Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
861 results about "Internet protocol suite" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
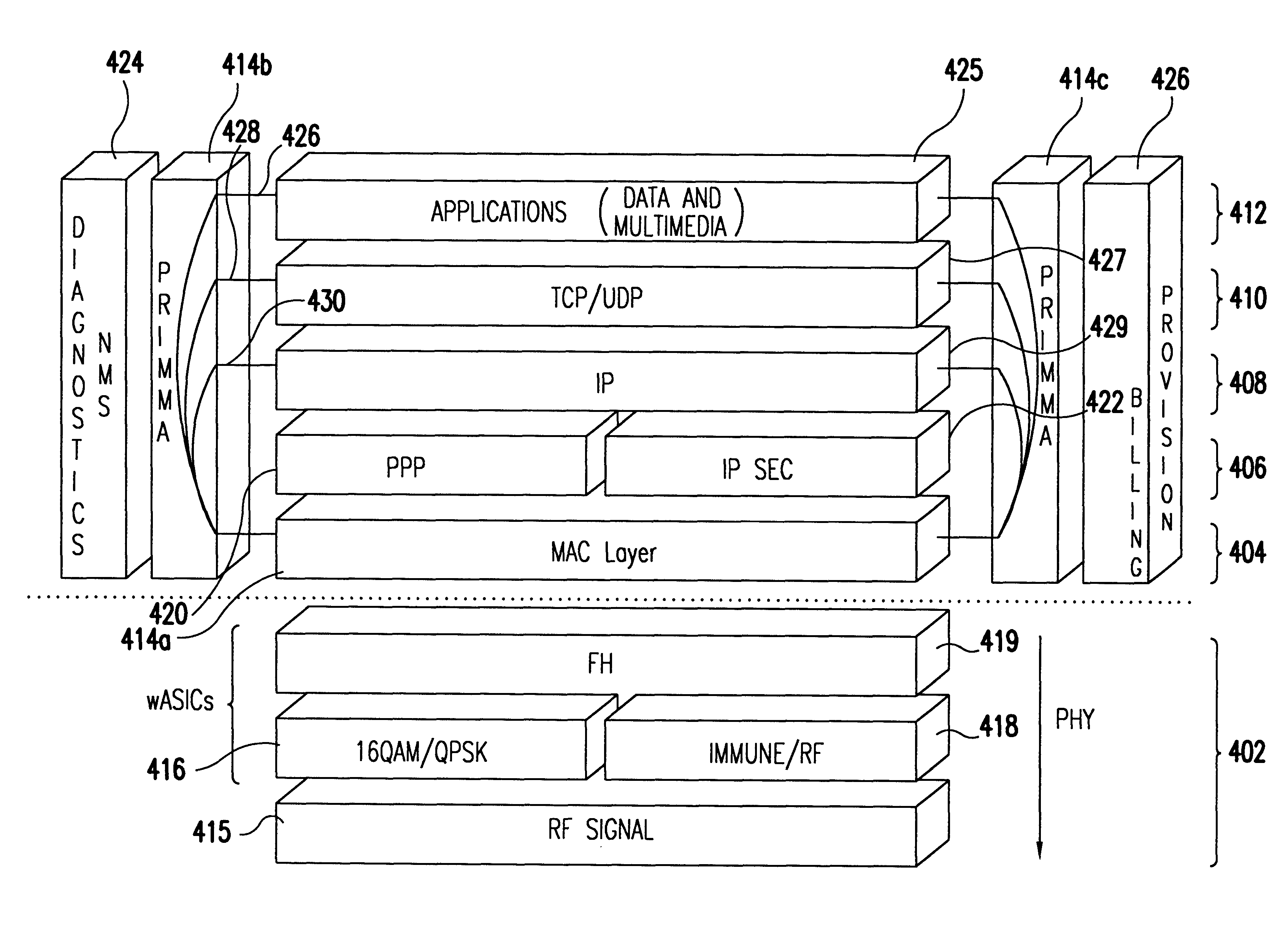
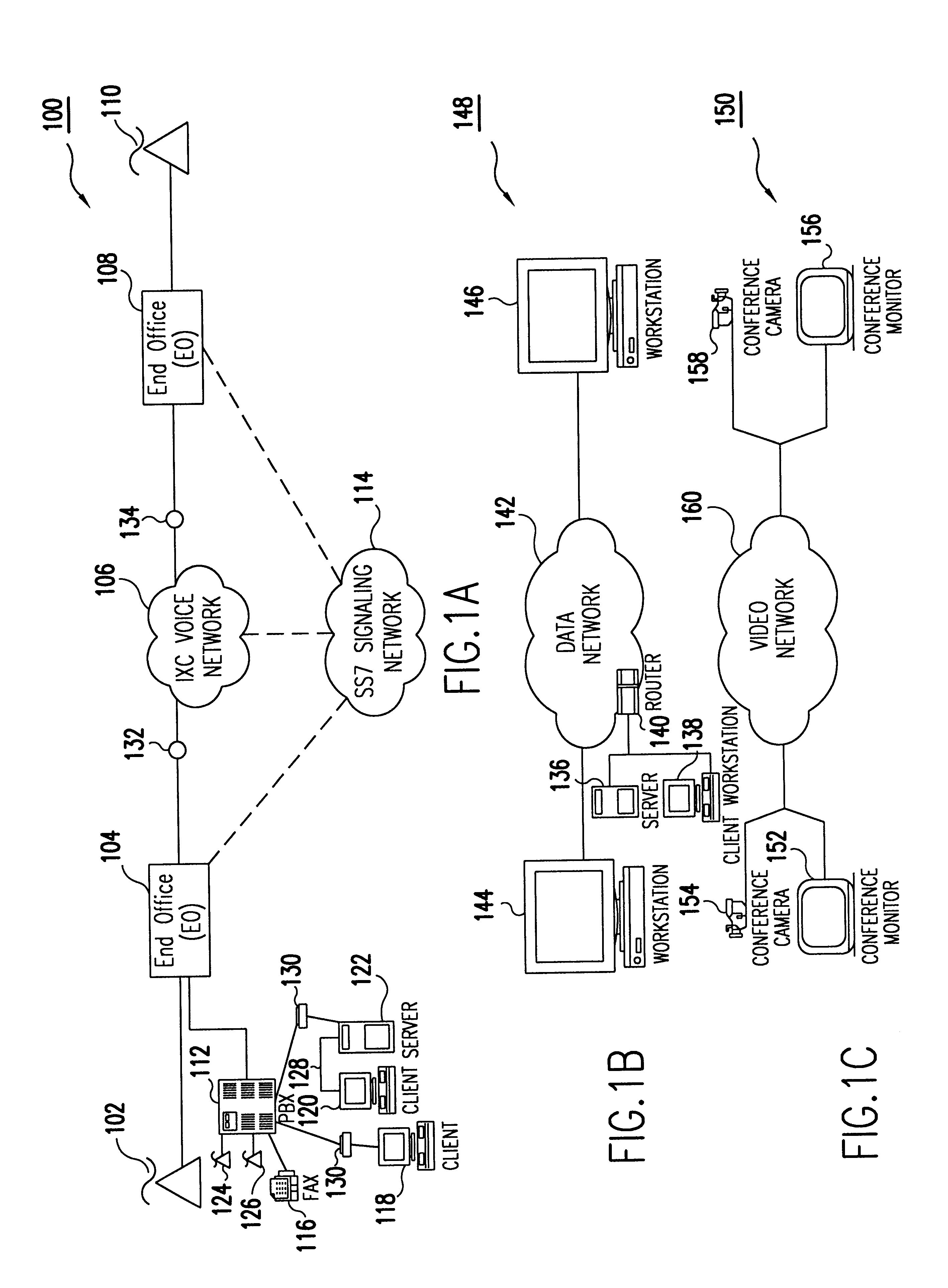
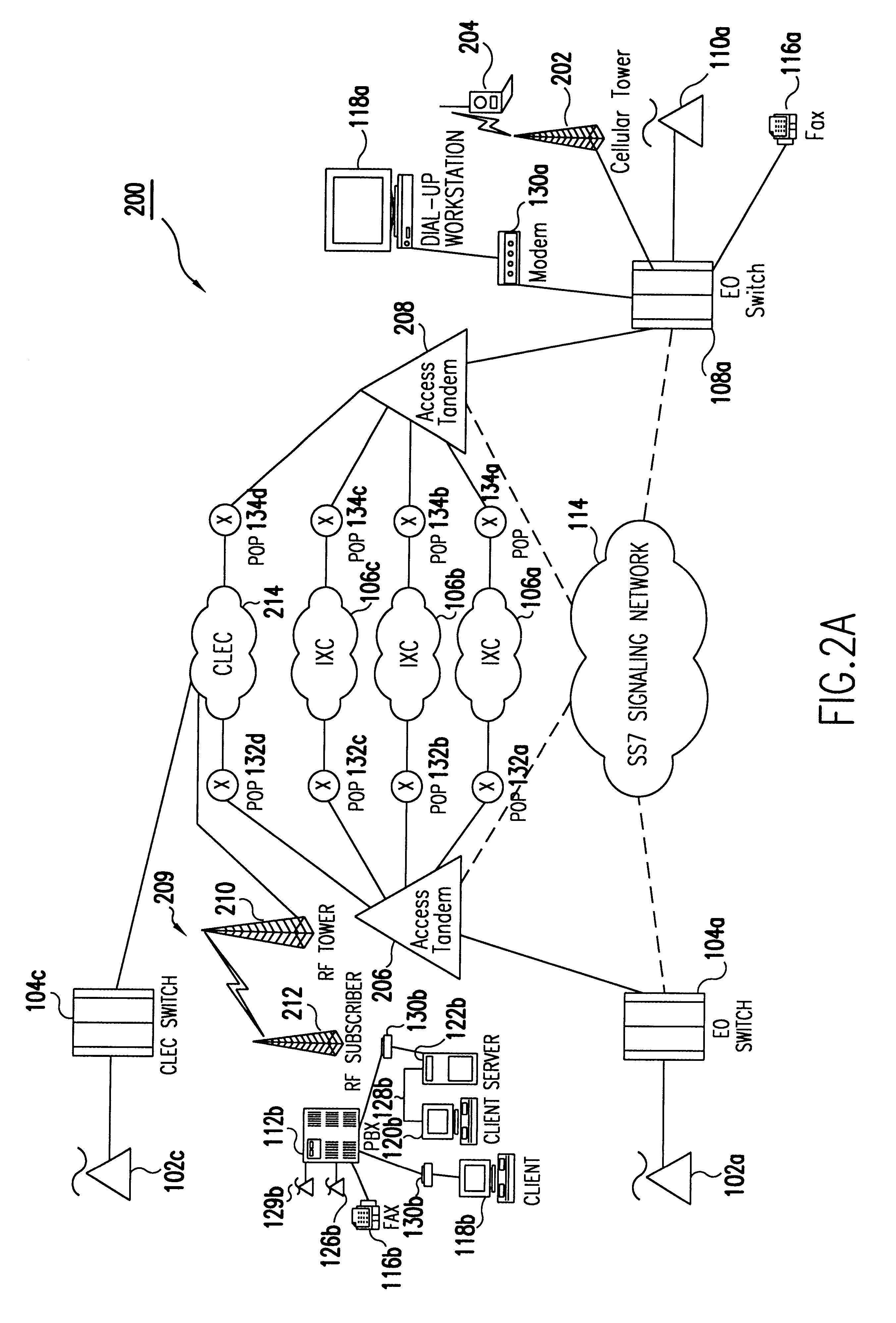
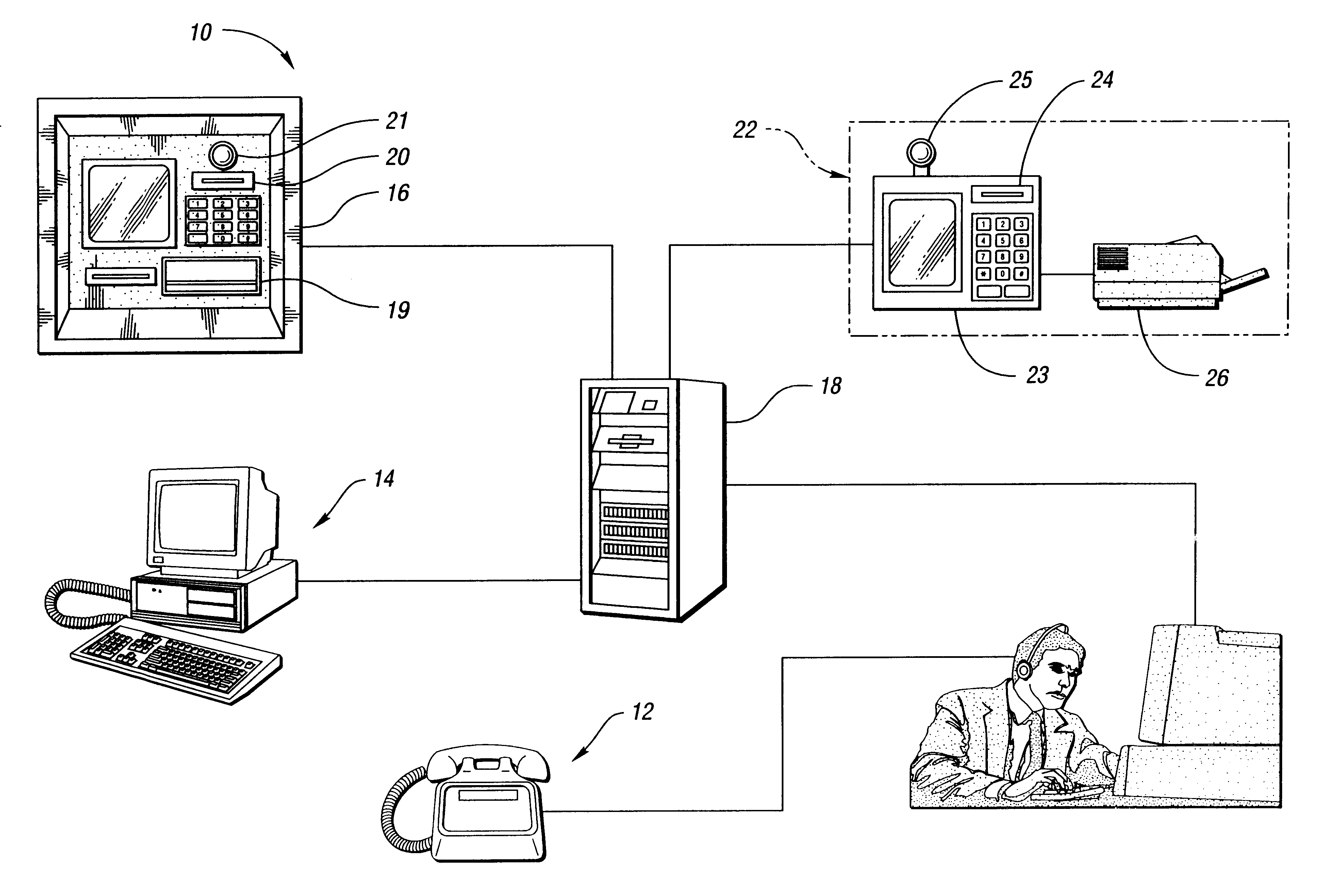
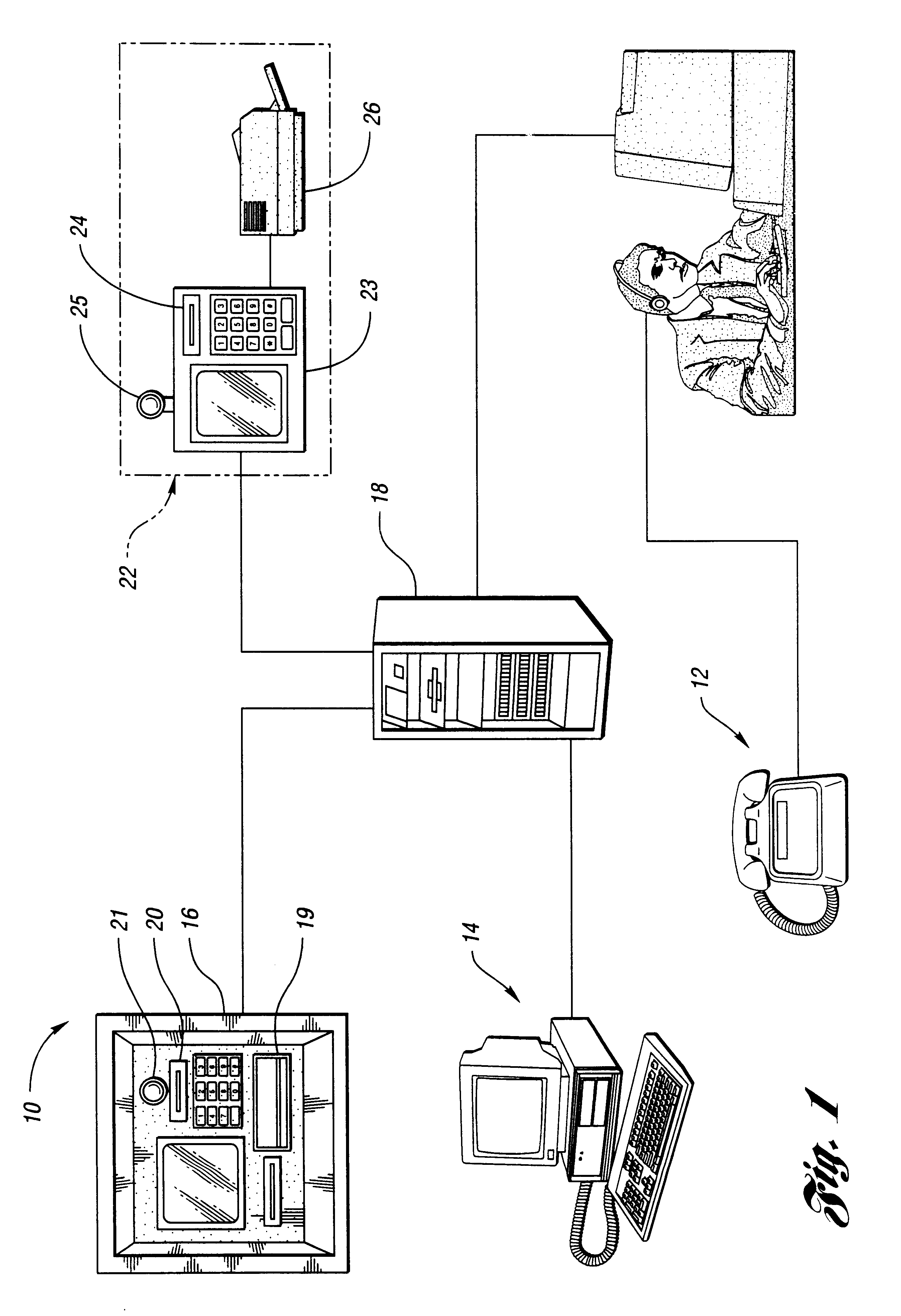
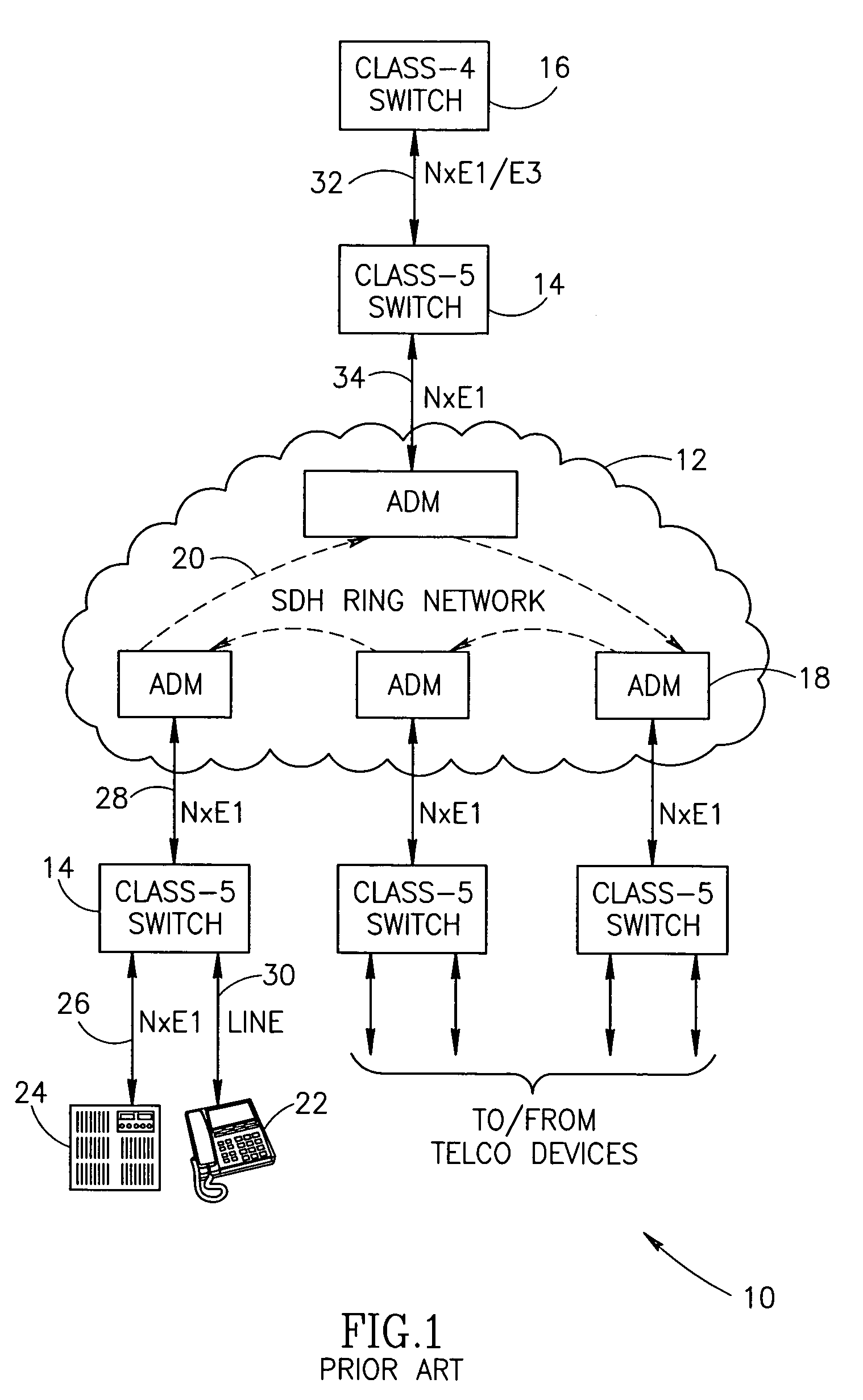
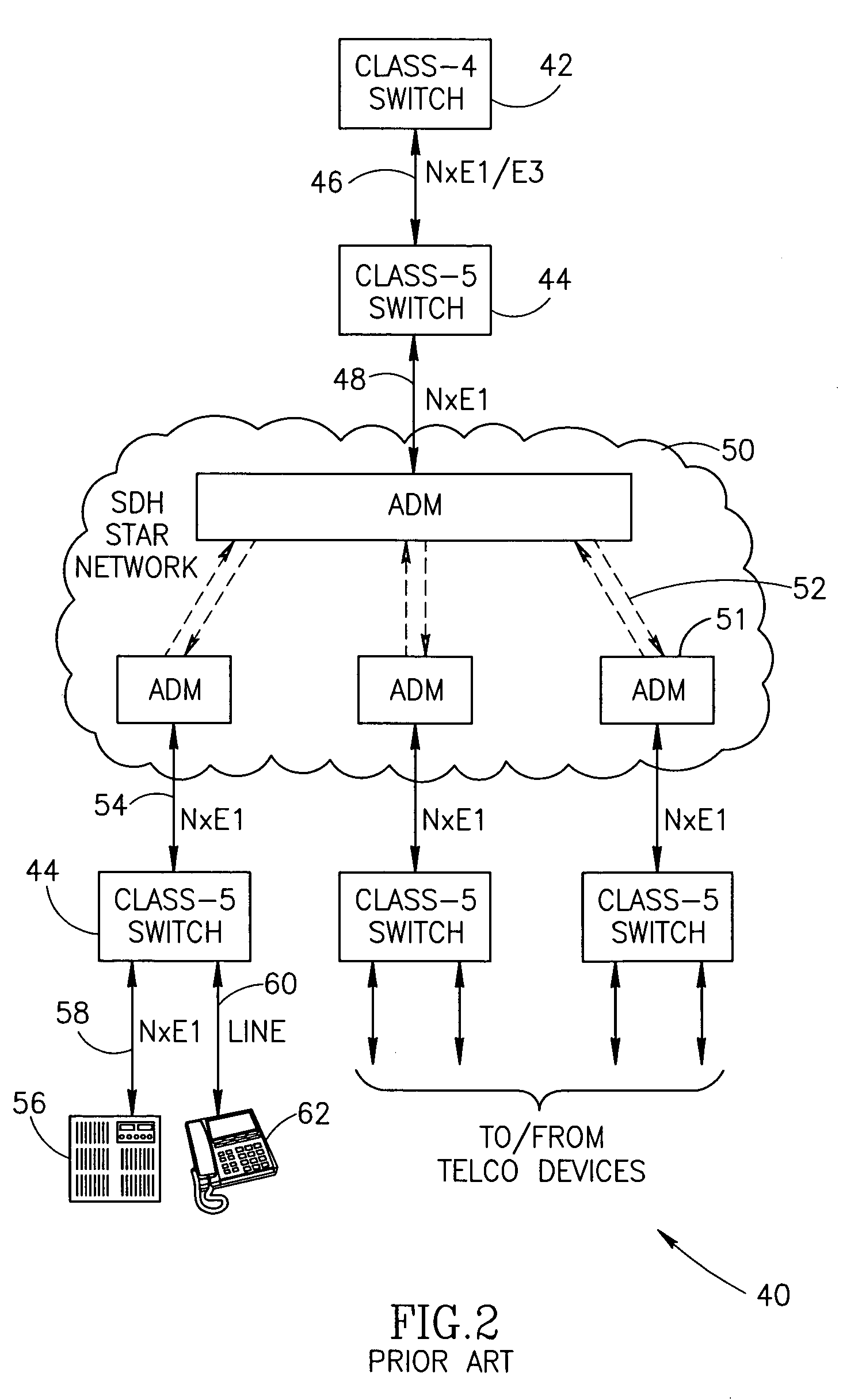
The Internet protocol suite is the conceptual model and set of communications protocols used in the Internet and similar computer networks. It is commonly known as TCP/IP because the foundational protocols in the suite are the Transmission Control Protocol (TCP) and the Internet Protocol (IP). During its development, versions of it were known as the Department of Defense (DoD) model because the development of the networking method was funded by the United States Department of Defense through DARPA.
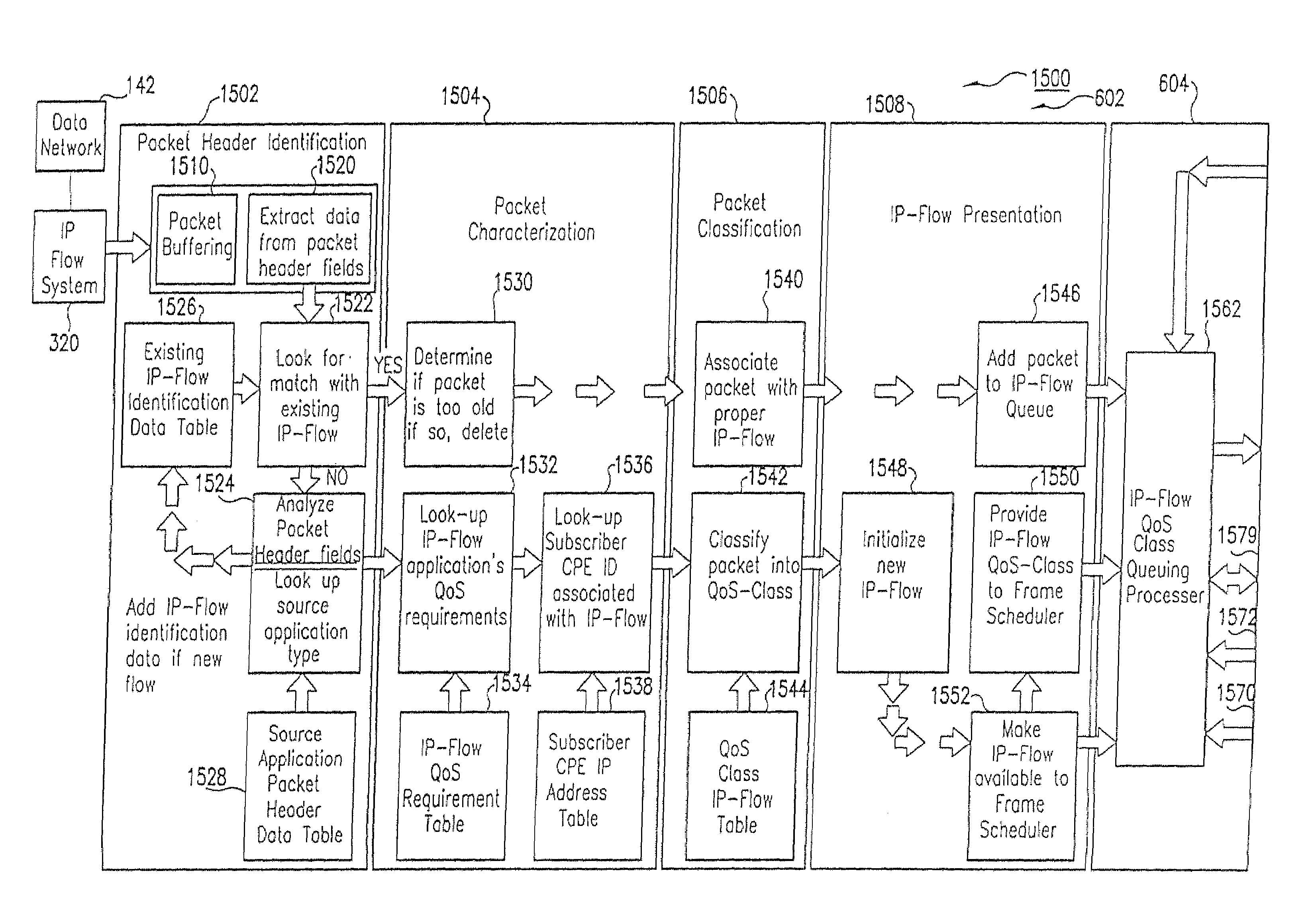
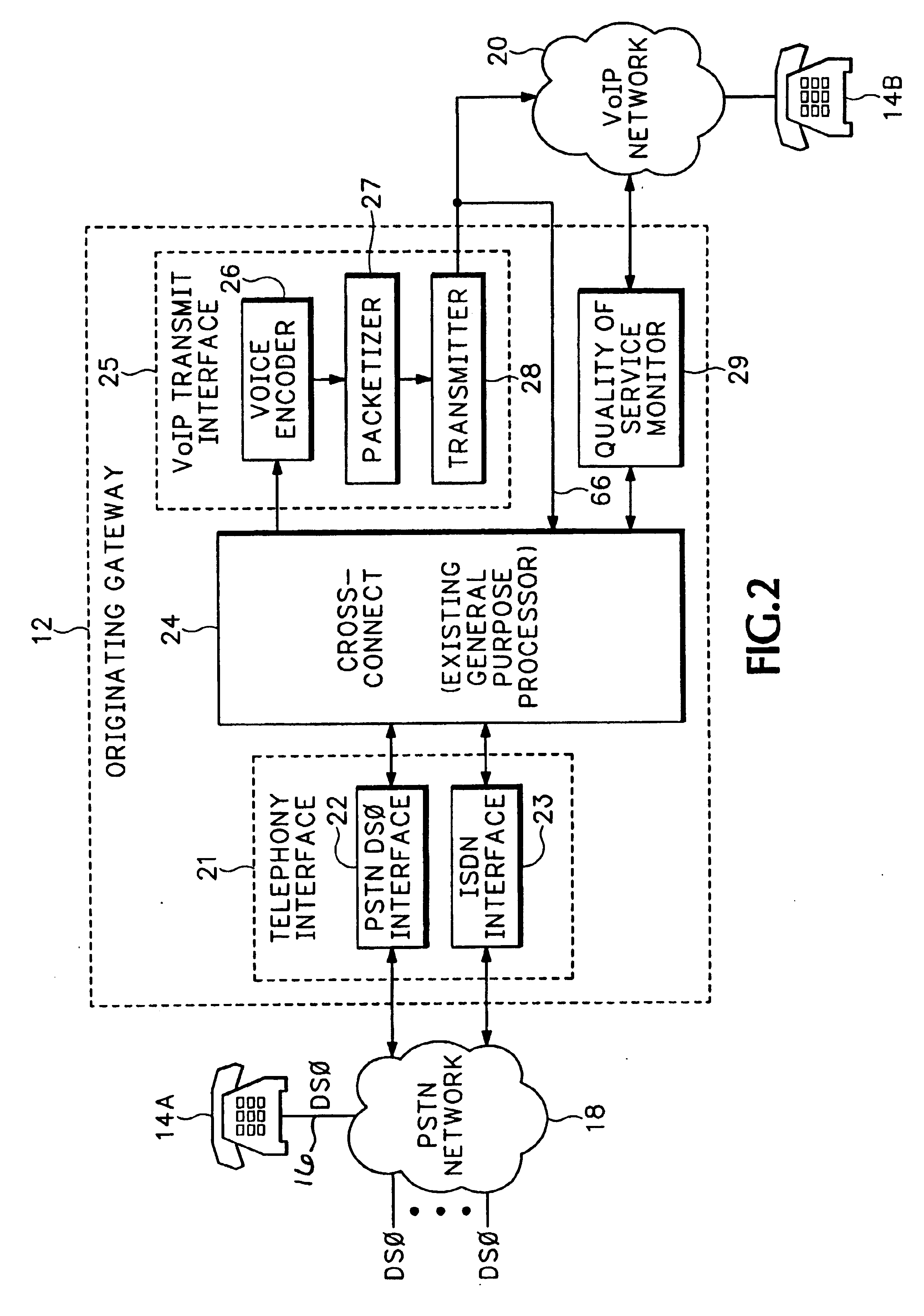
Method and computer program product for internet protocol (IP)-flow classification in a wireless point to multi-point (PtMP) transmission system
InactiveUS7251218B2Special service provision for substationError detection/prevention using signal quality detectorQuality of serviceWireless access point
A system and method for Internet Protocol (IP) flow classification group IP flows in a packet-centric wireless point to multi-point telecommunications system is disclosed. The method comprises analyzing an IP flow in a packet-centric manner, classifying the IP flow, scheduling the IP flow for transmission over a shared wireless bandwidth between a wireless base station and at least one subscriber customer premises equipment (CPE) station, allocating the shared wireless bandwidth to a communication of the IP flow between the wireless base station and a subscriber CPE station so as to optimize end-user quality of service (QoS) associated with the IP flow.
Owner:INTELLECTUAL VENTURES I LLC
Transmission control protocol/internet protocol (TCP/IP) packet-centric wireless point to multi-point (PTMP) transmission system architecture
InactiveUS6862622B2Special service provision for substationError detection/prevention using signal quality detectorTransport systemWorkstation
A packet-centric wireless point to multi-point telecommunications system includes: a wireless base station communicating via a packet-centric protocol to a first data network; one or more host workstations communicating via the packet-centric protocol to the first data network; one or more subscriber customer premise equipment (CPE) stations coupled with the wireless base station over a shared bandwidth via the packet-centric protocol over a wireless medium; and one or more subscriber workstations coupled via the packet-centric protocol to each of the subscriber CPE stations over a second network. The packet-centric protocol can be transmission control protocol / internet protocol (TCP / IP). The packet-centric protocol can be a user datagram protocol / internet protocol (UDP / IP). The system can include a resource allocation means for allocating shared bandwidth among the subscriber CPE stations. The resource allocation is performed to optimize end-user quality of service (QoS). The wireless communication medium can include at least one of: a radio frequency (RF) communications medium; a cable communications medium; and a satellite communications medium. The wireless communication medium can further include a telecommunications access method including at least one of: a time division multiple access (TDMA) access method; a time division multiple access / time division duplex (TDMA / TDD) access method; a code division multiple access (CDMA) access method; and a frequency division multiple access (FDMA) access method.The first data network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN). The second network includes at least one of: a wireline network; a wireless network; a local area network (LAN); and a wide area network (WAN).
Owner:INTELLECTUAL VENTURES I LLC
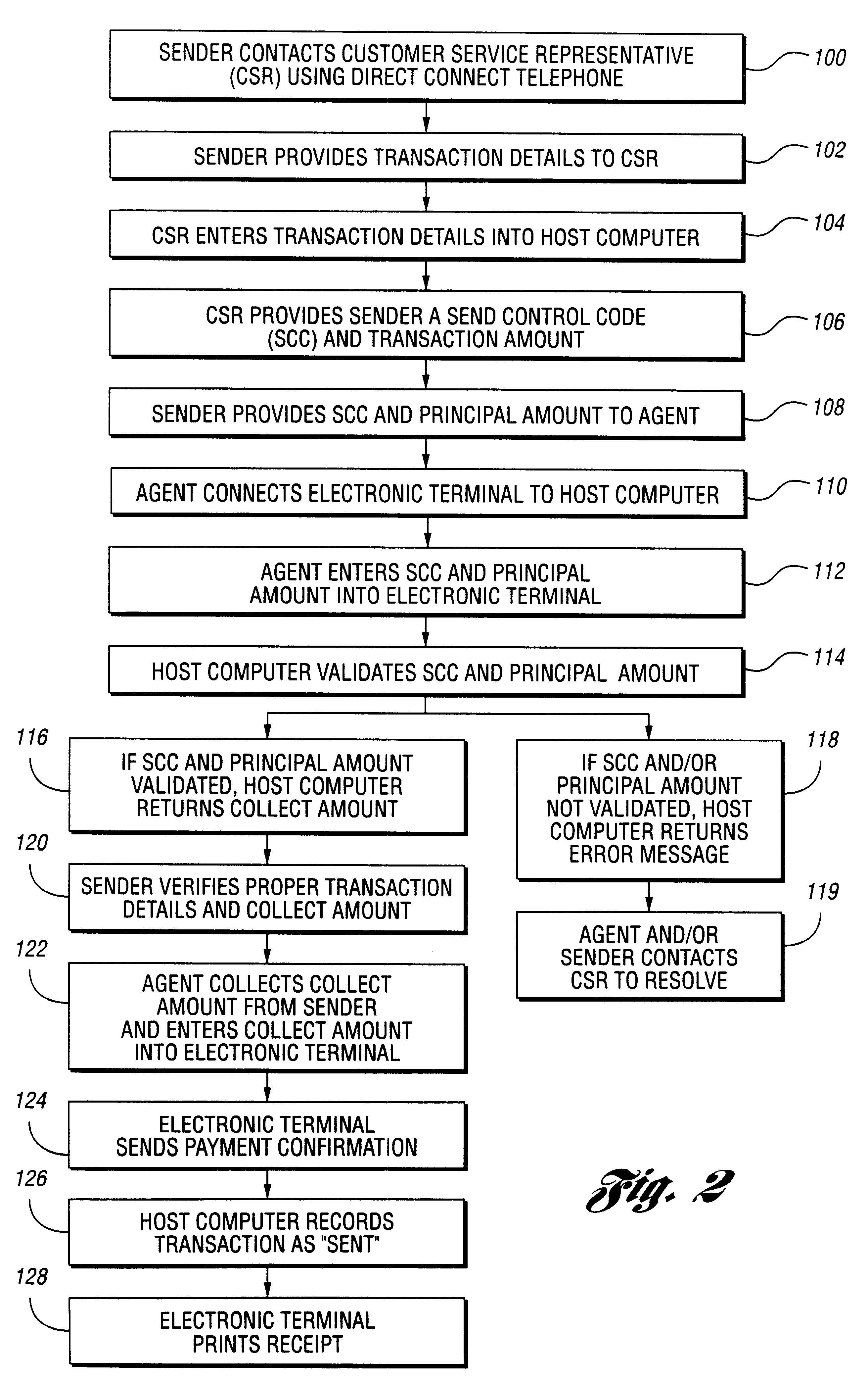
System and method for performing money transfer transaction using TCP/IP
InactiveUS6502747B1Low costShorten the timeComplete banking machinesFinanceInternet protocol suiteProtocol for Carrying Authentication for Network Access
A method of performing a money transfer transaction through a financial services institution includes receiving information regarding the transaction on a first computer of the financial services institution from a first electronic device using the Transmission Control Protocol / Internet Protocol suite (TCP / IP). The method may also include establishing a T1 connection between the first computer and the first electronic device. A system for performing a money transfer transaction using TCP / IP is also disclosed.
Owner:THE WESTERN UNION CO
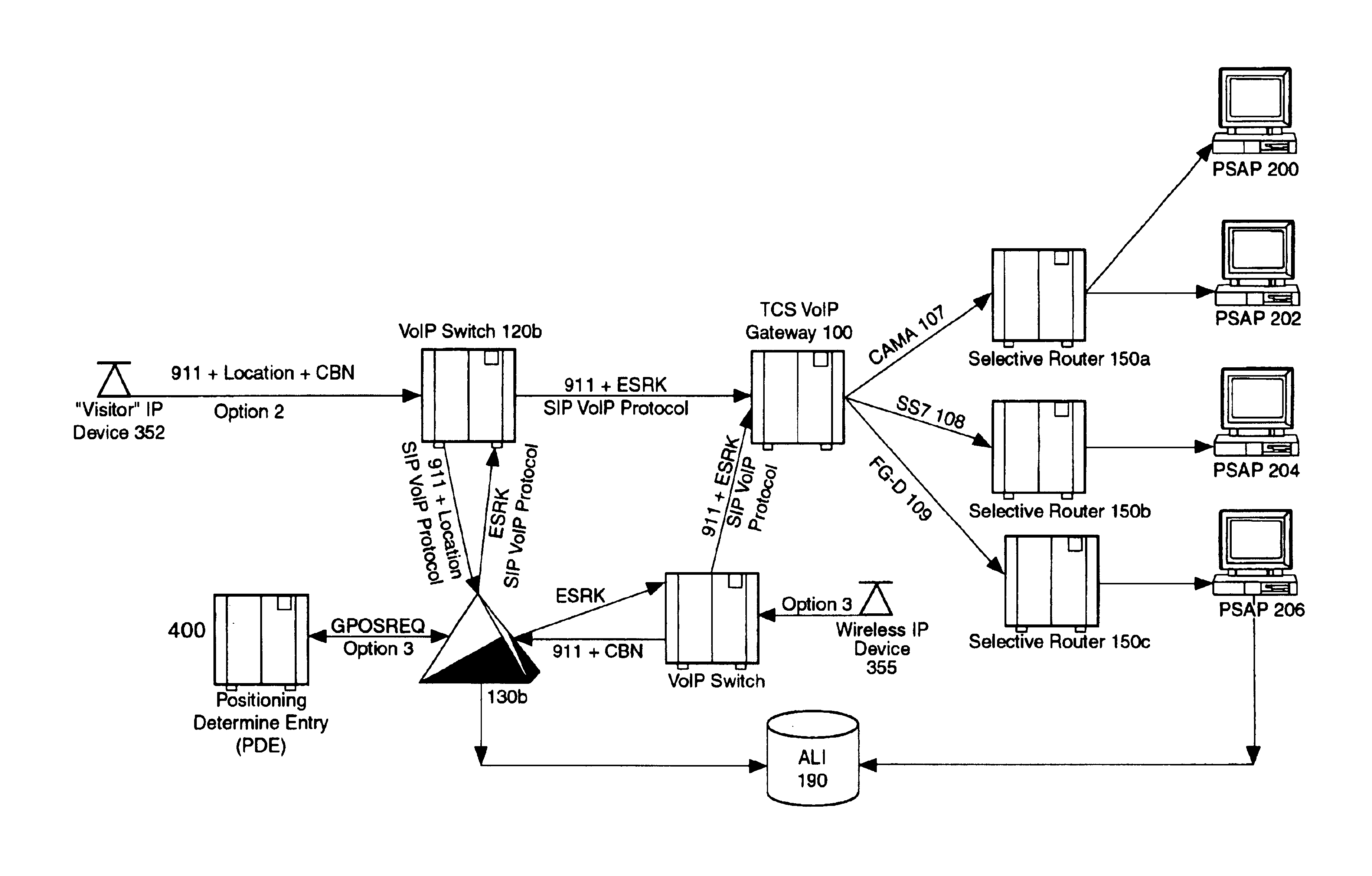
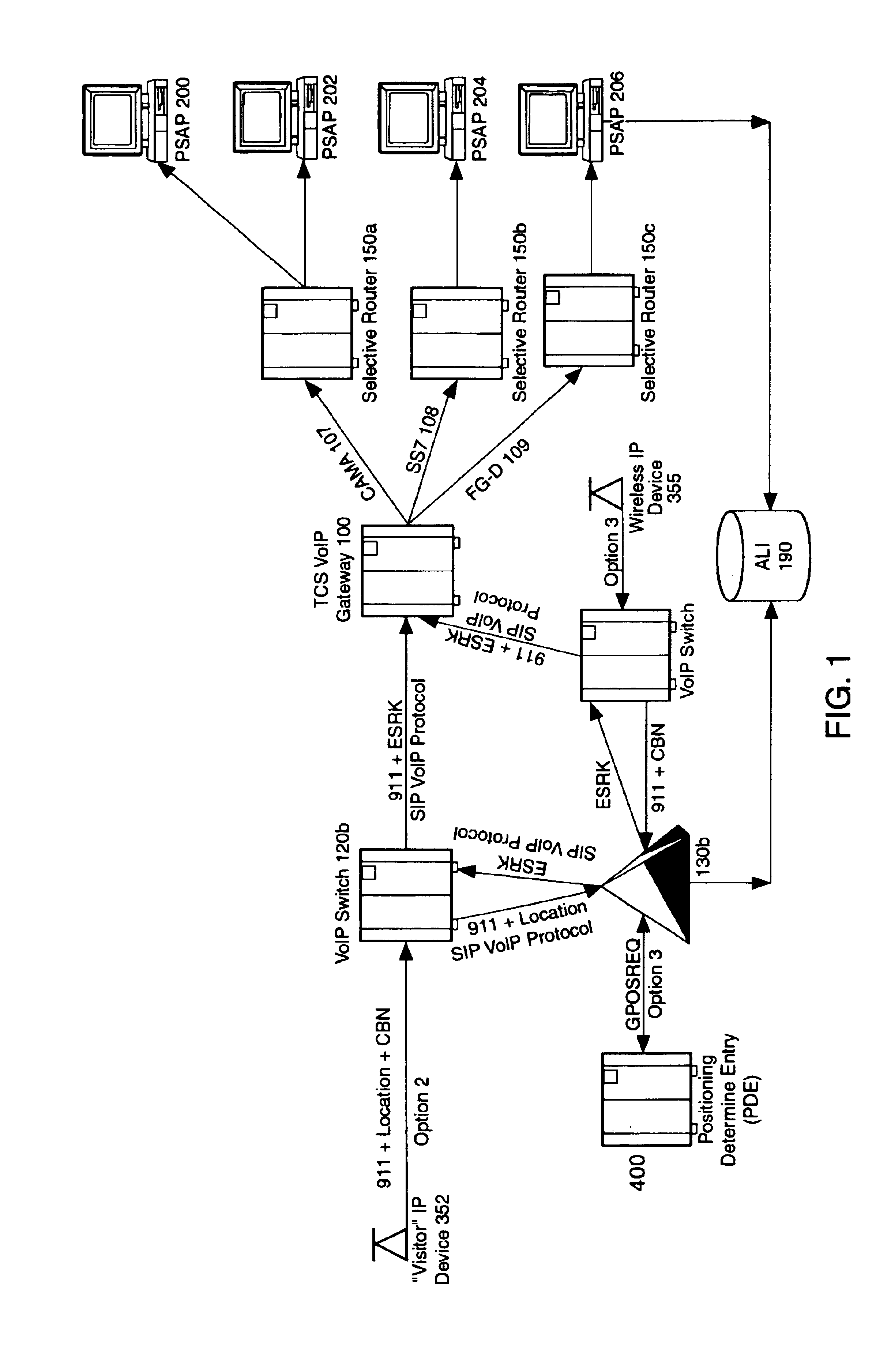
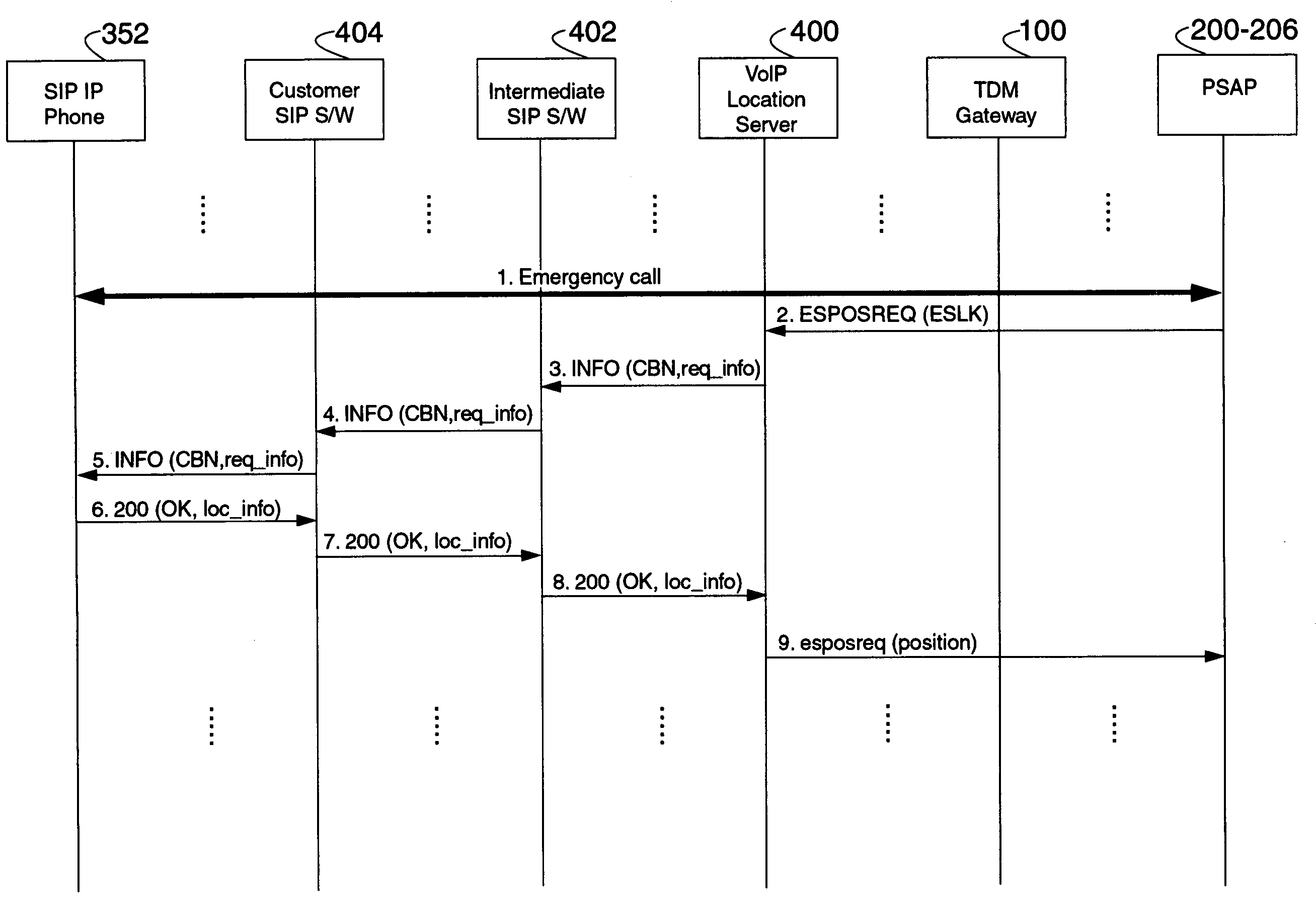
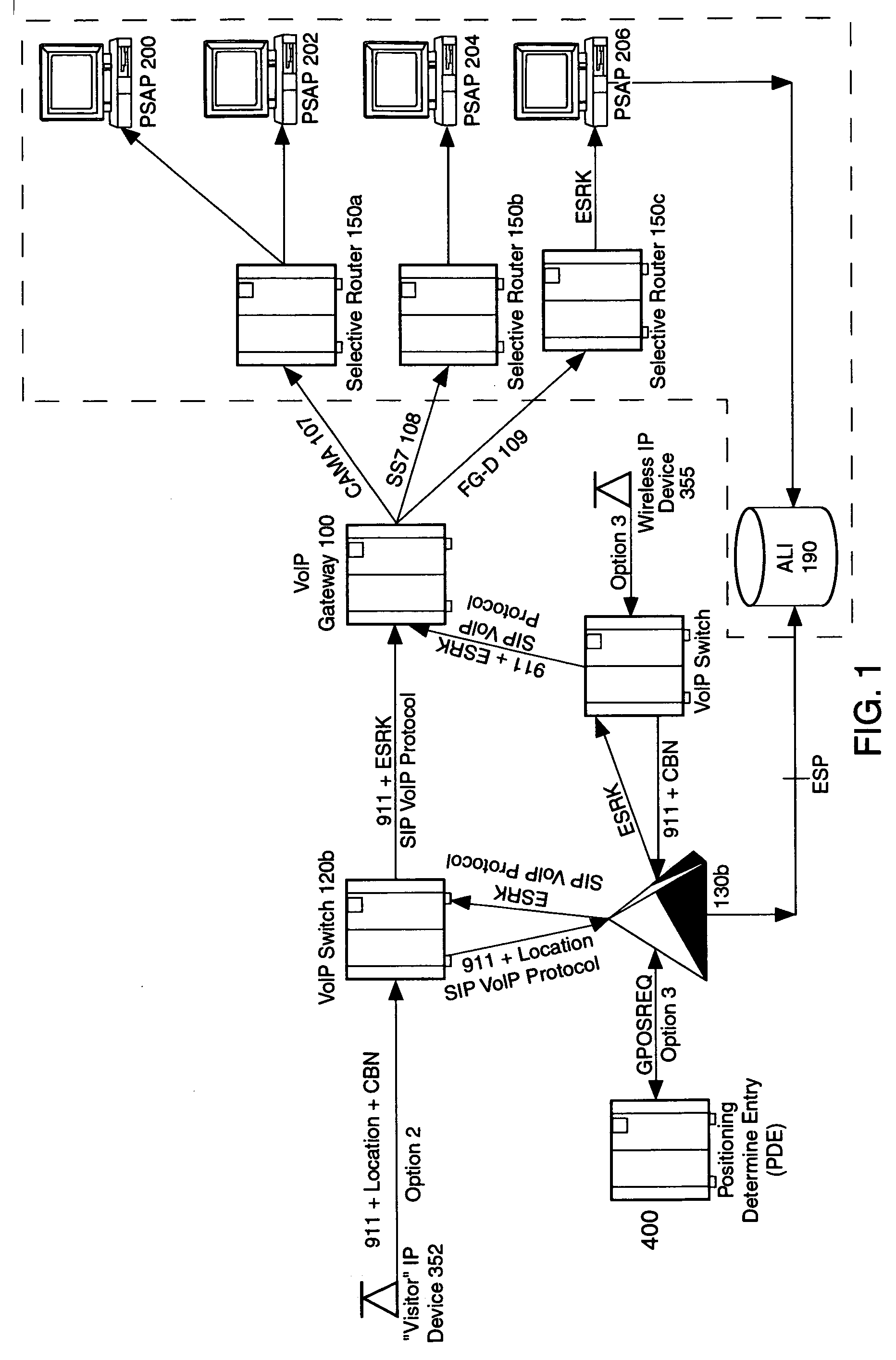
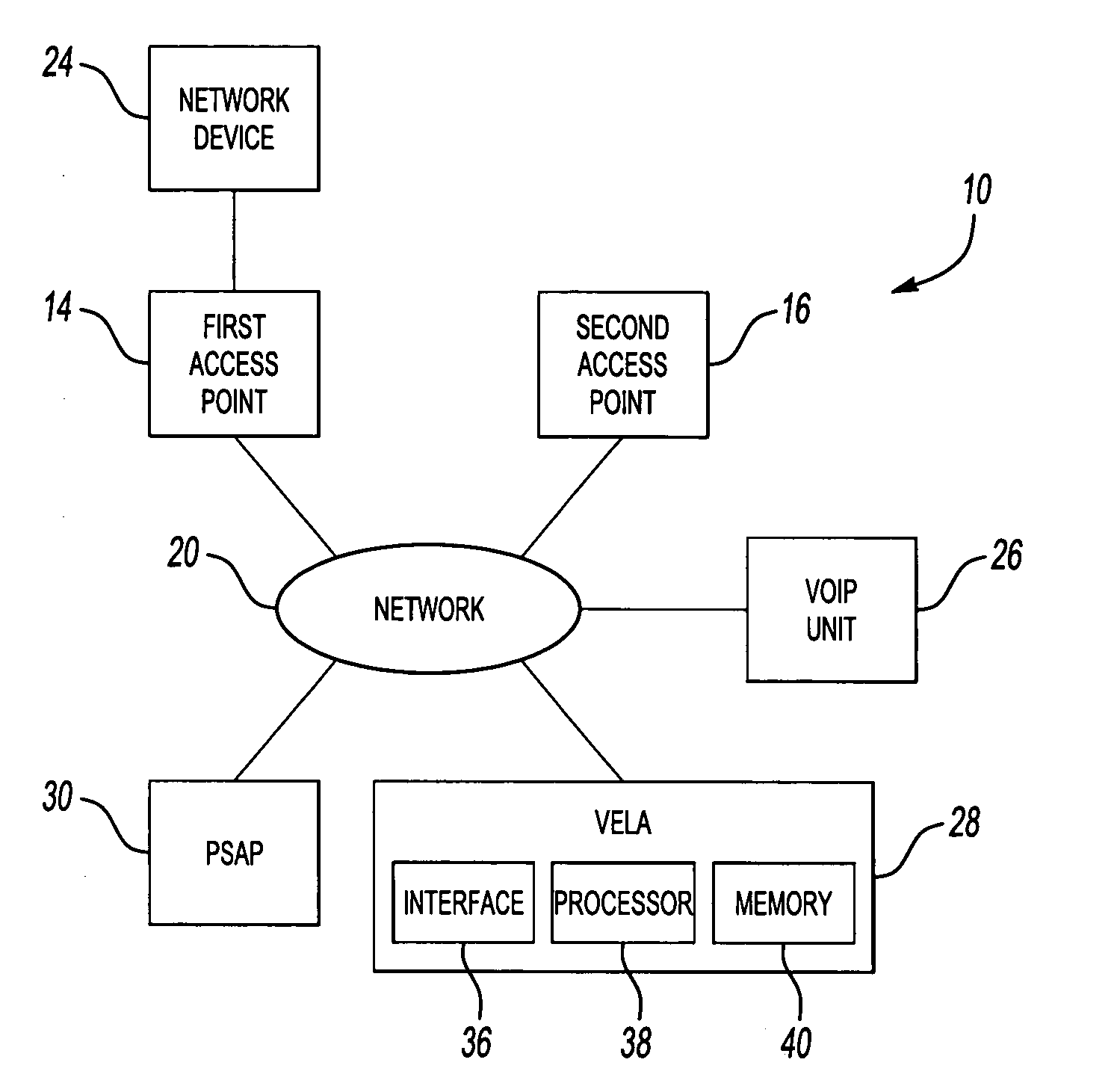
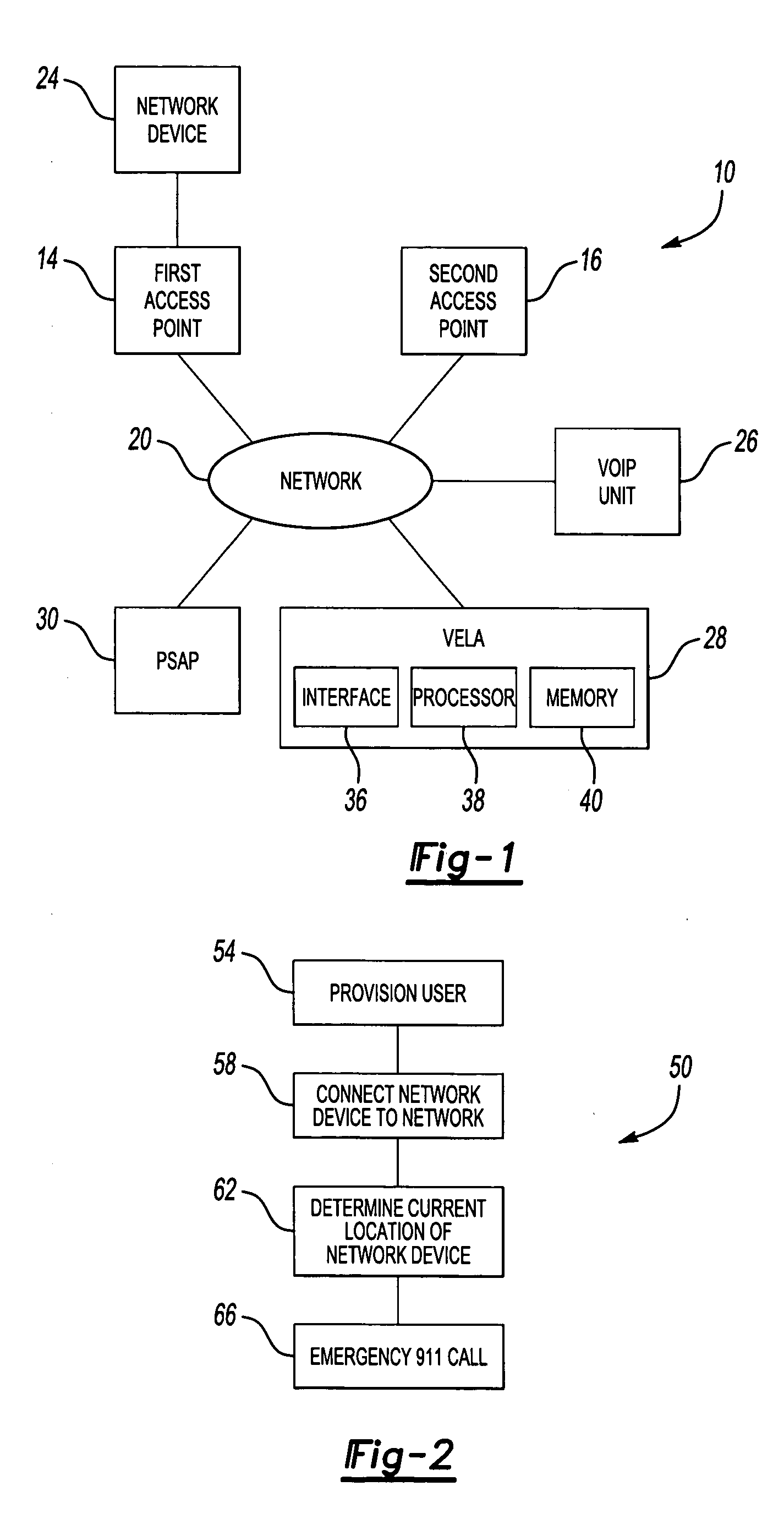
Enhanced E911 location information using voice over internet protocol (VoIP)
An E-9-1-1 voice-over-IP (VoIP) solution is provided wherein a 911 call from a wireless VoIP device is routed directly to the correct Public Safety Answer Point (PSAP) via dedicated trunks, together with correct location information and call-back number. VoIP gateways are implemented locally, at least one per LATA, and accept VoIP packetized data inbound, and convert it to standard wireline voice calls. Calls are routed to an IP address at the VoIP gateway, which then egresses the call to a voice port at a selective router. Dedicated voice trunks (CAMA, SS7, FG-D) are installed between each local VoIP gateway and appropriate selective routers. An Automatic Location Identification (ALI) database is provisioned with ESRKs dedicated for VoIP use. TCP / IP circuits may be established between some or all of the various local VoIP gateways.
Owner:TELECOMM SYST INC
Solutions for voice over internet protocol (VoIP) 911 location services
ActiveUS7260186B2Emergency connection handlingSpecial service for subscribersInternet protocol suiteTTEthernet
An E-9-1-1 voice-over-IP (VoIP) solution is provided wherein a 911 call from a mobile VoIP device is routed directly to the correct Public Safety Answer Point (PSAP) via dedicated trunks, together with correct location information and call-back number. VoIP gateways are implemented locally, at least one per LATA, and accept VoIP packetized data inbound, and convert it to standard wireline voice calls. Calls are routed to an IP address at the VoIP gateway, which then egresses the call to a voice port at a selective router. Mid-call updating of location of a moving VoIP terminal is provided to a PSAP. The location of the VoIP is validated using HTTP based protocol by pushing location information to a VoIP location server, and comparing it against a geographic location database to confirm that a contained street address is valid.
Owner:TELECOMM SYST INC
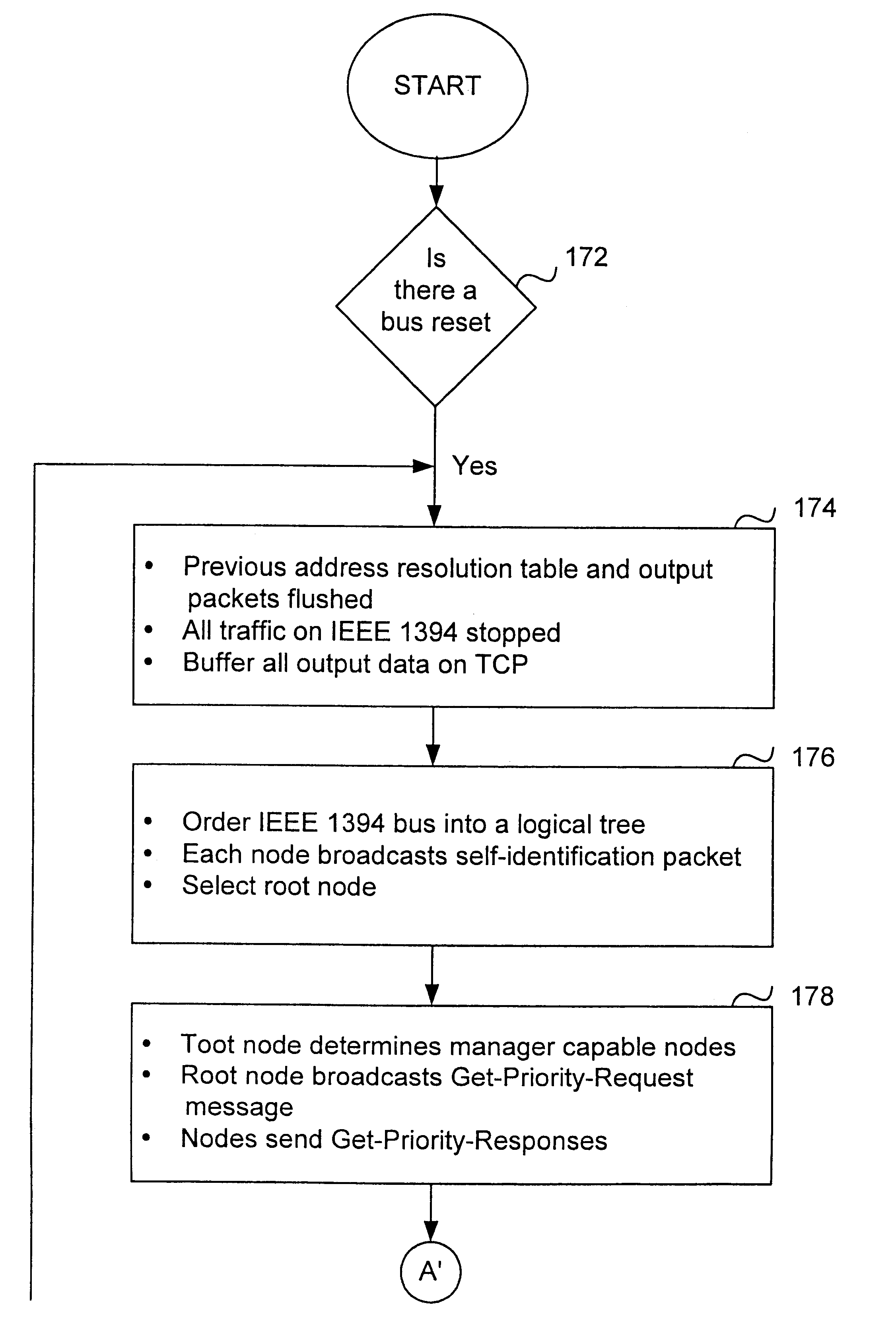
Method and apparatus for operating the internet protocol over a high-speed serial bus
InactiveUS6219697B1Efficiently and correctly determineDigital computer detailsTransmissionInternet protocol suiteTransport layer
A method and apparatus of integrating the IEEE 1394 protocol with the IP protocol in which the IEEE 1394 high speed serial bus operates as the physical and link layer medium and the IP operates as the transport layer. There are differences in the protocols which require special consideration when integrating the two protocols. The IEEE 1394 configures packets with memory information and the IP operates under channel based I / O thereby necessitating a modification of the data transfer scheme to accomplish IP transfers over the IEEE 1394. Further, due to differences in packet headers, the IEEE 1394 packet header is modified to encapsulate IP packets. Moreover, in order to determine network packets quickly and efficiently, an identifier is inserted in each network packet header indicating that the packet should be processed by the network. Finally, in order to support the ability to insert or remove nodes on the network without a loss of data, the IP interface must not be disturbed. This is accomplished by maintaining constant IP addresses across bus resets which are caused by insertion or removal of nodes from the network.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
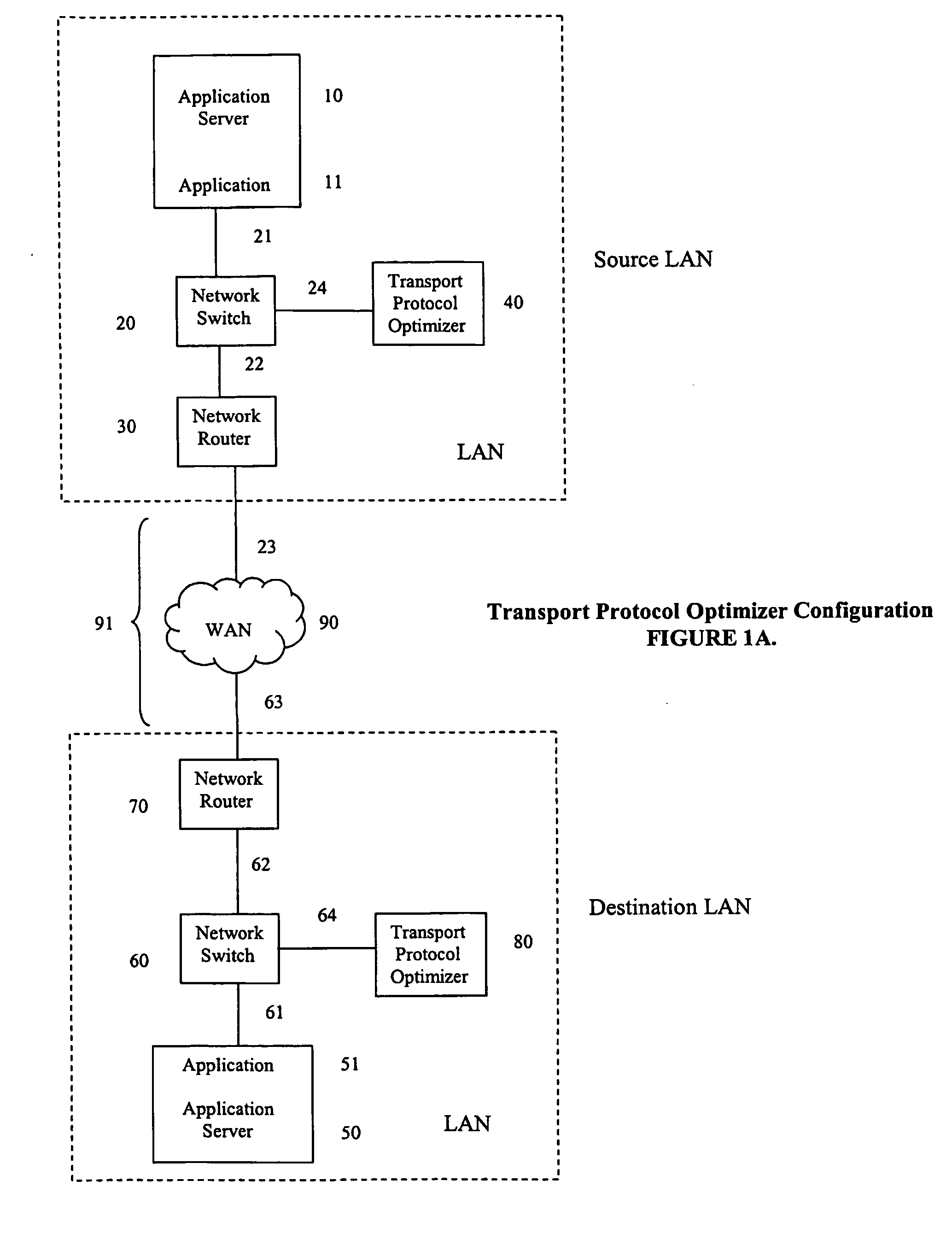
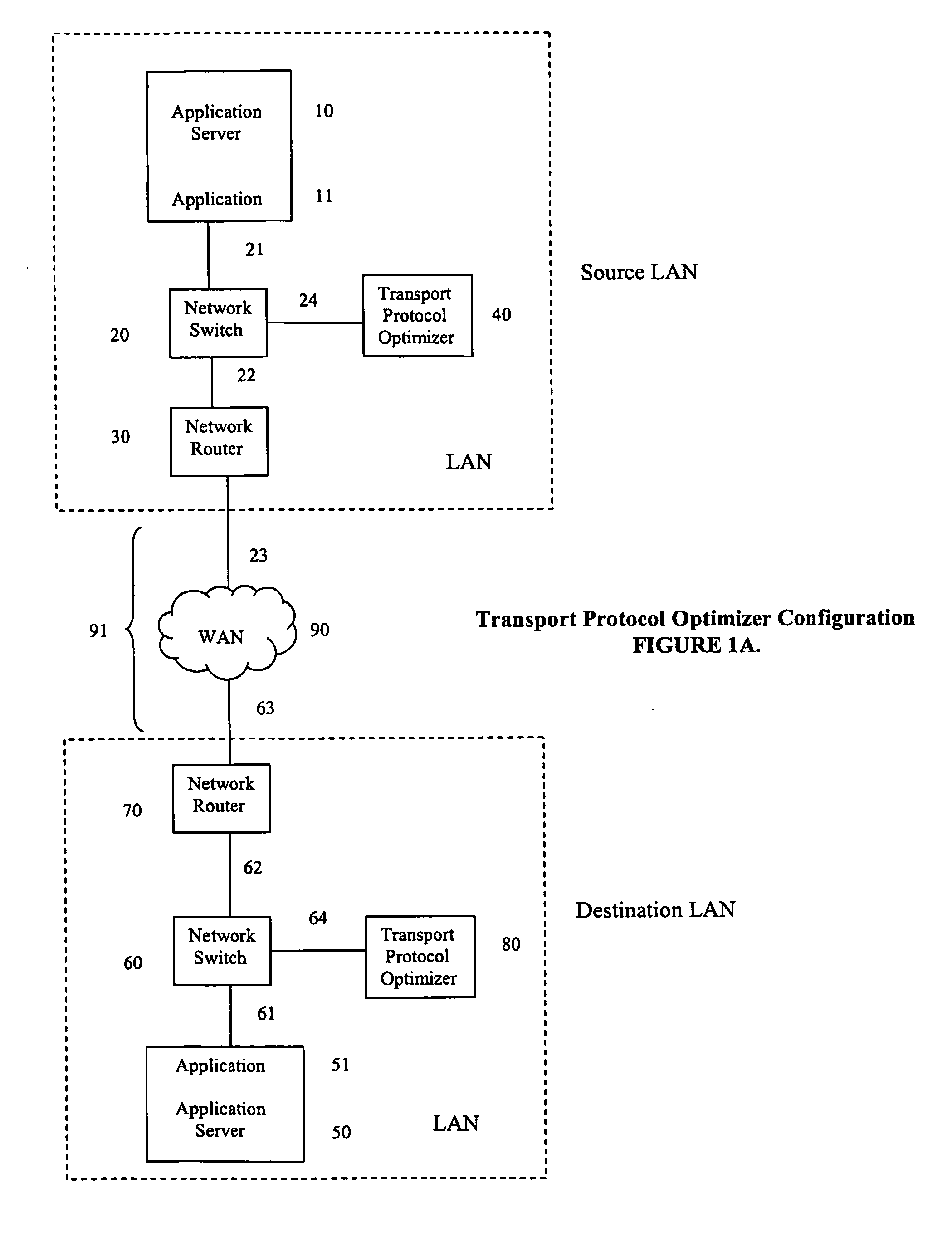
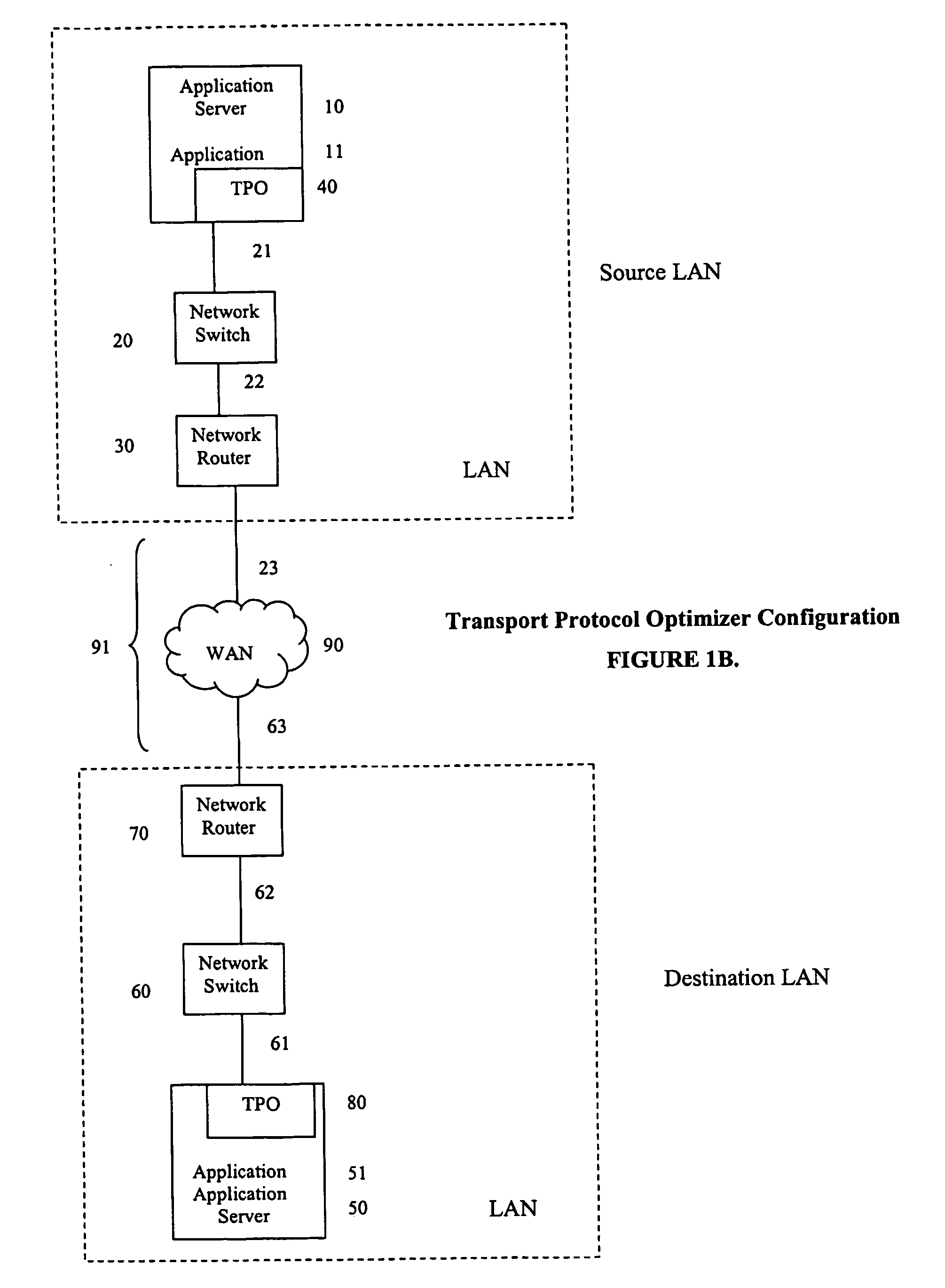
Internet protocol optimizer
InactiveUS20070110046A1Time-division multiplexData switching by path configurationInternet protocol suiteThroughput
A method for optimizing the throughput of TCP / IP applications by aggregating user application data and consolidating multiple TCP / IP connection streams into a single optimized stream for delivery to a destination application. Optimization of the internet protocol uses a packet interceptor to intercept packets from a source application, a packet driver to aggregate the intercepted packets, a data mover to transport the aggregated packets to another data mover at the destination, a destination packet driver to disaggregate the transported aggregated packets, and a destination end processor to deliver the disaggregated IP packets to the destination application.
Owner:NETWORK EXECUTIVE SOFTWARE
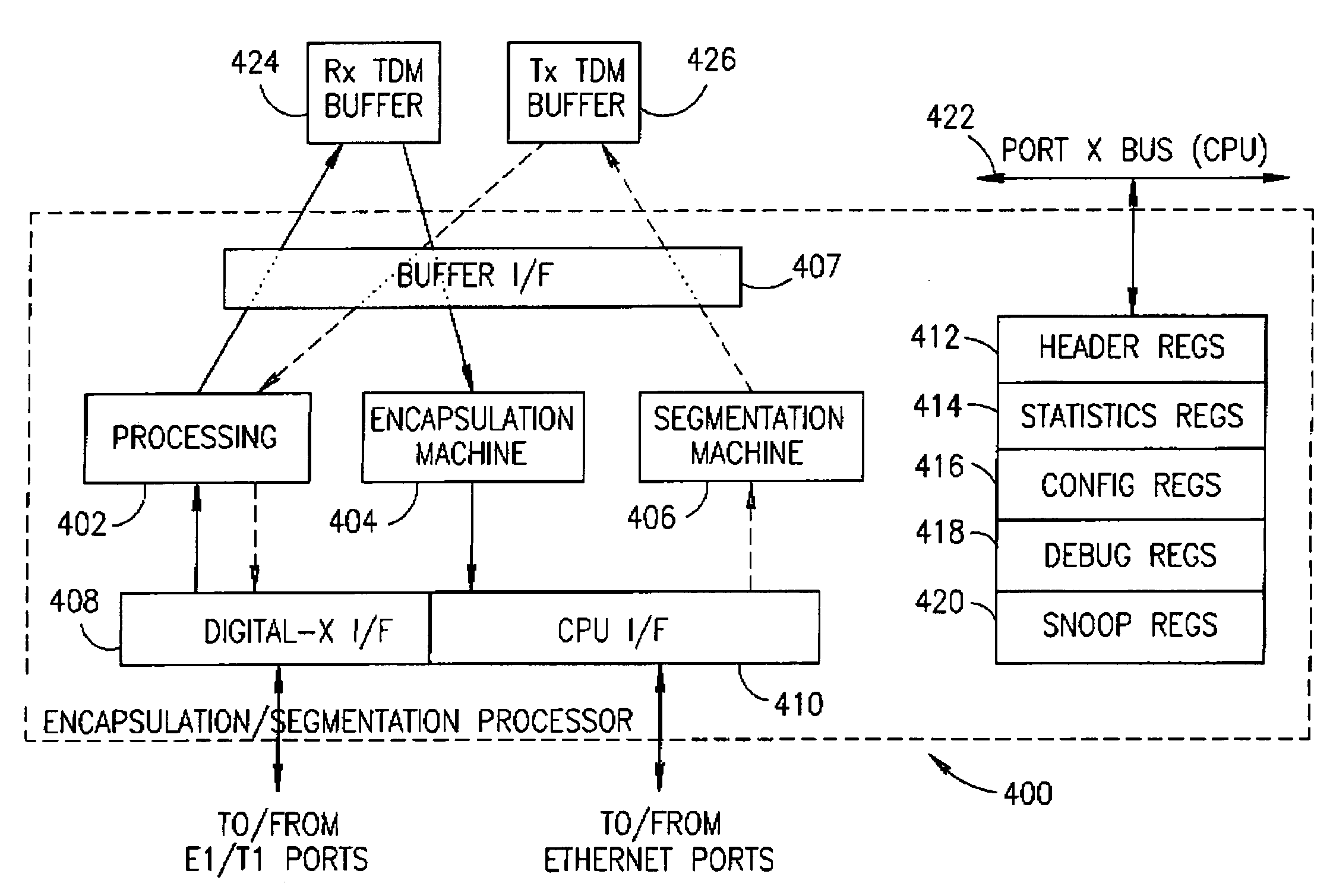
Facility for transporting TDM streams over an asynchronous ethernet network using internet protocol
InactiveUS6963561B1Low costTime-division multiplexData switching by path configurationInternet protocol suiteSTM-1
A transport facility adapted to transport TDM bit streams using IP packets over an asynchronous Ethernet network. TDM bit streams such as E1, T1, E3, T3, OC-3, OC-12, STM-1, STM-4, etc. are received, buffered and encapsulated into Ethernet frames. The Circuit Emulation Device (CED) receives, buffers and assembles in real-time ingress data from TDM ports into Ethernet Frames and forwards them to an Ethernet interface. The TDM data is encapsulated within RTP, UDP and IP packets before being encapsulated within an Ethernet frame. In the egress direction, Ethernet frames enter the encapsulation / segmentation processor from the Ethernet port and the IP, UDP and RTP packets are extracted from the frame. TDM data is extracted and the bit streams are re-generated and forwarded to the TDM ports for transmission over legacy TDM facilities.
Owner:VENTURE LENDING & LEASING III
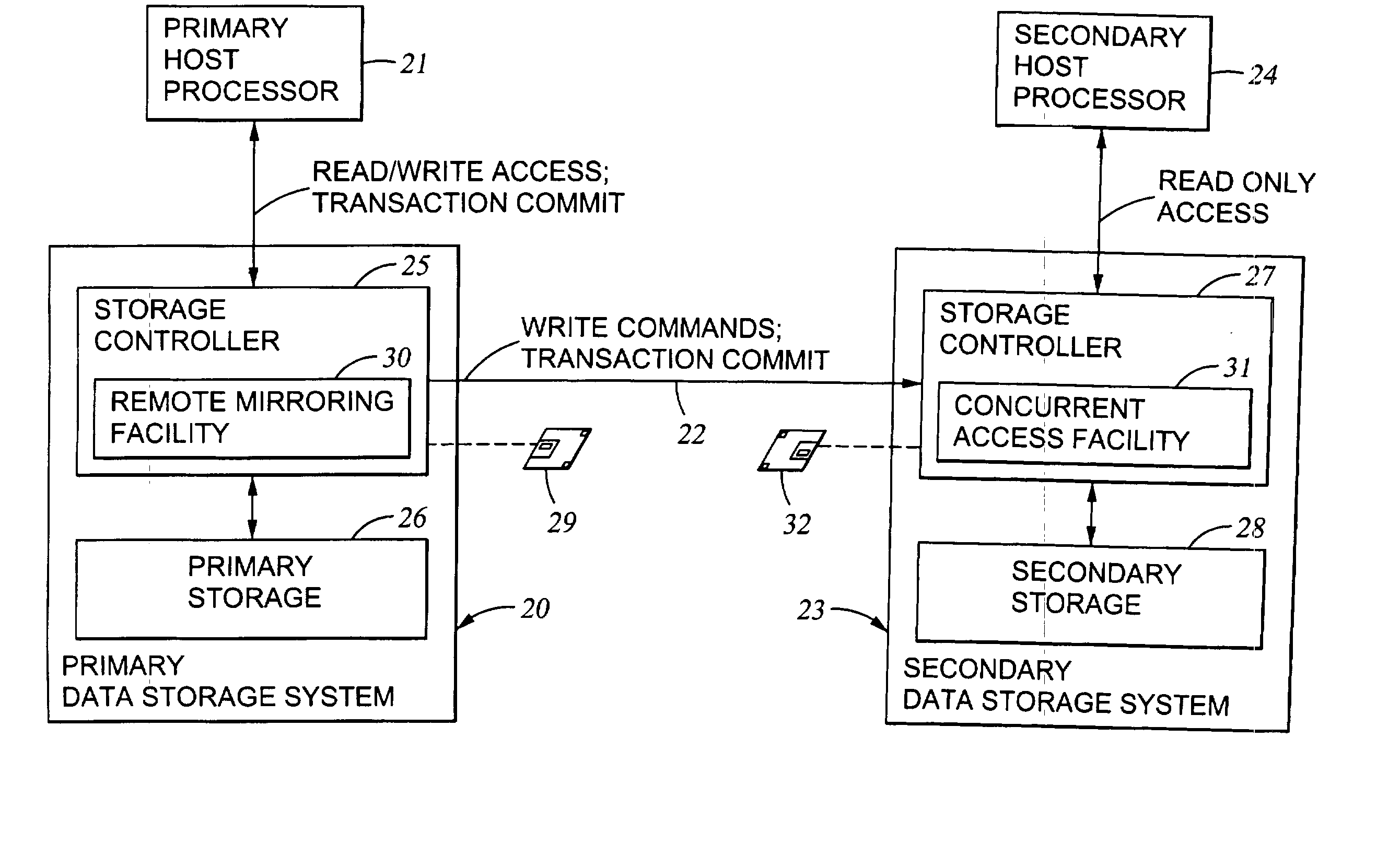
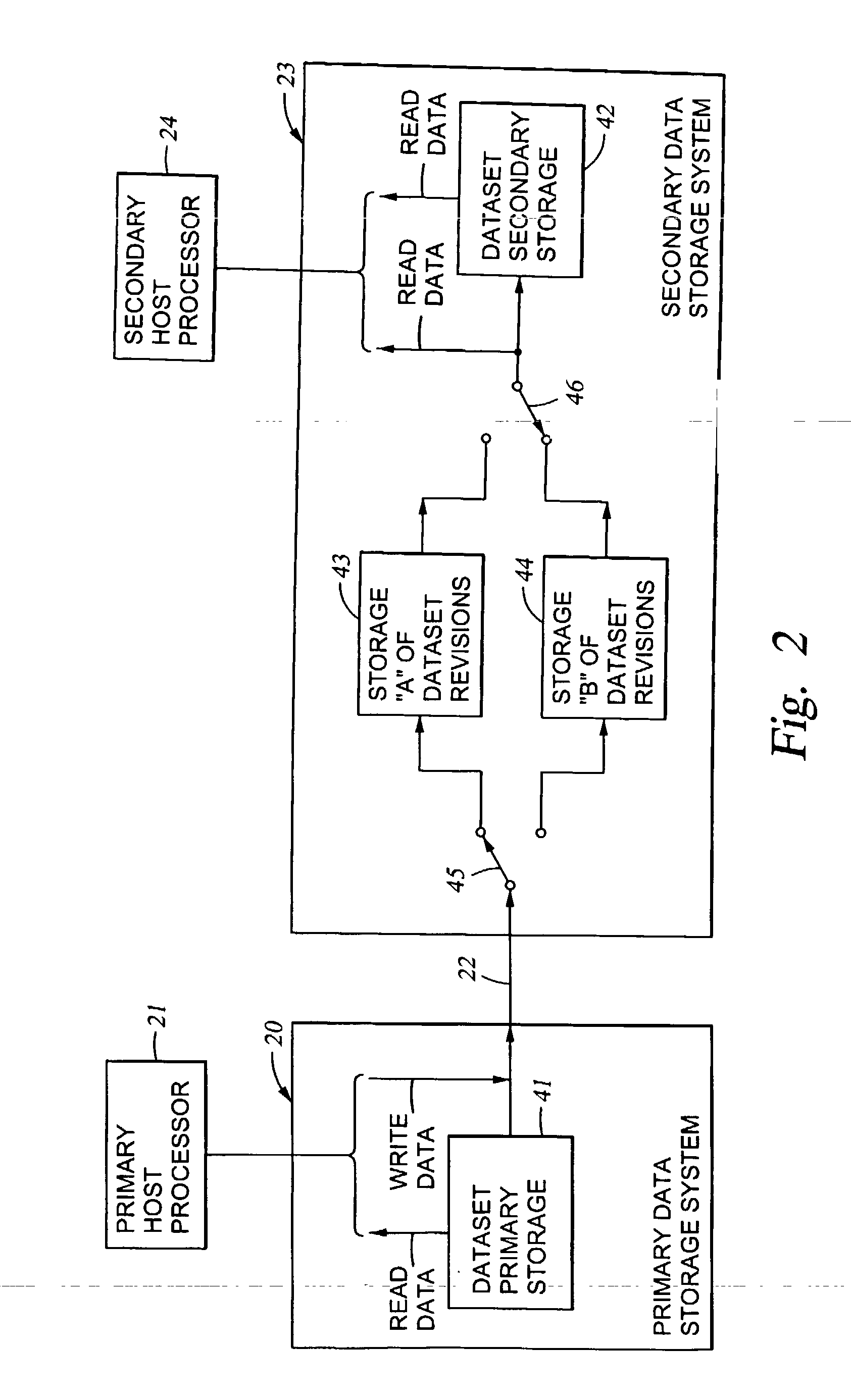
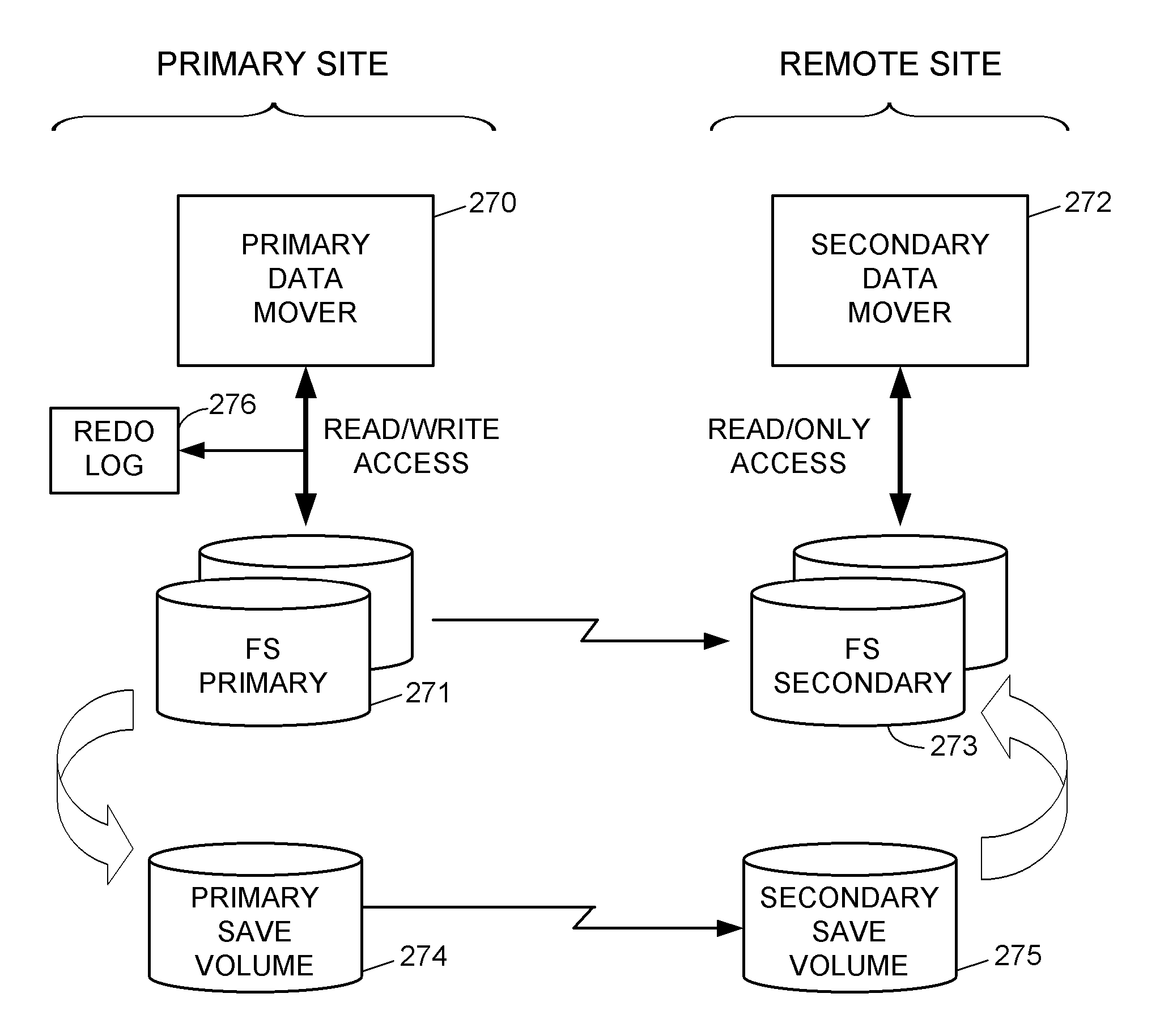
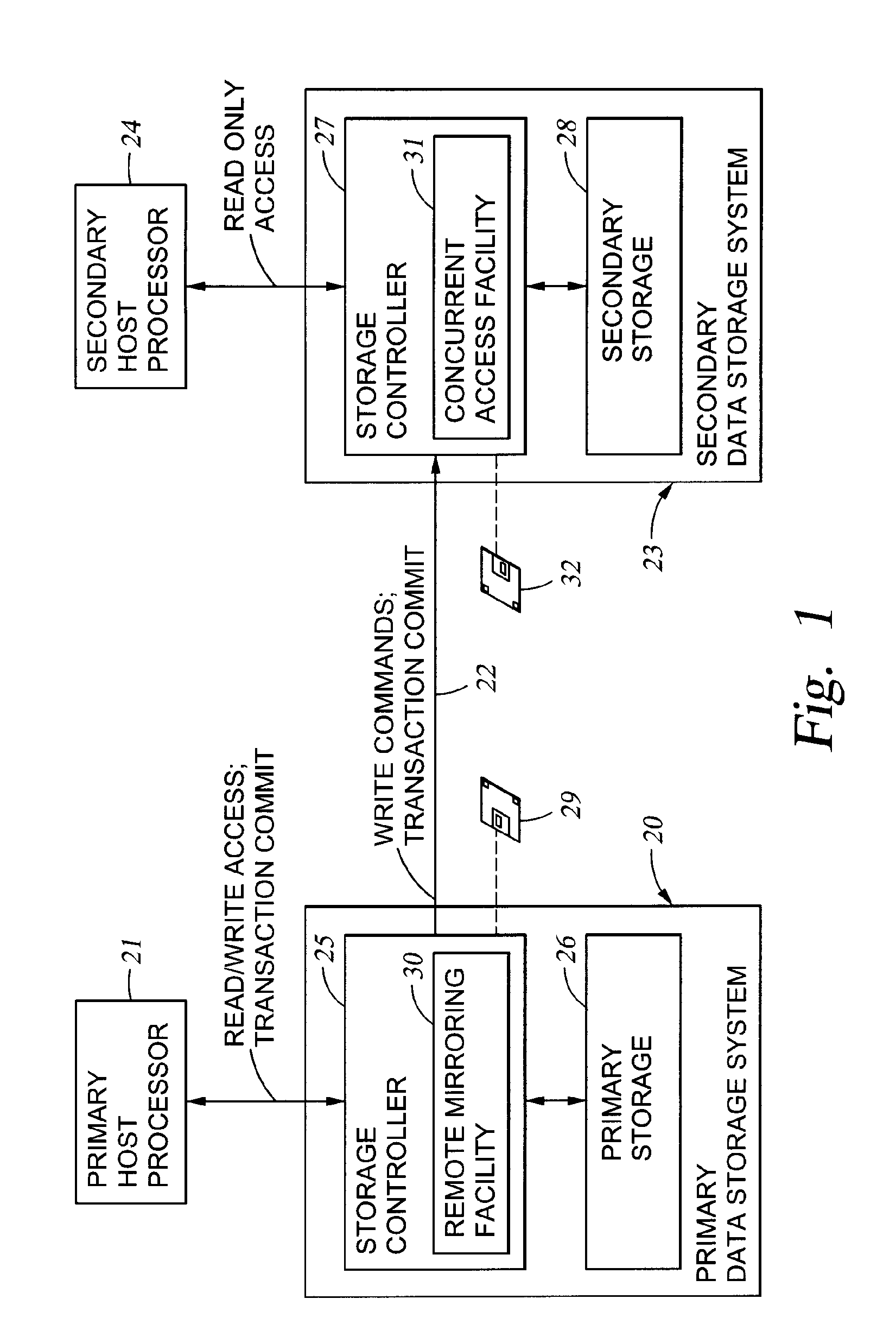
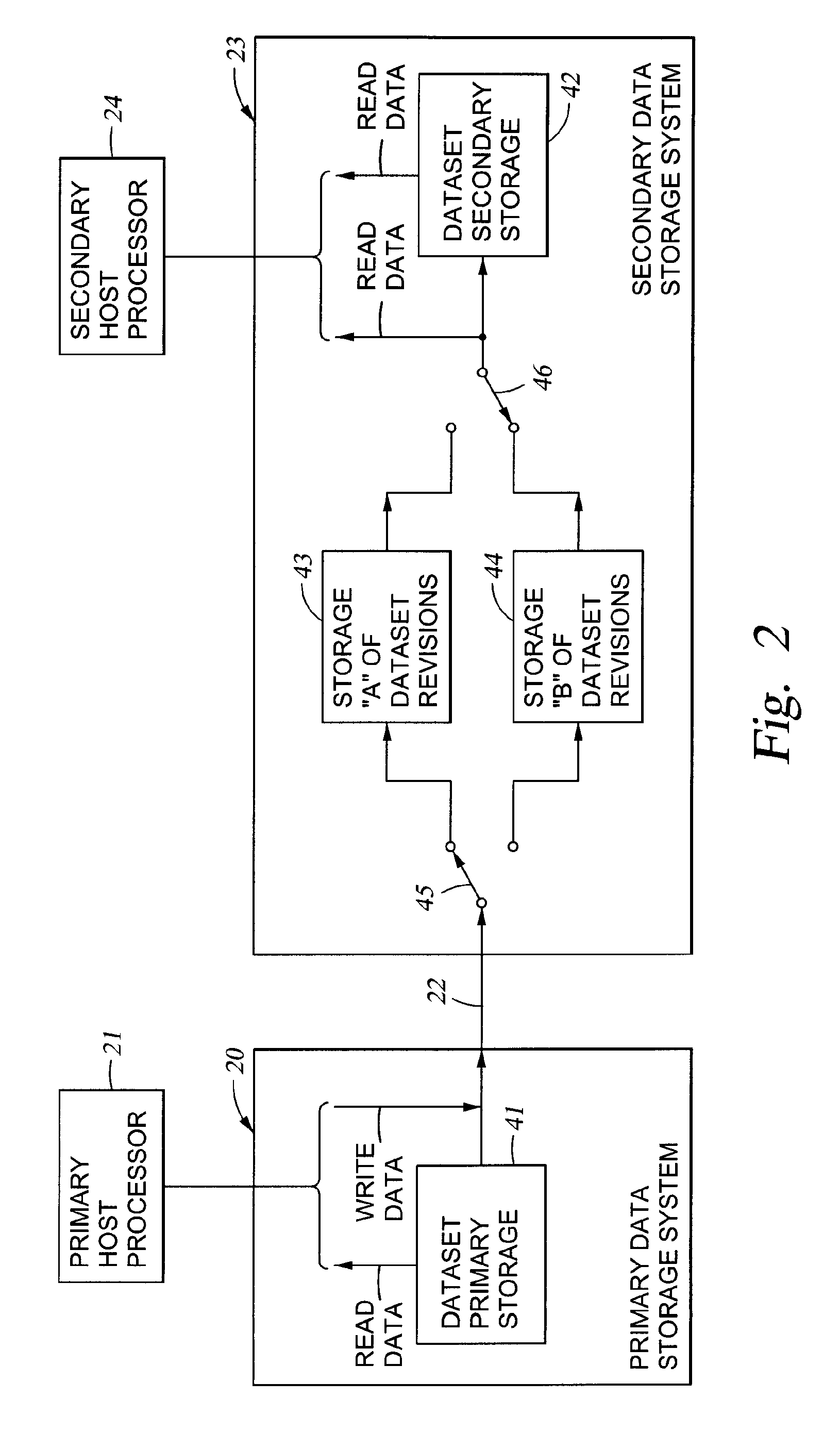
Replication of remote copy data for internet protocol (IP) transmission
ActiveUS20030217119A1Special service provision for substationError detection/correctionInternet protocol suiteRouting table
Consistent updates are made automatically over a wide-area IP network, concurrently with read-only access to the remote copies. A replication control protocol (RCP) is layered over TCP / IP providing the capability for a remote site to replicate and rebroadcast blocks of the remote copy data to specified groups of destinations, as configured in a routing table. A volume multicast layer over RCP provides for multicasting to specified volume extents of the blocks. The blocks are copied at the logical level, so that it does not matter what physical structure is used for storing the remote copies. Save volumes buffer the remote copy data transmitted between the primary or secondary file system volume and the IP network, in order to ensure independence between the replication process, the IP transport method, and the primary file system being replicated.
Owner:EMC IP HLDG CO LLC
Method of implementing content-centric network (CCN) using internet protocol (IP)-based network in gateway, and gateway
ActiveUS20130173822A1Multiple digital computer combinationsNetwork connectionsInternet protocol suiteTTEthernet
A method of implementing a Content-Centric Network (CCN) using an Internet Protocol (IP)-based network, and a gateway that may implement such a method, are provided. A method of implementing a CCN using an IP-based network may involve: determining an application protocol and a packet type corresponding to the application protocol of an IP-based network, the application protocol being included in an IP packet of an IP-based network, and generating a content name corresponding to the IP packet, based on the application protocol and the packet type.
Owner:SAMSUNG ELECTRONICS CO LTD
Method to provide dynamic internet protocol security policy service
InactiveUS6839338B1Overcome problemsWireless network protocolsRadio/inductive link selection arrangementsInternet protocol suiteForeign agent
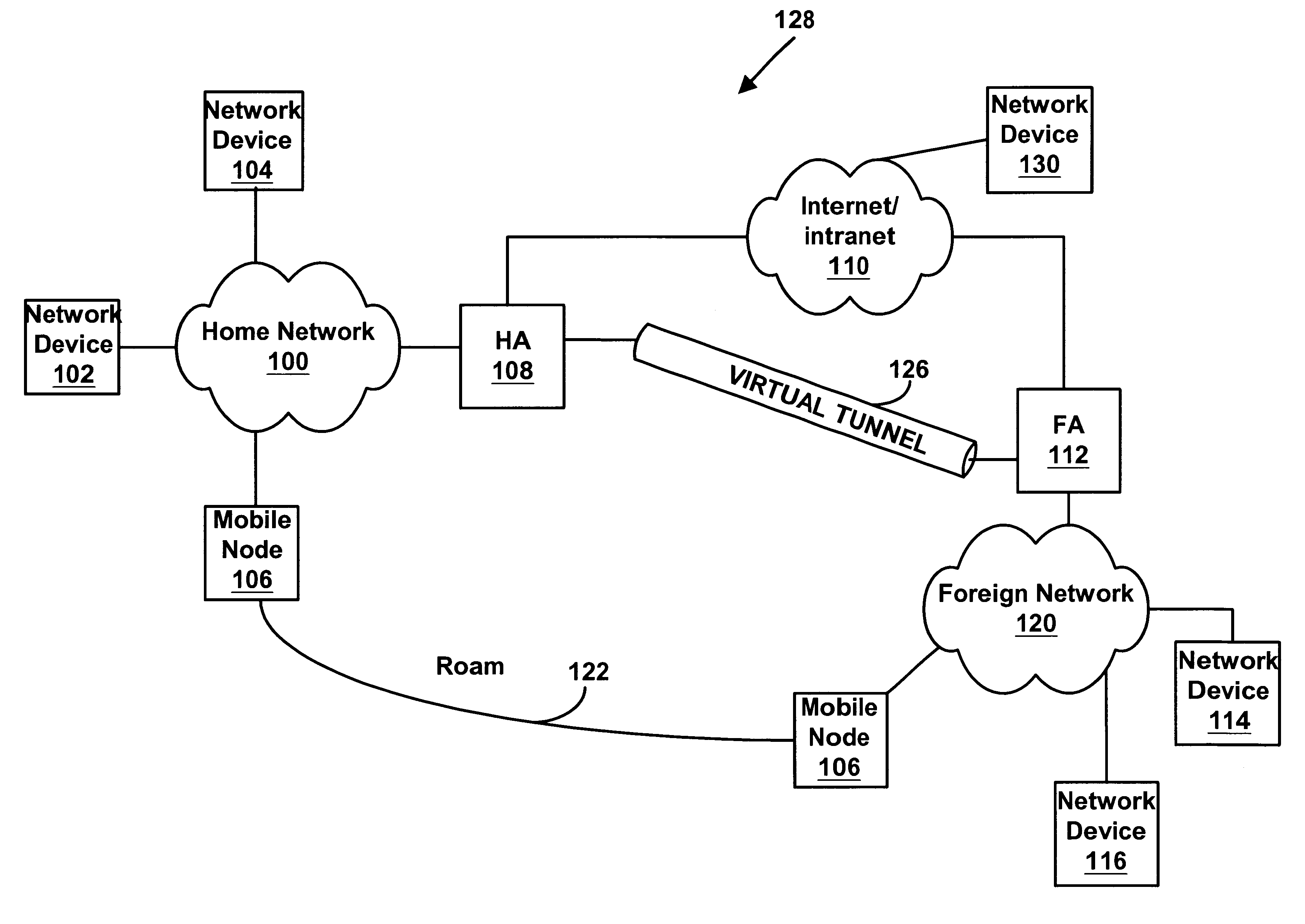
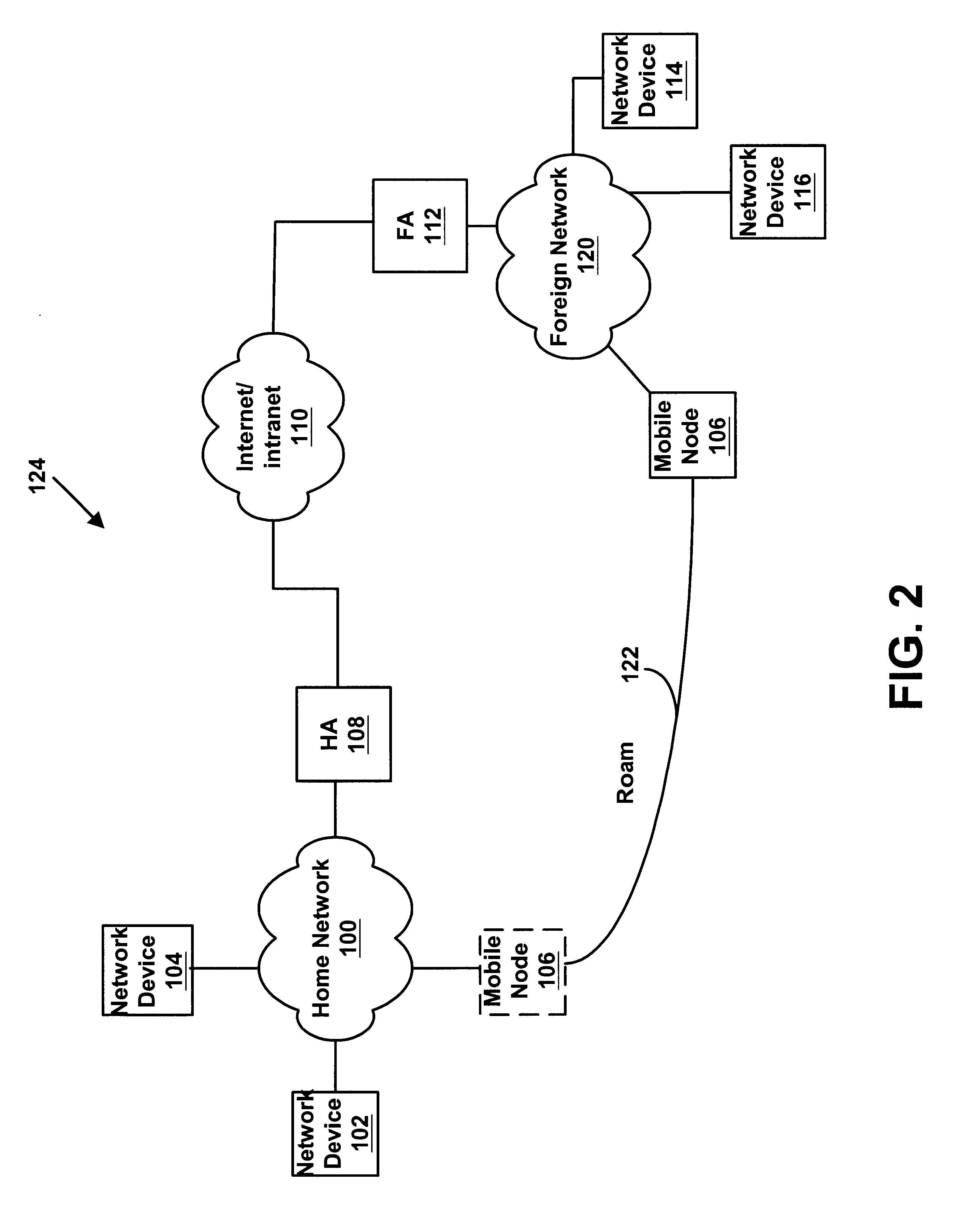
A mobile node may roam away from its home network to a foreign network. The mobile node may communicate using the Mobile Internet Protocol, and it may use Internet Protocol security to communicate with its home network. A foreign agent on the foreign network and a home agent on the home network may dynamically link a policy to be used for a Internet Protocol security session between the foreign agent and the home agent. The foreign agent and the home agent may dynamically create a filter to be used for the Internet Protocol Security session.
Owner:FORTINET
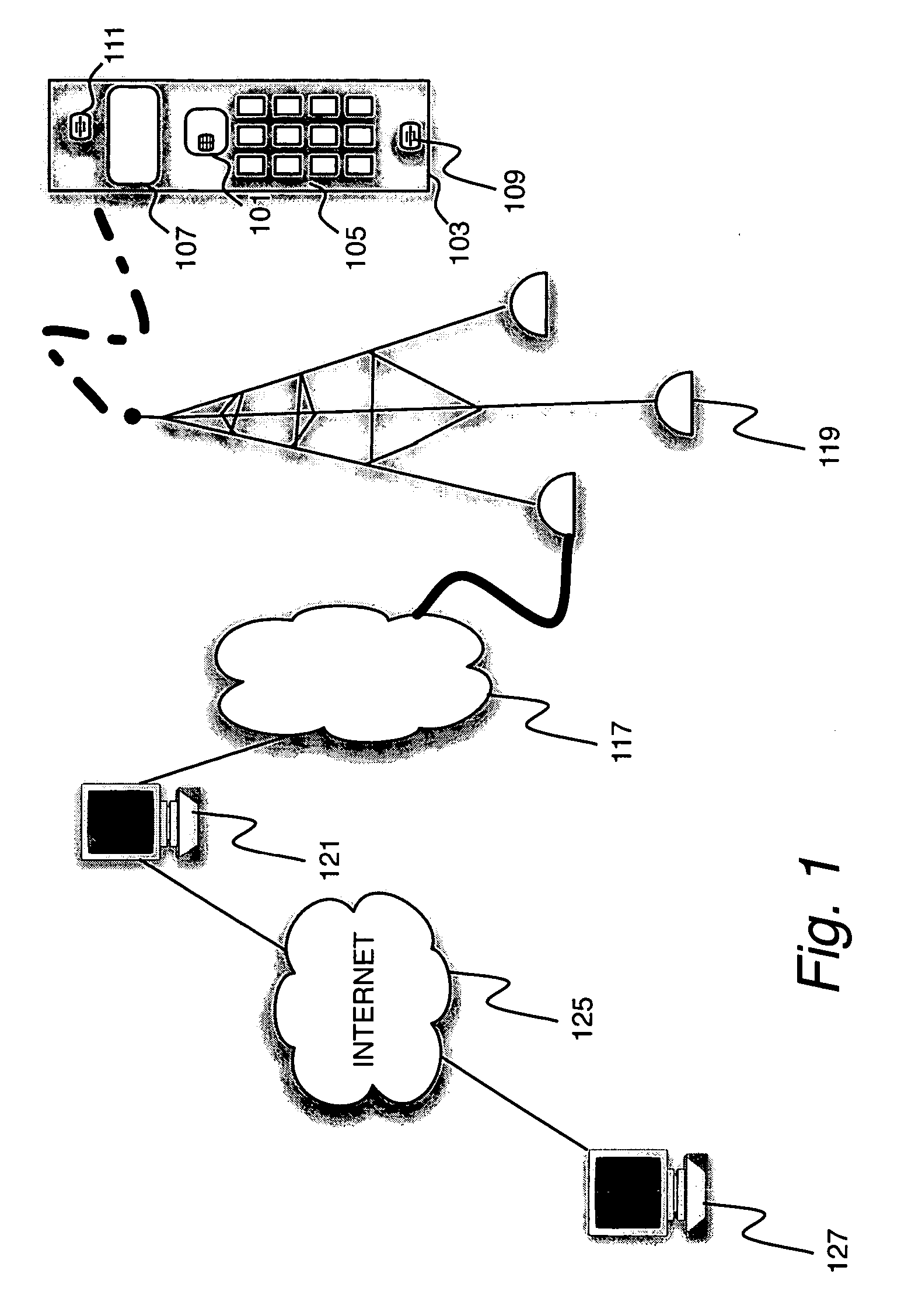
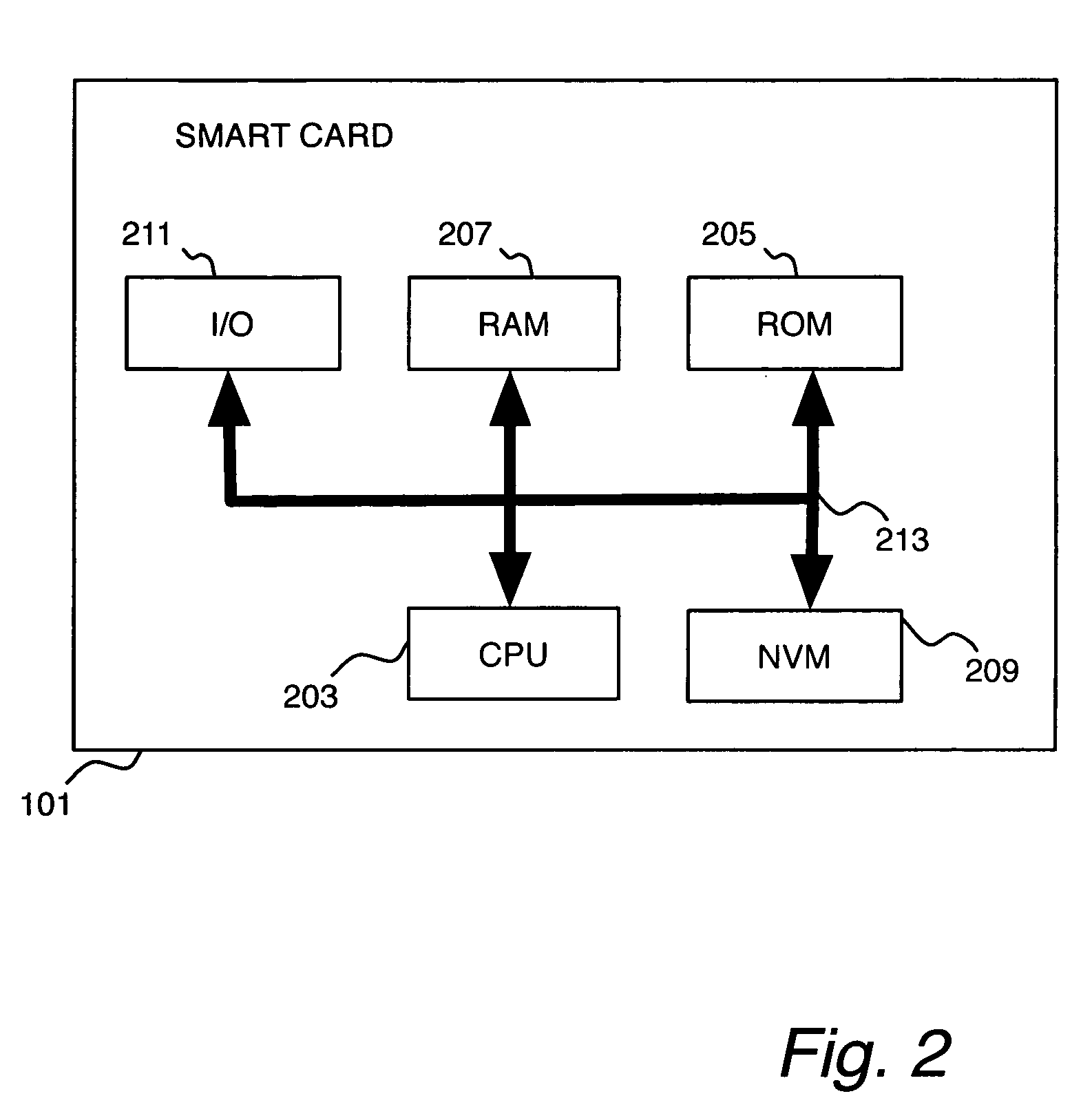
Communications of UICC in mobile devices using Internet protocols
InactiveUS20060079284A1Wireless network protocolsSubstation equipmentInternet protocol suiteWeb browser
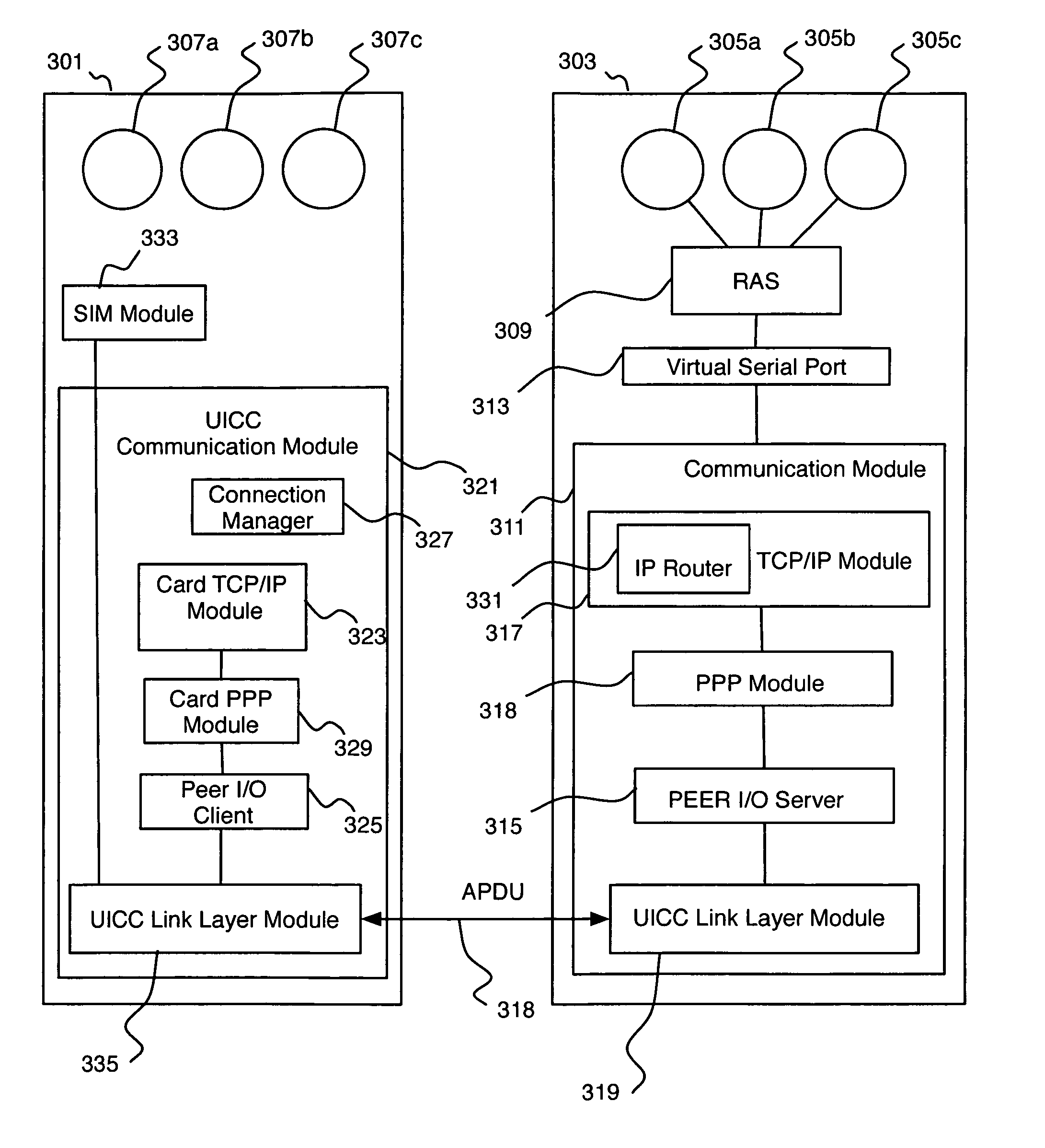
A mobile device and UICC communication using standard Internet protocols. Such communication allows users access to their UICC information using standard web browsers and allows use of the UICCs to communicate with remote servers and thereby provide secure services for Internet transactions. The mobile device has a communications module to selectively communicate with the UICC processor or with at least one node on a network, the mobile device communications module has an Internet protocol module operable to receive messages issued from a first Internet application as Internet protocol packets, and to transmit the packets to target IP addresses; and operable to receive Internet protocol packets, to process the packets, and to send the messages contained in the packets to the first Internet application.
Owner:AXALTO INC
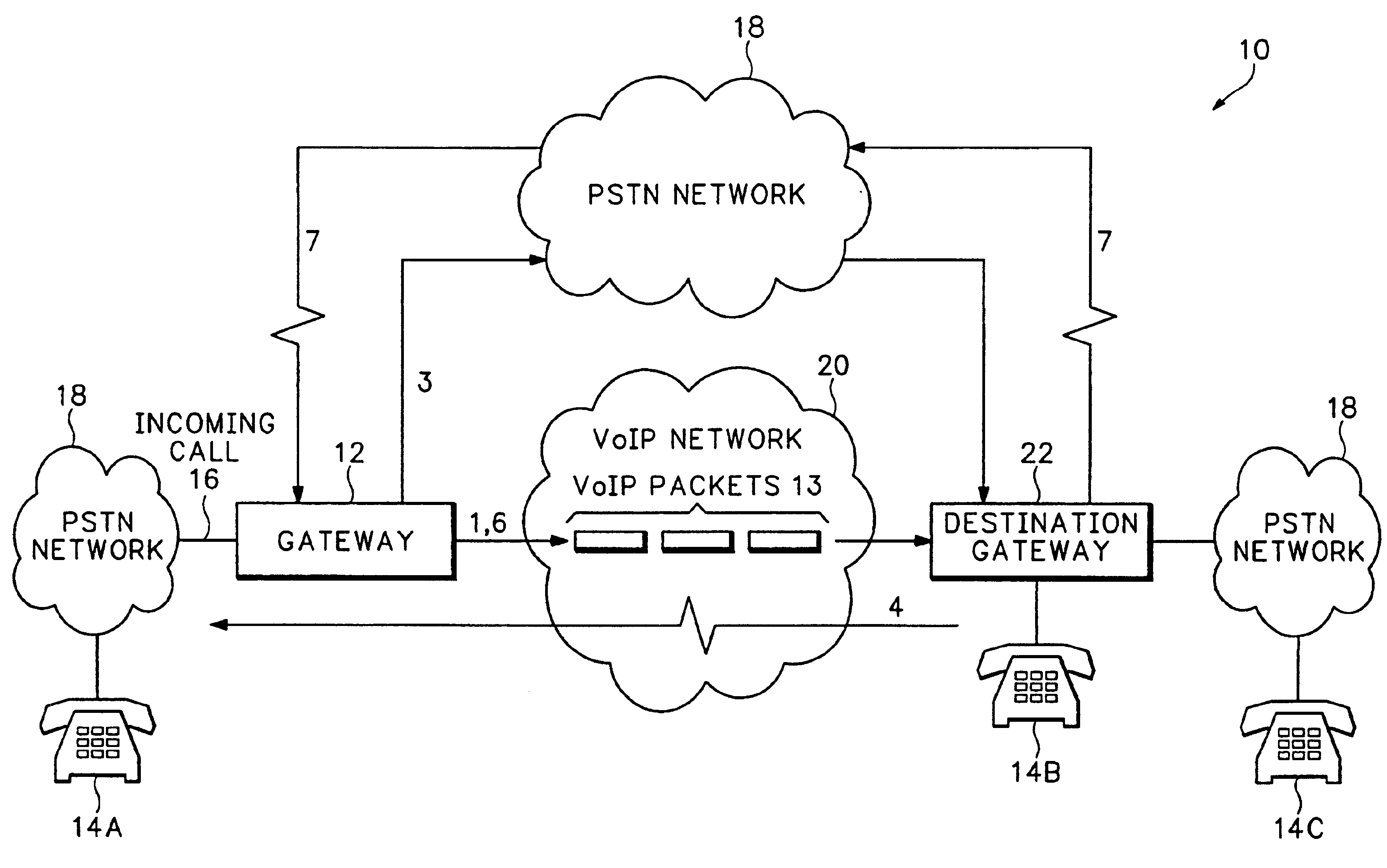
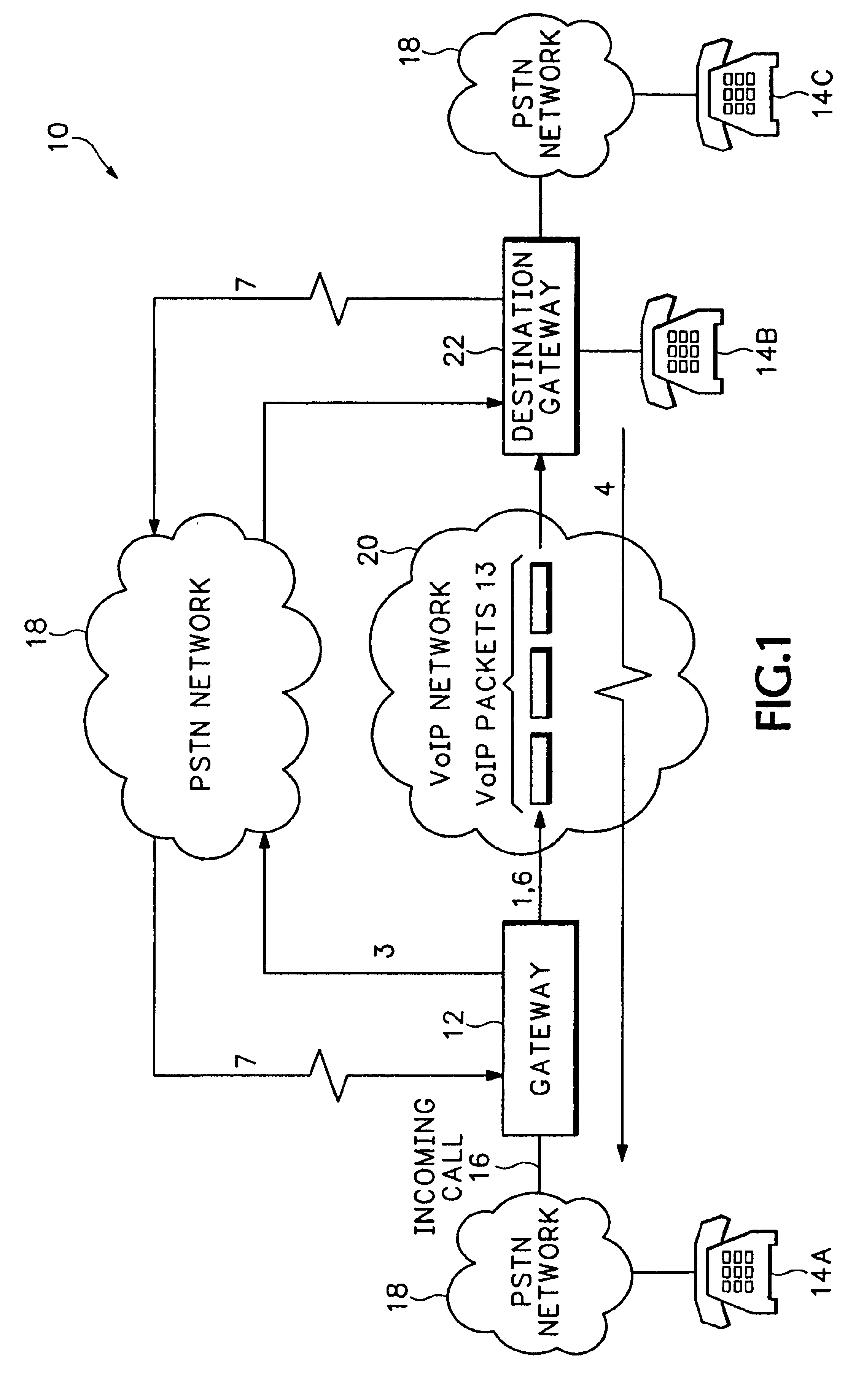
Voice over internet protocol call fallback for quality of service degradation
InactiveUS6868080B1Optimal utilization of VoIP without sacrificing the quality of the call connectionMultiplex system selection arrangementsInterconnection arrangementsInternet protocol suiteCall termination
The invention provides a way to fallback to a PSTN call at any time during a VoIP call when Quality of Service in a VoIP network falls below some acceptable level. The PSTN fallback calls can be retrieved “midcall” and rerouted back over the VoIP network. This provides optimal utilization of VoIP without sacrificing the quality of the call connection. Calls are cheaper because PSTN fallback calls are only established temporarily for the amount of time that the QoS problem exists on the VoIP network. Call fallback is conducted in a VoIP gateway by first receiving an incoming call. A Voice over IP (VoIP) call is established for the incoming call over the VoIP network. VoIP packets are encoded from the voice signals in the incoming call and sent over the VoIP network. Quality of service of the VoIP network is monitored during the VoIP call and a fallback call is setup over a PSTN network at any time during the VoIP call when the monitored quality of service of the VoIP network degrades. For a time the voice signals from the incoming call are cross connected to both the output for the fallback call and the output for the VoIP call. When a destination gateway starts receiving the voice signals from the fallback call, the VoIP call is dropped. The quality of service on the VoIP network continues to be monitored during the fallback call. A new VoIP call will be reestablished over the VoIP network during the fallback call when the quality of service of the VoIP network improves. Voice from the incoming call is for a time again cross connected to both the fallback call and the new VoIP call. After the destination gateway starts receiving audio packets again over the new VoIP call, the PSTN fallback call is terminated.
Owner:CISCO TECH INC
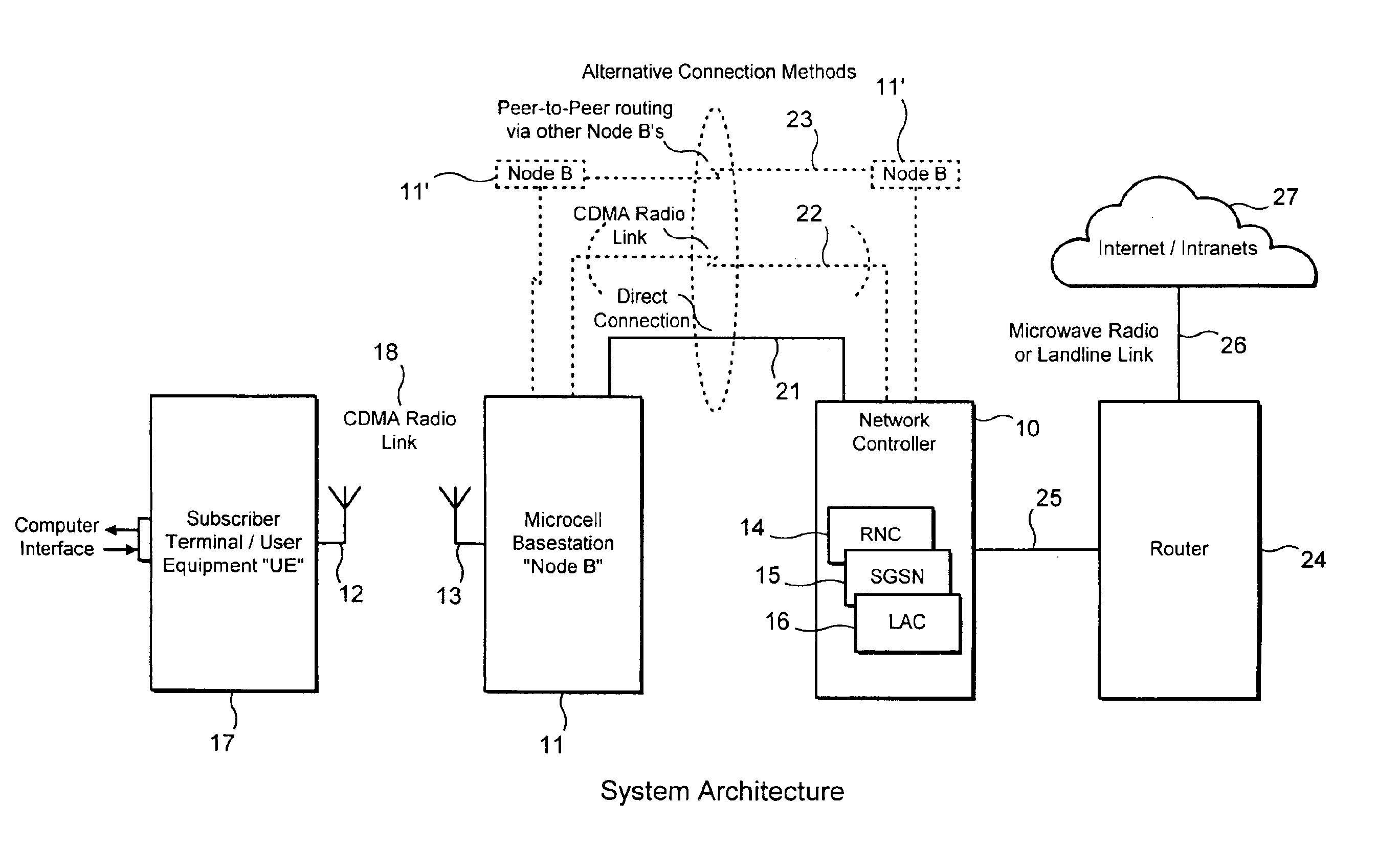
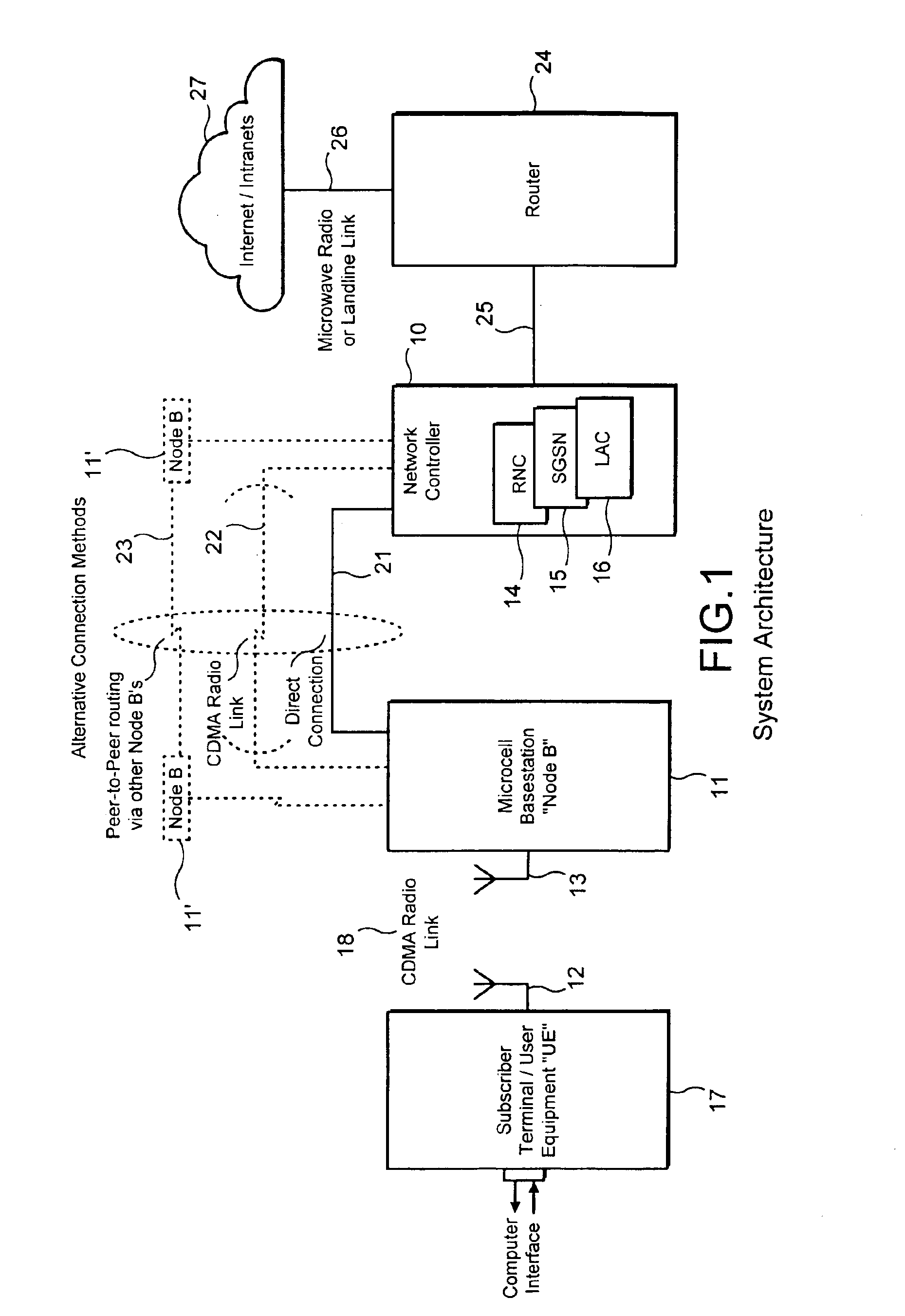
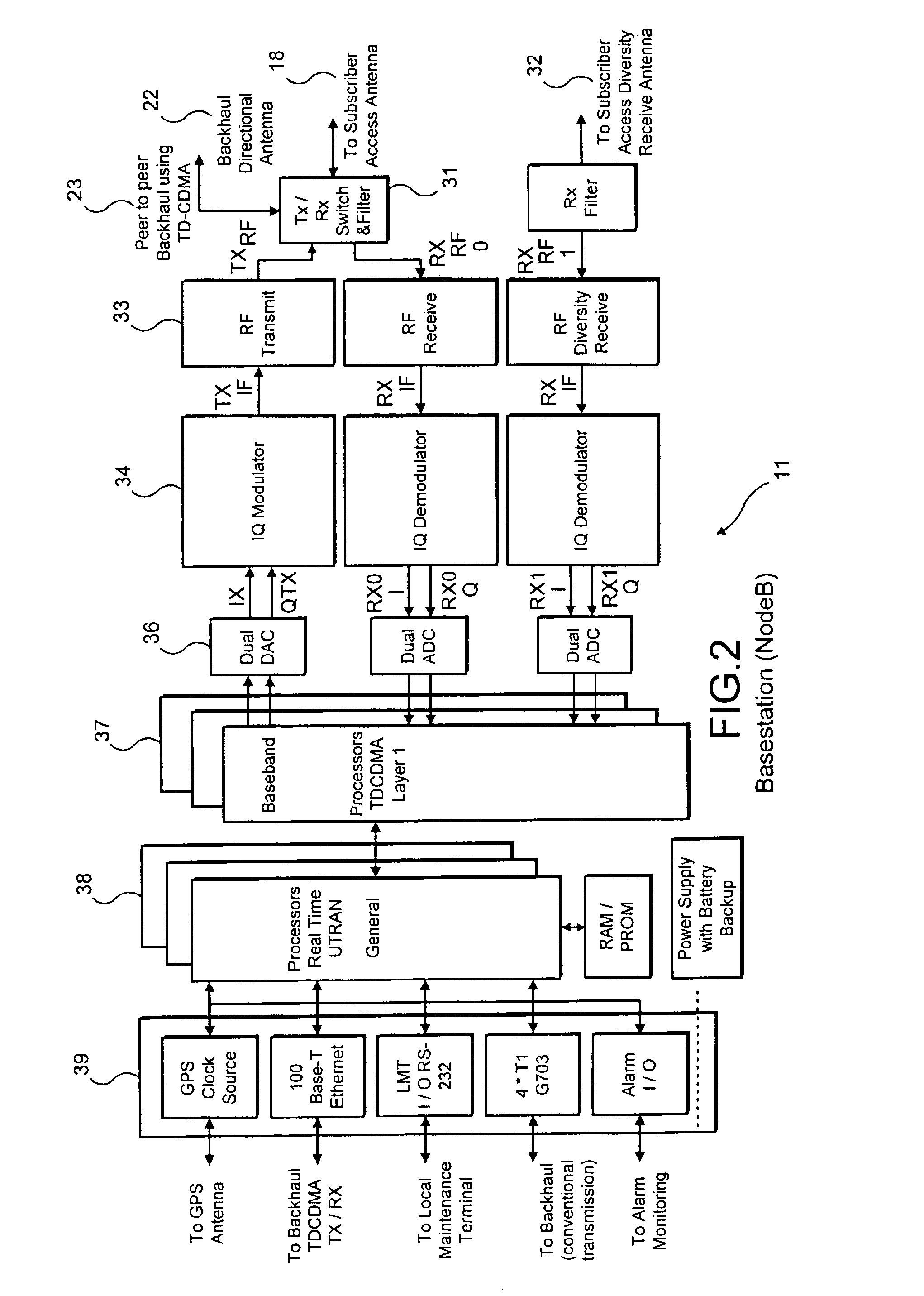
Cellular wireless internet access system using spread spectrum and internet protocol
InactiveUS6865169B1Reduce environmental impactOvercome lossMultiplex communicationNetwork topologiesTime-division multiplexingUser equipment
A cellular wireless internet access system which operates in the 2.5 to 2.68 GHz band and which must comply with complex government regulations on power levels, subscriber equipment and interference levels yet which provides high data rates to users and cell sizes of 1½ miles radius or more from base stations with subscriber equipment and antennas mounted indoors. Such base stations are mounted low and use spread-spectrum transmission to comply with interference rules with respect to adjacent license areas. An unidirectional tear-drop coverage pattern is used at multiple cells to further reduce interference when required. Time division duplex is used to allow the system to operate on any single channel of varying bandwidth within the 2.5 to 2.68 GHz band. Backhaul transmission from base stations to the Internet is provided using base station radio equipment, operating either on a different frequency in the band or on the same frequency using a time-division peer-to-peer technique. Different effective data-rates are provided by a prioritization tiering technique.
Owner:NVIDIA CORP
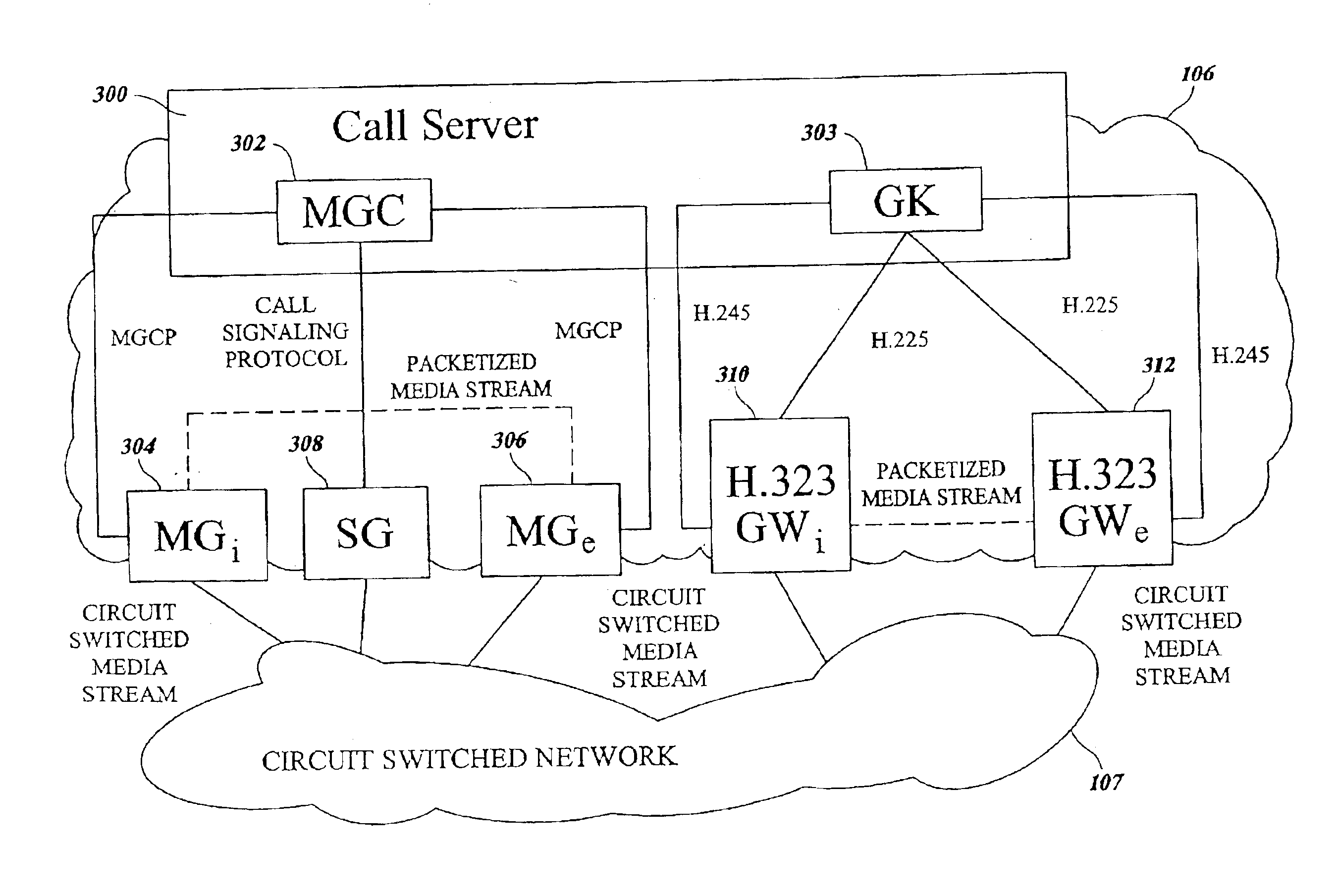
Method and apparatus for interworking between internet protocol (IP) telephony protocols
InactiveUS6885658B1Interconnection arrangementsTime-division multiplexInternet protocol suiteTTEthernet
A method and an apparatus for interworking between internet protocol (IP) telephony protocols includes a call server. The call server includes a first protocol agent for communicating with a first protocol device according to a first protocol. A second protocol agent communicates with a second protocol device according to a second protocol. An interworking agent provides functions usable by the first and second protocol agents to communicate with each other according to a third protocol. The third protocol is a superset of functions provided by the first and second protocols.
Owner:GENBAND US LLC
Method and system for locating a voice over internet protocol (VoIP) device connected to a network
ActiveUS20060056388A1Low costImprove featuresSpecial service for subscribersConnection managementInternet protocol suitePhysical address
A method and system for locating a device connected to a network by determining a current network address for the device and comparing the current network address to a network address in a user profile. If the network addresses match, the device is located based on a physical address associated with the network address in the user profile.
Owner:COMCAST CABLE COMM LLC
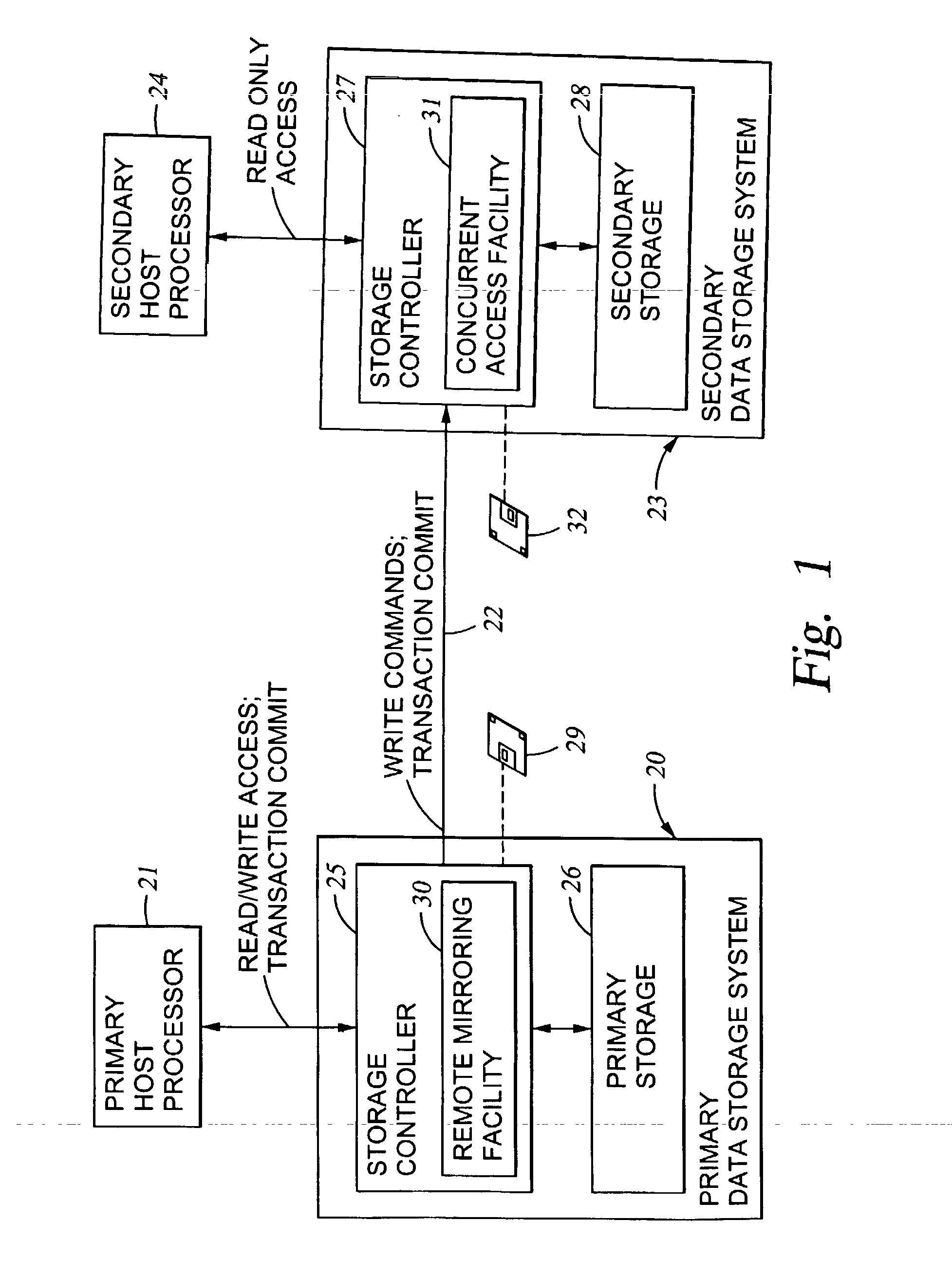
Replication of remote copy data for internet protocol (IP) transmission
ActiveUS7546364B2Special service provision for substationDigital computer detailsInternet protocol suiteRouting table
Owner:EMC IP HLDG CO LLC
Internet protocol (IP) phone with search and advertising capability
InactiveUS7525955B2Data switching by path configurationMultiple digital computer combinationsInternet protocol suitePlain old telephone system
A software platform in an Internet Protocol (IP) phone having the ability to be used with different communication infrastructures such as broadband, wireless communication and Plain Old Telephone System (POTS) service. Further, the software platform in the IP phone has the ability to be used with different applications operating on the IP phone. Further, the IP phone has the ability to perform additional functionality than traditional Public Switched Telephone Network (PSTN) phones, such as searches and advertising, given its ability to converge voice and data within a single terminal.
Owner:H W TECH L C
Congestion control for internet protocol storage
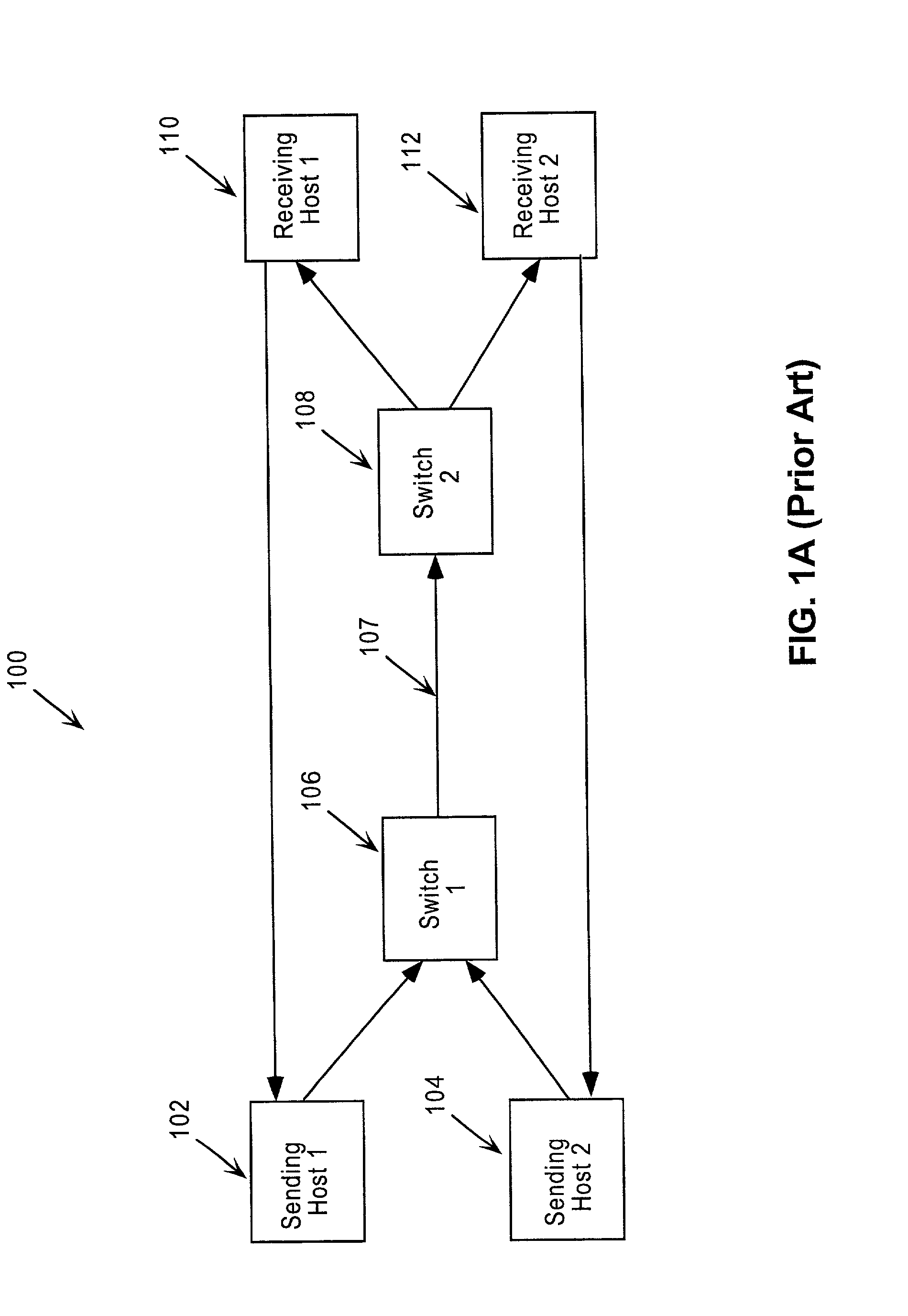
InactiveUS20010032269A1Energy efficient ICTMultiple digital computer combinationsNetworked systemThroughput
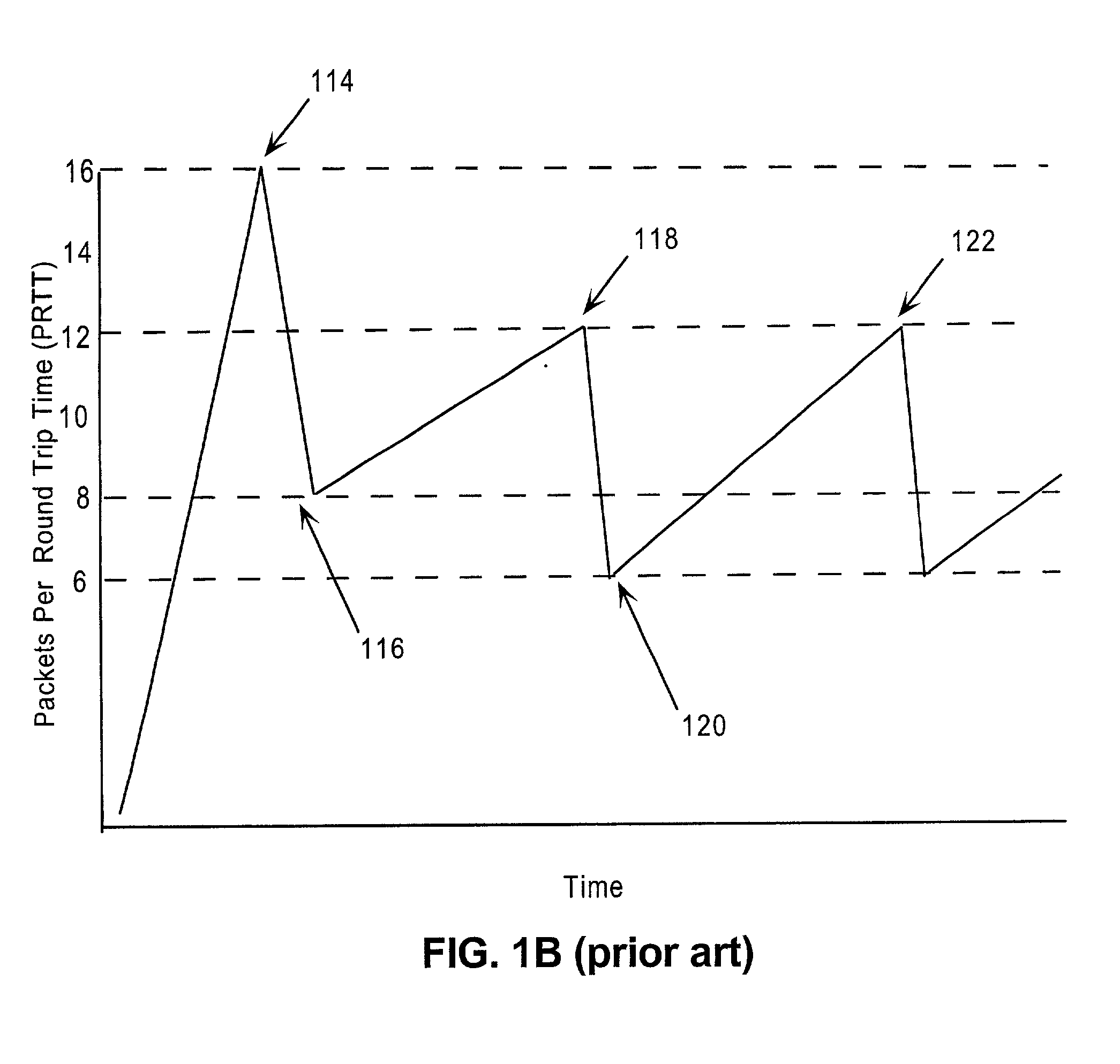
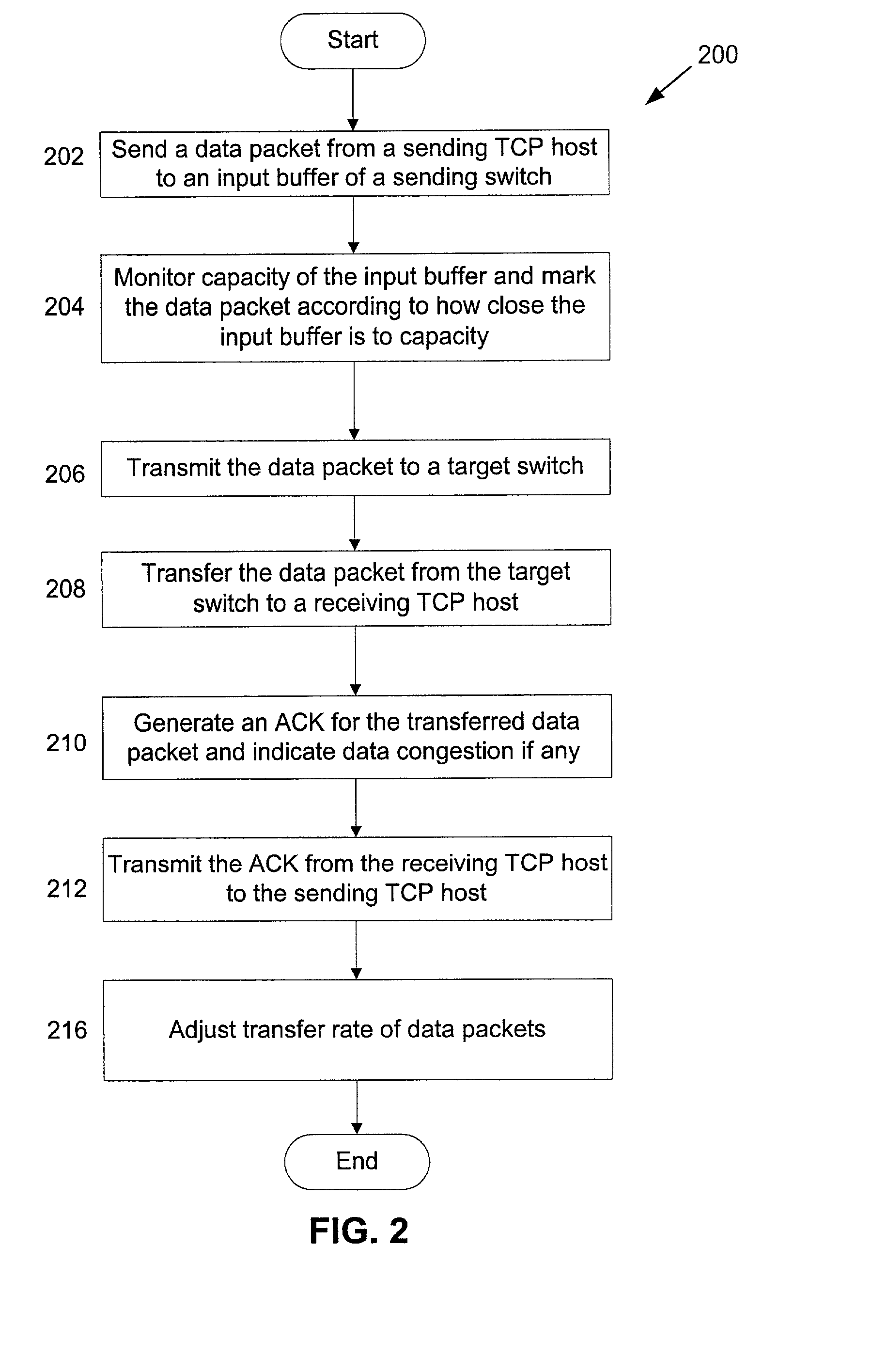
A network system for actively controlling congestion to optimize throughput is provided. The network system includes a sending host which is configured to send packet traffic at a set rate. The network system also includes a sending switch for receiving the packet traffic. The sending switch includes an input buffer for receiving the packet traffic at the set rate where the input buffer is actively monitored to ascertain a capacity level. The sending switch also includes code for setting a probability factor that is correlated to the capacity level where the probability factor increases as the capacity level increases and decreases as the capacity level decreases. The sending switch also has code for randomly generating a value where the value is indicative of whether packets being sent by the sending switch are to be marked with a congestion indicator. The sending switch also includes transmit code that forwards the packet traffic out of the sending switch where the packet traffic includes one of marked packets and unmarked packets. The network system also has a receiving end which is the recipient of the packet traffic and also generates acknowledgment packets back to the sending host where the acknowledgment packets are marked with the congestion indicator when receiving marked packets and are not marked with the congestion indicator when receiving unmarked packets. In another example, the sending host is configured to monitor the acknowledgment packets and to adjust the set rate based on whether the acknowledgment packets are marked with the congestion indicator. In a further example, the set rate is decreased every time one of the marked packets is detected and increased when no marked packets are detected per round trip time (PRTT).
Owner:ADAPTEC +1
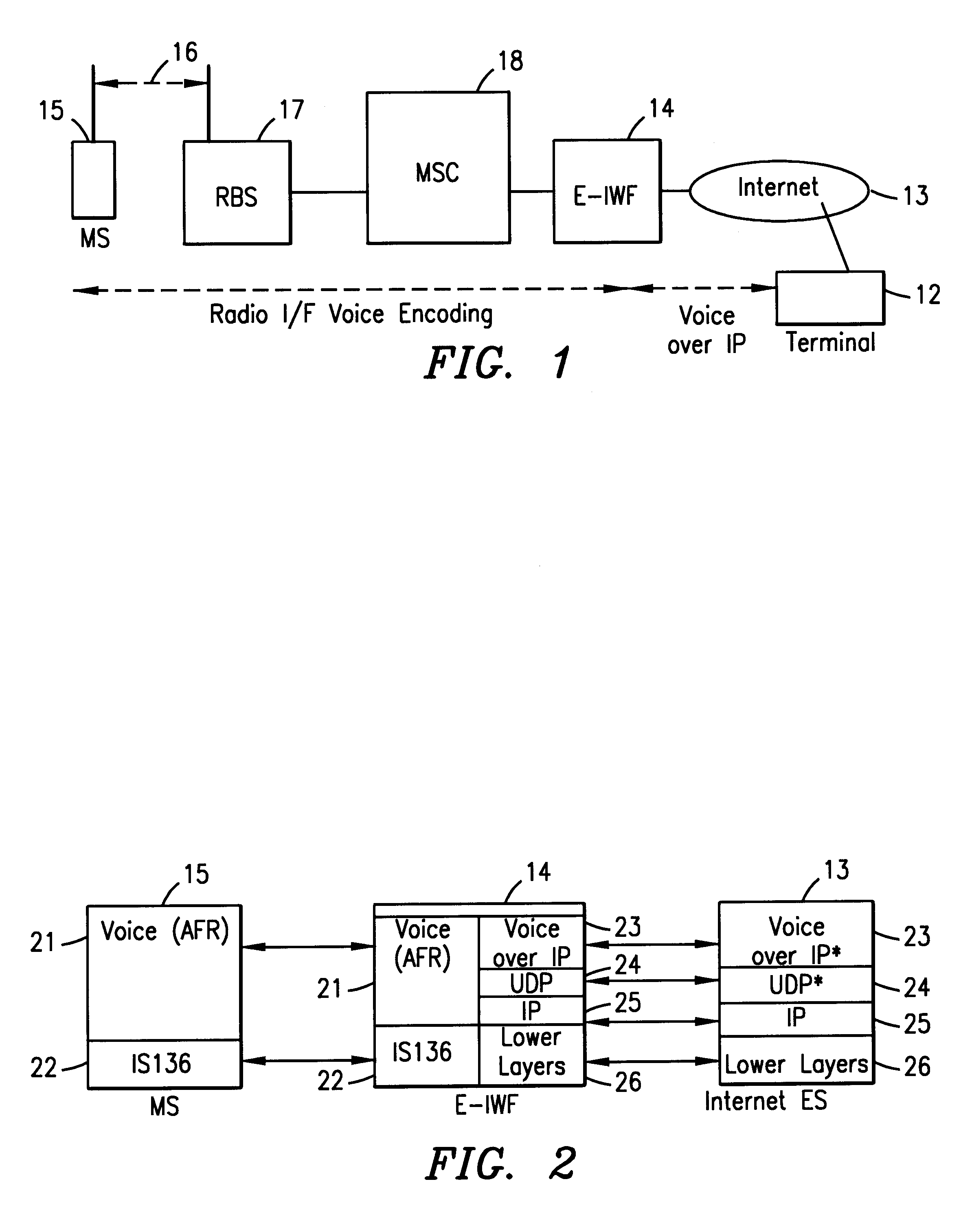
Enhanced interworking function for interfacing digital cellular voice and fax protocols and internet protocols
Owner:TELEFON AB LM ERICSSON (PUBL)
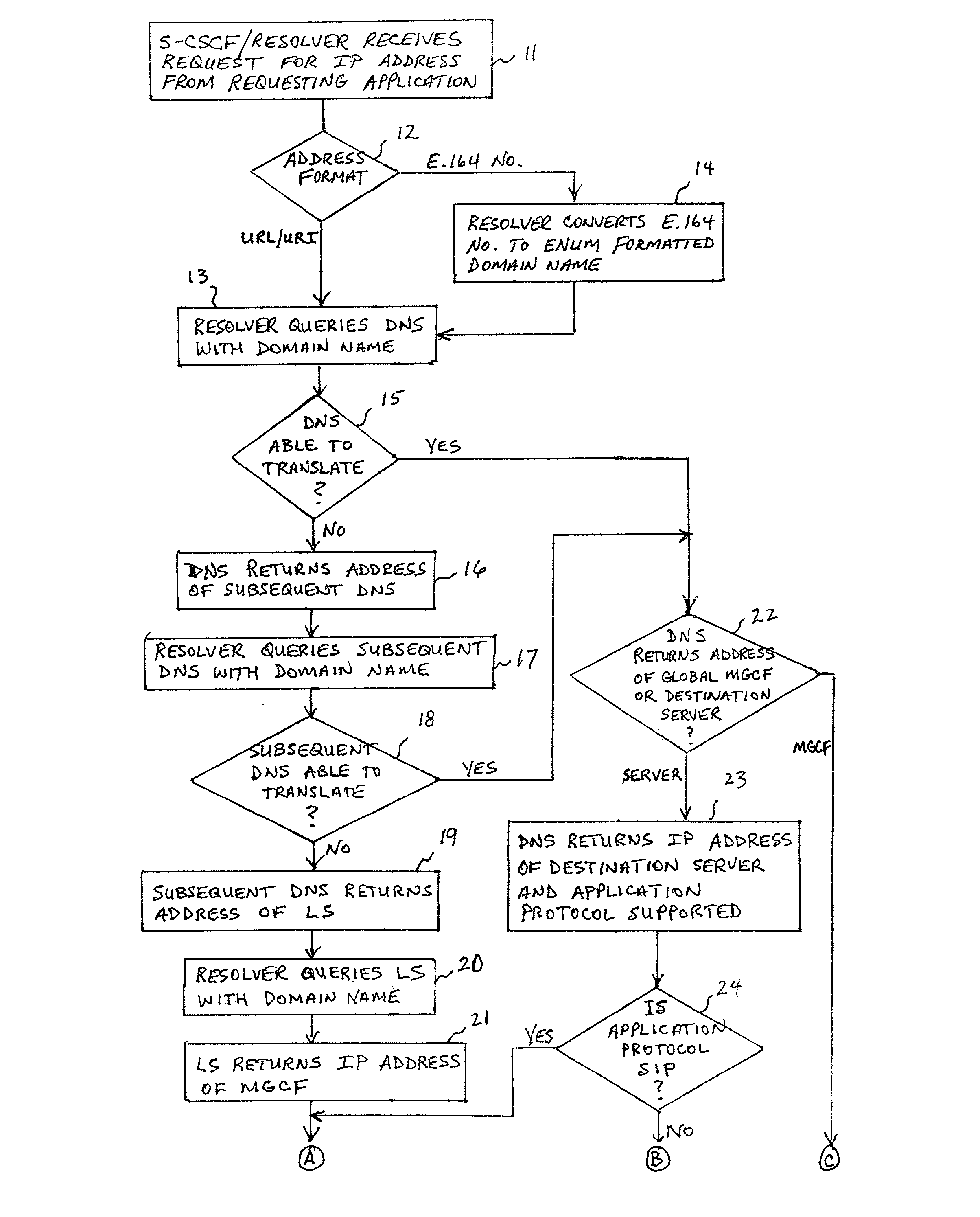
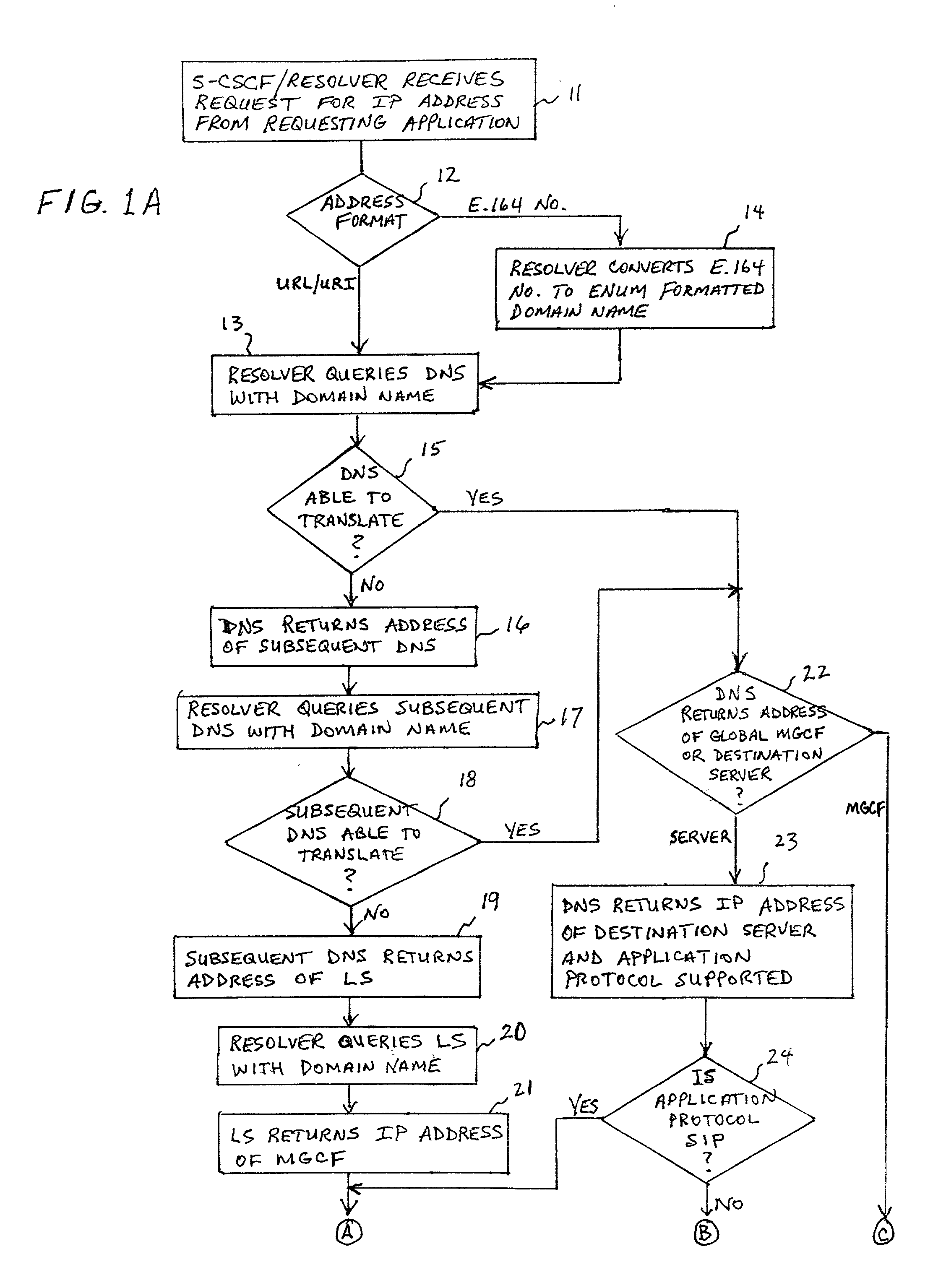
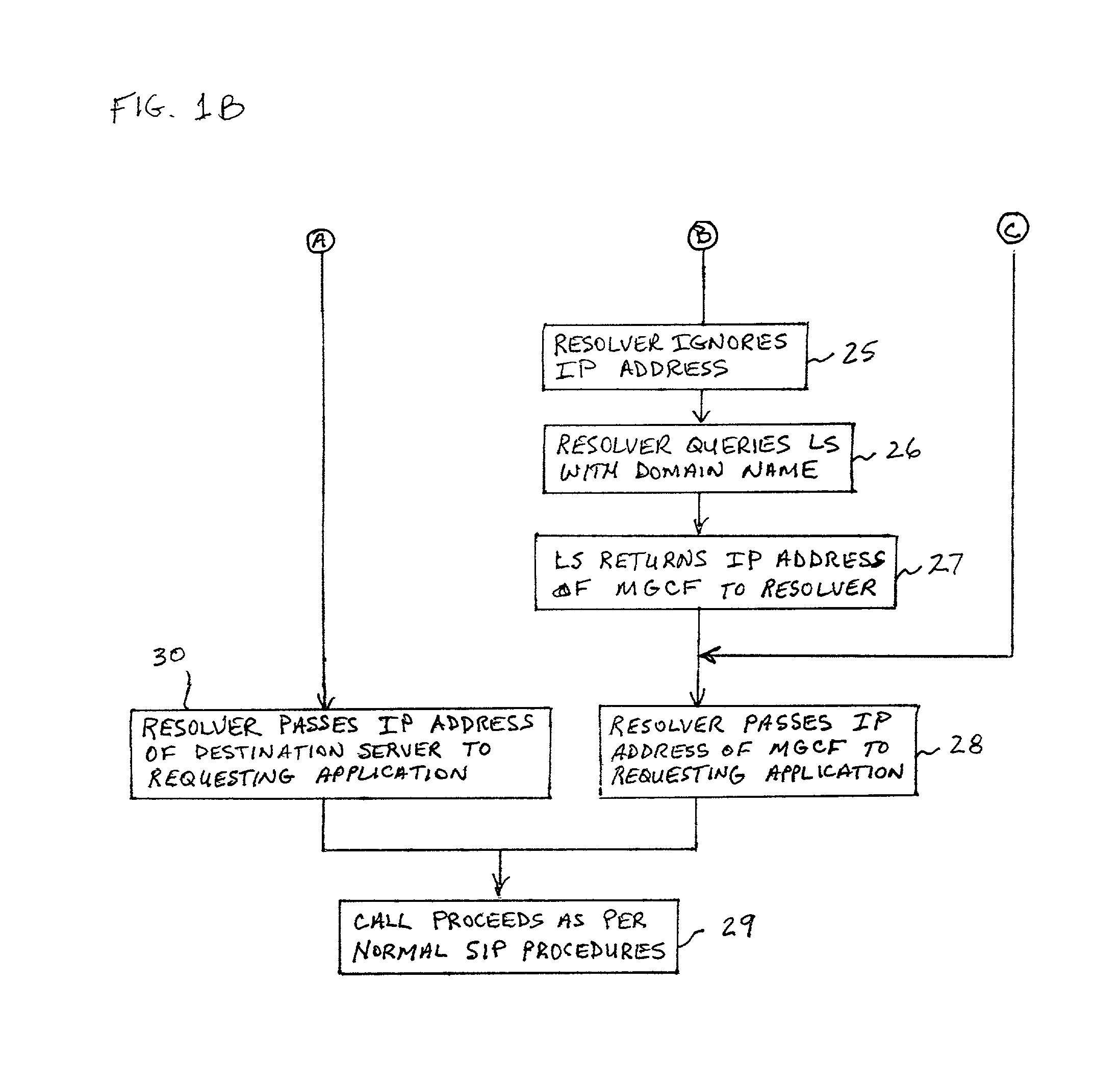
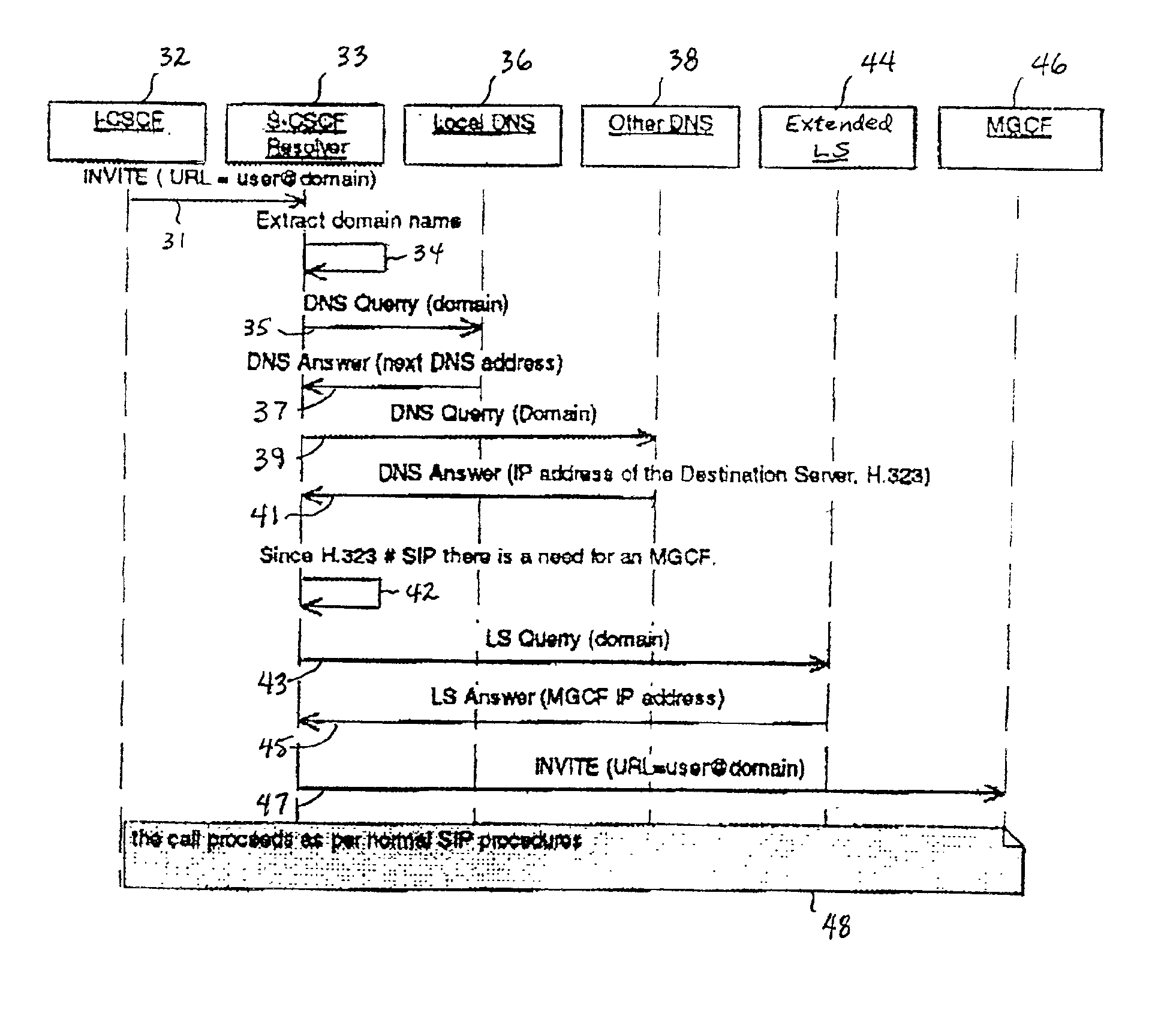
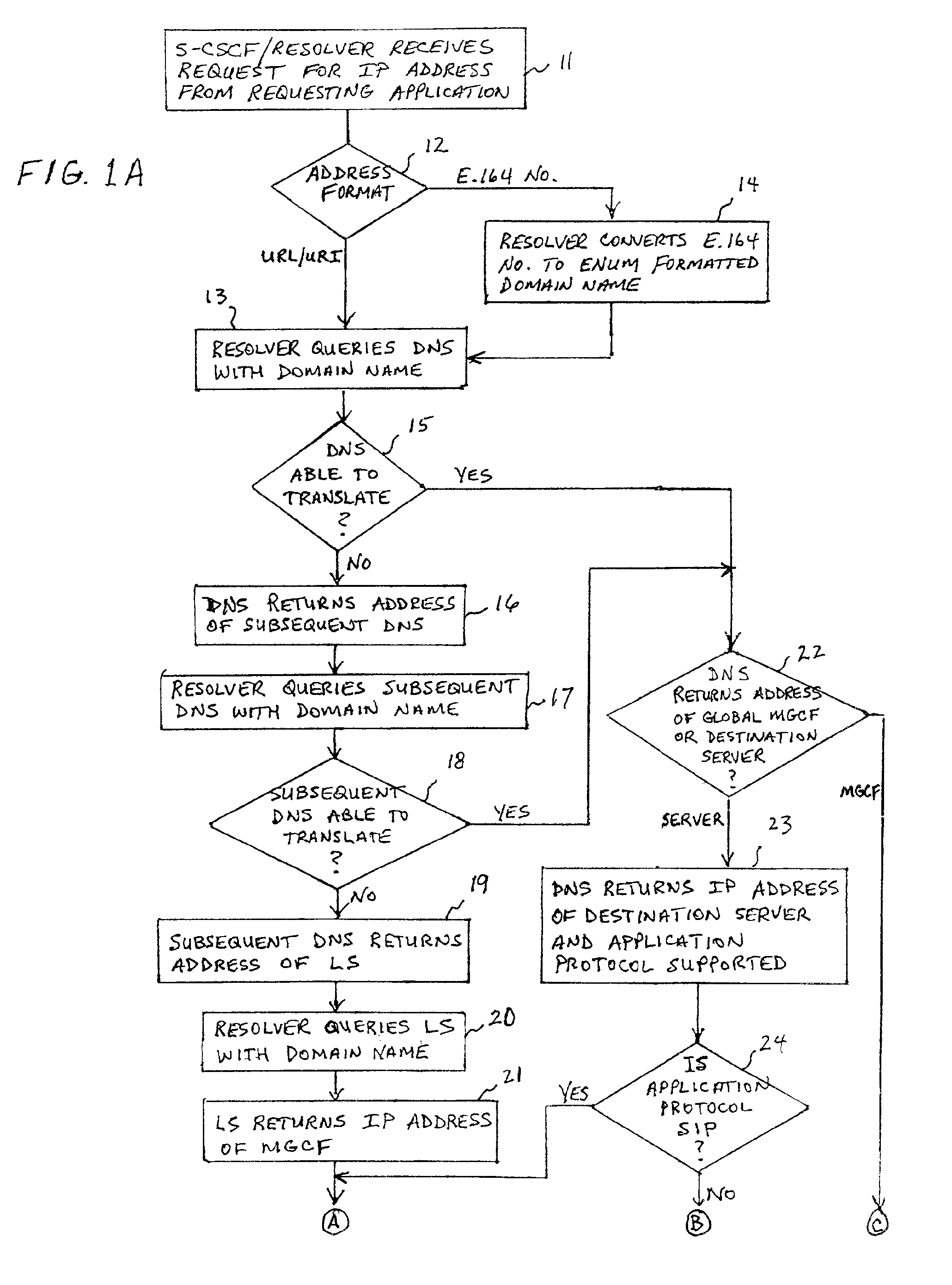
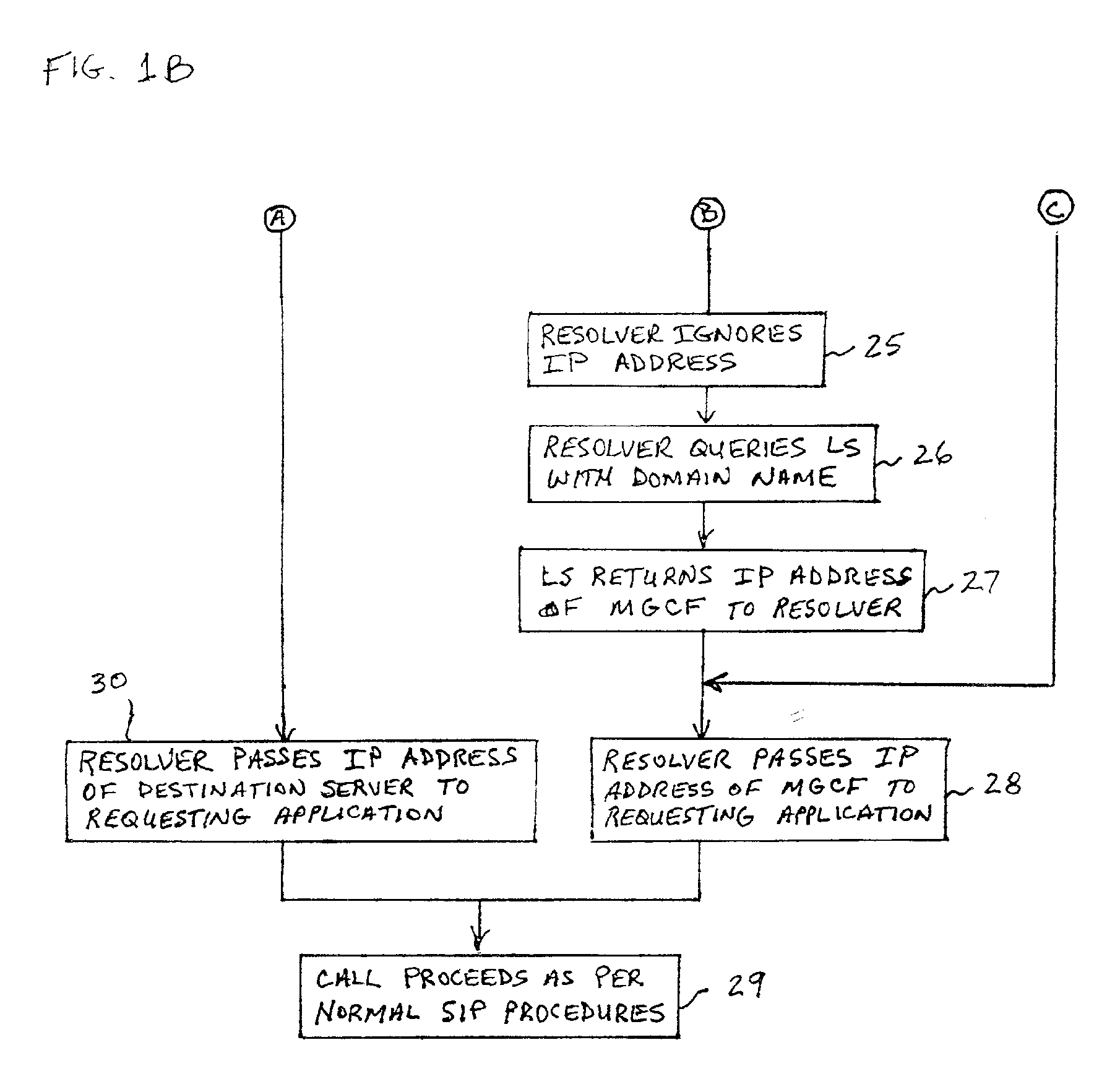
System and method for address resolution in internet protocol (IP) -based networks
ActiveUS20020027915A1Data switching by path configurationNetwork connectionsInternet protocol suiteDomain name
A system and unified method of address resolution in an IP-based network. A Resolver determines whether an input address is a URL / URI, and if so, extracts a domain name. If the input address is an E.164 number, the Resolver converts the E.164 number into a domain name in ENUM format. The Resolver then sends a domain name query to a DNS which, if able, returns the IP address for either a Global MGCF or a destination server along with a supported Application protocol. If the DNS is unable to perform the translation, or the Application protocol returned is not supported by the requesting application, the Resolver sends a domain name query to an extended Location Server (LS) to obtain an IP address of a gateway function capable of interfacing with the destination server.
Owner:TELEFON AB LM ERICSSON (PUBL)
Authenticating endpoints of a voice over internet protocol call connection
InactiveUS6961857B1User identity/authority verificationMultiple digital computer combinationsInternet protocol suiteTimestamp
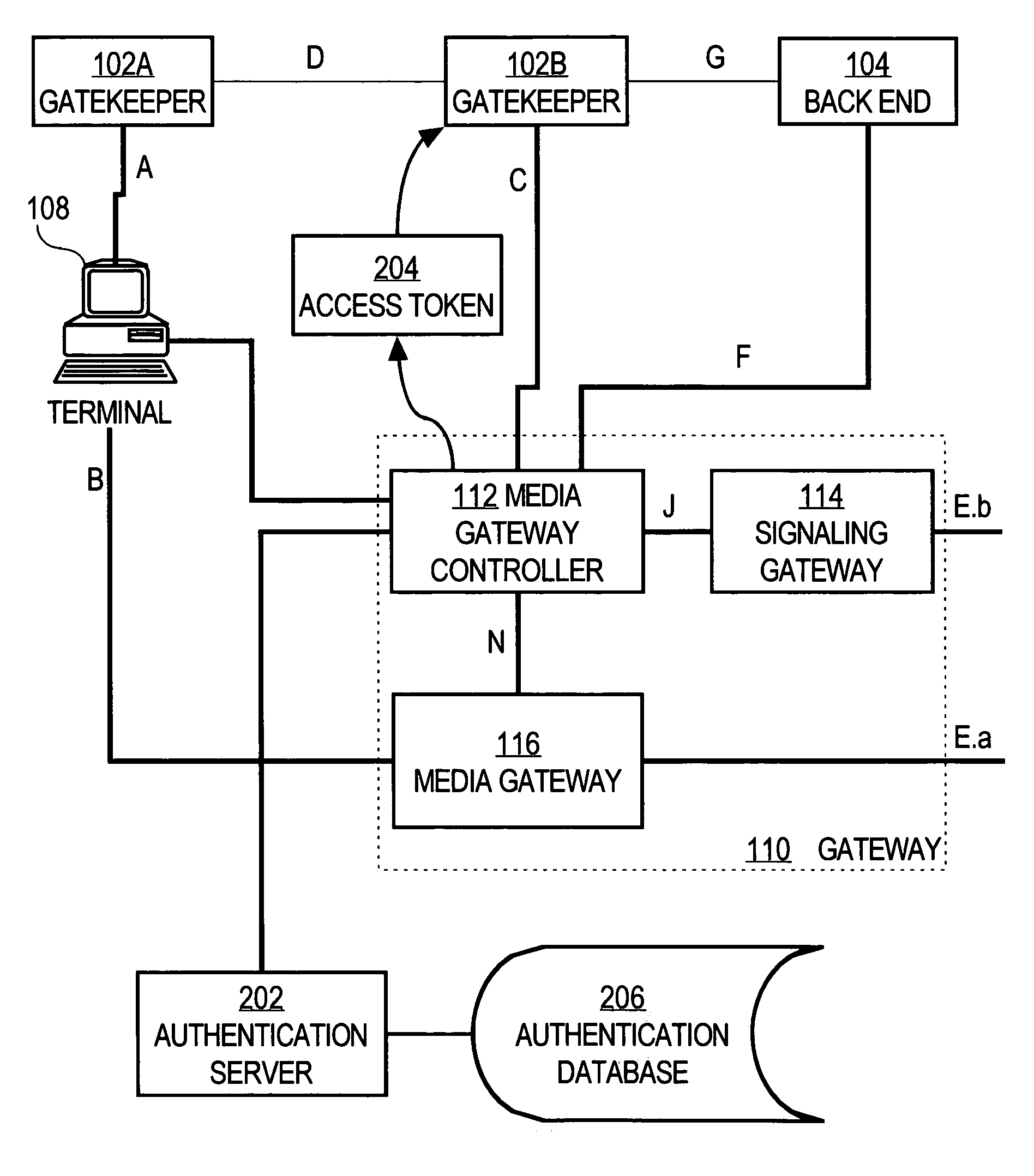
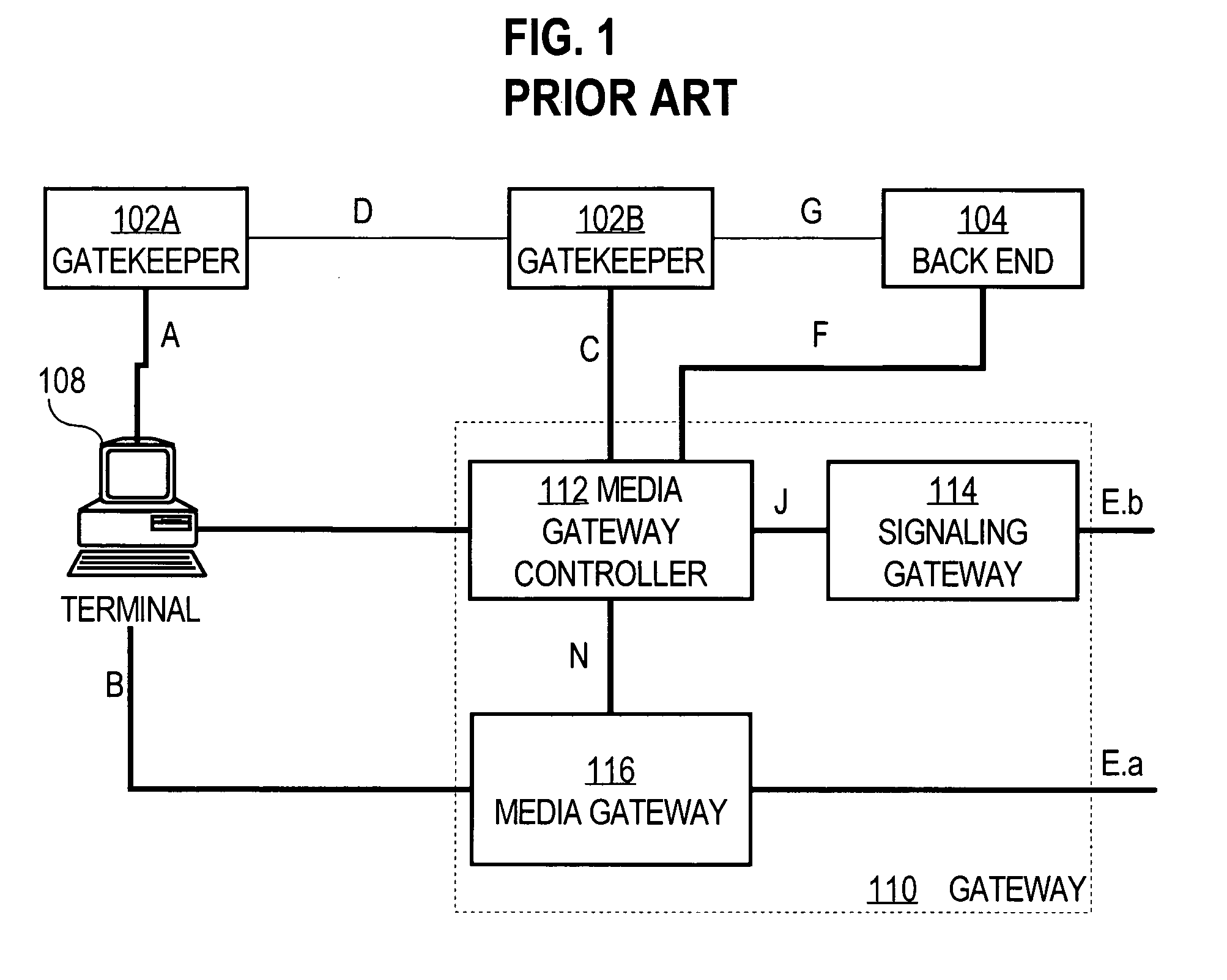
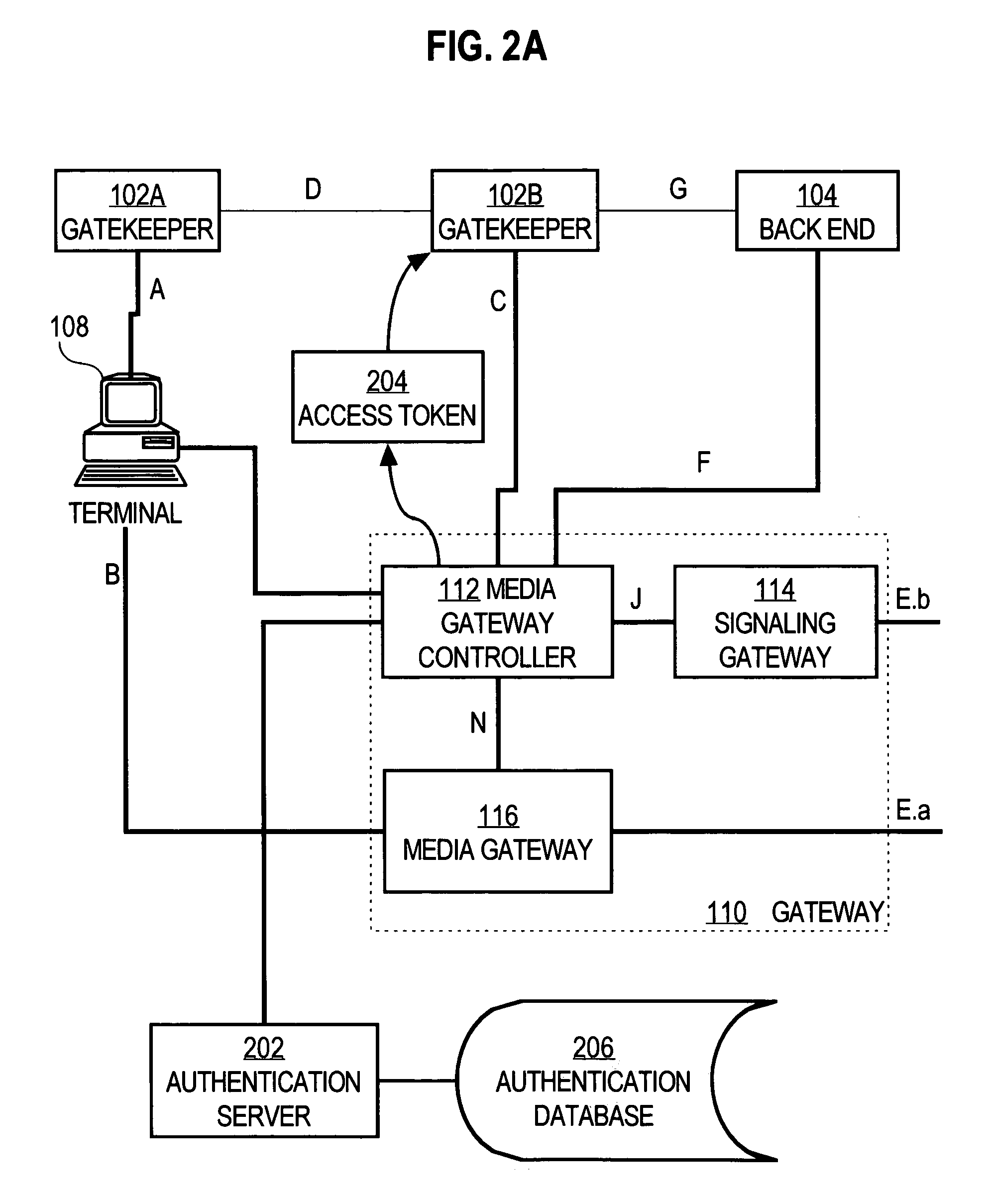
A method and apparatus for securely establishing voice over Internet Protocol calls are disclosed. In a Registration Security approach, a Gatekeeper sends an Access Token in all Registration Request messages. The Access Token contains information that authenticates the Gateway to the Gatekeeper. The Gatekeeper formats a message to an authentication server that will authenticate the information contained in the token, and the server responds with either an Access-Accept or Access-Reject message. The Gatekeeper responds to the Gateway with either a Registration Confirm message or a Registration Reject message. If a call is then placed from a successfully authenticated Gateway, that Gateway generates a new Access Token that is identical to the one generated during registration, except for the timestamp. The Gatekeeper uses the authentication server to authenticate the originating gateway, before sending the designation side Access Confirm message. As a result, a non-authenticated endpoint that knows a Gateway's address cannot use the Gateway address to circumvent security and access the telephone network to place unauthorized calls or free calls. In Admission or Per-Call Security, a Gateway is also required to include an Access Token in all originating side Admission Request messages. Such token contains information that identifies the user of the Gateway to the Gatekeeper, based on an account number and PIN obtained from the user. The Access Token is authenticated in the manner described above.
Owner:CISCO TECH INC
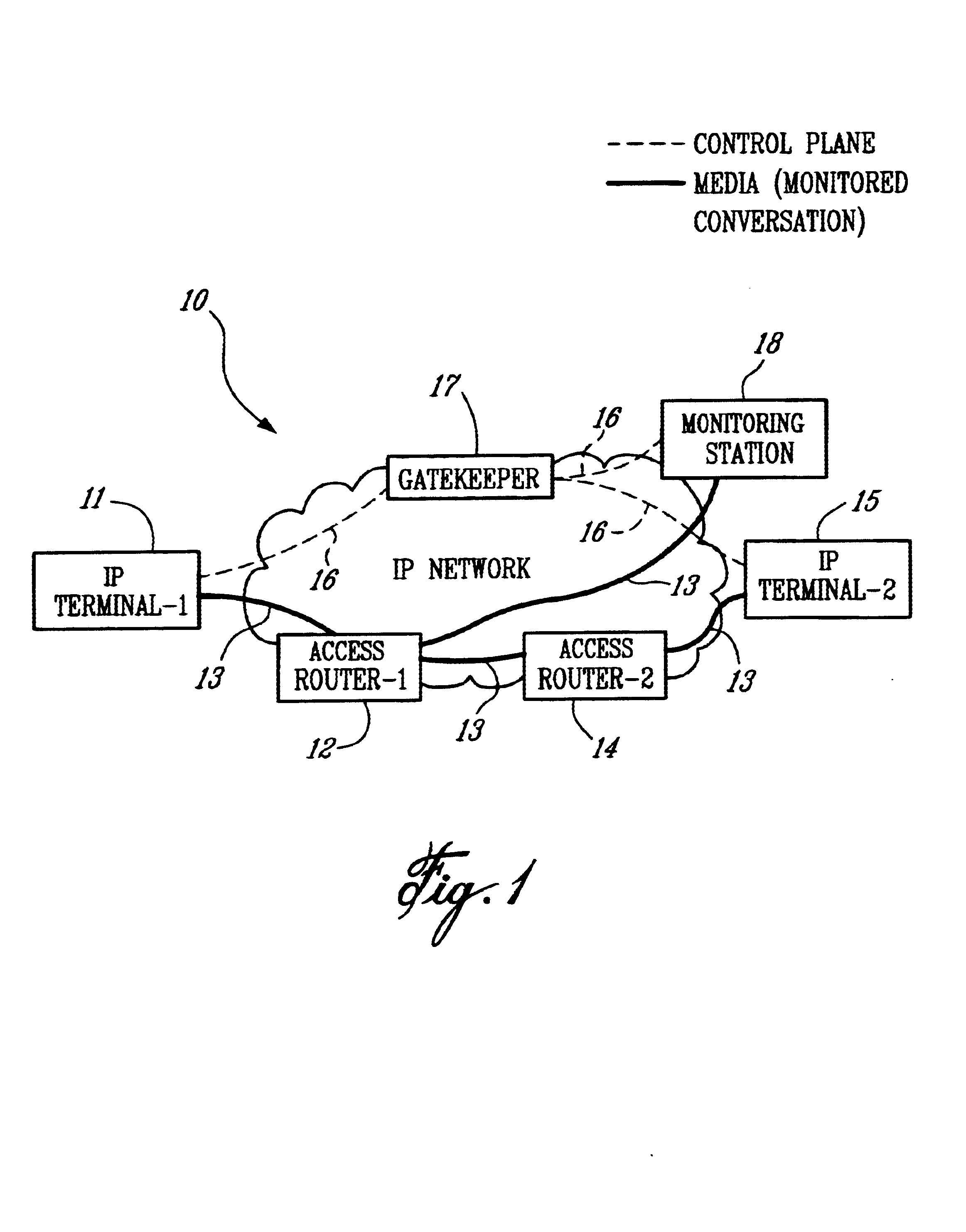
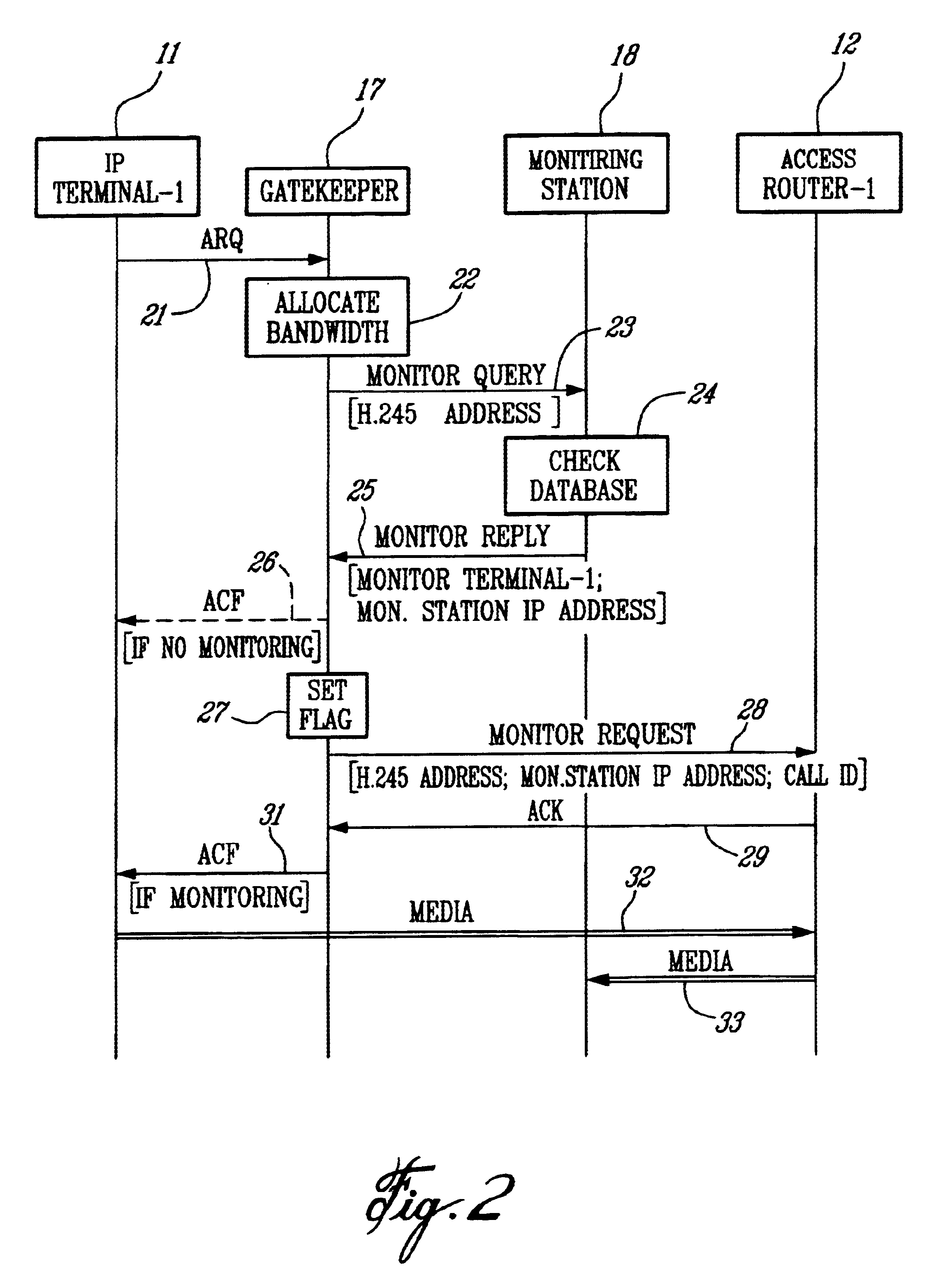
Method of monitoring calls in an internet protocol (IP)-based network
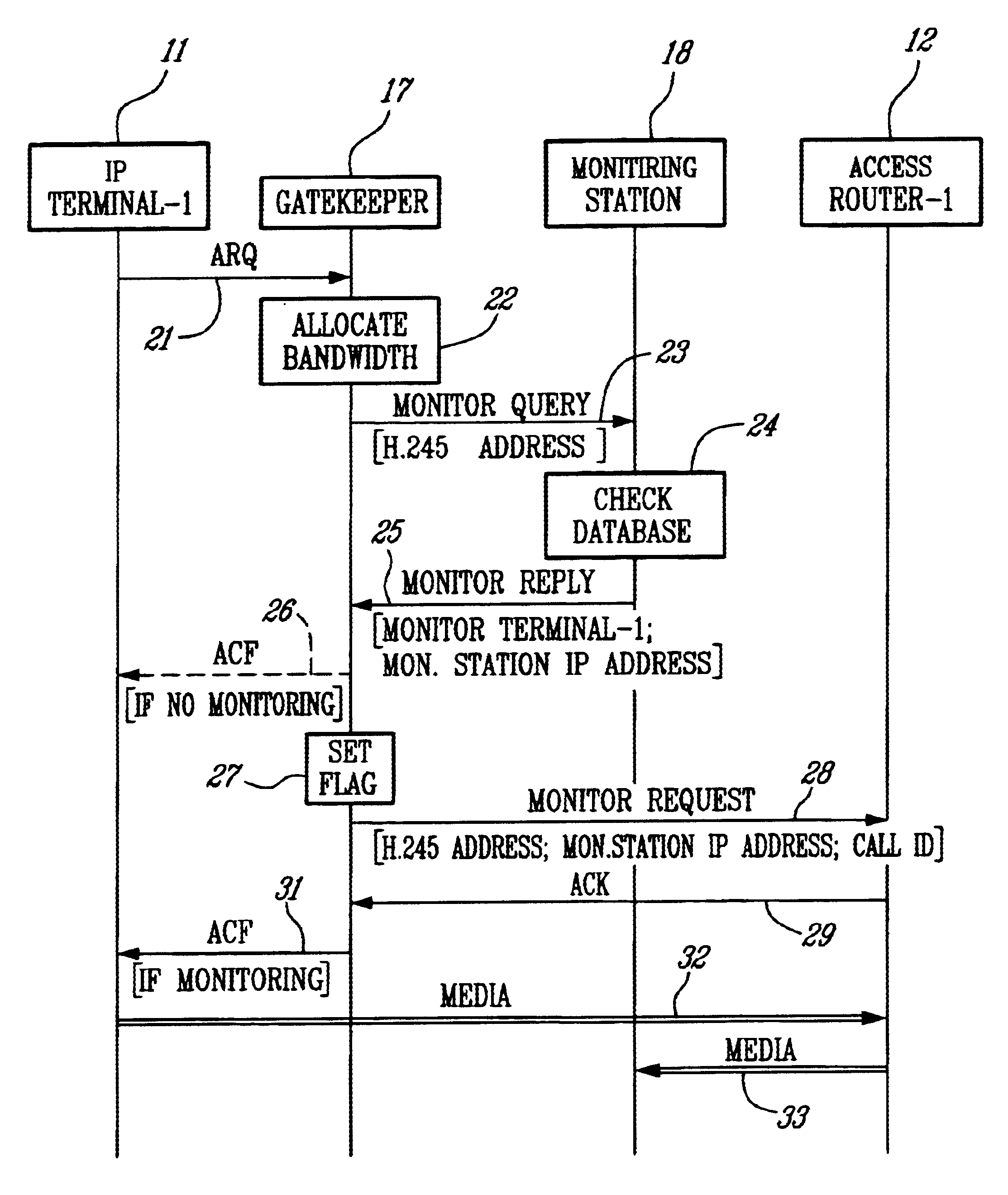
InactiveUS6839323B1Error preventionFrequency-division multiplex detailsInternet protocol suiteTTEthernet
A method of monitoring a call with a mobile terminal (MT) in an Internet Protocol (IP)-based network having a Gatekeeper that controls the network, a plurality of access routers that provide access to the network, and a Monitoring Station having monitoring facilities and a database of MTs to be monitored. When the MT sends an Admission Request message to the Gatekeeper, the Gatekeeper sends a query to the Monitoring Station asking whether the MT is to be monitored. The Monitoring Station sends a reply to the Gatekeeper indicating that the MT is to be monitored and providing an IP address where monitored packets are to be sent. The Gatekeeper then sends a monitoring request message to the access router associated with the MT. The request identifies the MT to be monitored, instructs the access router to monitor the MT, and provides a unique call identification (Call ID) and the IP address where monitored packets are to be sent. When the access router detects a packet associated with the MT, the router sends all packets associated with the MT to the Monitoring Station. The method also controls monitoring during intra-domain and inter-domain handoffs of the MT.
Owner:TELEFON AB LM ERICSSON (PUBL)
System and method for address resolution in internet protocol (IP)-based networks
ActiveUS6917612B2Data switching by path configurationNetwork connectionsInternet protocol suiteDomain name
A system and unified method of address resolution in an IP-based network. A Resolver determines whether an input address is a URL / URI, and if so, extracts a domain name. If the input address is an E.164 number, the Resolver converts the E.164 number into a domain name in ENUM format. The Resolver then sends a domain name query to a DNS which, if able, returns the IP address for either a Global MGCF or a destination server along with a supported Application protocol. If the DNS is unable to perform the translation, or the Application protocol returned is not supported by the requesting application, the Resolver sends a domain name query to an extended Location Server (LS) to obtain an IP address of a gateway function capable of interfacing with the destination server.
Owner:TELEFON AB LM ERICSSON (PUBL)
Network address translation for voice over internet protocol router
InactiveUS7346044B1Reduce the number of portsReduce in quantityNetwork connectionsInternet protocol suiteTTEthernet
A network address translation apparatus and method within a Voice over Internet Protocol (VoIP) router is described. This apparatus and method operates within networking devices such as routers, switches, bridges, etc. These devices masks both source and destination addresses and may either replace or complement a firewall in providing security. According to one embodiment, network type information, corresponding to the gateways within connection, is embedded in a port number within a packet header. This network type information is extracted and analyzed to identify the network types of both gateways within the connection. According to another embodiment, a port number is assigned according to the network types of both gateways within a connection. Thus, this network type information may be identified by processing the port number on which a packet is received.
Owner:SPICE I2I
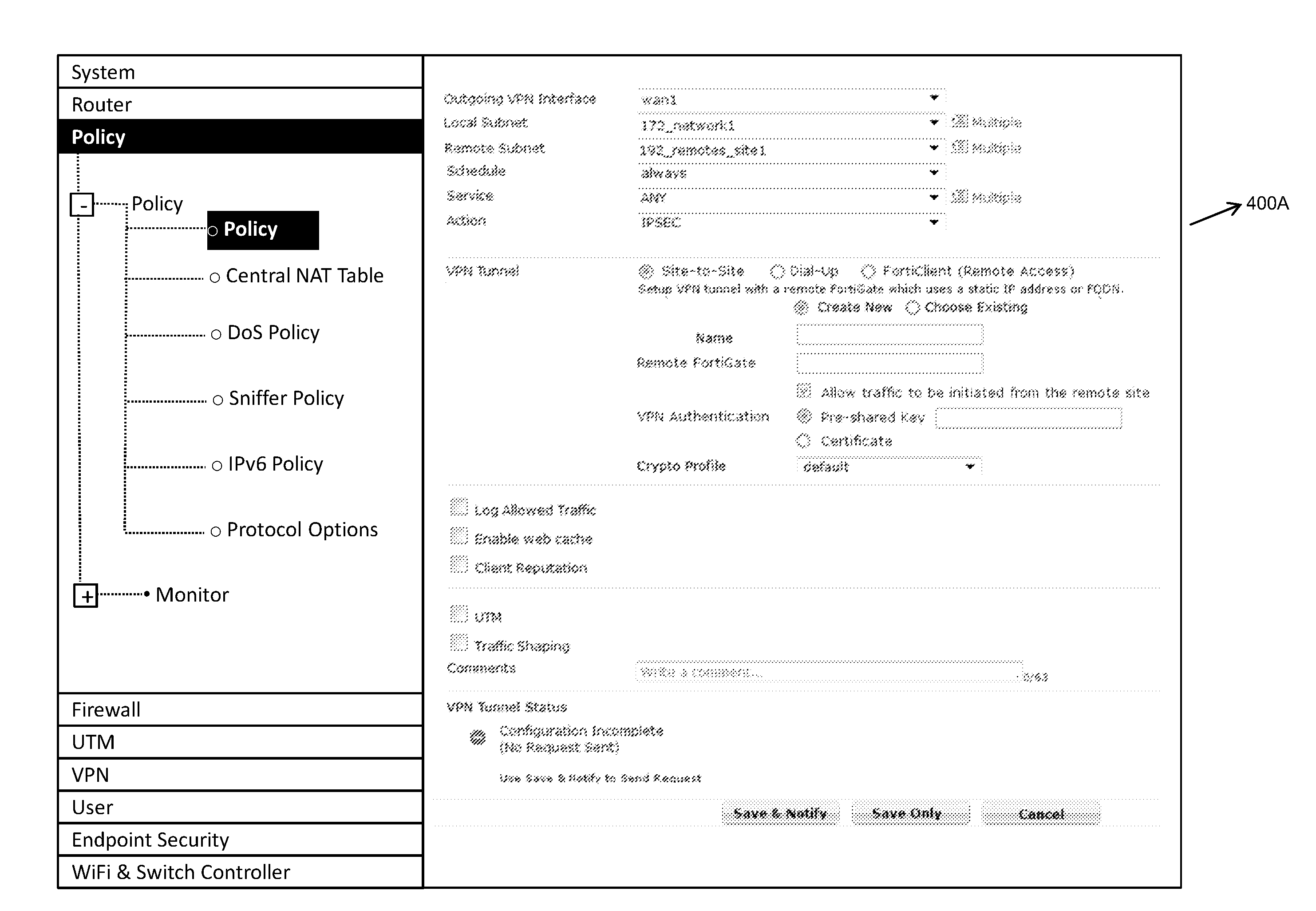
Policy-based configuration of internet protocol security for a virtual private network
ActiveUS20130298182A1Computer security arrangementsData switching networksInternet protocol suiteIPsec
A method for performing policy-based configuration of Internet Protocol Security (IPSec) for a Virtual Private Network (VPN) is provided. According to one embodiment, a browser-based interface of a network device displays a policy page through which multiple settings may be configured for a VPN connection. The settings include a type of IPSec tunnel to be established between the network device and a peer. One or more parameter values corresponding to one or more of the settings are received and responsive thereto a policy file is created or modified corresponding to the VPN connection. The policy file has contained therein multiple parameter values corresponding to the settings. Establishment of the VPN connection between the network device and the peer is requested based on the parameter values contained within the policy file by sending a notification request, including the policy file, from the network device to the peer.
Owner:FORTINET
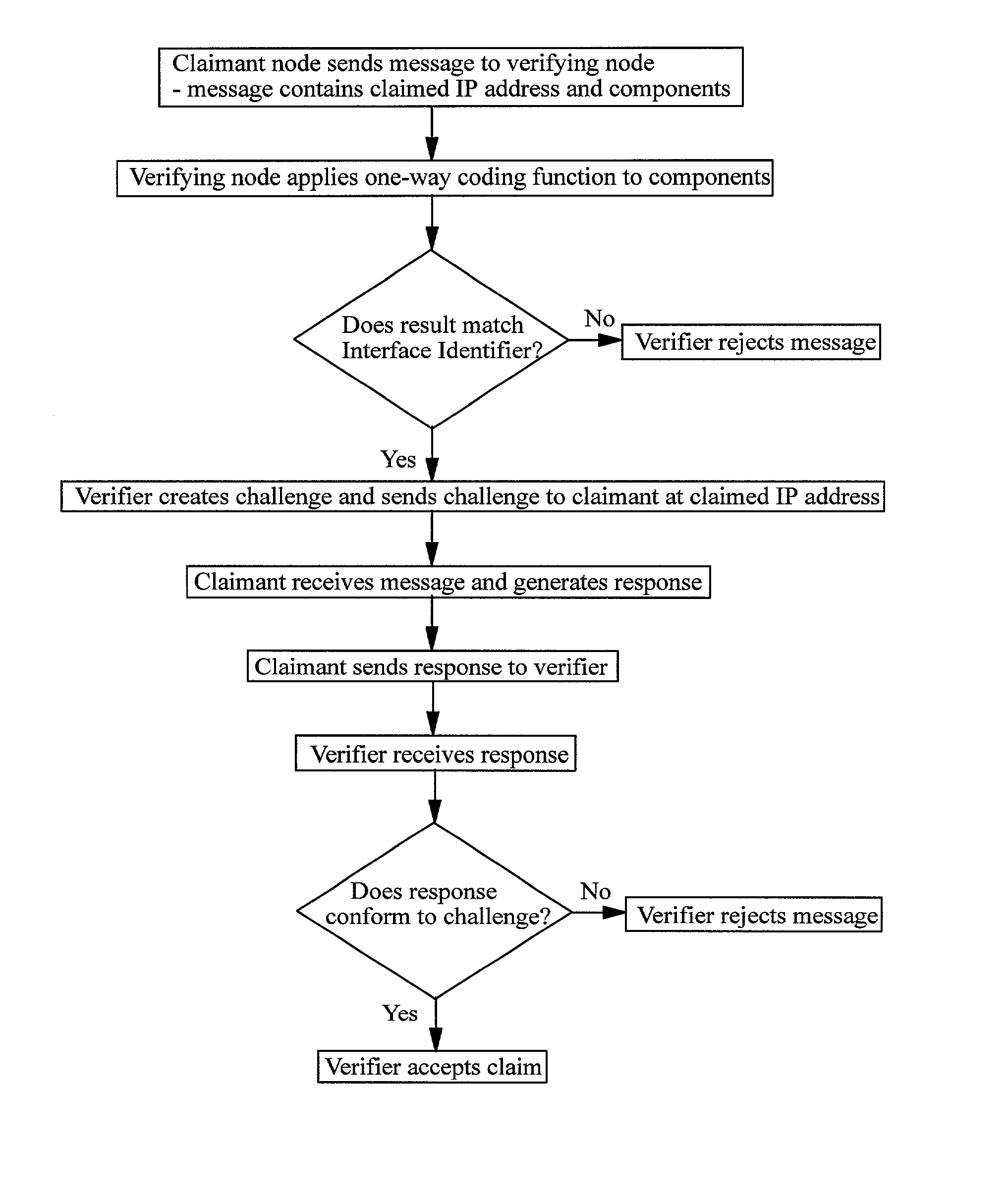
Address mechanisms in internet protocol
ActiveUS20020133607A1User identity/authority verificationMultiple digital computer combinationsInternet protocol suiteComputer hardware
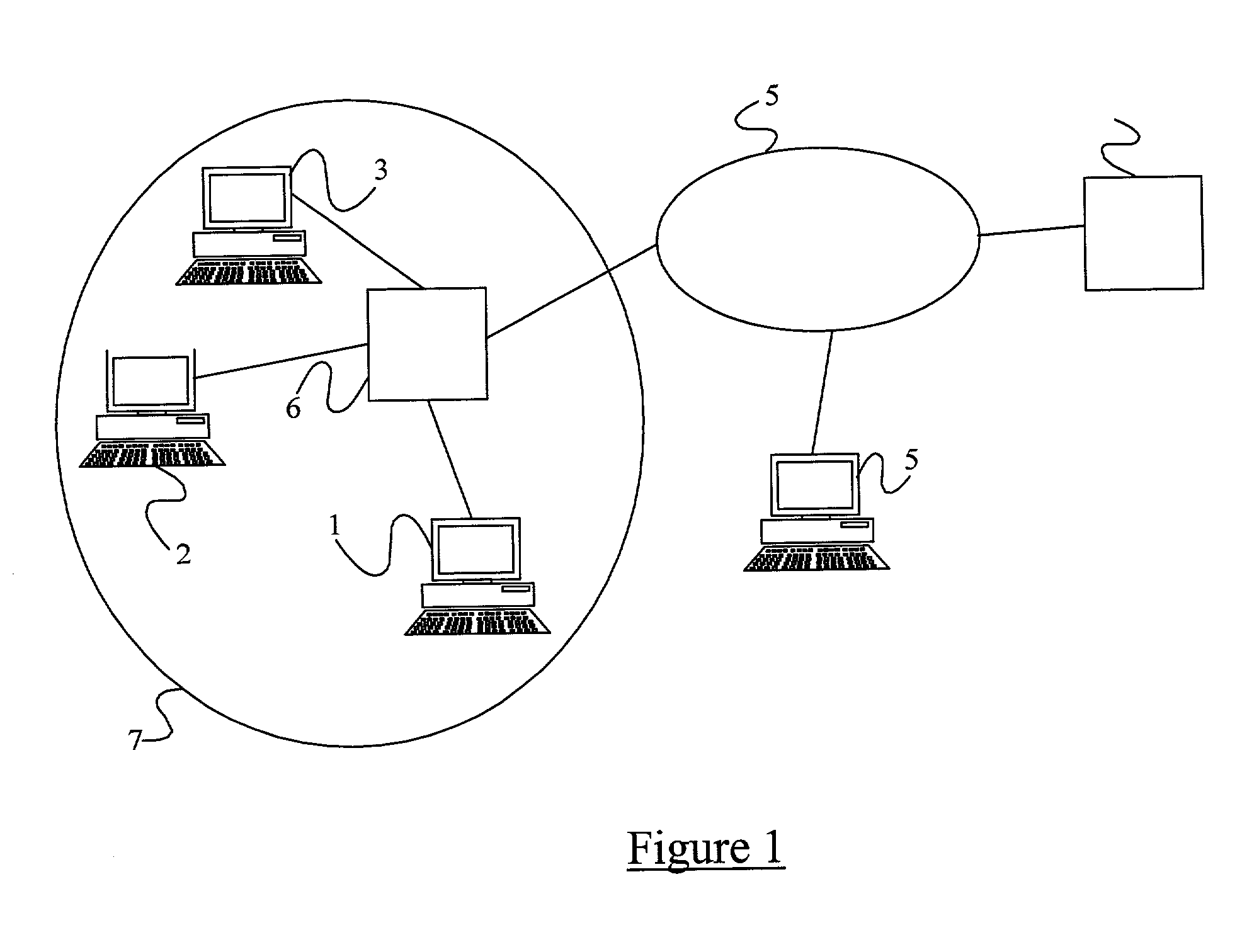
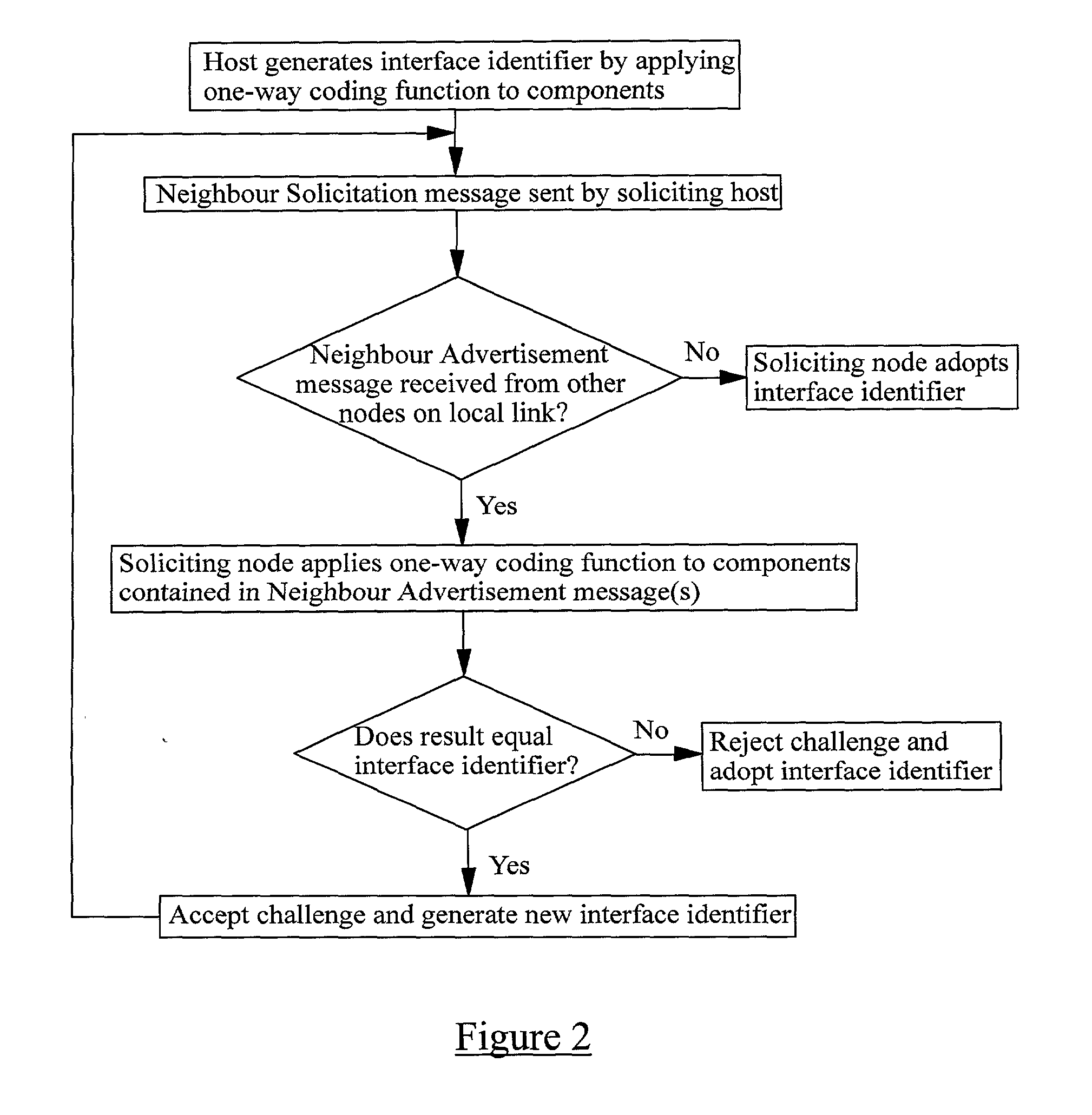
A method of verifying that a host coupled to an IP network is authorised to use an IP address which the host claims to own, the IP address comprising a routing prefix and an interface identifier part. The method comprises receiving from the host one or more components, applying a one-way coding function to the or each component and / or derivatives of the or each component, and comparing the result or a derivative of the result against the interface identifier part of the IP address. If the result or its derivative matches the interface identifier the host is assumed to be authorised to use the IP address and if the result or its derivative does not match the interface identifier the host is assumed not to be authorised to use the IP address.
Owner:TELEFON AB LM ERICSSON (PUBL)
Simplified method of configuring internet protocol security tunnels
InactiveUS6076168AMultiple digital computer combinationsProgram controlTraffic capacityInternet protocol suite
A method of securing data traffic between a local and remote host systems is provided. The method includes autogenerating a filter having rules associated with a defined tunnel. The filter rules are used to permit or deny acceptance of transmitted data by the host system and to direct traffic to the tunnel. The tunnel, on the other hand, is used to keep data confidential. The method further includes autogeneration of a counterpart tunnel and associated filter to be used by the remote host when in communication with the local host. The method further autogenerates a new filter to reflect changes to any one of the tunnels and autodeactivates the filter associated with a deleted tunnel.
Owner:IBM CORP
Bit error resilience for an internet protocol stack
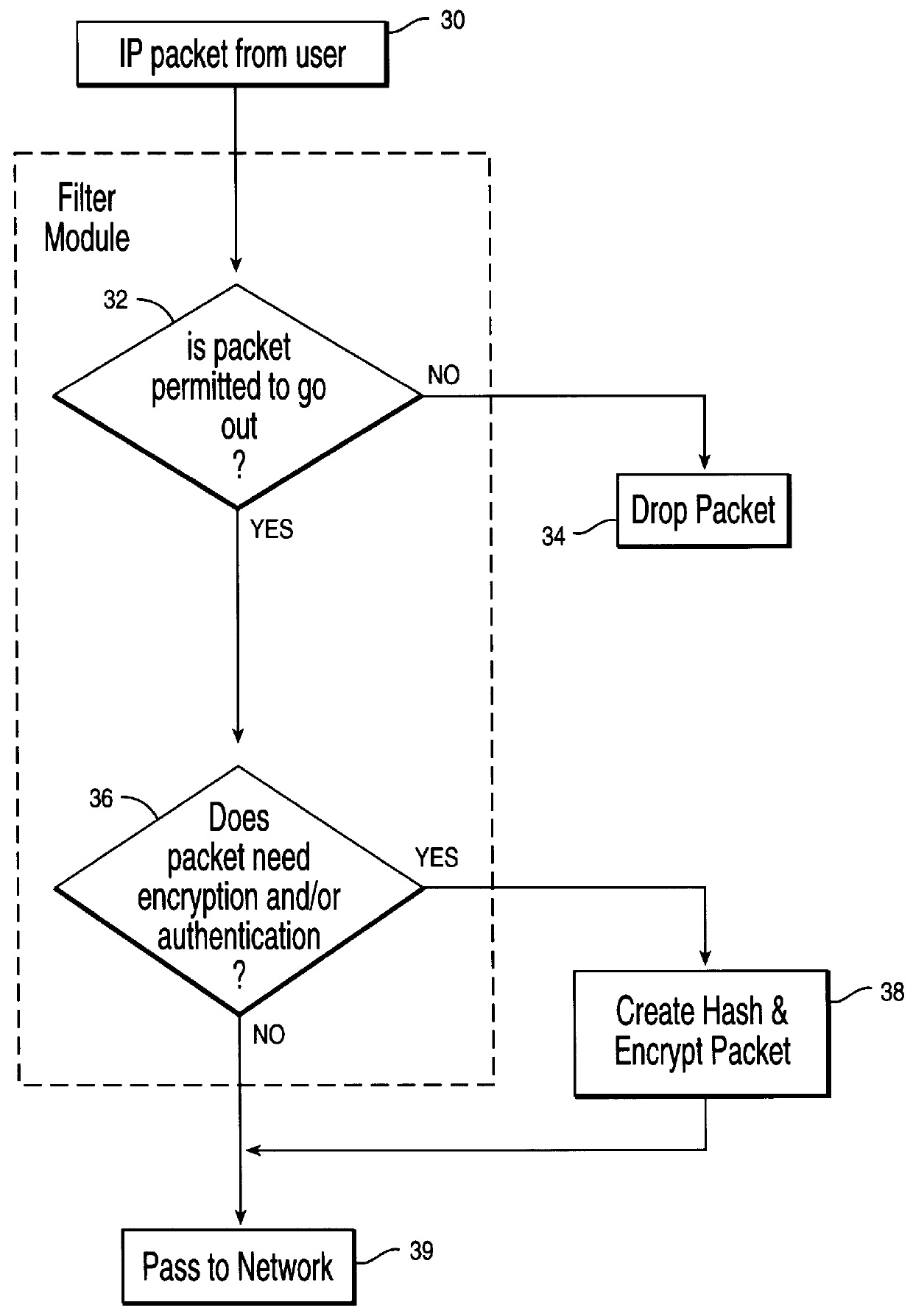
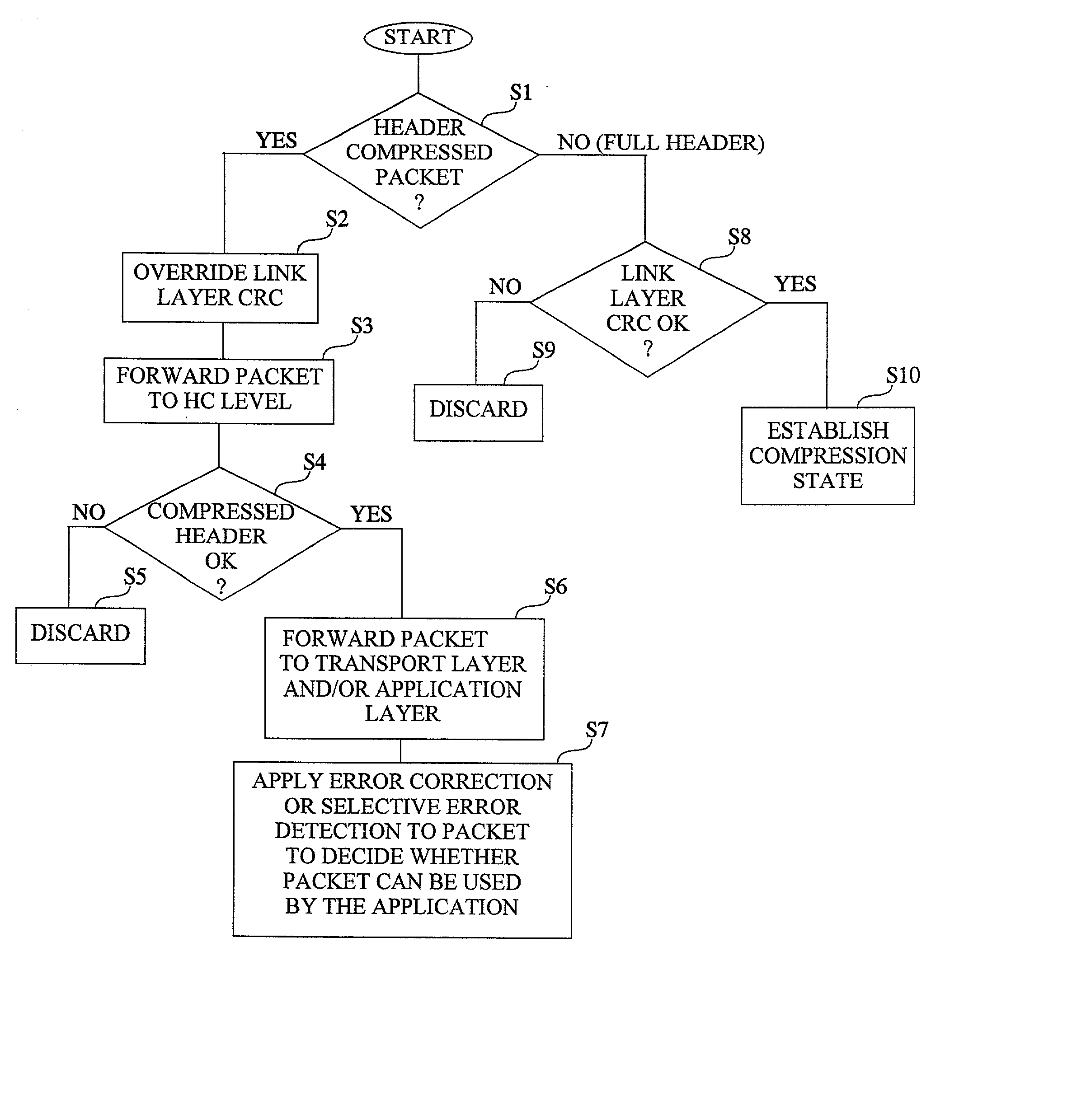
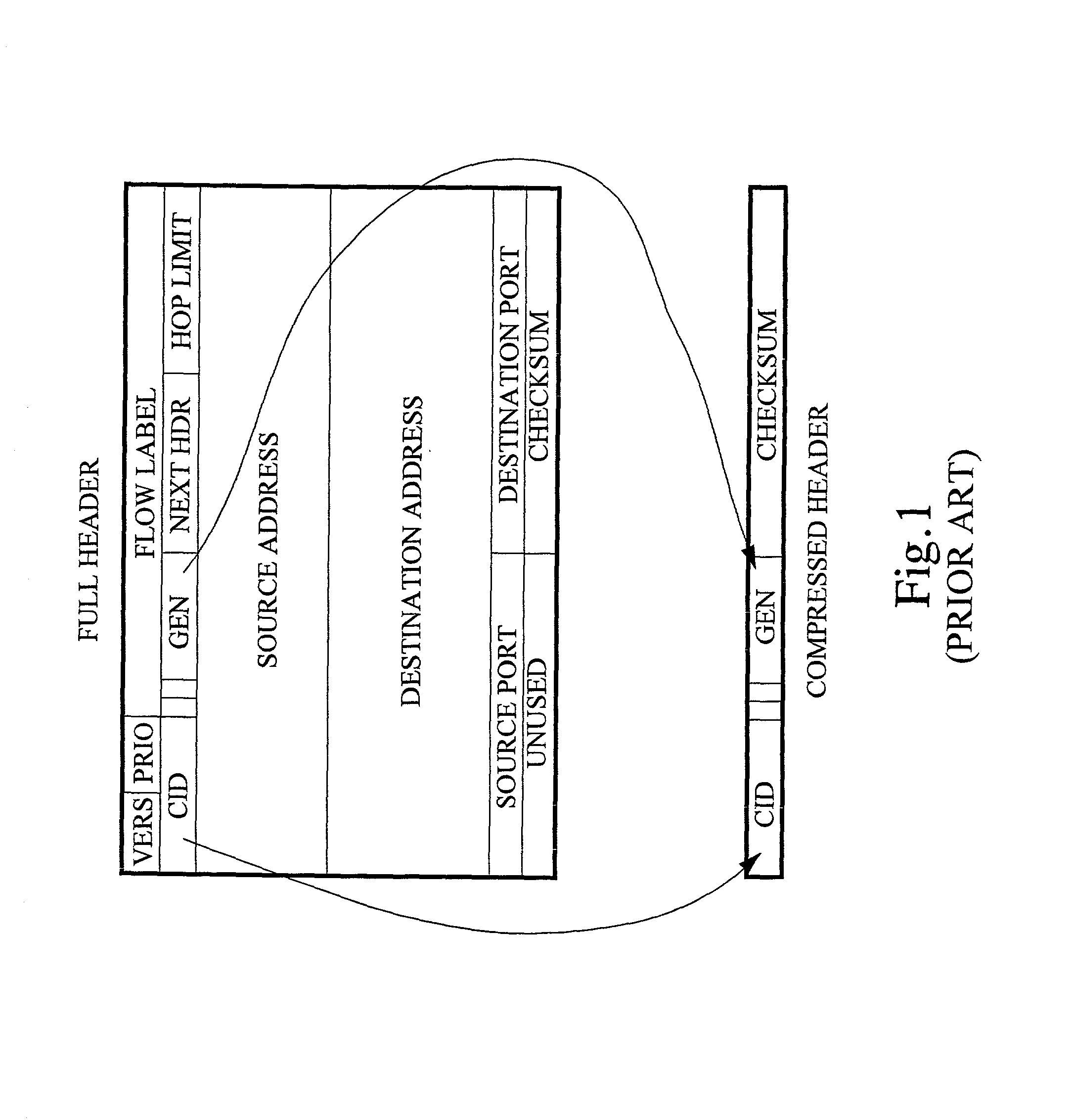
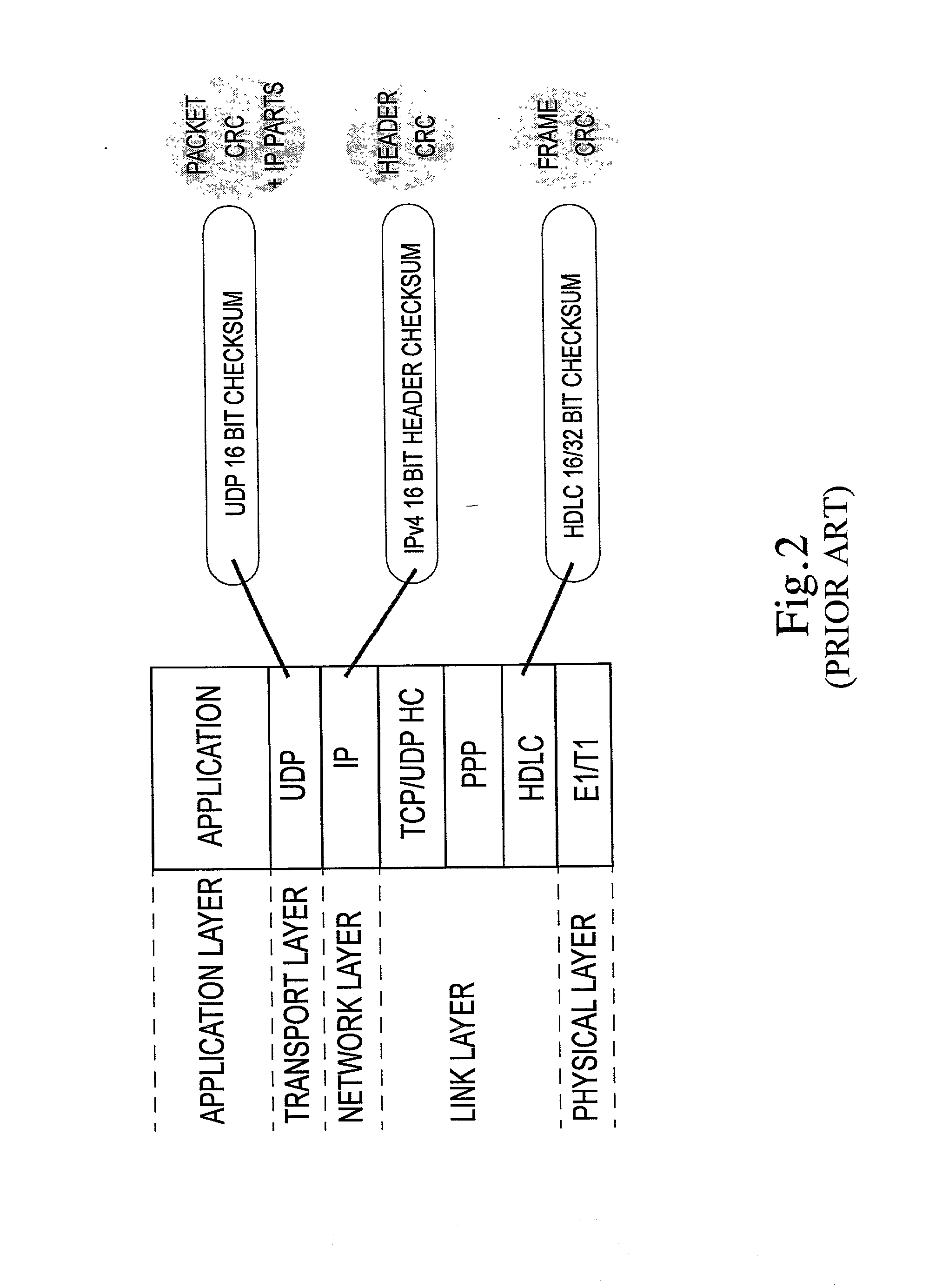
ActiveUS20020071432A1Accurate protectionWithout seriously degrading application qualityError preventionTransmission systemsInternet protocol suitePacket loss
The invention concerns the bit error resilience of an IP protocol stack based on a secure link layer, in which packet flows are header compressed according to a suitable header compression standard. According to the invention, by analyzing each packet at the link layer it can be determined whether the packet is a full header packet, in which case the link layer checksum evaluation is used as normal for discarding faulty full header packets, or a header compressed packet in which case the link layer checksum evaluation is ignored and the packet is propagated upwards in the protocol stack. This solution not only opens up for more intelligent higher-level handling of faulty header compressed packets, but also solves the problem of properly protecting full header packets at the link layer. In order to compensate for ignoring the link layer checksum evaluation for header compressed packets, header protection is introduced at the header compression level of the link layer by using one or more local checksums. The invention is particularly applicable to delay-sensitive real-time data such as compressed voice or video.
Owner:TELEFON AB LM ERICSSON (PUBL)
Allocation of internet protocol (IP) multimedia subsystem (IMS) charges
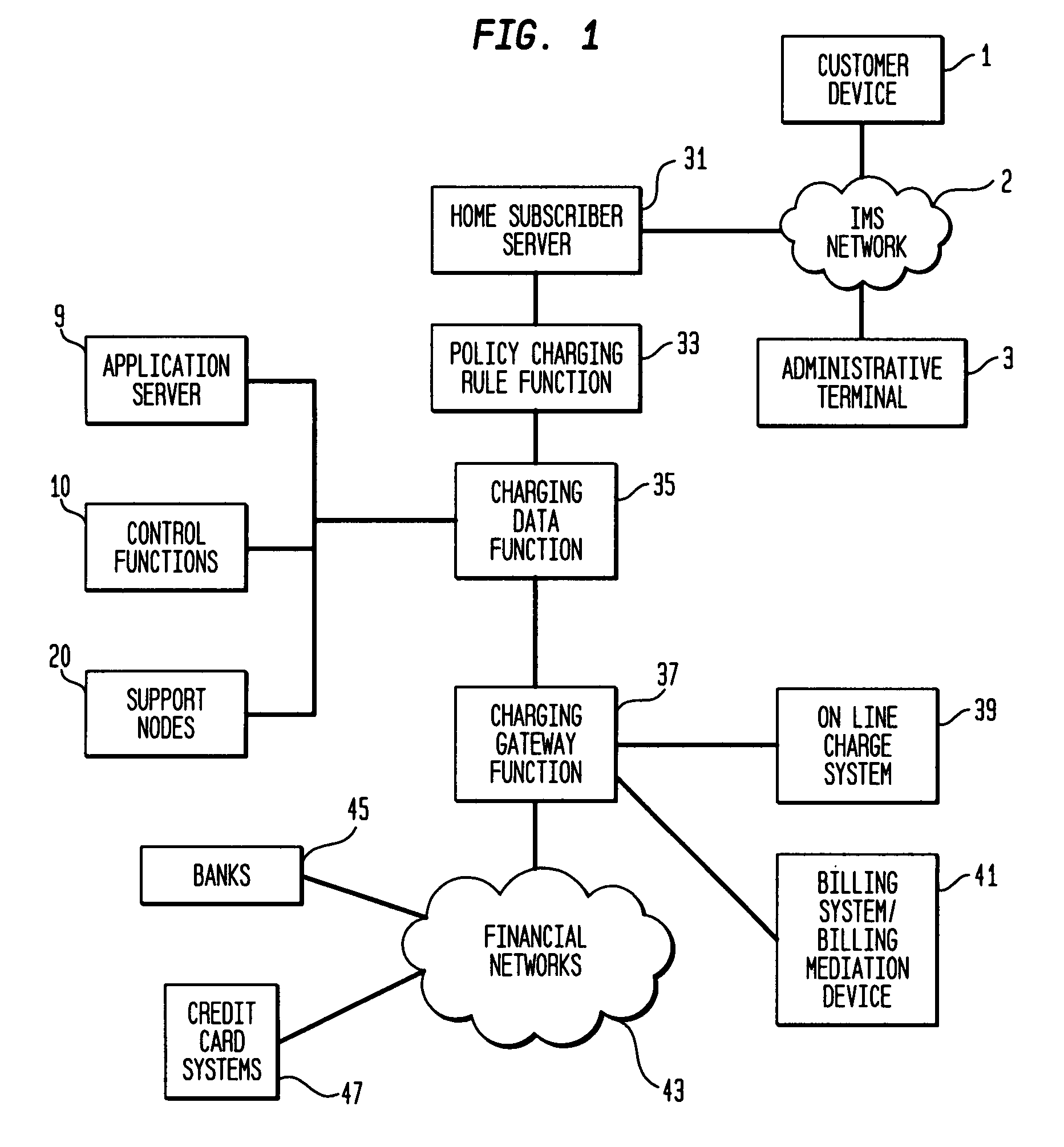
InactiveUS20070270123A1Telephonic communicationNetwork connectionsInternet protocol suiteControl system
This invention relates to methods and apparatus for providing customized cost allocations for telecommunications session in an Internet Protocol Multimedia Subsystem (IMS) network. A Home Subscriber Service stores data describing the policies and rules for allocating charges requested by a particular customer. The charge message sent to charge control system is the product of the charges for the telecommunications session and the policies and rules for allocating charges. Advantageously, this arrangement permits each customer to specify a preferred charge allocation arrangement.
Owner:RPX CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com