Access verification method and terminal applied to wireless local area network WLAN
A wireless local area network and terminal technology, which is applied in the field of network communication to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] see figure 2 , figure 2 It is a flowchart of the method provided by Embodiment 1 of the present invention. Such as figure 1 As shown, the process may include the following steps:
[0032] Step 201, the terminal downloads the APP application software, and the APP application software includes the public key of the certification authority and the asymmetric encryption algorithm engine.
[0033] Specifically, the terminal can download the above-mentioned APP application software from a designated secure website in a trusted network environment.
[0034] Step 202, the terminal installs and runs the downloaded APP application software, and generates a terminal public-private key pair through the asymmetric encryption algorithm engine included in the APP application software.
[0035] Here, the terminal public-private key pair includes a terminal public key and a terminal private key.
[0036] Step 203, the terminal uses the public key of the authentication center to e...
Embodiment 2
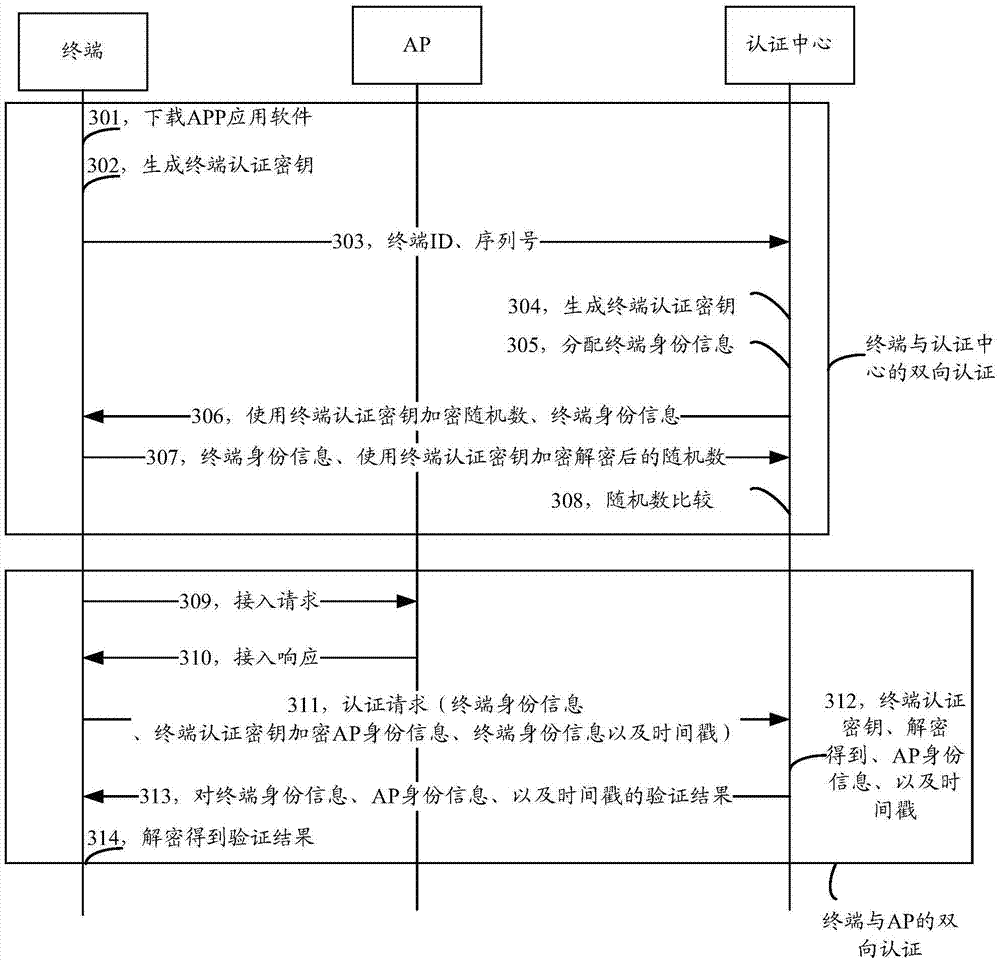
[0064] see image 3 , image 3 It is a flow chart of the method provided by Embodiment 2 of the present invention. Such as image 3 As shown, the process may include the following steps:
[0065] Step 301, the terminal downloads APP application software, and the APP application software includes an algorithm factor, a serial number, and an encryption algorithm.
[0066] Specifically, the terminal can download the above-mentioned APP application software from a designated secure website in a trusted network environment.
[0067] Step 302, the terminal installs and runs the downloaded APP application software, and uses its own terminal ID, algorithm factor, serial number, and encryption algorithm to calculate a terminal authentication key.
[0068] Step 303, the terminal sends the terminal ID and serial number to the authentication center.
[0069] In step 304, the authentication center calculates the terminal authentication key based on the received terminal ID and serial ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com