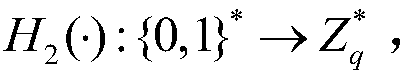Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
150results about How to "Guaranteed anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Modifiable reputation evaluation system and method based on block chain, and electronic payment system
ActiveCN107967557AAvoid injusticeGuaranteed transaction privacyFinanceDigital data protectionRing signatureE-commerce
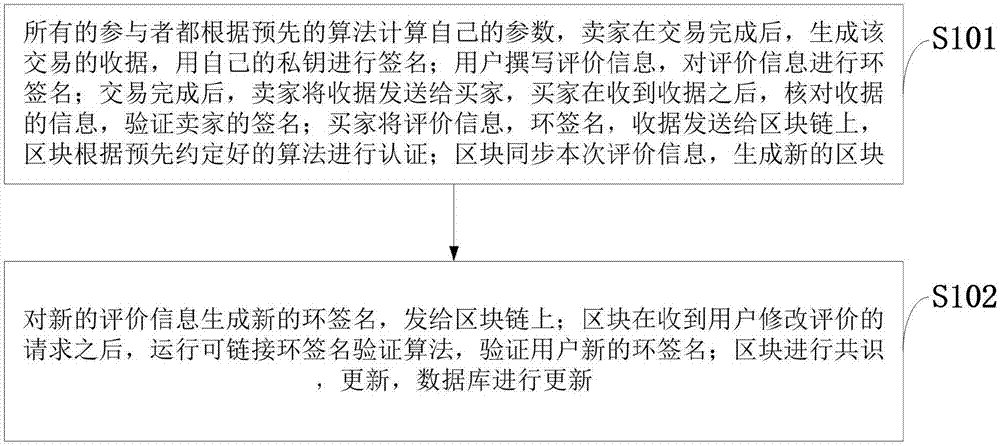
The invention belongs to the e-commerce technology field and discloses a modifiable reputation evaluation system and method based on a block chain, and an electronic payment system. A receipt from a seller is received by a user, the signature of the seller in the receipt is verified, and the evaluation information is generated; after verification is completed, a ring signature of the evaluation information is generated by the user, and the ring signature is sent to the block chain; the receipt and the ring signature of the user are verified by the block chain; a database is updated after the block is generated; a new signature is acquired by the user through a signature algorithm, and the new signature is sent to the block chain; validity of the signature is verified by the block chain, and whether the two signatures are completed by the same user is determined; a pointer corresponding to the block of a previous message is modified after verification completion, the previous message ismarked as invalid, and the previously-revoked information is replaced by the block of the message. The method is advantaged in that on the condition that user anonymity and transaction non-tamperability are guaranteed, integrity and openness of the evaluation information are guaranteed, and reliability of the evaluation information is guaranteed.
Owner:XIDIAN UNIV
Method and apparatus for electronic commerce using digital ticket to provide anonymity
InactiveUS20060085359A1Minimize informationEasy to usePublic key for secure communicationUser identity/authority verificationDigital signatureAnonymity
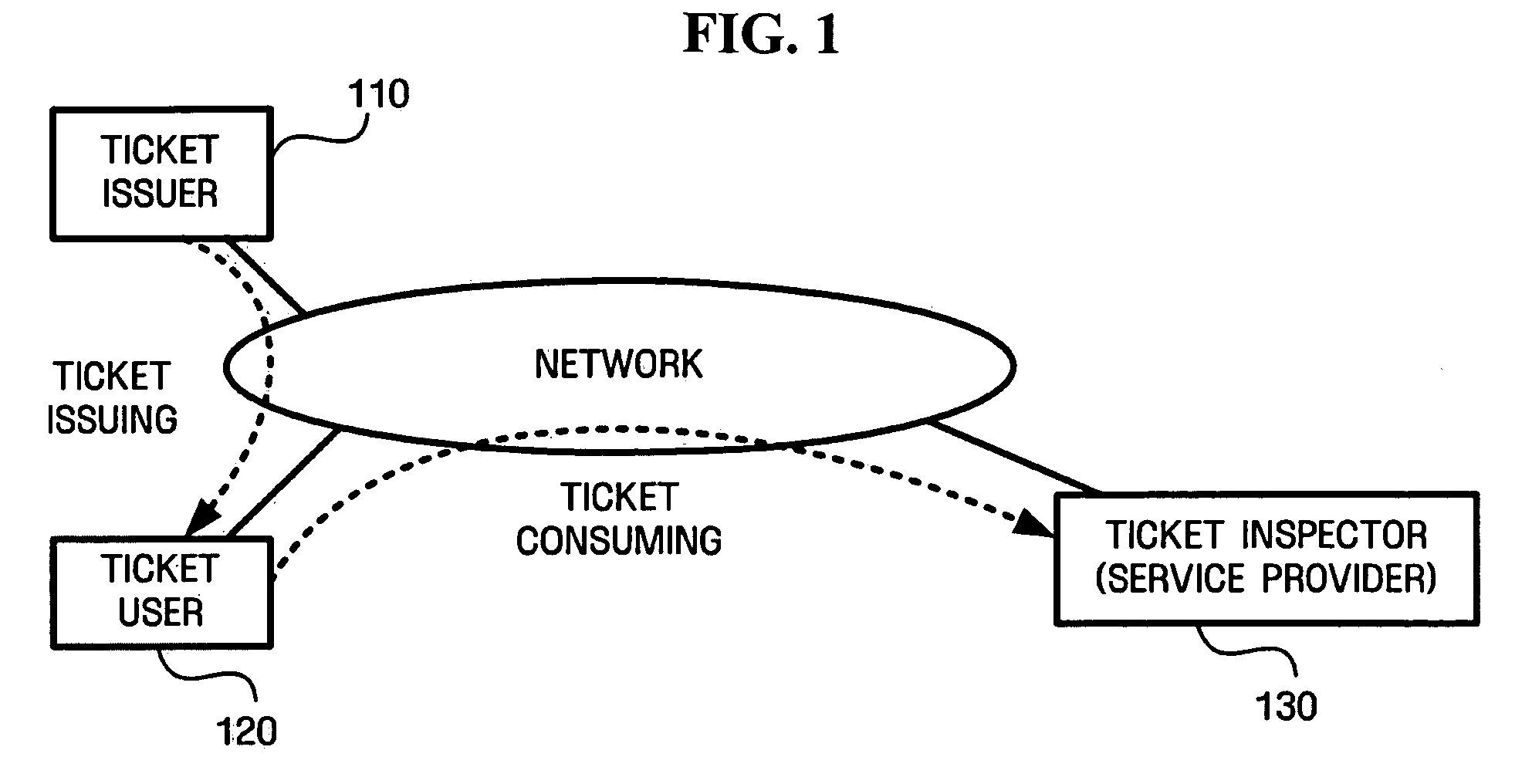
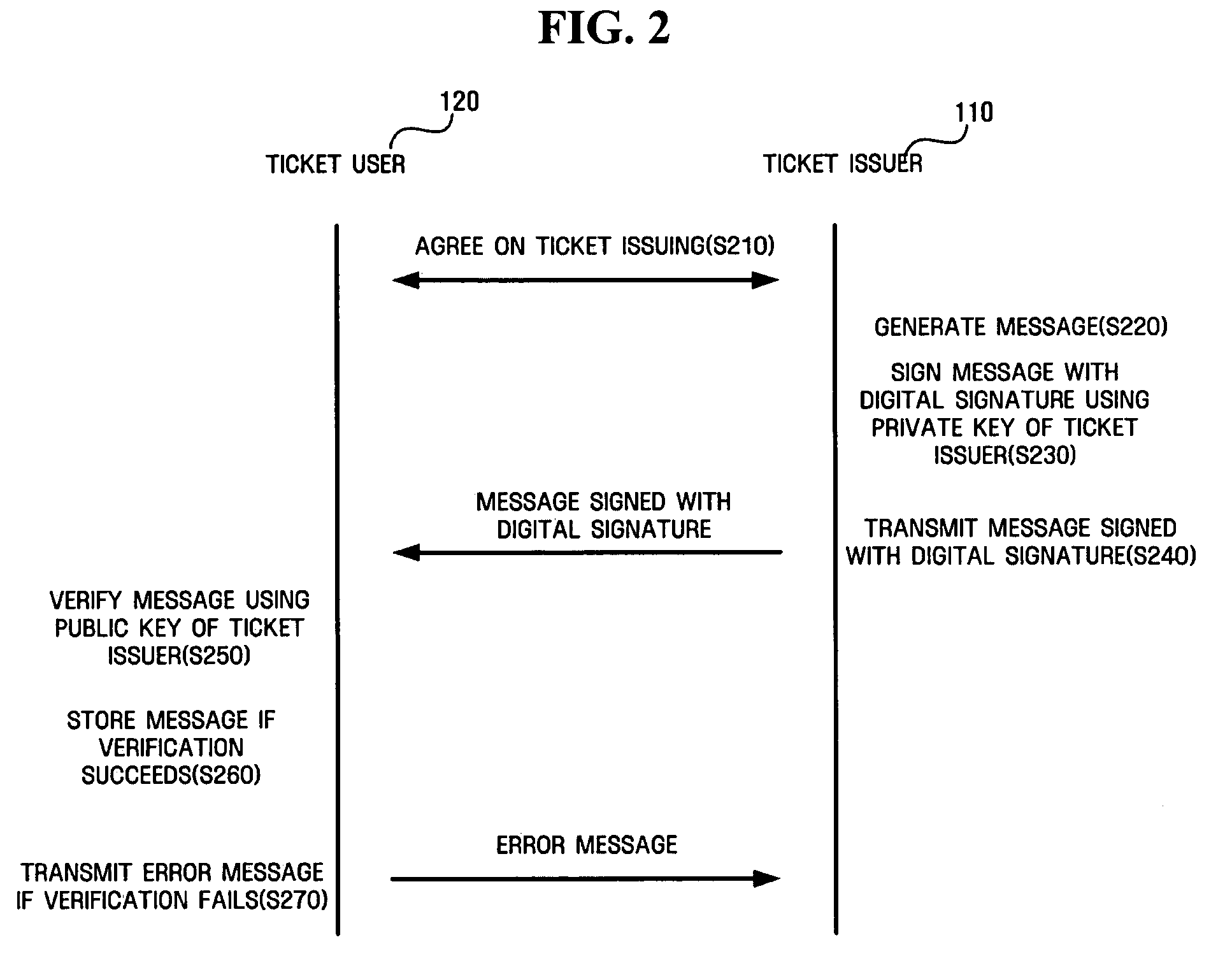
A method and apparatus for electronic commerce using a digital ticket are provided. The method for electronic commerce using a digital ticket includes hiding a message comprising a random number and transmitting the hidden message to a ticket issuer, receiving the hidden message signed with a digital signature by the ticket issuer, verifying the digital signature on the message, and transmitting the message with the verified digital signature to the ticket issuer to consume a digital ticket.
Owner:SAMSUNG ELECTRONICS CO LTD
IOV (Internet of Vehicles) anonymous authentication system with controllable link, and IOV anonymous authentication method
ActiveCN109391631AProtect private informationRealize controllable linkKey distribution for secure communicationEncryption apparatus with shift registers/memoriesService providerTrusted authority
The invention discloses an IOV (Internet of Vehicles) anonymous authentication system with a controllable link, and an IOV anonymous authentication method, and relates to the IO field. The system includes a system initialization module which is used for completing the initialization work of an IOV system and a TA (trusted authority); a registration module which is used for completing the registration of an OBU (onboard unit) and an RSU (roadside unit) to the TA; an OBU joining module which is used for obtaining a group certificate from the RSU when the OBU enters the communication range of a new RSU; a signature module which is used for completing the signature of a vehicle about a message; an authentication module which is used for completing the signature information authentication afterthe OBU receives the signature information; a link module which is used by an SP (service provider) to determine whether the two signature messages are linkable or not; an identity tracking module which is used for completing the process that the TA exposes the real identity of a signer of a valid signature message. The construction of the system uses a more lightweight elliptic curve operation to make the authentication process more efficient.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
PUF-based three-factor anonymous user authentication protocol method in Internet of Things
ActiveCN111818039ASave memorySave computing powerKey distribution for secure communicationSecurity arrangementAttackThe Internet
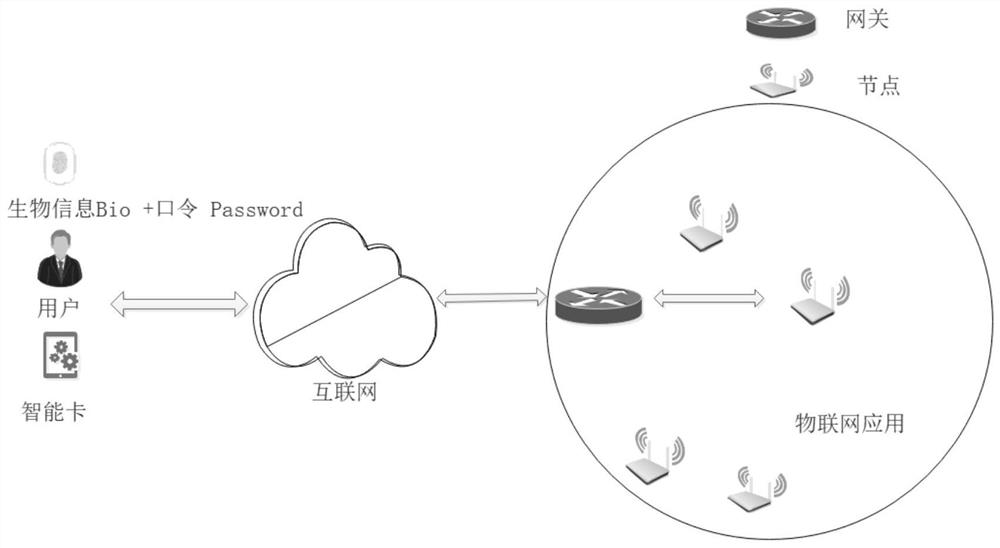
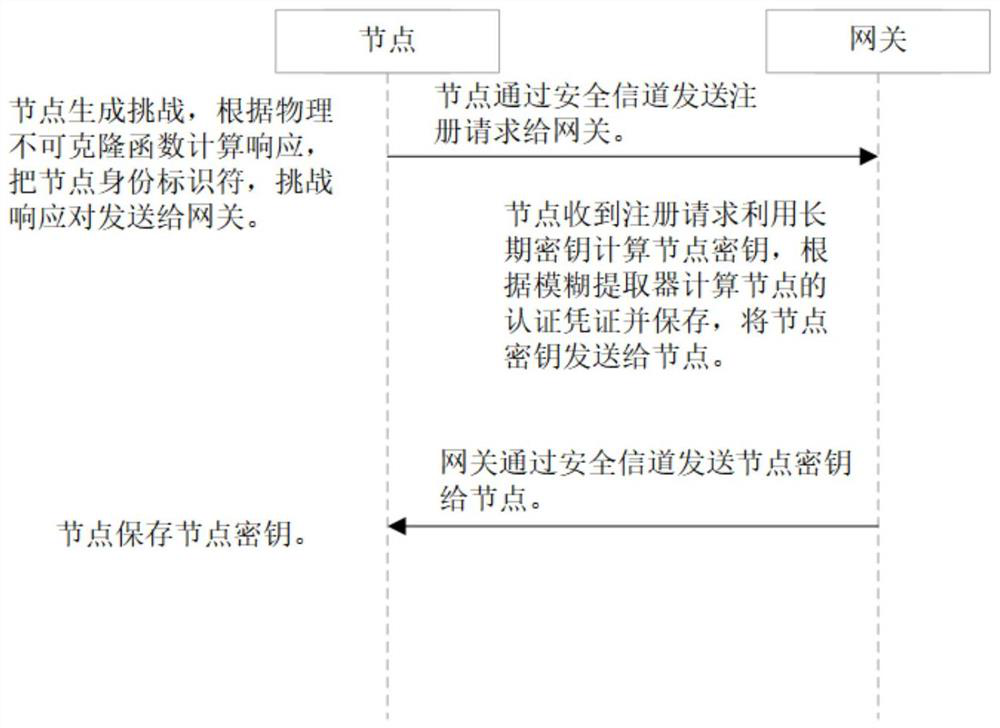
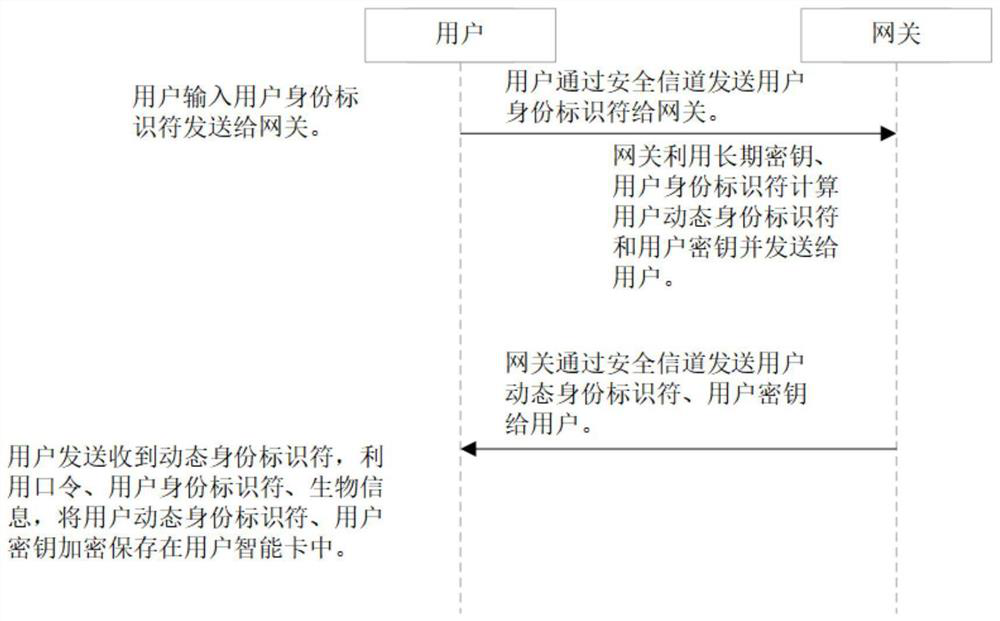
The invention discloses a PUF (Physical Unclonable Function)-based three-factor anonymous user authentication protocol method in the Internet of Things, which solves the security problems such as physical clone attacks and the like, and is implemented by the following steps that: a gateway generates a long-term key for registration and key negotiation of nodes and users; the node sends a PUF-basedchallenge and response to the gateway, and the gateway generates an authentication certificate and sends a node key to the node to complete registration; the user sends the identity identifier to thegateway, the gateway generates a user dynamic identity identifier and a user key and sends the user dynamic identity identifier and the user key to the user, and the user encrypts and stores the userdynamic identity identifier and the user key in the smart card to complete registration; and the user, the gateway and the node perform mutual authentication and key agreement to form a PUF-based three-factor anonymous user authentication protocol method in the Internet of Things. Based on three-factor authentication, smart card loss, password guessing attack and the like can be resisted; the method achieves the anonymity of the user and the node, is small in calculation amount, is high in efficiency, is suitable for IOT nodes with limited resources, and is used for IOT safety communication.
Owner:XIDIAN UNIV
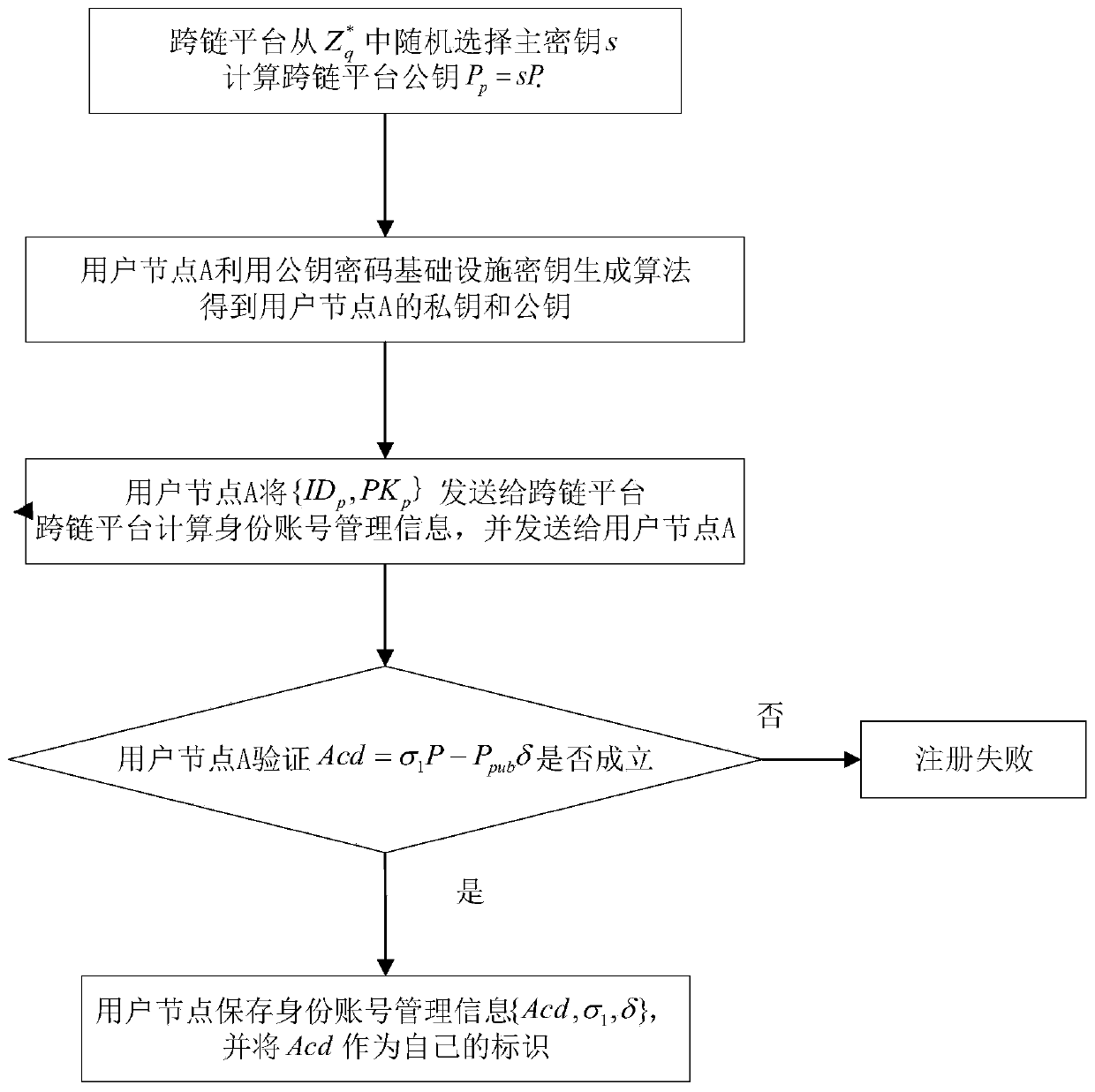
Identity authentication method for heterogeneous blockchain in cross-chain scene
ActiveCN110505058AImprove the efficiency of authentication methodsEnsure safetyKey distribution for secure communicationMultiple keys/algorithms usageComputation complexityProcess efficiency
The invention discloses an identity authentication method for a heterogeneous blockchain in a cross-chain scene. The method comprises the following steps: 1) registering a user node A of a PKI blockchain system with a cross-chain platform; 2) registering a user node B of the CLC block chain system with a cross-chain platform; 3) enabling the user node A of the PKI block chain system to perform system authentication and key negotiation; 4) enabling the CLC block chain system user node B to perform system authentication and key agreement; and 5) enabling the user node A of the PKI block chain system to verify the key. Identity authentication between the block chain systems adopting different public key cryptography systems in the architecture in a cross-chain scene is realized, then the twoheterogeneous block chain systems can communicate safely, and the method has the advantages of high process efficiency, low computation complexity and low communication overhead.
Owner:XIDIAN UNIV
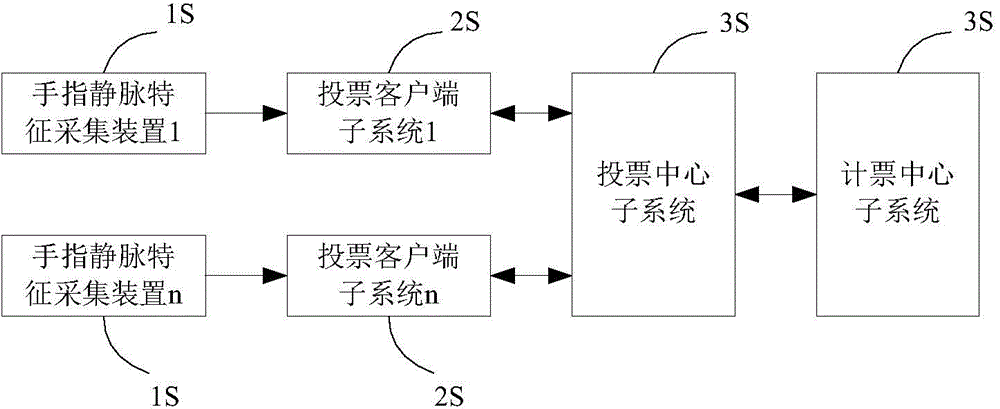
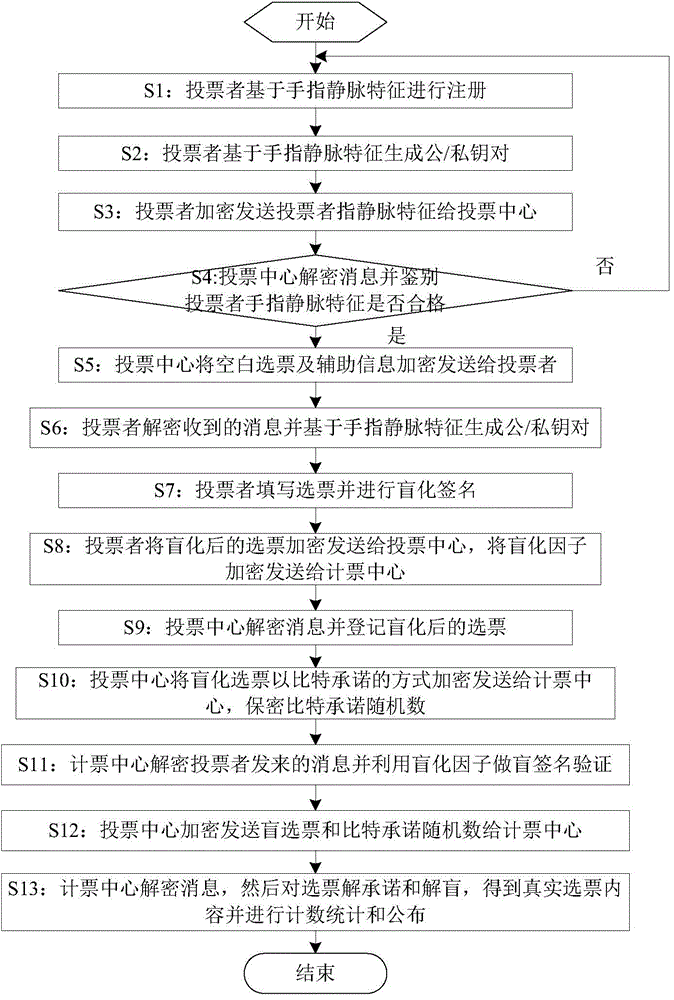
Electronic voting system based on finger vein feature recognition
ActiveCN104392534ASafe Finger Vein AuthenticationImprove ease of useVoting apparatusCharacter and pattern recognitionSystem verificationEngineering
The invention discloses an electronic voting system based on finger vein feature recognition. The system comprises a finger vein feature acquisition device, a voting client sub-system, a voting center sub-system and a vote counting center sub-system. The finger vein image of a voter is acquired by the finger vein feature acquisition device, the voter is registered in the voting center sub-system by the finger vein feature, the legality of the voter is verified by the voting center sub-system, and the vote is issued to the voter if the voter is qualified. A biological characteristic public / private key pair of the voter can be generated by software of the voting client sub-system, and the voting process is realized by the interaction of security protocols such as certificate signing among the voting client sub-system, the voting center sub-system and the vote counting center sub-system. Compared with other electronic voting systems, the system enables a finger vein feature recognition technology to be introduced, and the finger vein feature recognition technology replaces ways such as passwords and digital certificates and takes part in the network identity authentication and the voting process, so that the safety and use convenience of the system are improved; the electronic voting system based on finger vein feature recognition also has anonymity, transparency and openness.
Owner:SOUTHWEST JIAOTONG UNIV
Data safe transmission method in body area network system
ActiveCN103200185AGuaranteed anonymityEnsure safetyKey distribution for secure communicationSecurity arrangementNetwork deploymentBody area network
The invention provides a data safe transmission method in a body area network system. The data safe transmission method in the body area network system comprises the following steps: according to the level structure deploy body area network system, and symmetric keys are prearranged in cluster heads and base stations, and symmetric keys are prearranged in concentrators and the cluster heads; the body area network system is initialized; each concentrator collects data and transmits the data to the cluster heads; and the data are sent to the base stations by the cluster heads, and are decrypted, stored, analyzed and processed through the base stations. The body area network structure is delaminated, simplicity and expansibility of network deploy are improved, and the data safe transmission method is beneficial for network life circles and energy control. The data safe transmission method not only can guarantee data privacy of users, but also can ensure network user context privacy, and prevent corresponding relations between two communication sides from being broken. In addition, information receivers are not limited, and therefore medical workers or relatives of patients can all conveniently and fast search disease information of patient information, the data safe transmission method accords with actual using requirements of a body area network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
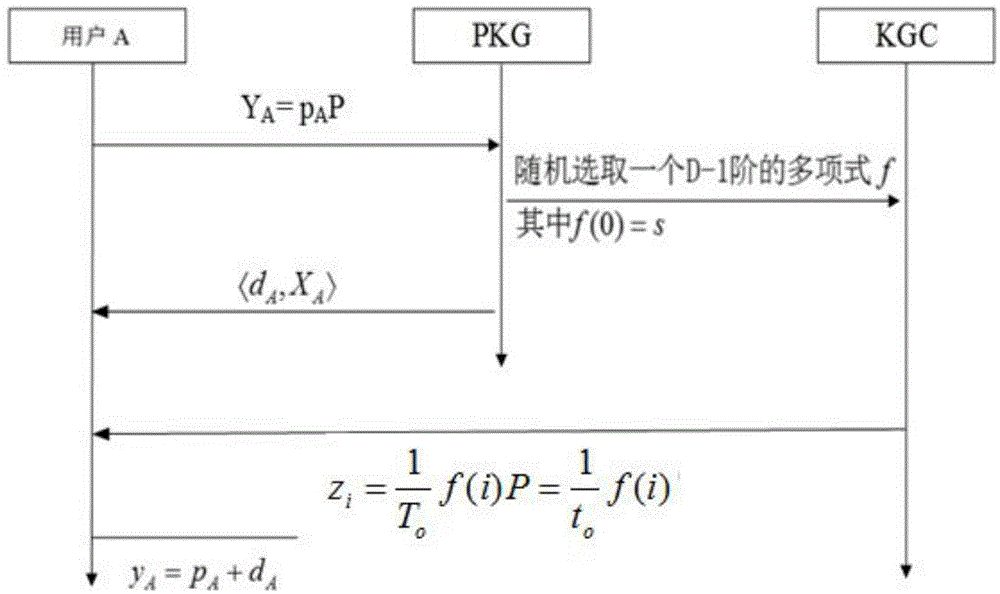
Disposable public key encryption structuring method based on fuzzy identity
InactiveCN104158661APrevent and reveal malicious activityAnonymityKey distribution for secure communicationPublic key for secure communicationUser needsComputerized system
The invention discloses a disposable public key encryption structuring method based on fuzzy identity. According to the method, a computer system is utilized to complete disposable public key anonymous encryption structure based on fuzzy identity and comprises a user A, a user B, a PKG (a public key generation center) and a KGC (a private key generation center), wherein two users need to send and receive messages to / from each other. The method comprises five steps: initialization, user secret key generation, disposable public key generation, encryption and decryption. Compared with the conventional method, the method has anonymity, unforgeability and traceability, and can effectively prevent disposable attack of malicious users and untrusted attack from a trusted center in the system. Meanwhile, compared with the conventional method, the method provided by the invention has relatively high calculation efficiency and relatively low communication expenditure.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
System for providing personalized services
InactiveUS6970067B1Prevent uncontrolled useGuaranteed anonymityTelevision system detailsElectric signal transmission systemsInternet privacyPersonalized medicine
A system comprises an apparatus which is capable of personalizing its behavior in accordance with a user profile, and a gatekeeper device which comprises control means for allowing a user to control said personalization of the apparatus. The gatekeeper device is capable of detecting apparatuses which have personalization capabilities and of notifying the user upon such detection. The user may then decide to establish a relationship with the apparatus, which relationship specifies the extent of personalization which the apparatus is allowed to exhibit and whether confirmation by the user is required at fixture occasions. The user is allowed to change the relationship at any time. The system enables the user to build up anonymous relationships with various apparatuses, providing the user with personalized services while privacy is guaranteed.
Owner:SURFACE ENGINEERED PRODS +2
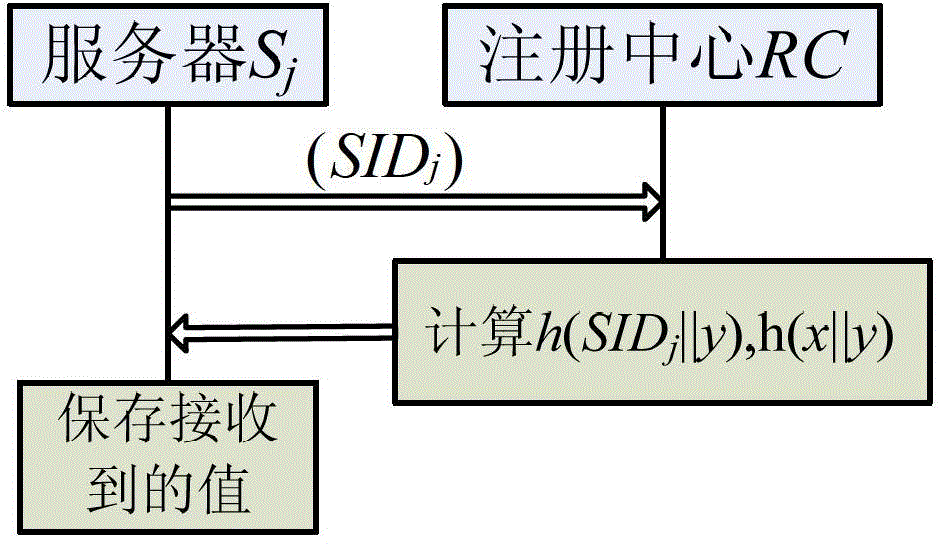
Remote identity authentication method participated in by registration center under multi-sever environment
ActiveCN103338201AGuaranteed anonymityAddress leak attacksUser identity/authority verificationSmart cardAnonymity
The invention discloses a remote identity authentication method participated in by a registration center under a multi-sever environment, which comprises the following steps: a user registration application is submitted to the registration center; a smart card is adopted to log in to a server which is registered in the registration center; the smart card performs local legality verification on a user, if yes, first logging-in requesting information is generated and sent to a server; the server generates second logging-in requesting information and sends the information to the registration center; the registration center performs legality verification on the server and the user identity according to the received second logging-in requesting information, if yes, the registration center generates first authentication information and sends the information to the server; the server performs legality verification on the registration center, if yes, the server sends second authentication information to the smart card; the smart card performs legality verification on the server and the registration center, if yes, the smart card, the server and the registration center jointly generate a session key. The method can prevent anonymity attack and avoid the attack caused by reveal of a verification table.
Owner:SHANDONG UNIV OF SCI & TECH
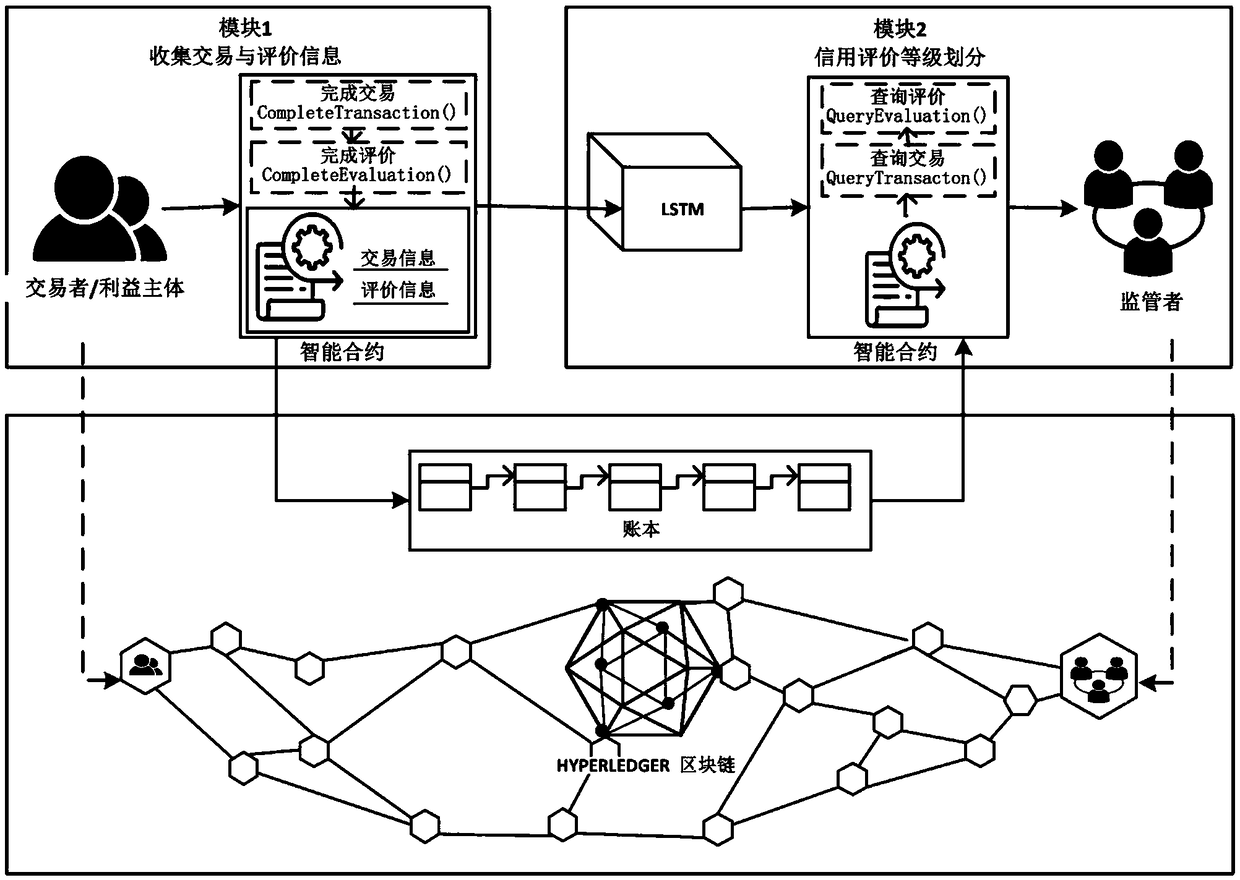
Block chain-based food safety multi-interest subject credit evaluation method
InactiveCN108717606AEasy to supervise and manageReduce regulatory costsResourcesCommerceFood supplySmart contract
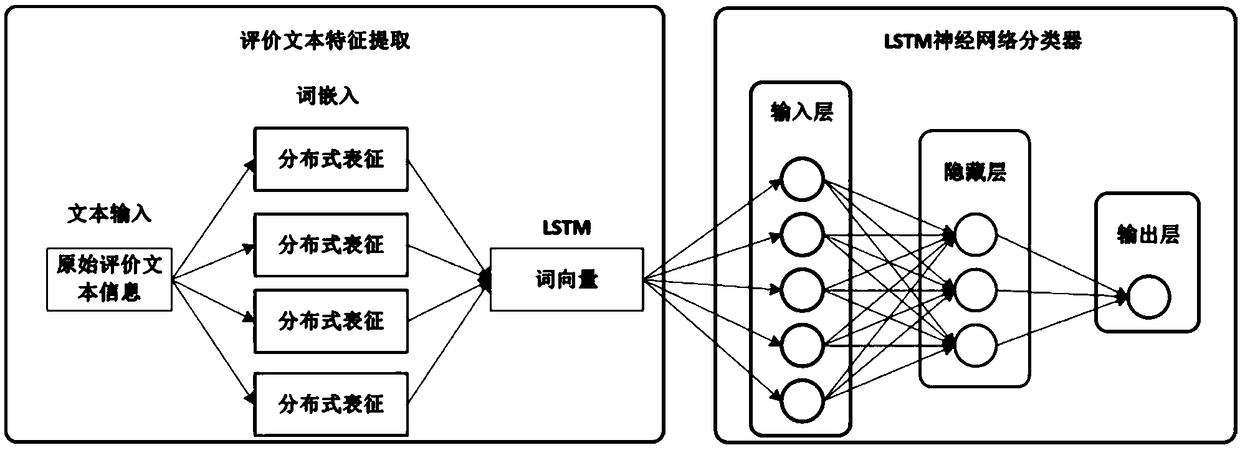
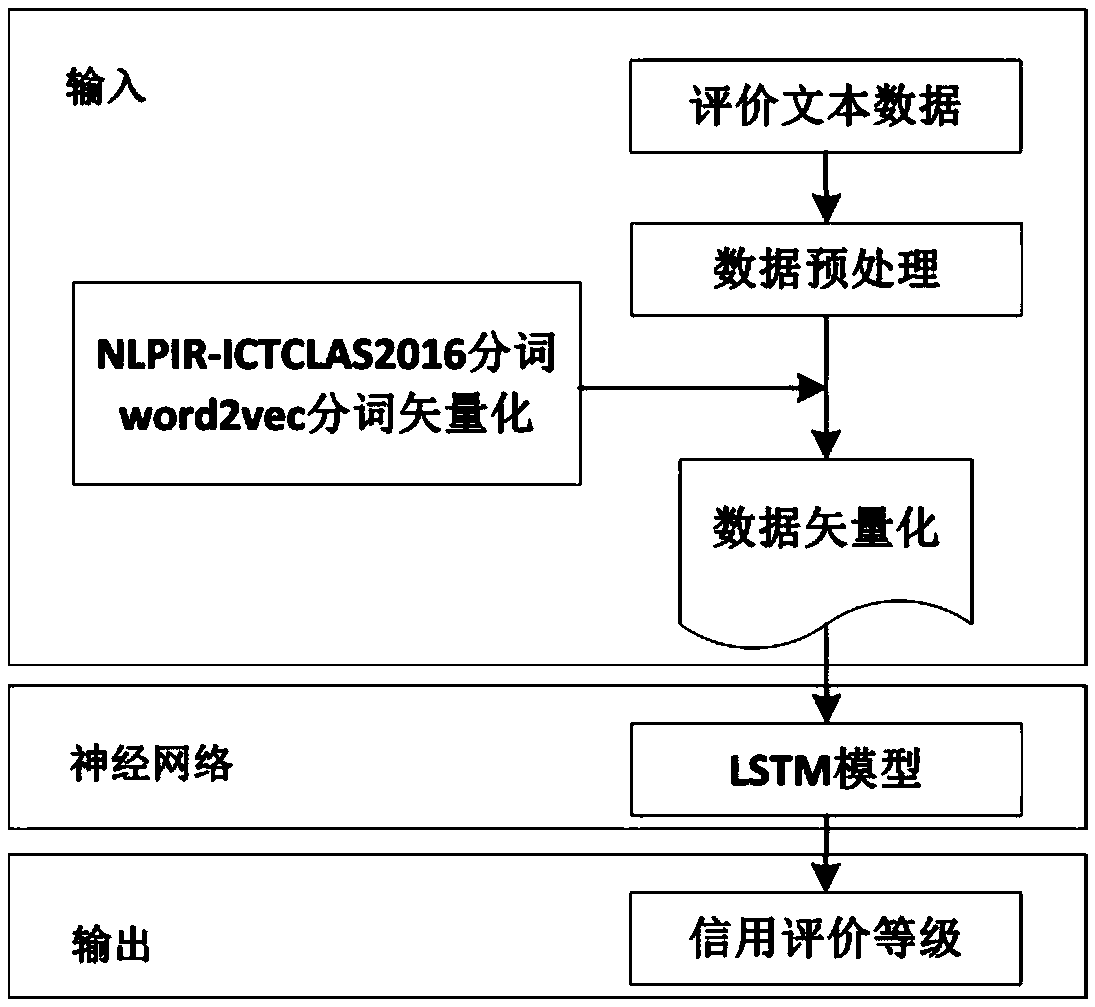
The invention provides a block chain-based good safety multi-interest subject credit evaluation method. According to the method, a Hyperledger block chain is taken as a bottom support technology of the credit evaluation method, multi-interest subjects (traders) on food supply chains and supervisors are endowed with different identity authorities, and the traders are endowed with identity anonymityand evaluation result publicity and transparency during the evaluation; and the supervisors collect evaluation information, for transactions, of the multi-interest subjects on the food supply chainsthrough intelligent contracts, carry emotion analysis on the fed back evaluation information by adoption of a deep learning algorithm long and short term memory (LSTM) model, and feed credit evaluation results back to both parties of the transactions. According to the method, the efficiency and correctness of traditional credit evaluation systems are improved and the effectiveness of food safety supervision is enhanced.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
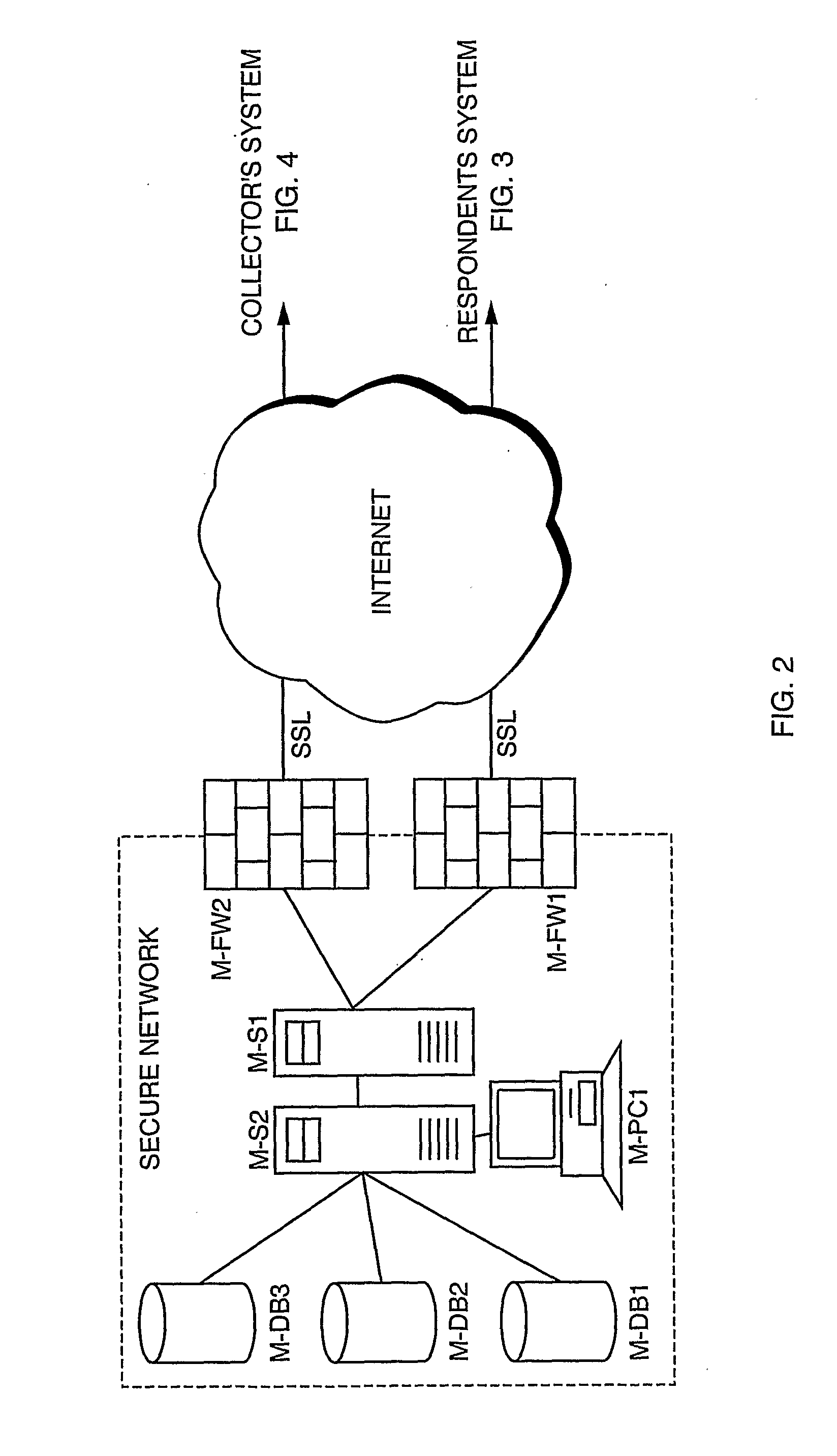
Transmission of Anonymous Information Through a Communication Network
InactiveUS20080294559A1Guaranteed anonymityComputer security arrangementsTransmissionCollections dataAnonymity
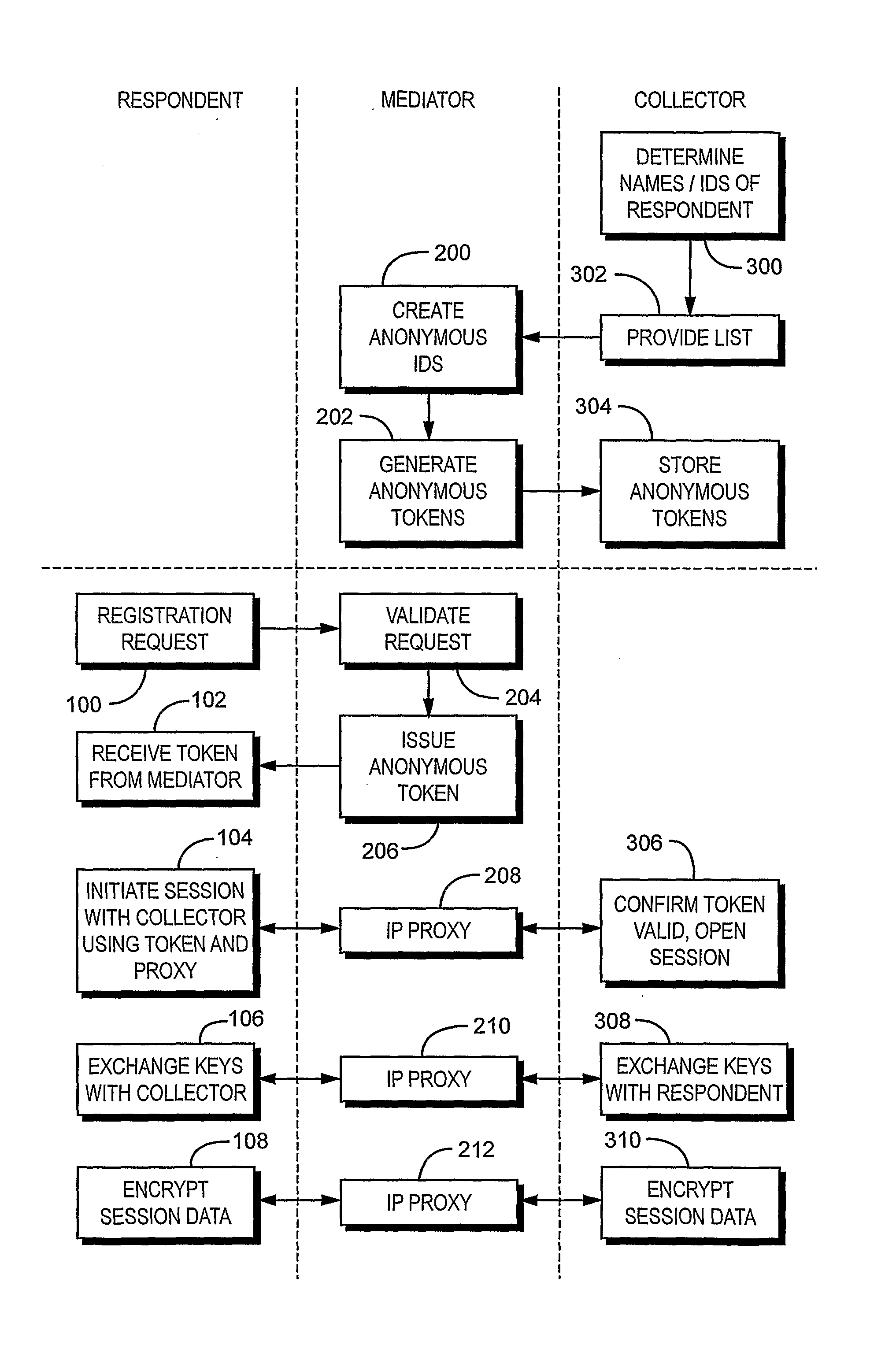
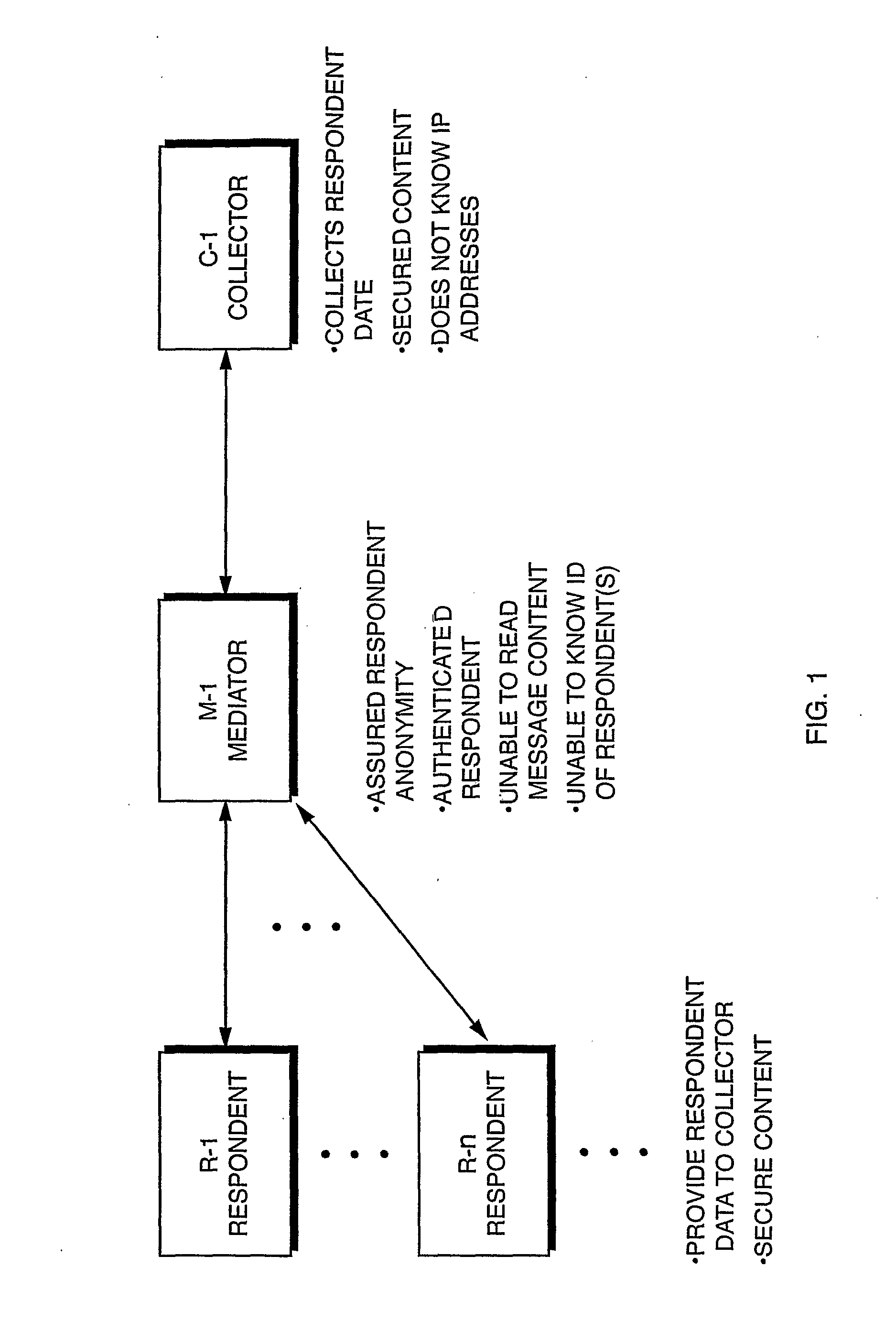
A system that enables anonymous data collection from Respondents, such as over the Internet using public key technologies, where the anonymity and authenticity of Respondents is provided by a trusted mediation service. The invention provides a simple and secure solution that allows authentication of research Respondents while maintaining their anonymity. The Collector cannot link Respondent's real identification and their responses, and a Mediator provides a communication service but has no access to the content of information exchanged between the Respondents and the Collector. According to one aspect of the invention, a Collector requests a list of anonymous Ids from the Mediator. The Mediator then generates a list of anonymous tokens which can then be used by the Respondents when they communicate with the Collector through the Mediator.
Owner:GENACTIS
Sensor network distributed access control method capable of protecting user privacy
InactiveCN102088462ADefend against compromise attacksGuaranteed anonymityNetwork topologiesTransmissionUser privacyRing signature
The invention discloses a sensor network distributed access control method capable of protecting user privacy. The method comprises the following steps: broadcasting a pre-established group access list pool to all of the network users by a network owner, and loading the group access list pool in all of sensor nodes; generating request information and ring signature information by a network user when the network user proposes an access requirement, transmitting the request information and the ring signature information to a sensor node to be accessed, wherein the request information includes a user random number; after the sensor node to be accessed receives the request information and the ring signature information, checking the request information according to the group access list pool to determine whether the request information is valid; refusing the request information if the request information is invalid; and determining whether the ring signature information is correct by the sensor node if the request information is valid, if correct, transmitting the data requested by the network user to the network user via the sensor node, otherwise, refusing the request information.
Owner:ZHEJIANG UNIV
Attribute-based anonymous authentication method and system thereof
InactiveCN104125199AFlexible Threshold Attribute Selective Presentation SchemeImprove communication efficiencyTransmissionInternet privacyService provision
The invention discloses an attribute-based anonymous authentication method which contains the following steps: 1) a trusted party TP generates a master key x and system public parameters according to set safety parameters; 2) a user U registers with the TP to submit attributes and initiates an attribute certificate issue request; 3) the TP verifies the attributes of the user U and issues an attribute certificate for the user U according to the attributes of the U, the master key x and the system public parameters; 4) the user U initiates an access request to a service provider SP; 5) the SP looks up an access strategy corresponding to the access request and returns the access strategy to the user U; 6) the user U selects an attributes that the U wants to use according to the access strategy, and an anonymous certificate is calculated by the use of the attribute certificate and a private key r and is sent to the SP; and 7) the SP verifies the anonymous certificate, and accepts the access request and provides corresponding service to the user if verification is passed and the access strategy is satisfied. According to the invention, privacy of a user is guaranteed, and a more flexible threshold attribute selective showing scheme is supported.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI +1
Privacy protection access control method in wireless sensor network supported by IP
ActiveCN109963282AGuaranteed unlinkabilityFlexible revocation processNetwork topologiesSecurity arrangementWireless mesh networkPrivacy protection
The invention discloses a privacy protection access control method in a wireless sensor network supported by an IP. According to the method, a group signature technology is applied, system users are divided into different user groups according to different access authorities, the group users use group signatures for anonymous access to guarantee user data access privacy, and leakage of user behavior modes is prevented. According to the method, users are divided into different user groups according to different access authorities by utilizing a group signature technology, the group users generate group signatures for identity authentication, and anyone in a network can verify the correctness of the group signatures but cannot know the identities of the signers; the identity authentication and authorization process of the Hidra protocol is improved by utilizing a false ticket mechanism and a self-updating ticket mechanism, so that the unlinkability of a protocol message is ensured; the block chain technology is used for managing the group public key, so that the secret key management and Hidra protocol user revocation process is more flexible; a responsibility investigation mechanismis improved by utilizing a block chain technology, so that the responsibility investigation process is public and transparent, and possible responsibility investigation disputes are solved.
Owner:SOUTH CHINA UNIV OF TECH
Communication method, device and system
InactiveCN101471772AProtect transmission securityGuaranteed anonymityKey distribution for secure communicationPublic key for secure communicationData informationAnonymity
The embodiment of the invention discloses a communication method, which comprises the steps as follows: data information is received, wherein, the data information is the information that is encrypted by utilizing a public key of a destination node; whether an identity parameter of the destination node carried by the data information is identical with the identity parameter of a present node; and the data information is decrypted by utilizing a private key of the present node if the identity parameter of the destination node is identical with the identity parameter of the present node. By the embodiment of the invention, the sent data information is encrypted by utilizing the public key of the destination node, and the received data information is decrypted by utilizing the private key of the destination node after the destination node receives the encrypted data information, thereby ensuring the anonymity of both communication sides on a transferring node, and protecting the transmission security of the data information.
Owner:HUAWEI TECH CO LTD
Location privacy protection method based on dynamic pseudonym exchange area
InactiveCN109561383AImprove privacy protectionGuaranteed anonymityParticular environment based servicesVehicle wireless communication serviceDiffie–Hellman key exchangeThe Internet
The invention discloses a location privacy protection method based on a dynamic pseudonym exchange area, and belongs to the field of location privacy protection of the Internet of vehicles. The methodcomprises the steps that a vehicle in the vehicular ad hoc network registers and generates a dynamic pseudonym in the driving process and periodically updates the pseudonym, then the vehicle dynamically establishes a pseudonym exchange area, carries out pseudonym exchange to enhance the location privacy, embeds an improved Diffie-Hellman key exchange protocol in the pseudonym exchange process atthe same time to protect the pseudonym exchange process, the vehicle initiating the pseudonym exchange uploads a pseudonym exchange log to a certification authority (CA) of the area after the completion of the pseudonym exchange, the CA re-establishes the relationship between a real ID and the pseudonym of the vehicle through analyzing the pseudonym exchange log so as to enable the CA to perform identity tracking and violation processing. The location privacy protection method solves a problem of location privacy of the vehicle in the driving process, and is an effective location privacy protection method which adapts to the communication environment of the Internet of vehicles and can claim the responsibility of violation vehicles.
Owner:KUNMING UNIV OF SCI & TECH
Credible inter-domain rapid authentication method on basis of separation mechanism network
InactiveCN102355663AImpossible to decryptImpossible to tamper withSecurity arrangementAnonymityInter-domain
The invention relates to a credible inter-domain rapid authentication method on the basis of a separation mechanism network for solving the problem of rapid authentication when a terminal in the separation mechanism network is subjected to inter-domain switching. In the method, a novel protocol is provided for realizing the rapid authentication when the terminal is subjected to inter-domain switching; and when the identity of a user is authenticated, the identity authentication of a terminal platform and the integrity check of the terminal platform are realized. In the method, when the terminal is subjected to inter-domain switching, an authentication center of a home domain does not need to participate again and an authentication center of a local domain can authenticate the mobile terminal by a Ticket. The method can resist the anti-replay attack, so that the credibility, safety, anonymity, anonymity of the identity of the user and untraceability of the identity of the user of the platform are ensured.
Owner:BEIJING JIAOTONG UNIV
Supervisable anonymous authentication method based on zero knowledge proof
ActiveCN109450645AGuaranteed anonymityProtect identity privacyKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationIdentity privacy
The invention discloses a supervisable anonymous authentication method based on zero knowledge proof, comprising three types of participants: a CA, a user and a verifier, wherein the CA generates an issuer key pair and a group key, the CA allocates a pair of private keys to the user during registration of the user, and meanwhile the CA issues a relevant certificate to the user according to the attribute information submitted by the user; when the user presents the certificate, the verifier specifies an attribute that needs to be presented on the certificate of the user, and the user signs thecertificate and hides attribute values that do not need to be presented; and the verifier verifies the signature, if the signature passes the verification, the certificate presented by the user is valid, or otherwise, the certificate presented by the user is invalid. By adoption of the supervisable anonymous authentication method disclosed by the invention, the anonymity of the user is also ensured while increasing a mandatory supervision function, thereby greatly improving the identity privacy of the user compared with the general identity supervision scheme. By adoption of the supervisable anonymous authentication method disclosed by the invention, a supervisable function is also added.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
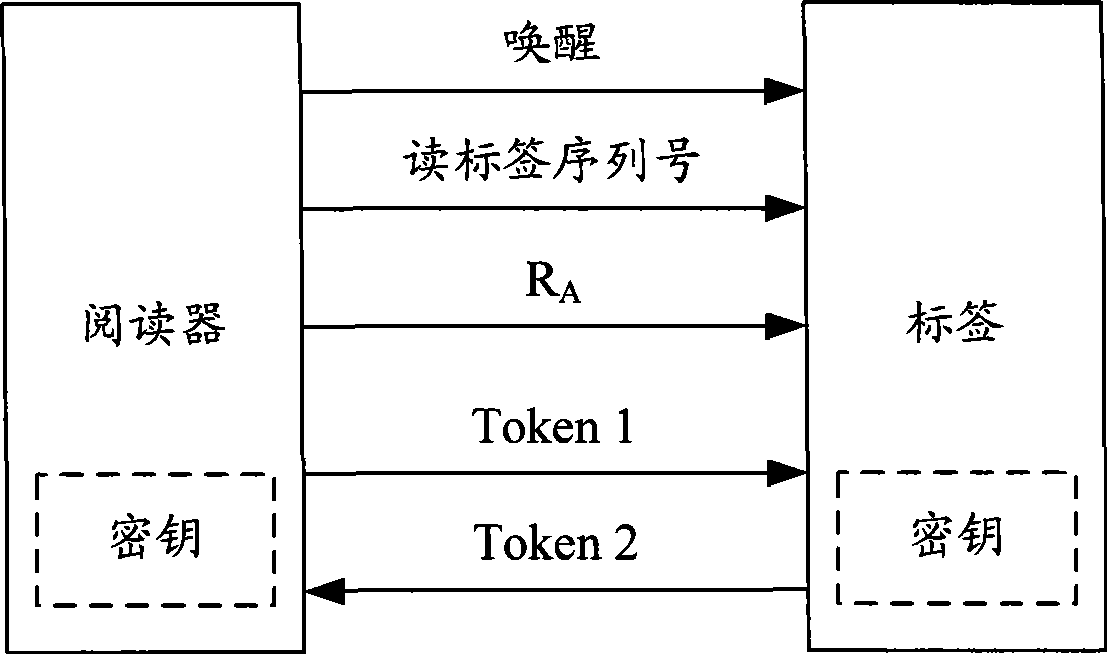
Method, system and device for authenticating radio frequency tag
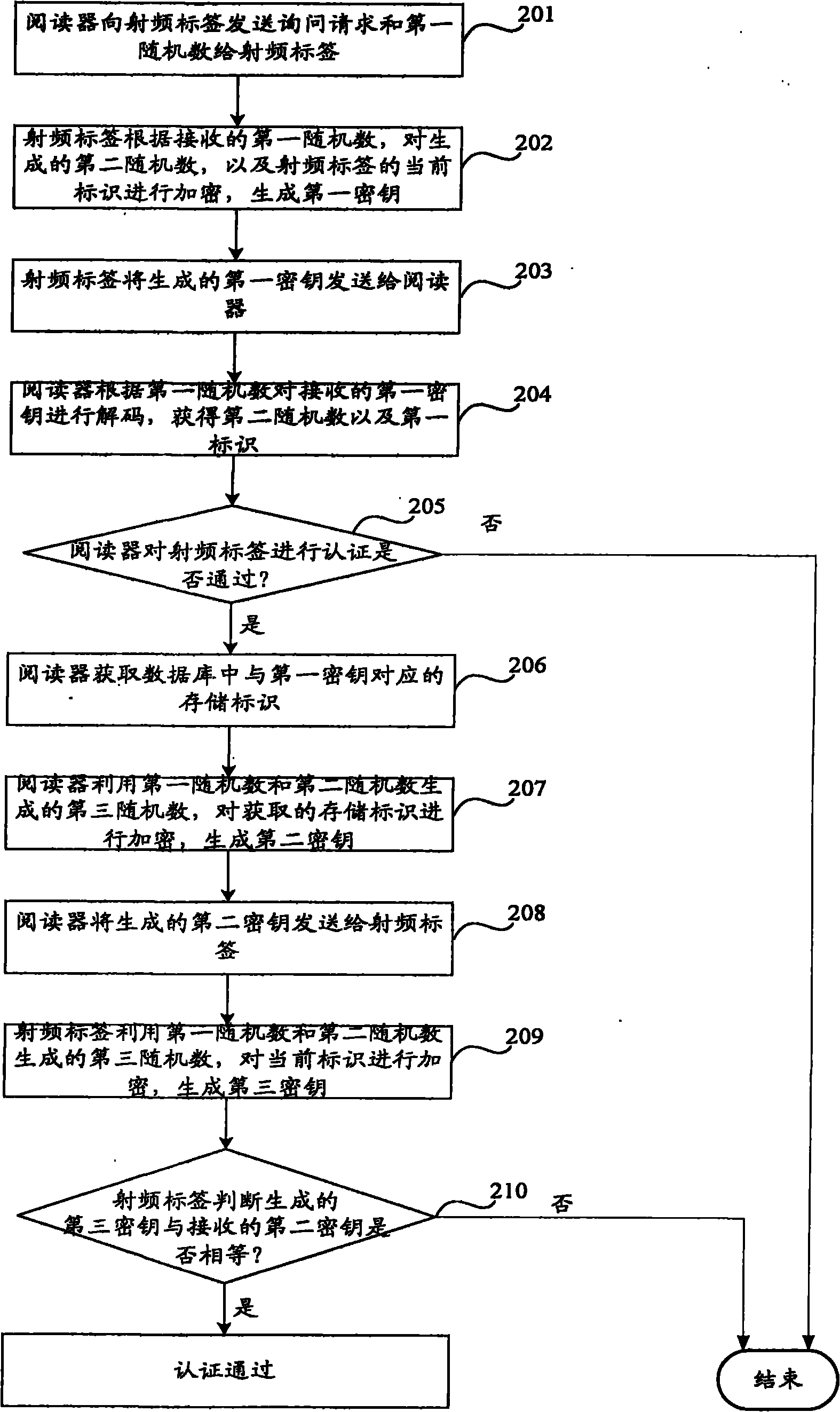
ActiveCN101980241AGuaranteed anonymityPrivacy protectionSensing record carriersRecord carriers used with machinesRadio frequencyRandom number generation
The invention discloses a method for authenticating a radio frequency tag. The method comprises the following steps that: the radio frequency tag receives a query request transmitted by a reader and a first random number generated by the reader; the radio frequency tag encrypts a generated second random number and a current identifier of the radio frequency tag according to the received first random number so as to generate a first key and transmit the first key to the reader; the radio frequency tag receives a second key returned by the reader, wherein the second key is generated by obtaining the second random number and a corresponding memory identifier by passing the authentication of the first key by the reader and encrypting the memory identifier by utilizing a third random number generated by the first random number and the second random number; and the radio frequency tag encrypts the current identifier by utilizing the third random number generated by the first random number and the second random number so as to generate a third key and confirms that the authentication of the reader is passed when the third key is equal to the received second key.
Owner:BEIJING WATCH DATA SYST
Safe and reliable communication method based on group authentication in smart home environment
ActiveCN111092717AGuaranteed anonymityRealize privacy protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHome environmentIntelligent equipment
The invention discloses a safe and reliable communication method based on group authentication in a smart home environment. An authentication process is divided into three stages, in the equipment initialization and registration stage, newly added gateway equipment initialization work and registration work of a group of smart home equipment are completed, in the authentication and key negotiationstage, mutual identity authentication of the gateway and the same group of smart equipment is completed, and a session key is generated between each piece of smart equipment and the gateway and used for encrypting and decrypting transmission data. According to the method provided by the invention, simultaneous identity authentication of a group of intelligent equipment can be realized, and the overhead of computing resources is reduced by utilizing operations with relatively low overhead, such as hash operation, linear polynomial calculation, number addition calculation and exclusive-OR operation.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Authentication method and apparatus for wireless radio frequency recognition system
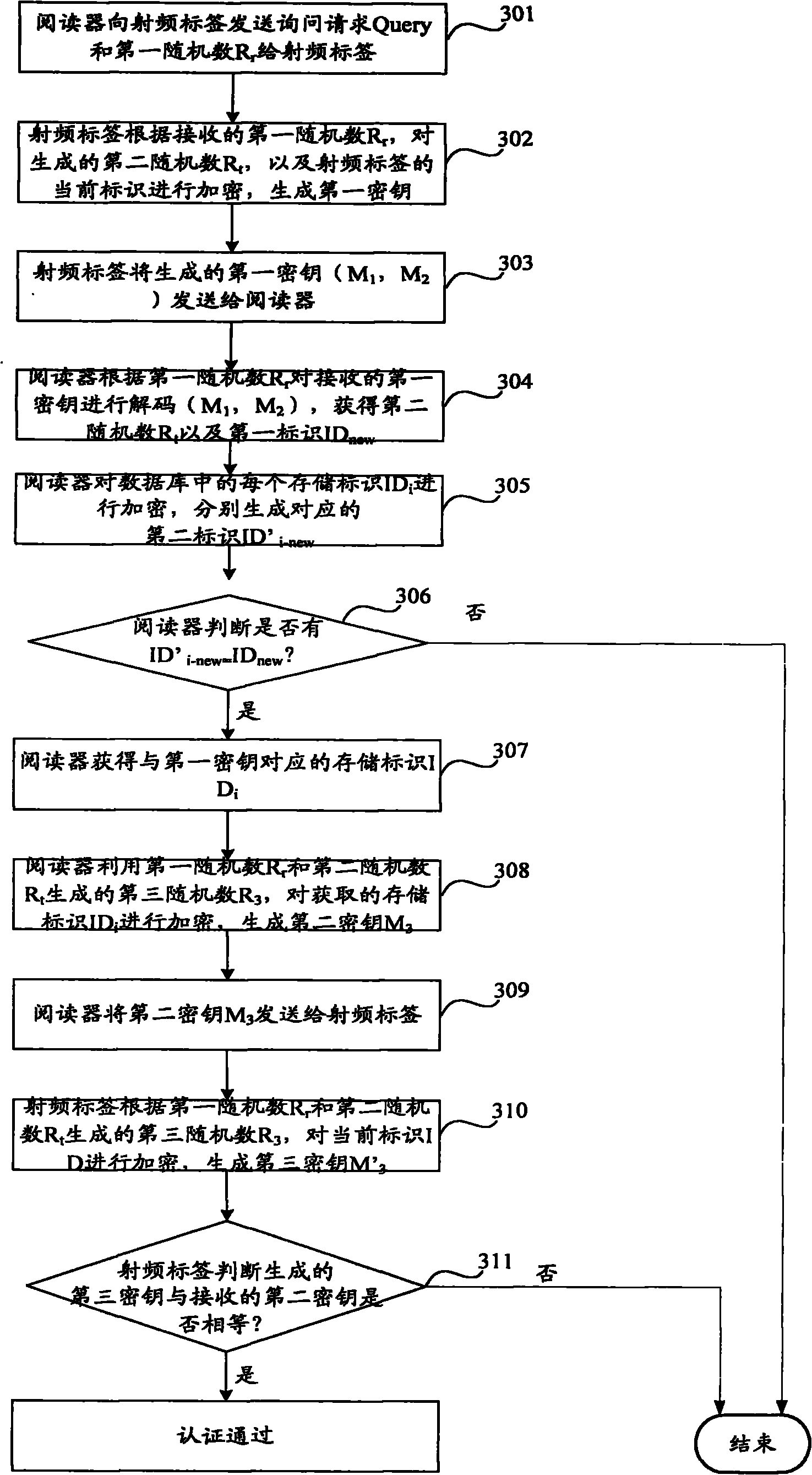
InactiveCN101488179AGuaranteed anonymitySolve the problem of data update out of syncCo-operative working arrangementsSensing record carriersRadio frequencyAir interface
The embodiment of the invention discloses an authentication method for a wireless radio frequency identification (RFID) system. Anonymity of a tag is ensured by updating ID in each authentication; and an (ID, P-key) pair of the tag is stored in a reader party, and only the (ID, P-key) part in the reader party, which is inconsistent with the content transmitted by the tag, is updated by the reader party, such that synchronicity of data update can be ensured. The embodiment of the invention also discloses an authentication device for the wireless radio frequency identification (RFID) system. By adopting the embodiment of the invention and by ensuring the anonymity of the tag through ID update, the asynchronism of data update easily caused by the adoption of an ID updating mechanism in a common RFID air interface protocol can be simultaneously solved.
Owner:HUAWEI TECH CO LTD
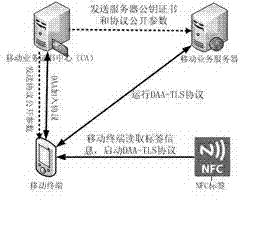
Method to protect communication security and privacy function of mobile client
InactiveCN102761556AGuaranteed anonymityGuaranteed confidentialityKey distribution for secure communicationUser identity/authority verificationCommunications securityEngineering
The invention relates to a method to protect a communication security and privacy function of a mobile client. The method comprises the following steps: combining a direct anonymous authentication (DAA) protocol and a transport layer security (TLS) protocol, and utilizing the identity privacy of a DAA protocol protection client with an NFC (Near Field Communication) function, as well as the privacy between the TLS protocol protection client and a server; reading the service website information and a website connecting with the server by the client with the NFC function, realizing the protection for the client identity privacy and the communication privacy through operating a modified TLS protocol between the client and the server; adopting an ellipse curve cryptography to realize the DAA protocol, wherein the client with a DAA certificate can complete the signature; and combining the DAA protocol and the TLS protocol so as to uniformly realize the anonymity and privacy of the communication between the mobile client and the server.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Digital currency tracking method based on monero
PendingCN110009318ATransaction SupervisionGuaranteed anonymityPayment circuitsProtocol authorisationDigital currencyFinancial transaction
The invention relates to a digital currency tracking method based on monero, and the method comprises the following steps: carrying out initialization on a system, generating system parameters, and generating a secret key for tracking authority; a user generating a transaction order, a payer generating a primary public key for a payee, and embedding into a long-term public key tracking tag; the payer performing mintage for a payment account; the payer pulling in a group of mixed accounts to hide a real payment account; generating a primary public key tracking tag; and completing the transaction order, and signing the transaction order; broadcasting the transaction order to a P2P network; a miner generating a block, collecting the transaction order in the P2P network, verifying the validity of the collected transaction order, using the valid transaction order to mine, generating a new block, and broadcasting the block; a tracking authority tracking a malicious payer, and tracking the primary public key and the long-term public key of the malicious payer when discovering the malicious payer so as to cancel the anonymity of the malicious payer and generate evidences to prove the correctness of the tracking result.
Owner:SHAANXI NORMAL UNIV
Anonymous subscription agreement and system thereof
ActiveCN105847008AProtection of rights and interestsReduce storageUser identity/authority verificationExpiration TimeDecorrelation
The invention provides an anonymous subscription agreement and a system thereof. The anonymous subscription agreement comprises the following steps: 1. a server generates a series of main system parameters, such as a login cycle and public and private key information thereof; 2. a user interacts with the server and executes a registration process, and in the process, the user provides a subscription interval time and pays a corresponding fee to obtain a valid signature from a service provider; 3. the user logs in by using the signature, logs in according to a fixed login cycle at a login stage, carries out a blind operation on the signature to generate a token of the current login cycle for login, carries out the next cycle after the login cycle is terminated, and changes the token to log in; 4. the anonymous agreement provides a connection operation, and the user can select to execute the connection operation when no decorrelation is required; and 5. when the user does not want to access the service, the user can execute a logout operation; and moreover, in the login and connection stages, inspection on the expiration time is contained, and if the subscription time interval is overdue, the user cannot log in anymore, so the benefits of the service provider are guaranteed.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Cloud server storage integrity detection method and system
InactiveCN106790311AEnhanced anonymityRealize quantitative storageTransmissionAnonymityOperating system
The invention provides a cloud server storage integrity detection method and a detection system with high efficiency and capability of supporting data delete and user identity anonymity. Compared with a traditional cloud server, the cloud server supporting data delete provided by the invention can know identities of different users owning the same file, so that the cloud server can infer the attribution of the encrypted file according to the identities of the users. An authenticator required for auditing and generated by the user does not contain any information of the user identity. In addition, when the user downloads the file, the user only needs to send a legal certificate to the cloud server without the need for any identity information. In the whole scheme, the cloud server does not know any information of the user identities. In the method, the quantitative storage of the cloud server is realized.
Owner:QINGDAO UNIV
Ring signature generation method based on SM9 digital signature algorithm
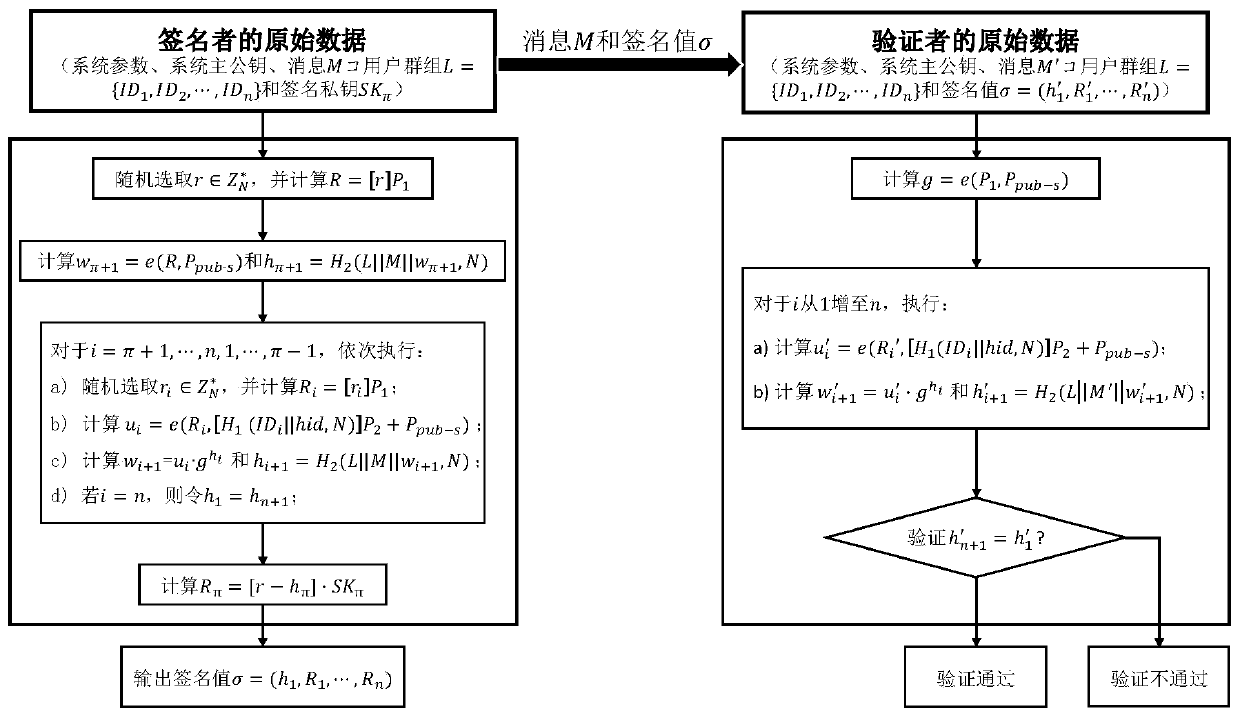
ActiveCN110912708AEasy to implementImprove securityUser identity/authority verificationRing signatureAnonymity
The invention discloses a ring signature generation method based on an SM9 digital signature algorithm, which is characterized by comprising a key generation center KGC, a signer and a Verifier, wherein the KGC is responsible for generating a user private key of a signed user in the system; setting the number of users in the ring to be n, marking the user group identifier set as L={ID1, ID2,..., IDn}, and the signer being the pi-th user in the user group, the private key of which is SKpi and the identifier of which is IDpi. The method comprises the following steps of (1) generating a ring signature of a to-be-signed message M, and (2) verifying the ring signature. In the process of generating the signature, a signer can spontaneously construct a user group to form a ring, the ring signature can be generated without the participation of other users, and meanwhile, the non-repudiation of the signature and the anonymity of the identity of the signer are ensured.
Owner:WUHAN UNIV
Multi-receiver signcryption method based on multiple variables and multiple security properties
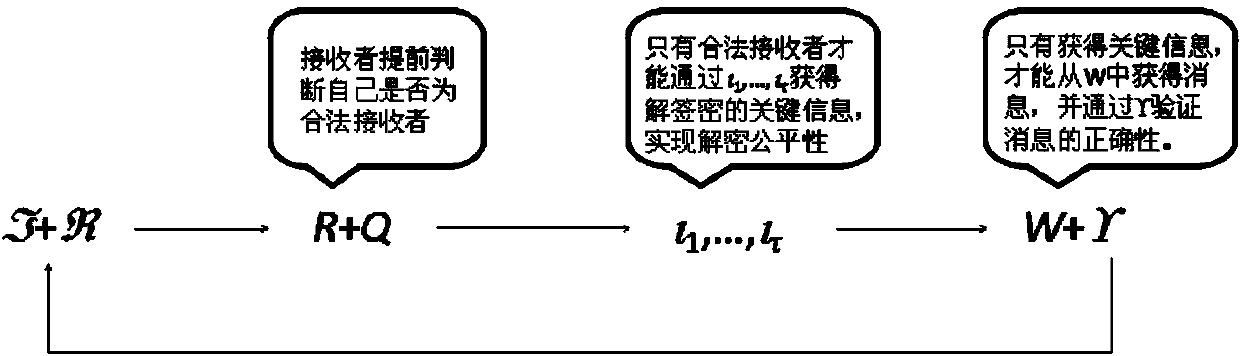
ActiveCN104539425AGuaranteed anonymityGuarantee the fairness of decryption signcryptionUser identity/authority verificationAlgorithmSigncryption
The invention discloses a multi-receiver signcryption method based on multiple variables and multiple security properties. The method is used for solving the technical problem that an existing multi-receiver signcryption method is poor in designcryption justice. According to the technical scheme, an algorithm KeyGen, a signcryption algorithm Signcrypt and a designcryption algorithm Designcrypt which are used for generating system parameters and secret key pairs of all users are involved in the method. The signcryption algorithm is based on a finite domain F with a characteristic q, totally N+tau participants are involved in a system, a leader L is selected from actual signcryption persons and calculates interference data, the interference data and real data are mixed together, so receivers can not judge the identities of the actual signcryption persons. By means of the threshold technology, the anonymity of senders is ensured; the identity list of the receivers is not directly given any more in communication data, and the anonymity and early judgment of the receivers are ensured; key information of designcryption and information of the authorized receivers are fused into a parameter list, and the designcryption justice is ensured.
Owner:东莞三航安视睿信息技术有限公司
System for identifying personal item, such as item of clothing, accessory or portable device
InactiveCN1384955AGuaranteed anonymityMemory record carrier reading problemsCo-operative working arrangementsComputer hardwareWeb site
The invention discloses a system in which an identification tag (2) is installed on personal items (3) such as clothing, accessories or portable devices, and the tag (2) has a storage device (11) for recording the assigned The personal code on the tag (2) and the transmitting device (12) are used to transmit a signal representing the personal code; the portable detection device (4) has a starting device (16) for starting the transmitting device (12) and The tag (2) sends a query signal and accordingly receives a signal representing the personal code and transmitted by the transmitting device (12) of the tag (2); making it possible to use the detected personal code as an e-mail address located on a dedicated Internet website Contact the owner of the tag (2), thus realizing a direct and effective way to establish interpersonal relationships between strangers while ensuring their anonymity.
Owner:保罗·博伦吉
VANETs anonymous authentication system and method based on ID-based group signature
ActiveCN109362062AImprove the strength of privacy protectionGuaranteed anonymityParticular environment based servicesVehicle-to-vehicle communicationThird partyPrivacy protection
The invention provides a VANETs anonymous authentication system based on an ID-based group signature, related to the technical field of wireless network security. The VANETs anonymous authentication system based on the ID-based group signature comprises a third-party trust institution, roadside units and vehicle units; and the third-party trust institution communicates with the vehicle units through the roadside units. The invention also provides a method for anonymous authentication using the VANETs anonymous authentication system based on the ID-based group signature; after the third-party trust institution generates an initial pseudonym, an initial trust value and a signature private key for the vehicle units, and generates a signature private key, a group private key and a group publickey for the roadside units, a V2I authentication protocol is performed between the vehicle unit and the roadside unit, and a V2V authentication protocol is performed among the vehicle units, and a shared key is generated when both are legal; and finally, the roadside units assist the third-party trust institution to track a true identity of the vehicle unit sending a malicious message and performfurther processing. The invention can ensure the anonymity of the vehicle node identity, avoid the certificate storage and management overhead, and improve the privacy protection strength and the authentication efficiency.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com