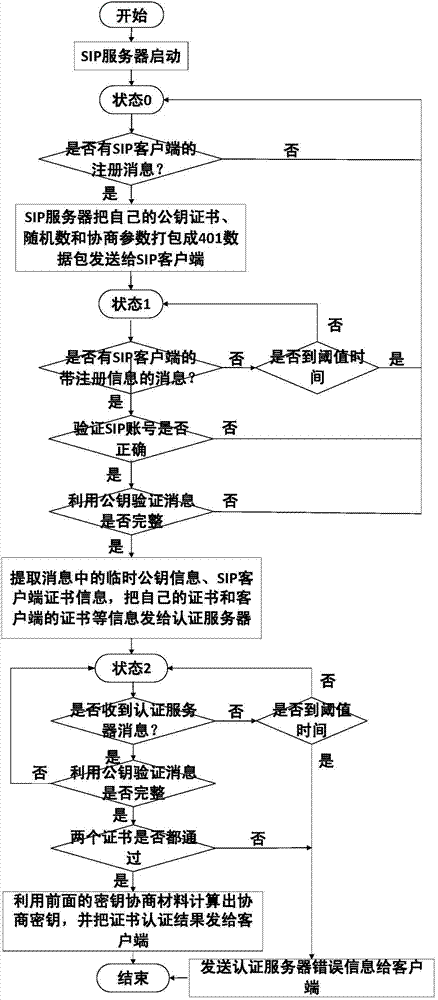
SIP (System In Package)-based security certificate registering method
The invention provides an SIP (System In Package)-based security certificate registering method. The method comprises the steps of transmitting a register data package into an SIP server by an SIP client; starting a register authentication module after the SIP server receives the register data package, transmitting an anauthorized data package, taking an authenticated activating grouped data, and requiring the SIP client to provide authentication information, wherein the authenticated activating grouped data comprises a public key certificate including an SIP server and a secrete key negotiating parameter; transmitting the register data package with register information including access authentication request grouped data by the SIP client according to user information, wherein the access authentication request grouped data comprises the public key certificate of the SIP client and the secrete key negotiating parameter of the SIP client; packaging the SIP server and the public key certificate of the SIP client into a certificate authentication request grouped data package by the SIP server and transmitting the SIP server and the public key certificate of the SIP client to a credible authentication server to verify; verifying whether a result is legal by the SIP server; and verifying the authentication result by the SIP client, and successfully approving by the SIP client if the authentication result is passed.
Owner:JIANGSU CAS JUNSHINE TECH
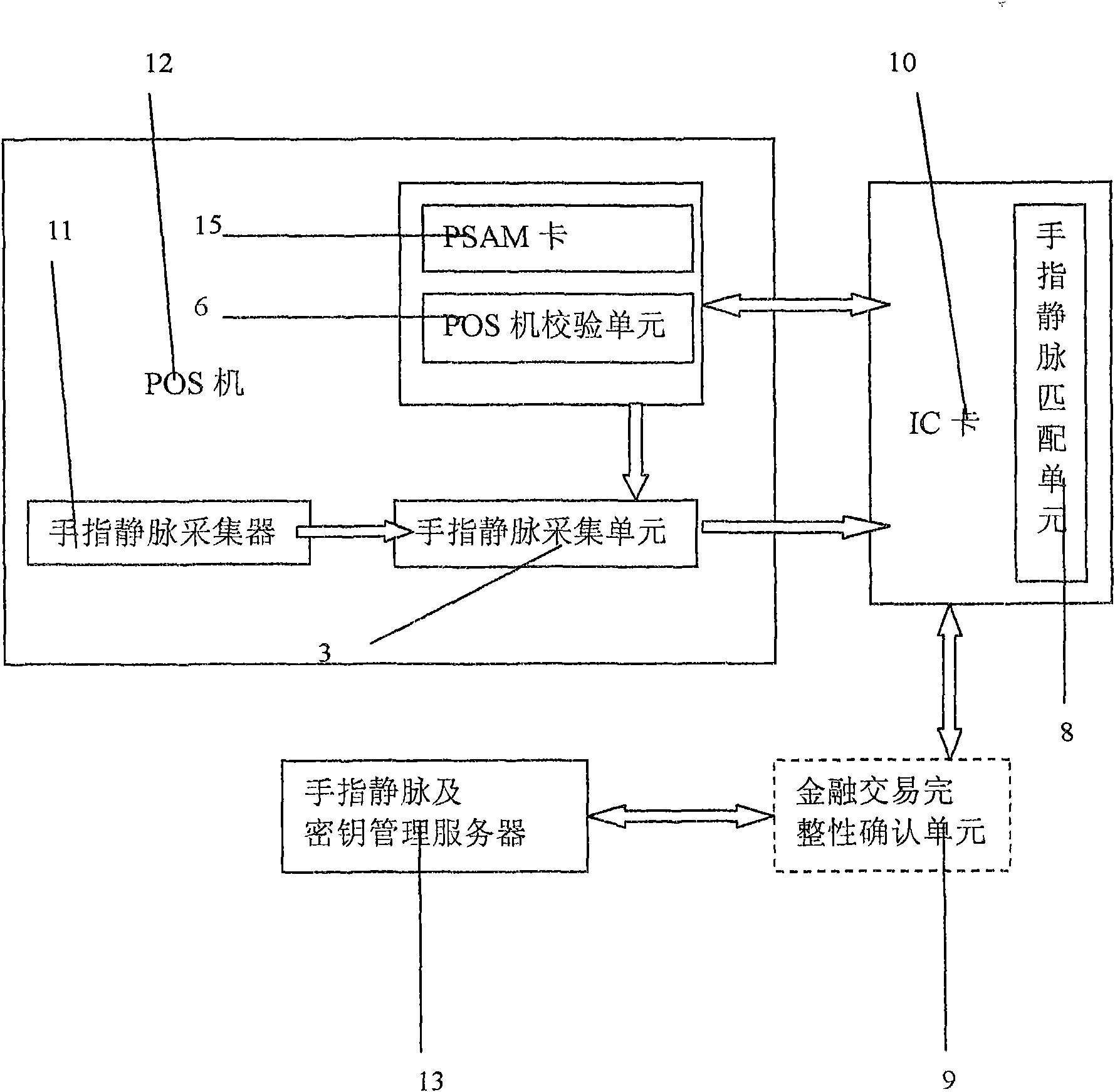
IC card consumption system integrating finger vein identification technology
ActiveCN101853542AGuaranteed confidentialityIntegrity guaranteedCharacter and pattern recognitionCoded identity card or credit card actuationComputer hardwareVein
The invention relates to the personal identity identification and IC card consumption field, which comprises the petty consumption of an offline electric wallet and an electric deposit book and the consumption transaction of an online credit card and a debit card. The invention particularly relates to a technology adopting biological identification technology-finger vein as IC card financial transaction user identity identification. The technical scheme of the invention adopts the IC card consumption system integrating the finger vein identification technology to replace the traditional magnetic stripe card system, which comprises an IC card issuing subsystem and a POS consumption subsystem.
Owner:张子文
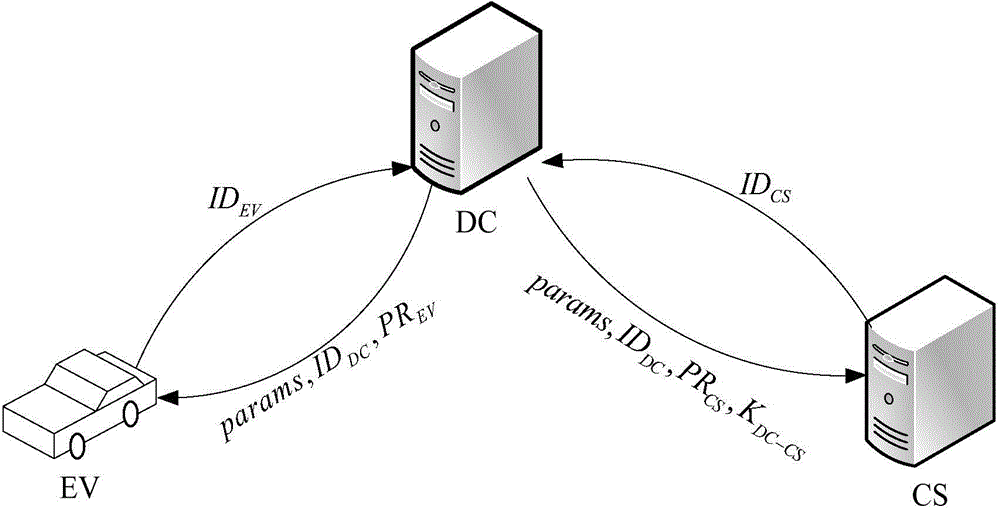
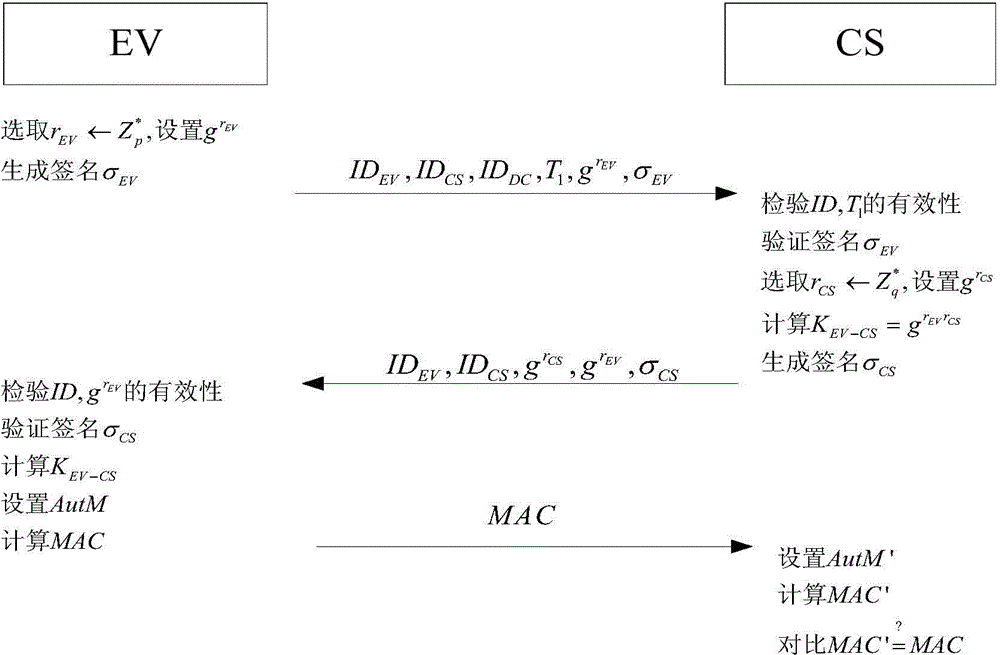
Access authentication method of electric automobile
The invention relates to an access authentication method of electric automobiles. The method comprises the following steps that: access authentication systems of the electric automobiles are established; access authentication between the electric automobiles and a charging station is carried out; and the charging station carries out batch signature authentication on the electric automobiles. According to the invention, identity aggregate signatures are introduced into identity validity inspection of the electric automobiles, and bidirectional authentication and session key negotiation are designed between the electric automobiles and the access authentication systems, so that the reasonable usage of the information resources in the station is ensured, and the safety of the whole network system is fundamentally ensured. The batch signature authentication mechanism enables the charging station to verify a plurality of electric automobile terminal signatures in the aggregate manner, the calculation load is lightened, and the performance is improved. The typical identity aggregate signature system is composed of five algorithms: system initialization, private key generation, signing, aggregation and aggregate verification, user identity information can be used to replace a public key thereof, the problem of high certificate cost is solved, and by compressing the plurality signatures into one, the high-efficiency verification is carried out.
Owner:STATE GRID CORP OF CHINA +2
Access verification method and terminal applied to wireless local area network WLAN
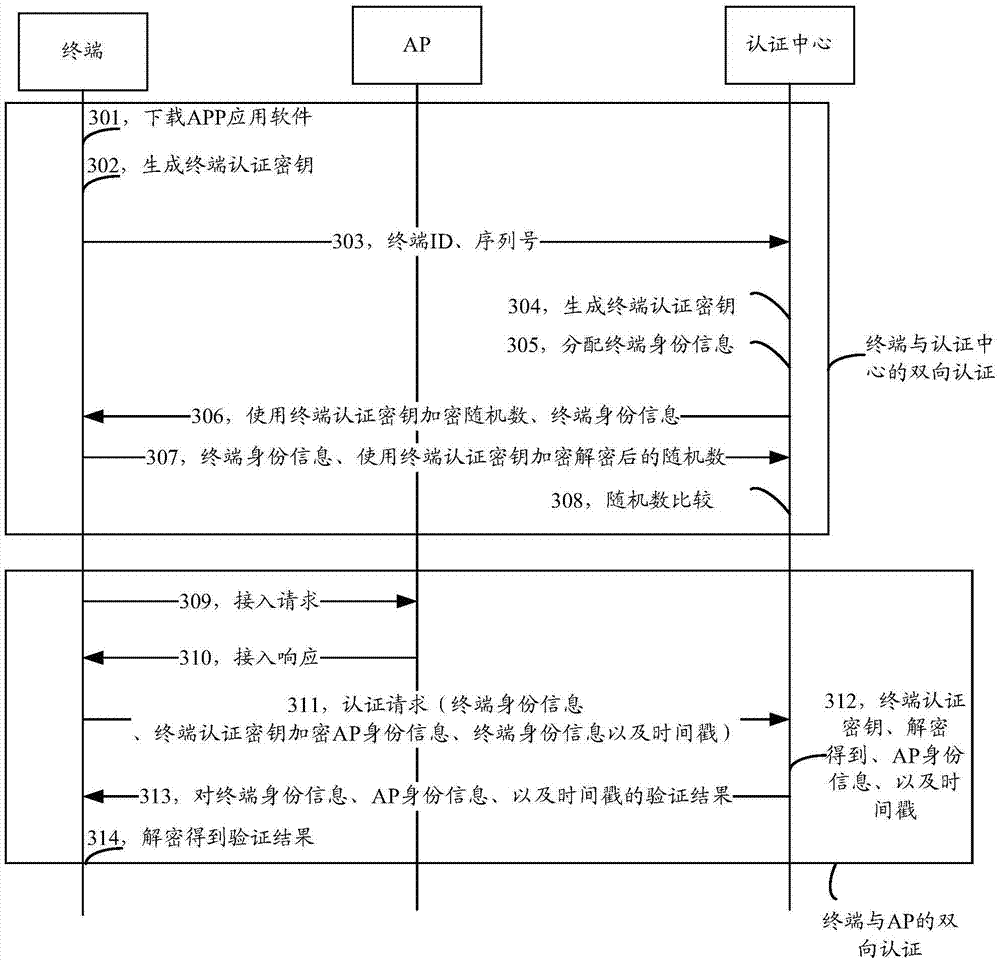
InactiveCN107026823AImplement two-way authenticationImprove securityTransmissionSecurity arrangementComputer networkComputer science
The invention provides an access verification method and terminal applied to a wireless local area network WLAN. According to the method and the terminal, bidirectional verification between the terminal and a verification center is realized, so identity registration of the terminal is finished; the bidirectional verification between the terminal and an AP (Access Point) is also realized; a mobile operator does not need to participate in the two bidirectional verification processes; through the bidirectional verification, a pseudo AP and a pseudo terminal can be identified; the security of accessing the WLAN by the terminal is improved; and the defect resulting from the fact that only one-way verification for the identity of UE can be realized based on an existing WiFi access verification mechanism is solved.
Owner:POTEVIO INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com