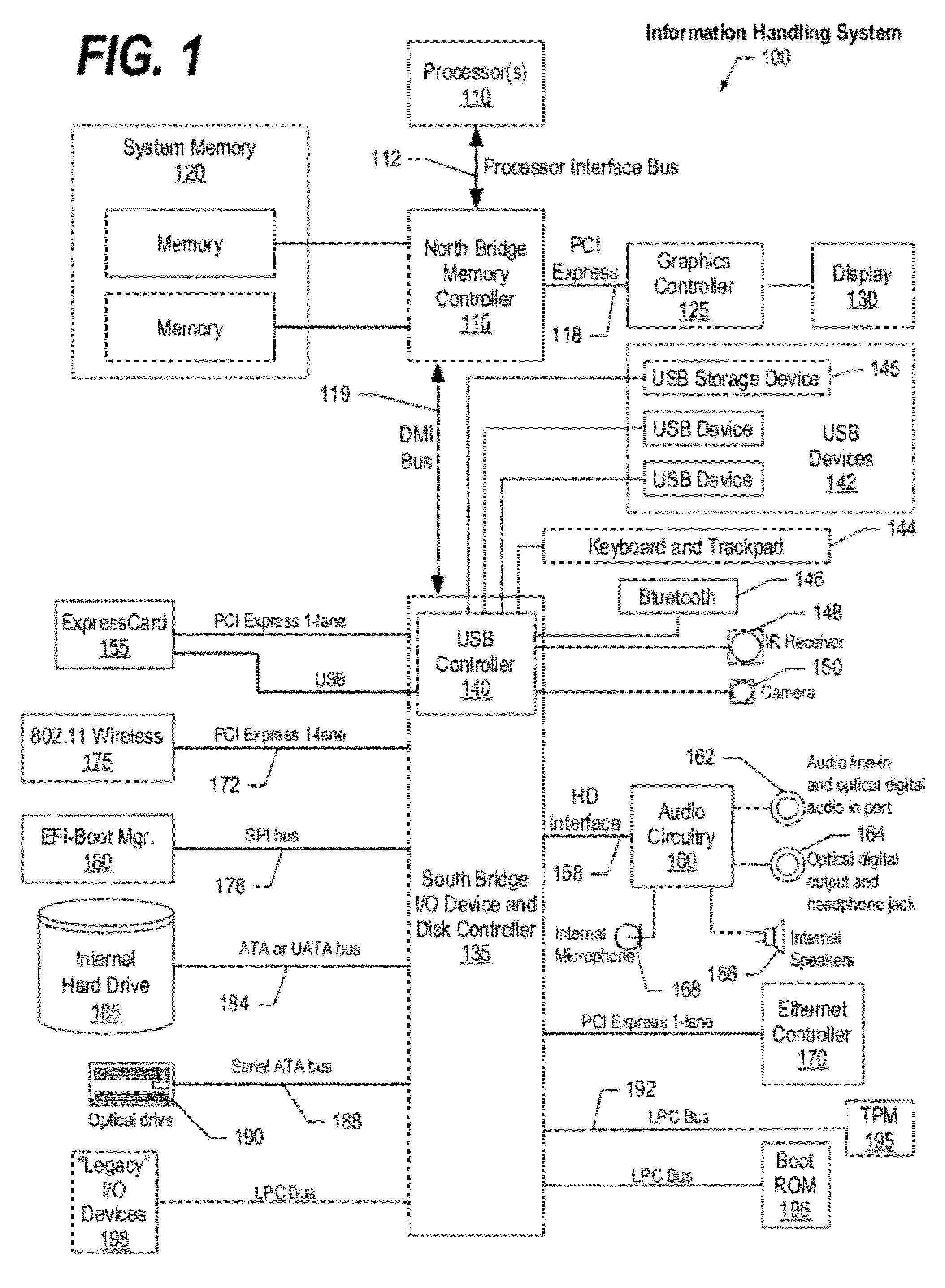
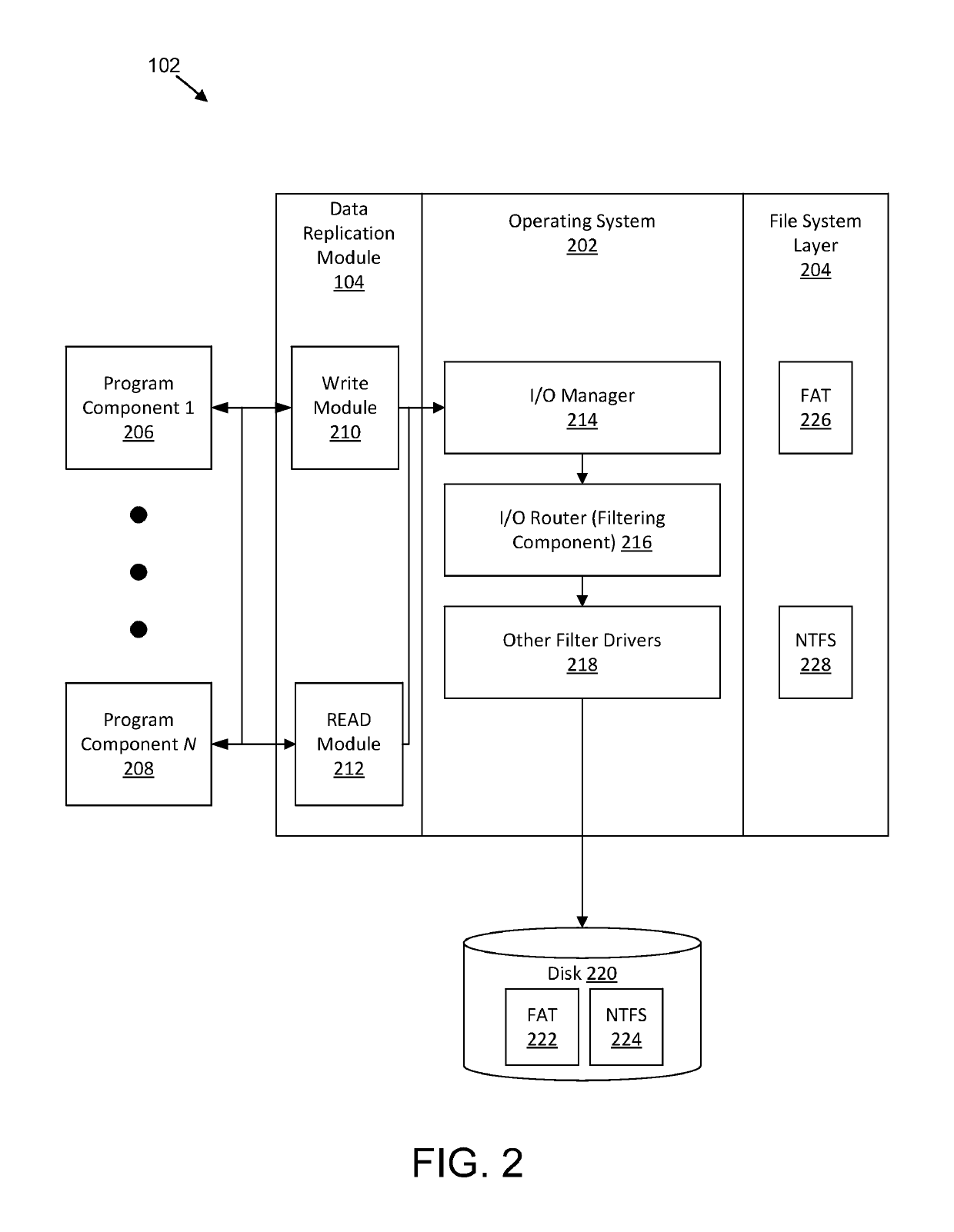
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
40 results about "Encrypting file system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
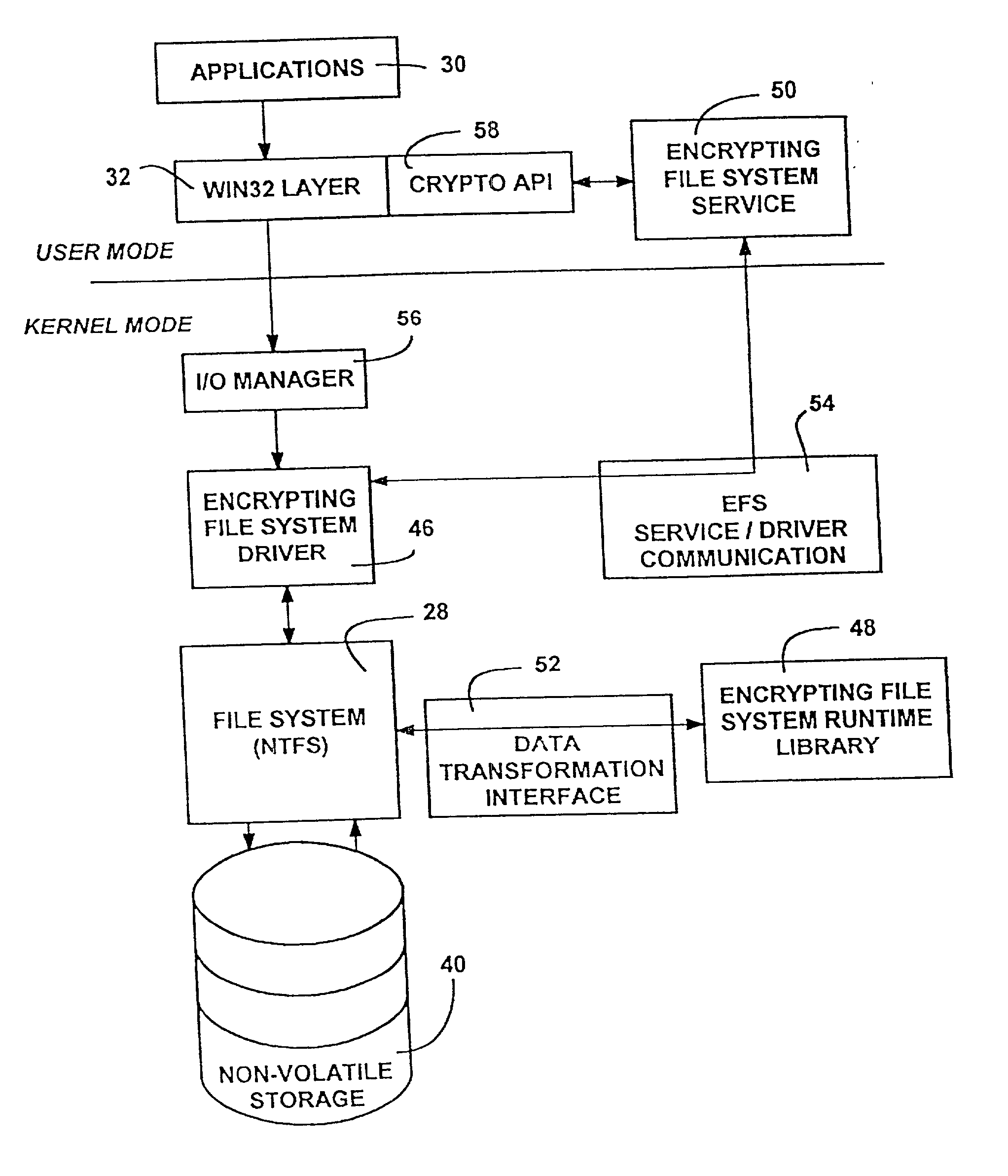
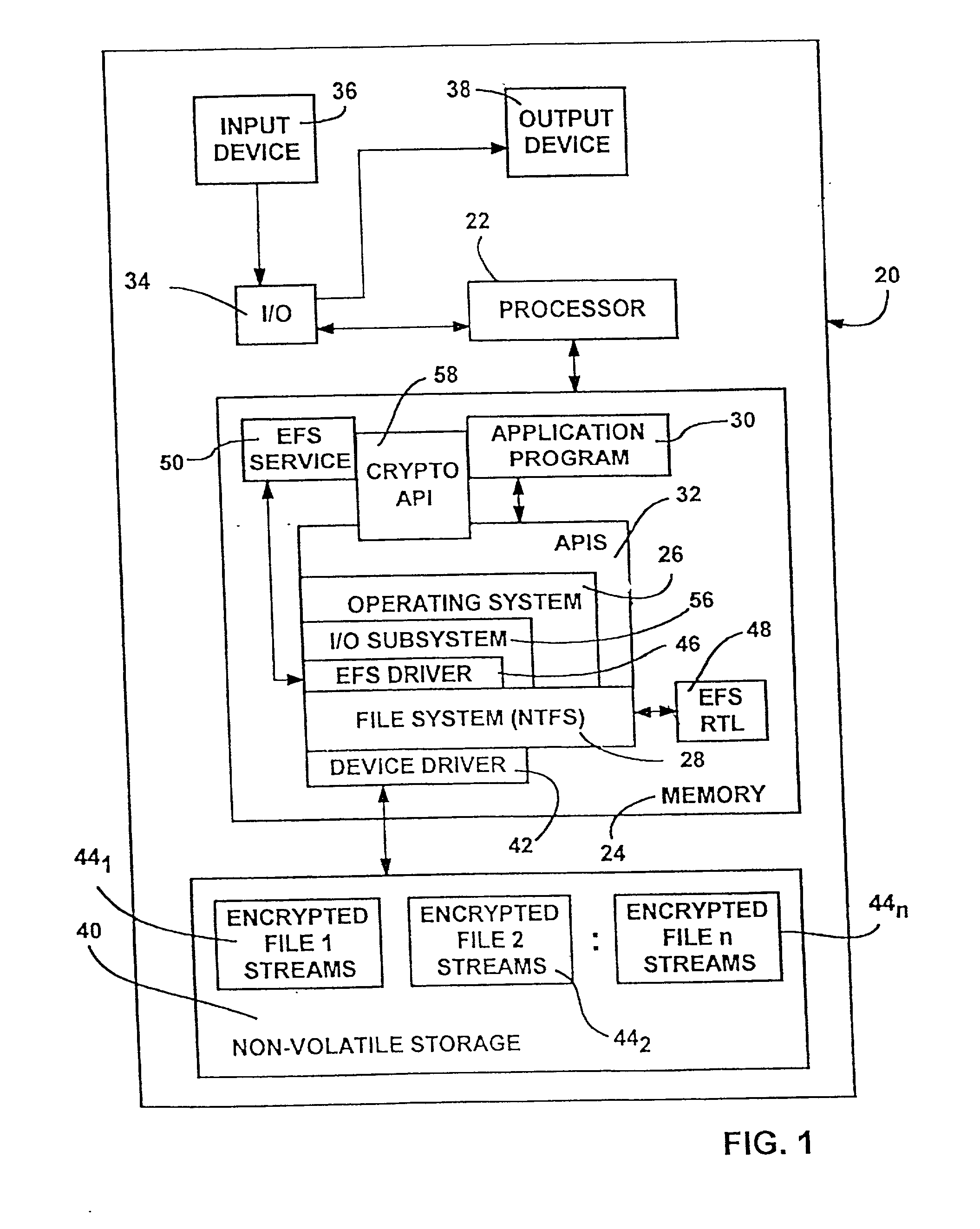
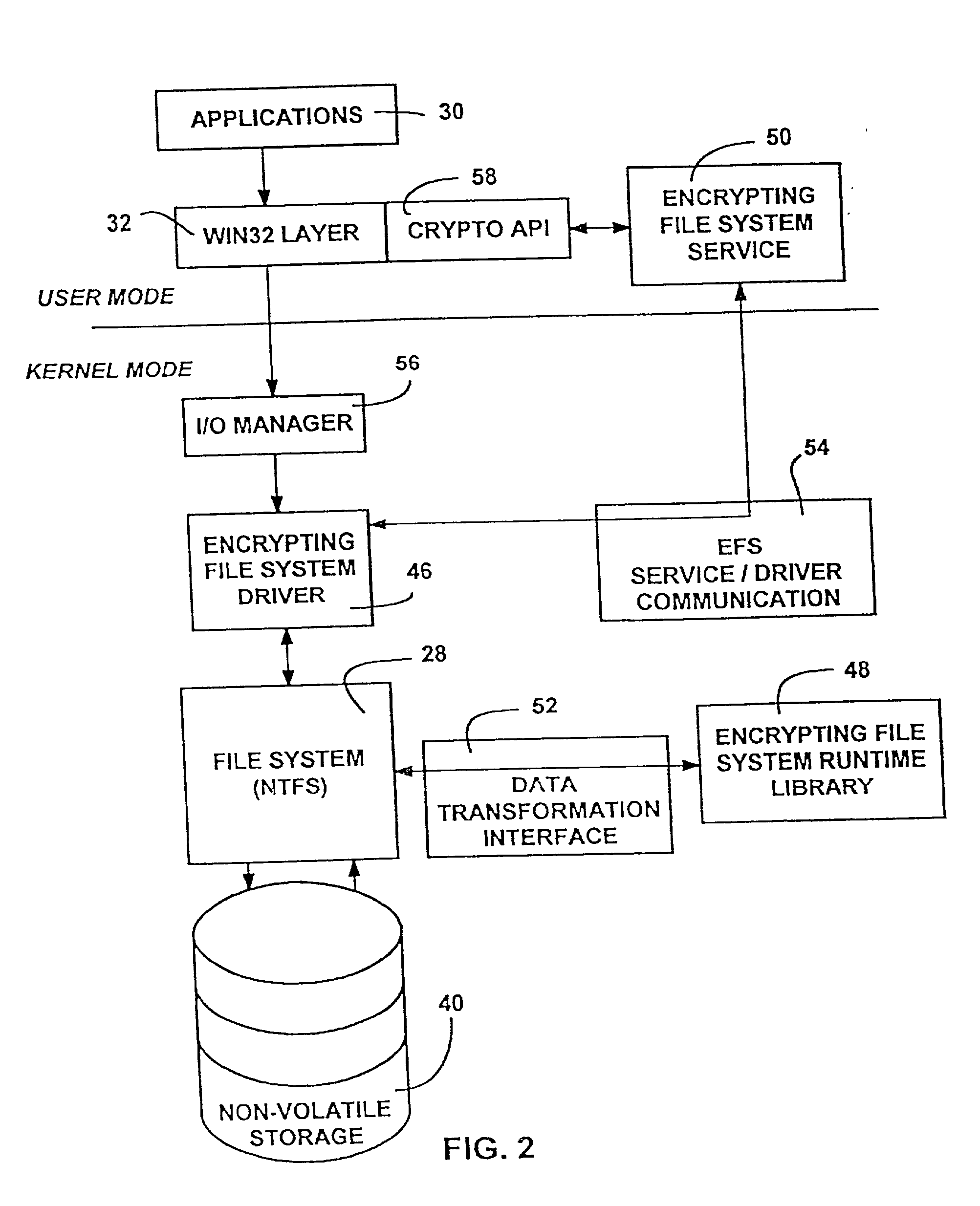
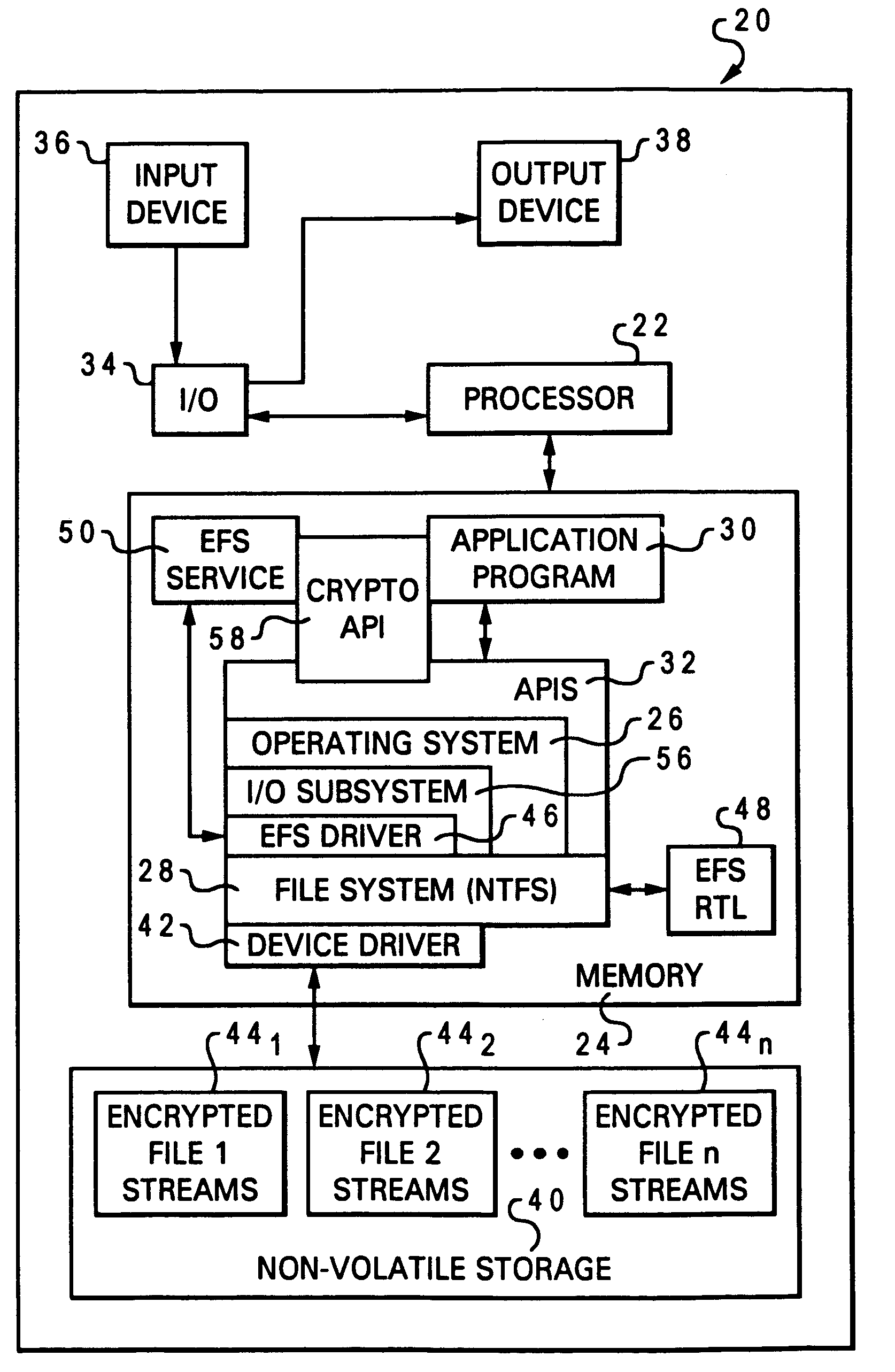
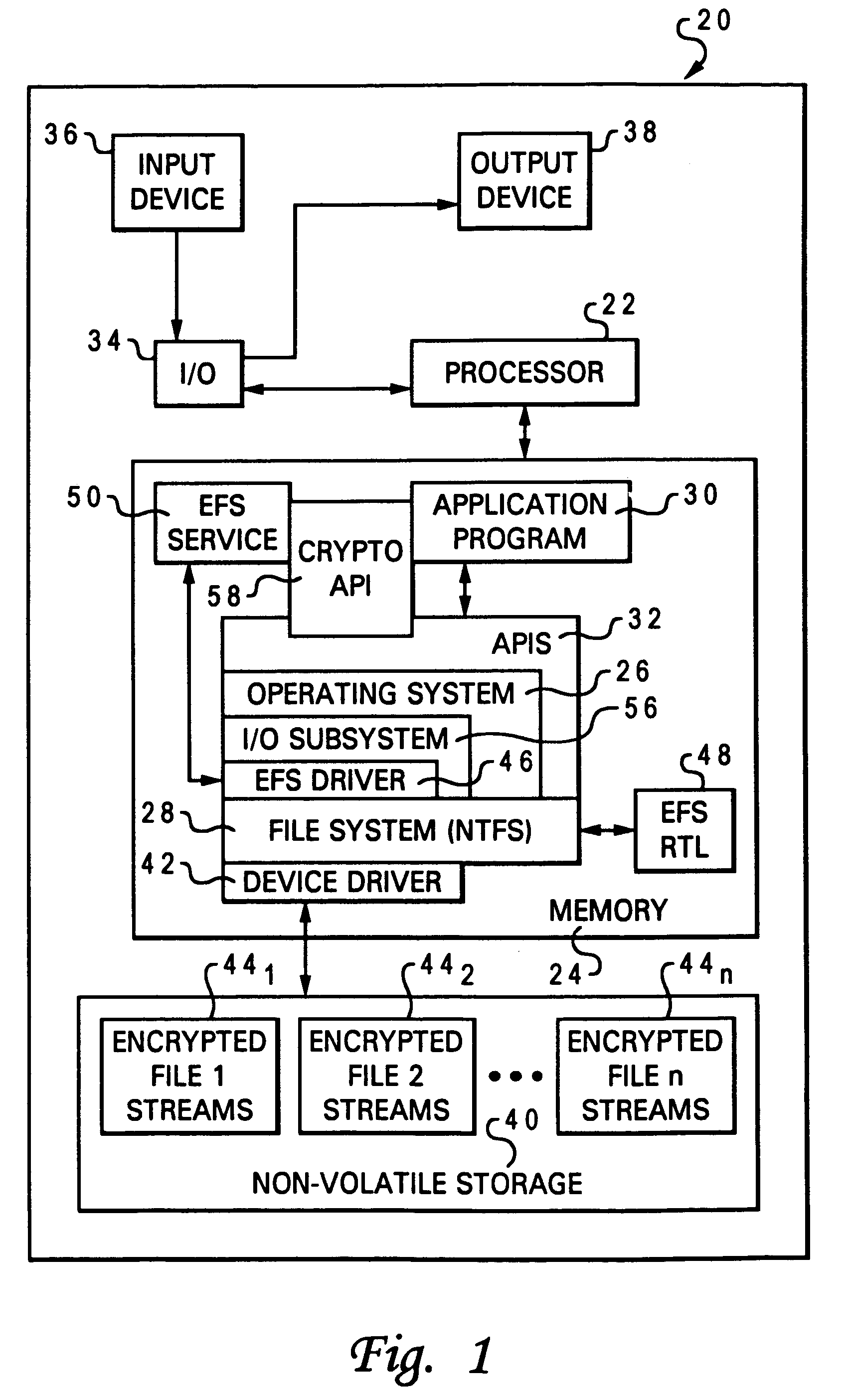
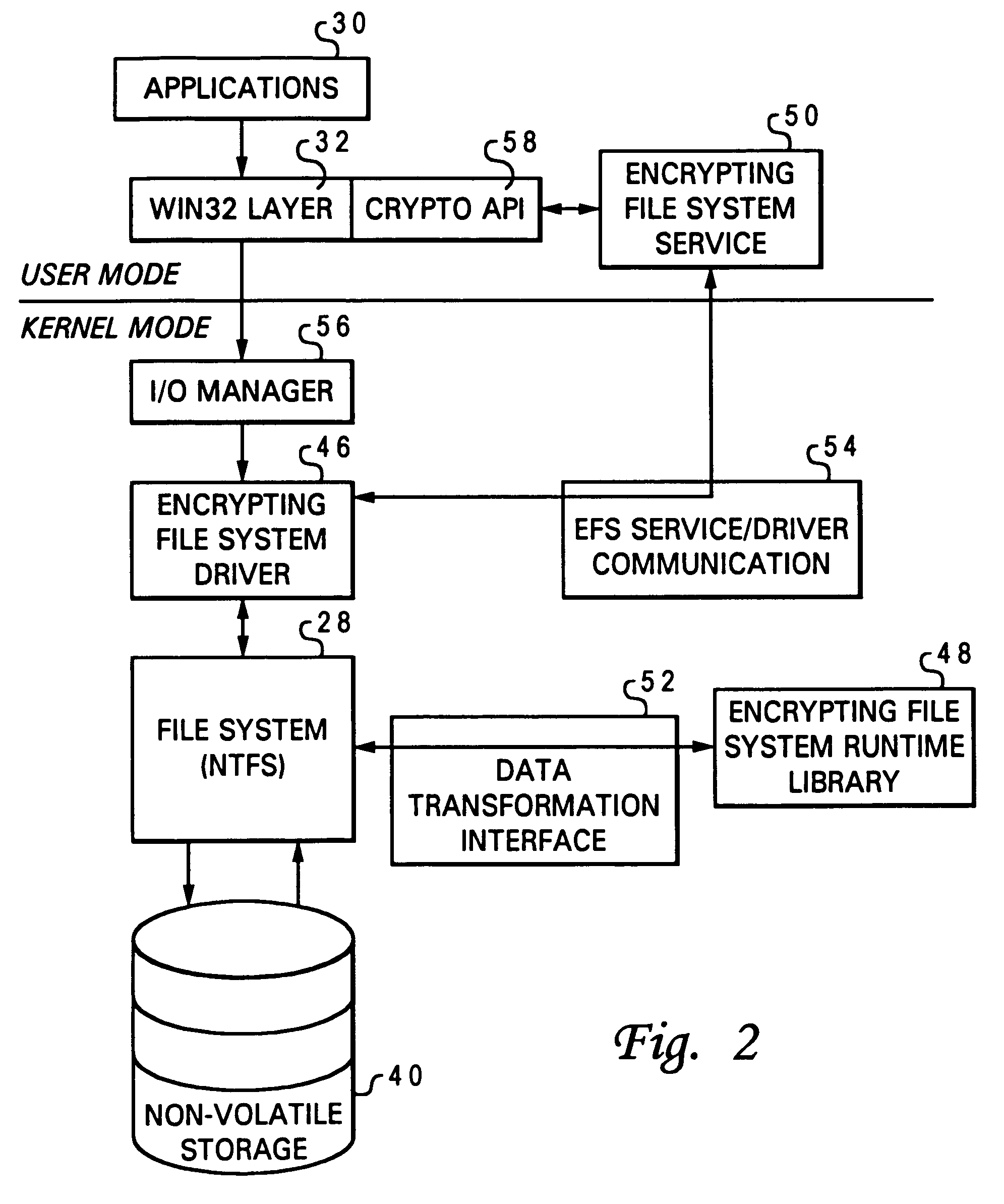
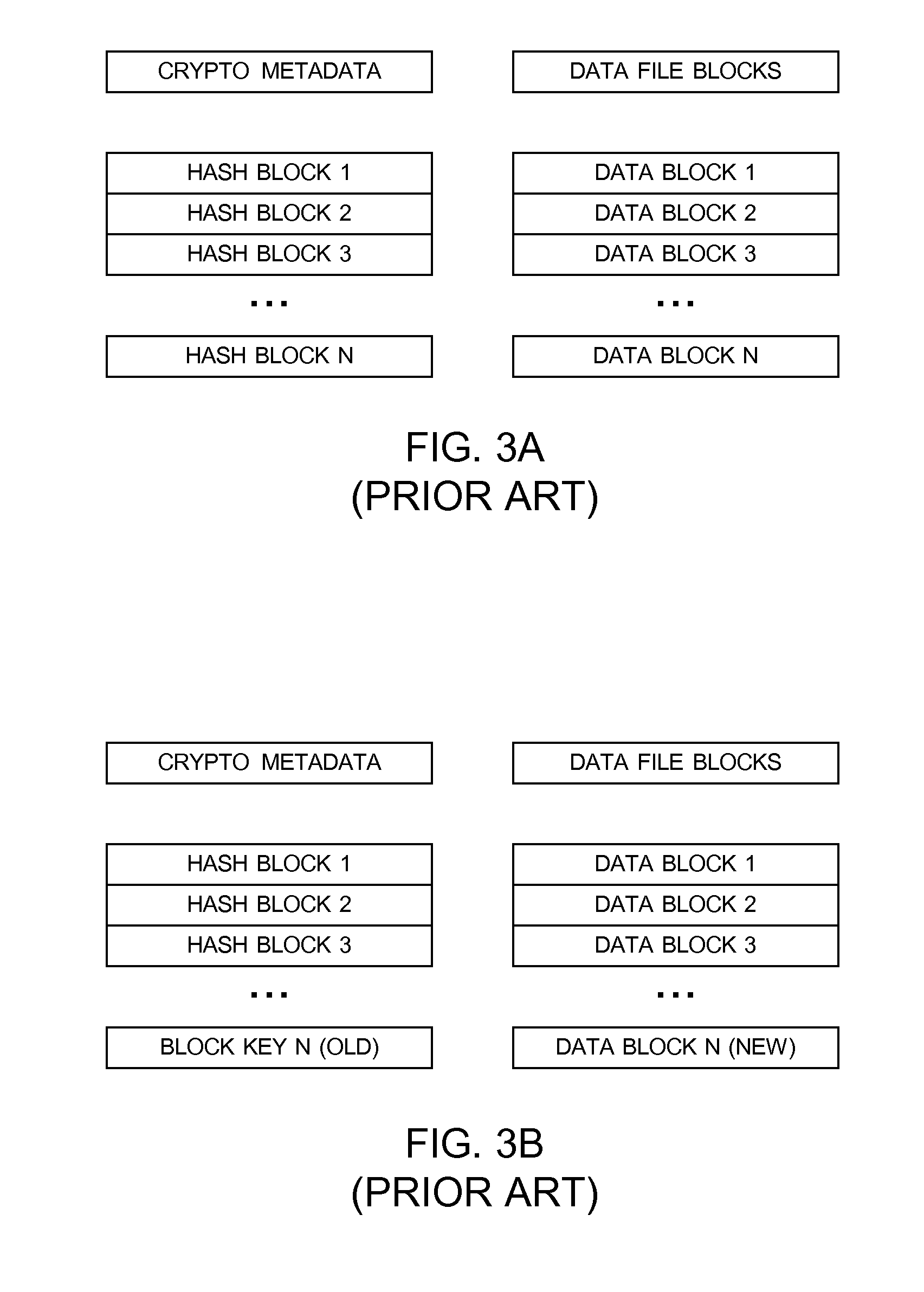
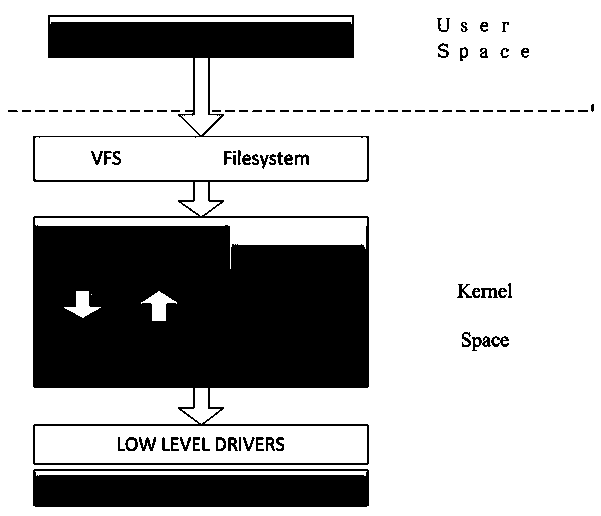
The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption.The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.. EFS is available in all versions of Windows except the home versions (see Supported operating systems below ...
Encrypted file system using TCPA
ActiveUS20030188179A1Digital data processing detailsUser identity/authority verificationComputerized systemControl register
A method for restricting access to an encryption key of an encrypted file system (EFS), whereby access is provided only when a computer system is booted in a trusted state. The EFS encrypts the files within a TPM chip according to TCPA specifications and simultaneously creates the encryption key, which is also stored in the TPM. The key is sealed to one or more platform control register (PCR) states (i.e., the TPM will export the key only when the PCRs are in a pre-defined state.). The original PCR states are modified during boot up of the computer system via a secure hashing algorithm, which extends a value of one PCR to a next PCR at each stage of the boot process and then hashes the value with the remaining content of the next PCR. When the system boot process is completed and before control passes to the user, the values within the PCRs are compared to values stored in a PCR table within the TPM, and the encryption key is exported to the OS kernel only when the PCR values match the table values. The control code of the TPM chip decrypts and exports the key only if the value of each and every PCR matches its corresponding table value. A complete match indicates that the computer system has completed a trusted boot sequence.
Owner:LENOVO PC INT
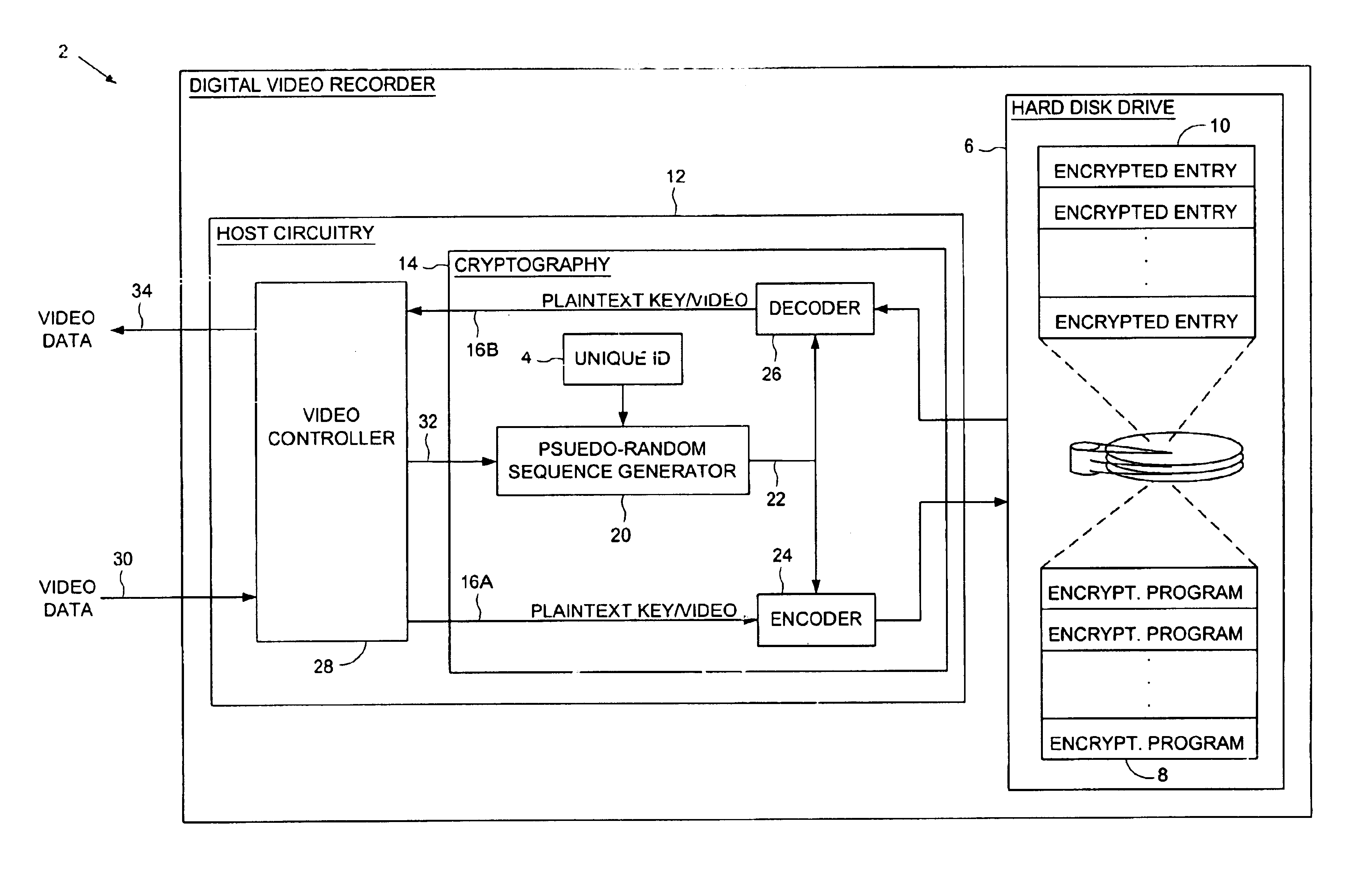
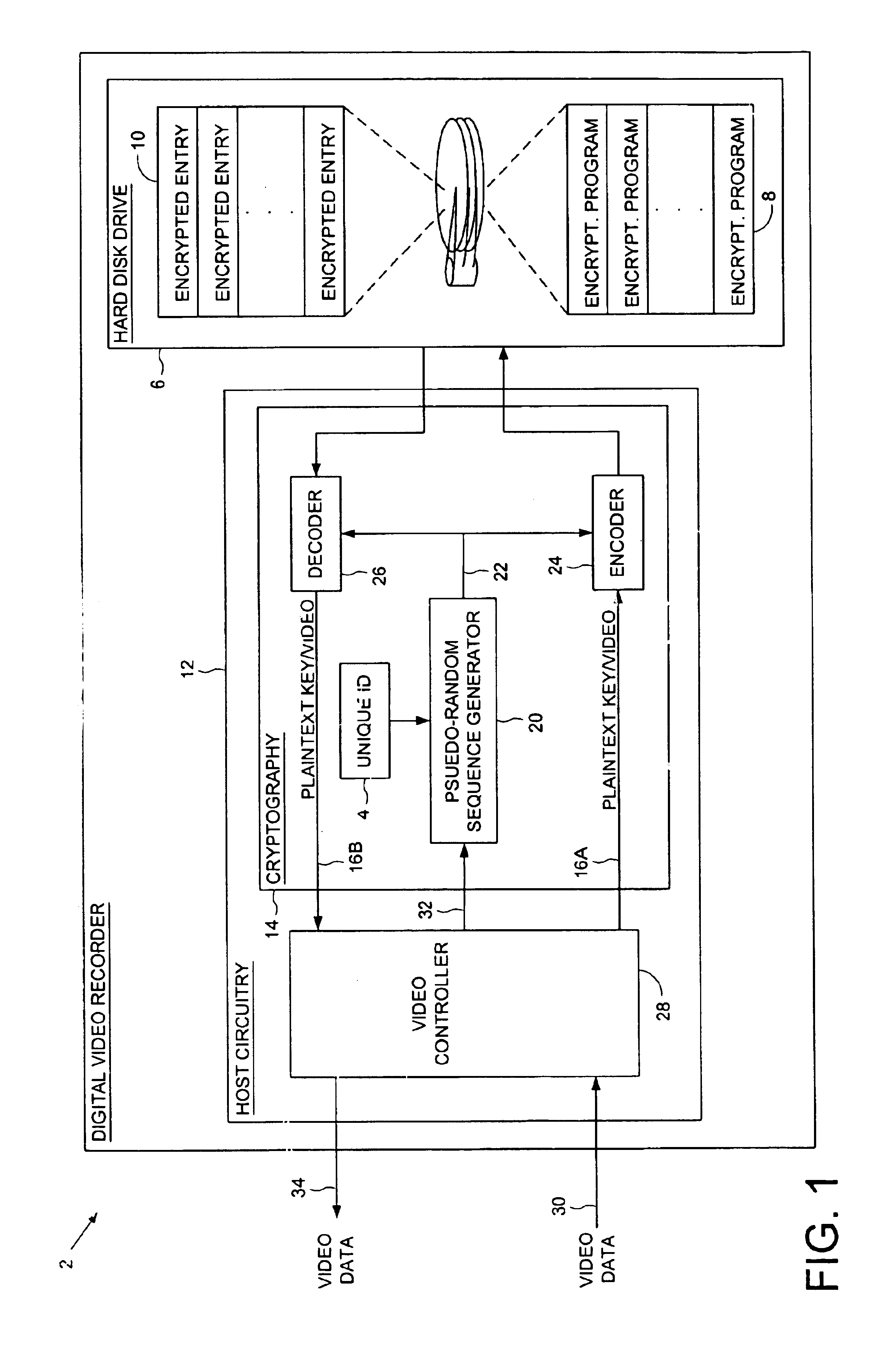
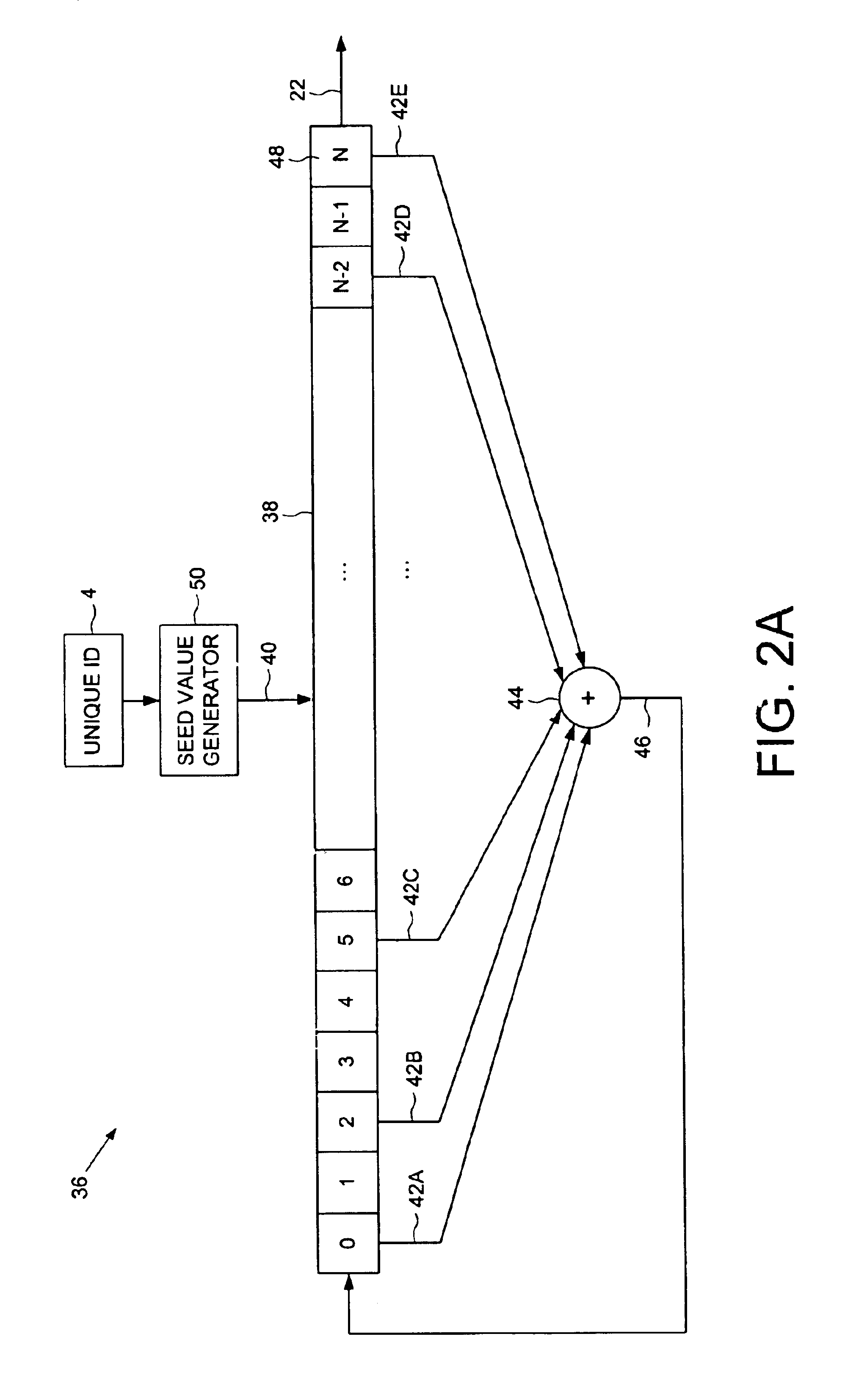
Digital video recorder employing a file system encrypted using a pseudo-random sequence generated from a unique ID
A digital video recorder (DVR) is disclosed comprising a unique ID, a hard disk drive (HDD) for storing a plurality of encrypted video programs and an encrypted file system, the encrypted file system comprising a plurality of encrypted file system entries for decrypting the plurality of video programs. The DVR further comprises host circuitry for interfacing with the HDD, the host circuitry comprising a cryptography facility for encrypting plaintext file system entries into the encrypted file system entries stored on the HDD, and for decrypting the encrypted file system entries read from the HDD into plaintext file system entries. The cryptography facility comprises a pseudo-random sequence generator, responsive to the unique ID, for generating a pseudo-random sequence. The cryptography facility further comprises an encoder for combining the pseudo-random sequence with the plaintext file system entries to generate the encrypted file system entries stored on the HDD, and a decoder for combining the pseudo-random sequence with the encrypted file system entries read from the HDD to generate the plaintext file system entries.
Owner:KEEN PERSONAL MEDIA +1
Encryption apparatus and method for providing an encrypted file system
InactiveUS20070253549A1Reduce the amount requiredSecure EncryptionComputer security arrangementsSecret communicationComputer hardwarePlaintext
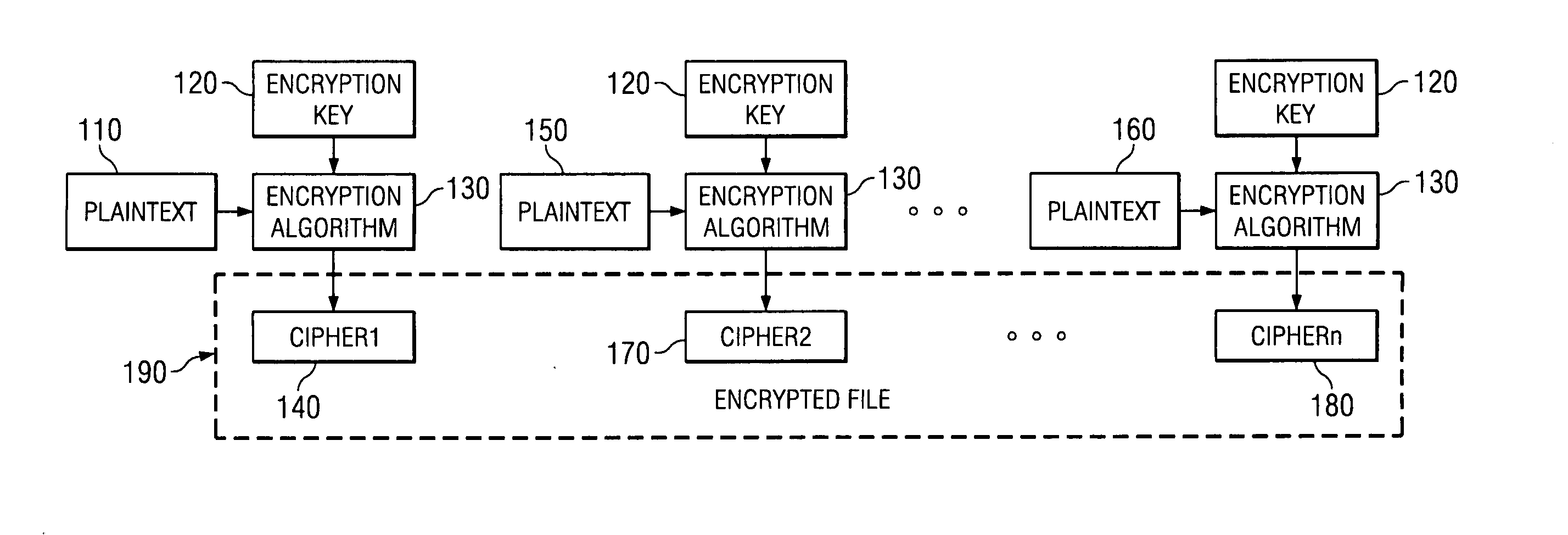
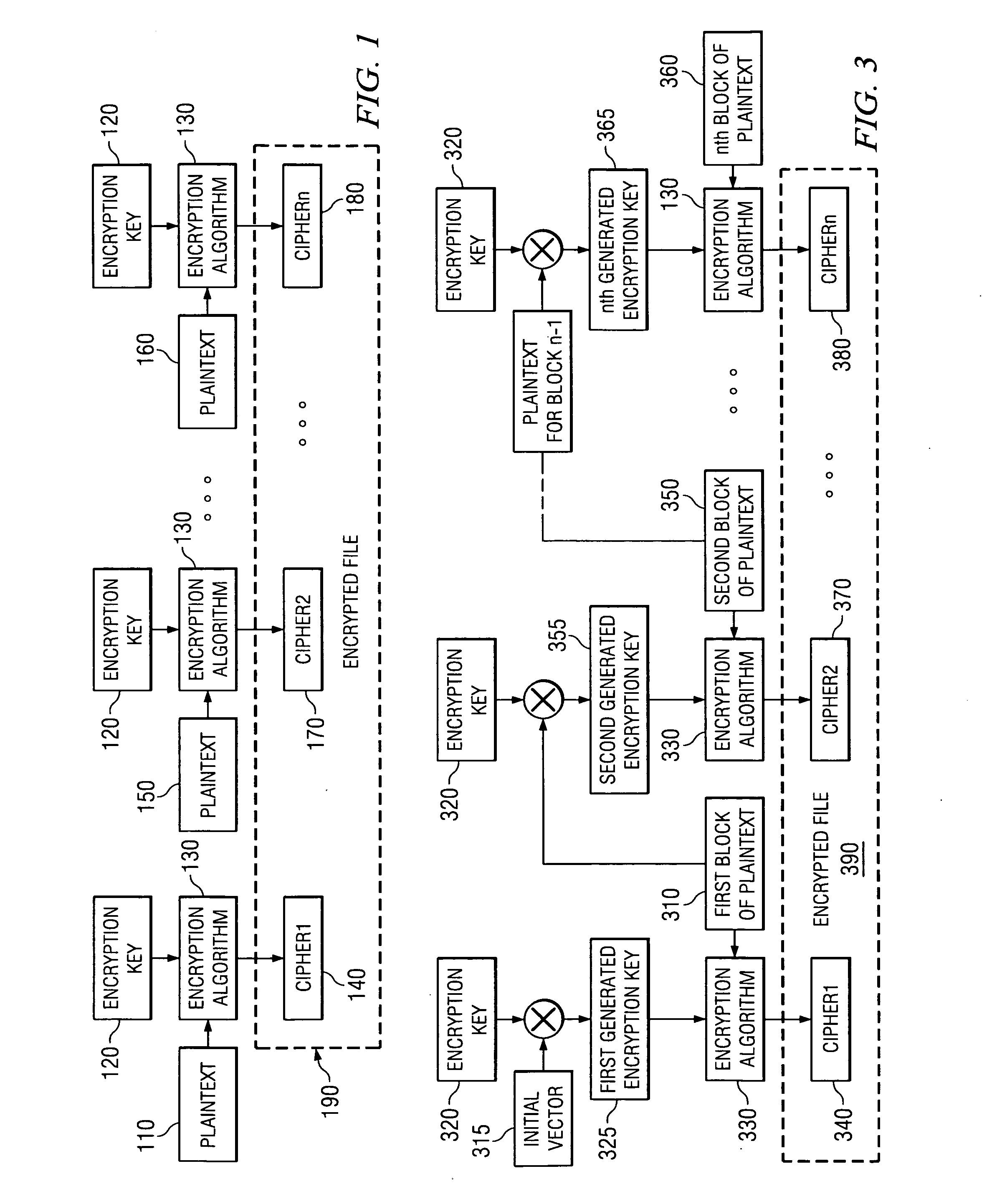
An encryption apparatus and method for providing an encrypted file system are provided. The encryption apparatus and method of the illustrative embodiments uses a combination of encryption methodologies so as to reduce the amount of decryption and re-encryption that is necessary to a file in the Encrypted File System in the event that the file needs to be modified. The encryption methodologies are interleaved, or alternated, with regard to each block of plaintext. In one illustrative embodiment, Plaintext Block Chaining (PBC) and Cipher Block Chaining (CBC) encryption methodologies are alternated for encrypting a sequence of blocks of data. The encryption of a block of plaintext is dependent upon the plaintext or a cipher generated for the plaintext of a previous block of data in the sequence of blocks of data so that the encryption is more secure than known Electronic Code Book encryption methodologies.
Owner:IBM CORP
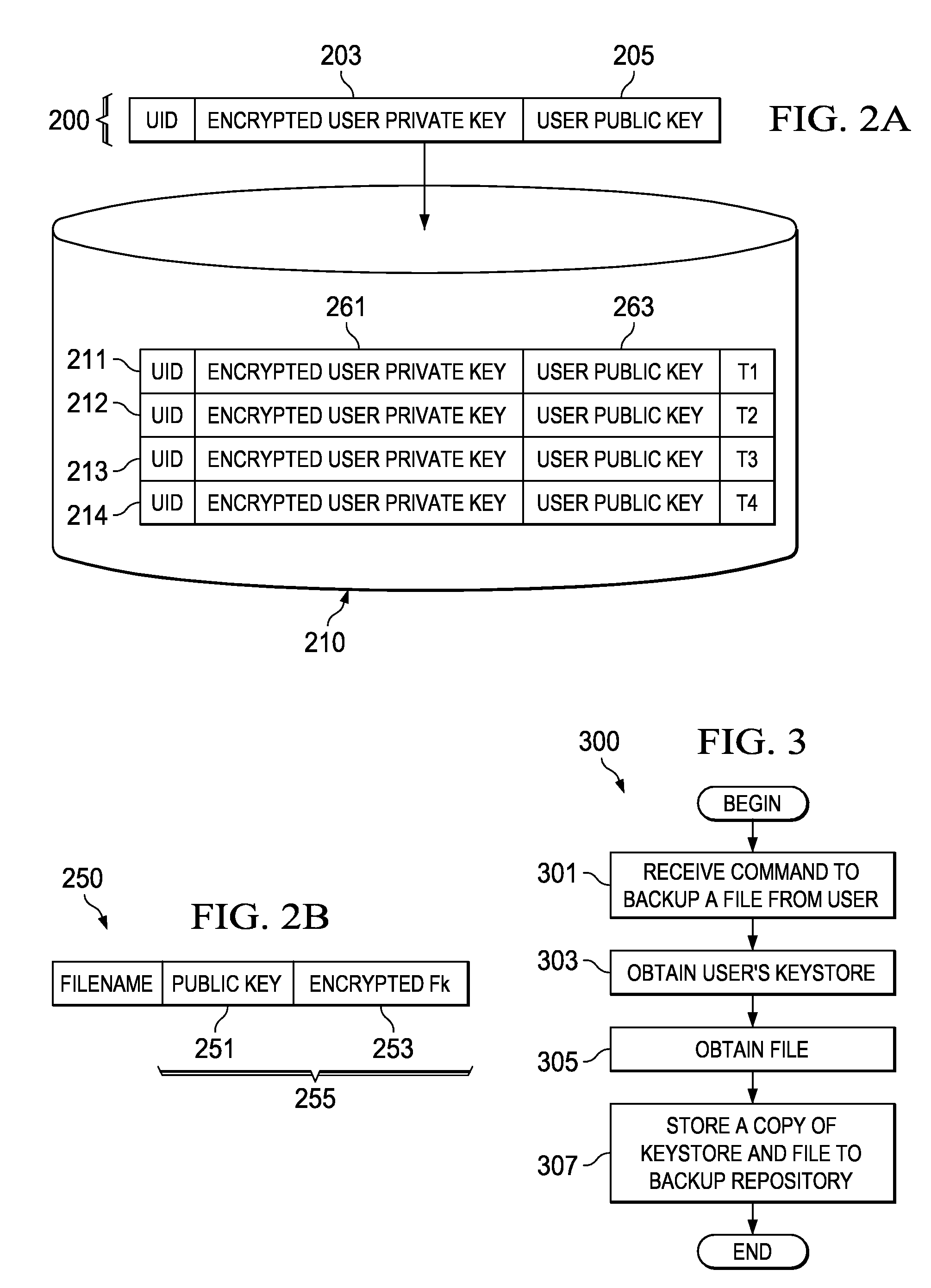
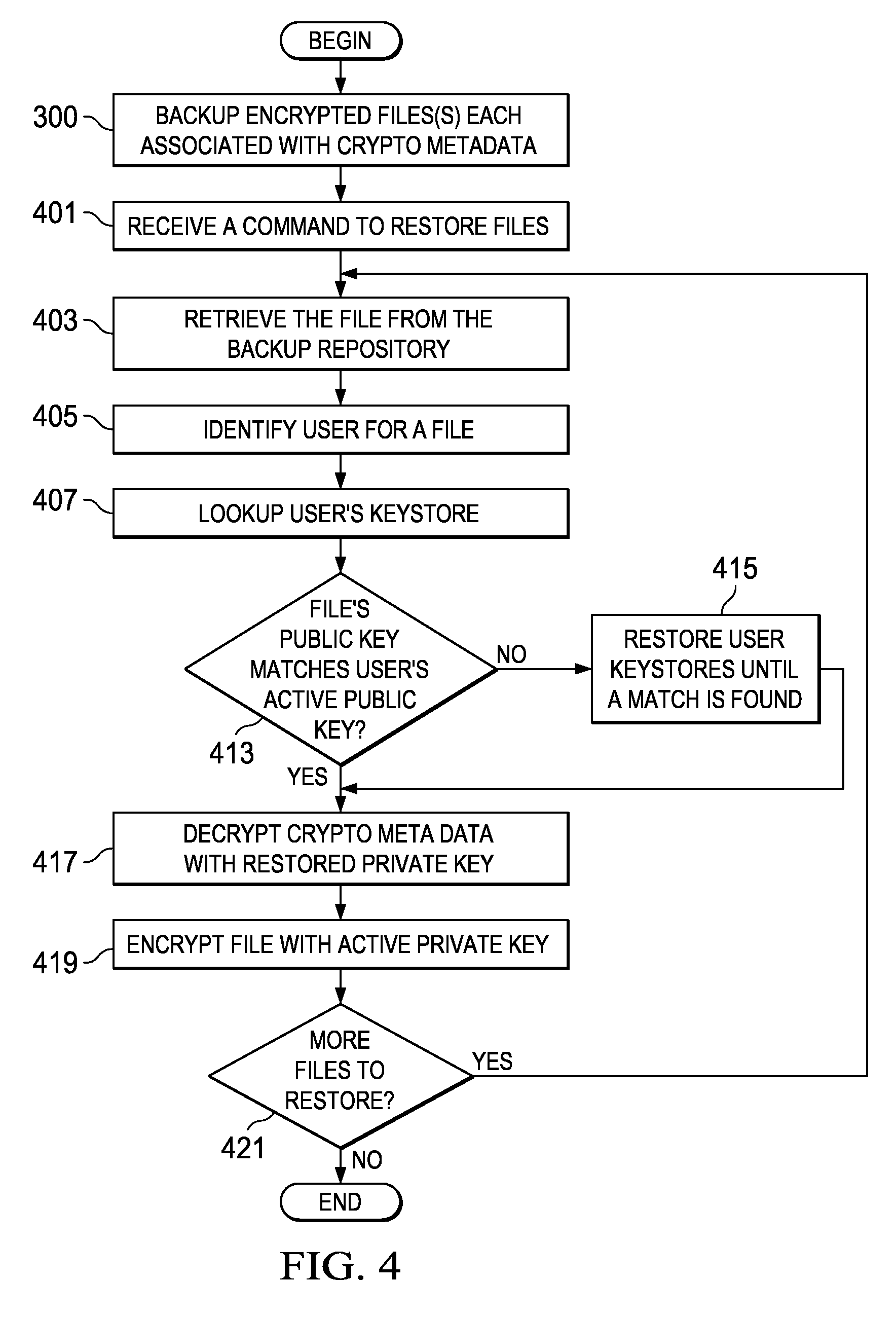
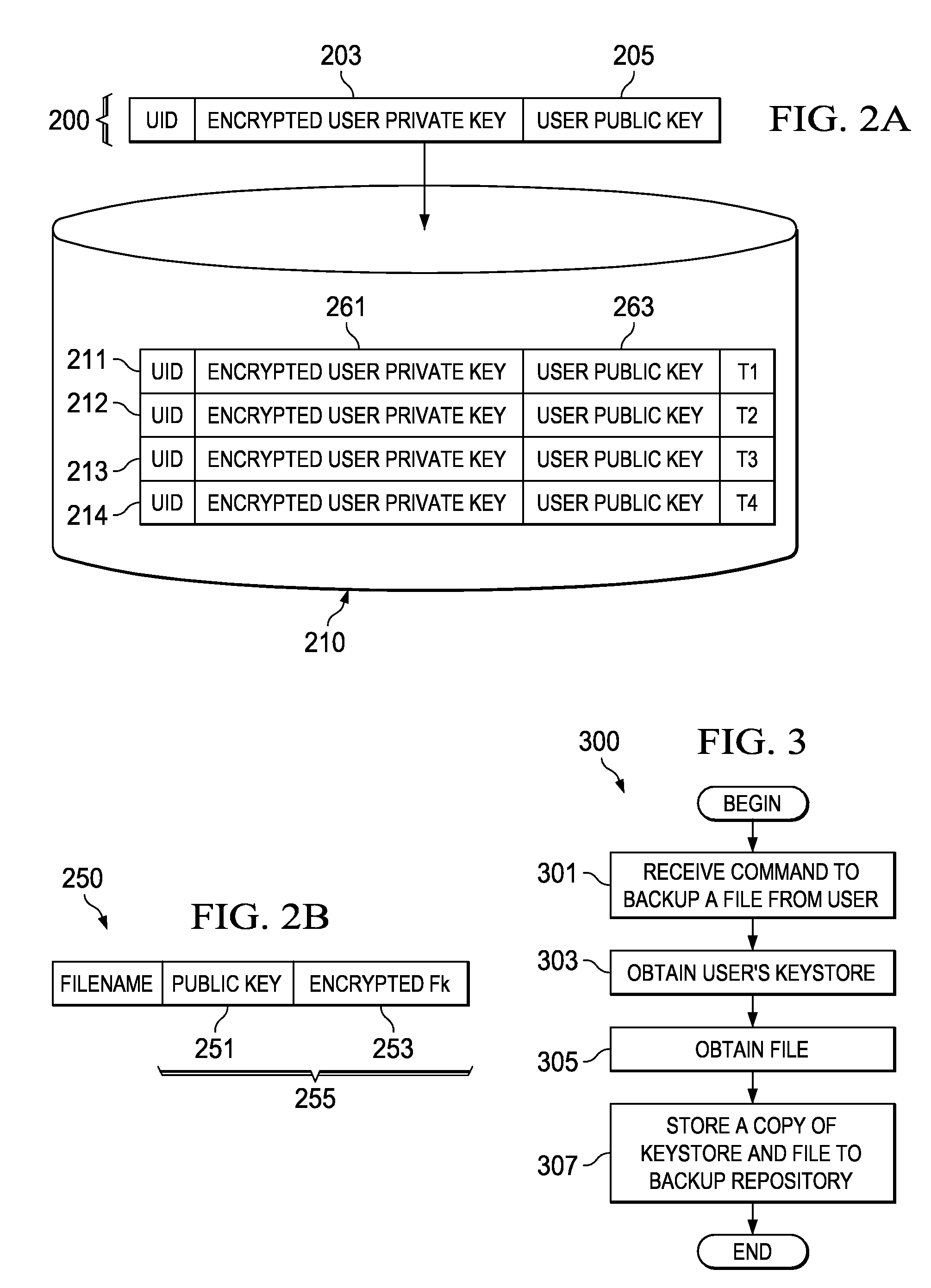
Method and apparatus for restoring encrypted files to an encrypting file system based on deprecated keystores
InactiveUS20090110198A1Error detection/correctionVolume/mass flow measurementData processing systemEncrypting file system
The present invention provides a computer implemented method, data processing system, and computer program product to restore an encrypted file. A computer receives a command to restore an encrypted file, wherein the encrypted file was previously backed up. The computer identifies a user associated with the encrypted file. The computer looks up a first keystore of the user based on the user, the first keystore having an active private key. The computer determines that a public key of the encrypted file fails to match an active public key of the first keystore. The computer restores a second keystore of the user to form a restored private key, wherein the second keystore was previously backed up. The computer responsive to a determination that the public key of the encrypted file fails to match the active public key of the first keystore, decrypts the encrypted file encryption key based on the restored private key to form a file encryption key. The computer encrypts the file encryption key with the active private key of the first keystore.
Owner:IBM CORP
General Purpose Distributed Encrypted File System
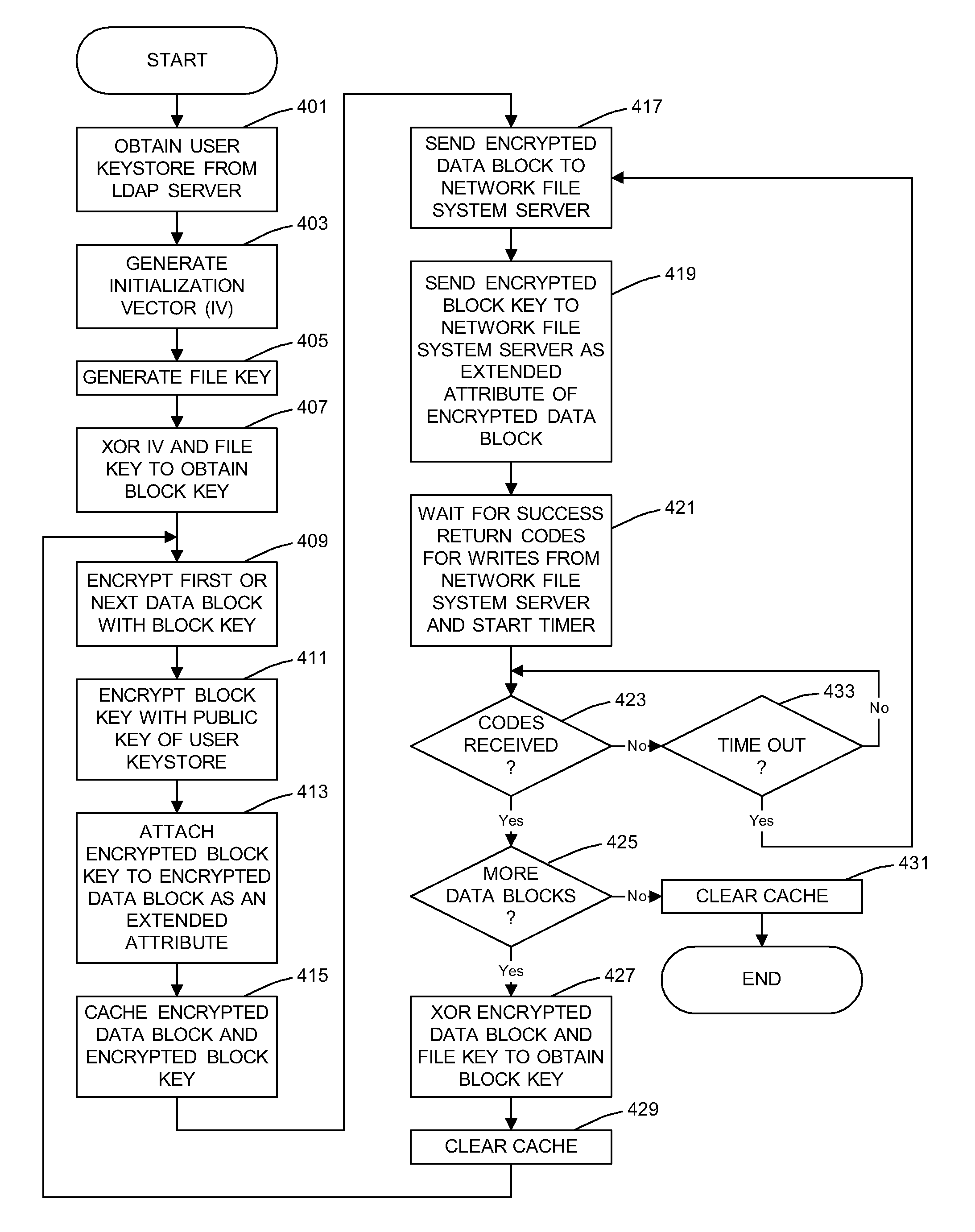
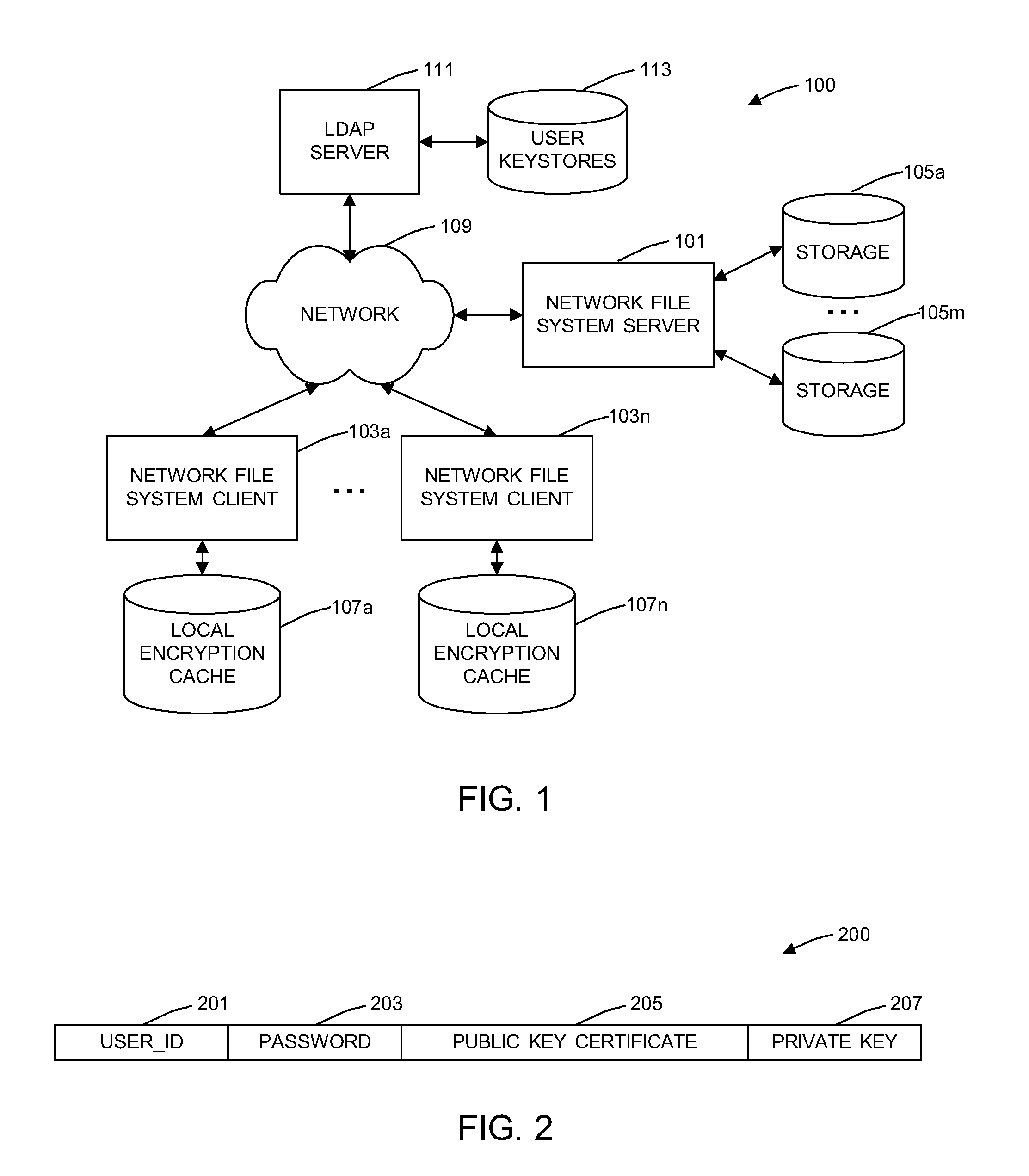
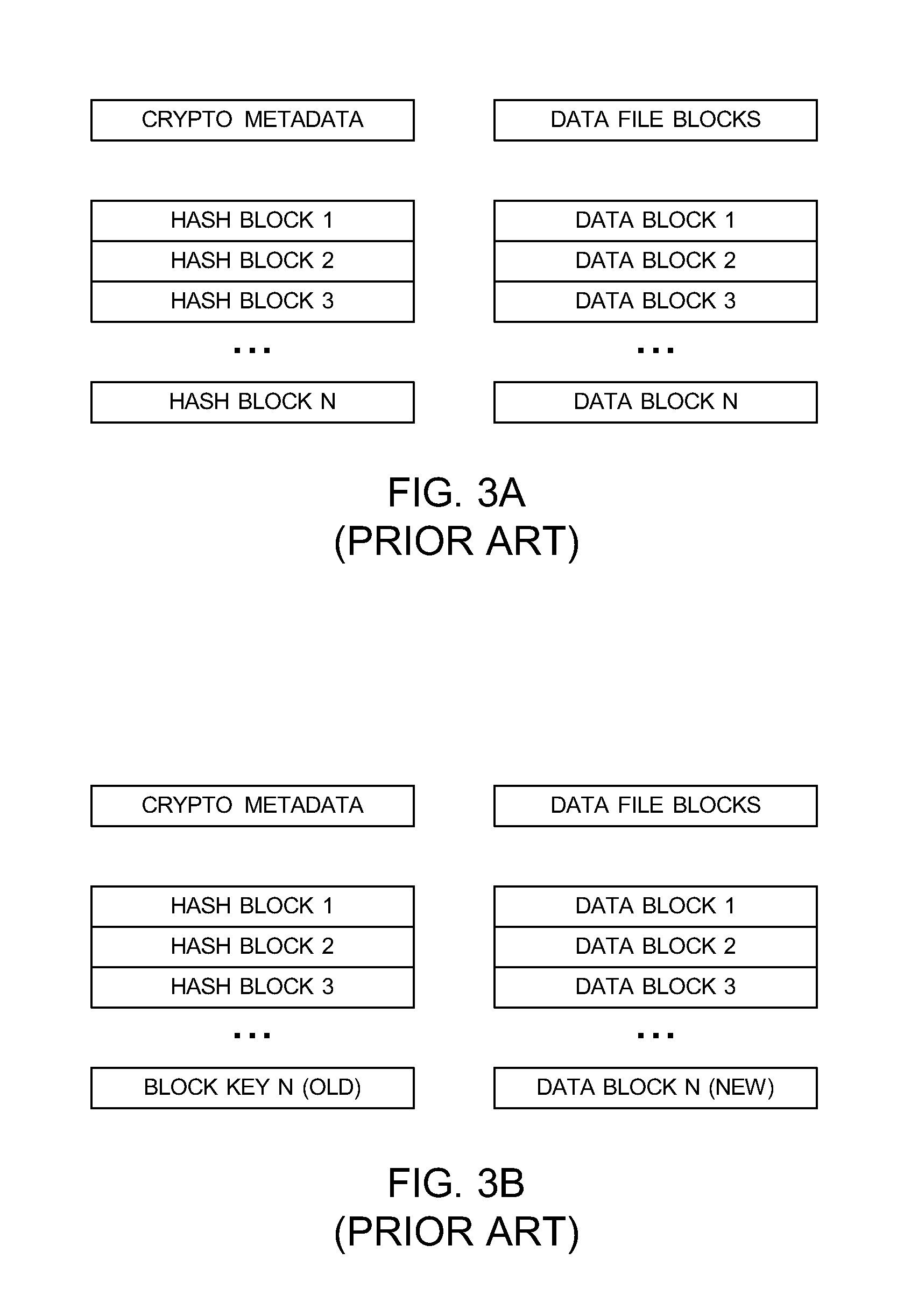
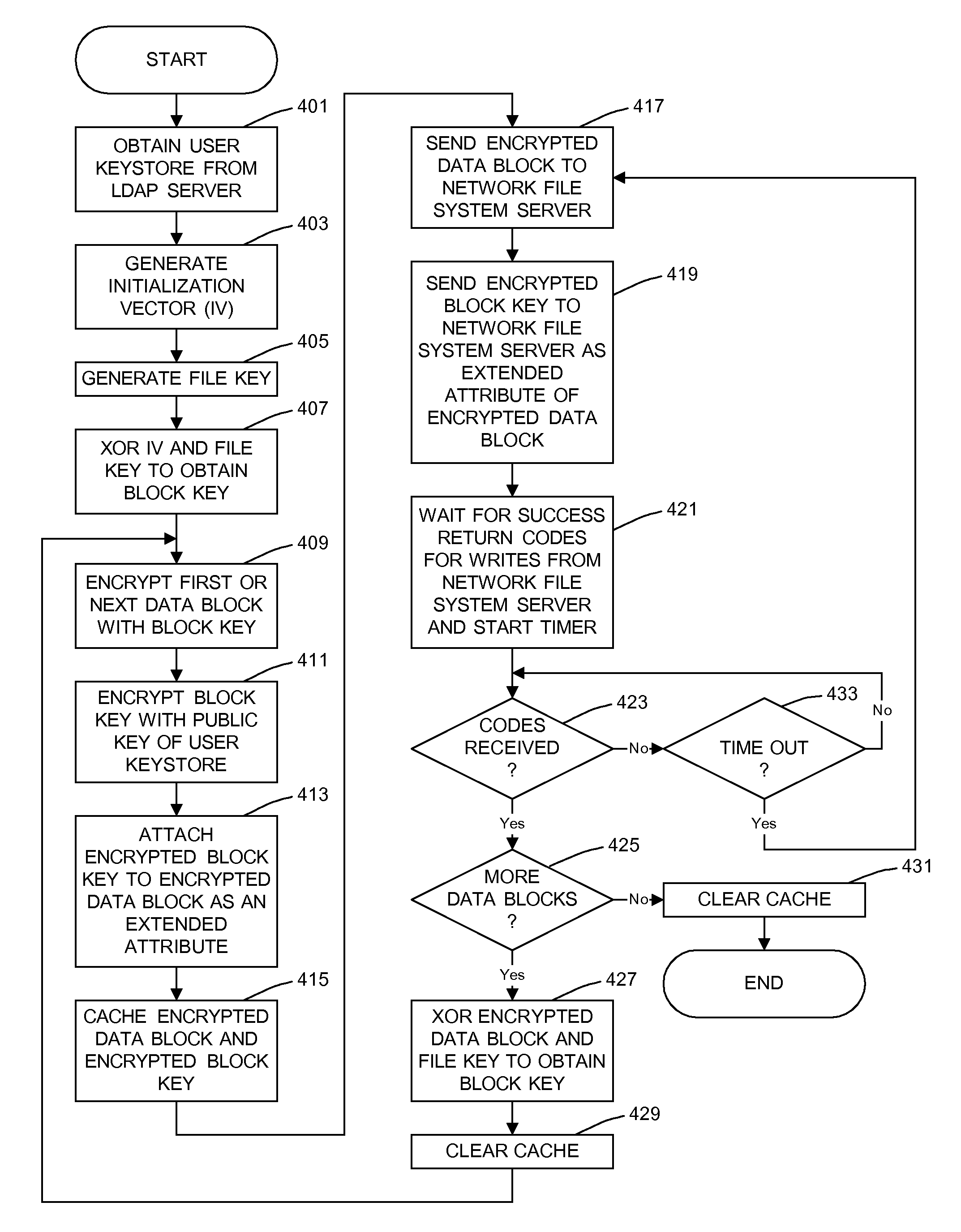
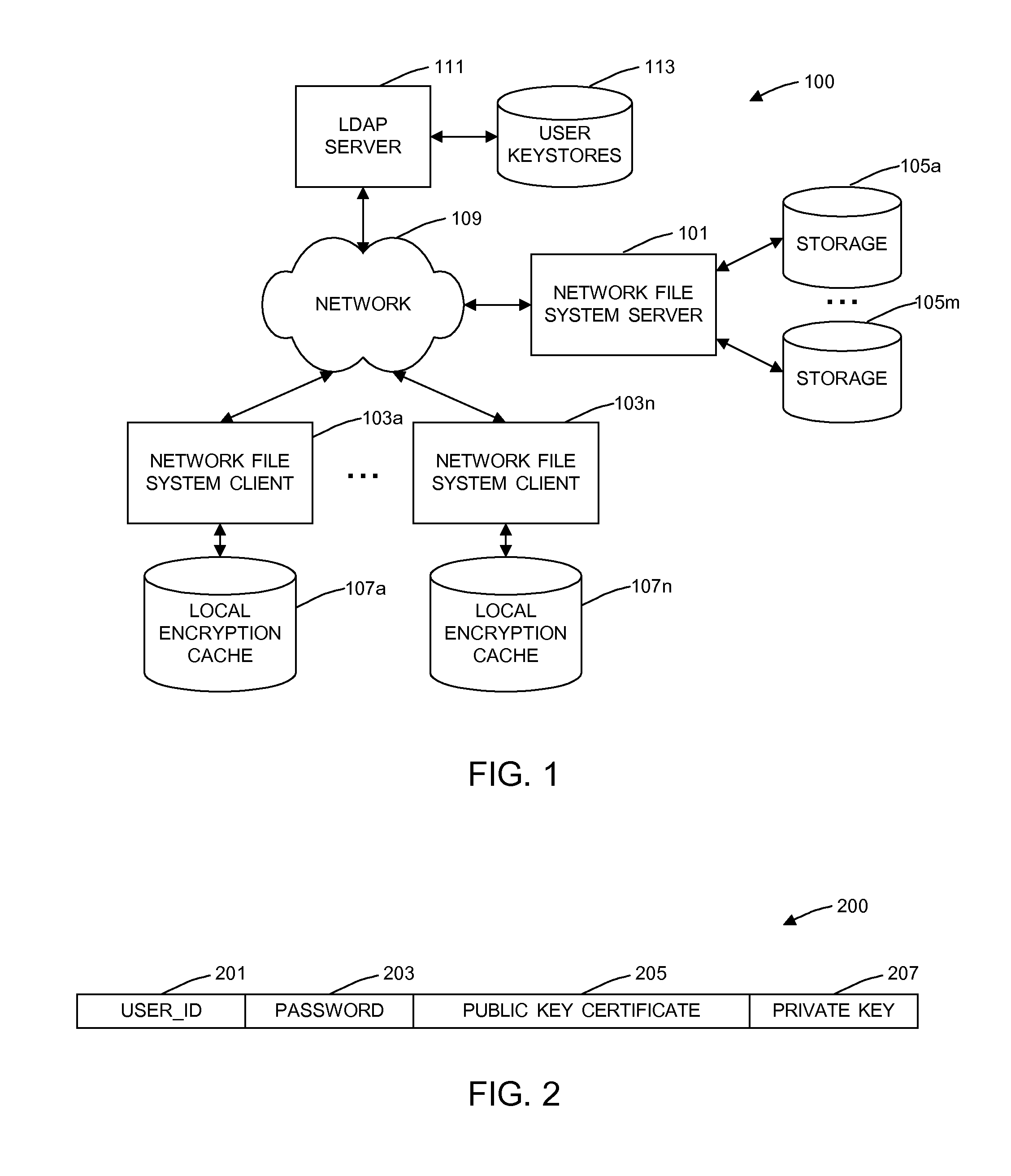
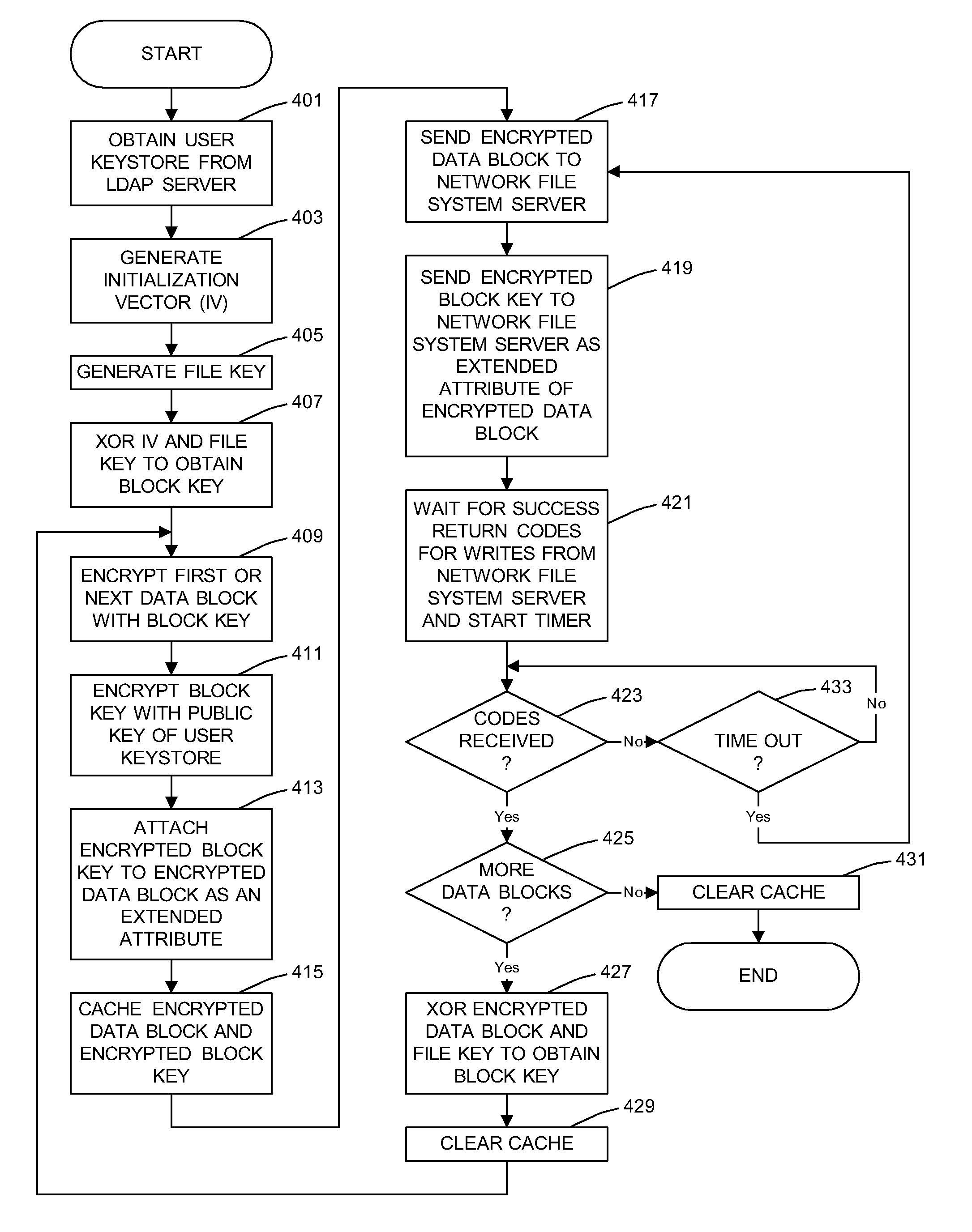
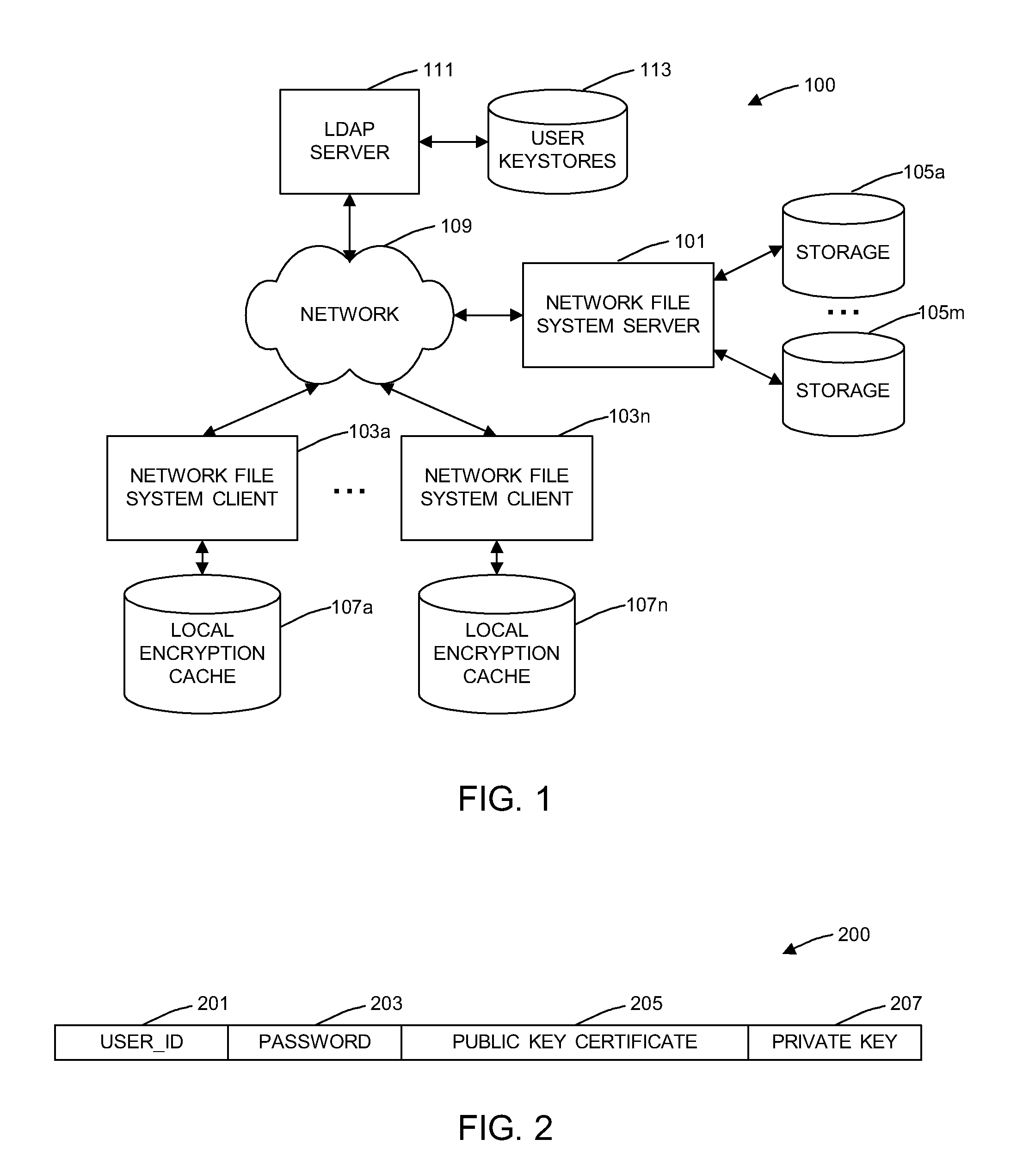
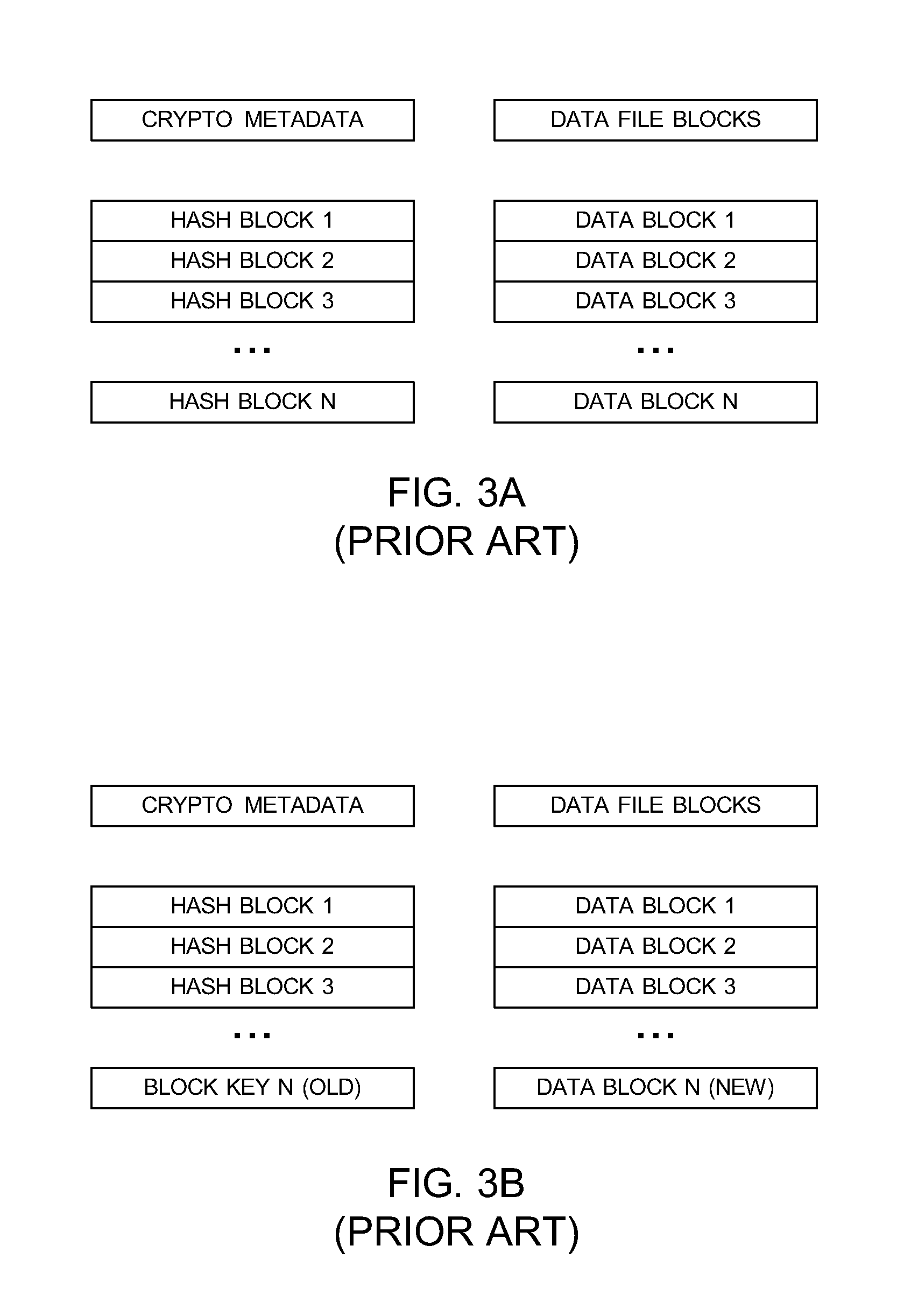
A general purpose distributed encrypted file system generates a block key on a client machine. The client machine encrypts a file using the block key. Then, the client encrypts the block key on the first client machine with a public key of a keystore associated with a user and associates the encrypted block key with the encrypted data block as crypto metadata. The client machine caches the encrypted data block and the crypto metadata and sends the encrypted data block and the crypto metadata to a network file system server. When the client machine receives a return code from the network file system server indicating successful writes of the encrypted data block and the crypto metadata, the client machine clears the cached encrypted data block and the crypto metadata.
Owner:IBM CORP
Encrypted file system using TCPA
InactiveUS7343493B2Without worrying about compromising the security of the EFSDigital data processing detailsUnauthorized memory use protectionControl registerComputerized system
A method for restricting access to an encryption key of an encrypted file system (EFS), whereby access is provided only when a computer system is booted in a trusted state. The EFS encrypts the files within a TPM chip according to TCPA specifications and simultaneously creates the encryption key, which is also stored in the TPM. The key is sealed to one or more platform control register (PCR) states (i.e., the TPM will export the key only when the PCRs are in a pre-defined state.). The original PCR states are modified during boot up of the computer system via a secure hashing algorithm, which extends a value of one PCR to a next PCR at each stage of the boot process and then hashes the value with the remaining content of the next PCR. When the system boot process is completed and before control passes to the user, the values within the PCRs are compared to values stored in a PCR table within the TPM, and the encryption key is exported to the OS kernel only when the PCR values match the table values. The control code of the TPM chip decrypts and exports the key only if the value of each and every PCR matches its corresponding table value. A complete match indicates that the computer system has completed a trusted boot sequence.
Owner:LENOVO PC INT
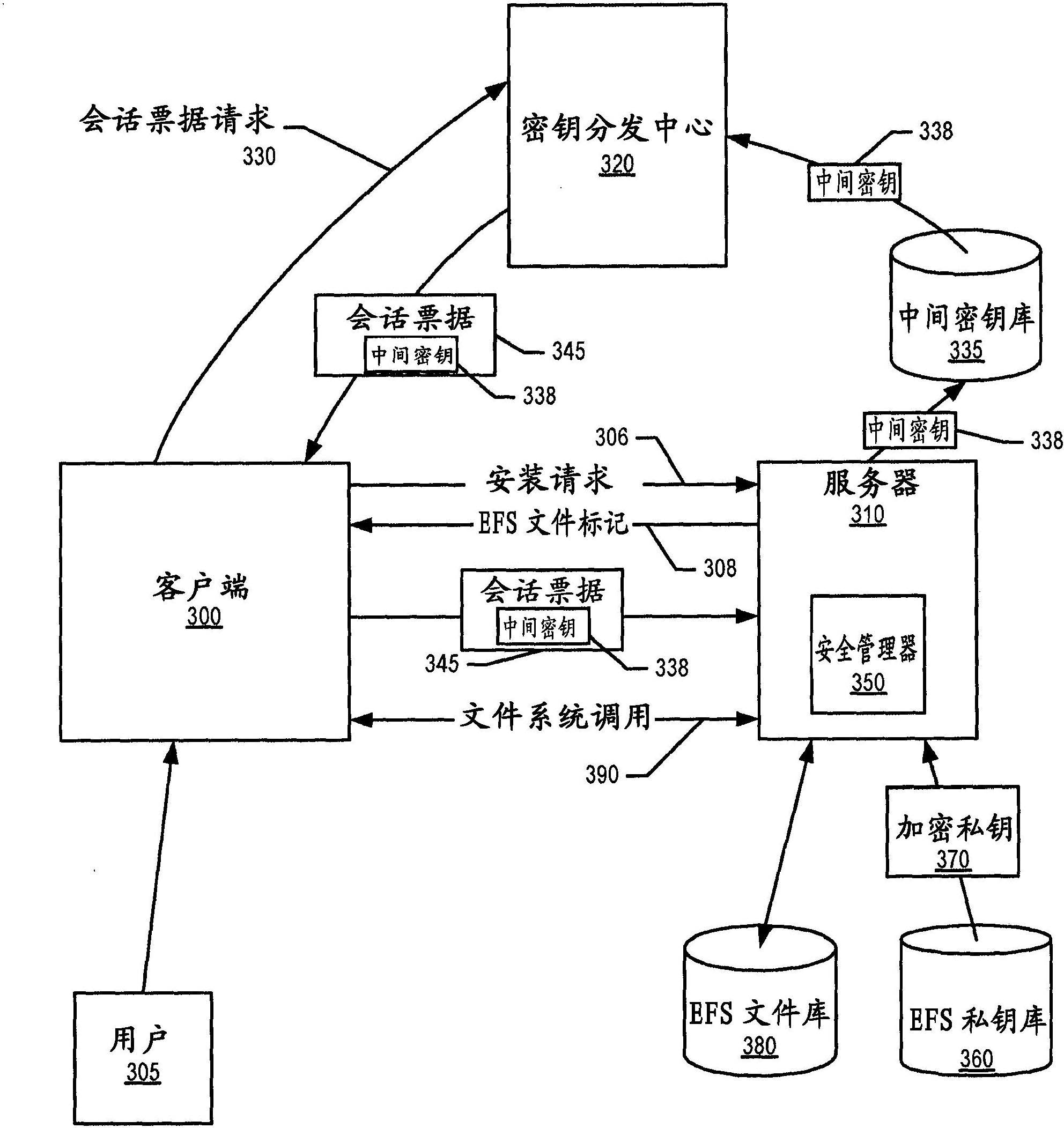
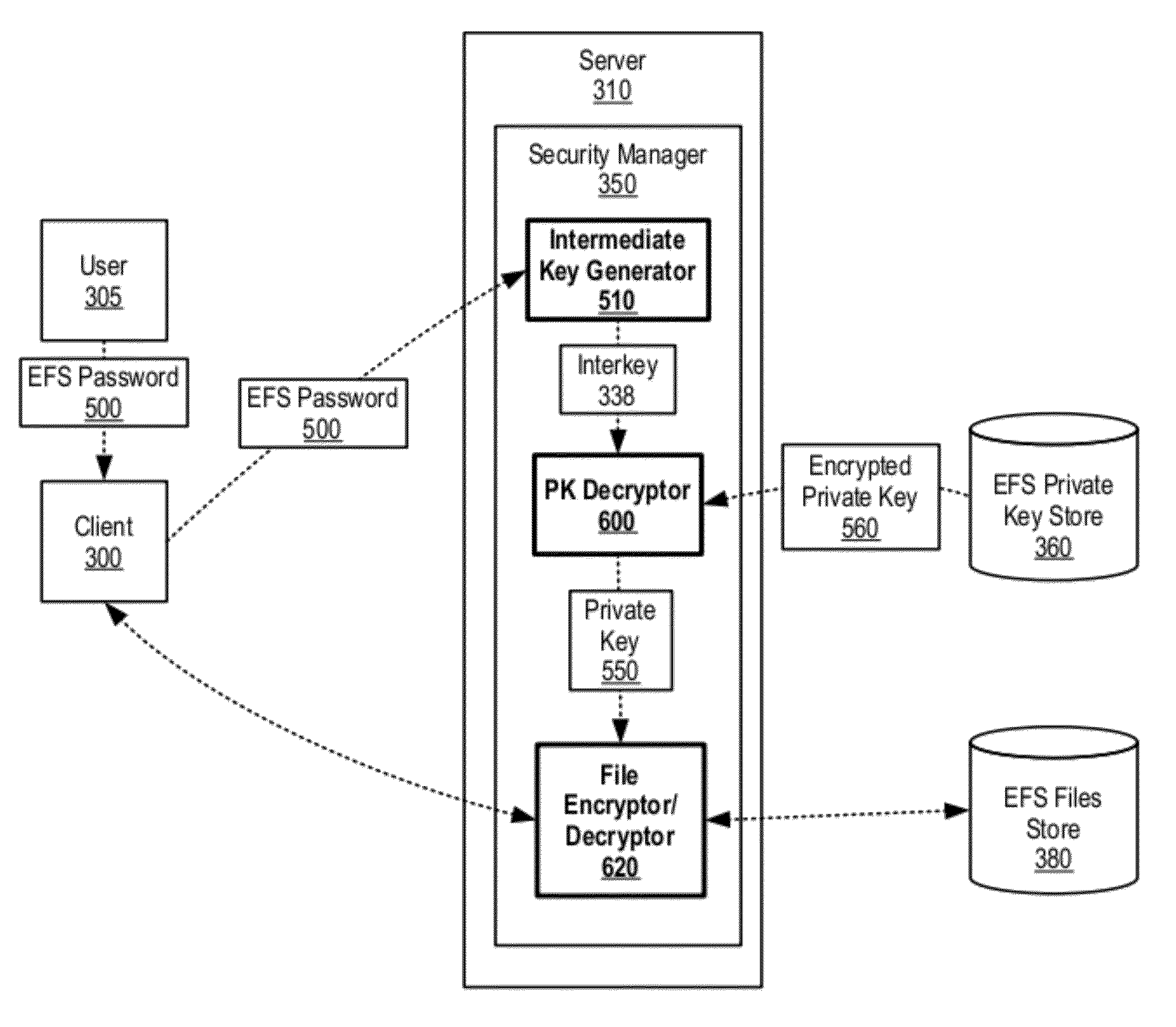
Secure kerberized access of encrypted file system
ActiveCN102668503AComputer security arrangementsSpecial data processing applicationsCryptographic protocolClient-side
A file server receives a request from a client to mount an encrypted file system. The file server informs the client that the requested file system is encrypted and, in turn, receives a session ticket from the client that includes a security protocol mounting selection. The file server decrypts the client's user's encrypted private key, and then decrypts the requested encrypted file system using the private key. In turn, the file server sends the decrypted file system to the client over a secure channel, which is based upon the security protocol mounting selection. In one embodiment, a key distribution center server receives a request from the client for the client's user to access the encrypted file system at the file server. The key distribution center server retrieves an intermediate key; includes the intermediate key in a session ticket; and sends the session ticket to the client.
Owner:INT BUSINESS MASCH CORP
Kernel-level virtual polymerization and parallel encryption method for class-oriented Linux system
InactiveCN103294958AReduce computing pressureImprove encryption and decryption throughputDigital data protectionMultiple encryptionComputer hardware
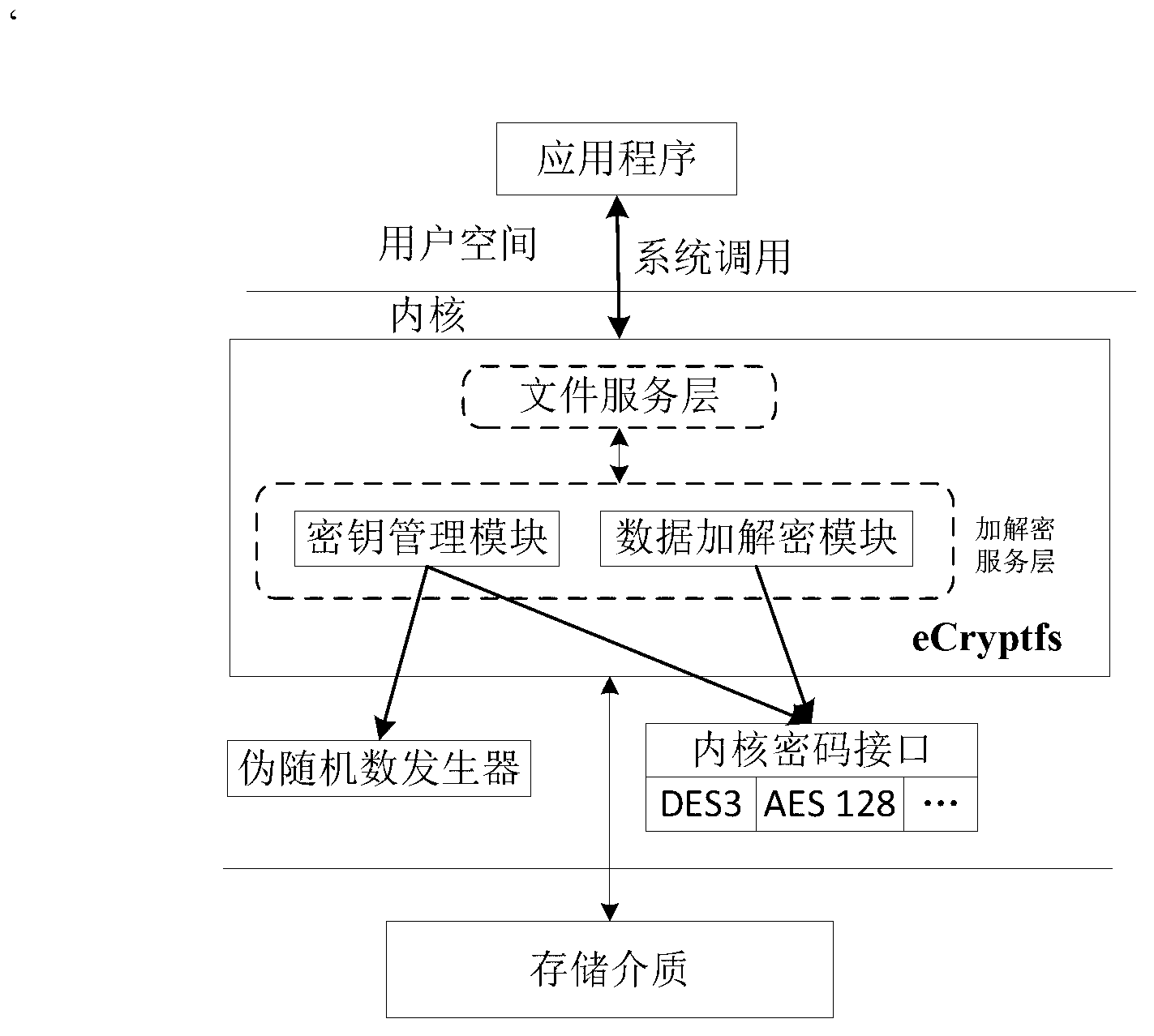
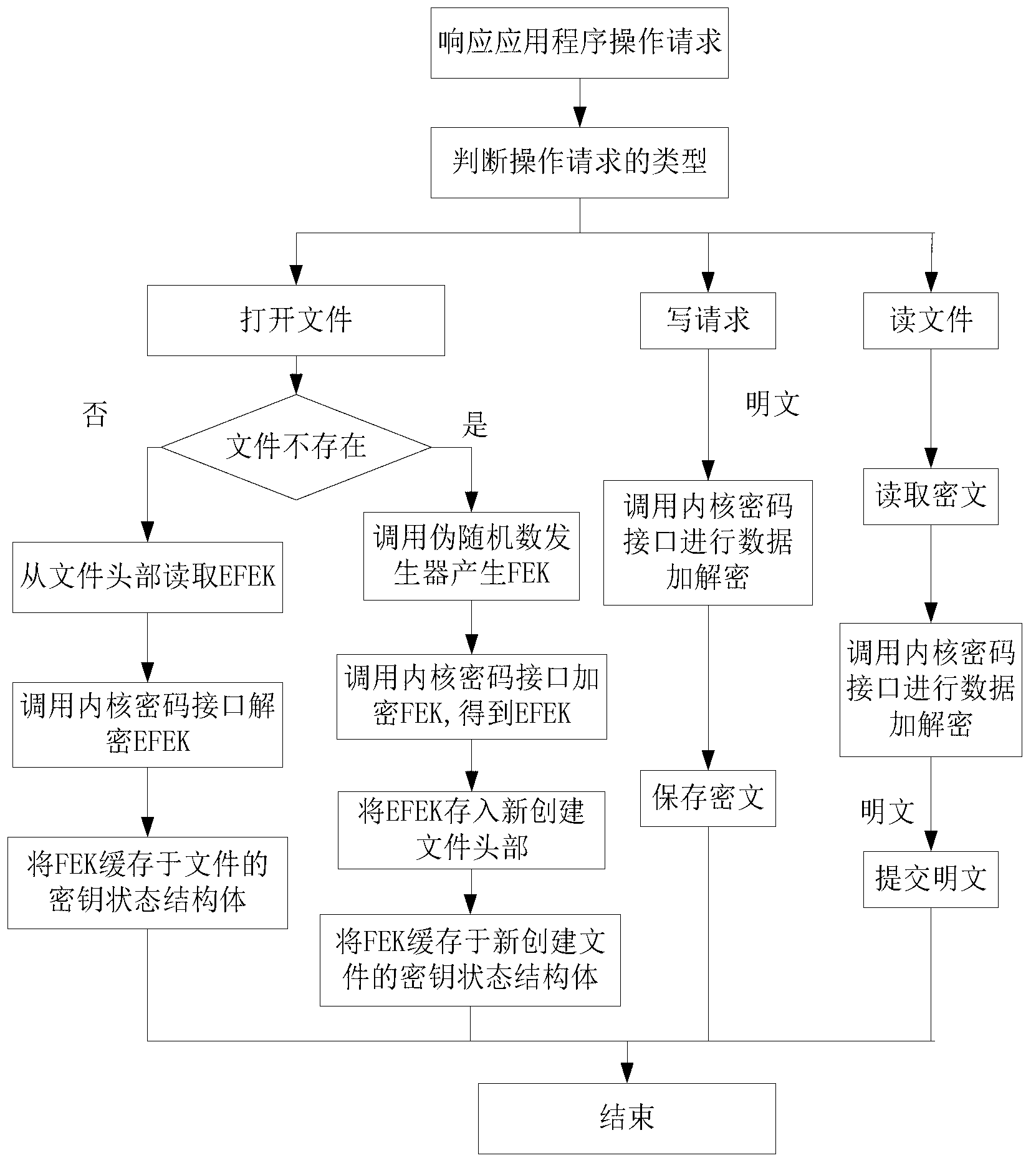
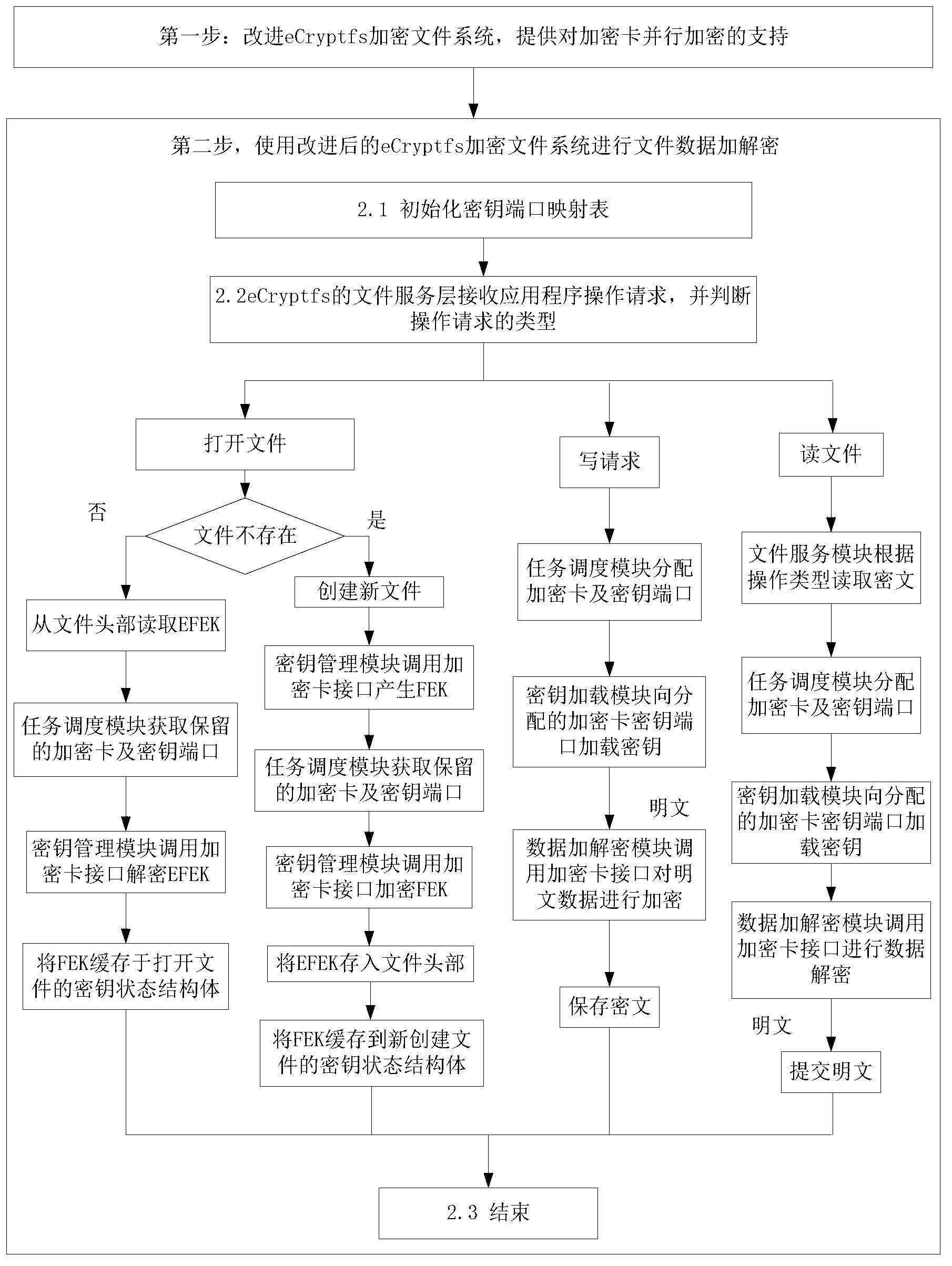
The invention discloses a kernel-level virtual polymerization and parallel encryption method for a class-oriented Linux system, and solves the technical problem of implementing parallel encryption of files by a Linux kernel drive encryption card. According to the technical scheme, an original key management module and an original data encrypting-decrypting module in an eCryptfs (enterprise cryptographic filesystem) are modified, and a virtual polymerization module is designed and implemented; in the virtual polymerization module, a key port mapping table is responsible for storing key port states of all encryption cards, a task scheduling module dispatches the encryption modules and key ports, and a key loading module imports keys to the key ports; the modified key management module and the modified data encrypting-decrypting module call programming ports of the encryption cards by the encryption cards and key ports dispatched by the virtual polymerization module, and encryption and decryption of the parallel files is completed. Through the method, the files can be encrypted and decrypted by multiple encryption cards on any class-oriented Linux computers supporting the eCryptfs, operational pressure of a system CPU (computer processing unit) is relieved, and encrypting speed and safety are improved.
Owner:NAT UNIV OF DEFENSE TECH
General purpose distributed encrypted file system
A general purpose distributed encrypted file system generates a block key on a client machine. The client machine encrypts a file using the block key. Then, the client encrypts the block key on the first client machine with a public key of a keystore associated with a user and associates the encrypted block key with the encrypted data block as crypto metadata. The client machine caches the encrypted data block and the crypto metadata and sends the encrypted data block and the crypto metadata to a network file system server. When the client machine receives a return code from the network file system server indicating successful writes of the encrypted data block and the crypto metadata, the client machine clears the cached encrypted data block and the crypto metadata.
Owner:INT BUSINESS MASCH CORP
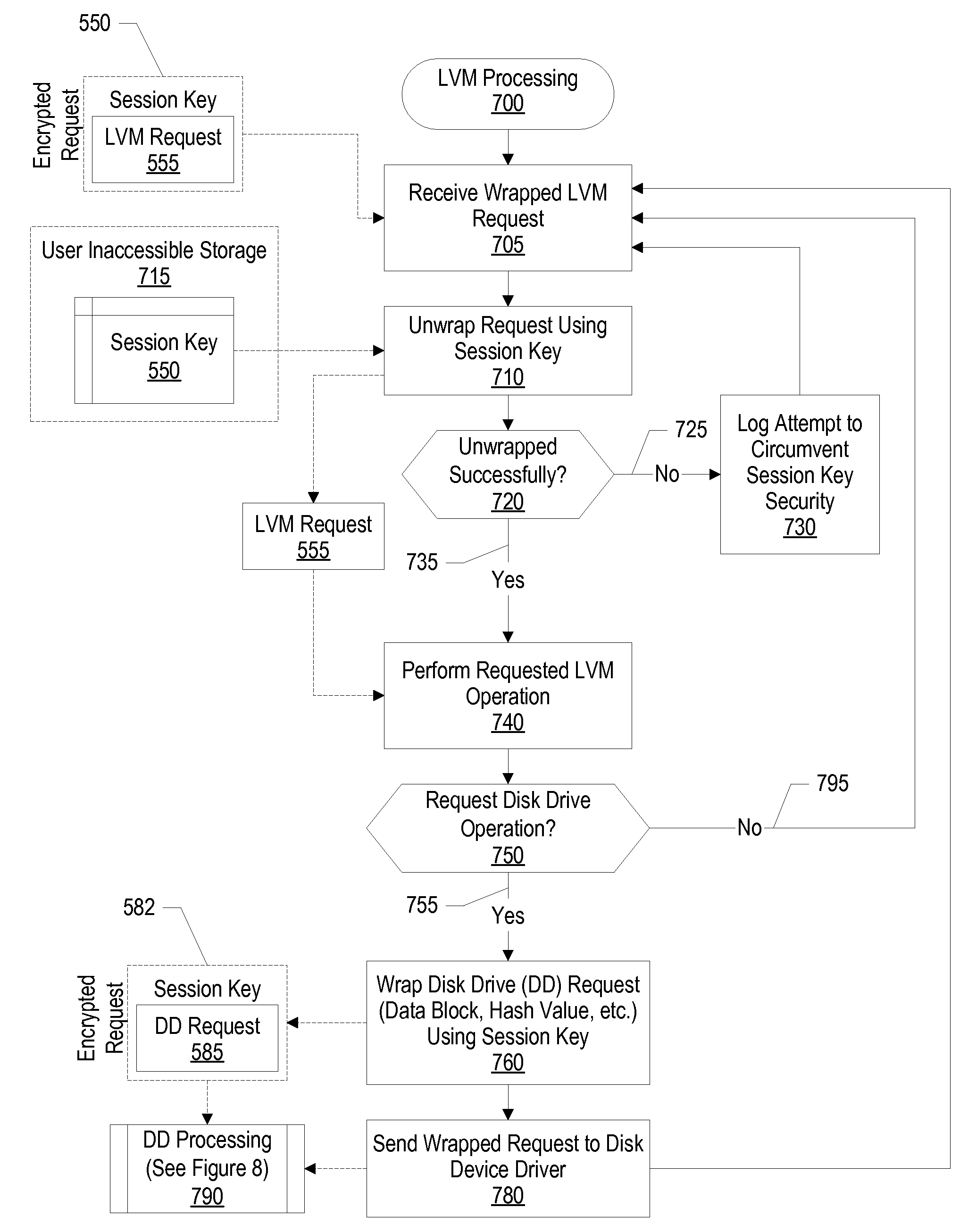
Preventing replay attacks in encrypted file systems
InactiveUS20090208002A1Encryption apparatus with shift registers/memoriesUnauthorized memory use protectionEncrypting file systemSession key
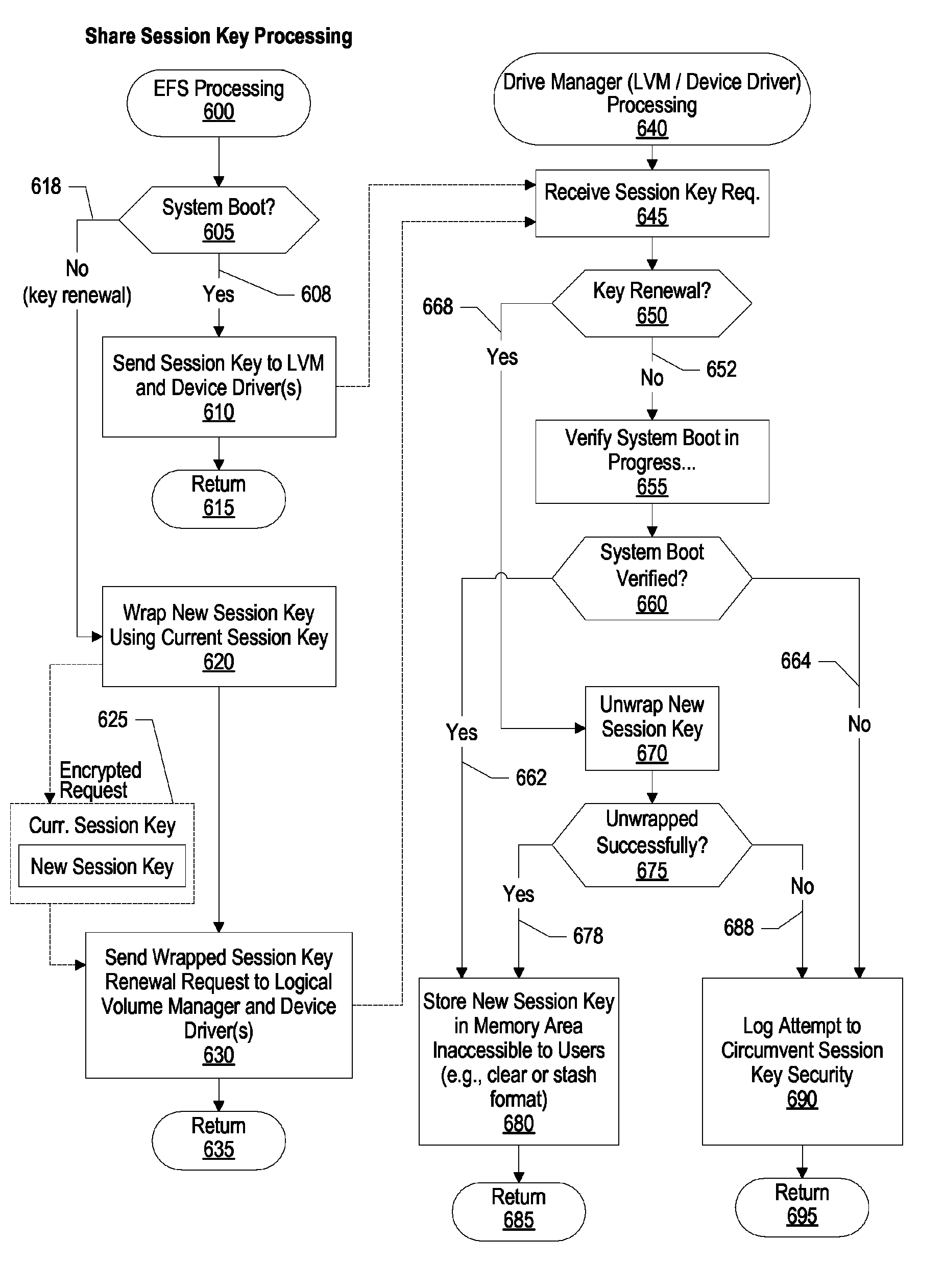
Replay attacks in an encrypted file system are prevented by generating a session key and providing the session key to one or more drive managers and an encrypted file system process. When a drive request is received by the encrypted file system process the drive request is encrypted using the generated session key. The encrypted drive request is sent to a drive manager. The drive manager attempts to decrypt the drive request using the session key. If the encrypted drive request is successfully decrypted, then the drive manager performs the requested operation. On the other hand, if the request is not decrypted successfully, then the request is not performed by the drive manager. Drive managers can include both disk device drivers and a logical volume managers.
Owner:IBM CORP
Encrypted file system mounting method and device
InactiveCN109033869AEnsure data securityWithout human interventionDigital data protectionEncrypting file systemData security
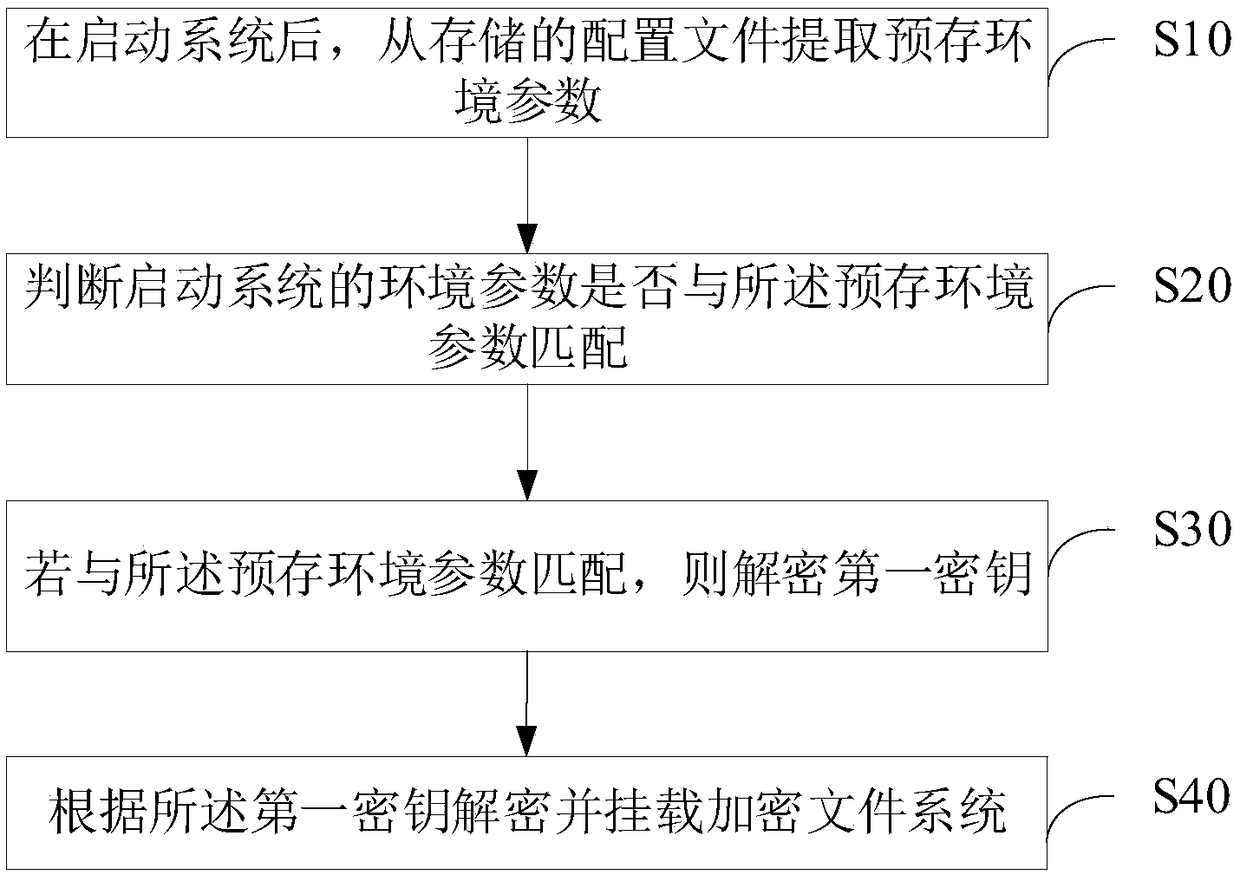
The invention relates to the field of file mounting and provides an encrypted file system mounting method and device. The method includes extracting pre-stored environment parameters from a stored configuration file after starting that system; judging whether an environmental parameter of the starting system matches with the pre-stored environmental parameter; decrypting the first key if it matches the pre-stored environment parameter; decrypting and mounting the encrypted file system according to the first key. The application can protect the data security of the encrypted file system, meanwhile ensure the normal operation of the encrypted file system without artificial interference, and reduce the operation cost.
Owner:深圳虚觅者科技有限公司
Method and apparatus for accessing an encrypted file system using non-local keys
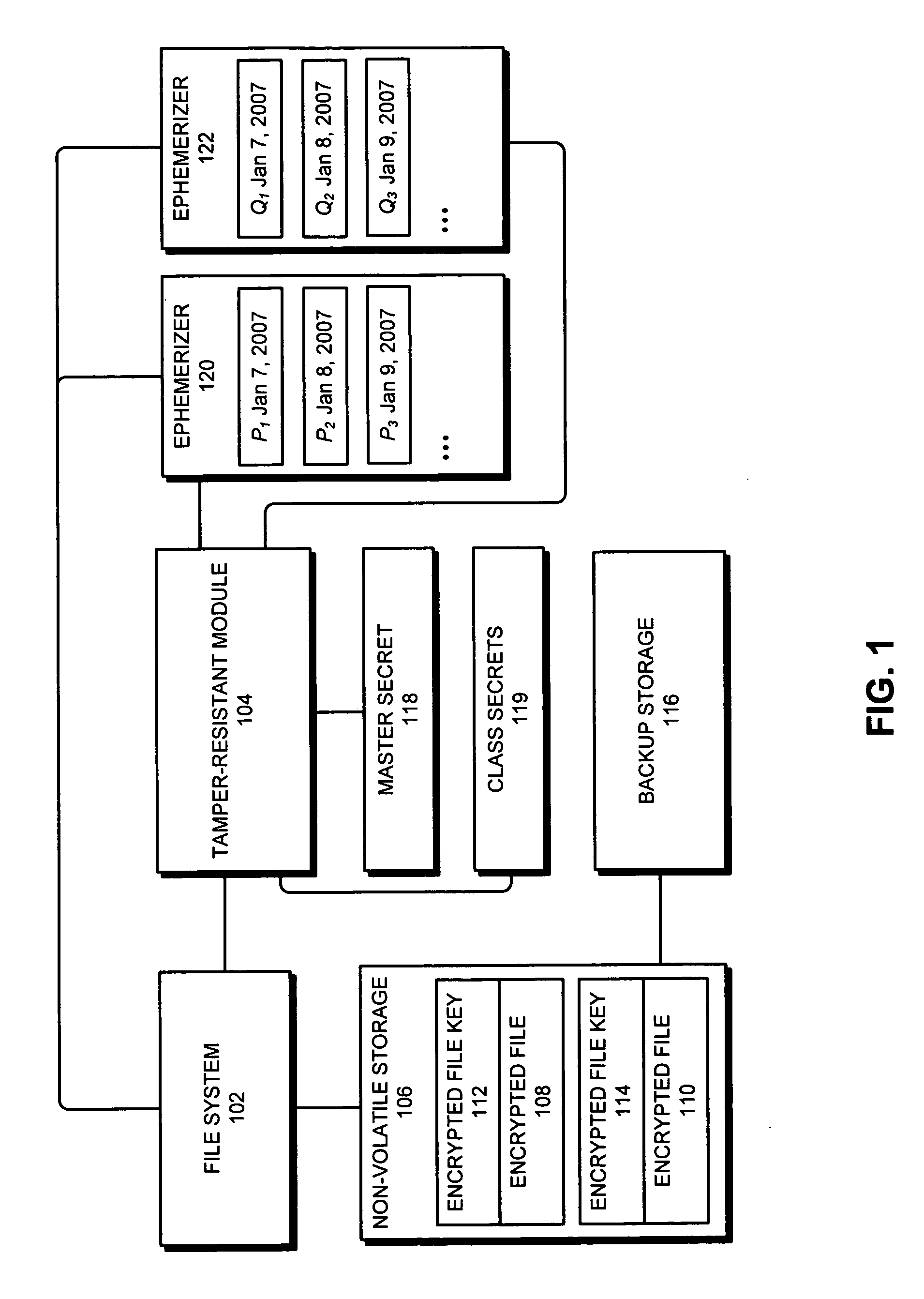
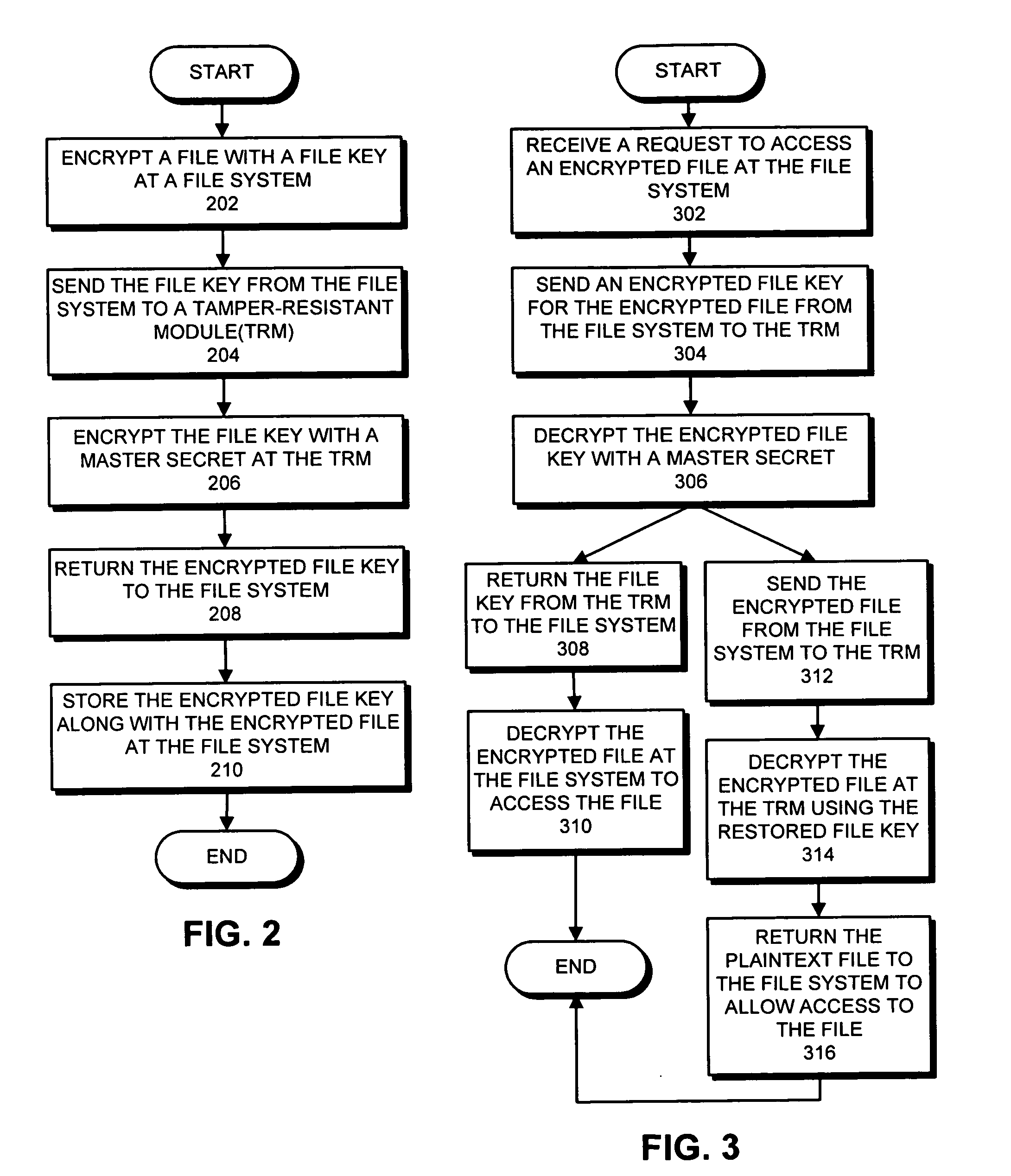
ActiveUS20080123858A1Key distribution for secure communicationUnauthorized memory use protectionNon localComputer module
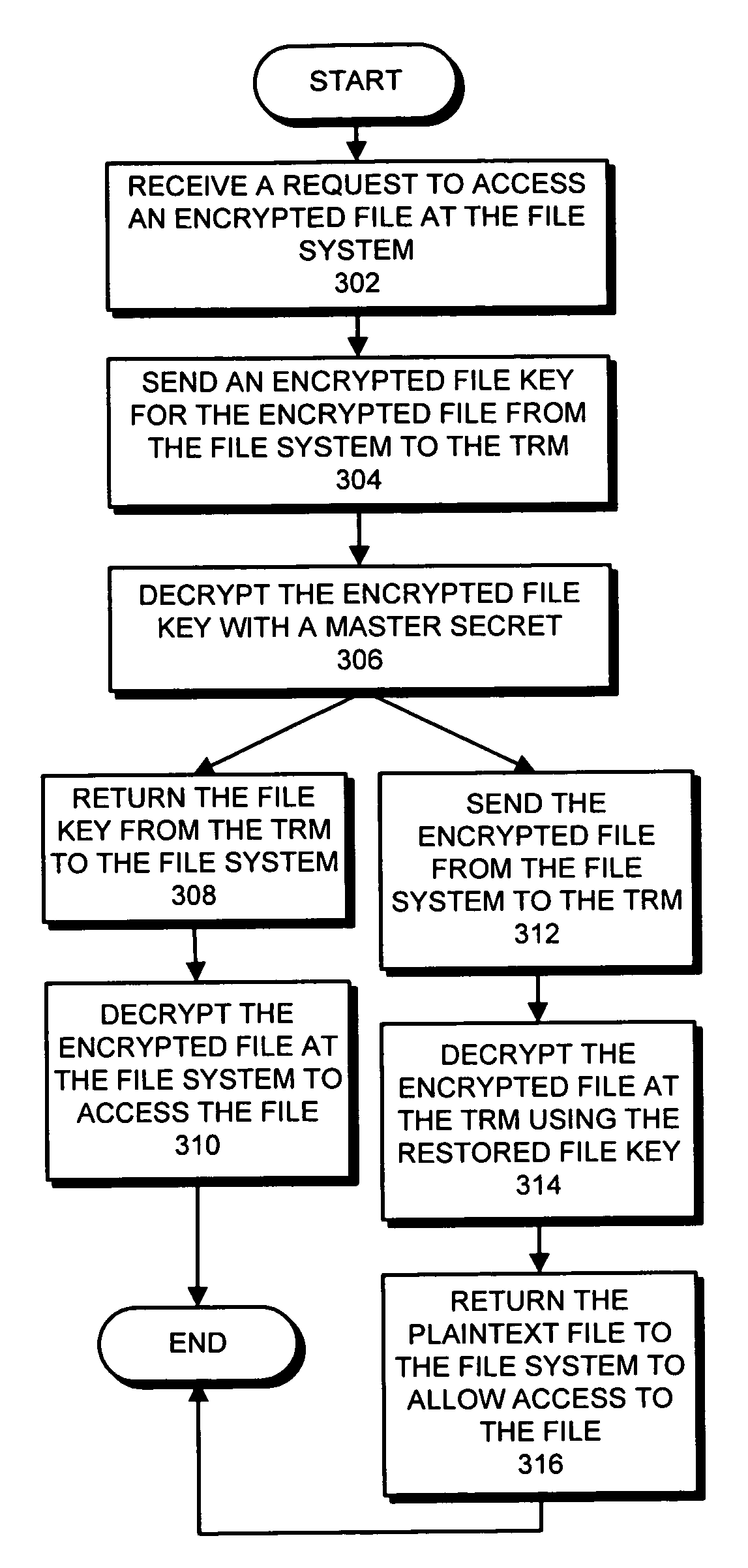
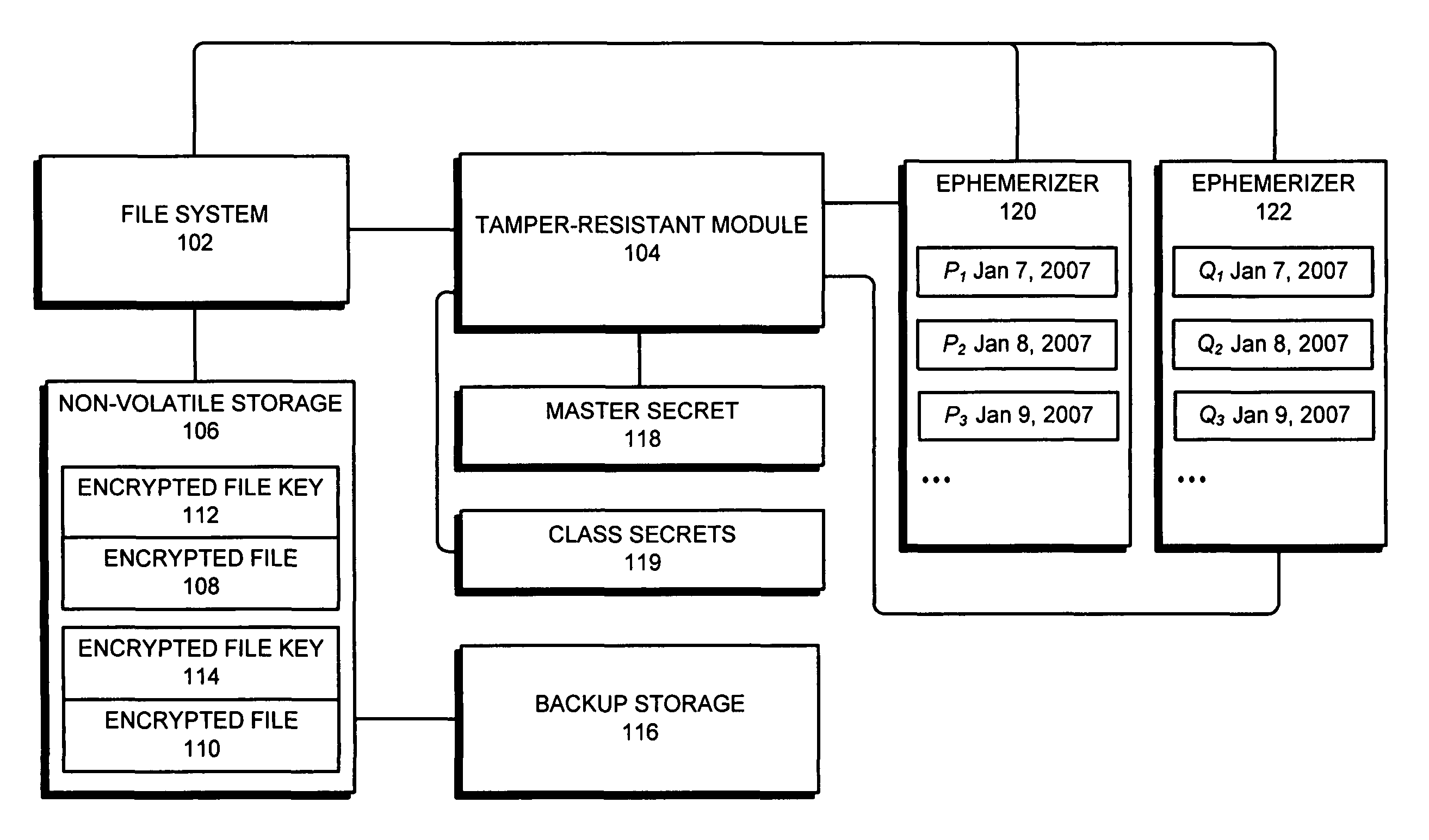
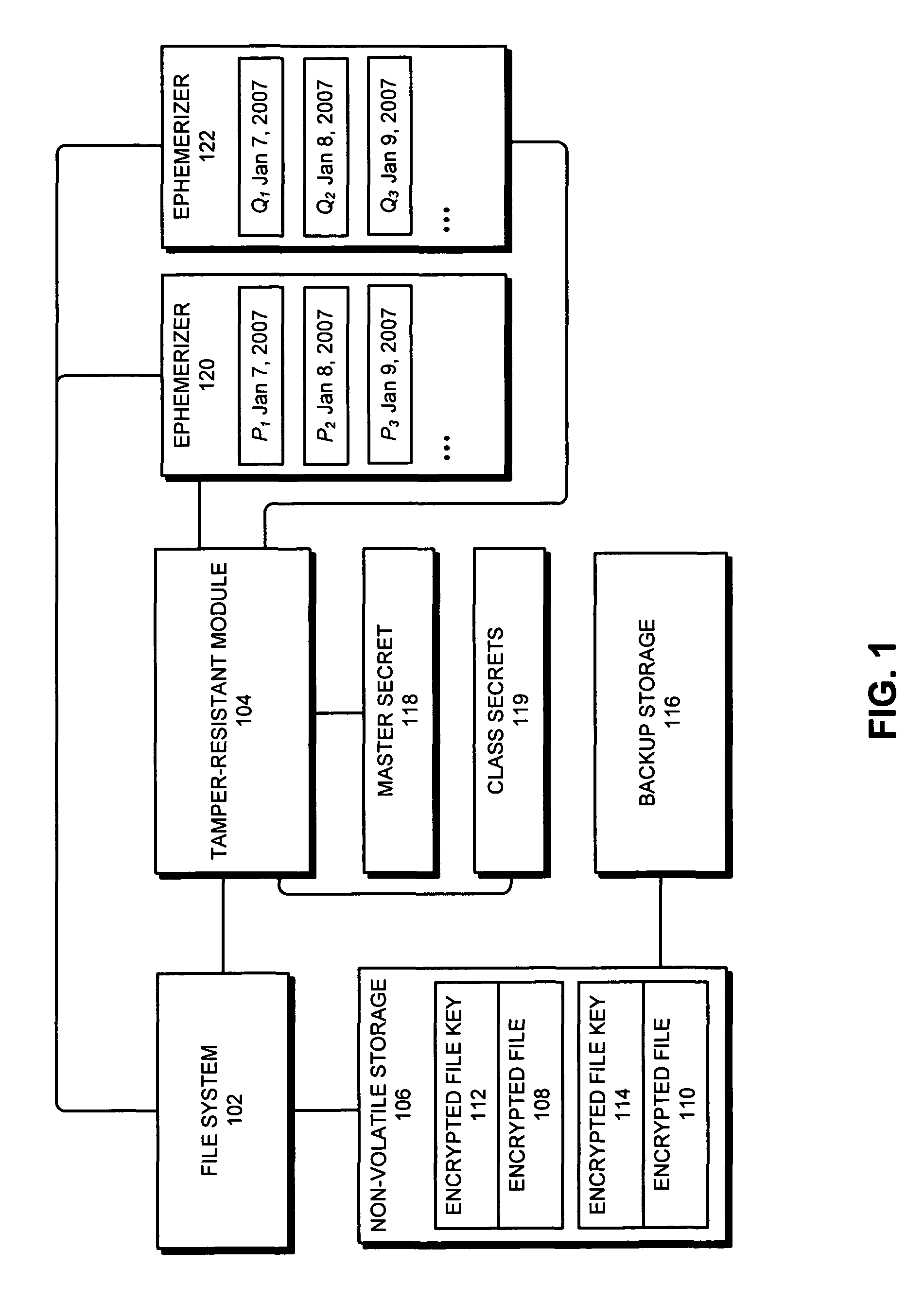
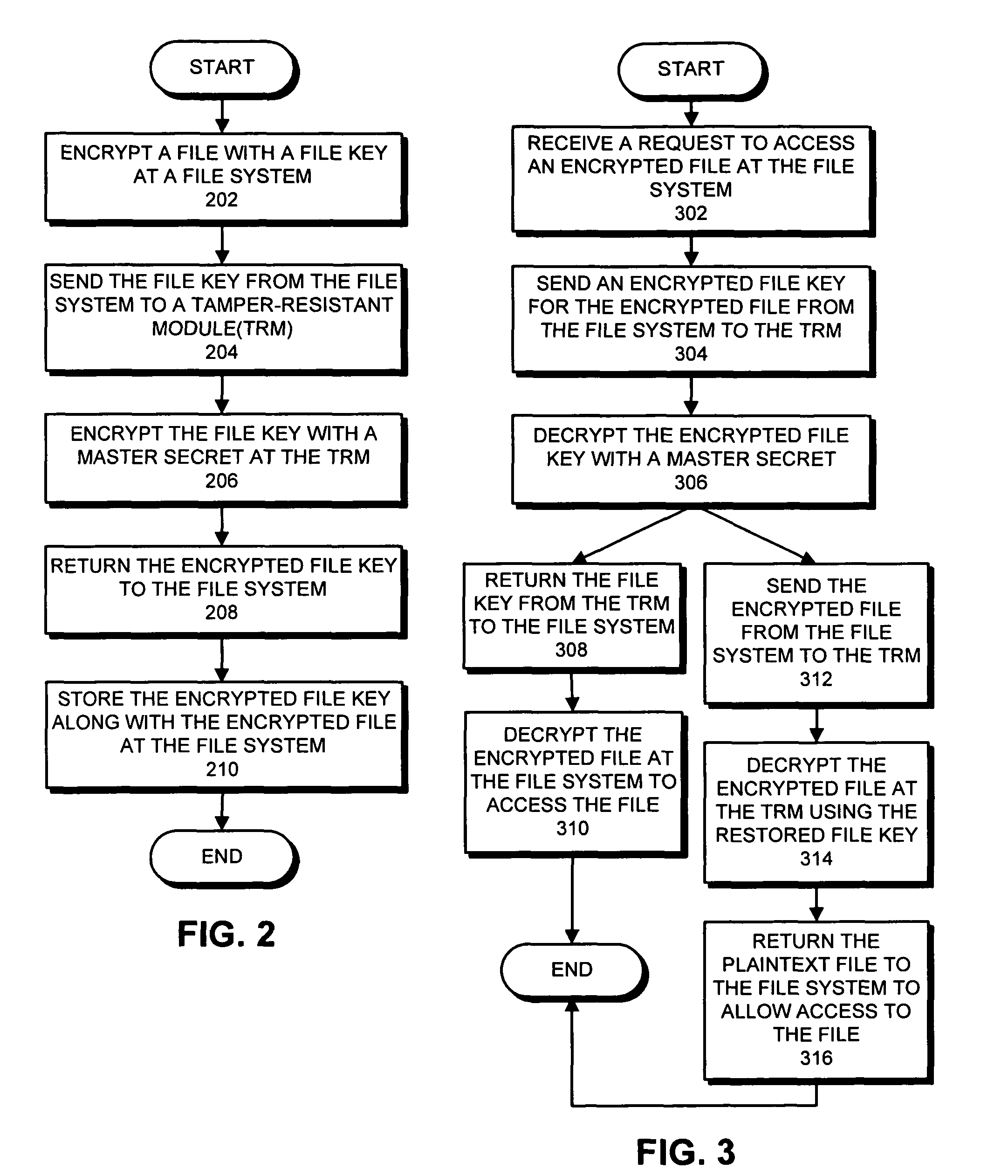
One embodiment of the present invention provides a system for accessing an encrypted file through a file system. During operation, the system receives a request to access the encrypted file. In response to the request, the system sends an encrypted file key for the encrypted file from the file system to a tamper-resistant module. Next, the tamper-resistant module uses a master secret to decrypt the encrypted file key to restore the file key, wherein the master secret is obtained from an external source by the tamper-resistant module. The system then uses the file key to access the encrypted file.
Owner:ORACLE INT CORP
Mobile phone payment protection method
ActiveCN102222292AAchieve local securityCache data protectionPayment architectureTransmissionPaymentSystem call
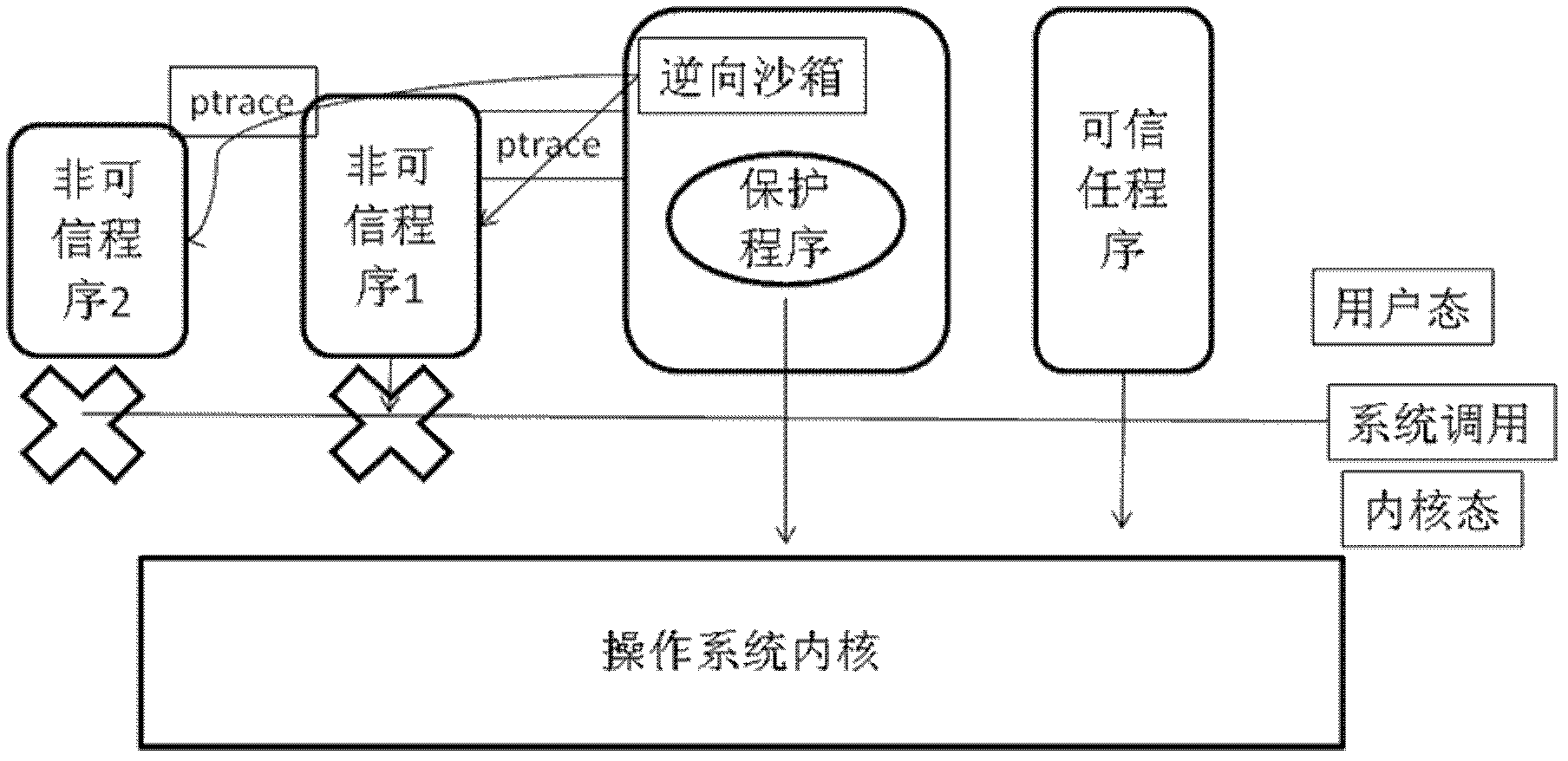
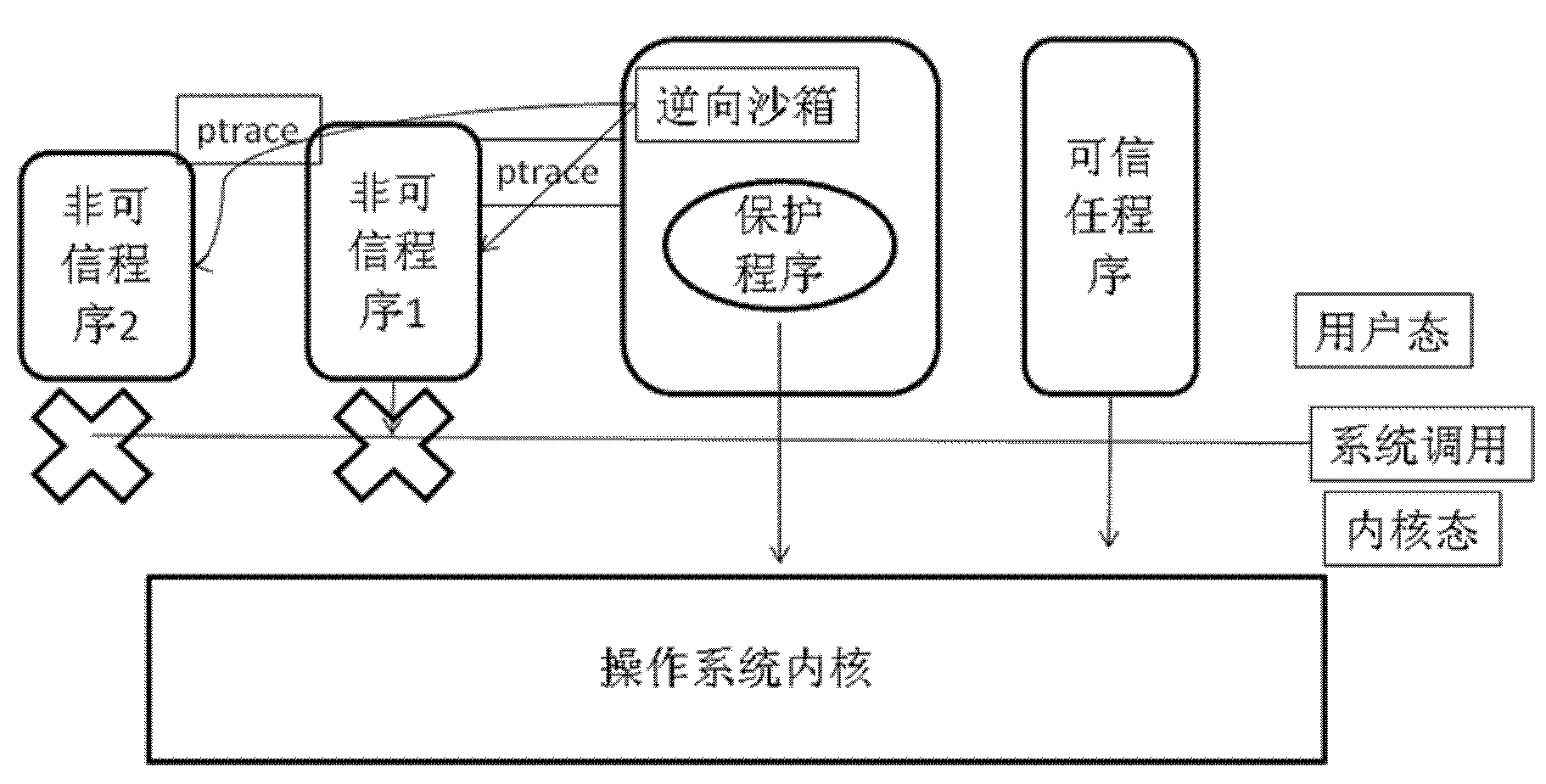
The invention provides a mobile phone payment protection method. The method comprises the following steps of: providing an encrypted file system, and protecting all reading and writing of a program to be redirected into the file system; performing encrypted storage on any reading and writing of the file system; performing the attach on the protected program by utilizing a ptrace function, and capturing transfer of a system of the all reading and writing of the protected program; and modifying the transfer of a path of a practical file system to be a path of a safe file system, and continuing running the program.
Owner:BEIJING BANGCLE TECH CO LTD
Data secure storage method of mobile terminal based on virtual disk
InactiveCN109325355AImprove customizabilityIncrease flexibilityInput/output to record carriersDigital data protectionPlaintextMultiple encryption
The invention provides a data safety storage method of a mobile terminal based on a virtual disk, belonging to the information safety field. The invention firstly creates an independent disk partitionin a hard disk, and simulates a disk partition by creating a file with a fixed size, and then formats the file content into a user-defined file system, so as to simulate the file into a disk, namelya virtual disk. Finally, combining with the real-time encryption technology, the encryption and decryption methods can be added in the process of reading and writing the disk to ensure the security ofthe data. The invention customizes the encrypted file system for the independent disk partition, constructs the encryption and decryption pipeline of the plaintext in the memory and the ciphertext onthe disk, avoids the plaintext traces left by the disk, and provides transparent data protection. The invention has higher security and flexibility, provides powerful protection for data in mobile terminal, can customize encrypted file system and identity authentication mechanism, and also can provide multiple encryption algorithms and working modes.
Owner:白令海
Method and apparatus for accessing an encrypted file system using non-local keys
ActiveUS8200964B2Key distribution for secure communicationUnauthorized memory use protectionNon localSystem usage
One embodiment of the present invention provides a system for accessing an encrypted file through a file system. During operation, the system receives a request to access the encrypted file. In response to the request, the system sends an encrypted file key for the encrypted file from the file system to a tamper-resistant module. Next, the tamper-resistant module uses a master secret to decrypt the encrypted file key to restore the file key, wherein the master secret is obtained from an external source by the tamper-resistant module. The system then uses the file key to access the encrypted file.
Owner:ORACLE INT CORP
Method for protecting linux operation system on loongson hardware platform
InactiveCN104636685AAnti-piracyProtect intellectual propertyInternal/peripheral component protectionOperational systemRandom access memory
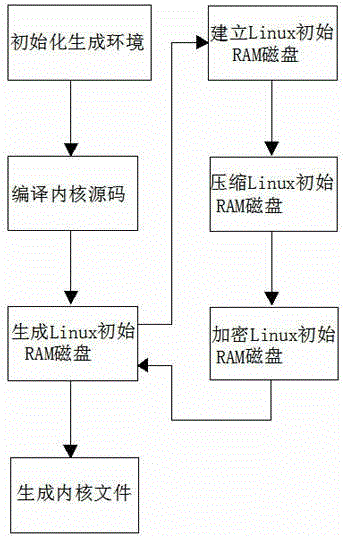
The invention discloses a method for protecting a linux operation system on a loongson hardware platform. According to the method for protecting linux operation system on the loongson hardware platform, a core encryption method and a file system encryption method are used. Core encryption is implemented by encrypting a Linux initial RAM (random-access memory) magnetic disk. The core encryption method comprises the following steps of encrypting the Linux initial RAM magnetic disk at a core generation stage; and decoding the Linux initial RAM magnetic disk when the system is started. File system encryption is implemented by using a linux equipment mapping technology, after file system encryption is implemented, file system mounting cannot be carried out directly, an encrypted file system requires to be mapped, and data of the file system can be read or written after mounting the mapped file system. By the method for protecting the linux operation system on the loongson hardware platform, a Linux core process is improved, and the inner operation mechanism, the procedure principle and key data of the Linux core process are protected fundamentally. The method not only can be used for preventing software copyright infringement and protecting intellectual property rights in a business environment, but also can be used for an environment requiring encryption such as defense and military, and has an anti-cracking function and an information leakage preventing function.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
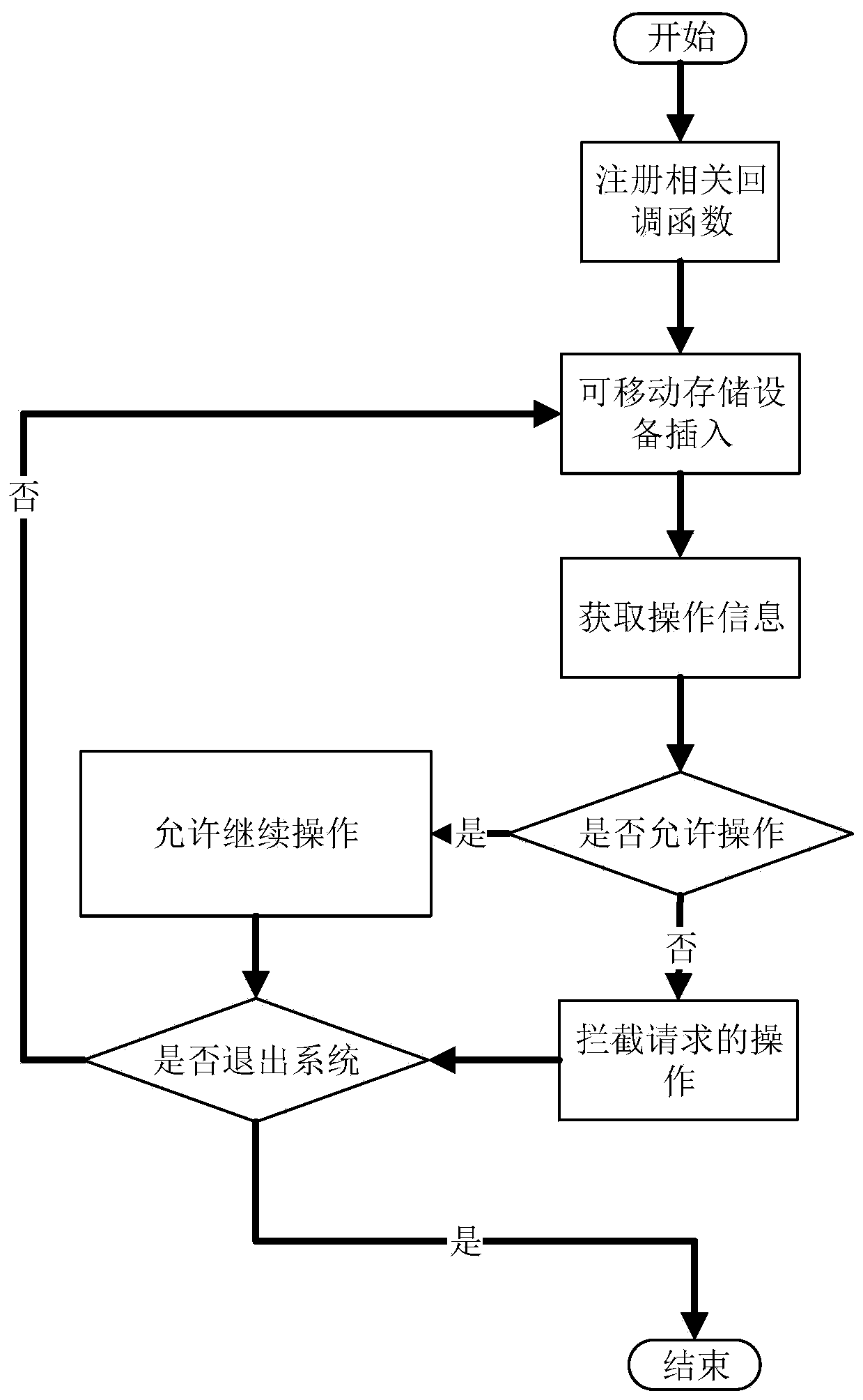
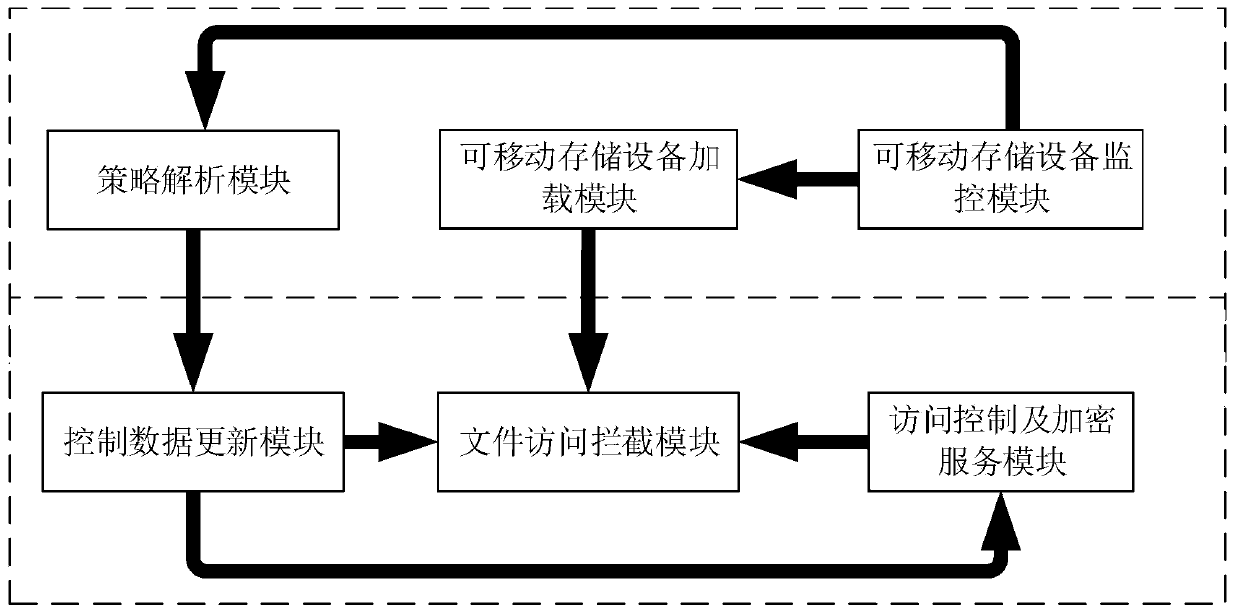
Removable storage device permission management method and system based on domestic operating system
ActiveCN110569650APerfect technology blankMultiple autonomyDigital data protectionClient-sideRights management
The invention provides a removable storage device permission management method and system based on a domestic operating system. The system includes: a real-time monitoring layer and an interception processing layer, and the real-time monitoring layer is used for monitoring insertion of the removable storage device, analyzing a storage control strategy of the removable storage device, sending control data related to the storage control strategy to the interception processing layer, and re-mounting a mounting directory of the removable storage device in a specified format of a virtual encryptedfile system. And the interception processing layer is used for intercepting the file access of the application layer to the removable storage device and controlling the file access behavior accordingto the control data generated by the control data updating module. According to the scheme provided by the invention, the system is high in compatibility, high in client security and convenient and flexible to deploy. The method does not depend on a specific environment, does not need to specially process the mobile storage device, and is high in flexibility. Permission subdivision management of the mobile storage device can be realized.
Owner:北京明朝万达科技股份有限公司
Secure Kerberized Access of Encrypted File System
ActiveUS20120204028A1Key distribution for secure communicationDigital data processing detailsCryptographic protocolClient-side
A file server receives a request from a client to mount an encrypted file system. The file server informs the client that the requested file system is encrypted and, in turn, receives a session ticket from the client that includes a security protocol mounting selection. The file server decrypts the client's user's encrypted private key, and then decrypts the requested encrypted file system using the private key. In turn, the file server sends the decrypted file system to the client over a secure channel, which is based upon the security protocol mounting selection. In one embodiment, a key distribution center server receives a request from the client for the client's user to access the encrypted file system at the file server. The key distribution center server retrieves an intermediate key; includes the intermediate key in a session ticket; and sends the session ticket to the client.
Owner:IBM CORP
Efficient data replication of an encrypted file system
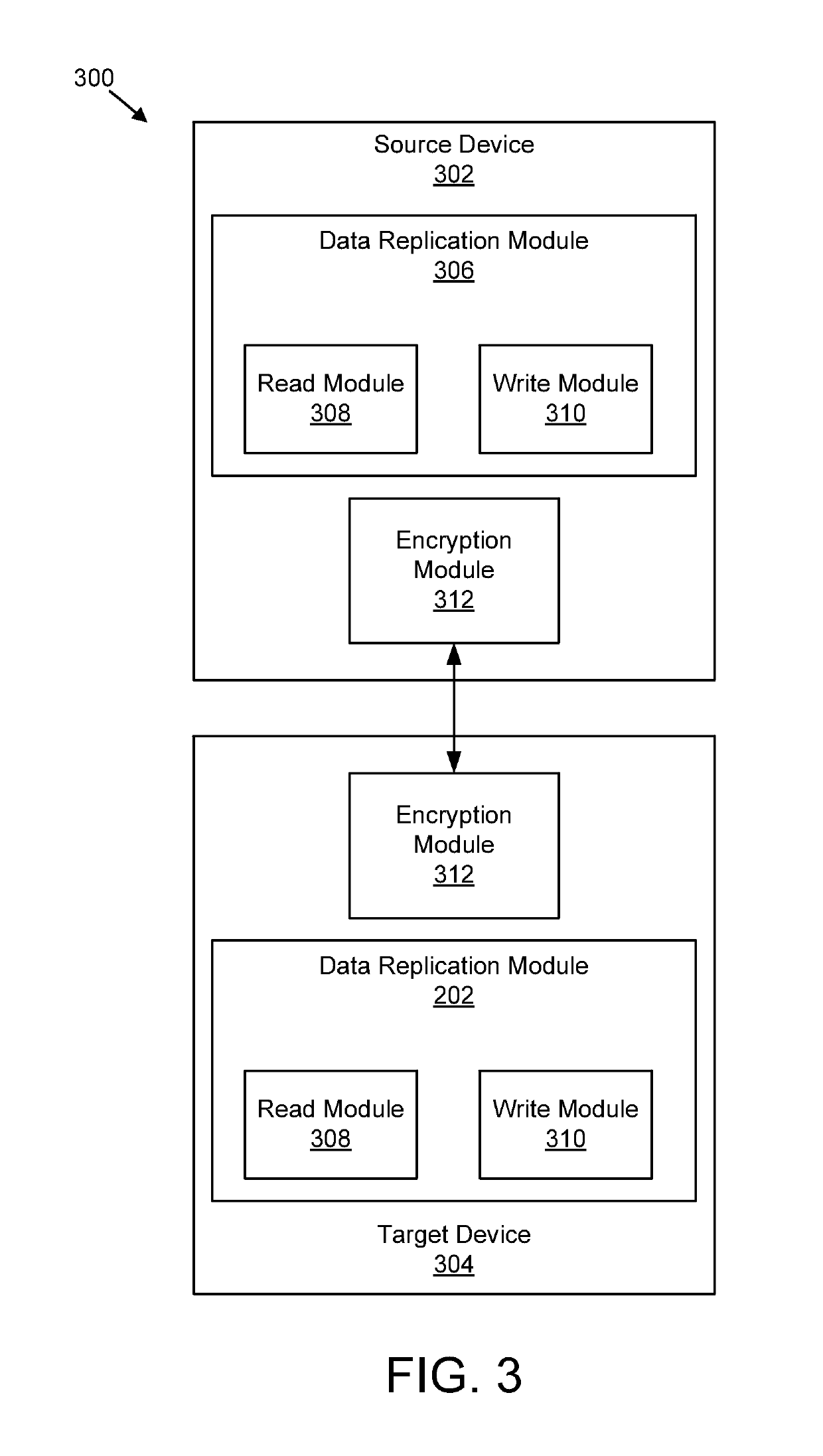
InactiveUS10298548B2Input/output to record carriersInternal/peripheral component protectionComputer hardwareEncrypting file system
An apparatus for data replication is disclosed. A method and computer program product also perform the functions of the apparatus. In one embodiment, an apparatus includes a read module configured to read into a communication buffer, from a persistent storage volume, a first file that is encrypted with file-level encryption without decrypting the first file. In certain embodiment, the apparatus also includes a write module configured to write data from a second file from the communication buffer, that is received from a source device and that is encrypted with file-level encryption, to the persistent storage volume without decrypting the second file.
Owner:INT BUSINESS MASCH CORP
Folder encryption method and device for Unix-like operating system
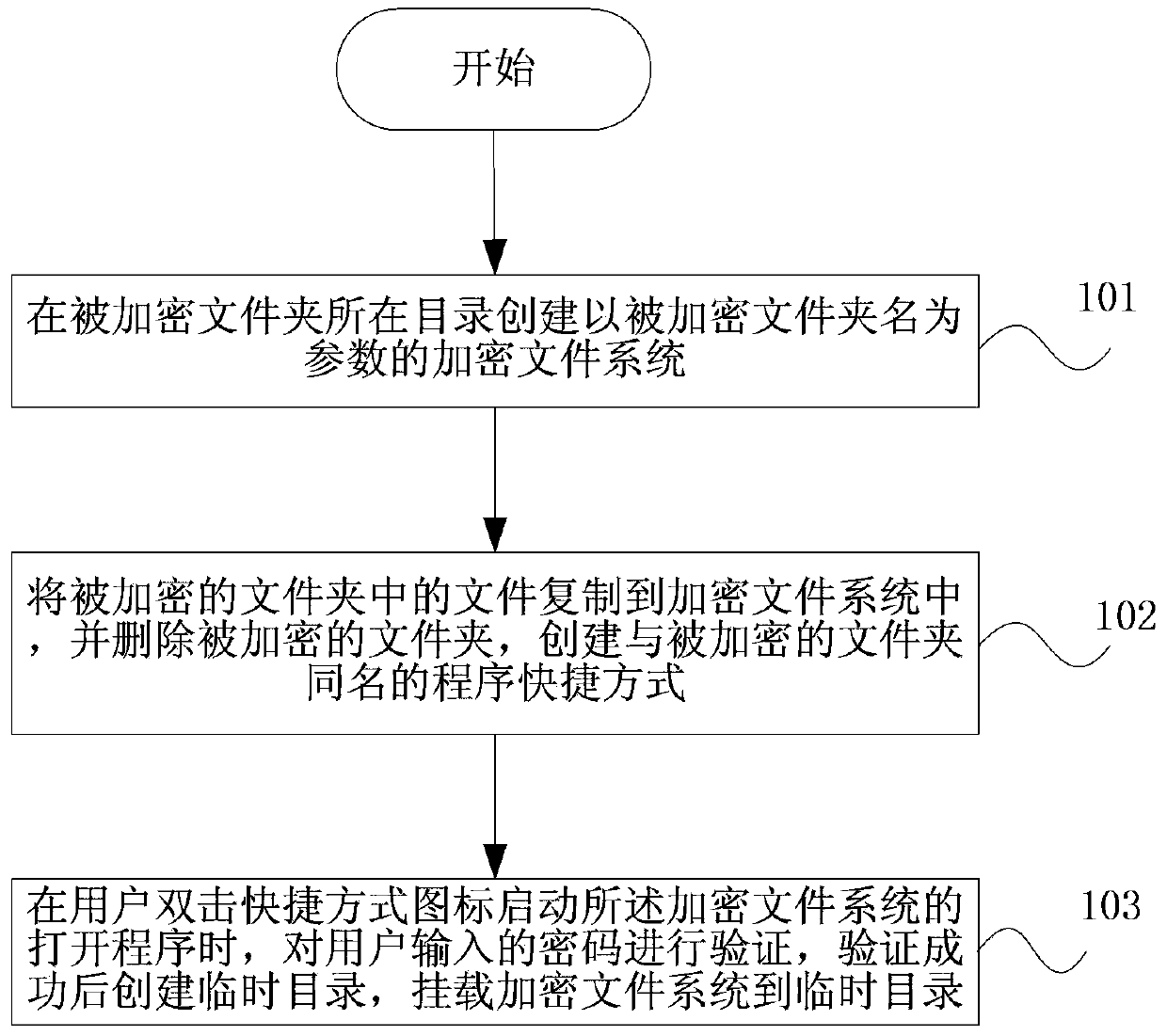
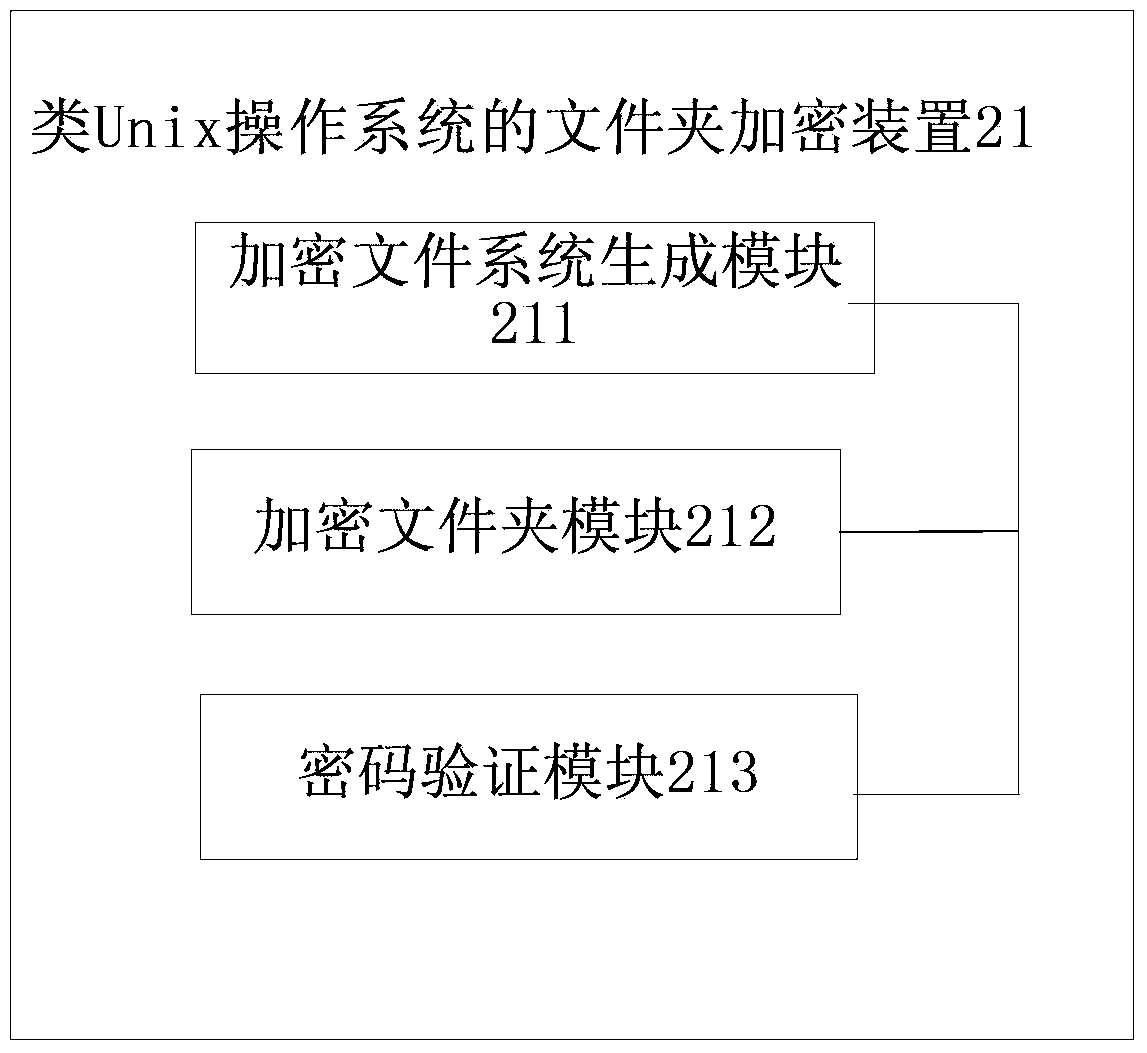
InactiveCN103425938AIntuitive EncryptionWork intuitivelyDigital data protectionOperational systemPassword
The invention discloses a folder encryption method and device for a Unix-like operating system. An encrypted file system is created in a catalog where an encrypted folder is located, wherein the name of the encrypted folder is used as a parameter of the encrypted file system; files in the encrypted folder are copied to the encrypted file system, the encrypted folder is deleted, and a routine shortcut with the same name as the encrypted folder is created; when a user double clicks a shortcut icon to enable a start routine of the encrypted file system, a password input by the user is verified, a temporary catalogue is created after the verification succeeds, and the encrypted file system is mounted to the temporary catalogue. The folder encryption method and device for the Unix-like operating system can encrypt folders and achieve the effect that encrypted files can be in a protection state under both a dynamic condition and a static condition by loading and unloading the encrypted file system.
Owner:亚太宝龙科技(湖南)有限公司
Method for optimizing performance of encryption card based on DEVICE MAPPER
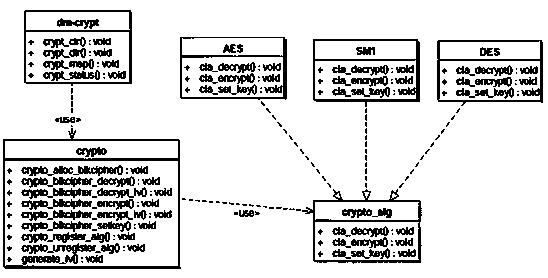
InactiveCN104268489ASave CPU timeReasonable designInternal/peripheral component protectionResource utilizationCPU time
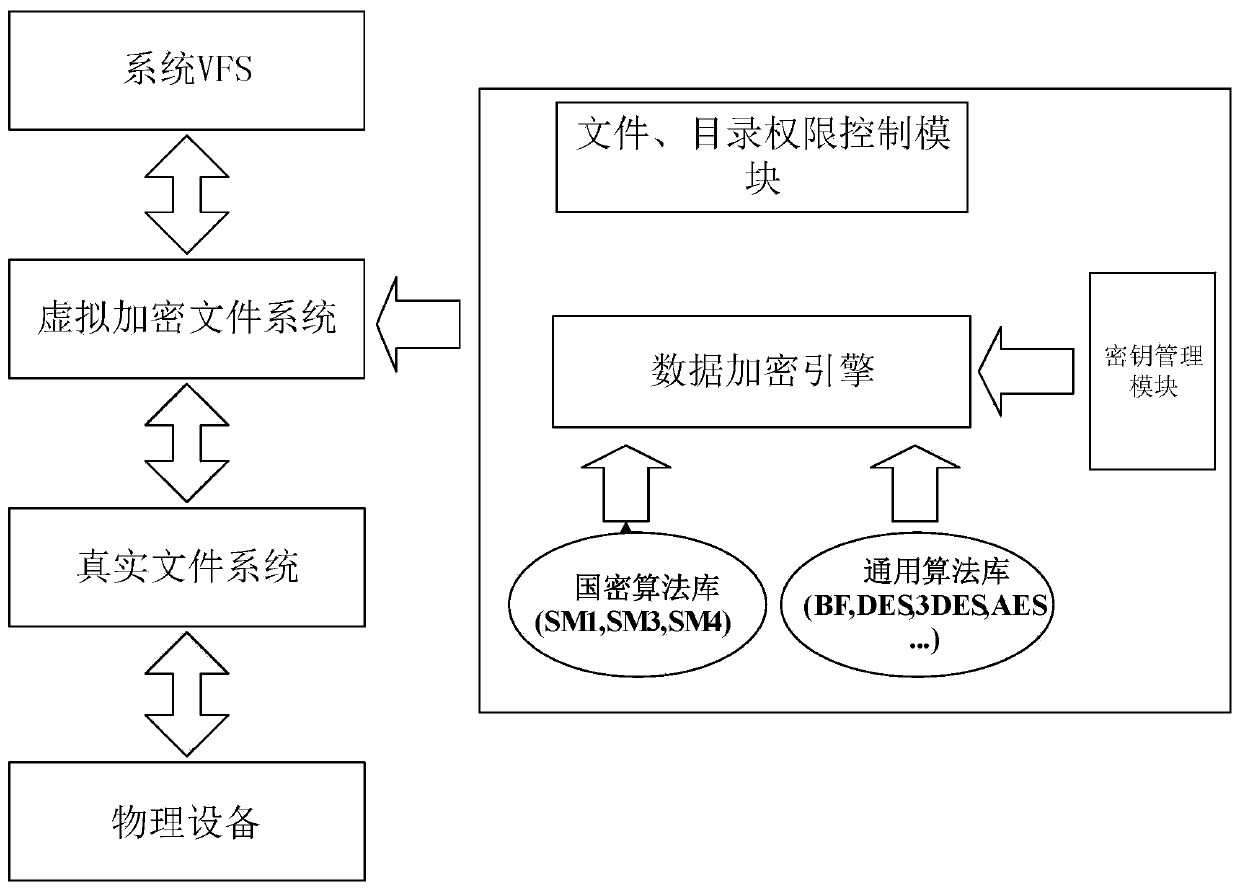
The invention provides a method for optimizing the performance of an encryption card based on DEVICE MAPPER. The API of the encryption card is integrated into the universal block device kernel framework Device Mapper so that a dm-crypt encryption block device module suitable for the encryption card can be realized, and furthermore, an encrypted file system can be established for protecting confidential data at a disk storage level; the encryption block device module comprises two modes, namely synchronous block encryption and asynchronous block encryption of the domestic encryption algorithm sm1, and a method for registering the algorithm sm1 to a kernel password manager is provided. Compared with the prior art, the method for optimizing the performance of the encryption card based on DEVICE MAPPER is characterized in that the increase of the speed is realized by virtue of parallel operating of a plurality of cards, and in the aspect of system resource utilization rate, principally, the previous encryption card working pattern is changed from waiting mode into an asynchronous working mode, and therefore, the time of the cpu is greatly saved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
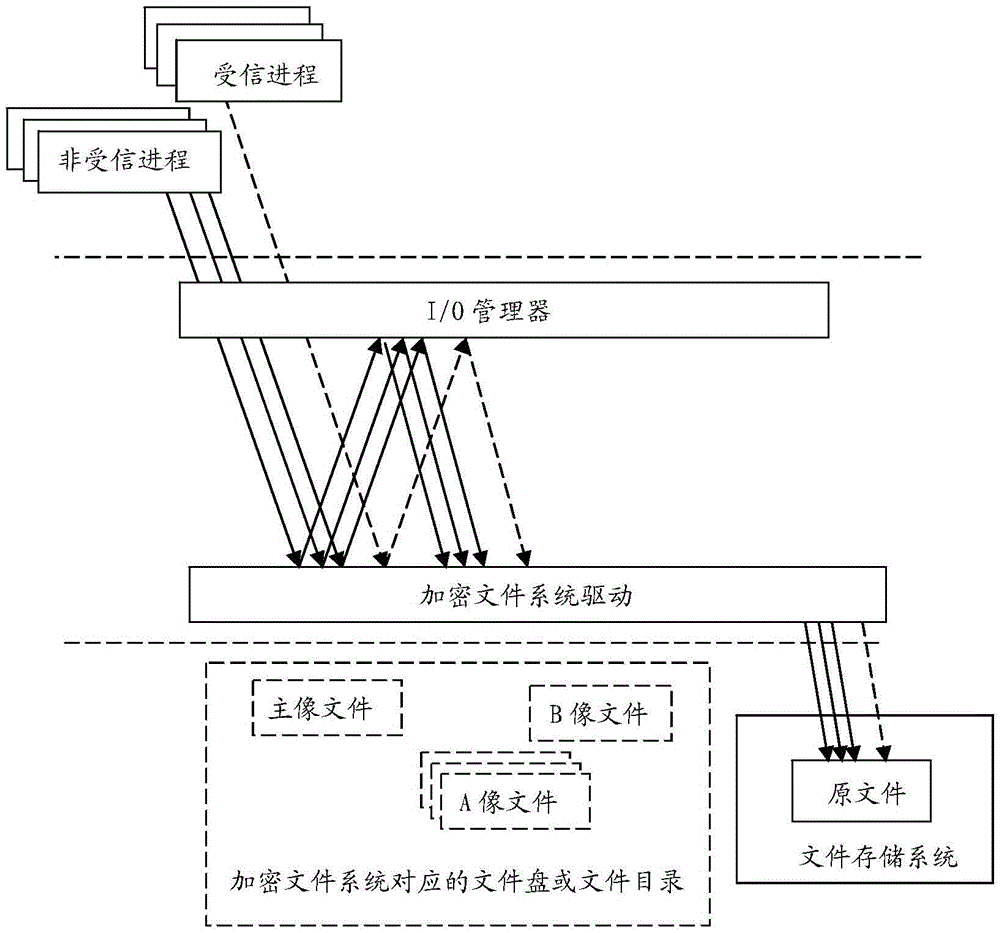
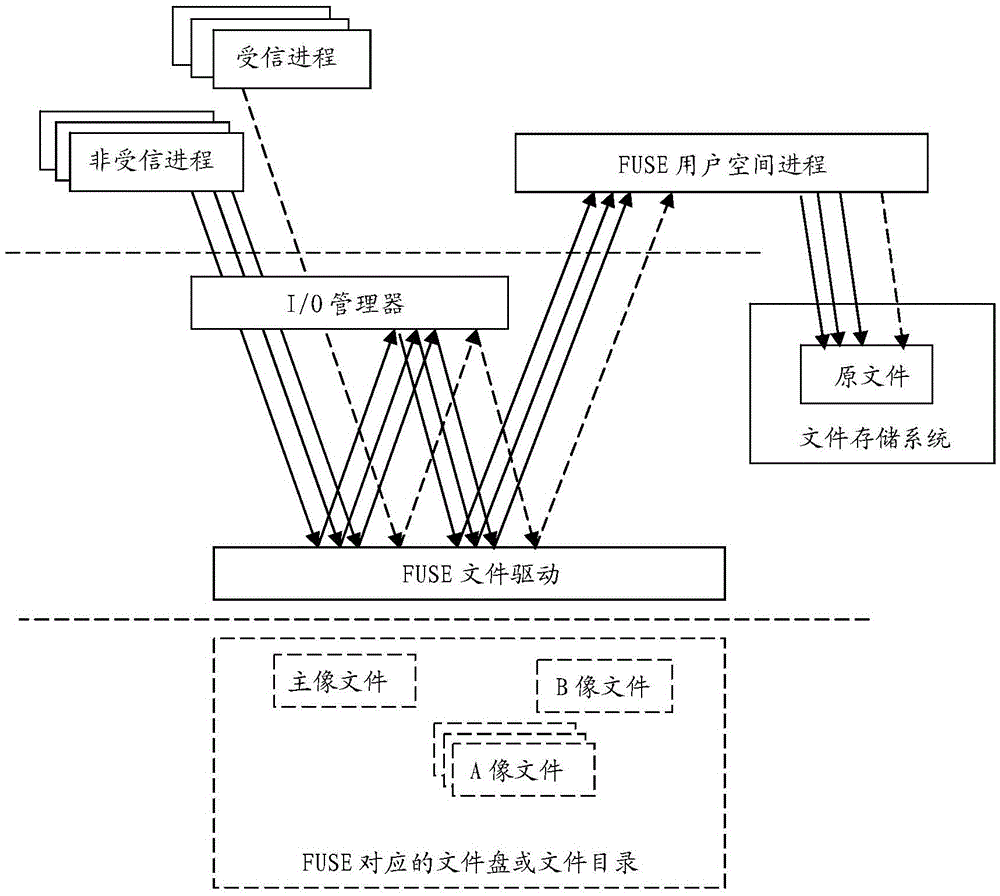
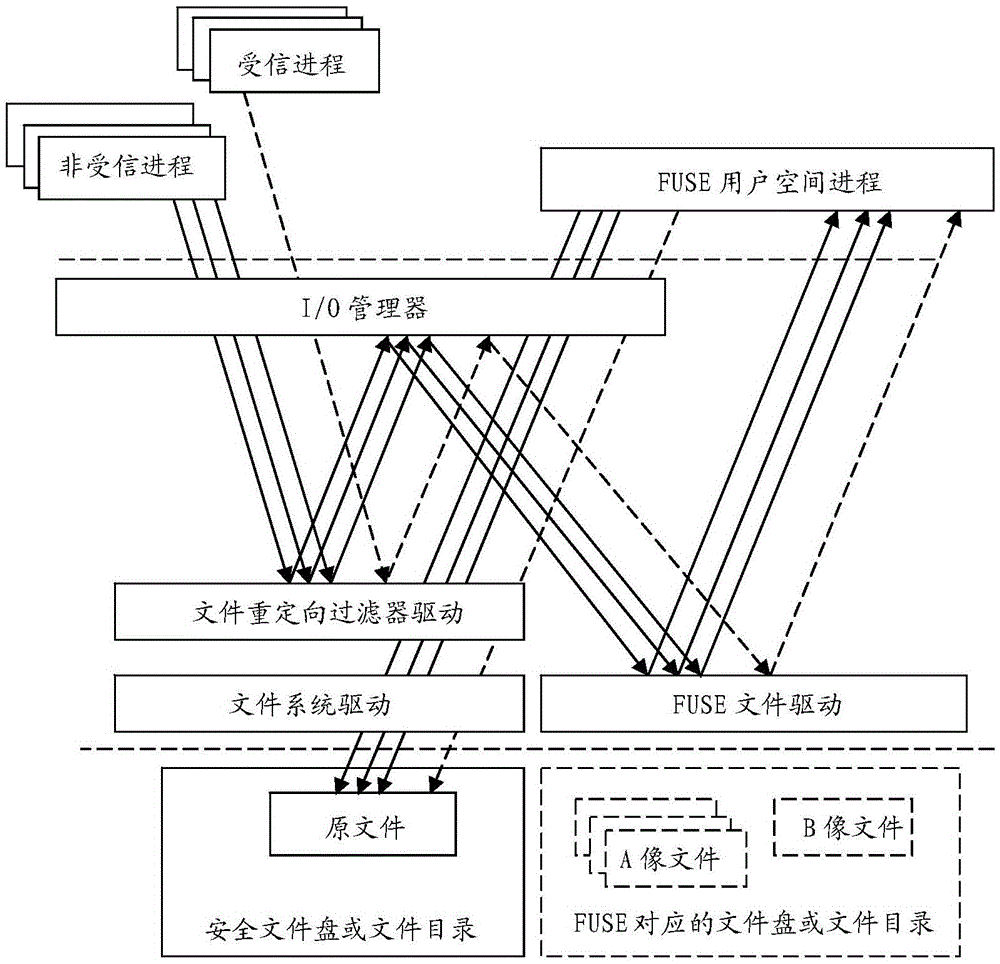
Encrypted file system based on multi-image files
The invention relates to an encrypted file system based on multi-image files. Each file in the encrypted file system is provided with a plurality of file images, i.e. a primary image file, a plurality of A image files, and a B image file; when one of the primary image files is opened or created by an untrusted process, the file opening or creating operation is redirected to one of the corresponding A image files, and the file opening or creating operations of different untrusted processes for the same primary image file are redirected to the different A image files; when one of the primary image files is opened or created by a trusted process, the file opening or creating operation is redirected to the corresponding B image file; the encrypted file system converts I / O operations for the A image files and the B image file of each file into operations for the corresponding original file, and automatically carries out file encryption and decryption processing during the operations. The encrypted file system provided by the invention avoids not only the mixing of cached data between the trusted processes and the untrusted processes, but also clear data leakage among the untrusted processes which might be caused by data storage and writing operations.
Owner:WUHAN UNIV OF TECH
Method and apparatus for restoring encrypted files to an encrypting file system based on deprecated keystores
InactiveUS8494167B2Error detection/correctionVolume/mass flow measurementData processing systemEncrypting file system
The present invention provides a computer implemented method, data processing system, and computer program product to restore an encrypted file. A computer receives a command to restore an encrypted file, wherein the encrypted file was previously backed up. The computer identifies a user associated with the encrypted file. The computer looks up a first keystore of the user based on the user, the first keystore having an active private key. The computer determines that a public key of the encrypted file fails to match an active public key of the first keystore. The computer restores a second keystore of the user to form a restored private key, wherein the second keystore was previously backed up. The computer responsive to a determination that the public key of the encrypted file fails to match the active public key of the first keystore, decrypts the encrypted file encryption key based on the restored private key to form a file encryption key. The computer encrypts the file encryption key with the active private key of the first keystore.
Owner:INT BUSINESS MASCH CORP
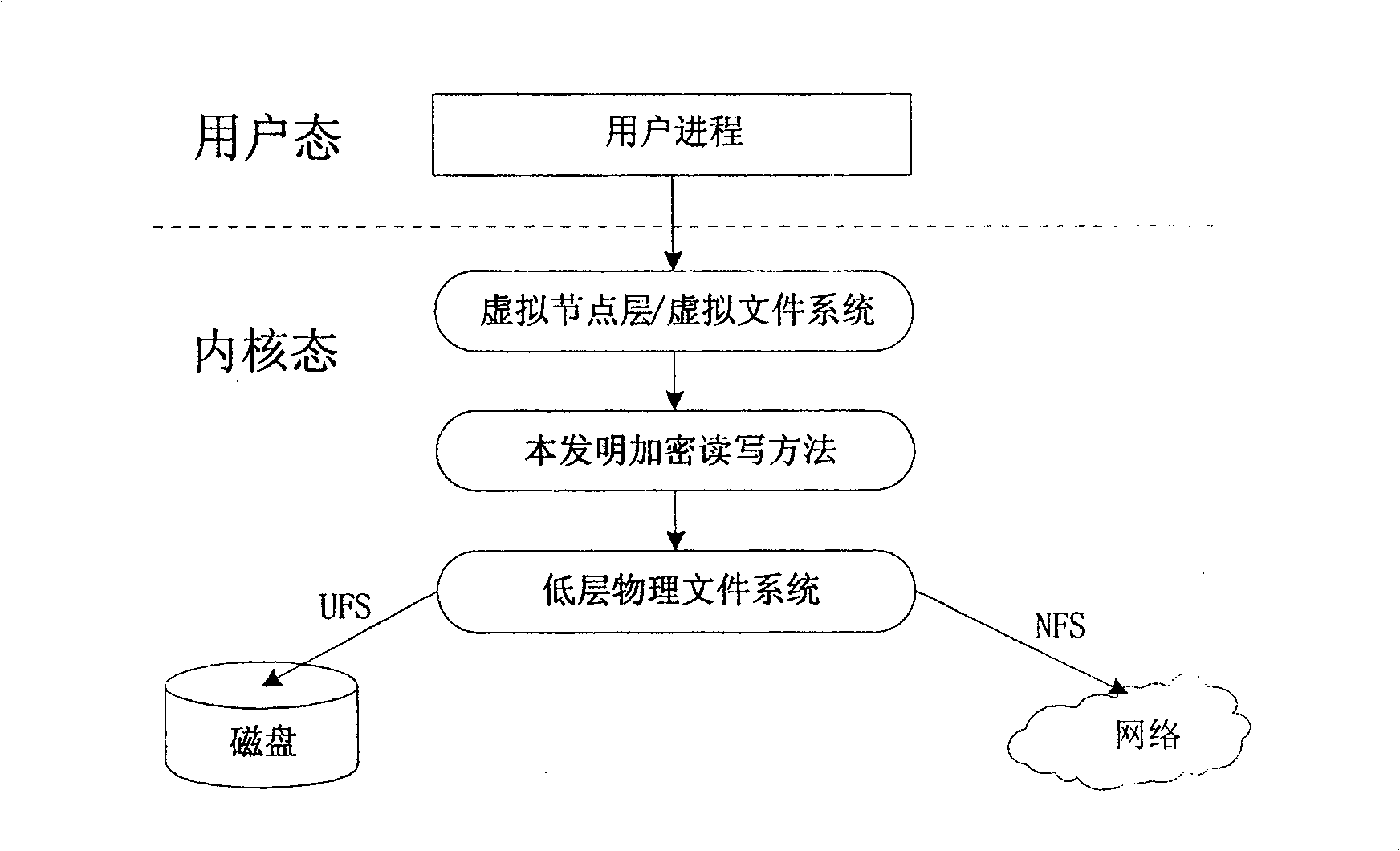
Encrypting read / write method in use for NAS storage system
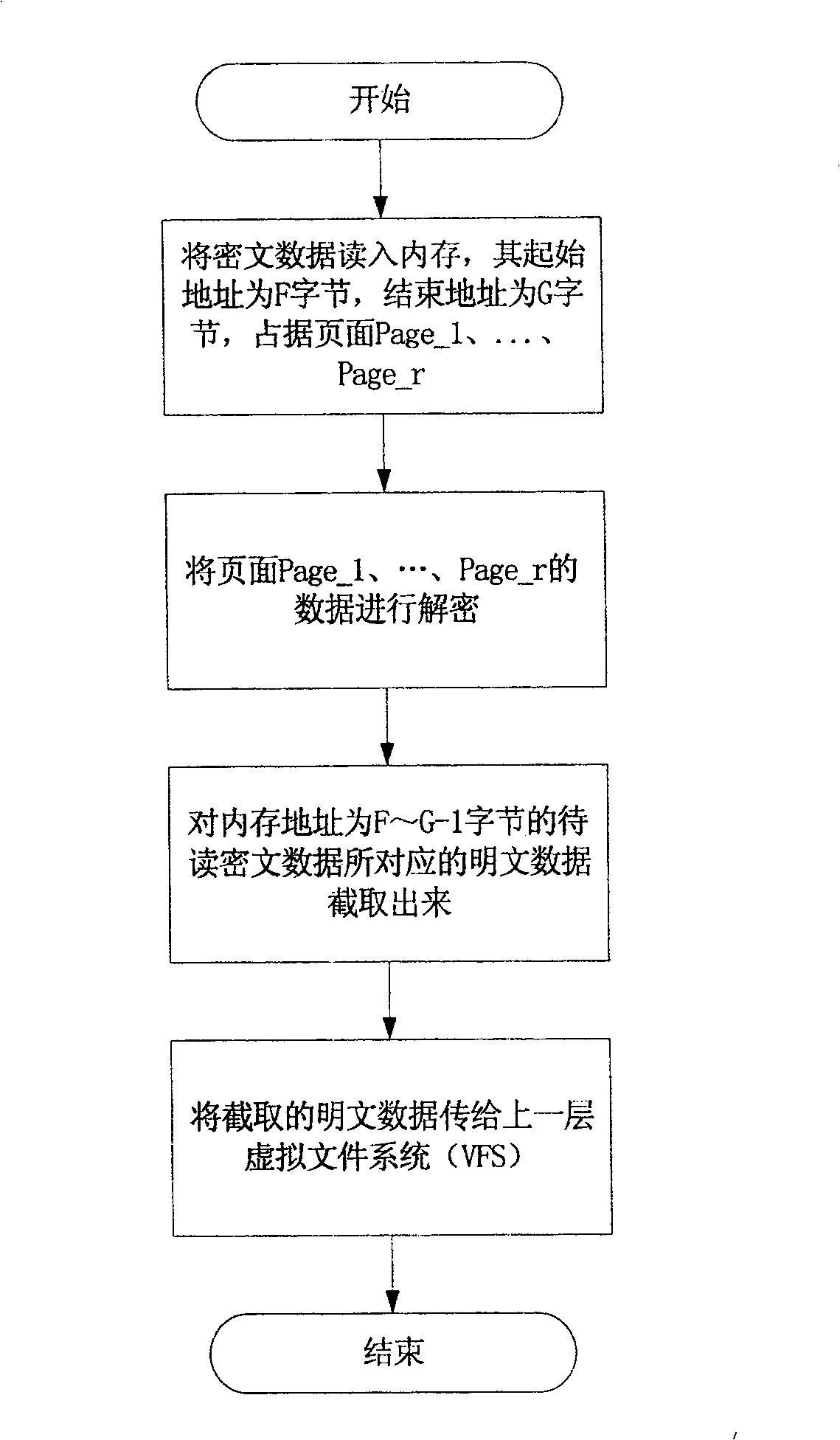
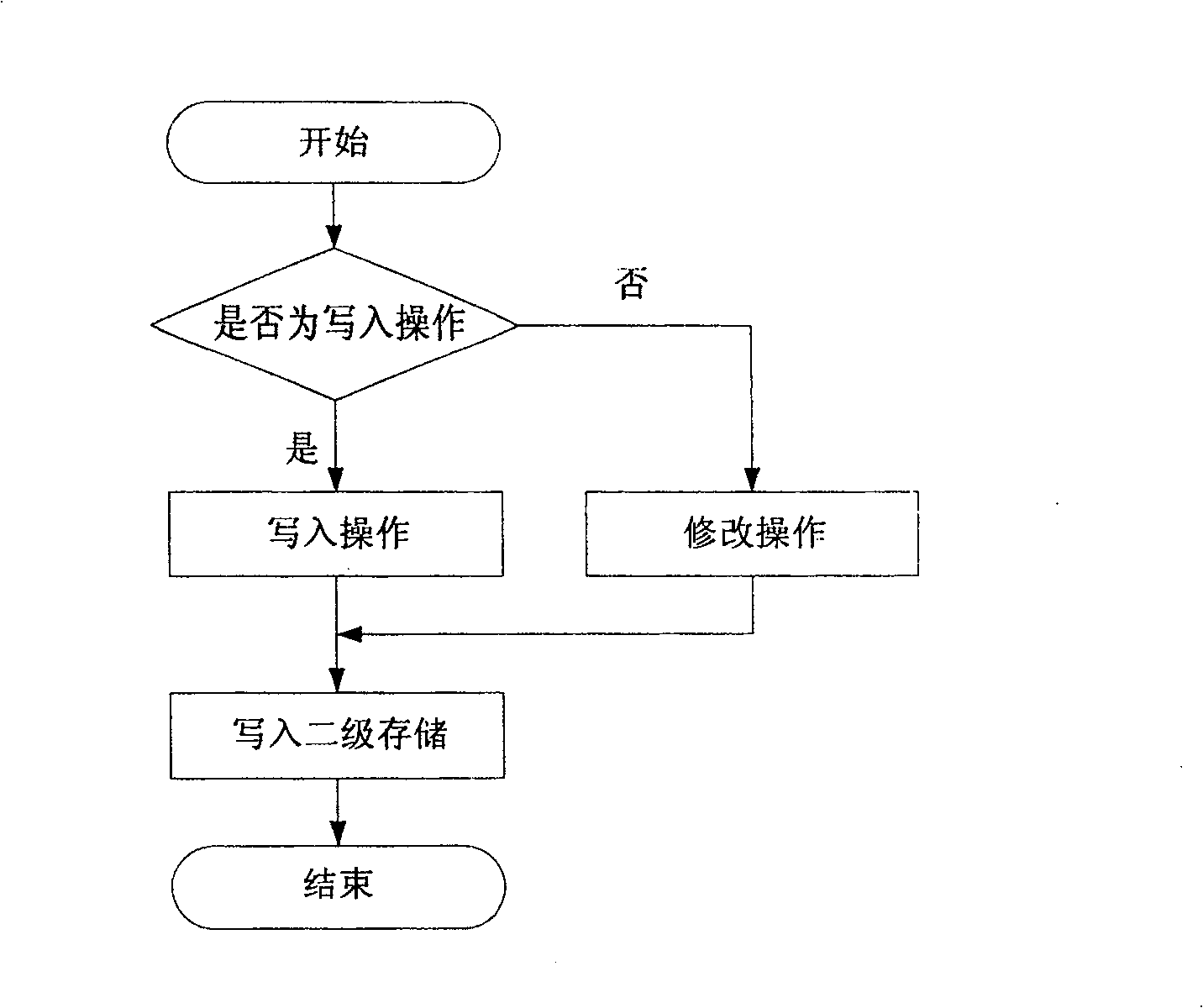
InactiveCN100536473COvercoming the inconvenience of useLow efficiencyUnauthorized memory use protectionTransmissionPlaintextComputer hardware
The invention discloses an encrypted reading and writing method at the kernel state file system layer. The method is located between the virtual file system and the physical file system. During the reading operation, the read ciphertext data is first decrypted and then transmitted to the upper layer virtual file system; when writing, first determine the type of write operation, if it is a write operation, first encrypt the plaintext data to be written, and then pass the intercepted ciphertext data to the underlying physical file system, if it is a modification operation , the ciphertext data read into the memory will be partially decrypted, overwritten, globally encrypted, and partially intercepted. This method not only has the inherent high efficiency of kernel state operations, but also uses partial decryption and partial interception to improve the efficiency of data operations. From the test process and test data, it can be known that using the encrypted reading and writing method of the present invention can simultaneously overcome the inconvenience of the application layer encryption program and the low efficiency of the user state encrypted file system.
Owner:HUAZHONG UNIV OF SCI & TECH
General purpose distributed encrypted file system
InactiveUS8751789B2Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareGeneral purpose
A general purpose distributed encrypted file system generates a block key on a client machine. The client machine encrypts a file using the block key. Then, the client encrypts the block key on the first client machine with a public key of a keystore associated with a user and associates the encrypted block key with the encrypted data block as crypto metadata. The client machine caches the encrypted data block and the crypto metadata and sends the encrypted data block and the crypto metadata to a network file system server. When the client machine receives a return code from the network file system server indicating successful writes of the encrypted data block and the crypto metadata, the client machine clears the cached encrypted data block and the crypto metadata.
Owner:INT BUSINESS MASCH CORP
A distributed code operation and interaction security method and a system thereof
InactiveCN109861945AGuaranteed enforceabilityDo not compromise securityKey distribution for secure communicationOperational systemCiphertext
The invention relates to a distributed code running and interactive security method and system thereof, comprising a client browser or an application (interface) and a web or other type of server, andan encrypted file system and a function call intercepting plug-in module and an encryption module, are arranged in the server. the client browser or the application (interface) issues a code dynamicsecurity execution request to the server, the file system requests the encryption module to encode and encrypt to generate the code ciphertext; the encryption module performs ciphertext encoding conversion and returns to the operating system; The cryptographic module is requested to perform a ciphertext encoding conversion request on the code running result by the server; the server merges the ciphertext of the unconverted code running result with the ciphertext of the code running result that can be displayed or applied (interface), and the fusion result is sent to browse Or application (interface). The method and system effectively protects the security of running code in a web server.
Owner:浙江智贝信息科技有限公司
Preventing replay attacks in encrypted file systems
InactiveUS8607071B2Unauthorized memory use protectionHardware monitoringEncrypting file systemComputer science
Owner:INT BUSINESS MASCH CORP
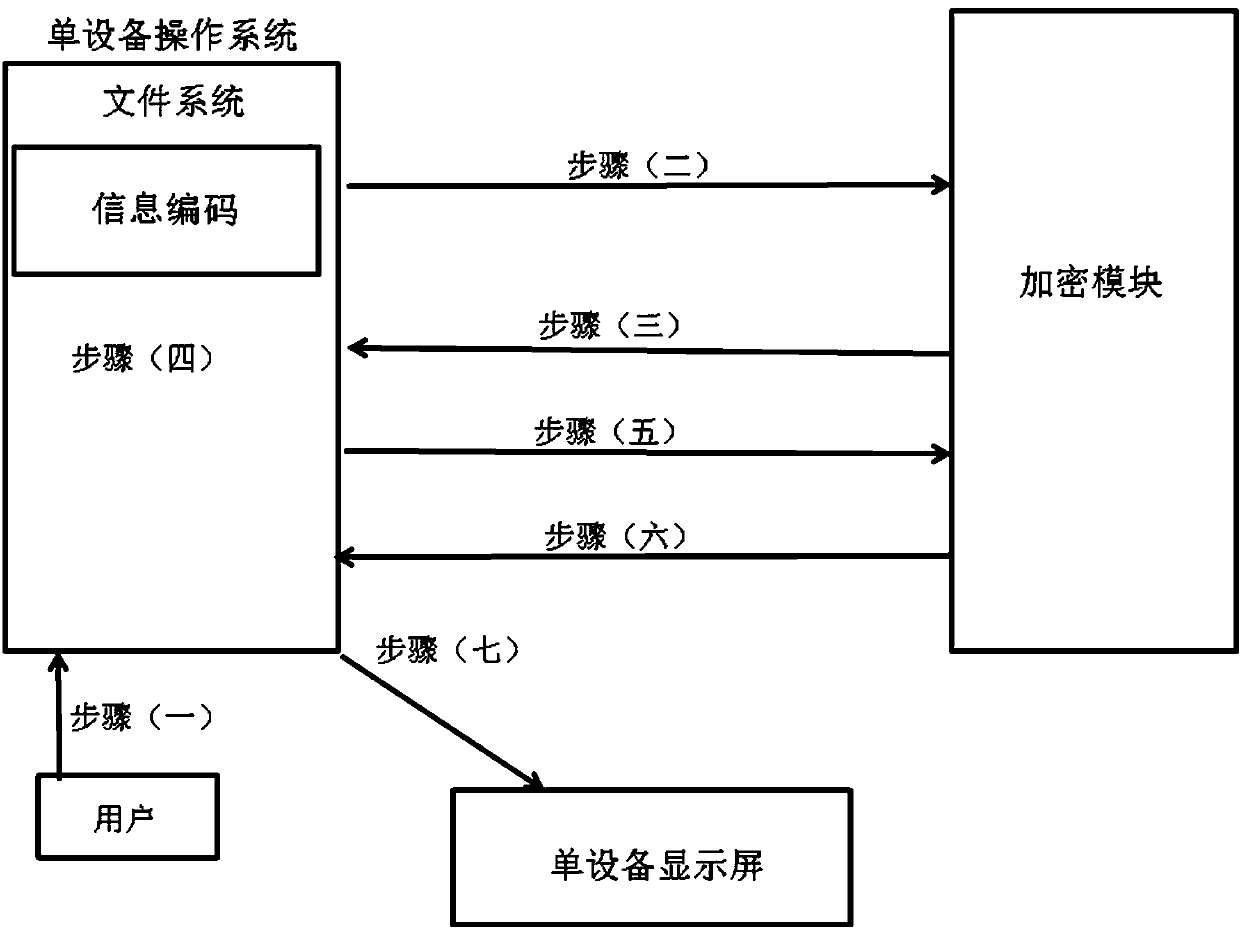
Single-device information security processing and interaction method and interaction system thereof
InactiveCN109858240ADo not compromise securityPerformance is not affectedPlatform integrity maintainanceInformation processingInteraction systems
The invention relates to a single-device information security processing and interaction method and an interaction system thereof. The system comprises a display screen and an operating system, an encrypted file system, a function calling interception plug-in module and an encryption module are arranged in the operating system, a user or an application (interface) sends a dynamic ciphertext culture security information request to the operating system, and the file system requests the encryption module to perform encoding encryption or ciphertext conversion to generate a new information ciphertext. The operating system puts forward a ciphertext coding conversion request to the encryption module. The encryption module carries out ciphertext coding conversion and returns the ciphertext codingconversion to the operation system. The operation system intercepts the image and / or text information to be displayed. The encryption module carries out code conversion on the ciphertext of the information processing result and returns the ciphertext to the operation system. The operating system fuses the intercepted information with the ciphertext of the converted information processing result,and a display screen of single equipment displays or an application (interface) processes the information processing ciphertext result. According to the invention, the security of the processed and used information in the operating system is effectively protected.
Owner:浙江智贝信息科技有限公司
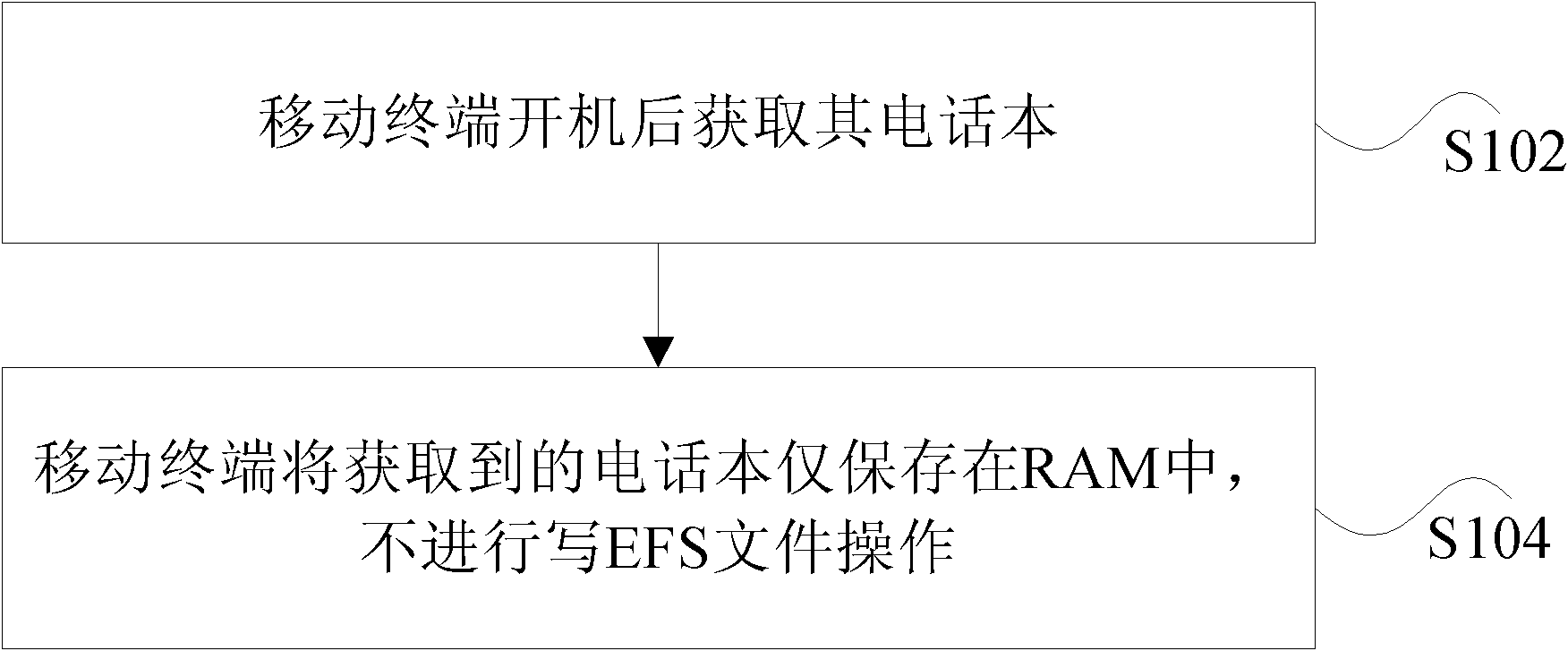
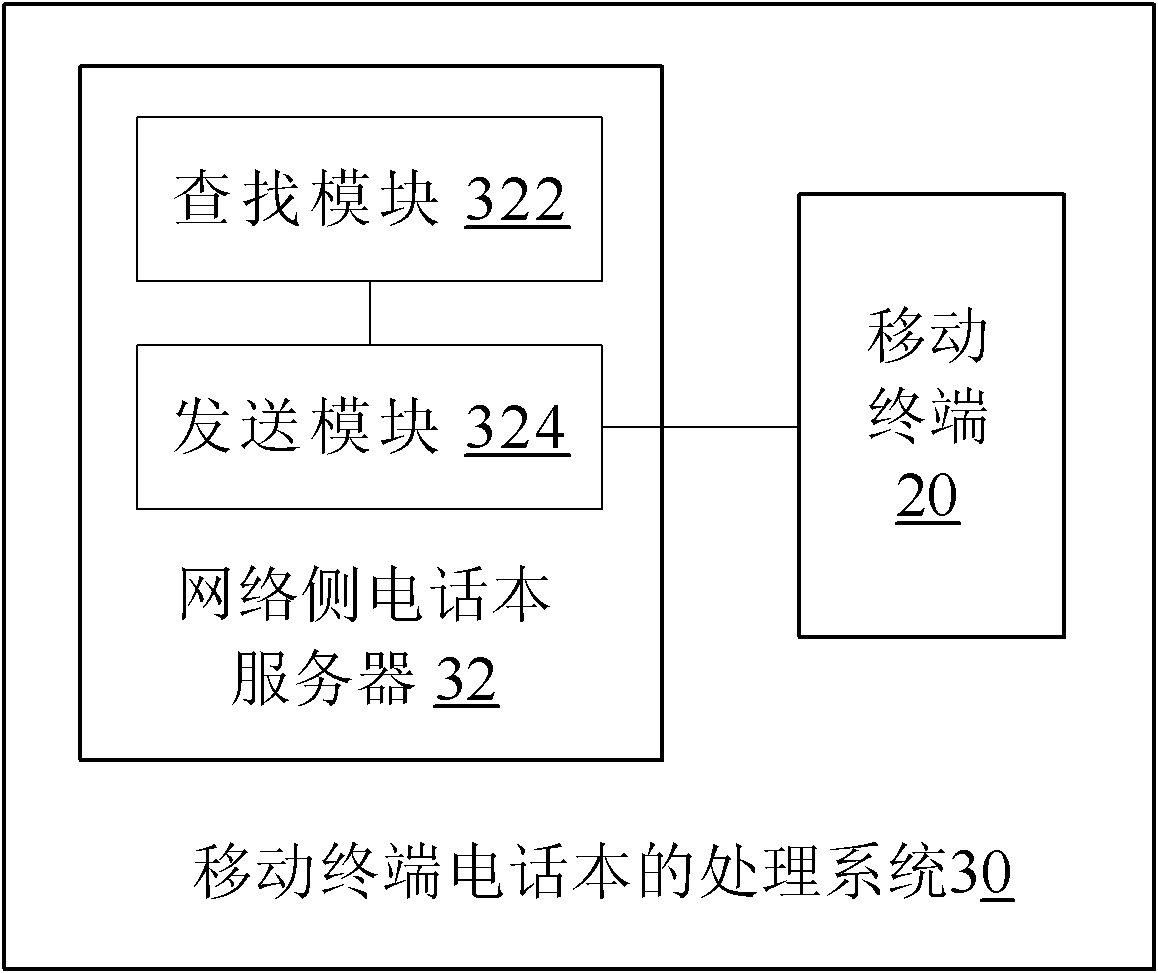
Method and system for processing contacts of mobile terminal and mobile terminal
ActiveCN102075626ASolve the problem of occupying EFS spaceReduce occupancySubstation equipmentNetwork data managementRandom access memoryEncrypting file system
The invention discloses a method and a system for processing contacts of a mobile terminal and a mobile terminal. The method comprises the steps that: the mobile terminal acquires the contacts thereof after startup; and the mobile terminal only stores the contacts acquired by the mobile terminal in a random access memory (RAM) and does not perform writing encrypt file system (EFS) file operation. The method, the system and the mobile terminal save EFS space, reduce the product cost of manufacturers and improve the product competitiveness of manufacturers.
Owner:ZTE CORP
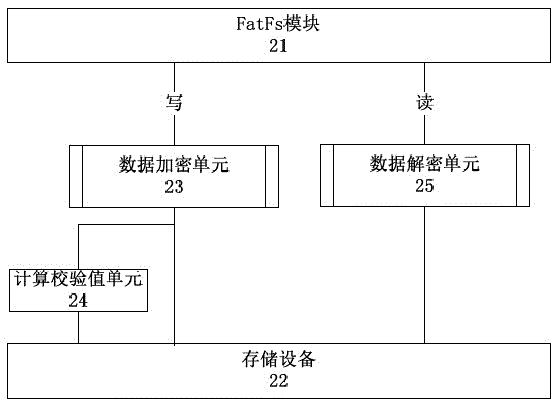
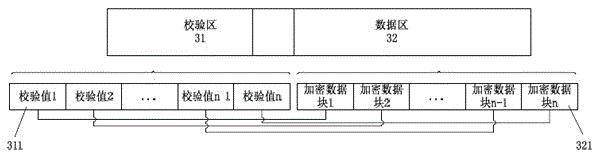
FatFs based encrypted file system and implementation method thereof
The invention discloses a FatFs based encrypted file system and an implementation method thereof. The implementation method of the FatFs based encrypted file system comprises the steps of encrypting data while being stored through an encryption and decryption layer, calculating check values of the encrypted data and writing the check values and the encrypted data into a storage device, wherein each data block corresponds to one check value; and taking the encrypted data out of the storage device while reading the data and decrypting the encrypted data through the encryption and decryption layer to obtain a plaintext. According to the FatFs based encrypted file system and the implementation method thereof, risks caused by tampering of the data can be avoided.
Owner:SHENZHEN ZHENGTONG ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com