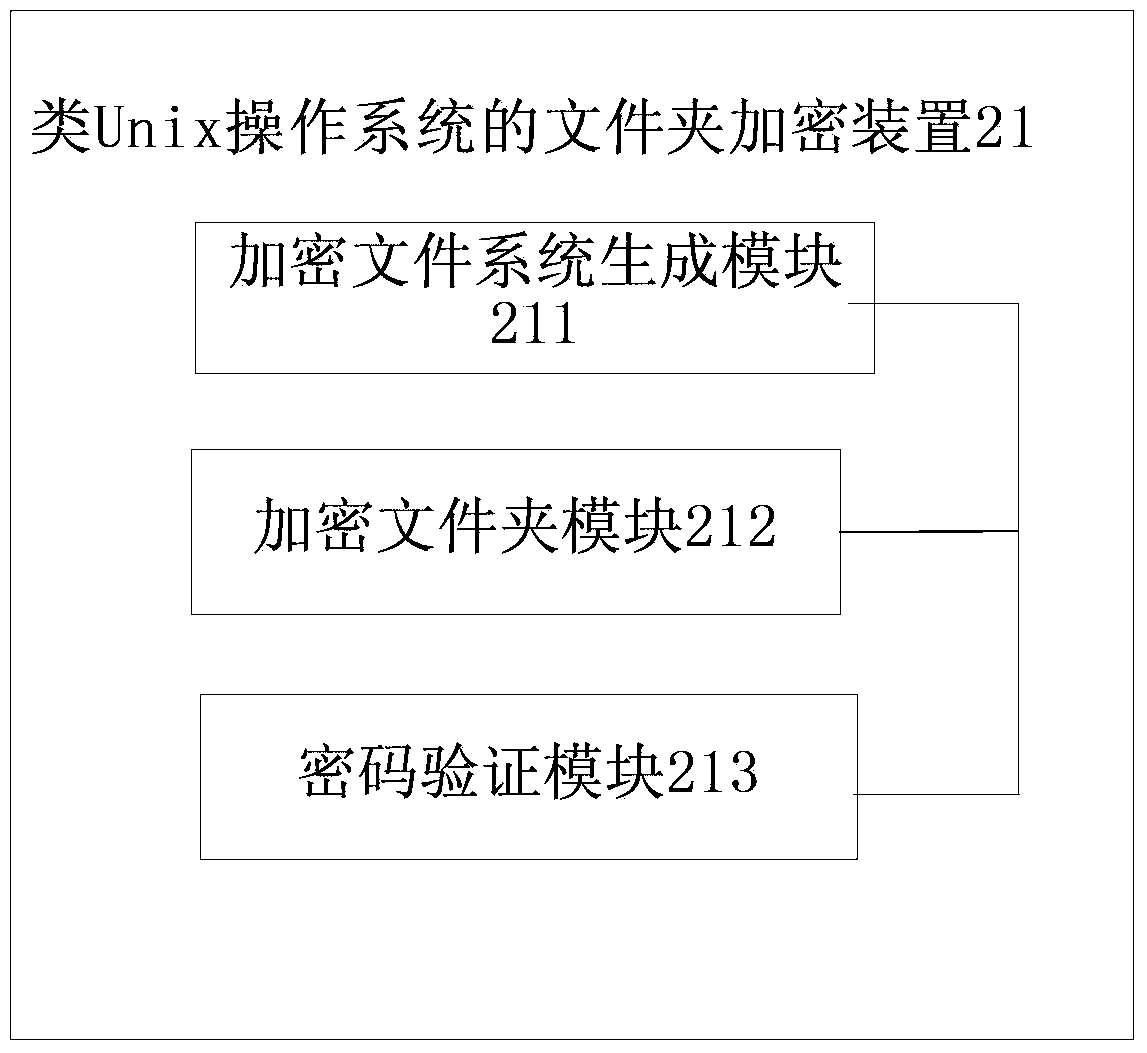
Folder encryption method and device for Unix-like operating system
An operating system and folder technology, applied in the direction of digital data protection, etc., can solve problems such as insufficient confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below in conjunction with specific embodiments and with reference to the accompanying drawings.
[0021] Unix-like systems (Unix-like) refer to various traditional Unix systems, such as FreeBSD, OpenBSD, Solaris of SUN, and various systems similar to traditional Unix, such as Minix, Linux, QNX, etc., which have inherited to a considerable extent The characteristics of the original UNIX have many similarities, and they all comply with the POSIX specification to a certain extent.
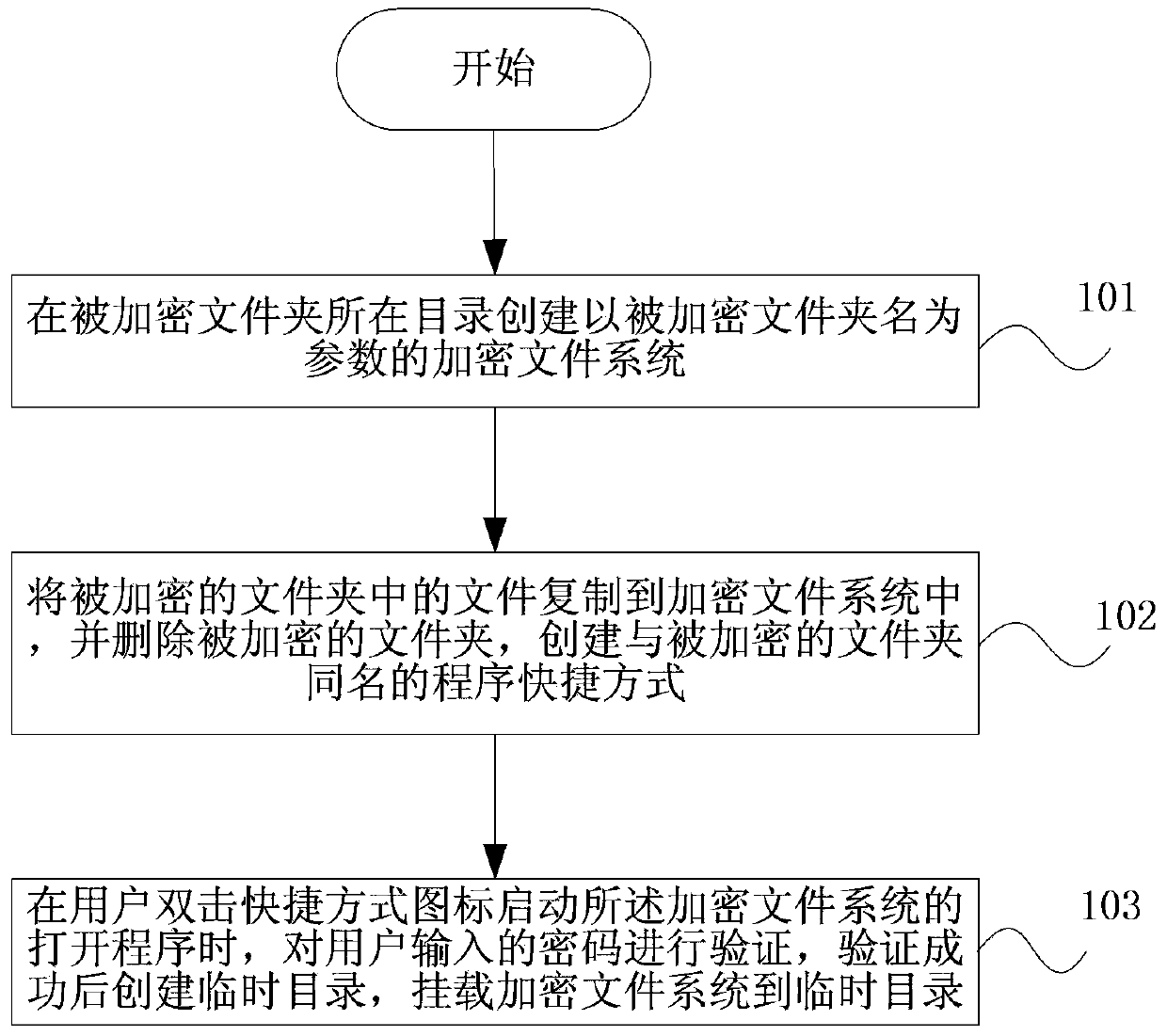
[0022] figure 1 It is a schematic diagram of an embodiment of the folder encryption method of the Unix-like operating system of the present invention. Such as figure 1 Shown:
[0023] Step 101, create an encrypted file system with the name of the encrypted folder as a parameter in the directory where the encrypted folder is located.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com