Encrypted file system based on multi-image files
A technology for encrypting file systems and files. It is applied in the field of information security and can solve problems such as trouble, frequent flashing, clearing cache, and data leakage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0052] Embodiment 1. User space encrypted file system based on multi-image files
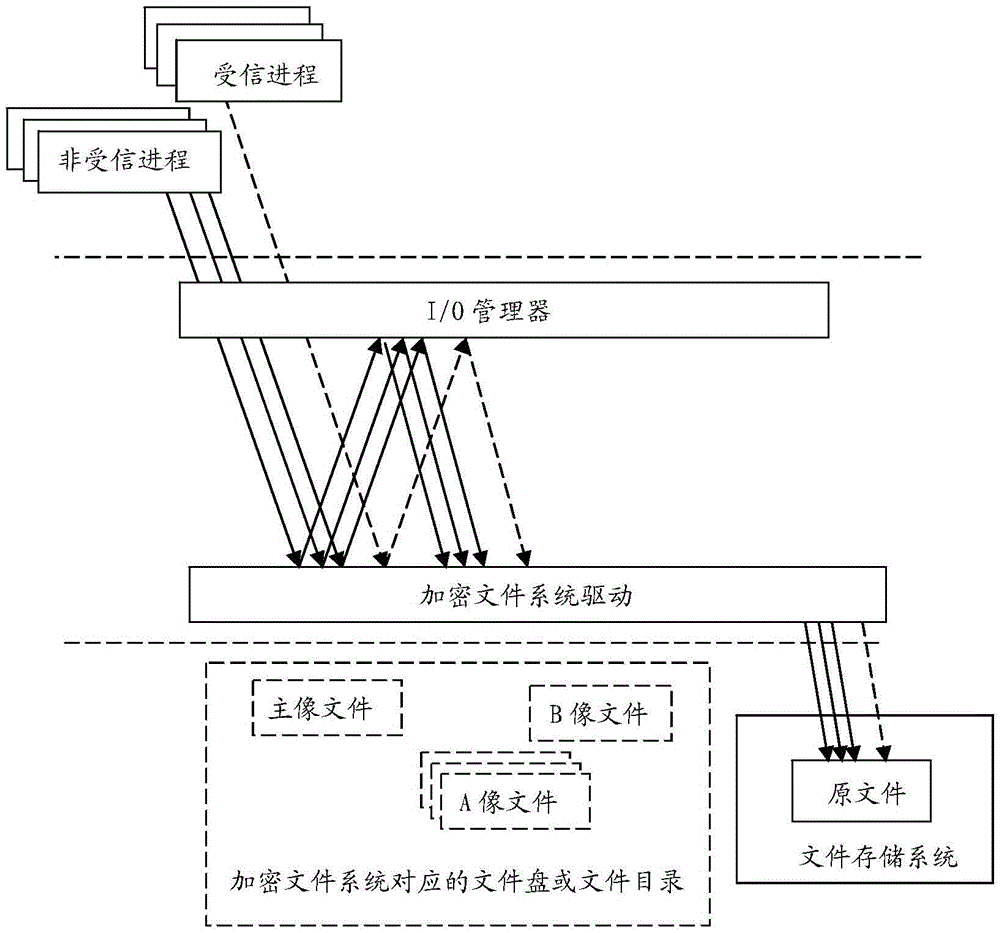
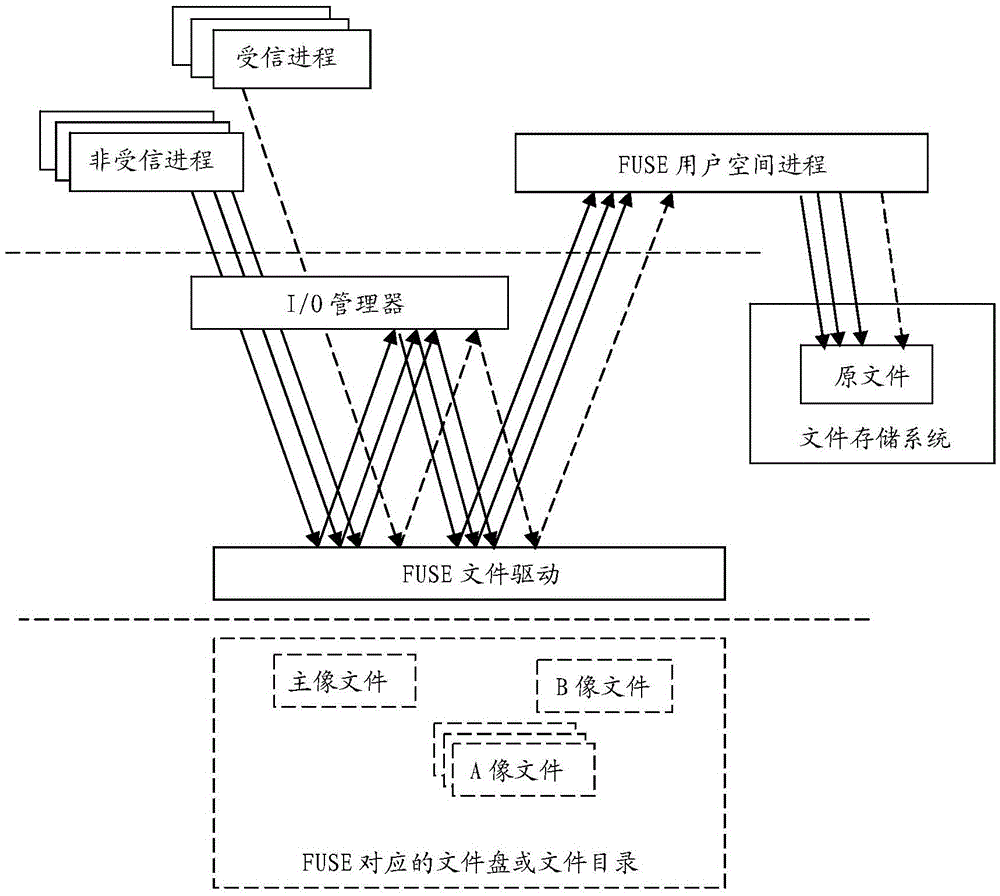
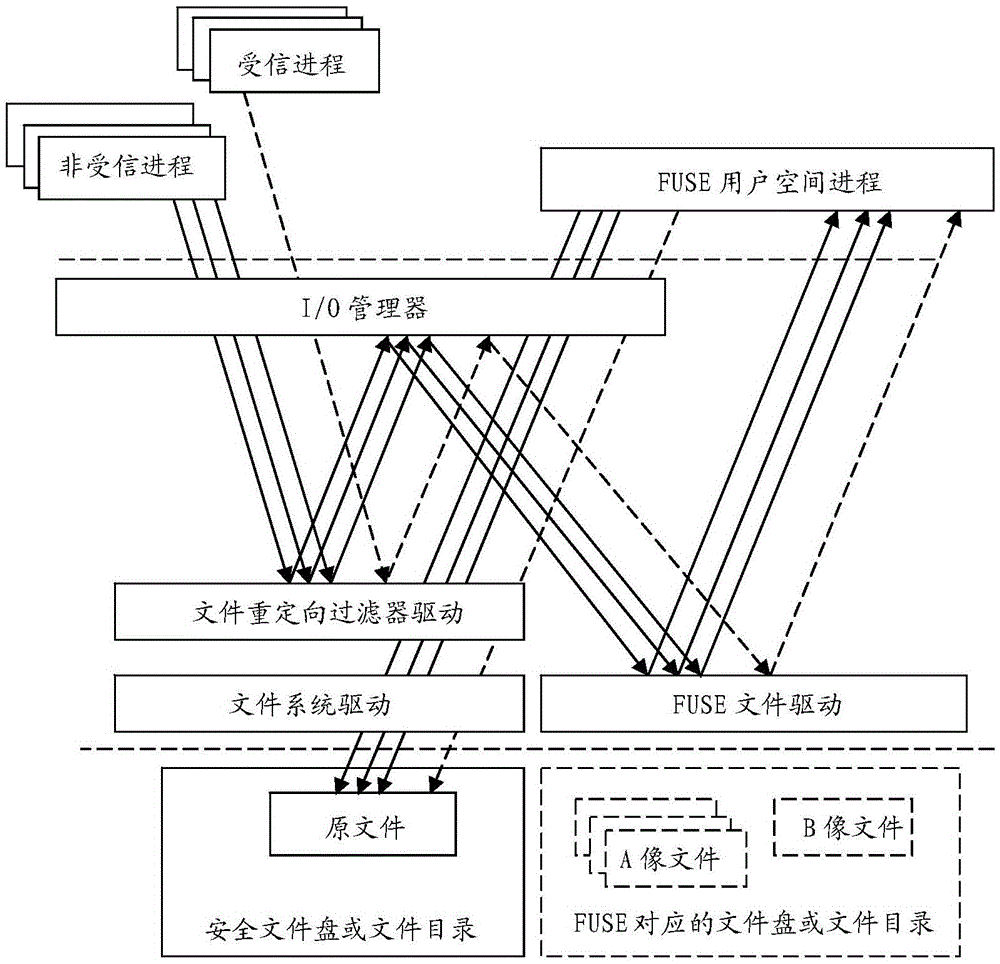
[0053] Such as figure 2 Shown, utilize the present invention and user space file system (FileSysteminUserSpace, FUSE) technology to develop a user space encrypted file system (a file system storing ciphertext), comprise FUSE file driver and FUSE user space process, wherein, FUSE file driver is The file system driver of the user space file system, the FUSE user space process is the running process of the user space program that the user space file system performs file I / O operation processing. Trusted process and untrusted process discrimination, file redirection, file data is plaintext or ciphertext discrimination, file data encryption and decryption processing and other functions (part or all) are implemented in the FUSE file driver, or (part or all) in the FUSE user Space process (program) implementation. If these functions (part or all) are driven and implemented in the FUSE file, it is no...
Embodiment approach 1
[0065] Use the strings corresponding to serial numbers 0, 1, 2, ...; the encrypted file system records the A image file or B image file that each original file is currently opened or created ; When the file opening or creation operation for a main image file is redirected to the A image file or the B image file of the corresponding original file, the encrypted file system selects an unused serial number of the A image file or the B image file as , For example, randomly select an unused serial number, or select the smallest unused serial number, or select a serial number that is 1 greater than the used serial number, etc.
Embodiment approach 2
[0067] The time is counted in milliseconds from a fixed moment. When redirecting an operation of opening or creating a main image file, the encrypted file system uses the string of the time count value at the current moment as the redirected A image. file or B like file .
[0068] The above two schemes are suitable for both ordinary files and file directories.
[0069] As can be seen from the above scheme, the file path of the A image file and the B image file contains the file path of the main image file, and the encrypted file system can determine the main image to be operated by the program process through the file path of the A image file or the B image file file to determine the original file to operate on. Since the file directories K:\__AFiles\ and K:\__BFiles\ have special purposes here, they cannot be used as ordinary file directories. The encrypted file system can check whether the file path of a file contains the file directory K:\__AFiles\ or K:\__BFiles\,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com