Method, system and device for authenticating radio frequency tag
A radio frequency tag and key authentication technology, applied in the field of information security, can solve the problems of difficult implementation of Hash function, low security level, processing power, and storage space, etc., to ensure anonymity, privacy protection, and improve the security level. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
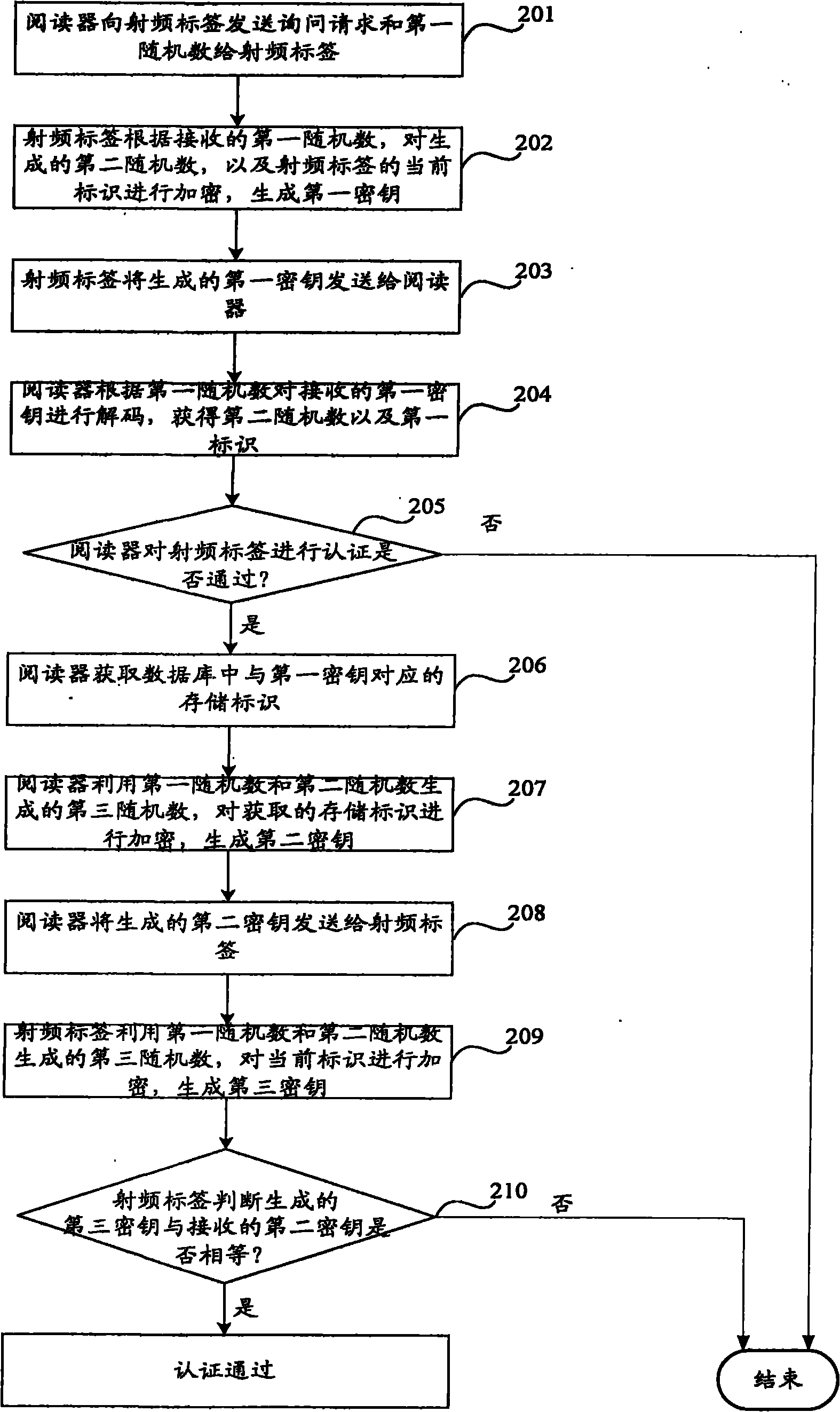
[0097] Embodiment 1. In this embodiment, the database of the reader has the storage identification ID of each radio frequency tag i (Among them, i=1, 2, 3----n), Query is a query request; R r Is the first random number generated by the reader, R t Is the second random number generated by the radio frequency tag; ID is the current identification of the radio frequency tag; CRC is the cyclic check function; Is the exclusive OR operator, || is the string associative, ∮ is the string concatenation, and f is the algorithm identifier.
[0098] See image 3 , The process of radio frequency label certification includes:
[0099] Step 301: The reader sends a query request Query and the first random number R to the radio frequency tag r Give the radio frequency tag.
[0100] Step 302: The radio frequency tag according to the received first random number R r , For the second random number R t , And the current identification of the radio frequency tag are encrypted to generate the first key.
[...
Embodiment 2
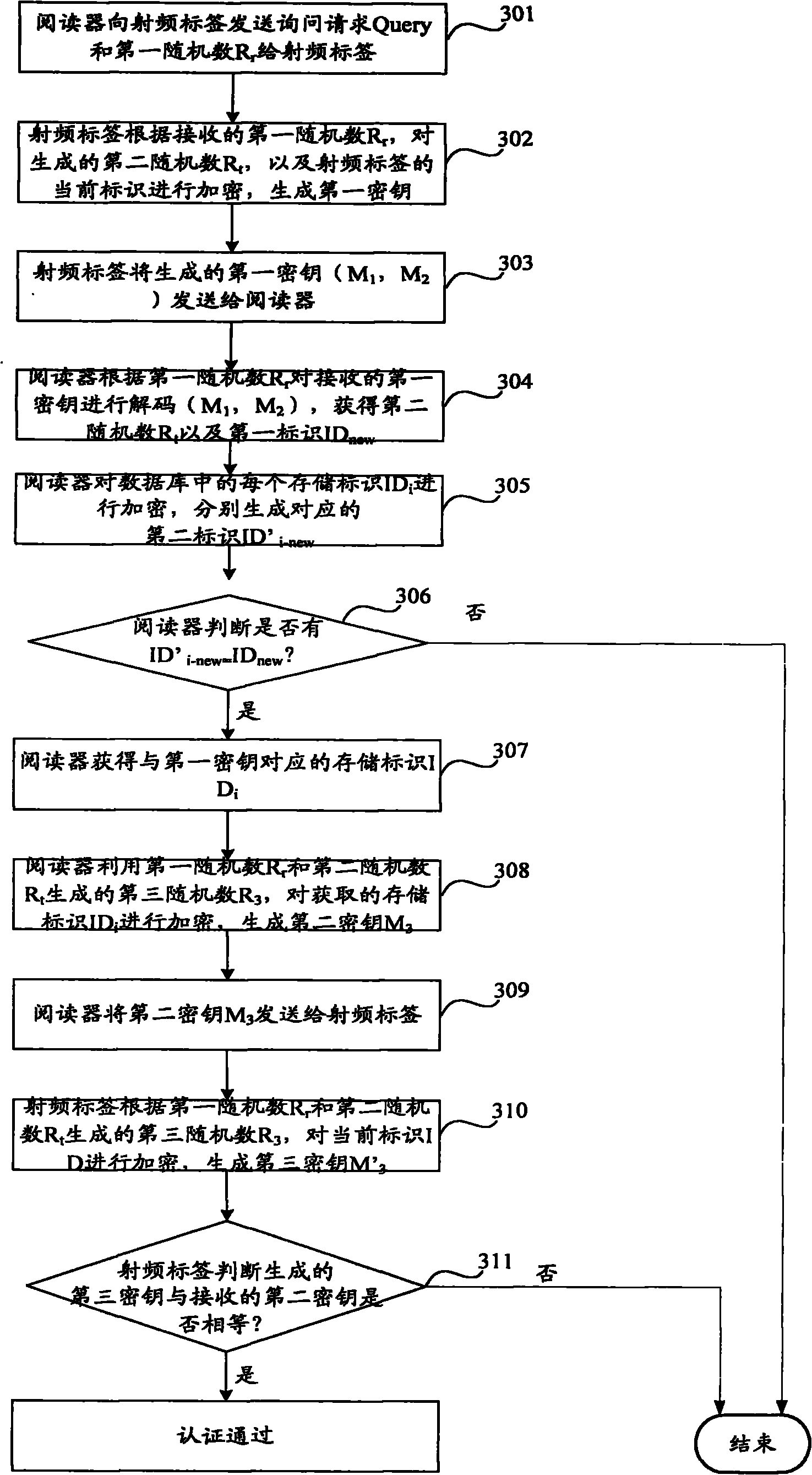
[0131] Embodiment 2. In this embodiment, the database of the reader has the storage identification ID of each radio frequency tag i (Among them, i=1, 2, 3----n), Query is a query request; R r Is the first random number generated by the reader, R t Is the second random number generated by the radio frequency tag; R u Is the fourth random number generated by the reader, here, it can be a four random number generated by the database in the reader; ID is the current identification of the radio frequency tag; CRC is a cyclic check function; It is the exclusive OR operator, || is the string associator, ∮ is the string concatenation, f is the algorithm identifier, and Computer is the operation instruction sent by the reader to the radio frequency tag.
[0132] See Image 6 , The process of radio frequency label certification includes:
[0133] Step 601: The reader initiates a query request Query, and generates a first random number R r .
[0134] Step 602: The reader requests Query and the ...
Embodiment 3
[0163] Embodiment 3: The identification protection key E stored in the RFID system k , That is, the reader of the RFID system, the identification protection key E is stored in the radio frequency tag k , That is, there is the identification protection key E in the reader's database k And, in this embodiment, the database of the reader has the storage identification ID of each radio frequency tag i (Among them, i=1, 2, 3----n), Query is a query request; R r Is the first random number generated by the reader, R t Is the second random number generated by the radio frequency tag; R u Is the fourth random number generated by the reader, here, it can be a four random number generated by the database in the reader; ID is the current identification of the radio frequency tag; CRC is a cyclic check function; It is the exclusive OR operator, || is the string associator, ∮ is the string concatenation, f is the algorithm identifier, and Computer is the operation instruction sent by the reader...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com