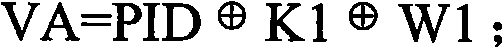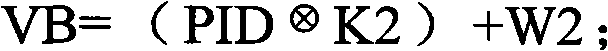Method and system for mutual authentication based on hash function
A two-way authentication and hash function technology, applied in the direction of digital transmission systems, transmission systems, collaborative devices, etc., can solve the problem of inappropriate low-performance electronic tags
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
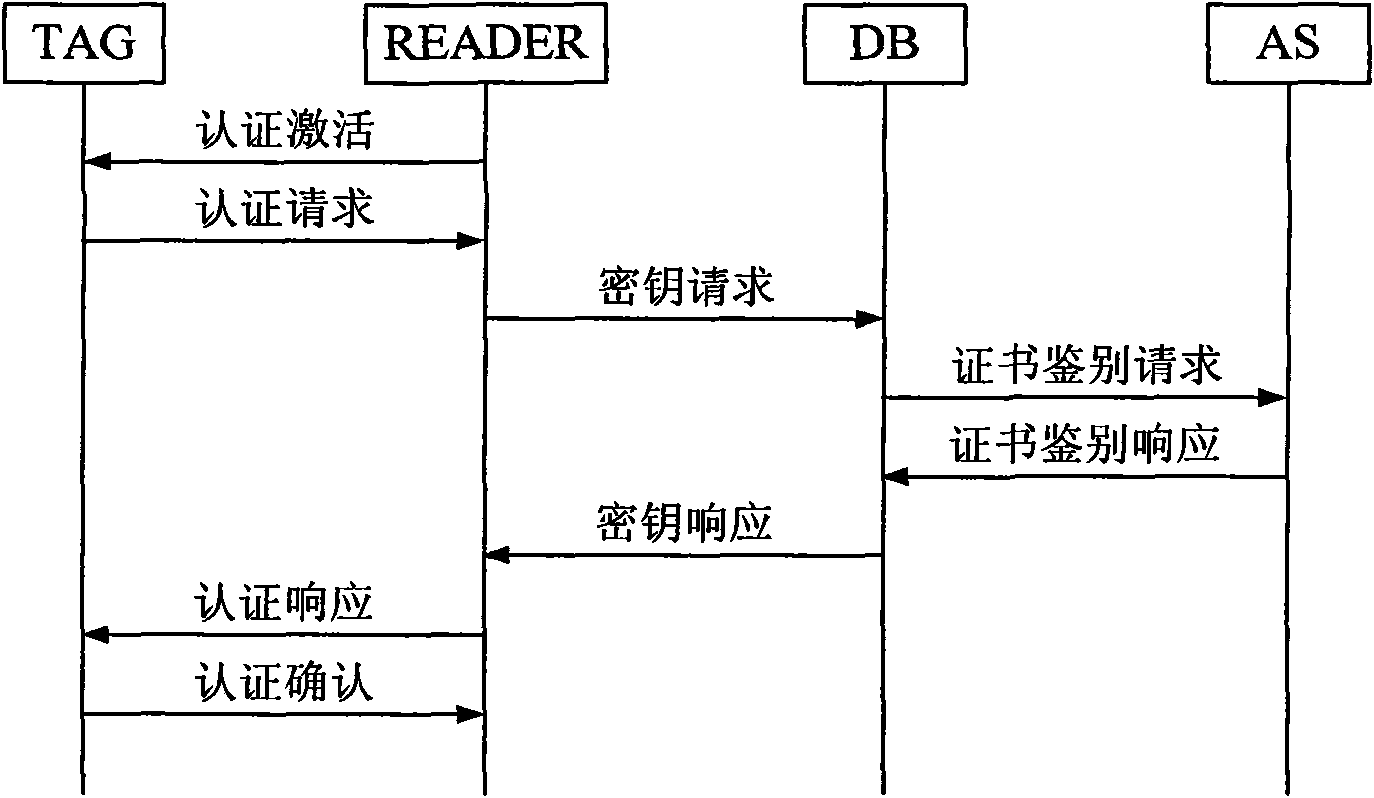
[0076] see figure 1 , the present invention provides a kind of two-way authentication method based on hash function, and this method comprises the following steps:
[0077] 1) Authentication activation: the authentication activation packet is sent by the reader-writer READER to the electronic tag TAG. The content of this group is empty, mainly to complete the READER providing energy to the electronic tag TAG.
[0078] After receiving the authentication activation packet, the electronic tag TAG constructs and sends the authentication request packet to the reader.
[0079] 2) Authentication request: the authentication request packet is sent by the electronic tag TAG to the READER. The content of the authentication request packet includes:
[0080] PIDs
[0081] in:
[0082] PID field: the current pseudo-identity of the electronic tag TAG;
[0083] N1 field: a one-time random number selected by the electronic tag TAG;
[0084] MIC1 field: The electronic tag TAG us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com